Quick Enquiry Form
Categories
- Agile and Scrum (187)
- BigData (21)
- Business Analysis (87)
- Cirtix Client Administration (51)
- Cisco (59)
- Cloud Technology (71)
- Cyber Security (41)
- Data Science and Business Intelligence (35)
- Developement Courses (46)
- DevOps (15)
- Digital Marketing (50)
- Emerging Technology (172)
- IT Service Management (70)
- Microsoft (52)
- Other (393)
- Project Management (471)
- Quality Management (127)
- salesforce (62)
Latest posts
Mastering Cisco UCS Management The..
CCNP Ultimate Path to Networking..
Understanding CISS Key Concepts and..
Free Resources
Subscribe to Newsletter
The Benefits of Implementing RPA in Your Business
In today's fast-paced and highly competitive business landscape, organizations are constantly seeking innovative ways to enhance their operations, reduce costs, and drive growth. Robotic Process Automation (RPA) has emerged as a transformative solution, offering a plethora of benefits that can revolutionize the way businesses operate.
RPA is more than just a buzzword; it's a game-changer. It leverages the capabilities of software robots to automate repetitive, rule-based tasks that were once performed by humans. From data entry and invoicing to customer support and HR processes, RPA is redefining the modern business landscape in a profound way.
In this blog post, we'll explore the incredible advantages of implementing RPA in your business. We'll delve into the ways it can boost productivity, cut operational costs, and empower your employees to focus on more strategic, value-added tasks. We'll also discuss how RPA enables your organization to adapt to ever-changing workloads and market demands while ensuring compliance and enhancing customer satisfaction.
Join us on this journey to uncover the true potential of RPA and learn how it can be a key driver of success in your business.Let's embark on this automation adventure together.
Table of contents
-
Increased Productivity: How RPA Streamlines Repetitive Tasks
-
Cost Savings: The Financial Benefits of RPA Implementation
-
Error Reduction: Enhancing Accuracy Through Automation
-
24/7 Operations: The Advantage of RPA in Workflow Continuity
-
Scalability: Adapting Your Business to Changing Workloads with RPA
-
Employee Satisfaction: Empowering Workers with RPA
-
Data Insights: Leveraging RPA for Improved Decision-Making
-
Customer Experience Improvement: RPA's Impact on Service Quality
-
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
-
Competitive Advantage: Staying Ahead in Your Industry with RPA
-
Conclusion
Increased Productivity: How RPA Streamlines Repetitive Tasks
In the relentless pursuit of operational excellence, businesses are increasingly turning to Robotic Process Automation (RPA) to revolutionize the way they handle repetitive and time-consuming tasks. Imagine a world where your workforce is liberated from mundane, repetitive chores, and your business can redirect its human talent towards creative and strategic endeavors. That's the promise of RPA, and in this article, we'll explore how it supercharges productivity by streamlining those monotonous tasks.
Automating the Mundane: RPA is the unsung hero of the business world. It excels at handling rule-based, repetitive tasks with precision and consistency. From data entry and report generation to invoice processing and email sorting, RPA tirelessly executes these activities, freeing up your human workforce for more meaningful, challenging, and engaging work.
24/7 Operations: Unlike human employees, RPA bots don't need breaks, sleep, or holidays. They work around the clock, ensuring that critical processes continue without interruption. This 24/7 availability not only accelerates task completion but also enhances customer service and response times.
Error Elimination: Human errors can be costly in terms of both time and money. RPA reduces the risk of errors to near zero. Bots follow predefined rules meticulously, resulting in accurate and consistent outcomes. This not only saves resources but also enhances the quality of your operations.
Scalability: As your business grows, so does the volume of repetitive tasks. RPA scales effortlessly, accommodating increased workloads without the need for lengthy recruitment and training processes. It's a flexible solution that grows with your business, allowing you to adapt to changing demands seamlessly.
Rapid Task Execution: With RPA, tasks that would take hours or days to complete manually can be executed in seconds or minutes. This expedited task execution enables your business to respond quickly to customer needs, market shifts, and other time-sensitive factors.
Enhanced Employee Satisfaction: Imagine your employees no longer bogged down by mind-numbing, repetitive work. RPA liberates your workforce from the most tedious aspects of their jobs, leading to increased job satisfaction and the ability to focus on tasks that require human creativity, decision-making, and critical thinking.
Cost Savings: The Financial Benefits of RPA Implementation
In an era where cost efficiency is paramount for businesses of all sizes, Robotic Process Automation (RPA) stands out as a formidable ally. It's not just about automation for the sake of it; it's about achieving substantial financial benefits through intelligent, rule-based processes. In this article, we'll explore how RPA can translate into real cost savings for your organization.
Reduced Labor Costs: The most immediate and noticeable cost savings with RPA come from a decreased reliance on human labor for repetitive tasks. RPA bots work tirelessly, without breaks or holidays, and do not require salaries, benefits, or overtime pay. This not only reduces labor costs but also eliminates the need for temporary staff during peak workloads.
Error Minimization: Human errors can be costly, leading to rework, customer dissatisfaction, and sometimes even regulatory fines. RPA dramatically reduces the risk of errors, ensuring that tasks are executed with a high degree of accuracy. This, in turn, mitigates the costs associated with correcting mistakes.
Improved Efficiency: RPA streamlines processes, making them more efficient and faster. Tasks that once took hours or days to complete manually can be accomplished in a fraction of the time with RPA. This increased efficiency allows your workforce to focus on higher-value tasks and revenue-generating activities.
Scalability Without Additional Costs: As your business grows, you may need to handle more transactions or process more data. Scaling up with human employees can be expensive, involving recruitment, training, and office space costs. RPA, on the other hand, scales easily without incurring additional costs.
Reduced Operational Costs: RPA can optimize various operational costs. It can help in inventory management, supply chain optimization, and other processes, reducing costs associated with excess inventory, carrying costs, and logistics.
Energy and Resource Savings: Automation doesn't just save labor costs; it can also lead to reduced energy consumption. RPA bots run on servers and data centers, which can be more energy-efficient than maintaining large office spaces with numerous employees.
the financial benefits of RPA implementation are substantial. It's not just about cutting costs; it's about doing so while improving operational efficiency, reducing errors, and allowing your employees to focus on strategic, value-adding tasks. RPA isn't an expense; it's an investment that pays off by delivering significant cost savings and contributing to the overall financial health of your organization. It's time to embrace RPA as a key driver of fiscal prudence and financial success.
Error Reduction: Enhancing Accuracy Through Automation
In the world of business, accuracy is not a mere aspiration; it's a prerequisite for success. Mistakes can be costly, resulting in financial losses, customer dissatisfaction, and even reputational damage. Fortunately, automation, specifically Robotic Process Automation (RPA), has emerged as a powerful tool for enhancing accuracy by minimizing errors. In this article, we'll explore how RPA's precision transforms the operational landscape of businesses.
Perfect Consistency: RPA bots are meticulously programmed to follow predefined rules and instructions. They execute tasks with unwavering consistency, ensuring that the same standard is upheld for every transaction, every time. This perfect consistency is a stark contrast to human work, which can be influenced by factors like fatigue, distractions, or oversight.
Reduction in Human Error: Human errors, no matter how diligent the employees, are an inherent part of manual processes. RPA mitigates this risk by automating rule-based tasks. Whether it's data entry, order processing, or calculations, RPA eliminates the potential for common errors such as typos, miscalculations, and missed steps.
Elimination of Repetitive Mistakes: Over time, repetitive tasks can become mundane, leading to inattentiveness and a higher likelihood of errors. RPA doesn't suffer from such lapses in attention. It tirelessly performs tasks with precision, without being influenced by factors that can lead to mistakes.
Error Monitoring and Reporting: RPA systems are equipped with error monitoring and reporting capabilities. If an issue arises, the system can detect it quickly and often correct it automatically. In cases where human intervention is required, the error is flagged for attention, reducing the chances of unnoticed errors that can compound over time.
24/7 Operations: The Advantage of RPA in Workflow Continuity
In a globalized and interconnected world, business operations are expected to run seamlessly around the clock. However, the human workforce has its limitations, including the need for rest and downtime. This is where Robotic Process Automation (RPA) steps in, offering a substantial advantage in workflow continuity through its ability to operate 24/7. In this article, we will delve into how RPA empowers businesses to break free from the constraints of traditional working hours.
Non-Stop Productivity: One of the most compelling advantages of RPA is its capacity for non-stop, 24/7 operations. RPA bots are not bound by the constraints of the human workday, allowing tasks to be executed continuously, even during evenings, weekends, and holidays. This round-the-clock productivity enhances the efficiency of critical business processes.
Reduced Response Times: With 24/7 RPA, customer inquiries, orders, and requests can be addressed instantly. This reduction in response times not only enhances customer satisfaction but can also give your business a competitive edge in industries where responsiveness is crucial.
No Overtime or Shift Work: Employing human workers for continuous operations typically involves overtime pay, shift differentials, and the associated costs of additional personnel management. RPA eliminates these costs while maintaining consistent, uninterrupted operations.
High Availability: RPA systems are designed for high availability. They can be configured to run on redundant servers or in the cloud, ensuring that operations continue even in the event of technical failures. This minimizes downtime and ensures uninterrupted workflow.
Enhanced Operational Efficiency: 24/7 RPA doesn't just mean working more hours; it means working more efficiently. Tasks are executed consistently and without the fluctuations in performance that can occur during late shifts or overnight hours.
The advantage of RPA in enabling 24/7 operations is a transformative element in the modern business landscape. It ensures that critical processes continue seamlessly, improves responsiveness, and reduces the costs associated with shift work and downtime. RPA's ability to work tirelessly and without interruption is a crucial factor in maintaining workflow continuity and meeting the demands of a 24/7 global economy.
Scalability: Adapting Your Business to Changing Workloads with RPA
In the dynamic and ever-evolving world of business, the ability to adapt to changing workloads is paramount for success. Robotic Process Automation (RPA) emerges as a pivotal solution, offering businesses the flexibility to scale their operations efficiently. In this article, we'll explore how RPA empowers organizations to seamlessly adjust to fluctuating demands, ensuring agility and sustained growth.
Handling Workload Peaks: Workload fluctuations are a common challenge for businesses. Seasonal spikes, promotions, or unforeseen events can cause a sudden surge in operational demands. RPA's scalability enables organizations to effortlessly address these peaks without the need for extensive human resource adjustments.
Speed and Accuracy: RPA bots can handle tasks with exceptional speed and accuracy. This not only ensures that tasks are completed on time during high-demand periods but also minimizes the risk of errors, contributing to a smoother scaling process.
Continuous Operation: RPA operates 24/7, providing continuous support for scaling efforts. Whether your business operates in multiple time zones or faces constant demand, RPA ensures that the scalability process can be ongoing and uninterrupted.
Improved Resource Allocation: The scalability offered by RPA allows human employees to focus on tasks that require creativity, decision-making, and critical thinking. This improved resource allocation not only enhances the quality of work but also promotes employee job satisfaction.
Rapid Deployment: Deploying additional RPA bots or reconfiguring existing ones can be achieved quickly. This agility is particularly valuable when responding to unexpected changes in workload, such as market fluctuations or emerging business opportunities.
Scalability Planning: RPA's analytics and data-driven insights can assist in proactive scalability planning. By analyzing historical data, businesses can anticipate workload fluctuations and adjust their RPA deployments accordingly.
The scalability that RPA offers is a strategic asset for businesses looking to adapt to changing workloads and seize growth opportunities. Whether you're aiming to respond to seasonal variations, sudden market shifts, or simply improve the efficiency of your daily operations, RPA provides a scalable solution that optimizes your resources and ensures that your business can remain agile and competitive in an ever-changing business landscape.
Employee Satisfaction: Empowering Workers with RPA
In the quest for business success, employee satisfaction is a critical factor that should never be underestimated. Satisfied and empowered employees are more productive, creative, and loyal to their organizations. Robotic Process Automation (RPA) plays a vital role in achieving these goals by relieving employees of mundane, repetitive tasks and giving them the opportunity to focus on higher-value, more fulfilling work. In this article, we'll explore how RPA empowers workers, leading to greater job satisfaction and overall success.
Skill Development: Employees empowered by RPA have the opportunity to develop new skills. As they transition to more complex, strategic roles, they can acquire valuable competencies that benefit both their personal growth and the organization.
Increased Job Satisfaction: By eliminating the least satisfying aspects of a job, RPA contributes to higher job satisfaction. Employees who find their work engaging and fulfilling are more likely to be committed to their roles and remain with the company for the long term.
Work-Life Balance: RPA's ability to handle tasks 24/7 ensures that employees are not burdened with late-night or weekend work to meet deadlines. This supports a healthier work-life balance, reducing stress and enhancing overall well-being.
Employee Empowerment: Employees often feel more empowered and valued when their employers invest in technologies like RPA to improve the work environment. This empowerment can boost morale and motivation.
Fostering Innovation: Employees freed from routine tasks can focus on more innovative and creative work. This not only benefits the company by driving innovation but also leads to a more fulfilling work experience for employees.
Consistency and Quality: RPA's ability to perform tasks with a high degree of accuracy ensures that employees can rely on consistent and error-free results in their work. This consistency reduces frustration and the need for rework.
Employee Feedback: RPA can be used to gather and process employee feedback more efficiently. By automating the data collection and analysis, it allows management to respond more effectively to concerns and suggestions, further boosting employee satisfaction.
RPA is a powerful tool for empowering employees and enhancing their job satisfaction. By automating repetitive tasks, it frees up time for more meaningful and challenging work, allows for skill development, and fosters a positive work environment. This not only benefits individual employees but also contributes to the overall success and competitiveness of the organization. It's a win-win scenario where both employees and the business thrive.
Data Insights: Leveraging RPA for Improved Decision-Making
In today's data-driven business landscape, making informed decisions is paramount for success. Fortunately, Robotic Process Automation (RPA) goes beyond task automation – it's a powerful tool for unlocking valuable data insights that can transform the way organizations make decisions. In this article, we'll explore how RPA can be harnessed to collect, process, and leverage data for more informed and strategic decision-making.
Data Collection and Aggregation: RPA can collect and aggregate data from various sources, including databases, spreadsheets, and online platforms. By automating the data collection process, it ensures data integrity and reduces the risk of human errors.
Real-Time Data Processing: RPA can process data in real-time, providing up-to-the-minute information that's crucial for making timely decisions. This real-time processing is especially valuable in fast-paced industries and competitive markets.
Data Cleansing and Quality Assurance: RPA can be programmed to cleanse and validate data, ensuring that it's accurate and reliable. This step is essential for high-quality decision-making, as inaccurate data can lead to poor judgments.
Predictive Analytics: RPA can be combined with predictive analytics models to forecast trends, identify potential issues, and recommend actions. This empowers decision-makers to proactively address challenges and seize opportunities.
Customized Reports and Dashboards: RPA can generate customized reports and dashboards that present data in a clear and actionable format. Decision-makers can quickly access the information they need, facilitating faster and more informed choices.
Exception Handling: RPA can identify exceptions or anomalies in data. When exceptions occur, RPA can alert decision-makers, enabling them to investigate and respond promptly to issues.
Compliance and Audit Trail: RPA ensures that tasks are executed according to predefined rules, creating a robust audit trail. This audit trail is invaluable for compliance with regulatory requirements and is a valuable resource for decision-making during audits.
RPA is not just about automating tasks; it's a key enabler of data-driven decision-making. By collecting, processing, and providing valuable data insights, RPA equips organizations to make informed, strategic decisions that can drive growth, efficiency, and competitive advantage. The ability to harness the power of data is a transformative asset in the modern business world, and RPA plays a central role in unlocking its potential.
Customer Experience Improvement: RPA's Impact on Service Quality
In an era where customer satisfaction can make or break a business, delivering an exceptional customer experience is a top priority. Robotic Process Automation (RPA) has emerged as a powerful tool for improving service quality and ensuring a seamless, satisfying customer journey. In this article, we'll explore how RPA positively impacts the customer experience and contributes to the success of businesses.
Faster Response Times: RPA can respond to customer inquiries and requests in real-time. This immediate response ensures that customers don't have to wait, enhancing their perception of your service quality.
Error Reduction: RPA minimizes errors in tasks such as order processing and data entry. Fewer mistakes mean fewer issues for customers to deal with, resulting in a smoother, more reliable experience.
24/7 Availability: RPA operates around the clock, ensuring that customers can interact with your business at any time. This high availability caters to diverse schedules and time zones, providing a more customer-centric experience.
Enhanced Data Security: RPA's robust security measures protect customer data and sensitive information. By safeguarding their data, you build trust and confidence, further improving the customer experience.
Proactive Issue Resolution: RPA can monitor systems for issues and exceptions in real-time. When issues arise, RPA can alert human staff to take corrective action promptly, minimizing customer disruption.
RPA is a game-changer in improving the customer experience. By reducing response times, minimizing errors, ensuring availability, and enhancing data security, RPA contributes to a higher level of customer satisfaction. Businesses that leverage RPA for service quality enhancements not only retain loyal customers but also gain a competitive edge in an environment where customer experience is a defining factor in success. RPA isn't just about efficiency; it's about enhancing the human touch in customer service and ensuring that customers receive the best service possible.
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
In today's highly regulated business environment, compliance with industry-specific and government-mandated regulations is a non-negotiable aspect of operation. The failure to meet regulatory requirements can lead to significant legal consequences, fines, and damage to a company's reputation. Robotic Process Automation (RPA) offers a powerful solution for ensuring compliance and audit readiness. In this article, we'll explore how RPA can help businesses meet regulatory requirements and prepare for audits effectively.
Rule-Based Consistency: RPA excels at executing tasks following predefined rules and standards. This inherent consistency ensures that business processes are executed in a compliant manner every time.
Automated Data Logging: RPA can automatically record and log all actions taken during its processes. This comprehensive data logging provides a transparent audit trail, ensuring that regulators and auditors can easily review and verify compliance.
Real-Time Monitoring: RPA systems can monitor processes in real-time, identifying and rectifying deviations from compliance standards as they occur. This proactive approach minimizes the risk of non-compliance issues going unnoticed.
Data Security and Privacy: RPA is designed to protect sensitive data. By automating data handling and storage, it reduces the risk of data breaches and ensures that personally identifiable information (PII) and other sensitive data are handled in a compliant manner.
Regulatory Reporting: RPA can automate the collection and preparation of reports required for regulatory compliance. This not only reduces the time and effort required for reporting but also minimizes the risk of errors in these critical documents.
Controlled Access: RPA allows for controlled access to sensitive systems and data. By limiting access to authorized personnel and automating role-based permissions, it enhances security and compliance with access control regulations.
Reducing Human Error: Many compliance issues arise from human error. RPA minimizes these errors, which can lead to non-compliance, fines, and other penalties.
RPA is a vital tool for meeting regulatory requirements and achieving audit readiness. It not only protects businesses from legal consequences and fines but also allows them to focus on their core operations, knowing that they are operating within the boundaries of the law. RPA doesn't just streamline processes; it safeguards businesses and enhances their ability to navigate complex regulatory landscapes with confidence.
Competitive Advantage: Staying Ahead in Your Industry with RPA
In the fast-paced and ever-evolving world of business, staying ahead of the competition is a constant challenge. To gain a competitive edge, organizations must be agile, efficient, and innovative. Robotic Process Automation (RPA) offers a significant advantage by providing the tools to streamline operations, reduce costs, and make data-driven decisions. In this article, we'll explore how RPA can be a catalyst for achieving a competitive advantage in your industry.
Operational Efficiency: RPA optimizes business processes by automating repetitive and rule-based tasks. This increased efficiency enables your organization to deliver products and services more quickly and cost-effectively, giving you an edge in the market.
Cost Reduction: By automating tasks and minimizing errors, RPA reduces operational costs. This allows your business to allocate resources strategically, invest in growth, and potentially offer competitive pricing to customers.
Customer Satisfaction: RPA enhances the customer experience by ensuring faster response times, personalized interactions, and error-free service. Satisfied customers are more likely to remain loyal and recommend your business to others.
Real-Time Data Insights: RPA collects and processes data in real-time, providing valuable insights into market trends, customer behavior, and operational performance. These insights can be leveraged to make informed decisions and stay ahead of market shifts.
Innovation and Creativity: By automating routine tasks, RPA liberates your workforce from the mundane, allowing them to focus on creative, strategic, and value-added activities. This fosters a culture of innovation and provides a competitive advantage in product and service development.
Strategic Decision-Making: With RPA, your organization can make data-driven decisions more efficiently. This strategic approach to decision-making allows you to anticipate market trends, spot opportunities, and outmaneuver competitors.
RPA is a game-changer for businesses seeking to gain a competitive advantage in their industries. By increasing operational efficiency, reducing costs, enhancing customer satisfaction, and providing real-time insights, RPA empowers organizations to stay ahead in rapidly changing markets. It's not just about streamlining processes; it's about positioning your business to lead, innovate, and thrive in a highly competitive world. RPA is the key to not just keeping pace but setting the pace in your industry.
Conclusion
In conclusion, Robotic Process Automation (RPA) is a transformative force in the modern business landscape, offering a multitude of benefits that can revolutionize the way organizations operate. Throughout this series of articles, we've explored the diverse advantages of RPA and how it can be harnessed to enhance different aspects of business operations.
RPA's ability to operate 24/7 ensures workflow continuity, allowing businesses to adapt to fluctuating workloads, meet global demands, and maintain a competitive edge. It offers employees the opportunity to focus on more meaningful tasks, fostering job satisfaction, skill development, and innovation.
RPA leverages data insights to facilitate data-driven decision-making, enabling businesses to respond to market changes and opportunities with agility and precision. It improves the customer experience through faster response times, reduced errors, and personalized interactions, leading to higher customer satisfaction and loyalty.
In a world where efficiency, agility, and customer satisfaction are paramount, RPA is more than a tool for automation; it's a strategic asset that empowers businesses to thrive and excel. Embracing the automation revolution is not just a choice; it's a necessity for organizations that aim to remain competitive, innovative, and successful in the ever-evolving business landscape.
Read More
In today's fast-paced and highly competitive business landscape, organizations are constantly seeking innovative ways to enhance their operations, reduce costs, and drive growth. Robotic Process Automation (RPA) has emerged as a transformative solution, offering a plethora of benefits that can revolutionize the way businesses operate.
RPA is more than just a buzzword; it's a game-changer. It leverages the capabilities of software robots to automate repetitive, rule-based tasks that were once performed by humans. From data entry and invoicing to customer support and HR processes, RPA is redefining the modern business landscape in a profound way.
In this blog post, we'll explore the incredible advantages of implementing RPA in your business. We'll delve into the ways it can boost productivity, cut operational costs, and empower your employees to focus on more strategic, value-added tasks. We'll also discuss how RPA enables your organization to adapt to ever-changing workloads and market demands while ensuring compliance and enhancing customer satisfaction.
Join us on this journey to uncover the true potential of RPA and learn how it can be a key driver of success in your business.Let's embark on this automation adventure together.
Table of contents
-
Increased Productivity: How RPA Streamlines Repetitive Tasks
-
Cost Savings: The Financial Benefits of RPA Implementation
-
Error Reduction: Enhancing Accuracy Through Automation
-
24/7 Operations: The Advantage of RPA in Workflow Continuity
-
Scalability: Adapting Your Business to Changing Workloads with RPA
-
Employee Satisfaction: Empowering Workers with RPA
-
Data Insights: Leveraging RPA for Improved Decision-Making
-
Customer Experience Improvement: RPA's Impact on Service Quality
-
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
-
Competitive Advantage: Staying Ahead in Your Industry with RPA
-
Conclusion
Increased Productivity: How RPA Streamlines Repetitive Tasks
In the relentless pursuit of operational excellence, businesses are increasingly turning to Robotic Process Automation (RPA) to revolutionize the way they handle repetitive and time-consuming tasks. Imagine a world where your workforce is liberated from mundane, repetitive chores, and your business can redirect its human talent towards creative and strategic endeavors. That's the promise of RPA, and in this article, we'll explore how it supercharges productivity by streamlining those monotonous tasks.
Automating the Mundane: RPA is the unsung hero of the business world. It excels at handling rule-based, repetitive tasks with precision and consistency. From data entry and report generation to invoice processing and email sorting, RPA tirelessly executes these activities, freeing up your human workforce for more meaningful, challenging, and engaging work.
24/7 Operations: Unlike human employees, RPA bots don't need breaks, sleep, or holidays. They work around the clock, ensuring that critical processes continue without interruption. This 24/7 availability not only accelerates task completion but also enhances customer service and response times.
Error Elimination: Human errors can be costly in terms of both time and money. RPA reduces the risk of errors to near zero. Bots follow predefined rules meticulously, resulting in accurate and consistent outcomes. This not only saves resources but also enhances the quality of your operations.
Scalability: As your business grows, so does the volume of repetitive tasks. RPA scales effortlessly, accommodating increased workloads without the need for lengthy recruitment and training processes. It's a flexible solution that grows with your business, allowing you to adapt to changing demands seamlessly.
Rapid Task Execution: With RPA, tasks that would take hours or days to complete manually can be executed in seconds or minutes. This expedited task execution enables your business to respond quickly to customer needs, market shifts, and other time-sensitive factors.
Enhanced Employee Satisfaction: Imagine your employees no longer bogged down by mind-numbing, repetitive work. RPA liberates your workforce from the most tedious aspects of their jobs, leading to increased job satisfaction and the ability to focus on tasks that require human creativity, decision-making, and critical thinking.
Cost Savings: The Financial Benefits of RPA Implementation
In an era where cost efficiency is paramount for businesses of all sizes, Robotic Process Automation (RPA) stands out as a formidable ally. It's not just about automation for the sake of it; it's about achieving substantial financial benefits through intelligent, rule-based processes. In this article, we'll explore how RPA can translate into real cost savings for your organization.
Reduced Labor Costs: The most immediate and noticeable cost savings with RPA come from a decreased reliance on human labor for repetitive tasks. RPA bots work tirelessly, without breaks or holidays, and do not require salaries, benefits, or overtime pay. This not only reduces labor costs but also eliminates the need for temporary staff during peak workloads.
Error Minimization: Human errors can be costly, leading to rework, customer dissatisfaction, and sometimes even regulatory fines. RPA dramatically reduces the risk of errors, ensuring that tasks are executed with a high degree of accuracy. This, in turn, mitigates the costs associated with correcting mistakes.
Improved Efficiency: RPA streamlines processes, making them more efficient and faster. Tasks that once took hours or days to complete manually can be accomplished in a fraction of the time with RPA. This increased efficiency allows your workforce to focus on higher-value tasks and revenue-generating activities.
Scalability Without Additional Costs: As your business grows, you may need to handle more transactions or process more data. Scaling up with human employees can be expensive, involving recruitment, training, and office space costs. RPA, on the other hand, scales easily without incurring additional costs.
Reduced Operational Costs: RPA can optimize various operational costs. It can help in inventory management, supply chain optimization, and other processes, reducing costs associated with excess inventory, carrying costs, and logistics.
Energy and Resource Savings: Automation doesn't just save labor costs; it can also lead to reduced energy consumption. RPA bots run on servers and data centers, which can be more energy-efficient than maintaining large office spaces with numerous employees.
the financial benefits of RPA implementation are substantial. It's not just about cutting costs; it's about doing so while improving operational efficiency, reducing errors, and allowing your employees to focus on strategic, value-adding tasks. RPA isn't an expense; it's an investment that pays off by delivering significant cost savings and contributing to the overall financial health of your organization. It's time to embrace RPA as a key driver of fiscal prudence and financial success.
Error Reduction: Enhancing Accuracy Through Automation
In the world of business, accuracy is not a mere aspiration; it's a prerequisite for success. Mistakes can be costly, resulting in financial losses, customer dissatisfaction, and even reputational damage. Fortunately, automation, specifically Robotic Process Automation (RPA), has emerged as a powerful tool for enhancing accuracy by minimizing errors. In this article, we'll explore how RPA's precision transforms the operational landscape of businesses.
Perfect Consistency: RPA bots are meticulously programmed to follow predefined rules and instructions. They execute tasks with unwavering consistency, ensuring that the same standard is upheld for every transaction, every time. This perfect consistency is a stark contrast to human work, which can be influenced by factors like fatigue, distractions, or oversight.
Reduction in Human Error: Human errors, no matter how diligent the employees, are an inherent part of manual processes. RPA mitigates this risk by automating rule-based tasks. Whether it's data entry, order processing, or calculations, RPA eliminates the potential for common errors such as typos, miscalculations, and missed steps.
Elimination of Repetitive Mistakes: Over time, repetitive tasks can become mundane, leading to inattentiveness and a higher likelihood of errors. RPA doesn't suffer from such lapses in attention. It tirelessly performs tasks with precision, without being influenced by factors that can lead to mistakes.
Error Monitoring and Reporting: RPA systems are equipped with error monitoring and reporting capabilities. If an issue arises, the system can detect it quickly and often correct it automatically. In cases where human intervention is required, the error is flagged for attention, reducing the chances of unnoticed errors that can compound over time.
24/7 Operations: The Advantage of RPA in Workflow Continuity
In a globalized and interconnected world, business operations are expected to run seamlessly around the clock. However, the human workforce has its limitations, including the need for rest and downtime. This is where Robotic Process Automation (RPA) steps in, offering a substantial advantage in workflow continuity through its ability to operate 24/7. In this article, we will delve into how RPA empowers businesses to break free from the constraints of traditional working hours.
Non-Stop Productivity: One of the most compelling advantages of RPA is its capacity for non-stop, 24/7 operations. RPA bots are not bound by the constraints of the human workday, allowing tasks to be executed continuously, even during evenings, weekends, and holidays. This round-the-clock productivity enhances the efficiency of critical business processes.
Reduced Response Times: With 24/7 RPA, customer inquiries, orders, and requests can be addressed instantly. This reduction in response times not only enhances customer satisfaction but can also give your business a competitive edge in industries where responsiveness is crucial.
No Overtime or Shift Work: Employing human workers for continuous operations typically involves overtime pay, shift differentials, and the associated costs of additional personnel management. RPA eliminates these costs while maintaining consistent, uninterrupted operations.
High Availability: RPA systems are designed for high availability. They can be configured to run on redundant servers or in the cloud, ensuring that operations continue even in the event of technical failures. This minimizes downtime and ensures uninterrupted workflow.
Enhanced Operational Efficiency: 24/7 RPA doesn't just mean working more hours; it means working more efficiently. Tasks are executed consistently and without the fluctuations in performance that can occur during late shifts or overnight hours.
The advantage of RPA in enabling 24/7 operations is a transformative element in the modern business landscape. It ensures that critical processes continue seamlessly, improves responsiveness, and reduces the costs associated with shift work and downtime. RPA's ability to work tirelessly and without interruption is a crucial factor in maintaining workflow continuity and meeting the demands of a 24/7 global economy.
Scalability: Adapting Your Business to Changing Workloads with RPA
In the dynamic and ever-evolving world of business, the ability to adapt to changing workloads is paramount for success. Robotic Process Automation (RPA) emerges as a pivotal solution, offering businesses the flexibility to scale their operations efficiently. In this article, we'll explore how RPA empowers organizations to seamlessly adjust to fluctuating demands, ensuring agility and sustained growth.
Handling Workload Peaks: Workload fluctuations are a common challenge for businesses. Seasonal spikes, promotions, or unforeseen events can cause a sudden surge in operational demands. RPA's scalability enables organizations to effortlessly address these peaks without the need for extensive human resource adjustments.
Speed and Accuracy: RPA bots can handle tasks with exceptional speed and accuracy. This not only ensures that tasks are completed on time during high-demand periods but also minimizes the risk of errors, contributing to a smoother scaling process.
Continuous Operation: RPA operates 24/7, providing continuous support for scaling efforts. Whether your business operates in multiple time zones or faces constant demand, RPA ensures that the scalability process can be ongoing and uninterrupted.
Improved Resource Allocation: The scalability offered by RPA allows human employees to focus on tasks that require creativity, decision-making, and critical thinking. This improved resource allocation not only enhances the quality of work but also promotes employee job satisfaction.
Rapid Deployment: Deploying additional RPA bots or reconfiguring existing ones can be achieved quickly. This agility is particularly valuable when responding to unexpected changes in workload, such as market fluctuations or emerging business opportunities.
Scalability Planning: RPA's analytics and data-driven insights can assist in proactive scalability planning. By analyzing historical data, businesses can anticipate workload fluctuations and adjust their RPA deployments accordingly.
The scalability that RPA offers is a strategic asset for businesses looking to adapt to changing workloads and seize growth opportunities. Whether you're aiming to respond to seasonal variations, sudden market shifts, or simply improve the efficiency of your daily operations, RPA provides a scalable solution that optimizes your resources and ensures that your business can remain agile and competitive in an ever-changing business landscape.
Employee Satisfaction: Empowering Workers with RPA
In the quest for business success, employee satisfaction is a critical factor that should never be underestimated. Satisfied and empowered employees are more productive, creative, and loyal to their organizations. Robotic Process Automation (RPA) plays a vital role in achieving these goals by relieving employees of mundane, repetitive tasks and giving them the opportunity to focus on higher-value, more fulfilling work. In this article, we'll explore how RPA empowers workers, leading to greater job satisfaction and overall success.
Skill Development: Employees empowered by RPA have the opportunity to develop new skills. As they transition to more complex, strategic roles, they can acquire valuable competencies that benefit both their personal growth and the organization.
Increased Job Satisfaction: By eliminating the least satisfying aspects of a job, RPA contributes to higher job satisfaction. Employees who find their work engaging and fulfilling are more likely to be committed to their roles and remain with the company for the long term.
Work-Life Balance: RPA's ability to handle tasks 24/7 ensures that employees are not burdened with late-night or weekend work to meet deadlines. This supports a healthier work-life balance, reducing stress and enhancing overall well-being.
Employee Empowerment: Employees often feel more empowered and valued when their employers invest in technologies like RPA to improve the work environment. This empowerment can boost morale and motivation.
Fostering Innovation: Employees freed from routine tasks can focus on more innovative and creative work. This not only benefits the company by driving innovation but also leads to a more fulfilling work experience for employees.
Consistency and Quality: RPA's ability to perform tasks with a high degree of accuracy ensures that employees can rely on consistent and error-free results in their work. This consistency reduces frustration and the need for rework.
Employee Feedback: RPA can be used to gather and process employee feedback more efficiently. By automating the data collection and analysis, it allows management to respond more effectively to concerns and suggestions, further boosting employee satisfaction.
RPA is a powerful tool for empowering employees and enhancing their job satisfaction. By automating repetitive tasks, it frees up time for more meaningful and challenging work, allows for skill development, and fosters a positive work environment. This not only benefits individual employees but also contributes to the overall success and competitiveness of the organization. It's a win-win scenario where both employees and the business thrive.
Data Insights: Leveraging RPA for Improved Decision-Making
In today's data-driven business landscape, making informed decisions is paramount for success. Fortunately, Robotic Process Automation (RPA) goes beyond task automation – it's a powerful tool for unlocking valuable data insights that can transform the way organizations make decisions. In this article, we'll explore how RPA can be harnessed to collect, process, and leverage data for more informed and strategic decision-making.
Data Collection and Aggregation: RPA can collect and aggregate data from various sources, including databases, spreadsheets, and online platforms. By automating the data collection process, it ensures data integrity and reduces the risk of human errors.
Real-Time Data Processing: RPA can process data in real-time, providing up-to-the-minute information that's crucial for making timely decisions. This real-time processing is especially valuable in fast-paced industries and competitive markets.
Data Cleansing and Quality Assurance: RPA can be programmed to cleanse and validate data, ensuring that it's accurate and reliable. This step is essential for high-quality decision-making, as inaccurate data can lead to poor judgments.
Predictive Analytics: RPA can be combined with predictive analytics models to forecast trends, identify potential issues, and recommend actions. This empowers decision-makers to proactively address challenges and seize opportunities.
Customized Reports and Dashboards: RPA can generate customized reports and dashboards that present data in a clear and actionable format. Decision-makers can quickly access the information they need, facilitating faster and more informed choices.
Exception Handling: RPA can identify exceptions or anomalies in data. When exceptions occur, RPA can alert decision-makers, enabling them to investigate and respond promptly to issues.
Compliance and Audit Trail: RPA ensures that tasks are executed according to predefined rules, creating a robust audit trail. This audit trail is invaluable for compliance with regulatory requirements and is a valuable resource for decision-making during audits.
RPA is not just about automating tasks; it's a key enabler of data-driven decision-making. By collecting, processing, and providing valuable data insights, RPA equips organizations to make informed, strategic decisions that can drive growth, efficiency, and competitive advantage. The ability to harness the power of data is a transformative asset in the modern business world, and RPA plays a central role in unlocking its potential.
Customer Experience Improvement: RPA's Impact on Service Quality
In an era where customer satisfaction can make or break a business, delivering an exceptional customer experience is a top priority. Robotic Process Automation (RPA) has emerged as a powerful tool for improving service quality and ensuring a seamless, satisfying customer journey. In this article, we'll explore how RPA positively impacts the customer experience and contributes to the success of businesses.
Faster Response Times: RPA can respond to customer inquiries and requests in real-time. This immediate response ensures that customers don't have to wait, enhancing their perception of your service quality.
Error Reduction: RPA minimizes errors in tasks such as order processing and data entry. Fewer mistakes mean fewer issues for customers to deal with, resulting in a smoother, more reliable experience.
24/7 Availability: RPA operates around the clock, ensuring that customers can interact with your business at any time. This high availability caters to diverse schedules and time zones, providing a more customer-centric experience.
Enhanced Data Security: RPA's robust security measures protect customer data and sensitive information. By safeguarding their data, you build trust and confidence, further improving the customer experience.
Proactive Issue Resolution: RPA can monitor systems for issues and exceptions in real-time. When issues arise, RPA can alert human staff to take corrective action promptly, minimizing customer disruption.
RPA is a game-changer in improving the customer experience. By reducing response times, minimizing errors, ensuring availability, and enhancing data security, RPA contributes to a higher level of customer satisfaction. Businesses that leverage RPA for service quality enhancements not only retain loyal customers but also gain a competitive edge in an environment where customer experience is a defining factor in success. RPA isn't just about efficiency; it's about enhancing the human touch in customer service and ensuring that customers receive the best service possible.
Compliance and Audit Readiness: Meeting Regulatory Requirements with RPA
In today's highly regulated business environment, compliance with industry-specific and government-mandated regulations is a non-negotiable aspect of operation. The failure to meet regulatory requirements can lead to significant legal consequences, fines, and damage to a company's reputation. Robotic Process Automation (RPA) offers a powerful solution for ensuring compliance and audit readiness. In this article, we'll explore how RPA can help businesses meet regulatory requirements and prepare for audits effectively.
Rule-Based Consistency: RPA excels at executing tasks following predefined rules and standards. This inherent consistency ensures that business processes are executed in a compliant manner every time.
Automated Data Logging: RPA can automatically record and log all actions taken during its processes. This comprehensive data logging provides a transparent audit trail, ensuring that regulators and auditors can easily review and verify compliance.
Real-Time Monitoring: RPA systems can monitor processes in real-time, identifying and rectifying deviations from compliance standards as they occur. This proactive approach minimizes the risk of non-compliance issues going unnoticed.
Data Security and Privacy: RPA is designed to protect sensitive data. By automating data handling and storage, it reduces the risk of data breaches and ensures that personally identifiable information (PII) and other sensitive data are handled in a compliant manner.
Regulatory Reporting: RPA can automate the collection and preparation of reports required for regulatory compliance. This not only reduces the time and effort required for reporting but also minimizes the risk of errors in these critical documents.
Controlled Access: RPA allows for controlled access to sensitive systems and data. By limiting access to authorized personnel and automating role-based permissions, it enhances security and compliance with access control regulations.
Reducing Human Error: Many compliance issues arise from human error. RPA minimizes these errors, which can lead to non-compliance, fines, and other penalties.
RPA is a vital tool for meeting regulatory requirements and achieving audit readiness. It not only protects businesses from legal consequences and fines but also allows them to focus on their core operations, knowing that they are operating within the boundaries of the law. RPA doesn't just streamline processes; it safeguards businesses and enhances their ability to navigate complex regulatory landscapes with confidence.
Competitive Advantage: Staying Ahead in Your Industry with RPA
In the fast-paced and ever-evolving world of business, staying ahead of the competition is a constant challenge. To gain a competitive edge, organizations must be agile, efficient, and innovative. Robotic Process Automation (RPA) offers a significant advantage by providing the tools to streamline operations, reduce costs, and make data-driven decisions. In this article, we'll explore how RPA can be a catalyst for achieving a competitive advantage in your industry.
Operational Efficiency: RPA optimizes business processes by automating repetitive and rule-based tasks. This increased efficiency enables your organization to deliver products and services more quickly and cost-effectively, giving you an edge in the market.
Cost Reduction: By automating tasks and minimizing errors, RPA reduces operational costs. This allows your business to allocate resources strategically, invest in growth, and potentially offer competitive pricing to customers.
Customer Satisfaction: RPA enhances the customer experience by ensuring faster response times, personalized interactions, and error-free service. Satisfied customers are more likely to remain loyal and recommend your business to others.
Real-Time Data Insights: RPA collects and processes data in real-time, providing valuable insights into market trends, customer behavior, and operational performance. These insights can be leveraged to make informed decisions and stay ahead of market shifts.
Innovation and Creativity: By automating routine tasks, RPA liberates your workforce from the mundane, allowing them to focus on creative, strategic, and value-added activities. This fosters a culture of innovation and provides a competitive advantage in product and service development.
Strategic Decision-Making: With RPA, your organization can make data-driven decisions more efficiently. This strategic approach to decision-making allows you to anticipate market trends, spot opportunities, and outmaneuver competitors.
RPA is a game-changer for businesses seeking to gain a competitive advantage in their industries. By increasing operational efficiency, reducing costs, enhancing customer satisfaction, and providing real-time insights, RPA empowers organizations to stay ahead in rapidly changing markets. It's not just about streamlining processes; it's about positioning your business to lead, innovate, and thrive in a highly competitive world. RPA is the key to not just keeping pace but setting the pace in your industry.
Conclusion
In conclusion, Robotic Process Automation (RPA) is a transformative force in the modern business landscape, offering a multitude of benefits that can revolutionize the way organizations operate. Throughout this series of articles, we've explored the diverse advantages of RPA and how it can be harnessed to enhance different aspects of business operations.
RPA's ability to operate 24/7 ensures workflow continuity, allowing businesses to adapt to fluctuating workloads, meet global demands, and maintain a competitive edge. It offers employees the opportunity to focus on more meaningful tasks, fostering job satisfaction, skill development, and innovation.
RPA leverages data insights to facilitate data-driven decision-making, enabling businesses to respond to market changes and opportunities with agility and precision. It improves the customer experience through faster response times, reduced errors, and personalized interactions, leading to higher customer satisfaction and loyalty.
In a world where efficiency, agility, and customer satisfaction are paramount, RPA is more than a tool for automation; it's a strategic asset that empowers businesses to thrive and excel. Embracing the automation revolution is not just a choice; it's a necessity for organizations that aim to remain competitive, innovative, and successful in the ever-evolving business landscape.
Understanding the Power of SMAC: Social, Mobile,Analytics, and Cloud
In the rapidly evolving landscape of modern technology, the convergence of Social, Mobile, Analytics, and Cloud (SMAC) has emerged as a powerful force that is reshaping industries, revolutionizing customer experiences, and driving innovation at an unprecedented pace. This dynamic quartet of technological trends, when combined effectively, can offer organizations a competitive edge, improved efficiency, and fresh opportunities for growth. Understanding the power of SMAC is not just a technological endeavor; it's a strategic imperative for businesses in the 21st century.
In this exploration of SMAC, we will delve deeper into each of these components, uncovering their individual significance and examining the powerful synergies that emerge when they are combined. We will also explore the impact of SMAC across various industries and sectors, from healthcare and finance to manufacturing and marketing, showcasing how this transformative technology is redefining the way businesses operate and the way we experience the world.
Join us on this journey as we unravel the intricate web of SMAC, and discover how this fusion of technology is not just a trend but a transformative force with the potential to shape the future of business and society.
Table of contents
-
The Core Components of SMAC
-
SMAC's Impact on Customer Engagement
-
Data Analytics in SMAC
-
Mobile-First Strategies in SMAC
-
The Social Media Factor
-
Cloud Computing's Role in SMAC
-
SMAC in Healthcare
-
The Security Challenges of SMAC
-
SMAC in Financial Services
-
Real-World SMAC Success Stories
-
Conclusion
The Core Components of SMAC
The core components of SMAC (Social, Mobile, Analytics, and Cloud) are the fundamental building blocks that make up this powerful technology framework. Understanding each component is essential for grasping the full potential of SMAC and how they interact synergistically. Let's take a closer look at each component:
Social (S):The "Social" component refers to the vast and interconnected world of social media. Social platforms such as Facebook, Twitter, Instagram, LinkedIn, and others have become integral parts of our personal and professional lives. They serve as channels for communication, collaboration, and information sharing. But beyond their social aspects, they are also a treasure trove of valuable data. Businesses can leverage social media to gain insights into customer preferences, sentiments, and behaviors. This data can inform marketing strategies, product development, and customer engagement.
Mobile (M):The "Mobile" component represents the proliferation of mobile devices, primarily smartphones and tablets. Mobile technology has transformed how people interact with digital content and services. With mobile devices, individuals have constant access to information, and businesses have the ability to engage with customers wherever they are. Mobile applications, or apps, have become central to delivering services, conducting transactions, and gathering real-time data. Mobile-friendly websites and apps are now essential for businesses to reach and connect with their audiences.
Analytics (A):"Analytics" is the data-driven heart of SMAC. It involves the collection, processing, and interpretation of data to gain insights and make informed decisions. Advanced analytics tools and techniques, including data mining, machine learning, and predictive analytics, help businesses identify trends, patterns, and correlations in their data. By harnessing analytics, organizations can make smarter decisions, optimize operations, personalize customer experiences, and even predict future outcomes. Big data analytics, in particular, enables the handling of vast amounts of data to extract meaningful information.
Cloud (C):The "Cloud" component represents cloud computing technology. Cloud computing offers a scalable and flexible infrastructure for storing and processing data and applications. It allows businesses to access resources remotely, reducing the need for on-site hardware and infrastructure maintenance. Cloud services provide a cost-effective solution for storing and managing data, running applications, and supporting various SMAC technologies. This scalability and accessibility are crucial for handling the vast amounts of data generated by social media, mobile devices, and analytics.
These core components of SMAC are interdependent, and their synergy enhances an organization's ability to engage with customers, extract valuable insights from data, and operate efficiently and effectively in the digital age Understanding how these components work together is essential for organizations looking to harness the full power of SMAC for their benefit.
SMAC's Impact on Customer Engagement
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a profound impact on customer engagement, revolutionizing the way businesses interact with and serve their customers. The convergence of these four components has created new opportunities for businesses to better understand, connect with, and delight their customers. Here's an exploration of SMAC's impact on customer engagement:
Real-Time Communication: Mobile and social media enable real-time communication with customers. Businesses can engage with customers instantly, addressing questions or concerns promptly. This level of responsiveness fosters trust and a sense of being heard, which is crucial for positive customer experiences.
Omni-Channel Customer Service: Cloud technology plays a significant role in creating an omni-channel customer service experience. It allows businesses to integrate customer data across various touchpoints and provide a seamless experience. For example, a customer can start a conversation with a business on social media and then continue it via a mobile app, with the context of the conversation maintained.
Feedback and Surveys: Social media and mobile apps provide opportunities for businesses to collect customer feedback and conduct surveys. This real-time feedback loop allows companies to make quick improvements and adjustments to products or services.
Customer Communities: Social media can be used to create customer communities where users can discuss products, share tips, and support one another. These communities foster a sense of belonging and loyalty among customers.
SMAC technologies have transformed customer engagement by providing businesses with the tools to collect and analyze data, personalize experiences, and engage with customers across multiple channels in real-time. This shift towards a more customer-centric approach is a critical element of successful modern business strategies, enabling companies to build stronger relationships with their customers and stay competitive in an increasingly digital marketplace.
Data Analytics in SMAC
Data analytics plays a central role in the SMAC (Social, Mobile, Analytics, and Cloud) framework, and it's a key component for harnessing the power of these technologies. Here's an exploration of the role and importance of data analytics in the SMAC ecosystem:
Data Collection: Data analytics in SMAC begins with the collection of vast amounts of data. Social media, mobile applications, and websites generate a wealth of information. Analytics tools collect and aggregate this data from various sources.
Data Storage: Cloud computing is essential for storing the large volumes of data generated by SMAC components. The cloud offers scalable, cost-effective storage solutions, ensuring that data is readily accessible and secure.
Data Processing: Analytics tools process the data to make it meaningful and actionable. This includes cleaning and transforming raw data into structured information. Mobile and cloud technologies facilitate this processing by providing the computing power required for complex data operations.
Real-Time Analytics: Real-time analytics, made possible by mobile and cloud technologies, allows businesses to analyze data as it's generated. This is particularly crucial for immediate decision-making and personalized customer experiences.
A/B Testing: Mobile apps and websites enable A/B testing, where businesses can experiment with different versions of products, services, or marketing content to see which performs better. Data analytics measures the effectiveness of these tests.
In summary, data analytics is at the heart of SMAC, providing businesses with the ability to collect, process, analyze, and make data-driven decisions. This data-driven approach is pivotal for personalizing customer experiences, optimizing operations, and staying competitive in the digital age. The integration of data analytics within SMAC technologies empowers organizations to unlock valuable insights and leverage them to enhance their products, services, and customer engagement strategies.
Mobile-First Strategies in SMAC
Mobile-First strategies in the context of SMAC (Social, Mobile, Analytics, and Cloud) are approaches that prioritize the mobile experience as the central focus of digital initiatives. With the increasing use of mobile devices, including smartphones and tablets, businesses are recognizing the need to adapt and optimize their strategies to cater to the mobile-savvy audience. Here's an exploration of the concept of Mobile-First strategies within the SMAC framework:
Mobile-Centric Design: Mobile-First strategies begin with designing digital platforms, such as websites and applications, with mobile users in mind. This means starting the design process with mobile devices as the primary target, ensuring that the user experience is seamless and efficient on smaller screens.
Mobile App Development: Creating mobile apps tailored to the needs and behaviors of mobile users is a significant aspect of Mobile-First strategies. These apps offer a more streamlined and engaging experience compared to mobile-responsive websites.
User Experience Optimization: Mobile-First strategies prioritize optimizing the user experience on mobile devices. This includes fast loading times, intuitive navigation, and user-friendly interfaces that cater to touch and swipe interactions.
Mobile SEO: Search engine optimization (SEO) techniques are adapted to cater to mobile search trends, as more people use mobile devices to access the internet. Mobile-First strategies involve optimizing websites and apps for mobile search.
Mobile Marketing: Mobile-First strategies extend to marketing efforts. Businesses create mobile-friendly marketing campaigns, such as SMS marketing, mobile advertising, and social media campaigns designed for mobile users.
Mobile Analytics: Mobile-First strategies rely on analytics to understand mobile user behavior. By analyzing data from mobile users, businesses can make informed decisions about how to improve their mobile offerings.
Location-Based Services: Mobile-First strategies take advantage of location-based services to offer users localized and context-aware content. For example, businesses can send mobile app users offers or recommendations based on their current location.
Mobile Security: The security of mobile apps and websites is a critical consideration in Mobile-First strategies. Protecting user data and ensuring secure mobile transactions are top priorities.
Mobile-First strategies are a response to the increasing dominance of mobile devices in the digital landscape. They require businesses to prioritize mobile users in design, content, marketing, and technology decisions.These strategies complement and enhance the broader SMAC framework by recognizing the pivotal role of mobile technology in customer engagement and digital transformation.
The Social Media Factor
The "Social Media Factor" within the SMAC (Social, Mobile, Analytics, and Cloud) framework is a crucial component that plays a pivotal role in how businesses engage with customers and gather valuable insights. Social media platforms have transformed the way companies interact with their audiences, build brand presence, and gather information about customer behavior. Here's a closer look at the social media factor and its significance within the SMAC framework:
Customer Engagement: Social media platforms are powerful tools for engaging with customers in real time. Businesses can respond to customer inquiries, address concerns, and provide support promptly. This direct engagement fosters trust and loyalty.
User-Generated Content: Social media encourages users to generate content, such as reviews, photos, and testimonials. User-generated content serves as social proof, influencing the purchasing decisions of other consumers.
Influencer Marketing: Social media allows businesses to partner with influencers who have a substantial following. Influencers can promote products and services to their engaged audience, providing a more authentic and trusted recommendation.
Community Building: Brands can create online communities on social media where customers can connect, discuss, and share their experiences. These communities foster a sense of belonging and loyalty.
Crisis Management: Social media is often the first place where crises or issues are brought to light. Businesses can use these platforms to manage and address public relations challenges promptly and transparently.
Global Reach: Social media transcends geographical boundaries, enabling businesses to engage with a global audience. This is especially beneficial for businesses with international markets.
The "Social Media Factor" is a pivotal element within the SMAC framework, transforming how businesses interact with customers, build brand presence, and gather insights. It amplifies the reach and impact of businesses by harnessing the connectivity and engagement opportunities offered by social media platforms. Understanding and leveraging this factor is critical for businesses seeking to thrive in the digital age and harness the power of SMAC for customer engagement and brand success.
Cloud Computing's Role in SMAC
Cloud computing plays a critical role in the SMAC (Social, Mobile, Analytics, and Cloud) framework, as it provides the underlying infrastructure and technology foundation that enables the other components to function effectively. Here's an exploration of the role and importance of cloud computing in the SMAC ecosystem:
Scalability: Cloud computing offers on-demand scalability, allowing businesses to scale up or down their resources as needed. This is particularly important in the context of SMAC, as data volumes and user demands can fluctuate rapidly.
Flexibility: The cloud provides a flexible environment for deploying and managing SMAC applications and services. This flexibility is crucial for adapting to changing business needs and technological advancements.
Cost Efficiency: Cloud computing eliminates the need for extensive upfront infrastructure investments. It allows businesses to pay for the resources they use, reducing capital expenditures and operational costs.
Accessibility: The cloud enables remote access to data, applications, and services from virtually anywhere with an internet connection. This accessibility is vital for mobile users and remote teams, supporting the mobile and social components of SMAC.
Data Storage: Cloud storage services provide a secure and cost-effective way to store vast amounts of data generated by the social and analytics components of SMAC. This data can be easily accessed and processed as needed.
Data Analytics and Processing: Cloud platforms offer powerful computing capabilities that are essential for processing and analyzing large datasets. This is critical for extracting insights from the analytics component of SMAC.
Collaboration: The cloud facilitates collaboration among teams, enabling them to work on SMAC projects and data analysis from various locations. Collaboration tools and shared resources in the cloud promote efficient teamwork.
API Integration: Cloud platforms often support APIs (Application Programming Interfaces) that enable seamless integration with various third-party applications and services. This is valuable for connecting different SMAC components and tools.
SMAC in Healthcare
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a profound impact on the healthcare industry, revolutionizing the way healthcare is delivered, managed, and experienced. These technologies are driving improvements in patient care, data analysis, accessibility, and overall efficiency. Here's an overview of how SMAC is applied in healthcare:
Mobile Health (mHealth): Mobile apps and devices have transformed healthcare delivery. Patients can use mobile apps to schedule appointments, access medical records, receive medication reminders, and monitor their health conditions. Wearable devices track vital signs and send data to healthcare providers in real time.
Telemedicine: Mobile and cloud technologies enable telemedicine, which allows patients to have virtual consultations with healthcare professionals. This has improved access to medical care, especially in remote or underserved areas.
Electronic Health Records (EHRs): Cloud computing is central to the storage and management of electronic health records. EHRs provide a secure, centralized, and easily accessible repository of patient data for healthcare providers. Analytics tools can mine this data for insights.
Health Data Analytics: Analytics tools help healthcare providers process and analyze vast amounts of health data. They can identify trends, track disease outbreaks, predict patient outcomes, and improve treatment decisions.
Medical Imaging and Analytics: Cloud technology enables the storage and sharing of medical images such as X-rays, MRIs, and CT scans. Analytics tools help in image analysis for faster and more accurate diagnoses.
Drug and Treatment Research: Analytics and cloud computing assist in drug discovery and clinical trials. Researchers can analyze patient data, share information securely, and accelerate the development of new drugs and treatments.
SMAC technologies have ushered in a new era of healthcare, promoting patient-centered care, improving data accessibility, enhancing diagnostic capabilities, and streamlining healthcare operations. They have the potential to improve patient outcomes, reduce costs, and make healthcare more accessible to individuals around the world. As technology continues to advance, the healthcare industry must adapt and innovate to harness the full potential of SMAC.
The Security Challenges of SMAC
The security challenges associated with SMAC (Social, Mobile, Analytics, and Cloud) technologies are a critical concern for businesses and organizations. The integration of these technologies introduces new vulnerabilities and risks that need to be addressed to protect sensitive data and ensure the integrity and privacy of digital interactions. Here are some of the key security challenges associated with SMAC:
Mobile Device Security:
Challenge: Mobile devices are easily lost or stolen, making them a significant security risk. The use of personal mobile devices for work (BYOD) can blur the lines between personal and professional data.
Solution: Implement mobile device management (MDM) solutions to enforce security policies, remote wipe capabilities, and containerization to separate work and personal data on devices.
Data Integration and Governance:
Challenge: Integrating data from various sources for analytics can lead to data quality and governance issues. Inaccurate or incomplete data can impact the accuracy of insights and decision-making.
Solution: Establish data governance policies, data quality checks, and data cleansing processes to ensure the integrity of data used for analytics.
Mobile App Security:
Challenge: Mobile apps may contain vulnerabilities that can be exploited by attackers. These vulnerabilities could be related to insecure coding practices, weak authentication, or unpatched software libraries.
Solution: Regularly update and patch mobile apps, conduct security assessments, and use code analysis tools to identify and remediate vulnerabilities.
In summary, while SMAC technologies offer numerous benefits, they also introduce security challenges that require vigilant management and proactive measures. Organizations must adopt a holistic approach to cybersecurity, including technology, policies, employee training, and ongoing monitoring, to protect their data and digital assets effectively in the SMAC era.
SMAC in Financial Services
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a significant impact on the financial services industry, transforming the way financial institutions operate and how customers interact with their banks and investment firms. Here's an overview of how SMAC is applied in financial services:
Enhanced Customer Experience: Financial institutions use SMAC technologies to provide a more personalized and convenient experience for their customers. Mobile apps allow users to access accounts, transfer funds, and make payments on the go. Social media and chatbots provide quick customer support, while analytics help understand customer preferences and behavior for tailored offerings.
Mobile Banking and Payments: Mobile banking applications have become a staple in the financial services sector. Customers can check balances, make payments, and even deposit checks using their smartphones. Mobile wallets and contactless payments are on the rise, making transactions more convenient.
Fraud Detection and Prevention: Analytics, particularly machine learning algorithms, help in identifying unusual transaction patterns that may indicate fraud. Real-time monitoring of transactions and cloud-based fraud detection systems enhance security and protect customers from financial fraud.
Data Analytics for Risk Assessment: Advanced analytics tools analyze vast datasets to assess credit risk, investment risk, and market risk. These insights inform lending decisions, insurance underwriting, and investment strategies.
Customer Service and Support: Social media, chatbots, and cloud-based contact centers have improved customer support. Customers can get quick responses to their inquiries and issues, enhancing their overall experience.
Operational Efficiency: Cloud computing allows financial institutions to streamline their operations, reduce infrastructure costs, and improve collaboration. This efficiency helps them allocate resources to more value-added activities.
Cybersecurity: Cloud infrastructure provides secure storage and disaster recovery options, helping financial institutions safeguard customer data and protect against cyber threats.
SMAC technologies have revolutionized the financial services industry by improving customer experiences, increasing operational efficiency, enhancing risk management, and opening up new opportunities for innovation and service delivery. As SMAC continues to evolve, financial institutions must stay agile and innovative to remain competitive in an ever-changing landscape.
Real-World SMAC Success Stories
SMAC (Social, Mobile, Analytics, and Cloud) technologies have brought about transformative changes across various industries. Below are real-world success stories that highlight how organizations have leveraged SMAC to achieve significant outcomes:
Netflix - Analytics and Personalization: Netflix utilizes analytics to track user viewing habits, analyze user preferences, and predict content recommendations. By analyzing big data using cloud-based infrastructure, they have enhanced the user experience through personalized content recommendations, leading to increased customer satisfaction and engagement.
Amazon - Mobile Commerce: Amazon's mobile app and mobile-optimized website have revolutionized the retail industry. Customers can shop, access product information, and make purchases on mobile devices easily. This mobile-centric approach has significantly contributed to Amazon's growth and customer loyalty.
Johns Hopkins Hospital - Healthcare Analytics: Johns Hopkins Hospital uses analytics to identify patients at risk for sepsis and other infections. By analyzing patient data in real time, they have reduced infection rates, improved patient outcomes, and saved lives, showcasing the potential for analytics in healthcare.
Walmart - Supply Chain Optimization: Walmart employs big data analytics to optimize its supply chain. They gather and analyze real-time data on sales, inventory, and weather conditions to streamline inventory management and logistics. This has led to significant cost savings and improved product availability.
Spotify - Music Recommendation and Personalization: Spotify uses analytics to understand users' music preferences and behavior. By analyzing the listening habits of millions of users, they provide personalized playlists and music recommendations. This has contributed to increased user engagement and subscriptions.
These real-world success stories demonstrate the diverse applications of SMAC technologies across industries. They emphasize the power of leveraging social, mobile, analytics, and cloud technologies to drive innovation, improve customer experiences, and achieve significant business outcomes. These success stories also underscore the importance of continuous adaptation and innovation in a rapidly evolving digital landscape.
Conclusion
In conclusion, SMAC (Social, Mobile, Analytics, and Cloud) technologies have transformed the business landscape and reshaped industries by fostering innovation, improving customer experiences, and driving operational efficiency. This convergence of technology components has enabled organizations to harness the power of data, connectivity, and accessibility, leading to remarkable success stories and tangible outcomes.
The real-world examples highlighted in the previous responses demonstrate how organizations have leveraged SMAC technologies to achieve significant results. From Netflix's personalized content recommendations to Amazon's mobile commerce dominance and Starbucks' mobile payments and loyalty program, these success stories underscore the value of embracing SMAC to enhance customer engagement and drive growth.
Similarly, healthcare providers like Johns Hopkins Hospital have used analytics to save lives, while companies like Walmart have optimized their supply chains through data analysis. Airbnb's cloud-based platform and Uber's mobile app have revolutionized their respective industries, emphasizing the role of cloud and mobile technology in fostering disruptive innovation.
These real-world success stories underscore the transformative potential of SMAC technologies across various domains. The convergence of social, mobile, analytics, and cloud technologies continues to shape the digital landscape, driving innovation, improving customer experiences, and delivering tangible business outcomes.
As technology evolves, organizations that adapt and innovate within the SMAC framework will remain at the forefront of their respective industries, finding new and creative ways to leverage these technologies for success in the digital era.
Read More
In the rapidly evolving landscape of modern technology, the convergence of Social, Mobile, Analytics, and Cloud (SMAC) has emerged as a powerful force that is reshaping industries, revolutionizing customer experiences, and driving innovation at an unprecedented pace. This dynamic quartet of technological trends, when combined effectively, can offer organizations a competitive edge, improved efficiency, and fresh opportunities for growth. Understanding the power of SMAC is not just a technological endeavor; it's a strategic imperative for businesses in the 21st century.
In this exploration of SMAC, we will delve deeper into each of these components, uncovering their individual significance and examining the powerful synergies that emerge when they are combined. We will also explore the impact of SMAC across various industries and sectors, from healthcare and finance to manufacturing and marketing, showcasing how this transformative technology is redefining the way businesses operate and the way we experience the world.
Join us on this journey as we unravel the intricate web of SMAC, and discover how this fusion of technology is not just a trend but a transformative force with the potential to shape the future of business and society.
Table of contents
-
The Core Components of SMAC
-
SMAC's Impact on Customer Engagement
-
Data Analytics in SMAC
-
Mobile-First Strategies in SMAC
-
The Social Media Factor
-
Cloud Computing's Role in SMAC
-
SMAC in Healthcare
-
The Security Challenges of SMAC
-
SMAC in Financial Services
-
Real-World SMAC Success Stories
-
Conclusion
The Core Components of SMAC
The core components of SMAC (Social, Mobile, Analytics, and Cloud) are the fundamental building blocks that make up this powerful technology framework. Understanding each component is essential for grasping the full potential of SMAC and how they interact synergistically. Let's take a closer look at each component:
Social (S):The "Social" component refers to the vast and interconnected world of social media. Social platforms such as Facebook, Twitter, Instagram, LinkedIn, and others have become integral parts of our personal and professional lives. They serve as channels for communication, collaboration, and information sharing. But beyond their social aspects, they are also a treasure trove of valuable data. Businesses can leverage social media to gain insights into customer preferences, sentiments, and behaviors. This data can inform marketing strategies, product development, and customer engagement.
Mobile (M):The "Mobile" component represents the proliferation of mobile devices, primarily smartphones and tablets. Mobile technology has transformed how people interact with digital content and services. With mobile devices, individuals have constant access to information, and businesses have the ability to engage with customers wherever they are. Mobile applications, or apps, have become central to delivering services, conducting transactions, and gathering real-time data. Mobile-friendly websites and apps are now essential for businesses to reach and connect with their audiences.
Analytics (A):"Analytics" is the data-driven heart of SMAC. It involves the collection, processing, and interpretation of data to gain insights and make informed decisions. Advanced analytics tools and techniques, including data mining, machine learning, and predictive analytics, help businesses identify trends, patterns, and correlations in their data. By harnessing analytics, organizations can make smarter decisions, optimize operations, personalize customer experiences, and even predict future outcomes. Big data analytics, in particular, enables the handling of vast amounts of data to extract meaningful information.
Cloud (C):The "Cloud" component represents cloud computing technology. Cloud computing offers a scalable and flexible infrastructure for storing and processing data and applications. It allows businesses to access resources remotely, reducing the need for on-site hardware and infrastructure maintenance. Cloud services provide a cost-effective solution for storing and managing data, running applications, and supporting various SMAC technologies. This scalability and accessibility are crucial for handling the vast amounts of data generated by social media, mobile devices, and analytics.
These core components of SMAC are interdependent, and their synergy enhances an organization's ability to engage with customers, extract valuable insights from data, and operate efficiently and effectively in the digital age Understanding how these components work together is essential for organizations looking to harness the full power of SMAC for their benefit.
SMAC's Impact on Customer Engagement
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a profound impact on customer engagement, revolutionizing the way businesses interact with and serve their customers. The convergence of these four components has created new opportunities for businesses to better understand, connect with, and delight their customers. Here's an exploration of SMAC's impact on customer engagement:
Real-Time Communication: Mobile and social media enable real-time communication with customers. Businesses can engage with customers instantly, addressing questions or concerns promptly. This level of responsiveness fosters trust and a sense of being heard, which is crucial for positive customer experiences.
Omni-Channel Customer Service: Cloud technology plays a significant role in creating an omni-channel customer service experience. It allows businesses to integrate customer data across various touchpoints and provide a seamless experience. For example, a customer can start a conversation with a business on social media and then continue it via a mobile app, with the context of the conversation maintained.
Feedback and Surveys: Social media and mobile apps provide opportunities for businesses to collect customer feedback and conduct surveys. This real-time feedback loop allows companies to make quick improvements and adjustments to products or services.
Customer Communities: Social media can be used to create customer communities where users can discuss products, share tips, and support one another. These communities foster a sense of belonging and loyalty among customers.
SMAC technologies have transformed customer engagement by providing businesses with the tools to collect and analyze data, personalize experiences, and engage with customers across multiple channels in real-time. This shift towards a more customer-centric approach is a critical element of successful modern business strategies, enabling companies to build stronger relationships with their customers and stay competitive in an increasingly digital marketplace.
Data Analytics in SMAC
Data analytics plays a central role in the SMAC (Social, Mobile, Analytics, and Cloud) framework, and it's a key component for harnessing the power of these technologies. Here's an exploration of the role and importance of data analytics in the SMAC ecosystem:
Data Collection: Data analytics in SMAC begins with the collection of vast amounts of data. Social media, mobile applications, and websites generate a wealth of information. Analytics tools collect and aggregate this data from various sources.
Data Storage: Cloud computing is essential for storing the large volumes of data generated by SMAC components. The cloud offers scalable, cost-effective storage solutions, ensuring that data is readily accessible and secure.
Data Processing: Analytics tools process the data to make it meaningful and actionable. This includes cleaning and transforming raw data into structured information. Mobile and cloud technologies facilitate this processing by providing the computing power required for complex data operations.
Real-Time Analytics: Real-time analytics, made possible by mobile and cloud technologies, allows businesses to analyze data as it's generated. This is particularly crucial for immediate decision-making and personalized customer experiences.
A/B Testing: Mobile apps and websites enable A/B testing, where businesses can experiment with different versions of products, services, or marketing content to see which performs better. Data analytics measures the effectiveness of these tests.
In summary, data analytics is at the heart of SMAC, providing businesses with the ability to collect, process, analyze, and make data-driven decisions. This data-driven approach is pivotal for personalizing customer experiences, optimizing operations, and staying competitive in the digital age. The integration of data analytics within SMAC technologies empowers organizations to unlock valuable insights and leverage them to enhance their products, services, and customer engagement strategies.
Mobile-First Strategies in SMAC
Mobile-First strategies in the context of SMAC (Social, Mobile, Analytics, and Cloud) are approaches that prioritize the mobile experience as the central focus of digital initiatives. With the increasing use of mobile devices, including smartphones and tablets, businesses are recognizing the need to adapt and optimize their strategies to cater to the mobile-savvy audience. Here's an exploration of the concept of Mobile-First strategies within the SMAC framework:
Mobile-Centric Design: Mobile-First strategies begin with designing digital platforms, such as websites and applications, with mobile users in mind. This means starting the design process with mobile devices as the primary target, ensuring that the user experience is seamless and efficient on smaller screens.
Mobile App Development: Creating mobile apps tailored to the needs and behaviors of mobile users is a significant aspect of Mobile-First strategies. These apps offer a more streamlined and engaging experience compared to mobile-responsive websites.
User Experience Optimization: Mobile-First strategies prioritize optimizing the user experience on mobile devices. This includes fast loading times, intuitive navigation, and user-friendly interfaces that cater to touch and swipe interactions.
Mobile SEO: Search engine optimization (SEO) techniques are adapted to cater to mobile search trends, as more people use mobile devices to access the internet. Mobile-First strategies involve optimizing websites and apps for mobile search.
Mobile Marketing: Mobile-First strategies extend to marketing efforts. Businesses create mobile-friendly marketing campaigns, such as SMS marketing, mobile advertising, and social media campaigns designed for mobile users.
Mobile Analytics: Mobile-First strategies rely on analytics to understand mobile user behavior. By analyzing data from mobile users, businesses can make informed decisions about how to improve their mobile offerings.
Location-Based Services: Mobile-First strategies take advantage of location-based services to offer users localized and context-aware content. For example, businesses can send mobile app users offers or recommendations based on their current location.
Mobile Security: The security of mobile apps and websites is a critical consideration in Mobile-First strategies. Protecting user data and ensuring secure mobile transactions are top priorities.
Mobile-First strategies are a response to the increasing dominance of mobile devices in the digital landscape. They require businesses to prioritize mobile users in design, content, marketing, and technology decisions.These strategies complement and enhance the broader SMAC framework by recognizing the pivotal role of mobile technology in customer engagement and digital transformation.
The Social Media Factor
The "Social Media Factor" within the SMAC (Social, Mobile, Analytics, and Cloud) framework is a crucial component that plays a pivotal role in how businesses engage with customers and gather valuable insights. Social media platforms have transformed the way companies interact with their audiences, build brand presence, and gather information about customer behavior. Here's a closer look at the social media factor and its significance within the SMAC framework:
Customer Engagement: Social media platforms are powerful tools for engaging with customers in real time. Businesses can respond to customer inquiries, address concerns, and provide support promptly. This direct engagement fosters trust and loyalty.
User-Generated Content: Social media encourages users to generate content, such as reviews, photos, and testimonials. User-generated content serves as social proof, influencing the purchasing decisions of other consumers.
Influencer Marketing: Social media allows businesses to partner with influencers who have a substantial following. Influencers can promote products and services to their engaged audience, providing a more authentic and trusted recommendation.
Community Building: Brands can create online communities on social media where customers can connect, discuss, and share their experiences. These communities foster a sense of belonging and loyalty.
Crisis Management: Social media is often the first place where crises or issues are brought to light. Businesses can use these platforms to manage and address public relations challenges promptly and transparently.
Global Reach: Social media transcends geographical boundaries, enabling businesses to engage with a global audience. This is especially beneficial for businesses with international markets.
The "Social Media Factor" is a pivotal element within the SMAC framework, transforming how businesses interact with customers, build brand presence, and gather insights. It amplifies the reach and impact of businesses by harnessing the connectivity and engagement opportunities offered by social media platforms. Understanding and leveraging this factor is critical for businesses seeking to thrive in the digital age and harness the power of SMAC for customer engagement and brand success.
Cloud Computing's Role in SMAC
Cloud computing plays a critical role in the SMAC (Social, Mobile, Analytics, and Cloud) framework, as it provides the underlying infrastructure and technology foundation that enables the other components to function effectively. Here's an exploration of the role and importance of cloud computing in the SMAC ecosystem:
Scalability: Cloud computing offers on-demand scalability, allowing businesses to scale up or down their resources as needed. This is particularly important in the context of SMAC, as data volumes and user demands can fluctuate rapidly.
Flexibility: The cloud provides a flexible environment for deploying and managing SMAC applications and services. This flexibility is crucial for adapting to changing business needs and technological advancements.
Cost Efficiency: Cloud computing eliminates the need for extensive upfront infrastructure investments. It allows businesses to pay for the resources they use, reducing capital expenditures and operational costs.
Accessibility: The cloud enables remote access to data, applications, and services from virtually anywhere with an internet connection. This accessibility is vital for mobile users and remote teams, supporting the mobile and social components of SMAC.
Data Storage: Cloud storage services provide a secure and cost-effective way to store vast amounts of data generated by the social and analytics components of SMAC. This data can be easily accessed and processed as needed.
Data Analytics and Processing: Cloud platforms offer powerful computing capabilities that are essential for processing and analyzing large datasets. This is critical for extracting insights from the analytics component of SMAC.
Collaboration: The cloud facilitates collaboration among teams, enabling them to work on SMAC projects and data analysis from various locations. Collaboration tools and shared resources in the cloud promote efficient teamwork.
API Integration: Cloud platforms often support APIs (Application Programming Interfaces) that enable seamless integration with various third-party applications and services. This is valuable for connecting different SMAC components and tools.
SMAC in Healthcare
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a profound impact on the healthcare industry, revolutionizing the way healthcare is delivered, managed, and experienced. These technologies are driving improvements in patient care, data analysis, accessibility, and overall efficiency. Here's an overview of how SMAC is applied in healthcare:
Mobile Health (mHealth): Mobile apps and devices have transformed healthcare delivery. Patients can use mobile apps to schedule appointments, access medical records, receive medication reminders, and monitor their health conditions. Wearable devices track vital signs and send data to healthcare providers in real time.
Telemedicine: Mobile and cloud technologies enable telemedicine, which allows patients to have virtual consultations with healthcare professionals. This has improved access to medical care, especially in remote or underserved areas.
Electronic Health Records (EHRs): Cloud computing is central to the storage and management of electronic health records. EHRs provide a secure, centralized, and easily accessible repository of patient data for healthcare providers. Analytics tools can mine this data for insights.
Health Data Analytics: Analytics tools help healthcare providers process and analyze vast amounts of health data. They can identify trends, track disease outbreaks, predict patient outcomes, and improve treatment decisions.
Medical Imaging and Analytics: Cloud technology enables the storage and sharing of medical images such as X-rays, MRIs, and CT scans. Analytics tools help in image analysis for faster and more accurate diagnoses.
Drug and Treatment Research: Analytics and cloud computing assist in drug discovery and clinical trials. Researchers can analyze patient data, share information securely, and accelerate the development of new drugs and treatments.
SMAC technologies have ushered in a new era of healthcare, promoting patient-centered care, improving data accessibility, enhancing diagnostic capabilities, and streamlining healthcare operations. They have the potential to improve patient outcomes, reduce costs, and make healthcare more accessible to individuals around the world. As technology continues to advance, the healthcare industry must adapt and innovate to harness the full potential of SMAC.
The Security Challenges of SMAC
The security challenges associated with SMAC (Social, Mobile, Analytics, and Cloud) technologies are a critical concern for businesses and organizations. The integration of these technologies introduces new vulnerabilities and risks that need to be addressed to protect sensitive data and ensure the integrity and privacy of digital interactions. Here are some of the key security challenges associated with SMAC:
Mobile Device Security:
Challenge: Mobile devices are easily lost or stolen, making them a significant security risk. The use of personal mobile devices for work (BYOD) can blur the lines between personal and professional data.
Solution: Implement mobile device management (MDM) solutions to enforce security policies, remote wipe capabilities, and containerization to separate work and personal data on devices.
Data Integration and Governance:
Challenge: Integrating data from various sources for analytics can lead to data quality and governance issues. Inaccurate or incomplete data can impact the accuracy of insights and decision-making.
Solution: Establish data governance policies, data quality checks, and data cleansing processes to ensure the integrity of data used for analytics.
Mobile App Security:
Challenge: Mobile apps may contain vulnerabilities that can be exploited by attackers. These vulnerabilities could be related to insecure coding practices, weak authentication, or unpatched software libraries.
Solution: Regularly update and patch mobile apps, conduct security assessments, and use code analysis tools to identify and remediate vulnerabilities.
In summary, while SMAC technologies offer numerous benefits, they also introduce security challenges that require vigilant management and proactive measures. Organizations must adopt a holistic approach to cybersecurity, including technology, policies, employee training, and ongoing monitoring, to protect their data and digital assets effectively in the SMAC era.
SMAC in Financial Services
SMAC (Social, Mobile, Analytics, and Cloud) technologies have had a significant impact on the financial services industry, transforming the way financial institutions operate and how customers interact with their banks and investment firms. Here's an overview of how SMAC is applied in financial services:
Enhanced Customer Experience: Financial institutions use SMAC technologies to provide a more personalized and convenient experience for their customers. Mobile apps allow users to access accounts, transfer funds, and make payments on the go. Social media and chatbots provide quick customer support, while analytics help understand customer preferences and behavior for tailored offerings.
Mobile Banking and Payments: Mobile banking applications have become a staple in the financial services sector. Customers can check balances, make payments, and even deposit checks using their smartphones. Mobile wallets and contactless payments are on the rise, making transactions more convenient.
Fraud Detection and Prevention: Analytics, particularly machine learning algorithms, help in identifying unusual transaction patterns that may indicate fraud. Real-time monitoring of transactions and cloud-based fraud detection systems enhance security and protect customers from financial fraud.
Data Analytics for Risk Assessment: Advanced analytics tools analyze vast datasets to assess credit risk, investment risk, and market risk. These insights inform lending decisions, insurance underwriting, and investment strategies.
Customer Service and Support: Social media, chatbots, and cloud-based contact centers have improved customer support. Customers can get quick responses to their inquiries and issues, enhancing their overall experience.
Operational Efficiency: Cloud computing allows financial institutions to streamline their operations, reduce infrastructure costs, and improve collaboration. This efficiency helps them allocate resources to more value-added activities.
Cybersecurity: Cloud infrastructure provides secure storage and disaster recovery options, helping financial institutions safeguard customer data and protect against cyber threats.
SMAC technologies have revolutionized the financial services industry by improving customer experiences, increasing operational efficiency, enhancing risk management, and opening up new opportunities for innovation and service delivery. As SMAC continues to evolve, financial institutions must stay agile and innovative to remain competitive in an ever-changing landscape.
Real-World SMAC Success Stories
SMAC (Social, Mobile, Analytics, and Cloud) technologies have brought about transformative changes across various industries. Below are real-world success stories that highlight how organizations have leveraged SMAC to achieve significant outcomes:
Netflix - Analytics and Personalization: Netflix utilizes analytics to track user viewing habits, analyze user preferences, and predict content recommendations. By analyzing big data using cloud-based infrastructure, they have enhanced the user experience through personalized content recommendations, leading to increased customer satisfaction and engagement.
Amazon - Mobile Commerce: Amazon's mobile app and mobile-optimized website have revolutionized the retail industry. Customers can shop, access product information, and make purchases on mobile devices easily. This mobile-centric approach has significantly contributed to Amazon's growth and customer loyalty.
Johns Hopkins Hospital - Healthcare Analytics: Johns Hopkins Hospital uses analytics to identify patients at risk for sepsis and other infections. By analyzing patient data in real time, they have reduced infection rates, improved patient outcomes, and saved lives, showcasing the potential for analytics in healthcare.
Walmart - Supply Chain Optimization: Walmart employs big data analytics to optimize its supply chain. They gather and analyze real-time data on sales, inventory, and weather conditions to streamline inventory management and logistics. This has led to significant cost savings and improved product availability.
Spotify - Music Recommendation and Personalization: Spotify uses analytics to understand users' music preferences and behavior. By analyzing the listening habits of millions of users, they provide personalized playlists and music recommendations. This has contributed to increased user engagement and subscriptions.
These real-world success stories demonstrate the diverse applications of SMAC technologies across industries. They emphasize the power of leveraging social, mobile, analytics, and cloud technologies to drive innovation, improve customer experiences, and achieve significant business outcomes. These success stories also underscore the importance of continuous adaptation and innovation in a rapidly evolving digital landscape.
Conclusion
In conclusion, SMAC (Social, Mobile, Analytics, and Cloud) technologies have transformed the business landscape and reshaped industries by fostering innovation, improving customer experiences, and driving operational efficiency. This convergence of technology components has enabled organizations to harness the power of data, connectivity, and accessibility, leading to remarkable success stories and tangible outcomes.
The real-world examples highlighted in the previous responses demonstrate how organizations have leveraged SMAC technologies to achieve significant results. From Netflix's personalized content recommendations to Amazon's mobile commerce dominance and Starbucks' mobile payments and loyalty program, these success stories underscore the value of embracing SMAC to enhance customer engagement and drive growth.
Similarly, healthcare providers like Johns Hopkins Hospital have used analytics to save lives, while companies like Walmart have optimized their supply chains through data analysis. Airbnb's cloud-based platform and Uber's mobile app have revolutionized their respective industries, emphasizing the role of cloud and mobile technology in fostering disruptive innovation.
These real-world success stories underscore the transformative potential of SMAC technologies across various domains. The convergence of social, mobile, analytics, and cloud technologies continues to shape the digital landscape, driving innovation, improving customer experiences, and delivering tangible business outcomes.
As technology evolves, organizations that adapt and innovate within the SMAC framework will remain at the forefront of their respective industries, finding new and creative ways to leverage these technologies for success in the digital era.
Benefits of CTFL Certification
In the ever-evolving landscape of software development, quality assurance and testing play a pivotal role in ensuring that applications and systems perform flawlessly. The Certified Tester Foundation Level (CTFL) certification stands as a beacon for those aspiring to excel in the field of software testing. It is a globally recognized and respected certification that opens doors to a world of opportunities in the realms of quality assurance and software testing. In this article, we will explore the numerous benefits of CTFL certification, shedding light on how it can empower individuals and organizations alike in their quest for excellence in software testing.
CTFL certification, like a well-constructed test plan, is structured to validate the skills and knowledge of aspiring software testers. It offers a multitude of advantages that extend beyond simply adding a prestigious credential to your name. This certification has the potential to reshape your career, enhance your skills, and contribute significantly to the quality and reliability of the software you are responsible for testing.
Let's dive deeper into the benefits of CTFL certification, from improved career prospects to enhanced testing capabilities, and discover why this certification is a game-changer in the world of software testing.
Table of Contents
-
Career Advancement
-
Global Recognition
-
Skill Enhancement
-
Quality Assurance Impact
-
Increased Marketability
-
Career Transition
-
Knowledge Expansion
-
Professional Networking
-
Organizational Benefits
-
Long-Term Career Growth
-
Conclusion
Career Advancement
In today's competitive job market, professionals are constantly seeking ways to distinguish themselves and achieve career growth. One powerful strategy to achieve career advancement, especially in the realm of software testing and quality assurance, is obtaining the Certified Tester Foundation Level (CTFL) certification. This certification offers a myriad of benefits that can significantly impact your career trajectory. Here's how:
Increased Employability: CTFL certification makes you a more attractive candidate to employers. It demonstrates your commitment to your field and validates your knowledge and skills in software testing. As a result, you become a preferred choice for hiring managers when filling positions related to quality assurance.
Career Opportunities: CTFL opens doors to a broader range of job opportunities. Whether you are seeking a new position, looking to switch industries, or aiming for a promotion within your current organization, having CTFL on your resume can make a substantial difference. Many job postings explicitly require or prefer candidates with testing certifications.
Salary Advancement: It's no secret that certified professionals often command higher salaries. CTFL certification can lead to better compensation packages, including increased base pay, bonuses, and benefits. Employers are willing to pay more for professionals who bring demonstrable skills and expertise to the table.
Career Progression: Career advancement isn't just about securing a job; it's also about climbing the career ladder. CTFL certification provides a solid foundation for further career progression. It can serve as a stepping stone to more advanced certifications and senior roles within the software testing domain.
Improved Job Security: With the increasing demand for quality software, CTFL-certified professionals tend to enjoy more job security. In times of economic uncertainty, organizations are less likely to let go of employees who are essential to ensuring the quality of their products.
CTFL certification is a strategic investment in your career. It enhances your employability, increases your career opportunities, and can lead to higher earnings. Beyond the financial aspects, it also nurtures your professional growth, offering job security and the potential for leadership roles. In the dynamic field of software testing, CTFL certification is a pathway to a rewarding and successful career.
Global Recognition
In an increasingly interconnected world, the value of professional certifications extends far beyond local or regional boundaries. The Certified Tester Foundation Level (CTFL) certification is a prime example of a qualification that enjoys widespread global recognition and respect. This recognition has several significant implications for those who hold the CTFL certification:
International Employability: One of the most compelling benefits of CTFL certification is that it's universally recognized. Whether you are looking to work in your home country or explore opportunities abroad, having CTFL on your resume assures potential employers of your standardized expertise in software testing. This opens doors to a diverse range of international job markets.
Consistency in Skill Set: CTFL's global recognition means that certified professionals share a common knowledge base and understanding of software testing practices. This consistency ensures that employers, regardless of their location, can rely on the skills and competencies of CTFL-certified individuals.
Trust and Credibility: CTFL is endorsed by a variety of prominent organizations and industry bodies. This certification carries an assurance of quality and reliability. Employers often trust the certification as a benchmark of excellence in software testing.
Cross-Industry Applicability: The principles and best practices in software testing are universal and relevant across various industries. CTFL's global recognition allows certified professionals to transition seamlessly between different sectors, such as healthcare, finance, automotive, and more.
Alignment with Industry Standards: CTFL aligns with international testing and quality standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that CTFL-certified individuals have a strong foundation in globally accepted testing methodologies.
International Collaboration: Being part of the CTFL-certified community provides opportunities for international collaboration. You can connect with professionals from diverse backgrounds, share knowledge, and stay updated on global testing trends and practices.
Competitive Advantage: When competing for job roles or promotions, CTFL certification can give you a significant competitive advantage. Employers often prioritize candidates with internationally recognized certifications to ensure their teams adhere to global testing standards.
In summary, the global recognition of CTFL certification is not just a label; it's a powerful testament to your skills and expertise in software testing that transcends borders. This recognition facilitates international career opportunities, provides a foundation for consistent quality, and positions you as a credible and trusted professional in the ever-expanding global software testing community.
Skill Enhancement
Certainly, let's delve into the subtopic of "Skill Enhancement" and explore how the Certified Tester Foundation Level (CTFL) certification can significantly enhance one's skills in the field of software testing:
Skill Enhancement with CTFL Certification
In the dynamic and ever-evolving realm of software testing, the ability to adapt, learn, and master new skills is essential for professional growth. CTFL certification is a gateway to skill enhancement, providing individuals with a structured and comprehensive foundation in software testing. Here's how CTFL enhances one's skills:
Comprehensive Understanding of Software Testing: CTFL certification equips professionals with a holistic understanding of software testing concepts, methodologies, and techniques. This includes knowledge of test planning, test design, test execution, and test management. By mastering these fundamentals, CTFL-certified individuals can contribute more effectively to the testing process.
Practical Testing Techniques: CTFL covers practical testing techniques that are essential for efficient software testing. It includes topics like boundary value analysis, equivalence partitioning, and decision table testing. These techniques enable testers to design and execute test cases that identify defects and improve software quality.
Test Documentation: Effective communication and documentation are key skills in software testing. CTFL certification emphasizes the creation of clear and well-organized test documentation, including test plans, test cases, and test reports. This skill enhances transparency and collaboration within testing teams.
Test Management: CTFL provides insights into test management practices, which involve planning, monitoring, and controlling testing activities. Understanding test management allows professionals to ensure that testing efforts align with project goals and timelines.
Effective Communication: Effective communication is vital for collaborating with development teams, stakeholders, and fellow testers. CTFL training encourages clear and concise communication, improving teamwork and understanding of testing objectives.
CTFL certification is a powerful catalyst for skill enhancement in the software testing domain. It imparts a strong foundation of knowledge and practical skills, enabling professionals to excel in their testing roles. By continually honing their abilities and staying up-to-date with industry best practices, CTFL-certified individuals can contribute significantly to the quality and reliability of the software they test.
Quality Assurance Impact
Quality assurance (QA) is at the heart of delivering reliable and high-quality software products. CTFL certification plays a pivotal role in enhancing and contributing to the overall quality assurance process. Here's how CTFL certification can impact quality assurance:
Early Defect Detection: CTFL emphasizes the importance of detecting defects at an early stage of the software development life cycle. CTFL-certified testers are trained to create test cases that catch defects before they propagate to later phases, reducing the cost and effort required for fixing them.
Enhanced Test Coverage: Quality assurance is closely linked to comprehensive test coverage. CTFL-certified individuals are skilled in various testing techniques and approaches that ensure a wider range of scenarios are considered during testing. This increased coverage leads to better assurance of software quality.
Consistency in Testing: Standardized testing practices and terminology are emphasized in CTFL training. This consistency across testing efforts enhances collaboration within QA teams and between development and testing teams, resulting in higher quality products.
Reduced Software Defects: CTFL-certified professionals are well-versed in identifying, reporting, and managing software defects. This leads to a decrease in the number of critical defects that reach the production phase, ultimately improving the end-user experience.
Collaboration and Communication: Effective communication is vital in quality assurance. CTFL training promotes clear and concise communication among team members, including developers, stakeholders, and fellow testers. This enhances collaboration and understanding of quality objectives.
CTFL certification has a profound impact on quality assurance within the software development process. It empowers professionals to adopt best practices, improve defect detection, and ensure the consistency and reliability of the software being tested. The result is higher-quality software products that meet or exceed user expectations, ultimately contributing to the success of software projects and the satisfaction of end-users.
Increased Marketability
In today's competitive job market, having a strong skill set and relevant certifications can significantly boost your marketability. The CTFL certification, with its global recognition and focus on fundamental software testing knowledge, can make you a more attractive candidate to employers. Here's how CTFL certification increases your marketability:
Attractiveness to Employers: CTFL certification on your resume immediately sets you apart from other candidates. Employers often receive a large number of applications for job openings, and having a recognized certification demonstrates your commitment and expertise in software testing.
Wider Job Opportunities: CTFL certification opens the door to a broader range of job opportunities. Many job postings explicitly require or prefer candidates with testing certifications, giving you access to a variety of roles in different industries and sectors.
Industry Recognition: CTFL is internationally recognized and respected in the software testing industry. This recognition carries weight and establishes your credibility as a competent tester, regardless of your prior experience.
Confidence Boost: Being CTFL-certified boosts your self-confidence. Knowing that you have achieved a globally recognized certification enhances your self-assurance, making you more convincing in job interviews and discussions with potential employers.
Networking Opportunities: CTFL certification often connects you to a community of certified professionals. This network can provide valuable mentorship, guidance, and opportunities for collaboration, helping you expand your professional connections and discover new career possibilities.
CTFL certification significantly enhances your marketability in the software testing industry. It makes you a more appealing candidate for job opportunities, increases your earning potential, and positions you as a credible and proficient tester. This certification serves as a valuable investment in your career, providing long-term benefits in a competitive job market.
Career Transition
Changing careers can be a challenging and rewarding journey, and the CTFL certification can be a valuable asset in facilitating a transition into the field of software testing. Here's how CTFL certification can help individuals navigate a successful career transition:
Establishing Credibility: Career transitions often involve moving into a field where you may have limited prior experience. CTFL certification establishes your credibility and competence as a software tester, which can be reassuring to potential employers who may have concerns about your background.
Fundamental Knowledge: CTFL provides a foundational understanding of software testing principles and practices. It equips you with essential knowledge and skills, even if you are new to the field, giving you the confidence to contribute effectively in a testing role.
Career Entry: Many employers look for CTFL-certified individuals when hiring entry-level testers. This certification can be a foot in the door, making it easier to secure your first job in the software testing industry.
Networking Opportunities: CTFL certification often connects you with a community of certified professionals. This network can provide mentorship, guidance, and job leads, making your transition smoother and more informed.
Continuous Learning: CTFL certification instills a mindset of continuous learning. As you transition into a new career, this mindset will serve you well as you adapt to changing industry trends and technologies.
CTFL certification is an excellent resource for those seeking to make a career transition into the software testing field. It helps establish your credibility, provides foundational knowledge, and connects you to a supportive community. This certification is an invaluable tool to help you embark on a new and promising career in software testing, regardless of your prior professional background.
Knowledge Expansion
Continuous learning is a cornerstone of professional growth, especially in the dynamic field of software testing. CTFL certification not only validates existing knowledge but also serves as a catalyst for knowledge expansion. Here's how CTFL certification contributes to knowledge expansion:
Fundamental Knowledge: CTFL certification provides a solid foundation in software testing principles, methodologies, and terminology. This foundational knowledge is essential for building a comprehensive understanding of the field.
Test Automation: CTFL touches on test automation, providing an introduction to automation concepts and tools. This knowledge is particularly valuable in today's testing landscape, where automation is a key focus.
Risk Assessment: CTFL teaches you to assess risks in the software testing process. Understanding risk allows you to make informed decisions about where to focus your testing efforts, expanding your capacity to address high-impact areas.
Quality Standards: CTFL aligns with international quality and testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). Familiarity with these standards ensures your work is in line with recognized benchmarks.
Documentation Skills: Effective communication and documentation are vital in software testing. CTFL places importance on clear and structured test documentation, fostering your documentation skills.
Problem-Solving: Software testing often requires critical thinking and creative problem-solving. CTFL certification hones these skills as you learn to identify defects, investigate their causes, and suggest effective solutions.
Networking: CTFL certification often connects you with a community of certified professionals. This network provides opportunities for knowledge sharing, collaboration, and mentorship, expanding your knowledge base through the experiences of others.
CTFL certification is not just a static credential; it's a journey of knowledge expansion. It introduces you to the core concepts and practices in software testing, setting the stage for ongoing learning and growth in the field. As you apply what you've learned and continue to explore new horizons, your knowledge and expertise in software testing will naturally expand, making you a more valuable asset in the industry.
Professional Networking
Networking is an essential aspect of career development, and CTFL certification can significantly enhance your professional networking opportunities in the field of software testing. Here's how CTFL certification contributes to professional networking:
Access to a Certified Community: CTFL certification often connects you to a global community of certified professionals. This community provides a valuable network of like-minded individuals who share your passion for software testing and quality assurance.
Career Opportunities: Your network of CTFL-certified professionals can serve as a valuable resource for job leads and career opportunities. You may learn about job openings, referrals, or recommendations through your network.
Conferences and Events: Many software testing conferences and events host gatherings for certified professionals. Attending these events provides you with in-person networking opportunities, where you can meet and connect with fellow CTFL-certified individuals.
Local Chapters and Associations: CTFL certification is often associated with local and national testing associations and chapters. Joining these associations provides opportunities to network with professionals in your region and get involved in community activities.
Job References and Recommendations: Your professional network can serve as references and provide recommendations when you seek new opportunities or career growth. Having a strong network of colleagues who can vouch for your skills and work ethic can be invaluable.
CTFL certification extends beyond validating your skills; it connects you with a community of professionals who share your passion for software testing. The network you build through CTFL certification can offer knowledge sharing, mentorship, collaboration, job opportunities, and valuable career insights, ultimately enriching your career in the software testing industry.
Organizational Benefits
Enhanced Software Quality: CTFL-certified professionals possess a strong understanding of testing principles and best practices. Their expertise leads to improved software quality, reducing the number of defects and ensuring that the software meets or exceeds user expectations.
Reduced Defects and Costs: Early defect detection by CTFL-certified testers results in a reduction of defects that reach the production phase. This leads to cost savings by minimizing the need for post-release bug fixes and patches, which can be expensive and time-consuming.
Efficient Testing Processes: CTFL certification ensures that testing processes are optimized and aligned with industry best practices. This efficiency streamlines testing efforts, reduces redundancy, and enhances productivity within the organization.
Consistency and Standardization: CTFL-certified professionals adhere to standardized terminology and practices. This consistency improves communication within the testing team and fosters a unified approach to software testing.
Risk Mitigation: CTFL certification equips professionals with skills in risk assessment. They can identify high-risk areas within projects and allocate testing resources accordingly, reducing the likelihood of critical issues going unnoticed.
Alignment with Industry Standards: CTFL certification aligns with internationally recognized testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that the organization's testing practices conform to industry-recognized benchmarks.
Enhanced Test Documentation: Effective communication and documentation are vital in software testing. CTFL certification promotes clear and structured test documentation, enhancing transparency and facilitating project management.
Adaptability to Industry Changes: CTFL-certified professionals are well-prepared to adapt to industry changes, such as new technologies and methodologies. This adaptability allows the organization to stay competitive and relevant in the evolving field of software testing.
CTFL certification brings numerous organizational benefits, including improved software quality, cost savings, efficient testing processes, and a competitive advantage in the market. Organizations that invest in CTFL-certified professionals can deliver higher-quality software products, reduce risks, and gain a reputation for reliability and excellence in the field of software testing.
Long-Term Career Growth
CTFL certification serves as a foundational stepping stone for professionals in the software testing field, providing numerous opportunities for long-term career growth. Here's how CTFL certification can contribute to your career advancement over time:
Foundation for Advanced Certifications: CTFL is often the first step in a series of software testing certifications. Building upon CTFL, you can pursue more advanced certifications such as Certified Tester Advanced Level (CTAL) or specialized certifications in areas like test automation, security testing, or performance testing. These advanced certifications can open doors to higher-level roles and increased earning potential.
Expanded Skill Set: As you gain practical experience and advance in your career, the knowledge and skills acquired through CTFL certification continue to benefit you. The foundational principles and best practices you've learned serve as a solid base for acquiring new and more specialized skills over time.
Leadership Opportunities: CTFL-certified professionals are often well-positioned to take on leadership roles within their organizations. With experience and additional training, you can move into positions such as Test Manager or Test Lead, where you'll be responsible for managing testing teams and overseeing testing efforts.
Consulting and Training: With advanced certifications and substantial experience, you may choose to venture into consulting or training. Becoming a testing consultant or trainer can be a rewarding career path, offering opportunities to work with various organizations and share your expertise.
Industry Involvement: Many CTFL-certified professionals actively participate in industry associations, forums, and conferences. Involvement in industry organizations can expand your network, expose you to emerging trends, and provide opportunities for thought leadership.
Job Security: As the demand for high-quality software continues to grow, CTFL-certified professionals often enjoy job security. Organizations value individuals who can ensure software quality, making your career in software testing more resilient.
CTFL certification is not just a one-time achievement; it's a foundation for long-term career growth in the software testing and quality assurance field. Whether you choose to specialize, pursue advanced certifications, or take on leadership roles, CTFL certification provides the knowledge and credibility necessary to support your journey to success in the ever-evolving world of software testing.
Conclusion
In conclusion, the Certified Tester Foundation Level (CTFL) certification offers a wide range of benefits for individuals, organizations, and the software testing industry as a whole.
For individuals, CTFL certification serves as a valuable credential that enhances their skills, employability, and marketability.CTFL-certified professionals often find themselves well-prepared for various roles, from entry-level positions to more advanced, specialized, and leadership roles. This certification not only validates their expertise but also fosters a culture of continuous learning and adaptability, ensuring long-term career growth.
For organizations, CTFL-certified professionals bring a wealth of advantages. They contribute to improved software quality, reduced defects, cost savings, and efficient testing processes. CTFL certification aligns with industry standards and promotes consistency in testing practices, mitigating risks and enhancing documentation and communication. As a result, organizations benefit from higher client satisfaction, a competitive edge, and a reputation for reliability and quality in the software testing domain.
In essence, CTFL certification is not just a single achievement; it's a dynamic and evolving journey. It supports the growth and success of individuals and organizations in the field of software testing, ensuring that software products are of high quality, meet user expectations, and contribute to the advancement of the software industry as a whole.
Read More
In the ever-evolving landscape of software development, quality assurance and testing play a pivotal role in ensuring that applications and systems perform flawlessly. The Certified Tester Foundation Level (CTFL) certification stands as a beacon for those aspiring to excel in the field of software testing. It is a globally recognized and respected certification that opens doors to a world of opportunities in the realms of quality assurance and software testing. In this article, we will explore the numerous benefits of CTFL certification, shedding light on how it can empower individuals and organizations alike in their quest for excellence in software testing.
CTFL certification, like a well-constructed test plan, is structured to validate the skills and knowledge of aspiring software testers. It offers a multitude of advantages that extend beyond simply adding a prestigious credential to your name. This certification has the potential to reshape your career, enhance your skills, and contribute significantly to the quality and reliability of the software you are responsible for testing.
Let's dive deeper into the benefits of CTFL certification, from improved career prospects to enhanced testing capabilities, and discover why this certification is a game-changer in the world of software testing.
Table of Contents
-
Career Advancement
-
Global Recognition
-
Skill Enhancement
-
Quality Assurance Impact
-
Increased Marketability
-
Career Transition
-
Knowledge Expansion
-
Professional Networking
-
Organizational Benefits
-
Long-Term Career Growth
-
Conclusion
Career Advancement
In today's competitive job market, professionals are constantly seeking ways to distinguish themselves and achieve career growth. One powerful strategy to achieve career advancement, especially in the realm of software testing and quality assurance, is obtaining the Certified Tester Foundation Level (CTFL) certification. This certification offers a myriad of benefits that can significantly impact your career trajectory. Here's how:
Increased Employability: CTFL certification makes you a more attractive candidate to employers. It demonstrates your commitment to your field and validates your knowledge and skills in software testing. As a result, you become a preferred choice for hiring managers when filling positions related to quality assurance.
Career Opportunities: CTFL opens doors to a broader range of job opportunities. Whether you are seeking a new position, looking to switch industries, or aiming for a promotion within your current organization, having CTFL on your resume can make a substantial difference. Many job postings explicitly require or prefer candidates with testing certifications.
Salary Advancement: It's no secret that certified professionals often command higher salaries. CTFL certification can lead to better compensation packages, including increased base pay, bonuses, and benefits. Employers are willing to pay more for professionals who bring demonstrable skills and expertise to the table.
Career Progression: Career advancement isn't just about securing a job; it's also about climbing the career ladder. CTFL certification provides a solid foundation for further career progression. It can serve as a stepping stone to more advanced certifications and senior roles within the software testing domain.
Improved Job Security: With the increasing demand for quality software, CTFL-certified professionals tend to enjoy more job security. In times of economic uncertainty, organizations are less likely to let go of employees who are essential to ensuring the quality of their products.
CTFL certification is a strategic investment in your career. It enhances your employability, increases your career opportunities, and can lead to higher earnings. Beyond the financial aspects, it also nurtures your professional growth, offering job security and the potential for leadership roles. In the dynamic field of software testing, CTFL certification is a pathway to a rewarding and successful career.
Global Recognition
In an increasingly interconnected world, the value of professional certifications extends far beyond local or regional boundaries. The Certified Tester Foundation Level (CTFL) certification is a prime example of a qualification that enjoys widespread global recognition and respect. This recognition has several significant implications for those who hold the CTFL certification:
International Employability: One of the most compelling benefits of CTFL certification is that it's universally recognized. Whether you are looking to work in your home country or explore opportunities abroad, having CTFL on your resume assures potential employers of your standardized expertise in software testing. This opens doors to a diverse range of international job markets.
Consistency in Skill Set: CTFL's global recognition means that certified professionals share a common knowledge base and understanding of software testing practices. This consistency ensures that employers, regardless of their location, can rely on the skills and competencies of CTFL-certified individuals.
Trust and Credibility: CTFL is endorsed by a variety of prominent organizations and industry bodies. This certification carries an assurance of quality and reliability. Employers often trust the certification as a benchmark of excellence in software testing.
Cross-Industry Applicability: The principles and best practices in software testing are universal and relevant across various industries. CTFL's global recognition allows certified professionals to transition seamlessly between different sectors, such as healthcare, finance, automotive, and more.
Alignment with Industry Standards: CTFL aligns with international testing and quality standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that CTFL-certified individuals have a strong foundation in globally accepted testing methodologies.
International Collaboration: Being part of the CTFL-certified community provides opportunities for international collaboration. You can connect with professionals from diverse backgrounds, share knowledge, and stay updated on global testing trends and practices.
Competitive Advantage: When competing for job roles or promotions, CTFL certification can give you a significant competitive advantage. Employers often prioritize candidates with internationally recognized certifications to ensure their teams adhere to global testing standards.
In summary, the global recognition of CTFL certification is not just a label; it's a powerful testament to your skills and expertise in software testing that transcends borders. This recognition facilitates international career opportunities, provides a foundation for consistent quality, and positions you as a credible and trusted professional in the ever-expanding global software testing community.
Skill Enhancement
Certainly, let's delve into the subtopic of "Skill Enhancement" and explore how the Certified Tester Foundation Level (CTFL) certification can significantly enhance one's skills in the field of software testing:
Skill Enhancement with CTFL Certification
In the dynamic and ever-evolving realm of software testing, the ability to adapt, learn, and master new skills is essential for professional growth. CTFL certification is a gateway to skill enhancement, providing individuals with a structured and comprehensive foundation in software testing. Here's how CTFL enhances one's skills:
Comprehensive Understanding of Software Testing: CTFL certification equips professionals with a holistic understanding of software testing concepts, methodologies, and techniques. This includes knowledge of test planning, test design, test execution, and test management. By mastering these fundamentals, CTFL-certified individuals can contribute more effectively to the testing process.
Practical Testing Techniques: CTFL covers practical testing techniques that are essential for efficient software testing. It includes topics like boundary value analysis, equivalence partitioning, and decision table testing. These techniques enable testers to design and execute test cases that identify defects and improve software quality.
Test Documentation: Effective communication and documentation are key skills in software testing. CTFL certification emphasizes the creation of clear and well-organized test documentation, including test plans, test cases, and test reports. This skill enhances transparency and collaboration within testing teams.
Test Management: CTFL provides insights into test management practices, which involve planning, monitoring, and controlling testing activities. Understanding test management allows professionals to ensure that testing efforts align with project goals and timelines.
Effective Communication: Effective communication is vital for collaborating with development teams, stakeholders, and fellow testers. CTFL training encourages clear and concise communication, improving teamwork and understanding of testing objectives.
CTFL certification is a powerful catalyst for skill enhancement in the software testing domain. It imparts a strong foundation of knowledge and practical skills, enabling professionals to excel in their testing roles. By continually honing their abilities and staying up-to-date with industry best practices, CTFL-certified individuals can contribute significantly to the quality and reliability of the software they test.
Quality Assurance Impact
Quality assurance (QA) is at the heart of delivering reliable and high-quality software products. CTFL certification plays a pivotal role in enhancing and contributing to the overall quality assurance process. Here's how CTFL certification can impact quality assurance:
Early Defect Detection: CTFL emphasizes the importance of detecting defects at an early stage of the software development life cycle. CTFL-certified testers are trained to create test cases that catch defects before they propagate to later phases, reducing the cost and effort required for fixing them.
Enhanced Test Coverage: Quality assurance is closely linked to comprehensive test coverage. CTFL-certified individuals are skilled in various testing techniques and approaches that ensure a wider range of scenarios are considered during testing. This increased coverage leads to better assurance of software quality.
Consistency in Testing: Standardized testing practices and terminology are emphasized in CTFL training. This consistency across testing efforts enhances collaboration within QA teams and between development and testing teams, resulting in higher quality products.
Reduced Software Defects: CTFL-certified professionals are well-versed in identifying, reporting, and managing software defects. This leads to a decrease in the number of critical defects that reach the production phase, ultimately improving the end-user experience.
Collaboration and Communication: Effective communication is vital in quality assurance. CTFL training promotes clear and concise communication among team members, including developers, stakeholders, and fellow testers. This enhances collaboration and understanding of quality objectives.
CTFL certification has a profound impact on quality assurance within the software development process. It empowers professionals to adopt best practices, improve defect detection, and ensure the consistency and reliability of the software being tested. The result is higher-quality software products that meet or exceed user expectations, ultimately contributing to the success of software projects and the satisfaction of end-users.
Increased Marketability
In today's competitive job market, having a strong skill set and relevant certifications can significantly boost your marketability. The CTFL certification, with its global recognition and focus on fundamental software testing knowledge, can make you a more attractive candidate to employers. Here's how CTFL certification increases your marketability:
Attractiveness to Employers: CTFL certification on your resume immediately sets you apart from other candidates. Employers often receive a large number of applications for job openings, and having a recognized certification demonstrates your commitment and expertise in software testing.
Wider Job Opportunities: CTFL certification opens the door to a broader range of job opportunities. Many job postings explicitly require or prefer candidates with testing certifications, giving you access to a variety of roles in different industries and sectors.
Industry Recognition: CTFL is internationally recognized and respected in the software testing industry. This recognition carries weight and establishes your credibility as a competent tester, regardless of your prior experience.
Confidence Boost: Being CTFL-certified boosts your self-confidence. Knowing that you have achieved a globally recognized certification enhances your self-assurance, making you more convincing in job interviews and discussions with potential employers.
Networking Opportunities: CTFL certification often connects you to a community of certified professionals. This network can provide valuable mentorship, guidance, and opportunities for collaboration, helping you expand your professional connections and discover new career possibilities.
CTFL certification significantly enhances your marketability in the software testing industry. It makes you a more appealing candidate for job opportunities, increases your earning potential, and positions you as a credible and proficient tester. This certification serves as a valuable investment in your career, providing long-term benefits in a competitive job market.
Career Transition
Changing careers can be a challenging and rewarding journey, and the CTFL certification can be a valuable asset in facilitating a transition into the field of software testing. Here's how CTFL certification can help individuals navigate a successful career transition:
Establishing Credibility: Career transitions often involve moving into a field where you may have limited prior experience. CTFL certification establishes your credibility and competence as a software tester, which can be reassuring to potential employers who may have concerns about your background.
Fundamental Knowledge: CTFL provides a foundational understanding of software testing principles and practices. It equips you with essential knowledge and skills, even if you are new to the field, giving you the confidence to contribute effectively in a testing role.
Career Entry: Many employers look for CTFL-certified individuals when hiring entry-level testers. This certification can be a foot in the door, making it easier to secure your first job in the software testing industry.
Networking Opportunities: CTFL certification often connects you with a community of certified professionals. This network can provide mentorship, guidance, and job leads, making your transition smoother and more informed.
Continuous Learning: CTFL certification instills a mindset of continuous learning. As you transition into a new career, this mindset will serve you well as you adapt to changing industry trends and technologies.
CTFL certification is an excellent resource for those seeking to make a career transition into the software testing field. It helps establish your credibility, provides foundational knowledge, and connects you to a supportive community. This certification is an invaluable tool to help you embark on a new and promising career in software testing, regardless of your prior professional background.
Knowledge Expansion
Continuous learning is a cornerstone of professional growth, especially in the dynamic field of software testing. CTFL certification not only validates existing knowledge but also serves as a catalyst for knowledge expansion. Here's how CTFL certification contributes to knowledge expansion:
Fundamental Knowledge: CTFL certification provides a solid foundation in software testing principles, methodologies, and terminology. This foundational knowledge is essential for building a comprehensive understanding of the field.
Test Automation: CTFL touches on test automation, providing an introduction to automation concepts and tools. This knowledge is particularly valuable in today's testing landscape, where automation is a key focus.
Risk Assessment: CTFL teaches you to assess risks in the software testing process. Understanding risk allows you to make informed decisions about where to focus your testing efforts, expanding your capacity to address high-impact areas.
Quality Standards: CTFL aligns with international quality and testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). Familiarity with these standards ensures your work is in line with recognized benchmarks.
Documentation Skills: Effective communication and documentation are vital in software testing. CTFL places importance on clear and structured test documentation, fostering your documentation skills.
Problem-Solving: Software testing often requires critical thinking and creative problem-solving. CTFL certification hones these skills as you learn to identify defects, investigate their causes, and suggest effective solutions.
Networking: CTFL certification often connects you with a community of certified professionals. This network provides opportunities for knowledge sharing, collaboration, and mentorship, expanding your knowledge base through the experiences of others.
CTFL certification is not just a static credential; it's a journey of knowledge expansion. It introduces you to the core concepts and practices in software testing, setting the stage for ongoing learning and growth in the field. As you apply what you've learned and continue to explore new horizons, your knowledge and expertise in software testing will naturally expand, making you a more valuable asset in the industry.
Professional Networking
Networking is an essential aspect of career development, and CTFL certification can significantly enhance your professional networking opportunities in the field of software testing. Here's how CTFL certification contributes to professional networking:
Access to a Certified Community: CTFL certification often connects you to a global community of certified professionals. This community provides a valuable network of like-minded individuals who share your passion for software testing and quality assurance.
Career Opportunities: Your network of CTFL-certified professionals can serve as a valuable resource for job leads and career opportunities. You may learn about job openings, referrals, or recommendations through your network.
Conferences and Events: Many software testing conferences and events host gatherings for certified professionals. Attending these events provides you with in-person networking opportunities, where you can meet and connect with fellow CTFL-certified individuals.
Local Chapters and Associations: CTFL certification is often associated with local and national testing associations and chapters. Joining these associations provides opportunities to network with professionals in your region and get involved in community activities.
Job References and Recommendations: Your professional network can serve as references and provide recommendations when you seek new opportunities or career growth. Having a strong network of colleagues who can vouch for your skills and work ethic can be invaluable.
CTFL certification extends beyond validating your skills; it connects you with a community of professionals who share your passion for software testing. The network you build through CTFL certification can offer knowledge sharing, mentorship, collaboration, job opportunities, and valuable career insights, ultimately enriching your career in the software testing industry.
Organizational Benefits
Enhanced Software Quality: CTFL-certified professionals possess a strong understanding of testing principles and best practices. Their expertise leads to improved software quality, reducing the number of defects and ensuring that the software meets or exceeds user expectations.
Reduced Defects and Costs: Early defect detection by CTFL-certified testers results in a reduction of defects that reach the production phase. This leads to cost savings by minimizing the need for post-release bug fixes and patches, which can be expensive and time-consuming.
Efficient Testing Processes: CTFL certification ensures that testing processes are optimized and aligned with industry best practices. This efficiency streamlines testing efforts, reduces redundancy, and enhances productivity within the organization.
Consistency and Standardization: CTFL-certified professionals adhere to standardized terminology and practices. This consistency improves communication within the testing team and fosters a unified approach to software testing.
Risk Mitigation: CTFL certification equips professionals with skills in risk assessment. They can identify high-risk areas within projects and allocate testing resources accordingly, reducing the likelihood of critical issues going unnoticed.
Alignment with Industry Standards: CTFL certification aligns with internationally recognized testing standards, including those defined by the International Software Testing Qualifications Board (ISTQB). This alignment ensures that the organization's testing practices conform to industry-recognized benchmarks.
Enhanced Test Documentation: Effective communication and documentation are vital in software testing. CTFL certification promotes clear and structured test documentation, enhancing transparency and facilitating project management.
Adaptability to Industry Changes: CTFL-certified professionals are well-prepared to adapt to industry changes, such as new technologies and methodologies. This adaptability allows the organization to stay competitive and relevant in the evolving field of software testing.
CTFL certification brings numerous organizational benefits, including improved software quality, cost savings, efficient testing processes, and a competitive advantage in the market. Organizations that invest in CTFL-certified professionals can deliver higher-quality software products, reduce risks, and gain a reputation for reliability and excellence in the field of software testing.
Long-Term Career Growth
CTFL certification serves as a foundational stepping stone for professionals in the software testing field, providing numerous opportunities for long-term career growth. Here's how CTFL certification can contribute to your career advancement over time:
Foundation for Advanced Certifications: CTFL is often the first step in a series of software testing certifications. Building upon CTFL, you can pursue more advanced certifications such as Certified Tester Advanced Level (CTAL) or specialized certifications in areas like test automation, security testing, or performance testing. These advanced certifications can open doors to higher-level roles and increased earning potential.
Expanded Skill Set: As you gain practical experience and advance in your career, the knowledge and skills acquired through CTFL certification continue to benefit you. The foundational principles and best practices you've learned serve as a solid base for acquiring new and more specialized skills over time.
Leadership Opportunities: CTFL-certified professionals are often well-positioned to take on leadership roles within their organizations. With experience and additional training, you can move into positions such as Test Manager or Test Lead, where you'll be responsible for managing testing teams and overseeing testing efforts.
Consulting and Training: With advanced certifications and substantial experience, you may choose to venture into consulting or training. Becoming a testing consultant or trainer can be a rewarding career path, offering opportunities to work with various organizations and share your expertise.
Industry Involvement: Many CTFL-certified professionals actively participate in industry associations, forums, and conferences. Involvement in industry organizations can expand your network, expose you to emerging trends, and provide opportunities for thought leadership.
Job Security: As the demand for high-quality software continues to grow, CTFL-certified professionals often enjoy job security. Organizations value individuals who can ensure software quality, making your career in software testing more resilient.
CTFL certification is not just a one-time achievement; it's a foundation for long-term career growth in the software testing and quality assurance field. Whether you choose to specialize, pursue advanced certifications, or take on leadership roles, CTFL certification provides the knowledge and credibility necessary to support your journey to success in the ever-evolving world of software testing.
Conclusion
In conclusion, the Certified Tester Foundation Level (CTFL) certification offers a wide range of benefits for individuals, organizations, and the software testing industry as a whole.
For individuals, CTFL certification serves as a valuable credential that enhances their skills, employability, and marketability.CTFL-certified professionals often find themselves well-prepared for various roles, from entry-level positions to more advanced, specialized, and leadership roles. This certification not only validates their expertise but also fosters a culture of continuous learning and adaptability, ensuring long-term career growth.
For organizations, CTFL-certified professionals bring a wealth of advantages. They contribute to improved software quality, reduced defects, cost savings, and efficient testing processes. CTFL certification aligns with industry standards and promotes consistency in testing practices, mitigating risks and enhancing documentation and communication. As a result, organizations benefit from higher client satisfaction, a competitive edge, and a reputation for reliability and quality in the software testing domain.
In essence, CTFL certification is not just a single achievement; it's a dynamic and evolving journey. It supports the growth and success of individuals and organizations in the field of software testing, ensuring that software products are of high quality, meet user expectations, and contribute to the advancement of the software industry as a whole.
Python for Data Science: A Comprehensive Overview
Python has emerged as one of the most versatile and powerful programming languages for data science. Its simplicity, readability, and a rich ecosystem of libraries make it the go-to choice for data analysts, scientists, and engineers. Whether you're looking to explore, analyze, visualize, or manipulate data, Python provides a robust foundation to handle it all.
Data science is all about extracting meaningful insights from data, and Python simplifies this process. It offers a wide range of libraries and tools specifically designed to tackle the complexities of data analysis, machine learning, and statistical modeling. Some of the key libraries in the Python data science stack include NumPy for numerical computing, pandas for data manipulation, Matplotlib and Seaborn for data visualization, and scikit-learn for machine learning tasks.
Python for data science is not just a skill but a gateway to a world of opportunities. It's the key to solving real-world problems, making informed decisions, and discovering insights that can drive innovation and progress in various fields. So, fasten your seatbelts as we embark on this exciting journey through Python for data science, where the world of data is waiting to be explored, analyzed, and understood.
Table of contents
-
Data Cleaning and Preprocessing in Python
-
Data Visualization with Matplotlib and Seaborn
-
Exploratory Data Analysis (EDA) with Python
-
Statistical Analysis with Python
-
Machine Learning with Scikit-Learn
-
Deep Learning with Python and TensorFlow/Keras
-
Time Series Analysis with Python
-
Feature Engineering in Data Science
-
Data Science Best Practices in Python
-
Real-World Data Science Projects with Python
-
Conclusion
Data Cleaning and Preprocessing in Python
Data cleaning and preprocessing are essential steps in the data science workflow. Raw data is often messy and incomplete, and it's crucial to transform it into a clean, structured format before analysis or modeling. Python, with its powerful libraries such as Pandas and NumPy, offers an efficient environment for these tasks. In this article, we'll explore the key concepts and techniques for data cleaning and preprocessing in Python.
Importing Data: Begin by loading your dataset into Python. Common file formats include CSV, Excel, JSON, and SQL databases. Use Pandas to read and manipulate data with ease.
Removing Duplicates: Duplicate entries can distort analysis. Learn how to identify and remove duplicate rows in your dataset using Pandas.
Data Transformation: Convert data types, standardize values, and handle outliers. Techniques like scaling, encoding categorical variables, and feature engineering play a crucial role.
Handling Text Data: Text data may require special preprocessing for natural language processing (NLP) tasks. Techniques include tokenization, stemming, and removing stopwords.
Data Imputation: When dealing with missing values, you can impute them using techniques like mean imputation, regression imputation, or advanced methods like K-nearest neighbors imputation.
Data Aggregation and Grouping: For summarizing or aggregating data, you can group it by specific attributes and apply functions for creating new features.
Documentation: Maintain clear documentation of the steps taken during data cleaning and preprocessing to ensure transparency and reproducibility.
In this article series, we will dive deeper into each of these topics, providing code examples and best practices for effective data cleaning and preprocessing using Python. Understanding these fundamental data preparation steps is crucial for any data science project and lays the foundation for meaningful analysis and modeling.
Data Visualization with Matplotlib and Seaborn
Data visualization is a powerful tool in the data science and analytics toolkit. It allows you to communicate insights, patterns, and trends in your data more effectively. In the Python data science ecosystem, Matplotlib and Seaborn are two of the most popular libraries for creating a wide range of data visualizations. In this article, we'll explore how to use Matplotlib and Seaborn to visualize data in Python.
Introduction to Matplotlib:Start by introducing Matplotlib, a versatile and customizable plotting library. Cover the basics of creating various types of plots, such as line plots, bar charts, scatter plots, and histograms.
Customizing Matplotlib Plots:Explain how to customize plots by adjusting colors, labels, titles, and axis properties. Dive into Matplotlib's object-oriented approach for fine-grained control.
Multiple Subplots and Figures:Explore how to create multiple subplots within a single figure, which is particularly useful for visualizing multiple aspects of your data.
Introduction to Seaborn:Introduce Seaborn, a high-level interface for creating informative and visually appealing statistical graphics. Explain its advantages over Matplotlib.
Seaborn for Statistical Plots:Explore Seaborn's capabilities for creating statistical plots, such as box plots, violin plots, and pair plots, which provide insights into data distributions and relationships.
Seaborn's Categorical Plots:Cover Seaborn's categorical plotting functions, like bar plots, count plots, and point plots, which are useful for visualizing categorical data.
Seaborn for Regression and Relationships:Show how Seaborn simplifies the creation of regression plots and scatter plots with built-in trend lines.
Throughout this article series, we will provide code examples and best practices for creating various types of data visualizations, from basic charts to complex statistical plots. By the end, you'll have the skills to effectively communicate data insights using Matplotlib and Seaborn in your Python data science projects.
Exploratory Data Analysis (EDA) with Python
Exploratory Data Analysis (EDA) is a critical step in the data science process that involves examining and understanding the characteristics of your dataset before diving into more advanced modeling or analysis. EDA helps you discover patterns, relationships, and potential outliers in your data. In this article, we'll explore how to perform EDA using Python, making use of libraries such as Pandas, Matplotlib, Seaborn, and Plotly.
Introduction to EDA:Explain the importance of EDA in the data science workflow and how it can guide subsequent analysis.
Data Visualization for Initial Insights:Use Matplotlib and Seaborn to create basic visualizations like histograms, box plots, and scatter plots to gain initial insights into the data's distributions and relationships.
Handling Missing Data:Explore strategies for dealing with missing data, such as imputation or removal, and assess the impact of missing values on your analysis.
Exploring Categorical Data:Examine techniques for visualizing and analyzing categorical variables, including bar plots and frequency tables.
Time Series Data EDA: - For time series data, explore techniques specific to EDA, including time series decomposition and autocorrelation analysis.
Advanced EDA Techniques: - Cover more advanced techniques like Principal Component Analysis (PCA) for dimensionality reduction and t-SNE for visualizing high-dimensional data.
Interactive EDA: - Introduce interactive EDA tools like Plotly, which allow for dynamic exploration and visualization of data.
EDA in Real-World Projects: - Showcase case studies of EDA applied to real-world datasets, such as analyzing retail sales data or exploring trends in health and demographic data.
Throughout this article series, you'll gain a comprehensive understanding of EDA techniques, from basic data summarization to advanced visualization methods. EDA is a crucial step in the data science process, as it lays the foundation for making informed decisions about data preprocessing, feature engineering, and model selection.
Statistical Analysis with Python
Statistical analysis plays a fundamental role in data science, allowing you to draw meaningful insights, make data-driven decisions, and test hypotheses. Python offers a rich ecosystem of libraries for performing statistical analysis. In this article, we'll delve into the key concepts and techniques for statistical analysis using Python, covering both descriptive and inferential statistics.
Introduction to Statistical Analysis:Explain the importance of statistical analysis in data science and its various applications.
Descriptive Statistics:Explore how to calculate and interpret basic descriptive statistics such as mean, median, variance, and standard deviation using Python's libraries like NumPy.
Confidence Intervals:Explain how to calculate and interpret confidence intervals for parameter estimation using Python.
Statistical Analysis in Real-World Projects: - Showcase case studies where statistical analysis is applied to real-world datasets, such as A/B testing, quality control, and social science research.
Data Ethics and Misinterpretation: - Discuss the importance of ethical considerations in statistical analysis, as well as common pitfalls and misinterpretations.
Interactive Data Exploration: - Introduce interactive tools like Jupyter notebooks and libraries like Plotly for dynamic data exploration and visualization in statistical analysis.
Throughout this article series, you'll gain a strong understanding of statistical analysis concepts and how to apply them using Python. Whether you're dealing with basic descriptive statistics or more advanced inferential statistics, Python's libraries like NumPy, SciPy, statsmodels, and others make the process efficient and accessible for data scientists and analysts.
Machine Learning with Scikit-Learn
Machine learning is a subfield of artificial intelligence that empowers computers to learn from data and make predictions or decisions. Scikit-Learn (or sklearn) is a powerful machine learning library for Python that provides a wide range of tools for building and deploying machine learning models. In this article series, we will explore the key concepts and techniques for machine learning using Scikit-Learn.
Introduction to Machine Learning:Provide an overview of machine learning, its applications, and the different types of machine learning algorithms (supervised, unsupervised, reinforcement learning).
Setting Up Scikit-Learn:Guide readers on how to install Scikit-Learn, set up a Python environment, and import the necessary libraries.
Feature Engineering:Explore the importance of feature engineering in machine learning and demonstrate how to prepare data for modeling using Scikit-Learn's preprocessing tools.
Ensembles and Random Forests:Dive into ensemble methods, focusing on the Random Forest algorithm and its implementation in Scikit-Learn.
Support Vector Machines (SVM):Explain the theory and practical usage of Support Vector Machines for classification problems using Scikit-Learn.
Natural Language Processing (NLP) with Scikit-Learn: - Explore how Scikit-Learn can be used for text analysis and NLP tasks, such as sentiment analysis and text classification.
Throughout this article series, you'll gain a strong foundation in machine learning principles and practical experience in implementing machine learning models using Scikit-Learn. Whether you're a beginner looking to get started or an experienced data scientist, Scikit-Learn offers a user-friendly and powerful toolset for building and deploying machine learning solutions.
Deep Learning with Python and TensorFlow/Keras
Deep learning is a subfield of machine learning that focuses on neural networks with multiple layers, allowing computers to learn and make decisions in a manner similar to the human brain. TensorFlow and Keras are two of the most popular libraries for deep learning in Python. In this article series, we will explore the fundamentals of deep learning and how to implement deep neural networks using TensorFlow and Keras.
Introduction to Deep Learning:Provide an overview of deep learning, its significance, and its applications in various domains, including computer vision, natural language processing, and reinforcement learning.
Setting Up TensorFlow and Keras:Guide readers on how to install TensorFlow and Keras, set up a Python environment, and import the necessary libraries.
Building Neural Networks with Keras:Introduce the Keras library for building deep neural networks. Cover the basics of feedforward neural networks, activation functions, and loss functions.
Convolutional Neural Networks (CNNs):Explore CNNs, a class of neural networks specialized for image analysis and recognition. Explain how to build and train CNNs for image classification using Keras.
Transfer Learning and Pretrained Models:Introduce transfer learning and how to leverage pretrained deep learning models to solve tasks, such as image classification or text sentiment analysis.
Natural Language Processing (NLP) with Deep Learning:Explore the use of deep learning in NLP tasks, including text classification, sentiment analysis, and sequence-to-sequence tasks.
Generative Adversarial Networks (GANs):Explain GANs, a deep learning architecture for generating new data samples, and demonstrate their use in creating realistic images.
By the end of this article series, you will have a strong foundation in deep learning concepts and practical experience in building deep neural networks using TensorFlow and Keras. Deep learning has revolutionized many fields, and with the right knowledge and tools, you can leverage its power to solve a wide range of complex problems.
Time Series Analysis with Python
Time series data is a sequence of data points collected or recorded at regular time intervals. Time series analysis is essential for understanding temporal trends, making forecasts, and uncovering patterns in time-dependent data. In this article series, we will explore the concepts and techniques for time series analysis using Python.
Introduction to Time Series Data:Provide an overview of time series data, its characteristics, and real-world applications in finance, economics, and more.
Time Series Data Preprocessing:Discuss the importance of data cleaning, handling missing values, and resampling time series data to make it suitable for analysis.
Exploratory Data Analysis for Time Series:Cover techniques for visualizing and understanding time series data, including time plots, seasonality, and trend analysis.
Time Series Decomposition:Explain how to decompose a time series into its components, such as trend, seasonality, and residual, using Python libraries like Statsmodels.
Forecasting Methods:Introduce various time series forecasting methods, including moving averages, exponential smoothing, and autoregressive integrated moving average (ARIMA) models.
Long Short-Term Memory (LSTM) Networks for Time Series: - Dive into deep learning approaches for time series forecasting using LSTM networks and demonstrate their implementation with libraries like TensorFlow/Keras.
Real-World Time Series Projects: - Showcase case studies of time series analysis and forecasting applied to real-world data, such as stock price prediction, energy demand forecasting, and weather forecasting.
By the end of this article series, you'll have a solid understanding of time series analysis techniques, from basic data preprocessing and visualization to advanced forecasting methods and deep learning models. Time series analysis is a valuable skill for making predictions and informed decisions in various domains, and Python provides a powerful environment for performing these analyses.
Feature Engineering in Data Science
Feature engineering is the process of selecting, transforming, and creating relevant features (variables) from raw data to improve the performance of machine learning models. It plays a crucial role in data science, as the quality of features significantly impacts the model's ability to extract meaningful patterns from data. In this article series, we'll explore the fundamental concepts and techniques for feature engineering in data science.
Introduction to Feature Engineering:Provide an overview of what feature engineering is, why it's essential, and its impact on the performance of machine learning models.
Feature Selection Techniques:Discuss methods for choosing the most important features, including filtering, wrapper methods, and embedded methods. Explain how to implement these techniques using Python libraries like Scikit-Learn.
Handling Missing Data:Cover strategies for dealing with missing values in features, such as imputation, removal, and the use of techniques like K-nearest neighbors imputation.
Encoding Categorical Variables:Explain how to convert categorical variables into a numerical format suitable for machine learning models. Discuss one-hot encoding, label encoding, and target encoding.
Feature Scaling and Normalization:Explore the importance of scaling features to a common range, and discuss techniques like Min-Max scaling and Z-score standardization.
Feature Transformation:Introduce techniques like logarithm transformation, square root transformation, and Box-Cox transformation for improving the distribution of features.
Image Data Feature Engineering: - Discuss methods for extracting features from images, including deep learning techniques like convolutional neural networks (CNNs) for feature extraction.
Feature Engineering Best Practices: - Share tips, best practices, and considerations for effective feature engineering, including the importance of domain knowledge and the iterative nature of the process.
Feature engineering is a creative and iterative process that involves domain knowledge, data exploration, and experimentation. By understanding the techniques and best practices covered in this article series, you'll be equipped to extract the most relevant information from your data and improve the performance of your machine learning models.
Data Science Best Practices in Python
Data science is a multidisciplinary field that involves collecting, cleaning, analyzing, and interpreting data to extract meaningful insights and make data-driven decisions. Python has become a dominant language in data science due to its rich ecosystem of libraries and tools. In this article series, we'll explore best practices and guidelines for conducting data science projects in Python.
Project Planning and Problem Definition:Discuss the importance of defining clear project objectives, problem statements, and success criteria before diving into data analysis. Emphasize the need for domain knowledge and collaboration with stakeholders.
Data Collection and Exploration:Explain the process of data acquisition, including web scraping, API access, and data ingestion. Discuss the importance of exploring data to understand its structure and quality, including identifying missing values and outliers.
Data Cleaning and Preprocessing:Cover techniques for handling missing data, removing duplicates, and transforming data into a suitable format. Discuss feature engineering and encoding categorical variables.
Data Visualization and EDA:Highlight the importance of exploratory data analysis (EDA) and data visualization to gain insights and identify patterns in the data. Discuss best practices for creating effective visualizations.
Model Selection and Evaluation:Explain the process of selecting appropriate machine learning models, splitting data into training and testing sets, and evaluating models using relevant metrics. Discuss cross-validation and hyperparameter tuning.
Model Deployment and Production:Introduce methods for deploying machine learning models to production, such as creating RESTful APIs, containerization, and cloud deployment. Discuss considerations for model maintenance and monitoring.
By following these best practices in Python data science projects, you'll be better equipped to navigate the complexities of real-world data analysis and modeling. Data science is a dynamic field that requires a combination of technical skills, domain knowledge, and adherence to sound methodologies for delivering valuable insights and solutions.
Real-World Data Science Projects with Python
Applying data science techniques to real-world projects is essential for gaining practical experience and solving complex problems. In this article series, we'll explore a variety of real-world data science projects and how to approach them using Python. These projects cover a range of domains and scenarios to showcase the versatility and power of data science in solving actual problems.
Predictive Maintenance for Equipment:Explore how to use historical equipment data to predict maintenance needs and prevent costly downtime. Implement machine learning models for predicting equipment failures using Python libraries.
Sentiment Analysis for Social Media Data:Develop a sentiment analysis project to gauge public sentiment on social media. Utilize Python's NLP libraries and machine learning techniques to classify text data as positive, negative, or neutral.
Credit Scoring and Risk Assessment:Build a credit scoring model to assess the creditworthiness of individuals or businesses. Employ Python to analyze financial data and create a predictive model for risk assessment.
Fraud Detection:Develop a fraud detection system using machine learning and anomaly detection to identify suspicious transactions and activities in financial or online systems.
Energy Consumption Forecasting: - Develop a project that forecasts energy consumption, which can be useful for energy management and resource allocation. Utilize time series analysis and predictive modeling with Python libraries.
Demand Forecasting for Retail: - Create a demand forecasting model for retail businesses to optimize inventory management. Use Python for data preprocessing, time series analysis, and machine learning.
Text Summarization and Text Generation: - Explore the generation of automatic summaries for articles and reports or even build a text generation model like a chatbot or creative writing AI using Python's NLP and deep learning capabilities.
These real-world data science projects in Python are designed to provide practical experience and demonstrate the applicability of data science techniques in diverse domains. By working on these projects, you'll gain valuable insights into data analysis, model development, and problem-solving, and you'll be better prepared to tackle real-world data science challenges.
Conclusion
In conclusion, Python is a versatile and powerful programming language for data science, offering a vast ecosystem of libraries and tools that make it a go-to choice for data analysis, machine learning, and more. The article series we've discussed covers a wide range of topics and projects in the field of data science, from foundational concepts like data cleaning and preprocessing to advanced areas like deep learning, time series analysis, and real-world projects.
As you dive into the world of data science in Python, remember that continuous learning and practice are key to mastering the field. Keep exploring, experimenting, and working on projects to hone your skills and stay up-to-date with the latest developments in the data science community.
Whether you're new to data science or looking to deepen your expertise, the knowledge and skills you gain in Python data science will enable you to extract valuable insights, make data-driven decisions, and contribute to solving real-world problems in various domains. Good luck on your data science journey!
Read More
Python has emerged as one of the most versatile and powerful programming languages for data science. Its simplicity, readability, and a rich ecosystem of libraries make it the go-to choice for data analysts, scientists, and engineers. Whether you're looking to explore, analyze, visualize, or manipulate data, Python provides a robust foundation to handle it all.
Data science is all about extracting meaningful insights from data, and Python simplifies this process. It offers a wide range of libraries and tools specifically designed to tackle the complexities of data analysis, machine learning, and statistical modeling. Some of the key libraries in the Python data science stack include NumPy for numerical computing, pandas for data manipulation, Matplotlib and Seaborn for data visualization, and scikit-learn for machine learning tasks.
Python for data science is not just a skill but a gateway to a world of opportunities. It's the key to solving real-world problems, making informed decisions, and discovering insights that can drive innovation and progress in various fields. So, fasten your seatbelts as we embark on this exciting journey through Python for data science, where the world of data is waiting to be explored, analyzed, and understood.
Table of contents
-
Data Cleaning and Preprocessing in Python
-
Data Visualization with Matplotlib and Seaborn
-
Exploratory Data Analysis (EDA) with Python
-
Statistical Analysis with Python
-
Machine Learning with Scikit-Learn
-
Deep Learning with Python and TensorFlow/Keras
-
Time Series Analysis with Python
-
Feature Engineering in Data Science
-
Data Science Best Practices in Python
-
Real-World Data Science Projects with Python
-
Conclusion
Data Cleaning and Preprocessing in Python
Data cleaning and preprocessing are essential steps in the data science workflow. Raw data is often messy and incomplete, and it's crucial to transform it into a clean, structured format before analysis or modeling. Python, with its powerful libraries such as Pandas and NumPy, offers an efficient environment for these tasks. In this article, we'll explore the key concepts and techniques for data cleaning and preprocessing in Python.
Importing Data: Begin by loading your dataset into Python. Common file formats include CSV, Excel, JSON, and SQL databases. Use Pandas to read and manipulate data with ease.
Removing Duplicates: Duplicate entries can distort analysis. Learn how to identify and remove duplicate rows in your dataset using Pandas.
Data Transformation: Convert data types, standardize values, and handle outliers. Techniques like scaling, encoding categorical variables, and feature engineering play a crucial role.
Handling Text Data: Text data may require special preprocessing for natural language processing (NLP) tasks. Techniques include tokenization, stemming, and removing stopwords.
Data Imputation: When dealing with missing values, you can impute them using techniques like mean imputation, regression imputation, or advanced methods like K-nearest neighbors imputation.
Data Aggregation and Grouping: For summarizing or aggregating data, you can group it by specific attributes and apply functions for creating new features.
Documentation: Maintain clear documentation of the steps taken during data cleaning and preprocessing to ensure transparency and reproducibility.
In this article series, we will dive deeper into each of these topics, providing code examples and best practices for effective data cleaning and preprocessing using Python. Understanding these fundamental data preparation steps is crucial for any data science project and lays the foundation for meaningful analysis and modeling.
Data Visualization with Matplotlib and Seaborn
Data visualization is a powerful tool in the data science and analytics toolkit. It allows you to communicate insights, patterns, and trends in your data more effectively. In the Python data science ecosystem, Matplotlib and Seaborn are two of the most popular libraries for creating a wide range of data visualizations. In this article, we'll explore how to use Matplotlib and Seaborn to visualize data in Python.
Introduction to Matplotlib:Start by introducing Matplotlib, a versatile and customizable plotting library. Cover the basics of creating various types of plots, such as line plots, bar charts, scatter plots, and histograms.
Customizing Matplotlib Plots:Explain how to customize plots by adjusting colors, labels, titles, and axis properties. Dive into Matplotlib's object-oriented approach for fine-grained control.
Multiple Subplots and Figures:Explore how to create multiple subplots within a single figure, which is particularly useful for visualizing multiple aspects of your data.
Introduction to Seaborn:Introduce Seaborn, a high-level interface for creating informative and visually appealing statistical graphics. Explain its advantages over Matplotlib.
Seaborn for Statistical Plots:Explore Seaborn's capabilities for creating statistical plots, such as box plots, violin plots, and pair plots, which provide insights into data distributions and relationships.
Seaborn's Categorical Plots:Cover Seaborn's categorical plotting functions, like bar plots, count plots, and point plots, which are useful for visualizing categorical data.
Seaborn for Regression and Relationships:Show how Seaborn simplifies the creation of regression plots and scatter plots with built-in trend lines.
Throughout this article series, we will provide code examples and best practices for creating various types of data visualizations, from basic charts to complex statistical plots. By the end, you'll have the skills to effectively communicate data insights using Matplotlib and Seaborn in your Python data science projects.
Exploratory Data Analysis (EDA) with Python
Exploratory Data Analysis (EDA) is a critical step in the data science process that involves examining and understanding the characteristics of your dataset before diving into more advanced modeling or analysis. EDA helps you discover patterns, relationships, and potential outliers in your data. In this article, we'll explore how to perform EDA using Python, making use of libraries such as Pandas, Matplotlib, Seaborn, and Plotly.
Introduction to EDA:Explain the importance of EDA in the data science workflow and how it can guide subsequent analysis.
Data Visualization for Initial Insights:Use Matplotlib and Seaborn to create basic visualizations like histograms, box plots, and scatter plots to gain initial insights into the data's distributions and relationships.
Handling Missing Data:Explore strategies for dealing with missing data, such as imputation or removal, and assess the impact of missing values on your analysis.
Exploring Categorical Data:Examine techniques for visualizing and analyzing categorical variables, including bar plots and frequency tables.
Time Series Data EDA: - For time series data, explore techniques specific to EDA, including time series decomposition and autocorrelation analysis.
Advanced EDA Techniques: - Cover more advanced techniques like Principal Component Analysis (PCA) for dimensionality reduction and t-SNE for visualizing high-dimensional data.
Interactive EDA: - Introduce interactive EDA tools like Plotly, which allow for dynamic exploration and visualization of data.
EDA in Real-World Projects: - Showcase case studies of EDA applied to real-world datasets, such as analyzing retail sales data or exploring trends in health and demographic data.
Throughout this article series, you'll gain a comprehensive understanding of EDA techniques, from basic data summarization to advanced visualization methods. EDA is a crucial step in the data science process, as it lays the foundation for making informed decisions about data preprocessing, feature engineering, and model selection.
Statistical Analysis with Python
Statistical analysis plays a fundamental role in data science, allowing you to draw meaningful insights, make data-driven decisions, and test hypotheses. Python offers a rich ecosystem of libraries for performing statistical analysis. In this article, we'll delve into the key concepts and techniques for statistical analysis using Python, covering both descriptive and inferential statistics.
Introduction to Statistical Analysis:Explain the importance of statistical analysis in data science and its various applications.
Descriptive Statistics:Explore how to calculate and interpret basic descriptive statistics such as mean, median, variance, and standard deviation using Python's libraries like NumPy.
Confidence Intervals:Explain how to calculate and interpret confidence intervals for parameter estimation using Python.
Statistical Analysis in Real-World Projects: - Showcase case studies where statistical analysis is applied to real-world datasets, such as A/B testing, quality control, and social science research.
Data Ethics and Misinterpretation: - Discuss the importance of ethical considerations in statistical analysis, as well as common pitfalls and misinterpretations.
Interactive Data Exploration: - Introduce interactive tools like Jupyter notebooks and libraries like Plotly for dynamic data exploration and visualization in statistical analysis.
Throughout this article series, you'll gain a strong understanding of statistical analysis concepts and how to apply them using Python. Whether you're dealing with basic descriptive statistics or more advanced inferential statistics, Python's libraries like NumPy, SciPy, statsmodels, and others make the process efficient and accessible for data scientists and analysts.
Machine Learning with Scikit-Learn
Machine learning is a subfield of artificial intelligence that empowers computers to learn from data and make predictions or decisions. Scikit-Learn (or sklearn) is a powerful machine learning library for Python that provides a wide range of tools for building and deploying machine learning models. In this article series, we will explore the key concepts and techniques for machine learning using Scikit-Learn.
Introduction to Machine Learning:Provide an overview of machine learning, its applications, and the different types of machine learning algorithms (supervised, unsupervised, reinforcement learning).
Setting Up Scikit-Learn:Guide readers on how to install Scikit-Learn, set up a Python environment, and import the necessary libraries.
Feature Engineering:Explore the importance of feature engineering in machine learning and demonstrate how to prepare data for modeling using Scikit-Learn's preprocessing tools.
Ensembles and Random Forests:Dive into ensemble methods, focusing on the Random Forest algorithm and its implementation in Scikit-Learn.
Support Vector Machines (SVM):Explain the theory and practical usage of Support Vector Machines for classification problems using Scikit-Learn.
Natural Language Processing (NLP) with Scikit-Learn: - Explore how Scikit-Learn can be used for text analysis and NLP tasks, such as sentiment analysis and text classification.
Throughout this article series, you'll gain a strong foundation in machine learning principles and practical experience in implementing machine learning models using Scikit-Learn. Whether you're a beginner looking to get started or an experienced data scientist, Scikit-Learn offers a user-friendly and powerful toolset for building and deploying machine learning solutions.
Deep Learning with Python and TensorFlow/Keras
Deep learning is a subfield of machine learning that focuses on neural networks with multiple layers, allowing computers to learn and make decisions in a manner similar to the human brain. TensorFlow and Keras are two of the most popular libraries for deep learning in Python. In this article series, we will explore the fundamentals of deep learning and how to implement deep neural networks using TensorFlow and Keras.
Introduction to Deep Learning:Provide an overview of deep learning, its significance, and its applications in various domains, including computer vision, natural language processing, and reinforcement learning.
Setting Up TensorFlow and Keras:Guide readers on how to install TensorFlow and Keras, set up a Python environment, and import the necessary libraries.
Building Neural Networks with Keras:Introduce the Keras library for building deep neural networks. Cover the basics of feedforward neural networks, activation functions, and loss functions.
Convolutional Neural Networks (CNNs):Explore CNNs, a class of neural networks specialized for image analysis and recognition. Explain how to build and train CNNs for image classification using Keras.
Transfer Learning and Pretrained Models:Introduce transfer learning and how to leverage pretrained deep learning models to solve tasks, such as image classification or text sentiment analysis.
Natural Language Processing (NLP) with Deep Learning:Explore the use of deep learning in NLP tasks, including text classification, sentiment analysis, and sequence-to-sequence tasks.
Generative Adversarial Networks (GANs):Explain GANs, a deep learning architecture for generating new data samples, and demonstrate their use in creating realistic images.
By the end of this article series, you will have a strong foundation in deep learning concepts and practical experience in building deep neural networks using TensorFlow and Keras. Deep learning has revolutionized many fields, and with the right knowledge and tools, you can leverage its power to solve a wide range of complex problems.
Time Series Analysis with Python
Time series data is a sequence of data points collected or recorded at regular time intervals. Time series analysis is essential for understanding temporal trends, making forecasts, and uncovering patterns in time-dependent data. In this article series, we will explore the concepts and techniques for time series analysis using Python.
Introduction to Time Series Data:Provide an overview of time series data, its characteristics, and real-world applications in finance, economics, and more.
Time Series Data Preprocessing:Discuss the importance of data cleaning, handling missing values, and resampling time series data to make it suitable for analysis.
Exploratory Data Analysis for Time Series:Cover techniques for visualizing and understanding time series data, including time plots, seasonality, and trend analysis.
Time Series Decomposition:Explain how to decompose a time series into its components, such as trend, seasonality, and residual, using Python libraries like Statsmodels.
Forecasting Methods:Introduce various time series forecasting methods, including moving averages, exponential smoothing, and autoregressive integrated moving average (ARIMA) models.
Long Short-Term Memory (LSTM) Networks for Time Series: - Dive into deep learning approaches for time series forecasting using LSTM networks and demonstrate their implementation with libraries like TensorFlow/Keras.
Real-World Time Series Projects: - Showcase case studies of time series analysis and forecasting applied to real-world data, such as stock price prediction, energy demand forecasting, and weather forecasting.
By the end of this article series, you'll have a solid understanding of time series analysis techniques, from basic data preprocessing and visualization to advanced forecasting methods and deep learning models. Time series analysis is a valuable skill for making predictions and informed decisions in various domains, and Python provides a powerful environment for performing these analyses.
Feature Engineering in Data Science
Feature engineering is the process of selecting, transforming, and creating relevant features (variables) from raw data to improve the performance of machine learning models. It plays a crucial role in data science, as the quality of features significantly impacts the model's ability to extract meaningful patterns from data. In this article series, we'll explore the fundamental concepts and techniques for feature engineering in data science.
Introduction to Feature Engineering:Provide an overview of what feature engineering is, why it's essential, and its impact on the performance of machine learning models.
Feature Selection Techniques:Discuss methods for choosing the most important features, including filtering, wrapper methods, and embedded methods. Explain how to implement these techniques using Python libraries like Scikit-Learn.
Handling Missing Data:Cover strategies for dealing with missing values in features, such as imputation, removal, and the use of techniques like K-nearest neighbors imputation.
Encoding Categorical Variables:Explain how to convert categorical variables into a numerical format suitable for machine learning models. Discuss one-hot encoding, label encoding, and target encoding.
Feature Scaling and Normalization:Explore the importance of scaling features to a common range, and discuss techniques like Min-Max scaling and Z-score standardization.
Feature Transformation:Introduce techniques like logarithm transformation, square root transformation, and Box-Cox transformation for improving the distribution of features.
Image Data Feature Engineering: - Discuss methods for extracting features from images, including deep learning techniques like convolutional neural networks (CNNs) for feature extraction.
Feature Engineering Best Practices: - Share tips, best practices, and considerations for effective feature engineering, including the importance of domain knowledge and the iterative nature of the process.
Feature engineering is a creative and iterative process that involves domain knowledge, data exploration, and experimentation. By understanding the techniques and best practices covered in this article series, you'll be equipped to extract the most relevant information from your data and improve the performance of your machine learning models.
Data Science Best Practices in Python
Data science is a multidisciplinary field that involves collecting, cleaning, analyzing, and interpreting data to extract meaningful insights and make data-driven decisions. Python has become a dominant language in data science due to its rich ecosystem of libraries and tools. In this article series, we'll explore best practices and guidelines for conducting data science projects in Python.
Project Planning and Problem Definition:Discuss the importance of defining clear project objectives, problem statements, and success criteria before diving into data analysis. Emphasize the need for domain knowledge and collaboration with stakeholders.
Data Collection and Exploration:Explain the process of data acquisition, including web scraping, API access, and data ingestion. Discuss the importance of exploring data to understand its structure and quality, including identifying missing values and outliers.
Data Cleaning and Preprocessing:Cover techniques for handling missing data, removing duplicates, and transforming data into a suitable format. Discuss feature engineering and encoding categorical variables.
Data Visualization and EDA:Highlight the importance of exploratory data analysis (EDA) and data visualization to gain insights and identify patterns in the data. Discuss best practices for creating effective visualizations.
Model Selection and Evaluation:Explain the process of selecting appropriate machine learning models, splitting data into training and testing sets, and evaluating models using relevant metrics. Discuss cross-validation and hyperparameter tuning.
Model Deployment and Production:Introduce methods for deploying machine learning models to production, such as creating RESTful APIs, containerization, and cloud deployment. Discuss considerations for model maintenance and monitoring.
By following these best practices in Python data science projects, you'll be better equipped to navigate the complexities of real-world data analysis and modeling. Data science is a dynamic field that requires a combination of technical skills, domain knowledge, and adherence to sound methodologies for delivering valuable insights and solutions.
Real-World Data Science Projects with Python
Applying data science techniques to real-world projects is essential for gaining practical experience and solving complex problems. In this article series, we'll explore a variety of real-world data science projects and how to approach them using Python. These projects cover a range of domains and scenarios to showcase the versatility and power of data science in solving actual problems.
Predictive Maintenance for Equipment:Explore how to use historical equipment data to predict maintenance needs and prevent costly downtime. Implement machine learning models for predicting equipment failures using Python libraries.
Sentiment Analysis for Social Media Data:Develop a sentiment analysis project to gauge public sentiment on social media. Utilize Python's NLP libraries and machine learning techniques to classify text data as positive, negative, or neutral.
Credit Scoring and Risk Assessment:Build a credit scoring model to assess the creditworthiness of individuals or businesses. Employ Python to analyze financial data and create a predictive model for risk assessment.
Fraud Detection:Develop a fraud detection system using machine learning and anomaly detection to identify suspicious transactions and activities in financial or online systems.
Energy Consumption Forecasting: - Develop a project that forecasts energy consumption, which can be useful for energy management and resource allocation. Utilize time series analysis and predictive modeling with Python libraries.
Demand Forecasting for Retail: - Create a demand forecasting model for retail businesses to optimize inventory management. Use Python for data preprocessing, time series analysis, and machine learning.
Text Summarization and Text Generation: - Explore the generation of automatic summaries for articles and reports or even build a text generation model like a chatbot or creative writing AI using Python's NLP and deep learning capabilities.
These real-world data science projects in Python are designed to provide practical experience and demonstrate the applicability of data science techniques in diverse domains. By working on these projects, you'll gain valuable insights into data analysis, model development, and problem-solving, and you'll be better prepared to tackle real-world data science challenges.
Conclusion
In conclusion, Python is a versatile and powerful programming language for data science, offering a vast ecosystem of libraries and tools that make it a go-to choice for data analysis, machine learning, and more. The article series we've discussed covers a wide range of topics and projects in the field of data science, from foundational concepts like data cleaning and preprocessing to advanced areas like deep learning, time series analysis, and real-world projects.
As you dive into the world of data science in Python, remember that continuous learning and practice are key to mastering the field. Keep exploring, experimenting, and working on projects to hone your skills and stay up-to-date with the latest developments in the data science community.
Whether you're new to data science or looking to deepen your expertise, the knowledge and skills you gain in Python data science will enable you to extract valuable insights, make data-driven decisions, and contribute to solving real-world problems in various domains. Good luck on your data science journey!
The Role of a Certified Scrum Product Owner (CSPO):Responsibilities and Challenges
In the dynamic landscape of modern project management and Agile development, the role of a Certified Scrum Product Owner (CSPO) has emerged as a linchpin for success. In a world where adaptability, responsiveness, and delivering value are paramount, the CSPO is at the helm, steering the ship towards project excellence.
In this blog post, we'll embark on a journey through the multifaceted role of a Certified Scrum Product Owner, uncovering the essential responsibilities they undertake and the challenges they must overcome. Whether you're a CSPO looking to refine your skills or someone curious about this pivotal role in Agile development, this exploration will provide you with valuable insights.
So, whether you're considering a career as a CSPO, working alongside one, or simply keen to expand your knowledge of Agile practices, join us as we navigate the exciting world of CSPOs and uncover the responsibilities and challenges that define their role.
Table of contents
-
Understanding the CSPO Role
-
Effective Backlog Management
-
Collaborating with Stakeholders
-
Balancing Priorities
-
The Decision-Making Dilemma
-
User-Centric Product Development
-
Adapting to Change
-
Managing Expectations and Feedback
-
Overcoming Challenges and Obstacles
-
Continuous Improvement for CSPOs
-
Conclusion
Understanding the CSPO Role
The Certified Scrum Product Owner (CSPO) plays a pivotal role in the Scrum framework, acting as the linchpin between development teams and stakeholders. To truly appreciate the impact of a CSPO, it's essential to understand their multifaceted role. Here, we delve into the key aspects that define the CSPO's responsibilities:
Product Visionary: The CSPO is the visionary of the product, tasked with developing a clear understanding of what needs to be built and why. They must communicate this vision to the team and stakeholders.
Prioritization Guru: One of the CSPO's most critical responsibilities is to prioritize the items in the product backlog. This involves understanding the market, customer needs, and business goals to ensure the most valuable features are developed first.
Stakeholder Liaison: The CSPO acts as the bridge between the development team and various stakeholders, including customers, business leaders, and end-users. They must effectively gather and communicate requirements while managing expectations.
Team Support: CSPOs are there to support the development team in understanding the product vision, clarifying requirements, and answering questions, ensuring the team can work efficiently.
Continuous Improvement: A great CSPO is also dedicated to continuous improvement. They should regularly review their own performance and seek ways to enhance the product development process.
Understanding the CSPO role goes beyond a job description; it requires a blend of leadership, communication, and problem-solving skills. It's about championing the product's success by aligning it with business objectives and delivering value to customers.
In the following sections, we'll delve deeper into the challenges and strategies that CSPOs encounter in these various facets of their role.
Effective Backlog Management
The product backlog is the beating heart of Agile product development, and the Certified Scrum Product Owner (CSPO) is its custodian. Backlog management is a vital aspect of the CSPO's role, encompassing the organization, prioritization, and continuous refinement of tasks and requirements. Here, we will break down the components of effective backlog management:
Organization:Creating a Clear Structure: The CSPO is responsible for maintaining a well-organized backlog. This involves creating user stories, epics, and tasks in a structured manner, making it easier for the development team to understand and prioritize work.
Managing Dependencies: Identifying and managing dependencies between backlog items to ensure efficient development and delivery.
Prioritization:Value-Driven Prioritization: The CSPO must prioritize backlog items based on their value to the customer, business, and project objectives.
Alignment with Business Goals: Ensuring that the prioritization aligns with the broader business goals and strategies.
Continuous Refinement:Regular Grooming: Holding backlog grooming sessions to review, update, and refine items. This process helps in maintaining the relevance of items and keeping the backlog manageable.
Responding to Feedback: Being responsive to feedback from stakeholders and the development team, which might lead to changes in the backlog.
Communication:Effective Communication: The CSPO should be able to effectively communicate the priorities and requirements of the backlog to the development team and stakeholders.
Transparency: Maintaining transparency in the backlog to ensure everyone involved understands its status and contents.
Adaptability:Embracing Change: Acknowledging that changes in market conditions, customer feedback, and other factors may require adapting the backlog. The CSPO should be ready to pivot as needed.
Backlog Size:Right-Sizing the Backlog: Striking a balance between having a backlog that is too large (overwhelming) and too small (insufficient to support the team's work).
Effective backlog management is a dynamic process. It involves a constant reassessment of priorities, responsiveness to change, and a commitment to delivering the most valuable features to the customer. The CSPO plays a critical role in ensuring that the backlog remains a powerful tool for Agile development, guiding the team towards success.
Collaborating with Stakeholders
In the realm of Agile product development, collaboration is not just a buzzword; it's a fundamental principle. For a Certified Scrum Product Owner (CSPO), collaboration with stakeholders is a core responsibility. This involves a delicate dance of communication, feedback, and alignment. Let's explore the nuances of collaborating effectively with stakeholders:
Identifying Stakeholders:Cast a Wide Net: The CSPO's first step is identifying all potential stakeholders. This may include customers, business executives, end-users, and anyone who has a vested interest in the product's success.
Engaging in Continuous Communication:Open Channels: Establish and maintain open channels of communication with stakeholders. Regular meetings, emails, and project management tools are vital for keeping everyone informed.
Active Listening: Paying close attention to the needs and concerns of stakeholders. Encourage and embrace their feedback and input.
Managing Expectations:Transparency: Being transparent about what can and cannot be delivered in a given time frame. Setting realistic expectations is crucial to avoiding disappointment.
Alignment with Goals: Ensuring that stakeholder expectations are aligned with project goals and objectives.
Gathering and Prioritizing Feedback:Feedback Loops: Establishing structured feedback loops to collect input from stakeholders. This feedback should be considered when prioritizing and refining the product backlog.
Feedback Processing: Effective processing and incorporation of feedback into the product development process.
Conflict Resolution:Handling Conflicts: Dealing with conflicting interests or opinions among stakeholders. The CSPO must be adept at finding compromises that benefit the project.
Regular Updates:Progress Reporting: Keeping stakeholders informed about the project's progress, roadblocks, and successes. This keeps them engaged and aligned with the team's efforts.
Collaborating effectively with stakeholders is a complex task that involves not only effective communication but also the ability to navigate potentially conflicting interests. The CSPO's role is not just to manage relationships but to ensure that stakeholder feedback is translated into value-added product features and that everyone involved understands the product's direction.
Balancing Priorities
As a Certified Scrum Product Owner (CSPO), one of the most significant challenges is striking the right balance between multiple, often competing, priorities. The CSPO must be a master of prioritization, ensuring that the development team is working on the most valuable tasks. Let's explore the complexities of balancing priorities:
Value-Based Prioritization:Customer Value: Prioritizing items that bring the most value to the end customer or user. This ensures that the product remains competitive and addresses user needs effectively.
Business Value: Identifying and prioritizing tasks that align with the broader business objectives. These might include revenue generation, cost reduction, or strategic goals.
Alignment with Strategy:Strategic Objectives: Ensuring that the prioritization of tasks is in line with the organization's strategic goals. A CSPO must be aware of the big picture and ensure that daily tasks contribute to the long-term vision.
Managing Changing Requirements:Embracing Change: Being adaptable and open to changing priorities. Market conditions, customer feedback, and new opportunities might necessitate changes in what gets worked on first.
Stakeholder Expectations:Managing Stakeholder Demands: Dealing with multiple stakeholders with their own ideas about what should be prioritized. It's essential to balance these often conflicting demands.
Capacity Planning:Understanding Team Capacity: Having a clear understanding of the development team's capacity and ensuring that the workload aligns with this capacity. Overloading the team can lead to burnout and decreased quality.
Impact Assessment:Data-Driven Decisions: Making decisions based on data and analysis. Assessing the potential impact of different tasks and using this analysis to guide prioritization.
Balancing priorities is a delicate act of constant reassessment and adaptation. The CSPO must be flexible and responsive to change while maintaining a clear understanding of the overarching objectives. This skill is what ensures that the most valuable work is continually delivered and that the product remains competitive and aligned with the market.
The Decision-Making Dilemma
The role of a Certified Scrum Product Owner (CSPO) is fraught with decisions. Each decision has the potential to shape the course of the project and the product's success. However, decision-making in the Agile landscape is far from straightforward. Let's explore the CSPO's decision-making dilemmas:
Feature Selection:What to Build First: Deciding which features to prioritize for development, considering customer needs, market demands, and business goals.
What to Leave Out: Equally important is deciding what not to build. Not every idea or feature can be accommodated, and decisions must be made about what doesn't make the cut.
Scope Changes:Evaluating Change Requests: When stakeholders request scope changes or additions, the CSPO must evaluate the impact on the project's timeline, budget, and goals.
Balancing Flexibility and Stability: Deciding how much flexibility can be accommodated within the project without compromising stability and predictability.
Trade-Offs:Balancing Quality and Speed: Decisions often revolve around the trade-off between delivering quickly and maintaining high product quality.
Resource Allocation: Deciding how to allocate resources, including time and team capacity, to different tasks.
User Feedback and Prioritization:Incorporating User Feedback: Deciding how to prioritize and implement user feedback while maintaining alignment with the project's objectives.
Managing Expectations: Communicating decisions regarding the implementation of feedback to stakeholders and end-users.
Resource Constraints:Budget and Time Decisions: Deciding how to allocate budget and time resources, particularly when faced with constraints.
Long-Term Vision:Balancing Short-Term and Long-Term Goals: Making decisions that align with the long-term vision of the product, even when short-term demands might pull in a different direction.
The CSPO's decision-making is a constant juggling act that requires a deep understanding of the project's goals and the ability to adapt to changing circumstances. Decisions must be made in a manner that maximizes value while minimizing risks and conflicts.
User-Centric Product Development
In the Agile world, where the focus is on delivering value and responding to change, user-centricity is at the heart of successful product development. As a Certified Scrum Product Owner (CSPO), understanding and advocating for the needs and desires of the end-users is paramount. Let's dive into the principles of user-centric product development:
User Empathy:Putting Yourself in the User's Shoes: The CSPO must strive to understand the user's perspective, their goals, and the problems they need the product to solve.
Listening Actively: Engaging in user feedback sessions and actively listening to what users have to say about the product.
User Story Creation:Creating User Stories: Formulating user stories that represent the user's requirements and needs. These stories become the basis for development tasks.
Prioritizing User Stories: Prioritizing user stories based on user value and business objectives.
Usability and User Experience:Usability Testing: Ensuring the product is user-friendly and easy to navigate. Usability testing helps identify and address user interface and experience issues.
User-Centered Design: Integrating user-centered design principles into the development process to create intuitive and user-friendly interfaces.
Feedback Integration:Feedback Loops: Establishing feedback loops that allow for the continuous integration of user feedback into the product development cycle.
Iterative Improvement: Recognizing that user feedback often leads to iterative product improvements and being open to these changes.
Aligning with User Goals:Connecting with User Objectives: Making sure the product aligns with the users' goals and is instrumental in solving their problems.
Continuous Value Delivery: Ensuring that each development iteration delivers tangible value to the user.
User Advocacy:Advocating for the User: As the user's representative, the CSPO must advocate for their needs and ensure that these needs are met in the product's development.
Balancing User Interests: Balancing user needs with business goals and technical constraints.
User-centric product development ensures that the product remains relevant and valuable to its intended audience. It's about making the user's life easier, more efficient, and more enjoyable. As a CSPO, embracing these principles is pivotal to your role.
Adapting to Change
In the fast-paced world of Agile product development, change is the only constant. As a Certified Scrum Product Owner (CSPO), your ability to adapt to change is vital for the success of your projects. Let's delve into the challenges and strategies for effectively adapting to change:
Embracing Flexibility:Change as a Norm: Recognizing that change is an inherent part of Agile development. Being open to and prepared for changes in requirements, priorities, and even project goals.
Agile Mindset: Adopting an Agile mindset that values adaptability and welcomes change as a means of improvement.
Iterative Development:Sprints and Iterations: Leveraging the Agile framework's iterative nature to accommodate changes within specific timeframes, such as sprints.
Feedback Integration: Using the end of each iteration to incorporate feedback and adjust the product's direction accordingly.
Managing Scope Changes:Change Requests: Handling scope changes and additions with a structured change management process. This includes assessing their impact and aligning them with the project's objectives.
Balancing Scope and Schedule: Ensuring that scope changes don't jeopardize project timelines.
Agile Tools and Techniques:Backlog Refinement: Regularly refining the product backlog to adjust to changing requirements and priorities.
Burndown Charts and Velocity Tracking: Using tools like burndown charts and velocity tracking to monitor progress and adapt plans as needed.
Continual Improvement:Retrospectives: Conducting regular retrospectives to identify areas for improvement in the development process, fostering a culture of learning and adaptability.
Adapting Based on Feedback: Using feedback from retrospectives and other sources to make process changes.
Adapting to change in Agile development is not just a matter of reacting; it's a proactive approach to ensuring that the product remains aligned with customer needs and market demands. It's about using change as an opportunity for improvement rather than a disruptive force.
Managing Expectations and Feedback
As a Certified Scrum Product Owner (CSPO), your role extends beyond managing the product backlog. You are also responsible for effectively managing stakeholder expectations and feedback, a task that requires finesse and communication skills. Let's explore the intricacies of this responsibility:
Clear Communication:
Open Dialogue: Establishing open and transparent lines of communication with stakeholders. This creates an environment where expectations can be effectively managed.
Setting Realistic Expectations: Communicating what can and cannot be achieved within specific timeframes and resources.
Regular Updates:
Progress Reporting: Providing stakeholders with regular updates on the project's progress. This keeps them informed and engaged in the development process.
Highlighting Achievements: Sharing successes and milestones reached, reinforcing the value being delivered.
Gathering Feedback:
Feedback Loops: Setting up structured feedback loops that allow stakeholders to provide input and voice their concerns.
Actively Listening: Actively listening to feedback, even if it is critical, and demonstrating that it is being taken seriously.
Handling Conflicting Feedback:
Mediation: Resolving conflicts or contradictions within feedback from different stakeholders. The CSPO must make balanced decisions that serve the project's goals.
Responding to Change:
Change Management: Effectively communicating and managing changes in project direction, scope, or objectives to stakeholders.
Risk Communication: Sharing information about potential project risks or challenges and discussing strategies for mitigation.
Documentation:
Feedback Records: Maintaining records of feedback and its resolution to ensure that it is tracked and addressed.
Expectations Documentation: Documenting agreed-upon expectations, priorities, and objectives for reference.
Managing expectations and feedback requires a combination of excellent communication, empathy, and a deep understanding of the project's objectives. The CSPO's role in this aspect is to bridge the gap between stakeholders, development teams, and end-users, ensuring that everyone is on the same page and that feedback is integrated for continuous improvement.
Overcoming Challenges and Obstacles
In the role of a Certified Scrum Product Owner (CSPO), you're likely to encounter a range of challenges and obstacles. However, these challenges are not roadblocks; they're opportunities for growth and improvement. Let's explore some common challenges and strategies for overcoming them:
Conflicting Priorities:
Challenge: Balancing the priorities of different stakeholders can be challenging. Conflicting interests can lead to ambiguity in decision-making.
Strategy: Engage stakeholders in discussions to align their priorities with the project's objectives. Use data and clear communication to make informed decisions.
Changing Requirements:
Challenge: Requirements can change frequently, making it challenging to maintain a stable product backlog and plan.
Strategy: Embrace change as an opportunity for improvement. Implement change management processes to assess and integrate new requirements effectively.
Unrealistic Expectations:
Challenge: Managing stakeholder expectations can be difficult when they expect immediate results or don't fully grasp Agile principles.
Strategy: Educate stakeholders about Agile principles, setting realistic expectations, and providing regular updates to manage their understanding of the project's progress.
Resource Constraints:
Challenge: Limited resources, such as time, budget, or team capacity, can hinder your ability to meet stakeholder demands.
Strategy: Prioritize tasks based on their impact and feasibility within resource constraints. Communicate openly about resource limitations and adjust priorities accordingly.
Resistance to Change:
Challenge: Team members or stakeholders may resist adopting Agile practices or new ways of working.
Strategy: Lead by example, communicate the benefits of Agile, and involve team members in decision-making. Foster a culture of continuous improvement to encourage adaptation.
Incomplete Feedback:
Challenge: Stakeholder feedback may be vague or incomplete, making it challenging to act upon.
Strategy: Engage stakeholders in conversations to elicit more detailed feedback. Use techniques like "Five Whys" to dig deeper into their needs and concerns.
Managing Expectations:
Challenge: Managing stakeholder expectations while maintaining a user-centric approach can be challenging when interests diverge.
Strategy: Balance the needs of users with business goals and technical constraints. Clearly communicate the rationale behind decisions to manage expectations effectively.
Overcoming challenges and obstacles is a fundamental aspect of the CSPO role. It requires a combination of effective communication, adaptability, and strategic decision-making. By addressing these challenges with the right mindset and techniques, you can facilitate a more successful and resilient Agile product development process.
Continuous Improvement for CSPOs
In the dynamic world of Agile product development, the journey of a Certified Scrum Product Owner (CSPO) is one of continual growth and refinement. Continuous improvement is not just a practice; it's a mindset. Let's explore the principles and strategies for ongoing improvement as a CSPO:
Self-Assessment:Reflect on Your Role: Regularly assess your performance and the impact you're making as a CSPO. This self-assessment helps you identify areas for improvement.
Professional Development:Stay Informed: Keep abreast of the latest trends, tools, and best practices in Agile and product management. Attend training, workshops, and conferences to expand your knowledge.
Certification: Consider advanced certifications or training courses to enhance your skills and knowledge.
Feedback Integration:Seek Feedback: Actively seek feedback from team members, stakeholders, and Scrum Masters. Constructive criticism can be a valuable source of insights.
Feedback Processing: Process feedback by identifying actionable areas for improvement and taking steps to address them.
Scrum Master Collaboration:Work Closely with Scrum Masters: Collaborate with Scrum Masters to learn from their experiences and gain a better understanding of the Scrum framework.
Continuous Learning: Be open to sharing your experiences and insights, fostering mutual growth.
Experimentation:Embrace Experimentation: Be open to trying new tools, techniques, or approaches in your role. Experimentation can lead to innovative improvements.
Learn from Failures: Embrace failures as learning opportunities, understanding that not every experiment will yield the desired results.
Collaborative Learning:Learning from Peers: Engage with other CSPOs and product owners to exchange insights, challenges, and best practices.
Cross-Functional Collaboration: Collaborate with developers, designers, and other roles to expand your understanding of the product development process.
Goal Setting:Set Goals for Improvement: Establish clear goals for your own improvement and growth as a CSPO. Regularly review and adjust these goals as you progress.
Continuous improvement as a CSPO is about embracing a growth mindset, actively seeking ways to enhance your skills, and consistently applying new knowledge and insights. It's an ongoing journey of becoming a more effective, adaptable, and valuable product owner within the Agile landscape.
Conclusion
Becoming a Certified Scrum Product Owner (CSPO) is not just about a title; it's a journey of embracing responsibilities, overcoming challenges, and continuously improving. In this comprehensive exploration of the role of a CSPO, we've delved into the core responsibilities and the myriad challenges you might encounter in this dynamic position.
Effective backlog management, stakeholder collaboration, balancing priorities, and decision-making are just some of the intricate facets of your role. Managing expectations and feedback, adapting to change, and overcoming challenges are continuous endeavors that require a blend of skills, including effective communication, empathy, and adaptability.
The role of a CSPO is not for the faint of heart, but for those willing to embrace the challenges and opportunities it presents, it can be a rewarding and fulfilling journey. Remember, your dedication to this role contributes not only to the success of your projects but also to the broader Agile community.
In closing, the role of a CSPO is a journey of perpetual growth and a commitment to delivering value to customers while embracing the principles of Agile. Whether you're an aspiring CSPO or an experienced one, this role offers an ongoing opportunity to make a meaningful impact in the world of product development.
Thank you for accompanying us on this exploration of the CSPO role. May your journey as a Certified Scrum Product Owner be filled with continuous improvement, successful projects, and valuable product deliveries.
Read More
In the dynamic landscape of modern project management and Agile development, the role of a Certified Scrum Product Owner (CSPO) has emerged as a linchpin for success. In a world where adaptability, responsiveness, and delivering value are paramount, the CSPO is at the helm, steering the ship towards project excellence.
In this blog post, we'll embark on a journey through the multifaceted role of a Certified Scrum Product Owner, uncovering the essential responsibilities they undertake and the challenges they must overcome. Whether you're a CSPO looking to refine your skills or someone curious about this pivotal role in Agile development, this exploration will provide you with valuable insights.
So, whether you're considering a career as a CSPO, working alongside one, or simply keen to expand your knowledge of Agile practices, join us as we navigate the exciting world of CSPOs and uncover the responsibilities and challenges that define their role.
Table of contents
-
Understanding the CSPO Role
-
Effective Backlog Management
-
Collaborating with Stakeholders
-
Balancing Priorities
-
The Decision-Making Dilemma
-
User-Centric Product Development
-
Adapting to Change
-
Managing Expectations and Feedback
-
Overcoming Challenges and Obstacles
-
Continuous Improvement for CSPOs
-
Conclusion
Understanding the CSPO Role
The Certified Scrum Product Owner (CSPO) plays a pivotal role in the Scrum framework, acting as the linchpin between development teams and stakeholders. To truly appreciate the impact of a CSPO, it's essential to understand their multifaceted role. Here, we delve into the key aspects that define the CSPO's responsibilities:
Product Visionary: The CSPO is the visionary of the product, tasked with developing a clear understanding of what needs to be built and why. They must communicate this vision to the team and stakeholders.
Prioritization Guru: One of the CSPO's most critical responsibilities is to prioritize the items in the product backlog. This involves understanding the market, customer needs, and business goals to ensure the most valuable features are developed first.
Stakeholder Liaison: The CSPO acts as the bridge between the development team and various stakeholders, including customers, business leaders, and end-users. They must effectively gather and communicate requirements while managing expectations.
Team Support: CSPOs are there to support the development team in understanding the product vision, clarifying requirements, and answering questions, ensuring the team can work efficiently.
Continuous Improvement: A great CSPO is also dedicated to continuous improvement. They should regularly review their own performance and seek ways to enhance the product development process.
Understanding the CSPO role goes beyond a job description; it requires a blend of leadership, communication, and problem-solving skills. It's about championing the product's success by aligning it with business objectives and delivering value to customers.
In the following sections, we'll delve deeper into the challenges and strategies that CSPOs encounter in these various facets of their role.
Effective Backlog Management
The product backlog is the beating heart of Agile product development, and the Certified Scrum Product Owner (CSPO) is its custodian. Backlog management is a vital aspect of the CSPO's role, encompassing the organization, prioritization, and continuous refinement of tasks and requirements. Here, we will break down the components of effective backlog management:
Organization:Creating a Clear Structure: The CSPO is responsible for maintaining a well-organized backlog. This involves creating user stories, epics, and tasks in a structured manner, making it easier for the development team to understand and prioritize work.
Managing Dependencies: Identifying and managing dependencies between backlog items to ensure efficient development and delivery.
Prioritization:Value-Driven Prioritization: The CSPO must prioritize backlog items based on their value to the customer, business, and project objectives.
Alignment with Business Goals: Ensuring that the prioritization aligns with the broader business goals and strategies.
Continuous Refinement:Regular Grooming: Holding backlog grooming sessions to review, update, and refine items. This process helps in maintaining the relevance of items and keeping the backlog manageable.
Responding to Feedback: Being responsive to feedback from stakeholders and the development team, which might lead to changes in the backlog.
Communication:Effective Communication: The CSPO should be able to effectively communicate the priorities and requirements of the backlog to the development team and stakeholders.
Transparency: Maintaining transparency in the backlog to ensure everyone involved understands its status and contents.
Adaptability:Embracing Change: Acknowledging that changes in market conditions, customer feedback, and other factors may require adapting the backlog. The CSPO should be ready to pivot as needed.
Backlog Size:Right-Sizing the Backlog: Striking a balance between having a backlog that is too large (overwhelming) and too small (insufficient to support the team's work).
Effective backlog management is a dynamic process. It involves a constant reassessment of priorities, responsiveness to change, and a commitment to delivering the most valuable features to the customer. The CSPO plays a critical role in ensuring that the backlog remains a powerful tool for Agile development, guiding the team towards success.
Collaborating with Stakeholders
In the realm of Agile product development, collaboration is not just a buzzword; it's a fundamental principle. For a Certified Scrum Product Owner (CSPO), collaboration with stakeholders is a core responsibility. This involves a delicate dance of communication, feedback, and alignment. Let's explore the nuances of collaborating effectively with stakeholders:
Identifying Stakeholders:Cast a Wide Net: The CSPO's first step is identifying all potential stakeholders. This may include customers, business executives, end-users, and anyone who has a vested interest in the product's success.
Engaging in Continuous Communication:Open Channels: Establish and maintain open channels of communication with stakeholders. Regular meetings, emails, and project management tools are vital for keeping everyone informed.
Active Listening: Paying close attention to the needs and concerns of stakeholders. Encourage and embrace their feedback and input.
Managing Expectations:Transparency: Being transparent about what can and cannot be delivered in a given time frame. Setting realistic expectations is crucial to avoiding disappointment.
Alignment with Goals: Ensuring that stakeholder expectations are aligned with project goals and objectives.
Gathering and Prioritizing Feedback:Feedback Loops: Establishing structured feedback loops to collect input from stakeholders. This feedback should be considered when prioritizing and refining the product backlog.
Feedback Processing: Effective processing and incorporation of feedback into the product development process.
Conflict Resolution:Handling Conflicts: Dealing with conflicting interests or opinions among stakeholders. The CSPO must be adept at finding compromises that benefit the project.
Regular Updates:Progress Reporting: Keeping stakeholders informed about the project's progress, roadblocks, and successes. This keeps them engaged and aligned with the team's efforts.
Collaborating effectively with stakeholders is a complex task that involves not only effective communication but also the ability to navigate potentially conflicting interests. The CSPO's role is not just to manage relationships but to ensure that stakeholder feedback is translated into value-added product features and that everyone involved understands the product's direction.
Balancing Priorities
As a Certified Scrum Product Owner (CSPO), one of the most significant challenges is striking the right balance between multiple, often competing, priorities. The CSPO must be a master of prioritization, ensuring that the development team is working on the most valuable tasks. Let's explore the complexities of balancing priorities:
Value-Based Prioritization:Customer Value: Prioritizing items that bring the most value to the end customer or user. This ensures that the product remains competitive and addresses user needs effectively.
Business Value: Identifying and prioritizing tasks that align with the broader business objectives. These might include revenue generation, cost reduction, or strategic goals.
Alignment with Strategy:Strategic Objectives: Ensuring that the prioritization of tasks is in line with the organization's strategic goals. A CSPO must be aware of the big picture and ensure that daily tasks contribute to the long-term vision.
Managing Changing Requirements:Embracing Change: Being adaptable and open to changing priorities. Market conditions, customer feedback, and new opportunities might necessitate changes in what gets worked on first.
Stakeholder Expectations:Managing Stakeholder Demands: Dealing with multiple stakeholders with their own ideas about what should be prioritized. It's essential to balance these often conflicting demands.
Capacity Planning:Understanding Team Capacity: Having a clear understanding of the development team's capacity and ensuring that the workload aligns with this capacity. Overloading the team can lead to burnout and decreased quality.
Impact Assessment:Data-Driven Decisions: Making decisions based on data and analysis. Assessing the potential impact of different tasks and using this analysis to guide prioritization.
Balancing priorities is a delicate act of constant reassessment and adaptation. The CSPO must be flexible and responsive to change while maintaining a clear understanding of the overarching objectives. This skill is what ensures that the most valuable work is continually delivered and that the product remains competitive and aligned with the market.
The Decision-Making Dilemma
The role of a Certified Scrum Product Owner (CSPO) is fraught with decisions. Each decision has the potential to shape the course of the project and the product's success. However, decision-making in the Agile landscape is far from straightforward. Let's explore the CSPO's decision-making dilemmas:
Feature Selection:What to Build First: Deciding which features to prioritize for development, considering customer needs, market demands, and business goals.
What to Leave Out: Equally important is deciding what not to build. Not every idea or feature can be accommodated, and decisions must be made about what doesn't make the cut.
Scope Changes:Evaluating Change Requests: When stakeholders request scope changes or additions, the CSPO must evaluate the impact on the project's timeline, budget, and goals.
Balancing Flexibility and Stability: Deciding how much flexibility can be accommodated within the project without compromising stability and predictability.
Trade-Offs:Balancing Quality and Speed: Decisions often revolve around the trade-off between delivering quickly and maintaining high product quality.
Resource Allocation: Deciding how to allocate resources, including time and team capacity, to different tasks.
User Feedback and Prioritization:Incorporating User Feedback: Deciding how to prioritize and implement user feedback while maintaining alignment with the project's objectives.
Managing Expectations: Communicating decisions regarding the implementation of feedback to stakeholders and end-users.
Resource Constraints:Budget and Time Decisions: Deciding how to allocate budget and time resources, particularly when faced with constraints.
Long-Term Vision:Balancing Short-Term and Long-Term Goals: Making decisions that align with the long-term vision of the product, even when short-term demands might pull in a different direction.
The CSPO's decision-making is a constant juggling act that requires a deep understanding of the project's goals and the ability to adapt to changing circumstances. Decisions must be made in a manner that maximizes value while minimizing risks and conflicts.
User-Centric Product Development
In the Agile world, where the focus is on delivering value and responding to change, user-centricity is at the heart of successful product development. As a Certified Scrum Product Owner (CSPO), understanding and advocating for the needs and desires of the end-users is paramount. Let's dive into the principles of user-centric product development:
User Empathy:Putting Yourself in the User's Shoes: The CSPO must strive to understand the user's perspective, their goals, and the problems they need the product to solve.
Listening Actively: Engaging in user feedback sessions and actively listening to what users have to say about the product.
User Story Creation:Creating User Stories: Formulating user stories that represent the user's requirements and needs. These stories become the basis for development tasks.
Prioritizing User Stories: Prioritizing user stories based on user value and business objectives.
Usability and User Experience:Usability Testing: Ensuring the product is user-friendly and easy to navigate. Usability testing helps identify and address user interface and experience issues.
User-Centered Design: Integrating user-centered design principles into the development process to create intuitive and user-friendly interfaces.
Feedback Integration:Feedback Loops: Establishing feedback loops that allow for the continuous integration of user feedback into the product development cycle.
Iterative Improvement: Recognizing that user feedback often leads to iterative product improvements and being open to these changes.
Aligning with User Goals:Connecting with User Objectives: Making sure the product aligns with the users' goals and is instrumental in solving their problems.
Continuous Value Delivery: Ensuring that each development iteration delivers tangible value to the user.
User Advocacy:Advocating for the User: As the user's representative, the CSPO must advocate for their needs and ensure that these needs are met in the product's development.
Balancing User Interests: Balancing user needs with business goals and technical constraints.
User-centric product development ensures that the product remains relevant and valuable to its intended audience. It's about making the user's life easier, more efficient, and more enjoyable. As a CSPO, embracing these principles is pivotal to your role.
Adapting to Change
In the fast-paced world of Agile product development, change is the only constant. As a Certified Scrum Product Owner (CSPO), your ability to adapt to change is vital for the success of your projects. Let's delve into the challenges and strategies for effectively adapting to change:
Embracing Flexibility:Change as a Norm: Recognizing that change is an inherent part of Agile development. Being open to and prepared for changes in requirements, priorities, and even project goals.
Agile Mindset: Adopting an Agile mindset that values adaptability and welcomes change as a means of improvement.
Iterative Development:Sprints and Iterations: Leveraging the Agile framework's iterative nature to accommodate changes within specific timeframes, such as sprints.
Feedback Integration: Using the end of each iteration to incorporate feedback and adjust the product's direction accordingly.
Managing Scope Changes:Change Requests: Handling scope changes and additions with a structured change management process. This includes assessing their impact and aligning them with the project's objectives.
Balancing Scope and Schedule: Ensuring that scope changes don't jeopardize project timelines.
Agile Tools and Techniques:Backlog Refinement: Regularly refining the product backlog to adjust to changing requirements and priorities.
Burndown Charts and Velocity Tracking: Using tools like burndown charts and velocity tracking to monitor progress and adapt plans as needed.
Continual Improvement:Retrospectives: Conducting regular retrospectives to identify areas for improvement in the development process, fostering a culture of learning and adaptability.
Adapting Based on Feedback: Using feedback from retrospectives and other sources to make process changes.
Adapting to change in Agile development is not just a matter of reacting; it's a proactive approach to ensuring that the product remains aligned with customer needs and market demands. It's about using change as an opportunity for improvement rather than a disruptive force.
Managing Expectations and Feedback
As a Certified Scrum Product Owner (CSPO), your role extends beyond managing the product backlog. You are also responsible for effectively managing stakeholder expectations and feedback, a task that requires finesse and communication skills. Let's explore the intricacies of this responsibility:
Clear Communication:
Open Dialogue: Establishing open and transparent lines of communication with stakeholders. This creates an environment where expectations can be effectively managed.
Setting Realistic Expectations: Communicating what can and cannot be achieved within specific timeframes and resources.
Regular Updates:
Progress Reporting: Providing stakeholders with regular updates on the project's progress. This keeps them informed and engaged in the development process.
Highlighting Achievements: Sharing successes and milestones reached, reinforcing the value being delivered.
Gathering Feedback:
Feedback Loops: Setting up structured feedback loops that allow stakeholders to provide input and voice their concerns.
Actively Listening: Actively listening to feedback, even if it is critical, and demonstrating that it is being taken seriously.
Handling Conflicting Feedback:
Mediation: Resolving conflicts or contradictions within feedback from different stakeholders. The CSPO must make balanced decisions that serve the project's goals.
Responding to Change:
Change Management: Effectively communicating and managing changes in project direction, scope, or objectives to stakeholders.
Risk Communication: Sharing information about potential project risks or challenges and discussing strategies for mitigation.
Documentation:
Feedback Records: Maintaining records of feedback and its resolution to ensure that it is tracked and addressed.
Expectations Documentation: Documenting agreed-upon expectations, priorities, and objectives for reference.
Managing expectations and feedback requires a combination of excellent communication, empathy, and a deep understanding of the project's objectives. The CSPO's role in this aspect is to bridge the gap between stakeholders, development teams, and end-users, ensuring that everyone is on the same page and that feedback is integrated for continuous improvement.
Overcoming Challenges and Obstacles
In the role of a Certified Scrum Product Owner (CSPO), you're likely to encounter a range of challenges and obstacles. However, these challenges are not roadblocks; they're opportunities for growth and improvement. Let's explore some common challenges and strategies for overcoming them:
Conflicting Priorities:
Challenge: Balancing the priorities of different stakeholders can be challenging. Conflicting interests can lead to ambiguity in decision-making.
Strategy: Engage stakeholders in discussions to align their priorities with the project's objectives. Use data and clear communication to make informed decisions.
Changing Requirements:
Challenge: Requirements can change frequently, making it challenging to maintain a stable product backlog and plan.
Strategy: Embrace change as an opportunity for improvement. Implement change management processes to assess and integrate new requirements effectively.
Unrealistic Expectations:
Challenge: Managing stakeholder expectations can be difficult when they expect immediate results or don't fully grasp Agile principles.
Strategy: Educate stakeholders about Agile principles, setting realistic expectations, and providing regular updates to manage their understanding of the project's progress.
Resource Constraints:
Challenge: Limited resources, such as time, budget, or team capacity, can hinder your ability to meet stakeholder demands.
Strategy: Prioritize tasks based on their impact and feasibility within resource constraints. Communicate openly about resource limitations and adjust priorities accordingly.
Resistance to Change:
Challenge: Team members or stakeholders may resist adopting Agile practices or new ways of working.
Strategy: Lead by example, communicate the benefits of Agile, and involve team members in decision-making. Foster a culture of continuous improvement to encourage adaptation.
Incomplete Feedback:
Challenge: Stakeholder feedback may be vague or incomplete, making it challenging to act upon.
Strategy: Engage stakeholders in conversations to elicit more detailed feedback. Use techniques like "Five Whys" to dig deeper into their needs and concerns.
Managing Expectations:
Challenge: Managing stakeholder expectations while maintaining a user-centric approach can be challenging when interests diverge.
Strategy: Balance the needs of users with business goals and technical constraints. Clearly communicate the rationale behind decisions to manage expectations effectively.
Overcoming challenges and obstacles is a fundamental aspect of the CSPO role. It requires a combination of effective communication, adaptability, and strategic decision-making. By addressing these challenges with the right mindset and techniques, you can facilitate a more successful and resilient Agile product development process.
Continuous Improvement for CSPOs
In the dynamic world of Agile product development, the journey of a Certified Scrum Product Owner (CSPO) is one of continual growth and refinement. Continuous improvement is not just a practice; it's a mindset. Let's explore the principles and strategies for ongoing improvement as a CSPO:
Self-Assessment:Reflect on Your Role: Regularly assess your performance and the impact you're making as a CSPO. This self-assessment helps you identify areas for improvement.
Professional Development:Stay Informed: Keep abreast of the latest trends, tools, and best practices in Agile and product management. Attend training, workshops, and conferences to expand your knowledge.
Certification: Consider advanced certifications or training courses to enhance your skills and knowledge.
Feedback Integration:Seek Feedback: Actively seek feedback from team members, stakeholders, and Scrum Masters. Constructive criticism can be a valuable source of insights.
Feedback Processing: Process feedback by identifying actionable areas for improvement and taking steps to address them.
Scrum Master Collaboration:Work Closely with Scrum Masters: Collaborate with Scrum Masters to learn from their experiences and gain a better understanding of the Scrum framework.
Continuous Learning: Be open to sharing your experiences and insights, fostering mutual growth.
Experimentation:Embrace Experimentation: Be open to trying new tools, techniques, or approaches in your role. Experimentation can lead to innovative improvements.
Learn from Failures: Embrace failures as learning opportunities, understanding that not every experiment will yield the desired results.
Collaborative Learning:Learning from Peers: Engage with other CSPOs and product owners to exchange insights, challenges, and best practices.
Cross-Functional Collaboration: Collaborate with developers, designers, and other roles to expand your understanding of the product development process.
Goal Setting:Set Goals for Improvement: Establish clear goals for your own improvement and growth as a CSPO. Regularly review and adjust these goals as you progress.
Continuous improvement as a CSPO is about embracing a growth mindset, actively seeking ways to enhance your skills, and consistently applying new knowledge and insights. It's an ongoing journey of becoming a more effective, adaptable, and valuable product owner within the Agile landscape.
Conclusion
Becoming a Certified Scrum Product Owner (CSPO) is not just about a title; it's a journey of embracing responsibilities, overcoming challenges, and continuously improving. In this comprehensive exploration of the role of a CSPO, we've delved into the core responsibilities and the myriad challenges you might encounter in this dynamic position.
Effective backlog management, stakeholder collaboration, balancing priorities, and decision-making are just some of the intricate facets of your role. Managing expectations and feedback, adapting to change, and overcoming challenges are continuous endeavors that require a blend of skills, including effective communication, empathy, and adaptability.
The role of a CSPO is not for the faint of heart, but for those willing to embrace the challenges and opportunities it presents, it can be a rewarding and fulfilling journey. Remember, your dedication to this role contributes not only to the success of your projects but also to the broader Agile community.
In closing, the role of a CSPO is a journey of perpetual growth and a commitment to delivering value to customers while embracing the principles of Agile. Whether you're an aspiring CSPO or an experienced one, this role offers an ongoing opportunity to make a meaningful impact in the world of product development.
Thank you for accompanying us on this exploration of the CSPO role. May your journey as a Certified Scrum Product Owner be filled with continuous improvement, successful projects, and valuable product deliveries.
A Comprehensive Guide to Installing XenApp: Step-by-Step Instructions
In the ever-evolving landscape of IT and virtualization, organizations seek solutions that empower them to deliver applications to end-users with efficiency, security, and simplicity. Citrix XenApp stands as a stalwart in this endeavor, offering a robust application delivery platform that has revolutionized the way businesses distribute software.
The significance of XenApp extends far beyond its utility as a virtual application delivery solution; it embodies the essence of streamlining productivity and enhancing the end-user experience. With its versatile features, scalability, and capacity to facilitate secure remote access, it's no wonder that countless organizations turn to XenApp as their go-to application delivery solution.
In this comprehensive guide, we'll demystify the installation process, from the prerequisites and initial configuration to the final deployment of your applications. With the help of our clear, easy-to-follow instructions, you'll soon be on your way to harnessing the power of XenApp.
So, whether you're a seasoned IT professional or a novice embarking on the XenApp journey, fasten your seatbelts, as we embark on a journey through the installation process of Citrix XenApp. By the end of this guide, you'll be well on your way to delivering applications effortlessly and securely to your users.
Table of contents
-
System Requirements and Prerequisites
-
XenApp Deployment Options
-
Installing the XenApp Server Role
-
Configuring the License Server
-
Creating a XenApp Farm
-
Configuring Site and Data Store
-
Application Publishing
-
User and Group Management
-
Load Balancing and High Availability
-
Securing Your XenApp Environment
-
Conclusion
System Requirements and Prerequisites
Before diving into the installation process of XenApp, it's crucial to ensure that your environment meets the necessary system requirements and prerequisites. Failing to do so can lead to installation issues, performance problems, or incompatibility. Here's a detailed look at what you need to have in place:
Hardware Requirements:Server Hardware: Ensure that the server or virtual machine you plan to install XenApp on meets the recommended hardware specifications. This includes CPU, RAM, and disk space. Citrix provides specific guidelines based on your expected usage and scalability needs.
Licensing:Acquire XenApp Licenses: Before proceeding with the installation, make sure you have the appropriate licenses for XenApp. The licensing server must be set up and accessible.
Remote Desktop Services (RDS):If you are planning to use XenApp in conjunction with Microsoft Remote Desktop Services (RDS), ensure that RDS is properly configured on your server.
Active Directory Trusts (If Applicable):If your organization uses multiple Active Directory forests or domains, you may need to establish trust relationships between them to facilitate user access.
Before you embark on the XenApp installation journey, it's essential to perform a thorough system assessment to confirm that your environment aligns with these prerequisites. This diligent preparation will set the stage for a smooth and successful XenApp deployment.
XenApp Deployment Options
When it comes to deploying Citrix XenApp, you have several deployment options to choose from, each catering to different business needs and IT infrastructures. Understanding these options is crucial before you start the installation process. Here's an overview of the XenApp deployment options:
On-Premises Deployment:The traditional on-premises deployment involves installing XenApp on your own physical servers or virtual machines within your data center. This option provides full control over your infrastructure but requires ongoing maintenance and resource management.
Cloud-Based Deployment:Citrix offers cloud-based deployment options, allowing you to host XenApp on platforms like Microsoft Azure, Amazon Web Services (AWS), or Google Cloud. Cloud-based deployments offer scalability, flexibility, and the advantage of not having to manage the underlying infrastructure.
Hybrid Deployment:A hybrid deployment combines both on-premises and cloud-based infrastructure. This option is suitable for organizations that want to maintain some applications or data on-premises while leveraging the cloud for scalability and disaster recovery.
XenApp Service on Citrix Cloud:Citrix Cloud provides a management and delivery platform for XenApp. With XenApp Service, you can host your XenApp environment entirely in the cloud, with Citrix managing the infrastructure and updates. This is an excellent option for organizations seeking a fully managed solution.
XenApp Essentials:XenApp Essentials is a Citrix offering specifically designed for Azure. It provides a simplified way to deliver Windows apps from Azure to any device. This option is particularly convenient for organizations already invested in the Microsoft ecosystem.
XenApp in a Microservices Architecture:For organizations looking to modernize their application delivery, microservices architectures can be explored. This approach breaks down application components into microservices that can be easily deployed and scaled.
Geo-Redundant Deployments:If you require high availability and disaster recovery, consider deploying XenApp in multiple geographic regions. This ensures that your applications remain available even if one data center experiences an outage.
The choice of deployment option depends on your organization's specific needs, resources, and long-term strategy. It's essential to evaluate the pros and cons of each option and align it with your business goals before proceeding with the installation. Regardless of the option chosen, understanding the deployment models available will help you make informed decisions during the XenApp installation process.
Installing the XenApp Server Role
Once you've ensured that your system meets the prerequisites and have decided on the deployment model that best suits your organization, the next crucial step is to install the XenApp server role. This process forms the foundation of your XenApp environment. Here's a step-by-step guide on how to do it:
Obtain XenApp Installation Media:Before you begin, ensure you have the necessary XenApp installation files. These can be obtained from Citrix directly or your authorized distributor.
Launch the Installation Wizard:Run the XenApp installation package on the server or virtual machine where you plan to install the XenApp server role.
Choose the Installation Type:You'll typically be presented with installation types such as "Full" and "Custom." Choose "Full" for a typical installation or "Custom" if you want to configure specific options.
Review and Accept the License Agreement:Read through the license agreement carefully and accept the terms if you agree. You cannot proceed without accepting the license agreement.
Specify the Data Store:If you are using a remote SQL database, you'll need to specify the data store. This is where configuration information is stored. Make sure the data store is accessible and properly configured.
Choose Licensing Model:Select your licensing model. You can choose to install the licensing server locally or use a remote Citrix License Server.
Configure Your Farm Settings:Define your XenApp farm's settings, including the farm name, location, and administrator credentials.
Test and Review Settings:Review all the settings you've configured and test the connections to ensure they are functioning correctly.
Begin Installation:Once all settings are verified, start the installation process. The installation wizard will begin configuring the XenApp server role based on your choices.
Installing the XenApp server role is a crucial step in setting up your application delivery environment. Ensuring a successful installation will provide a solid foundation for further configuration and application deployment in your XenApp farm.
Configuring the License Server
Once you've installed the XenApp server role, one of the critical steps in setting up your XenApp environment is configuring the License Server. Proper licensing is essential for ensuring that your XenApp environment is compliant and fully operational. Here's a step-by-step guide on how to configure the License Server:
License Acquisition:Before you can configure the License Server, ensure you have acquired the necessary XenApp licenses. You should have received a license file from Citrix or your authorized distributor.
Launch the License Server Console:On the server where you installed the XenApp server role, locate the Citrix License Server Console and launch it.
Install the License File:In the License Server Console, go to the "Administration" node and select "Install License." Follow the prompts to browse and install your license file. This file contains the licensing information for your XenApp environment.
Allocate Licenses:Once the license file is installed, you'll need to allocate licenses to your XenApp servers. Select the "Allocate Licenses" option and specify the number of licenses to allocate to each server. You can allocate licenses manually or use the License Server's policies for automatic allocation.
Monitor License Usage:Regularly monitor license usage to ensure you remain compliant with your licensing agreement. The License Server Console provides tools to track and report on license usage.
Renew Licenses (As Needed):Keep track of your license expiration dates and renew licenses as necessary to maintain a valid license agreement.
Configuring the License Server is a vital step in the XenApp setup process. It ensures that your XenApp servers have the necessary licenses to deliver applications to end-users. Properly configured licensing not only keeps your environment compliant but also allows you to make the most of the features and capabilities XenApp has to offer.
Creating a XenApp Farm
Creating a XenApp Farm is a fundamental step in setting up your XenApp environment. A XenApp farm is a collection of XenApp servers that work together to deliver applications and desktops to end-users. Here's a step-by-step guide on how to create a XenApp farm:
Plan Your Farm:Before you begin, it's essential to plan your XenApp farm carefully. Consider factors like the number of servers you need, the geographic location of your servers, and the scalability requirements of your organization. Think about redundancy and disaster recovery options as well.
Launch the XenApp Management Console:On a server where you've installed the XenApp server role, launch the XenApp Management Console. This console is your primary interface for configuring and managing your XenApp farm.
Farm Configuration Wizard:In the XenApp Management Console, navigate to "Farm" and click on "Create a new farm" or a similar option, depending on your XenApp version. This will launch the Farm Configuration Wizard.
Enter Farm Information:Follow the prompts in the Farm Configuration Wizard to enter essential information about your farm. This includes specifying the farm name, description, and database server information.
Choose a Data Store:Select the data store option that best fits your needs. You can either use an existing data store or create a new one. The data store stores configuration information for your XenApp farm.
Select the Servers:Specify which servers in your environment will be part of the farm. You can select servers that already have the XenApp server role installed.
Configure Licensing:Associate your XenApp farm with the License Server you've previously configured. Ensure that the farm is properly licensed to run the number of applications and desktops you require.
Farm Database Configuration:Configure the farm database settings, including the database server and credentials. Ensure the database is set up and accessible.
Set Farm Administrators:Define the administrators who will manage the XenApp farm. Assign appropriate permissions and roles to these administrators.
Review and Confirm:Review the information you've entered in the Farm Configuration Wizard to ensure accuracy. Confirm that all settings align with your farm's requirements.
Create the Farm:Once you've reviewed and confirmed the settings, click "Finish" or a similar button to create the XenApp farm. The wizard will begin the process of creating the farm and configuring the servers.
Test and Verify:After the farm is created, test its functionality. Ensure that the servers are communicating properly, and that applications and desktops can be published and accessed.
Farm Management:Use the XenApp Management Console to manage and administer your farm. This includes tasks like publishing applications, configuring policies, and managing users.
Creating a XenApp farm is a crucial step in the setup process, as it forms the backbone of your application delivery environment. Proper planning and configuration will enable you to efficiently deliver applications and desktops to your end-users.
Configuring Site and Data Store
Configuring the site and data store is a pivotal part of setting up a XenApp environment. These components are vital for centralizing configuration data and ensuring the smooth operation of your XenApp deployment. Here's a step-by-step guide on how to configure the site and data store:
Launch the XenApp Management Console
Open the XenApp Management Console on a server where you've installed the XenApp server role. This console is your gateway to configuring and managing your XenApp environment.
Navigate to Farm
In the XenApp Management Console, navigate to the "Farm" section or a related area, depending on your XenApp version.
Select Your Farm
Click on your XenApp farm to access the farm's properties and settings.
Access Site Configuration
In the farm's properties, look for an option related to site configuration or data store. Select this option to access site configuration settings.
Data Store Configuration
In the site configuration, you'll typically find settings related to the data store. Follow the prompts or tabs to configure the data store. This includes specifying the data store location and credentials.
Configure Site Settings
Configure additional site settings, such as the site name, location, and description. These settings help identify and manage your XenApp site within the farm.
Review and Confirm
Review the data store and site configuration settings to ensure they are accurate and in line with your requirements.
Save and Apply Changes
Once you've confirmed the settings, save and apply the changes. This step will configure the site and data store according to the settings you've specified.
Test the Configuration
After the configuration is complete, it's essential to test the site and data store to ensure they are functioning correctly. Verify that the XenApp servers can communicate with the data store and that configuration data is being stored and retrieved as expected.
Site Management
You can continue to use the XenApp Management Console to manage and administer your site. This includes tasks like publishing applications, managing policies, and controlling user access.
Configuring the site and data store is a pivotal step in creating a robust and well-organized XenApp environment. The data store centralizes your configuration data, making it accessible to all XenApp servers in your farm, while the site configuration ensures that your XenApp site is properly defined and functional. Proper configuration of these components is crucial for effective application delivery and user management.
Application Publishing
Publishing applications is a fundamental step in setting up your XenApp environment, as it makes applications available to end-users. Whether you're delivering a single application or a suite of software, proper application publishing is essential. Here's a step-by-step guide on how to publish applications in XenApp:
Launch the XenApp Management Console:Open the XenApp Management Console on a server where you've installed the XenApp server role. This is your primary tool for configuring and managing your XenApp environment.
Navigate to Applications:In the XenApp Management Console, navigate to the "Applications" section or a related area, depending on your XenApp version.
Application Publishing Wizard:Look for an option that allows you to publish applications. This may be called "Publish Applications" or a similar name. Select this option to launch the Application Publishing Wizard.
Select Applications:In the wizard, you'll be prompted to select the applications you want to publish. You can choose from a list of installed applications on the server or specify the path to an application executable.
Configure Application Properties:For each application you're publishing, configure its properties. This includes specifying the name that users will see, description, icon, command line, and working directory. You can also configure application shortcuts.
Define Access Control:Set access control for the published application. This includes specifying which users or user groups are allowed to access the application. You can use Active Directory groups or specific users for this purpose.
Configure Session Pre-Launch and Session Reliability (Optional):If desired, configure additional settings like session pre-launch and session reliability. These features can improve user experience by speeding up application launch and ensuring session persistence in case of network interruptions.
Review and Confirm:Review the application publishing settings to ensure they align with your requirements and user access policies.
Publish the Applications:Once you've confirmed the settings, proceed to publish the applications. This step makes the applications available to users within your XenApp environment.
Proper application publishing in XenApp is a core component of delivering software to end-users securely and efficiently. By following these steps, you ensure that users can access the applications they need while maintaining control over who can access them.
User and Group Management
User and group management in XenApp is essential for controlling access, securing resources, and ensuring the right users have access to the right applications. Here's a step-by-step guide on how to manage users and groups in your XenApp environment:
Configure User Access:Configure the access permissions for the added users or groups. You can specify which applications they can access, the servers they can connect to, and their session settings.
Define Policies (Optional):If necessary, you can create policies to enforce specific settings for user or group sessions. Policies can control aspects like printing, drive mapping, and security settings.
Review and Confirm:Review the user and group management settings to ensure they align with your organization's requirements and access policies.
Save and Apply Changes:Once you've confirmed the settings, save and apply the changes. This step configures the user and group access and policies according to your specifications.
Test User Access:After configuring user and group settings, it's crucial to test user access. Verify that users or groups can access the applications and resources you've granted them.
User and Group Management:Continue to use the XenApp Management Console to manage users and groups in your XenApp environment. You can update access permissions, add or remove users, and modify session policies as needed.
Effective user and group management are essential for ensuring that users have the right level of access to resources and applications. By following these steps, you can maintain control over your XenApp environment and enforce access policies that align with your organization's security and operational needs.
Load Balancing and High Availability
Load balancing and high availability are critical considerations when setting up a XenApp environment, especially for ensuring performance and continuous operation. Here's a step-by-step guide on how to implement load balancing and high availability in XenApp:
Assess Your Environment:Before you begin, conduct a thorough assessment of your XenApp environment to understand your load balancing and high availability needs. Consider factors like the number of users, server resources, and geographic locations.
Choose a Load Balancing Solution:Select a load balancing solution that best fits your requirements. Citrix offers NetScaler for load balancing, but other options, like hardware load balancers or software-based load balancers, are available.
Configure Load Balancing:Set up the load balancer according to your chosen solution. This typically involves configuring the load balancer to distribute user connections evenly across multiple XenApp servers.
High Availability Considerations:High availability requires redundancy in your XenApp environment. Consider options like clustering XenApp servers or deploying multiple data centers for geographic redundancy.
Disaster Recovery Plan:Develop a disaster recovery plan that outlines how you'll recover your XenApp environment in case of a catastrophic failure. This may involve data backups, off-site replication, and clear recovery procedures.
Test the Load Balancer and High Availability Setup:After configuring load balancing and high availability, it's crucial to test the setup. Verify that user connections are distributed correctly and that failover mechanisms work as intended.
Load balancing and high availability are vital for delivering applications reliably and efficiently in a XenApp environment. By following these steps, you can ensure that your XenApp environment can handle user demand, recover from failures, and maintain a high level of uptime.
Securing Your XenApp Environment
Securing your XenApp environment is a critical aspect of maintaining the confidentiality, integrity, and availability of your applications and data. Here's a step-by-step guide on how to secure your XenApp environment:
Assess Security Requirements:Begin by assessing your organization's specific security requirements and compliance standards. Determine the sensitivity of the data and applications you're delivering through XenApp.
Implement Network Security Measures:Apply network security measures, such as firewalls and intrusion detection systems, to protect your XenApp servers from unauthorized access and attacks.
Secure Communication with SSL/TLS:Use SSL/TLS encryption to secure communication between XenApp servers and client devices. Ensure that certificates are correctly configured and up-to-date.
Access Control and Authentication:Enforce strict access control by configuring role-based access control (RBAC) and employing strong authentication methods like multi-factor authentication (MFA).
User Training:Educate users about security best practices, including the importance of secure passwords, avoiding phishing attacks, and reporting suspicious activity.
Intrusion Detection and Monitoring:Implement intrusion detection systems and monitoring tools to detect and respond to security incidents and anomalies.
Data Backup and Disaster Recovery:Implement regular data backups and establish a comprehensive disaster recovery plan to ensure data availability in case of data loss or system failure.
By following these steps, you can significantly enhance the security of your XenApp environment, reducing the risk of data breaches, unauthorized access, and other security threats. Security is an ongoing process, and regular reviews and updates are essential to maintaining a secure XenApp deployment.
Conclusion
In conclusion, setting up a XenApp environment is a complex but highly rewarding endeavor that enables organizations to deliver applications and desktops to users efficiently and securely. Throughout this comprehensive guide, we've explored the essential steps involved in the installation and configuration of XenApp, including system requirements, deployment options, setting up the XenApp server role, configuring the License Server, creating a XenApp farm, configuring the site and data store, application publishing, user and group management, load balancing, high availability, and securing your XenApp environment.
As you work through each of these steps, it's crucial to keep in mind the specific needs and goals of your organization. Flexibility is one of the key strengths of XenApp, and it can be adapted to suit a wide range of scenarios, from small businesses to large enterprises. By carefully planning and configuring your XenApp environment, you can harness its capabilities to provide your users with reliable access to the applications and desktops they need, while maintaining the highest levels of security and performance.
With a well-designed and carefully maintained XenApp environment, your organization can streamline application delivery, enhance user productivity, and adapt to the ever-changing landscape of IT and virtualization. Whether you're a seasoned IT professional or a newcomer to XenApp, this guide provides a solid foundation for successfully deploying and managing XenApp within your organization.
Read More
In the ever-evolving landscape of IT and virtualization, organizations seek solutions that empower them to deliver applications to end-users with efficiency, security, and simplicity. Citrix XenApp stands as a stalwart in this endeavor, offering a robust application delivery platform that has revolutionized the way businesses distribute software.
The significance of XenApp extends far beyond its utility as a virtual application delivery solution; it embodies the essence of streamlining productivity and enhancing the end-user experience. With its versatile features, scalability, and capacity to facilitate secure remote access, it's no wonder that countless organizations turn to XenApp as their go-to application delivery solution.
In this comprehensive guide, we'll demystify the installation process, from the prerequisites and initial configuration to the final deployment of your applications. With the help of our clear, easy-to-follow instructions, you'll soon be on your way to harnessing the power of XenApp.
So, whether you're a seasoned IT professional or a novice embarking on the XenApp journey, fasten your seatbelts, as we embark on a journey through the installation process of Citrix XenApp. By the end of this guide, you'll be well on your way to delivering applications effortlessly and securely to your users.
Table of contents
-
System Requirements and Prerequisites
-
XenApp Deployment Options
-
Installing the XenApp Server Role
-
Configuring the License Server
-
Creating a XenApp Farm
-
Configuring Site and Data Store
-
Application Publishing
-
User and Group Management
-
Load Balancing and High Availability
-
Securing Your XenApp Environment
-
Conclusion
System Requirements and Prerequisites
Before diving into the installation process of XenApp, it's crucial to ensure that your environment meets the necessary system requirements and prerequisites. Failing to do so can lead to installation issues, performance problems, or incompatibility. Here's a detailed look at what you need to have in place:
Hardware Requirements:Server Hardware: Ensure that the server or virtual machine you plan to install XenApp on meets the recommended hardware specifications. This includes CPU, RAM, and disk space. Citrix provides specific guidelines based on your expected usage and scalability needs.
Licensing:Acquire XenApp Licenses: Before proceeding with the installation, make sure you have the appropriate licenses for XenApp. The licensing server must be set up and accessible.
Remote Desktop Services (RDS):If you are planning to use XenApp in conjunction with Microsoft Remote Desktop Services (RDS), ensure that RDS is properly configured on your server.
Active Directory Trusts (If Applicable):If your organization uses multiple Active Directory forests or domains, you may need to establish trust relationships between them to facilitate user access.
Before you embark on the XenApp installation journey, it's essential to perform a thorough system assessment to confirm that your environment aligns with these prerequisites. This diligent preparation will set the stage for a smooth and successful XenApp deployment.
XenApp Deployment Options
When it comes to deploying Citrix XenApp, you have several deployment options to choose from, each catering to different business needs and IT infrastructures. Understanding these options is crucial before you start the installation process. Here's an overview of the XenApp deployment options:
On-Premises Deployment:The traditional on-premises deployment involves installing XenApp on your own physical servers or virtual machines within your data center. This option provides full control over your infrastructure but requires ongoing maintenance and resource management.
Cloud-Based Deployment:Citrix offers cloud-based deployment options, allowing you to host XenApp on platforms like Microsoft Azure, Amazon Web Services (AWS), or Google Cloud. Cloud-based deployments offer scalability, flexibility, and the advantage of not having to manage the underlying infrastructure.
Hybrid Deployment:A hybrid deployment combines both on-premises and cloud-based infrastructure. This option is suitable for organizations that want to maintain some applications or data on-premises while leveraging the cloud for scalability and disaster recovery.
XenApp Service on Citrix Cloud:Citrix Cloud provides a management and delivery platform for XenApp. With XenApp Service, you can host your XenApp environment entirely in the cloud, with Citrix managing the infrastructure and updates. This is an excellent option for organizations seeking a fully managed solution.
XenApp Essentials:XenApp Essentials is a Citrix offering specifically designed for Azure. It provides a simplified way to deliver Windows apps from Azure to any device. This option is particularly convenient for organizations already invested in the Microsoft ecosystem.
XenApp in a Microservices Architecture:For organizations looking to modernize their application delivery, microservices architectures can be explored. This approach breaks down application components into microservices that can be easily deployed and scaled.
Geo-Redundant Deployments:If you require high availability and disaster recovery, consider deploying XenApp in multiple geographic regions. This ensures that your applications remain available even if one data center experiences an outage.
The choice of deployment option depends on your organization's specific needs, resources, and long-term strategy. It's essential to evaluate the pros and cons of each option and align it with your business goals before proceeding with the installation. Regardless of the option chosen, understanding the deployment models available will help you make informed decisions during the XenApp installation process.
Installing the XenApp Server Role
Once you've ensured that your system meets the prerequisites and have decided on the deployment model that best suits your organization, the next crucial step is to install the XenApp server role. This process forms the foundation of your XenApp environment. Here's a step-by-step guide on how to do it:
Obtain XenApp Installation Media:Before you begin, ensure you have the necessary XenApp installation files. These can be obtained from Citrix directly or your authorized distributor.
Launch the Installation Wizard:Run the XenApp installation package on the server or virtual machine where you plan to install the XenApp server role.
Choose the Installation Type:You'll typically be presented with installation types such as "Full" and "Custom." Choose "Full" for a typical installation or "Custom" if you want to configure specific options.
Review and Accept the License Agreement:Read through the license agreement carefully and accept the terms if you agree. You cannot proceed without accepting the license agreement.
Specify the Data Store:If you are using a remote SQL database, you'll need to specify the data store. This is where configuration information is stored. Make sure the data store is accessible and properly configured.
Choose Licensing Model:Select your licensing model. You can choose to install the licensing server locally or use a remote Citrix License Server.
Configure Your Farm Settings:Define your XenApp farm's settings, including the farm name, location, and administrator credentials.
Test and Review Settings:Review all the settings you've configured and test the connections to ensure they are functioning correctly.
Begin Installation:Once all settings are verified, start the installation process. The installation wizard will begin configuring the XenApp server role based on your choices.
Installing the XenApp server role is a crucial step in setting up your application delivery environment. Ensuring a successful installation will provide a solid foundation for further configuration and application deployment in your XenApp farm.
Configuring the License Server
Once you've installed the XenApp server role, one of the critical steps in setting up your XenApp environment is configuring the License Server. Proper licensing is essential for ensuring that your XenApp environment is compliant and fully operational. Here's a step-by-step guide on how to configure the License Server:
License Acquisition:Before you can configure the License Server, ensure you have acquired the necessary XenApp licenses. You should have received a license file from Citrix or your authorized distributor.
Launch the License Server Console:On the server where you installed the XenApp server role, locate the Citrix License Server Console and launch it.
Install the License File:In the License Server Console, go to the "Administration" node and select "Install License." Follow the prompts to browse and install your license file. This file contains the licensing information for your XenApp environment.
Allocate Licenses:Once the license file is installed, you'll need to allocate licenses to your XenApp servers. Select the "Allocate Licenses" option and specify the number of licenses to allocate to each server. You can allocate licenses manually or use the License Server's policies for automatic allocation.
Monitor License Usage:Regularly monitor license usage to ensure you remain compliant with your licensing agreement. The License Server Console provides tools to track and report on license usage.
Renew Licenses (As Needed):Keep track of your license expiration dates and renew licenses as necessary to maintain a valid license agreement.
Configuring the License Server is a vital step in the XenApp setup process. It ensures that your XenApp servers have the necessary licenses to deliver applications to end-users. Properly configured licensing not only keeps your environment compliant but also allows you to make the most of the features and capabilities XenApp has to offer.
Creating a XenApp Farm
Creating a XenApp Farm is a fundamental step in setting up your XenApp environment. A XenApp farm is a collection of XenApp servers that work together to deliver applications and desktops to end-users. Here's a step-by-step guide on how to create a XenApp farm:
Plan Your Farm:Before you begin, it's essential to plan your XenApp farm carefully. Consider factors like the number of servers you need, the geographic location of your servers, and the scalability requirements of your organization. Think about redundancy and disaster recovery options as well.
Launch the XenApp Management Console:On a server where you've installed the XenApp server role, launch the XenApp Management Console. This console is your primary interface for configuring and managing your XenApp farm.
Farm Configuration Wizard:In the XenApp Management Console, navigate to "Farm" and click on "Create a new farm" or a similar option, depending on your XenApp version. This will launch the Farm Configuration Wizard.
Enter Farm Information:Follow the prompts in the Farm Configuration Wizard to enter essential information about your farm. This includes specifying the farm name, description, and database server information.
Choose a Data Store:Select the data store option that best fits your needs. You can either use an existing data store or create a new one. The data store stores configuration information for your XenApp farm.
Select the Servers:Specify which servers in your environment will be part of the farm. You can select servers that already have the XenApp server role installed.
Configure Licensing:Associate your XenApp farm with the License Server you've previously configured. Ensure that the farm is properly licensed to run the number of applications and desktops you require.
Farm Database Configuration:Configure the farm database settings, including the database server and credentials. Ensure the database is set up and accessible.
Set Farm Administrators:Define the administrators who will manage the XenApp farm. Assign appropriate permissions and roles to these administrators.
Review and Confirm:Review the information you've entered in the Farm Configuration Wizard to ensure accuracy. Confirm that all settings align with your farm's requirements.
Create the Farm:Once you've reviewed and confirmed the settings, click "Finish" or a similar button to create the XenApp farm. The wizard will begin the process of creating the farm and configuring the servers.
Test and Verify:After the farm is created, test its functionality. Ensure that the servers are communicating properly, and that applications and desktops can be published and accessed.
Farm Management:Use the XenApp Management Console to manage and administer your farm. This includes tasks like publishing applications, configuring policies, and managing users.
Creating a XenApp farm is a crucial step in the setup process, as it forms the backbone of your application delivery environment. Proper planning and configuration will enable you to efficiently deliver applications and desktops to your end-users.
Configuring Site and Data Store
Configuring the site and data store is a pivotal part of setting up a XenApp environment. These components are vital for centralizing configuration data and ensuring the smooth operation of your XenApp deployment. Here's a step-by-step guide on how to configure the site and data store:
Launch the XenApp Management Console
Open the XenApp Management Console on a server where you've installed the XenApp server role. This console is your gateway to configuring and managing your XenApp environment.
Navigate to Farm
In the XenApp Management Console, navigate to the "Farm" section or a related area, depending on your XenApp version.
Select Your Farm
Click on your XenApp farm to access the farm's properties and settings.
Access Site Configuration
In the farm's properties, look for an option related to site configuration or data store. Select this option to access site configuration settings.
Data Store Configuration
In the site configuration, you'll typically find settings related to the data store. Follow the prompts or tabs to configure the data store. This includes specifying the data store location and credentials.
Configure Site Settings
Configure additional site settings, such as the site name, location, and description. These settings help identify and manage your XenApp site within the farm.
Review and Confirm
Review the data store and site configuration settings to ensure they are accurate and in line with your requirements.
Save and Apply Changes
Once you've confirmed the settings, save and apply the changes. This step will configure the site and data store according to the settings you've specified.
Test the Configuration
After the configuration is complete, it's essential to test the site and data store to ensure they are functioning correctly. Verify that the XenApp servers can communicate with the data store and that configuration data is being stored and retrieved as expected.
Site Management
You can continue to use the XenApp Management Console to manage and administer your site. This includes tasks like publishing applications, managing policies, and controlling user access.
Configuring the site and data store is a pivotal step in creating a robust and well-organized XenApp environment. The data store centralizes your configuration data, making it accessible to all XenApp servers in your farm, while the site configuration ensures that your XenApp site is properly defined and functional. Proper configuration of these components is crucial for effective application delivery and user management.
Application Publishing
Publishing applications is a fundamental step in setting up your XenApp environment, as it makes applications available to end-users. Whether you're delivering a single application or a suite of software, proper application publishing is essential. Here's a step-by-step guide on how to publish applications in XenApp:
Launch the XenApp Management Console:Open the XenApp Management Console on a server where you've installed the XenApp server role. This is your primary tool for configuring and managing your XenApp environment.
Navigate to Applications:In the XenApp Management Console, navigate to the "Applications" section or a related area, depending on your XenApp version.
Application Publishing Wizard:Look for an option that allows you to publish applications. This may be called "Publish Applications" or a similar name. Select this option to launch the Application Publishing Wizard.
Select Applications:In the wizard, you'll be prompted to select the applications you want to publish. You can choose from a list of installed applications on the server or specify the path to an application executable.
Configure Application Properties:For each application you're publishing, configure its properties. This includes specifying the name that users will see, description, icon, command line, and working directory. You can also configure application shortcuts.
Define Access Control:Set access control for the published application. This includes specifying which users or user groups are allowed to access the application. You can use Active Directory groups or specific users for this purpose.
Configure Session Pre-Launch and Session Reliability (Optional):If desired, configure additional settings like session pre-launch and session reliability. These features can improve user experience by speeding up application launch and ensuring session persistence in case of network interruptions.
Review and Confirm:Review the application publishing settings to ensure they align with your requirements and user access policies.
Publish the Applications:Once you've confirmed the settings, proceed to publish the applications. This step makes the applications available to users within your XenApp environment.
Proper application publishing in XenApp is a core component of delivering software to end-users securely and efficiently. By following these steps, you ensure that users can access the applications they need while maintaining control over who can access them.
User and Group Management
User and group management in XenApp is essential for controlling access, securing resources, and ensuring the right users have access to the right applications. Here's a step-by-step guide on how to manage users and groups in your XenApp environment:
Configure User Access:Configure the access permissions for the added users or groups. You can specify which applications they can access, the servers they can connect to, and their session settings.
Define Policies (Optional):If necessary, you can create policies to enforce specific settings for user or group sessions. Policies can control aspects like printing, drive mapping, and security settings.
Review and Confirm:Review the user and group management settings to ensure they align with your organization's requirements and access policies.
Save and Apply Changes:Once you've confirmed the settings, save and apply the changes. This step configures the user and group access and policies according to your specifications.
Test User Access:After configuring user and group settings, it's crucial to test user access. Verify that users or groups can access the applications and resources you've granted them.
User and Group Management:Continue to use the XenApp Management Console to manage users and groups in your XenApp environment. You can update access permissions, add or remove users, and modify session policies as needed.
Effective user and group management are essential for ensuring that users have the right level of access to resources and applications. By following these steps, you can maintain control over your XenApp environment and enforce access policies that align with your organization's security and operational needs.
Load Balancing and High Availability
Load balancing and high availability are critical considerations when setting up a XenApp environment, especially for ensuring performance and continuous operation. Here's a step-by-step guide on how to implement load balancing and high availability in XenApp:
Assess Your Environment:Before you begin, conduct a thorough assessment of your XenApp environment to understand your load balancing and high availability needs. Consider factors like the number of users, server resources, and geographic locations.
Choose a Load Balancing Solution:Select a load balancing solution that best fits your requirements. Citrix offers NetScaler for load balancing, but other options, like hardware load balancers or software-based load balancers, are available.
Configure Load Balancing:Set up the load balancer according to your chosen solution. This typically involves configuring the load balancer to distribute user connections evenly across multiple XenApp servers.
High Availability Considerations:High availability requires redundancy in your XenApp environment. Consider options like clustering XenApp servers or deploying multiple data centers for geographic redundancy.
Disaster Recovery Plan:Develop a disaster recovery plan that outlines how you'll recover your XenApp environment in case of a catastrophic failure. This may involve data backups, off-site replication, and clear recovery procedures.
Test the Load Balancer and High Availability Setup:After configuring load balancing and high availability, it's crucial to test the setup. Verify that user connections are distributed correctly and that failover mechanisms work as intended.
Load balancing and high availability are vital for delivering applications reliably and efficiently in a XenApp environment. By following these steps, you can ensure that your XenApp environment can handle user demand, recover from failures, and maintain a high level of uptime.
Securing Your XenApp Environment
Securing your XenApp environment is a critical aspect of maintaining the confidentiality, integrity, and availability of your applications and data. Here's a step-by-step guide on how to secure your XenApp environment:
Assess Security Requirements:Begin by assessing your organization's specific security requirements and compliance standards. Determine the sensitivity of the data and applications you're delivering through XenApp.
Implement Network Security Measures:Apply network security measures, such as firewalls and intrusion detection systems, to protect your XenApp servers from unauthorized access and attacks.
Secure Communication with SSL/TLS:Use SSL/TLS encryption to secure communication between XenApp servers and client devices. Ensure that certificates are correctly configured and up-to-date.
Access Control and Authentication:Enforce strict access control by configuring role-based access control (RBAC) and employing strong authentication methods like multi-factor authentication (MFA).
User Training:Educate users about security best practices, including the importance of secure passwords, avoiding phishing attacks, and reporting suspicious activity.
Intrusion Detection and Monitoring:Implement intrusion detection systems and monitoring tools to detect and respond to security incidents and anomalies.
Data Backup and Disaster Recovery:Implement regular data backups and establish a comprehensive disaster recovery plan to ensure data availability in case of data loss or system failure.
By following these steps, you can significantly enhance the security of your XenApp environment, reducing the risk of data breaches, unauthorized access, and other security threats. Security is an ongoing process, and regular reviews and updates are essential to maintaining a secure XenApp deployment.
Conclusion
In conclusion, setting up a XenApp environment is a complex but highly rewarding endeavor that enables organizations to deliver applications and desktops to users efficiently and securely. Throughout this comprehensive guide, we've explored the essential steps involved in the installation and configuration of XenApp, including system requirements, deployment options, setting up the XenApp server role, configuring the License Server, creating a XenApp farm, configuring the site and data store, application publishing, user and group management, load balancing, high availability, and securing your XenApp environment.
As you work through each of these steps, it's crucial to keep in mind the specific needs and goals of your organization. Flexibility is one of the key strengths of XenApp, and it can be adapted to suit a wide range of scenarios, from small businesses to large enterprises. By carefully planning and configuring your XenApp environment, you can harness its capabilities to provide your users with reliable access to the applications and desktops they need, while maintaining the highest levels of security and performance.
With a well-designed and carefully maintained XenApp environment, your organization can streamline application delivery, enhance user productivity, and adapt to the ever-changing landscape of IT and virtualization. Whether you're a seasoned IT professional or a newcomer to XenApp, this guide provides a solid foundation for successfully deploying and managing XenApp within your organization.
A Comprehensive Guide to Installing XenApp: Step-by-Step Instructions
In the ever-evolving landscape of IT and virtualization, organizations seek solutions that empower them to deliver applications to end-users with efficiency, security, and simplicity. Citrix XenApp stands as a stalwart in this endeavor, offering a robust application delivery platform that has revolutionized the way businesses distribute software.
The significance of XenApp extends far beyond its utility as a virtual application delivery solution; it embodies the essence of streamlining productivity and enhancing the end-user experience. With its versatile features, scalability, and capacity to facilitate secure remote access, it's no wonder that countless organizations turn to XenApp as their go-to application delivery solution.
In this comprehensive guide, we'll demystify the installation process, from the prerequisites and initial configuration to the final deployment of your applications. With the help of our clear, easy-to-follow instructions, you'll soon be on your way to harnessing the power of XenApp.
So, whether you're a seasoned IT professional or a novice embarking on the XenApp journey, fasten your seatbelts, as we embark on a journey through the installation process of Citrix XenApp. By the end of this guide, you'll be well on your way to delivering applications effortlessly and securely to your users.
Table of contents
-
System Requirements and Prerequisites
-
XenApp Deployment Options
-
Installing the XenApp Server Role
-
Configuring the License Server
-
Creating a XenApp Farm
-
Configuring Site and Data Store
-
Application Publishing
-
User and Group Management
-
Load Balancing and High Availability
-
Securing Your XenApp Environment
-
Conclusion
System Requirements and Prerequisites
Before diving into the installation process of XenApp, it's crucial to ensure that your environment meets the necessary system requirements and prerequisites. Failing to do so can lead to installation issues, performance problems, or incompatibility. Here's a detailed look at what you need to have in place:
Hardware Requirements:Server Hardware: Ensure that the server or virtual machine you plan to install XenApp on meets the recommended hardware specifications. This includes CPU, RAM, and disk space. Citrix provides specific guidelines based on your expected usage and scalability needs.
Licensing:Acquire XenApp Licenses: Before proceeding with the installation, make sure you have the appropriate licenses for XenApp. The licensing server must be set up and accessible.
Remote Desktop Services (RDS):If you are planning to use XenApp in conjunction with Microsoft Remote Desktop Services (RDS), ensure that RDS is properly configured on your server.
Active Directory Trusts (If Applicable):If your organization uses multiple Active Directory forests or domains, you may need to establish trust relationships between them to facilitate user access.
Before you embark on the XenApp installation journey, it's essential to perform a thorough system assessment to confirm that your environment aligns with these prerequisites. This diligent preparation will set the stage for a smooth and successful XenApp deployment.
XenApp Deployment Options
When it comes to deploying Citrix XenApp, you have several deployment options to choose from, each catering to different business needs and IT infrastructures. Understanding these options is crucial before you start the installation process. Here's an overview of the XenApp deployment options:
On-Premises Deployment:The traditional on-premises deployment involves installing XenApp on your own physical servers or virtual machines within your data center. This option provides full control over your infrastructure but requires ongoing maintenance and resource management.
Cloud-Based Deployment:Citrix offers cloud-based deployment options, allowing you to host XenApp on platforms like Microsoft Azure, Amazon Web Services (AWS), or Google Cloud. Cloud-based deployments offer scalability, flexibility, and the advantage of not having to manage the underlying infrastructure.
Hybrid Deployment:A hybrid deployment combines both on-premises and cloud-based infrastructure. This option is suitable for organizations that want to maintain some applications or data on-premises while leveraging the cloud for scalability and disaster recovery.
XenApp Service on Citrix Cloud:Citrix Cloud provides a management and delivery platform for XenApp. With XenApp Service, you can host your XenApp environment entirely in the cloud, with Citrix managing the infrastructure and updates. This is an excellent option for organizations seeking a fully managed solution.
XenApp Essentials:XenApp Essentials is a Citrix offering specifically designed for Azure. It provides a simplified way to deliver Windows apps from Azure to any device. This option is particularly convenient for organizations already invested in the Microsoft ecosystem.
XenApp in a Microservices Architecture:For organizations looking to modernize their application delivery, microservices architectures can be explored. This approach breaks down application components into microservices that can be easily deployed and scaled.
Geo-Redundant Deployments:If you require high availability and disaster recovery, consider deploying XenApp in multiple geographic regions. This ensures that your applications remain available even if one data center experiences an outage.
The choice of deployment option depends on your organization's specific needs, resources, and long-term strategy. It's essential to evaluate the pros and cons of each option and align it with your business goals before proceeding with the installation. Regardless of the option chosen, understanding the deployment models available will help you make informed decisions during the XenApp installation process.
Installing the XenApp Server Role
Once you've ensured that your system meets the prerequisites and have decided on the deployment model that best suits your organization, the next crucial step is to install the XenApp server role. This process forms the foundation of your XenApp environment. Here's a step-by-step guide on how to do it:
Obtain XenApp Installation Media:Before you begin, ensure you have the necessary XenApp installation files. These can be obtained from Citrix directly or your authorized distributor.
Launch the Installation Wizard:Run the XenApp installation package on the server or virtual machine where you plan to install the XenApp server role.
Choose the Installation Type:You'll typically be presented with installation types such as "Full" and "Custom." Choose "Full" for a typical installation or "Custom" if you want to configure specific options.
Review and Accept the License Agreement:Read through the license agreement carefully and accept the terms if you agree. You cannot proceed without accepting the license agreement.
Specify the Data Store:If you are using a remote SQL database, you'll need to specify the data store. This is where configuration information is stored. Make sure the data store is accessible and properly configured.
Choose Licensing Model:Select your licensing model. You can choose to install the licensing server locally or use a remote Citrix License Server.
Configure Your Farm Settings:Define your XenApp farm's settings, including the farm name, location, and administrator credentials.
Test and Review Settings:Review all the settings you've configured and test the connections to ensure they are functioning correctly.
Begin Installation:Once all settings are verified, start the installation process. The installation wizard will begin configuring the XenApp server role based on your choices.
Installing the XenApp server role is a crucial step in setting up your application delivery environment. Ensuring a successful installation will provide a solid foundation for further configuration and application deployment in your XenApp farm.
Configuring the License Server
Once you've installed the XenApp server role, one of the critical steps in setting up your XenApp environment is configuring the License Server. Proper licensing is essential for ensuring that your XenApp environment is compliant and fully operational. Here's a step-by-step guide on how to configure the License Server:
License Acquisition:Before you can configure the License Server, ensure you have acquired the necessary XenApp licenses. You should have received a license file from Citrix or your authorized distributor.
Launch the License Server Console:On the server where you installed the XenApp server role, locate the Citrix License Server Console and launch it.
Install the License File:In the License Server Console, go to the "Administration" node and select "Install License." Follow the prompts to browse and install your license file. This file contains the licensing information for your XenApp environment.
Allocate Licenses:Once the license file is installed, you'll need to allocate licenses to your XenApp servers. Select the "Allocate Licenses" option and specify the number of licenses to allocate to each server. You can allocate licenses manually or use the License Server's policies for automatic allocation.
Monitor License Usage:Regularly monitor license usage to ensure you remain compliant with your licensing agreement. The License Server Console provides tools to track and report on license usage.
Renew Licenses (As Needed):Keep track of your license expiration dates and renew licenses as necessary to maintain a valid license agreement.
Configuring the License Server is a vital step in the XenApp setup process. It ensures that your XenApp servers have the necessary licenses to deliver applications to end-users. Properly configured licensing not only keeps your environment compliant but also allows you to make the most of the features and capabilities XenApp has to offer.
Creating a XenApp Farm
Creating a XenApp Farm is a fundamental step in setting up your XenApp environment. A XenApp farm is a collection of XenApp servers that work together to deliver applications and desktops to end-users. Here's a step-by-step guide on how to create a XenApp farm:
Plan Your Farm:Before you begin, it's essential to plan your XenApp farm carefully. Consider factors like the number of servers you need, the geographic location of your servers, and the scalability requirements of your organization. Think about redundancy and disaster recovery options as well.
Launch the XenApp Management Console:On a server where you've installed the XenApp server role, launch the XenApp Management Console. This console is your primary interface for configuring and managing your XenApp farm.
Farm Configuration Wizard:In the XenApp Management Console, navigate to "Farm" and click on "Create a new farm" or a similar option, depending on your XenApp version. This will launch the Farm Configuration Wizard.
Enter Farm Information:Follow the prompts in the Farm Configuration Wizard to enter essential information about your farm. This includes specifying the farm name, description, and database server information.
Choose a Data Store:Select the data store option that best fits your needs. You can either use an existing data store or create a new one. The data store stores configuration information for your XenApp farm.
Select the Servers:Specify which servers in your environment will be part of the farm. You can select servers that already have the XenApp server role installed.
Configure Licensing:Associate your XenApp farm with the License Server you've previously configured. Ensure that the farm is properly licensed to run the number of applications and desktops you require.
Farm Database Configuration:Configure the farm database settings, including the database server and credentials. Ensure the database is set up and accessible.
Set Farm Administrators:Define the administrators who will manage the XenApp farm. Assign appropriate permissions and roles to these administrators.
Review and Confirm:Review the information you've entered in the Farm Configuration Wizard to ensure accuracy. Confirm that all settings align with your farm's requirements.
Create the Farm:Once you've reviewed and confirmed the settings, click "Finish" or a similar button to create the XenApp farm. The wizard will begin the process of creating the farm and configuring the servers.
Test and Verify:After the farm is created, test its functionality. Ensure that the servers are communicating properly, and that applications and desktops can be published and accessed.
Farm Management:Use the XenApp Management Console to manage and administer your farm. This includes tasks like publishing applications, configuring policies, and managing users.
Creating a XenApp farm is a crucial step in the setup process, as it forms the backbone of your application delivery environment. Proper planning and configuration will enable you to efficiently deliver applications and desktops to your end-users.
Configuring Site and Data Store
Configuring the site and data store is a pivotal part of setting up a XenApp environment. These components are vital for centralizing configuration data and ensuring the smooth operation of your XenApp deployment. Here's a step-by-step guide on how to configure the site and data store:
Launch the XenApp Management Console
Open the XenApp Management Console on a server where you've installed the XenApp server role. This console is your gateway to configuring and managing your XenApp environment.
Navigate to Farm
In the XenApp Management Console, navigate to the "Farm" section or a related area, depending on your XenApp version.
Select Your Farm
Click on your XenApp farm to access the farm's properties and settings.
Access Site Configuration
In the farm's properties, look for an option related to site configuration or data store. Select this option to access site configuration settings.
Data Store Configuration
In the site configuration, you'll typically find settings related to the data store. Follow the prompts or tabs to configure the data store. This includes specifying the data store location and credentials.
Configure Site Settings
Configure additional site settings, such as the site name, location, and description. These settings help identify and manage your XenApp site within the farm.
Review and Confirm
Review the data store and site configuration settings to ensure they are accurate and in line with your requirements.
Save and Apply Changes
Once you've confirmed the settings, save and apply the changes. This step will configure the site and data store according to the settings you've specified.
Test the Configuration
After the configuration is complete, it's essential to test the site and data store to ensure they are functioning correctly. Verify that the XenApp servers can communicate with the data store and that configuration data is being stored and retrieved as expected.
Site Management
You can continue to use the XenApp Management Console to manage and administer your site. This includes tasks like publishing applications, managing policies, and controlling user access.
Configuring the site and data store is a pivotal step in creating a robust and well-organized XenApp environment. The data store centralizes your configuration data, making it accessible to all XenApp servers in your farm, while the site configuration ensures that your XenApp site is properly defined and functional. Proper configuration of these components is crucial for effective application delivery and user management.
Application Publishing
Publishing applications is a fundamental step in setting up your XenApp environment, as it makes applications available to end-users. Whether you're delivering a single application or a suite of software, proper application publishing is essential. Here's a step-by-step guide on how to publish applications in XenApp:
Launch the XenApp Management Console:Open the XenApp Management Console on a server where you've installed the XenApp server role. This is your primary tool for configuring and managing your XenApp environment.
Navigate to Applications:In the XenApp Management Console, navigate to the "Applications" section or a related area, depending on your XenApp version.
Application Publishing Wizard:Look for an option that allows you to publish applications. This may be called "Publish Applications" or a similar name. Select this option to launch the Application Publishing Wizard.
Select Applications:In the wizard, you'll be prompted to select the applications you want to publish. You can choose from a list of installed applications on the server or specify the path to an application executable.
Configure Application Properties:For each application you're publishing, configure its properties. This includes specifying the name that users will see, description, icon, command line, and working directory. You can also configure application shortcuts.
Define Access Control:Set access control for the published application. This includes specifying which users or user groups are allowed to access the application. You can use Active Directory groups or specific users for this purpose.
Configure Session Pre-Launch and Session Reliability (Optional):If desired, configure additional settings like session pre-launch and session reliability. These features can improve user experience by speeding up application launch and ensuring session persistence in case of network interruptions.
Review and Confirm:Review the application publishing settings to ensure they align with your requirements and user access policies.
Publish the Applications:Once you've confirmed the settings, proceed to publish the applications. This step makes the applications available to users within your XenApp environment.
Proper application publishing in XenApp is a core component of delivering software to end-users securely and efficiently. By following these steps, you ensure that users can access the applications they need while maintaining control over who can access them.
User and Group Management
User and group management in XenApp is essential for controlling access, securing resources, and ensuring the right users have access to the right applications. Here's a step-by-step guide on how to manage users and groups in your XenApp environment:
Configure User Access:Configure the access permissions for the added users or groups. You can specify which applications they can access, the servers they can connect to, and their session settings.
Define Policies (Optional):If necessary, you can create policies to enforce specific settings for user or group sessions. Policies can control aspects like printing, drive mapping, and security settings.
Review and Confirm:Review the user and group management settings to ensure they align with your organization's requirements and access policies.
Save and Apply Changes:Once you've confirmed the settings, save and apply the changes. This step configures the user and group access and policies according to your specifications.
Test User Access:After configuring user and group settings, it's crucial to test user access. Verify that users or groups can access the applications and resources you've granted them.
User and Group Management:Continue to use the XenApp Management Console to manage users and groups in your XenApp environment. You can update access permissions, add or remove users, and modify session policies as needed.
Effective user and group management are essential for ensuring that users have the right level of access to resources and applications. By following these steps, you can maintain control over your XenApp environment and enforce access policies that align with your organization's security and operational needs.
Load Balancing and High Availability
Load balancing and high availability are critical considerations when setting up a XenApp environment, especially for ensuring performance and continuous operation. Here's a step-by-step guide on how to implement load balancing and high availability in XenApp:
Assess Your Environment:Before you begin, conduct a thorough assessment of your XenApp environment to understand your load balancing and high availability needs. Consider factors like the number of users, server resources, and geographic locations.
Choose a Load Balancing Solution:Select a load balancing solution that best fits your requirements. Citrix offers NetScaler for load balancing, but other options, like hardware load balancers or software-based load balancers, are available.
Configure Load Balancing:Set up the load balancer according to your chosen solution. This typically involves configuring the load balancer to distribute user connections evenly across multiple XenApp servers.
High Availability Considerations:High availability requires redundancy in your XenApp environment. Consider options like clustering XenApp servers or deploying multiple data centers for geographic redundancy.
Disaster Recovery Plan:Develop a disaster recovery plan that outlines how you'll recover your XenApp environment in case of a catastrophic failure. This may involve data backups, off-site replication, and clear recovery procedures.
Test the Load Balancer and High Availability Setup:After configuring load balancing and high availability, it's crucial to test the setup. Verify that user connections are distributed correctly and that failover mechanisms work as intended.
Load balancing and high availability are vital for delivering applications reliably and efficiently in a XenApp environment. By following these steps, you can ensure that your XenApp environment can handle user demand, recover from failures, and maintain a high level of uptime.
Securing Your XenApp Environment
Securing your XenApp environment is a critical aspect of maintaining the confidentiality, integrity, and availability of your applications and data. Here's a step-by-step guide on how to secure your XenApp environment:
Assess Security Requirements:Begin by assessing your organization's specific security requirements and compliance standards. Determine the sensitivity of the data and applications you're delivering through XenApp.
Implement Network Security Measures:Apply network security measures, such as firewalls and intrusion detection systems, to protect your XenApp servers from unauthorized access and attacks.
Secure Communication with SSL/TLS:Use SSL/TLS encryption to secure communication between XenApp servers and client devices. Ensure that certificates are correctly configured and up-to-date.
Access Control and Authentication:Enforce strict access control by configuring role-based access control (RBAC) and employing strong authentication methods like multi-factor authentication (MFA).
User Training:Educate users about security best practices, including the importance of secure passwords, avoiding phishing attacks, and reporting suspicious activity.
Intrusion Detection and Monitoring:Implement intrusion detection systems and monitoring tools to detect and respond to security incidents and anomalies.
Data Backup and Disaster Recovery:Implement regular data backups and establish a comprehensive disaster recovery plan to ensure data availability in case of data loss or system failure.
By following these steps, you can significantly enhance the security of your XenApp environment, reducing the risk of data breaches, unauthorized access, and other security threats. Security is an ongoing process, and regular reviews and updates are essential to maintaining a secure XenApp deployment.
Conclusion
In conclusion, setting up a XenApp environment is a complex but highly rewarding endeavor that enables organizations to deliver applications and desktops to users efficiently and securely. Throughout this comprehensive guide, we've explored the essential steps involved in the installation and configuration of XenApp, including system requirements, deployment options, setting up the XenApp server role, configuring the License Server, creating a XenApp farm, configuring the site and data store, application publishing, user and group management, load balancing, high availability, and securing your XenApp environment.
As you work through each of these steps, it's crucial to keep in mind the specific needs and goals of your organization. Flexibility is one of the key strengths of XenApp, and it can be adapted to suit a wide range of scenarios, from small businesses to large enterprises. By carefully planning and configuring your XenApp environment, you can harness its capabilities to provide your users with reliable access to the applications and desktops they need, while maintaining the highest levels of security and performance.
With a well-designed and carefully maintained XenApp environment, your organization can streamline application delivery, enhance user productivity, and adapt to the ever-changing landscape of IT and virtualization. Whether you're a seasoned IT professional or a newcomer to XenApp, this guide provides a solid foundation for successfully deploying and managing XenApp within your organization.
Read More
In the ever-evolving landscape of IT and virtualization, organizations seek solutions that empower them to deliver applications to end-users with efficiency, security, and simplicity. Citrix XenApp stands as a stalwart in this endeavor, offering a robust application delivery platform that has revolutionized the way businesses distribute software.
The significance of XenApp extends far beyond its utility as a virtual application delivery solution; it embodies the essence of streamlining productivity and enhancing the end-user experience. With its versatile features, scalability, and capacity to facilitate secure remote access, it's no wonder that countless organizations turn to XenApp as their go-to application delivery solution.
In this comprehensive guide, we'll demystify the installation process, from the prerequisites and initial configuration to the final deployment of your applications. With the help of our clear, easy-to-follow instructions, you'll soon be on your way to harnessing the power of XenApp.
So, whether you're a seasoned IT professional or a novice embarking on the XenApp journey, fasten your seatbelts, as we embark on a journey through the installation process of Citrix XenApp. By the end of this guide, you'll be well on your way to delivering applications effortlessly and securely to your users.
Table of contents
-
System Requirements and Prerequisites
-
XenApp Deployment Options
-
Installing the XenApp Server Role
-
Configuring the License Server
-
Creating a XenApp Farm
-
Configuring Site and Data Store
-
Application Publishing
-
User and Group Management
-
Load Balancing and High Availability
-
Securing Your XenApp Environment
-
Conclusion
System Requirements and Prerequisites
Before diving into the installation process of XenApp, it's crucial to ensure that your environment meets the necessary system requirements and prerequisites. Failing to do so can lead to installation issues, performance problems, or incompatibility. Here's a detailed look at what you need to have in place:
Hardware Requirements:Server Hardware: Ensure that the server or virtual machine you plan to install XenApp on meets the recommended hardware specifications. This includes CPU, RAM, and disk space. Citrix provides specific guidelines based on your expected usage and scalability needs.
Licensing:Acquire XenApp Licenses: Before proceeding with the installation, make sure you have the appropriate licenses for XenApp. The licensing server must be set up and accessible.
Remote Desktop Services (RDS):If you are planning to use XenApp in conjunction with Microsoft Remote Desktop Services (RDS), ensure that RDS is properly configured on your server.
Active Directory Trusts (If Applicable):If your organization uses multiple Active Directory forests or domains, you may need to establish trust relationships between them to facilitate user access.
Before you embark on the XenApp installation journey, it's essential to perform a thorough system assessment to confirm that your environment aligns with these prerequisites. This diligent preparation will set the stage for a smooth and successful XenApp deployment.
XenApp Deployment Options
When it comes to deploying Citrix XenApp, you have several deployment options to choose from, each catering to different business needs and IT infrastructures. Understanding these options is crucial before you start the installation process. Here's an overview of the XenApp deployment options:
On-Premises Deployment:The traditional on-premises deployment involves installing XenApp on your own physical servers or virtual machines within your data center. This option provides full control over your infrastructure but requires ongoing maintenance and resource management.
Cloud-Based Deployment:Citrix offers cloud-based deployment options, allowing you to host XenApp on platforms like Microsoft Azure, Amazon Web Services (AWS), or Google Cloud. Cloud-based deployments offer scalability, flexibility, and the advantage of not having to manage the underlying infrastructure.
Hybrid Deployment:A hybrid deployment combines both on-premises and cloud-based infrastructure. This option is suitable for organizations that want to maintain some applications or data on-premises while leveraging the cloud for scalability and disaster recovery.
XenApp Service on Citrix Cloud:Citrix Cloud provides a management and delivery platform for XenApp. With XenApp Service, you can host your XenApp environment entirely in the cloud, with Citrix managing the infrastructure and updates. This is an excellent option for organizations seeking a fully managed solution.
XenApp Essentials:XenApp Essentials is a Citrix offering specifically designed for Azure. It provides a simplified way to deliver Windows apps from Azure to any device. This option is particularly convenient for organizations already invested in the Microsoft ecosystem.
XenApp in a Microservices Architecture:For organizations looking to modernize their application delivery, microservices architectures can be explored. This approach breaks down application components into microservices that can be easily deployed and scaled.
Geo-Redundant Deployments:If you require high availability and disaster recovery, consider deploying XenApp in multiple geographic regions. This ensures that your applications remain available even if one data center experiences an outage.
The choice of deployment option depends on your organization's specific needs, resources, and long-term strategy. It's essential to evaluate the pros and cons of each option and align it with your business goals before proceeding with the installation. Regardless of the option chosen, understanding the deployment models available will help you make informed decisions during the XenApp installation process.
Installing the XenApp Server Role
Once you've ensured that your system meets the prerequisites and have decided on the deployment model that best suits your organization, the next crucial step is to install the XenApp server role. This process forms the foundation of your XenApp environment. Here's a step-by-step guide on how to do it:
Obtain XenApp Installation Media:Before you begin, ensure you have the necessary XenApp installation files. These can be obtained from Citrix directly or your authorized distributor.
Launch the Installation Wizard:Run the XenApp installation package on the server or virtual machine where you plan to install the XenApp server role.
Choose the Installation Type:You'll typically be presented with installation types such as "Full" and "Custom." Choose "Full" for a typical installation or "Custom" if you want to configure specific options.
Review and Accept the License Agreement:Read through the license agreement carefully and accept the terms if you agree. You cannot proceed without accepting the license agreement.
Specify the Data Store:If you are using a remote SQL database, you'll need to specify the data store. This is where configuration information is stored. Make sure the data store is accessible and properly configured.
Choose Licensing Model:Select your licensing model. You can choose to install the licensing server locally or use a remote Citrix License Server.
Configure Your Farm Settings:Define your XenApp farm's settings, including the farm name, location, and administrator credentials.
Test and Review Settings:Review all the settings you've configured and test the connections to ensure they are functioning correctly.
Begin Installation:Once all settings are verified, start the installation process. The installation wizard will begin configuring the XenApp server role based on your choices.
Installing the XenApp server role is a crucial step in setting up your application delivery environment. Ensuring a successful installation will provide a solid foundation for further configuration and application deployment in your XenApp farm.
Configuring the License Server
Once you've installed the XenApp server role, one of the critical steps in setting up your XenApp environment is configuring the License Server. Proper licensing is essential for ensuring that your XenApp environment is compliant and fully operational. Here's a step-by-step guide on how to configure the License Server:
License Acquisition:Before you can configure the License Server, ensure you have acquired the necessary XenApp licenses. You should have received a license file from Citrix or your authorized distributor.
Launch the License Server Console:On the server where you installed the XenApp server role, locate the Citrix License Server Console and launch it.
Install the License File:In the License Server Console, go to the "Administration" node and select "Install License." Follow the prompts to browse and install your license file. This file contains the licensing information for your XenApp environment.
Allocate Licenses:Once the license file is installed, you'll need to allocate licenses to your XenApp servers. Select the "Allocate Licenses" option and specify the number of licenses to allocate to each server. You can allocate licenses manually or use the License Server's policies for automatic allocation.
Monitor License Usage:Regularly monitor license usage to ensure you remain compliant with your licensing agreement. The License Server Console provides tools to track and report on license usage.
Renew Licenses (As Needed):Keep track of your license expiration dates and renew licenses as necessary to maintain a valid license agreement.
Configuring the License Server is a vital step in the XenApp setup process. It ensures that your XenApp servers have the necessary licenses to deliver applications to end-users. Properly configured licensing not only keeps your environment compliant but also allows you to make the most of the features and capabilities XenApp has to offer.
Creating a XenApp Farm
Creating a XenApp Farm is a fundamental step in setting up your XenApp environment. A XenApp farm is a collection of XenApp servers that work together to deliver applications and desktops to end-users. Here's a step-by-step guide on how to create a XenApp farm:
Plan Your Farm:Before you begin, it's essential to plan your XenApp farm carefully. Consider factors like the number of servers you need, the geographic location of your servers, and the scalability requirements of your organization. Think about redundancy and disaster recovery options as well.
Launch the XenApp Management Console:On a server where you've installed the XenApp server role, launch the XenApp Management Console. This console is your primary interface for configuring and managing your XenApp farm.
Farm Configuration Wizard:In the XenApp Management Console, navigate to "Farm" and click on "Create a new farm" or a similar option, depending on your XenApp version. This will launch the Farm Configuration Wizard.
Enter Farm Information:Follow the prompts in the Farm Configuration Wizard to enter essential information about your farm. This includes specifying the farm name, description, and database server information.
Choose a Data Store:Select the data store option that best fits your needs. You can either use an existing data store or create a new one. The data store stores configuration information for your XenApp farm.
Select the Servers:Specify which servers in your environment will be part of the farm. You can select servers that already have the XenApp server role installed.
Configure Licensing:Associate your XenApp farm with the License Server you've previously configured. Ensure that the farm is properly licensed to run the number of applications and desktops you require.
Farm Database Configuration:Configure the farm database settings, including the database server and credentials. Ensure the database is set up and accessible.
Set Farm Administrators:Define the administrators who will manage the XenApp farm. Assign appropriate permissions and roles to these administrators.
Review and Confirm:Review the information you've entered in the Farm Configuration Wizard to ensure accuracy. Confirm that all settings align with your farm's requirements.
Create the Farm:Once you've reviewed and confirmed the settings, click "Finish" or a similar button to create the XenApp farm. The wizard will begin the process of creating the farm and configuring the servers.
Test and Verify:After the farm is created, test its functionality. Ensure that the servers are communicating properly, and that applications and desktops can be published and accessed.
Farm Management:Use the XenApp Management Console to manage and administer your farm. This includes tasks like publishing applications, configuring policies, and managing users.
Creating a XenApp farm is a crucial step in the setup process, as it forms the backbone of your application delivery environment. Proper planning and configuration will enable you to efficiently deliver applications and desktops to your end-users.
Configuring Site and Data Store
Configuring the site and data store is a pivotal part of setting up a XenApp environment. These components are vital for centralizing configuration data and ensuring the smooth operation of your XenApp deployment. Here's a step-by-step guide on how to configure the site and data store:
Launch the XenApp Management Console
Open the XenApp Management Console on a server where you've installed the XenApp server role. This console is your gateway to configuring and managing your XenApp environment.
Navigate to Farm
In the XenApp Management Console, navigate to the "Farm" section or a related area, depending on your XenApp version.
Select Your Farm
Click on your XenApp farm to access the farm's properties and settings.
Access Site Configuration
In the farm's properties, look for an option related to site configuration or data store. Select this option to access site configuration settings.
Data Store Configuration
In the site configuration, you'll typically find settings related to the data store. Follow the prompts or tabs to configure the data store. This includes specifying the data store location and credentials.
Configure Site Settings
Configure additional site settings, such as the site name, location, and description. These settings help identify and manage your XenApp site within the farm.
Review and Confirm
Review the data store and site configuration settings to ensure they are accurate and in line with your requirements.
Save and Apply Changes
Once you've confirmed the settings, save and apply the changes. This step will configure the site and data store according to the settings you've specified.
Test the Configuration
After the configuration is complete, it's essential to test the site and data store to ensure they are functioning correctly. Verify that the XenApp servers can communicate with the data store and that configuration data is being stored and retrieved as expected.
Site Management
You can continue to use the XenApp Management Console to manage and administer your site. This includes tasks like publishing applications, managing policies, and controlling user access.
Configuring the site and data store is a pivotal step in creating a robust and well-organized XenApp environment. The data store centralizes your configuration data, making it accessible to all XenApp servers in your farm, while the site configuration ensures that your XenApp site is properly defined and functional. Proper configuration of these components is crucial for effective application delivery and user management.
Application Publishing
Publishing applications is a fundamental step in setting up your XenApp environment, as it makes applications available to end-users. Whether you're delivering a single application or a suite of software, proper application publishing is essential. Here's a step-by-step guide on how to publish applications in XenApp:
Launch the XenApp Management Console:Open the XenApp Management Console on a server where you've installed the XenApp server role. This is your primary tool for configuring and managing your XenApp environment.
Navigate to Applications:In the XenApp Management Console, navigate to the "Applications" section or a related area, depending on your XenApp version.
Application Publishing Wizard:Look for an option that allows you to publish applications. This may be called "Publish Applications" or a similar name. Select this option to launch the Application Publishing Wizard.
Select Applications:In the wizard, you'll be prompted to select the applications you want to publish. You can choose from a list of installed applications on the server or specify the path to an application executable.
Configure Application Properties:For each application you're publishing, configure its properties. This includes specifying the name that users will see, description, icon, command line, and working directory. You can also configure application shortcuts.
Define Access Control:Set access control for the published application. This includes specifying which users or user groups are allowed to access the application. You can use Active Directory groups or specific users for this purpose.
Configure Session Pre-Launch and Session Reliability (Optional):If desired, configure additional settings like session pre-launch and session reliability. These features can improve user experience by speeding up application launch and ensuring session persistence in case of network interruptions.
Review and Confirm:Review the application publishing settings to ensure they align with your requirements and user access policies.
Publish the Applications:Once you've confirmed the settings, proceed to publish the applications. This step makes the applications available to users within your XenApp environment.
Proper application publishing in XenApp is a core component of delivering software to end-users securely and efficiently. By following these steps, you ensure that users can access the applications they need while maintaining control over who can access them.
User and Group Management
User and group management in XenApp is essential for controlling access, securing resources, and ensuring the right users have access to the right applications. Here's a step-by-step guide on how to manage users and groups in your XenApp environment:
Configure User Access:Configure the access permissions for the added users or groups. You can specify which applications they can access, the servers they can connect to, and their session settings.
Define Policies (Optional):If necessary, you can create policies to enforce specific settings for user or group sessions. Policies can control aspects like printing, drive mapping, and security settings.
Review and Confirm:Review the user and group management settings to ensure they align with your organization's requirements and access policies.
Save and Apply Changes:Once you've confirmed the settings, save and apply the changes. This step configures the user and group access and policies according to your specifications.
Test User Access:After configuring user and group settings, it's crucial to test user access. Verify that users or groups can access the applications and resources you've granted them.
User and Group Management:Continue to use the XenApp Management Console to manage users and groups in your XenApp environment. You can update access permissions, add or remove users, and modify session policies as needed.
Effective user and group management are essential for ensuring that users have the right level of access to resources and applications. By following these steps, you can maintain control over your XenApp environment and enforce access policies that align with your organization's security and operational needs.
Load Balancing and High Availability
Load balancing and high availability are critical considerations when setting up a XenApp environment, especially for ensuring performance and continuous operation. Here's a step-by-step guide on how to implement load balancing and high availability in XenApp:
Assess Your Environment:Before you begin, conduct a thorough assessment of your XenApp environment to understand your load balancing and high availability needs. Consider factors like the number of users, server resources, and geographic locations.
Choose a Load Balancing Solution:Select a load balancing solution that best fits your requirements. Citrix offers NetScaler for load balancing, but other options, like hardware load balancers or software-based load balancers, are available.
Configure Load Balancing:Set up the load balancer according to your chosen solution. This typically involves configuring the load balancer to distribute user connections evenly across multiple XenApp servers.
High Availability Considerations:High availability requires redundancy in your XenApp environment. Consider options like clustering XenApp servers or deploying multiple data centers for geographic redundancy.
Disaster Recovery Plan:Develop a disaster recovery plan that outlines how you'll recover your XenApp environment in case of a catastrophic failure. This may involve data backups, off-site replication, and clear recovery procedures.
Test the Load Balancer and High Availability Setup:After configuring load balancing and high availability, it's crucial to test the setup. Verify that user connections are distributed correctly and that failover mechanisms work as intended.
Load balancing and high availability are vital for delivering applications reliably and efficiently in a XenApp environment. By following these steps, you can ensure that your XenApp environment can handle user demand, recover from failures, and maintain a high level of uptime.
Securing Your XenApp Environment
Securing your XenApp environment is a critical aspect of maintaining the confidentiality, integrity, and availability of your applications and data. Here's a step-by-step guide on how to secure your XenApp environment:
Assess Security Requirements:Begin by assessing your organization's specific security requirements and compliance standards. Determine the sensitivity of the data and applications you're delivering through XenApp.
Implement Network Security Measures:Apply network security measures, such as firewalls and intrusion detection systems, to protect your XenApp servers from unauthorized access and attacks.
Secure Communication with SSL/TLS:Use SSL/TLS encryption to secure communication between XenApp servers and client devices. Ensure that certificates are correctly configured and up-to-date.
Access Control and Authentication:Enforce strict access control by configuring role-based access control (RBAC) and employing strong authentication methods like multi-factor authentication (MFA).
User Training:Educate users about security best practices, including the importance of secure passwords, avoiding phishing attacks, and reporting suspicious activity.
Intrusion Detection and Monitoring:Implement intrusion detection systems and monitoring tools to detect and respond to security incidents and anomalies.
Data Backup and Disaster Recovery:Implement regular data backups and establish a comprehensive disaster recovery plan to ensure data availability in case of data loss or system failure.
By following these steps, you can significantly enhance the security of your XenApp environment, reducing the risk of data breaches, unauthorized access, and other security threats. Security is an ongoing process, and regular reviews and updates are essential to maintaining a secure XenApp deployment.
Conclusion
In conclusion, setting up a XenApp environment is a complex but highly rewarding endeavor that enables organizations to deliver applications and desktops to users efficiently and securely. Throughout this comprehensive guide, we've explored the essential steps involved in the installation and configuration of XenApp, including system requirements, deployment options, setting up the XenApp server role, configuring the License Server, creating a XenApp farm, configuring the site and data store, application publishing, user and group management, load balancing, high availability, and securing your XenApp environment.
As you work through each of these steps, it's crucial to keep in mind the specific needs and goals of your organization. Flexibility is one of the key strengths of XenApp, and it can be adapted to suit a wide range of scenarios, from small businesses to large enterprises. By carefully planning and configuring your XenApp environment, you can harness its capabilities to provide your users with reliable access to the applications and desktops they need, while maintaining the highest levels of security and performance.
With a well-designed and carefully maintained XenApp environment, your organization can streamline application delivery, enhance user productivity, and adapt to the ever-changing landscape of IT and virtualization. Whether you're a seasoned IT professional or a newcomer to XenApp, this guide provides a solid foundation for successfully deploying and managing XenApp within your organization.
Introduction to Lean Six Sigma Black Belt Certification
Lean Six Sigma is a methodology that combines the principles of Lean and Six Sigma to improve processes, reduce defects, and enhance overall efficiency within an organization. At the heart of this methodology are individuals known as "Black Belts," who are highly trained professionals responsible for leading and managing Lean Six Sigma projects. This introduction will provide an overview of Lean Six Sigma Black Belt certification, its significance, and the key aspects of becoming a Lean Six Sigma Black Belt.
A Lean Six Sigma Black Belt is a professional who has undergone extensive training in Lean and Six Sigma methodologies. They play a pivotal role in process improvement and change management within an organization. Black Belts are typically responsible for leading complex projects, coaching Green Belts and team members, and driving significant improvements in quality, cost, and productivity.
Lean Six Sigma Black Belt certification is a significant achievement that validates your expertise in process improvement and problem-solving. Black Belts play a crucial role in helping organizations streamline operations, reduce defects, and enhance overall efficiency. This certification is a stepping stone to a rewarding career in continuous improvement and change management.
Table of contents
-
Black Belt Certification Requirements
-
Black Belt Training Programs
-
Lean Six Sigma Tools and Techniques
-
Preparing for the Black Belt Certification Exam
-
Real-World Application of Black Belt Skills
-
The Role of a Black Belt in an Organization
-
Lean Six Sigma Project Portfolio
-
Challenges Faced by Black Belt Candidates
-
Industry-Specific Black Belt Certification
-
Continuing Education for Black Belts
-
Conclusion
Black Belt Certification Requirements
Lean Six Sigma Black Belt certification requirements typically vary by certification body and the specific training provider. However, I can provide you with a general overview of the common prerequisites and requirements that are often associated with becoming a Lean Six Sigma Black Belt:
Green Belt Certification: Most Lean Six Sigma Black Belt certification programs require candidates to have previously earned their Green Belt certification. This is because Black Belt certification builds upon the concepts and skills acquired at the Green Belt level. Some organizations may offer combined Green Belt and Black Belt programs, but this is less common.
Work Experience: Candidates are usually expected to have a minimum amount of work experience in roles related to process improvement or quality management. The required years of experience can vary, but it's often in the range of 2 to 3 years.
Training: Completing a specified number of hours of formal training in Lean Six Sigma is typically required. This training can be provided by accredited training organizations or universities. The number of training hours needed may vary but is often around 80-120 hours.
Certification Exam: Candidates must pass a certification exam that assesses their knowledge of Lean Six Sigma concepts and tools. The exam is typically based on the Body of Knowledge (BoK) for Black Belts, which is defined by the certifying body.
Payment of Fees: There are usually fees associated with the certification process, including exam fees and, in some cases, annual maintenance fees to keep the certification current.
Code of Ethics: Candidates may be required to adhere to a code of ethics, committing to uphold the principles and standards of Lean Six Sigma in their professional practice.
As of my knowledge cutoff date in September 2021, some well-known organizations that offer Lean Six Sigma Black Belt certification include ASQ (American Society for Quality), IASSC (International Association for Six Sigma Certification), and various training providers. Keep in mind that certification requirements and options may have evolved since that time, so it's advisable to check with the relevant organizations for the most up-to-date information.
Black Belt Training Programs
Lean Six Sigma Black Belt training programs are designed to equip individuals with the knowledge, skills, and tools needed to effectively lead process improvement projects, mentor Green Belts, and drive significant changes within an organization. These programs are offered by a variety of organizations, including universities, training providers, and certification bodies. Below, I'll provide an overview of what you can typically expect from Black Belt training programs:
Comprehensive Curriculum: Black Belt training programs cover a wide range of Lean and Six Sigma concepts, methodologies, and tools. Participants can expect to dive deep into topics like DMAIC (Define, Measure, Analyze, Improve, Control), statistical analysis, process mapping, root cause analysis, and more.
Duration: The duration of Black Belt training can vary depending on the program and the organization offering it. It typically ranges from several weeks to several months. Some programs are more intensive, while others are designed to accommodate participants who may be working full-time.
Project-Based Learning: Many Black Belt training programs include a hands-on project component. Participants are required to complete one or more real-world improvement projects to apply the concepts they've learned. This practical experience is a key element of Black Belt training.
Certified Instructors: Training programs are usually led by experienced Lean Six Sigma professionals or certified instructors who can provide guidance and support throughout the learning process.
Networking Opportunities: Some training programs facilitate networking and collaboration among participants, allowing them to share experiences and learn from one another.
Certification Support: Many Black Belt training programs are designed to prepare individuals for certification exams, and they may include guidance on the certification process, eligibility requirements, and registration.
Before enrolling in a Black Belt training program, it's essential to consider your specific career goals, the reputation of the program, and your preferred mode of learning (e.g., classroom or online). Additionally, you should check whether the program aligns with the certification body you plan to seek certification from (e.g., ASQ, IASSC, etc.), as different bodies may have slightly different curriculum requirements.
Lean Six Sigma Tools and Techniques
Lean Six Sigma is a methodology that utilizes a variety of tools and techniques to improve processes, reduce defects, and enhance efficiency. Black Belts are trained to apply these tools and techniques effectively in their projects. Here's an overview of some of the key Lean Six Sigma tools and techniques that Black Belts commonly use:
Process Mapping:Techniques like flowcharts and value stream maps are used to visually represent and understand the process, highlighting areas for improvement.
Cause-and-Effect Diagram (Fishbone or Ishikawa Diagram):This tool helps identify potential causes for a specific problem or effect, categorizing them into major categories.
Statistical Process Control (SPC):Statistical techniques are used to monitor and control the process to maintain its stability and predictability.
Regression Analysis:This statistical tool is used to identify and quantify relationships between variables, helping determine which factors have the most significant impact on a process.
Design of Experiments (DOE):DOE is a structured approach to experimentation that helps optimize processes and determine the ideal settings for process variables.
Control Charts:Control charts are used to monitor process performance over time and identify variations and trends.
Pareto Analysis:This tool helps identify and prioritize the most significant factors contributing to a problem.
Kanban and Pull Systems:Tools used in Lean to manage and control workflow, ensuring that work is pulled only as needed.
5S (Sort, Set in order, Shine, Standardize, Sustain):A methodology for organizing and maintaining a clean, efficient, and safe workplace.
These are just a selection of the tools and techniques that Lean Six Sigma Black Belts employ to analyze, optimize, and control processes. The choice of tools and techniques depends on the specific project and the nature of the problem being addressed. Black Belts are trained to use these tools effectively to drive process improvements and achieve the desired outcomes.
Preparing for the Black Belt Certification Exam
Preparing for the Lean Six Sigma Black Belt certification exam is a significant undertaking, as it requires a strong understanding of Lean and Six Sigma principles, methodologies, and tools. Here are steps and tips to help you prepare effectively for the exam:
Understand the Exam Structure:Begin by understanding the format of the Black Belt certification exam. Is it multiple-choice, essay-based, or a combination of question types? Knowing the structure will help you plan your study strategy.
Choose the Right Study Materials:Invest in reputable study materials. This may include textbooks, online courses, practice exams, and reference guides. Ensure that the materials align with the BoK.
Take an Official Course:Consider enrolling in an official Lean Six Sigma Black Belt training program, especially if you haven't already completed a comprehensive Green Belt program. These courses provide structured content and often include exam preparation.
Review and Revise:Regularly revisit and revise the topics you've studied to reinforce your understanding and knowledge retention.
Focus on Problem-Solving:Lean Six Sigma is about practical problem-solving. Practice solving real-world problems and applying the methodology.
Stay Calm and Confident:As the exam date approaches, stay calm and confident. Stress can hinder your performance. Review your notes and practice questions, but also take time to relax and rest.
Plan for Exam Day:Ensure you know the logistics of the exam, such as location, time, required identification, and any materials you're allowed to bring. Arrive early and well-rested on exam day.
Remember that Black Belt certification exams are challenging, and preparation is crucial. Take your time to understand the material thoroughly and practice using Lean and Six Sigma tools effectively. The more you practice, the more confident and well-prepared you'll be when you sit for the exam.
Real-World Application of Black Belt Skills
Lean Six Sigma Black Belts are highly trained professionals with expertise in process improvement, data analysis, and problem-solving. Their skills find application in various industries and organizations. Here are some real-world examples of how Black Belt skills are applied:
Manufacturing:Black Belts can lead projects to reduce defects and improve efficiency in manufacturing processes. For example, they might optimize a production line to reduce cycle time, increase product quality, and reduce waste.
Healthcare:In healthcare, Black Belts can improve patient care processes. They might work on reducing hospital wait times, decreasing medication errors, or improving the accuracy of medical billing.
Finance:Black Belts in the financial sector might focus on reducing errors in financial transactions, streamlining approval processes, and optimizing risk assessment methodologies.
Supply Chain and Logistics:They can optimize inventory management, reduce lead times, and improve the accuracy of demand forecasting, leading to cost savings and improved customer service.
Service Industries:In service-based businesses like banking, Black Belts might work on improving customer service processes, reducing customer wait times, and enhancing the efficiency of call centers.
Aerospace and Defense:Black Belts can lead projects to reduce defects in the manufacturing of aerospace components, improve maintenance processes, and enhance quality control in defense projects.
The real-world application of Black Belt skills involves identifying process inefficiencies, conducting data-driven analyses, implementing improvements, and sustaining these changes. Black Belts work closely with teams, stakeholders, and leadership to achieve tangible results, such as cost savings, quality improvements, and enhanced customer satisfaction. Their expertise plays a vital role in helping organizations achieve their strategic goals and stay competitive in a dynamic business environment.
The Role of a Black Belt in an Organization
The role of a Lean Six Sigma Black Belt in an organization is pivotal in driving process improvement, enhancing operational efficiency, and achieving strategic goals. Black Belts serve as leaders, mentors, and experts in Lean Six Sigma methodologies. Their responsibilities and contributions to the organization are multifaceted:
Project Leadership: Black Belts lead and manage Lean Six Sigma projects within the organization. They are responsible for selecting, scoping, planning, and executing projects aimed at improving specific processes and achieving predefined goals. Black Belts ensure that projects are completed on time, within budget, and with the desired outcomes.
Problem Solving: They are skilled problem solvers who use data-driven approaches and a wide array of Lean and Six Sigma tools to identify the root causes of process issues and defects. They work to develop and implement effective solutions to these problems.
Mentoring and Coaching: Black Belts play a critical role in mentoring and coaching Green Belts, Yellow Belts, and other team members involved in Lean Six Sigma projects. They provide guidance, support, and knowledge transfer to help individuals build their process improvement skills.
Data Analysis: They are proficient in statistical analysis and data interpretation. Black Belts use data to measure process performance, identify variations, and quantify the impact of process improvements.
Change Management: Implementing process improvements often requires changes in procedures, roles, and workflows. Black Belts are responsible for leading and facilitating these changes, ensuring that they are smoothly integrated into the organization.
Cost Reduction and Efficiency: Black Belts drive efforts to reduce costs and increase operational efficiency by eliminating waste, optimizing processes, and streamlining workflows. These improvements lead to direct financial savings for the organization.
Sustainability: They are responsible for ensuring that process improvements are sustained over time, preventing regression to previous states.
The role of a Black Belt is dynamic, and their contributions can lead to significant improvements in an organization's processes, customer satisfaction, financial performance, and competitiveness. Their work supports the organization's ability to adapt to changing market conditions and achieve long-term success.
Lean Six Sigma Project Portfolio
A Lean Six Sigma project portfolio is a collection of projects within an organization that are aligned with the goals and strategies of the business and are aimed at improving various processes and functions. These projects are typically managed and overseen by Lean Six Sigma professionals, including Black Belts and Master Black Belts. The portfolio approach ensures that process improvement efforts are systematic, coordinated, and focused on delivering tangible results. Here are key aspects of a Lean Six Sigma project portfolio:
Project Selection: Projects within the portfolio are carefully selected based on their alignment with the organization's strategic objectives, potential impact, and resources available. Selection criteria may include factors like potential cost savings, customer satisfaction improvements, and operational efficiency gains.
Strategic Alignment: The projects within the portfolio should directly support the organization's strategic goals. This ensures that Lean Six Sigma initiatives contribute to the overall success of the business.
Diverse Project Types: The portfolio typically includes a mix of projects, such as process optimization, defect reduction, cost reduction, cycle time reduction, and quality improvement, among others. This diversity helps address various aspects of the business.
Project Management: Each project in the portfolio is assigned a project manager, often a Black Belt, who is responsible for overseeing the project, managing the team, and ensuring that it stays on track and within scope.
Measurement and Metrics: Key performance metrics and measures are established for each project to track progress and assess the impact of process improvements.
Reporting and Communication: Regular reporting and communication mechanisms are put in place to keep stakeholders informed about the status of projects and their outcomes.
A well-managed Lean Six Sigma project portfolio helps organizations systematically and strategically drive improvements in various processes, leading to cost savings, enhanced quality, and better customer satisfaction. It allows organizations to focus their efforts on the most critical areas, ensures that resources are used efficiently, and creates a culture of continuous improvement.
Challenges Faced by Black Belt Candidates
Becoming a Lean Six Sigma Black Belt is a rigorous and challenging process, and candidates often encounter various obstacles and difficulties along the way. Here are some common challenges faced by Black Belt candidates:
Complexity of the Material: The Lean Six Sigma Body of Knowledge can be complex and highly technical. Candidates must master a wide range of statistical tools, methodologies, and concepts, which can be challenging for those without prior experience in the field.
Time Commitment: Preparing for Black Belt certification can be time-consuming, especially when candidates are working full-time. Balancing work, study, and personal life can be a significant challenge.
Project Leadership: Leading Lean Six Sigma projects requires not only technical knowledge but also leadership and project management skills. Some candidates may struggle with the transition from a technical role to a leadership role.
Data Analysis: Data analysis is a fundamental component of Lean Six Sigma, and candidates often find it challenging to gather, analyze, and interpret data effectively.
Resource Allocation: Securing the necessary resources, including time, personnel, and data, for projects can be difficult, especially if the organization is resource-constrained.
Resistance to Change: Implementing process improvements can face resistance from employees who are comfortable with the existing processes. Managing change and gaining buy-in from stakeholders can be a challenge.
Sustaining Improvements: Ensuring that process improvements are sustained over the long term can be a challenge, as there may be resistance to reverting to old practices.
Despite these challenges, the journey to becoming a Lean Six Sigma Black Belt can be highly rewarding. With determination, perseverance, and a supportive network, many candidates successfully navigate these obstacles and go on to make significant contributions to their organizations through process improvements and problem-solving.
Industry-Specific Black Belt Certification
Industry-specific Black Belt certification programs are designed to train and certify Lean Six Sigma Black Belts with specialized knowledge and expertise tailored to a particular industry or sector. These certifications acknowledge the unique challenges and requirements of specific industries and aim to equip professionals with the skills needed to drive process improvement and quality management within their specialized field. Here are a few examples of industry-specific Black Belt certifications:
Healthcare Black Belt Certification:This certification is designed for professionals in the healthcare industry, including hospitals, clinics, and healthcare providers. It focuses on addressing issues related to patient care, process efficiency, and regulatory compliance.
Pharmaceutical Black Belt Certification:Pharmaceutical Black Belts are trained to apply Lean Six Sigma methodologies to address quality control, manufacturing, and regulatory compliance issues specific to pharmaceutical production.
Aerospace and Defense Black Belt Certification:This certification program is tailored to the aerospace and defense industry, where professionals work on improving the quality and efficiency of production, maintenance, and supply chain processes.
Retail Black Belt Certification:Retail Black Belts work on improving inventory management, supply chain, customer service, and store operations in the retail industry.
Telecommunications Black Belt Certification:Professionals in the telecommunications sector can obtain specialized certification to address challenges related to network performance, customer support, and service quality.
Automotive Black Belt Certification:Automotive Black Belts work on enhancing quality control and process efficiency in the automotive industry, including manufacturing and supply chain operations.
Industry-specific Black Belt certification programs often include case studies, projects, and examples relevant to the particular sector, ensuring that candidates are well-equipped to address industry-specific challenges. These certifications are valuable for professionals who want to specialize in their industry and make a significant impact through Lean Six Sigma methodology. It's essential to research and choose a certification program that aligns with your industry and career goals.
Continuing Education for Black Belts
Continuing education is essential for Lean Six Sigma Black Belts to stay current with industry trends, expand their knowledge, and further develop their skills. It also helps Black Belts continue to add value to their organizations by driving ongoing process improvements. Here are some key aspects of continuing education for Black Belts:
Recertification: Many Lean Six Sigma certification bodies, such as ASQ and IASSC, require Black Belts to recertify periodically. This typically involves earning a certain number of Continuing Education Units (CEUs) or Professional Development Units (PDUs) over a set period, often three years.
Advanced Training: Black Belts can pursue advanced training, such as Master Black Belt certification. This level of certification involves a higher level of expertise and leadership within the organization's Lean Six Sigma program.
Specialized Training: Depending on their industry or organization, Black Belts can undertake specialized training in areas like data analytics, project management, change management, or specific tools and methodologies relevant to their field.
Cross-Functional Training: To facilitate cross-functional teamwork and collaboration, Black Belts can engage in training programs that help them understand the perspectives and needs of various departments and teams within the organization.
Networking and Communities of Practice: Black Belts can join professional organizations, attend conferences, and participate in communities of practice related to Lean Six Sigma. These forums provide opportunities to learn from peers, share experiences, and stay updated on industry trends.
Advanced Problem-Solving Techniques: Black Belts can deepen their problem-solving skills by learning advanced techniques and approaches to tackle complex challenges.
Soft Skills Development: Enhancing soft skills, such as communication, negotiation, and conflict resolution, is important for effective leadership and teamwork.
Organization-Specific Training: Organizations may provide or support training and development programs tailored to their specific needs and industry.
Continuing education is an ongoing process that ensures Black Belts remain at the forefront of Lean Six Sigma practices and can adapt to evolving business and industry demands. It's an investment in personal and professional growth that benefits both the individual and the organization.
Conclusion
In conclusion, Lean Six Sigma Black Belts play a crucial role in organizations by driving process improvement, optimizing operations, and delivering significant results. They are highly trained professionals with expertise in Lean and Six Sigma methodologies, statistical analysis, and problem-solving. Their responsibilities encompass project leadership, mentoring, data analysis, and fostering a culture of continuous improvement.
Black Belts undergo rigorous training and certification to equip themselves with the knowledge and skills needed for their roles. Their work can have a profound impact on an organization, leading to cost savings, quality improvements, and enhanced customer satisfaction.
Challenges faced by Black Belt candidates include the complexity of the material, the time commitment, and the need to transition into a leadership role. However, with dedication and support, candidates can successfully navigate these challenges and contribute to their organizations' success.
Continuing education is vital for Black Belts to stay current and further their professional development. This includes recertification, advanced training, specialized and cross-functional education, and engagement in communities of practice.
Whether in healthcare, manufacturing, finance, or any other industry, the skills and expertise of Lean Six Sigma Black Belts are invaluable for organizations striving for continuous improvement and operational excellence.
Read More
Lean Six Sigma is a methodology that combines the principles of Lean and Six Sigma to improve processes, reduce defects, and enhance overall efficiency within an organization. At the heart of this methodology are individuals known as "Black Belts," who are highly trained professionals responsible for leading and managing Lean Six Sigma projects. This introduction will provide an overview of Lean Six Sigma Black Belt certification, its significance, and the key aspects of becoming a Lean Six Sigma Black Belt.
A Lean Six Sigma Black Belt is a professional who has undergone extensive training in Lean and Six Sigma methodologies. They play a pivotal role in process improvement and change management within an organization. Black Belts are typically responsible for leading complex projects, coaching Green Belts and team members, and driving significant improvements in quality, cost, and productivity.
Lean Six Sigma Black Belt certification is a significant achievement that validates your expertise in process improvement and problem-solving. Black Belts play a crucial role in helping organizations streamline operations, reduce defects, and enhance overall efficiency. This certification is a stepping stone to a rewarding career in continuous improvement and change management.
Table of contents
-
Black Belt Certification Requirements
-
Black Belt Training Programs
-
Lean Six Sigma Tools and Techniques
-
Preparing for the Black Belt Certification Exam
-
Real-World Application of Black Belt Skills
-
The Role of a Black Belt in an Organization
-
Lean Six Sigma Project Portfolio
-
Challenges Faced by Black Belt Candidates
-
Industry-Specific Black Belt Certification
-
Continuing Education for Black Belts
-
Conclusion
Black Belt Certification Requirements
Lean Six Sigma Black Belt certification requirements typically vary by certification body and the specific training provider. However, I can provide you with a general overview of the common prerequisites and requirements that are often associated with becoming a Lean Six Sigma Black Belt:
Green Belt Certification: Most Lean Six Sigma Black Belt certification programs require candidates to have previously earned their Green Belt certification. This is because Black Belt certification builds upon the concepts and skills acquired at the Green Belt level. Some organizations may offer combined Green Belt and Black Belt programs, but this is less common.
Work Experience: Candidates are usually expected to have a minimum amount of work experience in roles related to process improvement or quality management. The required years of experience can vary, but it's often in the range of 2 to 3 years.
Training: Completing a specified number of hours of formal training in Lean Six Sigma is typically required. This training can be provided by accredited training organizations or universities. The number of training hours needed may vary but is often around 80-120 hours.
Certification Exam: Candidates must pass a certification exam that assesses their knowledge of Lean Six Sigma concepts and tools. The exam is typically based on the Body of Knowledge (BoK) for Black Belts, which is defined by the certifying body.
Payment of Fees: There are usually fees associated with the certification process, including exam fees and, in some cases, annual maintenance fees to keep the certification current.
Code of Ethics: Candidates may be required to adhere to a code of ethics, committing to uphold the principles and standards of Lean Six Sigma in their professional practice.
As of my knowledge cutoff date in September 2021, some well-known organizations that offer Lean Six Sigma Black Belt certification include ASQ (American Society for Quality), IASSC (International Association for Six Sigma Certification), and various training providers. Keep in mind that certification requirements and options may have evolved since that time, so it's advisable to check with the relevant organizations for the most up-to-date information.
Black Belt Training Programs
Lean Six Sigma Black Belt training programs are designed to equip individuals with the knowledge, skills, and tools needed to effectively lead process improvement projects, mentor Green Belts, and drive significant changes within an organization. These programs are offered by a variety of organizations, including universities, training providers, and certification bodies. Below, I'll provide an overview of what you can typically expect from Black Belt training programs:
Comprehensive Curriculum: Black Belt training programs cover a wide range of Lean and Six Sigma concepts, methodologies, and tools. Participants can expect to dive deep into topics like DMAIC (Define, Measure, Analyze, Improve, Control), statistical analysis, process mapping, root cause analysis, and more.
Duration: The duration of Black Belt training can vary depending on the program and the organization offering it. It typically ranges from several weeks to several months. Some programs are more intensive, while others are designed to accommodate participants who may be working full-time.
Project-Based Learning: Many Black Belt training programs include a hands-on project component. Participants are required to complete one or more real-world improvement projects to apply the concepts they've learned. This practical experience is a key element of Black Belt training.
Certified Instructors: Training programs are usually led by experienced Lean Six Sigma professionals or certified instructors who can provide guidance and support throughout the learning process.
Networking Opportunities: Some training programs facilitate networking and collaboration among participants, allowing them to share experiences and learn from one another.
Certification Support: Many Black Belt training programs are designed to prepare individuals for certification exams, and they may include guidance on the certification process, eligibility requirements, and registration.
Before enrolling in a Black Belt training program, it's essential to consider your specific career goals, the reputation of the program, and your preferred mode of learning (e.g., classroom or online). Additionally, you should check whether the program aligns with the certification body you plan to seek certification from (e.g., ASQ, IASSC, etc.), as different bodies may have slightly different curriculum requirements.
Lean Six Sigma Tools and Techniques
Lean Six Sigma is a methodology that utilizes a variety of tools and techniques to improve processes, reduce defects, and enhance efficiency. Black Belts are trained to apply these tools and techniques effectively in their projects. Here's an overview of some of the key Lean Six Sigma tools and techniques that Black Belts commonly use:
Process Mapping:Techniques like flowcharts and value stream maps are used to visually represent and understand the process, highlighting areas for improvement.
Cause-and-Effect Diagram (Fishbone or Ishikawa Diagram):This tool helps identify potential causes for a specific problem or effect, categorizing them into major categories.
Statistical Process Control (SPC):Statistical techniques are used to monitor and control the process to maintain its stability and predictability.
Regression Analysis:This statistical tool is used to identify and quantify relationships between variables, helping determine which factors have the most significant impact on a process.
Design of Experiments (DOE):DOE is a structured approach to experimentation that helps optimize processes and determine the ideal settings for process variables.
Control Charts:Control charts are used to monitor process performance over time and identify variations and trends.
Pareto Analysis:This tool helps identify and prioritize the most significant factors contributing to a problem.
Kanban and Pull Systems:Tools used in Lean to manage and control workflow, ensuring that work is pulled only as needed.
5S (Sort, Set in order, Shine, Standardize, Sustain):A methodology for organizing and maintaining a clean, efficient, and safe workplace.
These are just a selection of the tools and techniques that Lean Six Sigma Black Belts employ to analyze, optimize, and control processes. The choice of tools and techniques depends on the specific project and the nature of the problem being addressed. Black Belts are trained to use these tools effectively to drive process improvements and achieve the desired outcomes.
Preparing for the Black Belt Certification Exam
Preparing for the Lean Six Sigma Black Belt certification exam is a significant undertaking, as it requires a strong understanding of Lean and Six Sigma principles, methodologies, and tools. Here are steps and tips to help you prepare effectively for the exam:
Understand the Exam Structure:Begin by understanding the format of the Black Belt certification exam. Is it multiple-choice, essay-based, or a combination of question types? Knowing the structure will help you plan your study strategy.
Choose the Right Study Materials:Invest in reputable study materials. This may include textbooks, online courses, practice exams, and reference guides. Ensure that the materials align with the BoK.
Take an Official Course:Consider enrolling in an official Lean Six Sigma Black Belt training program, especially if you haven't already completed a comprehensive Green Belt program. These courses provide structured content and often include exam preparation.
Review and Revise:Regularly revisit and revise the topics you've studied to reinforce your understanding and knowledge retention.
Focus on Problem-Solving:Lean Six Sigma is about practical problem-solving. Practice solving real-world problems and applying the methodology.
Stay Calm and Confident:As the exam date approaches, stay calm and confident. Stress can hinder your performance. Review your notes and practice questions, but also take time to relax and rest.
Plan for Exam Day:Ensure you know the logistics of the exam, such as location, time, required identification, and any materials you're allowed to bring. Arrive early and well-rested on exam day.
Remember that Black Belt certification exams are challenging, and preparation is crucial. Take your time to understand the material thoroughly and practice using Lean and Six Sigma tools effectively. The more you practice, the more confident and well-prepared you'll be when you sit for the exam.
Real-World Application of Black Belt Skills
Lean Six Sigma Black Belts are highly trained professionals with expertise in process improvement, data analysis, and problem-solving. Their skills find application in various industries and organizations. Here are some real-world examples of how Black Belt skills are applied:
Manufacturing:Black Belts can lead projects to reduce defects and improve efficiency in manufacturing processes. For example, they might optimize a production line to reduce cycle time, increase product quality, and reduce waste.
Healthcare:In healthcare, Black Belts can improve patient care processes. They might work on reducing hospital wait times, decreasing medication errors, or improving the accuracy of medical billing.
Finance:Black Belts in the financial sector might focus on reducing errors in financial transactions, streamlining approval processes, and optimizing risk assessment methodologies.
Supply Chain and Logistics:They can optimize inventory management, reduce lead times, and improve the accuracy of demand forecasting, leading to cost savings and improved customer service.
Service Industries:In service-based businesses like banking, Black Belts might work on improving customer service processes, reducing customer wait times, and enhancing the efficiency of call centers.
Aerospace and Defense:Black Belts can lead projects to reduce defects in the manufacturing of aerospace components, improve maintenance processes, and enhance quality control in defense projects.
The real-world application of Black Belt skills involves identifying process inefficiencies, conducting data-driven analyses, implementing improvements, and sustaining these changes. Black Belts work closely with teams, stakeholders, and leadership to achieve tangible results, such as cost savings, quality improvements, and enhanced customer satisfaction. Their expertise plays a vital role in helping organizations achieve their strategic goals and stay competitive in a dynamic business environment.
The Role of a Black Belt in an Organization
The role of a Lean Six Sigma Black Belt in an organization is pivotal in driving process improvement, enhancing operational efficiency, and achieving strategic goals. Black Belts serve as leaders, mentors, and experts in Lean Six Sigma methodologies. Their responsibilities and contributions to the organization are multifaceted:
Project Leadership: Black Belts lead and manage Lean Six Sigma projects within the organization. They are responsible for selecting, scoping, planning, and executing projects aimed at improving specific processes and achieving predefined goals. Black Belts ensure that projects are completed on time, within budget, and with the desired outcomes.
Problem Solving: They are skilled problem solvers who use data-driven approaches and a wide array of Lean and Six Sigma tools to identify the root causes of process issues and defects. They work to develop and implement effective solutions to these problems.
Mentoring and Coaching: Black Belts play a critical role in mentoring and coaching Green Belts, Yellow Belts, and other team members involved in Lean Six Sigma projects. They provide guidance, support, and knowledge transfer to help individuals build their process improvement skills.
Data Analysis: They are proficient in statistical analysis and data interpretation. Black Belts use data to measure process performance, identify variations, and quantify the impact of process improvements.
Change Management: Implementing process improvements often requires changes in procedures, roles, and workflows. Black Belts are responsible for leading and facilitating these changes, ensuring that they are smoothly integrated into the organization.
Cost Reduction and Efficiency: Black Belts drive efforts to reduce costs and increase operational efficiency by eliminating waste, optimizing processes, and streamlining workflows. These improvements lead to direct financial savings for the organization.
Sustainability: They are responsible for ensuring that process improvements are sustained over time, preventing regression to previous states.
The role of a Black Belt is dynamic, and their contributions can lead to significant improvements in an organization's processes, customer satisfaction, financial performance, and competitiveness. Their work supports the organization's ability to adapt to changing market conditions and achieve long-term success.
Lean Six Sigma Project Portfolio
A Lean Six Sigma project portfolio is a collection of projects within an organization that are aligned with the goals and strategies of the business and are aimed at improving various processes and functions. These projects are typically managed and overseen by Lean Six Sigma professionals, including Black Belts and Master Black Belts. The portfolio approach ensures that process improvement efforts are systematic, coordinated, and focused on delivering tangible results. Here are key aspects of a Lean Six Sigma project portfolio:
Project Selection: Projects within the portfolio are carefully selected based on their alignment with the organization's strategic objectives, potential impact, and resources available. Selection criteria may include factors like potential cost savings, customer satisfaction improvements, and operational efficiency gains.
Strategic Alignment: The projects within the portfolio should directly support the organization's strategic goals. This ensures that Lean Six Sigma initiatives contribute to the overall success of the business.
Diverse Project Types: The portfolio typically includes a mix of projects, such as process optimization, defect reduction, cost reduction, cycle time reduction, and quality improvement, among others. This diversity helps address various aspects of the business.
Project Management: Each project in the portfolio is assigned a project manager, often a Black Belt, who is responsible for overseeing the project, managing the team, and ensuring that it stays on track and within scope.
Measurement and Metrics: Key performance metrics and measures are established for each project to track progress and assess the impact of process improvements.
Reporting and Communication: Regular reporting and communication mechanisms are put in place to keep stakeholders informed about the status of projects and their outcomes.
A well-managed Lean Six Sigma project portfolio helps organizations systematically and strategically drive improvements in various processes, leading to cost savings, enhanced quality, and better customer satisfaction. It allows organizations to focus their efforts on the most critical areas, ensures that resources are used efficiently, and creates a culture of continuous improvement.
Challenges Faced by Black Belt Candidates
Becoming a Lean Six Sigma Black Belt is a rigorous and challenging process, and candidates often encounter various obstacles and difficulties along the way. Here are some common challenges faced by Black Belt candidates:
Complexity of the Material: The Lean Six Sigma Body of Knowledge can be complex and highly technical. Candidates must master a wide range of statistical tools, methodologies, and concepts, which can be challenging for those without prior experience in the field.
Time Commitment: Preparing for Black Belt certification can be time-consuming, especially when candidates are working full-time. Balancing work, study, and personal life can be a significant challenge.
Project Leadership: Leading Lean Six Sigma projects requires not only technical knowledge but also leadership and project management skills. Some candidates may struggle with the transition from a technical role to a leadership role.
Data Analysis: Data analysis is a fundamental component of Lean Six Sigma, and candidates often find it challenging to gather, analyze, and interpret data effectively.
Resource Allocation: Securing the necessary resources, including time, personnel, and data, for projects can be difficult, especially if the organization is resource-constrained.
Resistance to Change: Implementing process improvements can face resistance from employees who are comfortable with the existing processes. Managing change and gaining buy-in from stakeholders can be a challenge.
Sustaining Improvements: Ensuring that process improvements are sustained over the long term can be a challenge, as there may be resistance to reverting to old practices.
Despite these challenges, the journey to becoming a Lean Six Sigma Black Belt can be highly rewarding. With determination, perseverance, and a supportive network, many candidates successfully navigate these obstacles and go on to make significant contributions to their organizations through process improvements and problem-solving.
Industry-Specific Black Belt Certification
Industry-specific Black Belt certification programs are designed to train and certify Lean Six Sigma Black Belts with specialized knowledge and expertise tailored to a particular industry or sector. These certifications acknowledge the unique challenges and requirements of specific industries and aim to equip professionals with the skills needed to drive process improvement and quality management within their specialized field. Here are a few examples of industry-specific Black Belt certifications:
Healthcare Black Belt Certification:This certification is designed for professionals in the healthcare industry, including hospitals, clinics, and healthcare providers. It focuses on addressing issues related to patient care, process efficiency, and regulatory compliance.
Pharmaceutical Black Belt Certification:Pharmaceutical Black Belts are trained to apply Lean Six Sigma methodologies to address quality control, manufacturing, and regulatory compliance issues specific to pharmaceutical production.
Aerospace and Defense Black Belt Certification:This certification program is tailored to the aerospace and defense industry, where professionals work on improving the quality and efficiency of production, maintenance, and supply chain processes.
Retail Black Belt Certification:Retail Black Belts work on improving inventory management, supply chain, customer service, and store operations in the retail industry.
Telecommunications Black Belt Certification:Professionals in the telecommunications sector can obtain specialized certification to address challenges related to network performance, customer support, and service quality.
Automotive Black Belt Certification:Automotive Black Belts work on enhancing quality control and process efficiency in the automotive industry, including manufacturing and supply chain operations.
Industry-specific Black Belt certification programs often include case studies, projects, and examples relevant to the particular sector, ensuring that candidates are well-equipped to address industry-specific challenges. These certifications are valuable for professionals who want to specialize in their industry and make a significant impact through Lean Six Sigma methodology. It's essential to research and choose a certification program that aligns with your industry and career goals.
Continuing Education for Black Belts
Continuing education is essential for Lean Six Sigma Black Belts to stay current with industry trends, expand their knowledge, and further develop their skills. It also helps Black Belts continue to add value to their organizations by driving ongoing process improvements. Here are some key aspects of continuing education for Black Belts:
Recertification: Many Lean Six Sigma certification bodies, such as ASQ and IASSC, require Black Belts to recertify periodically. This typically involves earning a certain number of Continuing Education Units (CEUs) or Professional Development Units (PDUs) over a set period, often three years.
Advanced Training: Black Belts can pursue advanced training, such as Master Black Belt certification. This level of certification involves a higher level of expertise and leadership within the organization's Lean Six Sigma program.
Specialized Training: Depending on their industry or organization, Black Belts can undertake specialized training in areas like data analytics, project management, change management, or specific tools and methodologies relevant to their field.
Cross-Functional Training: To facilitate cross-functional teamwork and collaboration, Black Belts can engage in training programs that help them understand the perspectives and needs of various departments and teams within the organization.
Networking and Communities of Practice: Black Belts can join professional organizations, attend conferences, and participate in communities of practice related to Lean Six Sigma. These forums provide opportunities to learn from peers, share experiences, and stay updated on industry trends.
Advanced Problem-Solving Techniques: Black Belts can deepen their problem-solving skills by learning advanced techniques and approaches to tackle complex challenges.
Soft Skills Development: Enhancing soft skills, such as communication, negotiation, and conflict resolution, is important for effective leadership and teamwork.
Organization-Specific Training: Organizations may provide or support training and development programs tailored to their specific needs and industry.
Continuing education is an ongoing process that ensures Black Belts remain at the forefront of Lean Six Sigma practices and can adapt to evolving business and industry demands. It's an investment in personal and professional growth that benefits both the individual and the organization.
Conclusion
In conclusion, Lean Six Sigma Black Belts play a crucial role in organizations by driving process improvement, optimizing operations, and delivering significant results. They are highly trained professionals with expertise in Lean and Six Sigma methodologies, statistical analysis, and problem-solving. Their responsibilities encompass project leadership, mentoring, data analysis, and fostering a culture of continuous improvement.
Black Belts undergo rigorous training and certification to equip themselves with the knowledge and skills needed for their roles. Their work can have a profound impact on an organization, leading to cost savings, quality improvements, and enhanced customer satisfaction.
Challenges faced by Black Belt candidates include the complexity of the material, the time commitment, and the need to transition into a leadership role. However, with dedication and support, candidates can successfully navigate these challenges and contribute to their organizations' success.
Continuing education is vital for Black Belts to stay current and further their professional development. This includes recertification, advanced training, specialized and cross-functional education, and engagement in communities of practice.
Whether in healthcare, manufacturing, finance, or any other industry, the skills and expertise of Lean Six Sigma Black Belts are invaluable for organizations striving for continuous improvement and operational excellence.
A Beginner's Guide to Google Cloud Platform CP100A Certification
Welcome to "A Beginner's Guide to Google Cloud Platform CP100A Certification." In an era where cloud computing is at the forefront of technology, mastering the ins and outs of cloud platforms has never been more crucial. Google Cloud Platform (GCP), one of the key players in the cloud computing industry, offers a myriad of services and solutions to help individuals and organizations harness the power of the cloud.
The CP100A certification is your passport to understanding and demonstrating your proficiency in Google Cloud Platform's fundamental concepts. Whether you're a complete newcomer to cloud computing or someone looking to expand their knowledge, this certification serves as an excellent starting point. It equips you with the foundational skills needed to work with GCP and opens doors to a world of cloud-based opportunities.
This guide is designed with beginners in mind, but it's equally valuable for those with some experience in cloud computing looking to solidify their knowledge and earn a recognized certification. Over the course of this guide, we'll navigate through the key aspects of the CP100A certification, breaking down the essentials, exploring study strategies, and offering practical insights that will help you embark on your journey towards becoming a certified Google Cloud Platform Associate.
We'll cover the basics, delve into the exam format, and provide guidance on resources, study techniques, and a study plan tailored for beginners. You'll find tips on how to prepare effectively, manage your time during the exam, and even gain motivation from the success stories of those who have walked this path before you.
So, whether you're a student, an IT professional, or an enthusiast looking to build your cloud computing expertise, this guide is here to help you unlock the doors to Google Cloud Platform and set you on the path to success with the CP100A certification.
Table of contents
Understanding the CP100A Certification
Prerequisites for CP100A
CP100A Exam Format and Structure
Syllabus Overview
Setting Up Your GCP Account
Study Resources for CP100A
Hands-on Labs and Practical Exercises
CP100A Study Plan
Tips for Acing the CP100A Exam
Success Stories and Testimonials
Conclusion
Understanding the CP100A Certification
The CP100A certification, officially known as "Google Cloud Platform Associate Cloud Engineer," is a foundational certification offered by Google Cloud. It is designed for individuals who want to establish their proficiency in the fundamental concepts and skills required to work with Google Cloud Platform (GCP). This certification is an excellent starting point for anyone who is new to GCP and cloud computing or for those with some experience who want to validate their knowledge.
Here's a closer look at the key aspects of the CP100A certification:
Purpose and Significance:The CP100A certification serves as an entry point into Google Cloud's certification program. It is a valuable credential for individuals who want to demonstrate their understanding of core GCP services and concepts.
Target Audience:The certification is suitable for a wide range of professionals, including but not limited to system administrators, network administrators, cloud architects, and IT professionals. It's also an excellent choice for students and technology enthusiasts looking to kickstart their cloud journey.
Prerequisites:Unlike some other GCP certifications, CP100A doesn't have strict prerequisites. However, Google Cloud recommends having some prior experience with GCP and general knowledge of cloud concepts. This means that even beginners can take the CP100A certification, making it an accessible starting point.
Exam Format:The CP100A exam typically consists of multiple-choice and multiple-select questions. The exact number of questions and the duration of the exam may vary, so it's important to check the official Google Cloud website for the most up-to-date information.
Exam Domains:The certification exam covers a range of topics, including setting up a GCP environment, deploying applications, monitoring and troubleshooting, and managing data storage and databases. Familiarity with key GCP services such as Compute Engine, App Engine, Kubernetes Engine, and BigQuery is essential.
Certification Benefits:Earning the CP100A certification demonstrates your foundational knowledge of GCP, which can be a strong selling point in your career. It can help you pursue cloud-related roles and is often a prerequisite for more advanced GCP certifications.
The CP100A certification provides a solid foundation for understanding Google Cloud Platform and sets the stage for further specialization in GCP services and cloud architecture. In this guide, we will delve deeper into the CP100A certification, offering insights, strategies, and resources to help you prepare effectively and excel in your pursuit of becoming a Google Cloud Platform Associate Cloud Engineer.
Prerequisites for CP100A
The CP100A certification, officially known as the "Google Cloud Platform Associate Cloud Engineer," is designed to be accessible to individuals who are new to Google Cloud and cloud computing in general. As such, it doesn't have strict prerequisites. However, there are some recommended prerequisites and skills that can be helpful for candidates to ensure a more successful and efficient certification journey:
Basic Cloud Knowledge: While not mandatory, having a general understanding of cloud computing concepts is beneficial. This can include familiarity with concepts like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Computer Science Fundamentals: Some background knowledge in computer science fundamentals, such as networking, storage, and virtualization, can be advantageous.
Linux Command Line: A basic understanding of the Linux command line can be helpful, as many GCP services interact with Linux-based systems.
Networking Basics: A grasp of fundamental networking concepts like IP addresses, subnets, and firewalls can facilitate your understanding of GCP's networking services.
Study Resources: Consider access to study resources, including official GCP documentation, online courses, and practice exams, to prepare effectively for the certification.
Google Cloud Free Tier: GCP offers a free tier with limited resources that you can use for hands-on practice. Having a GCP free tier account is a practical step to explore the platform and gain practical experience.
It's important to note that the CP100A certification is designed for beginners, and Google Cloud offers a wealth of resources and training materials to help you acquire the knowledge and skills needed to pass the exam. While these prerequisites and skills can be helpful, they are not strict requirements, and anyone interested in Google Cloud can pursue this certification. The key is to be committed to learning and use the available resources to prepare effectively.
CP100A Exam Format and Structure
The CP100A certification exam, officially known as the "Google Cloud Platform Associate Cloud Engineer" exam, follows a specific format and structure. Understanding the format of the exam is crucial for effective preparation. As of my last knowledge update in September 2021, here's what you can expect:
Exam Format:
Type of Questions: The CP100A exam primarily consists of multiple-choice and multiple-select questions. Multiple-select questions require you to choose more than one correct answer from the given options.
Number of Questions: The exact number of questions may vary. However, expect to answer around 50 multiple-choice and multiple-select questions.
Duration: The exam duration can also vary, but it typically lasts for about 2 hours. Be sure to check the most current information on the Google Cloud website or certification platform for the precise details.
Exam Structure: The CP100A exam is designed to test your knowledge and skills in several domains related to Google Cloud. These domains typically include:
Setting Up a GCP Environment:
This domain covers topics related to creating and configuring GCP projects, setting up billing, and navigating the GCP Console.
Managing Compute Resources:
Questions in this domain pertain to managing virtual machine instances, understanding instance templates, and working with Google Compute Engine.
Networking:
This domain explores GCP networking concepts, including Virtual Private Cloud (VPC), firewall rules, load balancers, and Cloud DNS.
Data Storage and Databases:
You'll encounter questions about Google Cloud Storage, Cloud SQL, Cloud Spanner, and Bigtable.
Security:
You'll need to demonstrate your knowledge of Identity and Access Management (IAM) in GCP, along with security best practices.
Remember that the weight of each domain in the exam may vary, so it's essential to study all topics thoroughly. Google Cloud provides an exam guide that details the specific skills and knowledge areas for each domain, which can be a valuable resource during your preparation.
For the most accurate and up-to-date information on the CP100A exam format and structure, I recommend visiting the official Google Cloud Certification website or contacting Google Cloud directly, as exam details may evolve over time.
Syllabus Overview
The CP100A certification, also known as the "Google Cloud Platform Associate Cloud Engineer" certification, covers a range of topics related to Google Cloud Platform (GCP). Here is an overview of the syllabus or key domains and topics typically included in the certification:
Setting Up a GCP Environment:
Creating and managing Google Cloud projects.
Configuring billing and setting up budgets.
Understanding and navigating the GCP Console.
Deploying and Implementing Applications:
Deploying applications to Google App Engine.
Managing containerized applications with Google Kubernetes Engine (GKE).
Running applications on virtual machine instances with Google Compute Engine.
Managing Compute Resources:
Creating, stopping, and starting virtual machine instances.
Using instance templates and custom images.
Managing instance groups for high availability.
Networking:
Creating and configuring Virtual Private Cloud (VPC) networks.
Configuring firewall rules to control network traffic.
Setting up and managing load balancers.
Data Storage and Databases:
Using Google Cloud Storage for object storage.
Managing data in Cloud SQL and Cloud Spanner.
Working with NoSQL databases using Cloud Bigtable.
Monitoring and Logging:
Setting up monitoring and alerts with Google Stackdriver.
Viewing and analyzing logs to troubleshoot issues.
Using Stackdriver Trace for application performance analysis.
Security:
Understanding Identity and Access Management (IAM) roles and permissions.
Configuring service accounts for secure access.
Implementing security best practices for Google Cloud services.
It's essential to note that the exam may consist of a varying number of questions covering these domains. Each domain's weight in the exam can also differ. Therefore, it's crucial to study all topics thoroughly to ensure success in the certification.
To prepare for the CP100A exam, you can use official Google Cloud documentation, online courses, practice exams, and other study resources, which align with these topics and domains. Google Cloud typically provides an exam guide that details the specific skills and knowledge areas you need to cover, so be sure to consult that guide for a more detailed breakdown of the syllabus.
Setting Up Your GCP Account
Setting up your Google Cloud Platform (GCP) account is the first step toward exploring and using GCP services and preparing for the CP100A certification. Here's a step-by-step guide on how to set up your GCP account:
Visit the GCP Console:
Open your web browser and go to the Google Cloud Console.
Create a Google Account (if you don't have one):
To use GCP, you'll need a Google Account. If you already have a Gmail or other Google account, you can use it. If not, you can create one during this process.
Sign In:
Sign in to your Google Account if you're not already logged in.
Create a GCP Project:
Once you're signed in and have access to the GCP Console, you can create a new GCP project. Projects help you organize your resources and billing. Click on the project drop-down (usually located in the top bar) and select "New Project." Follow the prompts to set a project name and configure other project settings.
Enable Billing:
If you haven't already, you will be prompted to enable billing for your GCP project. This is required to access and use paid services.
By following these steps, you'll have successfully set up your GCP account and be ready to start exploring Google Cloud services, which is a vital first step in preparing for the CP100A certification. Remember to manage your account and budget carefully to avoid unexpected charges, especially if you're using paid services.
Study Resources for CP100A
When preparing for the CP100A certification (Google Cloud Platform Associate Cloud Engineer), it's essential to use a variety of study resources to build a strong foundation of knowledge and skills. Here are some valuable study resources to help you in your preparation:
Official Google Cloud Documentation:The official Google Cloud documentation is a comprehensive and up-to-date resource that covers all aspects of GCP services and features. It is an essential reference for the certification.
Udemy and Other Online Courses:Platforms like Udemy offer various GCP certification courses, including CP100A. Look for courses with high ratings and good reviews.
Practice Exams:Using practice exams is an excellent way to test your knowledge and get a feel for the actual exam format. Google Cloud provides official practice exams for CP100A. Additionally, there are third-party practice exams available online.
Google Cloud Quicklabs:Quicklabs provides hands-on labs that allow you to practice using GCP services in a controlled environment. Some of these labs are available for free.
Books:There are books dedicated to GCP certification preparation, such as "Google Cloud Certified - Associate Cloud Engineer Study Guide" by Dan Sullivan.
Hands-On Practice:Sign up for a free GCP account and practice what you've learned. You can use the free credits provided by GCP to explore and experiment with different services.
Remember that the key to success in certification exams like CP100A is not just reading or watching, but actively practicing and applying your knowledge through hands-on labs and real-world scenarios. Make sure to create a study plan and allocate time for review and practice as well.
Hands-on Labs and Practical Exercises
Hands-on labs and practical exercises are essential components of your preparation for the CP100A (Google Cloud Platform Associate Cloud Engineer) certification. They provide you with a tangible understanding of GCP services, allowing you to apply your knowledge in real-world scenarios. Here are some hands-on labs and practical exercises you can perform to enhance your GCP skills:
GCP Quicklabs:Google Cloud provides a platform called Quicklabs that offers a wide range of hands-on labs. These labs guide you through various GCP services and concepts, allowing you to gain practical experience. Some of these labs are free, while others may require payment.
VPC Networking Configuration:Create and configure Virtual Private Cloud (VPC) networks. Implement network segmentation, firewall rules, and external IP addresses. Practice setting up VPNs or Interconnect for secure connections.
Security Practices:Implement Identity and Access Management (IAM) roles and permissions for GCP services. Practice securing resources and services using IAM.
Scaling and Load Balancing:Configure autoscaling for your applications and services. Set up load balancers to distribute traffic across multiple instances.
Data Analytics:Explore data analytics by running queries in BigQuery, managing data with Cloud Datastore, and practicing data analysis with Google Data Studio.
Backup and Disaster Recovery:Implement backup and disaster recovery strategies for your applications and data, using GCP services like Cloud Storage for backups.
When working on these hands-on labs and exercises, pay close attention to best practices, security considerations, and cost management. Hands-on experience not only reinforces your knowledge but also gives you practical insights into real-world GCP usage, which can be invaluable when taking the CP100A exam and working with Google Cloud in your career.
CP100A Study Plan
Creating a well-structured study plan is crucial for effectively preparing for the CP100A (Google Cloud Platform Associate Cloud Engineer) certification. Here's a sample study plan to help you get started. Keep in mind that the timeline may vary depending on your current knowledge and the time you can commit to studying each day.
Week 1: Orientation and Fundamentals
Days 1-2:
Set up your GCP account if you haven't already.
Familiarize yourself with the GCP Console and navigation.
Days 3-4:
Explore Google Cloud's core services and learn about the GCP environment.
Review the official GCP documentation and introductory videos.
Days 5-7:
Start with basic networking concepts in GCP, including VPCs, subnets, and firewalls.
Complete hands-on labs to practice setting up VPCs and firewall rules.
Week 2: Compute and Storage
Days 8-9:
Study GCP compute services such as Compute Engine, App Engine, and Kubernetes Engine.
Deploy a simple web application on App Engine.
Days 10-11:
Dive into GCP storage services, including Google Cloud Storage, Cloud SQL, and Cloud Bigtable.
Perform hands-on exercises for data storage and retrieval.
Days 12-14:
Review networking in more detail, focusing on load balancing and Cloud DNS.
Practice creating and configuring load balancers.
Week 3: Monitoring, Logging, and IAM
Days 15-16:
Learn how to set up monitoring and alerts using Stackdriver.
Create custom dashboards to monitor GCP resources.
Days 17-18:
Understand Identity and Access Management (IAM) roles and permissions.
Set up IAM policies to secure GCP resources.
Days 19-21:
Explore logs and logging with Stackdriver.
Create alerting policies for critical events.
Week 4: Security and More Advanced Topics
Days 22-23:
Study GCP security best practices, encryption, and network security.
Learn about authentication and authorization with service accounts.
Days 24-25:
Explore serverless computing with Cloud Functions, Cloud Scheduler, and Cloud Tasks.
Deploy serverless functions and schedule tasks.
Days 26-28:
Review data analytics with BigQuery and data storage with Datastore.
Learn about dataflow and Pub/Sub for data streaming.
Week 5: Review and Practice
Days 29-30:
Review the study material, focusing on any areas you find challenging.
Take practice exams to assess your knowledge and identify weak points.
Days 31-35:
Continue reviewing and practicing as needed.
Day 36:
Take an official Google Cloud practice exam (if available) to simulate the exam environment.
Week 6: Final Exam and Certification
Day 37:
Take the CP100A certification exam.
Day 38-40:
Celebrate your accomplishment, and consider sharing your success with the GCP community.
Day 41:
Reflect on your journey and consider the next steps in your GCP certification path.
Tips for Acing the CP100A Exam
Acing the CP100A exam (Google Cloud Platform Associate Cloud Engineer) requires a combination of knowledge, preparation, and effective test-taking strategies. Here are some tips to help you perform your best on the exam:
Understand the Exam Format:Familiarize yourself with the format and structure of the exam. Understand the types of questions you'll encounter, such as multiple-choice and multiple-select questions.
Review the Exam Guide:Google provides an official exam guide that outlines the topics, skills, and knowledge areas covered in the exam. Use this guide as a blueprint for your study plan.
Create a Study Plan:Develop a study plan that covers all the exam domains. Allocate more time to areas where you have weaker knowledge.
Hands-On Practice:Practical experience is invaluable. Ensure you've completed hands-on labs and have applied your knowledge in real-world scenarios.
Official Google Cloud Practice Exams:Take advantage of any official Google Cloud practice exams available. These are designed to simulate the actual exam environment and can help you assess your readiness.
Third-Party Practice Exams:Consider using third-party practice exams and questions from reputable sources. They can provide additional test preparation and a different perspective on the material.
By following these tips, you can increase your chances of acing the CP100A exam and earning your Google Cloud Platform Associate Cloud Engineer certification. Remember that effective preparation and practical experience are key to success.
Success Stories and Testimonials
Reading success stories and testimonials from individuals who have passed the CP100A (Google Cloud Platform Associate Cloud Engineer) exam can be a great source of motivation and inspiration as you prepare for your own certification journey. Here are some fictional success stories and testimonials to provide you with an idea of what success can look like:
Success Story: Alice's Journey to Becoming a Certified GCP Associate Cloud Engineer
Alice, a recent computer science graduate, was determined to kickstart her career in cloud computing. With no prior experience in Google Cloud Platform (GCP), she embarked on her CP100A certification journey. She diligently followed a study plan, completed hands-on labs, and practiced with practice exams.
After weeks of preparation, Alice took the CP100A exam and passed with flying colors. Her certification opened doors to a job at a leading tech company, where she now works on cloud solutions for clients worldwide. Alice's success story is proof that with dedication and determination, anyone can achieve their GCP certification dreams.
Success Story: Sarah's Transition to a Cloud Career
Sarah, an experienced network administrator, decided to pivot her career toward cloud computing. She chose Google Cloud Platform as her platform of choice. While preparing for the CP100A exam, she utilized a variety of study resources, including online courses and practice exams.
Sarah's hard work paid off when she passed the CP100A exam. Her new certification made her a valuable asset to her organization as they transitioned to the cloud. She now leads cloud migration projects and has become an advocate for GCP within her industry.
Conclusion
In conclusion, the CP100A (Google Cloud Platform Associate Cloud Engineer) certification represents an exciting opportunity for individuals looking to establish their foundational knowledge in Google Cloud Platform (GCP). This certification is designed for those new to GCP and cloud computing, as well as those with some experience who want to validate their skills.
Throughout this guide, we've explored the essentials of the CP100A certification, including its purpose, prerequisites, exam format, and key exam domains. We've also provided a structured study plan, recommended study resources, and tips for acing the exam. Additionally, we shared fictional success stories and testimonials to inspire and motivate you on your certification journey.
Whether you're a recent graduate, an IT professional seeking new horizons, or someone simply passionate about cloud technology, the CP100A certification can be a valuable asset in your career journey. Stay determined, stay focused, and, most importantly, enjoy the learning process. Best of luck on your journey to becoming a certified GCP professional!
Read More
Welcome to "A Beginner's Guide to Google Cloud Platform CP100A Certification." In an era where cloud computing is at the forefront of technology, mastering the ins and outs of cloud platforms has never been more crucial. Google Cloud Platform (GCP), one of the key players in the cloud computing industry, offers a myriad of services and solutions to help individuals and organizations harness the power of the cloud.
The CP100A certification is your passport to understanding and demonstrating your proficiency in Google Cloud Platform's fundamental concepts. Whether you're a complete newcomer to cloud computing or someone looking to expand their knowledge, this certification serves as an excellent starting point. It equips you with the foundational skills needed to work with GCP and opens doors to a world of cloud-based opportunities.
This guide is designed with beginners in mind, but it's equally valuable for those with some experience in cloud computing looking to solidify their knowledge and earn a recognized certification. Over the course of this guide, we'll navigate through the key aspects of the CP100A certification, breaking down the essentials, exploring study strategies, and offering practical insights that will help you embark on your journey towards becoming a certified Google Cloud Platform Associate.
We'll cover the basics, delve into the exam format, and provide guidance on resources, study techniques, and a study plan tailored for beginners. You'll find tips on how to prepare effectively, manage your time during the exam, and even gain motivation from the success stories of those who have walked this path before you.
So, whether you're a student, an IT professional, or an enthusiast looking to build your cloud computing expertise, this guide is here to help you unlock the doors to Google Cloud Platform and set you on the path to success with the CP100A certification.
Table of contents
Understanding the CP100A Certification
Prerequisites for CP100A
CP100A Exam Format and Structure
Syllabus Overview
Setting Up Your GCP Account
Study Resources for CP100A
Hands-on Labs and Practical Exercises
CP100A Study Plan
Tips for Acing the CP100A Exam
Success Stories and Testimonials
Conclusion
Understanding the CP100A Certification
The CP100A certification, officially known as "Google Cloud Platform Associate Cloud Engineer," is a foundational certification offered by Google Cloud. It is designed for individuals who want to establish their proficiency in the fundamental concepts and skills required to work with Google Cloud Platform (GCP). This certification is an excellent starting point for anyone who is new to GCP and cloud computing or for those with some experience who want to validate their knowledge.
Here's a closer look at the key aspects of the CP100A certification:
Purpose and Significance:The CP100A certification serves as an entry point into Google Cloud's certification program. It is a valuable credential for individuals who want to demonstrate their understanding of core GCP services and concepts.
Target Audience:The certification is suitable for a wide range of professionals, including but not limited to system administrators, network administrators, cloud architects, and IT professionals. It's also an excellent choice for students and technology enthusiasts looking to kickstart their cloud journey.
Prerequisites:Unlike some other GCP certifications, CP100A doesn't have strict prerequisites. However, Google Cloud recommends having some prior experience with GCP and general knowledge of cloud concepts. This means that even beginners can take the CP100A certification, making it an accessible starting point.
Exam Format:The CP100A exam typically consists of multiple-choice and multiple-select questions. The exact number of questions and the duration of the exam may vary, so it's important to check the official Google Cloud website for the most up-to-date information.
Exam Domains:The certification exam covers a range of topics, including setting up a GCP environment, deploying applications, monitoring and troubleshooting, and managing data storage and databases. Familiarity with key GCP services such as Compute Engine, App Engine, Kubernetes Engine, and BigQuery is essential.
Certification Benefits:Earning the CP100A certification demonstrates your foundational knowledge of GCP, which can be a strong selling point in your career. It can help you pursue cloud-related roles and is often a prerequisite for more advanced GCP certifications.
The CP100A certification provides a solid foundation for understanding Google Cloud Platform and sets the stage for further specialization in GCP services and cloud architecture. In this guide, we will delve deeper into the CP100A certification, offering insights, strategies, and resources to help you prepare effectively and excel in your pursuit of becoming a Google Cloud Platform Associate Cloud Engineer.
Prerequisites for CP100A
The CP100A certification, officially known as the "Google Cloud Platform Associate Cloud Engineer," is designed to be accessible to individuals who are new to Google Cloud and cloud computing in general. As such, it doesn't have strict prerequisites. However, there are some recommended prerequisites and skills that can be helpful for candidates to ensure a more successful and efficient certification journey:
Basic Cloud Knowledge: While not mandatory, having a general understanding of cloud computing concepts is beneficial. This can include familiarity with concepts like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Computer Science Fundamentals: Some background knowledge in computer science fundamentals, such as networking, storage, and virtualization, can be advantageous.
Linux Command Line: A basic understanding of the Linux command line can be helpful, as many GCP services interact with Linux-based systems.
Networking Basics: A grasp of fundamental networking concepts like IP addresses, subnets, and firewalls can facilitate your understanding of GCP's networking services.
Study Resources: Consider access to study resources, including official GCP documentation, online courses, and practice exams, to prepare effectively for the certification.
Google Cloud Free Tier: GCP offers a free tier with limited resources that you can use for hands-on practice. Having a GCP free tier account is a practical step to explore the platform and gain practical experience.
It's important to note that the CP100A certification is designed for beginners, and Google Cloud offers a wealth of resources and training materials to help you acquire the knowledge and skills needed to pass the exam. While these prerequisites and skills can be helpful, they are not strict requirements, and anyone interested in Google Cloud can pursue this certification. The key is to be committed to learning and use the available resources to prepare effectively.
CP100A Exam Format and Structure
The CP100A certification exam, officially known as the "Google Cloud Platform Associate Cloud Engineer" exam, follows a specific format and structure. Understanding the format of the exam is crucial for effective preparation. As of my last knowledge update in September 2021, here's what you can expect:
Exam Format:
Type of Questions: The CP100A exam primarily consists of multiple-choice and multiple-select questions. Multiple-select questions require you to choose more than one correct answer from the given options.
Number of Questions: The exact number of questions may vary. However, expect to answer around 50 multiple-choice and multiple-select questions.
Duration: The exam duration can also vary, but it typically lasts for about 2 hours. Be sure to check the most current information on the Google Cloud website or certification platform for the precise details.
Exam Structure: The CP100A exam is designed to test your knowledge and skills in several domains related to Google Cloud. These domains typically include:
Setting Up a GCP Environment:
This domain covers topics related to creating and configuring GCP projects, setting up billing, and navigating the GCP Console.
Managing Compute Resources:
Questions in this domain pertain to managing virtual machine instances, understanding instance templates, and working with Google Compute Engine.
Networking:
This domain explores GCP networking concepts, including Virtual Private Cloud (VPC), firewall rules, load balancers, and Cloud DNS.
Data Storage and Databases:
You'll encounter questions about Google Cloud Storage, Cloud SQL, Cloud Spanner, and Bigtable.
Security:
You'll need to demonstrate your knowledge of Identity and Access Management (IAM) in GCP, along with security best practices.
Remember that the weight of each domain in the exam may vary, so it's essential to study all topics thoroughly. Google Cloud provides an exam guide that details the specific skills and knowledge areas for each domain, which can be a valuable resource during your preparation.
For the most accurate and up-to-date information on the CP100A exam format and structure, I recommend visiting the official Google Cloud Certification website or contacting Google Cloud directly, as exam details may evolve over time.
Syllabus Overview
The CP100A certification, also known as the "Google Cloud Platform Associate Cloud Engineer" certification, covers a range of topics related to Google Cloud Platform (GCP). Here is an overview of the syllabus or key domains and topics typically included in the certification:
Setting Up a GCP Environment:
Creating and managing Google Cloud projects.
Configuring billing and setting up budgets.
Understanding and navigating the GCP Console.
Deploying and Implementing Applications:
Deploying applications to Google App Engine.
Managing containerized applications with Google Kubernetes Engine (GKE).
Running applications on virtual machine instances with Google Compute Engine.
Managing Compute Resources:
Creating, stopping, and starting virtual machine instances.
Using instance templates and custom images.
Managing instance groups for high availability.
Networking:
Creating and configuring Virtual Private Cloud (VPC) networks.
Configuring firewall rules to control network traffic.
Setting up and managing load balancers.
Data Storage and Databases:
Using Google Cloud Storage for object storage.
Managing data in Cloud SQL and Cloud Spanner.
Working with NoSQL databases using Cloud Bigtable.
Monitoring and Logging:
Setting up monitoring and alerts with Google Stackdriver.
Viewing and analyzing logs to troubleshoot issues.
Using Stackdriver Trace for application performance analysis.
Security:
Understanding Identity and Access Management (IAM) roles and permissions.
Configuring service accounts for secure access.
Implementing security best practices for Google Cloud services.
It's essential to note that the exam may consist of a varying number of questions covering these domains. Each domain's weight in the exam can also differ. Therefore, it's crucial to study all topics thoroughly to ensure success in the certification.
To prepare for the CP100A exam, you can use official Google Cloud documentation, online courses, practice exams, and other study resources, which align with these topics and domains. Google Cloud typically provides an exam guide that details the specific skills and knowledge areas you need to cover, so be sure to consult that guide for a more detailed breakdown of the syllabus.
Setting Up Your GCP Account
Setting up your Google Cloud Platform (GCP) account is the first step toward exploring and using GCP services and preparing for the CP100A certification. Here's a step-by-step guide on how to set up your GCP account:
Visit the GCP Console:
Open your web browser and go to the Google Cloud Console.
Create a Google Account (if you don't have one):
To use GCP, you'll need a Google Account. If you already have a Gmail or other Google account, you can use it. If not, you can create one during this process.
Sign In:
Sign in to your Google Account if you're not already logged in.
Create a GCP Project:
Once you're signed in and have access to the GCP Console, you can create a new GCP project. Projects help you organize your resources and billing. Click on the project drop-down (usually located in the top bar) and select "New Project." Follow the prompts to set a project name and configure other project settings.
Enable Billing:
If you haven't already, you will be prompted to enable billing for your GCP project. This is required to access and use paid services.
By following these steps, you'll have successfully set up your GCP account and be ready to start exploring Google Cloud services, which is a vital first step in preparing for the CP100A certification. Remember to manage your account and budget carefully to avoid unexpected charges, especially if you're using paid services.
Study Resources for CP100A
When preparing for the CP100A certification (Google Cloud Platform Associate Cloud Engineer), it's essential to use a variety of study resources to build a strong foundation of knowledge and skills. Here are some valuable study resources to help you in your preparation:
Official Google Cloud Documentation:The official Google Cloud documentation is a comprehensive and up-to-date resource that covers all aspects of GCP services and features. It is an essential reference for the certification.
Udemy and Other Online Courses:Platforms like Udemy offer various GCP certification courses, including CP100A. Look for courses with high ratings and good reviews.
Practice Exams:Using practice exams is an excellent way to test your knowledge and get a feel for the actual exam format. Google Cloud provides official practice exams for CP100A. Additionally, there are third-party practice exams available online.
Google Cloud Quicklabs:Quicklabs provides hands-on labs that allow you to practice using GCP services in a controlled environment. Some of these labs are available for free.
Books:There are books dedicated to GCP certification preparation, such as "Google Cloud Certified - Associate Cloud Engineer Study Guide" by Dan Sullivan.
Hands-On Practice:Sign up for a free GCP account and practice what you've learned. You can use the free credits provided by GCP to explore and experiment with different services.
Remember that the key to success in certification exams like CP100A is not just reading or watching, but actively practicing and applying your knowledge through hands-on labs and real-world scenarios. Make sure to create a study plan and allocate time for review and practice as well.
Hands-on Labs and Practical Exercises
Hands-on labs and practical exercises are essential components of your preparation for the CP100A (Google Cloud Platform Associate Cloud Engineer) certification. They provide you with a tangible understanding of GCP services, allowing you to apply your knowledge in real-world scenarios. Here are some hands-on labs and practical exercises you can perform to enhance your GCP skills:
GCP Quicklabs:Google Cloud provides a platform called Quicklabs that offers a wide range of hands-on labs. These labs guide you through various GCP services and concepts, allowing you to gain practical experience. Some of these labs are free, while others may require payment.
VPC Networking Configuration:Create and configure Virtual Private Cloud (VPC) networks. Implement network segmentation, firewall rules, and external IP addresses. Practice setting up VPNs or Interconnect for secure connections.
Security Practices:Implement Identity and Access Management (IAM) roles and permissions for GCP services. Practice securing resources and services using IAM.
Scaling and Load Balancing:Configure autoscaling for your applications and services. Set up load balancers to distribute traffic across multiple instances.
Data Analytics:Explore data analytics by running queries in BigQuery, managing data with Cloud Datastore, and practicing data analysis with Google Data Studio.
Backup and Disaster Recovery:Implement backup and disaster recovery strategies for your applications and data, using GCP services like Cloud Storage for backups.
When working on these hands-on labs and exercises, pay close attention to best practices, security considerations, and cost management. Hands-on experience not only reinforces your knowledge but also gives you practical insights into real-world GCP usage, which can be invaluable when taking the CP100A exam and working with Google Cloud in your career.
CP100A Study Plan
Creating a well-structured study plan is crucial for effectively preparing for the CP100A (Google Cloud Platform Associate Cloud Engineer) certification. Here's a sample study plan to help you get started. Keep in mind that the timeline may vary depending on your current knowledge and the time you can commit to studying each day.
Week 1: Orientation and Fundamentals
Days 1-2:
Set up your GCP account if you haven't already.
Familiarize yourself with the GCP Console and navigation.
Days 3-4:
Explore Google Cloud's core services and learn about the GCP environment.
Review the official GCP documentation and introductory videos.
Days 5-7:
Start with basic networking concepts in GCP, including VPCs, subnets, and firewalls.
Complete hands-on labs to practice setting up VPCs and firewall rules.
Week 2: Compute and Storage
Days 8-9:
Study GCP compute services such as Compute Engine, App Engine, and Kubernetes Engine.
Deploy a simple web application on App Engine.
Days 10-11:
Dive into GCP storage services, including Google Cloud Storage, Cloud SQL, and Cloud Bigtable.
Perform hands-on exercises for data storage and retrieval.
Days 12-14:
Review networking in more detail, focusing on load balancing and Cloud DNS.
Practice creating and configuring load balancers.
Week 3: Monitoring, Logging, and IAM
Days 15-16:
Learn how to set up monitoring and alerts using Stackdriver.
Create custom dashboards to monitor GCP resources.
Days 17-18:
Understand Identity and Access Management (IAM) roles and permissions.
Set up IAM policies to secure GCP resources.
Days 19-21:
Explore logs and logging with Stackdriver.
Create alerting policies for critical events.
Week 4: Security and More Advanced Topics
Days 22-23:
Study GCP security best practices, encryption, and network security.
Learn about authentication and authorization with service accounts.
Days 24-25:
Explore serverless computing with Cloud Functions, Cloud Scheduler, and Cloud Tasks.
Deploy serverless functions and schedule tasks.
Days 26-28:
Review data analytics with BigQuery and data storage with Datastore.
Learn about dataflow and Pub/Sub for data streaming.
Week 5: Review and Practice
Days 29-30:
Review the study material, focusing on any areas you find challenging.
Take practice exams to assess your knowledge and identify weak points.
Days 31-35:
Continue reviewing and practicing as needed.
Day 36:
Take an official Google Cloud practice exam (if available) to simulate the exam environment.
Week 6: Final Exam and Certification
Day 37:
Take the CP100A certification exam.
Day 38-40:
Celebrate your accomplishment, and consider sharing your success with the GCP community.
Day 41:
Reflect on your journey and consider the next steps in your GCP certification path.
Tips for Acing the CP100A Exam
Acing the CP100A exam (Google Cloud Platform Associate Cloud Engineer) requires a combination of knowledge, preparation, and effective test-taking strategies. Here are some tips to help you perform your best on the exam:
Understand the Exam Format:Familiarize yourself with the format and structure of the exam. Understand the types of questions you'll encounter, such as multiple-choice and multiple-select questions.
Review the Exam Guide:Google provides an official exam guide that outlines the topics, skills, and knowledge areas covered in the exam. Use this guide as a blueprint for your study plan.
Create a Study Plan:Develop a study plan that covers all the exam domains. Allocate more time to areas where you have weaker knowledge.
Hands-On Practice:Practical experience is invaluable. Ensure you've completed hands-on labs and have applied your knowledge in real-world scenarios.
Official Google Cloud Practice Exams:Take advantage of any official Google Cloud practice exams available. These are designed to simulate the actual exam environment and can help you assess your readiness.
Third-Party Practice Exams:Consider using third-party practice exams and questions from reputable sources. They can provide additional test preparation and a different perspective on the material.
By following these tips, you can increase your chances of acing the CP100A exam and earning your Google Cloud Platform Associate Cloud Engineer certification. Remember that effective preparation and practical experience are key to success.
Success Stories and Testimonials
Reading success stories and testimonials from individuals who have passed the CP100A (Google Cloud Platform Associate Cloud Engineer) exam can be a great source of motivation and inspiration as you prepare for your own certification journey. Here are some fictional success stories and testimonials to provide you with an idea of what success can look like:
Success Story: Alice's Journey to Becoming a Certified GCP Associate Cloud Engineer
Alice, a recent computer science graduate, was determined to kickstart her career in cloud computing. With no prior experience in Google Cloud Platform (GCP), she embarked on her CP100A certification journey. She diligently followed a study plan, completed hands-on labs, and practiced with practice exams.
After weeks of preparation, Alice took the CP100A exam and passed with flying colors. Her certification opened doors to a job at a leading tech company, where she now works on cloud solutions for clients worldwide. Alice's success story is proof that with dedication and determination, anyone can achieve their GCP certification dreams.
Success Story: Sarah's Transition to a Cloud Career
Sarah, an experienced network administrator, decided to pivot her career toward cloud computing. She chose Google Cloud Platform as her platform of choice. While preparing for the CP100A exam, she utilized a variety of study resources, including online courses and practice exams.
Sarah's hard work paid off when she passed the CP100A exam. Her new certification made her a valuable asset to her organization as they transitioned to the cloud. She now leads cloud migration projects and has become an advocate for GCP within her industry.
Conclusion
In conclusion, the CP100A (Google Cloud Platform Associate Cloud Engineer) certification represents an exciting opportunity for individuals looking to establish their foundational knowledge in Google Cloud Platform (GCP). This certification is designed for those new to GCP and cloud computing, as well as those with some experience who want to validate their skills.
Throughout this guide, we've explored the essentials of the CP100A certification, including its purpose, prerequisites, exam format, and key exam domains. We've also provided a structured study plan, recommended study resources, and tips for acing the exam. Additionally, we shared fictional success stories and testimonials to inspire and motivate you on your certification journey.
Whether you're a recent graduate, an IT professional seeking new horizons, or someone simply passionate about cloud technology, the CP100A certification can be a valuable asset in your career journey. Stay determined, stay focused, and, most importantly, enjoy the learning process. Best of luck on your journey to becoming a certified GCP professional!
An Introduction to ISO 20000: What You Need to Know
In today's rapidly evolving digital landscape, effective IT service management is crucial for businesses to stay competitive, deliver exceptional customer experiences, and ensure the smooth operation of their IT services. One framework that has gained prominence in this regard is ISO 20000.
ISO 20000 is an internationally recognized standard for IT Service Management (ITSM). It provides a set of best practices and guidelines for organizations to establish, implement, maintain, and continually improve their ITSM system. This standard is designed to ensure that IT services meet the needs of the organization and its customers, while also complying with regulatory and quality requirements.
Over the course of this blog series, we will delve deeper into these components, explore best practices, and provide insights into achieving ISO 20000 certification.
Whether you're an IT professional, a business owner, or simply someone interested in IT service management, understanding ISO 20000 is invaluable in today's technology-driven world. It's a path to ensuring that IT services are not just reliable but also a strategic asset for your organization.
Stay tuned as we explore the principles, benefits, and practical steps towards implementing ISO 20000 IT Service Management. The journey begins here.
Table of contents
-
The Origins of ISO 20000
-
The Importance of Standardization
-
Key Principles of ISO 20000
-
ISO 20000 vs. Other ITSM Frameworks
-
Benefits of ISO 20000
-
The Structure of ISO 20000
-
Certification Process
-
Common Misconceptions about ISO 20000
-
ISO 20000 in Different Industries
-
Case Studies and Success Stories
-
Conclusion
The Origins of ISO 20000
The Origins of ISO 20000: From ITIL to Global Standard
ISO 20000, formally known as ISO/IEC 20000, is an international standard that has its roots in the Information Technology Infrastructure Library (ITIL) and the need for global consistency in IT service management practices.
ITIL and the Need for Standardization
The story of ISO 20000 begins with ITIL, a set of best practices for IT service management that originated in the United Kingdom in the 1980s. ITIL was developed by the UK government in response to a lack of standardization and structure in IT service management practices. ITIL provided a framework for organizations to better manage their IT services, with a focus on aligning IT with business needs, improving service quality, and increasing efficiency.
ITIL gained widespread acceptance and was adopted by organizations worldwide. It became the de facto framework for IT service management, and its popularity spurred the need for an international standard that would ensure consistency and quality in IT service management practices across the globe.
The Path to ISO 20000
The journey towards ISO 20000 can be summarized in the following key milestones:
BS 15000: The first significant step toward international standardization was the development of the British Standard BS 15000. Published in 2000, BS 15000 was essentially a formalization of ITIL concepts into a national standard. This standard laid the groundwork for what would later become ISO 20000.
ISO/IEC 20000-1 and -2: The international standardization process began with the collaboration of several international standards bodies. ISO/IEC 20000 was published in 2005, comprising two parts: Part 1 specifies the requirements for IT service management, while Part 2 provides guidance on the application of Part 1. These standards were developed to provide a globally accepted framework for IT service management.
ISO 20000-2018: The standard has seen updates and revisions over the years, with ISO 20000:2018 being the most recent version as of my last knowledge update in September 2021. This revision refined and expanded the standard to align with modern IT service management practices and principles.
Why ISO 20000 Matters
ISO 20000 is vital because it brings a unified approach to IT service management, which is especially crucial in today's globally interconnected business environment. It provides a framework that organizations can use to ensure that their IT services are reliable, efficient, and meet both customer and regulatory requirements.
In summary, ISO 20000's origins can be traced back to the need for standardization in IT service management, stemming from the success of ITIL. It has since evolved into an internationally recognized standard, helping organizations worldwide improve their IT service delivery and achieve operational excellence. As IT continues to be a critical component of modern business operations, ISO 20000's relevance and importance continue to grow.
The Importance of Standardization
In the ever-evolving world of information technology, where innovation and change are constant, standardization plays a pivotal role in ensuring the efficiency, quality, and reliability of IT services. Standardization is particularly crucial in the realm of IT Service Management (ITSM), and ISO 20000 is a prime example of how it contributes to excellence. Let's delve into the significance of standardization in ITSM:
Consistency and Predictability: Standardization establishes a set of consistent processes, procedures, and best practices. In the context of ITSM, this consistency ensures that IT services are delivered in a predictable manner. Customers and stakeholders can rely on consistent service quality, which fosters trust and confidence.
Improved Efficiency: Standardized processes eliminate redundancy and confusion in IT service delivery. This, in turn, leads to improved efficiency, as employees can follow well-defined procedures, reducing the time and effort required to complete tasks.
Quality Assurance: Quality control is a fundamental aspect of standardization. By adhering to established standards and best practices, organizations can consistently deliver high-quality IT services. Standardization helps identify and address potential quality issues proactively.
Risk Management: Standardization aids in risk management by identifying and mitigating potential risks in IT service delivery. By following standardized processes and procedures, organizations can reduce the likelihood of errors and vulnerabilities that might negatively impact services.
Scalability: Standardized processes can be scaled more easily. As organizations grow or adapt to changing circumstances, they can expand their IT service operations efficiently by replicating established standards and processes.
Knowledge Sharing: Standardized processes and best practices make it easier for employees to share knowledge and collaborate. This contributes to a culture of continuous improvement and learning within the organization.
Competitive Advantage: Organizations that adhere to internationally recognized standards like ISO 20000 gain a competitive advantage. They can demonstrate their commitment to quality and best practices, which can be a selling point for customers and partners.
In the realm of ITSM, ISO 20000 exemplifies the importance of standardization by providing a globally recognized framework for IT service management. It empowers organizations to align their IT services with business objectives, deliver consistent quality, and remain adaptable in a rapidly changing IT landscape.
In summary, standardization in IT Service Management is essential for achieving operational excellence, meeting customer expectations, and managing risk. ISO 20000's global acceptance underscores the importance of adhering to best practices and standards to ensure that IT services are a strategic asset for organizations in today's technology-driven world.
Key Principles of ISO 20000
Certainly, ISO 20000 is built upon several key principles that guide IT Service Management (ITSM) practices. These principles provide a foundation for organizations seeking to implement ISO 20000 and improve their IT services. Here are the key principles of ISO 20000:
Customer Focus: ISO 20000 places a strong emphasis on meeting customer needs and delivering services that align with the organization's overall business objectives. It requires IT service providers to understand and prioritize customer requirements and expectations.
Leadership and Commitment: The commitment of top management is crucial for the successful implementation of ISO 20000. Leaders within the organization must support and drive the ITSM initiatives, setting the tone for a culture of service excellence.
Process Approach: ISO 20000 promotes a process-driven approach to ITSM. This means defining, documenting, and consistently following well-defined processes and procedures to manage IT services effectively.
Improvement: Continuous improvement is a fundamental principle of ISO 20000. Organizations are encouraged to regularly monitor and measure their ITSM processes, identify areas for improvement, and implement changes to enhance service quality.
Supplier Management: ISO 20000 acknowledges the role of suppliers and service providers in the delivery of IT services. It emphasizes the importance of managing and monitoring supplier relationships to ensure they meet service requirements.
Service Level Management: This principle underscores the need to define, agree upon, and manage service level agreements (SLAs) with customers. It involves setting clear expectations for service quality, availability, and performance.
Documentation and Records: Proper documentation and record-keeping are vital for demonstrating compliance with ISO 20000 requirements. This principle ensures that organizations maintain accurate records of their ITSM processes and activities.
These key principles provide a holistic framework for IT service management that is not only aligned with customer needs but also focused on continuous improvement and accountability. Organizations that adhere to these principles are better positioned to deliver high-quality IT services that drive business success and customer satisfaction.
ISO 20000 vs. Other ITSM Frameworks
IT Service Management (ITSM) is critical for organizations to deliver efficient and high-quality IT services. To achieve this, various ITSM frameworks and standards have been developed, each with its own approach and methodologies. ISO 20000 is one such standard, but how does it compare to other well-known ITSM frameworks like ITIL and COBIT? Let's explore the key differences and similarities in this comparative analysis:
ISO 20000: The International Standard
Focus: ISO 20000 is an international standard that specifies requirements for ITSM. It emphasizes process-driven IT service delivery, compliance, and continual improvement.
Certification: ISO 20000 provides a certification process for organizations to demonstrate compliance with the standard.
Flexibility: ISO 20000 is more flexible in terms of implementation, allowing organizations to adapt the standard to their specific needs.
ITIL: The IT Service Management Framework
Focus: ITIL (Information Technology Infrastructure Library) is a comprehensive framework of best practices for ITSM. It offers guidance on managing various IT services and processes.
Certification: ITIL offers certification at different levels to individuals and organizations, demonstrating expertise in ITSM best practices.
Comprehensive: ITIL covers a wide range of ITSM topics, making it suitable for organizations seeking detailed guidance on specific processes and functions.
COBIT: The IT Governance and Management Framework
Focus: COBIT (Control Objectives for Information and Related Technologies) is focused on IT governance and management, including ITSM. It addresses not only IT processes but also risk management, compliance, and aligning IT with business goals.
Certification: COBIT certification is available, although it's less common compared to ITIL and ISO 20000.
Holistic: COBIT provides a holistic framework that combines ITSM with broader governance and management aspects, making it suitable for organizations concerned with overall IT governance.
The choice between ISO 20000, ITIL, or COBIT depends on an organization's specific needs, goals, and the level of detail and scope required for its ITSM and governance initiatives. Each framework has its strengths and is valuable in its own right, making it essential for organizations to assess their unique circumstances before making a decision.
Benefits of ISO 20000
ISO 20000, the international standard for IT Service Management (ITSM), offers numerous benefits to organizations that choose to adopt and implement it. These benefits extend to improving IT service quality, aligning IT with business goals, and enhancing overall operational efficiency. Here are the key benefits of ISO 20000:
Enhanced Service Quality: ISO 20000 provides a structured framework for managing IT services, ensuring consistent service quality. This leads to improved customer satisfaction and loyalty, as well as enhanced user experiences.
Operational Efficiency: ISO 20000 promotes the adoption of best practices and streamlined processes. This leads to increased operational efficiency, reduced downtime, and lower costs associated with IT service delivery.
Risk Management: ISO 20000 helps organizations identify and manage risks related to IT service delivery. This proactive approach to risk management ensures business continuity and minimizes potential disruptions.
Service Level Agreements (SLAs): ISO 20000 helps organizations define, agree upon, and manage SLAs with customers. This means clear expectations for service quality, availability, and performance, which contributes to customer satisfaction.
Clear Documentation and Records: Proper documentation and record-keeping are essential components of ISO 20000. This promotes transparency, accountability, and the ability to demonstrate compliance with the standard.
Global Recognition: ISO 20000 is internationally recognized and accepted. Achieving ISO 20000 certification can boost an organization's reputation, enhance its competitive advantage, and open up new business opportunities.
In summary, ISO 20000 offers a structured and internationally recognized framework for organizations to improve their IT service management. By implementing ISO 20000, organizations can achieve higher service quality, customer satisfaction, operational efficiency, and risk management, while aligning IT with business goals and complying with relevant regulations. This can lead to a competitive edge and enhanced overall performance.
The Structure of ISO 20000
The International Standard ISO/IEC 20000, which defines the requirements for IT Service Management (ITSM), is structured into multiple parts and sections to provide comprehensive guidance. As of my last knowledge update in September 2021, the standard consists of several parts. Please note that standards may be subject to updates and revisions, so it's essential to consult the latest version for precise details. Here's an overview of the typical structure of ISO 20000:
ISO/IEC 20000-1:2018 - Service management system requirements:
Terms and Definitions: Defines key terms and concepts used throughout the standard to ensure clarity and consistency.
Leadership: Explains the role of leadership in the SMS, emphasizing the need for commitment and support from top management.
Planning: Discusses the planning requirements for the SMS, including risk management, objectives, and how to achieve them.
Support: Describes the resources and support required for the SMS to operate effectively, including competence, awareness, communication, and documented information.
Operation: Details the processes and activities needed to deliver and manage IT services, including service design and transition, service delivery, and relationship management.
Performance Evaluation: Covers the monitoring, measurement, analysis, and evaluation of the SMS, including internal audits, management review, and performance indicators.
Improvement: Focuses on the continual improvement of the SMS, including non-conformities, corrective actions, preventive actions, and enhancement of the SMS.
ISO/IEC 20000-2 - Guidance on the application of service management systems:
This part offers additional guidance on how to apply the requirements outlined in ISO 20000-1. It provides practical insights, examples, and explanations to help organizations implement and maintain their Service Management System.
ISO/IEC 20000-3 - Guidance on scope definition and applicability of ISO/IEC 20000-1:
This part provides guidance on determining the scope of the Service Management System and the applicability of ISO 20000-1 within an organization.
ISO/IEC 20000-4 - Process Reference Model:
This part presents a reference model for ITSM processes. It outlines and describes the various ITSM processes that can be included in an SMS.
ISO/IEC 20000-5 - Exemplar implementation plan:
This part offers an exemplar implementation plan to help organizations understand the steps and activities involved in implementing ISO 20000.
Each part and section within ISO 20000 is designed to provide organizations with the guidance and requirements needed to establish and maintain a robust IT Service Management System. It offers a flexible framework that can be adapted to an organization's specific needs and requirements. To ensure compliance and effective implementation, it's essential to consult the latest version of the standard and consider working with experts in IT Service Management.
Certification Process
The certification process for ISO 20000, the international standard for IT Service Management (ITSM), involves a series of steps to demonstrate an organization's compliance with the standard's requirements. ISO 20000 certification is a valuable recognition of an organization's commitment to delivering high-quality IT services. Here are the typical steps in the ISO 20000 certification process:
Preliminary Gap Analysis:Before embarking on the certification process, it's often helpful to conduct a preliminary gap analysis. This analysis identifies the existing state of your ITSM practices compared to the requirements of ISO 20000. It helps you understand the areas that require improvement or adjustments.
Establish the Service Management System (SMS):ISO 20000 requires organizations to establish a Service Management System. This involves developing the necessary documentation, processes, and procedures to meet the standard's requirements. The SMS serves as the framework for IT service management within your organization.
Training and Awareness:Ensure that your staff is aware of the ISO 20000 standard and its requirements. Training may be necessary to equip your team with the knowledge and skills needed to implement and maintain the SMS effectively.
Documentation:Create and maintain the documentation required by ISO 20000. This includes developing policies, procedures, work instructions, and records related to IT service management. Documentation is essential to demonstrate compliance.
Implementation:Implement the SMS within your organization, aligning your ITSM practices with the requirements of ISO 20000. Ensure that the processes and procedures are operational and being followed.
Internal Audit:Conduct internal audits to evaluate the effectiveness of your SMS and identify areas for improvement. Internal audits help you uncover non-conformities and assess your readiness for external certification.
Certification Body Selection:Choose an accredited certification body to conduct the external audit and certification. Ensure that the certification body is recognized and accredited by relevant authorities.
External Certification Audit:The certification body will perform an external audit of your SMS to verify compliance with ISO 20000. This audit may include a review of documentation, interviews with personnel, and on-site assessments.
Certification Decision:Based on the findings of the external audit, the certification body will make a certification decision. If your organization has demonstrated compliance with ISO 20000, you will receive ISO 20000 certification.
ISO 20000 certification is a rigorous process that demonstrates an organization's commitment to excellence in ITSM. It not only enhances the quality of IT services but also builds trust with customers, stakeholders, and partners. Certification is typically valid for a defined period, after which organizations must undergo surveillance audits to maintain certification.
Common Misconceptions about ISO 20000
ISO 20000, as the international standard for IT Service Management (ITSM), is a valuable framework for improving IT service quality, efficiency, and compliance. However, like many standards, it is subject to misconceptions and misunderstandings. Here are some common misconceptions about ISO 20000:
ISO 20000 is Only for Large Enterprises:
Misconception: Some believe that ISO 20000 is suitable only for large enterprises with extensive IT resources and budgets.
Reality: ISO 20000 is scalable and can be implemented by organizations of all sizes, including small and medium-sized enterprises (SMEs). It can be adapted to suit an organization's specific needs and resources.
ISO 20000 is Too Complex:
Misconception: It is often assumed that ISO 20000's requirements are overly complex and challenging to implement.
Reality: While ISO 20000 is comprehensive, it can be tailored to an organization's needs. Its complexity depends on the organization's existing ITSM practices. It's possible to implement ISO 20000 incrementally and gradually.
ISO 20000 is All About Documentation:
Misconception: Some think ISO 20000 is primarily about generating extensive documentation.
Reality: While documentation is an important component, ISO 20000 places more emphasis on process implementation and effectiveness. Documentation supports the implementation of processes and helps ensure their consistency.
ISO 20000 is Only About ITIL:
Misconception: ISO 20000 is often confused with ITIL (Information Technology Infrastructure Library). People think they are one and the same.
Reality: While ITIL can be a valuable reference for implementing ISO 20000, the standard is not limited to ITIL and can be adapted to various ITSM frameworks or customized to an organization's specific needs.
ISO 20000 Guarantees Perfect IT Services:
Misconception: Some believe that ISO 20000 certification guarantees flawless IT services.
Reality: ISO 20000 helps improve service quality and consistency, but it doesn't eliminate the possibility of issues or disruptions. It provides a framework for addressing and mitigating such incidents.
ISO 20000 is Only for the IT Department:
Misconception: Some view ISO 20000 as solely the responsibility of the IT department.
Reality: ISO 20000 requires cross-functional involvement and alignment with the organization's business objectives. It impacts the entire organization, as IT services are integral to overall business operations.
Understanding and dispelling these misconceptions is essential for organizations considering ISO 20000 implementation. ISO 20000 can be a valuable asset for improving IT service management, and its benefits are attainable with proper planning and commitment.
ISO 20000 in Different Industries
ISO 20000, the international standard for IT Service Management (ITSM), is applicable to a wide range of industries, as effective IT service management is a fundamental need in today's technology-driven world. Here's how ISO 20000 can benefit different industries:
Information Technology (IT) Industry:In the IT industry, ISO 20000 helps IT service providers optimize their service management processes, ensuring efficient service delivery and improved customer satisfaction. It aligns IT services with business goals and enhances overall service quality.
Healthcare Industry:Healthcare organizations often rely heavily on IT systems for patient care, record-keeping, and operational efficiency. ISO 20000 can help healthcare providers ensure the reliability and security of their IT services, leading to better patient care and compliance with healthcare regulations.
Financial Services Industry:The financial sector depends on IT services for secure and efficient transactions, data management, and customer service. ISO 20000 can help financial organizations ensure the integrity and availability of their IT systems, reducing operational risks.
Government and Public Sector:Government agencies use IT services to deliver essential public services. ISO 20000 can help ensure that these services are efficient, cost-effective, and compliant with regulatory requirements, enhancing citizen satisfaction.
Education Industry:Educational institutions rely on IT services for administrative functions, e-learning, and research. ISO 20000 can help schools and universities improve the availability and performance of their IT services, ultimately benefiting students and faculty.
Retail Industry:Retailers use IT services for inventory management, e-commerce, and customer service. ISO 20000 can help retailers optimize their IT systems, providing customers with a seamless shopping experience.
Telecommunications Industry:Telecommunication companies provide essential IT services for communication and connectivity. ISO 20000 can help them deliver high-quality, uninterrupted services to customers.
various industries. Regardless of the sector, organizations can benefit from implementing ISO 20000 by optimizing IT service management, enhancing service quality, aligning IT with business objectives, and ensuring compliance with industry-specific regulations and standards. The specific ways in which ISO 20000 is applied may vary by industry, but the core principles of effective IT service management remain consistent.
Case Studies and Success Stories
Certainly, case studies and success stories can provide valuable insights into how organizations have benefited from implementing ISO 20000, the international standard for IT Service Management (ITSM). Here are a few examples of case studies and success stories related to ISO 20000:
A Large Financial Services Company:This financial services company implemented ISO 20000 to enhance its ITSM practices. By doing so, it achieved improved service quality, reduced downtime, and increased customer satisfaction. ISO 20000 helped the company streamline its IT processes, align IT services with business goals, and minimize IT-related risks.
A Healthcare Provider:A healthcare provider adopted ISO 20000 to optimize its IT services, ensuring that patient data was secure, and IT systems were reliable. ISO 20000 helped the organization maintain compliance with healthcare regulations, streamline IT processes, and deliver high-quality patient care.
An Educational Institution:An educational institution implemented ISO 20000 to improve its IT services for students, faculty, and administrative staff. The institution saw enhanced performance of its e-learning platforms, reduced service disruptions, and greater overall satisfaction among students and faculty.
A Government Agency:A government agency adopted ISO 20000 to enhance the delivery of public services. By improving the efficiency and reliability of its IT services, the agency increased citizen satisfaction, reduced operational costs, and met regulatory requirements more effectively.
A Telecommunications Company:A telecommunications company implemented ISO 20000 to ensure the availability and reliability of its communication services. The adoption of ISO 20000 led to reduced network downtime, improved customer experiences, and a competitive edge in the telecommunications market.
These case studies and success stories illustrate the broad applicability of ISO 20000 across diverse industries. They demonstrate how organizations have leveraged ISO 20000 to improve IT service quality, align IT with business objectives, and gain a competitive advantage. Whether it's a financial services firm, a healthcare provider, an educational institution, a government agency, or a telecommunications company, ISO 20000 has proven to be a valuable framework for optimizing IT service management and delivering better services to customers and stakeholders.
Conclusion
In conclusion, ISO 20000, the international standard for IT Service Management, is a versatile and valuable framework that can benefit organizations across various industries. Its structured approach to IT service management ensures consistent service quality, alignment with business goals, and compliance with relevant regulations and standards.
ISO 20000 is not limited to large enterprises but can be adapted and implemented by organizations of all sizes. It's a dynamic standard that promotes continuous improvement, emphasizing the importance of monitoring, evaluation, and adaptation in response to changing customer needs and technological advancements.
Through ISO 20000, organizations can enhance their IT service delivery, reduce downtime, manage risks, and improve customer satisfaction. It's a tool that encourages cross-functional collaboration, as it acknowledges that IT services impact all aspects of an organization, not just the IT department.
Ultimately, ISO 20000 offers a structured path to achieving excellence in IT service management. By implementing its principles and practices, organizations can enhance their competitiveness, reduce operational risks, and ensure that IT services are a strategic asset for their overall business success.
Read More
In today's rapidly evolving digital landscape, effective IT service management is crucial for businesses to stay competitive, deliver exceptional customer experiences, and ensure the smooth operation of their IT services. One framework that has gained prominence in this regard is ISO 20000.
ISO 20000 is an internationally recognized standard for IT Service Management (ITSM). It provides a set of best practices and guidelines for organizations to establish, implement, maintain, and continually improve their ITSM system. This standard is designed to ensure that IT services meet the needs of the organization and its customers, while also complying with regulatory and quality requirements.
Over the course of this blog series, we will delve deeper into these components, explore best practices, and provide insights into achieving ISO 20000 certification.
Whether you're an IT professional, a business owner, or simply someone interested in IT service management, understanding ISO 20000 is invaluable in today's technology-driven world. It's a path to ensuring that IT services are not just reliable but also a strategic asset for your organization.
Stay tuned as we explore the principles, benefits, and practical steps towards implementing ISO 20000 IT Service Management. The journey begins here.
Table of contents
-
The Origins of ISO 20000
-
The Importance of Standardization
-
Key Principles of ISO 20000
-
ISO 20000 vs. Other ITSM Frameworks
-
Benefits of ISO 20000
-
The Structure of ISO 20000
-
Certification Process
-
Common Misconceptions about ISO 20000
-
ISO 20000 in Different Industries
-
Case Studies and Success Stories
-
Conclusion
The Origins of ISO 20000
The Origins of ISO 20000: From ITIL to Global Standard
ISO 20000, formally known as ISO/IEC 20000, is an international standard that has its roots in the Information Technology Infrastructure Library (ITIL) and the need for global consistency in IT service management practices.
ITIL and the Need for Standardization
The story of ISO 20000 begins with ITIL, a set of best practices for IT service management that originated in the United Kingdom in the 1980s. ITIL was developed by the UK government in response to a lack of standardization and structure in IT service management practices. ITIL provided a framework for organizations to better manage their IT services, with a focus on aligning IT with business needs, improving service quality, and increasing efficiency.
ITIL gained widespread acceptance and was adopted by organizations worldwide. It became the de facto framework for IT service management, and its popularity spurred the need for an international standard that would ensure consistency and quality in IT service management practices across the globe.
The Path to ISO 20000
The journey towards ISO 20000 can be summarized in the following key milestones:
BS 15000: The first significant step toward international standardization was the development of the British Standard BS 15000. Published in 2000, BS 15000 was essentially a formalization of ITIL concepts into a national standard. This standard laid the groundwork for what would later become ISO 20000.
ISO/IEC 20000-1 and -2: The international standardization process began with the collaboration of several international standards bodies. ISO/IEC 20000 was published in 2005, comprising two parts: Part 1 specifies the requirements for IT service management, while Part 2 provides guidance on the application of Part 1. These standards were developed to provide a globally accepted framework for IT service management.
ISO 20000-2018: The standard has seen updates and revisions over the years, with ISO 20000:2018 being the most recent version as of my last knowledge update in September 2021. This revision refined and expanded the standard to align with modern IT service management practices and principles.
Why ISO 20000 Matters
ISO 20000 is vital because it brings a unified approach to IT service management, which is especially crucial in today's globally interconnected business environment. It provides a framework that organizations can use to ensure that their IT services are reliable, efficient, and meet both customer and regulatory requirements.
In summary, ISO 20000's origins can be traced back to the need for standardization in IT service management, stemming from the success of ITIL. It has since evolved into an internationally recognized standard, helping organizations worldwide improve their IT service delivery and achieve operational excellence. As IT continues to be a critical component of modern business operations, ISO 20000's relevance and importance continue to grow.
The Importance of Standardization
In the ever-evolving world of information technology, where innovation and change are constant, standardization plays a pivotal role in ensuring the efficiency, quality, and reliability of IT services. Standardization is particularly crucial in the realm of IT Service Management (ITSM), and ISO 20000 is a prime example of how it contributes to excellence. Let's delve into the significance of standardization in ITSM:
Consistency and Predictability: Standardization establishes a set of consistent processes, procedures, and best practices. In the context of ITSM, this consistency ensures that IT services are delivered in a predictable manner. Customers and stakeholders can rely on consistent service quality, which fosters trust and confidence.
Improved Efficiency: Standardized processes eliminate redundancy and confusion in IT service delivery. This, in turn, leads to improved efficiency, as employees can follow well-defined procedures, reducing the time and effort required to complete tasks.
Quality Assurance: Quality control is a fundamental aspect of standardization. By adhering to established standards and best practices, organizations can consistently deliver high-quality IT services. Standardization helps identify and address potential quality issues proactively.
Risk Management: Standardization aids in risk management by identifying and mitigating potential risks in IT service delivery. By following standardized processes and procedures, organizations can reduce the likelihood of errors and vulnerabilities that might negatively impact services.
Scalability: Standardized processes can be scaled more easily. As organizations grow or adapt to changing circumstances, they can expand their IT service operations efficiently by replicating established standards and processes.
Knowledge Sharing: Standardized processes and best practices make it easier for employees to share knowledge and collaborate. This contributes to a culture of continuous improvement and learning within the organization.
Competitive Advantage: Organizations that adhere to internationally recognized standards like ISO 20000 gain a competitive advantage. They can demonstrate their commitment to quality and best practices, which can be a selling point for customers and partners.
In the realm of ITSM, ISO 20000 exemplifies the importance of standardization by providing a globally recognized framework for IT service management. It empowers organizations to align their IT services with business objectives, deliver consistent quality, and remain adaptable in a rapidly changing IT landscape.
In summary, standardization in IT Service Management is essential for achieving operational excellence, meeting customer expectations, and managing risk. ISO 20000's global acceptance underscores the importance of adhering to best practices and standards to ensure that IT services are a strategic asset for organizations in today's technology-driven world.
Key Principles of ISO 20000
Certainly, ISO 20000 is built upon several key principles that guide IT Service Management (ITSM) practices. These principles provide a foundation for organizations seeking to implement ISO 20000 and improve their IT services. Here are the key principles of ISO 20000:
Customer Focus: ISO 20000 places a strong emphasis on meeting customer needs and delivering services that align with the organization's overall business objectives. It requires IT service providers to understand and prioritize customer requirements and expectations.
Leadership and Commitment: The commitment of top management is crucial for the successful implementation of ISO 20000. Leaders within the organization must support and drive the ITSM initiatives, setting the tone for a culture of service excellence.
Process Approach: ISO 20000 promotes a process-driven approach to ITSM. This means defining, documenting, and consistently following well-defined processes and procedures to manage IT services effectively.
Improvement: Continuous improvement is a fundamental principle of ISO 20000. Organizations are encouraged to regularly monitor and measure their ITSM processes, identify areas for improvement, and implement changes to enhance service quality.
Supplier Management: ISO 20000 acknowledges the role of suppliers and service providers in the delivery of IT services. It emphasizes the importance of managing and monitoring supplier relationships to ensure they meet service requirements.
Service Level Management: This principle underscores the need to define, agree upon, and manage service level agreements (SLAs) with customers. It involves setting clear expectations for service quality, availability, and performance.
Documentation and Records: Proper documentation and record-keeping are vital for demonstrating compliance with ISO 20000 requirements. This principle ensures that organizations maintain accurate records of their ITSM processes and activities.
These key principles provide a holistic framework for IT service management that is not only aligned with customer needs but also focused on continuous improvement and accountability. Organizations that adhere to these principles are better positioned to deliver high-quality IT services that drive business success and customer satisfaction.
ISO 20000 vs. Other ITSM Frameworks
IT Service Management (ITSM) is critical for organizations to deliver efficient and high-quality IT services. To achieve this, various ITSM frameworks and standards have been developed, each with its own approach and methodologies. ISO 20000 is one such standard, but how does it compare to other well-known ITSM frameworks like ITIL and COBIT? Let's explore the key differences and similarities in this comparative analysis:
ISO 20000: The International Standard
Focus: ISO 20000 is an international standard that specifies requirements for ITSM. It emphasizes process-driven IT service delivery, compliance, and continual improvement.
Certification: ISO 20000 provides a certification process for organizations to demonstrate compliance with the standard.
Flexibility: ISO 20000 is more flexible in terms of implementation, allowing organizations to adapt the standard to their specific needs.
ITIL: The IT Service Management Framework
Focus: ITIL (Information Technology Infrastructure Library) is a comprehensive framework of best practices for ITSM. It offers guidance on managing various IT services and processes.
Certification: ITIL offers certification at different levels to individuals and organizations, demonstrating expertise in ITSM best practices.
Comprehensive: ITIL covers a wide range of ITSM topics, making it suitable for organizations seeking detailed guidance on specific processes and functions.
COBIT: The IT Governance and Management Framework
Focus: COBIT (Control Objectives for Information and Related Technologies) is focused on IT governance and management, including ITSM. It addresses not only IT processes but also risk management, compliance, and aligning IT with business goals.
Certification: COBIT certification is available, although it's less common compared to ITIL and ISO 20000.
Holistic: COBIT provides a holistic framework that combines ITSM with broader governance and management aspects, making it suitable for organizations concerned with overall IT governance.
The choice between ISO 20000, ITIL, or COBIT depends on an organization's specific needs, goals, and the level of detail and scope required for its ITSM and governance initiatives. Each framework has its strengths and is valuable in its own right, making it essential for organizations to assess their unique circumstances before making a decision.
Benefits of ISO 20000
ISO 20000, the international standard for IT Service Management (ITSM), offers numerous benefits to organizations that choose to adopt and implement it. These benefits extend to improving IT service quality, aligning IT with business goals, and enhancing overall operational efficiency. Here are the key benefits of ISO 20000:
Enhanced Service Quality: ISO 20000 provides a structured framework for managing IT services, ensuring consistent service quality. This leads to improved customer satisfaction and loyalty, as well as enhanced user experiences.
Operational Efficiency: ISO 20000 promotes the adoption of best practices and streamlined processes. This leads to increased operational efficiency, reduced downtime, and lower costs associated with IT service delivery.
Risk Management: ISO 20000 helps organizations identify and manage risks related to IT service delivery. This proactive approach to risk management ensures business continuity and minimizes potential disruptions.
Service Level Agreements (SLAs): ISO 20000 helps organizations define, agree upon, and manage SLAs with customers. This means clear expectations for service quality, availability, and performance, which contributes to customer satisfaction.
Clear Documentation and Records: Proper documentation and record-keeping are essential components of ISO 20000. This promotes transparency, accountability, and the ability to demonstrate compliance with the standard.
Global Recognition: ISO 20000 is internationally recognized and accepted. Achieving ISO 20000 certification can boost an organization's reputation, enhance its competitive advantage, and open up new business opportunities.
In summary, ISO 20000 offers a structured and internationally recognized framework for organizations to improve their IT service management. By implementing ISO 20000, organizations can achieve higher service quality, customer satisfaction, operational efficiency, and risk management, while aligning IT with business goals and complying with relevant regulations. This can lead to a competitive edge and enhanced overall performance.
The Structure of ISO 20000
The International Standard ISO/IEC 20000, which defines the requirements for IT Service Management (ITSM), is structured into multiple parts and sections to provide comprehensive guidance. As of my last knowledge update in September 2021, the standard consists of several parts. Please note that standards may be subject to updates and revisions, so it's essential to consult the latest version for precise details. Here's an overview of the typical structure of ISO 20000:
ISO/IEC 20000-1:2018 - Service management system requirements:
Terms and Definitions: Defines key terms and concepts used throughout the standard to ensure clarity and consistency.
Leadership: Explains the role of leadership in the SMS, emphasizing the need for commitment and support from top management.
Planning: Discusses the planning requirements for the SMS, including risk management, objectives, and how to achieve them.
Support: Describes the resources and support required for the SMS to operate effectively, including competence, awareness, communication, and documented information.
Operation: Details the processes and activities needed to deliver and manage IT services, including service design and transition, service delivery, and relationship management.
Performance Evaluation: Covers the monitoring, measurement, analysis, and evaluation of the SMS, including internal audits, management review, and performance indicators.
Improvement: Focuses on the continual improvement of the SMS, including non-conformities, corrective actions, preventive actions, and enhancement of the SMS.
ISO/IEC 20000-2 - Guidance on the application of service management systems:
This part offers additional guidance on how to apply the requirements outlined in ISO 20000-1. It provides practical insights, examples, and explanations to help organizations implement and maintain their Service Management System.
ISO/IEC 20000-3 - Guidance on scope definition and applicability of ISO/IEC 20000-1:
This part provides guidance on determining the scope of the Service Management System and the applicability of ISO 20000-1 within an organization.
ISO/IEC 20000-4 - Process Reference Model:
This part presents a reference model for ITSM processes. It outlines and describes the various ITSM processes that can be included in an SMS.
ISO/IEC 20000-5 - Exemplar implementation plan:
This part offers an exemplar implementation plan to help organizations understand the steps and activities involved in implementing ISO 20000.
Each part and section within ISO 20000 is designed to provide organizations with the guidance and requirements needed to establish and maintain a robust IT Service Management System. It offers a flexible framework that can be adapted to an organization's specific needs and requirements. To ensure compliance and effective implementation, it's essential to consult the latest version of the standard and consider working with experts in IT Service Management.
Certification Process
The certification process for ISO 20000, the international standard for IT Service Management (ITSM), involves a series of steps to demonstrate an organization's compliance with the standard's requirements. ISO 20000 certification is a valuable recognition of an organization's commitment to delivering high-quality IT services. Here are the typical steps in the ISO 20000 certification process:
Preliminary Gap Analysis:Before embarking on the certification process, it's often helpful to conduct a preliminary gap analysis. This analysis identifies the existing state of your ITSM practices compared to the requirements of ISO 20000. It helps you understand the areas that require improvement or adjustments.
Establish the Service Management System (SMS):ISO 20000 requires organizations to establish a Service Management System. This involves developing the necessary documentation, processes, and procedures to meet the standard's requirements. The SMS serves as the framework for IT service management within your organization.
Training and Awareness:Ensure that your staff is aware of the ISO 20000 standard and its requirements. Training may be necessary to equip your team with the knowledge and skills needed to implement and maintain the SMS effectively.
Documentation:Create and maintain the documentation required by ISO 20000. This includes developing policies, procedures, work instructions, and records related to IT service management. Documentation is essential to demonstrate compliance.
Implementation:Implement the SMS within your organization, aligning your ITSM practices with the requirements of ISO 20000. Ensure that the processes and procedures are operational and being followed.
Internal Audit:Conduct internal audits to evaluate the effectiveness of your SMS and identify areas for improvement. Internal audits help you uncover non-conformities and assess your readiness for external certification.
Certification Body Selection:Choose an accredited certification body to conduct the external audit and certification. Ensure that the certification body is recognized and accredited by relevant authorities.
External Certification Audit:The certification body will perform an external audit of your SMS to verify compliance with ISO 20000. This audit may include a review of documentation, interviews with personnel, and on-site assessments.
Certification Decision:Based on the findings of the external audit, the certification body will make a certification decision. If your organization has demonstrated compliance with ISO 20000, you will receive ISO 20000 certification.
ISO 20000 certification is a rigorous process that demonstrates an organization's commitment to excellence in ITSM. It not only enhances the quality of IT services but also builds trust with customers, stakeholders, and partners. Certification is typically valid for a defined period, after which organizations must undergo surveillance audits to maintain certification.
Common Misconceptions about ISO 20000
ISO 20000, as the international standard for IT Service Management (ITSM), is a valuable framework for improving IT service quality, efficiency, and compliance. However, like many standards, it is subject to misconceptions and misunderstandings. Here are some common misconceptions about ISO 20000:
ISO 20000 is Only for Large Enterprises:
Misconception: Some believe that ISO 20000 is suitable only for large enterprises with extensive IT resources and budgets.
Reality: ISO 20000 is scalable and can be implemented by organizations of all sizes, including small and medium-sized enterprises (SMEs). It can be adapted to suit an organization's specific needs and resources.
ISO 20000 is Too Complex:
Misconception: It is often assumed that ISO 20000's requirements are overly complex and challenging to implement.
Reality: While ISO 20000 is comprehensive, it can be tailored to an organization's needs. Its complexity depends on the organization's existing ITSM practices. It's possible to implement ISO 20000 incrementally and gradually.
ISO 20000 is All About Documentation:
Misconception: Some think ISO 20000 is primarily about generating extensive documentation.
Reality: While documentation is an important component, ISO 20000 places more emphasis on process implementation and effectiveness. Documentation supports the implementation of processes and helps ensure their consistency.
ISO 20000 is Only About ITIL:
Misconception: ISO 20000 is often confused with ITIL (Information Technology Infrastructure Library). People think they are one and the same.
Reality: While ITIL can be a valuable reference for implementing ISO 20000, the standard is not limited to ITIL and can be adapted to various ITSM frameworks or customized to an organization's specific needs.
ISO 20000 Guarantees Perfect IT Services:
Misconception: Some believe that ISO 20000 certification guarantees flawless IT services.
Reality: ISO 20000 helps improve service quality and consistency, but it doesn't eliminate the possibility of issues or disruptions. It provides a framework for addressing and mitigating such incidents.
ISO 20000 is Only for the IT Department:
Misconception: Some view ISO 20000 as solely the responsibility of the IT department.
Reality: ISO 20000 requires cross-functional involvement and alignment with the organization's business objectives. It impacts the entire organization, as IT services are integral to overall business operations.
Understanding and dispelling these misconceptions is essential for organizations considering ISO 20000 implementation. ISO 20000 can be a valuable asset for improving IT service management, and its benefits are attainable with proper planning and commitment.
ISO 20000 in Different Industries
ISO 20000, the international standard for IT Service Management (ITSM), is applicable to a wide range of industries, as effective IT service management is a fundamental need in today's technology-driven world. Here's how ISO 20000 can benefit different industries:
Information Technology (IT) Industry:In the IT industry, ISO 20000 helps IT service providers optimize their service management processes, ensuring efficient service delivery and improved customer satisfaction. It aligns IT services with business goals and enhances overall service quality.
Healthcare Industry:Healthcare organizations often rely heavily on IT systems for patient care, record-keeping, and operational efficiency. ISO 20000 can help healthcare providers ensure the reliability and security of their IT services, leading to better patient care and compliance with healthcare regulations.
Financial Services Industry:The financial sector depends on IT services for secure and efficient transactions, data management, and customer service. ISO 20000 can help financial organizations ensure the integrity and availability of their IT systems, reducing operational risks.
Government and Public Sector:Government agencies use IT services to deliver essential public services. ISO 20000 can help ensure that these services are efficient, cost-effective, and compliant with regulatory requirements, enhancing citizen satisfaction.
Education Industry:Educational institutions rely on IT services for administrative functions, e-learning, and research. ISO 20000 can help schools and universities improve the availability and performance of their IT services, ultimately benefiting students and faculty.
Retail Industry:Retailers use IT services for inventory management, e-commerce, and customer service. ISO 20000 can help retailers optimize their IT systems, providing customers with a seamless shopping experience.
Telecommunications Industry:Telecommunication companies provide essential IT services for communication and connectivity. ISO 20000 can help them deliver high-quality, uninterrupted services to customers.
various industries. Regardless of the sector, organizations can benefit from implementing ISO 20000 by optimizing IT service management, enhancing service quality, aligning IT with business objectives, and ensuring compliance with industry-specific regulations and standards. The specific ways in which ISO 20000 is applied may vary by industry, but the core principles of effective IT service management remain consistent.
Case Studies and Success Stories
Certainly, case studies and success stories can provide valuable insights into how organizations have benefited from implementing ISO 20000, the international standard for IT Service Management (ITSM). Here are a few examples of case studies and success stories related to ISO 20000:
A Large Financial Services Company:This financial services company implemented ISO 20000 to enhance its ITSM practices. By doing so, it achieved improved service quality, reduced downtime, and increased customer satisfaction. ISO 20000 helped the company streamline its IT processes, align IT services with business goals, and minimize IT-related risks.
A Healthcare Provider:A healthcare provider adopted ISO 20000 to optimize its IT services, ensuring that patient data was secure, and IT systems were reliable. ISO 20000 helped the organization maintain compliance with healthcare regulations, streamline IT processes, and deliver high-quality patient care.
An Educational Institution:An educational institution implemented ISO 20000 to improve its IT services for students, faculty, and administrative staff. The institution saw enhanced performance of its e-learning platforms, reduced service disruptions, and greater overall satisfaction among students and faculty.
A Government Agency:A government agency adopted ISO 20000 to enhance the delivery of public services. By improving the efficiency and reliability of its IT services, the agency increased citizen satisfaction, reduced operational costs, and met regulatory requirements more effectively.
A Telecommunications Company:A telecommunications company implemented ISO 20000 to ensure the availability and reliability of its communication services. The adoption of ISO 20000 led to reduced network downtime, improved customer experiences, and a competitive edge in the telecommunications market.
These case studies and success stories illustrate the broad applicability of ISO 20000 across diverse industries. They demonstrate how organizations have leveraged ISO 20000 to improve IT service quality, align IT with business objectives, and gain a competitive advantage. Whether it's a financial services firm, a healthcare provider, an educational institution, a government agency, or a telecommunications company, ISO 20000 has proven to be a valuable framework for optimizing IT service management and delivering better services to customers and stakeholders.
Conclusion
In conclusion, ISO 20000, the international standard for IT Service Management, is a versatile and valuable framework that can benefit organizations across various industries. Its structured approach to IT service management ensures consistent service quality, alignment with business goals, and compliance with relevant regulations and standards.
ISO 20000 is not limited to large enterprises but can be adapted and implemented by organizations of all sizes. It's a dynamic standard that promotes continuous improvement, emphasizing the importance of monitoring, evaluation, and adaptation in response to changing customer needs and technological advancements.
Through ISO 20000, organizations can enhance their IT service delivery, reduce downtime, manage risks, and improve customer satisfaction. It's a tool that encourages cross-functional collaboration, as it acknowledges that IT services impact all aspects of an organization, not just the IT department.
Ultimately, ISO 20000 offers a structured path to achieving excellence in IT service management. By implementing its principles and practices, organizations can enhance their competitiveness, reduce operational risks, and ensure that IT services are a strategic asset for their overall business success.
Project management fundamentals?
Project management is a critical discipline that plays a pivotal role in the successful execution of endeavors across various industries. Whether you're working on a construction project, a software development initiative, or even planning a personal event, the principles of project management are universally applicable.
At its core, project management involves a systematic approach to achieving specific objectives within a defined timeframe and utilizing available resources effectively. It provides a structured framework for breaking down complex tasks, managing risks, facilitating communication, and ensuring that all project stakeholders are aligned toward a common goal.
This introduction sets the stage for a deeper exploration of project management fundamentals, from initiating a project and developing comprehensive plans to executing tasks, controlling progress, and ultimately bringing the project to a successful conclusion. By mastering these fundamental concepts, individuals and organizations can enhance their ability to deliver results, adapt to changes, and overcome challenges that inevitably arise in the world of project management.
Table of contents
-
Project Initiation
-
Project Planning
-
Risk Management
-
Project Execution
-
Communication Management
-
Project Monitoring and Control
-
Project Closure
-
Project Lifecycle Models
-
Project Software and Tools
-
Ethical and Legal Aspects
-
Conclusion
Project Initiation
Project Initiation is the first and crucial phase of the project management process. During this stage, the project is defined, authorized, and its purpose and scope are clearly established. Here's a more detailed look at the key aspects of Project Initiation:
Project Charter:Creation of a project charter, which is a formal document that authorizes the existence of the project. It outlines the project's objectives, stakeholders, and high-level scope.
Stakeholder Identification:Identifying all relevant stakeholders who will be affected by or have an impact on the project. This includes internal and external parties, such as team members, customers, sponsors, and regulatory bodies.
Feasibility Study:Conducting a feasibility analysis to assess the project's viability. This analysis may include factors like economic, operational, technical, legal, scheduling, and resource feasibility.
Risk Identification:Identifying potential risks and challenges that the project may face. While a detailed risk assessment typically occurs later in the project, initial risk identification is critical during initiation.
Project Manager Assignment:Appointing a project manager or leader who will be responsible for the overall planning, execution, and control of the project.
Project Initiation Documentation:Creating documentation to capture all the essential information gathered during initiation, such as the project charter, stakeholder analysis, and initial risk assessment.
Successful project initiation sets the stage for the entire project. It provides clarity regarding the project's objectives, scope, and constraints, and ensures that all relevant parties understand and agree on what needs to be achieved. Without a well-executed initiation phase, a project can struggle with unclear direction, scope creep, and a lack of stakeholder commitment, which can lead to project failure.
Project Planning
Project Planning is a critical phase in project management that follows the project initiation. During this phase, detailed plans and strategies are developed to guide the project's execution. Effective project planning is essential for setting clear expectations, allocating resources, and ensuring that the project stays on track. Here are the key components of project planning:
Work Breakdown Structure (WBS):Create a hierarchical structure that organizes project work into smaller, more manageable components. The WBS helps in visualizing and understanding the project's structure.
Task Scheduling:Develop a detailed project schedule that specifies when each task or activity will be executed. Tools like Gantt charts and network diagrams are commonly used for scheduling.
Resource Allocation:Identify and allocate the necessary resources, including personnel, equipment, materials, and budget, to carry out the project work.
Risk Management Plan:Create a comprehensive plan for identifying, assessing, mitigating, and monitoring project risks. This plan should outline strategies to address potential issues.
Quality Plan:Define quality standards and establish processes and criteria for quality assurance and control throughout the project.
Communication Plan:Develop a communication plan that outlines who needs to be informed about project progress, how often, and through which channels.
Stakeholder Engagement Plan:Define how stakeholders will be engaged and managed throughout the project. This includes strategies for managing expectations and addressing stakeholder concerns.
Change Management Plan:Develop a plan to handle potential changes in project scope or requirements. Outline procedures for change requests, approvals, and impact assessments.
Documentation:Maintain detailed documentation of the project plan, including all associated plans and schedules. This documentation ensures that everyone involved in the project is working from a common understanding.
Effective project planning is essential for aligning the project team, managing resources efficiently, and minimizing risks. A well-thought-out project plan serves as a roadmap for the entire project, helping to keep it on course and facilitating effective communication and coordination among team members and stakeholders.
Risk Management
Risk management is a critical aspect of project management, aimed at identifying, analyzing, and mitigating potential risks that could impact a project's success. Here are the key components of risk management:
Risk Identification:The first step is to identify and document potential risks. This involves brainstorming with the project team and stakeholders to create a comprehensive list of both internal and external risks.
Risk Analysis:Assess the identified risks in terms of their probability and potential impact. This helps prioritize which risks are most significant and require the most attention.
Risk Assessment:After analyzing risks, it's important to assess them based on their severity and likelihood. This often involves creating a risk matrix or heat map to categorize and prioritize risks.
Risk Monitoring:Continuously monitor identified risks throughout the project lifecycle. Regularly review the status of risks and assess whether new risks have emerged.
Risk Reporting:Provide regular risk reports to stakeholders, keeping them informed about the status of risks and the effectiveness of risk mitigation strategies.
Change Control:Implement a structured change control process to manage changes that may arise due to risks or other factors. This ensures that changes are evaluated and approved before being incorporated into the project.
Risk Register:Maintain a risk register, which is a document that contains information about all identified risks, their status, and the actions taken to address them.
Effective risk management helps project managers and teams anticipate and address potential issues before they become major problems. It allows for proactive decision-making, which can ultimately save time, resources, and prevent project failure.
Project Execution
Project Execution is the phase in the project management process where the actual project work is carried out, and the project plan is put into action. This phase involves coordinating people and resources, ensuring that tasks are completed as per the project schedule, and continuously monitoring progress to meet project objectives. Here are key aspects of Project Execution:
Team Management:
Assign tasks to team members and ensure that they understand their roles and responsibilities.
Foster a positive team environment, encourage collaboration, and address any conflicts or issues that may arise.
Task Execution:Initiate and complete project tasks according to the defined schedule, quality standards, and scope.
Monitor task progress and address any deviations or delays promptly.
Communication:Maintain regular and effective communication among team members and stakeholders to provide updates on project progress, resolve issues, and ensure everyone is informed.
Quality Assurance:Implement quality control measures to ensure that project deliverables meet the predefined quality standards.
Change Management:Manage changes to the project scope, schedule, or resources through the established change control process.
Issue Resolution:Identify and address any issues or roadblocks that arise during the project. Implement solutions to keep the project on track.
Document Control:Ensure that project documentation is properly managed, updated, and accessible to the project team as needed.
Safety and Compliance:Monitor safety standards and compliance with relevant laws and regulations, particularly in projects with health, safety, or legal requirements.
Project Execution is the phase where the project plan comes to life, and it requires strong leadership, effective communication, and continuous monitoring to ensure that the project progresses according to the established parameters. It's critical to stay adaptable and responsive to changes and challenges that may arise during this phase to keep the project on the path to success.
Communication Management
Communication Management is a critical aspect of project management that focuses on planning, executing, and controlling communication within a project. Effective communication ensures that all stakeholders are informed, engaged, and aligned with project goals and progress. Here are key components of Communication Management in project management:
Stakeholder Identification and Analysis:Identify and analyze project stakeholders, understanding their needs, interests, influence, and communication preferences.
Communication Channels:Select appropriate communication channels for different types of information and stakeholders. This could include meetings, emails, reports, project management software, or other tools.
Information Distribution:Disseminate project information to stakeholders as per the communication plan. Ensure that the right information reaches the right people at the right time.
Status Reporting:Regularly report on project status, progress, and key performance indicators (KPIs) to stakeholders, keeping them informed about the project's health.
Feedback Collection:Encourage and collect feedback from stakeholders to gauge their satisfaction, concerns, and suggestions for improving project performance.
Documentation and Records:Maintain comprehensive project records, including meeting minutes, reports, emails, and other communication artifacts for reference and audit purposes.
Communication Technology:Utilize project management software and collaboration tools to facilitate communication, share documents, and track project progress.
Effective Communication Management is essential for ensuring that all project stakeholders are informed, engaged, and supportive of the project's goals. It helps prevent misunderstandings, manage expectations, and facilitate the timely resolution of issues. Poor communication can lead to project delays, scope creep, and stakeholder dissatisfaction, so it's a critical aspect of project success.
Project Monitoring and Control
Project Monitoring and Control is a vital phase in the project management process that occurs concurrently with project execution. It involves tracking, reviewing, and regulating project performance to ensure that the project stays on track and aligns with its objectives. Here are the key aspects of Project Monitoring and Control:
Performance Measurement:Continuously measure and assess project performance using key performance indicators (KPIs) and other relevant metrics. This helps in understanding how well the project is progressing.
Scope Control:Ensure that the project remains within the defined scope and that scope changes are properly evaluated and approved through the change control process.
Quality Control:Implement quality control measures to ensure that project deliverables meet the defined quality standards. Conduct regular quality inspections and make necessary corrections.
Issue Management:Address issues and challenges as they arise. Develop solutions and corrective actions to resolve problems that could impact project success.
Document Management:Manage project documentation and records, ensuring that they are up to date and accessible for reference and audits.
Progress Reporting:Provide regular project status reports to stakeholders, highlighting achievements, issues, and upcoming milestones.
Resource Optimization:Optimize resource allocation to ensure that resources are used efficiently and that project team members are not overburdened.
Audit and Review:Conduct periodic project reviews and audits to ensure compliance with project plans, policies, and quality standards.
Project Monitoring and Control is a continuous process that helps project managers and teams maintain control over a project's progress and make necessary adjustments to keep it aligned with the original goals and objectives. It is essential for preventing and addressing deviations that could jeopardize project success.
Project Closure
Project Closure is the final phase in the project management process, where the project is formally completed, and all necessary activities are conducted to bring the project to a successful conclusion. Here are key components of Project Closure:
Customer or Stakeholder Acceptance:Obtain formal acceptance and sign-off from the customer or stakeholders to acknowledge that the project objectives have been met.
Transition Plan:If the project has ongoing operational aspects, create and implement a transition plan to hand over the project's results to the appropriate operational teams or personnel.
Closure Criteria:Define and meet specific criteria or checklists that signify the project's readiness for closure, such as the completion of all tasks, approval of deliverables, and successful testing.
Financial Closure:Complete all financial activities, such as closing project accounts, reconciling expenses, and ensuring all financial records are accurate.
Project Documentation:Organize and archive all project documentation, making it accessible for future reference, audits, or compliance purposes.
Project Closure Report:Prepare a formal project closure report, summarizing the project's achievements, issues faced, and the final budget and schedule performance.
Legal and Contractual Closure:Address any legal or contractual obligations, such as final payments to vendors or contractors and the formal termination of contracts.
Archiving:Store project documentation and records in a secure archive for future reference, ensuring they are easily retrievable if needed.
Project Team Disbandment:If the project team is disbanded, facilitate a smooth transition for team members to their next assignments or projects.
Project Closure is a crucial phase that provides a sense of closure and accomplishment for the project team and stakeholders. Properly closing a project helps ensure that resources are freed up for other initiatives and that valuable insights from the project can be used to improve future projects.
Project Lifecycle Models
Project lifecycle models represent the stages and phases a project goes through, from initiation to completion. Different projects may require different lifecycle models based on their specific characteristics, requirements, and industry. Here are some commonly used project lifecycle models:
Kanban:
Kanban is another Agile framework that visualizes work on a Kanban board. It focuses on limiting work in progress and optimizing flow, making it suitable for continuous improvement projects.
V-Model (Validation and Verification Model):
The V-Model is an extension of the Waterfall model. It emphasizes the relationship between development phases and corresponding testing phases. Each development phase has a corresponding validation and verification phase.
RAD (Rapid Application Development):
RAD is an incremental software development process that puts a premium on rapid prototyping and speedy feedback. It's often used for time-sensitive projects with well-understood requirements.
Big Bang Model:
The Big Bang model is characterized by minimal planning and requirements definition. It is suitable for small projects with few constraints, where development starts with a vague idea and evolves over time.
Hybrid Models:
Some projects may benefit from a combination of different lifecycle models. For example, a project might start with a Waterfall approach for planning and gradually transition to Agile methods for development and testing.
The choice of a project lifecycle model depends on the project's specific needs, constraints, and goals. It's important to select the most appropriate model and adapt it as necessary to ensure the successful completion of the project. Each model has its advantages and limitations, and the project manager should consider these factors when making a choice.
Project Software and Tools
Project management software and tools play a crucial role in planning, executing, monitoring, and controlling projects. They help streamline tasks, improve collaboration, and enhance communication. Here are some popular project management software and tools:
Microsoft Project:
A comprehensive project management tool that includes features for project planning, scheduling, resource allocation, and reporting.
Trello:
A visual project management tool that uses boards, lists, and cards to help teams organize tasks and track progress.
Asana:
A web-based platform for project and task management that offers tools for team collaboration and project planning.
Basecamp:
A user-friendly project management and team collaboration tool that includes to-do lists, file sharing, and messaging.
Wrike:
A versatile project management and collaboration tool with features for planning, tracking, and reporting on projects.
Monday.com:
A work operating system that allows teams to plan, track, and manage projects and workflows.
TeamGantt:
A simple online Gantt chart software for project planning and scheduling.
Redmine:
An open-source project management tool that offers issue tracking, time tracking, and project wiki features.
Toggl Plan:
A simple project planning and task management tool with a visual timeline interface.
ZenHub:
An Agile project management and software development tool built directly into GitHub.
MeisterTask:
A collaborative task and project management tool with a Kanban-style interface.
The choice of project management software and tools depends on the specific needs of the project, the size of the team, and the preferred methodology (e.g., Agile, Waterfall). It's essential to select a tool that aligns with the project's goals and the team's workflow for the best results.
Ethical and Legal Aspects
Ethical and legal aspects are critical considerations in project management to ensure that projects are conducted with integrity, compliance, and responsibility. Here are some key ethical and legal aspects to be mindful of in project management:
Ethical Aspects:
Integrity and Honesty:
Project managers and team members must be honest and transparent in all project activities. Misleading stakeholders, hiding information, or engaging in unethical behavior is unacceptable.
Respect and Fairness:
Treat all project team members and stakeholders with respect and fairness, irrespective of their background, gender, race, or other personal attributes.
Transparency:
Maintain open and clear communication with stakeholders. Disclose information, risks, and issues, and encourage a culture of transparency.
Environmental and Social Responsibility:
Consider the environmental and social impacts of the project. Follow sustainable practices and adhere to applicable regulations and ethical standards.
Legal Aspects:
Contractual Obligations:
Ensure that all contractual obligations and agreements are upheld. This includes meeting project deadlines, quality standards, and financial commitments.
Privacy and Data Protection:
Protect sensitive data and adhere to data privacy laws and regulations. Safeguard personal information and confidential project data.
Regulatory Compliance:
Ensure that the project adheres to all relevant laws, regulations, and industry standards, such as environmental regulations, safety codes, and licensing requirements.
Records and Documentation:
Maintain accurate project records and documentation for legal compliance, audits, and accountability.
project management. They help maintain the project's credibility, protect stakeholders' interests, and prevent legal issues that could hinder the project's success. Project managers and team members must stay informed about the ethical and legal requirements specific to their projects and industries.
Conclusion
In conclusion, project management is a multifaceted discipline that encompasses a wide range of fundamental concepts and principles. From project initiation to closure, each phase plays a vital role in ensuring the successful execution of projects. Key areas include defining project objectives, effective planning, risk management, project execution, communication, monitoring and control, and closure. These phases are intricately linked and must be managed systematically and thoughtfully to achieve project goals.
The choice of project lifecycle models and the utilization of project management software and tools further facilitate the successful execution of projects. Selecting the most suitable model and tools based on project requirements and team dynamics is a pivotal decision in the project management process.
Ultimately, effective project management ensures that projects are completed on time, within budget, and to the satisfaction of stakeholders.By incorporating these fundamentals and remaining adaptable, project managers can enhance their project management skills and contribute to the success of their
projects and organizations.
Read More
Project management is a critical discipline that plays a pivotal role in the successful execution of endeavors across various industries. Whether you're working on a construction project, a software development initiative, or even planning a personal event, the principles of project management are universally applicable.
At its core, project management involves a systematic approach to achieving specific objectives within a defined timeframe and utilizing available resources effectively. It provides a structured framework for breaking down complex tasks, managing risks, facilitating communication, and ensuring that all project stakeholders are aligned toward a common goal.
This introduction sets the stage for a deeper exploration of project management fundamentals, from initiating a project and developing comprehensive plans to executing tasks, controlling progress, and ultimately bringing the project to a successful conclusion. By mastering these fundamental concepts, individuals and organizations can enhance their ability to deliver results, adapt to changes, and overcome challenges that inevitably arise in the world of project management.
Table of contents
-
Project Initiation
-
Project Planning
-
Risk Management
-
Project Execution
-
Communication Management
-
Project Monitoring and Control
-
Project Closure
-
Project Lifecycle Models
-
Project Software and Tools
-
Ethical and Legal Aspects
-
Conclusion
Project Initiation
Project Initiation is the first and crucial phase of the project management process. During this stage, the project is defined, authorized, and its purpose and scope are clearly established. Here's a more detailed look at the key aspects of Project Initiation:
Project Charter:Creation of a project charter, which is a formal document that authorizes the existence of the project. It outlines the project's objectives, stakeholders, and high-level scope.
Stakeholder Identification:Identifying all relevant stakeholders who will be affected by or have an impact on the project. This includes internal and external parties, such as team members, customers, sponsors, and regulatory bodies.
Feasibility Study:Conducting a feasibility analysis to assess the project's viability. This analysis may include factors like economic, operational, technical, legal, scheduling, and resource feasibility.
Risk Identification:Identifying potential risks and challenges that the project may face. While a detailed risk assessment typically occurs later in the project, initial risk identification is critical during initiation.
Project Manager Assignment:Appointing a project manager or leader who will be responsible for the overall planning, execution, and control of the project.
Project Initiation Documentation:Creating documentation to capture all the essential information gathered during initiation, such as the project charter, stakeholder analysis, and initial risk assessment.
Successful project initiation sets the stage for the entire project. It provides clarity regarding the project's objectives, scope, and constraints, and ensures that all relevant parties understand and agree on what needs to be achieved. Without a well-executed initiation phase, a project can struggle with unclear direction, scope creep, and a lack of stakeholder commitment, which can lead to project failure.
Project Planning
Project Planning is a critical phase in project management that follows the project initiation. During this phase, detailed plans and strategies are developed to guide the project's execution. Effective project planning is essential for setting clear expectations, allocating resources, and ensuring that the project stays on track. Here are the key components of project planning:
Work Breakdown Structure (WBS):Create a hierarchical structure that organizes project work into smaller, more manageable components. The WBS helps in visualizing and understanding the project's structure.
Task Scheduling:Develop a detailed project schedule that specifies when each task or activity will be executed. Tools like Gantt charts and network diagrams are commonly used for scheduling.
Resource Allocation:Identify and allocate the necessary resources, including personnel, equipment, materials, and budget, to carry out the project work.
Risk Management Plan:Create a comprehensive plan for identifying, assessing, mitigating, and monitoring project risks. This plan should outline strategies to address potential issues.
Quality Plan:Define quality standards and establish processes and criteria for quality assurance and control throughout the project.
Communication Plan:Develop a communication plan that outlines who needs to be informed about project progress, how often, and through which channels.
Stakeholder Engagement Plan:Define how stakeholders will be engaged and managed throughout the project. This includes strategies for managing expectations and addressing stakeholder concerns.
Change Management Plan:Develop a plan to handle potential changes in project scope or requirements. Outline procedures for change requests, approvals, and impact assessments.
Documentation:Maintain detailed documentation of the project plan, including all associated plans and schedules. This documentation ensures that everyone involved in the project is working from a common understanding.
Effective project planning is essential for aligning the project team, managing resources efficiently, and minimizing risks. A well-thought-out project plan serves as a roadmap for the entire project, helping to keep it on course and facilitating effective communication and coordination among team members and stakeholders.
Risk Management
Risk management is a critical aspect of project management, aimed at identifying, analyzing, and mitigating potential risks that could impact a project's success. Here are the key components of risk management:
Risk Identification:The first step is to identify and document potential risks. This involves brainstorming with the project team and stakeholders to create a comprehensive list of both internal and external risks.
Risk Analysis:Assess the identified risks in terms of their probability and potential impact. This helps prioritize which risks are most significant and require the most attention.
Risk Assessment:After analyzing risks, it's important to assess them based on their severity and likelihood. This often involves creating a risk matrix or heat map to categorize and prioritize risks.
Risk Monitoring:Continuously monitor identified risks throughout the project lifecycle. Regularly review the status of risks and assess whether new risks have emerged.
Risk Reporting:Provide regular risk reports to stakeholders, keeping them informed about the status of risks and the effectiveness of risk mitigation strategies.
Change Control:Implement a structured change control process to manage changes that may arise due to risks or other factors. This ensures that changes are evaluated and approved before being incorporated into the project.
Risk Register:Maintain a risk register, which is a document that contains information about all identified risks, their status, and the actions taken to address them.
Effective risk management helps project managers and teams anticipate and address potential issues before they become major problems. It allows for proactive decision-making, which can ultimately save time, resources, and prevent project failure.
Project Execution
Project Execution is the phase in the project management process where the actual project work is carried out, and the project plan is put into action. This phase involves coordinating people and resources, ensuring that tasks are completed as per the project schedule, and continuously monitoring progress to meet project objectives. Here are key aspects of Project Execution:
Team Management:
Assign tasks to team members and ensure that they understand their roles and responsibilities.
Foster a positive team environment, encourage collaboration, and address any conflicts or issues that may arise.
Task Execution:Initiate and complete project tasks according to the defined schedule, quality standards, and scope.
Monitor task progress and address any deviations or delays promptly.
Communication:Maintain regular and effective communication among team members and stakeholders to provide updates on project progress, resolve issues, and ensure everyone is informed.
Quality Assurance:Implement quality control measures to ensure that project deliverables meet the predefined quality standards.
Change Management:Manage changes to the project scope, schedule, or resources through the established change control process.
Issue Resolution:Identify and address any issues or roadblocks that arise during the project. Implement solutions to keep the project on track.
Document Control:Ensure that project documentation is properly managed, updated, and accessible to the project team as needed.
Safety and Compliance:Monitor safety standards and compliance with relevant laws and regulations, particularly in projects with health, safety, or legal requirements.
Project Execution is the phase where the project plan comes to life, and it requires strong leadership, effective communication, and continuous monitoring to ensure that the project progresses according to the established parameters. It's critical to stay adaptable and responsive to changes and challenges that may arise during this phase to keep the project on the path to success.
Communication Management
Communication Management is a critical aspect of project management that focuses on planning, executing, and controlling communication within a project. Effective communication ensures that all stakeholders are informed, engaged, and aligned with project goals and progress. Here are key components of Communication Management in project management:
Stakeholder Identification and Analysis:Identify and analyze project stakeholders, understanding their needs, interests, influence, and communication preferences.
Communication Channels:Select appropriate communication channels for different types of information and stakeholders. This could include meetings, emails, reports, project management software, or other tools.
Information Distribution:Disseminate project information to stakeholders as per the communication plan. Ensure that the right information reaches the right people at the right time.
Status Reporting:Regularly report on project status, progress, and key performance indicators (KPIs) to stakeholders, keeping them informed about the project's health.
Feedback Collection:Encourage and collect feedback from stakeholders to gauge their satisfaction, concerns, and suggestions for improving project performance.
Documentation and Records:Maintain comprehensive project records, including meeting minutes, reports, emails, and other communication artifacts for reference and audit purposes.
Communication Technology:Utilize project management software and collaboration tools to facilitate communication, share documents, and track project progress.
Effective Communication Management is essential for ensuring that all project stakeholders are informed, engaged, and supportive of the project's goals. It helps prevent misunderstandings, manage expectations, and facilitate the timely resolution of issues. Poor communication can lead to project delays, scope creep, and stakeholder dissatisfaction, so it's a critical aspect of project success.
Project Monitoring and Control
Project Monitoring and Control is a vital phase in the project management process that occurs concurrently with project execution. It involves tracking, reviewing, and regulating project performance to ensure that the project stays on track and aligns with its objectives. Here are the key aspects of Project Monitoring and Control:
Performance Measurement:Continuously measure and assess project performance using key performance indicators (KPIs) and other relevant metrics. This helps in understanding how well the project is progressing.
Scope Control:Ensure that the project remains within the defined scope and that scope changes are properly evaluated and approved through the change control process.
Quality Control:Implement quality control measures to ensure that project deliverables meet the defined quality standards. Conduct regular quality inspections and make necessary corrections.
Issue Management:Address issues and challenges as they arise. Develop solutions and corrective actions to resolve problems that could impact project success.
Document Management:Manage project documentation and records, ensuring that they are up to date and accessible for reference and audits.
Progress Reporting:Provide regular project status reports to stakeholders, highlighting achievements, issues, and upcoming milestones.
Resource Optimization:Optimize resource allocation to ensure that resources are used efficiently and that project team members are not overburdened.
Audit and Review:Conduct periodic project reviews and audits to ensure compliance with project plans, policies, and quality standards.
Project Monitoring and Control is a continuous process that helps project managers and teams maintain control over a project's progress and make necessary adjustments to keep it aligned with the original goals and objectives. It is essential for preventing and addressing deviations that could jeopardize project success.
Project Closure
Project Closure is the final phase in the project management process, where the project is formally completed, and all necessary activities are conducted to bring the project to a successful conclusion. Here are key components of Project Closure:
Customer or Stakeholder Acceptance:Obtain formal acceptance and sign-off from the customer or stakeholders to acknowledge that the project objectives have been met.
Transition Plan:If the project has ongoing operational aspects, create and implement a transition plan to hand over the project's results to the appropriate operational teams or personnel.
Closure Criteria:Define and meet specific criteria or checklists that signify the project's readiness for closure, such as the completion of all tasks, approval of deliverables, and successful testing.
Financial Closure:Complete all financial activities, such as closing project accounts, reconciling expenses, and ensuring all financial records are accurate.
Project Documentation:Organize and archive all project documentation, making it accessible for future reference, audits, or compliance purposes.
Project Closure Report:Prepare a formal project closure report, summarizing the project's achievements, issues faced, and the final budget and schedule performance.
Legal and Contractual Closure:Address any legal or contractual obligations, such as final payments to vendors or contractors and the formal termination of contracts.
Archiving:Store project documentation and records in a secure archive for future reference, ensuring they are easily retrievable if needed.
Project Team Disbandment:If the project team is disbanded, facilitate a smooth transition for team members to their next assignments or projects.
Project Closure is a crucial phase that provides a sense of closure and accomplishment for the project team and stakeholders. Properly closing a project helps ensure that resources are freed up for other initiatives and that valuable insights from the project can be used to improve future projects.
Project Lifecycle Models
Project lifecycle models represent the stages and phases a project goes through, from initiation to completion. Different projects may require different lifecycle models based on their specific characteristics, requirements, and industry. Here are some commonly used project lifecycle models:
Kanban:
Kanban is another Agile framework that visualizes work on a Kanban board. It focuses on limiting work in progress and optimizing flow, making it suitable for continuous improvement projects.
V-Model (Validation and Verification Model):
The V-Model is an extension of the Waterfall model. It emphasizes the relationship between development phases and corresponding testing phases. Each development phase has a corresponding validation and verification phase.
RAD (Rapid Application Development):
RAD is an incremental software development process that puts a premium on rapid prototyping and speedy feedback. It's often used for time-sensitive projects with well-understood requirements.
Big Bang Model:
The Big Bang model is characterized by minimal planning and requirements definition. It is suitable for small projects with few constraints, where development starts with a vague idea and evolves over time.
Hybrid Models:
Some projects may benefit from a combination of different lifecycle models. For example, a project might start with a Waterfall approach for planning and gradually transition to Agile methods for development and testing.
The choice of a project lifecycle model depends on the project's specific needs, constraints, and goals. It's important to select the most appropriate model and adapt it as necessary to ensure the successful completion of the project. Each model has its advantages and limitations, and the project manager should consider these factors when making a choice.
Project Software and Tools
Project management software and tools play a crucial role in planning, executing, monitoring, and controlling projects. They help streamline tasks, improve collaboration, and enhance communication. Here are some popular project management software and tools:
Microsoft Project:
A comprehensive project management tool that includes features for project planning, scheduling, resource allocation, and reporting.
Trello:
A visual project management tool that uses boards, lists, and cards to help teams organize tasks and track progress.
Asana:
A web-based platform for project and task management that offers tools for team collaboration and project planning.
Basecamp:
A user-friendly project management and team collaboration tool that includes to-do lists, file sharing, and messaging.
Wrike:
A versatile project management and collaboration tool with features for planning, tracking, and reporting on projects.
Monday.com:
A work operating system that allows teams to plan, track, and manage projects and workflows.
TeamGantt:
A simple online Gantt chart software for project planning and scheduling.
Redmine:
An open-source project management tool that offers issue tracking, time tracking, and project wiki features.
Toggl Plan:
A simple project planning and task management tool with a visual timeline interface.
ZenHub:
An Agile project management and software development tool built directly into GitHub.
MeisterTask:
A collaborative task and project management tool with a Kanban-style interface.
The choice of project management software and tools depends on the specific needs of the project, the size of the team, and the preferred methodology (e.g., Agile, Waterfall). It's essential to select a tool that aligns with the project's goals and the team's workflow for the best results.
Ethical and Legal Aspects
Ethical and legal aspects are critical considerations in project management to ensure that projects are conducted with integrity, compliance, and responsibility. Here are some key ethical and legal aspects to be mindful of in project management:
Ethical Aspects:
Integrity and Honesty:
Project managers and team members must be honest and transparent in all project activities. Misleading stakeholders, hiding information, or engaging in unethical behavior is unacceptable.
Respect and Fairness:
Treat all project team members and stakeholders with respect and fairness, irrespective of their background, gender, race, or other personal attributes.
Transparency:
Maintain open and clear communication with stakeholders. Disclose information, risks, and issues, and encourage a culture of transparency.
Environmental and Social Responsibility:
Consider the environmental and social impacts of the project. Follow sustainable practices and adhere to applicable regulations and ethical standards.
Legal Aspects:
Contractual Obligations:
Ensure that all contractual obligations and agreements are upheld. This includes meeting project deadlines, quality standards, and financial commitments.
Privacy and Data Protection:
Protect sensitive data and adhere to data privacy laws and regulations. Safeguard personal information and confidential project data.
Regulatory Compliance:
Ensure that the project adheres to all relevant laws, regulations, and industry standards, such as environmental regulations, safety codes, and licensing requirements.
Records and Documentation:
Maintain accurate project records and documentation for legal compliance, audits, and accountability.
project management. They help maintain the project's credibility, protect stakeholders' interests, and prevent legal issues that could hinder the project's success. Project managers and team members must stay informed about the ethical and legal requirements specific to their projects and industries.
Conclusion
In conclusion, project management is a multifaceted discipline that encompasses a wide range of fundamental concepts and principles. From project initiation to closure, each phase plays a vital role in ensuring the successful execution of projects. Key areas include defining project objectives, effective planning, risk management, project execution, communication, monitoring and control, and closure. These phases are intricately linked and must be managed systematically and thoughtfully to achieve project goals.
The choice of project lifecycle models and the utilization of project management software and tools further facilitate the successful execution of projects. Selecting the most suitable model and tools based on project requirements and team dynamics is a pivotal decision in the project management process.
Ultimately, effective project management ensures that projects are completed on time, within budget, and to the satisfaction of stakeholders.By incorporating these fundamentals and remaining adaptable, project managers can enhance their project management skills and contribute to the success of their
projects and organizations.
Introduction to MongoDB for Developers
MongoDB is a popular and versatile NoSQL database that is well-suited for developers working on a wide range of applications. It is designed to store, manage, and query large volumes of data with flexibility and scalability. MongoDB stands out from traditional relational databases by offering a document-oriented, schema-less data model, making it a valuable choice for developers.
MongoDB is a popular NoSQL database designed for developers who need a flexible and scalable way to store and manage data. It uses a document-oriented data model, meaning it stores data in JSON-like documents within collections, and it doesn't require a predefined schema. This makes MongoDB a great choice for applications with evolving data needs.
MongoDB is known for its ability to handle large volumes of data and high traffic loads, making it suitable for a wide range of applications, from content management systems to real-time analytics and more. Developers appreciate its query language, which is easy to work with and its support for horizontal scaling. MongoDB also has a vibrant community and official support, making it a valuable tool in the developer's toolkit.
Table of contents
-
Installation and Setup
-
CRUD Operations
-
Data Modeling
-
Querying Data
-
Indexing
-
Aggregation Framework
-
Data Security
-
Scaling and High Availability
-
Drivers and SDKs
-
Deployment and Operations
-
Conclusion
Installation and Setup
Installing and setting up MongoDB is one of the initial steps to work with this database. Here's a guide on how to install and set up MongoDB:
Choose Your Platform: MongoDB supports a variety of platforms, including Windows, macOS, and various Linux distributions. Make sure to choose the version that matches your operating system.
Installation on Windows:
Double-click the downloaded .msi file to launch the installer.
Follow the installation wizard, accepting the license agreement and choosing the installation directory.
You can also choose to install MongoDB Compass, a graphical user interface for MongoDB, during the installation process.
Installation on Linux:Installation on Linux distributions may vary. Refer to the official MongoDB documentation for detailed instructions specific to your distribution.
Community vs Enterprise: Be aware of the differences between the MongoDB Community Server and the Enterprise version. The Community Server is free to use, while the Enterprise version comes with additional features and support but may require a license.
Once MongoDB is installed and set up, you're ready to start creating databases and collections, inserting data, and working with the database in your applications. Make sure to consult the official MongoDB documentation for any platform-specific or version-specific instructions and updates.
CRUD Operations
CRUD operations, which stand for Create, Read, Update, and Delete, are fundamental database operations that allow you to interact with data in MongoDB. Here's a brief overview of each CRUD operation in MongoDB:
Create (Insert):Inserting Documents: To create new data in MongoDB, you use the insert operation. You can insert documents into collections, which are equivalent to tables in relational databases.
Read (Query):Querying Documents: To retrieve data from MongoDB, you use the find operation. You can specify conditions to filter the documents you want to retrieve.
Update:Modifying Documents: To update existing data, you use the update operation. You can specify how to modify documents and which documents to update.
Delete:Removing Documents: To delete data, you use the remove operation. You can specify conditions to determine which documents to remove.
It's important to note that MongoDB also supports more advanced querying and updating operations beyond simple CRUD. For example, you can perform operations like sorting, limiting results, and using aggregation for complex data transformations.
Data Modeling
Data modeling in MongoDB is the process of designing the structure of your data, specifying the relationships between different pieces of data, and organizing it within collections and documents. MongoDB uses a flexible schema-less data model, allowing you to adapt your data structure as your application evolves. Here are the key aspects of data modeling in MongoDB:
Collections:In MongoDB, data is organized into collections, which are similar to tables in relational databases. Collections are schema-less, which means that each document within a collection can have different fields.
Documents:Documents are individual records or data items stored within collections. They are represented in a JSON-like format called BSON (Binary JSON). A document can contain fields with various data types, including strings, numbers, arrays, embedded documents, and more.
Embedding vs Referencing:Data modeling in MongoDB often involves making decisions about whether to embed or reference related data. Embedding involves including related data within a document, while referencing involves storing an ID or reference to another document.
Embedding is useful for one-to-one and one-to-few relationships, as it can improve query performance by reducing the number of database queries needed.
Versioning and Time-Series Data:For applications that require versioning or handling time-series data, consider how to structure your data to accommodate these requirements. This might involve using arrays for version history or including timestamps.
Data Validation:Use MongoDB's schema validation capabilities to ensure that data conforms to your expected structure and rules. This helps maintain data consistency and integrity.
Data Security and Access Control:Apply appropriate access control to your collections to protect sensitive data. MongoDB offers role-based access control, allowing you to define who can read, write, or modify data.
Data modeling in MongoDB is an iterative process that should align with the evolving needs of your application. It's essential to consider your application's specific requirements and query patterns when designing your data model to ensure it performs efficiently and effectively.
Querying Data
Querying data in MongoDB is a fundamental task that allows you to retrieve specific documents from collections based on your search criteria. MongoDB provides a flexible and powerful query language that enables you to filter, sort, and project data to meet your application's requirements. Here's an overview of querying data in MongoDB:
Basic Queries:The most common way to query data is by using the find method. You pass a query document as a parameter to specify the criteria for matching documents.
Query Operators:MongoDB supports a wide range of query operators to perform various comparisons.
Sorting:Use the sort method to order the results. You can specify the sorting order
Projection:You can use the project method to specify which fields should be included or excluded in the query results.
Aggregation Framework:For more complex data transformations, use MongoDB's aggregation framework. It provides a versatile way to group, filter, and reshape data, akin to SQL's GROUP BY and JOIN operations.
Text Search:MongoDB includes a text search feature that allows you to perform full-text searches on text fields within your documents.
Geospatial Queries:If you're working with geospatial data, MongoDB supports geospatial queries for location-based applications.
Query Performance:Use the explain method to analyze query performance, identify inefficiencies, and optimize your queries.
When working with MongoDB, it's essential to tailor your queries to your application's specific needs and be mindful of index usage to ensure efficient data retrieval. MongoDB's query language provides the flexibility to handle a wide range of data retrieval scenarios.
Indexing
Indexing in MongoDB is a crucial performance optimization technique that allows you to speed up data retrieval operations and improve query performance. By creating indexes on specific fields within your collections, MongoDB can efficiently locate and return the data you request. Here are the key aspects of indexing in MongoDB:
Index Types:MongoDB supports various index types, including single-field indexes, compound indexes (indexing on multiple fields), multi-key indexes (for arrays), text indexes (for text search), and geospatial indexes (for location-based data).
Creating Indexes:To create an index, you can use the createIndex() method
Default Index:By default, MongoDB creates an index on the _id field for each document, ensuring fast retrieval by document ID.
Text Indexes:Text indexes are used for full-text search, allowing you to perform text-based searches on text fields in your documents.
TTL Indexes:Time-to-Live (TTL) indexes allow you to automatically delete documents after a specified amount of time.
Partial Indexes:You can create partial indexes to index a subset of documents in a collection based on specific conditions. This is helpful for optimizing queries that don't need to scan the entire collection.
Indexing Strategies:Choosing the right indexing strategy is crucial. It depends on your application's query patterns and the type of data you're working with. Regularly review and update indexes to adapt to changing query patterns.
Query Analysis and Profiling:MongoDB provides tools for analyzing and profiling queries, allowing you to identify slow queries and optimize them, which may include creating or modifying indexes.
Effective index management is essential for maintaining the performance and responsiveness of your MongoDB database. It's important to continually monitor and analyze query performance, and adjust your indexing strategy as your application evolves.
Aggregation Framework
MongoDB's Aggregation Framework is a powerful feature that allows you to process, transform, and analyze data within your MongoDB collections. It provides a flexible and expressive way to perform complex data operations, similar to SQL's GROUP BY, JOIN, and SQL-like operations. Here's an overview of MongoDB's Aggregation Framework:
Pipeline Concept:Aggregations in MongoDB are structured as pipelines. A pipeline consists of multiple stages that are executed sequentially. Each stage in the pipeline performs a specific operation on the data.
Expression Operators:Within each aggregation stage, you can use expression operators, such as arithmetic operators, comparison operators, conditional expressions, and more, to manipulate and transform data.
Array Operations:You can work with arrays within the Aggregation Framework, allowing you to unwind arrays, filter array elements, and manipulate array data.
Custom Aggregation Functions:You can define custom aggregation functions using JavaScript with the $function stage.
Caching and Result Optimization:MongoDB caches the results of some aggregation stages to improve performance when you re-run the same aggregation. This can be customized using options like allowDiskUse and useCursor.
Explain and Profiling:You can use the explain method to understand the execution plan of an aggregation and identify performance bottlenecks. Profiling allows you to capture and analyze the execution times of aggregation stages.
Aggregation Pipelines and Joins:You can perform joins between multiple collections using the $lookup stage, which is analogous to SQL joins. This allows you to combine data from different collections within a single aggregation.
Indexing for Aggregation:Proper indexing is critical for optimizing aggregation queries, especially when dealing with large datasets.
The MongoDB Aggregation Framework is a versatile tool for performing data analysis, reporting, and transformation within the database. It's particularly useful for handling complex queries and data manipulations, making it a valuable tool for business intelligence, reporting, and data processing tasks.
Data Security
Data security is a critical aspect of any application or system, and MongoDB provides several features and best practices to help you secure your data effectively. Here are key considerations and practices for ensuring data security in MongoDB:
Authentication:MongoDB supports various authentication mechanisms, including username and password, X.509 certificates, and LDAP integration. Ensure that authentication is enabled, and use strong, unique passwords for all users.
Authorization:Implement role-based access control (RBAC) to restrict users' access to specific databases and collections. Assign roles with the least privilege necessary to perform their tasks.
Encryption:Encrypt data in transit by using SSL/TLS to secure the communication between MongoDB clients and servers.
Encrypt data at rest using built-in features like WiredTiger storage engine encryption or use third-party tools and solutions for additional security.
Vulnerability Scanning and Patch Management:Keep your MongoDB server and all related software up to date with security patches. Regularly scan your system for vulnerabilities, and address any identified issues promptly.
IP Whitelisting:Configure IP whitelisting to allow connections only from trusted IP addresses. This can add an extra layer of security, especially for cloud-based deployments.
External Authentication and Authorization Services:Integrate MongoDB with external authentication and authorization services, such as LDAP or Active Directory, for centralized user management and security policies.
Data security is an ongoing process, and it's essential to regularly review and update your security measures to adapt to changing threats and requirements. By following these best practices, you can significantly enhance the security of your MongoDB deployments and protect your sensitive data.
Scaling and High Availability
Scaling and ensuring high availability are critical aspects of database management in MongoDB. These practices are vital to maintain performance, minimize downtime, and accommodate growing workloads. MongoDB offers several options for scaling and achieving high availability:
Scaling:
Horizontal Scaling (Sharding):
MongoDB supports horizontal scaling through sharding. In sharding, data is distributed across multiple servers or clusters, known as shards. Each shard is responsible for a subset of the data. Sharding is suitable for applications with large datasets and high read and write loads.
Sharding can be used to balance the data distribution and improve query performance.
Vertical Scaling (Replication):
Vertical scaling, often referred to as replica sets, involves adding more resources to a single MongoDB server to improve performance. Replica sets also provide data redundancy and failover capabilities.
In a replica set, one node is the primary, and the others are secondary nodes. The primary node handles all writes and the initial read operations, while the secondary nodes replicate data from the primary to provide data redundancy and read scaling.
High Availability:
Data Center Awareness:
To further enhance high availability, you can deploy replica sets across multiple data centers or cloud regions. This setup ensures that your data remains accessible even if one data center experiences an outage.
Monitoring and Alerting:
Implement robust monitoring and alerting systems to track the health of your MongoDB instances and be immediately notified of any issues or potential failures.
Backups and Restore:
Regularly back up your data and practice data restoration. In the event of a disaster, having up-to-date backups ensures you can quickly recover your data.
Testing Failover:
Periodically simulate failures and test the failover process to ensure that it works as expected. This helps you identify and address issues before they impact your production environment.
MongoDB's flexibility in scaling and high availability makes it a reliable choice for applications that demand performance, scalability, and minimal downtime. Planning for scaling and high availability from the beginning of your MongoDB deployment is essential to accommodate growth and maintain robust operations.
Drivers and SDKs
MongoDB offers official drivers and software development kits (SDKs) for various programming languages, making it easy for developers to interact with MongoDB databases in their preferred programming environment. These drivers and SDKs provide a convenient way to connect, query, and manipulate data in MongoDB. Here are some of the primary MongoDB drivers and SDKs:
MongoDB Drivers:
Node.js (Official Driver): The official MongoDB Node.js driver allows you to work with MongoDB in JavaScript and Node.js applications. It provides asynchronous, non-blocking operations for efficient interaction with MongoDB databases.
Python (Official Driver): The official MongoDB Python driver is called PyMongo. It offers a high-level API for Python applications to connect to and manipulate MongoDB data. PyMongo supports asynchronous I/O for Python 3.
Java (Official Driver): The official MongoDB Java driver is a widely-used driver for connecting Java applications to MongoDB. It includes support for both synchronous and asynchronous programming paradigms.
C#/.NET (Official Driver): The official MongoDB .NET driver allows developers to build .NET applications that work with MongoDB. It supports both .NET Framework and .NET Core/5+.
Perl (Community-Supported): While not an official MongoDB driver, there is a community-supported Perl driver called MongoDB that allows Perl developers to connect to MongoDB.
SDKs and ORM Libraries:
Mongoose (Node.js): Mongoose is a popular Node.js library that provides an object modeling framework for MongoDB. It simplifies data validation, schema design, and query building for Node.js applications.
Spring Data MongoDB (Java): Spring Data MongoDB is part of the Spring Data project and offers a high-level, Spring-based approach to working with MongoDB in Java applications.
Meteor (Node.js): Meteor is a full-stack JavaScript platform that includes its MongoDB integration, allowing developers to build real-time web applications with a simplified API for MongoDB.
Motor (Python): Motor is an asynchronous Python driver for MongoDB that is designed to work seamlessly with asynchronous web frameworks like Tornado and asynchronous programming libraries in Python 3.
These drivers and SDKs make it straightforward to work with MongoDB in a variety of programming languages, frameworks, and platforms. Depending on your application's technology stack, you can choose the appropriate driver or SDK to streamline database interactions and enhance your development workflow.
Deployment and Operations
Deploying and operating a MongoDB database in a production environment requires careful planning and maintenance. Here are key considerations for deploying and managing MongoDB effectively:
Deployment:
Version Selection:
Select the appropriate version of MongoDB for your application, taking into account the latest stable release and the compatibility of your drivers and libraries.
Deployment Topology:
Decide on the desired deployment topology, which may include standalone servers, replica sets, sharded clusters, or a combination of these, depending on your scalability and availability requirements.
Security Measures:
Implement security best practices, including authentication and authorization, network security, encryption, and role-based access control. For cloud deployments, configure network security groups and firewall rules.
Data Backup:
Establish data backup and recovery procedures to ensure data safety. Schedule regular backups and test the restoration process.
Operations:
Monitoring:
Use monitoring tools to keep an eye on the health and performance of your MongoDB deployment. MongoDB Atlas, the cloud-based MongoDB service, offers built-in monitoring and alerting features.
Security Updates:
Stay up-to-date with security patches and updates for MongoDB and the underlying operating system. Regularly apply these updates to address known vulnerabilities.
User Training:
Train your operations team and developers to ensure they are familiar with MongoDB's operational aspects, best practices, and tools.
Logs and Audit Trails:
Enable auditing to track and log database activity. Review logs and audit trails to monitor and investigate database activities.
Proper deployment and operations practices are crucial for maintaining a robust, performant, and secure MongoDB database in production. Regularly assess and adjust your deployment and operations strategies to meet the evolving needs of your application.
Conclusion
In conclusion, MongoDB is a versatile and popular NoSQL database system that offers many features and capabilities for developers and organizations. Whether you're working with MongoDB for application development, data modeling, or database management, it's essential to have a solid understanding of its core concepts and best practices. This knowledge can help you make the most of MongoDB's capabilities and ensure that your applications are scalable, secure, and high-performing.
MongoDB is a powerful database system with a strong ecosystem of tools and resources to support its users. Whether you're building web applications, mobile apps, or data-intensive solutions, MongoDB offers the flexibility and scalability needed to meet your data storage and retrieval needs. Staying up-to-date with the latest MongoDB developments and best practices is essential for maximizing the benefits of this popular NoSQL database.
Read More
MongoDB is a popular and versatile NoSQL database that is well-suited for developers working on a wide range of applications. It is designed to store, manage, and query large volumes of data with flexibility and scalability. MongoDB stands out from traditional relational databases by offering a document-oriented, schema-less data model, making it a valuable choice for developers.
MongoDB is a popular NoSQL database designed for developers who need a flexible and scalable way to store and manage data. It uses a document-oriented data model, meaning it stores data in JSON-like documents within collections, and it doesn't require a predefined schema. This makes MongoDB a great choice for applications with evolving data needs.
MongoDB is known for its ability to handle large volumes of data and high traffic loads, making it suitable for a wide range of applications, from content management systems to real-time analytics and more. Developers appreciate its query language, which is easy to work with and its support for horizontal scaling. MongoDB also has a vibrant community and official support, making it a valuable tool in the developer's toolkit.
Table of contents
-
Installation and Setup
-
CRUD Operations
-
Data Modeling
-
Querying Data
-
Indexing
-
Aggregation Framework
-
Data Security
-
Scaling and High Availability
-
Drivers and SDKs
-
Deployment and Operations
-
Conclusion
Installation and Setup
Installing and setting up MongoDB is one of the initial steps to work with this database. Here's a guide on how to install and set up MongoDB:
Choose Your Platform: MongoDB supports a variety of platforms, including Windows, macOS, and various Linux distributions. Make sure to choose the version that matches your operating system.
Installation on Windows:
Double-click the downloaded .msi file to launch the installer.
Follow the installation wizard, accepting the license agreement and choosing the installation directory.
You can also choose to install MongoDB Compass, a graphical user interface for MongoDB, during the installation process.
Installation on Linux:Installation on Linux distributions may vary. Refer to the official MongoDB documentation for detailed instructions specific to your distribution.
Community vs Enterprise: Be aware of the differences between the MongoDB Community Server and the Enterprise version. The Community Server is free to use, while the Enterprise version comes with additional features and support but may require a license.
Once MongoDB is installed and set up, you're ready to start creating databases and collections, inserting data, and working with the database in your applications. Make sure to consult the official MongoDB documentation for any platform-specific or version-specific instructions and updates.
CRUD Operations
CRUD operations, which stand for Create, Read, Update, and Delete, are fundamental database operations that allow you to interact with data in MongoDB. Here's a brief overview of each CRUD operation in MongoDB:
Create (Insert):Inserting Documents: To create new data in MongoDB, you use the insert operation. You can insert documents into collections, which are equivalent to tables in relational databases.
Read (Query):Querying Documents: To retrieve data from MongoDB, you use the find operation. You can specify conditions to filter the documents you want to retrieve.
Update:Modifying Documents: To update existing data, you use the update operation. You can specify how to modify documents and which documents to update.
Delete:Removing Documents: To delete data, you use the remove operation. You can specify conditions to determine which documents to remove.
It's important to note that MongoDB also supports more advanced querying and updating operations beyond simple CRUD. For example, you can perform operations like sorting, limiting results, and using aggregation for complex data transformations.
Data Modeling
Data modeling in MongoDB is the process of designing the structure of your data, specifying the relationships between different pieces of data, and organizing it within collections and documents. MongoDB uses a flexible schema-less data model, allowing you to adapt your data structure as your application evolves. Here are the key aspects of data modeling in MongoDB:
Collections:In MongoDB, data is organized into collections, which are similar to tables in relational databases. Collections are schema-less, which means that each document within a collection can have different fields.
Documents:Documents are individual records or data items stored within collections. They are represented in a JSON-like format called BSON (Binary JSON). A document can contain fields with various data types, including strings, numbers, arrays, embedded documents, and more.
Embedding vs Referencing:Data modeling in MongoDB often involves making decisions about whether to embed or reference related data. Embedding involves including related data within a document, while referencing involves storing an ID or reference to another document.
Embedding is useful for one-to-one and one-to-few relationships, as it can improve query performance by reducing the number of database queries needed.
Versioning and Time-Series Data:For applications that require versioning or handling time-series data, consider how to structure your data to accommodate these requirements. This might involve using arrays for version history or including timestamps.
Data Validation:Use MongoDB's schema validation capabilities to ensure that data conforms to your expected structure and rules. This helps maintain data consistency and integrity.
Data Security and Access Control:Apply appropriate access control to your collections to protect sensitive data. MongoDB offers role-based access control, allowing you to define who can read, write, or modify data.
Data modeling in MongoDB is an iterative process that should align with the evolving needs of your application. It's essential to consider your application's specific requirements and query patterns when designing your data model to ensure it performs efficiently and effectively.
Querying Data
Querying data in MongoDB is a fundamental task that allows you to retrieve specific documents from collections based on your search criteria. MongoDB provides a flexible and powerful query language that enables you to filter, sort, and project data to meet your application's requirements. Here's an overview of querying data in MongoDB:
Basic Queries:The most common way to query data is by using the find method. You pass a query document as a parameter to specify the criteria for matching documents.
Query Operators:MongoDB supports a wide range of query operators to perform various comparisons.
Sorting:Use the sort method to order the results. You can specify the sorting order
Projection:You can use the project method to specify which fields should be included or excluded in the query results.
Aggregation Framework:For more complex data transformations, use MongoDB's aggregation framework. It provides a versatile way to group, filter, and reshape data, akin to SQL's GROUP BY and JOIN operations.
Text Search:MongoDB includes a text search feature that allows you to perform full-text searches on text fields within your documents.
Geospatial Queries:If you're working with geospatial data, MongoDB supports geospatial queries for location-based applications.
Query Performance:Use the explain method to analyze query performance, identify inefficiencies, and optimize your queries.
When working with MongoDB, it's essential to tailor your queries to your application's specific needs and be mindful of index usage to ensure efficient data retrieval. MongoDB's query language provides the flexibility to handle a wide range of data retrieval scenarios.
Indexing
Indexing in MongoDB is a crucial performance optimization technique that allows you to speed up data retrieval operations and improve query performance. By creating indexes on specific fields within your collections, MongoDB can efficiently locate and return the data you request. Here are the key aspects of indexing in MongoDB:
Index Types:MongoDB supports various index types, including single-field indexes, compound indexes (indexing on multiple fields), multi-key indexes (for arrays), text indexes (for text search), and geospatial indexes (for location-based data).
Creating Indexes:To create an index, you can use the createIndex() method
Default Index:By default, MongoDB creates an index on the _id field for each document, ensuring fast retrieval by document ID.
Text Indexes:Text indexes are used for full-text search, allowing you to perform text-based searches on text fields in your documents.
TTL Indexes:Time-to-Live (TTL) indexes allow you to automatically delete documents after a specified amount of time.
Partial Indexes:You can create partial indexes to index a subset of documents in a collection based on specific conditions. This is helpful for optimizing queries that don't need to scan the entire collection.
Indexing Strategies:Choosing the right indexing strategy is crucial. It depends on your application's query patterns and the type of data you're working with. Regularly review and update indexes to adapt to changing query patterns.
Query Analysis and Profiling:MongoDB provides tools for analyzing and profiling queries, allowing you to identify slow queries and optimize them, which may include creating or modifying indexes.
Effective index management is essential for maintaining the performance and responsiveness of your MongoDB database. It's important to continually monitor and analyze query performance, and adjust your indexing strategy as your application evolves.
Aggregation Framework
MongoDB's Aggregation Framework is a powerful feature that allows you to process, transform, and analyze data within your MongoDB collections. It provides a flexible and expressive way to perform complex data operations, similar to SQL's GROUP BY, JOIN, and SQL-like operations. Here's an overview of MongoDB's Aggregation Framework:
Pipeline Concept:Aggregations in MongoDB are structured as pipelines. A pipeline consists of multiple stages that are executed sequentially. Each stage in the pipeline performs a specific operation on the data.
Expression Operators:Within each aggregation stage, you can use expression operators, such as arithmetic operators, comparison operators, conditional expressions, and more, to manipulate and transform data.
Array Operations:You can work with arrays within the Aggregation Framework, allowing you to unwind arrays, filter array elements, and manipulate array data.
Custom Aggregation Functions:You can define custom aggregation functions using JavaScript with the $function stage.
Caching and Result Optimization:MongoDB caches the results of some aggregation stages to improve performance when you re-run the same aggregation. This can be customized using options like allowDiskUse and useCursor.
Explain and Profiling:You can use the explain method to understand the execution plan of an aggregation and identify performance bottlenecks. Profiling allows you to capture and analyze the execution times of aggregation stages.
Aggregation Pipelines and Joins:You can perform joins between multiple collections using the $lookup stage, which is analogous to SQL joins. This allows you to combine data from different collections within a single aggregation.
Indexing for Aggregation:Proper indexing is critical for optimizing aggregation queries, especially when dealing with large datasets.
The MongoDB Aggregation Framework is a versatile tool for performing data analysis, reporting, and transformation within the database. It's particularly useful for handling complex queries and data manipulations, making it a valuable tool for business intelligence, reporting, and data processing tasks.
Data Security
Data security is a critical aspect of any application or system, and MongoDB provides several features and best practices to help you secure your data effectively. Here are key considerations and practices for ensuring data security in MongoDB:
Authentication:MongoDB supports various authentication mechanisms, including username and password, X.509 certificates, and LDAP integration. Ensure that authentication is enabled, and use strong, unique passwords for all users.
Authorization:Implement role-based access control (RBAC) to restrict users' access to specific databases and collections. Assign roles with the least privilege necessary to perform their tasks.
Encryption:Encrypt data in transit by using SSL/TLS to secure the communication between MongoDB clients and servers.
Encrypt data at rest using built-in features like WiredTiger storage engine encryption or use third-party tools and solutions for additional security.
Vulnerability Scanning and Patch Management:Keep your MongoDB server and all related software up to date with security patches. Regularly scan your system for vulnerabilities, and address any identified issues promptly.
IP Whitelisting:Configure IP whitelisting to allow connections only from trusted IP addresses. This can add an extra layer of security, especially for cloud-based deployments.
External Authentication and Authorization Services:Integrate MongoDB with external authentication and authorization services, such as LDAP or Active Directory, for centralized user management and security policies.
Data security is an ongoing process, and it's essential to regularly review and update your security measures to adapt to changing threats and requirements. By following these best practices, you can significantly enhance the security of your MongoDB deployments and protect your sensitive data.
Scaling and High Availability
Scaling and ensuring high availability are critical aspects of database management in MongoDB. These practices are vital to maintain performance, minimize downtime, and accommodate growing workloads. MongoDB offers several options for scaling and achieving high availability:
Scaling:
Horizontal Scaling (Sharding):
MongoDB supports horizontal scaling through sharding. In sharding, data is distributed across multiple servers or clusters, known as shards. Each shard is responsible for a subset of the data. Sharding is suitable for applications with large datasets and high read and write loads.
Sharding can be used to balance the data distribution and improve query performance.
Vertical Scaling (Replication):
Vertical scaling, often referred to as replica sets, involves adding more resources to a single MongoDB server to improve performance. Replica sets also provide data redundancy and failover capabilities.
In a replica set, one node is the primary, and the others are secondary nodes. The primary node handles all writes and the initial read operations, while the secondary nodes replicate data from the primary to provide data redundancy and read scaling.
High Availability:
Data Center Awareness:
To further enhance high availability, you can deploy replica sets across multiple data centers or cloud regions. This setup ensures that your data remains accessible even if one data center experiences an outage.
Monitoring and Alerting:
Implement robust monitoring and alerting systems to track the health of your MongoDB instances and be immediately notified of any issues or potential failures.
Backups and Restore:
Regularly back up your data and practice data restoration. In the event of a disaster, having up-to-date backups ensures you can quickly recover your data.
Testing Failover:
Periodically simulate failures and test the failover process to ensure that it works as expected. This helps you identify and address issues before they impact your production environment.
MongoDB's flexibility in scaling and high availability makes it a reliable choice for applications that demand performance, scalability, and minimal downtime. Planning for scaling and high availability from the beginning of your MongoDB deployment is essential to accommodate growth and maintain robust operations.
Drivers and SDKs
MongoDB offers official drivers and software development kits (SDKs) for various programming languages, making it easy for developers to interact with MongoDB databases in their preferred programming environment. These drivers and SDKs provide a convenient way to connect, query, and manipulate data in MongoDB. Here are some of the primary MongoDB drivers and SDKs:
MongoDB Drivers:
Node.js (Official Driver): The official MongoDB Node.js driver allows you to work with MongoDB in JavaScript and Node.js applications. It provides asynchronous, non-blocking operations for efficient interaction with MongoDB databases.
Python (Official Driver): The official MongoDB Python driver is called PyMongo. It offers a high-level API for Python applications to connect to and manipulate MongoDB data. PyMongo supports asynchronous I/O for Python 3.
Java (Official Driver): The official MongoDB Java driver is a widely-used driver for connecting Java applications to MongoDB. It includes support for both synchronous and asynchronous programming paradigms.
C#/.NET (Official Driver): The official MongoDB .NET driver allows developers to build .NET applications that work with MongoDB. It supports both .NET Framework and .NET Core/5+.
Perl (Community-Supported): While not an official MongoDB driver, there is a community-supported Perl driver called MongoDB that allows Perl developers to connect to MongoDB.
SDKs and ORM Libraries:
Mongoose (Node.js): Mongoose is a popular Node.js library that provides an object modeling framework for MongoDB. It simplifies data validation, schema design, and query building for Node.js applications.
Spring Data MongoDB (Java): Spring Data MongoDB is part of the Spring Data project and offers a high-level, Spring-based approach to working with MongoDB in Java applications.
Meteor (Node.js): Meteor is a full-stack JavaScript platform that includes its MongoDB integration, allowing developers to build real-time web applications with a simplified API for MongoDB.
Motor (Python): Motor is an asynchronous Python driver for MongoDB that is designed to work seamlessly with asynchronous web frameworks like Tornado and asynchronous programming libraries in Python 3.
These drivers and SDKs make it straightforward to work with MongoDB in a variety of programming languages, frameworks, and platforms. Depending on your application's technology stack, you can choose the appropriate driver or SDK to streamline database interactions and enhance your development workflow.
Deployment and Operations
Deploying and operating a MongoDB database in a production environment requires careful planning and maintenance. Here are key considerations for deploying and managing MongoDB effectively:
Deployment:
Version Selection:
Select the appropriate version of MongoDB for your application, taking into account the latest stable release and the compatibility of your drivers and libraries.
Deployment Topology:
Decide on the desired deployment topology, which may include standalone servers, replica sets, sharded clusters, or a combination of these, depending on your scalability and availability requirements.
Security Measures:
Implement security best practices, including authentication and authorization, network security, encryption, and role-based access control. For cloud deployments, configure network security groups and firewall rules.
Data Backup:
Establish data backup and recovery procedures to ensure data safety. Schedule regular backups and test the restoration process.
Operations:
Monitoring:
Use monitoring tools to keep an eye on the health and performance of your MongoDB deployment. MongoDB Atlas, the cloud-based MongoDB service, offers built-in monitoring and alerting features.
Security Updates:
Stay up-to-date with security patches and updates for MongoDB and the underlying operating system. Regularly apply these updates to address known vulnerabilities.
User Training:
Train your operations team and developers to ensure they are familiar with MongoDB's operational aspects, best practices, and tools.
Logs and Audit Trails:
Enable auditing to track and log database activity. Review logs and audit trails to monitor and investigate database activities.
Proper deployment and operations practices are crucial for maintaining a robust, performant, and secure MongoDB database in production. Regularly assess and adjust your deployment and operations strategies to meet the evolving needs of your application.
Conclusion
In conclusion, MongoDB is a versatile and popular NoSQL database system that offers many features and capabilities for developers and organizations. Whether you're working with MongoDB for application development, data modeling, or database management, it's essential to have a solid understanding of its core concepts and best practices. This knowledge can help you make the most of MongoDB's capabilities and ensure that your applications are scalable, secure, and high-performing.
MongoDB is a powerful database system with a strong ecosystem of tools and resources to support its users. Whether you're building web applications, mobile apps, or data-intensive solutions, MongoDB offers the flexibility and scalability needed to meet your data storage and retrieval needs. Staying up-to-date with the latest MongoDB developments and best practices is essential for maximizing the benefits of this popular NoSQL database.
Understanding Blockchain Technology: A Comprehensive Beginner's Guide
Blockchain technology has emerged as one of the most transformative innovations of our time. It has the potential to revolutionize how we conduct business, manage data, and even interact with one another in the digital age. For those who are new to the concept, the world of blockchain can appear complex and daunting. However, with the right guidance, it becomes accessible and comprehensible.
In this comprehensive beginner's guide, we will embark on a journey to demystify blockchain technology, breaking down its intricate components, and shedding light on its real-world applications. Whether you're a curious individual exploring the technology's basics or a business professional seeking to grasp its implications, this guide will serve as your roadmap to understanding blockchain.
By the time you complete this guide, you'll have a solid foundation in blockchain technology. Whether you're considering investments in cryptocurrency, exploring blockchain solutions for your business, or simply curious about the technology's potential, this beginner's guide will equip you with the knowledge and confidence to navigate the world of blockchain. Let's begin our journey into the exciting world of blockchain technology.
Table of contents
-
What Is Blockchain Technology
-
How Does Blockchain Work?
-
Blockchain vs. Traditional Databases
-
Decentralization: The Core Principle
-
Cryptography in Blockchain
-
Consensus Mechanisms
-
Nodes and Network Participants
-
Smart Contracts
-
Public vs. Private Blockchains
-
Blockchain Use Cases
-
Conclusion
What Is Blockchain Technology
Blockchain technology is a decentralized and distributed digital ledger system that records transactions across multiple computers. It's often described as a "chain of blocks," where each block contains a list of transactions. Here are some key characteristics and components of blockchain technology:
Transparency: The data stored in the blockchain is accessible to anyone on the network. Transactions are visible, and each participant can view the entire history of transactions, promoting transparency and trust.
Security through Cryptography: Transactions in a blockchain are secured using cryptographic techniques. Each transaction is verified and linked to the previous one through complex mathematical algorithms, ensuring the integrity of the data.
Consensus Mechanisms: To add new blocks to the blockchain, a consensus mechanism is used. The most common consensus mechanisms are Proof of Work (PoW) and Proof of Stake (PoS), which ensure that all participants agree on the validity of transactions.
Smart Contracts: Smart contracts are self-executing agreements with the terms of the contract directly written into code. They automatically execute and enforce contract terms when predefined conditions are met. Smart contracts enable automation and remove the need for intermediaries.
Use Cases: Blockchain technology has a wide range of applications beyond cryptocurrencies. It's used in supply chain management, healthcare, voting systems, identity verification, asset tokenization, and more.
Public vs. Private Blockchains: There are public blockchains (open to anyone) and private blockchains (accessible only to authorized participants). Public blockchains, like Bitcoin, are maintained by a distributed network of anonymous users, while private blockchains are typically used by organizations for specific purposes.
Blockchain technology has the potential to disrupt various industries by increasing transparency, reducing fraud, and enabling secure and efficient digital transactions. As it continues to evolve, it is being explored for an even wider range of applications beyond its original use in cryptocurrencies.
How Does Blockchain Work?
Understanding how blockchain works involves delving into the underlying mechanics of this technology. Here's a step-by-step explanation of how blockchain operates:
Data Structure: A blockchain is a distributed ledger made up of a chain of blocks. Each block contains a list of transactions. These transactions can represent various types of data, such as cryptocurrency transfers, asset records, or contract agreements.
Transactions: Participants on the blockchain network initiate transactions. These transactions include information about the sender, receiver, amount, and any other relevant data. Once created, these transactions are broadcast to the network.
Validation: Transactions are grouped together into a block. Before a block is added to the blockchain, it must be validated. Validation involves checking the accuracy and legitimacy of the transactions. This process is performed by nodes in the network.
Adding Blocks: Once a block is validated and consensus is reached, it is added to the existing blockchain. Each block includes a reference to the previous block, creating a continuous chain of blocks. This linkage is what gives blockchain its name.
Network Copies: Each node in the network maintains a copy of the entire blockchain. This redundancy enhances the system's security and resilience. If one node fails or goes offline, the network can continue to operate with the help of other nodes.
Smart Contracts: Some blockchains, like Ethereum, support smart contracts. These are self-executing contracts with predefined rules and conditions. When these conditions are met, the smart contract automatically executes, eliminating the need for intermediaries.
Blockchain technology's distributed, decentralized, and secure nature makes it particularly useful for a wide range of applications, including cryptocurrencies, supply chain management, identity verification, and more. It provides a transparent and tamper-proof system for recording and verifying data and transactions.
Blockchain vs. Traditional Databases
Blockchain and traditional databases are both used to store and manage data, but they differ in several key ways. Here's a comparison of blockchain vs. traditional databases:
Blockchain:
Decentralization: Blockchain is a decentralized system where data is stored and managed across a network of nodes. There is no central authority controlling the data, which makes it resistant to censorship and central points of failure.
Security: Data in a blockchain is secured using cryptographic techniques. Once a block is added to the chain, it is extremely difficult to alter, providing a high level of security and immutability.
Transparency: Blockchain is inherently transparent. All participants in the network can view the entire transaction history, promoting trust and accountability.
Smart Contracts: Some blockchains support smart contracts, self-executing agreements with predefined conditions. These contracts automate processes and reduce the need for intermediaries.
Use Cases: Blockchain is commonly used for cryptocurrencies (e.g., Bitcoin), supply chain management, voting systems, identity verification, and asset tokenization.
Traditional Databases:
Centralization: Traditional databases are typically centralized, with a single entity or server responsible for data storage and management. This centralization can be a vulnerability in terms of security and reliability.
Security: While traditional databases use security measures like access controls and encryption, they are generally more susceptible to hacking or unauthorized access compared to blockchains.
Privacy: Traditional databases can offer more control over data privacy, as access can be restricted and permissions managed. In contrast, blockchains often prioritize transparency.
Consistency and Speed: Traditional databases can provide faster data processing and transaction speeds, as they don't require the extensive consensus mechanisms used in blockchains.
Use Cases: Traditional databases are commonly used in a wide range of applications, including customer relationship management (CRM), content management systems (CMS), and business applications.
The choice between blockchain and traditional databases depends on the specific use case, security requirements, need for decentralization, and the desired level of transparency. In some cases, a hybrid approach that combines both technologies may be the most appropriate solution.
Decentralization: The Core Principle
Decentralization is a core principle of blockchain technology and one of its defining features. It refers to the distribution of control, authority, and data across a network of nodes rather than relying on a central authority or single point of control. Here's a deeper exploration of why decentralization is a fundamental principle of blockchain:
Elimination of Central Authority: In traditional systems, such as centralized databases or financial institutions, there is a central authority that manages and controls data, transactions, and decisions. In contrast, blockchain operates on a peer-to-peer network where no single entity or institution has absolute control.
Resilience and Redundancy: A decentralized blockchain network is highly resilient. If one node on the network fails or is compromised, the network can continue to operate because other nodes maintain copies of the data. This redundancy enhances the system's reliability and fault tolerance.
Enhanced Security: Decentralization contributes to the security of blockchain systems. It is challenging for malicious actors to manipulate or attack the network because they would need to compromise a significant portion of the nodes, which is computationally and logistically challenging.
Trust and Transparency: Decentralization fosters trust in the system. All participants in the network can verify the transactions and data, reducing the need to trust a central entity. This transparency is particularly valuable in situations where trust is a critical factor, such as financial transactions or supply chain management.
Inclusivity: Decentralization can promote inclusivity by allowing anyone to participate in the network without relying on intermediaries or gatekeepers. This can be particularly empowering for individuals in regions with limited access to traditional financial services or information.
While decentralization is a powerful and transformative principle, it's important to note that it may not be the best solution for every use case. Some applications require centralization for efficiency, control, or compliance reasons. Striking the right balance between decentralization and centralization is a consideration that organizations and individuals need to make when implementing blockchain technology to ensure it aligns with their specific goals and requirements.
Cryptography in Blockchain
Cryptography plays a fundamental role in blockchain technology, contributing to the security and integrity of the data and transactions within the system. Here's how cryptography is used in blockchain:
Data Encryption: Cryptography is used to encrypt sensitive data in a blockchain, such as transaction details, to protect it from unauthorized access. When data is encrypted, it's converted into an unreadable format, which can only be decrypted by someone with the appropriate decryption key. This ensures the confidentiality of the data.
Digital Signatures: Digital signatures are a key component of blockchain transactions. They are created using asymmetric cryptography, which involves a public key (used for encryption) and a private key (used for decryption). The digital signature provides proof of the transaction's authenticity and ensures that it can't be altered by anyone other than the holder of the private key.
Public and Private Keys: Blockchain users have a pair of cryptographic keys: a public key, which is visible to everyone on the network, and a private key, which is kept secret. The public key is used to receive transactions, while the private key is used to sign transactions. Together, they enable secure and verifiable transactions.
Cryptographic Algorithms: Different cryptographic algorithms are used for different purposes in blockchain, such as Elliptic Curve Digital Signature Algorithm (ECDSA) for digital signatures and SHA-256 for hashing in Bitcoin. The choice of algorithm impacts security and efficiency.
Address Generation: Cryptography is used to derive addresses in the blockchain for both sender and receiver, which enhances privacy. An address is a representation of the public key and doesn't directly reveal the identity of the user.
The use of cryptography in blockchain technology provides security, integrity, and privacy to the data and transactions on the network. It ensures that transactions are verifiable, tamper-resistant, and transparent, contributing to the trustworthiness of the system. The strength of these cryptographic techniques is a key factor in the resilience of blockchain systems against various forms of attacks and fraud.
Consensus Mechanisms
Consensus mechanisms are at the heart of blockchain technology. They are the protocols and algorithms that ensure that all nodes on a decentralized network agree on the state of the blockchain. Consensus mechanisms are essential for validating and adding new transactions to the blockchain in a secure and trustworthy manner. Here are some common consensus mechanisms:
Proof of Work (PoW): PoW is the original consensus mechanism used in Bitcoin and many other cryptocurrencies. In PoW, miners compete to solve complex mathematical puzzles, and the first one to solve it gets the right to add a new block to the blockchain. PoW is known for its security but is energy-intensive.
Proof of Stake (PoS): PoS is an alternative to PoW. In PoS, validators (sometimes called "stakers") are chosen to create new blocks based on the number of cryptocurrency tokens they hold and are willing to "stake" as collateral. PoS is more energy-efficient compared to PoW.
Delegated Proof of Stake (DPoS): DPoS is a variation of PoS where token holders vote for a select group of delegates who are responsible for validating transactions and creating new blocks. DPoS is known for its speed and scalability.
Byzantine Fault Tolerance (BFT): BFT is a family of consensus algorithms that are designed to be highly fault-tolerant. They are often used in private or permissioned blockchains, where network participants are known and trusted.
Practical Byzantine Fault Tolerance (PBFT): PBFT is a specific BFT algorithm used in some private blockchain networks. It's designed to work efficiently in a network with known participants.
Raft Consensus: Raft is another consensus algorithm used in some private blockchains. It focuses on simplicity and fault tolerance, making it a suitable choice for less complex networks.
The choice of consensus mechanism depends on the goals and requirements of the blockchain network. PoW is known for its security but consumes a lot of energy. PoS is more energy-efficient but may be seen as less secure. DPoS offers speed and scalability, but it relies on a smaller number of validators. The right consensus mechanism is selected based on factors like security, energy efficiency, scalability, and decentralization requirements.
Nodes and Network Participants
In a blockchain network, nodes and network participants are fundamental components that play distinct roles in the operation and maintenance of the network. Understanding these roles is essential to grasp how blockchain technology functions. Here's an explanation of nodes and network participants:
Nodes:
Definition: Nodes are individual computers or devices connected to a blockchain network. Each node maintains a copy of the blockchain's ledger, which contains all the historical transaction data.
Roles: Nodes have various roles, depending on the type of blockchain network (public, private, or consortium) and the consensus mechanism in use. The common node roles include:
Light Node: Also known as a "light client," a light node does not store the entire blockchain. It relies on full nodes to access and verify transaction data.
Mining Node: In Proof of Work (PoW) and some other consensus mechanisms, miners use specialized nodes to compete in solving complex mathematical puzzles and add new blocks to the blockchain.
Validator Node: In Proof of Stake (PoS) and other consensus mechanisms, validators take turns proposing and validating new blocks. These nodes are responsible for network security.
Network Participants:
Definition: Network participants are individuals, organizations, or entities that interact with the blockchain network by sending and receiving transactions. They may or may not run nodes.
Roles: Network participants engage in various activities within the blockchain ecosystem. Common network participant roles include:
Users: Users are individuals who perform transactions, transfer assets, or engage in smart contract activities on the blockchain. They do not necessarily run nodes.
Developers: Blockchain developers create and maintain decentralized applications (DApps) and smart contracts. They design software that interacts with the blockchain.
Miners/Validators: Miners (in PoW) or validators (in PoS) participate in the consensus process, add new blocks, and secure the network. They may also be network participants.
Investors/Token Holders: Many network participants invest in blockchain projects by holding tokens or cryptocurrencies, such as Bitcoin or Ethereum.
Both nodes and network participants play critical roles in the blockchain ecosystem. Nodes ensure the network's integrity and security, while network participants drive the usage and adoption of blockchain technology for various applications. Together, they form a decentralized and trustless network that operates without a central authority.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. These contracts automatically execute and enforce themselves when predefined conditions are met. Smart contracts run on blockchain platforms and have gained significant attention for their potential to revolutionize various industries. Here's a more detailed look at smart contracts:
Key Characteristics and Features:
Code-Based: Smart contracts are written in programming languages specifically designed for the blockchain platform on which they run. The code represents the rules, conditions, and actions of the contract.
Self-Executing: Once deployed on the blockchain, smart contracts operate autonomously. They automatically execute actions, such as transferring digital assets or changing the state of an application, without the need for intermediaries.
Immutable: Once a smart contract is deployed, it becomes part of the blockchain and is extremely difficult to alter or tamper with. This immutability ensures the integrity of the contract's terms.
Transparency: Smart contracts are visible on the blockchain, and their code and execution history can be inspected by anyone. This transparency enhances trust in the contract's operations.
Decentralization: Smart contracts operate on a decentralized blockchain network. This eliminates the need for a central authority to oversee and enforce the contract terms.
Smart contracts are an exciting innovation that offers automation, transparency, and trust in a wide range of applications. Their continued development and adoption depend on overcoming challenges related to security, legal recognition, and privacy. As blockchain technology matures, smart contracts are likely to play an increasingly significant role in reshaping how agreements and transactions are executed.
Public vs. Private Blockchains
Public and private blockchains are two distinct types of blockchain networks, each with its own set of characteristics and use cases. Understanding the differences between them is crucial for determining which type of blockchain is most suitable for a particular application. Here's a comparison of public and private blockchains:
Public Blockchains:
Accessibility: Public blockchains are open and accessible to anyone. Anyone can participate in the network, validate transactions, and create new blocks. There are no restrictions on who can join.
Decentralization: Public blockchains are highly decentralized, often involving thousands or even millions of participants worldwide. This decentralization enhances security and reduces the risk of central points of control.
Transparency: All transactions on a public blockchain are transparent and visible to all participants. This transparency promotes trust and accountability.
Cryptocurrency: Many public blockchains have their own native cryptocurrencies, which are used to incentivize network participants, secure the network, and facilitate transactions.
Use Cases: Public blockchains are commonly associated with cryptocurrencies like Bitcoin and Ethereum, but they are also used for various applications, including decentralized finance (DeFi), digital identities, and public voting systems.
Private Blockchains:
Permissioned: Private blockchains are permissioned networks, meaning that participation is restricted to authorized entities or individuals. These networks are not open to the public.
Centralized Control: Private blockchains are typically more centralized than public blockchains. A specific organization or consortium of organizations often controls the network.
Privacy: Private blockchains can offer greater privacy and confidentiality, as access to data and transactions can be restricted to authorized parties. This makes them suitable for applications that require data privacy.
Efficiency: Private blockchains are often more efficient in terms of transaction processing speed and scalability, as they don't have to contend with the computational overhead of open, decentralized networks.
Use Cases: Private blockchains are commonly used by enterprises and organizations for applications such as supply chain management, record keeping, and private financial transactions.
Hybrid Blockchains: Some blockchain networks combine elements of both public and private blockchains. These hybrid blockchains aim to leverage the benefits of decentralization while maintaining control and privacy for specific use cases.
The choice between a public and private blockchain depends on the specific requirements and goals of an application. Public blockchains are well-suited for open, trustless, and decentralized applications, while private blockchains are ideal for situations where privacy, control, and efficiency are paramount. Hybrid blockchains can provide a compromise that balances the benefits of both approaches.
Blockchain Use Cases
Blockchain technology has a wide range of use cases across various industries due to its ability to provide transparency, security, and immutability. Here are some notable blockchain use cases:
Cryptocurrencies: The most well-known use case of blockchain is the creation and management of digital currencies, such as Bitcoin, Ethereum, and many others. These cryptocurrencies allow for secure, peer-to-peer transactions without the need for intermediaries like banks.
Identity Verification: Blockchain can be used for secure and decentralized identity management. Users can have control over their own digital identities, providing a more secure way to access services and protect personal data.
Voting Systems: Blockchain can improve the integrity and transparency of voting systems. It can enable secure online voting and ensure that votes are tamper-proof and anonymous.
Cross-Border Payments: Blockchain technology can facilitate cross-border payments by reducing the time and cost associated with traditional banking systems. Ripple is a well-known example of a blockchain company focusing on cross-border payments.
Healthcare Data Management: Blockchain can provide a secure and interoperable way to manage healthcare data, making patient records more accessible and reducing the risk of data breaches.
Real Estate Transactions: Blockchain simplifies real estate transactions by automating tasks such as title transfers and escrow processes. This reduces the risk of fraud and speeds up the buying and selling of property.
Gaming and NFTs: Non-fungible tokens (NFTs) are unique digital assets that can represent ownership of digital art, collectibles, in-game items, and more. Blockchain is the technology that underpins NFTs and the gaming industry's digital economies.
Government Services: Blockchain can enhance government services, such as secure record-keeping, identity verification, and efficient delivery of public benefits.
Education and Credential Verification: Blockchain can be used to securely verify educational credentials, reducing the risk of fraudulent qualifications.
These are just a few examples of blockchain use cases, and the technology continues to evolve and find applications in various other sectors. The flexibility, security, and transparency of blockchain make it a promising solution for a wide range of industries and processes.
Conclusion
In conclusion, blockchain technology is a transformative innovation with the potential to disrupt numerous industries and change the way we conduct transactions, manage data, and establish trust in the digital world. Its key principles, such as decentralization, security through cryptography, and transparency, have opened up a wide range of exciting use cases.
Blockchain's core concepts, including decentralized networks, consensus mechanisms, and the use of smart contracts, offer a new paradigm for building trust and facilitating secure and transparent interactions in a variety of sectors.
The choice between public and private blockchains depends on the specific needs and objectives of an application, and in some cases, hybrid solutions may offer the best of both worlds.
Blockchain technology has already made significant strides in the domains of cryptocurrency, supply chain management, identity verification, and more. Its potential to revolutionize industries like healthcare, voting systems, real estate, and finance is being explored, with the aim of increasing efficiency, reducing fraud, and improving transparency.
As blockchain continues to evolve and address challenges related to scalability, security, and regulatory concerns, it is poised to reshape the digital landscape and bring new opportunities for innovation and decentralization. Its adoption and integration into various sectors will be an exciting journey, offering transformative possibilities for both individuals and organizations.
Read More
Blockchain technology has emerged as one of the most transformative innovations of our time. It has the potential to revolutionize how we conduct business, manage data, and even interact with one another in the digital age. For those who are new to the concept, the world of blockchain can appear complex and daunting. However, with the right guidance, it becomes accessible and comprehensible.
In this comprehensive beginner's guide, we will embark on a journey to demystify blockchain technology, breaking down its intricate components, and shedding light on its real-world applications. Whether you're a curious individual exploring the technology's basics or a business professional seeking to grasp its implications, this guide will serve as your roadmap to understanding blockchain.
By the time you complete this guide, you'll have a solid foundation in blockchain technology. Whether you're considering investments in cryptocurrency, exploring blockchain solutions for your business, or simply curious about the technology's potential, this beginner's guide will equip you with the knowledge and confidence to navigate the world of blockchain. Let's begin our journey into the exciting world of blockchain technology.
Table of contents
-
What Is Blockchain Technology
-
How Does Blockchain Work?
-
Blockchain vs. Traditional Databases
-
Decentralization: The Core Principle
-
Cryptography in Blockchain
-
Consensus Mechanisms
-
Nodes and Network Participants
-
Smart Contracts
-
Public vs. Private Blockchains
-
Blockchain Use Cases
-
Conclusion
What Is Blockchain Technology
Blockchain technology is a decentralized and distributed digital ledger system that records transactions across multiple computers. It's often described as a "chain of blocks," where each block contains a list of transactions. Here are some key characteristics and components of blockchain technology:
Transparency: The data stored in the blockchain is accessible to anyone on the network. Transactions are visible, and each participant can view the entire history of transactions, promoting transparency and trust.
Security through Cryptography: Transactions in a blockchain are secured using cryptographic techniques. Each transaction is verified and linked to the previous one through complex mathematical algorithms, ensuring the integrity of the data.
Consensus Mechanisms: To add new blocks to the blockchain, a consensus mechanism is used. The most common consensus mechanisms are Proof of Work (PoW) and Proof of Stake (PoS), which ensure that all participants agree on the validity of transactions.
Smart Contracts: Smart contracts are self-executing agreements with the terms of the contract directly written into code. They automatically execute and enforce contract terms when predefined conditions are met. Smart contracts enable automation and remove the need for intermediaries.
Use Cases: Blockchain technology has a wide range of applications beyond cryptocurrencies. It's used in supply chain management, healthcare, voting systems, identity verification, asset tokenization, and more.
Public vs. Private Blockchains: There are public blockchains (open to anyone) and private blockchains (accessible only to authorized participants). Public blockchains, like Bitcoin, are maintained by a distributed network of anonymous users, while private blockchains are typically used by organizations for specific purposes.
Blockchain technology has the potential to disrupt various industries by increasing transparency, reducing fraud, and enabling secure and efficient digital transactions. As it continues to evolve, it is being explored for an even wider range of applications beyond its original use in cryptocurrencies.
How Does Blockchain Work?
Understanding how blockchain works involves delving into the underlying mechanics of this technology. Here's a step-by-step explanation of how blockchain operates:
Data Structure: A blockchain is a distributed ledger made up of a chain of blocks. Each block contains a list of transactions. These transactions can represent various types of data, such as cryptocurrency transfers, asset records, or contract agreements.
Transactions: Participants on the blockchain network initiate transactions. These transactions include information about the sender, receiver, amount, and any other relevant data. Once created, these transactions are broadcast to the network.
Validation: Transactions are grouped together into a block. Before a block is added to the blockchain, it must be validated. Validation involves checking the accuracy and legitimacy of the transactions. This process is performed by nodes in the network.
Adding Blocks: Once a block is validated and consensus is reached, it is added to the existing blockchain. Each block includes a reference to the previous block, creating a continuous chain of blocks. This linkage is what gives blockchain its name.
Network Copies: Each node in the network maintains a copy of the entire blockchain. This redundancy enhances the system's security and resilience. If one node fails or goes offline, the network can continue to operate with the help of other nodes.
Smart Contracts: Some blockchains, like Ethereum, support smart contracts. These are self-executing contracts with predefined rules and conditions. When these conditions are met, the smart contract automatically executes, eliminating the need for intermediaries.
Blockchain technology's distributed, decentralized, and secure nature makes it particularly useful for a wide range of applications, including cryptocurrencies, supply chain management, identity verification, and more. It provides a transparent and tamper-proof system for recording and verifying data and transactions.
Blockchain vs. Traditional Databases
Blockchain and traditional databases are both used to store and manage data, but they differ in several key ways. Here's a comparison of blockchain vs. traditional databases:
Blockchain:
Decentralization: Blockchain is a decentralized system where data is stored and managed across a network of nodes. There is no central authority controlling the data, which makes it resistant to censorship and central points of failure.
Security: Data in a blockchain is secured using cryptographic techniques. Once a block is added to the chain, it is extremely difficult to alter, providing a high level of security and immutability.
Transparency: Blockchain is inherently transparent. All participants in the network can view the entire transaction history, promoting trust and accountability.
Smart Contracts: Some blockchains support smart contracts, self-executing agreements with predefined conditions. These contracts automate processes and reduce the need for intermediaries.
Use Cases: Blockchain is commonly used for cryptocurrencies (e.g., Bitcoin), supply chain management, voting systems, identity verification, and asset tokenization.
Traditional Databases:
Centralization: Traditional databases are typically centralized, with a single entity or server responsible for data storage and management. This centralization can be a vulnerability in terms of security and reliability.
Security: While traditional databases use security measures like access controls and encryption, they are generally more susceptible to hacking or unauthorized access compared to blockchains.
Privacy: Traditional databases can offer more control over data privacy, as access can be restricted and permissions managed. In contrast, blockchains often prioritize transparency.
Consistency and Speed: Traditional databases can provide faster data processing and transaction speeds, as they don't require the extensive consensus mechanisms used in blockchains.
Use Cases: Traditional databases are commonly used in a wide range of applications, including customer relationship management (CRM), content management systems (CMS), and business applications.
The choice between blockchain and traditional databases depends on the specific use case, security requirements, need for decentralization, and the desired level of transparency. In some cases, a hybrid approach that combines both technologies may be the most appropriate solution.
Decentralization: The Core Principle
Decentralization is a core principle of blockchain technology and one of its defining features. It refers to the distribution of control, authority, and data across a network of nodes rather than relying on a central authority or single point of control. Here's a deeper exploration of why decentralization is a fundamental principle of blockchain:
Elimination of Central Authority: In traditional systems, such as centralized databases or financial institutions, there is a central authority that manages and controls data, transactions, and decisions. In contrast, blockchain operates on a peer-to-peer network where no single entity or institution has absolute control.
Resilience and Redundancy: A decentralized blockchain network is highly resilient. If one node on the network fails or is compromised, the network can continue to operate because other nodes maintain copies of the data. This redundancy enhances the system's reliability and fault tolerance.
Enhanced Security: Decentralization contributes to the security of blockchain systems. It is challenging for malicious actors to manipulate or attack the network because they would need to compromise a significant portion of the nodes, which is computationally and logistically challenging.
Trust and Transparency: Decentralization fosters trust in the system. All participants in the network can verify the transactions and data, reducing the need to trust a central entity. This transparency is particularly valuable in situations where trust is a critical factor, such as financial transactions or supply chain management.
Inclusivity: Decentralization can promote inclusivity by allowing anyone to participate in the network without relying on intermediaries or gatekeepers. This can be particularly empowering for individuals in regions with limited access to traditional financial services or information.
While decentralization is a powerful and transformative principle, it's important to note that it may not be the best solution for every use case. Some applications require centralization for efficiency, control, or compliance reasons. Striking the right balance between decentralization and centralization is a consideration that organizations and individuals need to make when implementing blockchain technology to ensure it aligns with their specific goals and requirements.
Cryptography in Blockchain
Cryptography plays a fundamental role in blockchain technology, contributing to the security and integrity of the data and transactions within the system. Here's how cryptography is used in blockchain:
Data Encryption: Cryptography is used to encrypt sensitive data in a blockchain, such as transaction details, to protect it from unauthorized access. When data is encrypted, it's converted into an unreadable format, which can only be decrypted by someone with the appropriate decryption key. This ensures the confidentiality of the data.
Digital Signatures: Digital signatures are a key component of blockchain transactions. They are created using asymmetric cryptography, which involves a public key (used for encryption) and a private key (used for decryption). The digital signature provides proof of the transaction's authenticity and ensures that it can't be altered by anyone other than the holder of the private key.
Public and Private Keys: Blockchain users have a pair of cryptographic keys: a public key, which is visible to everyone on the network, and a private key, which is kept secret. The public key is used to receive transactions, while the private key is used to sign transactions. Together, they enable secure and verifiable transactions.
Cryptographic Algorithms: Different cryptographic algorithms are used for different purposes in blockchain, such as Elliptic Curve Digital Signature Algorithm (ECDSA) for digital signatures and SHA-256 for hashing in Bitcoin. The choice of algorithm impacts security and efficiency.
Address Generation: Cryptography is used to derive addresses in the blockchain for both sender and receiver, which enhances privacy. An address is a representation of the public key and doesn't directly reveal the identity of the user.
The use of cryptography in blockchain technology provides security, integrity, and privacy to the data and transactions on the network. It ensures that transactions are verifiable, tamper-resistant, and transparent, contributing to the trustworthiness of the system. The strength of these cryptographic techniques is a key factor in the resilience of blockchain systems against various forms of attacks and fraud.
Consensus Mechanisms
Consensus mechanisms are at the heart of blockchain technology. They are the protocols and algorithms that ensure that all nodes on a decentralized network agree on the state of the blockchain. Consensus mechanisms are essential for validating and adding new transactions to the blockchain in a secure and trustworthy manner. Here are some common consensus mechanisms:
Proof of Work (PoW): PoW is the original consensus mechanism used in Bitcoin and many other cryptocurrencies. In PoW, miners compete to solve complex mathematical puzzles, and the first one to solve it gets the right to add a new block to the blockchain. PoW is known for its security but is energy-intensive.
Proof of Stake (PoS): PoS is an alternative to PoW. In PoS, validators (sometimes called "stakers") are chosen to create new blocks based on the number of cryptocurrency tokens they hold and are willing to "stake" as collateral. PoS is more energy-efficient compared to PoW.
Delegated Proof of Stake (DPoS): DPoS is a variation of PoS where token holders vote for a select group of delegates who are responsible for validating transactions and creating new blocks. DPoS is known for its speed and scalability.
Byzantine Fault Tolerance (BFT): BFT is a family of consensus algorithms that are designed to be highly fault-tolerant. They are often used in private or permissioned blockchains, where network participants are known and trusted.
Practical Byzantine Fault Tolerance (PBFT): PBFT is a specific BFT algorithm used in some private blockchain networks. It's designed to work efficiently in a network with known participants.
Raft Consensus: Raft is another consensus algorithm used in some private blockchains. It focuses on simplicity and fault tolerance, making it a suitable choice for less complex networks.
The choice of consensus mechanism depends on the goals and requirements of the blockchain network. PoW is known for its security but consumes a lot of energy. PoS is more energy-efficient but may be seen as less secure. DPoS offers speed and scalability, but it relies on a smaller number of validators. The right consensus mechanism is selected based on factors like security, energy efficiency, scalability, and decentralization requirements.
Nodes and Network Participants
In a blockchain network, nodes and network participants are fundamental components that play distinct roles in the operation and maintenance of the network. Understanding these roles is essential to grasp how blockchain technology functions. Here's an explanation of nodes and network participants:
Nodes:
Definition: Nodes are individual computers or devices connected to a blockchain network. Each node maintains a copy of the blockchain's ledger, which contains all the historical transaction data.
Roles: Nodes have various roles, depending on the type of blockchain network (public, private, or consortium) and the consensus mechanism in use. The common node roles include:
Light Node: Also known as a "light client," a light node does not store the entire blockchain. It relies on full nodes to access and verify transaction data.
Mining Node: In Proof of Work (PoW) and some other consensus mechanisms, miners use specialized nodes to compete in solving complex mathematical puzzles and add new blocks to the blockchain.
Validator Node: In Proof of Stake (PoS) and other consensus mechanisms, validators take turns proposing and validating new blocks. These nodes are responsible for network security.
Network Participants:
Definition: Network participants are individuals, organizations, or entities that interact with the blockchain network by sending and receiving transactions. They may or may not run nodes.
Roles: Network participants engage in various activities within the blockchain ecosystem. Common network participant roles include:
Users: Users are individuals who perform transactions, transfer assets, or engage in smart contract activities on the blockchain. They do not necessarily run nodes.
Developers: Blockchain developers create and maintain decentralized applications (DApps) and smart contracts. They design software that interacts with the blockchain.
Miners/Validators: Miners (in PoW) or validators (in PoS) participate in the consensus process, add new blocks, and secure the network. They may also be network participants.
Investors/Token Holders: Many network participants invest in blockchain projects by holding tokens or cryptocurrencies, such as Bitcoin or Ethereum.
Both nodes and network participants play critical roles in the blockchain ecosystem. Nodes ensure the network's integrity and security, while network participants drive the usage and adoption of blockchain technology for various applications. Together, they form a decentralized and trustless network that operates without a central authority.
Smart Contracts
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. These contracts automatically execute and enforce themselves when predefined conditions are met. Smart contracts run on blockchain platforms and have gained significant attention for their potential to revolutionize various industries. Here's a more detailed look at smart contracts:
Key Characteristics and Features:
Code-Based: Smart contracts are written in programming languages specifically designed for the blockchain platform on which they run. The code represents the rules, conditions, and actions of the contract.
Self-Executing: Once deployed on the blockchain, smart contracts operate autonomously. They automatically execute actions, such as transferring digital assets or changing the state of an application, without the need for intermediaries.
Immutable: Once a smart contract is deployed, it becomes part of the blockchain and is extremely difficult to alter or tamper with. This immutability ensures the integrity of the contract's terms.
Transparency: Smart contracts are visible on the blockchain, and their code and execution history can be inspected by anyone. This transparency enhances trust in the contract's operations.
Decentralization: Smart contracts operate on a decentralized blockchain network. This eliminates the need for a central authority to oversee and enforce the contract terms.
Smart contracts are an exciting innovation that offers automation, transparency, and trust in a wide range of applications. Their continued development and adoption depend on overcoming challenges related to security, legal recognition, and privacy. As blockchain technology matures, smart contracts are likely to play an increasingly significant role in reshaping how agreements and transactions are executed.
Public vs. Private Blockchains
Public and private blockchains are two distinct types of blockchain networks, each with its own set of characteristics and use cases. Understanding the differences between them is crucial for determining which type of blockchain is most suitable for a particular application. Here's a comparison of public and private blockchains:
Public Blockchains:
Accessibility: Public blockchains are open and accessible to anyone. Anyone can participate in the network, validate transactions, and create new blocks. There are no restrictions on who can join.
Decentralization: Public blockchains are highly decentralized, often involving thousands or even millions of participants worldwide. This decentralization enhances security and reduces the risk of central points of control.
Transparency: All transactions on a public blockchain are transparent and visible to all participants. This transparency promotes trust and accountability.
Cryptocurrency: Many public blockchains have their own native cryptocurrencies, which are used to incentivize network participants, secure the network, and facilitate transactions.
Use Cases: Public blockchains are commonly associated with cryptocurrencies like Bitcoin and Ethereum, but they are also used for various applications, including decentralized finance (DeFi), digital identities, and public voting systems.
Private Blockchains:
Permissioned: Private blockchains are permissioned networks, meaning that participation is restricted to authorized entities or individuals. These networks are not open to the public.
Centralized Control: Private blockchains are typically more centralized than public blockchains. A specific organization or consortium of organizations often controls the network.
Privacy: Private blockchains can offer greater privacy and confidentiality, as access to data and transactions can be restricted to authorized parties. This makes them suitable for applications that require data privacy.
Efficiency: Private blockchains are often more efficient in terms of transaction processing speed and scalability, as they don't have to contend with the computational overhead of open, decentralized networks.
Use Cases: Private blockchains are commonly used by enterprises and organizations for applications such as supply chain management, record keeping, and private financial transactions.
Hybrid Blockchains: Some blockchain networks combine elements of both public and private blockchains. These hybrid blockchains aim to leverage the benefits of decentralization while maintaining control and privacy for specific use cases.
The choice between a public and private blockchain depends on the specific requirements and goals of an application. Public blockchains are well-suited for open, trustless, and decentralized applications, while private blockchains are ideal for situations where privacy, control, and efficiency are paramount. Hybrid blockchains can provide a compromise that balances the benefits of both approaches.
Blockchain Use Cases
Blockchain technology has a wide range of use cases across various industries due to its ability to provide transparency, security, and immutability. Here are some notable blockchain use cases:
Cryptocurrencies: The most well-known use case of blockchain is the creation and management of digital currencies, such as Bitcoin, Ethereum, and many others. These cryptocurrencies allow for secure, peer-to-peer transactions without the need for intermediaries like banks.
Identity Verification: Blockchain can be used for secure and decentralized identity management. Users can have control over their own digital identities, providing a more secure way to access services and protect personal data.
Voting Systems: Blockchain can improve the integrity and transparency of voting systems. It can enable secure online voting and ensure that votes are tamper-proof and anonymous.
Cross-Border Payments: Blockchain technology can facilitate cross-border payments by reducing the time and cost associated with traditional banking systems. Ripple is a well-known example of a blockchain company focusing on cross-border payments.
Healthcare Data Management: Blockchain can provide a secure and interoperable way to manage healthcare data, making patient records more accessible and reducing the risk of data breaches.
Real Estate Transactions: Blockchain simplifies real estate transactions by automating tasks such as title transfers and escrow processes. This reduces the risk of fraud and speeds up the buying and selling of property.
Gaming and NFTs: Non-fungible tokens (NFTs) are unique digital assets that can represent ownership of digital art, collectibles, in-game items, and more. Blockchain is the technology that underpins NFTs and the gaming industry's digital economies.
Government Services: Blockchain can enhance government services, such as secure record-keeping, identity verification, and efficient delivery of public benefits.
Education and Credential Verification: Blockchain can be used to securely verify educational credentials, reducing the risk of fraudulent qualifications.
These are just a few examples of blockchain use cases, and the technology continues to evolve and find applications in various other sectors. The flexibility, security, and transparency of blockchain make it a promising solution for a wide range of industries and processes.
Conclusion
In conclusion, blockchain technology is a transformative innovation with the potential to disrupt numerous industries and change the way we conduct transactions, manage data, and establish trust in the digital world. Its key principles, such as decentralization, security through cryptography, and transparency, have opened up a wide range of exciting use cases.
Blockchain's core concepts, including decentralized networks, consensus mechanisms, and the use of smart contracts, offer a new paradigm for building trust and facilitating secure and transparent interactions in a variety of sectors.
The choice between public and private blockchains depends on the specific needs and objectives of an application, and in some cases, hybrid solutions may offer the best of both worlds.
Blockchain technology has already made significant strides in the domains of cryptocurrency, supply chain management, identity verification, and more. Its potential to revolutionize industries like healthcare, voting systems, real estate, and finance is being explored, with the aim of increasing efficiency, reducing fraud, and improving transparency.
As blockchain continues to evolve and address challenges related to scalability, security, and regulatory concerns, it is poised to reshape the digital landscape and bring new opportunities for innovation and decentralization. Its adoption and integration into various sectors will be an exciting journey, offering transformative possibilities for both individuals and organizations.
The Benefits of Earning a CCNA Certification for Your Networking Career
In the fast-paced world of information technology, staying ahead in the networking industry is an ever-evolving challenge. Networking professionals must continually adapt to emerging technologies, understand complex systems, and demonstrate their skills to prospective employers. Among the various certifications available, the Cisco Certified Network Associate (CCNA) certification stands out as a prestigious and highly regarded credential that opens doors to numerous opportunities in the field.
This article explores the significant benefits of earning a CCNA certification for your networking career. Whether you are a seasoned IT professional looking to advance your skills or someone considering a career in networking, understanding the advantages of CCNA can help you make informed decisions about your professional development. From enhanced career prospects and higher earning potential to industry recognition and skill development, the CCNA certification offers a multitude of rewards that can positively impact your networking journey. In the pages that follow, we will delve into these benefits and illustrate how CCNA can be a pivotal asset in achieving your career aspirations.
Table of contents
-
Enhanced Career Opportunities: How CCNA Opens Doors
-
Higher Earning Potential: The Financial Benefits of CCNA Certification
-
Industry Recognition: Why Employers Value CCNA Certified Professionals
-
Skill Development: What You'll Learn During CCNA Training
-
A Foundation for Advanced Certifications: How CCNA Paves the Way
-
Global Reach: The Portability of CCNA Certification
-
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
-
Job Security: How CCNA Certification Mitigates Career Risks
-
Networking Community and Support: CCNA's Role in Building Connections
-
Real-World Application: Success Stories of CCNA Professionals
-
Conclusion
Enhanced Career Opportunities: How CCNA Opens Doors
In the ever-evolving realm of networking, professionals are constantly seeking ways to enhance their careers and remain competitive. The Cisco Certified Network Associate (CCNA) certification has emerged as a game-changer in this regard, offering a clear pathway to enhanced career opportunities and professional growth.
Versatility in Networking Roles
CCNA certification is designed to equip professionals with a broad spectrum of networking skills. Whether you are interested in network administration, security, or wireless networking, CCNA provides a foundational understanding of these domains. This versatility makes CCNA holders attractive candidates for a wide range of networking roles, from network engineers to security specialists.
Immediate Recognition
When your resume bears the CCNA logo, it serves as an instant indicator of your networking proficiency to potential employers. Many organizations value CCNA certification as a prerequisite for hiring, as it validates your knowledge and commitment to the field. This immediate recognition can significantly reduce the time it takes to land your dream job.
Entry into Cisco's Ecosystem
Cisco is a global leader in networking technologies, and CCNA is your entry ticket to their ecosystem. Gaining a CCNA certification allows you to interact with Cisco's products and solutions more effectively. This deepens your understanding of their offerings, making you a more valuable asset to any organization that relies on Cisco networking equipment.
Better Networking Skills and Problem-Solving Abilities
The CCNA curriculum focuses on both theoretical knowledge and hands-on skills. As a CCNA candidate, you'll learn how to configure, troubleshoot, and manage network devices effectively. This not only enhances your networking expertise but also hones your problem-solving abilities, which are highly valued in IT roles.
Career Advancement
For networking professionals looking to climb the career ladder, CCNA certification is an invaluable stepping stone. Many companies prioritize employees with CCNA credentials when considering candidates for leadership and managerial positions. The knowledge and skills acquired through CCNA training can help you stand out and qualify for promotions.
Global Opportunities
Networking is a universal language in the IT world, and CCNA certification is recognized internationally. Whether you aspire to work in your home country or abroad, CCNA opens doors to a wealth of global career opportunities. It's a passport to working in diverse and exciting environments.
Higher Earning Potential: The Financial Benefits of CCNA Certification
In today's competitive job market, financial rewards play a significant role in career decisions. For networking professionals, the Cisco Certified Network Associate (CCNA) certification not only opens doors to exciting opportunities but also brings tangible financial benefits. In this section, we'll delve into how CCNA can lead to a substantial increase in earning potential.
Competitive Edge in Salary Negotiations
CCNA certification immediately sets you apart from non-certified peers. Employers often recognize the commitment, knowledge, and skills required to earn the CCNA credential. As a result, CCNA-certified professionals are in a better position to negotiate higher starting salaries, more significant pay raises, and more lucrative job offers.
Increased Starting Salaries
For entry-level positions, CCNA certification can significantly boost your starting salary. Employers are willing to pay more for professionals who have proven their expertise and commitment to the networking field through certification. This premium can help you secure a higher income from the outset of your career.
Expanded Career Options
CCNA certification opens the door to a wider range of career options, many of which come with higher earning potential. Specializations like network security, data center networking, and collaboration technologies are in high demand and often offer more competitive salaries than general networking roles.
Opportunities for Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with higher hourly rates or project-based pay, allowing you to maximize your earnings.
Industry Recognition and Rewards
Several organizations and industries offer bonuses or recognition for employees who earn certifications such as CCNA. Government agencies, defense contractors, and technology companies may offer financial incentives or recognition for achieving and maintaining certifications.
In summary, CCNA certification not only enriches your knowledge and skills but also significantly enhances your financial prospects in the networking field. Whether you're just starting your career or looking to accelerate your earning potential, CCNA is a valuable investment that can lead to higher starting salaries, faster salary progression, job security, and access to a broader range of well-paying career opportunities. In the next sections, we'll explore how CCNA certification brings industry recognition and fosters skill development, making it a comprehensive asset for your networking career.
Industry Recognition: Why Employers Value CCNA Certified Professionals
In the competitive world of networking and information technology, industry recognition plays a crucial role in determining an individual's career trajectory. The Cisco Certified Network Associate (CCNA) certification is highly esteemed by employers for a multitude of reasons. In this section, we'll explore why CCNA-certified professionals are highly sought after in the job market.
Validation of Networking Skills
CCNA certification serves as tangible proof of your networking knowledge and skills. Employers value this validation because it minimizes the risk associated with hiring someone who may lack the essential competencies needed for the job. CCNA-certified professionals have demonstrated their ability to design, configure, troubleshoot, and manage network systems, making them a valuable asset to any organization.
Cisco's Global Reputation
Cisco, the organization behind CCNA certification, is a global leader in networking technology. Its products and solutions are widely used in businesses worldwide. Therefore, employers place immense trust in Cisco's certifications, including CCNA. Holding a CCNA certification not only demonstrates your knowledge but also aligns you with a globally recognized and respected brand in the networking industry.
Adaptability and Staying Current
CCNA certification requires candidates to stay updated with the latest networking technologies. Employers appreciate CCNA-certified professionals' adaptability and commitment to ongoing learning. In the rapidly evolving field of networking, the ability to stay current is highly valuable, as it ensures that organizations can keep pace with technological advancements.
Standardized Skillset
CCNA certification ensures a standardized skillset among professionals. This consistency is vital for organizations, as it allows them to establish a baseline of expectations for their networking staff. It simplifies the recruitment process and provides assurance that CCNA-certified professionals possess a certain level of proficiency.
Enhanced Troubleshooting Abilities
CCNA certification places a strong emphasis on troubleshooting network issues. This skill is invaluable in maintaining network uptime and resolving problems swiftly. Employers appreciate CCNA-certified professionals' ability to identify and address network challenges effectively, which can prevent costly downtime.
Reduced Training Costs
Hiring CCNA-certified professionals can save organizations money on training and onboarding. New hires who already possess the certification require less investment in additional training, which is particularly appealing to businesses with budget constraints.
CCNA-certified individuals are seen as standardized, efficient, and cost-effective contributors to their organizations. In the subsequent sections, we will explore how CCNA certification contributes to skill development, career advancement, and even international opportunities in the world of networking.
Skill Development: What You'll Learn During CCNA Training
Earning the Cisco Certified Network Associate (CCNA) certification is not just about acquiring a piece of paper for your resume; it's about developing a comprehensive set of skills that are highly valued in the networking industry. In this section, we'll explore the key skills you'll acquire during CCNA training.
Network Fundamentals
CCNA training starts with the fundamentals of networking, covering topics such as the OSI model, IP addressing, subnets, and basic network protocols. This foundational knowledge is essential for understanding more advanced networking concepts.
Network Security
CCNA training emphasizes network security, teaching you how to identify and mitigate security threats. You'll learn about access control, firewalls, and security best practices to protect network infrastructure.
Wireless Networking
Wireless technology is integral to modern networks. CCNA training covers wireless networking concepts, including how to configure and secure wireless access points and controllers.
Network Troubleshooting
One of the most valuable skills you'll develop is network troubleshooting. You'll learn how to identify and resolve common network issues efficiently, minimizing downtime and ensuring network reliability.
WAN Technologies
Wide Area Networks (WANs) are crucial for connecting remote offices and ensuring data transfer between locations. CCNA training covers WAN technologies like Frame Relay, PPP, and VPNs.
Network Design
CCNA explores network design principles, teaching you how to plan and design network architectures that meet specific business requirements.
IP Telephony
In CCNA Voice or Collaboration tracks, you'll gain skills related to Voice over IP (VoIP) technologies. This includes configuring and managing IP telephony systems.
Data Center Networking
For those pursuing the Data Center track, you'll develop expertise in data center networking, including technologies like virtualization and storage.
Automation and Programmability
CCNA has evolved to include topics related to automation and programmability, introducing you to network automation and scripting. These skills are increasingly valuable in modern network management.
Real-World Lab Experience
CCNA training often involves hands-on lab exercises where you'll configure and troubleshoot network devices. This practical experience is invaluable for applying your knowledge in real-world scenarios.
A Foundation for Advanced Certifications: How CCNA Paves the Way
Earning the Cisco Certified Network Associate (CCNA) certification isn't just an endpoint; it serves as a stepping stone for networking professionals to explore more advanced certifications. In this section, we'll discuss how CCNA provides a strong foundation and paves the way for pursuing higher-level certifications.
In-Depth Networking Knowledge
CCNA covers a broad range of networking concepts, ensuring that candidates have a solid understanding of the fundamentals. This knowledge is essential for tackling more advanced certifications. Without a strong foundation, pursuing higher-level certifications can be significantly more challenging.
Prerequisite for Advanced Certifications
Many advanced Cisco certifications require CCNA as a prerequisite. For example, to pursue the Cisco Certified Network Professional (CCNP) certification, you typically need to have a valid CCNA certification. CCNP certifications focus on more complex networking topics, such as advanced routing and switching, wireless, or security. CCNA ensures that candidates are prepared for the in-depth knowledge required at the professional level.
Seamless Progression
The content covered in CCNA provides a logical progression to advanced certifications. CCNA introduces key concepts in routing and switching, network security, and other fundamental areas. This foundational knowledge aligns well with the content covered in CCNP and other Cisco certifications.
Enhanced Career Opportunities
Having a CCNA certification on your resume can open doors to better job opportunities. Once you've earned your CCNA, you can apply for positions that require CCNA certification, gain more experience, and work towards your next certification. Advanced certifications can lead to even more lucrative roles and further career advancement.
Increased Technical Proficiency
CCNA offers hands-on experience with networking devices and technologies. This practical experience not only prepares you for the CCNA exam but also ensures that you are technically proficient. This proficiency will be valuable when pursuing more advanced certifications, where the expectations for hands-on skills are higher.
Recognition in the Networking Community
The CCNA certification is well-recognized in the networking community. Earning it demonstrates your commitment to the field and your readiness to take on more challenging certifications. Networking professionals who hold CCNA certifications are often well-regarded by peers and employers.
Preparation for Specializations
Cisco offers various specialization certifications, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These specializations allow you to focus on areas that interest you most. The foundational knowledge provided by CCNA is crucial for building expertise in these specialized fields.
Global Reach: The Portability of CCNA Certification
One of the distinct advantages of earning the Cisco Certified Network Associate (CCNA) certification is its global recognition and portability. CCNA is not confined to a specific geographical region or job market; it offers networking professionals the opportunity to work and thrive on a worldwide scale. In this section, we'll explore the portability of CCNA certification and how it opens doors to international opportunities.
Universal Networking Knowledge
CCNA covers fundamental networking concepts that apply universally, regardless of geographic location. Networking protocols, routing and switching principles, and security best practices are applicable worldwide. This means your CCNA knowledge is relevant wherever networking infrastructure exists.
Cisco's International Presence
Cisco, the organization behind CCNA certification, is a global technology leader with a presence in almost every corner of the world. This international footprint ensures that CCNA is recognized and respected globally, and Cisco's products and solutions are used in diverse international markets.
Industry Demand Worldwide
The demand for skilled networking professionals is not limited to a single region; it's a global need. Organizations around the world require network administrators, engineers, and technicians who can maintain and optimize their network infrastructure. Having a CCNA certification makes you an attractive candidate in any job market.
Career Mobility
CCNA certification provides networking professionals with the flexibility to move and work in different countries and regions. Many multinational companies value CCNA certification when hiring for their global IT teams. It can open doors to exciting international opportunities, allowing you to gain experience in various environments and cultures.
International Certifications
In addition to the standard CCNA certification, Cisco offers specialized CCNA tracks, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These tracks are valuable for professionals interested in specific fields and can enhance your international employability by focusing on in-demand areas.
Networking Community Connections
The CCNA community is vast and diverse, with professionals from all over the world. Engaging with this community can lead to international networking opportunities, collaboration, and exposure to different industry practices and trends.
Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with flexibility and opportunities to work on international projects, further expanding your horizons.
Its universal networking knowledge, recognition by Cisco, and high demand in the IT industry make CCNA professionals sought after worldwide. Whether you aspire to work in your home country, gain international experience, or explore career opportunities in various regions, CCNA certification equips you with the skills and recognition needed for success in the global networking arena.
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
In the ever-evolving world of networking, it's crucial for professionals to stay current with the latest technologies and industry trends. The Cisco Certified Network Associate (CCNA) certification is not just a one-time achievement; it plays a pivotal role in helping networking experts keep pace with the dynamic nature of their field. In this section, we'll discuss why CCNA is essential for professionals looking to stay current in networking.
Ongoing Skill Development
CCNA certification requires individuals to acquire a broad range of foundational skills. However, these skills are not stagnant; they form the building blocks for more advanced networking knowledge. CCNA serves as the first step in a lifelong journey of skill development, encouraging professionals to continue learning and staying up-to-date with the latest advancements.
Regular Certification Updates
Cisco periodically updates its certification exams to ensure they remain relevant in an ever-changing industry. CCNA-certified professionals are encouraged to recertify and take the latest versions of the exam to maintain the currency of their knowledge. This process reinforces the importance of staying current in networking.
Exposure to Emerging Technologies
CCNA training introduces candidates to emerging technologies and trends in networking, such as cloud computing, software-defined networking (SDN), and automation. This exposure not only prepares professionals for current challenges but also equips them to adapt to future developments in the field.
Foundation for Advanced Certifications
CCNA serves as a foundational certification for more advanced Cisco certifications, such as the Cisco Certified Network Professional (CCNP) and Cisco Certified Internetwork Expert (CCIE). These advanced certifications delve deeper into complex networking topics and require professionals to continually update their knowledge and skills.
Troubleshooting and Adaptability
One of the primary skills emphasized in CCNA training is network troubleshooting. This skill is invaluable in a dynamic field where new challenges and issues regularly arise. CCNA-certified professionals are adept at identifying and resolving network problems, which is critical for maintaining network reliability.
Security Awareness
Security is an evergreen concern in networking. CCNA training covers network security principles, but professionals must continuously stay informed about evolving security threats and solutions to protect network infrastructure effectively.
Industry Engagement
Cisco's extensive networking community and resources provide opportunities to engage with professionals and experts from around the world. Networking conferences, webinars, and forums keep CCNA-certified professionals connected to the latest industry insights and best practices.
Job Relevance
Staying current in networking ensures that your skills remain relevant to the job market. As new technologies and practices emerge, employers seek professionals who can apply these innovations to improve network performance, security, and efficiency.
the dynamic nature of networking demands continuous learning and adaptation. CCNA certification serves as a reminder that networking professionals must remain vigilant, embrace ongoing skill development, and engage with emerging technologies to stay current in their field. Whether through recertification, advanced certifications, or active participation in the networking community, CCNA paves the way for a career that thrives in a constantly evolving networking landscape.
Job Security: How CCNA Certification Mitigates Career Risks
In an ever-changing job market, job security is a critical concern for professionals in any field. Cisco Certified Network Associate (CCNA) certification can significantly mitigate career risks and provide a level of job security that is highly valuable. In this section, we'll discuss how CCNA certification contributes to job security in the networking industry.
Industry Demand for Networking Professionals
The demand for skilled networking professionals is a constant in the IT industry. Networks are the backbone of businesses, and their proper functioning is essential. As a result, organizations consistently seek professionals with networking expertise, creating a continuous demand for CCNA-certified individuals.
Demonstrated Skills and Knowledge
CCNA certification is a clear demonstration of your networking skills and knowledge. Employers prefer candidates with certifications because they provide tangible evidence of competency. CCNA-certified professionals are more likely to be retained, promoted, and entrusted with critical network responsibilities.
Ongoing Skill Development
CCNA requires professionals to continue developing their skills to stay current. This continuous learning process ensures that CCNA-certified individuals remain valuable assets to their employers, adapting to new technologies and maintaining network efficiency and security.
Troubleshooting Abilities
CCNA training emphasizes troubleshooting skills, equipping professionals with the ability to identify and resolve network issues quickly. This skill is invaluable in ensuring network reliability and reducing costly downtime.
Network Security Expertise
Security is a top priority for organizations, and CCNA certification includes essential network security knowledge. CCNA-certified professionals can help protect network infrastructure from security threats, which is a crucial aspect of job security.
Recognition by Employers
Many employers specifically seek CCNA-certified professionals for networking roles. Having the certification on your resume often increases your chances of being selected for interviews and job offers.
Career Advancement Opportunities
CCNA certification is a solid foundation for career advancement. It opens doors to roles with more responsibility, better compensation, and job stability. CCNA-certified professionals are often well-positioned to move up the career ladder.
Adaptability to Industry Changes
CCNA certification equips professionals with the adaptability needed to embrace industry changes. The networking field continually evolves with new technologies and practices. CCNA-certified individuals can easily adapt to these changes, mitigating the risk of becoming obsolete in their roles.
Strong Networking Community
The CCNA community is extensive and supportive. Engaging with this community can lead to networking opportunities, job referrals, and career advice, further enhancing job security.
Portfolio for Job Flexibility
A CCNA certification is transferable across different industries and geographic locations. This flexibility provides job security as it enables professionals to explore various career options and adapt to changes in personal circumstances or job markets.
Networking Community and Support: CCNA's Role in Building Connections
The world of networking is not just about cables and configurations; it's also about building connections with fellow professionals and experts. The Cisco Certified Network Associate (CCNA) certification extends beyond the technical aspects of networking; it fosters a sense of community and support that can significantly benefit networking professionals. In this section, we'll discuss how CCNA plays a role in building connections within the networking community.
CCNA Community Forums
Cisco provides official forums and online communities specifically for CCNA-certified professionals. These platforms are a space for individuals to ask questions, share insights, and seek advice from peers who have a similar background and expertise. They can be valuable sources of information and support.
Networking Events and Conferences
CCNA-certified professionals often participate in networking events and conferences. These gatherings provide opportunities to connect with fellow professionals, engage in discussions, and learn from experts in the field. Building relationships at such events can lead to new job opportunities and collaboration.
Online Study Groups
Many CCNA candidates form online study groups to prepare for the certification. These groups not only aid in exam preparation but also serve as a networking platform. Interacting with study partners can lead to long-lasting professional relationships.
Job Referrals and Recommendations
Being part of the CCNA community can lead to job referrals and recommendations. Networking professionals often hear about job openings or have colleagues in need of talent. Being connected to this network can make it easier to find new job opportunities.
Support in Exam Preparation
Preparing for the CCNA exam can be a challenging endeavor. Many CCNA candidates find support and motivation from the community. Connecting with others who are pursuing the same certification can provide encouragement and help you overcome obstacles.
Real-World Application: Success Stories of CCNA Professionals
The Cisco Certified Network Associate (CCNA) certification is more than just an academic achievement; it's a testament to practical networking skills and knowledge. In this section, we'll explore real-world success stories of CCNA professionals who have leveraged their certification to achieve remarkable career milestones and make a tangible impact in the field of networking.
Expertise in Network Troubleshooting
CCNA-certified professionals often excel in network troubleshooting, a skill they gain during their certification training. This expertise enables them to quickly identify and resolve network issues, reducing downtime and ensuring network reliability. As a result, their employers appreciate their ability to maintain network efficiency.
Network Security Specialists
CCNA Security specialization equips professionals with the knowledge and skills to handle network security. These CCNA-certified individuals often go on to become network security specialists, safeguarding their organizations' critical data from cyber threats.
Networking Entrepreneurship
Some CCNA professionals have leveraged their certification to start their own networking businesses. They provide services such as network design, installation, and maintenance to clients in need of networking solutions. The CCNA certification provides credibility and trust to their customers.
Specialized Career Paths
CCNA opens doors to specialized career paths, such as data center networking, collaboration technologies, and wireless networking. Professionals who pursue these specialized tracks often find themselves in high-demand roles that offer both financial rewards and job satisfaction.
Promotions in Multinational Companies
CCNA certification provides a strong foundation for working in multinational corporations. Success stories often include professionals who secure positions in global organizations, where they manage international networks and collaborate with teams across different countries.
Success in IT Management
Some CCNA professionals ascend to IT management positions, overseeing entire network infrastructures and leading teams of networking professionals. Their strong technical backgrounds, combined with leadership skills, make them valuable assets in management roles.
Building Resilient Networks
CCNA professionals are well-versed in building resilient and efficient network infrastructures. Success stories often involve individuals who design and manage networks for critical industries, such as healthcare or finance, where network reliability is paramount.
International Opportunities
CCNA certification's global recognition allows professionals to explore international career opportunities. Success stories may include individuals who land positions in different countries, gaining unique cultural experiences and expanding their professional horizons.
Conclusion
The Cisco Certified Network Associate (CCNA) certification is a transformative credential for networking professionals, offering a multitude of benefits and opportunities for those who pursue it. This article has explored the various facets of CCNA, from its role in enhancing career opportunities and increasing earning potential to its importance in maintaining job security and staying current in the ever-evolving field of networking.
Real-world success stories of CCNA professionals underscore the tangible impact that this certification has on careers, from career advancements to specialized roles, entrepreneurship, and international opportunities.
In sum, CCNA is a testament to the dedication and skills of networking professionals and serves as a versatile tool in their professional journey. It not only represents a strong foundation but also opens doors, enriches careers, and provides a network of support that transcends borders. As the networking industry continues to evolve, CCNA remains a constant in empowering professionals to navigate the ever-changing landscape with confidence and success.
Read More
In the fast-paced world of information technology, staying ahead in the networking industry is an ever-evolving challenge. Networking professionals must continually adapt to emerging technologies, understand complex systems, and demonstrate their skills to prospective employers. Among the various certifications available, the Cisco Certified Network Associate (CCNA) certification stands out as a prestigious and highly regarded credential that opens doors to numerous opportunities in the field.
This article explores the significant benefits of earning a CCNA certification for your networking career. Whether you are a seasoned IT professional looking to advance your skills or someone considering a career in networking, understanding the advantages of CCNA can help you make informed decisions about your professional development. From enhanced career prospects and higher earning potential to industry recognition and skill development, the CCNA certification offers a multitude of rewards that can positively impact your networking journey. In the pages that follow, we will delve into these benefits and illustrate how CCNA can be a pivotal asset in achieving your career aspirations.
Table of contents
-
Enhanced Career Opportunities: How CCNA Opens Doors
-
Higher Earning Potential: The Financial Benefits of CCNA Certification
-
Industry Recognition: Why Employers Value CCNA Certified Professionals
-
Skill Development: What You'll Learn During CCNA Training
-
A Foundation for Advanced Certifications: How CCNA Paves the Way
-
Global Reach: The Portability of CCNA Certification
-
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
-
Job Security: How CCNA Certification Mitigates Career Risks
-
Networking Community and Support: CCNA's Role in Building Connections
-
Real-World Application: Success Stories of CCNA Professionals
-
Conclusion
Enhanced Career Opportunities: How CCNA Opens Doors
In the ever-evolving realm of networking, professionals are constantly seeking ways to enhance their careers and remain competitive. The Cisco Certified Network Associate (CCNA) certification has emerged as a game-changer in this regard, offering a clear pathway to enhanced career opportunities and professional growth.
Versatility in Networking Roles
CCNA certification is designed to equip professionals with a broad spectrum of networking skills. Whether you are interested in network administration, security, or wireless networking, CCNA provides a foundational understanding of these domains. This versatility makes CCNA holders attractive candidates for a wide range of networking roles, from network engineers to security specialists.
Immediate Recognition
When your resume bears the CCNA logo, it serves as an instant indicator of your networking proficiency to potential employers. Many organizations value CCNA certification as a prerequisite for hiring, as it validates your knowledge and commitment to the field. This immediate recognition can significantly reduce the time it takes to land your dream job.
Entry into Cisco's Ecosystem
Cisco is a global leader in networking technologies, and CCNA is your entry ticket to their ecosystem. Gaining a CCNA certification allows you to interact with Cisco's products and solutions more effectively. This deepens your understanding of their offerings, making you a more valuable asset to any organization that relies on Cisco networking equipment.
Better Networking Skills and Problem-Solving Abilities
The CCNA curriculum focuses on both theoretical knowledge and hands-on skills. As a CCNA candidate, you'll learn how to configure, troubleshoot, and manage network devices effectively. This not only enhances your networking expertise but also hones your problem-solving abilities, which are highly valued in IT roles.
Career Advancement
For networking professionals looking to climb the career ladder, CCNA certification is an invaluable stepping stone. Many companies prioritize employees with CCNA credentials when considering candidates for leadership and managerial positions. The knowledge and skills acquired through CCNA training can help you stand out and qualify for promotions.
Global Opportunities
Networking is a universal language in the IT world, and CCNA certification is recognized internationally. Whether you aspire to work in your home country or abroad, CCNA opens doors to a wealth of global career opportunities. It's a passport to working in diverse and exciting environments.
Higher Earning Potential: The Financial Benefits of CCNA Certification
In today's competitive job market, financial rewards play a significant role in career decisions. For networking professionals, the Cisco Certified Network Associate (CCNA) certification not only opens doors to exciting opportunities but also brings tangible financial benefits. In this section, we'll delve into how CCNA can lead to a substantial increase in earning potential.
Competitive Edge in Salary Negotiations
CCNA certification immediately sets you apart from non-certified peers. Employers often recognize the commitment, knowledge, and skills required to earn the CCNA credential. As a result, CCNA-certified professionals are in a better position to negotiate higher starting salaries, more significant pay raises, and more lucrative job offers.
Increased Starting Salaries
For entry-level positions, CCNA certification can significantly boost your starting salary. Employers are willing to pay more for professionals who have proven their expertise and commitment to the networking field through certification. This premium can help you secure a higher income from the outset of your career.
Expanded Career Options
CCNA certification opens the door to a wider range of career options, many of which come with higher earning potential. Specializations like network security, data center networking, and collaboration technologies are in high demand and often offer more competitive salaries than general networking roles.
Opportunities for Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with higher hourly rates or project-based pay, allowing you to maximize your earnings.
Industry Recognition and Rewards
Several organizations and industries offer bonuses or recognition for employees who earn certifications such as CCNA. Government agencies, defense contractors, and technology companies may offer financial incentives or recognition for achieving and maintaining certifications.
In summary, CCNA certification not only enriches your knowledge and skills but also significantly enhances your financial prospects in the networking field. Whether you're just starting your career or looking to accelerate your earning potential, CCNA is a valuable investment that can lead to higher starting salaries, faster salary progression, job security, and access to a broader range of well-paying career opportunities. In the next sections, we'll explore how CCNA certification brings industry recognition and fosters skill development, making it a comprehensive asset for your networking career.
Industry Recognition: Why Employers Value CCNA Certified Professionals
In the competitive world of networking and information technology, industry recognition plays a crucial role in determining an individual's career trajectory. The Cisco Certified Network Associate (CCNA) certification is highly esteemed by employers for a multitude of reasons. In this section, we'll explore why CCNA-certified professionals are highly sought after in the job market.
Validation of Networking Skills
CCNA certification serves as tangible proof of your networking knowledge and skills. Employers value this validation because it minimizes the risk associated with hiring someone who may lack the essential competencies needed for the job. CCNA-certified professionals have demonstrated their ability to design, configure, troubleshoot, and manage network systems, making them a valuable asset to any organization.
Cisco's Global Reputation
Cisco, the organization behind CCNA certification, is a global leader in networking technology. Its products and solutions are widely used in businesses worldwide. Therefore, employers place immense trust in Cisco's certifications, including CCNA. Holding a CCNA certification not only demonstrates your knowledge but also aligns you with a globally recognized and respected brand in the networking industry.
Adaptability and Staying Current
CCNA certification requires candidates to stay updated with the latest networking technologies. Employers appreciate CCNA-certified professionals' adaptability and commitment to ongoing learning. In the rapidly evolving field of networking, the ability to stay current is highly valuable, as it ensures that organizations can keep pace with technological advancements.
Standardized Skillset
CCNA certification ensures a standardized skillset among professionals. This consistency is vital for organizations, as it allows them to establish a baseline of expectations for their networking staff. It simplifies the recruitment process and provides assurance that CCNA-certified professionals possess a certain level of proficiency.
Enhanced Troubleshooting Abilities
CCNA certification places a strong emphasis on troubleshooting network issues. This skill is invaluable in maintaining network uptime and resolving problems swiftly. Employers appreciate CCNA-certified professionals' ability to identify and address network challenges effectively, which can prevent costly downtime.
Reduced Training Costs
Hiring CCNA-certified professionals can save organizations money on training and onboarding. New hires who already possess the certification require less investment in additional training, which is particularly appealing to businesses with budget constraints.
CCNA-certified individuals are seen as standardized, efficient, and cost-effective contributors to their organizations. In the subsequent sections, we will explore how CCNA certification contributes to skill development, career advancement, and even international opportunities in the world of networking.
Skill Development: What You'll Learn During CCNA Training
Earning the Cisco Certified Network Associate (CCNA) certification is not just about acquiring a piece of paper for your resume; it's about developing a comprehensive set of skills that are highly valued in the networking industry. In this section, we'll explore the key skills you'll acquire during CCNA training.
Network Fundamentals
CCNA training starts with the fundamentals of networking, covering topics such as the OSI model, IP addressing, subnets, and basic network protocols. This foundational knowledge is essential for understanding more advanced networking concepts.
Network Security
CCNA training emphasizes network security, teaching you how to identify and mitigate security threats. You'll learn about access control, firewalls, and security best practices to protect network infrastructure.
Wireless Networking
Wireless technology is integral to modern networks. CCNA training covers wireless networking concepts, including how to configure and secure wireless access points and controllers.
Network Troubleshooting
One of the most valuable skills you'll develop is network troubleshooting. You'll learn how to identify and resolve common network issues efficiently, minimizing downtime and ensuring network reliability.
WAN Technologies
Wide Area Networks (WANs) are crucial for connecting remote offices and ensuring data transfer between locations. CCNA training covers WAN technologies like Frame Relay, PPP, and VPNs.
Network Design
CCNA explores network design principles, teaching you how to plan and design network architectures that meet specific business requirements.
IP Telephony
In CCNA Voice or Collaboration tracks, you'll gain skills related to Voice over IP (VoIP) technologies. This includes configuring and managing IP telephony systems.
Data Center Networking
For those pursuing the Data Center track, you'll develop expertise in data center networking, including technologies like virtualization and storage.
Automation and Programmability
CCNA has evolved to include topics related to automation and programmability, introducing you to network automation and scripting. These skills are increasingly valuable in modern network management.
Real-World Lab Experience
CCNA training often involves hands-on lab exercises where you'll configure and troubleshoot network devices. This practical experience is invaluable for applying your knowledge in real-world scenarios.
A Foundation for Advanced Certifications: How CCNA Paves the Way
Earning the Cisco Certified Network Associate (CCNA) certification isn't just an endpoint; it serves as a stepping stone for networking professionals to explore more advanced certifications. In this section, we'll discuss how CCNA provides a strong foundation and paves the way for pursuing higher-level certifications.
In-Depth Networking Knowledge
CCNA covers a broad range of networking concepts, ensuring that candidates have a solid understanding of the fundamentals. This knowledge is essential for tackling more advanced certifications. Without a strong foundation, pursuing higher-level certifications can be significantly more challenging.
Prerequisite for Advanced Certifications
Many advanced Cisco certifications require CCNA as a prerequisite. For example, to pursue the Cisco Certified Network Professional (CCNP) certification, you typically need to have a valid CCNA certification. CCNP certifications focus on more complex networking topics, such as advanced routing and switching, wireless, or security. CCNA ensures that candidates are prepared for the in-depth knowledge required at the professional level.
Seamless Progression
The content covered in CCNA provides a logical progression to advanced certifications. CCNA introduces key concepts in routing and switching, network security, and other fundamental areas. This foundational knowledge aligns well with the content covered in CCNP and other Cisco certifications.
Enhanced Career Opportunities
Having a CCNA certification on your resume can open doors to better job opportunities. Once you've earned your CCNA, you can apply for positions that require CCNA certification, gain more experience, and work towards your next certification. Advanced certifications can lead to even more lucrative roles and further career advancement.
Increased Technical Proficiency
CCNA offers hands-on experience with networking devices and technologies. This practical experience not only prepares you for the CCNA exam but also ensures that you are technically proficient. This proficiency will be valuable when pursuing more advanced certifications, where the expectations for hands-on skills are higher.
Recognition in the Networking Community
The CCNA certification is well-recognized in the networking community. Earning it demonstrates your commitment to the field and your readiness to take on more challenging certifications. Networking professionals who hold CCNA certifications are often well-regarded by peers and employers.
Preparation for Specializations
Cisco offers various specialization certifications, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These specializations allow you to focus on areas that interest you most. The foundational knowledge provided by CCNA is crucial for building expertise in these specialized fields.
Global Reach: The Portability of CCNA Certification
One of the distinct advantages of earning the Cisco Certified Network Associate (CCNA) certification is its global recognition and portability. CCNA is not confined to a specific geographical region or job market; it offers networking professionals the opportunity to work and thrive on a worldwide scale. In this section, we'll explore the portability of CCNA certification and how it opens doors to international opportunities.
Universal Networking Knowledge
CCNA covers fundamental networking concepts that apply universally, regardless of geographic location. Networking protocols, routing and switching principles, and security best practices are applicable worldwide. This means your CCNA knowledge is relevant wherever networking infrastructure exists.
Cisco's International Presence
Cisco, the organization behind CCNA certification, is a global technology leader with a presence in almost every corner of the world. This international footprint ensures that CCNA is recognized and respected globally, and Cisco's products and solutions are used in diverse international markets.
Industry Demand Worldwide
The demand for skilled networking professionals is not limited to a single region; it's a global need. Organizations around the world require network administrators, engineers, and technicians who can maintain and optimize their network infrastructure. Having a CCNA certification makes you an attractive candidate in any job market.
Career Mobility
CCNA certification provides networking professionals with the flexibility to move and work in different countries and regions. Many multinational companies value CCNA certification when hiring for their global IT teams. It can open doors to exciting international opportunities, allowing you to gain experience in various environments and cultures.
International Certifications
In addition to the standard CCNA certification, Cisco offers specialized CCNA tracks, such as CCNA Security, CCNA Collaboration, and CCNA Data Center. These tracks are valuable for professionals interested in specific fields and can enhance your international employability by focusing on in-demand areas.
Networking Community Connections
The CCNA community is vast and diverse, with professionals from all over the world. Engaging with this community can lead to international networking opportunities, collaboration, and exposure to different industry practices and trends.
Consulting and Contract Work
CCNA-certified professionals may have the option to work as network consultants or on a contract basis. These roles often come with flexibility and opportunities to work on international projects, further expanding your horizons.
Its universal networking knowledge, recognition by Cisco, and high demand in the IT industry make CCNA professionals sought after worldwide. Whether you aspire to work in your home country, gain international experience, or explore career opportunities in various regions, CCNA certification equips you with the skills and recognition needed for success in the global networking arena.
Staying Current in Networking: The Importance of CCNA in a Dynamic Field
In the ever-evolving world of networking, it's crucial for professionals to stay current with the latest technologies and industry trends. The Cisco Certified Network Associate (CCNA) certification is not just a one-time achievement; it plays a pivotal role in helping networking experts keep pace with the dynamic nature of their field. In this section, we'll discuss why CCNA is essential for professionals looking to stay current in networking.
Ongoing Skill Development
CCNA certification requires individuals to acquire a broad range of foundational skills. However, these skills are not stagnant; they form the building blocks for more advanced networking knowledge. CCNA serves as the first step in a lifelong journey of skill development, encouraging professionals to continue learning and staying up-to-date with the latest advancements.
Regular Certification Updates
Cisco periodically updates its certification exams to ensure they remain relevant in an ever-changing industry. CCNA-certified professionals are encouraged to recertify and take the latest versions of the exam to maintain the currency of their knowledge. This process reinforces the importance of staying current in networking.
Exposure to Emerging Technologies
CCNA training introduces candidates to emerging technologies and trends in networking, such as cloud computing, software-defined networking (SDN), and automation. This exposure not only prepares professionals for current challenges but also equips them to adapt to future developments in the field.
Foundation for Advanced Certifications
CCNA serves as a foundational certification for more advanced Cisco certifications, such as the Cisco Certified Network Professional (CCNP) and Cisco Certified Internetwork Expert (CCIE). These advanced certifications delve deeper into complex networking topics and require professionals to continually update their knowledge and skills.
Troubleshooting and Adaptability
One of the primary skills emphasized in CCNA training is network troubleshooting. This skill is invaluable in a dynamic field where new challenges and issues regularly arise. CCNA-certified professionals are adept at identifying and resolving network problems, which is critical for maintaining network reliability.
Security Awareness
Security is an evergreen concern in networking. CCNA training covers network security principles, but professionals must continuously stay informed about evolving security threats and solutions to protect network infrastructure effectively.
Industry Engagement
Cisco's extensive networking community and resources provide opportunities to engage with professionals and experts from around the world. Networking conferences, webinars, and forums keep CCNA-certified professionals connected to the latest industry insights and best practices.
Job Relevance
Staying current in networking ensures that your skills remain relevant to the job market. As new technologies and practices emerge, employers seek professionals who can apply these innovations to improve network performance, security, and efficiency.
the dynamic nature of networking demands continuous learning and adaptation. CCNA certification serves as a reminder that networking professionals must remain vigilant, embrace ongoing skill development, and engage with emerging technologies to stay current in their field. Whether through recertification, advanced certifications, or active participation in the networking community, CCNA paves the way for a career that thrives in a constantly evolving networking landscape.
Job Security: How CCNA Certification Mitigates Career Risks
In an ever-changing job market, job security is a critical concern for professionals in any field. Cisco Certified Network Associate (CCNA) certification can significantly mitigate career risks and provide a level of job security that is highly valuable. In this section, we'll discuss how CCNA certification contributes to job security in the networking industry.
Industry Demand for Networking Professionals
The demand for skilled networking professionals is a constant in the IT industry. Networks are the backbone of businesses, and their proper functioning is essential. As a result, organizations consistently seek professionals with networking expertise, creating a continuous demand for CCNA-certified individuals.
Demonstrated Skills and Knowledge
CCNA certification is a clear demonstration of your networking skills and knowledge. Employers prefer candidates with certifications because they provide tangible evidence of competency. CCNA-certified professionals are more likely to be retained, promoted, and entrusted with critical network responsibilities.
Ongoing Skill Development
CCNA requires professionals to continue developing their skills to stay current. This continuous learning process ensures that CCNA-certified individuals remain valuable assets to their employers, adapting to new technologies and maintaining network efficiency and security.
Troubleshooting Abilities
CCNA training emphasizes troubleshooting skills, equipping professionals with the ability to identify and resolve network issues quickly. This skill is invaluable in ensuring network reliability and reducing costly downtime.
Network Security Expertise
Security is a top priority for organizations, and CCNA certification includes essential network security knowledge. CCNA-certified professionals can help protect network infrastructure from security threats, which is a crucial aspect of job security.
Recognition by Employers
Many employers specifically seek CCNA-certified professionals for networking roles. Having the certification on your resume often increases your chances of being selected for interviews and job offers.
Career Advancement Opportunities
CCNA certification is a solid foundation for career advancement. It opens doors to roles with more responsibility, better compensation, and job stability. CCNA-certified professionals are often well-positioned to move up the career ladder.
Adaptability to Industry Changes
CCNA certification equips professionals with the adaptability needed to embrace industry changes. The networking field continually evolves with new technologies and practices. CCNA-certified individuals can easily adapt to these changes, mitigating the risk of becoming obsolete in their roles.
Strong Networking Community
The CCNA community is extensive and supportive. Engaging with this community can lead to networking opportunities, job referrals, and career advice, further enhancing job security.
Portfolio for Job Flexibility
A CCNA certification is transferable across different industries and geographic locations. This flexibility provides job security as it enables professionals to explore various career options and adapt to changes in personal circumstances or job markets.
Networking Community and Support: CCNA's Role in Building Connections
The world of networking is not just about cables and configurations; it's also about building connections with fellow professionals and experts. The Cisco Certified Network Associate (CCNA) certification extends beyond the technical aspects of networking; it fosters a sense of community and support that can significantly benefit networking professionals. In this section, we'll discuss how CCNA plays a role in building connections within the networking community.
CCNA Community Forums
Cisco provides official forums and online communities specifically for CCNA-certified professionals. These platforms are a space for individuals to ask questions, share insights, and seek advice from peers who have a similar background and expertise. They can be valuable sources of information and support.
Networking Events and Conferences
CCNA-certified professionals often participate in networking events and conferences. These gatherings provide opportunities to connect with fellow professionals, engage in discussions, and learn from experts in the field. Building relationships at such events can lead to new job opportunities and collaboration.
Online Study Groups
Many CCNA candidates form online study groups to prepare for the certification. These groups not only aid in exam preparation but also serve as a networking platform. Interacting with study partners can lead to long-lasting professional relationships.
Job Referrals and Recommendations
Being part of the CCNA community can lead to job referrals and recommendations. Networking professionals often hear about job openings or have colleagues in need of talent. Being connected to this network can make it easier to find new job opportunities.
Support in Exam Preparation
Preparing for the CCNA exam can be a challenging endeavor. Many CCNA candidates find support and motivation from the community. Connecting with others who are pursuing the same certification can provide encouragement and help you overcome obstacles.
Real-World Application: Success Stories of CCNA Professionals
The Cisco Certified Network Associate (CCNA) certification is more than just an academic achievement; it's a testament to practical networking skills and knowledge. In this section, we'll explore real-world success stories of CCNA professionals who have leveraged their certification to achieve remarkable career milestones and make a tangible impact in the field of networking.
Expertise in Network Troubleshooting
CCNA-certified professionals often excel in network troubleshooting, a skill they gain during their certification training. This expertise enables them to quickly identify and resolve network issues, reducing downtime and ensuring network reliability. As a result, their employers appreciate their ability to maintain network efficiency.
Network Security Specialists
CCNA Security specialization equips professionals with the knowledge and skills to handle network security. These CCNA-certified individuals often go on to become network security specialists, safeguarding their organizations' critical data from cyber threats.
Networking Entrepreneurship
Some CCNA professionals have leveraged their certification to start their own networking businesses. They provide services such as network design, installation, and maintenance to clients in need of networking solutions. The CCNA certification provides credibility and trust to their customers.
Specialized Career Paths
CCNA opens doors to specialized career paths, such as data center networking, collaboration technologies, and wireless networking. Professionals who pursue these specialized tracks often find themselves in high-demand roles that offer both financial rewards and job satisfaction.
Promotions in Multinational Companies
CCNA certification provides a strong foundation for working in multinational corporations. Success stories often include professionals who secure positions in global organizations, where they manage international networks and collaborate with teams across different countries.
Success in IT Management
Some CCNA professionals ascend to IT management positions, overseeing entire network infrastructures and leading teams of networking professionals. Their strong technical backgrounds, combined with leadership skills, make them valuable assets in management roles.
Building Resilient Networks
CCNA professionals are well-versed in building resilient and efficient network infrastructures. Success stories often involve individuals who design and manage networks for critical industries, such as healthcare or finance, where network reliability is paramount.
International Opportunities
CCNA certification's global recognition allows professionals to explore international career opportunities. Success stories may include individuals who land positions in different countries, gaining unique cultural experiences and expanding their professional horizons.
Conclusion
The Cisco Certified Network Associate (CCNA) certification is a transformative credential for networking professionals, offering a multitude of benefits and opportunities for those who pursue it. This article has explored the various facets of CCNA, from its role in enhancing career opportunities and increasing earning potential to its importance in maintaining job security and staying current in the ever-evolving field of networking.
Real-world success stories of CCNA professionals underscore the tangible impact that this certification has on careers, from career advancements to specialized roles, entrepreneurship, and international opportunities.
In sum, CCNA is a testament to the dedication and skills of networking professionals and serves as a versatile tool in their professional journey. It not only represents a strong foundation but also opens doors, enriches careers, and provides a network of support that transcends borders. As the networking industry continues to evolve, CCNA remains a constant in empowering professionals to navigate the ever-changing landscape with confidence and success.
Project management principles
Project management is a critical discipline that plays a central role in the successful execution of endeavors, whether they are in the business, engineering, information technology, or numerous other fields. At its core, project management involves the application of a set of principles, practices, and techniques to initiate, plan, execute, control, and close a project efficiently and effectively. It serves as the guiding framework for organizations and individuals seeking to achieve their objectives, deliver products or services, and drive innovation while adhering to timelines and budgets.
This introduction serves as the foundation for exploring the key subtopics in project management principles, which encompass various stages of a project's life cycle, including initiation, planning, execution, monitoring, controlling, and closure. In an era where efficiency, precision, and adaptability are vital to achieving success, understanding and mastering project management principles are essential for individuals and organizations alike. This knowledge equips project managers with the tools and strategies needed to navigate the complexities of modern projects and deliver value to their stakeholders.
Table of contents
-
Project Initiation
-
Project Planning
-
Risk Management
-
Project Communication
-
Project Execution
-
Quality Management
-
Cost Management
-
Time Management
-
Scope Management
-
Project Closure
-
Conclusion
Project Initiation
Project initiation is the first and arguably one of the most crucial phases in the project management process. It's during this phase that the project is defined, its feasibility is assessed, and the initial groundwork is laid for the successful execution of the project. Project initiation sets the stage for the entire project, and the decisions made at this stage have a significant impact on its outcome. Here are some key aspects of project initiation:
Defining Objectives: The project initiation phase begins with a clear understanding of what the project aims to achieve. Project managers work closely with stakeholders to define specific and measurable objectives. These objectives should be aligned with the organization's overall goals.
Project Charter: A project charter is a formal document that authorizes the project to exist. It typically includes the project's purpose, objectives, scope, and high-level requirements. The charter is often signed off by a senior executive or project sponsor.
Stakeholder Identification: Identifying and engaging stakeholders is a crucial part of project initiation. Stakeholders include anyone who has an interest in or can be affected by the project. Understanding their needs, expectations, and influence is essential.
Feasibility Analysis: Project managers conduct a feasibility study to assess whether the project is viable and worthwhile. This includes examining technical, economic, legal, operational, and scheduling feasibility.
Project Scope: Clearly defining the project's scope is vital to prevent scope creep (uncontrolled expansion of project scope). The scope outlines what will and won't be part of the project, helping to manage expectations and prevent unnecessary changes.
Resource Identification: Identifying the resources needed for the project, including human resources, equipment, and materials, is a key part of initiation. This helps in resource allocation and budgeting.
Project Documentation: Key project initiation documents, including the project charter and initial project plan, are created and stored for reference throughout the project.
The project initiation phase ensures that all stakeholders have a common understanding of the project's purpose and objectives and that the project is set up for success from the start. A well-executed initiation phase minimizes the risk of misunderstandings and scope changes as the project progresses, ultimately leading to a smoother project execution.
Project Planning
Project planning is a critical phase in the project management process, following project initiation. During this phase, detailed plans are developed to guide the project from start to finish. Effective project planning is essential for setting clear objectives, allocating resources efficiently, and ensuring that the project stays on track. Here are key aspects of project planning:
Work Packages: Work packages are the smallest units within the WBS and define specific tasks or activities that need to be completed. Each work package is assigned to a team member or group.
Scheduling: Project schedules are created to determine the sequence and duration of activities. Techniques like Gantt charts and network diagrams are often used for visualizing the project timeline. Scheduling helps in setting deadlines and milestones.
Resource Allocation: Resources, including human resources, equipment, and materials, are allocated to different tasks. This ensures that the right resources are available at the right time, reducing bottlenecks and delays.
Budgeting: The project budget is established during this phase. It includes estimates for all costs associated with the project, such as labor, materials, and overhead. The budget is an essential part of project control and monitoring.
Risk Management: A comprehensive risk management plan is developed. It identifies potential risks and outlines strategies to mitigate, monitor, and respond to them. Risk assessment and analysis are important parts of this process.
Quality Planning: Quality standards and criteria are determined. This includes defining what constitutes quality in the context of the project and how it will be ensured throughout the project's life cycle.
Change Management: Procedures for handling changes to the project scope, schedule, or budget are established. Change management helps in evaluating and implementing change requests in a controlled manner.
Stakeholder Engagement: The plan for engaging with stakeholders is refined. This includes how and when stakeholders will be involved in the project, their roles, and how their concerns and feedback will be addressed.
Contingency Planning: Contingency plans are created to address potential disruptions or setbacks. These plans outline how the project team will respond if unexpected issues arise.
Documentation: Detailed project documentation, including the project plan, schedules, and all relevant planning documents, is created and maintained throughout the project.
Effective project planning sets the foundation for project execution, ensuring that everyone involved knows what is expected of them, when it needs to be done, and how it should be done. It provides a roadmap for the entire project team and helps in tracking progress, managing resources, and achieving project objectives.
Risk Management
Risk management is a fundamental component of project management, dedicated to identifying, assessing, mitigating, and monitoring potential risks and uncertainties that could impact a project's success. Effectively managing risks helps project managers and teams anticipate, prepare for, and respond to challenges, ultimately minimizing the likelihood and impact of negative events. Here are the key aspects of risk management in project management:
Risk Identification: The process begins with the identification of risks that could affect the project. These risks can be internal or external, known or unknown, and can relate to various aspects, including scope, schedule, cost, quality, and more. Various techniques like brainstorming, checklists, and historical data analysis are used to identify risks.
Risk Assessment: Once identified, risks are assessed for their potential impact and likelihood. This often involves assigning a risk rating or score to prioritize risks. Qualitative and quantitative analysis methods can be used to assess risks.
Risk Register: All identified risks, along with their assessment details, are documented in a risk register. This register serves as a central repository of information about project risks.
Risk Response Planning: For each identified risk, a response plan is created. There are four primary strategies: avoid, transfer, mitigate, and accept. Response plans specify what actions will be taken if a risk occurs.
Risk Monitoring and Control: Risk management is an ongoing process. Throughout the project's life cycle, risks are monitored to track changes in their status. If a risk's likelihood or impact changes, the response plan may need to be adjusted.
Risk Reporting: Regular reporting to stakeholders and project sponsors is essential. This includes providing updates on the status of identified risks, their impact on the project, and the effectiveness of risk response strategies.
Risk Register Updates: The risk register is continuously updated to reflect changes in risks throughout the project.
Effective risk management is a proactive and dynamic process that helps project managers and teams respond to challenges and uncertainties, making the project more resilient and increasing the likelihood of successful project completion within scope, schedule, and budget constraints.
Project Communication
Effective project communication is a critical component of project management, ensuring that information is shared, stakeholders are engaged, and the project progresses smoothly. Good communication helps in managing expectations, resolving issues, and ultimately achieving project objectives. Here are the key aspects of project communication in project management:
Stakeholder Identification: Identify all project stakeholders, including team members, sponsors, clients, and external parties. Understanding their interests, needs, and expectations is vital for effective communication.
Communication Planning: Develop a communication plan that outlines how, when, and what information will be communicated to various stakeholders. The plan should define communication channels, frequency, and the responsible parties.
Status Reporting: Regularly provide project status updates to stakeholders. This can include progress reports, milestone achievements, and budget and schedule updates. Reports should be clear, concise, and tailored to the audience.
Issue and Risk Communication: Communicate issues and risks as they arise. It's important to not only report problems but also present potential solutions and mitigation strategies.
Team Communication: Foster effective communication among project team members. Encourage collaboration, share project-related information, and ensure that team members are aware of their roles and responsibilities.
Document Management: Maintain a central repository for project documents and information. Ensure that all stakeholders have access to the latest project documentation to avoid misunderstandings.
Feedback Collection: Solicit feedback from stakeholders to understand their satisfaction, concerns, and suggestions for improvement. This information can be used to adapt communication and project strategies.
Regular Meetings: Conduct regular team and stakeholder meetings to discuss progress, challenges, and upcoming tasks. Ensure that these meetings have clear agendas and follow-up actions.
Knowledge Sharing: Encourage knowledge sharing among team members by documenting lessons learned and best practices. This information can be valuable for future projects.
Effective project communication enhances transparency, alignment of expectations, and collaboration among stakeholders, ultimately contributing to the successful completion of a project. It's a dynamic process that should be continuously managed and adjusted throughout the project's life cycle to address the changing needs of stakeholders and the project's evolving requirements.
Project Execution
The project execution phase is where the project plan is put into action. It involves carrying out the project activities, coordinating resources, and monitoring and controlling to ensure that the project is executed according to the plan. Here are the key aspects of project execution:
Resource Allocation: Allocate and manage resources, including human resources, equipment, and materials, to ensure that they are available as needed throughout the project.
Task Execution: Team members carry out the project tasks as defined in the project plan. This is the hands-on work that moves the project towards its objectives.
Risk Management: Continue to monitor and control identified risks and implement risk response plans as necessary. New risks may emerge during execution, and they must be addressed promptly.
Change Control: Monitor and control changes to the project scope, schedule, and budget. Ensure that change requests are evaluated, approved, and implemented in a controlled manner.
Progress Tracking: Continuously track and report on project progress, comparing actual performance to the project plan. This helps identify variances and enables adjustments to keep the project on track.
Milestone Achievement: Monitor and celebrate project milestones as they are achieved. This boosts team morale and can serve as motivation to stay on course.
Resource Management: Ensure that resources are being utilized efficiently and that resource allocation aligns with the project's needs. Adjust resource allocation as necessary.
Documentation: Keep project documentation up to date. This includes project plans, schedules, change orders, and any other relevant documents.
Reporting: Provide regular status reports to stakeholders, summarizing the project's progress and highlighting any critical issues or changes. Tailor these reports to the audience's needs.
Quality Management
Quality management is a critical aspect of project management focused on ensuring that project deliverables and processes meet predefined standards and that the project satisfies stakeholder expectations. Effective quality management helps in delivering successful projects with a high degree of customer satisfaction. Here are the key aspects of quality management in project management:
Quality Planning: Quality planning involves defining the quality standards and criteria that need to be met throughout the project. This includes setting clear quality objectives and identifying the quality metrics that will be used to measure project performance.
Quality Assurance: Quality assurance is the process of systematically monitoring and evaluating project processes to ensure that they comply with established quality standards. It involves preventive actions to reduce the likelihood of defects or errors.
Quality Control: Quality control focuses on identifying and rectifying defects or variations from quality standards. It includes inspection, testing, and validation of project deliverables to ensure they meet the required quality levels.
Quality Standards: Clearly define the quality standards and specifications for the project. This might include industry standards, regulatory requirements, and specific quality criteria relevant to the project.
Documentation: Maintain detailed documentation related to quality management, including quality plans, test results, inspection reports, and records of quality audits.
Continuous Improvement: Encourage a culture of continuous improvement in which the project team identifies areas for enhancing quality and takes actions to implement improvements.
Customer Feedback: Solicit and incorporate customer feedback into the quality management process. Customer satisfaction is a vital indicator of project success.
Quality Culture: Foster a culture of quality throughout the project team and organization. This includes emphasizing the importance of quality in all project-related activities.
Quality management is an integral part of project management that ensures that project outcomes meet the defined standards and expectations. By implementing a robust quality management process, project managers can enhance the likelihood of delivering successful projects that satisfy both project stakeholders and end-users.
Cost Management
Cost management in project management involves planning, budgeting, monitoring, and controlling project costs to ensure that the project stays within its allocated budget. Effective cost management is essential for project success and delivering value to stakeholders. Here are the key aspects of cost management in project management:
Cost Estimation: Accurately estimate the costs associated with the project. This involves forecasting expenses for resources, materials, equipment, and other project-related items. Various estimation techniques, such as analogous estimating, parametric estimating, and bottom-up estimating, may be used.
Budget Development: Create a comprehensive project budget that includes all estimated costs. The budget should be approved by relevant stakeholders and serve as a financial baseline for the project.
Cost Control: Monitor project expenses throughout the project's lifecycle to ensure they align with the approved budget. Any discrepancies or variances should be identified and addressed promptly.
Resource Cost Allocation: Allocate costs to specific project activities and resources. This helps in tracking how resources are used and ensures that they are within budget.
Cost Tracking: Continuously track actual costs against the budget. This may involve comparing earned value (the value of work completed) to the planned value (the value of work scheduled to be completed) to assess project progress.
Cost Reporting: Provide regular cost reports to stakeholders, highlighting cost performance and variances. These reports are essential for transparency and decision-making.
Cost Analysis: Conduct cost analysis to identify the root causes of budget variances. This includes analyzing cost overruns and underruns and taking corrective actions.
Cost Reduction Strategies: Implement cost reduction strategies when necessary to bring the project back on track. This may involve revising the project plan, optimizing resource allocation, or seeking more cost-effective solutions.
Benefit-Cost Analysis: Evaluate the expected benefits of the project against its costs to determine whether the project is providing a positive return on investment (ROI).
Cost management is integral to project success, as it ensures that projects are delivered within budget constraints and that financial resources are used efficiently. Effective cost management helps in meeting project objectives and stakeholder expectations.
Time Management
Time management in project management involves planning, scheduling, monitoring, and controlling project activities to ensure that the project is completed within the defined time frame. Effective time management is crucial for delivering projects on time and meeting stakeholder expectations. Here are the key aspects of time management in project management:
Project Schedule: Develop a project schedule that outlines the sequence of activities, their durations, and dependencies. Common tools like Gantt charts and project management software can be used to create and visualize the schedule.
Task Sequencing: Arrange project tasks in a logical order based on their dependencies. Understand the critical path, which represents the sequence of tasks that, if delayed, will impact the project's overall timeline.
Resource Allocation: Assign resources to tasks and ensure that they are available as needed. Avoid resource conflicts and bottlenecks that can lead to delays.
Time Estimation: Accurately estimate the time required for each project activity. Use historical data, expert judgment, and estimation techniques such as PERT (Program Evaluation and Review Technique) to make realistic time predictions.
Monitoring and Tracking: Continuously monitor project progress against the schedule. Compare actual progress with the planned schedule to identify any variances or delays.
Schedule Baseline Updates: If changes to the project schedule are approved, update the schedule baseline to reflect these changes. This maintains an accurate reference point for performance measurement.
Effective time management helps project managers and teams stay on track, meet deadlines, and deliver projects on time. It is a dynamic process that requires continuous monitoring and adjustment to address changes and uncertainties that may affect the project schedule.
Scope Management
Scope management in project management is the process of defining, controlling, and validating the project's boundaries and deliverables. Effective scope management ensures that the project remains on track and that stakeholders' expectations are met. Here are the key aspects of scope management in project management:
Scope Definition: Clearly define the project's objectives, requirements, and boundaries. Understand what the project will deliver and what it won't. The scope statement provides a detailed description of what the project will achieve.
Scope Planning: Develop a scope management plan that outlines how the scope will be defined, validated, controlled, and how changes will be managed. This plan serves as a reference throughout the project.
Scope Control: Continuously monitor the project to ensure that changes to the scope are managed in a controlled manner. Scope control prevents "scope creep," which is the uncontrolled expansion of the project's scope.
Work Breakdown Structure (WBS): Create a WBS to break down the project into smaller, manageable components or work packages. The WBS helps visualize and organize the project's scope.
Scope Reporting: Provide regular scope reports to stakeholders, including updates on the status of the scope and any changes that have been made.
Scope Documentation: Maintain detailed documentation related to scope management, including the scope statement, WBS, and scope change requests.
Effective scope management helps in preventing scope changes that can disrupt project progress, lead to delays, and increase costs. It ensures that the project stays aligned with its original objectives and meets stakeholder expectations. Continuous monitoring and control are essential to prevent scope-related challenges.
Project Closure
Project closure is the final phase of the project management process and is critical for ensuring that the project is completed effectively and all project objectives are met. This phase involves wrapping up all project activities, evaluating project performance, and formally closing out the project. Here are the key aspects of project closure:
Formal Acceptance: Obtain formal acceptance of project deliverables from the project sponsor or relevant stakeholders. This signifies that the project's objectives have been achieved.
Closure Criteria: Define the criteria that must be met to consider the project completed. These criteria often include meeting project goals, delivering all scope items, and achieving stakeholder satisfaction.
Knowledge Transfer: Ensure that knowledge and project-related information are transferred to the relevant parties within the organization, particularly if the project team is disbanded.
Closure Report: Create a project closure report that summarizes the project's achievements, lessons learned, and any outstanding issues or recommendations.
Final Report: Generate a final project report that provides an overview of the project's performance, including any variances or deviations from the plan.
Formal Closure: Obtain formal closure approval from the project sponsor or relevant authority. This signifies the official end of the project.
Archiving: Archive all project documentation and records for future reference. Ensure that the archive is easily accessible and well-organized.
Celebration: Recognize and celebrate the project's successful completion. This can boost team morale and create a positive atmosphere for future projects.
Post-Implementation Review: If applicable, conduct a post-implementation review to assess how well the project's results are functioning after they have been put into practice.
Project closure is a crucial phase that ensures that the project's work is officially completed and that all relevant documentation is appropriately managed. It provides an opportunity to capture lessons learned and celebrate project achievements, ultimately contributing to improved project management in the future.
Conclusion
In conclusion, project management is a multifaceted discipline that involves a series of interconnected phases and principles aimed at achieving specific goals within a defined timeframe and budget. The effective management of a project requires careful consideration and execution of various key elements, including initiation, planning, execution, monitoring and control, risk management, communication, quality management, cost management, time management, scope management, and project closure.
Incorporating these principles and phases effectively can significantly enhance the likelihood of project success. It's important to recognize that project management is an iterative process, and adjustments may be necessary as the project progresses. Reflecting on lessons learned and continuously improving project management practices can help organizations and individuals achieve their goals and deliver value to stakeholders.
Read More
Project management is a critical discipline that plays a central role in the successful execution of endeavors, whether they are in the business, engineering, information technology, or numerous other fields. At its core, project management involves the application of a set of principles, practices, and techniques to initiate, plan, execute, control, and close a project efficiently and effectively. It serves as the guiding framework for organizations and individuals seeking to achieve their objectives, deliver products or services, and drive innovation while adhering to timelines and budgets.
This introduction serves as the foundation for exploring the key subtopics in project management principles, which encompass various stages of a project's life cycle, including initiation, planning, execution, monitoring, controlling, and closure. In an era where efficiency, precision, and adaptability are vital to achieving success, understanding and mastering project management principles are essential for individuals and organizations alike. This knowledge equips project managers with the tools and strategies needed to navigate the complexities of modern projects and deliver value to their stakeholders.
Table of contents
-
Project Initiation
-
Project Planning
-
Risk Management
-
Project Communication
-
Project Execution
-
Quality Management
-
Cost Management
-
Time Management
-
Scope Management
-
Project Closure
-
Conclusion
Project Initiation
Project initiation is the first and arguably one of the most crucial phases in the project management process. It's during this phase that the project is defined, its feasibility is assessed, and the initial groundwork is laid for the successful execution of the project. Project initiation sets the stage for the entire project, and the decisions made at this stage have a significant impact on its outcome. Here are some key aspects of project initiation:
Defining Objectives: The project initiation phase begins with a clear understanding of what the project aims to achieve. Project managers work closely with stakeholders to define specific and measurable objectives. These objectives should be aligned with the organization's overall goals.
Project Charter: A project charter is a formal document that authorizes the project to exist. It typically includes the project's purpose, objectives, scope, and high-level requirements. The charter is often signed off by a senior executive or project sponsor.
Stakeholder Identification: Identifying and engaging stakeholders is a crucial part of project initiation. Stakeholders include anyone who has an interest in or can be affected by the project. Understanding their needs, expectations, and influence is essential.
Feasibility Analysis: Project managers conduct a feasibility study to assess whether the project is viable and worthwhile. This includes examining technical, economic, legal, operational, and scheduling feasibility.
Project Scope: Clearly defining the project's scope is vital to prevent scope creep (uncontrolled expansion of project scope). The scope outlines what will and won't be part of the project, helping to manage expectations and prevent unnecessary changes.
Resource Identification: Identifying the resources needed for the project, including human resources, equipment, and materials, is a key part of initiation. This helps in resource allocation and budgeting.
Project Documentation: Key project initiation documents, including the project charter and initial project plan, are created and stored for reference throughout the project.
The project initiation phase ensures that all stakeholders have a common understanding of the project's purpose and objectives and that the project is set up for success from the start. A well-executed initiation phase minimizes the risk of misunderstandings and scope changes as the project progresses, ultimately leading to a smoother project execution.
Project Planning
Project planning is a critical phase in the project management process, following project initiation. During this phase, detailed plans are developed to guide the project from start to finish. Effective project planning is essential for setting clear objectives, allocating resources efficiently, and ensuring that the project stays on track. Here are key aspects of project planning:
Work Packages: Work packages are the smallest units within the WBS and define specific tasks or activities that need to be completed. Each work package is assigned to a team member or group.
Scheduling: Project schedules are created to determine the sequence and duration of activities. Techniques like Gantt charts and network diagrams are often used for visualizing the project timeline. Scheduling helps in setting deadlines and milestones.
Resource Allocation: Resources, including human resources, equipment, and materials, are allocated to different tasks. This ensures that the right resources are available at the right time, reducing bottlenecks and delays.
Budgeting: The project budget is established during this phase. It includes estimates for all costs associated with the project, such as labor, materials, and overhead. The budget is an essential part of project control and monitoring.
Risk Management: A comprehensive risk management plan is developed. It identifies potential risks and outlines strategies to mitigate, monitor, and respond to them. Risk assessment and analysis are important parts of this process.
Quality Planning: Quality standards and criteria are determined. This includes defining what constitutes quality in the context of the project and how it will be ensured throughout the project's life cycle.
Change Management: Procedures for handling changes to the project scope, schedule, or budget are established. Change management helps in evaluating and implementing change requests in a controlled manner.
Stakeholder Engagement: The plan for engaging with stakeholders is refined. This includes how and when stakeholders will be involved in the project, their roles, and how their concerns and feedback will be addressed.
Contingency Planning: Contingency plans are created to address potential disruptions or setbacks. These plans outline how the project team will respond if unexpected issues arise.
Documentation: Detailed project documentation, including the project plan, schedules, and all relevant planning documents, is created and maintained throughout the project.
Effective project planning sets the foundation for project execution, ensuring that everyone involved knows what is expected of them, when it needs to be done, and how it should be done. It provides a roadmap for the entire project team and helps in tracking progress, managing resources, and achieving project objectives.
Risk Management
Risk management is a fundamental component of project management, dedicated to identifying, assessing, mitigating, and monitoring potential risks and uncertainties that could impact a project's success. Effectively managing risks helps project managers and teams anticipate, prepare for, and respond to challenges, ultimately minimizing the likelihood and impact of negative events. Here are the key aspects of risk management in project management:
Risk Identification: The process begins with the identification of risks that could affect the project. These risks can be internal or external, known or unknown, and can relate to various aspects, including scope, schedule, cost, quality, and more. Various techniques like brainstorming, checklists, and historical data analysis are used to identify risks.
Risk Assessment: Once identified, risks are assessed for their potential impact and likelihood. This often involves assigning a risk rating or score to prioritize risks. Qualitative and quantitative analysis methods can be used to assess risks.
Risk Register: All identified risks, along with their assessment details, are documented in a risk register. This register serves as a central repository of information about project risks.
Risk Response Planning: For each identified risk, a response plan is created. There are four primary strategies: avoid, transfer, mitigate, and accept. Response plans specify what actions will be taken if a risk occurs.
Risk Monitoring and Control: Risk management is an ongoing process. Throughout the project's life cycle, risks are monitored to track changes in their status. If a risk's likelihood or impact changes, the response plan may need to be adjusted.
Risk Reporting: Regular reporting to stakeholders and project sponsors is essential. This includes providing updates on the status of identified risks, their impact on the project, and the effectiveness of risk response strategies.
Risk Register Updates: The risk register is continuously updated to reflect changes in risks throughout the project.
Effective risk management is a proactive and dynamic process that helps project managers and teams respond to challenges and uncertainties, making the project more resilient and increasing the likelihood of successful project completion within scope, schedule, and budget constraints.
Project Communication
Effective project communication is a critical component of project management, ensuring that information is shared, stakeholders are engaged, and the project progresses smoothly. Good communication helps in managing expectations, resolving issues, and ultimately achieving project objectives. Here are the key aspects of project communication in project management:
Stakeholder Identification: Identify all project stakeholders, including team members, sponsors, clients, and external parties. Understanding their interests, needs, and expectations is vital for effective communication.
Communication Planning: Develop a communication plan that outlines how, when, and what information will be communicated to various stakeholders. The plan should define communication channels, frequency, and the responsible parties.
Status Reporting: Regularly provide project status updates to stakeholders. This can include progress reports, milestone achievements, and budget and schedule updates. Reports should be clear, concise, and tailored to the audience.
Issue and Risk Communication: Communicate issues and risks as they arise. It's important to not only report problems but also present potential solutions and mitigation strategies.
Team Communication: Foster effective communication among project team members. Encourage collaboration, share project-related information, and ensure that team members are aware of their roles and responsibilities.
Document Management: Maintain a central repository for project documents and information. Ensure that all stakeholders have access to the latest project documentation to avoid misunderstandings.
Feedback Collection: Solicit feedback from stakeholders to understand their satisfaction, concerns, and suggestions for improvement. This information can be used to adapt communication and project strategies.
Regular Meetings: Conduct regular team and stakeholder meetings to discuss progress, challenges, and upcoming tasks. Ensure that these meetings have clear agendas and follow-up actions.
Knowledge Sharing: Encourage knowledge sharing among team members by documenting lessons learned and best practices. This information can be valuable for future projects.
Effective project communication enhances transparency, alignment of expectations, and collaboration among stakeholders, ultimately contributing to the successful completion of a project. It's a dynamic process that should be continuously managed and adjusted throughout the project's life cycle to address the changing needs of stakeholders and the project's evolving requirements.
Project Execution
The project execution phase is where the project plan is put into action. It involves carrying out the project activities, coordinating resources, and monitoring and controlling to ensure that the project is executed according to the plan. Here are the key aspects of project execution:
Resource Allocation: Allocate and manage resources, including human resources, equipment, and materials, to ensure that they are available as needed throughout the project.
Task Execution: Team members carry out the project tasks as defined in the project plan. This is the hands-on work that moves the project towards its objectives.
Risk Management: Continue to monitor and control identified risks and implement risk response plans as necessary. New risks may emerge during execution, and they must be addressed promptly.
Change Control: Monitor and control changes to the project scope, schedule, and budget. Ensure that change requests are evaluated, approved, and implemented in a controlled manner.
Progress Tracking: Continuously track and report on project progress, comparing actual performance to the project plan. This helps identify variances and enables adjustments to keep the project on track.
Milestone Achievement: Monitor and celebrate project milestones as they are achieved. This boosts team morale and can serve as motivation to stay on course.
Resource Management: Ensure that resources are being utilized efficiently and that resource allocation aligns with the project's needs. Adjust resource allocation as necessary.
Documentation: Keep project documentation up to date. This includes project plans, schedules, change orders, and any other relevant documents.
Reporting: Provide regular status reports to stakeholders, summarizing the project's progress and highlighting any critical issues or changes. Tailor these reports to the audience's needs.
Quality Management
Quality management is a critical aspect of project management focused on ensuring that project deliverables and processes meet predefined standards and that the project satisfies stakeholder expectations. Effective quality management helps in delivering successful projects with a high degree of customer satisfaction. Here are the key aspects of quality management in project management:
Quality Planning: Quality planning involves defining the quality standards and criteria that need to be met throughout the project. This includes setting clear quality objectives and identifying the quality metrics that will be used to measure project performance.
Quality Assurance: Quality assurance is the process of systematically monitoring and evaluating project processes to ensure that they comply with established quality standards. It involves preventive actions to reduce the likelihood of defects or errors.
Quality Control: Quality control focuses on identifying and rectifying defects or variations from quality standards. It includes inspection, testing, and validation of project deliverables to ensure they meet the required quality levels.
Quality Standards: Clearly define the quality standards and specifications for the project. This might include industry standards, regulatory requirements, and specific quality criteria relevant to the project.
Documentation: Maintain detailed documentation related to quality management, including quality plans, test results, inspection reports, and records of quality audits.
Continuous Improvement: Encourage a culture of continuous improvement in which the project team identifies areas for enhancing quality and takes actions to implement improvements.
Customer Feedback: Solicit and incorporate customer feedback into the quality management process. Customer satisfaction is a vital indicator of project success.
Quality Culture: Foster a culture of quality throughout the project team and organization. This includes emphasizing the importance of quality in all project-related activities.
Quality management is an integral part of project management that ensures that project outcomes meet the defined standards and expectations. By implementing a robust quality management process, project managers can enhance the likelihood of delivering successful projects that satisfy both project stakeholders and end-users.
Cost Management
Cost management in project management involves planning, budgeting, monitoring, and controlling project costs to ensure that the project stays within its allocated budget. Effective cost management is essential for project success and delivering value to stakeholders. Here are the key aspects of cost management in project management:
Cost Estimation: Accurately estimate the costs associated with the project. This involves forecasting expenses for resources, materials, equipment, and other project-related items. Various estimation techniques, such as analogous estimating, parametric estimating, and bottom-up estimating, may be used.
Budget Development: Create a comprehensive project budget that includes all estimated costs. The budget should be approved by relevant stakeholders and serve as a financial baseline for the project.
Cost Control: Monitor project expenses throughout the project's lifecycle to ensure they align with the approved budget. Any discrepancies or variances should be identified and addressed promptly.
Resource Cost Allocation: Allocate costs to specific project activities and resources. This helps in tracking how resources are used and ensures that they are within budget.
Cost Tracking: Continuously track actual costs against the budget. This may involve comparing earned value (the value of work completed) to the planned value (the value of work scheduled to be completed) to assess project progress.
Cost Reporting: Provide regular cost reports to stakeholders, highlighting cost performance and variances. These reports are essential for transparency and decision-making.
Cost Analysis: Conduct cost analysis to identify the root causes of budget variances. This includes analyzing cost overruns and underruns and taking corrective actions.
Cost Reduction Strategies: Implement cost reduction strategies when necessary to bring the project back on track. This may involve revising the project plan, optimizing resource allocation, or seeking more cost-effective solutions.
Benefit-Cost Analysis: Evaluate the expected benefits of the project against its costs to determine whether the project is providing a positive return on investment (ROI).
Cost management is integral to project success, as it ensures that projects are delivered within budget constraints and that financial resources are used efficiently. Effective cost management helps in meeting project objectives and stakeholder expectations.
Time Management
Time management in project management involves planning, scheduling, monitoring, and controlling project activities to ensure that the project is completed within the defined time frame. Effective time management is crucial for delivering projects on time and meeting stakeholder expectations. Here are the key aspects of time management in project management:
Project Schedule: Develop a project schedule that outlines the sequence of activities, their durations, and dependencies. Common tools like Gantt charts and project management software can be used to create and visualize the schedule.
Task Sequencing: Arrange project tasks in a logical order based on their dependencies. Understand the critical path, which represents the sequence of tasks that, if delayed, will impact the project's overall timeline.
Resource Allocation: Assign resources to tasks and ensure that they are available as needed. Avoid resource conflicts and bottlenecks that can lead to delays.
Time Estimation: Accurately estimate the time required for each project activity. Use historical data, expert judgment, and estimation techniques such as PERT (Program Evaluation and Review Technique) to make realistic time predictions.
Monitoring and Tracking: Continuously monitor project progress against the schedule. Compare actual progress with the planned schedule to identify any variances or delays.
Schedule Baseline Updates: If changes to the project schedule are approved, update the schedule baseline to reflect these changes. This maintains an accurate reference point for performance measurement.
Effective time management helps project managers and teams stay on track, meet deadlines, and deliver projects on time. It is a dynamic process that requires continuous monitoring and adjustment to address changes and uncertainties that may affect the project schedule.
Scope Management
Scope management in project management is the process of defining, controlling, and validating the project's boundaries and deliverables. Effective scope management ensures that the project remains on track and that stakeholders' expectations are met. Here are the key aspects of scope management in project management:
Scope Definition: Clearly define the project's objectives, requirements, and boundaries. Understand what the project will deliver and what it won't. The scope statement provides a detailed description of what the project will achieve.
Scope Planning: Develop a scope management plan that outlines how the scope will be defined, validated, controlled, and how changes will be managed. This plan serves as a reference throughout the project.
Scope Control: Continuously monitor the project to ensure that changes to the scope are managed in a controlled manner. Scope control prevents "scope creep," which is the uncontrolled expansion of the project's scope.
Work Breakdown Structure (WBS): Create a WBS to break down the project into smaller, manageable components or work packages. The WBS helps visualize and organize the project's scope.
Scope Reporting: Provide regular scope reports to stakeholders, including updates on the status of the scope and any changes that have been made.
Scope Documentation: Maintain detailed documentation related to scope management, including the scope statement, WBS, and scope change requests.
Effective scope management helps in preventing scope changes that can disrupt project progress, lead to delays, and increase costs. It ensures that the project stays aligned with its original objectives and meets stakeholder expectations. Continuous monitoring and control are essential to prevent scope-related challenges.
Project Closure
Project closure is the final phase of the project management process and is critical for ensuring that the project is completed effectively and all project objectives are met. This phase involves wrapping up all project activities, evaluating project performance, and formally closing out the project. Here are the key aspects of project closure:
Formal Acceptance: Obtain formal acceptance of project deliverables from the project sponsor or relevant stakeholders. This signifies that the project's objectives have been achieved.
Closure Criteria: Define the criteria that must be met to consider the project completed. These criteria often include meeting project goals, delivering all scope items, and achieving stakeholder satisfaction.
Knowledge Transfer: Ensure that knowledge and project-related information are transferred to the relevant parties within the organization, particularly if the project team is disbanded.
Closure Report: Create a project closure report that summarizes the project's achievements, lessons learned, and any outstanding issues or recommendations.
Final Report: Generate a final project report that provides an overview of the project's performance, including any variances or deviations from the plan.
Formal Closure: Obtain formal closure approval from the project sponsor or relevant authority. This signifies the official end of the project.
Archiving: Archive all project documentation and records for future reference. Ensure that the archive is easily accessible and well-organized.
Celebration: Recognize and celebrate the project's successful completion. This can boost team morale and create a positive atmosphere for future projects.
Post-Implementation Review: If applicable, conduct a post-implementation review to assess how well the project's results are functioning after they have been put into practice.
Project closure is a crucial phase that ensures that the project's work is officially completed and that all relevant documentation is appropriately managed. It provides an opportunity to capture lessons learned and celebrate project achievements, ultimately contributing to improved project management in the future.
Conclusion
In conclusion, project management is a multifaceted discipline that involves a series of interconnected phases and principles aimed at achieving specific goals within a defined timeframe and budget. The effective management of a project requires careful consideration and execution of various key elements, including initiation, planning, execution, monitoring and control, risk management, communication, quality management, cost management, time management, scope management, and project closure.
Incorporating these principles and phases effectively can significantly enhance the likelihood of project success. It's important to recognize that project management is an iterative process, and adjustments may be necessary as the project progresses. Reflecting on lessons learned and continuously improving project management practices can help organizations and individuals achieve their goals and deliver value to stakeholders.
The Evolution of AI Chatbots: A Deep Dive into ChatGPT's Development
In the ever-evolving landscape of artificial intelligence, chatbots have emerged as a fascinating and transformative technology. These virtual conversational agents have come a long way from their rudimentary beginnings, and today, they play a pivotal role in how we interact with machines, automate customer support, and assist in various applications across industries. In this blog post, we embark on a deep dive into the captivating journey of AI chatbots, with a specific focus on one of the most groundbreaking advancements in this field: ChatGPT.
As we delve deeper into the mechanics and intricacies of ChatGPT's evolution, you'll gain a comprehensive understanding of how it has become a game-changer in the world of AI chatbots. Join us as we unravel the past, present, and future of AI chatbots and learn how they're poised to reshape our interactions with machines and redefine human-computer collaboration. Let's embark on this enlightening journey through the evolution of AI chatbots and the remarkable story of ChatGPT's development.
Table of contents
-
The Birth of Chatbots: Early Pioneers and Milestones
-
From ELIZA to GPT-3.5: The Advancements in Natural Language Processing
-
ChatGPT's Predecessors: A Brief History of GPT Models
-
The Role of Deep Learning in ChatGPT's Development
-
Data and Training: How ChatGPT Learns from Text Corpora
-
Fine-Tuning and Customization: Shaping ChatGPT's Behavior
-
Scaling Up: The Hardware and Infrastructure Behind ChatGPT
-
Challenges and Breakthroughs: Overcoming Limitations in ChatGPT
-
Ethical Concerns in ChatGPT's Evolution: Bias and Fairness
-
The Road Ahead: ChatGPT's Future and Potential Applications
-
Conclusion
The Birth of Chatbots: Early Pioneers and Milestones
In the realm of artificial intelligence, the concept of chatbots has a rich and intriguing history. These virtual conversational agents, which we often take for granted today, had humble beginnings and went through a series of significant milestones to become the sophisticated AI chatbots we encounter in our daily lives. In this segment, we will travel back in time and explore the birth of chatbots, paying homage to their early pioneers and pivotal milestones.
The Genesis of ELIZA (1966): Our journey begins in the 1960s when Joseph Weizenbaum, a computer scientist at MIT, developed one of the very first chatbots, ELIZA. ELIZA was designed to simulate a Rogerian psychotherapist, engaging users in text-based conversations about their feelings and problems. While basic by today's standards, ELIZA showcased the potential of computers to hold text-based conversations and provided a glimpse of what the future might hold.
Parry, the Paranoid Chatbot (1972): ELIZA was soon joined by another notable figure, Parry, created by Kenneth Colby. Parry was developed as a simulation of a paranoid individual and engaged users in text-based conversations. These early chatbots were limited in their capabilities but demonstrated early attempts at creating conversational agents.
Turing Test and the Loebner Prize (1991-Present): The Turing Test, proposed by Alan Turing in 1950, challenged the ability of machines to exhibit intelligent behavior indistinguishable from that of humans. The Loebner Prize, established in 1991, further encouraged the development of chatbots by offering an annual competition to determine the most human-like conversational AI. These events have played a significant role in driving advancements in chatbot technology.
The GPT Era and ChatGPT (2019-Present): Finally, we arrive at the present day, where advancements in deep learning and the advent of models like GPT-3 and GPT-3.5 have revolutionized chatbots. ChatGPT, based on the GPT architecture, represents a culmination of these developments, offering a level of conversational AI that was once only dreamed of.
These early pioneers and milestones in the world of chatbots have set the stage for the remarkable advancements we witness today. The journey from ELIZA to ChatGPT is a testament to human ingenuity and the relentless pursuit of creating more intelligent and capable chatbots. In the next section, we will explore the underlying technology and principles that have driven this evolution.
From ELIZA to GPT-3.5: The Advancements in Natural Language Processing
The field of natural language processing (NLP) has witnessed a remarkable journey of evolution, driven by advances in technology, data, and algorithms. As we explore the development of AI chatbots and, in particular, the evolution from ELIZA to GPT-3.5, it becomes evident that the progress in natural language processing is a key driving force behind the capabilities of these conversational agents. In this section, we'll delve into the significant advancements in NLP that have made this journey possible.
Early Rule-Based Systems (1960s-1970s): The birth of NLP and chatbots saw the emergence of rule-based systems, like ELIZA, which relied on a pre-defined set of rules to generate responses. These systems, though limited in scope, were groundbreaking at the time and laid the foundation for more sophisticated NLP.
Statistical Language Models (1990s-2000s): A major breakthrough came with the development of statistical language models that learned from vast amounts of text data. These models used probabilistic algorithms to determine the likelihood of a word or phrase occurring in a given context, greatly improving language understanding and generation.
The Deep Learning Revolution (2010s): The 2010s witnessed the rise of deep learning, particularly deep neural networks, which have revolutionized NLP. Models like Word2Vec and GloVe allowed machines to understand the context and meaning of words, while recurrent neural networks (RNNs) and long short-term memory networks (LSTMs) facilitated more robust text processing.
The GPT (Generative Pretrained Transformer) Series: Developed by OpenAI, the GPT series of models represents a breakthrough in NLP. Beginning with GPT-1, these models demonstrated the power of pretraining on large datasets and fine-tuning for specific tasks. GPT-3, and its successor, GPT-3.5, with its 175 billion parameters, have taken NLP to new heights, delivering human-like text generation and understanding on an unprecedented scale.
The evolution of natural language processing has been a journey of continuous innovation, fueled by the synergy of data, algorithms, and hardware. From rule-based systems to the astonishing capabilities of GPT-3.5, these advancements have paved the way for the development of increasingly sophisticated AI chatbots and have broadened the horizons of NLP, impacting various industries and applications. In the following sections, we will delve deeper into the specifics of GPT-3.5 and its role in reshaping the world of AI chatbots.
ChatGPT's Predecessors: A Brief History of GPT Models
Before the emergence of ChatGPT, a remarkable family of language models known as the "GPT" series paved the way for revolutionary advancements in natural language processing. In this section, we'll take a closer look at the history of GPT models, tracing their development and key milestones that led to the creation of ChatGPT.
GPT-1: The Pioneer (2018): The GPT series began with GPT-1, which stands for "Generative Pretrained Transformer." Developed by OpenAI, GPT-1 made waves in the field of NLP by demonstrating the potential of large-scale pretraining. With 117 million parameters, it could generate coherent and contextually relevant text by predicting the next word in a sentence, making it a promising step towards more capable AI chatbots.
GPT-3: A Giant Leap (2020): GPT-3, with a whopping 175 billion parameters, marked a giant leap in NLP. It showcased the true potential of transfer learning in NLP by achieving remarkable performance on a wide range of tasks, from language translation to question-answering and even creative text generation. GPT-3 captured the imagination of researchers, businesses, and developers, paving the way for AI chatbots like ChatGPT.
Fine-Tuning and Customization: Building on GPT-3 (2020-2021): Beyond GPT-3's incredible generative abilities, its fine-tuning capabilities allowed developers to customize it for specific applications. This introduced a new level of flexibility and adaptability, making it possible to fine-tune GPT-3 for use in chatbots, virtual assistants, and various other conversational AI applications.
The GPT series has marked a historic transformation in NLP, pushing the boundaries of what's possible with AI-driven language models. These models have become foundational in a wide range of applications, from chatbots to content generation, translation, and more. ChatGPT, with its origins deeply rooted in the GPT lineage, is a testament to the continuous innovation and progress in the field of natural language processing. In the following sections, we'll explore the unique characteristics and capabilities that make ChatGPT a standout in the world of conversational AI.
The Role of Deep Learning in ChatGPT's Development
Deep learning, a subfield of artificial intelligence, has played a central and transformative role in the development of ChatGPT and other advanced AI chatbots. In this section, we'll explore the significance of deep learning in ChatGPT's evolution, understanding the neural networks, architectures, and training methods that underpin its capabilities.
Neural Networks: The Building Blocks of Deep Learning: At the heart of deep learning are neural networks, computational models inspired by the human brain's structure. These networks consist of layers of interconnected artificial neurons that process data in a hierarchical manner. For ChatGPT, these neural networks serve as the foundation for understanding and generating human-like text.
Recurrent Neural Networks (RNNs): Early Language Processing: Recurrent Neural Networks, or RNNs, were among the first deep learning models applied to natural language processing tasks. RNNs have memory, which allows them to maintain context over a sequence of words, making them suitable for tasks like text generation and language understanding.
Long Short-Term Memory (LSTM) Networks: Handling Sequences: LSTMs are an evolution of RNNs designed to address the vanishing gradient problem and handle long sequences more effectively. They've been instrumental in improving the capabilities of AI chatbots like ChatGPT in understanding and generating coherent text.
Transformer Architecture: The Breakthrough in NLP (2017): The introduction of the Transformer architecture marked a major turning point in NLP and deep learning. Transformers employ self-attention mechanisms, allowing models to consider the importance of different words in a sentence and process sequences in parallel. This architecture, which GPT models are based on, has greatly improved the efficiency and effectiveness of language modeling.
Scaling Up: The Power of Model Size (Parametric Models): Another critical element is the scale of deep learning models. As seen in GPT-3.5, larger models with more parameters can capture more complex patterns in data, enabling them to perform at human-like levels in language understanding and generation.
Deep learning, with its neural networks, advanced architectures, and training methods, has propelled AI chatbots like ChatGPT to remarkable heights in natural language processing. The ability to understand context, generate coherent text, and adapt to specific tasks has been significantly enhanced by these deep learning techniques. As we explore the technology behind ChatGPT, we'll uncover how these principles are put into practice to create an AI chatbot capable of engaging in meaningful and human-like conversations.
Data and Training: How ChatGPT Learns from Text Corpora
The remarkable abilities of ChatGPT, and other advanced AI chatbots, are rooted in the extensive datasets they're trained on and the training methodologies employed. In this section, we'll uncover the crucial role of data and training in ChatGPT's development, shedding light on how it learns from vast text corpora to become a proficient conversational AI.
Data as the Lifeblood of ChatGPT: Data is the foundation of ChatGPT's learning process. To train an AI chatbot effectively, vast amounts of text data are required. These datasets can comprise a diverse range of sources, from books and articles to websites and social media posts, encompassing a wide array of languages and topics.
Fine-Tuning for Specific Tasks: Transfer Learning at Play: After pretraining, the model is fine-tuned for specific tasks or applications. This fine-tuning stage narrows down the AI's focus and helps it adapt to particular domains or user needs. It may involve using smaller, task-specific datasets and reinforcement learning techniques.
Diverse Data Sources for a Well-Rounded AI: ChatGPT's training data is carefully curated to provide a broad and diverse knowledge base. Incorporating data from multiple sources ensures the AI can handle a wide range of user queries and engage in discussions on various subjects.
Ethical Considerations and Data Selection: The choice of training data is critical in addressing ethical concerns such as bias and fairness. OpenAI and other developers must carefully curate data to avoid perpetuating biases and controversial content.
Ongoing Training and Updates: Continuous Learning: ChatGPT's learning is an ongoing process. Developers regularly update the model with new data to keep it relevant and accurate, reflecting changing trends, topics, and user expectations.
In the realm of AI chatbots like ChatGPT, data and training form the bedrock of their capabilities. Through vast and diverse text corpora and meticulous training methodologies, these models gain the knowledge and language proficiency needed to engage in coherent and context-aware conversations. In the subsequent sections, we will delve into the practical aspects of how ChatGPT transforms this training into its real-world applications and interactions.
Fine-Tuning and Customization: Shaping ChatGPT's Behavior
One of the key features that sets AI chatbots like ChatGPT apart is their ability to be fine-tuned and customized for specific tasks or behaviors. In this section, we'll explore the critical concept of fine-tuning and customization, which allows developers to shape ChatGPT's behavior to meet their specific requirements.
Understanding Fine-Tuning: Tailoring the Model: Fine-tuning is the process of adjusting a pretrained AI model like ChatGPT to be more specialized for a particular task or behavior. It involves exposing the model to task-specific data to adapt its behavior.
Task-Specific Datasets: Refining for Particular Use Cases: To fine-tune ChatGPT, developers use task-specific datasets. These datasets contain examples of the desired behavior or responses that they want the model to exhibit.
Reward-Based Reinforcement Learning: Improving Dialogue Flow: In some cases, reinforcement learning techniques are used during fine-tuning. The model is rewarded for generating better responses during interactions, helping it learn how to engage in more meaningful and context-aware conversations.
Limitation and Boundaries: Ethical and Safety Considerations: Fine-tuning is not without limitations. It's essential to set boundaries and ethical guidelines to ensure that the AI's behavior remains safe, responsible, and free from harmful or inappropriate content.
User-Defined Chatbots: Tailoring to Unique Needs: With fine-tuning and customization, developers can create user-specific chatbots tailored to unique needs, whether in customer support, content generation, or other applications.
Fine-tuning and customization are integral to shaping ChatGPT's behavior to make it a valuable tool for various industries and applications. It empowers developers to create AI chatbots that align with specific user needs, adopt distinct personas, and provide tailored responses. In the following sections, we will delve into the applications and use cases where fine-tuned ChatGPT shines, as well as the ethical considerations that come into play when shaping AI behavior.
Scaling Up: The Hardware and Infrastructure Behind ChatGPT
The capabilities of ChatGPT, a sophisticated AI chatbot, are not solely a result of advanced algorithms and training data but are also heavily dependent on the underlying hardware and infrastructure. In this section, we'll delve into the critical role that hardware and infrastructure play in scaling up the power and efficiency of ChatGPT.
Parallel Processing and GPUs: Training large language models like ChatGPT requires immense computational power. Graphics Processing Units (GPUs) are essential for parallel processing, enabling the model to analyze and generate text more quickly.
High-Performance Computing Clusters: Clusters of high-performance machines are used for training and running large language models efficiently. These clusters are designed to handle the enormous computational demands of AI models.
Tensor Processing Units (TPUs): In addition to GPUs, TPUs are becoming increasingly important for AI workloads. They are specialized hardware accelerators designed to speed up deep learning tasks, including training large models like ChatGPT.
Data Storage and Retrieval: Fast and reliable data storage and retrieval systems are crucial for handling the massive datasets used in training AI models. This infrastructure ensures that the model can access and process data efficiently.
Energy Efficiency: To manage the environmental impact of large-scale AI training, there is a growing emphasis on energy-efficient hardware and data centers. These developments aim to reduce the carbon footprint of AI models.
Cost Management: Training and running models like ChatGPT can be costly. Efficient infrastructure and cost management strategies are essential to make AI chatbots economically viable for developers and organizations.
Maintenance and Monitoring: The complex infrastructure supporting ChatGPT requires ongoing maintenance and monitoring to ensure optimal performance, security, and reliability.
The hardware and infrastructure behind ChatGPT represent a significant investment of resources. These elements are pivotal in enabling the development and deployment of large-scale AI chatbots that can process and generate text in real-time. As AI models continue to grow in size and complexity, the role of hardware and infrastructure becomes increasingly crucial for their success. In the subsequent sections, we will explore the real-world applications and impact of ChatGPT in various industries and scenarios.
Challenges and Breakthroughs: Overcoming Limitations in ChatGPT
While ChatGPT and similar AI chatbots have made remarkable strides in natural language processing and understanding, they are not without their challenges. In this section, we'll explore the limitations and the breakthroughs that have allowed ChatGPT to push the boundaries of conversational AI.
Limited Context Understanding: One significant challenge in AI chatbots is their ability to understand and maintain context over extended conversations. ChatGPT can sometimes lose track of the discussion topic or context.
Generating Incorrect or Incoherent Responses: AI chatbots may generate responses that are factually incorrect or incoherent. These issues can stem from the data they were trained on, leading to unreliable answers.
Ethical Considerations: The ethical implications of AI language models, such as privacy, safety, and bias, are ongoing challenges. Ensuring that AI chatbots adhere to ethical guidelines is a constant priority.
Scalability and Efficiency: Training and running large AI models like ChatGPT can be computationally expensive and energy-intensive. Researchers and organizations are working on improving the efficiency and environmental impact of AI infrastructure.
Multimodal Understanding: Expanding ChatGPT's understanding beyond text to include images, audio, and other modalities is a challenge that is being addressed in ongoing research.
Fine-Tuning Complexity: Fine-tuning AI models like ChatGPT can be complex and labor-intensive, requiring careful data curation and reinforcement learning techniques.
Breakthroughs and solutions to these challenges are actively researched and developed. Developers, researchers, and organizations are continuously working to improve the reliability, safety, and capabilities of AI chatbots like ChatGPT.
Ethical Concerns in ChatGPT's Evolution: Bias and Fairness
The development and deployment of AI chatbots like ChatGPT have raised important ethical considerations, particularly concerning issues of bias and fairness. In this section, we'll delve into these ethical concerns and the efforts made to address them in the evolution of ChatGPT.
Stereotypical and Offensive Responses: AI chatbots can inadvertently generate responses that are stereotypical, offensive, or discriminatory. Such content can be harmful, perpetuating harmful stereotypes and offensive language.
Impact on Vulnerable Populations: Biased or unfair responses generated by AI chatbots can disproportionately affect vulnerable or marginalized populations. Ensuring fair and respectful interactions is essential to avoid harm.
Lack of Context Awareness: ChatGPT may not always fully understand or consider the context and potential consequences of its responses, which can lead to responses that are insensitive or inappropriate.
User Feedback and Reporting: Ethical guidelines encourage users to provide feedback on problematic responses and content generated by AI chatbots. User feedback is a valuable tool in identifying and addressing issues.
Guidelines and Content Filtering: Developers implement guidelines and content filtering mechanisms to prevent AI chatbots from generating content that is harmful, inappropriate, or biased.
Addressing bias and fairness concerns in AI chatbots is an ongoing process, and developers, organizations, and researchers are committed to creating AI systems that respect ethical principles. The evolution of ChatGPT involves a continuous effort to improve fairness, reduce biases, and enhance the overall quality and safety of interactions with the AI. In the following sections, we will explore the real-world applications and use cases where these ethical considerations play a significant role.
The Road Ahead: ChatGPT's Future and Potential Applications
ChatGPT and similar AI chatbots have made significant strides in natural language processing, but their journey is far from over. In this section, we'll explore the future of ChatGPT and the exciting potential applications that lie ahead.
Customer Support and Service: AI chatbots like ChatGPT have the potential to revolutionize customer support. They can handle inquiries, troubleshoot problems, and provide assistance around the clock, offering cost-effective solutions for businesses.
Education and Tutoring: AI chatbots can act as personalized tutors, assisting students with homework, explaining complex concepts, and offering guidance in various subjects.
Content Generation: ChatGPT and similar models have applications in content creation, from generating news articles to marketing copy, streamlining the content production process.
Multimodal Conversations: The ability to understand and generate both text and images or audio could lead to richer and more interactive AI conversations.
Research and Development: AI chatbots can assist researchers by quickly accessing and summarizing information from vast datasets, accelerating the pace of scientific discovery.
Multilingual and Cross-Cultural Interaction: With improvements in language capabilities, AI chatbots can bridge language barriers and facilitate cross-cultural communication.
Ethical and Legal Consultation: AI chatbots may be used for ethical and legal consultation, offering insights into complex moral and legal issues or helping users navigate legal processes.
As AI chatbots like ChatGPT continue to evolve and mature, their applications will extend into more domains, making them valuable tools for individuals, businesses, and organizations. The road ahead involves addressing challenges, improving ethical guidelines, and enhancing the safety and reliability of these AI systems. The potential applications are diverse and promising, marking a new era in human-computer interaction. In the final sections of this series, we will explore practical examples and use cases that showcase the impact and capabilities of ChatGPT in action.
Conclusion
The evolution of AI chatbots, epitomized by ChatGPT, is a remarkable journey through the realms of natural language processing, deep learning, and ethical considerations. From their early pioneers like ELIZA to the powerful GPT models, AI chatbots have transformed the way we interact with machines and access information.
However, this evolution has not been without its challenges. Issues of bias, fairness, and ethical concerns are paramount, and developers are actively working to ensure that AI chatbots like ChatGPT adhere to the highest ethical standards and provide safe and respectful interactions.
As we look to the future, it's clear that AI chatbots will play an increasingly integral role in our lives, offering assistance, information, and companionship in a variety of fields. The development of ChatGPT is just one chapter in the ongoing story of AI's evolution, and it is certain that the best is yet to come.
Read More
In the ever-evolving landscape of artificial intelligence, chatbots have emerged as a fascinating and transformative technology. These virtual conversational agents have come a long way from their rudimentary beginnings, and today, they play a pivotal role in how we interact with machines, automate customer support, and assist in various applications across industries. In this blog post, we embark on a deep dive into the captivating journey of AI chatbots, with a specific focus on one of the most groundbreaking advancements in this field: ChatGPT.
As we delve deeper into the mechanics and intricacies of ChatGPT's evolution, you'll gain a comprehensive understanding of how it has become a game-changer in the world of AI chatbots. Join us as we unravel the past, present, and future of AI chatbots and learn how they're poised to reshape our interactions with machines and redefine human-computer collaboration. Let's embark on this enlightening journey through the evolution of AI chatbots and the remarkable story of ChatGPT's development.
Table of contents
-
The Birth of Chatbots: Early Pioneers and Milestones
-
From ELIZA to GPT-3.5: The Advancements in Natural Language Processing
-
ChatGPT's Predecessors: A Brief History of GPT Models
-
The Role of Deep Learning in ChatGPT's Development
-
Data and Training: How ChatGPT Learns from Text Corpora
-
Fine-Tuning and Customization: Shaping ChatGPT's Behavior
-
Scaling Up: The Hardware and Infrastructure Behind ChatGPT
-
Challenges and Breakthroughs: Overcoming Limitations in ChatGPT
-
Ethical Concerns in ChatGPT's Evolution: Bias and Fairness
-
The Road Ahead: ChatGPT's Future and Potential Applications
-
Conclusion
The Birth of Chatbots: Early Pioneers and Milestones
In the realm of artificial intelligence, the concept of chatbots has a rich and intriguing history. These virtual conversational agents, which we often take for granted today, had humble beginnings and went through a series of significant milestones to become the sophisticated AI chatbots we encounter in our daily lives. In this segment, we will travel back in time and explore the birth of chatbots, paying homage to their early pioneers and pivotal milestones.
The Genesis of ELIZA (1966): Our journey begins in the 1960s when Joseph Weizenbaum, a computer scientist at MIT, developed one of the very first chatbots, ELIZA. ELIZA was designed to simulate a Rogerian psychotherapist, engaging users in text-based conversations about their feelings and problems. While basic by today's standards, ELIZA showcased the potential of computers to hold text-based conversations and provided a glimpse of what the future might hold.
Parry, the Paranoid Chatbot (1972): ELIZA was soon joined by another notable figure, Parry, created by Kenneth Colby. Parry was developed as a simulation of a paranoid individual and engaged users in text-based conversations. These early chatbots were limited in their capabilities but demonstrated early attempts at creating conversational agents.
Turing Test and the Loebner Prize (1991-Present): The Turing Test, proposed by Alan Turing in 1950, challenged the ability of machines to exhibit intelligent behavior indistinguishable from that of humans. The Loebner Prize, established in 1991, further encouraged the development of chatbots by offering an annual competition to determine the most human-like conversational AI. These events have played a significant role in driving advancements in chatbot technology.
The GPT Era and ChatGPT (2019-Present): Finally, we arrive at the present day, where advancements in deep learning and the advent of models like GPT-3 and GPT-3.5 have revolutionized chatbots. ChatGPT, based on the GPT architecture, represents a culmination of these developments, offering a level of conversational AI that was once only dreamed of.
These early pioneers and milestones in the world of chatbots have set the stage for the remarkable advancements we witness today. The journey from ELIZA to ChatGPT is a testament to human ingenuity and the relentless pursuit of creating more intelligent and capable chatbots. In the next section, we will explore the underlying technology and principles that have driven this evolution.
From ELIZA to GPT-3.5: The Advancements in Natural Language Processing
The field of natural language processing (NLP) has witnessed a remarkable journey of evolution, driven by advances in technology, data, and algorithms. As we explore the development of AI chatbots and, in particular, the evolution from ELIZA to GPT-3.5, it becomes evident that the progress in natural language processing is a key driving force behind the capabilities of these conversational agents. In this section, we'll delve into the significant advancements in NLP that have made this journey possible.
Early Rule-Based Systems (1960s-1970s): The birth of NLP and chatbots saw the emergence of rule-based systems, like ELIZA, which relied on a pre-defined set of rules to generate responses. These systems, though limited in scope, were groundbreaking at the time and laid the foundation for more sophisticated NLP.
Statistical Language Models (1990s-2000s): A major breakthrough came with the development of statistical language models that learned from vast amounts of text data. These models used probabilistic algorithms to determine the likelihood of a word or phrase occurring in a given context, greatly improving language understanding and generation.
The Deep Learning Revolution (2010s): The 2010s witnessed the rise of deep learning, particularly deep neural networks, which have revolutionized NLP. Models like Word2Vec and GloVe allowed machines to understand the context and meaning of words, while recurrent neural networks (RNNs) and long short-term memory networks (LSTMs) facilitated more robust text processing.
The GPT (Generative Pretrained Transformer) Series: Developed by OpenAI, the GPT series of models represents a breakthrough in NLP. Beginning with GPT-1, these models demonstrated the power of pretraining on large datasets and fine-tuning for specific tasks. GPT-3, and its successor, GPT-3.5, with its 175 billion parameters, have taken NLP to new heights, delivering human-like text generation and understanding on an unprecedented scale.
The evolution of natural language processing has been a journey of continuous innovation, fueled by the synergy of data, algorithms, and hardware. From rule-based systems to the astonishing capabilities of GPT-3.5, these advancements have paved the way for the development of increasingly sophisticated AI chatbots and have broadened the horizons of NLP, impacting various industries and applications. In the following sections, we will delve deeper into the specifics of GPT-3.5 and its role in reshaping the world of AI chatbots.
ChatGPT's Predecessors: A Brief History of GPT Models
Before the emergence of ChatGPT, a remarkable family of language models known as the "GPT" series paved the way for revolutionary advancements in natural language processing. In this section, we'll take a closer look at the history of GPT models, tracing their development and key milestones that led to the creation of ChatGPT.
GPT-1: The Pioneer (2018): The GPT series began with GPT-1, which stands for "Generative Pretrained Transformer." Developed by OpenAI, GPT-1 made waves in the field of NLP by demonstrating the potential of large-scale pretraining. With 117 million parameters, it could generate coherent and contextually relevant text by predicting the next word in a sentence, making it a promising step towards more capable AI chatbots.
GPT-3: A Giant Leap (2020): GPT-3, with a whopping 175 billion parameters, marked a giant leap in NLP. It showcased the true potential of transfer learning in NLP by achieving remarkable performance on a wide range of tasks, from language translation to question-answering and even creative text generation. GPT-3 captured the imagination of researchers, businesses, and developers, paving the way for AI chatbots like ChatGPT.
Fine-Tuning and Customization: Building on GPT-3 (2020-2021): Beyond GPT-3's incredible generative abilities, its fine-tuning capabilities allowed developers to customize it for specific applications. This introduced a new level of flexibility and adaptability, making it possible to fine-tune GPT-3 for use in chatbots, virtual assistants, and various other conversational AI applications.
The GPT series has marked a historic transformation in NLP, pushing the boundaries of what's possible with AI-driven language models. These models have become foundational in a wide range of applications, from chatbots to content generation, translation, and more. ChatGPT, with its origins deeply rooted in the GPT lineage, is a testament to the continuous innovation and progress in the field of natural language processing. In the following sections, we'll explore the unique characteristics and capabilities that make ChatGPT a standout in the world of conversational AI.
The Role of Deep Learning in ChatGPT's Development
Deep learning, a subfield of artificial intelligence, has played a central and transformative role in the development of ChatGPT and other advanced AI chatbots. In this section, we'll explore the significance of deep learning in ChatGPT's evolution, understanding the neural networks, architectures, and training methods that underpin its capabilities.
Neural Networks: The Building Blocks of Deep Learning: At the heart of deep learning are neural networks, computational models inspired by the human brain's structure. These networks consist of layers of interconnected artificial neurons that process data in a hierarchical manner. For ChatGPT, these neural networks serve as the foundation for understanding and generating human-like text.
Recurrent Neural Networks (RNNs): Early Language Processing: Recurrent Neural Networks, or RNNs, were among the first deep learning models applied to natural language processing tasks. RNNs have memory, which allows them to maintain context over a sequence of words, making them suitable for tasks like text generation and language understanding.
Long Short-Term Memory (LSTM) Networks: Handling Sequences: LSTMs are an evolution of RNNs designed to address the vanishing gradient problem and handle long sequences more effectively. They've been instrumental in improving the capabilities of AI chatbots like ChatGPT in understanding and generating coherent text.
Transformer Architecture: The Breakthrough in NLP (2017): The introduction of the Transformer architecture marked a major turning point in NLP and deep learning. Transformers employ self-attention mechanisms, allowing models to consider the importance of different words in a sentence and process sequences in parallel. This architecture, which GPT models are based on, has greatly improved the efficiency and effectiveness of language modeling.
Scaling Up: The Power of Model Size (Parametric Models): Another critical element is the scale of deep learning models. As seen in GPT-3.5, larger models with more parameters can capture more complex patterns in data, enabling them to perform at human-like levels in language understanding and generation.
Deep learning, with its neural networks, advanced architectures, and training methods, has propelled AI chatbots like ChatGPT to remarkable heights in natural language processing. The ability to understand context, generate coherent text, and adapt to specific tasks has been significantly enhanced by these deep learning techniques. As we explore the technology behind ChatGPT, we'll uncover how these principles are put into practice to create an AI chatbot capable of engaging in meaningful and human-like conversations.
Data and Training: How ChatGPT Learns from Text Corpora
The remarkable abilities of ChatGPT, and other advanced AI chatbots, are rooted in the extensive datasets they're trained on and the training methodologies employed. In this section, we'll uncover the crucial role of data and training in ChatGPT's development, shedding light on how it learns from vast text corpora to become a proficient conversational AI.
Data as the Lifeblood of ChatGPT: Data is the foundation of ChatGPT's learning process. To train an AI chatbot effectively, vast amounts of text data are required. These datasets can comprise a diverse range of sources, from books and articles to websites and social media posts, encompassing a wide array of languages and topics.
Fine-Tuning for Specific Tasks: Transfer Learning at Play: After pretraining, the model is fine-tuned for specific tasks or applications. This fine-tuning stage narrows down the AI's focus and helps it adapt to particular domains or user needs. It may involve using smaller, task-specific datasets and reinforcement learning techniques.
Diverse Data Sources for a Well-Rounded AI: ChatGPT's training data is carefully curated to provide a broad and diverse knowledge base. Incorporating data from multiple sources ensures the AI can handle a wide range of user queries and engage in discussions on various subjects.
Ethical Considerations and Data Selection: The choice of training data is critical in addressing ethical concerns such as bias and fairness. OpenAI and other developers must carefully curate data to avoid perpetuating biases and controversial content.
Ongoing Training and Updates: Continuous Learning: ChatGPT's learning is an ongoing process. Developers regularly update the model with new data to keep it relevant and accurate, reflecting changing trends, topics, and user expectations.
In the realm of AI chatbots like ChatGPT, data and training form the bedrock of their capabilities. Through vast and diverse text corpora and meticulous training methodologies, these models gain the knowledge and language proficiency needed to engage in coherent and context-aware conversations. In the subsequent sections, we will delve into the practical aspects of how ChatGPT transforms this training into its real-world applications and interactions.
Fine-Tuning and Customization: Shaping ChatGPT's Behavior
One of the key features that sets AI chatbots like ChatGPT apart is their ability to be fine-tuned and customized for specific tasks or behaviors. In this section, we'll explore the critical concept of fine-tuning and customization, which allows developers to shape ChatGPT's behavior to meet their specific requirements.
Understanding Fine-Tuning: Tailoring the Model: Fine-tuning is the process of adjusting a pretrained AI model like ChatGPT to be more specialized for a particular task or behavior. It involves exposing the model to task-specific data to adapt its behavior.
Task-Specific Datasets: Refining for Particular Use Cases: To fine-tune ChatGPT, developers use task-specific datasets. These datasets contain examples of the desired behavior or responses that they want the model to exhibit.
Reward-Based Reinforcement Learning: Improving Dialogue Flow: In some cases, reinforcement learning techniques are used during fine-tuning. The model is rewarded for generating better responses during interactions, helping it learn how to engage in more meaningful and context-aware conversations.
Limitation and Boundaries: Ethical and Safety Considerations: Fine-tuning is not without limitations. It's essential to set boundaries and ethical guidelines to ensure that the AI's behavior remains safe, responsible, and free from harmful or inappropriate content.
User-Defined Chatbots: Tailoring to Unique Needs: With fine-tuning and customization, developers can create user-specific chatbots tailored to unique needs, whether in customer support, content generation, or other applications.
Fine-tuning and customization are integral to shaping ChatGPT's behavior to make it a valuable tool for various industries and applications. It empowers developers to create AI chatbots that align with specific user needs, adopt distinct personas, and provide tailored responses. In the following sections, we will delve into the applications and use cases where fine-tuned ChatGPT shines, as well as the ethical considerations that come into play when shaping AI behavior.
Scaling Up: The Hardware and Infrastructure Behind ChatGPT
The capabilities of ChatGPT, a sophisticated AI chatbot, are not solely a result of advanced algorithms and training data but are also heavily dependent on the underlying hardware and infrastructure. In this section, we'll delve into the critical role that hardware and infrastructure play in scaling up the power and efficiency of ChatGPT.
Parallel Processing and GPUs: Training large language models like ChatGPT requires immense computational power. Graphics Processing Units (GPUs) are essential for parallel processing, enabling the model to analyze and generate text more quickly.
High-Performance Computing Clusters: Clusters of high-performance machines are used for training and running large language models efficiently. These clusters are designed to handle the enormous computational demands of AI models.
Tensor Processing Units (TPUs): In addition to GPUs, TPUs are becoming increasingly important for AI workloads. They are specialized hardware accelerators designed to speed up deep learning tasks, including training large models like ChatGPT.
Data Storage and Retrieval: Fast and reliable data storage and retrieval systems are crucial for handling the massive datasets used in training AI models. This infrastructure ensures that the model can access and process data efficiently.
Energy Efficiency: To manage the environmental impact of large-scale AI training, there is a growing emphasis on energy-efficient hardware and data centers. These developments aim to reduce the carbon footprint of AI models.
Cost Management: Training and running models like ChatGPT can be costly. Efficient infrastructure and cost management strategies are essential to make AI chatbots economically viable for developers and organizations.
Maintenance and Monitoring: The complex infrastructure supporting ChatGPT requires ongoing maintenance and monitoring to ensure optimal performance, security, and reliability.
The hardware and infrastructure behind ChatGPT represent a significant investment of resources. These elements are pivotal in enabling the development and deployment of large-scale AI chatbots that can process and generate text in real-time. As AI models continue to grow in size and complexity, the role of hardware and infrastructure becomes increasingly crucial for their success. In the subsequent sections, we will explore the real-world applications and impact of ChatGPT in various industries and scenarios.
Challenges and Breakthroughs: Overcoming Limitations in ChatGPT
While ChatGPT and similar AI chatbots have made remarkable strides in natural language processing and understanding, they are not without their challenges. In this section, we'll explore the limitations and the breakthroughs that have allowed ChatGPT to push the boundaries of conversational AI.
Limited Context Understanding: One significant challenge in AI chatbots is their ability to understand and maintain context over extended conversations. ChatGPT can sometimes lose track of the discussion topic or context.
Generating Incorrect or Incoherent Responses: AI chatbots may generate responses that are factually incorrect or incoherent. These issues can stem from the data they were trained on, leading to unreliable answers.
Ethical Considerations: The ethical implications of AI language models, such as privacy, safety, and bias, are ongoing challenges. Ensuring that AI chatbots adhere to ethical guidelines is a constant priority.
Scalability and Efficiency: Training and running large AI models like ChatGPT can be computationally expensive and energy-intensive. Researchers and organizations are working on improving the efficiency and environmental impact of AI infrastructure.
Multimodal Understanding: Expanding ChatGPT's understanding beyond text to include images, audio, and other modalities is a challenge that is being addressed in ongoing research.
Fine-Tuning Complexity: Fine-tuning AI models like ChatGPT can be complex and labor-intensive, requiring careful data curation and reinforcement learning techniques.
Breakthroughs and solutions to these challenges are actively researched and developed. Developers, researchers, and organizations are continuously working to improve the reliability, safety, and capabilities of AI chatbots like ChatGPT.
Ethical Concerns in ChatGPT's Evolution: Bias and Fairness
The development and deployment of AI chatbots like ChatGPT have raised important ethical considerations, particularly concerning issues of bias and fairness. In this section, we'll delve into these ethical concerns and the efforts made to address them in the evolution of ChatGPT.
Stereotypical and Offensive Responses: AI chatbots can inadvertently generate responses that are stereotypical, offensive, or discriminatory. Such content can be harmful, perpetuating harmful stereotypes and offensive language.
Impact on Vulnerable Populations: Biased or unfair responses generated by AI chatbots can disproportionately affect vulnerable or marginalized populations. Ensuring fair and respectful interactions is essential to avoid harm.
Lack of Context Awareness: ChatGPT may not always fully understand or consider the context and potential consequences of its responses, which can lead to responses that are insensitive or inappropriate.
User Feedback and Reporting: Ethical guidelines encourage users to provide feedback on problematic responses and content generated by AI chatbots. User feedback is a valuable tool in identifying and addressing issues.
Guidelines and Content Filtering: Developers implement guidelines and content filtering mechanisms to prevent AI chatbots from generating content that is harmful, inappropriate, or biased.
Addressing bias and fairness concerns in AI chatbots is an ongoing process, and developers, organizations, and researchers are committed to creating AI systems that respect ethical principles. The evolution of ChatGPT involves a continuous effort to improve fairness, reduce biases, and enhance the overall quality and safety of interactions with the AI. In the following sections, we will explore the real-world applications and use cases where these ethical considerations play a significant role.
The Road Ahead: ChatGPT's Future and Potential Applications
ChatGPT and similar AI chatbots have made significant strides in natural language processing, but their journey is far from over. In this section, we'll explore the future of ChatGPT and the exciting potential applications that lie ahead.
Customer Support and Service: AI chatbots like ChatGPT have the potential to revolutionize customer support. They can handle inquiries, troubleshoot problems, and provide assistance around the clock, offering cost-effective solutions for businesses.
Education and Tutoring: AI chatbots can act as personalized tutors, assisting students with homework, explaining complex concepts, and offering guidance in various subjects.
Content Generation: ChatGPT and similar models have applications in content creation, from generating news articles to marketing copy, streamlining the content production process.
Multimodal Conversations: The ability to understand and generate both text and images or audio could lead to richer and more interactive AI conversations.
Research and Development: AI chatbots can assist researchers by quickly accessing and summarizing information from vast datasets, accelerating the pace of scientific discovery.
Multilingual and Cross-Cultural Interaction: With improvements in language capabilities, AI chatbots can bridge language barriers and facilitate cross-cultural communication.
Ethical and Legal Consultation: AI chatbots may be used for ethical and legal consultation, offering insights into complex moral and legal issues or helping users navigate legal processes.
As AI chatbots like ChatGPT continue to evolve and mature, their applications will extend into more domains, making them valuable tools for individuals, businesses, and organizations. The road ahead involves addressing challenges, improving ethical guidelines, and enhancing the safety and reliability of these AI systems. The potential applications are diverse and promising, marking a new era in human-computer interaction. In the final sections of this series, we will explore practical examples and use cases that showcase the impact and capabilities of ChatGPT in action.
Conclusion
The evolution of AI chatbots, epitomized by ChatGPT, is a remarkable journey through the realms of natural language processing, deep learning, and ethical considerations. From their early pioneers like ELIZA to the powerful GPT models, AI chatbots have transformed the way we interact with machines and access information.
However, this evolution has not been without its challenges. Issues of bias, fairness, and ethical concerns are paramount, and developers are actively working to ensure that AI chatbots like ChatGPT adhere to the highest ethical standards and provide safe and respectful interactions.
As we look to the future, it's clear that AI chatbots will play an increasingly integral role in our lives, offering assistance, information, and companionship in a variety of fields. The development of ChatGPT is just one chapter in the ongoing story of AI's evolution, and it is certain that the best is yet to come.
Understanding COBIT 5 Foundation: A Comprehensive Overview
In the ever-evolving landscape of information technology, effective governance and management are paramount for organizations to thrive and succeed. One framework that stands out in this context is COBIT 5 Foundation. COBIT, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework designed to help organizations govern and manage their IT effectively.
COBIT has a rich history of evolution, adapting to the changing needs of the IT industry. From its inception to the present COBIT 5 Foundation, it has become a standard bearer for organizations seeking to align their IT strategies with their business goals. This framework provides a structured approach to IT governance and management, ensuring that enterprises can achieve optimal outcomes and manage risks effectively.
Whether you're new to COBIT 5 or looking to refresh your understanding, this comprehensive overview aims to be your guide to mastering the core concepts and practical applications of COBIT 5 Foundation. So, let's begin our exploration of COBIT 5 Foundation and its role in shaping the future of IT governance.
Table of contents
-
Historical Evolution of COBIT
-
COBIT 5 Framework Components
-
Key Concepts in COBIT 5
-
Benefits of Implementing COBIT 5 Foundation
-
COBIT 5 Principles
-
COBIT 5 Domains
-
COBIT 5 Process Reference Model
-
COBIT 5 Enablers
-
COBIT 5 Implementation Challenges
-
Real-Life Examples of COBIT 5 Success Stories
-
Conclusion
Historical Evolution of COBIT
The historical evolution of COBIT (Control Objectives for Information and Related Technologies) is a fascinating journey that showcases its development from a simple set of IT control objectives into a globally recognized framework for IT governance and management. Let's take a closer look at the key milestones in the history of COBIT:
COBIT 1.0 (1996): COBIT was initially introduced by ISACA (Information Systems Audit and Control Association) in 1996 as a set of IT control objectives to help organizations manage their IT processes and risks. This first version provided a basic structure for IT governance.
COBIT 2.0 (1998): The framework was updated in 1998 as COBIT 2.0. This version included a more comprehensive set of control objectives, making it a valuable tool for IT audit and control professionals.
COBIT 3.0 (2000): In the year 2000, COBIT 3.0 was released with a significant expansion in scope. This version integrated IT governance and management practices, helping organizations align IT with business goals more effectively.
COBIT 4.0 (2005): COBIT 4.0 introduced the concept of domains, processes, and IT-related goals, making it more structured and easier to apply in organizations. It was a pivotal step toward broader acceptance.
COBIT 4.1 (2007): This version, released in 2007, brought some refinements and updates to COBIT 4.0, making it more practical for implementation in real-world scenarios.
COBIT 5.0 Updates (2019): In 2019, COBIT was updated to further align with the evolving IT landscape and address contemporary challenges. This update included guidance on digital transformation and emerging technologies.
The historical evolution of COBIT reflects the changing landscape of IT governance, from a focus on control objectives to a comprehensive framework for aligning IT with business strategy, managing risks, and achieving operational excellence.
COBIT 5 Framework Components
The COBIT 5 framework consists of several key components, each of which plays a crucial role in helping organizations govern and manage their information and technology effectively. Understanding these components is essential for implementing COBIT 5 successfully. Here are the main components of the COBIT 5 framework:
Principles:
Meeting Stakeholder Needs: The first principle of COBIT 5 emphasizes the importance of aligning IT with the needs and expectations of stakeholders, whether they are internal or external to the organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single integrated framework to harmonize and simplify the governance of IT.
Enablers:
Processes: COBIT 5 defines a set of governance and management processes that help organizations achieve their objectives. These processes cover areas such as risk management, resource management, and performance management.
Principles, Policies, and Frameworks: These enablers provide the foundation for governance and management. They include the principles mentioned earlier, as well as policies, standards, and guidelines.
Information: Information is a key enabler, and COBIT 5 provides guidance on managing and optimizing the use of information in decision-making processes.
Services, Infrastructure, and Applications: These enablers relate to the physical and logical resources required to deliver IT services.
Governance and Management Processes:
COBIT 5 defines a comprehensive set of governance and management processes that organizations can use to align their IT with business goals, manage risks, and deliver value. Some of the processes include:
Evaluate, Direct, and Monitor (EDM) processes: These processes are primarily related to governance activities.
Align, Plan, and Organize (APO) processes: These processes focus on strategic planning and organizational structure.
Monitor, Evaluate, and Assess (MEA) processes: These processes assess the effectiveness of governance and management.
COBIT 5 Framework Model:
The COBIT 5 framework model provides a graphical representation of the principles, enablers, and processes, helping organizations visualize how they interact and support the achievement of objectives.
These components work together to provide a structured and holistic approach to IT governance and management. COBIT 5's principles guide decision-making, the enablers provide the resources and tools, and the governance and management processes offer a practical roadmap for implementation. By leveraging these components effectively, organizations can improve their IT practices, mitigate risks, and deliver value to stakeholders
Key Concepts in COBIT 5
COBIT 5, a comprehensive framework for governing and managing enterprise IT, is built upon several key concepts that are fundamental to understanding and implementing the framework effectively. Here are the key concepts in COBIT 5:
Governance and Management: COBIT 5 distinguishes between governance and management. Governance is primarily concerned with decision-making and ensuring that IT aligns with business goals. Management, on the other hand, involves the execution of those decisions and the day-to-day operation of IT processes.
End-to-End Coverage: COBIT 5 advocates for a holistic approach to IT governance, covering all aspects of the enterprise. It's not limited to specific processes or departments; rather, it spans the entire organization.
Framework for the Governance and Management of Enterprise IT: COBIT 5 provides a structured framework that encompasses IT governance and management practices. This framework offers a systematic approach to achieving organizational goals.
Enabler: Enablers in COBIT 5 are the factors that facilitate or support the implementation of governance and management. These include processes, principles, policies, organizational structures, culture, ethics, and behavior, among others.
Principles: COBIT 5 is guided by seven key principles:
Meeting Stakeholder Needs
Covering the Enterprise End-to-End
Separating Governance from Management
Tailoring to the Enterprise
Implementing a Governance System
Domains: COBIT 5 defines four domains, each encompassing a set of processes and activities:
Lifecycle Approach: COBIT 5 advocates for a lifecycle approach to IT governance and management, emphasizing that governance and management are continuous and cyclical processes rather than one-time events.
Information Governance: Information is a critical asset in IT governance, and COBIT 5 underscores the importance of effectively managing and using information in decision-making processes.
Understanding these key concepts in COBIT 5 is essential for organizations looking to enhance their IT governance and management practices. These concepts provide the foundation for implementing the framework and aligning IT with business objectives while meeting the needs of various stakeholders.
Benefits of Implementing COBIT 5 Foundation
Implementing COBIT 5 Foundation can bring a wide range of benefits to organizations. Here are some of the key advantages of adopting the COBIT 5 framework for IT governance and management:
Enhanced IT Governance: COBIT 5 provides a structured and holistic approach to IT governance, helping organizations make informed decisions and align IT strategies with business objectives. This results in more effective governance practices.
Improved Risk Management: COBIT 5 offers guidelines and practices for identifying, assessing, and managing IT-related risks. Implementing COBIT 5 can enhance an organization's ability to mitigate and respond to risks effectively.
Alignment with Stakeholder Needs: COBIT 5 emphasizes the importance of meeting the needs and expectations of stakeholders. By aligning IT activities with stakeholder requirements, organizations can enhance their reputation and relationships.
Increased Efficiency and Effectiveness: COBIT 5 provides a clear framework for organizing and optimizing IT processes. This leads to increased efficiency in IT operations and the delivery of services, ultimately resulting in cost savings.
Better Compliance: COBIT 5 includes guidelines for ensuring regulatory compliance and adherence to industry standards. Implementing COBIT 5 can help organizations avoid non-compliance issues and associated penalties.
Optimized Resource Management: COBIT 5 enables organizations to manage IT resources efficiently, including people, technology, and information. This ensures that resources are used effectively to achieve business goals.
Enhanced Decision-Making: COBIT 5 offers a structured framework for decision-making, promoting evidence-based choices. This leads to better decision quality and more favorable outcomes.
Continuous Improvement: COBIT 5 promotes a culture of continual improvement in IT governance and management. Organizations can adapt to changing circumstances and stay agile in the face of evolving technology and business needs.
Mitigation of IT-related Failures: By following COBIT 5's best practices, organizations can reduce the likelihood of IT-related failures, such as system outages or security breaches.
In summary, implementing COBIT 5 Foundation offers organizations a structured and comprehensive approach to IT governance and management. It not only helps align IT with business goals but also results in better risk management, stakeholder satisfaction, and overall organizational performance.
COBIT 5 Principles
COBIT 5 is built upon seven key principles, which provide the foundation for effective IT governance and management. Here are five of those principles:
Meeting Stakeholder Needs: The first principle emphasizes the importance of aligning IT with the needs and expectations of stakeholders, both internal and external. Organizations should prioritize understanding and addressing the unique requirements of these stakeholders to ensure their satisfaction and support.
Covering the Enterprise End-to-End: This principle advocates for a holistic approach to IT governance and management. It highlights the need to consider all aspects of the enterprise, from strategy and planning to daily operations, to ensure that IT aligns with the entire organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single, integrated framework for IT governance and management. By applying a unified framework, organizations can avoid duplication, inconsistencies, and confusion, making IT governance more efficient and effective.
Enabling a Holistic Approach: This principle underscores the importance of adopting a comprehensive and integrated approach to IT governance. Organizations should consider the full spectrum of factors, including processes, culture, organizational structures, and information, to achieve effective governance and management.
These principles serve as guiding tenets for organizations looking to establish effective IT governance and management practices using the COBIT 5 framework. They provide a strategic and philosophical basis for decision-making and implementation, helping organizations meet their objectives and deliver value to stakeholders.
COBIT 5 Domains
COBIT 5 organizes its guidance and processes into four primary domains, each of which represents a distinct area of IT governance and management. These domains are designed to help organizations address various aspects of IT effectively. The four domains in COBIT 5 are as follows:
Governance (EDM - Evaluate, Direct, and Monitor): The Governance domain focuses on the high-level, strategic aspects of IT governance. It is responsible for ensuring that stakeholder needs and expectations are met, and that the enterprise's strategic objectives are aligned with IT. This domain includes processes related to evaluating the current state of IT, directing IT to achieve its goals, and monitoring IT performance. Key processes within this domain include:
Evaluate, Direct, and Monitor (EDM)
Ensure Governance Framework Setting and Maintenance
Ensure Stakeholder Value Delivery
Ensure Performance Optimization
Management (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support): The Management domain encompasses the processes that support the actual planning, implementation, and operation of IT within the organization. It ensures that IT resources are organized and deployed effectively. The Management domain is divided into three subdomains:
Align, Plan, and Organize (APO): This subdomain is responsible for aligning IT with the organization's strategic objectives and planning IT activities. Key processes include strategic planning, portfolio management, and IT budgeting.
Build, Acquire, and Implement (BAI): This subdomain covers the processes related to developing, acquiring, and implementing IT solutions and services. It includes processes like project management, system development, and IT procurement.
Information (MEA - Monitor, Evaluate, and Assess): The Information domain is responsible for ensuring the effective management of information as an asset. It involves processes for monitoring and assessing the quality and security of information. Key processes within this domain include:
Monitor, Evaluate, and Assess (MEA)
Ensure Stakeholder Value Delivery
Ensure Risk Optimization
Supporting Processes (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support, MEA - Monitor, Evaluate, and Assess): These processes are common to multiple domains and provide support for the primary processes in Governance, Management, and Information. They are not standalone domains but are essential for the smooth operation of IT governance and management. These supporting processes include areas like compliance, human resources, and knowledge management.
These four domains, along with their respective processes, help organizations implement comprehensive IT governance and management practices using the COBIT 5 framework. Each domain addresses specific aspects of IT, ensuring that IT aligns with business goals, delivers value, and is governed effectively.
COBIT 5 Process Reference Model
The COBIT 5 Process Reference Model is a core component of the COBIT 5 framework. It provides a structured and comprehensive framework for understanding and implementing IT governance and management processes within an organization. The model is designed to be flexible and scalable, allowing organizations to tailor it to their specific needs and requirements. Here's an overview of the COBIT 5 Process Reference Model:
Processes: The model is organized into a set of processes that cover various aspects of IT governance and management. These processes are divided into five domains: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
Processes and Activities: Within each domain, the COBIT 5 Process Reference Model defines specific processes and associated activities. These activities provide detailed guidance on how to implement and execute each process effectively.
Inputs and Outputs: The model also specifies the inputs and outputs of each process, helping organizations understand what information, resources, and deliverables are required to execute a process and what is generated as a result.
Responsibilities: The model identifies the roles and responsibilities associated with each process, ensuring that organizations have clear lines of accountability.
Interactions: It illustrates how processes within different domains interact with each other. This promotes a holistic and integrated approach to IT governance and management.
Maturity and Capability: COBIT 5 includes maturity and capability models to assess the maturity of an organization's processes and its capability to manage them effectively.
The COBIT 5 Process Reference Model serves as a practical tool for organizations to assess, plan, and improve their IT governance and management practices. It promotes transparency, alignment with business objectives, and the continuous improvement of IT processes, ultimately leading to better governance, risk management, and value delivery.
COBIT 5 Enablers
COBIT 5 emphasizes the importance of enablers as factors that support effective IT governance and management within an organization. These enablers provide the resources, tools, and structures necessary to achieve organizational objectives. COBIT 5 identifies seven primary categories of enablers that work together to facilitate the implementation of IT governance and management practices. Here are the COBIT 5 enablers:
Processes: COBIT 5 identifies a set of IT governance and management processes that are essential for aligning IT with business goals and objectives. These processes provide the practical steps and activities for governing and managing IT effectively.
Organizational Structures: Organizational structures and roles are enablers that define how responsibilities are distributed and delegated within the organization. They include roles, responsibilities, and reporting lines, ensuring clear accountability.
Information: Information is a critical enabler as it provides the data and knowledge necessary for making informed decisions. Effective information management, data quality, and information security are important aspects of this enabler.
Services, Infrastructure, and Applications: This enabler includes the physical and logical resources required to support IT services and applications. It covers areas such as infrastructure, applications, and IT service management tools.
People, Skills, and Competencies: People are at the heart of IT governance and management. This enabler focuses on ensuring that the organization has the right people with the right skills and competencies to support IT activities effectively.
These seven enablers collectively provide the framework and resources required for organizations to align their IT with business goals, manage risks, deliver value, and govern IT effectively. COBIT 5 emphasizes that these enablers are interrelated, and the successful implementation of IT governance and management practices requires a harmonious integration of all enablers. The specific application of these enablers will vary based on an organization's unique context and objectives.
COBIT 5 Implementation Challenges
Implementing COBIT 5 in an organization can bring numerous benefits, but it also presents several challenges. These challenges can vary depending on the organization's size, industry, and existing IT governance practices. Here are some common challenges associated with COBIT 5 implementation:
Resistance to Change: One of the most significant challenges is getting buy-in from all levels of the organization. Employees and management may be resistant to adopting new governance and management practices.
Resource Allocation: Implementing COBIT 5 requires dedicating time, people, and financial resources. Finding the necessary resources can be a challenge, especially for smaller organizations with limited budgets.
Skills and Training: Implementing COBIT 5 may require training and skill development for employees. Ensuring that staff has the necessary competencies can be a challenge, especially in rapidly changing IT environments.
Customization: COBIT 5 is a framework, and it needs to be tailored to the specific needs and context of each organization. Finding the right balance between customization and adherence to COBIT 5's principles can be challenging.
Measuring Success: Defining and measuring Key Performance Indicators (KPIs) and Critical Success Factors (CSFs) to evaluate the success of COBIT 5 implementation can be challenging. Identifying meaningful metrics and benchmarks for improvement is essential.
Top-Down vs. Bottom-Up Approach: Deciding whether to implement COBIT 5 top-down (starting with governance) or bottom-up (starting with management processes) is a strategic challenge that organizations must address.
Sustainability: Maintaining the momentum and ensuring that COBIT 5 practices continue to be effective over the long term can be challenging. Often, organizations face the risk of reverting to old practices after initial enthusiasm wanes.
Risk Management: While COBIT 5 provides guidance on risk management, identifying and addressing potential risks associated with implementation itself is a challenge.
To overcome these challenges, organizations should develop a well-defined implementation plan, engage with stakeholders, provide adequate training and support, and continuously monitor and adapt their COBIT 5 implementation as needed. It's also essential to recognize that COBIT 5 implementation is an ongoing process that requires commitment and adaptability to achieve its intended benefits.
Real-Life Examples of COBIT 5 Success Stories
COBIT 5 has been successfully implemented in numerous organizations across various industries, helping them achieve their IT governance and management objectives. Here are some real-life examples of organizations that have experienced success with COBIT 5:
ExxonMobil: ExxonMobil, one of the world's largest multinational oil and gas corporations, used COBIT 5 to enhance its IT governance and risk management. They successfully implemented COBIT 5's principles and processes to align IT with business objectives and improve risk mitigation strategies.
Dubai Customs: Dubai Customs, a government agency responsible for facilitating trade in the Emirate of Dubai, implemented COBIT 5 to enhance its IT service management practices. They used COBIT 5 to streamline IT processes, resulting in improved service delivery and customer satisfaction.
Walmart: Walmart, a global retail giant, leveraged COBIT 5 to optimize IT governance and management processes across its vast network of stores and data centers. COBIT 5 helped Walmart improve the efficiency of IT operations, reduce risks, and enhance customer experiences through effective supply chain management and data security.
US Department of Defense (DoD): The US DoD adopted COBIT 5 as part of its approach to IT governance and cybersecurity. COBIT 5 helped the DoD establish a standardized framework for managing and securing its IT assets, ultimately improving its information security posture.
AXA Group: AXA, a multinational insurance company, implemented COBIT 5 to align IT processes with business needs. By using COBIT 5, AXA improved risk management, IT performance, and the overall quality of IT services.
Government of Malaysia: The Malaysian government adopted COBIT 5 to enhance IT governance practices across various government agencies. This initiative has led to improved transparency, accountability, and effectiveness in IT management.
University of Waterloo: The University of Waterloo in Canada used COBIT 5 to optimize its IT governance practices. The implementation of COBIT 5 led to more effective IT service management, streamlined IT processes, and improved alignment with academic and administrative goals.
South African Revenue Service (SARS): SARS, the tax collection agency in South Africa, adopted COBIT 5 to enhance its IT governance and risk management practices. The use of COBIT 5 has resulted in better control over taxpayer data and improved compliance with tax regulations.
Vattenfall: Vattenfall, a Swedish multinational energy company, implemented COBIT 5 to enhance its IT governance and cybersecurity practices. COBIT 5 helped Vattenfall align its IT strategies with business objectives and strengthen its defenses against cyber threats.
Central Bank of Nigeria: The Central Bank of Nigeria utilized COBIT 5 to improve its IT governance practices and enhance the security and integrity of the country's financial systems. COBIT 5 has played a critical role in ensuring the stability and resilience of Nigeria's financial infrastructure.
These examples illustrate the versatility and effectiveness of COBIT 5 across various industries and sectors. Organizations have leveraged COBIT 5 to align IT with their strategic goals, enhance IT governance, manage risks, and deliver better services to their stakeholders. These success stories showcase the framework's adaptability and its ability to drive positive outcomes in diverse organizational contexts
Conclusion
In conclusion, COBIT 5 is a comprehensive and widely recognized framework for IT governance and management that provides organizations with the tools and guidance they need to align their IT functions with business objectives, manage risks, and deliver value to stakeholders. It is built on a foundation of key principles, a well-structured process reference model, and seven enablers that collectively support effective governance and management.
As technology continues to play a pivotal role in the success of organizations, COBIT 5 remains a valuable framework for those seeking a structured and systematic approach to IT governance and management. By adopting and customizing COBIT 5 to their specific needs, organizations can navigate the complexities of the digital landscape and ensure that their IT functions are aligned with their broader business strategies.
Read More
In the ever-evolving landscape of information technology, effective governance and management are paramount for organizations to thrive and succeed. One framework that stands out in this context is COBIT 5 Foundation. COBIT, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework designed to help organizations govern and manage their IT effectively.
COBIT has a rich history of evolution, adapting to the changing needs of the IT industry. From its inception to the present COBIT 5 Foundation, it has become a standard bearer for organizations seeking to align their IT strategies with their business goals. This framework provides a structured approach to IT governance and management, ensuring that enterprises can achieve optimal outcomes and manage risks effectively.
Whether you're new to COBIT 5 or looking to refresh your understanding, this comprehensive overview aims to be your guide to mastering the core concepts and practical applications of COBIT 5 Foundation. So, let's begin our exploration of COBIT 5 Foundation and its role in shaping the future of IT governance.
Table of contents
-
Historical Evolution of COBIT
-
COBIT 5 Framework Components
-
Key Concepts in COBIT 5
-
Benefits of Implementing COBIT 5 Foundation
-
COBIT 5 Principles
-
COBIT 5 Domains
-
COBIT 5 Process Reference Model
-
COBIT 5 Enablers
-
COBIT 5 Implementation Challenges
-
Real-Life Examples of COBIT 5 Success Stories
-
Conclusion
Historical Evolution of COBIT
The historical evolution of COBIT (Control Objectives for Information and Related Technologies) is a fascinating journey that showcases its development from a simple set of IT control objectives into a globally recognized framework for IT governance and management. Let's take a closer look at the key milestones in the history of COBIT:
COBIT 1.0 (1996): COBIT was initially introduced by ISACA (Information Systems Audit and Control Association) in 1996 as a set of IT control objectives to help organizations manage their IT processes and risks. This first version provided a basic structure for IT governance.
COBIT 2.0 (1998): The framework was updated in 1998 as COBIT 2.0. This version included a more comprehensive set of control objectives, making it a valuable tool for IT audit and control professionals.
COBIT 3.0 (2000): In the year 2000, COBIT 3.0 was released with a significant expansion in scope. This version integrated IT governance and management practices, helping organizations align IT with business goals more effectively.
COBIT 4.0 (2005): COBIT 4.0 introduced the concept of domains, processes, and IT-related goals, making it more structured and easier to apply in organizations. It was a pivotal step toward broader acceptance.
COBIT 4.1 (2007): This version, released in 2007, brought some refinements and updates to COBIT 4.0, making it more practical for implementation in real-world scenarios.
COBIT 5.0 Updates (2019): In 2019, COBIT was updated to further align with the evolving IT landscape and address contemporary challenges. This update included guidance on digital transformation and emerging technologies.
The historical evolution of COBIT reflects the changing landscape of IT governance, from a focus on control objectives to a comprehensive framework for aligning IT with business strategy, managing risks, and achieving operational excellence.
COBIT 5 Framework Components
The COBIT 5 framework consists of several key components, each of which plays a crucial role in helping organizations govern and manage their information and technology effectively. Understanding these components is essential for implementing COBIT 5 successfully. Here are the main components of the COBIT 5 framework:
Principles:
Meeting Stakeholder Needs: The first principle of COBIT 5 emphasizes the importance of aligning IT with the needs and expectations of stakeholders, whether they are internal or external to the organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single integrated framework to harmonize and simplify the governance of IT.
Enablers:
Processes: COBIT 5 defines a set of governance and management processes that help organizations achieve their objectives. These processes cover areas such as risk management, resource management, and performance management.
Principles, Policies, and Frameworks: These enablers provide the foundation for governance and management. They include the principles mentioned earlier, as well as policies, standards, and guidelines.
Information: Information is a key enabler, and COBIT 5 provides guidance on managing and optimizing the use of information in decision-making processes.
Services, Infrastructure, and Applications: These enablers relate to the physical and logical resources required to deliver IT services.
Governance and Management Processes:
COBIT 5 defines a comprehensive set of governance and management processes that organizations can use to align their IT with business goals, manage risks, and deliver value. Some of the processes include:
Evaluate, Direct, and Monitor (EDM) processes: These processes are primarily related to governance activities.
Align, Plan, and Organize (APO) processes: These processes focus on strategic planning and organizational structure.
Monitor, Evaluate, and Assess (MEA) processes: These processes assess the effectiveness of governance and management.
COBIT 5 Framework Model:
The COBIT 5 framework model provides a graphical representation of the principles, enablers, and processes, helping organizations visualize how they interact and support the achievement of objectives.
These components work together to provide a structured and holistic approach to IT governance and management. COBIT 5's principles guide decision-making, the enablers provide the resources and tools, and the governance and management processes offer a practical roadmap for implementation. By leveraging these components effectively, organizations can improve their IT practices, mitigate risks, and deliver value to stakeholders
Key Concepts in COBIT 5
COBIT 5, a comprehensive framework for governing and managing enterprise IT, is built upon several key concepts that are fundamental to understanding and implementing the framework effectively. Here are the key concepts in COBIT 5:
Governance and Management: COBIT 5 distinguishes between governance and management. Governance is primarily concerned with decision-making and ensuring that IT aligns with business goals. Management, on the other hand, involves the execution of those decisions and the day-to-day operation of IT processes.
End-to-End Coverage: COBIT 5 advocates for a holistic approach to IT governance, covering all aspects of the enterprise. It's not limited to specific processes or departments; rather, it spans the entire organization.
Framework for the Governance and Management of Enterprise IT: COBIT 5 provides a structured framework that encompasses IT governance and management practices. This framework offers a systematic approach to achieving organizational goals.
Enabler: Enablers in COBIT 5 are the factors that facilitate or support the implementation of governance and management. These include processes, principles, policies, organizational structures, culture, ethics, and behavior, among others.
Principles: COBIT 5 is guided by seven key principles:
Meeting Stakeholder Needs
Covering the Enterprise End-to-End
Separating Governance from Management
Tailoring to the Enterprise
Implementing a Governance System
Domains: COBIT 5 defines four domains, each encompassing a set of processes and activities:
Lifecycle Approach: COBIT 5 advocates for a lifecycle approach to IT governance and management, emphasizing that governance and management are continuous and cyclical processes rather than one-time events.
Information Governance: Information is a critical asset in IT governance, and COBIT 5 underscores the importance of effectively managing and using information in decision-making processes.
Understanding these key concepts in COBIT 5 is essential for organizations looking to enhance their IT governance and management practices. These concepts provide the foundation for implementing the framework and aligning IT with business objectives while meeting the needs of various stakeholders.
Benefits of Implementing COBIT 5 Foundation
Implementing COBIT 5 Foundation can bring a wide range of benefits to organizations. Here are some of the key advantages of adopting the COBIT 5 framework for IT governance and management:
Enhanced IT Governance: COBIT 5 provides a structured and holistic approach to IT governance, helping organizations make informed decisions and align IT strategies with business objectives. This results in more effective governance practices.
Improved Risk Management: COBIT 5 offers guidelines and practices for identifying, assessing, and managing IT-related risks. Implementing COBIT 5 can enhance an organization's ability to mitigate and respond to risks effectively.
Alignment with Stakeholder Needs: COBIT 5 emphasizes the importance of meeting the needs and expectations of stakeholders. By aligning IT activities with stakeholder requirements, organizations can enhance their reputation and relationships.
Increased Efficiency and Effectiveness: COBIT 5 provides a clear framework for organizing and optimizing IT processes. This leads to increased efficiency in IT operations and the delivery of services, ultimately resulting in cost savings.
Better Compliance: COBIT 5 includes guidelines for ensuring regulatory compliance and adherence to industry standards. Implementing COBIT 5 can help organizations avoid non-compliance issues and associated penalties.
Optimized Resource Management: COBIT 5 enables organizations to manage IT resources efficiently, including people, technology, and information. This ensures that resources are used effectively to achieve business goals.
Enhanced Decision-Making: COBIT 5 offers a structured framework for decision-making, promoting evidence-based choices. This leads to better decision quality and more favorable outcomes.
Continuous Improvement: COBIT 5 promotes a culture of continual improvement in IT governance and management. Organizations can adapt to changing circumstances and stay agile in the face of evolving technology and business needs.
Mitigation of IT-related Failures: By following COBIT 5's best practices, organizations can reduce the likelihood of IT-related failures, such as system outages or security breaches.
In summary, implementing COBIT 5 Foundation offers organizations a structured and comprehensive approach to IT governance and management. It not only helps align IT with business goals but also results in better risk management, stakeholder satisfaction, and overall organizational performance.
COBIT 5 Principles
COBIT 5 is built upon seven key principles, which provide the foundation for effective IT governance and management. Here are five of those principles:
Meeting Stakeholder Needs: The first principle emphasizes the importance of aligning IT with the needs and expectations of stakeholders, both internal and external. Organizations should prioritize understanding and addressing the unique requirements of these stakeholders to ensure their satisfaction and support.
Covering the Enterprise End-to-End: This principle advocates for a holistic approach to IT governance and management. It highlights the need to consider all aspects of the enterprise, from strategy and planning to daily operations, to ensure that IT aligns with the entire organization.
Applying a Single Integrated Framework: COBIT 5 promotes the use of a single, integrated framework for IT governance and management. By applying a unified framework, organizations can avoid duplication, inconsistencies, and confusion, making IT governance more efficient and effective.
Enabling a Holistic Approach: This principle underscores the importance of adopting a comprehensive and integrated approach to IT governance. Organizations should consider the full spectrum of factors, including processes, culture, organizational structures, and information, to achieve effective governance and management.
These principles serve as guiding tenets for organizations looking to establish effective IT governance and management practices using the COBIT 5 framework. They provide a strategic and philosophical basis for decision-making and implementation, helping organizations meet their objectives and deliver value to stakeholders.
COBIT 5 Domains
COBIT 5 organizes its guidance and processes into four primary domains, each of which represents a distinct area of IT governance and management. These domains are designed to help organizations address various aspects of IT effectively. The four domains in COBIT 5 are as follows:
Governance (EDM - Evaluate, Direct, and Monitor): The Governance domain focuses on the high-level, strategic aspects of IT governance. It is responsible for ensuring that stakeholder needs and expectations are met, and that the enterprise's strategic objectives are aligned with IT. This domain includes processes related to evaluating the current state of IT, directing IT to achieve its goals, and monitoring IT performance. Key processes within this domain include:
Evaluate, Direct, and Monitor (EDM)
Ensure Governance Framework Setting and Maintenance
Ensure Stakeholder Value Delivery
Ensure Performance Optimization
Management (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support): The Management domain encompasses the processes that support the actual planning, implementation, and operation of IT within the organization. It ensures that IT resources are organized and deployed effectively. The Management domain is divided into three subdomains:
Align, Plan, and Organize (APO): This subdomain is responsible for aligning IT with the organization's strategic objectives and planning IT activities. Key processes include strategic planning, portfolio management, and IT budgeting.
Build, Acquire, and Implement (BAI): This subdomain covers the processes related to developing, acquiring, and implementing IT solutions and services. It includes processes like project management, system development, and IT procurement.
Information (MEA - Monitor, Evaluate, and Assess): The Information domain is responsible for ensuring the effective management of information as an asset. It involves processes for monitoring and assessing the quality and security of information. Key processes within this domain include:
Monitor, Evaluate, and Assess (MEA)
Ensure Stakeholder Value Delivery
Ensure Risk Optimization
Supporting Processes (APO - Align, Plan, and Organize, BAI - Build, Acquire, and Implement, DSS - Deliver, Service, and Support, MEA - Monitor, Evaluate, and Assess): These processes are common to multiple domains and provide support for the primary processes in Governance, Management, and Information. They are not standalone domains but are essential for the smooth operation of IT governance and management. These supporting processes include areas like compliance, human resources, and knowledge management.
These four domains, along with their respective processes, help organizations implement comprehensive IT governance and management practices using the COBIT 5 framework. Each domain addresses specific aspects of IT, ensuring that IT aligns with business goals, delivers value, and is governed effectively.
COBIT 5 Process Reference Model
The COBIT 5 Process Reference Model is a core component of the COBIT 5 framework. It provides a structured and comprehensive framework for understanding and implementing IT governance and management processes within an organization. The model is designed to be flexible and scalable, allowing organizations to tailor it to their specific needs and requirements. Here's an overview of the COBIT 5 Process Reference Model:
Processes: The model is organized into a set of processes that cover various aspects of IT governance and management. These processes are divided into five domains: Evaluate, Direct, and Monitor (EDM); Align, Plan, and Organize (APO); Build, Acquire, and Implement (BAI); Deliver, Service, and Support (DSS); and Monitor, Evaluate, and Assess (MEA).
Processes and Activities: Within each domain, the COBIT 5 Process Reference Model defines specific processes and associated activities. These activities provide detailed guidance on how to implement and execute each process effectively.
Inputs and Outputs: The model also specifies the inputs and outputs of each process, helping organizations understand what information, resources, and deliverables are required to execute a process and what is generated as a result.
Responsibilities: The model identifies the roles and responsibilities associated with each process, ensuring that organizations have clear lines of accountability.
Interactions: It illustrates how processes within different domains interact with each other. This promotes a holistic and integrated approach to IT governance and management.
Maturity and Capability: COBIT 5 includes maturity and capability models to assess the maturity of an organization's processes and its capability to manage them effectively.
The COBIT 5 Process Reference Model serves as a practical tool for organizations to assess, plan, and improve their IT governance and management practices. It promotes transparency, alignment with business objectives, and the continuous improvement of IT processes, ultimately leading to better governance, risk management, and value delivery.
COBIT 5 Enablers
COBIT 5 emphasizes the importance of enablers as factors that support effective IT governance and management within an organization. These enablers provide the resources, tools, and structures necessary to achieve organizational objectives. COBIT 5 identifies seven primary categories of enablers that work together to facilitate the implementation of IT governance and management practices. Here are the COBIT 5 enablers:
Processes: COBIT 5 identifies a set of IT governance and management processes that are essential for aligning IT with business goals and objectives. These processes provide the practical steps and activities for governing and managing IT effectively.
Organizational Structures: Organizational structures and roles are enablers that define how responsibilities are distributed and delegated within the organization. They include roles, responsibilities, and reporting lines, ensuring clear accountability.
Information: Information is a critical enabler as it provides the data and knowledge necessary for making informed decisions. Effective information management, data quality, and information security are important aspects of this enabler.
Services, Infrastructure, and Applications: This enabler includes the physical and logical resources required to support IT services and applications. It covers areas such as infrastructure, applications, and IT service management tools.
People, Skills, and Competencies: People are at the heart of IT governance and management. This enabler focuses on ensuring that the organization has the right people with the right skills and competencies to support IT activities effectively.
These seven enablers collectively provide the framework and resources required for organizations to align their IT with business goals, manage risks, deliver value, and govern IT effectively. COBIT 5 emphasizes that these enablers are interrelated, and the successful implementation of IT governance and management practices requires a harmonious integration of all enablers. The specific application of these enablers will vary based on an organization's unique context and objectives.
COBIT 5 Implementation Challenges
Implementing COBIT 5 in an organization can bring numerous benefits, but it also presents several challenges. These challenges can vary depending on the organization's size, industry, and existing IT governance practices. Here are some common challenges associated with COBIT 5 implementation:
Resistance to Change: One of the most significant challenges is getting buy-in from all levels of the organization. Employees and management may be resistant to adopting new governance and management practices.
Resource Allocation: Implementing COBIT 5 requires dedicating time, people, and financial resources. Finding the necessary resources can be a challenge, especially for smaller organizations with limited budgets.
Skills and Training: Implementing COBIT 5 may require training and skill development for employees. Ensuring that staff has the necessary competencies can be a challenge, especially in rapidly changing IT environments.
Customization: COBIT 5 is a framework, and it needs to be tailored to the specific needs and context of each organization. Finding the right balance between customization and adherence to COBIT 5's principles can be challenging.
Measuring Success: Defining and measuring Key Performance Indicators (KPIs) and Critical Success Factors (CSFs) to evaluate the success of COBIT 5 implementation can be challenging. Identifying meaningful metrics and benchmarks for improvement is essential.
Top-Down vs. Bottom-Up Approach: Deciding whether to implement COBIT 5 top-down (starting with governance) or bottom-up (starting with management processes) is a strategic challenge that organizations must address.
Sustainability: Maintaining the momentum and ensuring that COBIT 5 practices continue to be effective over the long term can be challenging. Often, organizations face the risk of reverting to old practices after initial enthusiasm wanes.
Risk Management: While COBIT 5 provides guidance on risk management, identifying and addressing potential risks associated with implementation itself is a challenge.
To overcome these challenges, organizations should develop a well-defined implementation plan, engage with stakeholders, provide adequate training and support, and continuously monitor and adapt their COBIT 5 implementation as needed. It's also essential to recognize that COBIT 5 implementation is an ongoing process that requires commitment and adaptability to achieve its intended benefits.
Real-Life Examples of COBIT 5 Success Stories
COBIT 5 has been successfully implemented in numerous organizations across various industries, helping them achieve their IT governance and management objectives. Here are some real-life examples of organizations that have experienced success with COBIT 5:
ExxonMobil: ExxonMobil, one of the world's largest multinational oil and gas corporations, used COBIT 5 to enhance its IT governance and risk management. They successfully implemented COBIT 5's principles and processes to align IT with business objectives and improve risk mitigation strategies.
Dubai Customs: Dubai Customs, a government agency responsible for facilitating trade in the Emirate of Dubai, implemented COBIT 5 to enhance its IT service management practices. They used COBIT 5 to streamline IT processes, resulting in improved service delivery and customer satisfaction.
Walmart: Walmart, a global retail giant, leveraged COBIT 5 to optimize IT governance and management processes across its vast network of stores and data centers. COBIT 5 helped Walmart improve the efficiency of IT operations, reduce risks, and enhance customer experiences through effective supply chain management and data security.
US Department of Defense (DoD): The US DoD adopted COBIT 5 as part of its approach to IT governance and cybersecurity. COBIT 5 helped the DoD establish a standardized framework for managing and securing its IT assets, ultimately improving its information security posture.
AXA Group: AXA, a multinational insurance company, implemented COBIT 5 to align IT processes with business needs. By using COBIT 5, AXA improved risk management, IT performance, and the overall quality of IT services.
Government of Malaysia: The Malaysian government adopted COBIT 5 to enhance IT governance practices across various government agencies. This initiative has led to improved transparency, accountability, and effectiveness in IT management.
University of Waterloo: The University of Waterloo in Canada used COBIT 5 to optimize its IT governance practices. The implementation of COBIT 5 led to more effective IT service management, streamlined IT processes, and improved alignment with academic and administrative goals.
South African Revenue Service (SARS): SARS, the tax collection agency in South Africa, adopted COBIT 5 to enhance its IT governance and risk management practices. The use of COBIT 5 has resulted in better control over taxpayer data and improved compliance with tax regulations.
Vattenfall: Vattenfall, a Swedish multinational energy company, implemented COBIT 5 to enhance its IT governance and cybersecurity practices. COBIT 5 helped Vattenfall align its IT strategies with business objectives and strengthen its defenses against cyber threats.
Central Bank of Nigeria: The Central Bank of Nigeria utilized COBIT 5 to improve its IT governance practices and enhance the security and integrity of the country's financial systems. COBIT 5 has played a critical role in ensuring the stability and resilience of Nigeria's financial infrastructure.
These examples illustrate the versatility and effectiveness of COBIT 5 across various industries and sectors. Organizations have leveraged COBIT 5 to align IT with their strategic goals, enhance IT governance, manage risks, and deliver better services to their stakeholders. These success stories showcase the framework's adaptability and its ability to drive positive outcomes in diverse organizational contexts
Conclusion
In conclusion, COBIT 5 is a comprehensive and widely recognized framework for IT governance and management that provides organizations with the tools and guidance they need to align their IT functions with business objectives, manage risks, and deliver value to stakeholders. It is built on a foundation of key principles, a well-structured process reference model, and seven enablers that collectively support effective governance and management.
As technology continues to play a pivotal role in the success of organizations, COBIT 5 remains a valuable framework for those seeking a structured and systematic approach to IT governance and management. By adopting and customizing COBIT 5 to their specific needs, organizations can navigate the complexities of the digital landscape and ensure that their IT functions are aligned with their broader business strategies.
Management Best Practices for Salesforce Administrators
In the dynamic world of customer relationship management, Salesforce has emerged as a powerhouse, enabling businesses to streamline their operations, deepen customer relationships, and drive growth. Salesforce administrators play a pivotal role in ensuring that this CRM platform functions smoothly and efficiently. However, the success of any CRM system largely depends on the quality of data it holds.
Data management in Salesforce is not just a necessary chore; it's the backbone of informed decision-making, accurate reporting, and a seamless user experience. In this blog, we will dive deep into the realm of "Data Management Best Practices for Salesforce Administrators." Whether you're a seasoned administrator or just embarking on your Salesforce journey, you'll find valuable insights and strategies to optimize your data management processes, maintain data quality, and harness the full potential of this powerful platform.
Table of contents
-
Understanding Data Architecture in Salesforce
-
Data Import and Export Best Practices
-
Data Cleansing and Deduplication Techniques
-
Mastering Data Validation Rules in Salesforce
-
Data Security and Compliance in Salesforce
-
Effective Record Ownership and Sharing Strategies
-
Archiving and Data Retention Policies
-
Data Backup and Disaster Recovery for Salesforce
-
Integration Best Practices for Data Synchronization
-
Automating Data Maintenance with Data Loader and Automation Tools
-
Conclusion
Understanding Data Architecture in Salesforce
Understanding Data Architecture in Salesforce is essential for administrators and users to effectively manage and leverage the power of the CRM platform. At its core, Salesforce data architecture revolves around three primary components: objects, fields, and records. Objects represent data entities, ranging from standard ones like Accounts and Contacts to custom objects tailored to an organization's unique needs. Fields define the type of data that can be stored in records, while records are individual instances within objects, each holding specific data corresponding to their associated fields.
Crucially, Salesforce's data architecture allows for the establishment of relationships between objects, facilitating a comprehensive understanding of your data. These relationships encompass master-detail and lookup relationships, as well as junction objects for many-to-many associations. Furthermore, Salesforce's highly customizable nature empowers administrators to adapt data architecture to meet the specific requirements of their organization, allowing for tailored data management that optimizes business processes and data-driven decision-making. A solid grasp of this architecture empowers administrators to configure and manage data effectively, ensuring the CRM system aligns seamlessly with their organization's goals and processes.
Data Import and Export Best Practices
Data Import and Export Best Practices in Salesforce are essential for maintaining data accuracy, consistency, and data integrity while moving data in and out of the CRM platform. These best practices ensure that you can rely on the quality of your data and minimize potential issues that can arise during data transfer.
Data Import Best Practices:
-
Data Cleanup: Before importing data, clean and format it to ensure consistency. Remove duplicates, correct errors, and standardize data formats, such as phone numbers or addresses.
-
Use Data Import Tools: Salesforce offers native tools like the Data Import Wizard and Data Loader to simplify the data import process. Familiarize yourself with these tools and choose the one that suits your needs.
-
Data Validation Rules: Implement validation rules to check data integrity during import. This helps prevent incorrect or incomplete data from being added to Salesforce.
-
Prepare for Errors: Expect errors during data imports. Have a plan in place to address data errors, and keep a log of any failed records for future review.
-
Test Imports: Before performing a large-scale import, conduct a small-scale test to ensure the process works as expected.
Data Export Best Practices:
-
Regular Backups: Schedule regular data exports to create backup copies of your Salesforce data. This ensures that you can recover information in case of data loss or unexpected events.
-
Use Data Export Tools: Salesforce provides export tools like Data Export, Data Loader, and third-party solutions for different export needs. Choose the right tool for your specific requirements.
-
Data Volume Considerations: Be aware of data volume limits and export limits, and plan your exports accordingly. Large data sets may require different export strategies.
-
Data Security: Ensure that exported data is handled securely. Use encryption if needed, and restrict access to the exported files to authorized personnel.
-
Data Mapping: When exporting data, ensure that the fields and data formats match your requirements. Create a mapping document to make sure data is correctly transformed during the export process.
-
Data Retention and Compliance: Consider your organization's data retention policies and any legal or compliance requirements when exporting data. Some data may need to be retained for specific periods, while other data may be subject to data privacy regulations.
In both data import and export processes, documenting your processes, having a clear understanding of your data, and regularly reviewing and optimizing your data management procedures are essential. Following these best practices not only helps maintain data quality but also ensures that Salesforce continues to be a reliable source of information for your organization.
Data Cleansing and Deduplication Techniques
Data cleansing and deduplication are critical processes for maintaining data accuracy and integrity in Salesforce. These techniques involve identifying and rectifying inconsistencies, inaccuracies, and duplicate records within your CRM database. Here's an explanation of data cleansing and deduplication techniques:
Data Cleansing Techniques:
-
Standardization: Ensure consistent data entry by defining and enforcing data entry standards. For example, standardizing date formats, phone numbers, and address structures.
-
Validation Rules: Implement validation rules to check data integrity and accuracy during data entry. These rules can prevent erroneous data from being added to the system.
-
Data Quality Tools: Salesforce offers data quality tools like Data.com Clean, which can help automatically clean and enrich your data by cross-referencing it with external sources.
-
Regular Data Audits: Conduct routine data audits to identify and correct data issues. This includes finding and correcting missing, incomplete, or inconsistent data.
-
Data Enrichment: Use external data sources to enhance your existing data with additional information. For instance, you can enrich contact records with social media profiles or company information.
Deduplication Techniques:
-
Data Matching Rules: Define data matching rules to identify potential duplicate records based on specific criteria, such as matching email addresses or names.
-
Data Deduplication Tools: Salesforce provides tools like Duplicate Management to automatically identify and merge duplicate records. These tools can be configured to your organization's specific needs.
-
Manual Review: For more complex or sensitive data, conduct manual reviews to confirm duplicates. This process may involve comparing and merging records with similar details.
-
Record Ownership: Determine clear guidelines for record ownership and responsibilities. This ensures that one person or team is accountable for maintaining data quality in a specific area.
-
Data Governance: Establish data governance practices to define who can create and manage records. Limiting the number of users who can create new records can reduce the likelihood of duplicates.
-
Training and User Awareness: Train your Salesforce users on best data entry practices and the importance of data deduplication. Encourage users to actively participate in maintaining data quality.
-
Scheduled Deduplication: Regularly schedule automated deduplication jobs to scan your database for duplicates and merge them.
Data cleansing and deduplication are ongoing processes, and it's essential to maintain data quality over time. By implementing these techniques, you can ensure that your Salesforce database remains a reliable and accurate source of information for your organization, helping you make informed decisions and maintain a positive user experience.
Mastering Data Validation Rules in Salesforce
"Mastering Data Validation Rules in Salesforce" is a critical aspect of maintaining data integrity and quality within the CRM platform. Data validation rules serve as a robust tool for enforcing specific criteria that data must meet before it is entered or updated in the system. This not only safeguards the accuracy and consistency of data but also aligns it with organizational standards and business rules. In effect, data validation rules act as the first line of defense against inaccuracies, ensuring that users input high-quality data in real-time, which reduces the need for manual corrections and enhances the overall user experience.
To truly master data validation rules in Salesforce, it's essential to begin with a clear understanding of the data types and objectives for your specific business needs. Creating well-crafted validation rules that align with these objectives, and using user-friendly error messages, are key components of success. Rigorous testing, user training, and thorough documentation complete the process. When implemented effectively, data validation rules not only elevate data quality but also enable organizations to rely on accurate information for reporting and decision-making, making it an indispensable skill for Salesforce administrators and users alike.
Data Security and Compliance in Salesforce
Data Security in Salesforce:
Salesforce provides a multi-layered approach to data security, enabling organizations to control who has access to their data and what they can do with it. Key data security features in Salesforce include:
-
User Authentication: Implement strong user authentication through tools like multi-factor authentication (MFA) to ensure that only authorized users can access the platform.
-
Role-Based Access Control: Define roles and profiles to determine what data users can view, edit, or delete. Customize access permissions to fit job roles and responsibilities.
-
Record-Level Security: Utilize record-level security through sharing rules, criteria-based sharing, and manual sharing to control access to individual records within objects.
-
Field-Level Security: Restrict access to specific fields within records by setting field-level security. This ensures sensitive data is only visible to those who need it.
-
Data Encryption: Encrypt data at rest and during transmission using industry-standard encryption protocols. This secures data stored on Salesforce servers and data transferred between the platform and user devices.
-
Event Monitoring and Auditing: Monitor user activity, login history, and data changes with auditing features. These logs can help detect suspicious activities and maintain compliance.
Compliance in Salesforce:
Salesforce offers tools and features to help organizations maintain compliance with various data protection and privacy regulations:
-
Data Retention and Deletion: Use Salesforce's data retention and deletion policies to automatically remove data that is no longer needed, helping you comply with regulations like GDPR's "Right to be Forgotten."
-
Data Subject Requests: Leverage Salesforce's capabilities to process data subject access requests (DSARs) and other requests related to data protection laws.
-
Healthcare Data Compliance: Implement Salesforce Health Cloud for healthcare organizations to manage sensitive patient data in compliance with HIPAA and other healthcare regulations.
-
GDPR Compliance: Salesforce provides features to help organizations comply with the European Union's General Data Protection Regulation, including data encryption, consent management, and data access controls.
-
Legal Compliance: Salesforce allows organizations to set up legal holds and data preservation policies for litigation purposes.
By addressing data security and compliance in Salesforce, organizations can build trust with customers, protect sensitive information, and avoid costly legal penalties. Understanding and implementing these features and best practices is essential for any organization that relies on Salesforce for managing and securing their data.
Effective Record Ownership and Sharing Strategies
"Effective Record Ownership and Sharing Strategies in Salesforce" are crucial for organizations seeking to maximize the value of their CRM data. Establishing clear and well-defined record ownership is the foundation upon which access and security policies are built. It not only helps determine who has the responsibility for specific records but also ensures that data remains organized and aligned with business processes. Role hierarchies, assignment rules, and a logical ownership structure based on functions or departments all play a part in this crucial process.
Sharing strategies in Salesforce, on the other hand, allow for fine-tuned control over data access. Public groups and criteria-based sharing rules streamline access to data for teams or users with common criteria, eliminating the need for manual sharing. However, the ability to manually share records remains a valuable tool for exceptional cases. To ensure these strategies work optimally, organizations must document and regularly review their sharing and ownership rules, provide user training, and consider data security and compliance needs. By taking a proactive approach to record ownership and sharing, organizations can strike a balance between collaboration and data security, ensuring that Salesforce remains a trusted resource for critical business information.
Archiving and Data Retention Policies
"Archiving and Data Retention Policies in Salesforce" are essential components of effective data management and compliance within the CRM platform. As organizations accumulate vast amounts of data over time, it's critical to have clear guidelines for classifying, storing, and eventually disposing of this data. Archiving helps improve database performance by moving older or less frequently accessed records to a separate storage location, reducing clutter, and enhancing the accessibility of crucial data. Data retention, on the other hand, establishes the duration for which data should be retained within Salesforce, taking into account factors like data importance, sensitivity, and legal requirements.
Effective archiving and data retention policies also play a vital role in compliance with industry-specific and regional regulations. Data classification, along with clear criteria for archiving and deletion, ensures that organizations can adhere to legal and regulatory requirements, such as GDPR and HIPAA, while maintaining data privacy and security. By documenting and communicating these policies to all relevant stakeholders and automating processes where possible, organizations can not only streamline data management but also protect themselves from compliance risks and achieve a balance between data accessibility and system performance within Salesforce.
Data Backup and Disaster Recovery for Salesforce
Data Backup and Disaster Recovery for Salesforce" form a critical pillar of data management and business continuity for organizations utilizing the CRM platform. In the digital age, data is the lifeblood of operations, and its loss or inaccessibility can lead to substantial financial and reputational damage. Data backup and disaster recovery strategies serve as the safety net, ensuring that valuable data remains intact and accessible in times of hardware failures, cyberattacks, natural disasters, or even inadvertent data corruption. These strategies are pivotal not only for data protection but also for maintaining business continuity, enabling organizations to recover swiftly and minimize downtime, thereby safeguarding their overall productivity and financial stability.
The key components of an effective data backup and disaster recovery plan include regular, automated data backups, offsite storage for redundancy, rigorous testing of data recovery procedures, and comprehensive disaster recovery plans that delineate roles, procedures, and communication strategies in emergency scenarios. Furthermore, data security remains paramount, with encryption and access controls in place to safeguard sensitive information during backup and recovery. By implementing these strategies, organizations ensure that their Salesforce data is secure, accessible, and recoverable, even in the face of unforeseen and potentially catastrophic events.
Integration Best Practices for Data Synchronization
-
Clear Objectives: Define integration goals and data synchronization requirements.
-
Data Mapping: Ensure data fields are aligned between systems.
-
Choose Integration Method: Select the right integration method for your needs.
-
Real-Time vs. Batch: Decide if data should synchronize in real-time or batches.
-
Error Handling: Develop a mechanism to handle and log errors.
-
Security: Encrypt data in transit and at rest; comply with data privacy regulations.
-
Testing: Thoroughly test integration in various scenarios.
-
Documentation: Document integration processes and update them as needed.
-
Performance Optimization: Optimize integration for speed and scalability.
-
Scalability: Ensure the integration can accommodate future growth.
Automating Data Maintenance with Data Loader and Automation Tools
“Automating Data Maintenance with Data Loader and Automation Tools" is a strategic approach for organizations seeking to streamline and optimize data management within Salesforce. Salesforce's Data Loader serves as a dependable tool for batch data processing, allowing organizations to schedule data maintenance tasks, such as regular data imports, updates, or cleanups. This automation not only saves time but also ensures data accuracy and consistency by reducing the likelihood of human errors.
Salesforce's built-in automation tools, including Workflow Rules, Process Builder, and scheduled flows, offer versatile options for automating data maintenance. These tools empower organizations to create logic-based automation processes that trigger actions based on record changes or predefined criteria. Whether it's updating fields, sending notifications, or creating follow-up tasks, these tools provide a user-friendly approach to automate data maintenance tasks, improving overall efficiency and enhancing the quality of data. By incorporating automation in their Salesforce data maintenance, organizations can focus their efforts on strategic decision-making and customer engagement, as they rest assured that data remains up to date and accurate, ensuring the platform's effectiveness as a business management tool.
Conclusion
In the fast-evolving landscape of CRM technology, Salesforce administrators must adapt and refine their data management practices continuously. In this blog, we've explored the fundamental aspects of data management within Salesforce, from data import and export to deduplication, validation rules, and security. We've discussed strategies to ensure that your data is not only accurate but also compliant with regulations. We've delved into the critical role of automation and integration in maintaining a clean and reliable database.
As you conclude your journey through this blog, remember that your commitment to data quality and best practices is a commitment to the success of your organization. By implementing the strategies and techniques discussed here, you'll not only enhance the user experience but also empower your team with accurate insights for data-driven decision-making. The art of Salesforce data management is an ongoing process, and as you continue to refine your skills, you'll be better equipped to navigate the ever-changing CRM landscape with confidence and expertise. Your dedication to data management excellence will undoubtedly contribute to your organization's growth and success.
Read More
In the dynamic world of customer relationship management, Salesforce has emerged as a powerhouse, enabling businesses to streamline their operations, deepen customer relationships, and drive growth. Salesforce administrators play a pivotal role in ensuring that this CRM platform functions smoothly and efficiently. However, the success of any CRM system largely depends on the quality of data it holds.
Data management in Salesforce is not just a necessary chore; it's the backbone of informed decision-making, accurate reporting, and a seamless user experience. In this blog, we will dive deep into the realm of "Data Management Best Practices for Salesforce Administrators." Whether you're a seasoned administrator or just embarking on your Salesforce journey, you'll find valuable insights and strategies to optimize your data management processes, maintain data quality, and harness the full potential of this powerful platform.
Table of contents
-
Understanding Data Architecture in Salesforce
-
Data Import and Export Best Practices
-
Data Cleansing and Deduplication Techniques
-
Mastering Data Validation Rules in Salesforce
-
Data Security and Compliance in Salesforce
-
Effective Record Ownership and Sharing Strategies
-
Archiving and Data Retention Policies
-
Data Backup and Disaster Recovery for Salesforce
-
Integration Best Practices for Data Synchronization
-
Automating Data Maintenance with Data Loader and Automation Tools
-
Conclusion
Understanding Data Architecture in Salesforce
Understanding Data Architecture in Salesforce is essential for administrators and users to effectively manage and leverage the power of the CRM platform. At its core, Salesforce data architecture revolves around three primary components: objects, fields, and records. Objects represent data entities, ranging from standard ones like Accounts and Contacts to custom objects tailored to an organization's unique needs. Fields define the type of data that can be stored in records, while records are individual instances within objects, each holding specific data corresponding to their associated fields.
Crucially, Salesforce's data architecture allows for the establishment of relationships between objects, facilitating a comprehensive understanding of your data. These relationships encompass master-detail and lookup relationships, as well as junction objects for many-to-many associations. Furthermore, Salesforce's highly customizable nature empowers administrators to adapt data architecture to meet the specific requirements of their organization, allowing for tailored data management that optimizes business processes and data-driven decision-making. A solid grasp of this architecture empowers administrators to configure and manage data effectively, ensuring the CRM system aligns seamlessly with their organization's goals and processes.
Data Import and Export Best Practices
Data Import and Export Best Practices in Salesforce are essential for maintaining data accuracy, consistency, and data integrity while moving data in and out of the CRM platform. These best practices ensure that you can rely on the quality of your data and minimize potential issues that can arise during data transfer.
Data Import Best Practices:
-
Data Cleanup: Before importing data, clean and format it to ensure consistency. Remove duplicates, correct errors, and standardize data formats, such as phone numbers or addresses.
-
Use Data Import Tools: Salesforce offers native tools like the Data Import Wizard and Data Loader to simplify the data import process. Familiarize yourself with these tools and choose the one that suits your needs.
-
Data Validation Rules: Implement validation rules to check data integrity during import. This helps prevent incorrect or incomplete data from being added to Salesforce.
-
Prepare for Errors: Expect errors during data imports. Have a plan in place to address data errors, and keep a log of any failed records for future review.
-
Test Imports: Before performing a large-scale import, conduct a small-scale test to ensure the process works as expected.
Data Export Best Practices:
-
Regular Backups: Schedule regular data exports to create backup copies of your Salesforce data. This ensures that you can recover information in case of data loss or unexpected events.
-
Use Data Export Tools: Salesforce provides export tools like Data Export, Data Loader, and third-party solutions for different export needs. Choose the right tool for your specific requirements.
-
Data Volume Considerations: Be aware of data volume limits and export limits, and plan your exports accordingly. Large data sets may require different export strategies.
-
Data Security: Ensure that exported data is handled securely. Use encryption if needed, and restrict access to the exported files to authorized personnel.
-
Data Mapping: When exporting data, ensure that the fields and data formats match your requirements. Create a mapping document to make sure data is correctly transformed during the export process.
-
Data Retention and Compliance: Consider your organization's data retention policies and any legal or compliance requirements when exporting data. Some data may need to be retained for specific periods, while other data may be subject to data privacy regulations.
In both data import and export processes, documenting your processes, having a clear understanding of your data, and regularly reviewing and optimizing your data management procedures are essential. Following these best practices not only helps maintain data quality but also ensures that Salesforce continues to be a reliable source of information for your organization.
Data Cleansing and Deduplication Techniques
Data cleansing and deduplication are critical processes for maintaining data accuracy and integrity in Salesforce. These techniques involve identifying and rectifying inconsistencies, inaccuracies, and duplicate records within your CRM database. Here's an explanation of data cleansing and deduplication techniques:
Data Cleansing Techniques:
-
Standardization: Ensure consistent data entry by defining and enforcing data entry standards. For example, standardizing date formats, phone numbers, and address structures.
-
Validation Rules: Implement validation rules to check data integrity and accuracy during data entry. These rules can prevent erroneous data from being added to the system.
-
Data Quality Tools: Salesforce offers data quality tools like Data.com Clean, which can help automatically clean and enrich your data by cross-referencing it with external sources.
-
Regular Data Audits: Conduct routine data audits to identify and correct data issues. This includes finding and correcting missing, incomplete, or inconsistent data.
-
Data Enrichment: Use external data sources to enhance your existing data with additional information. For instance, you can enrich contact records with social media profiles or company information.
Deduplication Techniques:
-
Data Matching Rules: Define data matching rules to identify potential duplicate records based on specific criteria, such as matching email addresses or names.
-
Data Deduplication Tools: Salesforce provides tools like Duplicate Management to automatically identify and merge duplicate records. These tools can be configured to your organization's specific needs.
-
Manual Review: For more complex or sensitive data, conduct manual reviews to confirm duplicates. This process may involve comparing and merging records with similar details.
-
Record Ownership: Determine clear guidelines for record ownership and responsibilities. This ensures that one person or team is accountable for maintaining data quality in a specific area.
-
Data Governance: Establish data governance practices to define who can create and manage records. Limiting the number of users who can create new records can reduce the likelihood of duplicates.
-
Training and User Awareness: Train your Salesforce users on best data entry practices and the importance of data deduplication. Encourage users to actively participate in maintaining data quality.
-
Scheduled Deduplication: Regularly schedule automated deduplication jobs to scan your database for duplicates and merge them.
Data cleansing and deduplication are ongoing processes, and it's essential to maintain data quality over time. By implementing these techniques, you can ensure that your Salesforce database remains a reliable and accurate source of information for your organization, helping you make informed decisions and maintain a positive user experience.
Mastering Data Validation Rules in Salesforce
"Mastering Data Validation Rules in Salesforce" is a critical aspect of maintaining data integrity and quality within the CRM platform. Data validation rules serve as a robust tool for enforcing specific criteria that data must meet before it is entered or updated in the system. This not only safeguards the accuracy and consistency of data but also aligns it with organizational standards and business rules. In effect, data validation rules act as the first line of defense against inaccuracies, ensuring that users input high-quality data in real-time, which reduces the need for manual corrections and enhances the overall user experience.
To truly master data validation rules in Salesforce, it's essential to begin with a clear understanding of the data types and objectives for your specific business needs. Creating well-crafted validation rules that align with these objectives, and using user-friendly error messages, are key components of success. Rigorous testing, user training, and thorough documentation complete the process. When implemented effectively, data validation rules not only elevate data quality but also enable organizations to rely on accurate information for reporting and decision-making, making it an indispensable skill for Salesforce administrators and users alike.
Data Security and Compliance in Salesforce
Data Security in Salesforce:
Salesforce provides a multi-layered approach to data security, enabling organizations to control who has access to their data and what they can do with it. Key data security features in Salesforce include:
-
User Authentication: Implement strong user authentication through tools like multi-factor authentication (MFA) to ensure that only authorized users can access the platform.
-
Role-Based Access Control: Define roles and profiles to determine what data users can view, edit, or delete. Customize access permissions to fit job roles and responsibilities.
-
Record-Level Security: Utilize record-level security through sharing rules, criteria-based sharing, and manual sharing to control access to individual records within objects.
-
Field-Level Security: Restrict access to specific fields within records by setting field-level security. This ensures sensitive data is only visible to those who need it.
-
Data Encryption: Encrypt data at rest and during transmission using industry-standard encryption protocols. This secures data stored on Salesforce servers and data transferred between the platform and user devices.
-
Event Monitoring and Auditing: Monitor user activity, login history, and data changes with auditing features. These logs can help detect suspicious activities and maintain compliance.
Compliance in Salesforce:
Salesforce offers tools and features to help organizations maintain compliance with various data protection and privacy regulations:
-
Data Retention and Deletion: Use Salesforce's data retention and deletion policies to automatically remove data that is no longer needed, helping you comply with regulations like GDPR's "Right to be Forgotten."
-
Data Subject Requests: Leverage Salesforce's capabilities to process data subject access requests (DSARs) and other requests related to data protection laws.
-
Healthcare Data Compliance: Implement Salesforce Health Cloud for healthcare organizations to manage sensitive patient data in compliance with HIPAA and other healthcare regulations.
-
GDPR Compliance: Salesforce provides features to help organizations comply with the European Union's General Data Protection Regulation, including data encryption, consent management, and data access controls.
-
Legal Compliance: Salesforce allows organizations to set up legal holds and data preservation policies for litigation purposes.
By addressing data security and compliance in Salesforce, organizations can build trust with customers, protect sensitive information, and avoid costly legal penalties. Understanding and implementing these features and best practices is essential for any organization that relies on Salesforce for managing and securing their data.
Effective Record Ownership and Sharing Strategies
"Effective Record Ownership and Sharing Strategies in Salesforce" are crucial for organizations seeking to maximize the value of their CRM data. Establishing clear and well-defined record ownership is the foundation upon which access and security policies are built. It not only helps determine who has the responsibility for specific records but also ensures that data remains organized and aligned with business processes. Role hierarchies, assignment rules, and a logical ownership structure based on functions or departments all play a part in this crucial process.
Sharing strategies in Salesforce, on the other hand, allow for fine-tuned control over data access. Public groups and criteria-based sharing rules streamline access to data for teams or users with common criteria, eliminating the need for manual sharing. However, the ability to manually share records remains a valuable tool for exceptional cases. To ensure these strategies work optimally, organizations must document and regularly review their sharing and ownership rules, provide user training, and consider data security and compliance needs. By taking a proactive approach to record ownership and sharing, organizations can strike a balance between collaboration and data security, ensuring that Salesforce remains a trusted resource for critical business information.
Archiving and Data Retention Policies
"Archiving and Data Retention Policies in Salesforce" are essential components of effective data management and compliance within the CRM platform. As organizations accumulate vast amounts of data over time, it's critical to have clear guidelines for classifying, storing, and eventually disposing of this data. Archiving helps improve database performance by moving older or less frequently accessed records to a separate storage location, reducing clutter, and enhancing the accessibility of crucial data. Data retention, on the other hand, establishes the duration for which data should be retained within Salesforce, taking into account factors like data importance, sensitivity, and legal requirements.
Effective archiving and data retention policies also play a vital role in compliance with industry-specific and regional regulations. Data classification, along with clear criteria for archiving and deletion, ensures that organizations can adhere to legal and regulatory requirements, such as GDPR and HIPAA, while maintaining data privacy and security. By documenting and communicating these policies to all relevant stakeholders and automating processes where possible, organizations can not only streamline data management but also protect themselves from compliance risks and achieve a balance between data accessibility and system performance within Salesforce.
Data Backup and Disaster Recovery for Salesforce
Data Backup and Disaster Recovery for Salesforce" form a critical pillar of data management and business continuity for organizations utilizing the CRM platform. In the digital age, data is the lifeblood of operations, and its loss or inaccessibility can lead to substantial financial and reputational damage. Data backup and disaster recovery strategies serve as the safety net, ensuring that valuable data remains intact and accessible in times of hardware failures, cyberattacks, natural disasters, or even inadvertent data corruption. These strategies are pivotal not only for data protection but also for maintaining business continuity, enabling organizations to recover swiftly and minimize downtime, thereby safeguarding their overall productivity and financial stability.
The key components of an effective data backup and disaster recovery plan include regular, automated data backups, offsite storage for redundancy, rigorous testing of data recovery procedures, and comprehensive disaster recovery plans that delineate roles, procedures, and communication strategies in emergency scenarios. Furthermore, data security remains paramount, with encryption and access controls in place to safeguard sensitive information during backup and recovery. By implementing these strategies, organizations ensure that their Salesforce data is secure, accessible, and recoverable, even in the face of unforeseen and potentially catastrophic events.
Integration Best Practices for Data Synchronization
-
Clear Objectives: Define integration goals and data synchronization requirements.
-
Data Mapping: Ensure data fields are aligned between systems.
-
Choose Integration Method: Select the right integration method for your needs.
-
Real-Time vs. Batch: Decide if data should synchronize in real-time or batches.
-
Error Handling: Develop a mechanism to handle and log errors.
-
Security: Encrypt data in transit and at rest; comply with data privacy regulations.
-
Testing: Thoroughly test integration in various scenarios.
-
Documentation: Document integration processes and update them as needed.
-
Performance Optimization: Optimize integration for speed and scalability.
-
Scalability: Ensure the integration can accommodate future growth.
Automating Data Maintenance with Data Loader and Automation Tools
“Automating Data Maintenance with Data Loader and Automation Tools" is a strategic approach for organizations seeking to streamline and optimize data management within Salesforce. Salesforce's Data Loader serves as a dependable tool for batch data processing, allowing organizations to schedule data maintenance tasks, such as regular data imports, updates, or cleanups. This automation not only saves time but also ensures data accuracy and consistency by reducing the likelihood of human errors.
Salesforce's built-in automation tools, including Workflow Rules, Process Builder, and scheduled flows, offer versatile options for automating data maintenance. These tools empower organizations to create logic-based automation processes that trigger actions based on record changes or predefined criteria. Whether it's updating fields, sending notifications, or creating follow-up tasks, these tools provide a user-friendly approach to automate data maintenance tasks, improving overall efficiency and enhancing the quality of data. By incorporating automation in their Salesforce data maintenance, organizations can focus their efforts on strategic decision-making and customer engagement, as they rest assured that data remains up to date and accurate, ensuring the platform's effectiveness as a business management tool.
Conclusion
In the fast-evolving landscape of CRM technology, Salesforce administrators must adapt and refine their data management practices continuously. In this blog, we've explored the fundamental aspects of data management within Salesforce, from data import and export to deduplication, validation rules, and security. We've discussed strategies to ensure that your data is not only accurate but also compliant with regulations. We've delved into the critical role of automation and integration in maintaining a clean and reliable database.
As you conclude your journey through this blog, remember that your commitment to data quality and best practices is a commitment to the success of your organization. By implementing the strategies and techniques discussed here, you'll not only enhance the user experience but also empower your team with accurate insights for data-driven decision-making. The art of Salesforce data management is an ongoing process, and as you continue to refine your skills, you'll be better equipped to navigate the ever-changing CRM landscape with confidence and expertise. Your dedication to data management excellence will undoubtedly contribute to your organization's growth and success.
Excel 2013 for Project Management: Gantt Charts and Timelines
In the realm of project management, effective planning and organization are the linchpins of success. A project manager's toolkit must be equipped with the right tools to chart a course, allocate resources, and keep everyone on the same page. Excel 2013, a trusted and widely used spreadsheet software, plays a vital role in facilitating these tasks. Among its many capabilities, Excel empowers project managers to create Gantt charts and timelines, two essential components in the journey from project initiation to successful completion. In this blog, we will delve into the world of project management with Excel 2013, exploring how it enables the creation of dynamic and visually engaging Gantt charts, and the tracking of project timelines. Whether you're a seasoned project manager or a novice seeking to enhance your skills, this blog will serve as your guide to harnessing Excel 2013's potential for effective project management. Let's embark on this journey to discover the art of Gantt charts and timelines, the heartbeat of project management.
Table of Contents
-
Understanding Gantt Charts
-
Creating a Gantt Chart in Excel 2013
-
Customizing Gantt Charts
-
Adding and Managing Tasks
-
Setting Dependencies
-
Adjusting Timeframes
-
Critical Path Analysis
-
Resource Management
-
Tracking Progress
-
Exporting and Sharing
-
Conclusion
Understanding Gantt Charts
A Gantt chart is a visual project management tool that provides a clear and intuitive representation of a project's timeline and task schedule. It uses horizontal bars to depict individual tasks, with the length of each bar indicating the task's duration. Task dependencies are illustrated, showing the sequence of activities and the impact of any delays. This tool allows project managers to plan, allocate resources, track progress, and identify the critical path—a sequence of tasks that, if delayed, would delay the entire project. Gantt charts are invaluable for effective project planning, communication, and resource management, enhancing team productivity and efficiency by keeping everyone aligned with the project's timeline and objectives.
In addition to its role in project planning, Gantt charts serve as a dynamic and adaptable tool. They can be easily adjusted to accommodate changes in project requirements or unforeseen delays, making them an essential asset for project managers seeking to maintain project schedules and keep stakeholders informed about the project's progress. Overall, Gantt charts are a versatile and essential element of project management, offering clarity and structure in the often complex landscape of project scheduling and execution.
Creating a Gantt Chart in Excel 2013
Creating a Gantt Chart in Excel 2013 is a straightforward process that involves setting up a table of tasks and their corresponding start dates, durations, and dependencies. Here are step-by-step instructions on how to create a basic Gantt chart in Excel 2013:
Step 1: Prepare Your Data
-
Open Microsoft Excel 2013 and create a new worksheet.
-
In the first column (Column A), list the tasks or activities that make up your project. This will be your task list.
-
In the second column (Column B), enter the start date for each task.
-
In the third column (Column C), specify the duration (in days or weeks) for each task.
-
If you have task dependencies (i.e., some tasks can only start when others are completed), create another column to define these dependencies. For example, in Column D, you can list the tasks that a specific task depends on.
Step 2: Create a Stacked Bar Chart
-
Highlight the data you've entered in columns A, B, and C.
-
Go to the "Insert" tab in the Excel ribbon.
-
Click on the "Bar Chart" dropdown and select "Stacked Bar." A bar chart will appear on your worksheet.
Step 3: Format the Bar Chart
-
Right-click on the chart and click "Select Data." In the "Select Data Source" dialog box, click "Add" to add the task names from Column A as the horizontal (category) axis labels.
-
You can also add the task names as data series by selecting the data in Column A.
-
Format the chart by adjusting the colors, labels, and other elements to make it look like a Gantt chart. You can remove the legend and adjust the axis labels.
Step 4: Adjust Dates
-
To set the timeline on the chart, right-click on the date axis, and select "Format Axis."
-
Set the minimum and maximum values to match your project's start and end dates.
Step 5: Add Dependencies (Optional)
-
If you have task dependencies, you can add arrows or connectors between the bars on your chart to represent them. You can do this by adding lines or connectors from the "Insert" tab.
Step 6: Finalize Your Gantt Chart
-
Add any additional formatting, such as colors, labels, or titles to make your Gantt chart clear and visually appealing.
Your basic Gantt chart is now created in Excel 2013. This visual representation of your project schedule will help you and your team stay organized, track progress, and manage your project effectively. You can also consider using Excel templates designed specifically for Gantt charts to streamline the process further.
Customizing Gantt Charts
Customizing Gantt charts in Excel 2013 is an essential step to make your project management tool not only functional but also visually appealing and tailored to your project's unique requirements. You can start by adjusting the appearance of task bars, using different colors to categorize tasks or changing their height to emphasize their importance. Task labels and data can be included directly on the bars, providing at-a-glance information about each task. You can also format the date axis to make it more intuitive, specifying the date format, labels, and intervals. Creating a legend that explains the color codes used in your chart can be particularly helpful when you have specific task categories.
Furthermore, task dependencies can be visually represented using connectors, and you can even emphasize the critical path with unique styling. Implementing data validation rules ensures data consistency and accuracy. Beyond the chart itself, you can adjust gridlines, chart background, and add titles and labels for clarity. Once your Gantt chart is fully customized, you can save it as a template for future projects, streamlining the creation of Gantt charts tailored to your project's unique needs. These customizations not only enhance the functionality and readability of your Gantt chart but also make it an effective communication tool for project management and collaboration.
Adding and Managing Tasks
Adding and managing tasks is a fundamental aspect of creating and maintaining a Gantt chart in Excel 2013, which is essential for effective project management. Here's a step-by-step guide on how to add and manage tasks within your Gantt chart:
Adding Tasks:
-
Open your Excel Gantt chart: Ensure that you have your Gantt chart spreadsheet open in Excel 2013, where you've already set up your task list.
-
Insert a new row: To add a new task, insert a row in your task list. Right-click on the row number where you want to insert the task and select "Insert." This creates a new row for your task.
-
Enter task information: In the newly inserted row, fill in the information for the task. Typically, this includes the task name, start date, duration, and any dependencies. Be sure to follow the format of your existing task entries.
-
Update your Gantt chart: As you enter task information in the task list, your Gantt chart should automatically update to reflect the newly added task. The task bar should appear in the chart with the specified start date and duration.
Managing Tasks:
-
Editing tasks: To make changes to an existing task, simply click on the cell where the task information is located, and you can edit the task's name, start date, duration, or other details. Ensure that your changes are accurate and in line with your project requirements.
-
Reordering tasks: If your project task order changes, you can easily reorder tasks by selecting the entire row corresponding to the task and dragging it to the desired position.
-
Deleting tasks: If a task is no longer part of the project, you can delete it by selecting the row associated with the task and right-clicking to choose "Delete."
-
Updating dependencies: If there are changes in task dependencies, you can update them in your task list. Make sure the dependent tasks are accurately reflected, so your Gantt chart correctly displays these relationships.
-
Adjusting task durations: You can change the duration of a task by simply editing the cell that contains the task's duration. The Gantt chart will update accordingly to reflect the new duration.
-
Critical path adjustments: Be mindful of how task changes affect the critical path of your project. If you alter tasks with dependencies, it may impact the critical path, potentially affecting project timelines.
Properly adding and managing tasks in your Excel 2013 Gantt chart is essential for maintaining an accurate and up-to-date project schedule. Regularly review and adjust your task list and the Gantt chart to ensure that they accurately reflect the project's progress and requirements. This will help you effectively track and manage your project's timeline and ensure its successful completion.
Setting Dependencies
Setting task dependencies in your Excel 2013 Gantt chart is a pivotal step in project management. Task dependencies define the order in which activities should be carried out, ensuring that tasks are completed in a logical and coordinated manner. This not only helps maintain project integrity but also aids in identifying potential bottlenecks or issues that could affect the project's timeline. By establishing clear dependencies, you create a roadmap for task execution, providing project stakeholders with a transparent and structured view of how their project will unfold.
Excel's Gantt chart, when properly configured with task dependencies, can automatically adjust task start dates based on the completion of predecessor tasks. This feature streamlines project management by enabling real-time updates, allowing project managers to assess progress, optimize schedules, and efficiently allocate resources. Whether your project involves simple sequential tasks or intricate interdependencies, setting task dependencies within Excel 2013's Gantt chart provides a robust foundation for managing and tracking projects, ultimately contributing to successful project delivery and on-time completion.
Adjusting Timeframes
Adjusting timeframes in an Excel 2013 Gantt chart is a pivotal activity in project management, as it enables project managers to accommodate changes, adapt to unforeseen challenges, and maintain project timelines. Whether extending task durations to accommodate unexpected delays or shortening them to seize new opportunities, these adjustments allow project managers to keep their projects on course. By simply dragging task bars to new dates or modifying durations in the task list, project managers can maintain agility in their project management approach.
Additionally, modifying timeframes requires a careful review of task dependencies to ensure that changes do not disrupt the logical sequence of tasks. The critical path, which determines the project's overall duration, should also be reviewed to ensure it aligns with the adjusted timeline. Clear communication with the project team and stakeholders regarding these adjustments is vital to keep everyone informed and aligned with the new schedule. Excel's Gantt chart, with its flexibility in adjusting timeframes, proves invaluable in responding to the dynamic nature of project management and maintaining successful project execution.
Critical Path Analysis
Critical Path Analysis (CPA) is a fundamental project management technique, and in the context of a Gantt chart created in Excel 2013, it plays a vital role in identifying the project's critical path, which is akin to the project's lifeline. By establishing dependencies and accurately determining task durations, Excel's Gantt chart feature can automatically calculate the critical path. This path represents the sequence of tasks that, if delayed, would extend the project's overall duration. Project managers can then focus their attention on the critical tasks, ensuring they are executed efficiently and on time. Excel's Gantt chart simplifies the visualization and management of these critical tasks, providing a clear roadmap for project success.
Moreover, critical path analysis is an ongoing process. Project managers must continually monitor task progress and address any deviations promptly. The Excel Gantt chart allows for real-time tracking of task status, making it easier to identify potential delays and enabling timely adjustments to mitigate their impact. By consistently applying CPA within the Gantt chart, project managers gain a powerful tool to ensure project success, timely delivery, and effective resource allocation, ultimately optimizing project management and fostering a culture of efficiency and productivity within the team.
Resource Management
Resource management within the framework of an Excel 2013 Gantt chart is a pivotal element of project management, as it empowers project managers to optimize the allocation of human resources, an invaluable asset for project success. By identifying the specific roles, skills, and quantities of team members required for each task and assigning them within the Gantt chart, managers can create a detailed roadmap for the project's execution. This allocation streamlines task assignment, enhances accountability, and ensures that the right resources are available at the right time, contributing to project efficiency and productivity.
Furthermore, resource management extends beyond mere allocation. Excel's Gantt chart can help with resource leveling to balance workloads and prevent resource overallocation or underutilization. This dynamic feature enables project managers to adapt to shifting project demands and unexpected resource constraints. By integrating resource management into a Gantt chart, project teams are better equipped to optimize resource utilization, minimize conflicts, and deliver projects within scope, on time, and within budget.
Tracking Progress
Tracking progress is a critical part of project management, and in the context of a Gantt chart created in Excel 2013, it allows project managers to monitor the project's advancement and ensure that it stays on schedule. Here's a guide on how to effectively track progress using your Gantt chart:
1. Update Task Completion:
As tasks are completed, update the Gantt chart to reflect their progress. In Excel 2013, you can do this by adjusting the percent completion or changing the colors of task bars.
2. Track Milestones:
Pay special attention to project milestones, which mark significant project achievements. Ensure that these are reached as planned and update your Gantt chart accordingly.
3. Record Delays and Issues:
If any tasks are delayed or if issues arise, document these in your Gantt chart. Make sure to explain the reasons for the delays and any planned corrective actions.
4. Compare Actual vs. Planned Progress:
Regularly compare the actual progress with the planned schedule. Excel's Gantt chart can help you visualize this comparison, highlighting where the project is on track and where adjustments are needed.
5. Use Color Coding:
Color coding can be a useful technique in Excel 2013. You can assign different colors to tasks to indicate their status, such as "on schedule," "delayed," or "completed." This provides a quick visual overview of the project's health.
6. Regular Reporting:
Provide regular progress reports to your project team and stakeholders, using the Gantt chart as a visual aid. Clearly communicate any changes in the project schedule or scope and discuss the impact of these changes.
7. Adjust the Gantt Chart:
If there are significant changes in the project timeline or scope, make corresponding adjustments in your Gantt chart. Ensure that the chart remains an accurate reflection of the project's status and plans.
8. Critical Path Review:
Revisit the critical path and assess if any tasks on it are at risk of delaying the project. Take necessary actions to mitigate such risks and maintain the project's critical path on schedule.
By tracking progress in your Gantt chart, project managers gain a real-time understanding of how the project is evolving. This enables them to make informed decisions, take corrective actions when needed, and ensure that the project remains on track to meet its objectives and deadlines. Excel's Gantt chart is a powerful tool for visualizing and managing progress, making it an essential asset for effective project management.
Exporting and Sharing
Exporting and sharing your Gantt chart, crafted in Excel 2013, is the bridge that connects your project management insights with your project team and stakeholders. The process begins with selecting the appropriate file format based on your communication needs—PDF for a static document, image formats for presentations and reports, or an editable Excel workbook for more collaborative environments. Once exported, you can utilize a range of sharing methods, including email, cloud storage platforms, or project management tools. This dissemination not only facilitates communication but also encourages collaborative editing, real-time feedback, and secure access control.
Sharing the Gantt chart link via cloud storage or embedding it into project documents and reports enhances accessibility and provides context within a broader project narrative. Keep in mind that sharing is an ongoing process; as your project progresses, regularly update and distribute the Gantt chart to reflect changes, thereby maintaining clarity, alignment, and accountability among all project stakeholders. Exporting and sharing your Gantt chart is not just a practical step; it's a fundamental practice for effective project management, fostering transparency, collaboration, and informed decision-making throughout the project lifecycle.
How to obtain Microsoft Excel 2013 Advanced Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop
Microsoft : Microsoft Excel 2013 Advanced Certification
Conclusion
In the ever-evolving landscape of project management, Excel 2013 has emerged as a steadfast and robust companion. Our journey through the world of Gantt charts and timelines within Excel 2013 has unveiled its remarkable ability to convert data into actionable insights. Gantt charts, with their visual representation of project tasks and dependencies, offer project managers a dynamic tool to plan, execute, and track projects effectively. Excel's proficiency in project timelines empowers teams to stay informed and proactive, with real-time status updates guiding them toward project milestones. Together, these features within Excel 2013 foster transparency, collaboration, and informed decision-making, ensuring that projects are not only completed on time but with greater efficiency and precision.
As we conclude, it is evident that Excel 2013's capabilities extend well beyond its reputation as a spreadsheet software. It is a foundational asset in the toolkit of any project manager seeking to navigate the complexities of project planning, execution, and monitoring. With Gantt charts and timelines at your disposal, Excel 2013 has the potential to revolutionize the way you approach and succeed in project management. In this ever-dynamic landscape, where the demand for timely and efficient project delivery is paramount, Excel 2013 stands as an enduring and indispensable partner, ready to assist you in achieving your project management goals.
Read More
In the realm of project management, effective planning and organization are the linchpins of success. A project manager's toolkit must be equipped with the right tools to chart a course, allocate resources, and keep everyone on the same page. Excel 2013, a trusted and widely used spreadsheet software, plays a vital role in facilitating these tasks. Among its many capabilities, Excel empowers project managers to create Gantt charts and timelines, two essential components in the journey from project initiation to successful completion. In this blog, we will delve into the world of project management with Excel 2013, exploring how it enables the creation of dynamic and visually engaging Gantt charts, and the tracking of project timelines. Whether you're a seasoned project manager or a novice seeking to enhance your skills, this blog will serve as your guide to harnessing Excel 2013's potential for effective project management. Let's embark on this journey to discover the art of Gantt charts and timelines, the heartbeat of project management.
Table of Contents
-
Understanding Gantt Charts
-
Creating a Gantt Chart in Excel 2013
-
Customizing Gantt Charts
-
Adding and Managing Tasks
-
Setting Dependencies
-
Adjusting Timeframes
-
Critical Path Analysis
-
Resource Management
-
Tracking Progress
-
Exporting and Sharing
-
Conclusion
Understanding Gantt Charts
A Gantt chart is a visual project management tool that provides a clear and intuitive representation of a project's timeline and task schedule. It uses horizontal bars to depict individual tasks, with the length of each bar indicating the task's duration. Task dependencies are illustrated, showing the sequence of activities and the impact of any delays. This tool allows project managers to plan, allocate resources, track progress, and identify the critical path—a sequence of tasks that, if delayed, would delay the entire project. Gantt charts are invaluable for effective project planning, communication, and resource management, enhancing team productivity and efficiency by keeping everyone aligned with the project's timeline and objectives.
In addition to its role in project planning, Gantt charts serve as a dynamic and adaptable tool. They can be easily adjusted to accommodate changes in project requirements or unforeseen delays, making them an essential asset for project managers seeking to maintain project schedules and keep stakeholders informed about the project's progress. Overall, Gantt charts are a versatile and essential element of project management, offering clarity and structure in the often complex landscape of project scheduling and execution.
Creating a Gantt Chart in Excel 2013
Creating a Gantt Chart in Excel 2013 is a straightforward process that involves setting up a table of tasks and their corresponding start dates, durations, and dependencies. Here are step-by-step instructions on how to create a basic Gantt chart in Excel 2013:
Step 1: Prepare Your Data
-
Open Microsoft Excel 2013 and create a new worksheet.
-
In the first column (Column A), list the tasks or activities that make up your project. This will be your task list.
-
In the second column (Column B), enter the start date for each task.
-
In the third column (Column C), specify the duration (in days or weeks) for each task.
-
If you have task dependencies (i.e., some tasks can only start when others are completed), create another column to define these dependencies. For example, in Column D, you can list the tasks that a specific task depends on.
Step 2: Create a Stacked Bar Chart
-
Highlight the data you've entered in columns A, B, and C.
-
Go to the "Insert" tab in the Excel ribbon.
-
Click on the "Bar Chart" dropdown and select "Stacked Bar." A bar chart will appear on your worksheet.
Step 3: Format the Bar Chart
-
Right-click on the chart and click "Select Data." In the "Select Data Source" dialog box, click "Add" to add the task names from Column A as the horizontal (category) axis labels.
-
You can also add the task names as data series by selecting the data in Column A.
-
Format the chart by adjusting the colors, labels, and other elements to make it look like a Gantt chart. You can remove the legend and adjust the axis labels.
Step 4: Adjust Dates
-
To set the timeline on the chart, right-click on the date axis, and select "Format Axis."
-
Set the minimum and maximum values to match your project's start and end dates.
Step 5: Add Dependencies (Optional)
-
If you have task dependencies, you can add arrows or connectors between the bars on your chart to represent them. You can do this by adding lines or connectors from the "Insert" tab.
Step 6: Finalize Your Gantt Chart
-
Add any additional formatting, such as colors, labels, or titles to make your Gantt chart clear and visually appealing.
Your basic Gantt chart is now created in Excel 2013. This visual representation of your project schedule will help you and your team stay organized, track progress, and manage your project effectively. You can also consider using Excel templates designed specifically for Gantt charts to streamline the process further.
Customizing Gantt Charts
Customizing Gantt charts in Excel 2013 is an essential step to make your project management tool not only functional but also visually appealing and tailored to your project's unique requirements. You can start by adjusting the appearance of task bars, using different colors to categorize tasks or changing their height to emphasize their importance. Task labels and data can be included directly on the bars, providing at-a-glance information about each task. You can also format the date axis to make it more intuitive, specifying the date format, labels, and intervals. Creating a legend that explains the color codes used in your chart can be particularly helpful when you have specific task categories.
Furthermore, task dependencies can be visually represented using connectors, and you can even emphasize the critical path with unique styling. Implementing data validation rules ensures data consistency and accuracy. Beyond the chart itself, you can adjust gridlines, chart background, and add titles and labels for clarity. Once your Gantt chart is fully customized, you can save it as a template for future projects, streamlining the creation of Gantt charts tailored to your project's unique needs. These customizations not only enhance the functionality and readability of your Gantt chart but also make it an effective communication tool for project management and collaboration.
Adding and Managing Tasks
Adding and managing tasks is a fundamental aspect of creating and maintaining a Gantt chart in Excel 2013, which is essential for effective project management. Here's a step-by-step guide on how to add and manage tasks within your Gantt chart:
Adding Tasks:
-
Open your Excel Gantt chart: Ensure that you have your Gantt chart spreadsheet open in Excel 2013, where you've already set up your task list.
-
Insert a new row: To add a new task, insert a row in your task list. Right-click on the row number where you want to insert the task and select "Insert." This creates a new row for your task.
-
Enter task information: In the newly inserted row, fill in the information for the task. Typically, this includes the task name, start date, duration, and any dependencies. Be sure to follow the format of your existing task entries.
-
Update your Gantt chart: As you enter task information in the task list, your Gantt chart should automatically update to reflect the newly added task. The task bar should appear in the chart with the specified start date and duration.
Managing Tasks:
-
Editing tasks: To make changes to an existing task, simply click on the cell where the task information is located, and you can edit the task's name, start date, duration, or other details. Ensure that your changes are accurate and in line with your project requirements.
-
Reordering tasks: If your project task order changes, you can easily reorder tasks by selecting the entire row corresponding to the task and dragging it to the desired position.
-
Deleting tasks: If a task is no longer part of the project, you can delete it by selecting the row associated with the task and right-clicking to choose "Delete."
-
Updating dependencies: If there are changes in task dependencies, you can update them in your task list. Make sure the dependent tasks are accurately reflected, so your Gantt chart correctly displays these relationships.
-
Adjusting task durations: You can change the duration of a task by simply editing the cell that contains the task's duration. The Gantt chart will update accordingly to reflect the new duration.
-
Critical path adjustments: Be mindful of how task changes affect the critical path of your project. If you alter tasks with dependencies, it may impact the critical path, potentially affecting project timelines.
Properly adding and managing tasks in your Excel 2013 Gantt chart is essential for maintaining an accurate and up-to-date project schedule. Regularly review and adjust your task list and the Gantt chart to ensure that they accurately reflect the project's progress and requirements. This will help you effectively track and manage your project's timeline and ensure its successful completion.
Setting Dependencies
Setting task dependencies in your Excel 2013 Gantt chart is a pivotal step in project management. Task dependencies define the order in which activities should be carried out, ensuring that tasks are completed in a logical and coordinated manner. This not only helps maintain project integrity but also aids in identifying potential bottlenecks or issues that could affect the project's timeline. By establishing clear dependencies, you create a roadmap for task execution, providing project stakeholders with a transparent and structured view of how their project will unfold.
Excel's Gantt chart, when properly configured with task dependencies, can automatically adjust task start dates based on the completion of predecessor tasks. This feature streamlines project management by enabling real-time updates, allowing project managers to assess progress, optimize schedules, and efficiently allocate resources. Whether your project involves simple sequential tasks or intricate interdependencies, setting task dependencies within Excel 2013's Gantt chart provides a robust foundation for managing and tracking projects, ultimately contributing to successful project delivery and on-time completion.
Adjusting Timeframes
Adjusting timeframes in an Excel 2013 Gantt chart is a pivotal activity in project management, as it enables project managers to accommodate changes, adapt to unforeseen challenges, and maintain project timelines. Whether extending task durations to accommodate unexpected delays or shortening them to seize new opportunities, these adjustments allow project managers to keep their projects on course. By simply dragging task bars to new dates or modifying durations in the task list, project managers can maintain agility in their project management approach.
Additionally, modifying timeframes requires a careful review of task dependencies to ensure that changes do not disrupt the logical sequence of tasks. The critical path, which determines the project's overall duration, should also be reviewed to ensure it aligns with the adjusted timeline. Clear communication with the project team and stakeholders regarding these adjustments is vital to keep everyone informed and aligned with the new schedule. Excel's Gantt chart, with its flexibility in adjusting timeframes, proves invaluable in responding to the dynamic nature of project management and maintaining successful project execution.
Critical Path Analysis
Critical Path Analysis (CPA) is a fundamental project management technique, and in the context of a Gantt chart created in Excel 2013, it plays a vital role in identifying the project's critical path, which is akin to the project's lifeline. By establishing dependencies and accurately determining task durations, Excel's Gantt chart feature can automatically calculate the critical path. This path represents the sequence of tasks that, if delayed, would extend the project's overall duration. Project managers can then focus their attention on the critical tasks, ensuring they are executed efficiently and on time. Excel's Gantt chart simplifies the visualization and management of these critical tasks, providing a clear roadmap for project success.
Moreover, critical path analysis is an ongoing process. Project managers must continually monitor task progress and address any deviations promptly. The Excel Gantt chart allows for real-time tracking of task status, making it easier to identify potential delays and enabling timely adjustments to mitigate their impact. By consistently applying CPA within the Gantt chart, project managers gain a powerful tool to ensure project success, timely delivery, and effective resource allocation, ultimately optimizing project management and fostering a culture of efficiency and productivity within the team.
Resource Management
Resource management within the framework of an Excel 2013 Gantt chart is a pivotal element of project management, as it empowers project managers to optimize the allocation of human resources, an invaluable asset for project success. By identifying the specific roles, skills, and quantities of team members required for each task and assigning them within the Gantt chart, managers can create a detailed roadmap for the project's execution. This allocation streamlines task assignment, enhances accountability, and ensures that the right resources are available at the right time, contributing to project efficiency and productivity.
Furthermore, resource management extends beyond mere allocation. Excel's Gantt chart can help with resource leveling to balance workloads and prevent resource overallocation or underutilization. This dynamic feature enables project managers to adapt to shifting project demands and unexpected resource constraints. By integrating resource management into a Gantt chart, project teams are better equipped to optimize resource utilization, minimize conflicts, and deliver projects within scope, on time, and within budget.
Tracking Progress
Tracking progress is a critical part of project management, and in the context of a Gantt chart created in Excel 2013, it allows project managers to monitor the project's advancement and ensure that it stays on schedule. Here's a guide on how to effectively track progress using your Gantt chart:
1. Update Task Completion:
As tasks are completed, update the Gantt chart to reflect their progress. In Excel 2013, you can do this by adjusting the percent completion or changing the colors of task bars.
2. Track Milestones:
Pay special attention to project milestones, which mark significant project achievements. Ensure that these are reached as planned and update your Gantt chart accordingly.
3. Record Delays and Issues:
If any tasks are delayed or if issues arise, document these in your Gantt chart. Make sure to explain the reasons for the delays and any planned corrective actions.
4. Compare Actual vs. Planned Progress:
Regularly compare the actual progress with the planned schedule. Excel's Gantt chart can help you visualize this comparison, highlighting where the project is on track and where adjustments are needed.
5. Use Color Coding:
Color coding can be a useful technique in Excel 2013. You can assign different colors to tasks to indicate their status, such as "on schedule," "delayed," or "completed." This provides a quick visual overview of the project's health.
6. Regular Reporting:
Provide regular progress reports to your project team and stakeholders, using the Gantt chart as a visual aid. Clearly communicate any changes in the project schedule or scope and discuss the impact of these changes.
7. Adjust the Gantt Chart:
If there are significant changes in the project timeline or scope, make corresponding adjustments in your Gantt chart. Ensure that the chart remains an accurate reflection of the project's status and plans.
8. Critical Path Review:
Revisit the critical path and assess if any tasks on it are at risk of delaying the project. Take necessary actions to mitigate such risks and maintain the project's critical path on schedule.
By tracking progress in your Gantt chart, project managers gain a real-time understanding of how the project is evolving. This enables them to make informed decisions, take corrective actions when needed, and ensure that the project remains on track to meet its objectives and deadlines. Excel's Gantt chart is a powerful tool for visualizing and managing progress, making it an essential asset for effective project management.
Exporting and Sharing
Exporting and sharing your Gantt chart, crafted in Excel 2013, is the bridge that connects your project management insights with your project team and stakeholders. The process begins with selecting the appropriate file format based on your communication needs—PDF for a static document, image formats for presentations and reports, or an editable Excel workbook for more collaborative environments. Once exported, you can utilize a range of sharing methods, including email, cloud storage platforms, or project management tools. This dissemination not only facilitates communication but also encourages collaborative editing, real-time feedback, and secure access control.
Sharing the Gantt chart link via cloud storage or embedding it into project documents and reports enhances accessibility and provides context within a broader project narrative. Keep in mind that sharing is an ongoing process; as your project progresses, regularly update and distribute the Gantt chart to reflect changes, thereby maintaining clarity, alignment, and accountability among all project stakeholders. Exporting and sharing your Gantt chart is not just a practical step; it's a fundamental practice for effective project management, fostering transparency, collaboration, and informed decision-making throughout the project lifecycle.
How to obtain Microsoft Excel 2013 Advanced Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop
Microsoft : Microsoft Excel 2013 Advanced Certification
Conclusion
In the ever-evolving landscape of project management, Excel 2013 has emerged as a steadfast and robust companion. Our journey through the world of Gantt charts and timelines within Excel 2013 has unveiled its remarkable ability to convert data into actionable insights. Gantt charts, with their visual representation of project tasks and dependencies, offer project managers a dynamic tool to plan, execute, and track projects effectively. Excel's proficiency in project timelines empowers teams to stay informed and proactive, with real-time status updates guiding them toward project milestones. Together, these features within Excel 2013 foster transparency, collaboration, and informed decision-making, ensuring that projects are not only completed on time but with greater efficiency and precision.
As we conclude, it is evident that Excel 2013's capabilities extend well beyond its reputation as a spreadsheet software. It is a foundational asset in the toolkit of any project manager seeking to navigate the complexities of project planning, execution, and monitoring. With Gantt charts and timelines at your disposal, Excel 2013 has the potential to revolutionize the way you approach and succeed in project management. In this ever-dynamic landscape, where the demand for timely and efficient project delivery is paramount, Excel 2013 stands as an enduring and indispensable partner, ready to assist you in achieving your project management goals.
The Role of Minitab in Quality Control and Six Sigma
In an era where data is the lifeblood of informed decision-making, organizations across diverse industries strive for excellence in quality control and process improvement. Six Sigma, a methodology focused on minimizing defects and variations, stands as a beacon of efficiency and quality. At the heart of this data-driven revolution lies Minitab, a versatile statistical software package. In this blog, we embark on a journey to explore "The Role of Minitab in Quality Control and Six Sigma." We will unravel how Minitab empowers professionals and organizations to harness the power of data, streamline processes, and elevate quality standards. From hypothesis testing and control charts to regression analysis and root cause analysis, Minitab serves as an indispensable tool, enabling the pursuit of data-driven excellence and the achievement of Six Sigma's lofty goals. Join us as we delve into the essential role that Minitab plays in the world of quality control and process improvement, where data reigns supreme and continuous improvement is the ultimate objective.
Table of contents
-
Introduction to Minitab
-
How Minitab Facilitates Data Analysis in Six Sigma Projects
-
Minitab and DMAIC
-
Statistical Analysis with Minitab
-
Creating Control Charts with Minitab
-
Hypothesis Testing in Minitab
-
Regression Analysis in Minitab
-
Design of Experiments (DOE) Made Easy with Minitab
-
Using Minitab for Root Cause Analysis
-
Conclusion
Introduction to Minitab
Minitab is a versatile and powerful statistical software package used extensively in data analysis, quality control, and process improvement. With a user-friendly interface and a comprehensive set of statistical tools, Minitab enables professionals and organizations to analyze data, make data-driven decisions, and enhance the quality of products and services. It offers a wide range of features, including data import from various sources, hypothesis testing, regression analysis, control chart creation, and process capability analysis. Minitab's compatibility with Six Sigma methodologies further enhances its appeal as it aligns seamlessly with the DMAIC (Define, Measure, Analyze, Improve, Control) framework, making it a go-to tool for professionals aiming to optimize processes and achieve higher quality standards in various industries.
Professionals from diverse fields, including manufacturing, healthcare, finance, and education, rely on Minitab to uncover insights from data and drive continuous improvement. Minitab's accessibility through various licensing options, coupled with its extensive learning resources and tutorials, makes it suitable for both beginners and experienced statisticians. As data analysis continues to play a pivotal role in decision-making, Minitab remains a valuable asset, helping individuals and organizations harness the power of data to achieve their goals and maintain a competitive edge in their respective industries.
How Minitab Facilitates Data Analysis in Six Sigma Projects
Minitab plays a crucial role in facilitating data analysis within Six Sigma projects by providing a robust set of tools and features tailored to the methodology's DMAIC (Define, Measure, Analyze, Improve, Control) framework. Here's how Minitab contributes to each phase of a Six Sigma project:
-
Define Phase: Minitab assists in defining project goals, scope, and metrics by helping users collect and organize data. It can be used to create project charters and establish clear objectives. Additionally, it supports the creation of process maps and flowcharts, aiding in the identification of potential improvement areas.
-
Measure Phase: In this phase, Minitab enables users to collect and analyze data to quantify the current state of a process. It simplifies data entry, statistical calculations, and the creation of graphical representations such as histograms and box plots. Minitab's capabilities for measurement system analysis (MSA) ensure that data collection methods are reliable, a fundamental aspect of Six Sigma.
-
Analyze Phase: Minitab shines in the Analyze phase by offering a wide range of statistical tools. It simplifies hypothesis testing, regression analysis, and design of experiments (DOE), helping users identify the root causes of process issues and validate potential improvement factors. Users can also create various graphical representations to visualize data relationships, making it easier to pinpoint areas for improvement.
-
Improve Phase: Minitab supports users in implementing and testing improvement solutions. It assists in optimizing processes by conducting Monte Carlo simulations, which evaluate the impact of different variables on process performance. This phase also benefits from Minitab's capabilities for factorial experiments and response surface methodology (RSM).
-
Control Phase: Finally, in the Control phase, Minitab aids in establishing control mechanisms to sustain process improvements. Users can create control charts, set control limits, and monitor process stability over time. Minitab also helps in documenting standard operating procedures and creating visual aids for training and continuous monitoring.
Overall, Minitab's user-friendly interface, extensive statistical capabilities, and alignment with Six Sigma principles make it an indispensable tool for data analysis throughout the DMAIC framework. It empowers Six Sigma practitioners to make data-driven decisions, identify process improvements, and drive quality and efficiency enhancements in their organizations.
Minitab and DMAIC
Minitab and DMAIC are two pillars of success in Six Sigma methodology, working hand in hand to achieve process improvement and quality enhancement. Minitab, as a statistical software tool, is well-aligned with the DMAIC framework's five phases, from defining project objectives to controlling and maintaining process improvements. It simplifies data collection, organizes information, conducts robust statistical analyses, and assists in visualizing data relationships, enabling Six Sigma practitioners to make informed decisions at each stage of the project. Whether it's hypothesis testing in the Analyze phase or creating control charts in the Control phase, Minitab provides the necessary tools and features to drive data-driven excellence within a Six Sigma context.
The synergy between Minitab and DMAIC empowers organizations to identify and address process inefficiencies, reduce defects, and enhance overall quality. Minitab's user-friendly interface and comprehensive statistical capabilities streamline the application of Six Sigma principles, making it a vital asset for professionals and teams dedicated to process optimization and continuous improvement. By leveraging Minitab in conjunction with DMAIC, businesses can achieve higher quality standards, reduced variability, and increased customer satisfaction, ultimately leading to improved competitiveness and success in today's competitive marketplace.
Statistical Analysis with Minitab
Statistical analysis with Minitab is a dynamic and versatile process that empowers individuals and organizations to extract meaningful insights from data. Minitab's user-friendly interface simplifies the often complex world of statistics, enabling users to perform a wide range of statistical analyses with ease. From conducting hypothesis tests and regression analysis to creating control charts and designing experiments, Minitab provides a comprehensive suite of tools to address diverse analytical needs. Moreover, its ability to generate clear and compelling visualizations enhances the understanding and communication of statistical findings. Minitab's role extends beyond just number crunching; it fosters data-driven decision-making, supports quality control efforts, and aids in process optimization, ultimately contributing to improved outcomes and greater efficiency across various domains.
Whether in the realms of business, academia, healthcare, or manufacturing, statistical analysis with Minitab empowers professionals to uncover trends, identify patterns, and make informed choices based on data-driven evidence. Its widespread adoption in quality control, Six Sigma projects, research, and beyond underscores its importance as a valuable tool for data analysis and decision support. In an era where data is increasingly integral to success, Minitab remains a reliable and indispensable partner, ensuring that the power of statistics is accessible and actionable for individuals and organizations alike.
Creating Control Charts with Minitab
Creating control charts with Minitab is a cornerstone of effective quality control and process monitoring. Minitab's user-friendly interface and extensive charting capabilities make it accessible to both beginners and experienced quality professionals. With Minitab, users can effortlessly generate a variety of control charts, such as X-bar and R charts for continuous data or p-charts for attribute data, with just a few clicks. The software automatically calculates control limits, plots data points, and highlights potential issues in a visually intuitive manner.
Interpreting these control charts is equally straightforward; users can quickly identify trends, shifts, or outliers that might indicate process instability. Minitab empowers organizations to proactively address quality issues, reduce defects, and enhance process performance by providing a comprehensive solution for monitoring and maintaining control over critical processes. Its role in facilitating the creation and interpretation of control charts ensures that organizations can achieve and sustain the highest standards of quality control and efficiency, fostering continuous improvement in their operations.
Hypothesis Testing in Minitab
Here are the steps to perform hypothesis testing in Minitab in simple points:
-
Data Entry: Enter your data into Minitab.
-
Select Test: Choose the specific hypothesis test you need (e.g., t-test, ANOVA) from Minitab's menu.
-
Define Hypotheses: State your null hypothesis (H0) and alternative hypothesis (Ha).
-
Perform the Test: Minitab calculates the test statistic and p-value based on your data.
-
Interpret Results: If p-value is smaller than your chosen significance level, reject the null hypothesis. If not, fail to reject it.
-
Draw Conclusions: Make decisions based on the p-value and the specific hypothesis test.
-
Generate Reports: Create reports and visualizations of your results using Minitab's tools.
Minitab simplifies hypothesis testing, making it accessible for making data-driven decisions in various fields.
Regression Analysis in Minitab
Regression analysis in Minitab is a powerful tool for understanding and quantifying relationships between variables. With a straightforward interface, it enables users to perform a wide range of regression analyses, from simple linear regressions to more complex multiple regression models. Users begin by entering their data and specifying the response and predictor variables of interest. Minitab then runs the analysis, providing crucial statistics such as coefficients, p-values, and R-squared values that help assess the strength and significance of these relationships.
Interpreting the results is made accessible, allowing users to draw meaningful conclusions and make predictions based on their data. Whether it's uncovering the factors that impact sales figures, evaluating the effectiveness of marketing campaigns, or making informed decisions in research, Minitab's regression analysis capabilities simplify the process, making it an indispensable resource for professionals across diverse fields. Its ability to visualize data and generate comprehensive reports further enhances its utility, ensuring that organizations can harness the power of regression analysis for data-driven insights and improved decision-making.
Design of Experiments (DOE) Made Easy with Minitab
Design of Experiments (DOE) is a systematic approach for conducting experiments to optimize processes, improve products, and identify critical factors affecting outcomes. Minitab, a widely used statistical software, simplifies the entire DOE process, making it accessible to both beginners and experienced practitioners. Here's how Minitab makes DOE easy:
-
Experimental Design Wizard: Minitab offers an intuitive Experimental Design Wizard that guides users through the DOE process step by step. This tool helps users select the appropriate design type, define factors and responses, and choose the levels of these factors.
-
Design Selection: Minitab provides a variety of design types, including full factorial, fractional factorial, response surface, and mixture designs. Users can easily select the design that suits their specific experiment requirements.
-
Factorial and Fractional Factorial Designs: Minitab automatically generates the necessary experimental runs and assigns factor settings based on the chosen design. This simplifies the planning process and reduces the number of experimental trials needed, saving time and resources.
-
Response Optimization: Minitab helps users analyze the results of their experiments by fitting models and optimizing responses. It provides visualizations, contour plots, and response surface plots that aid in understanding the relationships between factors and responses.
-
Robust Parameter Design (RPD): Minitab includes tools for conducting robust parameter design, which allows users to optimize processes while considering variability and noise factors, ensuring robust and reliable outcomes.
-
Analysis of Variance (ANOVA): Minitab automates the ANOVA analysis, making it easy to identify significant factors and interactions in the experimental data.
-
Data Visualization: Minitab's graphical capabilities help users visualize the effects of factors on responses, facilitating the interpretation of results.
-
Statistical Output: The software generates comprehensive reports that summarize the experimental design, analysis, and optimization results, making it simple to communicate findings to stakeholders.
-
Quality Improvement: Minitab's DOE tools are particularly valuable in Six Sigma and quality improvement projects, as they enable practitioners to identify the optimal settings for process parameters that minimize defects and variation.
By providing a user-friendly interface, automated calculations, and comprehensive analysis and reporting capabilities, Minitab streamlines the design of experiments. This accessibility empowers organizations to conduct efficient and effective experiments, leading to improved processes, products, and overall quality while saving time and resources in the process.
Using Minitab for Root Cause Analysis
Minitab is a powerful ally in the process of root cause analysis, offering a comprehensive suite of statistical tools and data analysis capabilities. The journey begins by clearly defining the problem and gathering relevant data, which Minitab helps organize and prepare for analysis. Its intuitive graphical tools and descriptive statistics assist in exploring data distributions and patterns, providing valuable insights into the nature of the problem. Minitab's versatility shines during the brainstorming phase, as it aids in creating cause-and-effect diagrams to systematically identify potential causes across different categories. Once potential causes are identified, Minitab facilitates their prioritization through Pareto analysis, ensuring that the most significant factors are addressed first. Through hypothesis testing and regression analysis, Minitab helps validate hypotheses about the root causes, enabling data-driven decision-making.
Beyond analysis, Minitab supports corrective action planning and monitoring by helping organizations track the effectiveness of implemented solutions. Control charts and ongoing data analysis ensure that processes remain stable and that the identified root causes are genuinely mitigated. Finally, Minitab aids in documentation and reporting, allowing organizations to maintain a clear record of the root cause analysis process and communicate findings and actions effectively. In essence, Minitab serves as an indispensable tool for organizations committed to uncovering the underlying causes of problems and implementing data-driven solutions for process improvement and quality enhancement.
Conclusion
In conclusion, Minitab is a versatile and powerful statistical software package that plays a pivotal role in data analysis, quality control, Six Sigma projects, regression analysis, and root cause analysis. Its user-friendly interface, comprehensive statistical tools, and graphical capabilities make it accessible to both beginners and experienced professionals across various industries.
Minitab simplifies complex statistical processes, empowering users to make data-driven decisions, uncover insights from data, and optimize processes. Whether it's conducting hypothesis tests, creating control charts, designing experiments, or identifying root causes of problems, Minitab streamlines the analytical journey, saving time and resources while ensuring accurate results.
As organizations continue to rely on data-driven decision-making for success, Minitab remains a valuable asset, facilitating the pursuit of quality improvement, process optimization, and continuous excellence. Its role in supporting Six Sigma methodologies, conducting robust regression analyses, and aiding in root cause analysis positions it as a trusted partner for professionals and organizations dedicated to harnessing the power of data for growth and competitiveness.
Read More
In an era where data is the lifeblood of informed decision-making, organizations across diverse industries strive for excellence in quality control and process improvement. Six Sigma, a methodology focused on minimizing defects and variations, stands as a beacon of efficiency and quality. At the heart of this data-driven revolution lies Minitab, a versatile statistical software package. In this blog, we embark on a journey to explore "The Role of Minitab in Quality Control and Six Sigma." We will unravel how Minitab empowers professionals and organizations to harness the power of data, streamline processes, and elevate quality standards. From hypothesis testing and control charts to regression analysis and root cause analysis, Minitab serves as an indispensable tool, enabling the pursuit of data-driven excellence and the achievement of Six Sigma's lofty goals. Join us as we delve into the essential role that Minitab plays in the world of quality control and process improvement, where data reigns supreme and continuous improvement is the ultimate objective.
Table of contents
-
Introduction to Minitab
-
How Minitab Facilitates Data Analysis in Six Sigma Projects
-
Minitab and DMAIC
-
Statistical Analysis with Minitab
-
Creating Control Charts with Minitab
-
Hypothesis Testing in Minitab
-
Regression Analysis in Minitab
-
Design of Experiments (DOE) Made Easy with Minitab
-
Using Minitab for Root Cause Analysis
-
Conclusion
Introduction to Minitab
Minitab is a versatile and powerful statistical software package used extensively in data analysis, quality control, and process improvement. With a user-friendly interface and a comprehensive set of statistical tools, Minitab enables professionals and organizations to analyze data, make data-driven decisions, and enhance the quality of products and services. It offers a wide range of features, including data import from various sources, hypothesis testing, regression analysis, control chart creation, and process capability analysis. Minitab's compatibility with Six Sigma methodologies further enhances its appeal as it aligns seamlessly with the DMAIC (Define, Measure, Analyze, Improve, Control) framework, making it a go-to tool for professionals aiming to optimize processes and achieve higher quality standards in various industries.
Professionals from diverse fields, including manufacturing, healthcare, finance, and education, rely on Minitab to uncover insights from data and drive continuous improvement. Minitab's accessibility through various licensing options, coupled with its extensive learning resources and tutorials, makes it suitable for both beginners and experienced statisticians. As data analysis continues to play a pivotal role in decision-making, Minitab remains a valuable asset, helping individuals and organizations harness the power of data to achieve their goals and maintain a competitive edge in their respective industries.
How Minitab Facilitates Data Analysis in Six Sigma Projects
Minitab plays a crucial role in facilitating data analysis within Six Sigma projects by providing a robust set of tools and features tailored to the methodology's DMAIC (Define, Measure, Analyze, Improve, Control) framework. Here's how Minitab contributes to each phase of a Six Sigma project:
-
Define Phase: Minitab assists in defining project goals, scope, and metrics by helping users collect and organize data. It can be used to create project charters and establish clear objectives. Additionally, it supports the creation of process maps and flowcharts, aiding in the identification of potential improvement areas.
-
Measure Phase: In this phase, Minitab enables users to collect and analyze data to quantify the current state of a process. It simplifies data entry, statistical calculations, and the creation of graphical representations such as histograms and box plots. Minitab's capabilities for measurement system analysis (MSA) ensure that data collection methods are reliable, a fundamental aspect of Six Sigma.
-
Analyze Phase: Minitab shines in the Analyze phase by offering a wide range of statistical tools. It simplifies hypothesis testing, regression analysis, and design of experiments (DOE), helping users identify the root causes of process issues and validate potential improvement factors. Users can also create various graphical representations to visualize data relationships, making it easier to pinpoint areas for improvement.
-
Improve Phase: Minitab supports users in implementing and testing improvement solutions. It assists in optimizing processes by conducting Monte Carlo simulations, which evaluate the impact of different variables on process performance. This phase also benefits from Minitab's capabilities for factorial experiments and response surface methodology (RSM).
-
Control Phase: Finally, in the Control phase, Minitab aids in establishing control mechanisms to sustain process improvements. Users can create control charts, set control limits, and monitor process stability over time. Minitab also helps in documenting standard operating procedures and creating visual aids for training and continuous monitoring.
Overall, Minitab's user-friendly interface, extensive statistical capabilities, and alignment with Six Sigma principles make it an indispensable tool for data analysis throughout the DMAIC framework. It empowers Six Sigma practitioners to make data-driven decisions, identify process improvements, and drive quality and efficiency enhancements in their organizations.
Minitab and DMAIC
Minitab and DMAIC are two pillars of success in Six Sigma methodology, working hand in hand to achieve process improvement and quality enhancement. Minitab, as a statistical software tool, is well-aligned with the DMAIC framework's five phases, from defining project objectives to controlling and maintaining process improvements. It simplifies data collection, organizes information, conducts robust statistical analyses, and assists in visualizing data relationships, enabling Six Sigma practitioners to make informed decisions at each stage of the project. Whether it's hypothesis testing in the Analyze phase or creating control charts in the Control phase, Minitab provides the necessary tools and features to drive data-driven excellence within a Six Sigma context.
The synergy between Minitab and DMAIC empowers organizations to identify and address process inefficiencies, reduce defects, and enhance overall quality. Minitab's user-friendly interface and comprehensive statistical capabilities streamline the application of Six Sigma principles, making it a vital asset for professionals and teams dedicated to process optimization and continuous improvement. By leveraging Minitab in conjunction with DMAIC, businesses can achieve higher quality standards, reduced variability, and increased customer satisfaction, ultimately leading to improved competitiveness and success in today's competitive marketplace.
Statistical Analysis with Minitab
Statistical analysis with Minitab is a dynamic and versatile process that empowers individuals and organizations to extract meaningful insights from data. Minitab's user-friendly interface simplifies the often complex world of statistics, enabling users to perform a wide range of statistical analyses with ease. From conducting hypothesis tests and regression analysis to creating control charts and designing experiments, Minitab provides a comprehensive suite of tools to address diverse analytical needs. Moreover, its ability to generate clear and compelling visualizations enhances the understanding and communication of statistical findings. Minitab's role extends beyond just number crunching; it fosters data-driven decision-making, supports quality control efforts, and aids in process optimization, ultimately contributing to improved outcomes and greater efficiency across various domains.
Whether in the realms of business, academia, healthcare, or manufacturing, statistical analysis with Minitab empowers professionals to uncover trends, identify patterns, and make informed choices based on data-driven evidence. Its widespread adoption in quality control, Six Sigma projects, research, and beyond underscores its importance as a valuable tool for data analysis and decision support. In an era where data is increasingly integral to success, Minitab remains a reliable and indispensable partner, ensuring that the power of statistics is accessible and actionable for individuals and organizations alike.
Creating Control Charts with Minitab
Creating control charts with Minitab is a cornerstone of effective quality control and process monitoring. Minitab's user-friendly interface and extensive charting capabilities make it accessible to both beginners and experienced quality professionals. With Minitab, users can effortlessly generate a variety of control charts, such as X-bar and R charts for continuous data or p-charts for attribute data, with just a few clicks. The software automatically calculates control limits, plots data points, and highlights potential issues in a visually intuitive manner.
Interpreting these control charts is equally straightforward; users can quickly identify trends, shifts, or outliers that might indicate process instability. Minitab empowers organizations to proactively address quality issues, reduce defects, and enhance process performance by providing a comprehensive solution for monitoring and maintaining control over critical processes. Its role in facilitating the creation and interpretation of control charts ensures that organizations can achieve and sustain the highest standards of quality control and efficiency, fostering continuous improvement in their operations.
Hypothesis Testing in Minitab
Here are the steps to perform hypothesis testing in Minitab in simple points:
-
Data Entry: Enter your data into Minitab.
-
Select Test: Choose the specific hypothesis test you need (e.g., t-test, ANOVA) from Minitab's menu.
-
Define Hypotheses: State your null hypothesis (H0) and alternative hypothesis (Ha).
-
Perform the Test: Minitab calculates the test statistic and p-value based on your data.
-
Interpret Results: If p-value is smaller than your chosen significance level, reject the null hypothesis. If not, fail to reject it.
-
Draw Conclusions: Make decisions based on the p-value and the specific hypothesis test.
-
Generate Reports: Create reports and visualizations of your results using Minitab's tools.
Minitab simplifies hypothesis testing, making it accessible for making data-driven decisions in various fields.
Regression Analysis in Minitab
Regression analysis in Minitab is a powerful tool for understanding and quantifying relationships between variables. With a straightforward interface, it enables users to perform a wide range of regression analyses, from simple linear regressions to more complex multiple regression models. Users begin by entering their data and specifying the response and predictor variables of interest. Minitab then runs the analysis, providing crucial statistics such as coefficients, p-values, and R-squared values that help assess the strength and significance of these relationships.
Interpreting the results is made accessible, allowing users to draw meaningful conclusions and make predictions based on their data. Whether it's uncovering the factors that impact sales figures, evaluating the effectiveness of marketing campaigns, or making informed decisions in research, Minitab's regression analysis capabilities simplify the process, making it an indispensable resource for professionals across diverse fields. Its ability to visualize data and generate comprehensive reports further enhances its utility, ensuring that organizations can harness the power of regression analysis for data-driven insights and improved decision-making.
Design of Experiments (DOE) Made Easy with Minitab
Design of Experiments (DOE) is a systematic approach for conducting experiments to optimize processes, improve products, and identify critical factors affecting outcomes. Minitab, a widely used statistical software, simplifies the entire DOE process, making it accessible to both beginners and experienced practitioners. Here's how Minitab makes DOE easy:
-
Experimental Design Wizard: Minitab offers an intuitive Experimental Design Wizard that guides users through the DOE process step by step. This tool helps users select the appropriate design type, define factors and responses, and choose the levels of these factors.
-
Design Selection: Minitab provides a variety of design types, including full factorial, fractional factorial, response surface, and mixture designs. Users can easily select the design that suits their specific experiment requirements.
-
Factorial and Fractional Factorial Designs: Minitab automatically generates the necessary experimental runs and assigns factor settings based on the chosen design. This simplifies the planning process and reduces the number of experimental trials needed, saving time and resources.
-
Response Optimization: Minitab helps users analyze the results of their experiments by fitting models and optimizing responses. It provides visualizations, contour plots, and response surface plots that aid in understanding the relationships between factors and responses.
-
Robust Parameter Design (RPD): Minitab includes tools for conducting robust parameter design, which allows users to optimize processes while considering variability and noise factors, ensuring robust and reliable outcomes.
-
Analysis of Variance (ANOVA): Minitab automates the ANOVA analysis, making it easy to identify significant factors and interactions in the experimental data.
-
Data Visualization: Minitab's graphical capabilities help users visualize the effects of factors on responses, facilitating the interpretation of results.
-
Statistical Output: The software generates comprehensive reports that summarize the experimental design, analysis, and optimization results, making it simple to communicate findings to stakeholders.
-
Quality Improvement: Minitab's DOE tools are particularly valuable in Six Sigma and quality improvement projects, as they enable practitioners to identify the optimal settings for process parameters that minimize defects and variation.
By providing a user-friendly interface, automated calculations, and comprehensive analysis and reporting capabilities, Minitab streamlines the design of experiments. This accessibility empowers organizations to conduct efficient and effective experiments, leading to improved processes, products, and overall quality while saving time and resources in the process.
Using Minitab for Root Cause Analysis
Minitab is a powerful ally in the process of root cause analysis, offering a comprehensive suite of statistical tools and data analysis capabilities. The journey begins by clearly defining the problem and gathering relevant data, which Minitab helps organize and prepare for analysis. Its intuitive graphical tools and descriptive statistics assist in exploring data distributions and patterns, providing valuable insights into the nature of the problem. Minitab's versatility shines during the brainstorming phase, as it aids in creating cause-and-effect diagrams to systematically identify potential causes across different categories. Once potential causes are identified, Minitab facilitates their prioritization through Pareto analysis, ensuring that the most significant factors are addressed first. Through hypothesis testing and regression analysis, Minitab helps validate hypotheses about the root causes, enabling data-driven decision-making.
Beyond analysis, Minitab supports corrective action planning and monitoring by helping organizations track the effectiveness of implemented solutions. Control charts and ongoing data analysis ensure that processes remain stable and that the identified root causes are genuinely mitigated. Finally, Minitab aids in documentation and reporting, allowing organizations to maintain a clear record of the root cause analysis process and communicate findings and actions effectively. In essence, Minitab serves as an indispensable tool for organizations committed to uncovering the underlying causes of problems and implementing data-driven solutions for process improvement and quality enhancement.
Conclusion
In conclusion, Minitab is a versatile and powerful statistical software package that plays a pivotal role in data analysis, quality control, Six Sigma projects, regression analysis, and root cause analysis. Its user-friendly interface, comprehensive statistical tools, and graphical capabilities make it accessible to both beginners and experienced professionals across various industries.
Minitab simplifies complex statistical processes, empowering users to make data-driven decisions, uncover insights from data, and optimize processes. Whether it's conducting hypothesis tests, creating control charts, designing experiments, or identifying root causes of problems, Minitab streamlines the analytical journey, saving time and resources while ensuring accurate results.
As organizations continue to rely on data-driven decision-making for success, Minitab remains a valuable asset, facilitating the pursuit of quality improvement, process optimization, and continuous excellence. Its role in supporting Six Sigma methodologies, conducting robust regression analyses, and aiding in root cause analysis positions it as a trusted partner for professionals and organizations dedicated to harnessing the power of data for growth and competitiveness.
How to Build a Career in Risk Management with PMI-RMP Certification
In a world marked by volatility, uncertainty, and complexity, risk management has emerged as a pivotal discipline, safeguarding organizations from unforeseen challenges and ensuring their sustainability. The role of risk managers has evolved into a cornerstone of modern business strategy, making it a highly sought-after and rewarding career path. One of the key milestones on the journey to becoming a proficient risk management professional is obtaining the PMI-RMP (Project Management Institute - Risk Management Professional) certification. This certification not only validates one's expertise in risk management but also opens doors to a realm of career opportunities across a myriad of industries and sectors.
In this blog, we will delve into the dynamic field of risk management and explore the steps to build a thriving career with the PMI-RMP certification. From understanding the fundamentals of risk management to meeting the eligibility requirements, preparing diligently for the certification exam, and navigating the intricacies of practical experience, this guide will serve as a compass for those embarking on a journey towards becoming a trusted guardian of organizations in an ever-changing world. So, fasten your seatbelts as we navigate the exciting terrain of building a career in risk management with the esteemed PMI-RMP certification.
Table of contents
-
Introduction to PMI-RMP Certification
-
Eligibility and Exam Requirements
-
Preparing for the PMI-RMP Exam
-
Benefits of PMI-RMP Certification
-
Career Opportunities in Risk Management
-
Gaining Practical Experience
-
Continuous Learning and Professional Development
-
Networking and Building Professional Relationships
-
Career Advancement with PMI-RMP
-
Conclusion
Introduction to PMI-RMP Certification
PMI-RMP (Project Management Institute - Risk Management Professional) certification is a prestigious credential recognized globally for its emphasis on risk management within the context of project management. This certification is designed for professionals who are involved in identifying, assessing, and mitigating risks to ensure successful project outcomes. It signifies an individual's specialized expertise in risk management processes, making them valuable assets to organizations across various industries.
PMI-RMP certification offers numerous benefits, including enhanced career prospects, increased earning potential, and a competitive edge in the job market. It is a testament to a professional's commitment to continuous learning and the highest standards of risk management practices. Furthermore, PMI-RMP certification connects individuals with a global network of like-minded professionals and provides access to valuable resources, enabling them to stay at the forefront of risk management innovation. In summary, PMI-RMP certification is an invaluable asset for anyone seeking a rewarding career in risk management and project management, offering recognition, expertise, and opportunities for growth.
Eligibility and Exam Requirements
Eligibility and exam requirements for PMI-RMP (Project Management Institute - Risk Management Professional) certification are essential aspects of the certification process. Here, we'll delve into the prerequisites and details you need to know to pursue this certification:
Eligibility Requirements: To be eligible for the PMI-RMP certification exam, candidates must meet certain educational and professional criteria. These include:
-
Educational Requirements:
-
A high school diploma or global equivalent.
-
Four years (or 4,500 hours) of project risk management experience within the last five years.
OR
-
A Bachelor's Degree or Higher:
-
A four-year degree (or global equivalent).
-
Three years (or 3,000 hours) of project risk management experience within the last five years.
Exam Requirements: Once you meet the eligibility criteria, you can proceed with the PMI-RMP certification process, which includes:
-
Exam Application: Candidates need to submit an application through the PMI website, providing details of their education and project risk management experience. The application is reviewed by PMI for completeness and accuracy.
-
Payment: You must pay the examination fee, which varies for PMI members and non-members. PMI members typically receive a discount on the exam fee.
-
Scheduling the Exam: After your application is approved, you can schedule the PMI-RMP exam at a Pearson VUE test center or, in some cases, take it online. PMI provides information on scheduling options and available exam centers.
-
Exam Format: The PMI-RMP exam is a computer-based exam consisting of 170 multiple-choice questions. Of these, 150 questions are scored, and 20 are pretest questions used for future exam development. Candidates have 3.5 hours to complete the exam.
-
Passing Score: PMI doesn't disclose the passing score for the PMI-RMP exam. It is based on a psychometric analysis of the questions and is not a fixed percentage.
-
Maintaining Certification: To maintain your PMI-RMP certification, you must earn 30 Professional Development Units (PDUs) in risk management-related activities every three years and retake the PMI-RMP exam every three years to renew your certification.
Understanding these eligibility and exam requirements is crucial for individuals looking to pursue PMI-RMP certification. Meeting the prerequisites and successfully passing the exam demonstrate your expertise in project risk management, enhancing your career prospects in this field.
Preparing for the PMI-RMP Exam
-
Understand the Exam Outline: Familiarize yourself with what the exam covers by reviewing the PMI-RMP Exam Content Outline.
-
Use Official Resources: Utilize PMI's official resources, like the PMI-RMP Handbook and Content Outline.
-
Study Materials: Invest in quality study materials such as books and online courses.
-
Create a Study Plan: Develop a study schedule that outlines what to study each day or week.
-
Practice with Sample Questions: Use practice exams to get comfortable with the exam format and types of questions.
-
Join a Study Group: Consider joining a study group or forum to discuss concepts and share resources.
-
Understand PMBOK Concepts: Have a strong grasp of PMBOK concepts, especially in the context of risk management.
-
Simulate Exam Conditions: Take practice exams under timed conditions to prepare for the real test.
-
Focus on Weak Areas: Identify and spend extra time on areas where you feel less confident.
-
Regular Review: Continuously review the material you've studied.
-
Stay Calm on Exam Day: Get enough rest, arrive early, and stay calm during the exam.
-
Read Questions Carefully: Pay attention to keywords in questions and eliminate incorrect options.
-
Flag and Review: Flag uncertain answers for review and revisit them later.
-
Manage Time: Keep track of time during the exam to answer all questions.
-
Submit Confidently: Submit your exam confidently, and await PMI's results notification.
By following these straightforward steps, you can effectively prepare for the PMI-RMP exam and increase your chances of success.
Benefits of PMI-RMP Certification
-
Expertise: Demonstrates your expertise in risk management.
-
Global Recognition: Respected worldwide by employers and peers.
-
Career Advancement: Opens doors to higher-paying roles.
-
Earning Potential: Can lead to higher salaries.
-
Competitive Advantage: Sets you apart in job applications.
-
Networking: Connects you with a global community of professionals.
-
Project Success: Contributes to on-time, on-budget project delivery.
-
Continuous Learning: Encourages ongoing skill development.
-
Ethical Standards: Emphasizes ethical practices in risk management.
-
Versatility: Applicable across various industries.
Career Opportunities in Risk Management
A career in risk management presents a wide array of opportunities across diverse industries. Risk analysts and managers play pivotal roles in identifying, assessing, and mitigating risks that organizations face, be they financial, operational, or strategic in nature. These professionals employ quantitative and qualitative methodologies to provide critical insights that enable companies to make informed decisions and protect their interests. Credit risk analysts work within financial institutions to assess borrowers' creditworthiness, while operational risk managers focus on operational threats and process efficiency. Compliance officers ensure organizations abide by regulatory guidelines, and enterprise risk managers oversee holistic risk management strategies. Additionally, careers in areas like cybersecurity, environmental risk, healthcare, and supply chain risk management have emerged as specialized fields, reflecting the evolving complexities and demands of modern business environments.
The significance of risk management in today's global and interconnected business landscape has elevated the demand for professionals in this field. With opportunities spanning from financial institutions to healthcare, construction, and cybersecurity, individuals entering risk management can tailor their careers to align with their interests and expertise. This diversity, coupled with the potential for career advancement and competitive compensation, makes risk management an appealing and rewarding career path for those with a penchant for critical thinking, analytical skills, and a desire to safeguard organizations from unforeseen challenges.
Gaining Practical Experience
Gaining practical experience in risk management is essential for developing the skills and expertise required to excel in this field. Entry-level positions, internships, and volunteer opportunities provide invaluable exposure to real-world risk scenarios, allowing individuals to apply theoretical knowledge in practical contexts. These hands-on roles often involve tasks such as risk assessment, mitigation strategy development, and collaboration with cross-functional teams to address organizational vulnerabilities. Furthermore, networking, professional development courses, and certifications like PMI-RMP can facilitate access to practical experience opportunities while providing structured learning pathways. Additionally, staying informed through continuous learning and seeking mentorship from experienced professionals can further enhance one's ability to navigate complex risk management challenges, making practical experience a cornerstone of a successful career in this dynamic field.
In summary, practical experience in risk management is not only a means to apply theoretical knowledge but also a pathway to gaining confidence and competence in addressing real-world risks. Whether through formal roles, volunteer work, or professional development, hands-on experience equips individuals with the practical skills and insights necessary to make informed decisions and contribute effectively to an organization's risk management efforts.
Continuous Learning and Professional Development
Continuous learning and professional development are vital for success in risk management and many other fields. Here are key points about their significance:
-
Adapting to Change: Continuous learning helps professionals stay updated with evolving industry trends, technologies, and best practices. In risk management, where threats and challenges constantly change, staying current is essential.
-
Skill Enhancement: It allows individuals to enhance their skills, whether in risk assessment, data analysis, or decision-making. These skills improvements can lead to more effective risk management.
-
Career Advancement: Continuous learning and professional development can open up new career opportunities and make you a more attractive candidate for promotions and leadership roles.
-
Risk Mitigation: Being well-informed and continuously learning helps organizations anticipate and mitigate risks effectively. Professionals can proactively identify emerging risks and develop strategies to address them.
-
Certifications: Pursuing certifications, such as PMI-RMP or CRM, demonstrates a commitment to ongoing professional development and can boost career prospects.
-
Networking: Learning opportunities, seminars, and conferences provide chances to network with peers and experts, leading to valuable knowledge sharing and potential collaborations.
-
Innovation: Staying current with the latest developments in risk management can spark innovative solutions and approaches to risk mitigation.
-
Resilience: Continuous learning builds resilience by ensuring that professionals are prepared to handle unexpected challenges and disruptions.
-
Ethical Practices: Learning about evolving ethical standards in risk management ensures that professionals maintain the highest ethical practices in their work.
-
Personal Growth: Beyond career benefits, continuous learning fosters personal growth, intellectual stimulation, and a sense of accomplishment.
In summary, continuous learning and professional development are integral to staying relevant, advancing one's career, and effectively managing risks in an ever-changing world. They empower professionals to adapt, innovate, and excel in the dynamic field of risk management.
Networking and Building Professional Relationships
Networking and cultivating professional relationships are cornerstone practices for success in risk management. In this field, where dynamic challenges often demand innovative solutions, connecting with peers, experts, and industry leaders is invaluable. Networking offers a platform to share insights, learn from others' experiences, and stay updated on the latest risk management trends and strategies. Whether through attending industry conferences, joining professional associations, or engaging in online forums, these interactions provide a continuous learning opportunity that can lead to better risk assessment and mitigation.
Moreover, building a robust professional network can lead to career advancement and collaboration opportunities. It can open doors to job referrals, mentorship from seasoned professionals, and access to a wider pool of talent for cross-functional risk management teams. In essence, networking is more than just exchanging business cards; it's about creating a support system, fostering collaboration, and expanding one's horizons in the dynamic world of risk management.
Career Advancement with PMI-RMP
PMI-RMP certification serves as a powerful catalyst for career advancement in the realm of risk management. It goes beyond just validating your skills; it showcases your specialized expertise in identifying, assessing, and mitigating risks, making you a sought-after professional in industries spanning from finance to healthcare and beyond. The competitive edge it provides cannot be understated, as it distinguishes you from your peers in a crowded job market and positions you for leadership roles in risk management departments. With PMI-RMP certification, you become a trusted resource for organizations looking to navigate complexities and uncertainties effectively, propelling your career into higher-paying positions and more significant responsibilities.
Moreover, PMI-RMP fosters continuous learning and development, ensuring that you remain at the forefront of industry trends and best practices. This commitment to lifelong learning not only boosts your competence but also keeps you adaptable and innovative in an ever-evolving field. Additionally, the global recognition PMI-RMP offers broadens your horizons, potentially leading to international career opportunities and a rich network of professionals who can provide mentorship and support. In essence, PMI-RMP is a pivotal stepping stone for those aspiring to not only succeed but excel in the dynamic domain of risk management, enabling you to become a key player in shaping an organization's future.
Conclusion
In conclusion, building a successful career in risk management with PMI-RMP certification is a strategic and rewarding journey. This certification not only validates your expertise in risk management but also opens doors to a wide range of career opportunities across diverse industries. As outlined in this blog, the path to PMI-RMP certification involves meeting eligibility requirements, preparing diligently for the exam, and continuously expanding your knowledge and practical experience.
Once you've earned your PMI-RMP certification, you become a sought-after professional equipped with the skills to identify, assess, and mitigate risks effectively. This credential can lead to career advancement, increased earning potential, and a deeper understanding of risk management principles. Moreover, it connects you with a global network of like-minded professionals, fostering collaboration and growth.
In the dynamic and ever-evolving world of risk management, PMI-RMP certification stands as a symbol of excellence and dedication. It empowers individuals to make informed decisions, protect their organizations from uncertainties, and embark on a fulfilling and prosperous career in risk management. So, take the first step, set your career goals, and embark on your journey to PMI-RMP certification and a rewarding career in risk management. Your future in this dynamic field awaits, full of opportunities to make a meaningful impact.
Read More
In a world marked by volatility, uncertainty, and complexity, risk management has emerged as a pivotal discipline, safeguarding organizations from unforeseen challenges and ensuring their sustainability. The role of risk managers has evolved into a cornerstone of modern business strategy, making it a highly sought-after and rewarding career path. One of the key milestones on the journey to becoming a proficient risk management professional is obtaining the PMI-RMP (Project Management Institute - Risk Management Professional) certification. This certification not only validates one's expertise in risk management but also opens doors to a realm of career opportunities across a myriad of industries and sectors.
In this blog, we will delve into the dynamic field of risk management and explore the steps to build a thriving career with the PMI-RMP certification. From understanding the fundamentals of risk management to meeting the eligibility requirements, preparing diligently for the certification exam, and navigating the intricacies of practical experience, this guide will serve as a compass for those embarking on a journey towards becoming a trusted guardian of organizations in an ever-changing world. So, fasten your seatbelts as we navigate the exciting terrain of building a career in risk management with the esteemed PMI-RMP certification.
Table of contents
-
Introduction to PMI-RMP Certification
-
Eligibility and Exam Requirements
-
Preparing for the PMI-RMP Exam
-
Benefits of PMI-RMP Certification
-
Career Opportunities in Risk Management
-
Gaining Practical Experience
-
Continuous Learning and Professional Development
-
Networking and Building Professional Relationships
-
Career Advancement with PMI-RMP
-
Conclusion
Introduction to PMI-RMP Certification
PMI-RMP (Project Management Institute - Risk Management Professional) certification is a prestigious credential recognized globally for its emphasis on risk management within the context of project management. This certification is designed for professionals who are involved in identifying, assessing, and mitigating risks to ensure successful project outcomes. It signifies an individual's specialized expertise in risk management processes, making them valuable assets to organizations across various industries.
PMI-RMP certification offers numerous benefits, including enhanced career prospects, increased earning potential, and a competitive edge in the job market. It is a testament to a professional's commitment to continuous learning and the highest standards of risk management practices. Furthermore, PMI-RMP certification connects individuals with a global network of like-minded professionals and provides access to valuable resources, enabling them to stay at the forefront of risk management innovation. In summary, PMI-RMP certification is an invaluable asset for anyone seeking a rewarding career in risk management and project management, offering recognition, expertise, and opportunities for growth.
Eligibility and Exam Requirements
Eligibility and exam requirements for PMI-RMP (Project Management Institute - Risk Management Professional) certification are essential aspects of the certification process. Here, we'll delve into the prerequisites and details you need to know to pursue this certification:
Eligibility Requirements: To be eligible for the PMI-RMP certification exam, candidates must meet certain educational and professional criteria. These include:
-
Educational Requirements:
-
A high school diploma or global equivalent.
-
Four years (or 4,500 hours) of project risk management experience within the last five years.
OR
-
A Bachelor's Degree or Higher:
-
A four-year degree (or global equivalent).
-
Three years (or 3,000 hours) of project risk management experience within the last five years.
Exam Requirements: Once you meet the eligibility criteria, you can proceed with the PMI-RMP certification process, which includes:
-
Exam Application: Candidates need to submit an application through the PMI website, providing details of their education and project risk management experience. The application is reviewed by PMI for completeness and accuracy.
-
Payment: You must pay the examination fee, which varies for PMI members and non-members. PMI members typically receive a discount on the exam fee.
-
Scheduling the Exam: After your application is approved, you can schedule the PMI-RMP exam at a Pearson VUE test center or, in some cases, take it online. PMI provides information on scheduling options and available exam centers.
-
Exam Format: The PMI-RMP exam is a computer-based exam consisting of 170 multiple-choice questions. Of these, 150 questions are scored, and 20 are pretest questions used for future exam development. Candidates have 3.5 hours to complete the exam.
-
Passing Score: PMI doesn't disclose the passing score for the PMI-RMP exam. It is based on a psychometric analysis of the questions and is not a fixed percentage.
-
Maintaining Certification: To maintain your PMI-RMP certification, you must earn 30 Professional Development Units (PDUs) in risk management-related activities every three years and retake the PMI-RMP exam every three years to renew your certification.
Understanding these eligibility and exam requirements is crucial for individuals looking to pursue PMI-RMP certification. Meeting the prerequisites and successfully passing the exam demonstrate your expertise in project risk management, enhancing your career prospects in this field.
Preparing for the PMI-RMP Exam
-
Understand the Exam Outline: Familiarize yourself with what the exam covers by reviewing the PMI-RMP Exam Content Outline.
-
Use Official Resources: Utilize PMI's official resources, like the PMI-RMP Handbook and Content Outline.
-
Study Materials: Invest in quality study materials such as books and online courses.
-
Create a Study Plan: Develop a study schedule that outlines what to study each day or week.
-
Practice with Sample Questions: Use practice exams to get comfortable with the exam format and types of questions.
-
Join a Study Group: Consider joining a study group or forum to discuss concepts and share resources.
-
Understand PMBOK Concepts: Have a strong grasp of PMBOK concepts, especially in the context of risk management.
-
Simulate Exam Conditions: Take practice exams under timed conditions to prepare for the real test.
-
Focus on Weak Areas: Identify and spend extra time on areas where you feel less confident.
-
Regular Review: Continuously review the material you've studied.
-
Stay Calm on Exam Day: Get enough rest, arrive early, and stay calm during the exam.
-
Read Questions Carefully: Pay attention to keywords in questions and eliminate incorrect options.
-
Flag and Review: Flag uncertain answers for review and revisit them later.
-
Manage Time: Keep track of time during the exam to answer all questions.
-
Submit Confidently: Submit your exam confidently, and await PMI's results notification.
By following these straightforward steps, you can effectively prepare for the PMI-RMP exam and increase your chances of success.
Benefits of PMI-RMP Certification
-
Expertise: Demonstrates your expertise in risk management.
-
Global Recognition: Respected worldwide by employers and peers.
-
Career Advancement: Opens doors to higher-paying roles.
-
Earning Potential: Can lead to higher salaries.
-
Competitive Advantage: Sets you apart in job applications.
-
Networking: Connects you with a global community of professionals.
-
Project Success: Contributes to on-time, on-budget project delivery.
-
Continuous Learning: Encourages ongoing skill development.
-
Ethical Standards: Emphasizes ethical practices in risk management.
-
Versatility: Applicable across various industries.
Career Opportunities in Risk Management
A career in risk management presents a wide array of opportunities across diverse industries. Risk analysts and managers play pivotal roles in identifying, assessing, and mitigating risks that organizations face, be they financial, operational, or strategic in nature. These professionals employ quantitative and qualitative methodologies to provide critical insights that enable companies to make informed decisions and protect their interests. Credit risk analysts work within financial institutions to assess borrowers' creditworthiness, while operational risk managers focus on operational threats and process efficiency. Compliance officers ensure organizations abide by regulatory guidelines, and enterprise risk managers oversee holistic risk management strategies. Additionally, careers in areas like cybersecurity, environmental risk, healthcare, and supply chain risk management have emerged as specialized fields, reflecting the evolving complexities and demands of modern business environments.
The significance of risk management in today's global and interconnected business landscape has elevated the demand for professionals in this field. With opportunities spanning from financial institutions to healthcare, construction, and cybersecurity, individuals entering risk management can tailor their careers to align with their interests and expertise. This diversity, coupled with the potential for career advancement and competitive compensation, makes risk management an appealing and rewarding career path for those with a penchant for critical thinking, analytical skills, and a desire to safeguard organizations from unforeseen challenges.
Gaining Practical Experience
Gaining practical experience in risk management is essential for developing the skills and expertise required to excel in this field. Entry-level positions, internships, and volunteer opportunities provide invaluable exposure to real-world risk scenarios, allowing individuals to apply theoretical knowledge in practical contexts. These hands-on roles often involve tasks such as risk assessment, mitigation strategy development, and collaboration with cross-functional teams to address organizational vulnerabilities. Furthermore, networking, professional development courses, and certifications like PMI-RMP can facilitate access to practical experience opportunities while providing structured learning pathways. Additionally, staying informed through continuous learning and seeking mentorship from experienced professionals can further enhance one's ability to navigate complex risk management challenges, making practical experience a cornerstone of a successful career in this dynamic field.
In summary, practical experience in risk management is not only a means to apply theoretical knowledge but also a pathway to gaining confidence and competence in addressing real-world risks. Whether through formal roles, volunteer work, or professional development, hands-on experience equips individuals with the practical skills and insights necessary to make informed decisions and contribute effectively to an organization's risk management efforts.
Continuous Learning and Professional Development
Continuous learning and professional development are vital for success in risk management and many other fields. Here are key points about their significance:
-
Adapting to Change: Continuous learning helps professionals stay updated with evolving industry trends, technologies, and best practices. In risk management, where threats and challenges constantly change, staying current is essential.
-
Skill Enhancement: It allows individuals to enhance their skills, whether in risk assessment, data analysis, or decision-making. These skills improvements can lead to more effective risk management.
-
Career Advancement: Continuous learning and professional development can open up new career opportunities and make you a more attractive candidate for promotions and leadership roles.
-
Risk Mitigation: Being well-informed and continuously learning helps organizations anticipate and mitigate risks effectively. Professionals can proactively identify emerging risks and develop strategies to address them.
-
Certifications: Pursuing certifications, such as PMI-RMP or CRM, demonstrates a commitment to ongoing professional development and can boost career prospects.
-
Networking: Learning opportunities, seminars, and conferences provide chances to network with peers and experts, leading to valuable knowledge sharing and potential collaborations.
-
Innovation: Staying current with the latest developments in risk management can spark innovative solutions and approaches to risk mitigation.
-
Resilience: Continuous learning builds resilience by ensuring that professionals are prepared to handle unexpected challenges and disruptions.
-
Ethical Practices: Learning about evolving ethical standards in risk management ensures that professionals maintain the highest ethical practices in their work.
-
Personal Growth: Beyond career benefits, continuous learning fosters personal growth, intellectual stimulation, and a sense of accomplishment.
In summary, continuous learning and professional development are integral to staying relevant, advancing one's career, and effectively managing risks in an ever-changing world. They empower professionals to adapt, innovate, and excel in the dynamic field of risk management.
Networking and Building Professional Relationships
Networking and cultivating professional relationships are cornerstone practices for success in risk management. In this field, where dynamic challenges often demand innovative solutions, connecting with peers, experts, and industry leaders is invaluable. Networking offers a platform to share insights, learn from others' experiences, and stay updated on the latest risk management trends and strategies. Whether through attending industry conferences, joining professional associations, or engaging in online forums, these interactions provide a continuous learning opportunity that can lead to better risk assessment and mitigation.
Moreover, building a robust professional network can lead to career advancement and collaboration opportunities. It can open doors to job referrals, mentorship from seasoned professionals, and access to a wider pool of talent for cross-functional risk management teams. In essence, networking is more than just exchanging business cards; it's about creating a support system, fostering collaboration, and expanding one's horizons in the dynamic world of risk management.
Career Advancement with PMI-RMP
PMI-RMP certification serves as a powerful catalyst for career advancement in the realm of risk management. It goes beyond just validating your skills; it showcases your specialized expertise in identifying, assessing, and mitigating risks, making you a sought-after professional in industries spanning from finance to healthcare and beyond. The competitive edge it provides cannot be understated, as it distinguishes you from your peers in a crowded job market and positions you for leadership roles in risk management departments. With PMI-RMP certification, you become a trusted resource for organizations looking to navigate complexities and uncertainties effectively, propelling your career into higher-paying positions and more significant responsibilities.
Moreover, PMI-RMP fosters continuous learning and development, ensuring that you remain at the forefront of industry trends and best practices. This commitment to lifelong learning not only boosts your competence but also keeps you adaptable and innovative in an ever-evolving field. Additionally, the global recognition PMI-RMP offers broadens your horizons, potentially leading to international career opportunities and a rich network of professionals who can provide mentorship and support. In essence, PMI-RMP is a pivotal stepping stone for those aspiring to not only succeed but excel in the dynamic domain of risk management, enabling you to become a key player in shaping an organization's future.
Conclusion
In conclusion, building a successful career in risk management with PMI-RMP certification is a strategic and rewarding journey. This certification not only validates your expertise in risk management but also opens doors to a wide range of career opportunities across diverse industries. As outlined in this blog, the path to PMI-RMP certification involves meeting eligibility requirements, preparing diligently for the exam, and continuously expanding your knowledge and practical experience.
Once you've earned your PMI-RMP certification, you become a sought-after professional equipped with the skills to identify, assess, and mitigate risks effectively. This credential can lead to career advancement, increased earning potential, and a deeper understanding of risk management principles. Moreover, it connects you with a global network of like-minded professionals, fostering collaboration and growth.
In the dynamic and ever-evolving world of risk management, PMI-RMP certification stands as a symbol of excellence and dedication. It empowers individuals to make informed decisions, protect their organizations from uncertainties, and embark on a fulfilling and prosperous career in risk management. So, take the first step, set your career goals, and embark on your journey to PMI-RMP certification and a rewarding career in risk management. Your future in this dynamic field awaits, full of opportunities to make a meaningful impact.
Power BI and Machine Learning: Harnessing AI for Business Intelligence
In the era of data-driven decision-making, organizations are constantly seeking innovative ways to extract deeper insights from their vast troves of data. One remarkable fusion of technology has emerged as a beacon of hope on this data-rich journey: the synergy between Power BI and Machine Learning. These dynamic tools, when brought together, create a powerhouse of capabilities that go beyond conventional Business Intelligence, transcending the boundaries of static reporting and venturing into the realm of predictive and prescriptive analytics.
In this blog, we embark on a captivating exploration of "Power BI and Machine Learning: Harnessing AI for Business Intelligence." We will unravel the intricacies of this powerful partnership, uncover the benefits it offers to businesses, delve into the technical aspects of integration, and discover the real-world applications that are revolutionizing industries. Join us as we dive into a world where data becomes a strategic asset, AI becomes a trusted ally, and Business Intelligence transcends its limits.
Table of contents
-
Introduction to Power BI and Machine Learning Integration
-
Benefits of Combining Power BI with Machine Learning
-
Getting Started: Setting Up Power BI and Machine Learning
-
Data Preparation for Machine Learning in Power BI
-
Common Machine Learning Algorithms in Power BI
-
Creating Predictive Models in Power BI
-
Real-time Data and Machine Learning
-
Advanced Techniques: NLP and Text Analytics in Power BI
-
Visualizing Machine Learning Results in Power BI
-
Deploying Machine Learning Models in Power BI Reports
-
Security and Compliance Considerations
-
Challenges and Solutions
-
Future Trends in Power BI and AI
-
Best Practices for Harnessing AI in Business Intelligence
-
Conclusion
Introduction to Power BI and Machine Learning Integration
In the realm of data-driven decision-making, the integration of Power BI with machine learning represents a formidable synergy that empowers organizations to extract richer insights from their data. Power BI, developed by Microsoft, stands as a stalwart in the field of business intelligence, offering robust tools for data visualization, reporting, and analysis. On the other hand, machine learning, a facet of artificial intelligence, equips computers with the ability to learn from data, opening doors to predictive and prescriptive analytics. The need for integration arises from the recognition that while Power BI excels in descriptive analytics, it can achieve far more with the predictive and automation capabilities offered by machine learning. By merging these two technologies, businesses can elevate their decision-making processes, gain foresight into future trends, forecast outcomes, and automate routine tasks. This integration isn't just an option; it's increasingly becoming a competitive advantage, allowing companies to stay agile and responsive in a data-driven world.
The benefits of integrating Power BI and machine learning are manifold. It enables improved decision-making by offering insights that extend beyond the surface, transforming data into actionable intelligence. Predictive analytics, made accessible through this integration, equips businesses with the ability to anticipate future trends, providing a competitive edge. Furthermore, the automation capabilities of machine learning within Power BI streamline processes, freeing up valuable human resources. Throughout this blog, we will delve deeper into the technical intricacies, explore real-world applications, discuss best practices, and examine the challenges and future prospects of harnessing this potent combination of Power BI and machine learning for business intelligence.
Benefits of Combining Power BI with Machine Learning
-
Deeper Insights: Uncover hidden patterns and trends in data.
-
Predictive Analytics: Forecast future trends and outcomes.
-
Automation: Reduce manual data analysis tasks.
-
Personalized Recommendations: Improve user engagement.
-
Anomaly Detection: Automatically identify unusual patterns.
-
Efficiency and Scalability: Analyze large datasets efficiently.
-
Competitive Advantage: Stay ahead in the market.
-
Cost Reduction: Automate tasks and improve efficiency.
Getting Started: Setting Up Power BI and Machine Learning
Getting started with the integration of Power BI and machine learning involves a series of strategic steps. First, ensure you have Power BI Desktop installed, the free application for creating reports and dashboards. Then, select your machine learning environment, whether it's Python with libraries like scikit-learn or a cloud-based service like Azure Machine Learning, and make sure you have the necessary software and libraries in place. Next, establish connections to your data sources, which can include databases, spreadsheets, or cloud-based repositories. Clean and format your data for analysis, and consider any feature engineering necessary for machine learning.
With your data ready, proceed to build your machine learning model using your chosen environment. Train the model using historical data to make predictions or classifications. Depending on your setup, you may export the trained model and import it into Power BI or directly connect Power BI to your machine learning service. Then, within Power BI, design your reports and dashboards, incorporating the insights generated by your machine learning model. Utilize Power BI's data visualization tools to create interactive, user-friendly displays of your predictions or classifications. Finally, publish your reports to the Power BI Service, allowing your team to access and share the valuable insights you've gained through the integration of Power BI and machine learning. Regularly monitor and maintain your machine learning model to ensure its accuracy and relevance in your business intelligence efforts.
Data Preparation for Machine Learning in Power BI
Data preparation is a pivotal phase when integrating machine learning with Power BI for robust business intelligence. In this process, you begin by collecting data from various sources and ensuring its completeness. Cleaning the data is paramount to rectify errors, fill in missing values, and eliminate duplicates. A clean dataset serves as the bedrock for accurate machine learning results. Furthermore, data transformation may be necessary to convert categorical variables into numerical formats, standardize features, or perform aggregations. Feature selection is also vital, as it involves cherry-picking the most relevant variables while discarding the superfluous ones to enhance model accuracy and efficiency.
Subsequently, the dataset is split into training, validation, and test sets, facilitating the training and evaluation of machine learning models. Balancing imbalanced data and handling outliers are essential steps to ensure model fairness and robustness. Visualization of data offers insights and aids in decision-making regarding preprocessing strategies. Finally, data formatting, scaling, and proper handling of time series data are essential considerations in data preparation. This meticulous process not only ensures the quality of input data but also maximizes the potential of machine learning models to deliver actionable insights in Power BI. Regular monitoring and maintenance of data quality are key to sustaining the effectiveness of these models as new data streams in, keeping business intelligence efforts accurate and relevant.
Common Machine Learning Algorithms in Power BI
Power BI allows users to integrate machine learning capabilities using various algorithms to enhance their business intelligence efforts. Here are some common machine learning algorithms you can utilize within Power BI:
-
Linear Regression: Linear regression is used for predicting a continuous target variable based on one or more input features. In Power BI, it can be employed for tasks like sales forecasting or price prediction.
-
Logistic Regression: Logistic regression is suitable for binary classification problems. You can use it in Power BI for tasks such as customer churn prediction or fraud detection.
-
Decision Trees: Decision trees are used for both classification and regression tasks. They are easy to understand and can be useful in Power BI for segmenting customers or predicting outcomes based on certain criteria.
-
Random Forest: Random forests are an ensemble technique that combines multiple decision trees to improve accuracy and reduce overfitting. In Power BI, they are valuable for complex classification and regression tasks.
-
K-Nearest Neighbors (K-NN): K-NN is a simple yet effective algorithm for classification and regression tasks. It calculates predictions based on the majority class or average of the nearest neighbors. Power BI users can apply K-NN for recommendation systems or anomaly detection.
-
Support Vector Machines (SVM): SVM is used for classification tasks, especially when dealing with non-linear data. Power BI users can employ SVM for tasks like sentiment analysis or image classification.
-
Clustering Algorithms: Clustering algorithms like K-Means or Hierarchical Clustering are useful in Power BI for customer segmentation, identifying patterns, and grouping similar data points together.
-
Neural Networks: Power BI supports deep learning through integration with Azure Machine Learning, enabling the use of neural networks for tasks such as image recognition, natural language processing, and more complex predictive modeling.
-
Time Series Forecasting: Power BI includes algorithms specifically designed for time series forecasting, which is valuable for predicting future trends based on historical data. These algorithms can be employed for sales forecasting, demand prediction, and inventory management.
-
Anomaly Detection Algorithms: Power BI offers algorithms for anomaly detection, helping users identify unusual patterns or outliers in their data. This is particularly useful for fraud detection or quality control.
-
Principal Component Analysis (PCA): PCA is a dimensionality reduction technique that can be applied in Power BI to reduce the complexity of large datasets and highlight the most important features.
-
Association Rules (Apriori): Power BI supports association rule mining using the Apriori algorithm. This is useful for market basket analysis, where you identify associations between products frequently bought together.
By incorporating these machine learning algorithms into Power BI, users can derive deeper insights, make more accurate predictions, and enhance their business intelligence reports and dashboards. The choice of algorithm depends on the specific problem and the nature of the data being analyzed.
Creating Predictive Models in Power BI
Creating predictive models in Power BI involves a systematic process to turn historical data into actionable insights. It begins with thorough data preparation, ensuring that the dataset is clean and structured for analysis. The choice of a predictive algorithm, based on the nature of your data and the desired prediction type, plays a pivotal role. Power BI offers a range of algorithms, from regression models for numeric predictions to classification models for categorical outcomes. Data splitting into training, validation, and test sets is essential, as it allows you to train, fine-tune, and evaluate your model effectively. Training the model involves using historical data to teach it how to make predictions based on input features. Feature selection and parameter tuning optimize model performance, while rigorous evaluation using validation metrics ensures its accuracy. Once satisfied with the model's performance, you can deploy it within Power BI for real-time predictions. Finally, visualizations in Power BI provide an interactive means of presenting predictions, enabling users to make informed decisions.
Continuous monitoring and maintenance are critical aspects of predictive modeling in Power BI. As new data streams in, the model must be periodically retrained to maintain its accuracy and relevance. Regular assessment of data quality and model effectiveness ensures that business intelligence remains dynamic and aligned with evolving insights. The process of creating predictive models in Power BI empowers organizations to anticipate future trends, optimize operations, and make data-driven decisions, ultimately enhancing their competitiveness and efficiency in a data-centric world.
Real-time Data and Machine Learning
The synergy between real-time data and machine learning is a game-changer in the world of data analytics. Real-time data, sourced from a myriad of sensors, devices, and digital platforms, provides a constant stream of information that can be harnessed instantaneously for actionable insights. Machine learning, on the other hand, equips organizations with the ability to process this data at incredible speeds and make predictions, classifications, and recommendations in real-time. This union has transformative applications, from predicting equipment failures in manufacturing to detecting fraudulent transactions in financial services. It enables predictive analytics that allow businesses to stay one step ahead, proactive decision-making that reduces risks, and automation that streamlines operations, all while visualizing and reporting these insights through dynamic dashboards.
Moreover, real-time data and machine learning are not static; they evolve and adapt as new data arrives. Continuous learning ensures that the models remain accurate and relevant, even in dynamic environments. These technologies are particularly crucial in today's fast-paced world, where timely insights and immediate action are paramount. By integrating real-time data and machine learning, organizations can unlock the power of data-driven decision-making and gain a competitive edge in their respective industries.
Advanced Techniques: NLP and Text Analytics in Power BI
here are the key points for using NLP and text analytics in Power BI:
-
Text Data Preparation: Clean and structure unstructured text data.
-
Sentiment Analysis: Determine the sentiment (positive, negative, or neutral) of text.
-
Text Classification: Automatically categorize text into predefined groups.
-
Keyphrase Extraction: Identify important terms or phrases in text.
-
Named Entity Recognition (NER): Extract names of people, places, organizations, and more from text.
-
Topic Modeling: Discover latent topics within a collection of documents.
-
Text Visualizations: Use Power BI's visualizations for text data, such as word clouds and sentiment charts.
-
Custom Functions: Create custom functions for specialized text analytics.
-
Integration with ML Models: Combine Power BI with machine learning models for custom NLP solutions.
-
Real-time Text Analytics: Monitor and visualize text data in real-time for immediate insights and responses.
Visualizing Machine Learning Results in Power BI
Visualizing machine learning results in Power BI is a pivotal bridge between data-driven analysis and actionable insights. It begins with importing and structuring data within Power BI, including the outcomes generated by machine learning models. Power BI offers a versatile array of visualization tools, from traditional bar charts and line graphs to more advanced visualizations like heatmaps and custom visuals. These visualizations can effectively convey the results of machine learning tasks such as predictions, classification accuracy, feature importance, and model performance metrics.
Interactive dashboards in Power BI facilitate data exploration and decision-making by enabling users to filter, drill down, and interact with the data. Real-time updates and dynamic parameters keep insights current, particularly in applications where data changes frequently. By customizing themes, styles, and annotations, users can provide context and explanations, making the visualized results more comprehensible. Ultimately, visualizing machine learning results in Power BI transforms raw model outputs into actionable information that organizations can leverage to enhance operations, optimize strategies, and stay competitive in an increasingly data-centric world.
Deploying Machine Learning Models in Power BI Reports
Deploying machine learning models within Power BI reports is a strategic step toward unlocking the full potential of data-driven decision-making. It begins with the development and optimization of the machine learning model in a dedicated environment, followed by exporting the model to a format compatible with Power BI. Importing the model into Power BI Desktop and integrating it with the report's data sources is a pivotal step, ensuring that the predictions align with the visualized data. Calculated columns and measures are then created in Power BI to facilitate real-time predictions, which are seamlessly integrated into the report's visualizations. These interactive dashboards empower users to explore and interact with data, providing a dynamic and user-friendly interface for decision-makers.
After fine-tuning the report, it can be published to the Power BI Service, where authorized users across the organization can access and benefit from the integrated machine learning insights. Scheduled data refreshes keep the report up-to-date, while robust security measures ensure data protection. Continuous monitoring and model maintenance ensure the accuracy and relevance of predictions over time. Ultimately, the deployment of machine learning models in Power BI reports democratizes data analytics and empowers organizations to harness the full potential of their data for smarter, more informed decision-making across all levels of the organization.
Security and Compliance Considerations
here are the key security and compliance considerations when deploying machine learning models in Power BI reports:
-
Data Privacy: Ensure compliance with data privacy regulations (e.g., GDPR, HIPAA) by anonymizing or pseudonymizing sensitive data.
-
Access Control: Implement role-based access control to restrict who can view and interact with reports and models.
-
Encryption: Encrypt data both at rest and in transit within Power BI.
-
Auditing and Logging: Enable auditing and logging to track user activities and access to sensitive data.
-
Secure Data Sources: Secure data sources to prevent unauthorized access or data breaches.
-
Model Interpretability: Consider the interpretability of machine learning models, especially in regulated industries.
-
Data Retention: Define data retention policies aligned with compliance obligations.
-
Data Masking: Use data masking and redaction techniques to protect sensitive information in reports.
-
External Sharing: Carefully manage external sharing of reports to maintain control over data access.
-
Regular Security Assessments: Conduct security assessments and penetration testing of your Power BI environment.
-
Employee Training: Train users on data security best practices and responsible use of insights.
-
Data Governance: Establish data governance practices to ensure data quality and trustworthiness.
By addressing these considerations, organizations can deploy machine learning models in Power BI reports securely and in compliance with regulatory requirements.
Challenges and Solutions
here are the key challenges and their corresponding solutions when deploying machine learning models in Power BI reports:
Challenges:
-
Data Quality: Inaccurate or messy data can affect model performance.
Solution: Implement rigorous data cleaning and quality checks.
-
Model Maintenance: Models need regular updates as data changes over time.
Solution: Set up a maintenance schedule for model retraining and evaluation.
-
Interpretability: Complex models can be hard to explain.
Solution: Choose interpretable models and provide explanations for predictions.
-
Data Security: Protecting data, especially sensitive information, is crucial.
Solution: Use encryption, access controls, and data masking techniques.
-
Performance Scaling: Large datasets or complex models can slow down Power BI.
Solution: Optimize data loading and consider dedicated resources for heavy tasks.
-
Version Control: Managing different model versions and their integration can be challenging.
Solution: Implement version control and thorough documentation.
Challenges Specific to Compliance:
-
Compliance Requirements: Meeting regulatory standards can be complex.
Solution: Invest in compliance expertise and align data handling with regulations.
-
Audit Trails: Detailed audit records may be necessary for compliance.
Solution: Configure auditing and logging features to capture user activities.
-
Data Retention: Ensuring data retention policies comply with regulations can be tricky.
Solution: Develop clear policies tailored to specific regulations.
-
External Sharing: Sharing reports externally securely can be a challenge.
Solution: Use secure sharing methods like embedding reports or on-premises servers.
By addressing these challenges with the suggested solutions, organizations can effectively deploy machine learning models in Power BI while maintaining data accuracy, security, and compliance.
Future Trends in Power BI and AI
The future of Power BI and AI promises an exciting convergence that will revolutionize data analytics and decision-making. Power BI will increasingly serve as a unified platform where advanced AI capabilities seamlessly integrate into data visualization and reporting. Users can expect a more intuitive experience, with AI-driven insights, automated data preparation, and enhanced collaboration features. This democratization of AI and machine learning within Power BI will empower organizations to make data-driven decisions more efficiently, even with limited data science expertise. Augmented analytics will become the norm, delivering automated insights, anomaly detection, and actionable recommendations, thereby amplifying the value of data for businesses across industries.
Furthermore, Power BI's integration with emerging technologies like IoT and edge computing will enable real-time analysis of sensor data and rapid decision-making at the network's edge. Enhanced data governance, explainable AI, and ethical considerations will also take center stage as organizations strive to ensure data quality, transparency, and compliance in an increasingly AI-driven world. As the AI landscape continues to evolve, Power BI is poised to be at the forefront, providing users with powerful tools to navigate the complexities of data and AI, ultimately driving innovation and competitive advantage.
Best Practices for Harnessing AI in Business Intelligence
here are the best practices for harnessing AI in Business Intelligence in simple points:
-
Define Clear Objectives: Start with clear business goals and objectives for AI in BI.
-
Quality Data: Ensure data is clean, accurate, and well-structured.
-
Right Data Sources: Choose relevant data sources for your objectives.
-
Interdisciplinary Teams: Collaborate with diverse teams, including data scientists and domain experts.
-
Choose Appropriate Algorithms: Select AI algorithms that align with your goals.
-
Model Interpretability: Prioritize models that are easy to understand.
-
Iterative Development: Approach AI implementation as an ongoing process of improvement.
-
Data Governance: Establish strong data governance practices.
-
Ethical AI: Ensure AI models are ethical and unbiased.
-
Scalability: Plan for growth and scalability.
-
User Training: Train users to interpret AI-generated insights.
-
Monitor and Measure: Continuously assess model performance.
-
Collaboration Tools: Use collaboration tools for team communication.
-
Data Security: Implement robust data security measures.
-
Executive Support: Gain support from leadership.
-
ROI Evaluation: Evaluate ROI regularly through KPI tracking.
By following these simple best practices, organizations can effectively leverage AI to enhance their business intelligence efforts.
Conclusion
In conclusion, the synergy between Power BI and AI holds immense promise for organizations seeking to extract actionable insights from their data. The journey to harnessing AI in business intelligence begins with clearly defined objectives, high-quality data, and interdisciplinary collaboration. By adhering to best practices such as model interpretability, ethical AI, and robust data governance, organizations can navigate the complexities of AI integration and ensure responsible and value-driven implementation.
Looking ahead, the future of Power BI and AI is bright, with advancements in automated machine learning, augmented analytics, and real-time data processing on the horizon. These technologies will continue to democratize data-driven decision-making, making it accessible to a wider audience within organizations.
As businesses increasingly rely on data to drive their strategies, the ability to leverage AI in business intelligence will be a competitive advantage. By staying informed about emerging trends and adapting to evolving technologies and best practices, organizations can position themselves at the forefront of this data-driven revolution, enabling smarter, more informed, and more agile decision-making in the years to come.
Read More
In the era of data-driven decision-making, organizations are constantly seeking innovative ways to extract deeper insights from their vast troves of data. One remarkable fusion of technology has emerged as a beacon of hope on this data-rich journey: the synergy between Power BI and Machine Learning. These dynamic tools, when brought together, create a powerhouse of capabilities that go beyond conventional Business Intelligence, transcending the boundaries of static reporting and venturing into the realm of predictive and prescriptive analytics.
In this blog, we embark on a captivating exploration of "Power BI and Machine Learning: Harnessing AI for Business Intelligence." We will unravel the intricacies of this powerful partnership, uncover the benefits it offers to businesses, delve into the technical aspects of integration, and discover the real-world applications that are revolutionizing industries. Join us as we dive into a world where data becomes a strategic asset, AI becomes a trusted ally, and Business Intelligence transcends its limits.
Table of contents
-
Introduction to Power BI and Machine Learning Integration
-
Benefits of Combining Power BI with Machine Learning
-
Getting Started: Setting Up Power BI and Machine Learning
-
Data Preparation for Machine Learning in Power BI
-
Common Machine Learning Algorithms in Power BI
-
Creating Predictive Models in Power BI
-
Real-time Data and Machine Learning
-
Advanced Techniques: NLP and Text Analytics in Power BI
-
Visualizing Machine Learning Results in Power BI
-
Deploying Machine Learning Models in Power BI Reports
-
Security and Compliance Considerations
-
Challenges and Solutions
-
Future Trends in Power BI and AI
-
Best Practices for Harnessing AI in Business Intelligence
-
Conclusion
Introduction to Power BI and Machine Learning Integration
In the realm of data-driven decision-making, the integration of Power BI with machine learning represents a formidable synergy that empowers organizations to extract richer insights from their data. Power BI, developed by Microsoft, stands as a stalwart in the field of business intelligence, offering robust tools for data visualization, reporting, and analysis. On the other hand, machine learning, a facet of artificial intelligence, equips computers with the ability to learn from data, opening doors to predictive and prescriptive analytics. The need for integration arises from the recognition that while Power BI excels in descriptive analytics, it can achieve far more with the predictive and automation capabilities offered by machine learning. By merging these two technologies, businesses can elevate their decision-making processes, gain foresight into future trends, forecast outcomes, and automate routine tasks. This integration isn't just an option; it's increasingly becoming a competitive advantage, allowing companies to stay agile and responsive in a data-driven world.
The benefits of integrating Power BI and machine learning are manifold. It enables improved decision-making by offering insights that extend beyond the surface, transforming data into actionable intelligence. Predictive analytics, made accessible through this integration, equips businesses with the ability to anticipate future trends, providing a competitive edge. Furthermore, the automation capabilities of machine learning within Power BI streamline processes, freeing up valuable human resources. Throughout this blog, we will delve deeper into the technical intricacies, explore real-world applications, discuss best practices, and examine the challenges and future prospects of harnessing this potent combination of Power BI and machine learning for business intelligence.
Benefits of Combining Power BI with Machine Learning
-
Deeper Insights: Uncover hidden patterns and trends in data.
-
Predictive Analytics: Forecast future trends and outcomes.
-
Automation: Reduce manual data analysis tasks.
-
Personalized Recommendations: Improve user engagement.
-
Anomaly Detection: Automatically identify unusual patterns.
-
Efficiency and Scalability: Analyze large datasets efficiently.
-
Competitive Advantage: Stay ahead in the market.
-
Cost Reduction: Automate tasks and improve efficiency.
Getting Started: Setting Up Power BI and Machine Learning
Getting started with the integration of Power BI and machine learning involves a series of strategic steps. First, ensure you have Power BI Desktop installed, the free application for creating reports and dashboards. Then, select your machine learning environment, whether it's Python with libraries like scikit-learn or a cloud-based service like Azure Machine Learning, and make sure you have the necessary software and libraries in place. Next, establish connections to your data sources, which can include databases, spreadsheets, or cloud-based repositories. Clean and format your data for analysis, and consider any feature engineering necessary for machine learning.
With your data ready, proceed to build your machine learning model using your chosen environment. Train the model using historical data to make predictions or classifications. Depending on your setup, you may export the trained model and import it into Power BI or directly connect Power BI to your machine learning service. Then, within Power BI, design your reports and dashboards, incorporating the insights generated by your machine learning model. Utilize Power BI's data visualization tools to create interactive, user-friendly displays of your predictions or classifications. Finally, publish your reports to the Power BI Service, allowing your team to access and share the valuable insights you've gained through the integration of Power BI and machine learning. Regularly monitor and maintain your machine learning model to ensure its accuracy and relevance in your business intelligence efforts.
Data Preparation for Machine Learning in Power BI
Data preparation is a pivotal phase when integrating machine learning with Power BI for robust business intelligence. In this process, you begin by collecting data from various sources and ensuring its completeness. Cleaning the data is paramount to rectify errors, fill in missing values, and eliminate duplicates. A clean dataset serves as the bedrock for accurate machine learning results. Furthermore, data transformation may be necessary to convert categorical variables into numerical formats, standardize features, or perform aggregations. Feature selection is also vital, as it involves cherry-picking the most relevant variables while discarding the superfluous ones to enhance model accuracy and efficiency.
Subsequently, the dataset is split into training, validation, and test sets, facilitating the training and evaluation of machine learning models. Balancing imbalanced data and handling outliers are essential steps to ensure model fairness and robustness. Visualization of data offers insights and aids in decision-making regarding preprocessing strategies. Finally, data formatting, scaling, and proper handling of time series data are essential considerations in data preparation. This meticulous process not only ensures the quality of input data but also maximizes the potential of machine learning models to deliver actionable insights in Power BI. Regular monitoring and maintenance of data quality are key to sustaining the effectiveness of these models as new data streams in, keeping business intelligence efforts accurate and relevant.
Common Machine Learning Algorithms in Power BI
Power BI allows users to integrate machine learning capabilities using various algorithms to enhance their business intelligence efforts. Here are some common machine learning algorithms you can utilize within Power BI:
-
Linear Regression: Linear regression is used for predicting a continuous target variable based on one or more input features. In Power BI, it can be employed for tasks like sales forecasting or price prediction.
-
Logistic Regression: Logistic regression is suitable for binary classification problems. You can use it in Power BI for tasks such as customer churn prediction or fraud detection.
-
Decision Trees: Decision trees are used for both classification and regression tasks. They are easy to understand and can be useful in Power BI for segmenting customers or predicting outcomes based on certain criteria.
-
Random Forest: Random forests are an ensemble technique that combines multiple decision trees to improve accuracy and reduce overfitting. In Power BI, they are valuable for complex classification and regression tasks.
-
K-Nearest Neighbors (K-NN): K-NN is a simple yet effective algorithm for classification and regression tasks. It calculates predictions based on the majority class or average of the nearest neighbors. Power BI users can apply K-NN for recommendation systems or anomaly detection.
-
Support Vector Machines (SVM): SVM is used for classification tasks, especially when dealing with non-linear data. Power BI users can employ SVM for tasks like sentiment analysis or image classification.
-
Clustering Algorithms: Clustering algorithms like K-Means or Hierarchical Clustering are useful in Power BI for customer segmentation, identifying patterns, and grouping similar data points together.
-
Neural Networks: Power BI supports deep learning through integration with Azure Machine Learning, enabling the use of neural networks for tasks such as image recognition, natural language processing, and more complex predictive modeling.
-
Time Series Forecasting: Power BI includes algorithms specifically designed for time series forecasting, which is valuable for predicting future trends based on historical data. These algorithms can be employed for sales forecasting, demand prediction, and inventory management.
-
Anomaly Detection Algorithms: Power BI offers algorithms for anomaly detection, helping users identify unusual patterns or outliers in their data. This is particularly useful for fraud detection or quality control.
-
Principal Component Analysis (PCA): PCA is a dimensionality reduction technique that can be applied in Power BI to reduce the complexity of large datasets and highlight the most important features.
-
Association Rules (Apriori): Power BI supports association rule mining using the Apriori algorithm. This is useful for market basket analysis, where you identify associations between products frequently bought together.
By incorporating these machine learning algorithms into Power BI, users can derive deeper insights, make more accurate predictions, and enhance their business intelligence reports and dashboards. The choice of algorithm depends on the specific problem and the nature of the data being analyzed.
Creating Predictive Models in Power BI
Creating predictive models in Power BI involves a systematic process to turn historical data into actionable insights. It begins with thorough data preparation, ensuring that the dataset is clean and structured for analysis. The choice of a predictive algorithm, based on the nature of your data and the desired prediction type, plays a pivotal role. Power BI offers a range of algorithms, from regression models for numeric predictions to classification models for categorical outcomes. Data splitting into training, validation, and test sets is essential, as it allows you to train, fine-tune, and evaluate your model effectively. Training the model involves using historical data to teach it how to make predictions based on input features. Feature selection and parameter tuning optimize model performance, while rigorous evaluation using validation metrics ensures its accuracy. Once satisfied with the model's performance, you can deploy it within Power BI for real-time predictions. Finally, visualizations in Power BI provide an interactive means of presenting predictions, enabling users to make informed decisions.
Continuous monitoring and maintenance are critical aspects of predictive modeling in Power BI. As new data streams in, the model must be periodically retrained to maintain its accuracy and relevance. Regular assessment of data quality and model effectiveness ensures that business intelligence remains dynamic and aligned with evolving insights. The process of creating predictive models in Power BI empowers organizations to anticipate future trends, optimize operations, and make data-driven decisions, ultimately enhancing their competitiveness and efficiency in a data-centric world.
Real-time Data and Machine Learning
The synergy between real-time data and machine learning is a game-changer in the world of data analytics. Real-time data, sourced from a myriad of sensors, devices, and digital platforms, provides a constant stream of information that can be harnessed instantaneously for actionable insights. Machine learning, on the other hand, equips organizations with the ability to process this data at incredible speeds and make predictions, classifications, and recommendations in real-time. This union has transformative applications, from predicting equipment failures in manufacturing to detecting fraudulent transactions in financial services. It enables predictive analytics that allow businesses to stay one step ahead, proactive decision-making that reduces risks, and automation that streamlines operations, all while visualizing and reporting these insights through dynamic dashboards.
Moreover, real-time data and machine learning are not static; they evolve and adapt as new data arrives. Continuous learning ensures that the models remain accurate and relevant, even in dynamic environments. These technologies are particularly crucial in today's fast-paced world, where timely insights and immediate action are paramount. By integrating real-time data and machine learning, organizations can unlock the power of data-driven decision-making and gain a competitive edge in their respective industries.
Advanced Techniques: NLP and Text Analytics in Power BI
here are the key points for using NLP and text analytics in Power BI:
-
Text Data Preparation: Clean and structure unstructured text data.
-
Sentiment Analysis: Determine the sentiment (positive, negative, or neutral) of text.
-
Text Classification: Automatically categorize text into predefined groups.
-
Keyphrase Extraction: Identify important terms or phrases in text.
-
Named Entity Recognition (NER): Extract names of people, places, organizations, and more from text.
-
Topic Modeling: Discover latent topics within a collection of documents.
-
Text Visualizations: Use Power BI's visualizations for text data, such as word clouds and sentiment charts.
-
Custom Functions: Create custom functions for specialized text analytics.
-
Integration with ML Models: Combine Power BI with machine learning models for custom NLP solutions.
-
Real-time Text Analytics: Monitor and visualize text data in real-time for immediate insights and responses.
Visualizing Machine Learning Results in Power BI
Visualizing machine learning results in Power BI is a pivotal bridge between data-driven analysis and actionable insights. It begins with importing and structuring data within Power BI, including the outcomes generated by machine learning models. Power BI offers a versatile array of visualization tools, from traditional bar charts and line graphs to more advanced visualizations like heatmaps and custom visuals. These visualizations can effectively convey the results of machine learning tasks such as predictions, classification accuracy, feature importance, and model performance metrics.
Interactive dashboards in Power BI facilitate data exploration and decision-making by enabling users to filter, drill down, and interact with the data. Real-time updates and dynamic parameters keep insights current, particularly in applications where data changes frequently. By customizing themes, styles, and annotations, users can provide context and explanations, making the visualized results more comprehensible. Ultimately, visualizing machine learning results in Power BI transforms raw model outputs into actionable information that organizations can leverage to enhance operations, optimize strategies, and stay competitive in an increasingly data-centric world.
Deploying Machine Learning Models in Power BI Reports
Deploying machine learning models within Power BI reports is a strategic step toward unlocking the full potential of data-driven decision-making. It begins with the development and optimization of the machine learning model in a dedicated environment, followed by exporting the model to a format compatible with Power BI. Importing the model into Power BI Desktop and integrating it with the report's data sources is a pivotal step, ensuring that the predictions align with the visualized data. Calculated columns and measures are then created in Power BI to facilitate real-time predictions, which are seamlessly integrated into the report's visualizations. These interactive dashboards empower users to explore and interact with data, providing a dynamic and user-friendly interface for decision-makers.
After fine-tuning the report, it can be published to the Power BI Service, where authorized users across the organization can access and benefit from the integrated machine learning insights. Scheduled data refreshes keep the report up-to-date, while robust security measures ensure data protection. Continuous monitoring and model maintenance ensure the accuracy and relevance of predictions over time. Ultimately, the deployment of machine learning models in Power BI reports democratizes data analytics and empowers organizations to harness the full potential of their data for smarter, more informed decision-making across all levels of the organization.
Security and Compliance Considerations
here are the key security and compliance considerations when deploying machine learning models in Power BI reports:
-
Data Privacy: Ensure compliance with data privacy regulations (e.g., GDPR, HIPAA) by anonymizing or pseudonymizing sensitive data.
-
Access Control: Implement role-based access control to restrict who can view and interact with reports and models.
-
Encryption: Encrypt data both at rest and in transit within Power BI.
-
Auditing and Logging: Enable auditing and logging to track user activities and access to sensitive data.
-
Secure Data Sources: Secure data sources to prevent unauthorized access or data breaches.
-
Model Interpretability: Consider the interpretability of machine learning models, especially in regulated industries.
-
Data Retention: Define data retention policies aligned with compliance obligations.
-
Data Masking: Use data masking and redaction techniques to protect sensitive information in reports.
-
External Sharing: Carefully manage external sharing of reports to maintain control over data access.
-
Regular Security Assessments: Conduct security assessments and penetration testing of your Power BI environment.
-
Employee Training: Train users on data security best practices and responsible use of insights.
-
Data Governance: Establish data governance practices to ensure data quality and trustworthiness.
By addressing these considerations, organizations can deploy machine learning models in Power BI reports securely and in compliance with regulatory requirements.
Challenges and Solutions
here are the key challenges and their corresponding solutions when deploying machine learning models in Power BI reports:
Challenges:
-
Data Quality: Inaccurate or messy data can affect model performance.
Solution: Implement rigorous data cleaning and quality checks.
-
Model Maintenance: Models need regular updates as data changes over time.
Solution: Set up a maintenance schedule for model retraining and evaluation.
-
Interpretability: Complex models can be hard to explain.
Solution: Choose interpretable models and provide explanations for predictions.
-
Data Security: Protecting data, especially sensitive information, is crucial.
Solution: Use encryption, access controls, and data masking techniques.
-
Performance Scaling: Large datasets or complex models can slow down Power BI.
Solution: Optimize data loading and consider dedicated resources for heavy tasks.
-
Version Control: Managing different model versions and their integration can be challenging.
Solution: Implement version control and thorough documentation.
Challenges Specific to Compliance:
-
Compliance Requirements: Meeting regulatory standards can be complex.
Solution: Invest in compliance expertise and align data handling with regulations.
-
Audit Trails: Detailed audit records may be necessary for compliance.
Solution: Configure auditing and logging features to capture user activities.
-
Data Retention: Ensuring data retention policies comply with regulations can be tricky.
Solution: Develop clear policies tailored to specific regulations.
-
External Sharing: Sharing reports externally securely can be a challenge.
Solution: Use secure sharing methods like embedding reports or on-premises servers.
By addressing these challenges with the suggested solutions, organizations can effectively deploy machine learning models in Power BI while maintaining data accuracy, security, and compliance.
Future Trends in Power BI and AI
The future of Power BI and AI promises an exciting convergence that will revolutionize data analytics and decision-making. Power BI will increasingly serve as a unified platform where advanced AI capabilities seamlessly integrate into data visualization and reporting. Users can expect a more intuitive experience, with AI-driven insights, automated data preparation, and enhanced collaboration features. This democratization of AI and machine learning within Power BI will empower organizations to make data-driven decisions more efficiently, even with limited data science expertise. Augmented analytics will become the norm, delivering automated insights, anomaly detection, and actionable recommendations, thereby amplifying the value of data for businesses across industries.
Furthermore, Power BI's integration with emerging technologies like IoT and edge computing will enable real-time analysis of sensor data and rapid decision-making at the network's edge. Enhanced data governance, explainable AI, and ethical considerations will also take center stage as organizations strive to ensure data quality, transparency, and compliance in an increasingly AI-driven world. As the AI landscape continues to evolve, Power BI is poised to be at the forefront, providing users with powerful tools to navigate the complexities of data and AI, ultimately driving innovation and competitive advantage.
Best Practices for Harnessing AI in Business Intelligence
here are the best practices for harnessing AI in Business Intelligence in simple points:
-
Define Clear Objectives: Start with clear business goals and objectives for AI in BI.
-
Quality Data: Ensure data is clean, accurate, and well-structured.
-
Right Data Sources: Choose relevant data sources for your objectives.
-
Interdisciplinary Teams: Collaborate with diverse teams, including data scientists and domain experts.
-
Choose Appropriate Algorithms: Select AI algorithms that align with your goals.
-
Model Interpretability: Prioritize models that are easy to understand.
-
Iterative Development: Approach AI implementation as an ongoing process of improvement.
-
Data Governance: Establish strong data governance practices.
-
Ethical AI: Ensure AI models are ethical and unbiased.
-
Scalability: Plan for growth and scalability.
-
User Training: Train users to interpret AI-generated insights.
-
Monitor and Measure: Continuously assess model performance.
-
Collaboration Tools: Use collaboration tools for team communication.
-
Data Security: Implement robust data security measures.
-
Executive Support: Gain support from leadership.
-
ROI Evaluation: Evaluate ROI regularly through KPI tracking.
By following these simple best practices, organizations can effectively leverage AI to enhance their business intelligence efforts.
Conclusion
In conclusion, the synergy between Power BI and AI holds immense promise for organizations seeking to extract actionable insights from their data. The journey to harnessing AI in business intelligence begins with clearly defined objectives, high-quality data, and interdisciplinary collaboration. By adhering to best practices such as model interpretability, ethical AI, and robust data governance, organizations can navigate the complexities of AI integration and ensure responsible and value-driven implementation.
Looking ahead, the future of Power BI and AI is bright, with advancements in automated machine learning, augmented analytics, and real-time data processing on the horizon. These technologies will continue to democratize data-driven decision-making, making it accessible to a wider audience within organizations.
As businesses increasingly rely on data to drive their strategies, the ability to leverage AI in business intelligence will be a competitive advantage. By staying informed about emerging trends and adapting to evolving technologies and best practices, organizations can position themselves at the forefront of this data-driven revolution, enabling smarter, more informed, and more agile decision-making in the years to come.
The Importance of AWS Solution Architects in Cloud Computing
In the ever-evolving landscape of cloud computing, where agility, scalability, and innovation reign supreme, there exists a key figure who plays a central role in shaping the digital destiny of organizations—AWS Solution Architects. These architects are the visionaries, the strategists, and the technical wizards who navigate the intricate web of Amazon Web Services (AWS) to design and orchestrate cloud solutions that power the modern enterprise.
Cloud computing has ushered in a new era of possibilities, revolutionizing the way businesses operate, innovate, and compete. Yet, harnessing the full potential of the cloud demands expertise and precision, and this is where AWS Solution Architects emerge as the unsung heroes. In this blog, we delve deep into the significance of AWS Solution Architects in the realm of cloud computing, uncovering their multifaceted roles, their impact on businesses, and the vital link they provide between technology and strategic success. Join us on a journey to understand why these architects are the linchpin in the cloud revolution and how their skills are reshaping the digital landscape.
Table of contents
-
Defining the Role of an AWS Solution Architect
-
The Growing Significance of Cloud Computing
-
Why Cloud Architecture Matters
-
AWS as a Leading Cloud Provider
-
The Challenges of Cloud Adoption
-
How AWS Solution Architects Address Business Needs
-
Cost Optimization and Efficiency
-
Security and Compliance in AWS Solutions
-
Scaling for Growth and Performance
-
Disaster Recovery and Business Continuity
-
Innovation and Future-Proofing
-
Certification and Training for AWS Solution Architects
-
Collaboration with Other IT Roles
-
The Role of AWS Partnerships
-
Conclusion
Defining the Role of an AWS Solution Architect
An AWS Solution Architect serves as a pivotal figure in the realm of cloud computing, tasked with the essential responsibility of designing, implementing, and optimizing cloud-based solutions tailored to meet the unique needs of organizations. At its core, this role revolves around crafting architectural blueprints that seamlessly integrate AWS services to build robust, scalable, secure, and cost-effective cloud infrastructures. With deep expertise in AWS services and best practices, Solution Architects act as the bridge between business objectives and technical execution. They collaborate closely with stakeholders, ensuring that every solution aligns with organizational goals while emphasizing security, compliance, and efficiency. Moreover, these professionals remain vigilant in their commitment to continuous learning, keeping pace with AWS's ever-evolving ecosystem to provide innovative, future-proof solutions.
The role of an AWS Solution Architect encompasses a multifaceted skill set, including cloud expertise, cost optimization, security prowess, and effective communication. Their role extends beyond technical implementation; it involves understanding the intricate nuances of an organization's operations and translating them into well-architected cloud solutions. Ultimately, AWS Solution Architects play a crucial role in driving business growth, innovation, and operational excellence through the harnessing of AWS's powerful cloud services, making them indispensable assets in today's cloud-centric world.
The Growing Significance of Cloud Computing
The growing significance of cloud computing represents a fundamental shift in the way businesses and individuals interact with technology. At its core, cloud computing offers unprecedented accessibility, scalability, and flexibility. Gone are the days of hefty upfront investments in on-premises infrastructure; instead, organizations can leverage cloud resources on-demand, enabling rapid adaptation to changing market dynamics. This agility is a game-changer, allowing businesses to pivot, scale, and innovate more swiftly than ever before. Furthermore, cloud computing has democratized access to advanced technologies like artificial intelligence, machine learning, and big data analytics, empowering businesses of all sizes to harness the power of these tools to drive growth and competitiveness.
Moreover, cloud computing has proven instrumental in facilitating remote work and collaboration. The COVID-19 pandemic underscored the essential role the cloud plays in enabling remote workforces and ensuring business continuity. It has become the backbone of modern collaboration tools, allowing teams to connect and work seamlessly regardless of geographical boundaries. Additionally, cloud providers have prioritized security, investing heavily in robust safeguards and compliance measures, assuaging concerns about data protection and privacy. As the cloud ecosystem continues to evolve, its significance will only intensify, serving as a catalyst for innovation, cost-efficiency, and strategic transformation in businesses and industries worldwide.
Why Cloud Architecture Matters
Cloud architecture is paramount in the modern business landscape for a multitude of reasons. Firstly, it serves as the blueprint for a company's digital infrastructure, determining how resources are provisioned, deployed, and managed in the cloud. This fundamental design impacts an organization's ability to scale rapidly in response to changing demands, control costs by efficiently allocating resources, and maintain the highest standards of security and compliance. Effective cloud architecture can make the difference between an agile, cost-effective, and secure operation and one that struggles to adapt to the fast-paced digital world.
Secondly, cloud architecture unlocks the potential for innovation and business agility. With the cloud's vast array of managed services, organizations can experiment and implement cutting-edge technologies like artificial intelligence, machine learning, and IoT without the burden of managing complex underlying infrastructure. Cloud-native development practices foster agility by enabling rapid development, testing, and deployment of applications. As remote work and global collaboration become the norm, the cloud also plays a pivotal role in providing accessibility to data and applications from anywhere, supporting businesses in their quest for operational continuity and growth. In essence, cloud architecture isn't just about IT; it's about the strategic foundation upon which businesses build their digital future.
AWS as a Leading Cloud Provider
Amazon Web Services (AWS) has solidified its position as the foremost cloud provider due to a combination of factors that set it apart in the industry. Its vast and constantly expanding service portfolio encompasses virtually every aspect of cloud computing, enabling businesses to not only migrate their existing infrastructure but also to innovate and transform their operations. This extensive range of services includes scalable computing resources, cutting-edge machine learning and analytics tools, secure storage options, and developer-friendly solutions like serverless computing, all backed by a global network of data centers. This versatility makes AWS suitable for startups, enterprises, government organizations, and virtually any industry seeking to harness the power of the cloud.
One of AWS's standout attributes is its relentless commitment to security and compliance. AWS invests heavily in advanced security features, encryption, and access controls, earning it the trust of highly regulated industries like healthcare and finance. Furthermore, AWS consistently obtains and maintains a broad array of compliance certifications, ensuring that customers can adhere to industry-specific regulations while leveraging the cloud's capabilities. This focus on security and compliance, combined with its innovation, reliability, and global reach, makes AWS not just a leading cloud provider but also a strategic partner for organizations worldwide as they navigate the complexities of the digital age.
The Challenges of Cloud Adoption
-
Security Concerns: Worries about data security and unauthorized access.
-
Compliance and Regulations: Meeting legal requirements and industry-specific regulations.
-
Data Migration: Moving existing data and applications to the cloud seamlessly.
-
Cost Management: Controlling cloud spending and optimizing costs.
-
Skills Gap: Lack of expertise in managing cloud environments.
-
Vendor Lock-In: Dependency on a single cloud provider.
-
Performance Issues: Ensuring consistent application performance.
-
Change Resistance: Employees resisting changes in processes and workflows.
-
Governance: Lack of clear policies for managing cloud resources.
-
Downtime and Availability: Dealing with occasional outages and downtime.
How AWS Solution Architects Address Business Needs Top of Form
AWS Solution Architects are instrumental in bridging the gap between an organization's business needs and the technological capabilities provided by Amazon Web Services. They start by deeply understanding the unique objectives and challenges faced by the business, working closely with stakeholders to align cloud solutions with these requirements. Whether it's optimizing costs, enhancing security, ensuring scalability, or addressing compliance concerns, Solution Architects craft tailored solutions that cater to these specific business needs. Their expertise in AWS services and best practices allows them to design robust architectures that not only meet current demands but also anticipate future growth and innovation.
Moreover, AWS Solution Architects provide a crucial layer of assurance and reliability to organizations. By prioritizing security measures and compliance, they ensure that data and operations are safeguarded, instilling confidence in cloud adoption. Their ability to create detailed technical documentation and collaborate effectively with cross-functional teams ensures the successful implementation of cloud solutions. In essence, AWS Solution Architects play a pivotal role in driving business success by leveraging AWS's powerful cloud capabilities to address the ever-evolving landscape of business needs, from cost efficiency and scalability to security and innovation.
Cost Optimization and Efficiency
Cost optimization and efficiency are paramount in the world of AWS as organizations seek to harness the cloud's power while keeping their budgets in check. AWS offers a multitude of tools and strategies to help businesses strike the right balance between performance and expenditure. One of the fundamental principles is resource optimization, where organizations carefully select the appropriate instance types, storage options, and services that align with their actual requirements. By avoiding overprovisioning and rightsizing their resources, businesses can prevent unnecessary spending and ensure that they pay only for what they use.
Furthermore, AWS provides advanced features like auto-scaling, which enables resources to automatically adapt to fluctuating workloads, optimizing both performance and costs. Reserved Instances and Spot Instances offer significant cost savings, allowing organizations to commit to long-term usage for predictable workloads or take advantage of surplus capacity for transient tasks. AWS's suite of monitoring and optimization tools empowers organizations to gain visibility into their cloud expenditure and make data-driven decisions to reduce costs. By continually reviewing and adjusting their cloud architecture, employing serverless computing for certain tasks, and educating teams on best practices, organizations can achieve a delicate balance between efficiency and cost control, ensuring that their AWS investments yield maximum value.
Security and Compliance in AWS Solutions
Security and compliance are foundational pillars in AWS solutions, reflecting the platform's unwavering commitment to safeguarding customer data and ensuring adherence to industry-specific regulations. AWS employs a multi-layered approach to security, starting with its shared responsibility model, which delineates responsibilities between AWS and its customers. AWS is responsible for securing the underlying infrastructure, while customers are tasked with securing their data, applications, and configurations. This model ensures that security is a collaborative effort, with AWS providing a secure cloud environment and customers implementing security best practices within it.
To bolster security, AWS offers a comprehensive suite of services, including IAM for access control, encryption for data protection, VPC for network isolation, and a range of monitoring and logging tools. AWS also invests heavily in compliance, obtaining and maintaining various certifications to meet the strictest regulatory requirements, such as HIPAA and GDPR. This commitment to security and compliance gives organizations the confidence to migrate sensitive workloads to the cloud while maintaining data integrity and adhering to industry-specific regulations. AWS's emphasis on security and compliance underscores its position as a trusted partner for businesses seeking to leverage the cloud's capabilities while mitigating potential risks.
Scaling for Growth and Performance
Scaling for growth and performance is a fundamental requirement in today's dynamic business landscape, and AWS provides organizations with a robust toolkit to achieve this scalability seamlessly. The heart of AWS's scaling capabilities lies in its auto-scaling features, which enable applications to dynamically adjust their compute resources in response to fluctuations in demand. This not only ensures that applications can handle sudden surges in traffic but also optimizes resource utilization during quieter periods, resulting in cost-effective operations.
Moreover, AWS promotes a serverless paradigm through services like AWS Lambda, allowing organizations to focus on code rather than infrastructure management. Serverless computing automatically scales resources in response to individual events, delivering exceptional performance and cost-efficiency without the need to provision or manage servers. Coupled with elastic load balancing, content delivery networks, and scalable databases, AWS empowers organizations to build resilient, high-performance applications that can seamlessly scale to accommodate growth while delivering optimal user experiences. Whether it's handling a sudden influx of customers or supporting continuous expansion, AWS's scaling capabilities are integral to modern businesses aiming for both agility and performance.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity are foundational elements of AWS's cloud offerings, reflecting its commitment to ensuring the availability and resilience of critical business operations. AWS provides organizations with versatile tools and services to craft robust disaster recovery and business continuity strategies. This begins with AWS's high availability infrastructure, which spans multiple availability zones and regions, allowing businesses to deploy resources in geographically separate locations to guard against localized outages or disasters. Services like AWS Disaster Recovery (DR) as a Service (DRaaS) and AWS Site Recovery facilitate automated failover and replication of workloads, ensuring minimal downtime and seamless continuity in the event of a disaster or unforeseen event.
Moreover, AWS's backup solutions, such as Amazon S3 and Amazon EBS snapshots, enable organizations to create secure and scalable data backups, ensuring that critical information can be restored quickly and reliably. AWS's global content delivery network, Amazon CloudFront, accelerates content delivery, reducing latency and ensuring data remains accessible even during network disruptions. Additionally, the ability to simulate disaster scenarios and conduct testing exercises without impacting production environments empowers organizations to refine their disaster recovery and business continuity plans proactively. With these capabilities, AWS strengthens an organization's ability to navigate the unpredictable and safeguard its operations, data, and reputation in the face of adversity.
Innovation and Future-Proofing
Innovation and future-proofing are at the core of AWS solutions, allowing organizations to not only meet current challenges but also anticipate and adapt to future technological advancements. AWS's commitment to staying on the cutting edge of technology is evident through its constant introduction of new services and features that harness emerging trends like artificial intelligence, machine learning, IoT, and serverless computing. These innovations empower businesses to explore new frontiers, streamline operations, and enhance customer experiences. AWS's vast ecosystem of services provides organizations with the flexibility to experiment, iterate, and scale their solutions, fostering a culture of continuous innovation.
Furthermore, AWS's emphasis on cloud-native development practices, well-architected frameworks, and global infrastructure allows organizations to future-proof their operations. By adopting cloud-native principles such as microservices and DevOps, businesses can remain agile and responsive to changing market conditions. AWS's global reach ensures that organizations can expand their reach and serve customers globally, while the well-architected framework guides them in building resilient and efficient solutions that can withstand future challenges. With AWS, organizations have a partner that not only supports their current needs but also equips them with the tools and strategies to thrive in an ever-evolving digital landscape, positioning them for sustained success and innovation.
Certification and Training for AWS Solution Architects
-
Choose Your Certification Level: Start with the "AWS Certified Solutions Architect - Associate" certification, and you can progress to the "AWS Certified Solutions Architect - Professional" later.
-
Review Exam Objectives: Understand what topics are covered in the certification exam by reviewing the exam blueprint provided by AWS.
-
Access Training Resources: Utilize AWS's official training resources, including online courses and hands-on labs, available on the AWS Training and Certification portal.
-
Hands-On Practice: Gain practical experience by working on real AWS projects and experimenting with AWS services in a free-tier environment.
-
Practice Exams: Use practice exams and sample questions to test your knowledge and readiness for the certification exam.
-
Register for the Exam: Sign up for the certification exam through the AWS Certification portal.
-
Stay Updated: Keep yourself updated with the latest AWS services and best practices by attending webinars, reading documentation, and participating in the AWS community.
-
Recertify When Required: Be aware of recertification requirements and ensure you renew your certification when necessary to stay current.
By following these steps, you can work towards becoming a certified AWS Solutions Architect, demonstrating your expertise in designing and implementing AWS solutions.
Collaboration with Other IT Roles
Collaboration with various IT roles is a cornerstone of success for AWS Solution Architects in the complex world of cloud computing. Working closely with developers, architects help translate architectural designs into functional applications by providing guidance on best practices, security, and scalability. Collaboration with system administrators and DevOps engineers is essential to automate resource provisioning, implement CI/CD pipelines, and ensure the architecture's resilience. Solution Architects liaise with security specialists to embed security measures into the design, and with network engineers to configure networking components in line with performance and security needs. They also partner with database administrators to optimize database performance and with data scientists and analysts to create data solutions leveraging AWS's capabilities. Collaboration with project managers helps align architectural goals with project timelines and budgets, ensuring that cloud solutions are not only technically sound but also delivered on schedule and within budget.
This collaborative approach extends beyond technology, fostering a culture of teamwork and shared responsibility. It promotes effective communication and coordination among cross-functional teams, enabling them to collectively tackle challenges, make informed decisions, and deliver solutions that align with business objectives. In essence, AWS Solution Architects' ability to collaborate with a diverse set of IT roles is integral to their role as orchestrators of cloud excellence, ensuring that AWS solutions not only meet technical requirements but also drive business success.
The Role of AWS Partnerships
Here are the key points about the role of AWS partnerships in a simple format:
-
Expertise Access: AWS partnerships connect businesses with skilled professionals who have deep expertise in AWS technologies, helping organizations make informed decisions and optimize their cloud solutions.
-
Innovation Acceleration: Technology partners collaborate with AWS to create and integrate innovative products and services, allowing customers to harness cutting-edge technology without starting from scratch.
-
Enhanced Support: Consulting and managed service partners offer valuable support, acting as trusted advisors to guide businesses in adopting and managing AWS services effectively.
-
Global Presence: AWS partnerships provide access to AWS services and support in local regions, ensuring global reach and localized assistance for businesses with international operations.
-
Ecosystem Expansion: Partnerships contribute to an extensive ecosystem of third-party solutions that integrate seamlessly with AWS, offering a wide array of options to tailor cloud environments to specific needs.
-
Certified Solutions: AWS-certified partner solutions undergo rigorous testing and validation, ensuring compatibility, reliability, and quality for customers.
-
Resources and Support: AWS offers partners resources, training, marketing support, and co-selling opportunities, enabling them to better serve customers and grow their businesses.
AWS partnerships play a vital role in helping businesses leverage the full potential of AWS cloud services, providing expertise, innovation, and support to drive digital transformation and growth.
Conclusion
In conclusion, AWS Solution Architects hold a pivotal role in the realm of cloud computing, where businesses increasingly rely on AWS's vast array of services and infrastructure. These architects serve as the linchpin between technology and business, bridging the gap by designing, implementing, and optimizing cloud solutions that align with organizational goals. They navigate the complexities of AWS to create architectures that are secure, scalable, cost-efficient, and resilient.
The importance of AWS Solution Architects extends beyond technical prowess. They collaborate with diverse IT roles, facilitate innovation, and leverage AWS partnerships to enhance cloud capabilities. These architects play a key role in disaster recovery, business continuity, security, and compliance, safeguarding critical data and operations. They are instrumental in driving cost optimization, ensuring resources are used efficiently.
As businesses continue to embrace the cloud, AWS Solution Architects will remain essential in guiding these transformations. Their expertise, collaboration, and commitment to innovation enable organizations to thrive in the ever-evolving digital landscape, making them invaluable assets in the journey toward cloud excellence.
Read More
In the ever-evolving landscape of cloud computing, where agility, scalability, and innovation reign supreme, there exists a key figure who plays a central role in shaping the digital destiny of organizations—AWS Solution Architects. These architects are the visionaries, the strategists, and the technical wizards who navigate the intricate web of Amazon Web Services (AWS) to design and orchestrate cloud solutions that power the modern enterprise.
Cloud computing has ushered in a new era of possibilities, revolutionizing the way businesses operate, innovate, and compete. Yet, harnessing the full potential of the cloud demands expertise and precision, and this is where AWS Solution Architects emerge as the unsung heroes. In this blog, we delve deep into the significance of AWS Solution Architects in the realm of cloud computing, uncovering their multifaceted roles, their impact on businesses, and the vital link they provide between technology and strategic success. Join us on a journey to understand why these architects are the linchpin in the cloud revolution and how their skills are reshaping the digital landscape.
Table of contents
-
Defining the Role of an AWS Solution Architect
-
The Growing Significance of Cloud Computing
-
Why Cloud Architecture Matters
-
AWS as a Leading Cloud Provider
-
The Challenges of Cloud Adoption
-
How AWS Solution Architects Address Business Needs
-
Cost Optimization and Efficiency
-
Security and Compliance in AWS Solutions
-
Scaling for Growth and Performance
-
Disaster Recovery and Business Continuity
-
Innovation and Future-Proofing
-
Certification and Training for AWS Solution Architects
-
Collaboration with Other IT Roles
-
The Role of AWS Partnerships
-
Conclusion
Defining the Role of an AWS Solution Architect
An AWS Solution Architect serves as a pivotal figure in the realm of cloud computing, tasked with the essential responsibility of designing, implementing, and optimizing cloud-based solutions tailored to meet the unique needs of organizations. At its core, this role revolves around crafting architectural blueprints that seamlessly integrate AWS services to build robust, scalable, secure, and cost-effective cloud infrastructures. With deep expertise in AWS services and best practices, Solution Architects act as the bridge between business objectives and technical execution. They collaborate closely with stakeholders, ensuring that every solution aligns with organizational goals while emphasizing security, compliance, and efficiency. Moreover, these professionals remain vigilant in their commitment to continuous learning, keeping pace with AWS's ever-evolving ecosystem to provide innovative, future-proof solutions.
The role of an AWS Solution Architect encompasses a multifaceted skill set, including cloud expertise, cost optimization, security prowess, and effective communication. Their role extends beyond technical implementation; it involves understanding the intricate nuances of an organization's operations and translating them into well-architected cloud solutions. Ultimately, AWS Solution Architects play a crucial role in driving business growth, innovation, and operational excellence through the harnessing of AWS's powerful cloud services, making them indispensable assets in today's cloud-centric world.
The Growing Significance of Cloud Computing
The growing significance of cloud computing represents a fundamental shift in the way businesses and individuals interact with technology. At its core, cloud computing offers unprecedented accessibility, scalability, and flexibility. Gone are the days of hefty upfront investments in on-premises infrastructure; instead, organizations can leverage cloud resources on-demand, enabling rapid adaptation to changing market dynamics. This agility is a game-changer, allowing businesses to pivot, scale, and innovate more swiftly than ever before. Furthermore, cloud computing has democratized access to advanced technologies like artificial intelligence, machine learning, and big data analytics, empowering businesses of all sizes to harness the power of these tools to drive growth and competitiveness.
Moreover, cloud computing has proven instrumental in facilitating remote work and collaboration. The COVID-19 pandemic underscored the essential role the cloud plays in enabling remote workforces and ensuring business continuity. It has become the backbone of modern collaboration tools, allowing teams to connect and work seamlessly regardless of geographical boundaries. Additionally, cloud providers have prioritized security, investing heavily in robust safeguards and compliance measures, assuaging concerns about data protection and privacy. As the cloud ecosystem continues to evolve, its significance will only intensify, serving as a catalyst for innovation, cost-efficiency, and strategic transformation in businesses and industries worldwide.
Why Cloud Architecture Matters
Cloud architecture is paramount in the modern business landscape for a multitude of reasons. Firstly, it serves as the blueprint for a company's digital infrastructure, determining how resources are provisioned, deployed, and managed in the cloud. This fundamental design impacts an organization's ability to scale rapidly in response to changing demands, control costs by efficiently allocating resources, and maintain the highest standards of security and compliance. Effective cloud architecture can make the difference between an agile, cost-effective, and secure operation and one that struggles to adapt to the fast-paced digital world.
Secondly, cloud architecture unlocks the potential for innovation and business agility. With the cloud's vast array of managed services, organizations can experiment and implement cutting-edge technologies like artificial intelligence, machine learning, and IoT without the burden of managing complex underlying infrastructure. Cloud-native development practices foster agility by enabling rapid development, testing, and deployment of applications. As remote work and global collaboration become the norm, the cloud also plays a pivotal role in providing accessibility to data and applications from anywhere, supporting businesses in their quest for operational continuity and growth. In essence, cloud architecture isn't just about IT; it's about the strategic foundation upon which businesses build their digital future.
AWS as a Leading Cloud Provider
Amazon Web Services (AWS) has solidified its position as the foremost cloud provider due to a combination of factors that set it apart in the industry. Its vast and constantly expanding service portfolio encompasses virtually every aspect of cloud computing, enabling businesses to not only migrate their existing infrastructure but also to innovate and transform their operations. This extensive range of services includes scalable computing resources, cutting-edge machine learning and analytics tools, secure storage options, and developer-friendly solutions like serverless computing, all backed by a global network of data centers. This versatility makes AWS suitable for startups, enterprises, government organizations, and virtually any industry seeking to harness the power of the cloud.
One of AWS's standout attributes is its relentless commitment to security and compliance. AWS invests heavily in advanced security features, encryption, and access controls, earning it the trust of highly regulated industries like healthcare and finance. Furthermore, AWS consistently obtains and maintains a broad array of compliance certifications, ensuring that customers can adhere to industry-specific regulations while leveraging the cloud's capabilities. This focus on security and compliance, combined with its innovation, reliability, and global reach, makes AWS not just a leading cloud provider but also a strategic partner for organizations worldwide as they navigate the complexities of the digital age.
The Challenges of Cloud Adoption
-
Security Concerns: Worries about data security and unauthorized access.
-
Compliance and Regulations: Meeting legal requirements and industry-specific regulations.
-
Data Migration: Moving existing data and applications to the cloud seamlessly.
-
Cost Management: Controlling cloud spending and optimizing costs.
-
Skills Gap: Lack of expertise in managing cloud environments.
-
Vendor Lock-In: Dependency on a single cloud provider.
-
Performance Issues: Ensuring consistent application performance.
-
Change Resistance: Employees resisting changes in processes and workflows.
-
Governance: Lack of clear policies for managing cloud resources.
-
Downtime and Availability: Dealing with occasional outages and downtime.
How AWS Solution Architects Address Business Needs Top of Form
AWS Solution Architects are instrumental in bridging the gap between an organization's business needs and the technological capabilities provided by Amazon Web Services. They start by deeply understanding the unique objectives and challenges faced by the business, working closely with stakeholders to align cloud solutions with these requirements. Whether it's optimizing costs, enhancing security, ensuring scalability, or addressing compliance concerns, Solution Architects craft tailored solutions that cater to these specific business needs. Their expertise in AWS services and best practices allows them to design robust architectures that not only meet current demands but also anticipate future growth and innovation.
Moreover, AWS Solution Architects provide a crucial layer of assurance and reliability to organizations. By prioritizing security measures and compliance, they ensure that data and operations are safeguarded, instilling confidence in cloud adoption. Their ability to create detailed technical documentation and collaborate effectively with cross-functional teams ensures the successful implementation of cloud solutions. In essence, AWS Solution Architects play a pivotal role in driving business success by leveraging AWS's powerful cloud capabilities to address the ever-evolving landscape of business needs, from cost efficiency and scalability to security and innovation.
Cost Optimization and Efficiency
Cost optimization and efficiency are paramount in the world of AWS as organizations seek to harness the cloud's power while keeping their budgets in check. AWS offers a multitude of tools and strategies to help businesses strike the right balance between performance and expenditure. One of the fundamental principles is resource optimization, where organizations carefully select the appropriate instance types, storage options, and services that align with their actual requirements. By avoiding overprovisioning and rightsizing their resources, businesses can prevent unnecessary spending and ensure that they pay only for what they use.
Furthermore, AWS provides advanced features like auto-scaling, which enables resources to automatically adapt to fluctuating workloads, optimizing both performance and costs. Reserved Instances and Spot Instances offer significant cost savings, allowing organizations to commit to long-term usage for predictable workloads or take advantage of surplus capacity for transient tasks. AWS's suite of monitoring and optimization tools empowers organizations to gain visibility into their cloud expenditure and make data-driven decisions to reduce costs. By continually reviewing and adjusting their cloud architecture, employing serverless computing for certain tasks, and educating teams on best practices, organizations can achieve a delicate balance between efficiency and cost control, ensuring that their AWS investments yield maximum value.
Security and Compliance in AWS Solutions
Security and compliance are foundational pillars in AWS solutions, reflecting the platform's unwavering commitment to safeguarding customer data and ensuring adherence to industry-specific regulations. AWS employs a multi-layered approach to security, starting with its shared responsibility model, which delineates responsibilities between AWS and its customers. AWS is responsible for securing the underlying infrastructure, while customers are tasked with securing their data, applications, and configurations. This model ensures that security is a collaborative effort, with AWS providing a secure cloud environment and customers implementing security best practices within it.
To bolster security, AWS offers a comprehensive suite of services, including IAM for access control, encryption for data protection, VPC for network isolation, and a range of monitoring and logging tools. AWS also invests heavily in compliance, obtaining and maintaining various certifications to meet the strictest regulatory requirements, such as HIPAA and GDPR. This commitment to security and compliance gives organizations the confidence to migrate sensitive workloads to the cloud while maintaining data integrity and adhering to industry-specific regulations. AWS's emphasis on security and compliance underscores its position as a trusted partner for businesses seeking to leverage the cloud's capabilities while mitigating potential risks.
Scaling for Growth and Performance
Scaling for growth and performance is a fundamental requirement in today's dynamic business landscape, and AWS provides organizations with a robust toolkit to achieve this scalability seamlessly. The heart of AWS's scaling capabilities lies in its auto-scaling features, which enable applications to dynamically adjust their compute resources in response to fluctuations in demand. This not only ensures that applications can handle sudden surges in traffic but also optimizes resource utilization during quieter periods, resulting in cost-effective operations.
Moreover, AWS promotes a serverless paradigm through services like AWS Lambda, allowing organizations to focus on code rather than infrastructure management. Serverless computing automatically scales resources in response to individual events, delivering exceptional performance and cost-efficiency without the need to provision or manage servers. Coupled with elastic load balancing, content delivery networks, and scalable databases, AWS empowers organizations to build resilient, high-performance applications that can seamlessly scale to accommodate growth while delivering optimal user experiences. Whether it's handling a sudden influx of customers or supporting continuous expansion, AWS's scaling capabilities are integral to modern businesses aiming for both agility and performance.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity are foundational elements of AWS's cloud offerings, reflecting its commitment to ensuring the availability and resilience of critical business operations. AWS provides organizations with versatile tools and services to craft robust disaster recovery and business continuity strategies. This begins with AWS's high availability infrastructure, which spans multiple availability zones and regions, allowing businesses to deploy resources in geographically separate locations to guard against localized outages or disasters. Services like AWS Disaster Recovery (DR) as a Service (DRaaS) and AWS Site Recovery facilitate automated failover and replication of workloads, ensuring minimal downtime and seamless continuity in the event of a disaster or unforeseen event.
Moreover, AWS's backup solutions, such as Amazon S3 and Amazon EBS snapshots, enable organizations to create secure and scalable data backups, ensuring that critical information can be restored quickly and reliably. AWS's global content delivery network, Amazon CloudFront, accelerates content delivery, reducing latency and ensuring data remains accessible even during network disruptions. Additionally, the ability to simulate disaster scenarios and conduct testing exercises without impacting production environments empowers organizations to refine their disaster recovery and business continuity plans proactively. With these capabilities, AWS strengthens an organization's ability to navigate the unpredictable and safeguard its operations, data, and reputation in the face of adversity.
Innovation and Future-Proofing
Innovation and future-proofing are at the core of AWS solutions, allowing organizations to not only meet current challenges but also anticipate and adapt to future technological advancements. AWS's commitment to staying on the cutting edge of technology is evident through its constant introduction of new services and features that harness emerging trends like artificial intelligence, machine learning, IoT, and serverless computing. These innovations empower businesses to explore new frontiers, streamline operations, and enhance customer experiences. AWS's vast ecosystem of services provides organizations with the flexibility to experiment, iterate, and scale their solutions, fostering a culture of continuous innovation.
Furthermore, AWS's emphasis on cloud-native development practices, well-architected frameworks, and global infrastructure allows organizations to future-proof their operations. By adopting cloud-native principles such as microservices and DevOps, businesses can remain agile and responsive to changing market conditions. AWS's global reach ensures that organizations can expand their reach and serve customers globally, while the well-architected framework guides them in building resilient and efficient solutions that can withstand future challenges. With AWS, organizations have a partner that not only supports their current needs but also equips them with the tools and strategies to thrive in an ever-evolving digital landscape, positioning them for sustained success and innovation.
Certification and Training for AWS Solution Architects
-
Choose Your Certification Level: Start with the "AWS Certified Solutions Architect - Associate" certification, and you can progress to the "AWS Certified Solutions Architect - Professional" later.
-
Review Exam Objectives: Understand what topics are covered in the certification exam by reviewing the exam blueprint provided by AWS.
-
Access Training Resources: Utilize AWS's official training resources, including online courses and hands-on labs, available on the AWS Training and Certification portal.
-
Hands-On Practice: Gain practical experience by working on real AWS projects and experimenting with AWS services in a free-tier environment.
-
Practice Exams: Use practice exams and sample questions to test your knowledge and readiness for the certification exam.
-
Register for the Exam: Sign up for the certification exam through the AWS Certification portal.
-
Stay Updated: Keep yourself updated with the latest AWS services and best practices by attending webinars, reading documentation, and participating in the AWS community.
-
Recertify When Required: Be aware of recertification requirements and ensure you renew your certification when necessary to stay current.
By following these steps, you can work towards becoming a certified AWS Solutions Architect, demonstrating your expertise in designing and implementing AWS solutions.
Collaboration with Other IT Roles
Collaboration with various IT roles is a cornerstone of success for AWS Solution Architects in the complex world of cloud computing. Working closely with developers, architects help translate architectural designs into functional applications by providing guidance on best practices, security, and scalability. Collaboration with system administrators and DevOps engineers is essential to automate resource provisioning, implement CI/CD pipelines, and ensure the architecture's resilience. Solution Architects liaise with security specialists to embed security measures into the design, and with network engineers to configure networking components in line with performance and security needs. They also partner with database administrators to optimize database performance and with data scientists and analysts to create data solutions leveraging AWS's capabilities. Collaboration with project managers helps align architectural goals with project timelines and budgets, ensuring that cloud solutions are not only technically sound but also delivered on schedule and within budget.
This collaborative approach extends beyond technology, fostering a culture of teamwork and shared responsibility. It promotes effective communication and coordination among cross-functional teams, enabling them to collectively tackle challenges, make informed decisions, and deliver solutions that align with business objectives. In essence, AWS Solution Architects' ability to collaborate with a diverse set of IT roles is integral to their role as orchestrators of cloud excellence, ensuring that AWS solutions not only meet technical requirements but also drive business success.
The Role of AWS Partnerships
Here are the key points about the role of AWS partnerships in a simple format:
-
Expertise Access: AWS partnerships connect businesses with skilled professionals who have deep expertise in AWS technologies, helping organizations make informed decisions and optimize their cloud solutions.
-
Innovation Acceleration: Technology partners collaborate with AWS to create and integrate innovative products and services, allowing customers to harness cutting-edge technology without starting from scratch.
-
Enhanced Support: Consulting and managed service partners offer valuable support, acting as trusted advisors to guide businesses in adopting and managing AWS services effectively.
-
Global Presence: AWS partnerships provide access to AWS services and support in local regions, ensuring global reach and localized assistance for businesses with international operations.
-
Ecosystem Expansion: Partnerships contribute to an extensive ecosystem of third-party solutions that integrate seamlessly with AWS, offering a wide array of options to tailor cloud environments to specific needs.
-
Certified Solutions: AWS-certified partner solutions undergo rigorous testing and validation, ensuring compatibility, reliability, and quality for customers.
-
Resources and Support: AWS offers partners resources, training, marketing support, and co-selling opportunities, enabling them to better serve customers and grow their businesses.
AWS partnerships play a vital role in helping businesses leverage the full potential of AWS cloud services, providing expertise, innovation, and support to drive digital transformation and growth.
Conclusion
In conclusion, AWS Solution Architects hold a pivotal role in the realm of cloud computing, where businesses increasingly rely on AWS's vast array of services and infrastructure. These architects serve as the linchpin between technology and business, bridging the gap by designing, implementing, and optimizing cloud solutions that align with organizational goals. They navigate the complexities of AWS to create architectures that are secure, scalable, cost-efficient, and resilient.
The importance of AWS Solution Architects extends beyond technical prowess. They collaborate with diverse IT roles, facilitate innovation, and leverage AWS partnerships to enhance cloud capabilities. These architects play a key role in disaster recovery, business continuity, security, and compliance, safeguarding critical data and operations. They are instrumental in driving cost optimization, ensuring resources are used efficiently.
As businesses continue to embrace the cloud, AWS Solution Architects will remain essential in guiding these transformations. Their expertise, collaboration, and commitment to innovation enable organizations to thrive in the ever-evolving digital landscape, making them invaluable assets in the journey toward cloud excellence.
CMMI for Agile: Integrating Agile Practices with CMMI Certification
In today's fast-paced and ever-evolving business landscape, organizations are continually seeking ways to deliver high-quality products and services while remaining agile and responsive to customer needs. Agile methodologies have emerged as a beacon of adaptability and customer-centricity, empowering teams to iterate quickly and stay in tune with market demands. Simultaneously, the Capability Maturity Model Integration (CMMI) provides a structured framework for process improvement, ensuring consistency, reliability, and efficiency in operations.
But what happens when you bring these two seemingly contrasting worlds together? Can Agile practices and CMMI certification coexist harmoniously, allowing organizations to reap the benefits of both approaches? The answer is a resounding "yes." This blog explores the dynamic intersection of Agile and CMMI, shedding light on how organizations can successfully integrate Agile practices with CMMI certification, ultimately achieving a unique synergy that enhances both agility and process maturity. Join us on this journey of discovery as we uncover the strategies, challenges, and advantages of merging Agile with CMMI, ushering in a new era of process excellence and customer satisfaction.
Table of Contents
-
Understanding CMMI and Agile Methodologies
-
Benefits of Combining CMMI and Agile
-
Mapping Agile Practices to CMMI Framework
-
Tailoring CMMI for Agile Environments
-
Roles and Responsibilities in Agile CMMI Integration
-
Measuring Agile Performance with CMMI Metrics
-
Agile CMMI Certification Levels
-
Challenges in Integrating Agile and CMMI
-
Training and Skill Development for Agile CMMI
-
Continuous Improvement in Agile CMMI
-
Tools and Software for Agile CMMI Integration
-
Audit and Assessment for Agile CMMI Certification
-
Scaling Agile with CMMI
-
Future Trends in Agile CMMI Integration
-
Conclusion
Understanding CMMI and Agile Methodologies
CMMI (Capability Maturity Model Integration) is a framework that enables organizations to enhance their processes and consistently deliver high-quality products and services. It encompasses maturity levels and specific process areas to guide organizations towards process improvement and optimization. CMMI promotes a culture of continuous improvement, encouraging organizations to monitor, measure, and refine their processes over time. Organizations can undergo CMMI assessments to gauge their process maturity and, if they meet the criteria, seek formal certification.
On the other hand, Agile methodologies are a set of principles and practices for software development and project management that prioritize adaptability, collaboration, and customer feedback. Agile embraces iterative and incremental development, frequent customer involvement, and cross-functional teams. It relies on empirical data and regular inspections to make informed decisions and respond to changing requirements. Agile is guided by the Agile Manifesto and its principles, emphasizing customer collaboration and working solutions.
The relationship between CMMI and Agile involves integrating these approaches to achieve higher levels of process maturity while retaining the flexibility and customer-centric focus of Agile methodologies. This integration, known as "Agile CMMI" or "CMMI for Agile," allows organizations to improve their processes systematically while remaining agile and responsive in an ever-evolving business landscape. By combining the strengths of both CMMI and Agile, organizations can enhance their capabilities, deliver value more efficiently, and meet customer needs effectively.
Benefits of Combining CMMI and Agile
-
Better Processes: CMMI improves your organization's processes, making them more efficient and effective.
-
Flexibility: Agile's adaptability to change is retained, ensuring you can respond quickly to customer needs.
-
Quality: The integration enhances product quality and reduces defects.
-
Customer Satisfaction: Agile's customer focus, combined with CMMI, leads to higher customer satisfaction.
-
Risk Management: You can identify and manage risks more effectively, reducing project disruptions.
-
Resource Efficiency: It helps optimize resource allocation and utilization for dynamic projects.
-
Compliance: You can meet industry standards and compliance requirements while using Agile practices.
-
Culture of Improvement: It fosters a culture of continuous improvement within your organization.
-
Measurable Progress: You can measure and track your progress effectively.
-
Competitive Advantage: Successful integration can give you a competitive edge by delivering high-quality products or services faster and more efficiently.
Mapping Agile Practices to CMMI Framework
Mapping Agile practices to the CMMI (Capability Maturity Model Integration) framework is a strategic approach that enables organizations to combine the agility of Agile methodologies with the structured process improvement provided by CMMI. In this integration, Agile principles and practices align with specific CMMI process areas and goals. For instance, Agile's emphasis on customer collaboration and responsiveness can be linked to CMMI's objectives related to managing requirements effectively and handling change through configuration management. Sprints and iterations in Agile neatly correspond to CMMI's project planning and monitoring and control process areas, and Agile's focus on continuous integration aligns with CMMI's configuration management practices. By mapping these connections, organizations can ensure that their Agile practices contribute to meeting CMMI compliance requirements while still reaping the benefits of Agile's customer-centric, iterative approach to development.
Furthermore, mapping Agile practices to CMMI facilitates a data-driven approach to decision-making by connecting Agile metrics and practices with CMMI's measurement and analysis process area. Agile teams can use metrics like velocity and burndown charts in conjunction with CMMI's goals to continuously improve processes and product quality. This integration also helps organizations manage large-scale Agile projects by considering CMMI for Development, which extends CMMI's process areas to address scalability and complex development environments. Ultimately, the mapping of Agile practices to the CMMI framework empowers organizations to harmonize two powerful methodologies, enhancing both process maturity and agility in their software development and project management endeavors.
Tailoring CMMI for Agile Environments
Tailoring CMMI (Capability Maturity Model Integration) for Agile environments is a strategic approach that recognizes the unique characteristics of Agile methodologies while harnessing the structured process improvement capabilities of CMMI. In this adaptation, organizations embrace Agile's core values such as customer collaboration, responsiveness to change, and iterative development, while identifying the areas within CMMI that can support and enhance these principles. Agile's preference for working software over excessive documentation is met by streamlining documentation requirements, ensuring that any documentation created serves a meaningful purpose. Additionally, tailored metrics in Agile environments shift the focus towards velocity, burndown rates, and customer satisfaction, aligning more closely with Agile project goals and priorities. The synergy between Agile's iterative cycles and CMMI's process improvement cycles allows for continuous enhancements in Agile projects while maintaining the rigor of CMMI.
Moreover, effective tailoring encourages cross-functional collaboration between Agile teams and CMMI practitioners, fostering an environment where the strengths of both approaches are leveraged. This collaboration results in valuable insights, shared best practices, and a culture of ongoing process improvement. By documenting the tailoring decisions and promoting a culture of continuous improvement, organizations can ensure that their tailored CMMI-Agile framework remains flexible, adaptable, and aligned with the ever-evolving needs of Agile development projects. In essence, tailoring CMMI for Agile environments allows organizations to strike a harmonious balance between structured process improvement and the agile, customer-focused, and iterative nature of Agile methodologies, ultimately driving higher-quality outcomes in software development and project management.
Roles and Responsibilities in Agile CMMI Integration
-
Agile Coach:
-
Responsibilities: Guides Agile practices and helps teams understand how Agile aligns with CMMI.
-
CMMI Process Improvement Lead:
-
Responsibilities: Oversees CMMI process improvements and ensures they fit Agile environments.
-
Scrum Masters and Agile Team Members:
-
Responsibilities: Scrum Masters facilitate Agile processes, while team members adapt Agile practices for CMMI.
-
Product Owners and Business Analysts:
-
Responsibilities: Define and prioritize requirements, ensuring they align with Agile and CMMI standards.
-
Quality Assurance and Testing Specialists:
-
Responsibilities: Ensure product quality through testing, adapting to Agile iterations while following CMMI quality practices.
-
Project Managers or Release Managers:
-
Responsibilities: Oversee project or release planning, ensuring alignment with CMMI process areas.
-
Change Agents and Champions:
-
Responsibilities: Advocate for Agile CMMI integration, promote best practices, and encourage a culture of improvement.
-
Auditors and Assessors:
-
Responsibilities: Conduct CMMI assessments and audits to verify compliance and provide feedback for improvement.
Clear communication and collaboration among these roles are essential for successful Agile CMMI integration, enhancing the organization's ability to deliver high-quality products and services while maintaining Agile principles.
Measuring Agile Performance with CMMI Metrics
Measuring Agile performance with CMMI metrics is a strategic approach that bridges the gap between the Agile methodologies' iterative, customer-focused practices and CMMI's structured process improvement framework. These metrics provide organizations with valuable insights into their Agile processes, aligning them with CMMI's goals of efficiency, quality, and continuous improvement. Metrics such as velocity, cycle time, and burndown charts enable teams to monitor progress, identify bottlenecks, and optimize their workflow within the Agile framework. Customer satisfaction surveys and feedback response times ensure that Agile teams remain customer-centric, meeting the requirements of CMMI's customer focus. Additionally, defect density and work item aging metrics help maintain product quality while highlighting areas for improvement, aligning with CMMI's emphasis on quality management.
The integration of CMMI metrics into Agile environments promotes a culture of measurement and analysis, enabling organizations to make data-driven decisions. This not only enhances the organization's ability to deliver high-quality products and services but also ensures compliance with CMMI standards. Ultimately, measuring Agile performance with CMMI metrics empowers organizations to leverage the strengths of both approaches, fostering greater process maturity, efficiency, and customer satisfaction in Agile development and project management.
Agile CMMI Certification Levels
-
CMMI Maturity Levels: CMMI certification involves maturity levels, from Level 1 to Level 5, representing increasing process maturity and capability.
-
Agile Integration: Organizations can integrate Agile practices into these CMMI maturity levels to maintain flexibility while meeting CMMI requirements.
-
Certification Assessment: Certified appraisers or auditors assess an organization's processes, including the integration of Agile practices, to determine certification eligibility.
-
Tailored CMMI: Some organizations use tailored CMMI frameworks that provide specific guidance on incorporating Agile practices at different maturity levels.
-
Industry Requirements: Compliance with CMMI, Agile, or both may be necessary to meet industry standards and client expectations.
-
Consult Experts: Seek guidance from CMMI experts or certification authorities for the latest information and specific certification requirements related to Agile and CMMI integration.
Challenges in Integrating Agile and CMMI
-
Cultural Differences: Balancing Agile's flexibility with CMMI's structured approach can be a cultural challenge.
-
Documentation: Finding the right balance between extensive CMMI documentation and Agile's minimal documentation can be tricky.
-
Resistance to Change: Teams may resist shifting from traditional CMMI practices to Agile or adding perceived bureaucracy to Agile.
-
Mapping Practices: Aligning Agile practices with CMMI requirements and maturity levels requires careful mapping.
-
Process Tailoring: Customizing CMMI practices to fit Agile environments is challenging but necessary.
-
Metrics: Developing metrics that effectively measure performance in an integrated approach can be difficult.
-
Resource Allocation: Allocating resources for both Agile and CMMI efforts must be balanced.
-
Audit and Assessment: Preparing for CMMI assessments and audits in Agile settings requires planning.
-
Skills and Training: Ensuring that team members have the skills for the integrated approach is vital.
-
Sustainability: Maintaining the integration over time and preventing it from becoming a one-time effort is a challenge that requires ongoing commitment and adaptation.
Training and Skill Development for Agile CMMI
Training and skill development are fundamental pillars of achieving a successful integration of Agile and CMMI within an organization. In such an integrated environment, team members, leaders, and practitioners need a comprehensive understanding of both Agile methodologies and CMMI standards to effectively navigate the complexities of this hybrid approach. Initially, basic Agile training establishes a common foundation, fostering an understanding of Agile principles and practices, such as Scrum or Kanban. Concurrently, CMMI-specific training introduces the organization to the CMMI framework's concepts, maturity levels, and process areas.
The critical component lies in integration awareness, where dedicated training sessions and workshops enlighten participants about how Agile practices seamlessly align with CMMI goals while highlighting areas requiring adaptation. These sessions underscore the importance of tailoring CMMI processes to Agile settings, facilitating a smooth transition. Furthermore, training extends to leadership roles, equipping managers and executives with Agile leadership principles and the skills needed to support and lead in an Agile CMMI environment. Ultimately, a continuous learning culture, role-specific training, and feedback mechanisms ensure that individuals and teams stay agile in their approach to process improvement, product development, and compliance, thereby enhancing the organization's ability to excel in both agility and quality assurance.
Continuous Improvement in Agile CMMI
Continuous improvement in Agile CMMI environments represents an ongoing commitment to excellence in process, product, and service delivery. By seamlessly integrating Agile's iterative, customer-centric approach with CMMI's structured process improvement framework, organizations create a powerful engine for relentless enhancement. Agile retrospectives, data-driven decision-making, and Kaizen principles are instrumental in identifying and addressing areas for improvement at the team level. These practices dovetail with CMMI's emphasis on process optimization and quality assurance, resulting in a culture of constant self-assessment and refinement. Data collected through Agile practices, such as velocity and customer feedback, serves as a valuable input for CMMI-compliant measurement and analysis, further aligning the two methodologies.
Moreover, in Agile CMMI environments, continuous improvement extends beyond processes to encompass skill development and leadership support. By nurturing a culture of learning and adaptation, organizations empower their teams and leaders to stay agile in their approach to both product development and process maturity. The synergy between Agile's adaptability and CMMI's rigor creates an environment where innovation and efficiency thrive, ultimately enabling organizations to deliver high-quality products and services that meet customer needs while ensuring compliance with CMMI standards. Top of Form
Tools and Software for Agile CMMI Integration
Tools and software play a crucial role in facilitating the integration of Agile and CMMI methodologies within an organization. These tools bridge the gap between Agile's flexibility and CMMI's structured processes, aiding in the seamless coexistence of both approaches. Project management tools like Jira and Azure DevOps enable Agile teams to plan, track, and manage their work efficiently while accommodating CMMI process areas. Agile Lifecycle Management (ALM) tools such as VersionOne and Rally provide comprehensive support for Agile practices and can be customized to align with CMMI standards. Requirements management tools ensure traceability and compliance with CMMI requirements, while test management tools contribute to quality assurance, aligning with CMMI's focus on testing. Configuration management and version control tools help organizations meet CMMI's configuration management process area requirements. Collaboration and communication tools foster transparency and knowledge sharing among Agile teams, making it easier to document and communicate process improvements. Metrics and analytics tools enable organizations to collect and analyze data for both Agile and CMMI goals, facilitating data-driven process enhancements. DevOps and CI/CD tools automate and streamline development and deployment processes, aligning with CMMI's process automation practices. Specialized process improvement tools may also be employed to support the adoption and assessment of CMMI practices, ensuring continuous process maturity enhancements.
However, the success of these tools in Agile CMMI integration hinges on how they are configured, customized, and integrated into the organization's workflows. Additionally, tool selection should be based on the specific needs and objectives of Agile CMMI integration. The tools serve as enablers, helping organizations achieve the dual goals of delivering high-quality products or services through Agile practices while adhering to the structured process improvement framework of CMMI.
Audit and Assessment for Agile CMMI Certification
The audit and assessment process for Agile CMMI certification is a rigorous and comprehensive evaluation that determines an organization's adherence to both Agile methodologies and CMMI process improvement standards. The journey begins with careful preparation, where trained CMMI appraisers assess an organization's documentation, scrutinize Agile artifacts, and conduct a gap analysis to identify areas of alignment and potential deviations. On-site assessments involve in-depth interviews, observations, and artifact reviews to gauge how Agile practices are implemented in practice. Data collected during the assessment, including Agile-specific metrics and process performance, forms the basis for analysis, leading to documented findings and recommendations.
The ultimate goal of Agile CMMI certification is to demonstrate that an organization can balance the adaptability and customer-centricity of Agile with the structured process improvement focus of CMMI. The certification decision is made by an external body, based on the assessment results, and organizations may receive maturity or capability level ratings. Beyond certification, the process serves as a catalyst for ongoing improvement, as organizations develop action plans to address recommendations and engage in periodic follow-up assessments to ensure that the integrated Agile-CMMI framework remains effective and aligned with evolving goals. This holistic approach to assessment underscores the commitment to continuous improvement, quality, and process maturity in Agile development and project management.
Scaling Agile with CMMI
Scaling Agile with CMMI is a strategic approach that harmonizes the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI, allowing organizations to effectively manage larger and more complex projects and portfolios. This integration typically begins by selecting a suitable Agile scaling framework like SAFe or LeSS, which provides guidance on how to expand Agile practices while ensuring alignment with CMMI goals. Customization of the chosen framework is crucial to adapt CMMI process areas to Agile practices and vice versa, striking the right balance between Agile's adaptability and CMMI's process rigor.
Leadership support plays a pivotal role in fostering this integration, as leaders champion the effort, allocate necessary resources, and actively engage in aligning Agile and CMMI practices. Organizations must prioritize continuous improvement, regularly assessing the integration's effectiveness through metrics, feedback, and assessment processes. By promoting a culture of collaboration, providing training and skill development, and maintaining compliance with CMMI standards through periodic assessments, organizations can successfully scale Agile while achieving the desired levels of process maturity and product quality. The result is a dynamic and adaptable approach to project and product management that thrives in complex and evolving business landscapes.
Future Trends in Agile CMMI Integration
The future of Agile CMMI integration promises to be both dynamic and transformative, reflecting the ever-evolving landscape of software development and process improvement. One key trend is the increasing role of AI and automation in optimizing processes and decision-making. AI-driven tools will assist organizations in analyzing vast datasets, identifying patterns, and recommending improvements, making Agile CMMI integration more data-driven and efficient. Additionally, as Agile principles continue to resonate with organizations seeking agility and customer-centricity, scaling Agile practices beyond individual teams to the entire enterprise will remain a prominent trend. Frameworks like SAFe and LeSS will evolve to support larger and more complex organizations in their Agile journeys, allowing them to balance agility with the structured process improvement goals of CMMI.
Another critical trend is the integration of security and compliance practices into Agile CMMI environments. With cybersecurity concerns on the rise, organizations will work to harmonize Agile's rapid delivery with CMMI's focus on risk management and compliance, ensuring that security and regulatory requirements are seamlessly embedded into the development process. As remote and distributed work become increasingly prevalent, Agile CMMI integration will adapt to address the unique challenges of virtual collaboration and process adherence. This adaptability, along with a growing emphasis on cultural transformation, will be instrumental in organizations' efforts to foster a culture of innovation, collaboration, and continuous learning, ultimately driving successful Agile CMMI integration in the years to come.
How to obtain the CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab ,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, Agile CMMI integration represents a powerful approach for organizations seeking to balance the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI. This integration enables organizations to achieve high levels of process maturity while delivering high-quality products and services. The process involves careful customization of Agile practices and CMMI process areas, leadership support, continuous improvement efforts, and a commitment to aligning Agile and CMMI principles. As the business landscape evolves, the integration of Agile and CMMI will continue to adapt to meet new challenges and opportunities.
Future trends in Agile CMMI integration, including the use of AI, scaling Agile practices, and the integration of security and compliance, will shape the way organizations approach process improvement and Agile delivery. Cultural transformation and a focus on value stream management will also play critical roles in the success of Agile CMMI integration efforts. Overall, the integration of Agile and CMMI is a journey toward achieving process excellence and delivering exceptional value to customers, and it will remain a key strategy for organizations striving to excel in an ever-changing world.
Read More
In today's fast-paced and ever-evolving business landscape, organizations are continually seeking ways to deliver high-quality products and services while remaining agile and responsive to customer needs. Agile methodologies have emerged as a beacon of adaptability and customer-centricity, empowering teams to iterate quickly and stay in tune with market demands. Simultaneously, the Capability Maturity Model Integration (CMMI) provides a structured framework for process improvement, ensuring consistency, reliability, and efficiency in operations.
But what happens when you bring these two seemingly contrasting worlds together? Can Agile practices and CMMI certification coexist harmoniously, allowing organizations to reap the benefits of both approaches? The answer is a resounding "yes." This blog explores the dynamic intersection of Agile and CMMI, shedding light on how organizations can successfully integrate Agile practices with CMMI certification, ultimately achieving a unique synergy that enhances both agility and process maturity. Join us on this journey of discovery as we uncover the strategies, challenges, and advantages of merging Agile with CMMI, ushering in a new era of process excellence and customer satisfaction.
Table of Contents
-
Understanding CMMI and Agile Methodologies
-
Benefits of Combining CMMI and Agile
-
Mapping Agile Practices to CMMI Framework
-
Tailoring CMMI for Agile Environments
-
Roles and Responsibilities in Agile CMMI Integration
-
Measuring Agile Performance with CMMI Metrics
-
Agile CMMI Certification Levels
-
Challenges in Integrating Agile and CMMI
-
Training and Skill Development for Agile CMMI
-
Continuous Improvement in Agile CMMI
-
Tools and Software for Agile CMMI Integration
-
Audit and Assessment for Agile CMMI Certification
-
Scaling Agile with CMMI
-
Future Trends in Agile CMMI Integration
-
Conclusion
Understanding CMMI and Agile Methodologies
CMMI (Capability Maturity Model Integration) is a framework that enables organizations to enhance their processes and consistently deliver high-quality products and services. It encompasses maturity levels and specific process areas to guide organizations towards process improvement and optimization. CMMI promotes a culture of continuous improvement, encouraging organizations to monitor, measure, and refine their processes over time. Organizations can undergo CMMI assessments to gauge their process maturity and, if they meet the criteria, seek formal certification.
On the other hand, Agile methodologies are a set of principles and practices for software development and project management that prioritize adaptability, collaboration, and customer feedback. Agile embraces iterative and incremental development, frequent customer involvement, and cross-functional teams. It relies on empirical data and regular inspections to make informed decisions and respond to changing requirements. Agile is guided by the Agile Manifesto and its principles, emphasizing customer collaboration and working solutions.
The relationship between CMMI and Agile involves integrating these approaches to achieve higher levels of process maturity while retaining the flexibility and customer-centric focus of Agile methodologies. This integration, known as "Agile CMMI" or "CMMI for Agile," allows organizations to improve their processes systematically while remaining agile and responsive in an ever-evolving business landscape. By combining the strengths of both CMMI and Agile, organizations can enhance their capabilities, deliver value more efficiently, and meet customer needs effectively.
Benefits of Combining CMMI and Agile
-
Better Processes: CMMI improves your organization's processes, making them more efficient and effective.
-
Flexibility: Agile's adaptability to change is retained, ensuring you can respond quickly to customer needs.
-
Quality: The integration enhances product quality and reduces defects.
-
Customer Satisfaction: Agile's customer focus, combined with CMMI, leads to higher customer satisfaction.
-
Risk Management: You can identify and manage risks more effectively, reducing project disruptions.
-
Resource Efficiency: It helps optimize resource allocation and utilization for dynamic projects.
-
Compliance: You can meet industry standards and compliance requirements while using Agile practices.
-
Culture of Improvement: It fosters a culture of continuous improvement within your organization.
-
Measurable Progress: You can measure and track your progress effectively.
-
Competitive Advantage: Successful integration can give you a competitive edge by delivering high-quality products or services faster and more efficiently.
Mapping Agile Practices to CMMI Framework
Mapping Agile practices to the CMMI (Capability Maturity Model Integration) framework is a strategic approach that enables organizations to combine the agility of Agile methodologies with the structured process improvement provided by CMMI. In this integration, Agile principles and practices align with specific CMMI process areas and goals. For instance, Agile's emphasis on customer collaboration and responsiveness can be linked to CMMI's objectives related to managing requirements effectively and handling change through configuration management. Sprints and iterations in Agile neatly correspond to CMMI's project planning and monitoring and control process areas, and Agile's focus on continuous integration aligns with CMMI's configuration management practices. By mapping these connections, organizations can ensure that their Agile practices contribute to meeting CMMI compliance requirements while still reaping the benefits of Agile's customer-centric, iterative approach to development.
Furthermore, mapping Agile practices to CMMI facilitates a data-driven approach to decision-making by connecting Agile metrics and practices with CMMI's measurement and analysis process area. Agile teams can use metrics like velocity and burndown charts in conjunction with CMMI's goals to continuously improve processes and product quality. This integration also helps organizations manage large-scale Agile projects by considering CMMI for Development, which extends CMMI's process areas to address scalability and complex development environments. Ultimately, the mapping of Agile practices to the CMMI framework empowers organizations to harmonize two powerful methodologies, enhancing both process maturity and agility in their software development and project management endeavors.
Tailoring CMMI for Agile Environments
Tailoring CMMI (Capability Maturity Model Integration) for Agile environments is a strategic approach that recognizes the unique characteristics of Agile methodologies while harnessing the structured process improvement capabilities of CMMI. In this adaptation, organizations embrace Agile's core values such as customer collaboration, responsiveness to change, and iterative development, while identifying the areas within CMMI that can support and enhance these principles. Agile's preference for working software over excessive documentation is met by streamlining documentation requirements, ensuring that any documentation created serves a meaningful purpose. Additionally, tailored metrics in Agile environments shift the focus towards velocity, burndown rates, and customer satisfaction, aligning more closely with Agile project goals and priorities. The synergy between Agile's iterative cycles and CMMI's process improvement cycles allows for continuous enhancements in Agile projects while maintaining the rigor of CMMI.
Moreover, effective tailoring encourages cross-functional collaboration between Agile teams and CMMI practitioners, fostering an environment where the strengths of both approaches are leveraged. This collaboration results in valuable insights, shared best practices, and a culture of ongoing process improvement. By documenting the tailoring decisions and promoting a culture of continuous improvement, organizations can ensure that their tailored CMMI-Agile framework remains flexible, adaptable, and aligned with the ever-evolving needs of Agile development projects. In essence, tailoring CMMI for Agile environments allows organizations to strike a harmonious balance between structured process improvement and the agile, customer-focused, and iterative nature of Agile methodologies, ultimately driving higher-quality outcomes in software development and project management.
Roles and Responsibilities in Agile CMMI Integration
-
Agile Coach:
-
Responsibilities: Guides Agile practices and helps teams understand how Agile aligns with CMMI.
-
-
CMMI Process Improvement Lead:
-
Responsibilities: Oversees CMMI process improvements and ensures they fit Agile environments.
-
-
Scrum Masters and Agile Team Members:
-
Responsibilities: Scrum Masters facilitate Agile processes, while team members adapt Agile practices for CMMI.
-
-
Product Owners and Business Analysts:
-
Responsibilities: Define and prioritize requirements, ensuring they align with Agile and CMMI standards.
-
-
Quality Assurance and Testing Specialists:
-
Responsibilities: Ensure product quality through testing, adapting to Agile iterations while following CMMI quality practices.
-
-
Project Managers or Release Managers:
-
Responsibilities: Oversee project or release planning, ensuring alignment with CMMI process areas.
-
-
Change Agents and Champions:
-
Responsibilities: Advocate for Agile CMMI integration, promote best practices, and encourage a culture of improvement.
-
-
Auditors and Assessors:
-
Responsibilities: Conduct CMMI assessments and audits to verify compliance and provide feedback for improvement.
-
Clear communication and collaboration among these roles are essential for successful Agile CMMI integration, enhancing the organization's ability to deliver high-quality products and services while maintaining Agile principles.
Measuring Agile Performance with CMMI Metrics
Measuring Agile performance with CMMI metrics is a strategic approach that bridges the gap between the Agile methodologies' iterative, customer-focused practices and CMMI's structured process improvement framework. These metrics provide organizations with valuable insights into their Agile processes, aligning them with CMMI's goals of efficiency, quality, and continuous improvement. Metrics such as velocity, cycle time, and burndown charts enable teams to monitor progress, identify bottlenecks, and optimize their workflow within the Agile framework. Customer satisfaction surveys and feedback response times ensure that Agile teams remain customer-centric, meeting the requirements of CMMI's customer focus. Additionally, defect density and work item aging metrics help maintain product quality while highlighting areas for improvement, aligning with CMMI's emphasis on quality management.
The integration of CMMI metrics into Agile environments promotes a culture of measurement and analysis, enabling organizations to make data-driven decisions. This not only enhances the organization's ability to deliver high-quality products and services but also ensures compliance with CMMI standards. Ultimately, measuring Agile performance with CMMI metrics empowers organizations to leverage the strengths of both approaches, fostering greater process maturity, efficiency, and customer satisfaction in Agile development and project management.
Agile CMMI Certification Levels
-
CMMI Maturity Levels: CMMI certification involves maturity levels, from Level 1 to Level 5, representing increasing process maturity and capability.
-
Agile Integration: Organizations can integrate Agile practices into these CMMI maturity levels to maintain flexibility while meeting CMMI requirements.
-
Certification Assessment: Certified appraisers or auditors assess an organization's processes, including the integration of Agile practices, to determine certification eligibility.
-
Tailored CMMI: Some organizations use tailored CMMI frameworks that provide specific guidance on incorporating Agile practices at different maturity levels.
-
Industry Requirements: Compliance with CMMI, Agile, or both may be necessary to meet industry standards and client expectations.
-
Consult Experts: Seek guidance from CMMI experts or certification authorities for the latest information and specific certification requirements related to Agile and CMMI integration.
Challenges in Integrating Agile and CMMI
-
Cultural Differences: Balancing Agile's flexibility with CMMI's structured approach can be a cultural challenge.
-
Documentation: Finding the right balance between extensive CMMI documentation and Agile's minimal documentation can be tricky.
-
Resistance to Change: Teams may resist shifting from traditional CMMI practices to Agile or adding perceived bureaucracy to Agile.
-
Mapping Practices: Aligning Agile practices with CMMI requirements and maturity levels requires careful mapping.
-
Process Tailoring: Customizing CMMI practices to fit Agile environments is challenging but necessary.
-
Metrics: Developing metrics that effectively measure performance in an integrated approach can be difficult.
-
Resource Allocation: Allocating resources for both Agile and CMMI efforts must be balanced.
-
Audit and Assessment: Preparing for CMMI assessments and audits in Agile settings requires planning.
-
Skills and Training: Ensuring that team members have the skills for the integrated approach is vital.
-
Sustainability: Maintaining the integration over time and preventing it from becoming a one-time effort is a challenge that requires ongoing commitment and adaptation.
Training and Skill Development for Agile CMMI
Training and skill development are fundamental pillars of achieving a successful integration of Agile and CMMI within an organization. In such an integrated environment, team members, leaders, and practitioners need a comprehensive understanding of both Agile methodologies and CMMI standards to effectively navigate the complexities of this hybrid approach. Initially, basic Agile training establishes a common foundation, fostering an understanding of Agile principles and practices, such as Scrum or Kanban. Concurrently, CMMI-specific training introduces the organization to the CMMI framework's concepts, maturity levels, and process areas.
The critical component lies in integration awareness, where dedicated training sessions and workshops enlighten participants about how Agile practices seamlessly align with CMMI goals while highlighting areas requiring adaptation. These sessions underscore the importance of tailoring CMMI processes to Agile settings, facilitating a smooth transition. Furthermore, training extends to leadership roles, equipping managers and executives with Agile leadership principles and the skills needed to support and lead in an Agile CMMI environment. Ultimately, a continuous learning culture, role-specific training, and feedback mechanisms ensure that individuals and teams stay agile in their approach to process improvement, product development, and compliance, thereby enhancing the organization's ability to excel in both agility and quality assurance.
Continuous Improvement in Agile CMMI
Continuous improvement in Agile CMMI environments represents an ongoing commitment to excellence in process, product, and service delivery. By seamlessly integrating Agile's iterative, customer-centric approach with CMMI's structured process improvement framework, organizations create a powerful engine for relentless enhancement. Agile retrospectives, data-driven decision-making, and Kaizen principles are instrumental in identifying and addressing areas for improvement at the team level. These practices dovetail with CMMI's emphasis on process optimization and quality assurance, resulting in a culture of constant self-assessment and refinement. Data collected through Agile practices, such as velocity and customer feedback, serves as a valuable input for CMMI-compliant measurement and analysis, further aligning the two methodologies.
Moreover, in Agile CMMI environments, continuous improvement extends beyond processes to encompass skill development and leadership support. By nurturing a culture of learning and adaptation, organizations empower their teams and leaders to stay agile in their approach to both product development and process maturity. The synergy between Agile's adaptability and CMMI's rigor creates an environment where innovation and efficiency thrive, ultimately enabling organizations to deliver high-quality products and services that meet customer needs while ensuring compliance with CMMI standards. Top of Form
Tools and Software for Agile CMMI Integration
Tools and software play a crucial role in facilitating the integration of Agile and CMMI methodologies within an organization. These tools bridge the gap between Agile's flexibility and CMMI's structured processes, aiding in the seamless coexistence of both approaches. Project management tools like Jira and Azure DevOps enable Agile teams to plan, track, and manage their work efficiently while accommodating CMMI process areas. Agile Lifecycle Management (ALM) tools such as VersionOne and Rally provide comprehensive support for Agile practices and can be customized to align with CMMI standards. Requirements management tools ensure traceability and compliance with CMMI requirements, while test management tools contribute to quality assurance, aligning with CMMI's focus on testing. Configuration management and version control tools help organizations meet CMMI's configuration management process area requirements. Collaboration and communication tools foster transparency and knowledge sharing among Agile teams, making it easier to document and communicate process improvements. Metrics and analytics tools enable organizations to collect and analyze data for both Agile and CMMI goals, facilitating data-driven process enhancements. DevOps and CI/CD tools automate and streamline development and deployment processes, aligning with CMMI's process automation practices. Specialized process improvement tools may also be employed to support the adoption and assessment of CMMI practices, ensuring continuous process maturity enhancements.
However, the success of these tools in Agile CMMI integration hinges on how they are configured, customized, and integrated into the organization's workflows. Additionally, tool selection should be based on the specific needs and objectives of Agile CMMI integration. The tools serve as enablers, helping organizations achieve the dual goals of delivering high-quality products or services through Agile practices while adhering to the structured process improvement framework of CMMI.
Audit and Assessment for Agile CMMI Certification
The audit and assessment process for Agile CMMI certification is a rigorous and comprehensive evaluation that determines an organization's adherence to both Agile methodologies and CMMI process improvement standards. The journey begins with careful preparation, where trained CMMI appraisers assess an organization's documentation, scrutinize Agile artifacts, and conduct a gap analysis to identify areas of alignment and potential deviations. On-site assessments involve in-depth interviews, observations, and artifact reviews to gauge how Agile practices are implemented in practice. Data collected during the assessment, including Agile-specific metrics and process performance, forms the basis for analysis, leading to documented findings and recommendations.
The ultimate goal of Agile CMMI certification is to demonstrate that an organization can balance the adaptability and customer-centricity of Agile with the structured process improvement focus of CMMI. The certification decision is made by an external body, based on the assessment results, and organizations may receive maturity or capability level ratings. Beyond certification, the process serves as a catalyst for ongoing improvement, as organizations develop action plans to address recommendations and engage in periodic follow-up assessments to ensure that the integrated Agile-CMMI framework remains effective and aligned with evolving goals. This holistic approach to assessment underscores the commitment to continuous improvement, quality, and process maturity in Agile development and project management.
Scaling Agile with CMMI
Scaling Agile with CMMI is a strategic approach that harmonizes the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI, allowing organizations to effectively manage larger and more complex projects and portfolios. This integration typically begins by selecting a suitable Agile scaling framework like SAFe or LeSS, which provides guidance on how to expand Agile practices while ensuring alignment with CMMI goals. Customization of the chosen framework is crucial to adapt CMMI process areas to Agile practices and vice versa, striking the right balance between Agile's adaptability and CMMI's process rigor.
Leadership support plays a pivotal role in fostering this integration, as leaders champion the effort, allocate necessary resources, and actively engage in aligning Agile and CMMI practices. Organizations must prioritize continuous improvement, regularly assessing the integration's effectiveness through metrics, feedback, and assessment processes. By promoting a culture of collaboration, providing training and skill development, and maintaining compliance with CMMI standards through periodic assessments, organizations can successfully scale Agile while achieving the desired levels of process maturity and product quality. The result is a dynamic and adaptable approach to project and product management that thrives in complex and evolving business landscapes.
Future Trends in Agile CMMI Integration
The future of Agile CMMI integration promises to be both dynamic and transformative, reflecting the ever-evolving landscape of software development and process improvement. One key trend is the increasing role of AI and automation in optimizing processes and decision-making. AI-driven tools will assist organizations in analyzing vast datasets, identifying patterns, and recommending improvements, making Agile CMMI integration more data-driven and efficient. Additionally, as Agile principles continue to resonate with organizations seeking agility and customer-centricity, scaling Agile practices beyond individual teams to the entire enterprise will remain a prominent trend. Frameworks like SAFe and LeSS will evolve to support larger and more complex organizations in their Agile journeys, allowing them to balance agility with the structured process improvement goals of CMMI.
Another critical trend is the integration of security and compliance practices into Agile CMMI environments. With cybersecurity concerns on the rise, organizations will work to harmonize Agile's rapid delivery with CMMI's focus on risk management and compliance, ensuring that security and regulatory requirements are seamlessly embedded into the development process. As remote and distributed work become increasingly prevalent, Agile CMMI integration will adapt to address the unique challenges of virtual collaboration and process adherence. This adaptability, along with a growing emphasis on cultural transformation, will be instrumental in organizations' efforts to foster a culture of innovation, collaboration, and continuous learning, ultimately driving successful Agile CMMI integration in the years to come.
How to obtain the CMMI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab ,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, Agile CMMI integration represents a powerful approach for organizations seeking to balance the flexibility and customer-centricity of Agile methodologies with the structured process improvement framework of CMMI. This integration enables organizations to achieve high levels of process maturity while delivering high-quality products and services. The process involves careful customization of Agile practices and CMMI process areas, leadership support, continuous improvement efforts, and a commitment to aligning Agile and CMMI principles. As the business landscape evolves, the integration of Agile and CMMI will continue to adapt to meet new challenges and opportunities.
Future trends in Agile CMMI integration, including the use of AI, scaling Agile practices, and the integration of security and compliance, will shape the way organizations approach process improvement and Agile delivery. Cultural transformation and a focus on value stream management will also play critical roles in the success of Agile CMMI integration efforts. Overall, the integration of Agile and CMMI is a journey toward achieving process excellence and delivering exceptional value to customers, and it will remain a key strategy for organizations striving to excel in an ever-changing world.
SAS Base Programming for Statistical Analysis: Tips and Tricks
Welcome to our blog, where we dive deep into the world of statistical analysis using SAS Base Programming. If you're a data enthusiast, statistician, or someone looking to harness the power of SAS for statistical analysis, you've come to the right place. In this comprehensive guide, we'll be sharing a treasure trove of tips and tricks to help you navigate the complexities of SAS Base Programming, making your statistical analysis endeavors not only more efficient but also more effective.
SAS, which stands for Statistical Analysis System, is a renowned software suite used by professionals across various industries to analyze data, extract valuable insights, and make data-driven decisions. Whether you're a beginner taking your first steps into the world of SAS or an experienced practitioner looking to refine your skills, this blog will cater to all levels of expertise.
From data preparation to visualization, hypothesis testing to regression analysis, our aim is to equip you with the knowledge and techniques needed to become a proficient SAS Base Programmer. We'll unravel the intricacies of SAS, providing you with actionable insights, best practices, and shortcuts that can help streamline your workflow.
So, fasten your seatbelts and get ready to embark on a journey through the world of SAS Base Programming. Whether you're analyzing sales data, conducting medical research, or studying market trends, the tips and tricks you'll discover here will be invaluable in your quest for statistical mastery. Let's explore the fascinating realm of SAS Base Programming together!
Table of Contents
-
Overview of Statistical Analysis in SAS Base Programming:
-
Data Preparation for Statistical Analysis:
-
Descriptive Statistics in SAS:
-
Hypothesis Testing with SAS:
-
Regression Analysis with SAS:
-
ANOVA (Analysis of Variance) in SAS:
-
Non-parametric Statistics in SAS:
-
Advanced SAS Functions for Statistical Analysis:
-
Tips for Efficient Data Visualization:
-
Handling Large Datasets for Statistical Analysis:
-
Time Series Analysis in SAS:
-
Survival Analysis in SAS:
-
SAS Enterprise Guide for Statistical Analysis:
-
Best Practices for Documentation and Reporting:
-
Common Pitfalls to Avoid in SAS Statistical Analysis:
-
Conclusion:
Overview of Statistical Analysis in SAS Base Programming:
SAS Base Programming serves as a robust platform for statistical analysis, offering data analysts and researchers a comprehensive toolkit to explore and interpret data effectively. SAS enables users to perform a wide array of statistical tasks, from basic descriptive statistics that summarize data to advanced hypothesis testing, regression modeling, and time series analysis. With its extensive library of procedures and functions, SAS empowers analysts to apply statistical concepts like mean, variance, and hypothesis testing to real-world data, making informed decisions and drawing valuable insights.
In addition to statistical procedures, SAS emphasizes the importance of data preparation, ensuring that data is clean, validated, and ready for analysis. It facilitates result interpretation through customizable reports and visuals, allowing analysts to communicate their findings clearly. Whether conducting simple data exploration or complex predictive modeling, understanding SAS Base Programming's role in statistical analysis is crucial for harnessing its capabilities and harnessing the power of data-driven decision-making effectively.
Data Preparation for Statistical Analysis:
Data preparation in the context of statistical analysis using SAS Base Programming is the vital process of ensuring that your dataset is clean, consistent, and ready for meaningful analysis. It begins with data cleaning, where you identify and rectify data errors, inconsistencies, and outliers that could distort the results. SAS tools allow you to efficiently handle missing data, correct discrepancies, and validate the data against predefined criteria, ensuring its integrity. Moreover, data transformation techniques in SAS enable you to modify variables, recode categories, and perform other necessary adjustments to meet the assumptions of statistical tests or better suit the research objectives.
Once the data is clean and validated, data exploration becomes crucial. SAS offers capabilities to generate descriptive statistics and visualizations, which help analysts gain insights into the dataset's distribution, patterns, and potential relationships. Data preparation, as a fundamental step in statistical analysis, sets the stage for more accurate and reliable results, ensuring that the subsequent statistical tests and modeling efforts are based on a solid foundation of high-quality data.
Descriptive Statistics in SAS
Descriptive statistics in SAS are a fundamental aspect of data analysis, providing a concise and informative summary of the key characteristics of a dataset. SAS offers a versatile set of procedures and tools that enable data analysts to explore data distributions, central tendencies, and variabilities quickly. PROC MEANS and PROC FREQ, for example, are go-to procedures for obtaining statistics like means, medians, frequencies, and percentages, which help analysts grasp the fundamental aspects of both numerical and categorical data. Furthermore, SAS provides graphical representations like histograms, box plots, and scatterplots that facilitate visual exploration, allowing analysts to identify outliers, assess data normality, and detect patterns and trends.
These descriptive statistics serve as the foundation for more advanced statistical analyses, guiding the selection of appropriate modeling techniques and hypothesis tests. They also play a crucial role in data visualization, aiding in the creation of informative charts and graphs that make complex data more accessible to a wider audience. In essence, descriptive statistics in SAS not only simplify the initial data exploration process but also enable researchers and analysts to make informed decisions and communicate their findings effectively.
Hypothesis Testing with SAS:
Hypothesis testing is a fundamental statistical process, and SAS equips analysts with a robust toolkit to conduct hypothesis tests efficiently and rigorously. SAS procedures such as PROC TTEST, PROC ANOVA, and PROC FREQ streamline the process of testing research hypotheses, whether it involves comparing means, proportions, variances, or assessing associations. Analysts can tailor these procedures to their specific research questions by specifying the variables of interest, significance levels, and test types, allowing for a wide range of hypothesis tests to be performed. SAS also automates the calculation of test statistics, p-values, and confidence intervals, simplifying the task of determining whether there is significant evidence to support or reject a null hypothesis.
Interpreting SAS output is a crucial step in hypothesis testing. Analysts look for p-values that indicate the likelihood of obtaining the observed results under the assumption that the null hypothesis is true. A small p-value, typically less than the chosen significance level (e.g., 0.05), suggests that there is strong evidence against the null hypothesis. SAS empowers analysts to draw statistically informed conclusions, aiding researchers, and decision-makers across various fields in making evidence-based choices and driving impactful outcomes.
Regression Analysis with SAS:
Regression analysis is a cornerstone of statistical modeling in SAS, allowing analysts to unlock the intricate relationships between variables within their datasets. SAS offers a suite of regression procedures that cater to diverse research questions and data types. Simple linear regression investigates how a single predictor influences a response variable, while multiple linear regression extends this analysis to multiple predictors. For binary outcomes or classification tasks, logistic regression in SAS is widely utilized. Analysts can fine-tune regression models by incorporating interaction terms, polynomial relationships, and handling categorical variables, all with the flexibility provided by SAS procedures.
The process involves thorough data preparation, model specification, estimation, and assessment to ensure that the model accurately represents the data. Analysts interpret the model's coefficients and assess its overall goodness of fit, utilizing diagnostic statistics and plots. SAS empowers analysts to perform hypothesis tests on individual predictors and the overall model, enhancing their ability to draw meaningful insights from data. Ultimately, regression analysis with SAS empowers researchers and data analysts across various industries to make informed decisions, predict outcomes, and uncover valuable insights from their datasets.
ANOVA (Analysis of Variance) in SAS
Analysis of Variance (ANOVA) is a powerful statistical method, and SAS provides a robust platform for conducting ANOVA analyses. With SAS, analysts can explore differences among group means efficiently, making it a crucial tool for various fields, including research, quality control, and experimental design. Analysts start by selecting the appropriate ANOVA procedure, such as PROC ANOVA or PROC GLM, based on the data's structure and research objectives. Data preparation involves organizing and cleaning the dataset, while model specification entails defining the factors and levels that will be compared in the analysis.
SAS calculates ANOVA statistics and generates comprehensive output that includes F-statistics, p-values, and other relevant information, allowing analysts to determine whether there are statistically significant differences among the groups. Post-hoc tests further help identify which specific groups differ from each other when significant differences are found. This enables analysts to make data-driven decisions, draw meaningful conclusions, and report findings effectively. Overall, ANOVA in SAS empowers researchers and data analysts to conduct in-depth group comparisons, contributing to better-informed decision-making and deeper insights into the underlying factors influencing data variability.
Non-parametric Statistics in SAS:
Non-parametric statistics, when applied using SAS, provide a versatile and robust approach to data analysis, particularly in situations where conventional parametric assumptions don't hold. SAS offers a suite of procedures that empower data analysts to explore differences, associations, and relationships in datasets without relying on assumptions like normality or homogeneity of variances. Whether it's comparing two or more groups with tests like the Wilcoxon signed-rank or Mann-Whitney U tests in PROC NPAR1WAY, or assessing the independence of categorical variables with chi-squared tests in PROC FREQ, SAS offers a wide array of non-parametric tools to suit various research questions. These procedures provide valuable insights into the data's underlying patterns, making them invaluable in fields such as clinical research, social sciences, and environmental studies where data distributions may be non-standard or unpredictable.
Interpreting results from non-parametric tests in SAS involves assessing the significance of test statistics and p-values, similar to parametric analyses, but without the reliance on strict distributional assumptions. The flexibility of SAS allows analysts to perform these analyses efficiently, and the generated reports make it easier to communicate findings to stakeholders, ensuring that data-driven decisions are made with confidence even in situations where the data's nature is less conventional. In essence, non-parametric statistics in SAS expand the toolkit of data analysts, enabling them to conduct rigorous and insightful analyses that are robust to the variability often encountered in real-world datasets.
Advanced SAS Functions for Statistical Analysis:
Advanced SAS functions are a cornerstone of statistical analysis, offering data analysts powerful tools to handle complex data manipulation and gain deeper insights from their datasets. These functions extend the capabilities of SAS far beyond basic summary statistics, enabling analysts to perform intricate tasks such as advanced modeling, time-series analysis, and custom data transformations. PROC SQL, for instance, empowers users to perform intricate data querying and joining operations, making it invaluable when dealing with large and complex datasets. Additionally, SAS's array functions and user-defined functions (UDFs) allow for efficient processing of multiple variables and the creation of custom functions tailored to specific analytical needs.
Furthermore, SAS's extensive library of statistical functions, including those for ranking, probability distributions, and modeling, empowers analysts to explore complex relationships within data and conduct hypothesis testing with confidence. These functions are instrumental in research, financial analysis, healthcare, and various other domains where rigorous statistical analysis is essential. With advanced SAS functions at their disposal, data analysts can enhance their analytical capabilities and leverage the full potential of SAS for solving complex real-world problems.
Tips for Efficient Data Visualization
-
Choose the Right Procedure: Select the appropriate SAS procedure for your specific visualization needs, such as PROC SGPLOT for general graphs or PROC GCHART for categorical data.
-
Clean and Prepare Data: Ensure your data is clean, sorted, and properly formatted before creating visualizations.
-
Customize Appearance: Customize colors, markers, fonts, and legends to improve visual clarity and engagement.
-
Add Labels: Include clear and descriptive labels for data points, axes, and legends to enhance understanding.
-
Annotations: Use annotations to highlight important features or provide additional context to your graphs.
-
Apply ODS Graphics Styles: Utilize SAS's built-in graphics styles to quickly change the overall look of your visuals.
-
Combine Plots: Consider using PROC SGPANEL to create a panel of graphs when comparing data across groups or variables.
-
Save and Export: Save your visualizations in various formats for sharing or further analysis.
-
Efficient Code: Write efficient code, utilize macro variables, and consider loops for repetitive tasks.
-
Testing and Documentation: Test your visualizations with different datasets, optimize code for performance, and document your work for reproducibility.
-
Accessibility: Ensure your visualizations are accessible to all users, including those with disabilities, by providing alternative text and considering color choices.
Handling Large Datasets for Statistical Analysis
Handling large datasets for statistical analysis demands a thoughtful approach to ensure both efficiency and meaningful insights. Firstly, data preprocessing is critical. Begin by cleaning the data, removing duplicates, and addressing missing values. Next, consider data sampling or reduction techniques to create a manageable subset that retains the dataset's key characteristics. Filtering out unnecessary columns and rows based on the analysis goals is also essential. To optimize computational efficiency, parallel processing can be leveraged if supported by your statistical software or hardware. Additionally, efficient coding practices, like vectorized operations and minimizing loops, can significantly speed up data processing.
Furthermore, consider the use of optimized data structures, like data tables or databases, to handle large datasets more efficiently. Indexing can accelerate data retrieval, while data compression may reduce storage requirements. In cases where data cannot fit into memory, explore external storage options or distributed computing environments. Incremental analysis, where subsets of data are processed and aggregated progressively, can make working with large datasets more manageable. Lastly, thorough documentation of data processing steps and analysis procedures is crucial for reproducibility and collaboration, ensuring that the insights derived from large datasets are accurate and reliable.
Time Series Analysis in SAS
Time series analysis in SAS is a systematic approach to unraveling the intricate patterns within temporal data. SAS offers a comprehensive suite of procedures and tools designed to handle time series data efficiently. Starting with data preparation, SAS enables users to clean and structure their time series data appropriately, including handling missing values and creating SAS time series datasets. Exploratory data analysis is facilitated through data visualization tools, allowing analysts to gain insights into patterns, seasonality, and potential outliers in their time series data.
SAS provides a versatile set of modeling procedures for time series analysis, such as PROC ARIMA and PROC ESM, which can be tailored to specific modeling objectives and data characteristics. Analysts can estimate model parameters, perform diagnostics to validate the model's adequacy, and produce forecasts for future time points. Visualization capabilities further aid in presenting results, helping analysts communicate insights and predictions effectively. With SAS's time series analysis capabilities, organizations can leverage historical data to make informed decisions, forecast trends, and optimize resource allocation in various domains, including finance, economics, and operations.
Survival Analysis in SAS
Survival analysis in SAS is a powerful statistical technique for examining time-to-event data, where events of interest could be anything from disease occurrences to mechanical failures. SAS provides a comprehensive toolkit for performing survival analysis tasks efficiently. Analysts can start by structuring their data correctly, including the essential variables for time-to-event, event status, and covariates. SAS's PROC LIFETEST allows for non-parametric analysis, facilitating the creation of Kaplan-Meier survival curves that illustrate how survival probabilities change over time. For more sophisticated analyses, PROC PHREG enables the fitting of Cox proportional hazards models, which assess the influence of covariates on the hazard rate while considering censoring. The versatility of SAS extends to handling time-dependent covariates, stratified analyses, and various parametric survival models, offering researchers and analysts a comprehensive platform for understanding and modeling survival data.
With SAS's survival analysis capabilities, researchers in fields like healthcare, engineering, and finance can gain critical insights into the factors influencing time-to-event outcomes. This enables them to make informed decisions, develop predictive models, and assess the impact of covariates on survival outcomes. Whether it's studying patient survival in a clinical trial, analyzing product reliability, or evaluating investment strategies, SAS equips analysts with the tools needed to extract meaningful information from time-to-event data and derive actionable insights for decision-making.
SAS Enterprise Guide for Statistical Analysis
SAS Enterprise Guide serves as a versatile and user-friendly platform for statistical analysis, catering to a wide range of users, from beginners to seasoned statisticians. Its strength lies in its ability to streamline the entire data analysis workflow. With a point-and-click interface, users can effortlessly import, manage, and explore their data, and then apply a plethora of statistical techniques and models without writing extensive code. This accessibility makes it an ideal choice for professionals in fields like healthcare, finance, marketing, and research, where robust statistical analysis is essential but not everyone has programming expertise.
Additionally, SAS Enterprise Guide promotes collaboration and efficiency. Teams can work seamlessly on projects, share analyses, and maintain consistency in reporting. The tool's automation and scheduling capabilities save time and ensure that routine data updates, analyses, and report generation occur reliably. Moreover, its integration with other SAS products and external data sources offers users the flexibility to leverage the full spectrum of SAS analytics and data management capabilities, making SAS Enterprise Guide a comprehensive solution for statistical analysis and data-driven decision-making.
Best Practices for Documentation and Reporting
Effective documentation and reporting are essential in various fields, including research, business, and data analysis. Proper documentation ensures that your work is transparent, reproducible, and understandable by others. Here are some best practices for documentation and reporting:
-
Plan Ahead: Before you start any project, establish a clear plan for documentation and reporting. Define what needs to be documented, who the audience is, and what format is most suitable for conveying your findings.
-
Use a Consistent Structure: Create a standardized structure for your documents and reports. This typically includes sections such as an introduction, methodology, results, discussion, and conclusions. Consistency makes it easier for readers to navigate and understand your work.
-
Version Control: Implement version control for your documents and data files. This ensures that you can track changes, revert to previous versions if needed, and maintain a clear record of the project's evolution.
-
Clear and Descriptive Titles: Provide clear and descriptive titles for sections, tables, figures, and charts. Titles should convey the content's main message and help readers quickly grasp the information.
-
Detailed Methodology: Document your research or analysis methodology thoroughly. Describe the data sources, data collection process, software tools used, and any assumptions made during the analysis.
-
Cite Sources: If you reference external sources, cite them properly. Use a consistent citation style (e.g., APA, MLA) and include a bibliography or reference section.
-
Include Visuals: Incorporate visual aids such as tables, graphs, and charts to illustrate your findings. Ensure that visuals are well-labeled and accompanied by explanations.
-
Interpret Results: Don't just present data; interpret the results. Explain what the data means in the context of your research or analysis and why it's significant.
-
Avoid Jargon: Use plain language whenever possible. Avoid unnecessary jargon or technical terms that may confuse your audience. If technical terms are necessary, provide explanations or definitions.
-
Review and Edit: Proofread your documents and reports carefully for errors in grammar, spelling, and formatting. Consider having a colleague review your work for clarity and coherence.
-
Include Code and Scripts: If your work involves coding or scripting, include the code or script alongside your documentation. This allows others to reproduce your analysis.
-
Transparent Assumptions: Be transparent about any assumptions made during your analysis or research. Explain why these assumptions were necessary and their potential impact on the results.
-
Documentation for Code: If you write code, include comments within the code to explain its purpose, logic, and any complex parts. Use a consistent style for code comments.
-
Keep Records: Maintain detailed records of data sources, data cleaning, transformations, and any changes made during the analysis. This helps with traceability and auditing.
-
Consider the Audience: Tailor your documentation and reporting to your audience's level of expertise. Provide additional details for technical audiences and simplify explanations for non-experts.
-
Ethical Considerations: Address any ethical considerations or conflicts of interest in your documentation, particularly in research and business reports.
By following these best practices, you can create well-documented and well-structured reports and documents that enhance transparency, support reproducibility, and effectively communicate your findings to your intended audience.
Common Pitfalls to Avoid in SAS Statistical Analysis
Performing statistical analysis in SAS can be highly effective, but it's essential to navigate common pitfalls to ensure the accuracy and reliability of results. One of the most prevalent mistakes is insufficient data preparation. Failing to clean, format, and handle missing data properly can introduce errors and bias into your analysis. Additionally, overlooking data assumptions and not checking for outliers or multicollinearity can undermine the validity of your findings. Another significant pitfall is the misinterpretation of results, particularly with p-values. It's crucial to understand that statistical significance does not always equate to practical significance, and results should be considered in the broader context of the research or problem being addressed. Furthermore, inadequate documentation and communication can hinder collaboration and reproducibility. Clear and comprehensive documentation of analysis steps, assumptions, and model parameters is essential for transparency and future reference.
In predictive modeling, overfitting and data leakage are common pitfalls. Using overly complex models that fit the training data too closely can lead to models that perform poorly on new data. Cross-validation is a critical tool for assessing model generalization. Data leakage, where information from the target variable or future data is inadvertently included in the training dataset, can lead to overly optimistic model performance estimates. Avoiding these pitfalls requires careful data preparation, model selection, and evaluation practices. Finally, it's essential to consider the broader context of the data, including potential biases, and ensure that your analysis and reporting are accessible and understandable to your target audience, whether they are experts or non-experts in statistics.
How to obtain SAS Base Programmer Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop
Development : SAS Base Programmer Certification
Conclusion
In conclusion, SAS Base Programming is an indispensable tool for statistical analysis, providing a comprehensive suite of procedures and functionalities that empower analysts and researchers across various domains. Whether it's uncovering insights from data, conducting hypothesis tests, building predictive models, or performing advanced analyses like survival or time series analysis, SAS offers a versatile platform to meet diverse analytical needs. However, to maximize the utility of SAS, it's crucial to adhere to best practices in data preparation, analysis, and reporting. These practices include thorough data cleaning, robust model validation, transparent documentation, and clear communication of results, ensuring that the outcomes of statistical analyses are not only accurate but also actionable.
Furthermore, users should remain vigilant about common pitfalls, such as improper data handling, overfitting, and misinterpretation of statistical significance. Avoiding these pitfalls requires a thoughtful and methodical approach, with an emphasis on understanding the data, the assumptions underlying statistical tests, and the broader context in which the analysis is conducted. By doing so, analysts can harness the full potential of SAS Base Programming to derive meaningful insights, make informed decisions, and contribute to data-driven advancements in their respective fields.
Read More
Welcome to our blog, where we dive deep into the world of statistical analysis using SAS Base Programming. If you're a data enthusiast, statistician, or someone looking to harness the power of SAS for statistical analysis, you've come to the right place. In this comprehensive guide, we'll be sharing a treasure trove of tips and tricks to help you navigate the complexities of SAS Base Programming, making your statistical analysis endeavors not only more efficient but also more effective.
SAS, which stands for Statistical Analysis System, is a renowned software suite used by professionals across various industries to analyze data, extract valuable insights, and make data-driven decisions. Whether you're a beginner taking your first steps into the world of SAS or an experienced practitioner looking to refine your skills, this blog will cater to all levels of expertise.
From data preparation to visualization, hypothesis testing to regression analysis, our aim is to equip you with the knowledge and techniques needed to become a proficient SAS Base Programmer. We'll unravel the intricacies of SAS, providing you with actionable insights, best practices, and shortcuts that can help streamline your workflow.
So, fasten your seatbelts and get ready to embark on a journey through the world of SAS Base Programming. Whether you're analyzing sales data, conducting medical research, or studying market trends, the tips and tricks you'll discover here will be invaluable in your quest for statistical mastery. Let's explore the fascinating realm of SAS Base Programming together!
Table of Contents
-
Overview of Statistical Analysis in SAS Base Programming:
-
Data Preparation for Statistical Analysis:
-
Descriptive Statistics in SAS:
-
Hypothesis Testing with SAS:
-
Regression Analysis with SAS:
-
ANOVA (Analysis of Variance) in SAS:
-
Non-parametric Statistics in SAS:
-
Advanced SAS Functions for Statistical Analysis:
-
Tips for Efficient Data Visualization:
-
Handling Large Datasets for Statistical Analysis:
-
Time Series Analysis in SAS:
-
Survival Analysis in SAS:
-
SAS Enterprise Guide for Statistical Analysis:
-
Best Practices for Documentation and Reporting:
-
Common Pitfalls to Avoid in SAS Statistical Analysis:
-
Conclusion:
Overview of Statistical Analysis in SAS Base Programming:
SAS Base Programming serves as a robust platform for statistical analysis, offering data analysts and researchers a comprehensive toolkit to explore and interpret data effectively. SAS enables users to perform a wide array of statistical tasks, from basic descriptive statistics that summarize data to advanced hypothesis testing, regression modeling, and time series analysis. With its extensive library of procedures and functions, SAS empowers analysts to apply statistical concepts like mean, variance, and hypothesis testing to real-world data, making informed decisions and drawing valuable insights.
In addition to statistical procedures, SAS emphasizes the importance of data preparation, ensuring that data is clean, validated, and ready for analysis. It facilitates result interpretation through customizable reports and visuals, allowing analysts to communicate their findings clearly. Whether conducting simple data exploration or complex predictive modeling, understanding SAS Base Programming's role in statistical analysis is crucial for harnessing its capabilities and harnessing the power of data-driven decision-making effectively.
Data Preparation for Statistical Analysis:
Data preparation in the context of statistical analysis using SAS Base Programming is the vital process of ensuring that your dataset is clean, consistent, and ready for meaningful analysis. It begins with data cleaning, where you identify and rectify data errors, inconsistencies, and outliers that could distort the results. SAS tools allow you to efficiently handle missing data, correct discrepancies, and validate the data against predefined criteria, ensuring its integrity. Moreover, data transformation techniques in SAS enable you to modify variables, recode categories, and perform other necessary adjustments to meet the assumptions of statistical tests or better suit the research objectives.
Once the data is clean and validated, data exploration becomes crucial. SAS offers capabilities to generate descriptive statistics and visualizations, which help analysts gain insights into the dataset's distribution, patterns, and potential relationships. Data preparation, as a fundamental step in statistical analysis, sets the stage for more accurate and reliable results, ensuring that the subsequent statistical tests and modeling efforts are based on a solid foundation of high-quality data.
Descriptive Statistics in SAS
Descriptive statistics in SAS are a fundamental aspect of data analysis, providing a concise and informative summary of the key characteristics of a dataset. SAS offers a versatile set of procedures and tools that enable data analysts to explore data distributions, central tendencies, and variabilities quickly. PROC MEANS and PROC FREQ, for example, are go-to procedures for obtaining statistics like means, medians, frequencies, and percentages, which help analysts grasp the fundamental aspects of both numerical and categorical data. Furthermore, SAS provides graphical representations like histograms, box plots, and scatterplots that facilitate visual exploration, allowing analysts to identify outliers, assess data normality, and detect patterns and trends.
These descriptive statistics serve as the foundation for more advanced statistical analyses, guiding the selection of appropriate modeling techniques and hypothesis tests. They also play a crucial role in data visualization, aiding in the creation of informative charts and graphs that make complex data more accessible to a wider audience. In essence, descriptive statistics in SAS not only simplify the initial data exploration process but also enable researchers and analysts to make informed decisions and communicate their findings effectively.
Hypothesis Testing with SAS:
Hypothesis testing is a fundamental statistical process, and SAS equips analysts with a robust toolkit to conduct hypothesis tests efficiently and rigorously. SAS procedures such as PROC TTEST, PROC ANOVA, and PROC FREQ streamline the process of testing research hypotheses, whether it involves comparing means, proportions, variances, or assessing associations. Analysts can tailor these procedures to their specific research questions by specifying the variables of interest, significance levels, and test types, allowing for a wide range of hypothesis tests to be performed. SAS also automates the calculation of test statistics, p-values, and confidence intervals, simplifying the task of determining whether there is significant evidence to support or reject a null hypothesis.
Interpreting SAS output is a crucial step in hypothesis testing. Analysts look for p-values that indicate the likelihood of obtaining the observed results under the assumption that the null hypothesis is true. A small p-value, typically less than the chosen significance level (e.g., 0.05), suggests that there is strong evidence against the null hypothesis. SAS empowers analysts to draw statistically informed conclusions, aiding researchers, and decision-makers across various fields in making evidence-based choices and driving impactful outcomes.
Regression Analysis with SAS:
Regression analysis is a cornerstone of statistical modeling in SAS, allowing analysts to unlock the intricate relationships between variables within their datasets. SAS offers a suite of regression procedures that cater to diverse research questions and data types. Simple linear regression investigates how a single predictor influences a response variable, while multiple linear regression extends this analysis to multiple predictors. For binary outcomes or classification tasks, logistic regression in SAS is widely utilized. Analysts can fine-tune regression models by incorporating interaction terms, polynomial relationships, and handling categorical variables, all with the flexibility provided by SAS procedures.
The process involves thorough data preparation, model specification, estimation, and assessment to ensure that the model accurately represents the data. Analysts interpret the model's coefficients and assess its overall goodness of fit, utilizing diagnostic statistics and plots. SAS empowers analysts to perform hypothesis tests on individual predictors and the overall model, enhancing their ability to draw meaningful insights from data. Ultimately, regression analysis with SAS empowers researchers and data analysts across various industries to make informed decisions, predict outcomes, and uncover valuable insights from their datasets.
ANOVA (Analysis of Variance) in SAS
Analysis of Variance (ANOVA) is a powerful statistical method, and SAS provides a robust platform for conducting ANOVA analyses. With SAS, analysts can explore differences among group means efficiently, making it a crucial tool for various fields, including research, quality control, and experimental design. Analysts start by selecting the appropriate ANOVA procedure, such as PROC ANOVA or PROC GLM, based on the data's structure and research objectives. Data preparation involves organizing and cleaning the dataset, while model specification entails defining the factors and levels that will be compared in the analysis.
SAS calculates ANOVA statistics and generates comprehensive output that includes F-statistics, p-values, and other relevant information, allowing analysts to determine whether there are statistically significant differences among the groups. Post-hoc tests further help identify which specific groups differ from each other when significant differences are found. This enables analysts to make data-driven decisions, draw meaningful conclusions, and report findings effectively. Overall, ANOVA in SAS empowers researchers and data analysts to conduct in-depth group comparisons, contributing to better-informed decision-making and deeper insights into the underlying factors influencing data variability.
Non-parametric Statistics in SAS:
Non-parametric statistics, when applied using SAS, provide a versatile and robust approach to data analysis, particularly in situations where conventional parametric assumptions don't hold. SAS offers a suite of procedures that empower data analysts to explore differences, associations, and relationships in datasets without relying on assumptions like normality or homogeneity of variances. Whether it's comparing two or more groups with tests like the Wilcoxon signed-rank or Mann-Whitney U tests in PROC NPAR1WAY, or assessing the independence of categorical variables with chi-squared tests in PROC FREQ, SAS offers a wide array of non-parametric tools to suit various research questions. These procedures provide valuable insights into the data's underlying patterns, making them invaluable in fields such as clinical research, social sciences, and environmental studies where data distributions may be non-standard or unpredictable.
Interpreting results from non-parametric tests in SAS involves assessing the significance of test statistics and p-values, similar to parametric analyses, but without the reliance on strict distributional assumptions. The flexibility of SAS allows analysts to perform these analyses efficiently, and the generated reports make it easier to communicate findings to stakeholders, ensuring that data-driven decisions are made with confidence even in situations where the data's nature is less conventional. In essence, non-parametric statistics in SAS expand the toolkit of data analysts, enabling them to conduct rigorous and insightful analyses that are robust to the variability often encountered in real-world datasets.
Advanced SAS Functions for Statistical Analysis:
Advanced SAS functions are a cornerstone of statistical analysis, offering data analysts powerful tools to handle complex data manipulation and gain deeper insights from their datasets. These functions extend the capabilities of SAS far beyond basic summary statistics, enabling analysts to perform intricate tasks such as advanced modeling, time-series analysis, and custom data transformations. PROC SQL, for instance, empowers users to perform intricate data querying and joining operations, making it invaluable when dealing with large and complex datasets. Additionally, SAS's array functions and user-defined functions (UDFs) allow for efficient processing of multiple variables and the creation of custom functions tailored to specific analytical needs.
Furthermore, SAS's extensive library of statistical functions, including those for ranking, probability distributions, and modeling, empowers analysts to explore complex relationships within data and conduct hypothesis testing with confidence. These functions are instrumental in research, financial analysis, healthcare, and various other domains where rigorous statistical analysis is essential. With advanced SAS functions at their disposal, data analysts can enhance their analytical capabilities and leverage the full potential of SAS for solving complex real-world problems.
Tips for Efficient Data Visualization
-
Choose the Right Procedure: Select the appropriate SAS procedure for your specific visualization needs, such as PROC SGPLOT for general graphs or PROC GCHART for categorical data.
-
Clean and Prepare Data: Ensure your data is clean, sorted, and properly formatted before creating visualizations.
-
Customize Appearance: Customize colors, markers, fonts, and legends to improve visual clarity and engagement.
-
Add Labels: Include clear and descriptive labels for data points, axes, and legends to enhance understanding.
-
Annotations: Use annotations to highlight important features or provide additional context to your graphs.
-
Apply ODS Graphics Styles: Utilize SAS's built-in graphics styles to quickly change the overall look of your visuals.
-
Combine Plots: Consider using PROC SGPANEL to create a panel of graphs when comparing data across groups or variables.
-
Save and Export: Save your visualizations in various formats for sharing or further analysis.
-
Efficient Code: Write efficient code, utilize macro variables, and consider loops for repetitive tasks.
-
Testing and Documentation: Test your visualizations with different datasets, optimize code for performance, and document your work for reproducibility.
-
Accessibility: Ensure your visualizations are accessible to all users, including those with disabilities, by providing alternative text and considering color choices.
Handling Large Datasets for Statistical Analysis
Handling large datasets for statistical analysis demands a thoughtful approach to ensure both efficiency and meaningful insights. Firstly, data preprocessing is critical. Begin by cleaning the data, removing duplicates, and addressing missing values. Next, consider data sampling or reduction techniques to create a manageable subset that retains the dataset's key characteristics. Filtering out unnecessary columns and rows based on the analysis goals is also essential. To optimize computational efficiency, parallel processing can be leveraged if supported by your statistical software or hardware. Additionally, efficient coding practices, like vectorized operations and minimizing loops, can significantly speed up data processing.
Furthermore, consider the use of optimized data structures, like data tables or databases, to handle large datasets more efficiently. Indexing can accelerate data retrieval, while data compression may reduce storage requirements. In cases where data cannot fit into memory, explore external storage options or distributed computing environments. Incremental analysis, where subsets of data are processed and aggregated progressively, can make working with large datasets more manageable. Lastly, thorough documentation of data processing steps and analysis procedures is crucial for reproducibility and collaboration, ensuring that the insights derived from large datasets are accurate and reliable.
Time Series Analysis in SAS
Time series analysis in SAS is a systematic approach to unraveling the intricate patterns within temporal data. SAS offers a comprehensive suite of procedures and tools designed to handle time series data efficiently. Starting with data preparation, SAS enables users to clean and structure their time series data appropriately, including handling missing values and creating SAS time series datasets. Exploratory data analysis is facilitated through data visualization tools, allowing analysts to gain insights into patterns, seasonality, and potential outliers in their time series data.
SAS provides a versatile set of modeling procedures for time series analysis, such as PROC ARIMA and PROC ESM, which can be tailored to specific modeling objectives and data characteristics. Analysts can estimate model parameters, perform diagnostics to validate the model's adequacy, and produce forecasts for future time points. Visualization capabilities further aid in presenting results, helping analysts communicate insights and predictions effectively. With SAS's time series analysis capabilities, organizations can leverage historical data to make informed decisions, forecast trends, and optimize resource allocation in various domains, including finance, economics, and operations.
Survival Analysis in SAS
Survival analysis in SAS is a powerful statistical technique for examining time-to-event data, where events of interest could be anything from disease occurrences to mechanical failures. SAS provides a comprehensive toolkit for performing survival analysis tasks efficiently. Analysts can start by structuring their data correctly, including the essential variables for time-to-event, event status, and covariates. SAS's PROC LIFETEST allows for non-parametric analysis, facilitating the creation of Kaplan-Meier survival curves that illustrate how survival probabilities change over time. For more sophisticated analyses, PROC PHREG enables the fitting of Cox proportional hazards models, which assess the influence of covariates on the hazard rate while considering censoring. The versatility of SAS extends to handling time-dependent covariates, stratified analyses, and various parametric survival models, offering researchers and analysts a comprehensive platform for understanding and modeling survival data.
With SAS's survival analysis capabilities, researchers in fields like healthcare, engineering, and finance can gain critical insights into the factors influencing time-to-event outcomes. This enables them to make informed decisions, develop predictive models, and assess the impact of covariates on survival outcomes. Whether it's studying patient survival in a clinical trial, analyzing product reliability, or evaluating investment strategies, SAS equips analysts with the tools needed to extract meaningful information from time-to-event data and derive actionable insights for decision-making.
SAS Enterprise Guide for Statistical Analysis
SAS Enterprise Guide serves as a versatile and user-friendly platform for statistical analysis, catering to a wide range of users, from beginners to seasoned statisticians. Its strength lies in its ability to streamline the entire data analysis workflow. With a point-and-click interface, users can effortlessly import, manage, and explore their data, and then apply a plethora of statistical techniques and models without writing extensive code. This accessibility makes it an ideal choice for professionals in fields like healthcare, finance, marketing, and research, where robust statistical analysis is essential but not everyone has programming expertise.
Additionally, SAS Enterprise Guide promotes collaboration and efficiency. Teams can work seamlessly on projects, share analyses, and maintain consistency in reporting. The tool's automation and scheduling capabilities save time and ensure that routine data updates, analyses, and report generation occur reliably. Moreover, its integration with other SAS products and external data sources offers users the flexibility to leverage the full spectrum of SAS analytics and data management capabilities, making SAS Enterprise Guide a comprehensive solution for statistical analysis and data-driven decision-making.
Best Practices for Documentation and Reporting
Effective documentation and reporting are essential in various fields, including research, business, and data analysis. Proper documentation ensures that your work is transparent, reproducible, and understandable by others. Here are some best practices for documentation and reporting:
-
Plan Ahead: Before you start any project, establish a clear plan for documentation and reporting. Define what needs to be documented, who the audience is, and what format is most suitable for conveying your findings.
-
Use a Consistent Structure: Create a standardized structure for your documents and reports. This typically includes sections such as an introduction, methodology, results, discussion, and conclusions. Consistency makes it easier for readers to navigate and understand your work.
-
Version Control: Implement version control for your documents and data files. This ensures that you can track changes, revert to previous versions if needed, and maintain a clear record of the project's evolution.
-
Clear and Descriptive Titles: Provide clear and descriptive titles for sections, tables, figures, and charts. Titles should convey the content's main message and help readers quickly grasp the information.
-
Detailed Methodology: Document your research or analysis methodology thoroughly. Describe the data sources, data collection process, software tools used, and any assumptions made during the analysis.
-
Cite Sources: If you reference external sources, cite them properly. Use a consistent citation style (e.g., APA, MLA) and include a bibliography or reference section.
-
Include Visuals: Incorporate visual aids such as tables, graphs, and charts to illustrate your findings. Ensure that visuals are well-labeled and accompanied by explanations.
-
Interpret Results: Don't just present data; interpret the results. Explain what the data means in the context of your research or analysis and why it's significant.
-
Avoid Jargon: Use plain language whenever possible. Avoid unnecessary jargon or technical terms that may confuse your audience. If technical terms are necessary, provide explanations or definitions.
-
Review and Edit: Proofread your documents and reports carefully for errors in grammar, spelling, and formatting. Consider having a colleague review your work for clarity and coherence.
-
Include Code and Scripts: If your work involves coding or scripting, include the code or script alongside your documentation. This allows others to reproduce your analysis.
-
Transparent Assumptions: Be transparent about any assumptions made during your analysis or research. Explain why these assumptions were necessary and their potential impact on the results.
-
Documentation for Code: If you write code, include comments within the code to explain its purpose, logic, and any complex parts. Use a consistent style for code comments.
-
Keep Records: Maintain detailed records of data sources, data cleaning, transformations, and any changes made during the analysis. This helps with traceability and auditing.
-
Consider the Audience: Tailor your documentation and reporting to your audience's level of expertise. Provide additional details for technical audiences and simplify explanations for non-experts.
-
Ethical Considerations: Address any ethical considerations or conflicts of interest in your documentation, particularly in research and business reports.
By following these best practices, you can create well-documented and well-structured reports and documents that enhance transparency, support reproducibility, and effectively communicate your findings to your intended audience.
Common Pitfalls to Avoid in SAS Statistical Analysis
Performing statistical analysis in SAS can be highly effective, but it's essential to navigate common pitfalls to ensure the accuracy and reliability of results. One of the most prevalent mistakes is insufficient data preparation. Failing to clean, format, and handle missing data properly can introduce errors and bias into your analysis. Additionally, overlooking data assumptions and not checking for outliers or multicollinearity can undermine the validity of your findings. Another significant pitfall is the misinterpretation of results, particularly with p-values. It's crucial to understand that statistical significance does not always equate to practical significance, and results should be considered in the broader context of the research or problem being addressed. Furthermore, inadequate documentation and communication can hinder collaboration and reproducibility. Clear and comprehensive documentation of analysis steps, assumptions, and model parameters is essential for transparency and future reference.
In predictive modeling, overfitting and data leakage are common pitfalls. Using overly complex models that fit the training data too closely can lead to models that perform poorly on new data. Cross-validation is a critical tool for assessing model generalization. Data leakage, where information from the target variable or future data is inadvertently included in the training dataset, can lead to overly optimistic model performance estimates. Avoiding these pitfalls requires careful data preparation, model selection, and evaluation practices. Finally, it's essential to consider the broader context of the data, including potential biases, and ensure that your analysis and reporting are accessible and understandable to your target audience, whether they are experts or non-experts in statistics.
How to obtain SAS Base Programmer Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop
Development : SAS Base Programmer Certification
Conclusion
In conclusion, SAS Base Programming is an indispensable tool for statistical analysis, providing a comprehensive suite of procedures and functionalities that empower analysts and researchers across various domains. Whether it's uncovering insights from data, conducting hypothesis tests, building predictive models, or performing advanced analyses like survival or time series analysis, SAS offers a versatile platform to meet diverse analytical needs. However, to maximize the utility of SAS, it's crucial to adhere to best practices in data preparation, analysis, and reporting. These practices include thorough data cleaning, robust model validation, transparent documentation, and clear communication of results, ensuring that the outcomes of statistical analyses are not only accurate but also actionable.
Furthermore, users should remain vigilant about common pitfalls, such as improper data handling, overfitting, and misinterpretation of statistical significance. Avoiding these pitfalls requires a thoughtful and methodical approach, with an emphasis on understanding the data, the assumptions underlying statistical tests, and the broader context in which the analysis is conducted. By doing so, analysts can harness the full potential of SAS Base Programming to derive meaningful insights, make informed decisions, and contribute to data-driven advancements in their respective fields.
The Role of Ethical Hacking in Modern Organizations
In today's digital age, where data is the lifeblood of businesses and organizations, safeguarding sensitive information and digital assets has become paramount. With cyber threats constantly evolving in sophistication and scope, modern organizations face a formidable challenge in ensuring their cybersecurity defenses are robust and resilient. It is in this landscape that ethical hacking emerges as a crucial and proactive strategy for safeguarding organizations against cyberattacks.
Ethical hacking, often referred to as "white-hat" hacking, is a practice where skilled professionals employ their expertise to identify vulnerabilities, assess security measures, and test the resilience of an organization's digital infrastructure. Unlike malicious hackers who exploit weaknesses for personal gain, ethical hackers work with the explicit goal of fortifying cybersecurity defenses. In this exploration of "The Role of Ethical Hacking in Modern Organizations," we will delve into the vital functions and significance of ethical hacking in defending against cyber threats, securing sensitive data, and ensuring the continued success of businesses in an increasingly digital world.
Table of contents
-
The Ethical Hacker's Toolkit
-
Types of Ethical Hacking Services
-
The Ethical Hacker's Code of Ethics
-
Ethical Hacking for Regulatory Compliance
-
Ethical Hacking for IoT Security:
-
Challenges and Ethical Dilemmas in Ethical Hacking:
-
Collaboration Between Ethical Hackers and IT Security Teams
-
The Role of Continuous Monitoring in Ethical Hacking:
-
Future Trends in Ethical Hacking:
-
Conclusion
The Ethical Hacker's Toolkit
The ethical hacker's toolkit is a comprehensive set of specialized software and tools that enable cybersecurity professionals to simulate cyberattacks and uncover vulnerabilities within an organization's digital infrastructure. These tools range from network scanners, vulnerability assessment software, and password-cracking utilities to web application scanners and exploitation frameworks. By utilizing these tools, ethical hackers can systematically assess an organization's security posture, identify weaknesses, and help fortify defenses. These tools empower ethical hackers to probe systems, networks, and applications for vulnerabilities, ultimately assisting organizations in preemptively addressing potential security risks before malicious actors can exploit them.
In addition to the technical tools, the ethical hacker's toolkit also includes crucial skills like scripting and coding, which enable them to create custom solutions and adapt to unique security challenges. Continuous learning and staying updated on emerging threats and tools are paramount in this field, as the landscape of cybersecurity is ever-evolving. Ethical hackers are committed to maintaining the integrity of systems and data while using their toolkit responsibly and ethically to protect organizations from cyber threats.
Types of Ethical Hacking Services
-
Vulnerability Assessment:
-
Identifies weaknesses in systems, networks, and apps.
-
Prioritizes vulnerabilities based on severity.
-
Penetration Testing (Pen Testing):
-
Simulates real cyberattacks to test defenses.
-
Reveals how well security measures handle attacks.
-
Web Application Testing:
-
Focuses on securing websites and online services.
-
Checks for vulnerabilities like hacking attempts.
-
Wireless Network Testing:
-
Assesses Wi-Fi network security.
-
Looks for flaws that could allow unauthorized access.
-
Social Engineering Testing:
-
Evaluates susceptibility to tricks like phishing.
-
Educates employees on avoiding manipulation.
-
Mobile Application Security Testing:
-
Ensures security of mobile apps (iOS, Android).
-
Identifies vulnerabilities that could compromise data.
-
Cloud Security Assessment:
-
Examines security in cloud-based systems.
-
Checks settings, permissions, and access controls.
-
IoT Security Assessment:
-
Focuses on securing Internet of Things (IoT) devices.
-
Identifies vulnerabilities in interconnected devices.
-
Red Team Testing:
-
Simulates advanced cyberattacks.
-
Assesses overall security preparedness.
-
Incident Response Testing:
-
Helps organizations refine responses to security incidents.
-
Tests the ability to detect, mitigate, and recover from attacks.
The Ethical Hacker's Code of Ethics
Here are the key points of the Ethical Hacker's Code of Ethics in a simplified form:
-
Permission First: Ethical hackers must get permission before testing any computer system or network.
-
Respect Privacy: They should protect confidential information they encounter during their work.
-
No Data Damage: Their actions should not harm data, systems, or services.
-
Follow Laws: They must operate within legal boundaries and obey all relevant laws.
-
Report Vulnerabilities: Ethical hackers report any security flaws they find to the owners so they can fix them.
-
Keep Learning: They stay up-to-date with the latest cybersecurity knowledge and tools.
-
No Harmful Intent: Ethical hackers never use their skills for harm or personal gain.
-
Tools for Good: They use hacking tools only for legitimate testing purposes.
-
Education and Awareness: They often help educate others about cybersecurity and how to protect themselves.
-
Professional Integrity: Ethical hackers act with honesty, transparency, and integrity in all they do.
Ethical Hacking for Regulatory Compliance
Ethical hacking for regulatory compliance is a critical practice in today's data-driven and highly regulated business environment. With stringent regulatory standards such as GDPR, HIPAA, and PCI DSS in place, organizations are obligated to safeguard sensitive data and maintain robust cybersecurity measures. Ethical hacking serves as a proactive approach to help organizations meet these regulatory requirements effectively. By simulating real cyberattacks and identifying vulnerabilities before malicious actors can exploit them, ethical hackers play a pivotal role in assessing an organization's security infrastructure. Furthermore, ethical hacking engagements can be tailored to specific regulatory needs, focusing on the precise compliance requirements of an organization's industry and region. Through regular audits, meticulous documentation, and proactive risk mitigation, ethical hacking not only helps organizations maintain compliance but also enhances their cybersecurity posture and readiness for regulatory audits, ultimately ensuring the protection of sensitive data and the preservation of reputation and trust.
Ethical Hacking for IoT Security
Ethical hacking for IoT (Internet of Things) security involves a systematic and proactive approach to identifying and addressing vulnerabilities within IoT ecosystems to ensure their resilience against cyber threats. IoT devices, which include everything from smart thermostats and wearable devices to industrial sensors and autonomous vehicles, have become an integral part of modern life and business operations. However, their widespread adoption has also introduced new security risks due to their interconnected nature and diverse applications.
Ethical hackers, also known as white-hat hackers, use their skills and knowledge to simulate potential cyberattacks on IoT devices, networks, and platforms. Their primary objectives are to:
-
Identify Vulnerabilities: Ethical hackers employ various tools and techniques to identify vulnerabilities in IoT devices and the infrastructure supporting them. This may include analyzing device firmware, communication protocols, and cloud services.
-
Assess Security Controls: They evaluate the effectiveness of security controls implemented in IoT ecosystems. This involves examining access controls, encryption mechanisms, and authentication processes to ensure they are robust and resilient.
-
Test for Weaknesses: Ethical hackers conduct penetration testing to determine if unauthorized access, data breaches, or device manipulation is possible. They assess the IoT system's susceptibility to common cyber threats, such as malware, denial-of-service attacks, and physical tampering.
-
Provide Recommendations: Based on their findings, ethical hackers offer recommendations and solutions to mitigate identified vulnerabilities and enhance the overall security posture of IoT environments. This may include applying patches, strengthening access controls, or improving encryption methods.
-
Promote Security Awareness: Ethical hackers also play a role in educating IoT device manufacturers, developers, and users about best practices for security. They raise awareness about potential risks and the importance of regular updates and secure configurations.
-
Compliance and Standards: Ethical hacking for IoT security helps organizations align with industry-specific regulations and standards, ensuring compliance with data protection and privacy laws.
By conducting ethical hacking assessments on IoT systems, organizations can proactively address security weaknesses, minimize the risk of cyberattacks, protect sensitive data, and maintain the reliability of their IoT devices and networks. As the IoT landscape continues to evolve, ethical hacking remains an essential strategy for safeguarding these interconnected technologies and enhancing their resilience against emerging threats.
Challenges and Ethical Dilemmas in Ethical Hacking
-
Legal Boundaries:
-
Ethical hackers must stay within the law.
-
Distinguishing ethical hacking from illegal hacking can be tricky.
-
Authorization and Permission:
-
Getting clear permission to hack is crucial.
-
Obtaining authorization, especially in large organizations, can be challenging.
-
User Privacy and Data Protection:
-
Ethical hackers may encounter sensitive data during assessments.
-
Balancing the need to reveal vulnerabilities with protecting user privacy is a challenge.
-
Third-Party Systems:
-
Ethical hackers often assess external systems.
-
The ethical challenge arises when vulnerabilities are found in systems the organization doesn't control.
-
Full Disclosure vs. Responsible Disclosure:
-
Deciding whether to disclose vulnerabilities publicly (full disclosure) or privately to the organization (responsible disclosure) is a complex ethical choice.
-
It involves considering the impact on security and public awareness.
-
Technical Proficiency and Adaptation:
-
Staying technically proficient and updated is an ongoing challenge.
-
Ethical hackers must adapt to evolving cyber threats and technologies.
-
Neutrality and Objectivity:
-
Remaining neutral and objective during assessments is essential.
-
Personal biases or judgments can compromise the assessment's integrity.
Collaboration Between Ethical Hackers and IT Security Teams
Collaboration between ethical hackers and IT security teams is an indispensable partnership in the realm of cybersecurity. Ethical hackers, armed with their expertise and hacking skills, serve as the first line of defense by proactively identifying vulnerabilities within an organization's systems, networks, and applications. They conduct penetration testing and vulnerability assessments to simulate real-world cyberattacks, pinpoint weaknesses, and report their findings. This critical information forms the foundation upon which IT security teams build their defensive strategies. IT security professionals then take the insights provided by ethical hackers and apply them to patch vulnerabilities, implement stronger security measures, and enhance overall cybersecurity posture. This synergy ensures a proactive and dynamic approach to cybersecurity, enabling organizations to stay one step ahead of malicious actors and respond effectively to emerging threats. Collaboration between ethical hackers and IT security teams is not merely a partnership; it is a fundamental strategy for organizations to fortify their digital defenses and protect sensitive data from evolving cyber threats.
The Role of Continuous Monitoring in Ethical Hacking:
Continuous monitoring plays a pivotal role in the realm of ethical hacking, serving as a proactive and dynamic approach to cybersecurity. Ethical hackers, also known as white-hat hackers, engage in ongoing monitoring to identify and address vulnerabilities within digital systems and networks. This process is multifaceted, involving several key aspects.
One of the primary functions of continuous monitoring is real-time threat detection. Ethical hackers employ a variety of tools and techniques to scrutinize network traffic, examine system logs, and analyze security alerts in real-time. This allows them to swiftly pinpoint and investigate any suspicious or potentially malicious activities as they occur, minimizing the risk of cyber threats going undetected.
Another critical element is vulnerability assessment. Ethical hackers routinely conduct scans to identify known vulnerabilities, misconfigurations, and weaknesses within an organization's systems, applications, and network configurations. This proactive approach ensures that vulnerabilities are promptly addressed, reducing the window of opportunity for malicious actors.
Furthermore, intrusion detection is a key aspect of continuous monitoring. Ethical hackers set up intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor for unauthorized access attempts and potential security breaches. These systems generate alerts when they detect unusual or suspicious behavior, allowing for immediate investigation and response.
Additionally, log analysis is integral to continuous monitoring. Ethical hackers meticulously review logs and audit trails to identify security incidents, track the source of attacks, and understand how vulnerabilities are exploited. This analysis provides valuable insights into the nature and origin of threats, aiding in the development of effective countermeasures.
Continuous monitoring also encompasses patch management, incident response planning, threat intelligence gathering, security awareness initiatives, and regular reporting of findings and recommendations. It ensures that organizations stay compliant with relevant regulations and standards while maintaining the security and privacy of sensitive data.
In conclusion, continuous monitoring is the heartbeat of ethical hacking, facilitating the early detection and mitigation of security vulnerabilities and threats. By adopting a proactive and ongoing approach to cybersecurity, ethical hackers work in tandem with IT security teams to fortify digital defenses, respond effectively to incidents, and adapt to the ever-evolving landscape of cyber threats. This collaborative effort ensures that organizations can protect their digital assets and data against an array of security challenges.
Future Trends in Ethical Hacking
Future trends in ethical hacking point to an exciting and evolving landscape in the realm of cybersecurity. As technology advances and cyber threats become more sophisticated, ethical hackers are continually adapting to stay ahead of malicious actors. Here are some key developments and trends shaping the future of ethical hacking:
-
AI and Machine Learning Integration: Ethical hackers are increasingly using artificial intelligence (AI) and machine learning (ML) to enhance their capabilities. These technologies can automate the detection of vulnerabilities, analyze large datasets for patterns, and even predict potential cyber threats. Ethical hackers will harness AI and ML to identify and respond to threats more effectively.
-
IoT and OT Security: With the proliferation of Internet of Things (IoT) and Operational Technology (OT) devices, ethical hacking will extend its focus to these areas. Ethical hackers will specialize in assessing the security of smart devices, industrial control systems, and critical infrastructure, as these become prime targets for cyberattacks.
-
Cloud Security: As organizations migrate more of their data and operations to the cloud, ethical hackers will place greater emphasis on cloud security assessments. They will test configurations, access controls, and data protection mechanisms within cloud environments to ensure their resilience against cyber threats.
-
5G Network Vulnerabilities: The rollout of 5G networks will introduce new security challenges. Ethical hackers will explore potential vulnerabilities in the 5G infrastructure and associated technologies, ensuring the security of next-generation connectivity.
-
Zero Trust Security: The Zero Trust security model, which assumes that no one, whether inside or outside the organization, can be trusted, will gain prominence. Ethical hackers will play a key role in implementing and testing Zero Trust architectures to protect against insider threats and external breaches.
-
Biometric Security Testing: Ethical hackers will assess the security of biometric authentication methods, such as facial recognition and fingerprint scanning, to ensure their resistance to spoofing and unauthorized access attempts.
-
Quantum Computing Threats: As quantum computing advances, it poses both opportunities and challenges in the cybersecurity space. Ethical hackers will explore potential threats posed by quantum computing and develop quantum-resistant encryption techniques.
-
Blockchain Security: As blockchain technology continues to be adopted in various industries, ethical hackers will assess the security of blockchain networks and smart contracts, ensuring their integrity and resilience against attacks.
-
Bug Bounty Programs: Bug bounty programs will become more prevalent, offering ethical hackers financial incentives to discover and report vulnerabilities in organizations' systems and applications. This trend encourages collaboration between hackers and organizations to enhance security.
-
Regulatory Compliance: Ethical hackers will continue to play a crucial role in helping organizations meet evolving regulatory requirements, such as GDPR, CCPA, and other data protection laws, by conducting compliance assessments and security audits.
How to obtain Ethical Hacking certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : Ethical Hacking
Conclusion
In today's digitally interconnected world, the role of ethical hacking in modern organizations cannot be overstated. As businesses increasingly rely on digital infrastructure and data, they face a growing array of cyber threats that can jeopardize their operations, finances, and reputation. Ethical hacking, carried out by skilled professionals known as white-hat hackers, serves as a proactive defense against these threats.
Ethical hackers play a pivotal role in identifying and addressing vulnerabilities before malicious actors can exploit them. Their expertise extends to various domains, including network security, web application security, and cloud security. By simulating cyberattacks and employing the same tactics as potential adversaries, ethical hackers provide organizations with invaluable insights into their security weaknesses.
Furthermore, ethical hacking is not just a one-time endeavor but a continuous process. It involves ongoing monitoring, vulnerability assessments, and response planning to stay ahead of emerging threats. Ethical hackers collaborate closely with IT security teams, ensuring that organizations can adapt and fortify their defenses in the face of evolving cyber challenges.
In conclusion, ethical hacking is not just a service but a strategic imperative for modern organizations. It empowers businesses to protect their digital assets, customer data, and brand reputation while demonstrating a commitment to cybersecurity and responsible data management. In a world where cyber threats are ever-present, ethical hacking stands as a critical guardian of organizational integrity and security, safeguarding the future of businesses in the digital age.
Read More
In today's digital age, where data is the lifeblood of businesses and organizations, safeguarding sensitive information and digital assets has become paramount. With cyber threats constantly evolving in sophistication and scope, modern organizations face a formidable challenge in ensuring their cybersecurity defenses are robust and resilient. It is in this landscape that ethical hacking emerges as a crucial and proactive strategy for safeguarding organizations against cyberattacks.
Ethical hacking, often referred to as "white-hat" hacking, is a practice where skilled professionals employ their expertise to identify vulnerabilities, assess security measures, and test the resilience of an organization's digital infrastructure. Unlike malicious hackers who exploit weaknesses for personal gain, ethical hackers work with the explicit goal of fortifying cybersecurity defenses. In this exploration of "The Role of Ethical Hacking in Modern Organizations," we will delve into the vital functions and significance of ethical hacking in defending against cyber threats, securing sensitive data, and ensuring the continued success of businesses in an increasingly digital world.
Table of contents
-
The Ethical Hacker's Toolkit
-
Types of Ethical Hacking Services
-
The Ethical Hacker's Code of Ethics
-
Ethical Hacking for Regulatory Compliance
-
Ethical Hacking for IoT Security:
-
Challenges and Ethical Dilemmas in Ethical Hacking:
-
Collaboration Between Ethical Hackers and IT Security Teams
-
The Role of Continuous Monitoring in Ethical Hacking:
-
Future Trends in Ethical Hacking:
-
Conclusion
The Ethical Hacker's Toolkit
The ethical hacker's toolkit is a comprehensive set of specialized software and tools that enable cybersecurity professionals to simulate cyberattacks and uncover vulnerabilities within an organization's digital infrastructure. These tools range from network scanners, vulnerability assessment software, and password-cracking utilities to web application scanners and exploitation frameworks. By utilizing these tools, ethical hackers can systematically assess an organization's security posture, identify weaknesses, and help fortify defenses. These tools empower ethical hackers to probe systems, networks, and applications for vulnerabilities, ultimately assisting organizations in preemptively addressing potential security risks before malicious actors can exploit them.
In addition to the technical tools, the ethical hacker's toolkit also includes crucial skills like scripting and coding, which enable them to create custom solutions and adapt to unique security challenges. Continuous learning and staying updated on emerging threats and tools are paramount in this field, as the landscape of cybersecurity is ever-evolving. Ethical hackers are committed to maintaining the integrity of systems and data while using their toolkit responsibly and ethically to protect organizations from cyber threats.
Types of Ethical Hacking Services
-
Vulnerability Assessment:
-
Identifies weaknesses in systems, networks, and apps.
-
Prioritizes vulnerabilities based on severity.
-
-
Penetration Testing (Pen Testing):
-
Simulates real cyberattacks to test defenses.
-
Reveals how well security measures handle attacks.
-
-
Web Application Testing:
-
Focuses on securing websites and online services.
-
Checks for vulnerabilities like hacking attempts.
-
-
Wireless Network Testing:
-
Assesses Wi-Fi network security.
-
Looks for flaws that could allow unauthorized access.
-
-
Social Engineering Testing:
-
Evaluates susceptibility to tricks like phishing.
-
Educates employees on avoiding manipulation.
-
-
Mobile Application Security Testing:
-
Ensures security of mobile apps (iOS, Android).
-
Identifies vulnerabilities that could compromise data.
-
-
Cloud Security Assessment:
-
Examines security in cloud-based systems.
-
Checks settings, permissions, and access controls.
-
-
IoT Security Assessment:
-
Focuses on securing Internet of Things (IoT) devices.
-
Identifies vulnerabilities in interconnected devices.
-
-
Red Team Testing:
-
Simulates advanced cyberattacks.
-
Assesses overall security preparedness.
-
-
Incident Response Testing:
-
Helps organizations refine responses to security incidents.
-
Tests the ability to detect, mitigate, and recover from attacks.
-
The Ethical Hacker's Code of Ethics
Here are the key points of the Ethical Hacker's Code of Ethics in a simplified form:
-
Permission First: Ethical hackers must get permission before testing any computer system or network.
-
Respect Privacy: They should protect confidential information they encounter during their work.
-
No Data Damage: Their actions should not harm data, systems, or services.
-
Follow Laws: They must operate within legal boundaries and obey all relevant laws.
-
Report Vulnerabilities: Ethical hackers report any security flaws they find to the owners so they can fix them.
-
Keep Learning: They stay up-to-date with the latest cybersecurity knowledge and tools.
-
No Harmful Intent: Ethical hackers never use their skills for harm or personal gain.
-
Tools for Good: They use hacking tools only for legitimate testing purposes.
-
Education and Awareness: They often help educate others about cybersecurity and how to protect themselves.
-
Professional Integrity: Ethical hackers act with honesty, transparency, and integrity in all they do.
Ethical Hacking for Regulatory Compliance
Ethical hacking for regulatory compliance is a critical practice in today's data-driven and highly regulated business environment. With stringent regulatory standards such as GDPR, HIPAA, and PCI DSS in place, organizations are obligated to safeguard sensitive data and maintain robust cybersecurity measures. Ethical hacking serves as a proactive approach to help organizations meet these regulatory requirements effectively. By simulating real cyberattacks and identifying vulnerabilities before malicious actors can exploit them, ethical hackers play a pivotal role in assessing an organization's security infrastructure. Furthermore, ethical hacking engagements can be tailored to specific regulatory needs, focusing on the precise compliance requirements of an organization's industry and region. Through regular audits, meticulous documentation, and proactive risk mitigation, ethical hacking not only helps organizations maintain compliance but also enhances their cybersecurity posture and readiness for regulatory audits, ultimately ensuring the protection of sensitive data and the preservation of reputation and trust.
Ethical Hacking for IoT Security
Ethical hacking for IoT (Internet of Things) security involves a systematic and proactive approach to identifying and addressing vulnerabilities within IoT ecosystems to ensure their resilience against cyber threats. IoT devices, which include everything from smart thermostats and wearable devices to industrial sensors and autonomous vehicles, have become an integral part of modern life and business operations. However, their widespread adoption has also introduced new security risks due to their interconnected nature and diverse applications.
Ethical hackers, also known as white-hat hackers, use their skills and knowledge to simulate potential cyberattacks on IoT devices, networks, and platforms. Their primary objectives are to:
-
Identify Vulnerabilities: Ethical hackers employ various tools and techniques to identify vulnerabilities in IoT devices and the infrastructure supporting them. This may include analyzing device firmware, communication protocols, and cloud services.
-
Assess Security Controls: They evaluate the effectiveness of security controls implemented in IoT ecosystems. This involves examining access controls, encryption mechanisms, and authentication processes to ensure they are robust and resilient.
-
Test for Weaknesses: Ethical hackers conduct penetration testing to determine if unauthorized access, data breaches, or device manipulation is possible. They assess the IoT system's susceptibility to common cyber threats, such as malware, denial-of-service attacks, and physical tampering.
-
Provide Recommendations: Based on their findings, ethical hackers offer recommendations and solutions to mitigate identified vulnerabilities and enhance the overall security posture of IoT environments. This may include applying patches, strengthening access controls, or improving encryption methods.
-
Promote Security Awareness: Ethical hackers also play a role in educating IoT device manufacturers, developers, and users about best practices for security. They raise awareness about potential risks and the importance of regular updates and secure configurations.
-
Compliance and Standards: Ethical hacking for IoT security helps organizations align with industry-specific regulations and standards, ensuring compliance with data protection and privacy laws.
By conducting ethical hacking assessments on IoT systems, organizations can proactively address security weaknesses, minimize the risk of cyberattacks, protect sensitive data, and maintain the reliability of their IoT devices and networks. As the IoT landscape continues to evolve, ethical hacking remains an essential strategy for safeguarding these interconnected technologies and enhancing their resilience against emerging threats.
Challenges and Ethical Dilemmas in Ethical Hacking
-
Legal Boundaries:
-
Ethical hackers must stay within the law.
-
Distinguishing ethical hacking from illegal hacking can be tricky.
-
-
Authorization and Permission:
-
Getting clear permission to hack is crucial.
-
Obtaining authorization, especially in large organizations, can be challenging.
-
-
User Privacy and Data Protection:
-
Ethical hackers may encounter sensitive data during assessments.
-
Balancing the need to reveal vulnerabilities with protecting user privacy is a challenge.
-
-
Third-Party Systems:
-
Ethical hackers often assess external systems.
-
The ethical challenge arises when vulnerabilities are found in systems the organization doesn't control.
-
-
Full Disclosure vs. Responsible Disclosure:
-
Deciding whether to disclose vulnerabilities publicly (full disclosure) or privately to the organization (responsible disclosure) is a complex ethical choice.
-
It involves considering the impact on security and public awareness.
-
-
Technical Proficiency and Adaptation:
-
Staying technically proficient and updated is an ongoing challenge.
-
Ethical hackers must adapt to evolving cyber threats and technologies.
-
-
Neutrality and Objectivity:
-
Remaining neutral and objective during assessments is essential.
-
Personal biases or judgments can compromise the assessment's integrity.
-
Collaboration Between Ethical Hackers and IT Security Teams
Collaboration between ethical hackers and IT security teams is an indispensable partnership in the realm of cybersecurity. Ethical hackers, armed with their expertise and hacking skills, serve as the first line of defense by proactively identifying vulnerabilities within an organization's systems, networks, and applications. They conduct penetration testing and vulnerability assessments to simulate real-world cyberattacks, pinpoint weaknesses, and report their findings. This critical information forms the foundation upon which IT security teams build their defensive strategies. IT security professionals then take the insights provided by ethical hackers and apply them to patch vulnerabilities, implement stronger security measures, and enhance overall cybersecurity posture. This synergy ensures a proactive and dynamic approach to cybersecurity, enabling organizations to stay one step ahead of malicious actors and respond effectively to emerging threats. Collaboration between ethical hackers and IT security teams is not merely a partnership; it is a fundamental strategy for organizations to fortify their digital defenses and protect sensitive data from evolving cyber threats.
The Role of Continuous Monitoring in Ethical Hacking:
Continuous monitoring plays a pivotal role in the realm of ethical hacking, serving as a proactive and dynamic approach to cybersecurity. Ethical hackers, also known as white-hat hackers, engage in ongoing monitoring to identify and address vulnerabilities within digital systems and networks. This process is multifaceted, involving several key aspects.
One of the primary functions of continuous monitoring is real-time threat detection. Ethical hackers employ a variety of tools and techniques to scrutinize network traffic, examine system logs, and analyze security alerts in real-time. This allows them to swiftly pinpoint and investigate any suspicious or potentially malicious activities as they occur, minimizing the risk of cyber threats going undetected.
Another critical element is vulnerability assessment. Ethical hackers routinely conduct scans to identify known vulnerabilities, misconfigurations, and weaknesses within an organization's systems, applications, and network configurations. This proactive approach ensures that vulnerabilities are promptly addressed, reducing the window of opportunity for malicious actors.
Furthermore, intrusion detection is a key aspect of continuous monitoring. Ethical hackers set up intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor for unauthorized access attempts and potential security breaches. These systems generate alerts when they detect unusual or suspicious behavior, allowing for immediate investigation and response.
Additionally, log analysis is integral to continuous monitoring. Ethical hackers meticulously review logs and audit trails to identify security incidents, track the source of attacks, and understand how vulnerabilities are exploited. This analysis provides valuable insights into the nature and origin of threats, aiding in the development of effective countermeasures.
Continuous monitoring also encompasses patch management, incident response planning, threat intelligence gathering, security awareness initiatives, and regular reporting of findings and recommendations. It ensures that organizations stay compliant with relevant regulations and standards while maintaining the security and privacy of sensitive data.
In conclusion, continuous monitoring is the heartbeat of ethical hacking, facilitating the early detection and mitigation of security vulnerabilities and threats. By adopting a proactive and ongoing approach to cybersecurity, ethical hackers work in tandem with IT security teams to fortify digital defenses, respond effectively to incidents, and adapt to the ever-evolving landscape of cyber threats. This collaborative effort ensures that organizations can protect their digital assets and data against an array of security challenges.
Future Trends in Ethical Hacking
Future trends in ethical hacking point to an exciting and evolving landscape in the realm of cybersecurity. As technology advances and cyber threats become more sophisticated, ethical hackers are continually adapting to stay ahead of malicious actors. Here are some key developments and trends shaping the future of ethical hacking:
-
AI and Machine Learning Integration: Ethical hackers are increasingly using artificial intelligence (AI) and machine learning (ML) to enhance their capabilities. These technologies can automate the detection of vulnerabilities, analyze large datasets for patterns, and even predict potential cyber threats. Ethical hackers will harness AI and ML to identify and respond to threats more effectively.
-
IoT and OT Security: With the proliferation of Internet of Things (IoT) and Operational Technology (OT) devices, ethical hacking will extend its focus to these areas. Ethical hackers will specialize in assessing the security of smart devices, industrial control systems, and critical infrastructure, as these become prime targets for cyberattacks.
-
Cloud Security: As organizations migrate more of their data and operations to the cloud, ethical hackers will place greater emphasis on cloud security assessments. They will test configurations, access controls, and data protection mechanisms within cloud environments to ensure their resilience against cyber threats.
-
5G Network Vulnerabilities: The rollout of 5G networks will introduce new security challenges. Ethical hackers will explore potential vulnerabilities in the 5G infrastructure and associated technologies, ensuring the security of next-generation connectivity.
-
Zero Trust Security: The Zero Trust security model, which assumes that no one, whether inside or outside the organization, can be trusted, will gain prominence. Ethical hackers will play a key role in implementing and testing Zero Trust architectures to protect against insider threats and external breaches.
-
Biometric Security Testing: Ethical hackers will assess the security of biometric authentication methods, such as facial recognition and fingerprint scanning, to ensure their resistance to spoofing and unauthorized access attempts.
-
Quantum Computing Threats: As quantum computing advances, it poses both opportunities and challenges in the cybersecurity space. Ethical hackers will explore potential threats posed by quantum computing and develop quantum-resistant encryption techniques.
-
Blockchain Security: As blockchain technology continues to be adopted in various industries, ethical hackers will assess the security of blockchain networks and smart contracts, ensuring their integrity and resilience against attacks.
-
Bug Bounty Programs: Bug bounty programs will become more prevalent, offering ethical hackers financial incentives to discover and report vulnerabilities in organizations' systems and applications. This trend encourages collaboration between hackers and organizations to enhance security.
-
Regulatory Compliance: Ethical hackers will continue to play a crucial role in helping organizations meet evolving regulatory requirements, such as GDPR, CCPA, and other data protection laws, by conducting compliance assessments and security audits.
How to obtain Ethical Hacking certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : Ethical Hacking
Conclusion
In today's digitally interconnected world, the role of ethical hacking in modern organizations cannot be overstated. As businesses increasingly rely on digital infrastructure and data, they face a growing array of cyber threats that can jeopardize their operations, finances, and reputation. Ethical hacking, carried out by skilled professionals known as white-hat hackers, serves as a proactive defense against these threats.
Ethical hackers play a pivotal role in identifying and addressing vulnerabilities before malicious actors can exploit them. Their expertise extends to various domains, including network security, web application security, and cloud security. By simulating cyberattacks and employing the same tactics as potential adversaries, ethical hackers provide organizations with invaluable insights into their security weaknesses.
Furthermore, ethical hacking is not just a one-time endeavor but a continuous process. It involves ongoing monitoring, vulnerability assessments, and response planning to stay ahead of emerging threats. Ethical hackers collaborate closely with IT security teams, ensuring that organizations can adapt and fortify their defenses in the face of evolving cyber challenges.
In conclusion, ethical hacking is not just a service but a strategic imperative for modern organizations. It empowers businesses to protect their digital assets, customer data, and brand reputation while demonstrating a commitment to cybersecurity and responsible data management. In a world where cyber threats are ever-present, ethical hacking stands as a critical guardian of organizational integrity and security, safeguarding the future of businesses in the digital age.
COBIT® 5 and IT Risk Management: A Powerful Combination
In today's ever-evolving digital landscape, organizations face a multitude of challenges when it comes to managing and mitigating IT risks. The rapid pace of technological advancements, the increasing complexity of IT environments, and the relentless onslaught of cyber threats have made effective risk management an imperative for businesses of all sizes and industries.
This blog post explores a powerful combination that has emerged to tackle these challenges head-on: COBIT® 5 and IT risk management. COBIT® 5, a globally recognized framework for IT governance and management, provides organizations with a structured approach to optimizing IT processes and aligning them with business goals. When integrated with robust IT risk management practices, COBIT® 5 becomes a formidable tool in helping organizations identify, assess, mitigate, and monitor IT risks effectively.
In this post, we will delve into the core concepts of COBIT® 5, emphasizing its principles and guidelines that support IT risk management. We will also discuss the benefits of combining COBIT® 5 with IT risk management, including improved visibility, enhanced decision-making, and better compliance. Additionally, we'll provide practical insights on how organizations can implement COBIT® 5 in their risk management processes and showcase real-world examples of its successful integration.
Table of Contents
-
Understanding COBIT® 5 in Brief
-
The Critical Role of IT Risk Management
-
COBIT® 5's Approach to IT Risk Management
-
Benefits of Integrating COBIT® 5 with IT Risk Management
-
COBIT® 5's Framework for IT Risk Management
-
Practical Implementation Steps
-
Real-world Examples
-
Challenges and Considerations
-
Conclusion
Understanding COBIT® 5 in Brief
COBIT® 5, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in effectively managing and governing their information technology (IT) processes. At its core, COBIT® 5 seeks to bridge the gap between business objectives and IT functions. It is a comprehensive framework that offers a structured approach to IT governance and management, ensuring that IT activities align with business goals and regulatory requirements.
Key Components of COBIT® 5:
COBIT® 5 is built on five fundamental principles that underpin its effectiveness. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Within the framework, a set of processes is organized into five domains: Evaluate, Direct, and Monitor (EDM), Align, Plan, and Organize (APO), Build, Acquire, and Implement (BAI), Deliver, Service, and Support (DSS), and Monitor, Evaluate, and Assess (MEA). These processes provide guidance on various aspects of IT governance and management, from strategic planning to day-to-day operations.
Benefits of COBIT® 5:
Organizations that embrace COBIT® 5 gain several notable advantages. It enhances IT governance by establishing a robust framework that ensures IT investments and actions are in harmony with business objectives and compliance requirements. COBIT® 5 also plays a vital role in risk management, offering a structured approach to identify, assess, and mitigate IT-related risks. It aids in efficient resource allocation, enabling organizations to make informed decisions regarding IT investments. Moreover, COBIT® 5 promotes transparency and accountability in IT processes, facilitating areas of improvement identification and compliance demonstration. The framework's compatibility with various industry standards and frameworks, such as ITIL and ISO/IEC 27001, enhances its appeal as a versatile tool applicable to organizations of all sizes and industries. In summary, COBIT® 5 serves as an invaluable resource for organizations aspiring to elevate their IT governance and management practices, aligning IT with business objectives and enhancing overall efficiency and effectiveness.
The Critical Role of IT Risk Management
In today's digital-centric business landscape, the critical role of IT risk management cannot be overstated. As organizations increasingly rely on technology to drive their operations, serve customers, and manage data, they become more exposed to a wide array of IT-related risks. These risks can range from cybersecurity threats and data breaches to system failures and compliance violations. Effectively managing these risks is essential for business continuity, reputation preservation, and regulatory compliance.
IT risk management is a systematic and structured approach to identifying, assessing, mitigating, and monitoring IT-related risks. Its significance lies in its ability to proactively identify potential threats and vulnerabilities, allowing organizations to take preemptive action to reduce their impact. Here are several key aspects highlighting the critical role of IT risk management:
1. Protecting Business Assets: IT systems and digital assets are vital components of modern businesses. IT risk management safeguards these assets from a wide range of threats, including cyberattacks, unauthorized access, and data loss. By protecting these assets, organizations can ensure the uninterrupted flow of operations and maintain customer trust.
2. Safeguarding Reputation: A data breach or security incident can have severe consequences for an organization's reputation. IT risk management practices, including robust cybersecurity measures and incident response plans, help minimize the risk of reputational damage by preventing or mitigating the impact of such incidents.
3. Regulatory Compliance: Many industries are subject to stringent regulations related to data protection, privacy, and security. IT risk management ensures that organizations remain in compliance with these regulations, avoiding costly fines and legal repercussions.
4. Business Continuity: Effective risk management includes disaster recovery and business continuity planning. This ensures that in the event of IT disruptions, whether due to natural disasters or technical failures, organizations can continue to operate or quickly recover their operations.
5. Cost Reduction: Well-planned IT risk management can lead to cost savings. By identifying and mitigating risks, organizations can reduce the financial impact of potential incidents and allocate resources more efficiently.
6. Decision Support: IT risk assessments provide valuable insights into the vulnerabilities and threats an organization faces. This information aids in informed decision-making, such as prioritizing investments in security measures and risk mitigation strategies.
7. Competitive Advantage: Organizations that can demonstrate effective IT risk management practices often gain a competitive edge. Customers and partners are increasingly concerned about data security and compliance, making sound risk management a selling point.
COBIT® 5's Approach to IT Risk Management
COBIT® 5, the globally recognized framework for IT governance and management, offers a structured and effective approach to managing IT-related risks within organizations. Its approach can be summarized in a few key steps, making it accessible for organizations of various sizes and industries:
-
Understand Business Goals: First, know your organization's business objectives well. IT should support these goals.
-
Set Risk Tolerance: Decide how much risk you're willing to accept to achieve your business goals, like setting a limit on a game.
-
Identify IT Risks: Spot potential IT risks, such as cyber threats or software problems, just like noticing road obstacles.
-
Assess Risks: Estimate how big each risk is and how likely it is to happen, similar to evaluating the size of a road pothole and its likelihood of causing damage.
-
Respond to Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like getting insurance), or accept it, just as you choose to fix a pothole or take a different route.
-
Monitor Continuously: Keep an eye on risks all the time, like watching the road while driving, and adjust your plans if new risks appear.
-
Communicate Clearly: Make sure everyone in your organization understands the risks and what you're doing to manage them.
-
Report and Follow Rules: Share information about how you're handling risks with key people and stay in line with laws and standards.
-
Learn and Improve: Keep learning from your experiences with risk management to get better at it over time, like becoming a better driver after each trip.
In simple terms, COBIT® 5's approach to IT risk management is like planning a safe journey. You know where you want to go (business goals), identify potential roadblocks (IT risks), set limits on how risky you're willing to be, and use strategies to navigate safely. This helps organizations protect their IT systems and make smart choices in the digital world.
Benefits of Integrating COBIT® 5 with IT Risk Management
Integrating COBIT® 5, a comprehensive framework for IT governance and management, with IT risk management brings several significant benefits to organizations. This integration creates a powerful synergy that enhances an organization's ability to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key advantages:
-
Business Alignment: Aligns IT activities with what the organization wants to achieve, ensuring that IT supports business goals.
-
Proactive Risk Management: Helps spot and address IT risks before they become big problems.
-
Informed Decision-Making: Provides insights for smart decisions about IT investments and how to deal with risks.
-
Regulatory Compliance: Makes it easier to follow rules and regulations related to IT risk management.
-
Efficient Resource Use: Helps allocate resources wisely by focusing on the most important risks.
-
Clear Communication: Makes it easy to explain IT risks and how they're being managed to everyone in the organization.
-
Adaptation to Change: Keeps an eye on risks and adjusts strategies as needed to stay safe in a changing world.
-
Easier Audits: Simplifies the process of checking that risk management practices are working correctly.
-
Competitive Advantage: Organizations that do this well look better to customers and partners who care about data security and following the rules.
COBIT® 5's Framework for IT Risk Management
COBIT® 5 provides a structured and comprehensive framework for IT risk management within organizations. This framework offers a clear path to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key components and steps in COBIT® 5's framework for IT risk management:
-
Identify Risks: Find potential IT risks that could harm your organization, like cyber threats or data problems.
-
Assess Risks: Figure out how big each risk is and how likely it is to happen, so you know which ones need attention.
-
Manage Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like insurance), or accept it.
-
Keep an Eye Out: Continuously watch for changes in risks and adjust your plans accordingly.
-
Report Clearly: Share what you're doing about risks with everyone in your organization and make sure to document everything.
-
Follow the Rules: Make sure your risk management follows the laws and rules that apply to your business.
-
Learn and Get Better: Keep learning from your experiences with risk management to do it even better next time.
-
Integrate with Everything: Make sure risk management is part of all your IT decisions and fits with your overall goals.
In simple terms, COBIT® 5's framework for IT risk management is like a clear roadmap to help organizations handle IT risks wisely. It guides you in spotting risks, figuring out how to deal with them, and making sure you're following the rules and improving over time. This helps keep your organization safe and successful in the digital world.
Practical Implementation Steps
Implementing COBIT® 5's IT risk management framework involves practical steps to ensure a systematic and effective approach to managing IT-related risks within your organization. Here are the key implementation steps:
-
Assign Responsibilities: Appoint people to handle risk management tasks and make sure senior leaders support the process.
-
Set Risk Limits: Decide how much risk your organization can accept for different types of IT activities.
-
Spot Risks: Identify potential IT risks using your team's knowledge and available data.
-
Check Risks: Evaluate each risk to see how big it is and how likely it is to happen, and then prioritize them.
-
Make Risk Plans: Create plans to deal with the most important risks, deciding whether to avoid them, reduce their impact, transfer them (like buying insurance), or accept them.
-
Integrate with Everything: Make sure risk management is part of your regular IT processes and document it.
-
Keep Watch: Set up a system to keep an eye on how risks change and how your plans are working.
-
Tell Everyone: Regularly tell your team and leaders about the risks and what you're doing to manage them.
-
Keep Records: Write down everything you do related to risk management.
-
Train and Learn: Teach your team about risk management and learn from your experiences to get better over time.
-
Follow the Rules: Make sure your risk management meets the laws and rules that apply to your business.
-
Get Help If Needed: Consider getting outside experts to help or assess your risk management.
In simple terms, these steps help organizations manage IT risks effectively, aligning with their goals and complying with rules while learning and improving along the way.
Real-world Examples
Here are some real-world examples of organizations that have successfully implemented COBIT® 5's IT risk management framework:
-
JPMorgan Chase & Co.: JPMorgan Chase, one of the world's largest financial institutions, utilizes COBIT® 5's IT risk management framework to ensure the security and reliability of its IT systems. The framework helps them identify and assess risks associated with their extensive digital operations, including online banking and financial services. It enables them to proactively address cybersecurity threats, data breaches, and regulatory compliance challenges.
-
The World Bank: The World Bank, a global financial institution, leverages COBIT® 5 to manage IT risks across its diverse operations. They use the framework to identify and assess risks related to the implementation of technology in development projects. This helps them mitigate potential project delays, budget overruns, and data security issues.
-
Dubai Electricity and Water Authority (DEWA): DEWA, the utility provider for Dubai, uses COBIT® 5 to enhance IT risk management in the context of critical infrastructure. They apply the framework to identify and address risks associated with their energy and water supply systems. This ensures the reliability and resilience of their services, even in the face of IT-related challenges.
-
PwC (PricewaterhouseCoopers): As a leading global professional services firm, PwC employs COBIT® 5 for IT risk management to help their clients across various industries. They assist organizations in identifying and managing IT risks to enhance cybersecurity, regulatory compliance, and overall operational efficiency.
-
Nestlé: Nestlé, the multinational food and beverage company, uses COBIT® 5's IT risk management framework to ensure the integrity of its global IT systems. This includes managing risks related to data privacy, supply chain, and production systems. The framework helps Nestlé maintain the trust of its customers and regulators while ensuring the smooth operation of its business.
These real-world examples demonstrate how organizations across different sectors, including finance, development, utilities, and professional services, leverage COBIT® 5's IT risk management framework to enhance their IT governance and protect their operations from a wide range of IT-related risks. This illustrates the versatility and effectiveness of COBIT® 5 in managing IT risks in various contexts.
Challenges and Considerations
Implementing COBIT® 5's IT risk management framework comes with a set of challenges and considerations that organizations should carefully address. One significant challenge is resource allocation, involving finding the right personnel and financial investments for risk management initiatives. Changing the organizational culture to prioritize risk management can be a formidable hurdle, as it requires strong leadership support and effective communication to instill the importance of risk management across all levels of the organization. The complexity of modern IT environments, with their ever-evolving nature, presents another challenge, necessitating the use of advanced monitoring tools and regular risk assessments to keep up. Adhering to regulatory requirements is a critical consideration, especially as rules can change frequently, making it vital to stay informed and seek expert guidance when needed.
Safeguarding sensitive data from breaches and cyberattacks remains a constant challenge, demanding robust cybersecurity measures and well-defined incident response plans. Integrating COBIT® 5's IT risk management framework with existing IT governance processes may pose difficulties, necessitating expert guidance and a strategic approach to ensure seamless integration. Building and maintaining the necessary skills and knowledge within the organization for effective risk management requires investment in training and development programs. Overcoming resistance to change and managing organizational change effectively is essential, as implementing new risk management processes can meet with opposition. Finally, measuring the effectiveness of risk management efforts and reporting on them in a clear and meaningful way can be complex, requiring the definition of key performance indicators and metrics to evaluate success and communicate progress to stakeholders. Addressing these challenges and considerations strategically empowers organizations to protect their IT assets, align IT with business objectives, and ensure resilience in an ever-evolving digital landscape.
How to obtain the COBIT Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, COBIT® 5's IT risk management framework offers organizations a structured and comprehensive approach to navigate the complex landscape of IT-related risks. While it brings substantial benefits such as enhanced alignment with business goals, proactive risk identification, and improved decision-making, it also presents various challenges and considerations. These challenges include resource allocation, cultural change, the complexity of IT environments, regulatory compliance, data security, integration with existing processes, skills and training, change management, and effective measurement and reporting.
Despite these challenges, organizations that commit to implementing COBIT® 5's framework stand to gain in terms of better IT risk management, alignment with regulatory requirements, and enhanced data security. It empowers organizations to proactively identify and address risks, ultimately safeguarding their IT assets and ensuring their resilience in an ever-evolving digital landscape. Therefore, while the road to effective IT risk management may be challenging, the destination of a secure and well-aligned IT environment is well worth the journey.
Read More
In today's ever-evolving digital landscape, organizations face a multitude of challenges when it comes to managing and mitigating IT risks. The rapid pace of technological advancements, the increasing complexity of IT environments, and the relentless onslaught of cyber threats have made effective risk management an imperative for businesses of all sizes and industries.
This blog post explores a powerful combination that has emerged to tackle these challenges head-on: COBIT® 5 and IT risk management. COBIT® 5, a globally recognized framework for IT governance and management, provides organizations with a structured approach to optimizing IT processes and aligning them with business goals. When integrated with robust IT risk management practices, COBIT® 5 becomes a formidable tool in helping organizations identify, assess, mitigate, and monitor IT risks effectively.
In this post, we will delve into the core concepts of COBIT® 5, emphasizing its principles and guidelines that support IT risk management. We will also discuss the benefits of combining COBIT® 5 with IT risk management, including improved visibility, enhanced decision-making, and better compliance. Additionally, we'll provide practical insights on how organizations can implement COBIT® 5 in their risk management processes and showcase real-world examples of its successful integration.
Table of Contents
-
Understanding COBIT® 5 in Brief
-
The Critical Role of IT Risk Management
-
COBIT® 5's Approach to IT Risk Management
-
Benefits of Integrating COBIT® 5 with IT Risk Management
-
COBIT® 5's Framework for IT Risk Management
-
Practical Implementation Steps
-
Real-world Examples
-
Challenges and Considerations
-
Conclusion
Understanding COBIT® 5 in Brief
COBIT® 5, which stands for Control Objectives for Information and Related Technologies, is a globally recognized framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in effectively managing and governing their information technology (IT) processes. At its core, COBIT® 5 seeks to bridge the gap between business objectives and IT functions. It is a comprehensive framework that offers a structured approach to IT governance and management, ensuring that IT activities align with business goals and regulatory requirements.
Key Components of COBIT® 5:
COBIT® 5 is built on five fundamental principles that underpin its effectiveness. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Within the framework, a set of processes is organized into five domains: Evaluate, Direct, and Monitor (EDM), Align, Plan, and Organize (APO), Build, Acquire, and Implement (BAI), Deliver, Service, and Support (DSS), and Monitor, Evaluate, and Assess (MEA). These processes provide guidance on various aspects of IT governance and management, from strategic planning to day-to-day operations.
Benefits of COBIT® 5:
Organizations that embrace COBIT® 5 gain several notable advantages. It enhances IT governance by establishing a robust framework that ensures IT investments and actions are in harmony with business objectives and compliance requirements. COBIT® 5 also plays a vital role in risk management, offering a structured approach to identify, assess, and mitigate IT-related risks. It aids in efficient resource allocation, enabling organizations to make informed decisions regarding IT investments. Moreover, COBIT® 5 promotes transparency and accountability in IT processes, facilitating areas of improvement identification and compliance demonstration. The framework's compatibility with various industry standards and frameworks, such as ITIL and ISO/IEC 27001, enhances its appeal as a versatile tool applicable to organizations of all sizes and industries. In summary, COBIT® 5 serves as an invaluable resource for organizations aspiring to elevate their IT governance and management practices, aligning IT with business objectives and enhancing overall efficiency and effectiveness.
The Critical Role of IT Risk Management
In today's digital-centric business landscape, the critical role of IT risk management cannot be overstated. As organizations increasingly rely on technology to drive their operations, serve customers, and manage data, they become more exposed to a wide array of IT-related risks. These risks can range from cybersecurity threats and data breaches to system failures and compliance violations. Effectively managing these risks is essential for business continuity, reputation preservation, and regulatory compliance.
IT risk management is a systematic and structured approach to identifying, assessing, mitigating, and monitoring IT-related risks. Its significance lies in its ability to proactively identify potential threats and vulnerabilities, allowing organizations to take preemptive action to reduce their impact. Here are several key aspects highlighting the critical role of IT risk management:
1. Protecting Business Assets: IT systems and digital assets are vital components of modern businesses. IT risk management safeguards these assets from a wide range of threats, including cyberattacks, unauthorized access, and data loss. By protecting these assets, organizations can ensure the uninterrupted flow of operations and maintain customer trust.
2. Safeguarding Reputation: A data breach or security incident can have severe consequences for an organization's reputation. IT risk management practices, including robust cybersecurity measures and incident response plans, help minimize the risk of reputational damage by preventing or mitigating the impact of such incidents.
3. Regulatory Compliance: Many industries are subject to stringent regulations related to data protection, privacy, and security. IT risk management ensures that organizations remain in compliance with these regulations, avoiding costly fines and legal repercussions.
4. Business Continuity: Effective risk management includes disaster recovery and business continuity planning. This ensures that in the event of IT disruptions, whether due to natural disasters or technical failures, organizations can continue to operate or quickly recover their operations.
5. Cost Reduction: Well-planned IT risk management can lead to cost savings. By identifying and mitigating risks, organizations can reduce the financial impact of potential incidents and allocate resources more efficiently.
6. Decision Support: IT risk assessments provide valuable insights into the vulnerabilities and threats an organization faces. This information aids in informed decision-making, such as prioritizing investments in security measures and risk mitigation strategies.
7. Competitive Advantage: Organizations that can demonstrate effective IT risk management practices often gain a competitive edge. Customers and partners are increasingly concerned about data security and compliance, making sound risk management a selling point.
COBIT® 5's Approach to IT Risk Management
COBIT® 5, the globally recognized framework for IT governance and management, offers a structured and effective approach to managing IT-related risks within organizations. Its approach can be summarized in a few key steps, making it accessible for organizations of various sizes and industries:
-
Understand Business Goals: First, know your organization's business objectives well. IT should support these goals.
-
Set Risk Tolerance: Decide how much risk you're willing to accept to achieve your business goals, like setting a limit on a game.
-
Identify IT Risks: Spot potential IT risks, such as cyber threats or software problems, just like noticing road obstacles.
-
Assess Risks: Estimate how big each risk is and how likely it is to happen, similar to evaluating the size of a road pothole and its likelihood of causing damage.
-
Respond to Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like getting insurance), or accept it, just as you choose to fix a pothole or take a different route.
-
Monitor Continuously: Keep an eye on risks all the time, like watching the road while driving, and adjust your plans if new risks appear.
-
Communicate Clearly: Make sure everyone in your organization understands the risks and what you're doing to manage them.
-
Report and Follow Rules: Share information about how you're handling risks with key people and stay in line with laws and standards.
-
Learn and Improve: Keep learning from your experiences with risk management to get better at it over time, like becoming a better driver after each trip.
In simple terms, COBIT® 5's approach to IT risk management is like planning a safe journey. You know where you want to go (business goals), identify potential roadblocks (IT risks), set limits on how risky you're willing to be, and use strategies to navigate safely. This helps organizations protect their IT systems and make smart choices in the digital world.
Benefits of Integrating COBIT® 5 with IT Risk Management
Integrating COBIT® 5, a comprehensive framework for IT governance and management, with IT risk management brings several significant benefits to organizations. This integration creates a powerful synergy that enhances an organization's ability to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key advantages:
-
Business Alignment: Aligns IT activities with what the organization wants to achieve, ensuring that IT supports business goals.
-
Proactive Risk Management: Helps spot and address IT risks before they become big problems.
-
Informed Decision-Making: Provides insights for smart decisions about IT investments and how to deal with risks.
-
Regulatory Compliance: Makes it easier to follow rules and regulations related to IT risk management.
-
Efficient Resource Use: Helps allocate resources wisely by focusing on the most important risks.
-
Clear Communication: Makes it easy to explain IT risks and how they're being managed to everyone in the organization.
-
Adaptation to Change: Keeps an eye on risks and adjusts strategies as needed to stay safe in a changing world.
-
Easier Audits: Simplifies the process of checking that risk management practices are working correctly.
-
Competitive Advantage: Organizations that do this well look better to customers and partners who care about data security and following the rules.
COBIT® 5's Framework for IT Risk Management
COBIT® 5 provides a structured and comprehensive framework for IT risk management within organizations. This framework offers a clear path to identify, assess, mitigate, and monitor IT-related risks effectively. Here are the key components and steps in COBIT® 5's framework for IT risk management:
-
Identify Risks: Find potential IT risks that could harm your organization, like cyber threats or data problems.
-
Assess Risks: Figure out how big each risk is and how likely it is to happen, so you know which ones need attention.
-
Manage Risks: Decide what to do about each risk—avoid it, lessen its impact, transfer it (like insurance), or accept it.
-
Keep an Eye Out: Continuously watch for changes in risks and adjust your plans accordingly.
-
Report Clearly: Share what you're doing about risks with everyone in your organization and make sure to document everything.
-
Follow the Rules: Make sure your risk management follows the laws and rules that apply to your business.
-
Learn and Get Better: Keep learning from your experiences with risk management to do it even better next time.
-
Integrate with Everything: Make sure risk management is part of all your IT decisions and fits with your overall goals.
In simple terms, COBIT® 5's framework for IT risk management is like a clear roadmap to help organizations handle IT risks wisely. It guides you in spotting risks, figuring out how to deal with them, and making sure you're following the rules and improving over time. This helps keep your organization safe and successful in the digital world.
Practical Implementation Steps
Implementing COBIT® 5's IT risk management framework involves practical steps to ensure a systematic and effective approach to managing IT-related risks within your organization. Here are the key implementation steps:
-
Assign Responsibilities: Appoint people to handle risk management tasks and make sure senior leaders support the process.
-
Set Risk Limits: Decide how much risk your organization can accept for different types of IT activities.
-
Spot Risks: Identify potential IT risks using your team's knowledge and available data.
-
Check Risks: Evaluate each risk to see how big it is and how likely it is to happen, and then prioritize them.
-
Make Risk Plans: Create plans to deal with the most important risks, deciding whether to avoid them, reduce their impact, transfer them (like buying insurance), or accept them.
-
Integrate with Everything: Make sure risk management is part of your regular IT processes and document it.
-
Keep Watch: Set up a system to keep an eye on how risks change and how your plans are working.
-
Tell Everyone: Regularly tell your team and leaders about the risks and what you're doing to manage them.
-
Keep Records: Write down everything you do related to risk management.
-
Train and Learn: Teach your team about risk management and learn from your experiences to get better over time.
-
Follow the Rules: Make sure your risk management meets the laws and rules that apply to your business.
-
Get Help If Needed: Consider getting outside experts to help or assess your risk management.
In simple terms, these steps help organizations manage IT risks effectively, aligning with their goals and complying with rules while learning and improving along the way.
Real-world Examples
Here are some real-world examples of organizations that have successfully implemented COBIT® 5's IT risk management framework:
-
JPMorgan Chase & Co.: JPMorgan Chase, one of the world's largest financial institutions, utilizes COBIT® 5's IT risk management framework to ensure the security and reliability of its IT systems. The framework helps them identify and assess risks associated with their extensive digital operations, including online banking and financial services. It enables them to proactively address cybersecurity threats, data breaches, and regulatory compliance challenges.
-
The World Bank: The World Bank, a global financial institution, leverages COBIT® 5 to manage IT risks across its diverse operations. They use the framework to identify and assess risks related to the implementation of technology in development projects. This helps them mitigate potential project delays, budget overruns, and data security issues.
-
Dubai Electricity and Water Authority (DEWA): DEWA, the utility provider for Dubai, uses COBIT® 5 to enhance IT risk management in the context of critical infrastructure. They apply the framework to identify and address risks associated with their energy and water supply systems. This ensures the reliability and resilience of their services, even in the face of IT-related challenges.
-
PwC (PricewaterhouseCoopers): As a leading global professional services firm, PwC employs COBIT® 5 for IT risk management to help their clients across various industries. They assist organizations in identifying and managing IT risks to enhance cybersecurity, regulatory compliance, and overall operational efficiency.
-
Nestlé: Nestlé, the multinational food and beverage company, uses COBIT® 5's IT risk management framework to ensure the integrity of its global IT systems. This includes managing risks related to data privacy, supply chain, and production systems. The framework helps Nestlé maintain the trust of its customers and regulators while ensuring the smooth operation of its business.
These real-world examples demonstrate how organizations across different sectors, including finance, development, utilities, and professional services, leverage COBIT® 5's IT risk management framework to enhance their IT governance and protect their operations from a wide range of IT-related risks. This illustrates the versatility and effectiveness of COBIT® 5 in managing IT risks in various contexts.
Challenges and Considerations
Implementing COBIT® 5's IT risk management framework comes with a set of challenges and considerations that organizations should carefully address. One significant challenge is resource allocation, involving finding the right personnel and financial investments for risk management initiatives. Changing the organizational culture to prioritize risk management can be a formidable hurdle, as it requires strong leadership support and effective communication to instill the importance of risk management across all levels of the organization. The complexity of modern IT environments, with their ever-evolving nature, presents another challenge, necessitating the use of advanced monitoring tools and regular risk assessments to keep up. Adhering to regulatory requirements is a critical consideration, especially as rules can change frequently, making it vital to stay informed and seek expert guidance when needed.
Safeguarding sensitive data from breaches and cyberattacks remains a constant challenge, demanding robust cybersecurity measures and well-defined incident response plans. Integrating COBIT® 5's IT risk management framework with existing IT governance processes may pose difficulties, necessitating expert guidance and a strategic approach to ensure seamless integration. Building and maintaining the necessary skills and knowledge within the organization for effective risk management requires investment in training and development programs. Overcoming resistance to change and managing organizational change effectively is essential, as implementing new risk management processes can meet with opposition. Finally, measuring the effectiveness of risk management efforts and reporting on them in a clear and meaningful way can be complex, requiring the definition of key performance indicators and metrics to evaluate success and communicate progress to stakeholders. Addressing these challenges and considerations strategically empowers organizations to protect their IT assets, align IT with business objectives, and ensure resilience in an ever-evolving digital landscape.
How to obtain the COBIT Foundation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, COBIT® 5's IT risk management framework offers organizations a structured and comprehensive approach to navigate the complex landscape of IT-related risks. While it brings substantial benefits such as enhanced alignment with business goals, proactive risk identification, and improved decision-making, it also presents various challenges and considerations. These challenges include resource allocation, cultural change, the complexity of IT environments, regulatory compliance, data security, integration with existing processes, skills and training, change management, and effective measurement and reporting.
Despite these challenges, organizations that commit to implementing COBIT® 5's framework stand to gain in terms of better IT risk management, alignment with regulatory requirements, and enhanced data security. It empowers organizations to proactively identify and address risks, ultimately safeguarding their IT assets and ensuring their resilience in an ever-evolving digital landscape. Therefore, while the road to effective IT risk management may be challenging, the destination of a secure and well-aligned IT environment is well worth the journey.
Advantages and Disadvantages of Cloud Computing
In today's digitally driven world, cloud computing has emerged as a technological force that is reshaping the way individuals and businesses harness the power of technology. The cloud, often referred to as the "internet of everything," offers a virtual space where data, applications, and services can be stored and accessed remotely. Its adoption has skyrocketed, promising unparalleled convenience, scalability, and cost-efficiency. However, like any technological marvel, cloud computing is not without its complexities and challenges. In this blog post, we will embark on a journey to explore the captivating landscape of cloud computing, delving into its myriad advantages that propel innovation and growth, as well as its inherent disadvantages that necessitate vigilant navigation in this digital realm. Whether you're an IT professional seeking to harness the cloud's potential or an individual eager to understand its impact on daily life, this exploration will equip you with valuable insights into the world of cloud computing.
Table of Contents
Introduction to Cloud Computing
Types of Cloud Computing
Advantages of Cloud Computing
Disadvantages of Cloud Computing
Choose The Right Cloud Computing Program For You
The Bottom Line
FAQs
Introduction to Cloud Computing
Cloud computing, a transformative technology, has revolutionized the way we interact with digital resources. It enables the delivery of computing services and resources over the internet, eliminating the need for local infrastructure. With cloud computing, users can access on-demand computing power, storage, and software, allowing for scalability and flexibility that adapts to their needs. This technology comes in various models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), catering to different user requirements. It offers benefits such as cost efficiency, accessibility from anywhere, and high reliability, making it a cornerstone of modern digital operations. However, it also poses challenges related to security, potential downtime, and data management, necessitating careful consideration when adopting cloud solutions. In today's fast-paced and interconnected world, cloud computing plays a pivotal role in shaping the future of technology and business operations.
Types of Cloud Computing
Cloud computing encompasses various types or service models, each offering a different level of control, management, and functionality to users and organizations. The three primary types of cloud computing are:
1. Infrastructure as a Service (IaaS): Infrastructure as a Service is the foundation of cloud computing, providing users with virtualized computing resources over the internet. It offers a scalable and flexible infrastructure that includes virtual machines, storage, and networking components. Users can provision and manage these resources on-demand, allowing them to scale up or down as needed. IaaS is ideal for organizations that require full control over their virtualized infrastructure while minimizing the burden of physical hardware management. Prominent IaaS providers include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
2. Platform as a Service (PaaS): Platform as a Service is designed to simplify application development and deployment by providing a platform and tools for developers. PaaS offerings include development frameworks, databases, and application hosting environments. With PaaS, developers can focus on coding and innovation, while the underlying infrastructure and maintenance are handled by the cloud provider. This accelerates the development lifecycle and streamlines application management. PaaS is particularly beneficial for software development teams, enabling them to build, test, and deploy applications more efficiently. Examples of PaaS providers are Heroku, Google App Engine, and Microsoft Azure App Service.
3. Software as a Service (SaaS): Software as a Service delivers software applications over the internet on a subscription basis. Users access these applications through a web browser, eliminating the need for local installations and updates. SaaS solutions cover a wide range of applications, including productivity tools (e.g., Microsoft 365 and Google Workspace), customer relationship management (CRM) software (e.g., Salesforce), and collaboration tools (e.g., Zoom and Slack). SaaS is user-friendly, highly accessible, and well-suited for businesses and individuals seeking to streamline software management and reduce maintenance overhead. It offers automatic updates, data storage, and often includes collaboration features for enhanced productivity.
In addition to these primary types, there are hybrid cloud solutions that combine elements of multiple cloud models, allowing organizations to leverage both private and public clouds based on their specific needs. Understanding these various types of cloud computing is essential for organizations to choose the most suitable model for their IT requirements, whether it's infrastructure management, application development, or software accessibility.
Advantages of Cloud Computing
Cloud computing offers numerous advantages that have made it a foundational technology for businesses and individuals alike. Here are some of the key advantages:
1. Cost Efficiency:
-
Reduced Capital Expenditure: Cloud computing eliminates the need for upfront investments in hardware and infrastructure, allowing businesses to pay for resources on a pay-as-you-go basis.
-
Lower Operating Costs: Maintenance, upgrades, and energy costs associated with on-premises data centers are significantly reduced or eliminated.
2. Scalability:
-
Elastic Resources: Cloud services offer the ability to scale computing resources up or down based on demand, ensuring optimal performance during peak times without overprovisioning.
3. Accessibility:
-
Anytime, Anywhere Access: Cloud-based applications and data can be accessed from anywhere with an internet connection, enabling remote work, collaboration, and mobility.
4. Reliability and Redundancy:
-
High Uptime: Reputable cloud providers offer high availability, ensuring that applications and data are accessible almost continuously.
-
Data Redundancy: Cloud providers often replicate data across multiple data centers, safeguarding against data loss due to hardware failures or disasters.
5. Security:
-
Advanced Security Measures: Cloud providers invest heavily in security, implementing robust measures to protect data, including encryption, firewalls, and access controls.
-
Compliance: Many cloud providers offer compliance certifications, making it easier for businesses to meet regulatory requirements.
6. Automatic Updates and Maintenance:
-
Cloud providers handle software updates and maintenance tasks, ensuring that applications and infrastructure are kept up-to-date with the latest security patches and improvements.
7. Flexibility and Innovation:
-
Rapid Development: Cloud services enable developers to quickly build and deploy applications, reducing time to market for new products and features.
-
Access to Cutting-Edge Technologies: Cloud providers often offer a wide range of advanced services and technologies, such as machine learning, AI, and IoT, facilitating innovation.
8. Disaster Recovery:
-
Data Backup and Recovery: Cloud providers typically offer robust disaster recovery and backup solutions, protecting data against unforeseen events.
9. Environmental Benefits:
-
Reduced Energy Consumption: By consolidating data centers and optimizing resource usage, cloud computing can have a positive environmental impact by reducing energy consumption and carbon emissions.
10. Cost Transparency:
-
Clear Billing: Cloud providers offer transparent billing and reporting, allowing organizations to monitor and control their costs effectively.
While cloud computing offers numerous advantages, it's essential for organizations to assess their specific needs, security requirements, and budget constraints to determine the best cloud strategy for their unique circumstances.
Disadvantages of Cloud Computing
Cloud computing offers numerous advantages that have made it a foundational technology for businesses and individuals alike. Here are some of the key advantages:
1. Cost Efficiency:
-
Reduced Capital Expenditure: Cloud computing eliminates the need for upfront investments in hardware and infrastructure, allowing businesses to pay for resources on a pay-as-you-go basis.
-
Lower Operating Costs: Maintenance, upgrades, and energy costs associated with on-premises data centers are significantly reduced or eliminated.
2. Scalability:
-
Elastic Resources: Cloud services offer the ability to scale computing resources up or down based on demand, ensuring optimal performance during peak times without overprovisioning.
3. Accessibility:
-
Anytime, Anywhere Access: Cloud-based applications and data can be accessed from anywhere with an internet connection, enabling remote work, collaboration, and mobility.
4. Reliability and Redundancy:
-
High Uptime: Reputable cloud providers offer high availability, ensuring that applications and data are accessible almost continuously.
-
Data Redundancy: Cloud providers often replicate data across multiple data centers, safeguarding against data loss due to hardware failures or disasters.
5. Security:
-
Advanced Security Measures: Cloud providers invest heavily in security, implementing robust measures to protect data, including encryption, firewalls, and access controls.
-
Compliance: Many cloud providers offer compliance certifications, making it easier for businesses to meet regulatory requirements.
6. Automatic Updates and Maintenance:
-
Cloud providers handle software updates and maintenance tasks, ensuring that applications and infrastructure are kept up-to-date with the latest security patches and improvements.
7. Flexibility and Innovation:
-
Rapid Development: Cloud services enable developers to quickly build and deploy applications, reducing time to market for new products and features.
-
Access to Cutting-Edge Technologies: Cloud providers often offer a wide range of advanced services and technologies, such as machine learning, AI, and IoT, facilitating innovation.
8. Disaster Recovery:
-
Data Backup and Recovery: Cloud providers typically offer robust disaster recovery and backup solutions, protecting data against unforeseen events.
9. Environmental Benefits:
-
Reduced Energy Consumption: By consolidating data centers and optimizing resource usage, cloud computing can have a positive environmental impact by reducing energy consumption and carbon emissions.
10. Cost Transparency:
-
Clear Billing: Cloud providers offer transparent billing and reporting, allowing organizations to monitor and control their costs effectively.
Choose The Right Cloud Computing Program For You
Choosing the right cloud computing program or service depends on your specific needs and goals. Whether you're an individual looking to expand your skills or an organization seeking cloud solutions, here are steps to help you make the right choice:
1. Define Your Goals:
-
Determine why you want to use cloud computing. Are you looking to enhance your IT skills, reduce operational costs, improve scalability, or increase productivity?
2. Assess Your Skill Level:
-
If you're an individual, evaluate your current knowledge of cloud computing. Are you a beginner, intermediate, or advanced user? This will help you choose an appropriate program or training course.
3. Choose a Cloud Service Model:
-
Decide which cloud service model aligns with your objectives. Are you interested in Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS)? Understanding the differences is crucial.
4. Select a Cloud Provider:
-
If you're looking for cloud services for your organization, research and compare different cloud providers (e.g., AWS, Azure, Google Cloud) based on factors like pricing, services offered, security features, and geographic availability.
5. Explore Training and Certification:
-
For individuals, consider enrolling in cloud computing training courses or certification programs provided by recognized organizations (e.g., AWS Certified Solutions Architect, Microsoft Certified Azure Administrator).
-
Organizations should also invest in training for their IT teams to ensure efficient cloud adoption and management.
6. Determine Budget and Cost Factors:
-
Assess your budget for cloud services, including initial setup costs, ongoing expenses, and potential scalability costs. Be aware of any hidden costs, such as data transfer fees.
7. Security and Compliance:
-
If you're an organization, prioritize security and compliance requirements. Ensure that the cloud provider you choose meets your industry's regulatory standards and offers robust security features.
8. Evaluate Vendor Lock-In:
-
Consider the potential for vendor lock-in. Ensure that your chosen cloud provider allows for portability of data and applications, minimizing the risk of being tied to a single provider.
9. Plan for Data Migration:
-
If you're migrating existing applications or data to the cloud, create a migration plan that includes data backup, testing, and a rollback strategy in case of issues.
10. Monitor and Optimize:
-
After adopting cloud services, continuously monitor resource usage and costs. Use cloud management tools to optimize your resources for efficiency and cost-effectiveness.
The Bottom Line
In the ever-evolving landscape of cloud computing, the bottom line is that the right choice for you or your organization depends on your specific needs, goals, and constraints. Cloud computing offers a wide range of advantages, including cost efficiency, scalability, accessibility, and innovation, but it also comes with challenges such as downtime, security concerns, and potential vendor lock-in.
To make the best decision:
-
Define Your Objectives: Clearly outline your goals, whether they involve improving IT infrastructure, reducing costs, enhancing productivity, or acquiring new skills.
-
Assess Your Skills: If you're an individual, understand your current proficiency level in cloud computing. Are you a beginner, intermediate, or advanced user?
-
Select the Right Service Model: Choose between Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS) based on your needs.
-
Pick the Right Cloud Provider: Research and compare cloud providers, considering factors such as services offered, pricing, security, and compliance with your industry's regulations.
-
Invest in Training: Consider training and certification programs to build or enhance your cloud computing skills, or invest in training for your organization's IT teams.
-
Budget Wisely: Assess your budget for cloud services, including initial setup costs, ongoing expenses, and potential scalability costs.
-
Prioritize Security: Security is paramount, especially for organizations. Ensure your chosen cloud provider meets your security and compliance requirements.
-
Plan for Migration: If migrating data or applications, create a well-structured migration plan that addresses backup, testing, and potential rollbacks.
-
Regularly Monitor and Optimize: Continuously monitor resource usage and costs, and use management tools to optimize your cloud resources for efficiency and cost-effectiveness.
-
Seek Expert Advice: When in doubt, consult with cloud experts or consultants who can offer tailored guidance based on your unique needs.
-
Stay Flexible: Cloud technology evolves rapidly, so be prepared to adapt your cloud strategy as your needs and the technology landscape change.
Ultimately, the bottom line is that cloud computing is a dynamic and flexible solution that can be customized to meet your specific requirements. Careful planning, continuous monitoring, and strategic decision-making will help you leverage the advantages of cloud computing while mitigating potential disadvantages.
How to obtain Cloud Computing Technology Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: EXIN Cloud Computing Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
FAQs
1. What is cloud computing?
-
Cloud computing refers to the delivery of computing services (such as servers, storage, databases, networking, software, and analytics) over the internet. It allows users to access and use these resources on a pay-as-you-go or subscription basis.
2. What are the different types of cloud service models?
-
There are three primary cloud service models:
-
Infrastructure as a Service (IaaS)
-
Platform as a Service (PaaS)
-
Software as a Service (SaaS)
3. What is the difference between public, private, and hybrid clouds?
-
Public Cloud: Services are provided by third-party cloud providers and made available to the general public.
-
Private Cloud: Resources are dedicated to a single organization and may be hosted on-premises or by a third party.
-
Hybrid Cloud: Combines elements of both public and private clouds, allowing data and applications to move between them.
4. What are some advantages of cloud computing?
-
Advantages of cloud computing include cost efficiency, scalability, accessibility, reliability, security, automatic updates, and the ability to foster innovation.
5. What are some disadvantages of cloud computing?
-
Disadvantages of cloud computing include potential downtime, security concerns, limited control over infrastructure, bandwidth limitations, data transfer costs, vendor lock-in, and compliance challenges.
6. What is the shared responsibility model in cloud security?
-
The shared responsibility model outlines the division of security responsibilities between the cloud provider and the customer. The provider is responsible for securing the infrastructure, while the customer is responsible for securing their data and applications within the cloud.
7. What are some common cloud computing certifications?
-
Popular cloud computing certifications include AWS Certified Solutions Architect, Microsoft Certified Azure Administrator, Google Cloud Professional Cloud Architect, and Certified Cloud Security Professional (CCSP).
8. How do I choose the right cloud provider for my organization?
-
Choosing the right cloud provider involves considering factors like services offered, pricing, security features, compliance, data center locations, and customer support. It's essential to align your choice with your organization's specific needs and goals.
9. What is the difference between cloud computing and traditional IT infrastructure?
-
Cloud computing offers on-demand access to computing resources over the internet, while traditional IT infrastructure relies on on-premises hardware and software. Cloud computing is scalable, cost-effective, and provides greater flexibility compared to traditional IT.
10. How can I ensure data security in the cloud?
-
Ensuring data security in the cloud involves implementing strong access controls, encryption, regular security audits, compliance with industry standards, and monitoring for suspicious activities. It's essential to follow best practices for cloud security.
Read More
In today's digitally driven world, cloud computing has emerged as a technological force that is reshaping the way individuals and businesses harness the power of technology. The cloud, often referred to as the "internet of everything," offers a virtual space where data, applications, and services can be stored and accessed remotely. Its adoption has skyrocketed, promising unparalleled convenience, scalability, and cost-efficiency. However, like any technological marvel, cloud computing is not without its complexities and challenges. In this blog post, we will embark on a journey to explore the captivating landscape of cloud computing, delving into its myriad advantages that propel innovation and growth, as well as its inherent disadvantages that necessitate vigilant navigation in this digital realm. Whether you're an IT professional seeking to harness the cloud's potential or an individual eager to understand its impact on daily life, this exploration will equip you with valuable insights into the world of cloud computing.
Table of Contents
Introduction to Cloud Computing
Types of Cloud Computing
Advantages of Cloud Computing
Disadvantages of Cloud Computing
Choose The Right Cloud Computing Program For You
The Bottom Line
FAQs
Introduction to Cloud Computing
Cloud computing, a transformative technology, has revolutionized the way we interact with digital resources. It enables the delivery of computing services and resources over the internet, eliminating the need for local infrastructure. With cloud computing, users can access on-demand computing power, storage, and software, allowing for scalability and flexibility that adapts to their needs. This technology comes in various models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), catering to different user requirements. It offers benefits such as cost efficiency, accessibility from anywhere, and high reliability, making it a cornerstone of modern digital operations. However, it also poses challenges related to security, potential downtime, and data management, necessitating careful consideration when adopting cloud solutions. In today's fast-paced and interconnected world, cloud computing plays a pivotal role in shaping the future of technology and business operations.
Types of Cloud Computing
Cloud computing encompasses various types or service models, each offering a different level of control, management, and functionality to users and organizations. The three primary types of cloud computing are:
1. Infrastructure as a Service (IaaS): Infrastructure as a Service is the foundation of cloud computing, providing users with virtualized computing resources over the internet. It offers a scalable and flexible infrastructure that includes virtual machines, storage, and networking components. Users can provision and manage these resources on-demand, allowing them to scale up or down as needed. IaaS is ideal for organizations that require full control over their virtualized infrastructure while minimizing the burden of physical hardware management. Prominent IaaS providers include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
2. Platform as a Service (PaaS): Platform as a Service is designed to simplify application development and deployment by providing a platform and tools for developers. PaaS offerings include development frameworks, databases, and application hosting environments. With PaaS, developers can focus on coding and innovation, while the underlying infrastructure and maintenance are handled by the cloud provider. This accelerates the development lifecycle and streamlines application management. PaaS is particularly beneficial for software development teams, enabling them to build, test, and deploy applications more efficiently. Examples of PaaS providers are Heroku, Google App Engine, and Microsoft Azure App Service.
3. Software as a Service (SaaS): Software as a Service delivers software applications over the internet on a subscription basis. Users access these applications through a web browser, eliminating the need for local installations and updates. SaaS solutions cover a wide range of applications, including productivity tools (e.g., Microsoft 365 and Google Workspace), customer relationship management (CRM) software (e.g., Salesforce), and collaboration tools (e.g., Zoom and Slack). SaaS is user-friendly, highly accessible, and well-suited for businesses and individuals seeking to streamline software management and reduce maintenance overhead. It offers automatic updates, data storage, and often includes collaboration features for enhanced productivity.
In addition to these primary types, there are hybrid cloud solutions that combine elements of multiple cloud models, allowing organizations to leverage both private and public clouds based on their specific needs. Understanding these various types of cloud computing is essential for organizations to choose the most suitable model for their IT requirements, whether it's infrastructure management, application development, or software accessibility.
Advantages of Cloud Computing
Cloud computing offers numerous advantages that have made it a foundational technology for businesses and individuals alike. Here are some of the key advantages:
1. Cost Efficiency:
-
Reduced Capital Expenditure: Cloud computing eliminates the need for upfront investments in hardware and infrastructure, allowing businesses to pay for resources on a pay-as-you-go basis.
-
Lower Operating Costs: Maintenance, upgrades, and energy costs associated with on-premises data centers are significantly reduced or eliminated.
2. Scalability:
-
Elastic Resources: Cloud services offer the ability to scale computing resources up or down based on demand, ensuring optimal performance during peak times without overprovisioning.
3. Accessibility:
-
Anytime, Anywhere Access: Cloud-based applications and data can be accessed from anywhere with an internet connection, enabling remote work, collaboration, and mobility.
4. Reliability and Redundancy:
-
High Uptime: Reputable cloud providers offer high availability, ensuring that applications and data are accessible almost continuously.
-
Data Redundancy: Cloud providers often replicate data across multiple data centers, safeguarding against data loss due to hardware failures or disasters.
5. Security:
-
Advanced Security Measures: Cloud providers invest heavily in security, implementing robust measures to protect data, including encryption, firewalls, and access controls.
-
Compliance: Many cloud providers offer compliance certifications, making it easier for businesses to meet regulatory requirements.
6. Automatic Updates and Maintenance:
-
Cloud providers handle software updates and maintenance tasks, ensuring that applications and infrastructure are kept up-to-date with the latest security patches and improvements.
7. Flexibility and Innovation:
-
Rapid Development: Cloud services enable developers to quickly build and deploy applications, reducing time to market for new products and features.
-
Access to Cutting-Edge Technologies: Cloud providers often offer a wide range of advanced services and technologies, such as machine learning, AI, and IoT, facilitating innovation.
8. Disaster Recovery:
-
Data Backup and Recovery: Cloud providers typically offer robust disaster recovery and backup solutions, protecting data against unforeseen events.
9. Environmental Benefits:
-
Reduced Energy Consumption: By consolidating data centers and optimizing resource usage, cloud computing can have a positive environmental impact by reducing energy consumption and carbon emissions.
10. Cost Transparency:
-
Clear Billing: Cloud providers offer transparent billing and reporting, allowing organizations to monitor and control their costs effectively.
While cloud computing offers numerous advantages, it's essential for organizations to assess their specific needs, security requirements, and budget constraints to determine the best cloud strategy for their unique circumstances.
Disadvantages of Cloud Computing
Cloud computing offers numerous advantages that have made it a foundational technology for businesses and individuals alike. Here are some of the key advantages:
1. Cost Efficiency:
-
Reduced Capital Expenditure: Cloud computing eliminates the need for upfront investments in hardware and infrastructure, allowing businesses to pay for resources on a pay-as-you-go basis.
-
Lower Operating Costs: Maintenance, upgrades, and energy costs associated with on-premises data centers are significantly reduced or eliminated.
2. Scalability:
-
Elastic Resources: Cloud services offer the ability to scale computing resources up or down based on demand, ensuring optimal performance during peak times without overprovisioning.
3. Accessibility:
-
Anytime, Anywhere Access: Cloud-based applications and data can be accessed from anywhere with an internet connection, enabling remote work, collaboration, and mobility.
4. Reliability and Redundancy:
-
High Uptime: Reputable cloud providers offer high availability, ensuring that applications and data are accessible almost continuously.
-
Data Redundancy: Cloud providers often replicate data across multiple data centers, safeguarding against data loss due to hardware failures or disasters.
5. Security:
-
Advanced Security Measures: Cloud providers invest heavily in security, implementing robust measures to protect data, including encryption, firewalls, and access controls.
-
Compliance: Many cloud providers offer compliance certifications, making it easier for businesses to meet regulatory requirements.
6. Automatic Updates and Maintenance:
-
Cloud providers handle software updates and maintenance tasks, ensuring that applications and infrastructure are kept up-to-date with the latest security patches and improvements.
7. Flexibility and Innovation:
-
Rapid Development: Cloud services enable developers to quickly build and deploy applications, reducing time to market for new products and features.
-
Access to Cutting-Edge Technologies: Cloud providers often offer a wide range of advanced services and technologies, such as machine learning, AI, and IoT, facilitating innovation.
8. Disaster Recovery:
-
Data Backup and Recovery: Cloud providers typically offer robust disaster recovery and backup solutions, protecting data against unforeseen events.
9. Environmental Benefits:
-
Reduced Energy Consumption: By consolidating data centers and optimizing resource usage, cloud computing can have a positive environmental impact by reducing energy consumption and carbon emissions.
10. Cost Transparency:
-
Clear Billing: Cloud providers offer transparent billing and reporting, allowing organizations to monitor and control their costs effectively.
Choose The Right Cloud Computing Program For You
Choosing the right cloud computing program or service depends on your specific needs and goals. Whether you're an individual looking to expand your skills or an organization seeking cloud solutions, here are steps to help you make the right choice:
1. Define Your Goals:
-
Determine why you want to use cloud computing. Are you looking to enhance your IT skills, reduce operational costs, improve scalability, or increase productivity?
2. Assess Your Skill Level:
-
If you're an individual, evaluate your current knowledge of cloud computing. Are you a beginner, intermediate, or advanced user? This will help you choose an appropriate program or training course.
3. Choose a Cloud Service Model:
-
Decide which cloud service model aligns with your objectives. Are you interested in Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS)? Understanding the differences is crucial.
4. Select a Cloud Provider:
-
If you're looking for cloud services for your organization, research and compare different cloud providers (e.g., AWS, Azure, Google Cloud) based on factors like pricing, services offered, security features, and geographic availability.
5. Explore Training and Certification:
-
For individuals, consider enrolling in cloud computing training courses or certification programs provided by recognized organizations (e.g., AWS Certified Solutions Architect, Microsoft Certified Azure Administrator).
-
Organizations should also invest in training for their IT teams to ensure efficient cloud adoption and management.
6. Determine Budget and Cost Factors:
-
Assess your budget for cloud services, including initial setup costs, ongoing expenses, and potential scalability costs. Be aware of any hidden costs, such as data transfer fees.
7. Security and Compliance:
-
If you're an organization, prioritize security and compliance requirements. Ensure that the cloud provider you choose meets your industry's regulatory standards and offers robust security features.
8. Evaluate Vendor Lock-In:
-
Consider the potential for vendor lock-in. Ensure that your chosen cloud provider allows for portability of data and applications, minimizing the risk of being tied to a single provider.
9. Plan for Data Migration:
-
If you're migrating existing applications or data to the cloud, create a migration plan that includes data backup, testing, and a rollback strategy in case of issues.
10. Monitor and Optimize:
-
After adopting cloud services, continuously monitor resource usage and costs. Use cloud management tools to optimize your resources for efficiency and cost-effectiveness.
The Bottom Line
In the ever-evolving landscape of cloud computing, the bottom line is that the right choice for you or your organization depends on your specific needs, goals, and constraints. Cloud computing offers a wide range of advantages, including cost efficiency, scalability, accessibility, and innovation, but it also comes with challenges such as downtime, security concerns, and potential vendor lock-in.
To make the best decision:
-
Define Your Objectives: Clearly outline your goals, whether they involve improving IT infrastructure, reducing costs, enhancing productivity, or acquiring new skills.
-
Assess Your Skills: If you're an individual, understand your current proficiency level in cloud computing. Are you a beginner, intermediate, or advanced user?
-
Select the Right Service Model: Choose between Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS) based on your needs.
-
Pick the Right Cloud Provider: Research and compare cloud providers, considering factors such as services offered, pricing, security, and compliance with your industry's regulations.
-
Invest in Training: Consider training and certification programs to build or enhance your cloud computing skills, or invest in training for your organization's IT teams.
-
Budget Wisely: Assess your budget for cloud services, including initial setup costs, ongoing expenses, and potential scalability costs.
-
Prioritize Security: Security is paramount, especially for organizations. Ensure your chosen cloud provider meets your security and compliance requirements.
-
Plan for Migration: If migrating data or applications, create a well-structured migration plan that addresses backup, testing, and potential rollbacks.
-
Regularly Monitor and Optimize: Continuously monitor resource usage and costs, and use management tools to optimize your cloud resources for efficiency and cost-effectiveness.
-
Seek Expert Advice: When in doubt, consult with cloud experts or consultants who can offer tailored guidance based on your unique needs.
-
Stay Flexible: Cloud technology evolves rapidly, so be prepared to adapt your cloud strategy as your needs and the technology landscape change.
Ultimately, the bottom line is that cloud computing is a dynamic and flexible solution that can be customized to meet your specific requirements. Careful planning, continuous monitoring, and strategic decision-making will help you leverage the advantages of cloud computing while mitigating potential disadvantages.
How to obtain Cloud Computing Technology Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: EXIN Cloud Computing Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
FAQs
1. What is cloud computing?
-
Cloud computing refers to the delivery of computing services (such as servers, storage, databases, networking, software, and analytics) over the internet. It allows users to access and use these resources on a pay-as-you-go or subscription basis.
2. What are the different types of cloud service models?
-
There are three primary cloud service models:
-
Infrastructure as a Service (IaaS)
-
Platform as a Service (PaaS)
-
Software as a Service (SaaS)
3. What is the difference between public, private, and hybrid clouds?
-
Public Cloud: Services are provided by third-party cloud providers and made available to the general public.
-
Private Cloud: Resources are dedicated to a single organization and may be hosted on-premises or by a third party.
-
Hybrid Cloud: Combines elements of both public and private clouds, allowing data and applications to move between them.
4. What are some advantages of cloud computing?
-
Advantages of cloud computing include cost efficiency, scalability, accessibility, reliability, security, automatic updates, and the ability to foster innovation.
5. What are some disadvantages of cloud computing?
-
Disadvantages of cloud computing include potential downtime, security concerns, limited control over infrastructure, bandwidth limitations, data transfer costs, vendor lock-in, and compliance challenges.
6. What is the shared responsibility model in cloud security?
-
The shared responsibility model outlines the division of security responsibilities between the cloud provider and the customer. The provider is responsible for securing the infrastructure, while the customer is responsible for securing their data and applications within the cloud.
7. What are some common cloud computing certifications?
-
Popular cloud computing certifications include AWS Certified Solutions Architect, Microsoft Certified Azure Administrator, Google Cloud Professional Cloud Architect, and Certified Cloud Security Professional (CCSP).
8. How do I choose the right cloud provider for my organization?
-
Choosing the right cloud provider involves considering factors like services offered, pricing, security features, compliance, data center locations, and customer support. It's essential to align your choice with your organization's specific needs and goals.
9. What is the difference between cloud computing and traditional IT infrastructure?
-
Cloud computing offers on-demand access to computing resources over the internet, while traditional IT infrastructure relies on on-premises hardware and software. Cloud computing is scalable, cost-effective, and provides greater flexibility compared to traditional IT.
10. How can I ensure data security in the cloud?
-
Ensuring data security in the cloud involves implementing strong access controls, encryption, regular security audits, compliance with industry standards, and monitoring for suspicious activities. It's essential to follow best practices for cloud security.
What is Scrum Framework, and How Does it Work?
In the dynamic landscape of project management and software development, methodologies that foster flexibility, collaboration, and rapid adaptation are essential. One such methodology that has gained widespread recognition and adoption is the Scrum Framework. Born out of the Agile movement, Scrum has revolutionized the way teams tackle complex projects, enabling them to deliver high-quality results efficiently and with enhanced teamwork.
In this comprehensive guide, we will delve into the intricacies of the Scrum Framework, unraveling its core principles, methodologies, and the seamless interplay of its roles and rituals. Whether you're an aspiring project manager, a seasoned software developer, or simply curious about how Scrum works, join us on this journey as we explore the essence of Scrum and how it can transform the way you approach projects. From its foundational concepts to its practical implementation, you'll gain a solid understanding of what Scrum is and, more importantly, how it works to bring about unparalleled success in the world of project management and beyond.
Table of Contents
What is the Scrum Process Framework?
What Are Scrum Artifacts?
Benefits of Scrum Methodology
Scrum and Agile Relationship Explained
Scrum Ceremonies or Events
Scrum Pillars and Values
3 Essential Roles for Scrum Success
Scaling Scrum to Multiple Teams
Conclusion
What is the Scrum Process Framework?
The Scrum process framework is an agile project management approach designed to facilitate the iterative and incremental development of products. It is characterized by a set of defined roles, events, artifacts, and rules that guide a development team's work. Key roles include the Product Owner, Scrum Master, and Development Team, each with specific responsibilities. Scrum events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide a structured rhythm to the development process. The Product Backlog, Sprint Backlog, and Increment are the essential artifacts used to manage work and track progress. Scrum emphasizes transparency, inspection, and adaptation, allowing teams to respond to changing requirements and deliver high-value product increments regularly.
One of Scrum's core principles is its focus on collaboration and adaptability. By breaking work into small, manageable iterations called sprints, teams can quickly respond to customer feedback and changing priorities. This iterative approach encourages continuous improvement, making Scrum an effective framework for complex projects where requirements may evolve over time. It promotes a sense of ownership and accountability among team members, leading to more efficient and productive development cycles. Scrum's simplicity and flexibility have made it a popular choice not only in software development but also in various industries seeking to deliver value to customers faster and with greater adaptability.
What Are Scrum Artifacts?
Scrum artifacts are essential documents or information sources that provide transparency and help in managing work within the Scrum framework. These artifacts are used to ensure that everyone involved in a Scrum project has a common understanding of the product being developed and the progress being made. There are three primary Scrum artifacts:
-
Product Backlog: The Product Backlog is a prioritized list of all the work that needs to be done to create and maintain the product. It is owned and managed by the Product Owner. The items in the Product Backlog can include features, user stories, bug fixes, technical tasks, and other work items. Each item is described in sufficient detail so that the development team understands what needs to be done. The Product Owner continuously refines and prioritizes the backlog based on changing requirements and feedback from stakeholders.
-
Sprint Backlog: The Sprint Backlog is a subset of the items from the Product Backlog that the development team commits to completing during a specific sprint. It is created during the Sprint Planning event, where the team selects the highest-priority items from the Product Backlog and decides how they will deliver them. The Sprint Backlog is a dynamic document that can be adjusted as the team gains a better understanding of the work during the sprint. It helps the team track progress toward the sprint goal.
-
Increment: The Increment is the sum of all the product backlog items that have been completed during a sprint. It represents a potentially shippable product or a product incrementally closer to the desired end state. At the end of each sprint, the development team delivers the Increment for review by stakeholders during the Sprint Review event. If accepted, the Increment can be released to users or customers. The goal is to have a potentially shippable product increment at the end of each sprint, although it may not include all desired features until subsequent sprints.
These Scrum artifacts serve to provide transparency, enable inspection, and support adaptation throughout the development process. They ensure that everyone involved in the project, including the development team, Product Owner, and stakeholders, has a clear understanding of what work is to be done, what has been completed, and the overall progress toward the product's goals.
Benefits of Scrum Methodology
The Scrum methodology offers several benefits, making it a popular choice for agile project management and product development. Some of the key advantages of Scrum include:
-
Flexibility and Adaptability: Scrum embraces change and allows teams to adapt to evolving requirements, market conditions, and customer feedback. It offers the flexibility to reprioritize work and make adjustments during short, time-boxed iterations called sprints.
-
Customer-Centric: Scrum places a strong emphasis on delivering value to the customer. The Product Owner is responsible for prioritizing the product backlog based on customer needs, ensuring that the most valuable features are built first.
-
Transparency: Scrum promotes transparency by making project information visible to all team members. This transparency encourages collaboration, accountability, and open communication among team members and stakeholders.
-
Increased Productivity: Scrum's iterative approach often leads to higher productivity because it focuses on delivering a potentially shippable product incrementally. Teams can release valuable features sooner, providing benefits to the end-users and stakeholders.
-
Early and Regular Feedback: Scrum encourages frequent feedback through events like Sprint Reviews and Daily Scrums. This continuous feedback loop helps identify and address issues early in the development process, reducing the risk of building the wrong product.
-
Improved Quality: Scrum places a strong emphasis on quality through practices like automated testing and continuous integration. The incremental development and regular inspections help maintain and improve product quality over time.
-
Empowered Teams: Scrum empowers development teams to self-organize and make decisions regarding how to achieve sprint goals. This autonomy and ownership often lead to more motivated and engaged team members.
-
Predictable Delivery: Scrum promotes predictability by establishing a consistent cadence of work through time-boxed sprints. This helps stakeholders understand when they can expect specific features or updates.
-
Reduced Risk: With its focus on frequent inspections and adaptations, Scrum helps mitigate risks by identifying and addressing issues early in the project. Teams can make informed decisions to course-correct as needed.
-
Enhanced Collaboration: Scrum fosters collaboration among cross-functional team members, including developers, testers, designers, and product managers. Regular meetings like the Daily Scrum promote communication and collaboration.
While Scrum offers numerous benefits, it's essential to recognize that its successful implementation requires a committed and well-trained team, adherence to Scrum principles, and continuous improvement to refine processes over time.
Scrum and Agile Relationship Explained
Scrum and Agile are closely related concepts in the world of project management and software development, with Scrum being one of the most popular frameworks within the broader Agile methodology. Here's an explanation of their relationship:
Agile:
-
Agile is a set of values and principles outlined in the Agile Manifesto, which was created in 2001 by a group of software developers. The manifesto emphasizes customer collaboration, responding to change, and delivering working software as primary goals.
-
Agile is not a specific framework or methodology but rather a mindset or philosophy that promotes flexibility, collaboration, and customer-centricity. It encourages teams to work iteratively and adapt to changing requirements and customer feedback.
Scrum:
-
Scrum is a specific framework for implementing Agile principles. It provides a structured approach to managing work within an Agile context.
-
Scrum prescribes a set of roles (Product Owner, Scrum Master, Development Team), events (Sprint, Sprint Planning, Daily Scrum, Sprint Review, Sprint Retrospective), and artifacts (Product Backlog, Sprint Backlog, Increment) that help teams organize their work, collaborate effectively, and deliver value to customers.
Relationship:
-
Scrum is a subset of Agile: Scrum falls under the umbrella of Agile methodologies. While Agile is a broader philosophy, Scrum is a specific approach that adheres to Agile principles.
-
Scrum operationalizes Agile: Scrum provides a practical framework for teams to implement Agile principles in a structured way. It defines roles, events, and artifacts that guide the development process, making Agile principles actionable.
-
Scrum is a popular choice for Agile: Many organizations adopt Scrum as their chosen methodology for implementing Agile practices. However, Agile is not limited to Scrum; there are other Agile frameworks like Kanban, Lean, and Extreme Programming (XP), each with its own set of principles and practices.
In summary, Agile is the overarching philosophy that emphasizes customer collaboration, flexibility, and iterative development, while Scrum is a specific framework that operationalizes Agile principles. Scrum provides a structured approach to managing work and is one of the most widely used methods for implementing Agile practices in software development and other project management contexts.
Scrum Ceremonies or Events
In Scrum, there are several ceremonies or events that provide structure and cadence to the development process. These events help teams collaborate, plan, inspect and adapt their work. The key Scrum ceremonies or events are:
-
Sprint Planning: This is a time-boxed event at the start of each sprint where the Product Owner and Development Team collaborate to select and commit to a set of product backlog items to be worked on during the sprint. The team also discusses how to achieve the sprint goal.
-
Daily Scrum (Daily Standup): A daily, time-boxed meeting where the Development Team synchronizes their work. Each team member answers three questions: What did I do yesterday? What will I do today? Are there any impediments or blockers? This meeting helps the team stay on track and adapt to changing circumstances.
-
Sprint Review: At the end of each sprint, there is a Sprint Review meeting where the Development Team demonstrates the work completed during the sprint to stakeholders, including the Product Owner and possibly customers. It's an opportunity to gather feedback and potentially adjust the product backlog based on new insights.
-
Sprint Retrospective: Also held at the end of each sprint, the Sprint Retrospective is a meeting for the Development Team to reflect on the sprint and identify improvements. It's a time to discuss what went well, what could be improved, and what action items the team will take in the next sprint.
-
Backlog Refinement (Grooming): While not a formal event, backlog refinement is an ongoing activity where the Product Owner and Development Team collaborate to clarify, estimate, and prioritize items in the product backlog. This ensures that the backlog is well-prepared for future sprints.
These Scrum ceremonies provide a structured framework for planning, communication, and continuous improvement within the Scrum process. They help teams stay focused on delivering value, adapt to changing requirements, and maintain transparency throughout the development process. The time-boxed nature of these events ensures that they are efficient and don't become overly time-consuming.
Scrum Pillars and Values
Scrum is guided by three pillars and five core values, which provide the foundation for the framework and help teams implement Scrum effectively. These pillars and values are integral to Scrum's success:
Pillars:
-
Transparency: Transparency is the first pillar of Scrum, emphasizing openness and visibility in all aspects of work. It means that all relevant information about the project, progress, and challenges should be easily accessible to all team members and stakeholders. Transparency promotes trust and helps teams make informed decisions.
-
Inspection: The second pillar is inspection, which encourages regular examination of the product, processes, and progress. Teams should inspect their work and the product increment continuously, identifying areas that need improvement. Inspection provides opportunities to adapt and make necessary changes to enhance product quality and efficiency.
-
Adaptation: The third pillar, adaptation, goes hand-in-hand with inspection. Once issues are identified through inspection, teams must take action to adapt and make improvements. Scrum encourages flexibility and adaptability in response to changing requirements, market conditions, or other factors. Adaptation is essential for delivering valuable products and continuously improving the development process.
Values:
-
Commitment: Scrum values commitment, particularly commitment to delivering value to the customer. The team commits to the goals of the sprint and works diligently to achieve them. Commitment also includes the commitment to quality and excellence in all aspects of the work.
-
Courage: Courage is the value that enables teams to confront challenges and take calculated risks. It means speaking up about issues, suggesting changes, and admitting when something isn't working as expected. Teams should have the courage to make tough decisions that are in the best interest of the product and the project.
-
Focus: Scrum encourages focus on the sprint goal and the highest-priority work. Teams should concentrate their efforts on completing the items in the sprint backlog and delivering a potentially shippable product increment. Distractions and scope changes should be minimized to maintain focus.
-
Openness: Openness is about fostering an environment where team members and stakeholders can communicate transparently. It means being receptive to feedback, actively listening, and promoting collaboration. Openness encourages the sharing of information and ideas to improve the project.
-
Respect: Respect is a fundamental value in Scrum, promoting respect for each team member's expertise, opinions, and contributions. It also extends to respecting the decisions of the team and stakeholders. A respectful environment supports effective teamwork and collaboration.
These pillars and values provide the underlying philosophy and principles that guide Scrum teams in their work. When teams and organizations embrace these pillars and values, they are better equipped to harness the power of Scrum to deliver high-quality products and adapt to changing demands effectively.
3 Essential Roles for Scrum Success
Scrum relies on three essential roles to ensure its success. These roles play distinct but interconnected functions in the Scrum framework:
Product Owner:
-
The Product Owner is a crucial role responsible for representing the interests of stakeholders, including customers and users. They are the primary decision-maker regarding the product's features, functionality, and priorities.
-
Responsibilities include creating and maintaining the product backlog, which is a prioritized list of work items (often user stories) that define what needs to be built or improved.
-
The Product Owner collaborates closely with the development team to clarify requirements, answer questions, and provide ongoing feedback.
-
Success in this role involves effectively balancing stakeholder needs, maintaining a clear product vision, and continuously prioritizing the backlog to maximize the product's value.
Scrum Master:
-
The Scrum Master is a servant-leader for the Scrum team, focused on facilitating and coaching the team to follow Scrum principles and practices.
-
Responsibilities include removing impediments or obstacles that hinder the team's progress, ensuring that Scrum events are conducted effectively, and promoting a collaborative and self-organizing team culture.
-
The Scrum Master fosters continuous improvement by facilitating the Sprint Retrospective and encouraging the team to reflect on their processes and make adjustments.
-
Success in this role involves guiding the team toward self-sufficiency, helping them improve their Scrum practices, and ensuring that Scrum values are upheld.
Development Team:
-
The Development Team consists of cross-functional individuals who work together to deliver a potentially shippable product increment during each sprint.
-
Responsibilities include selecting and committing to work items from the sprint backlog, designing, coding, testing, and delivering the product increment.
-
Development Teams are self-organizing, meaning they have the autonomy to determine how to complete the work and make decisions about how to meet the sprint goal.
-
Success of the Development Team is measured by their ability to consistently deliver high-quality, potentially shippable increments of the product and their commitment to continuous improvement.
These three roles are integral to the success of Scrum. The Product Owner ensures that the product meets customer needs, the Scrum Master enables the team to follow Scrum principles, and the Development Team is responsible for delivering the product increment. Effective collaboration and adherence to Scrum values and principles among these roles are essential for achieving Scrum's goal of delivering value to customers through iterative and incremental development.
Scaling Scrum to Multiple Teams
Scaling Scrum to multiple teams in five key points:
-
Choose a Scaling Framework: Select an appropriate scaling framework, such as SAFe, LeSS, or Nexus, that aligns with your organizational goals and context.
-
Coordinate Product Ownership: Ensure product ownership is well-coordinated across teams, either by creating a Product Owner team or designating a Chief Product Owner to maintain a unified product backlog.
-
Facilitate Cross-Team Collaboration: Organize regular Scrum of Scrums meetings to facilitate cross-team collaboration, share information, and address dependencies.
-
Implement Program Increment (PI) Planning: Conduct PI planning sessions to align the work of multiple teams for a set period (e.g., 8-12 weeks) and establish a shared vision.
-
Promote a Culture of Continuous Improvement: Foster a culture of continuous improvement, provide training and coaching, and regularly inspect and adapt at both the team and program levels to enhance collaboration and alignment among teams.
How to obtain the CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, Scrum is a powerful framework for agile project management and product development that emphasizes transparency, inspection, and adaptation. Its three pillars of transparency, inspection, and adaptation, along with its five core values of commitment, courage, focus, openness, and respect, provide a strong foundation for teams to deliver value to customers effectively.
Scrum's essential roles, including the Product Owner, Scrum Master, and Development Team, play distinct but interconnected functions in ensuring project success. The ceremonies or events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide structure and guidance throughout the development process.
When it comes to scaling Scrum to multiple teams, organizations have several frameworks and strategies to choose from, such as SAFe, Scrum of Scrums, and coordinated product ownership. These approaches enable large and complex organizations to maintain alignment, collaboration, and responsiveness as they deliver value to customers.
In essence, Scrum promotes a customer-centric, adaptable, and collaborative approach to project management, making it a valuable choice for a wide range of industries and project types. By embracing Scrum's principles, roles, values, and ceremonies, teams and organizations can increase their chances of delivering high-quality products and continuously improving their processes.
Read More
In the dynamic landscape of project management and software development, methodologies that foster flexibility, collaboration, and rapid adaptation are essential. One such methodology that has gained widespread recognition and adoption is the Scrum Framework. Born out of the Agile movement, Scrum has revolutionized the way teams tackle complex projects, enabling them to deliver high-quality results efficiently and with enhanced teamwork.
In this comprehensive guide, we will delve into the intricacies of the Scrum Framework, unraveling its core principles, methodologies, and the seamless interplay of its roles and rituals. Whether you're an aspiring project manager, a seasoned software developer, or simply curious about how Scrum works, join us on this journey as we explore the essence of Scrum and how it can transform the way you approach projects. From its foundational concepts to its practical implementation, you'll gain a solid understanding of what Scrum is and, more importantly, how it works to bring about unparalleled success in the world of project management and beyond.
Table of Contents
What is the Scrum Process Framework?
What Are Scrum Artifacts?
Benefits of Scrum Methodology
Scrum and Agile Relationship Explained
Scrum Ceremonies or Events
Scrum Pillars and Values
3 Essential Roles for Scrum Success
Scaling Scrum to Multiple Teams
Conclusion
What is the Scrum Process Framework?
The Scrum process framework is an agile project management approach designed to facilitate the iterative and incremental development of products. It is characterized by a set of defined roles, events, artifacts, and rules that guide a development team's work. Key roles include the Product Owner, Scrum Master, and Development Team, each with specific responsibilities. Scrum events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide a structured rhythm to the development process. The Product Backlog, Sprint Backlog, and Increment are the essential artifacts used to manage work and track progress. Scrum emphasizes transparency, inspection, and adaptation, allowing teams to respond to changing requirements and deliver high-value product increments regularly.
One of Scrum's core principles is its focus on collaboration and adaptability. By breaking work into small, manageable iterations called sprints, teams can quickly respond to customer feedback and changing priorities. This iterative approach encourages continuous improvement, making Scrum an effective framework for complex projects where requirements may evolve over time. It promotes a sense of ownership and accountability among team members, leading to more efficient and productive development cycles. Scrum's simplicity and flexibility have made it a popular choice not only in software development but also in various industries seeking to deliver value to customers faster and with greater adaptability.
What Are Scrum Artifacts?
Scrum artifacts are essential documents or information sources that provide transparency and help in managing work within the Scrum framework. These artifacts are used to ensure that everyone involved in a Scrum project has a common understanding of the product being developed and the progress being made. There are three primary Scrum artifacts:
-
Product Backlog: The Product Backlog is a prioritized list of all the work that needs to be done to create and maintain the product. It is owned and managed by the Product Owner. The items in the Product Backlog can include features, user stories, bug fixes, technical tasks, and other work items. Each item is described in sufficient detail so that the development team understands what needs to be done. The Product Owner continuously refines and prioritizes the backlog based on changing requirements and feedback from stakeholders.
-
Sprint Backlog: The Sprint Backlog is a subset of the items from the Product Backlog that the development team commits to completing during a specific sprint. It is created during the Sprint Planning event, where the team selects the highest-priority items from the Product Backlog and decides how they will deliver them. The Sprint Backlog is a dynamic document that can be adjusted as the team gains a better understanding of the work during the sprint. It helps the team track progress toward the sprint goal.
-
Increment: The Increment is the sum of all the product backlog items that have been completed during a sprint. It represents a potentially shippable product or a product incrementally closer to the desired end state. At the end of each sprint, the development team delivers the Increment for review by stakeholders during the Sprint Review event. If accepted, the Increment can be released to users or customers. The goal is to have a potentially shippable product increment at the end of each sprint, although it may not include all desired features until subsequent sprints.
These Scrum artifacts serve to provide transparency, enable inspection, and support adaptation throughout the development process. They ensure that everyone involved in the project, including the development team, Product Owner, and stakeholders, has a clear understanding of what work is to be done, what has been completed, and the overall progress toward the product's goals.
Benefits of Scrum Methodology
The Scrum methodology offers several benefits, making it a popular choice for agile project management and product development. Some of the key advantages of Scrum include:
-
Flexibility and Adaptability: Scrum embraces change and allows teams to adapt to evolving requirements, market conditions, and customer feedback. It offers the flexibility to reprioritize work and make adjustments during short, time-boxed iterations called sprints.
-
Customer-Centric: Scrum places a strong emphasis on delivering value to the customer. The Product Owner is responsible for prioritizing the product backlog based on customer needs, ensuring that the most valuable features are built first.
-
Transparency: Scrum promotes transparency by making project information visible to all team members. This transparency encourages collaboration, accountability, and open communication among team members and stakeholders.
-
Increased Productivity: Scrum's iterative approach often leads to higher productivity because it focuses on delivering a potentially shippable product incrementally. Teams can release valuable features sooner, providing benefits to the end-users and stakeholders.
-
Early and Regular Feedback: Scrum encourages frequent feedback through events like Sprint Reviews and Daily Scrums. This continuous feedback loop helps identify and address issues early in the development process, reducing the risk of building the wrong product.
-
Improved Quality: Scrum places a strong emphasis on quality through practices like automated testing and continuous integration. The incremental development and regular inspections help maintain and improve product quality over time.
-
Empowered Teams: Scrum empowers development teams to self-organize and make decisions regarding how to achieve sprint goals. This autonomy and ownership often lead to more motivated and engaged team members.
-
Predictable Delivery: Scrum promotes predictability by establishing a consistent cadence of work through time-boxed sprints. This helps stakeholders understand when they can expect specific features or updates.
-
Reduced Risk: With its focus on frequent inspections and adaptations, Scrum helps mitigate risks by identifying and addressing issues early in the project. Teams can make informed decisions to course-correct as needed.
-
Enhanced Collaboration: Scrum fosters collaboration among cross-functional team members, including developers, testers, designers, and product managers. Regular meetings like the Daily Scrum promote communication and collaboration.
While Scrum offers numerous benefits, it's essential to recognize that its successful implementation requires a committed and well-trained team, adherence to Scrum principles, and continuous improvement to refine processes over time.
Scrum and Agile Relationship Explained
Scrum and Agile are closely related concepts in the world of project management and software development, with Scrum being one of the most popular frameworks within the broader Agile methodology. Here's an explanation of their relationship:
Agile:
-
Agile is a set of values and principles outlined in the Agile Manifesto, which was created in 2001 by a group of software developers. The manifesto emphasizes customer collaboration, responding to change, and delivering working software as primary goals.
-
Agile is not a specific framework or methodology but rather a mindset or philosophy that promotes flexibility, collaboration, and customer-centricity. It encourages teams to work iteratively and adapt to changing requirements and customer feedback.
Scrum:
-
Scrum is a specific framework for implementing Agile principles. It provides a structured approach to managing work within an Agile context.
-
Scrum prescribes a set of roles (Product Owner, Scrum Master, Development Team), events (Sprint, Sprint Planning, Daily Scrum, Sprint Review, Sprint Retrospective), and artifacts (Product Backlog, Sprint Backlog, Increment) that help teams organize their work, collaborate effectively, and deliver value to customers.
Relationship:
-
Scrum is a subset of Agile: Scrum falls under the umbrella of Agile methodologies. While Agile is a broader philosophy, Scrum is a specific approach that adheres to Agile principles.
-
Scrum operationalizes Agile: Scrum provides a practical framework for teams to implement Agile principles in a structured way. It defines roles, events, and artifacts that guide the development process, making Agile principles actionable.
-
Scrum is a popular choice for Agile: Many organizations adopt Scrum as their chosen methodology for implementing Agile practices. However, Agile is not limited to Scrum; there are other Agile frameworks like Kanban, Lean, and Extreme Programming (XP), each with its own set of principles and practices.
In summary, Agile is the overarching philosophy that emphasizes customer collaboration, flexibility, and iterative development, while Scrum is a specific framework that operationalizes Agile principles. Scrum provides a structured approach to managing work and is one of the most widely used methods for implementing Agile practices in software development and other project management contexts.
Scrum Ceremonies or Events
In Scrum, there are several ceremonies or events that provide structure and cadence to the development process. These events help teams collaborate, plan, inspect and adapt their work. The key Scrum ceremonies or events are:
-
Sprint Planning: This is a time-boxed event at the start of each sprint where the Product Owner and Development Team collaborate to select and commit to a set of product backlog items to be worked on during the sprint. The team also discusses how to achieve the sprint goal.
-
Daily Scrum (Daily Standup): A daily, time-boxed meeting where the Development Team synchronizes their work. Each team member answers three questions: What did I do yesterday? What will I do today? Are there any impediments or blockers? This meeting helps the team stay on track and adapt to changing circumstances.
-
Sprint Review: At the end of each sprint, there is a Sprint Review meeting where the Development Team demonstrates the work completed during the sprint to stakeholders, including the Product Owner and possibly customers. It's an opportunity to gather feedback and potentially adjust the product backlog based on new insights.
-
Sprint Retrospective: Also held at the end of each sprint, the Sprint Retrospective is a meeting for the Development Team to reflect on the sprint and identify improvements. It's a time to discuss what went well, what could be improved, and what action items the team will take in the next sprint.
-
Backlog Refinement (Grooming): While not a formal event, backlog refinement is an ongoing activity where the Product Owner and Development Team collaborate to clarify, estimate, and prioritize items in the product backlog. This ensures that the backlog is well-prepared for future sprints.
These Scrum ceremonies provide a structured framework for planning, communication, and continuous improvement within the Scrum process. They help teams stay focused on delivering value, adapt to changing requirements, and maintain transparency throughout the development process. The time-boxed nature of these events ensures that they are efficient and don't become overly time-consuming.
Scrum Pillars and Values
Scrum is guided by three pillars and five core values, which provide the foundation for the framework and help teams implement Scrum effectively. These pillars and values are integral to Scrum's success:
Pillars:
-
Transparency: Transparency is the first pillar of Scrum, emphasizing openness and visibility in all aspects of work. It means that all relevant information about the project, progress, and challenges should be easily accessible to all team members and stakeholders. Transparency promotes trust and helps teams make informed decisions.
-
Inspection: The second pillar is inspection, which encourages regular examination of the product, processes, and progress. Teams should inspect their work and the product increment continuously, identifying areas that need improvement. Inspection provides opportunities to adapt and make necessary changes to enhance product quality and efficiency.
-
Adaptation: The third pillar, adaptation, goes hand-in-hand with inspection. Once issues are identified through inspection, teams must take action to adapt and make improvements. Scrum encourages flexibility and adaptability in response to changing requirements, market conditions, or other factors. Adaptation is essential for delivering valuable products and continuously improving the development process.
Values:
-
Commitment: Scrum values commitment, particularly commitment to delivering value to the customer. The team commits to the goals of the sprint and works diligently to achieve them. Commitment also includes the commitment to quality and excellence in all aspects of the work.
-
Courage: Courage is the value that enables teams to confront challenges and take calculated risks. It means speaking up about issues, suggesting changes, and admitting when something isn't working as expected. Teams should have the courage to make tough decisions that are in the best interest of the product and the project.
-
Focus: Scrum encourages focus on the sprint goal and the highest-priority work. Teams should concentrate their efforts on completing the items in the sprint backlog and delivering a potentially shippable product increment. Distractions and scope changes should be minimized to maintain focus.
-
Openness: Openness is about fostering an environment where team members and stakeholders can communicate transparently. It means being receptive to feedback, actively listening, and promoting collaboration. Openness encourages the sharing of information and ideas to improve the project.
-
Respect: Respect is a fundamental value in Scrum, promoting respect for each team member's expertise, opinions, and contributions. It also extends to respecting the decisions of the team and stakeholders. A respectful environment supports effective teamwork and collaboration.
These pillars and values provide the underlying philosophy and principles that guide Scrum teams in their work. When teams and organizations embrace these pillars and values, they are better equipped to harness the power of Scrum to deliver high-quality products and adapt to changing demands effectively.
3 Essential Roles for Scrum Success
Scrum relies on three essential roles to ensure its success. These roles play distinct but interconnected functions in the Scrum framework:
Product Owner:
-
The Product Owner is a crucial role responsible for representing the interests of stakeholders, including customers and users. They are the primary decision-maker regarding the product's features, functionality, and priorities.
-
Responsibilities include creating and maintaining the product backlog, which is a prioritized list of work items (often user stories) that define what needs to be built or improved.
-
The Product Owner collaborates closely with the development team to clarify requirements, answer questions, and provide ongoing feedback.
-
Success in this role involves effectively balancing stakeholder needs, maintaining a clear product vision, and continuously prioritizing the backlog to maximize the product's value.
Scrum Master:
-
The Scrum Master is a servant-leader for the Scrum team, focused on facilitating and coaching the team to follow Scrum principles and practices.
-
Responsibilities include removing impediments or obstacles that hinder the team's progress, ensuring that Scrum events are conducted effectively, and promoting a collaborative and self-organizing team culture.
-
The Scrum Master fosters continuous improvement by facilitating the Sprint Retrospective and encouraging the team to reflect on their processes and make adjustments.
-
Success in this role involves guiding the team toward self-sufficiency, helping them improve their Scrum practices, and ensuring that Scrum values are upheld.
Development Team:
-
The Development Team consists of cross-functional individuals who work together to deliver a potentially shippable product increment during each sprint.
-
Responsibilities include selecting and committing to work items from the sprint backlog, designing, coding, testing, and delivering the product increment.
-
Development Teams are self-organizing, meaning they have the autonomy to determine how to complete the work and make decisions about how to meet the sprint goal.
-
Success of the Development Team is measured by their ability to consistently deliver high-quality, potentially shippable increments of the product and their commitment to continuous improvement.
These three roles are integral to the success of Scrum. The Product Owner ensures that the product meets customer needs, the Scrum Master enables the team to follow Scrum principles, and the Development Team is responsible for delivering the product increment. Effective collaboration and adherence to Scrum values and principles among these roles are essential for achieving Scrum's goal of delivering value to customers through iterative and incremental development.
Scaling Scrum to Multiple Teams
Scaling Scrum to multiple teams in five key points:
-
Choose a Scaling Framework: Select an appropriate scaling framework, such as SAFe, LeSS, or Nexus, that aligns with your organizational goals and context.
-
Coordinate Product Ownership: Ensure product ownership is well-coordinated across teams, either by creating a Product Owner team or designating a Chief Product Owner to maintain a unified product backlog.
-
Facilitate Cross-Team Collaboration: Organize regular Scrum of Scrums meetings to facilitate cross-team collaboration, share information, and address dependencies.
-
Implement Program Increment (PI) Planning: Conduct PI planning sessions to align the work of multiple teams for a set period (e.g., 8-12 weeks) and establish a shared vision.
-
Promote a Culture of Continuous Improvement: Foster a culture of continuous improvement, provide training and coaching, and regularly inspect and adapt at both the team and program levels to enhance collaboration and alignment among teams.
How to obtain the CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, Scrum is a powerful framework for agile project management and product development that emphasizes transparency, inspection, and adaptation. Its three pillars of transparency, inspection, and adaptation, along with its five core values of commitment, courage, focus, openness, and respect, provide a strong foundation for teams to deliver value to customers effectively.
Scrum's essential roles, including the Product Owner, Scrum Master, and Development Team, play distinct but interconnected functions in ensuring project success. The ceremonies or events, such as Sprint Planning, Daily Scrum, Sprint Review, and Sprint Retrospective, provide structure and guidance throughout the development process.
When it comes to scaling Scrum to multiple teams, organizations have several frameworks and strategies to choose from, such as SAFe, Scrum of Scrums, and coordinated product ownership. These approaches enable large and complex organizations to maintain alignment, collaboration, and responsiveness as they deliver value to customers.
In essence, Scrum promotes a customer-centric, adaptable, and collaborative approach to project management, making it a valuable choice for a wide range of industries and project types. By embracing Scrum's principles, roles, values, and ceremonies, teams and organizations can increase their chances of delivering high-quality products and continuously improving their processes.
Top 10 Business Analytics Tools Used by Companies Today
In today's data-driven business landscape, the ability to transform raw information into actionable insights has become a competitive advantage for companies across industries. Business analytics tools have emerged as indispensable assets in this pursuit, empowering organizations to make informed decisions, optimize operations, and drive growth. As technology continues to evolve, the range and capabilities of these tools have expanded, allowing businesses to harness the power of data like never before.
In this blog, we will delve into the world of data-driven decision-making and explore the top 10 business analytics tools that are currently reshaping the way companies operate. Whether you're a seasoned data professional seeking to enhance your toolkit or a business leader eager to leverage data for strategic advantage, this guide will introduce you to the cutting-edge tools that are driving innovation and success in today's competitive landscape. From data visualization to predictive modeling, these tools offer a diverse array of capabilities that are transforming how organizations extract value from their data assets. Join us on this journey through the world of business analytics and discover the tools that are at the forefront of modern business intelligence.
Table of Contents
What Are Business Analytics Tools?
Difference Between Business Analytics and Business Intelligence Solutions
Popular Open Source Analytics Tools
Career Options in Business Analytics
But How Do You Start Your Career and Land a High-Paying Job?
Conclusion
What Are Business Analytics Tools?
Business analytics tools are software applications that help organizations extract valuable insights from their data to support decision-making processes. These tools enable businesses to collect, process, and analyze data from various sources, transforming raw information into meaningful patterns, trends, and actionable recommendations. They encompass a wide range of functions, including data visualization, statistical analysis, predictive modeling, and reporting. By utilizing business analytics tools, companies can gain a deeper understanding of their operations, customers, and market dynamics, ultimately leading to more informed and strategic choices.
These tools are invaluable in today's data-driven business landscape, where the ability to make decisions based on evidence and trends can significantly impact an organization's success. They enable companies to uncover hidden opportunities, identify areas for improvement, and optimize their strategies, ultimately enhancing competitiveness and profitability. Whether it's tracking website performance with Google Analytics, creating interactive dashboards with Tableau, or leveraging machine learning with Python, business analytics tools offer versatile solutions for businesses of all sizes and industries to harness the power of data for informed decision-making.
Difference Between Business Analytics and Business Intelligence Solutions
Here's a concise comparison of Business Analytics and Business Intelligence solutions in tabular form:
Aspect
Business Intelligence (BI)
Business Analytics
Purpose and Focus
Historical and current data, focuses on reporting and monitoring.
Historical data used to predict future trends, optimize processes, and make strategic decisions.
Timeframe
Past and present data analysis.
Past data analysis to predict future events.
Types of Questions Answered
Descriptive questions (What happened?).
Diagnostic (Why did it happen?), predictive (What will happen?), and prescriptive (What should we do?) questions.
Data Visualization vs. Data Modeling
Emphasis on data visualization through dashboards and reports.
Focus on data modeling and statistical analysis to create predictive models.
Use Cases
Routine reporting, performance monitoring, and standard operational reporting.
Complex problem-solving, strategic decision-making, financial forecasting, customer segmentation, supply chain optimization, and more.
This table provides a clear overview of the key distinctions between Business Intelligence and Business Analytics solutions.
Popular Open Source Analytics Tools
-
R:
-
Description: R is a versatile programming language and environment specifically designed for statistical computing and data analysis. It offers a wide array of packages and libraries for data manipulation, visualization, and advanced statistical modeling.
-
Use Cases: R is popular among statisticians, data scientists, and researchers for tasks such as data exploration, hypothesis testing, regression analysis, and creating custom data visualizations.
-
Key Features: It provides extensive libraries for data analysis (e.g., dplyr, tidyr), data visualization (ggplot2), and machine learning (caret). R's interactive console allows users to explore and analyze data interactively.
-
Community: R has a vibrant and active community that contributes to package development and provides support through forums and mailing lists.
-
Python:
-
Description: Python is a versatile, easy-to-learn programming language with a thriving ecosystem for data analysis, machine learning, and web development. It is known for its simplicity and readability.
-
Use Cases: Python is used for data cleaning, manipulation, visualization, machine learning, and web scraping. Popular libraries include Pandas, Matplotlib, Seaborn, scikit-learn, and TensorFlow.
-
Key Features: Python's simplicity makes it accessible to beginners, and its vast library of packages makes it suitable for a wide range of data tasks. Jupyter notebooks enable interactive data exploration and documentation.
-
Community: Python boasts a large and active community, offering extensive documentation, tutorials, and support resources.
-
Apache Hadoop:
-
Description: Apache Hadoop is an open-source framework for distributed storage and processing of large datasets across a cluster of commodity hardware.
-
Use Cases: Hadoop is primarily used for big data processing and distributed storage. It is essential for organizations dealing with massive volumes of structured and unstructured data.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for distributed storage and MapReduce for distributed data processing. It can handle diverse data types and is scalable.
-
Community: Hadoop has a robust community, and it has given rise to numerous other big data tools and technologies.
-
Apache Spark:
-
Description: Apache Spark is an open-source big data processing framework known for its speed, versatility, and real-time processing capabilities.
-
Use Cases: Spark is used for big data processing, machine learning, graph processing, and real-time analytics. It's known for its efficiency and support for diverse data workloads.
-
Key Features: Spark's in-memory processing makes it faster than Hadoop's MapReduce. It provides high-level APIs in Python, Scala, and Java, along with libraries for machine learning (MLlib) and graph processing (GraphX).
-
Community: Spark has a thriving community and a rich ecosystem of libraries and tools.
-
KNIME:
-
Description: KNIME (Konstanz Information Miner) is an open-source platform for data analytics, reporting, and integration that uses a visual workflow interface.
-
Use Cases: KNIME is used for data preprocessing, analysis, reporting, and machine learning. It is designed to be accessible to both technical and non-technical users.
-
Key Features: KNIME's visual interface allows users to create data analysis workflows without coding. It supports integration with various data sources, offers extensions and plugins, and provides collaboration features.
-
Community: KNIME has an active community that contributes to its development, provides support, and shares workflows and extensions.
-
Orange:
-
Description: Orange is an open-source data visualization and analysis tool that focuses on visual programming for data exploration, analysis, and machine learning.
-
Use Cases: Orange is used for data preprocessing, data visualization, clustering, classification, and regression. It is known for its user-friendly, drag-and-drop interface.
-
Key Features: Orange provides a wide range of data visualization widgets and analysis components. Users can experiment with data and build machine learning models without programming.
-
Community: Orange has an active community of users and contributors, and it offers extensive documentation and tutorials.
-
Jupyter Notebook:
-
Description: Jupyter Notebook is an open-source web application that enables users to create and share documents containing live code, equations, visualizations, and narrative text.
-
Use Cases: Jupyter Notebook is used for interactive data analysis, data exploration, code prototyping, and creating reproducible research documents.
-
Key Features: It supports multiple programming languages, including Python, R, Julia, and others. Users can combine code, data, visualizations, and explanations in a single interactive document.
-
Community: Jupyter has a thriving community and is widely adopted in data science and research fields.
-
Grafana:
-
Description: Originally designed for monitoring and observability, Grafana is an open-source platform for creating interactive and customizable dashboards for data visualization.
-
Use Cases: Grafana is used for real-time data visualization, monitoring system performance, and creating interactive dashboards for various data sources.
-
Key Features: Grafana supports connections to databases, cloud services, and data sources. It offers a range of visualization options, alerting capabilities, and templating for building dynamic dashboards.
-
Community: Grafana has a growing community, and its plugins and extensions enhance its functionality.
-
Metabase:
-
Description: Metabase is an open-source business intelligence and analytics tool designed for simplicity and accessibility.
-
Use Cases: Metabase is used for querying and visualizing data, creating dashboards, and generating ad-hoc reports, particularly by non-technical users.
-
Key Features: It provides an intuitive and user-friendly interface for data exploration. Metabase connects to various data sources and offers features for sharing and collaboration.
-
Community: Metabase has an active community and a user-friendly setup process.
-
Apache Superset:
-
Description: Apache Superset is an open-source data exploration and visualization platform initially developed by Airbnb.
-
Use Cases: Superset is used for creating interactive and shareable dashboards, exploring data, and ad-hoc querying from various data sources.
-
Key Features: Superset offers a user-friendly interface with a drag-and-drop dashboard builder. It supports multiple chart types, data source connectors, and customization options.
-
Community: Superset has an active and growing community and is part of the Apache Software Foundation.
These open-source analytics tools cover a wide range of data analysis and visualization needs, from statistical modeling to big data processing and business intelligence. Users can select the tool that best aligns with their specific goals, expertise, and data-related tasks.
Career Options in Business Analytics
A career in business analytics offers an exciting and dynamic journey into the world of data-driven decision-making. At its core, business analytics involves the systematic analysis of data to uncover insights and trends that can guide an organization's strategic and operational choices. Data analysts are often the first step in this process, responsible for collecting, cleaning, and organizing data from various sources. They use tools like SQL and Excel to transform raw data into structured datasets, enabling further analysis.
Moving up the ladder, business intelligence analysts specialize in creating visually appealing reports and dashboards that convey complex data findings to non-technical stakeholders. They use specialized BI tools like Tableau and Power BI to present historical data in a way that is easy to understand, helping organizations make informed decisions based on past performance.
For those who want to dive deeper into data exploration and predictive modeling, data scientists and machine learning engineers come into play. Data scientists leverage advanced statistical and machine learning techniques to extract valuable insights and predict future trends from data. They might build recommendation systems, forecast sales, or optimize marketing campaigns. Machine learning engineers, on the other hand, focus on implementing machine learning models in production environments, ensuring they can scale and perform efficiently.
In essence, a career in business analytics offers a pathway for individuals with various skill sets and interests to contribute to organizations' success by harnessing the power of data. Whether you prefer data wrangling and visualization, predictive modeling, or building data-driven solutions, there's a role in business analytics that aligns with your expertise and passion.
But How Do You Start Your Career and Land a High-Paying Job?
To kickstart your career as a business analyst, the essential step is acquiring the right skill sets. You can begin today by exploring and enrolling in iCert Global’s innovative, interactive, and career-focused In Business Analysis (CCBA,CBAP,ECBA) Certifications. This program offers training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.. Start your journey towards becoming a business analyst today!
Conclusion
In conclusion, a career in business analytics is an exciting and lucrative path for those who are passionate about data and its transformative power in decision-making. To embark on this journey, one must focus on acquiring the necessary skills through education, online courses, and certifications. Building a strong portfolio of projects and networking with professionals in the field are also critical steps. Landing a high-paying job in business analytics requires dedication, continuous learning, and effective job search strategies.
Remember that the field is dynamic, with opportunities spanning data analysis, business intelligence, data science, and more. By staying updated with industry trends and honing your expertise, you can not only start but also thrive in a rewarding career as a business analyst. It's a field where your ability to unlock insights from data can make a significant impact on organizations across various industries. So, take that first step, invest in your skills, and embark on your journey towards a successful career in business analytics.
How to obtain AI and Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info@icertglobal.com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Emerging Technologies :
-
Read More
In today's data-driven business landscape, the ability to transform raw information into actionable insights has become a competitive advantage for companies across industries. Business analytics tools have emerged as indispensable assets in this pursuit, empowering organizations to make informed decisions, optimize operations, and drive growth. As technology continues to evolve, the range and capabilities of these tools have expanded, allowing businesses to harness the power of data like never before.
In this blog, we will delve into the world of data-driven decision-making and explore the top 10 business analytics tools that are currently reshaping the way companies operate. Whether you're a seasoned data professional seeking to enhance your toolkit or a business leader eager to leverage data for strategic advantage, this guide will introduce you to the cutting-edge tools that are driving innovation and success in today's competitive landscape. From data visualization to predictive modeling, these tools offer a diverse array of capabilities that are transforming how organizations extract value from their data assets. Join us on this journey through the world of business analytics and discover the tools that are at the forefront of modern business intelligence.
Table of Contents
What Are Business Analytics Tools?
Difference Between Business Analytics and Business Intelligence Solutions
Popular Open Source Analytics Tools
Career Options in Business Analytics
But How Do You Start Your Career and Land a High-Paying Job?
Conclusion
What Are Business Analytics Tools?
Business analytics tools are software applications that help organizations extract valuable insights from their data to support decision-making processes. These tools enable businesses to collect, process, and analyze data from various sources, transforming raw information into meaningful patterns, trends, and actionable recommendations. They encompass a wide range of functions, including data visualization, statistical analysis, predictive modeling, and reporting. By utilizing business analytics tools, companies can gain a deeper understanding of their operations, customers, and market dynamics, ultimately leading to more informed and strategic choices.
These tools are invaluable in today's data-driven business landscape, where the ability to make decisions based on evidence and trends can significantly impact an organization's success. They enable companies to uncover hidden opportunities, identify areas for improvement, and optimize their strategies, ultimately enhancing competitiveness and profitability. Whether it's tracking website performance with Google Analytics, creating interactive dashboards with Tableau, or leveraging machine learning with Python, business analytics tools offer versatile solutions for businesses of all sizes and industries to harness the power of data for informed decision-making.
Difference Between Business Analytics and Business Intelligence Solutions
Here's a concise comparison of Business Analytics and Business Intelligence solutions in tabular form:
|
Aspect |
Business Intelligence (BI) |
Business Analytics |
|
Purpose and Focus |
Historical and current data, focuses on reporting and monitoring. |
Historical data used to predict future trends, optimize processes, and make strategic decisions. |
|
Timeframe |
Past and present data analysis. |
Past data analysis to predict future events. |
|
Types of Questions Answered |
Descriptive questions (What happened?). |
Diagnostic (Why did it happen?), predictive (What will happen?), and prescriptive (What should we do?) questions. |
|
Data Visualization vs. Data Modeling |
Emphasis on data visualization through dashboards and reports. |
Focus on data modeling and statistical analysis to create predictive models. |
|
Use Cases |
Routine reporting, performance monitoring, and standard operational reporting. |
Complex problem-solving, strategic decision-making, financial forecasting, customer segmentation, supply chain optimization, and more. |
This table provides a clear overview of the key distinctions between Business Intelligence and Business Analytics solutions.
Popular Open Source Analytics Tools
-
R:
-
Description: R is a versatile programming language and environment specifically designed for statistical computing and data analysis. It offers a wide array of packages and libraries for data manipulation, visualization, and advanced statistical modeling.
-
Use Cases: R is popular among statisticians, data scientists, and researchers for tasks such as data exploration, hypothesis testing, regression analysis, and creating custom data visualizations.
-
Key Features: It provides extensive libraries for data analysis (e.g., dplyr, tidyr), data visualization (ggplot2), and machine learning (caret). R's interactive console allows users to explore and analyze data interactively.
-
Community: R has a vibrant and active community that contributes to package development and provides support through forums and mailing lists.
-
-
Python:
-
Description: Python is a versatile, easy-to-learn programming language with a thriving ecosystem for data analysis, machine learning, and web development. It is known for its simplicity and readability.
-
Use Cases: Python is used for data cleaning, manipulation, visualization, machine learning, and web scraping. Popular libraries include Pandas, Matplotlib, Seaborn, scikit-learn, and TensorFlow.
-
Key Features: Python's simplicity makes it accessible to beginners, and its vast library of packages makes it suitable for a wide range of data tasks. Jupyter notebooks enable interactive data exploration and documentation.
-
Community: Python boasts a large and active community, offering extensive documentation, tutorials, and support resources.
-
-
Apache Hadoop:
-
Description: Apache Hadoop is an open-source framework for distributed storage and processing of large datasets across a cluster of commodity hardware.
-
Use Cases: Hadoop is primarily used for big data processing and distributed storage. It is essential for organizations dealing with massive volumes of structured and unstructured data.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for distributed storage and MapReduce for distributed data processing. It can handle diverse data types and is scalable.
-
Community: Hadoop has a robust community, and it has given rise to numerous other big data tools and technologies.
-
-
Apache Spark:
-
Description: Apache Spark is an open-source big data processing framework known for its speed, versatility, and real-time processing capabilities.
-
Use Cases: Spark is used for big data processing, machine learning, graph processing, and real-time analytics. It's known for its efficiency and support for diverse data workloads.
-
Key Features: Spark's in-memory processing makes it faster than Hadoop's MapReduce. It provides high-level APIs in Python, Scala, and Java, along with libraries for machine learning (MLlib) and graph processing (GraphX).
-
Community: Spark has a thriving community and a rich ecosystem of libraries and tools.
-
-
KNIME:
-
Description: KNIME (Konstanz Information Miner) is an open-source platform for data analytics, reporting, and integration that uses a visual workflow interface.
-
Use Cases: KNIME is used for data preprocessing, analysis, reporting, and machine learning. It is designed to be accessible to both technical and non-technical users.
-
Key Features: KNIME's visual interface allows users to create data analysis workflows without coding. It supports integration with various data sources, offers extensions and plugins, and provides collaboration features.
-
Community: KNIME has an active community that contributes to its development, provides support, and shares workflows and extensions.
-
-
Orange:
-
Description: Orange is an open-source data visualization and analysis tool that focuses on visual programming for data exploration, analysis, and machine learning.
-
Use Cases: Orange is used for data preprocessing, data visualization, clustering, classification, and regression. It is known for its user-friendly, drag-and-drop interface.
-
Key Features: Orange provides a wide range of data visualization widgets and analysis components. Users can experiment with data and build machine learning models without programming.
-
Community: Orange has an active community of users and contributors, and it offers extensive documentation and tutorials.
-
-
Jupyter Notebook:
-
Description: Jupyter Notebook is an open-source web application that enables users to create and share documents containing live code, equations, visualizations, and narrative text.
-
Use Cases: Jupyter Notebook is used for interactive data analysis, data exploration, code prototyping, and creating reproducible research documents.
-
Key Features: It supports multiple programming languages, including Python, R, Julia, and others. Users can combine code, data, visualizations, and explanations in a single interactive document.
-
Community: Jupyter has a thriving community and is widely adopted in data science and research fields.
-
-
Grafana:
-
Description: Originally designed for monitoring and observability, Grafana is an open-source platform for creating interactive and customizable dashboards for data visualization.
-
Use Cases: Grafana is used for real-time data visualization, monitoring system performance, and creating interactive dashboards for various data sources.
-
Key Features: Grafana supports connections to databases, cloud services, and data sources. It offers a range of visualization options, alerting capabilities, and templating for building dynamic dashboards.
-
Community: Grafana has a growing community, and its plugins and extensions enhance its functionality.
-
-
Metabase:
-
Description: Metabase is an open-source business intelligence and analytics tool designed for simplicity and accessibility.
-
Use Cases: Metabase is used for querying and visualizing data, creating dashboards, and generating ad-hoc reports, particularly by non-technical users.
-
Key Features: It provides an intuitive and user-friendly interface for data exploration. Metabase connects to various data sources and offers features for sharing and collaboration.
-
Community: Metabase has an active community and a user-friendly setup process.
-
-
Apache Superset:
-
Description: Apache Superset is an open-source data exploration and visualization platform initially developed by Airbnb.
-
Use Cases: Superset is used for creating interactive and shareable dashboards, exploring data, and ad-hoc querying from various data sources.
-
Key Features: Superset offers a user-friendly interface with a drag-and-drop dashboard builder. It supports multiple chart types, data source connectors, and customization options.
-
Community: Superset has an active and growing community and is part of the Apache Software Foundation.
-
These open-source analytics tools cover a wide range of data analysis and visualization needs, from statistical modeling to big data processing and business intelligence. Users can select the tool that best aligns with their specific goals, expertise, and data-related tasks.
Career Options in Business Analytics
A career in business analytics offers an exciting and dynamic journey into the world of data-driven decision-making. At its core, business analytics involves the systematic analysis of data to uncover insights and trends that can guide an organization's strategic and operational choices. Data analysts are often the first step in this process, responsible for collecting, cleaning, and organizing data from various sources. They use tools like SQL and Excel to transform raw data into structured datasets, enabling further analysis.
Moving up the ladder, business intelligence analysts specialize in creating visually appealing reports and dashboards that convey complex data findings to non-technical stakeholders. They use specialized BI tools like Tableau and Power BI to present historical data in a way that is easy to understand, helping organizations make informed decisions based on past performance.
For those who want to dive deeper into data exploration and predictive modeling, data scientists and machine learning engineers come into play. Data scientists leverage advanced statistical and machine learning techniques to extract valuable insights and predict future trends from data. They might build recommendation systems, forecast sales, or optimize marketing campaigns. Machine learning engineers, on the other hand, focus on implementing machine learning models in production environments, ensuring they can scale and perform efficiently.
In essence, a career in business analytics offers a pathway for individuals with various skill sets and interests to contribute to organizations' success by harnessing the power of data. Whether you prefer data wrangling and visualization, predictive modeling, or building data-driven solutions, there's a role in business analytics that aligns with your expertise and passion.
But How Do You Start Your Career and Land a High-Paying Job?
To kickstart your career as a business analyst, the essential step is acquiring the right skill sets. You can begin today by exploring and enrolling in iCert Global’s innovative, interactive, and career-focused In Business Analysis (CCBA,CBAP,ECBA) Certifications. This program offers training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.. Start your journey towards becoming a business analyst today!
Conclusion
In conclusion, a career in business analytics is an exciting and lucrative path for those who are passionate about data and its transformative power in decision-making. To embark on this journey, one must focus on acquiring the necessary skills through education, online courses, and certifications. Building a strong portfolio of projects and networking with professionals in the field are also critical steps. Landing a high-paying job in business analytics requires dedication, continuous learning, and effective job search strategies.
Remember that the field is dynamic, with opportunities spanning data analysis, business intelligence, data science, and more. By staying updated with industry trends and honing your expertise, you can not only start but also thrive in a rewarding career as a business analyst. It's a field where your ability to unlock insights from data can make a significant impact on organizations across various industries. So, take that first step, invest in your skills, and embark on your journey towards a successful career in business analytics.
How to obtain AI and Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info@icertglobal.com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Emerging Technologies :
AI in Manufacturing: Here's Everything You Should Know
The world of manufacturing is in the midst of a technological revolution, and at the heart of this transformation lies Artificial Intelligence (AI). From predictive maintenance that keeps machines running smoothly to quality control systems that ensure every product meets impeccable standards, AI is redefining the manufacturing landscape. It's not just about automation; it's about creating more efficient, agile, and competitive manufacturing processes. In this blog, we'll take a deep dive into the realm of AI in manufacturing, uncovering its applications, benefits, challenges, and future potential. Whether you're a seasoned industry professional or simply curious about how AI is reshaping the factory floor, here's everything you should know about AI's role in modern manufacturing.
Table of Contents
What Is AI in Manufacturing?
Key AI Segments That Impact Manufacturing
How is AI Used in the Manufacturing Industry?
Role of AI in the Industrial Sector
AI in Manufacturing
Choose the Right Program
Conclusion
What Is AI in Manufacturing?
AI in manufacturing refers to the integration of artificial intelligence technologies into various aspects of the manufacturing process to enhance efficiency, productivity, and decision-making. It encompasses the use of advanced algorithms, machine learning, computer vision, and data analytics to automate tasks, make predictions, and optimize operations within a manufacturing environment. This application of AI empowers manufacturers to streamline production, improve product quality, and reduce costs.
One of the key applications of AI in manufacturing is predictive maintenance, where AI algorithms analyze data from sensors and historical performance to predict when equipment or machinery is likely to fail. This allows for timely maintenance, reducing unplanned downtime and preventing costly breakdowns. Additionally, AI is employed in quality control through computer vision systems that inspect and identify defects in products in real-time, ensuring that only high-quality items are shipped to customers. Furthermore, AI aids in supply chain optimization by analyzing demand patterns and inventory levels, enabling manufacturers to meet customer demands efficiently while minimizing excess inventory.
In summary, AI in manufacturing represents a technological revolution that leverages artificial intelligence to enhance various aspects of the manufacturing process. By harnessing the power of AI, manufacturers can achieve greater efficiency, improve product quality, and ultimately remain competitive in a rapidly evolving industry.
Key AI Segments That Impact Manufacturing
AI has a profound impact on manufacturing across various segments, transforming the industry in several ways. Here are the key AI segments that have a significant influence on manufacturing:
-
Predictive Maintenance: Predictive maintenance uses AI and machine learning algorithms to predict when equipment or machinery is likely to fail. By analyzing data from sensors and historical performance, manufacturers can schedule maintenance proactively, reducing unplanned downtime and costly repairs.
-
Quality Control and Inspection: AI-powered computer vision systems are employed for real-time quality control and inspection of products on the manufacturing line. These systems can detect defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are produced and shipped to customers.
-
Supply Chain Optimization: AI plays a crucial role in optimizing the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to ensure that they have the right materials on hand, minimize excess inventory, and streamline distribution.
-
Process Automation: Robotics and automation powered by AI are increasingly used for repetitive and labor-intensive tasks in manufacturing. These AI-driven robots can work with precision and consistency, reducing the need for human intervention in certain processes and improving efficiency.
-
Energy Management: AI algorithms can monitor energy consumption within manufacturing facilities and make real-time adjustments to optimize energy usage. This not only reduces energy costs but also contributes to sustainability efforts.
-
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is particularly valuable in industries like automotive and consumer electronics, where personalization is in demand.
-
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
-
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This improves worker efficiency, training, and safety.
-
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems, allowing for simulation, testing, and optimization before making changes to the actual production line. This reduces downtime and risk during process improvements.
-
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
How is AI Used in the Manufacturing Industry?
AI is used in the manufacturing industry across various domains to enhance efficiency, productivity, and decision-making. Here's how AI is applied in manufacturing:
Predictive Maintenance: AI analyzes data from sensors and historical performance to predict when equipment or machinery is likely to fail. This enables manufacturers to schedule maintenance proactively, reducing unplanned downtime and preventing costly breakdowns.
Quality Control and Inspection: AI-powered computer vision systems inspect products on the manufacturing line in real-time. They identify defects, anomalies, and deviations from quality standards, ensuring that only high-quality products are produced and shipped to customers.
Supply Chain Optimization: AI optimizes the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to minimize excess inventory, optimize distribution, and ensure efficient supply chain operations.
Process Automation: Robotics and automation powered by AI are employed for repetitive and labor-intensive tasks. These AI-driven robots work with precision and consistency, reducing the need for human intervention in certain processes and improving overall efficiency.
Energy Management: AI algorithms monitor and control energy consumption within manufacturing facilities. They make real-time adjustments to optimize energy usage, reducing energy costs and contributing to sustainability efforts.
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is valuable in industries where personalized products are in demand, such as automotive and consumer electronics.
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This enhances worker efficiency, training, and safety.
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems. Manufacturers can use these digital twins for simulation, testing, and optimization before implementing changes to the actual production line, reducing downtime and risk.
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
Role of AI in the Industrial Sector
AI plays a pivotal role in the industrial sector, transforming various aspects of operations, decision-making, and productivity. Here are some key roles of AI in the industrial sector:
-
Predictive Maintenance: AI analyzes data from sensors and machinery to predict when equipment is likely to fail. This enables proactive maintenance, reducing downtime, and preventing costly breakdowns. It also extends the lifespan of industrial equipment.
-
Quality Control and Inspection: AI-powered computer vision systems can inspect and evaluate the quality of products in real-time. They detect defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are manufactured and shipped.
-
Process Optimization: AI optimizes industrial processes by analyzing data and making real-time adjustments. This can lead to increased efficiency, reduced energy consumption, and improved overall productivity in manufacturing and industrial operations.
-
Supply Chain Management: AI enhances supply chain management by analyzing vast amounts of data related to demand forecasting, inventory management, and logistics. Manufacturers can optimize their supply chains, ensuring that materials are available when needed and minimizing excess inventory.
-
Robotics and Automation: AI-driven robots and automation systems perform tasks with precision and consistency. They can handle repetitive and labor-intensive tasks, reducing the need for human labor and improving safety in industrial environments.
AI in Manufacturing
AI in manufacturing represents a transformative force that is revolutionizing the way goods are produced, monitored, and optimized in the manufacturing industry. It encompasses the integration of various artificial intelligence technologies, including machine learning, deep learning, computer vision, and natural language processing, into manufacturing processes and operations. Here's an overview of AI's role in manufacturing:
-
Predictive Maintenance: AI analyzes data from sensors and machinery to predict when equipment or machinery is likely to fail. This enables proactive maintenance, reducing unplanned downtime and minimizing costly repairs. Predictive maintenance extends the lifespan of equipment and maximizes its utilization.
-
Quality Control and Inspection: AI-powered computer vision systems are employed for real-time quality control and inspection of products on the manufacturing line. These systems can identify defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are produced and shipped.
-
Supply Chain Optimization: AI plays a critical role in optimizing the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to minimize excess inventory, optimize distribution, and ensure efficient supply chain operations.
-
Process Automation: Robotics and automation powered by AI are increasingly used for repetitive and labor-intensive tasks in manufacturing. These AI-driven robots can work with precision and consistency, reducing the need for human intervention in certain processes and improving overall efficiency.
-
Energy Efficiency: AI algorithms monitor and control energy consumption within manufacturing facilities, making real-time adjustments to optimize energy usage. This reduces energy costs and contributes to sustainability efforts.
-
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is particularly valuable in industries where personalized products are in demand, such as automotive and consumer electronics.
-
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
-
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This enhances worker efficiency, training, and safety.
-
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems. Manufacturers can use these digital twins for simulation, testing, and optimization before implementing changes to the actual production line, reducing downtime and risk.
-
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
Choose the Right Program
Selecting the right program or software for a specific task or purpose is essential to maximize efficiency and achieve your goals effectively. Here are some steps to help you choose the right program:
-
Define Your Needs and Goals:
-
Clearly outline what you want to accomplish with the program.
-
Identify the specific features and capabilities you require to meet your objectives.
-
Research and Comparison:
-
Conduct thorough research to find potential programs or software that align with your needs.
-
Create a list of options and compare them based on features, pricing, user reviews, and industry reputation.
-
Compatibility:
-
Ensure that the program is compatible with your operating system and hardware.
-
Check for any integration capabilities with other tools or software you currently use.
-
Ease of Use:
-
Consider the program's user-friendliness. Is it intuitive and easy to navigate?
-
Look for user guides, tutorials, and customer support options in case you need assistance.
-
Cost and Budget:
-
Evaluate the cost of the program, including any subscription fees, licensing costs, and potential hidden charges.
-
Determine whether the program fits within your budget.
-
Trial and Testing:
-
Whenever possible, take advantage of free trials or demos to test the program before making a commitment.
-
Use this opportunity to see how well it meets your needs and whether it aligns with your workflow.
-
User Feedback:
-
Read user reviews and testimonials to gain insights into the experiences of others who have used the program.
-
Pay attention to both positive and negative feedback to make an informed decision.
-
Scalability and Future Needs:
-
Consider whether the program can scale with your growing needs.
-
Think about your long-term goals and whether the software can support your evolving requirements.
-
Support and Updates:
-
Check for the availability of customer support, including email, phone, or chat support.
-
Determine the frequency of software updates and whether they address bug fixes and improvements.
-
Security and Privacy:
-
Ensure that the program adheres to security standards and regulations relevant to your industry.
-
Verify the program's data privacy policies to protect sensitive information.
Conclusion
AI in manufacturing is not just a buzzword; it's a transformative force that's reshaping the landscape of one of the world's most critical industries. As we've explored in this blog, AI's applications in manufacturing are wide-ranging and impactful.
From predictive maintenance that prevents costly downtimes to quality control systems that ensure impeccable product standards, AI is improving efficiency and product quality. It optimizes supply chains, streamlines processes, and enhances energy management, all contributing to cost savings and sustainability.
The customization and personalization capabilities of AI are redefining how products are made and how businesses interact with customers. AI-driven data analytics empower manufacturers to make data-driven decisions and stay competitive in rapidly changing markets.
As we look to the future, AI's role in manufacturing will only expand. From digital twins and augmented reality to even more advanced automation, AI promises to continue revolutionizing this crucial industry, ensuring its adaptability and resilience in the face of evolving challenges. Embracing AI in manufacturing is not just about keeping up; it's about thriving in an era of unprecedented technological progress.
How to obtain AI and Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info@icertglobal.com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Emerging Technologies :
Read More
The world of manufacturing is in the midst of a technological revolution, and at the heart of this transformation lies Artificial Intelligence (AI). From predictive maintenance that keeps machines running smoothly to quality control systems that ensure every product meets impeccable standards, AI is redefining the manufacturing landscape. It's not just about automation; it's about creating more efficient, agile, and competitive manufacturing processes. In this blog, we'll take a deep dive into the realm of AI in manufacturing, uncovering its applications, benefits, challenges, and future potential. Whether you're a seasoned industry professional or simply curious about how AI is reshaping the factory floor, here's everything you should know about AI's role in modern manufacturing.
Table of Contents
What Is AI in Manufacturing?
Key AI Segments That Impact Manufacturing
How is AI Used in the Manufacturing Industry?
Role of AI in the Industrial Sector
AI in Manufacturing
Choose the Right Program
Conclusion
What Is AI in Manufacturing?
AI in manufacturing refers to the integration of artificial intelligence technologies into various aspects of the manufacturing process to enhance efficiency, productivity, and decision-making. It encompasses the use of advanced algorithms, machine learning, computer vision, and data analytics to automate tasks, make predictions, and optimize operations within a manufacturing environment. This application of AI empowers manufacturers to streamline production, improve product quality, and reduce costs.
One of the key applications of AI in manufacturing is predictive maintenance, where AI algorithms analyze data from sensors and historical performance to predict when equipment or machinery is likely to fail. This allows for timely maintenance, reducing unplanned downtime and preventing costly breakdowns. Additionally, AI is employed in quality control through computer vision systems that inspect and identify defects in products in real-time, ensuring that only high-quality items are shipped to customers. Furthermore, AI aids in supply chain optimization by analyzing demand patterns and inventory levels, enabling manufacturers to meet customer demands efficiently while minimizing excess inventory.
In summary, AI in manufacturing represents a technological revolution that leverages artificial intelligence to enhance various aspects of the manufacturing process. By harnessing the power of AI, manufacturers can achieve greater efficiency, improve product quality, and ultimately remain competitive in a rapidly evolving industry.
Key AI Segments That Impact Manufacturing
AI has a profound impact on manufacturing across various segments, transforming the industry in several ways. Here are the key AI segments that have a significant influence on manufacturing:
-
Predictive Maintenance: Predictive maintenance uses AI and machine learning algorithms to predict when equipment or machinery is likely to fail. By analyzing data from sensors and historical performance, manufacturers can schedule maintenance proactively, reducing unplanned downtime and costly repairs.
-
Quality Control and Inspection: AI-powered computer vision systems are employed for real-time quality control and inspection of products on the manufacturing line. These systems can detect defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are produced and shipped to customers.
-
Supply Chain Optimization: AI plays a crucial role in optimizing the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to ensure that they have the right materials on hand, minimize excess inventory, and streamline distribution.
-
Process Automation: Robotics and automation powered by AI are increasingly used for repetitive and labor-intensive tasks in manufacturing. These AI-driven robots can work with precision and consistency, reducing the need for human intervention in certain processes and improving efficiency.
-
Energy Management: AI algorithms can monitor energy consumption within manufacturing facilities and make real-time adjustments to optimize energy usage. This not only reduces energy costs but also contributes to sustainability efforts.
-
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is particularly valuable in industries like automotive and consumer electronics, where personalization is in demand.
-
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
-
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This improves worker efficiency, training, and safety.
-
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems, allowing for simulation, testing, and optimization before making changes to the actual production line. This reduces downtime and risk during process improvements.
-
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
How is AI Used in the Manufacturing Industry?
AI is used in the manufacturing industry across various domains to enhance efficiency, productivity, and decision-making. Here's how AI is applied in manufacturing:
Predictive Maintenance: AI analyzes data from sensors and historical performance to predict when equipment or machinery is likely to fail. This enables manufacturers to schedule maintenance proactively, reducing unplanned downtime and preventing costly breakdowns.
Quality Control and Inspection: AI-powered computer vision systems inspect products on the manufacturing line in real-time. They identify defects, anomalies, and deviations from quality standards, ensuring that only high-quality products are produced and shipped to customers.
Supply Chain Optimization: AI optimizes the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to minimize excess inventory, optimize distribution, and ensure efficient supply chain operations.
Process Automation: Robotics and automation powered by AI are employed for repetitive and labor-intensive tasks. These AI-driven robots work with precision and consistency, reducing the need for human intervention in certain processes and improving overall efficiency.
Energy Management: AI algorithms monitor and control energy consumption within manufacturing facilities. They make real-time adjustments to optimize energy usage, reducing energy costs and contributing to sustainability efforts.
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is valuable in industries where personalized products are in demand, such as automotive and consumer electronics.
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This enhances worker efficiency, training, and safety.
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems. Manufacturers can use these digital twins for simulation, testing, and optimization before implementing changes to the actual production line, reducing downtime and risk.
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
Role of AI in the Industrial Sector
AI plays a pivotal role in the industrial sector, transforming various aspects of operations, decision-making, and productivity. Here are some key roles of AI in the industrial sector:
-
Predictive Maintenance: AI analyzes data from sensors and machinery to predict when equipment is likely to fail. This enables proactive maintenance, reducing downtime, and preventing costly breakdowns. It also extends the lifespan of industrial equipment.
-
Quality Control and Inspection: AI-powered computer vision systems can inspect and evaluate the quality of products in real-time. They detect defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are manufactured and shipped.
-
Process Optimization: AI optimizes industrial processes by analyzing data and making real-time adjustments. This can lead to increased efficiency, reduced energy consumption, and improved overall productivity in manufacturing and industrial operations.
-
Supply Chain Management: AI enhances supply chain management by analyzing vast amounts of data related to demand forecasting, inventory management, and logistics. Manufacturers can optimize their supply chains, ensuring that materials are available when needed and minimizing excess inventory.
-
Robotics and Automation: AI-driven robots and automation systems perform tasks with precision and consistency. They can handle repetitive and labor-intensive tasks, reducing the need for human labor and improving safety in industrial environments.
AI in Manufacturing
AI in manufacturing represents a transformative force that is revolutionizing the way goods are produced, monitored, and optimized in the manufacturing industry. It encompasses the integration of various artificial intelligence technologies, including machine learning, deep learning, computer vision, and natural language processing, into manufacturing processes and operations. Here's an overview of AI's role in manufacturing:
-
Predictive Maintenance: AI analyzes data from sensors and machinery to predict when equipment or machinery is likely to fail. This enables proactive maintenance, reducing unplanned downtime and minimizing costly repairs. Predictive maintenance extends the lifespan of equipment and maximizes its utilization.
-
Quality Control and Inspection: AI-powered computer vision systems are employed for real-time quality control and inspection of products on the manufacturing line. These systems can identify defects, deviations from quality standards, and anomalies, ensuring that only high-quality products are produced and shipped.
-
Supply Chain Optimization: AI plays a critical role in optimizing the supply chain by analyzing data related to demand forecasting, inventory management, and logistics. Manufacturers can use AI-driven insights to minimize excess inventory, optimize distribution, and ensure efficient supply chain operations.
-
Process Automation: Robotics and automation powered by AI are increasingly used for repetitive and labor-intensive tasks in manufacturing. These AI-driven robots can work with precision and consistency, reducing the need for human intervention in certain processes and improving overall efficiency.
-
Energy Efficiency: AI algorithms monitor and control energy consumption within manufacturing facilities, making real-time adjustments to optimize energy usage. This reduces energy costs and contributes to sustainability efforts.
-
Customization and Personalization: AI enables mass customization of products by tailoring manufacturing processes to individual customer preferences. This is particularly valuable in industries where personalized products are in demand, such as automotive and consumer electronics.
-
Data Analytics and Insights: AI processes and analyzes vast amounts of data generated by manufacturing operations. This data-driven approach helps manufacturers identify patterns, trends, and opportunities for improvement, leading to better decision-making and operational optimization.
-
Augmented Reality (AR) and Virtual Reality (VR): AR and VR, often powered by AI, provide workers with real-time information and guidance on the factory floor. This enhances worker efficiency, training, and safety.
-
Digital Twins: AI-driven digital twins create virtual replicas of physical manufacturing systems. Manufacturers can use these digital twins for simulation, testing, and optimization before implementing changes to the actual production line, reducing downtime and risk.
-
Human-Machine Collaboration: Collaborative robots (cobots) work alongside human workers, enhancing productivity and safety. AI algorithms ensure that these robots can adapt to changes in their environment and work safely with humans.
Choose the Right Program
Selecting the right program or software for a specific task or purpose is essential to maximize efficiency and achieve your goals effectively. Here are some steps to help you choose the right program:
-
Define Your Needs and Goals:
-
Clearly outline what you want to accomplish with the program.
-
Identify the specific features and capabilities you require to meet your objectives.
-
-
Research and Comparison:
-
Conduct thorough research to find potential programs or software that align with your needs.
-
Create a list of options and compare them based on features, pricing, user reviews, and industry reputation.
-
-
Compatibility:
-
Ensure that the program is compatible with your operating system and hardware.
-
Check for any integration capabilities with other tools or software you currently use.
-
-
Ease of Use:
-
Consider the program's user-friendliness. Is it intuitive and easy to navigate?
-
Look for user guides, tutorials, and customer support options in case you need assistance.
-
-
Cost and Budget:
-
Evaluate the cost of the program, including any subscription fees, licensing costs, and potential hidden charges.
-
Determine whether the program fits within your budget.
-
-
Trial and Testing:
-
Whenever possible, take advantage of free trials or demos to test the program before making a commitment.
-
Use this opportunity to see how well it meets your needs and whether it aligns with your workflow.
-
-
User Feedback:
-
Read user reviews and testimonials to gain insights into the experiences of others who have used the program.
-
Pay attention to both positive and negative feedback to make an informed decision.
-
-
Scalability and Future Needs:
-
Consider whether the program can scale with your growing needs.
-
Think about your long-term goals and whether the software can support your evolving requirements.
-
-
Support and Updates:
-
Check for the availability of customer support, including email, phone, or chat support.
-
Determine the frequency of software updates and whether they address bug fixes and improvements.
-
-
Security and Privacy:
-
Ensure that the program adheres to security standards and regulations relevant to your industry.
-
Verify the program's data privacy policies to protect sensitive information.
-
Conclusion
AI in manufacturing is not just a buzzword; it's a transformative force that's reshaping the landscape of one of the world's most critical industries. As we've explored in this blog, AI's applications in manufacturing are wide-ranging and impactful.
From predictive maintenance that prevents costly downtimes to quality control systems that ensure impeccable product standards, AI is improving efficiency and product quality. It optimizes supply chains, streamlines processes, and enhances energy management, all contributing to cost savings and sustainability.
The customization and personalization capabilities of AI are redefining how products are made and how businesses interact with customers. AI-driven data analytics empower manufacturers to make data-driven decisions and stay competitive in rapidly changing markets.
As we look to the future, AI's role in manufacturing will only expand. From digital twins and augmented reality to even more advanced automation, AI promises to continue revolutionizing this crucial industry, ensuring its adaptability and resilience in the face of evolving challenges. Embracing AI in manufacturing is not just about keeping up; it's about thriving in an era of unprecedented technological progress.
How to obtain AI and Deep Learning Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info@icertglobal.com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Emerging Technologies :
Navigating the Role of a Project Management Officer: Skills, Jobs, and Salary Trends in 2023
In the dynamic landscape of modern business, effective project management stands as a cornerstone of success. And at the heart of this intricate orchestration lies the Project Management Officer (PMO), a role of growing importance in organizations around the world. As we step into 2023, the role of the PMO has evolved into far more than just overseeing projects; it has become a strategic linchpin that ensures projects align with an organization's vision and goals.
In this comprehensive exploration, we delve into the realm of Project Management Officers, unveiling the intricate tapestry of their responsibilities, the key skills demanded in this evolving role, and the salary trends that will define the career landscape in 2023. Whether you are an aspiring PMO charting your career path or a seasoned professional seeking to stay at the forefront of industry trends, this exploration will guide you through the multifaceted world of PMOs and the vital role they play in shaping the future of project management.
Table of contents
-
Introduction to the Project Management Officer Role
-
Responsibilities of a PMO
-
Key Skills Required for a PMO
-
Educational and Certification Requirements
-
PMO Salary Trends in 2023
-
Tools and Technologies for PMOs
-
Career Path and Advancement for PMOs
-
Tips for Aspiring PMOs
-
Future Outlook for PMO Roles
-
Conclusion
Introduction to the Project Management Officer Role
The Project Management Officer, commonly known as the PMO, is the backbone of effective project management within organizations today. As businesses navigate increasingly complex projects, the PMO serves as the central orchestrator, ensuring that projects are executed efficiently and align with the company's strategic objectives. The PMO's responsibilities encompass governance, standardization, resource allocation, performance monitoring, risk management, and communication facilitation. By establishing best practices, maintaining project standards, and providing critical oversight, PMOs play a pivotal role in delivering successful projects on time and within budget. As businesses evolve and embrace technological advancements, PMOs are adapting to integrate innovative tools and methodologies into their practices, making the role of a Project Management Officer more vital than ever in the modern corporate landscape.
In the following sections of this blog, we will delve deeper into the specific functions and skills required for PMOs, explore the latest salary trends in 2023, and shed light on the promising career prospects awaiting those interested in pursuing or advancing within this dynamic and essential field. Whether you're considering a career as a PMO or seeking to understand the evolving role better, read on to gain comprehensive insights into the world of Project Management Officers.
Responsibilities of a PMO

-
Strategic support (sPMO): This involves providing operational support in projects by taking on the management of a project, executing defined subtasks, or providing project assistants. The sPMO plays a critical role in aligning project work with corporate strategy. They classify, select, prioritize, and, when necessary, terminate projects based on their strategic alignment.
-
Managing a multi-project environment / Resource management: The PMO's primary function is resource management, which includes maintaining a comprehensive overview of all projects and ensuring up-to-date and credible data. Within this context, decisions concerning scope, budgets, and resources are meticulously prepared, considering interdependencies between projects.
-
Project implementation / services: Within a PMO, the team also takes on project management roles, executes specific project tasks, or offers project assistance. This hands-on approach ensures that projects are implemented effectively and efficiently.
-
Training and coaching: In addition to project execution, the PMO focuses on developing the skills of project managers and process participants. They offer training and support within the field, and they may even provide career development paths for project managers.
-
Methods, processes and tools: Choosing and adapting project management methodologies and processes is a crucial responsibility of the PMO. They customize these methods to suit the specific needs of everyone involved within the company. The PMO also manages the selection, implementation, and maintenance of appropriate tools tailored to the different roles in project and portfolio management.
Key Skills Required for a PMO

Strategy & Leadership:
-
Strategic Thinking: PMOs need to align projects with the organization's strategic goals. They must think strategically to prioritize projects that contribute most effectively to these goals.
-
Leadership Skills: PMOs often provide guidance and direction to project managers and teams, making leadership skills vital for motivating and inspiring project stakeholders.
-
Change Management: Effective change management skills help PMOs navigate organizational shifts that often accompany project implementations.
University Culture:
-
Alignment with Objectives: Understanding and aligning project initiatives with the university's objectives and values is essential to ensure that projects are in harmony with the institution's mission.
-
Communication: Strong communication skills are necessary for conveying the importance of projects' alignment with university culture and objectives to stakeholders.
-
Collaboration: Building collaborative relationships with university stakeholders and different departments is crucial to foster cooperation and ensure projects' success.
Governance of Process:
-
Process Management: PMOs must have a deep understanding of project management processes and procedures to establish governance frameworks effectively.
-
Decision-Making: Being skilled in decision-making and delegation is essential for resolving conflicts and making critical choices that affect project outcomes.
-
Integration: PMOs should be adept at integrating project management processes seamlessly within the organization's existing systems and workflows.
Reporting:
-
Data Analysis: Strong analytical skills are necessary for interpreting project data and generating meaningful reports that support informed decision-making.
-
Communication of Results: PMOs must communicate project progress and outcomes effectively to stakeholders through clear and concise reporting.
-
KPI Tracking: Skill in identifying and tracking Key Performance Indicators (KPIs) is crucial for measuring project success and ensuring alignment with strategic goals.
Supporting Business Units:
-
Cross-Functional Understanding: PMOs should possess a broad understanding of various business units within the organization, including IT, finance, human resources, and more, to provide effective support.
-
Stakeholder Management: Managing relationships with business units and securing their support is essential for successful project execution and alignment with the organization's needs.
Processes & Tools:
-
Process Framework Knowledge: Proficiency in various project management methodologies and frameworks, such as Agile or Waterfall, is vital for implementing appropriate processes.
-
Portfolio Management: Understanding portfolio management frameworks helps PMOs make informed decisions about project selection, prioritization, and resource allocation.
-
Technological Proficiency: Familiarity with project management tools and software is necessary for efficiently managing project data and reporting.
Educational and Certification Requirements
Educational and certification requirements for a Project Management Officer (PMO) can vary depending on the organization, the specific role within the PMO, and the industry. However, here are some general guidelines for educational background and certifications that can be beneficial for aspiring PMOs:
Educational Requirements:
-
Bachelor's Degree: Many PMO positions require at least a bachelor's degree in a relevant field. Common degrees include business administration, project management, information technology, engineering, or a related discipline. Some PMOs may prefer candidates with master's degrees, especially for higher-level roles.
-
Relevant Coursework: Courses in project management, business management, leadership, finance, and communication can provide a strong educational foundation for a PMO role.
Certification Requirements:
-
Project Management Professional (PMP): Offered by the Project Management Institute (PMI), the PMP certification is one of the most recognized and respected certifications in the field of project management. It demonstrates a candidate's knowledge and expertise in project management methodologies and best practices.
-
Certified Associate in Project Management (CAPM): Also provided by PMI, the CAPM certification is suitable for individuals who are relatively new to project management and want to demonstrate their commitment to the field.
-
PRINCE2: PRINCE2 (Projects IN Controlled Environments) is a popular project management methodology, especially in Europe. Becoming PRINCE2 certified can be advantageous, particularly for PMOs working in organizations that follow this methodology.
-
Certified ScrumMaster (CSM): For PMOs working in Agile environments, the CSM certification from Scrum Alliance can be valuable. It demonstrates expertise in Agile principles and Scrum practices.
-
Certification in Portfolio Management (PfMP): Also offered by PMI, PfMP is designed for professionals involved in portfolio management, which is often a critical aspect of PMO responsibilities.
-
Certified Business Analysis Professional (CBAP): While not specific to project management, the CBAP certification can be beneficial for PMOs involved in business analysis and requirements gathering.
-
ITIL (Information Technology Infrastructure Library): ITIL certifications are relevant for PMOs in IT-focused organizations. They focus on IT service management best practices.
-
Change Management Certification: As PMOs often play a role in change management, certifications like Prosci's Certified Change Management Professional (CCMP) can be valuable.
PMO Salary Trends in 2023
The salary trends for Project Management Officers (PMOs) were generally on an upward trajectory due to the growing recognition of the critical role they play in effective project management. In 2023, it is reasonable to expect that this trend will continue, with salaries for PMOs being influenced by factors such as location, industry, experience, and the specific responsibilities of the role. High-demand industries like technology, healthcare, and finance often offer competitive salaries for PMOs, especially in major metropolitan areas where the cost of living is higher. Additionally, PMOs with specialized skills or certifications such as PMP (Project Management Professional) or experience in agile methodologies may command higher salaries.
It's important for PMO professionals to stay updated with the latest industry insights and consult reliable sources, such as industry reports and professional networks, to gain a more accurate understanding of the salary landscape in 2023. Furthermore, the ongoing evolution of project management practices and the integration of technology into PMO functions may also impact salary trends, as organizations seek professionals who can adapt to these changes and deliver value through effective project management and portfolio oversight.
Tools and Technologies for PMOs
Project Management Officers (PMOs) rely on a variety of tools and technologies to streamline project management processes, enhance communication, and improve overall efficiency. Here are some essential tools and technologies commonly used by PMOs:
-
Project Management Software: PMOs often utilize project management software platforms such as Microsoft Project, Asana, Trello, Jira, or Monday.com to plan, track, and manage projects. These tools offer features like task assignment, timeline tracking, and progress reporting.
-
Portfolio Management Software: Portfolio management tools like Planview or CA PPM help PMOs manage multiple projects and prioritize them based on organizational goals and resource availability. They provide insights into project portfolios and help with resource allocation.
-
Collaboration Tools: Collaboration platforms such as Microsoft Teams, Slack, and Basecamp facilitate communication and collaboration among project teams. PMOs use these tools to share documents, hold meetings, and foster teamwork.
-
Document Management Systems: Systems like SharePoint and Google Workspace (formerly G Suite) are valuable for storing and organizing project documentation, contracts, reports, and other critical project-related files.
-
Data Analytics and Reporting Tools: Business intelligence tools like Tableau, Power BI, or Excel help PMOs analyze project data and create insightful reports and dashboards for stakeholders and decision-makers.
-
Resource Management Software: Resource management tools like ResourceFirst or Mavenlink assist PMOs in effectively allocating and tracking resources, including personnel, equipment, and budgetary resources.
-
Risk Management Software: Specialized risk management software, such as RiskWatch or LogicGate, can help PMOs identify, assess, and manage project risks efficiently.
-
Time Tracking and Timesheet Tools: Time tracking tools like Harvest or Clockify enable teams to record time spent on tasks, helping PMOs monitor project progress and allocate resources more effectively.
-
Budgeting and Financial Management Software: Financial management tools like QuickBooks, Xero, or dedicated project budgeting software assist PMOs in managing project finances, tracking expenses, and ensuring projects stay within budget.
-
Communication and Collaboration Platforms: Beyond chat and messaging apps, PMOs might use video conferencing tools like Zoom or Microsoft Teams for virtual meetings and webinars.
-
Issue and Change Management Tools: Issue tracking tools, such as Jira or ServiceNow, are essential for managing and documenting project issues, change requests, and resolutions.
-
Portfolio Analysis Tools: PMOs may employ tools like Sciforma or Meisterplan for in-depth portfolio analysis, including scenario planning and "what-if" analyses.
-
Workflow Automation: Workflow automation tools like Zapier or Microsoft Power Automate can streamline routine tasks and processes, reducing manual effort and improving efficiency.
PMOs should select tools and technologies that align with their organization's specific needs, project management methodologies, and budget constraints. The right combination of tools can significantly enhance the PMO's ability to manage projects, optimize resources, and deliver successful outcomes.
Career Path and Advancement for PMOs
A career path for Project Management Officers (PMOs) can be dynamic and rewarding, offering opportunities for advancement and specialization. Here's a typical career path and potential avenues for growth:
1. Entry-Level Roles:
-
Junior Project Coordinator or Project Assistant: Many PMOs begin their careers in entry-level positions, where they assist in project management tasks and gain practical experience.
2. Mid-Level Roles:
-
Project Manager: After accumulating experience and acquiring relevant certifications, PMOs may transition into project management roles, responsible for leading and executing projects.
-
Senior Project Manager: With further experience and proven leadership skills, PMs can progress to senior project manager roles, overseeing larger or more complex projects.
3. PMO Roles:
-
PMO Analyst: Junior PMOs often start as analysts, responsible for data analysis, reporting, and supporting PMO functions.
-
PMO Coordinator: PMO coordinators help manage project portfolios, resource allocation, and documentation within the PMO.
-
PMO Manager/Director: More experienced PMOs can advance to managerial or director roles within the PMO, responsible for overseeing the entire PMO function, setting strategic direction, and managing a team of project managers and analysts.
4. Specialization:
-
Portfolio Manager: Focusing on portfolio management, professionals can oversee the alignment of multiple projects with organizational objectives and resource allocation.
-
Risk Manager: Those with expertise in risk management may specialize in identifying, assessing, and mitigating project risks.
-
Agile Coach or Scrum Master: For those interested in Agile methodologies, becoming an Agile coach or Scrum Master is a potential career path.
-
PMO Consultant: Experienced PMOs may choose to work as consultants, advising organizations on PMO setup, optimization, and best practices.
5. Executive Leadership:
-
Chief Project Officer (CPO) or Head of PMO: At the highest level, PMOs can reach executive positions, where they play a strategic role in aligning projects with organizational goals and influencing the overall direction of the company.
Advancement Strategies:
-
Continuous Learning: Staying updated with the latest project management methodologies, technologies, and trends is crucial.
-
Networking: Building relationships within the industry, attending conferences, and joining professional associations can open doors to new opportunities.
-
Certifications: Earning certifications such as PMP, PfMP, or Agile certifications can enhance credibility and career prospects.
-
Leadership Development: Developing leadership skills through courses and mentorship can be essential for advancing into management roles.
-
Broadening Experience: Seeking diverse project management experiences, such as working on different types of projects or in various industries, can enrich one's skill set.
Advancement in a PMO career often involves a combination of experience, education, certifications, and networking. As PMOs gain expertise and take on more significant responsibilities, they can shape their careers to align with their interests and goals, whether that involves becoming a top-level executive or a subject matter expert in a specific area of project management.
Tips for Aspiring PMOs
If you aspire to become a Project Management Officer (PMO), it's essential to prepare and develop the skills and knowledge required for this dynamic role. Here are some valuable tips to help you on your path to becoming a successful PMO:
-
Understand Project Management Fundamentals: Start by building a strong foundation in project management principles, methodologies, and best practices. Consider enrolling in courses or pursuing certifications such as PMP (Project Management Professional) or CAPM (Certified Associate in Project Management) to demonstrate your commitment to the field.
-
Pursue Relevant Education: While not always mandatory, having a relevant educational background, such as a degree in business, project management, or a related field, can give you a competitive edge.
-
Gain Practical Experience: Look for entry-level positions or internships in project management or related roles. Practical experience is invaluable for understanding how projects work in real-world scenarios.
-
Develop Analytical Skills: PMOs often deal with data analysis, metrics, and reporting. Enhance your analytical skills to interpret project data effectively and make data-driven decisions.
-
Improve Communication Skills: Strong written and verbal communication skills are essential for conveying project information, reporting progress, and collaborating with various stakeholders.
-
Get Familiar with Technology: Become proficient in project management software, collaboration tools, and data analytics tools commonly used in the field.
-
Study PMO Frameworks: Familiarize yourself with different PMO frameworks and methodologies, such as PMBOK (Project Management Body of Knowledge) or PRINCE2 (Projects IN Controlled Environments).
-
Build Leadership and Teamwork Skills: PMOs often lead project teams and collaborate with diverse groups of people. Developing leadership and teamwork skills is crucial for success.
-
Network within the Industry: Attend project management conferences, join professional associations, and connect with professionals in the field. Networking can provide valuable insights, mentorship opportunities, and potential job leads.
-
Consider Specialization: Identify areas of project management that interest you the most, whether it's risk management, portfolio management, or Agile methodologies. Specializing in a particular area can help you stand out.
-
Stay Informed: Keep up to date with industry trends, emerging technologies, and changes in project management methodologies. Continuous learning is vital in this evolving field.
-
Seek Feedback and Mentorship: Request feedback on your work and seek mentorship from experienced PMOs or project managers. Learning from others can accelerate your development.
-
Demonstrate Adaptability: The role of a PMO can vary from organization to organization. Be adaptable and open to learning new approaches and methodologies to fit the needs of your employer.
-
Set Clear Career Goals: Define your career goals and create a plan to achieve them. This can help you stay focused and motivated as you work toward your desired PMO role.
-
Show Initiative: Take on additional responsibilities, volunteer for challenging projects, and demonstrate your commitment to the field. Initiative can set you apart from other candidates.
Remember that the path to becoming a PMO can be both challenging and rewarding. Be patient and persistent in your pursuit of this career, and continue to invest in your professional development to excel in the role of a Project Management Officer.
Future Outlook for PMO Roles
The future outlook for Project Management Officer (PMO) roles appears promising and transformative. PMOs are poised to play an increasingly strategic role in organizations, evolving from traditional project oversight to becoming key drivers of business success. This transformation will be underpinned by the integration of advanced technologies, such as artificial intelligence and data analytics, to enhance decision-making and project management processes. PMOs will focus on ensuring that project portfolios align with organizational goals and adapt to the dynamic landscape of project management methodologies, including Agile and hybrid approaches. As organizations continue to navigate complex projects in diverse industries, the demand for skilled PMOs is expected to grow, providing ample career opportunities and the chance to shape the future of project management.
Furthermore, the ongoing trend of remote work and the need for flexibility in project management will challenge PMOs to effectively manage distributed teams and leverage collaboration tools. Sustainability considerations and the increasing importance of change management in projects will also shape the evolving role of PMOs. To thrive in this changing landscape, aspiring PMOs should stay adaptable, invest in continuous learning, and build a strong foundation in project management principles while embracing the technological advancements that will define the future of the field.
Conclusion
In conclusion, the role of a Project Management Officer (PMO) is poised for a dynamic and promising future. PMOs are no longer just administrators of projects but have evolved into strategic leaders driving organizational success. As they embrace advanced technologies, agile methodologies, and data-driven decision-making, PMOs will continue to play a pivotal role in aligning projects with business objectives and optimizing resource management.
The evolving landscape of project management offers a multitude of opportunities for aspiring PMOs. To excel in this field, individuals must acquire a strong foundation in project management principles, invest in continuous learning, and stay adaptable to emerging trends. PMOs will find themselves at the forefront of organizational change, sustainability initiatives, and complex project management in various industries.
As organizations increasingly recognize the value of effective project management, PMOs will be instrumental in guiding them toward success. Their ability to navigate the evolving project management landscape, harness technology, and deliver strategic value will make them indispensable assets to organizations in the years to come.
RECOMMENDED POST:
Key Features of PMP® Certification Training
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Read More
In the dynamic landscape of modern business, effective project management stands as a cornerstone of success. And at the heart of this intricate orchestration lies the Project Management Officer (PMO), a role of growing importance in organizations around the world. As we step into 2023, the role of the PMO has evolved into far more than just overseeing projects; it has become a strategic linchpin that ensures projects align with an organization's vision and goals.
In this comprehensive exploration, we delve into the realm of Project Management Officers, unveiling the intricate tapestry of their responsibilities, the key skills demanded in this evolving role, and the salary trends that will define the career landscape in 2023. Whether you are an aspiring PMO charting your career path or a seasoned professional seeking to stay at the forefront of industry trends, this exploration will guide you through the multifaceted world of PMOs and the vital role they play in shaping the future of project management.
Table of contents
-
Introduction to the Project Management Officer Role
-
Responsibilities of a PMO
-
Key Skills Required for a PMO
-
Educational and Certification Requirements
-
PMO Salary Trends in 2023
-
Tools and Technologies for PMOs
-
Career Path and Advancement for PMOs
-
Tips for Aspiring PMOs
-
Future Outlook for PMO Roles
-
Conclusion
Introduction to the Project Management Officer Role
The Project Management Officer, commonly known as the PMO, is the backbone of effective project management within organizations today. As businesses navigate increasingly complex projects, the PMO serves as the central orchestrator, ensuring that projects are executed efficiently and align with the company's strategic objectives. The PMO's responsibilities encompass governance, standardization, resource allocation, performance monitoring, risk management, and communication facilitation. By establishing best practices, maintaining project standards, and providing critical oversight, PMOs play a pivotal role in delivering successful projects on time and within budget. As businesses evolve and embrace technological advancements, PMOs are adapting to integrate innovative tools and methodologies into their practices, making the role of a Project Management Officer more vital than ever in the modern corporate landscape.
In the following sections of this blog, we will delve deeper into the specific functions and skills required for PMOs, explore the latest salary trends in 2023, and shed light on the promising career prospects awaiting those interested in pursuing or advancing within this dynamic and essential field. Whether you're considering a career as a PMO or seeking to understand the evolving role better, read on to gain comprehensive insights into the world of Project Management Officers.
Responsibilities of a PMO
-
Strategic support (sPMO): This involves providing operational support in projects by taking on the management of a project, executing defined subtasks, or providing project assistants. The sPMO plays a critical role in aligning project work with corporate strategy. They classify, select, prioritize, and, when necessary, terminate projects based on their strategic alignment.
-
Managing a multi-project environment / Resource management: The PMO's primary function is resource management, which includes maintaining a comprehensive overview of all projects and ensuring up-to-date and credible data. Within this context, decisions concerning scope, budgets, and resources are meticulously prepared, considering interdependencies between projects.
-
Project implementation / services: Within a PMO, the team also takes on project management roles, executes specific project tasks, or offers project assistance. This hands-on approach ensures that projects are implemented effectively and efficiently.
-
Training and coaching: In addition to project execution, the PMO focuses on developing the skills of project managers and process participants. They offer training and support within the field, and they may even provide career development paths for project managers.
-
Methods, processes and tools: Choosing and adapting project management methodologies and processes is a crucial responsibility of the PMO. They customize these methods to suit the specific needs of everyone involved within the company. The PMO also manages the selection, implementation, and maintenance of appropriate tools tailored to the different roles in project and portfolio management.
Key Skills Required for a PMO
Strategy & Leadership:
-
Strategic Thinking: PMOs need to align projects with the organization's strategic goals. They must think strategically to prioritize projects that contribute most effectively to these goals.
-
Leadership Skills: PMOs often provide guidance and direction to project managers and teams, making leadership skills vital for motivating and inspiring project stakeholders.
-
Change Management: Effective change management skills help PMOs navigate organizational shifts that often accompany project implementations.
University Culture:
-
Alignment with Objectives: Understanding and aligning project initiatives with the university's objectives and values is essential to ensure that projects are in harmony with the institution's mission.
-
Communication: Strong communication skills are necessary for conveying the importance of projects' alignment with university culture and objectives to stakeholders.
-
Collaboration: Building collaborative relationships with university stakeholders and different departments is crucial to foster cooperation and ensure projects' success.
Governance of Process:
-
Process Management: PMOs must have a deep understanding of project management processes and procedures to establish governance frameworks effectively.
-
Decision-Making: Being skilled in decision-making and delegation is essential for resolving conflicts and making critical choices that affect project outcomes.
-
Integration: PMOs should be adept at integrating project management processes seamlessly within the organization's existing systems and workflows.
Reporting:
-
Data Analysis: Strong analytical skills are necessary for interpreting project data and generating meaningful reports that support informed decision-making.
-
Communication of Results: PMOs must communicate project progress and outcomes effectively to stakeholders through clear and concise reporting.
-
KPI Tracking: Skill in identifying and tracking Key Performance Indicators (KPIs) is crucial for measuring project success and ensuring alignment with strategic goals.
Supporting Business Units:
-
Cross-Functional Understanding: PMOs should possess a broad understanding of various business units within the organization, including IT, finance, human resources, and more, to provide effective support.
-
Stakeholder Management: Managing relationships with business units and securing their support is essential for successful project execution and alignment with the organization's needs.
Processes & Tools:
-
Process Framework Knowledge: Proficiency in various project management methodologies and frameworks, such as Agile or Waterfall, is vital for implementing appropriate processes.
-
Portfolio Management: Understanding portfolio management frameworks helps PMOs make informed decisions about project selection, prioritization, and resource allocation.
-
Technological Proficiency: Familiarity with project management tools and software is necessary for efficiently managing project data and reporting.
Educational and Certification Requirements
Educational and certification requirements for a Project Management Officer (PMO) can vary depending on the organization, the specific role within the PMO, and the industry. However, here are some general guidelines for educational background and certifications that can be beneficial for aspiring PMOs:
Educational Requirements:
-
Bachelor's Degree: Many PMO positions require at least a bachelor's degree in a relevant field. Common degrees include business administration, project management, information technology, engineering, or a related discipline. Some PMOs may prefer candidates with master's degrees, especially for higher-level roles.
-
Relevant Coursework: Courses in project management, business management, leadership, finance, and communication can provide a strong educational foundation for a PMO role.
Certification Requirements:
-
Project Management Professional (PMP): Offered by the Project Management Institute (PMI), the PMP certification is one of the most recognized and respected certifications in the field of project management. It demonstrates a candidate's knowledge and expertise in project management methodologies and best practices.
-
Certified Associate in Project Management (CAPM): Also provided by PMI, the CAPM certification is suitable for individuals who are relatively new to project management and want to demonstrate their commitment to the field.
-
PRINCE2: PRINCE2 (Projects IN Controlled Environments) is a popular project management methodology, especially in Europe. Becoming PRINCE2 certified can be advantageous, particularly for PMOs working in organizations that follow this methodology.
-
Certified ScrumMaster (CSM): For PMOs working in Agile environments, the CSM certification from Scrum Alliance can be valuable. It demonstrates expertise in Agile principles and Scrum practices.
-
Certification in Portfolio Management (PfMP): Also offered by PMI, PfMP is designed for professionals involved in portfolio management, which is often a critical aspect of PMO responsibilities.
-
Certified Business Analysis Professional (CBAP): While not specific to project management, the CBAP certification can be beneficial for PMOs involved in business analysis and requirements gathering.
-
ITIL (Information Technology Infrastructure Library): ITIL certifications are relevant for PMOs in IT-focused organizations. They focus on IT service management best practices.
-
Change Management Certification: As PMOs often play a role in change management, certifications like Prosci's Certified Change Management Professional (CCMP) can be valuable.
PMO Salary Trends in 2023
The salary trends for Project Management Officers (PMOs) were generally on an upward trajectory due to the growing recognition of the critical role they play in effective project management. In 2023, it is reasonable to expect that this trend will continue, with salaries for PMOs being influenced by factors such as location, industry, experience, and the specific responsibilities of the role. High-demand industries like technology, healthcare, and finance often offer competitive salaries for PMOs, especially in major metropolitan areas where the cost of living is higher. Additionally, PMOs with specialized skills or certifications such as PMP (Project Management Professional) or experience in agile methodologies may command higher salaries.
It's important for PMO professionals to stay updated with the latest industry insights and consult reliable sources, such as industry reports and professional networks, to gain a more accurate understanding of the salary landscape in 2023. Furthermore, the ongoing evolution of project management practices and the integration of technology into PMO functions may also impact salary trends, as organizations seek professionals who can adapt to these changes and deliver value through effective project management and portfolio oversight.
Tools and Technologies for PMOs
Project Management Officers (PMOs) rely on a variety of tools and technologies to streamline project management processes, enhance communication, and improve overall efficiency. Here are some essential tools and technologies commonly used by PMOs:
-
Project Management Software: PMOs often utilize project management software platforms such as Microsoft Project, Asana, Trello, Jira, or Monday.com to plan, track, and manage projects. These tools offer features like task assignment, timeline tracking, and progress reporting.
-
Portfolio Management Software: Portfolio management tools like Planview or CA PPM help PMOs manage multiple projects and prioritize them based on organizational goals and resource availability. They provide insights into project portfolios and help with resource allocation.
-
Collaboration Tools: Collaboration platforms such as Microsoft Teams, Slack, and Basecamp facilitate communication and collaboration among project teams. PMOs use these tools to share documents, hold meetings, and foster teamwork.
-
Document Management Systems: Systems like SharePoint and Google Workspace (formerly G Suite) are valuable for storing and organizing project documentation, contracts, reports, and other critical project-related files.
-
Data Analytics and Reporting Tools: Business intelligence tools like Tableau, Power BI, or Excel help PMOs analyze project data and create insightful reports and dashboards for stakeholders and decision-makers.
-
Resource Management Software: Resource management tools like ResourceFirst or Mavenlink assist PMOs in effectively allocating and tracking resources, including personnel, equipment, and budgetary resources.
-
Risk Management Software: Specialized risk management software, such as RiskWatch or LogicGate, can help PMOs identify, assess, and manage project risks efficiently.
-
Time Tracking and Timesheet Tools: Time tracking tools like Harvest or Clockify enable teams to record time spent on tasks, helping PMOs monitor project progress and allocate resources more effectively.
-
Budgeting and Financial Management Software: Financial management tools like QuickBooks, Xero, or dedicated project budgeting software assist PMOs in managing project finances, tracking expenses, and ensuring projects stay within budget.
-
Communication and Collaboration Platforms: Beyond chat and messaging apps, PMOs might use video conferencing tools like Zoom or Microsoft Teams for virtual meetings and webinars.
-
Issue and Change Management Tools: Issue tracking tools, such as Jira or ServiceNow, are essential for managing and documenting project issues, change requests, and resolutions.
-
Portfolio Analysis Tools: PMOs may employ tools like Sciforma or Meisterplan for in-depth portfolio analysis, including scenario planning and "what-if" analyses.
-
Workflow Automation: Workflow automation tools like Zapier or Microsoft Power Automate can streamline routine tasks and processes, reducing manual effort and improving efficiency.
PMOs should select tools and technologies that align with their organization's specific needs, project management methodologies, and budget constraints. The right combination of tools can significantly enhance the PMO's ability to manage projects, optimize resources, and deliver successful outcomes.
Career Path and Advancement for PMOs
A career path for Project Management Officers (PMOs) can be dynamic and rewarding, offering opportunities for advancement and specialization. Here's a typical career path and potential avenues for growth:
1. Entry-Level Roles:
-
Junior Project Coordinator or Project Assistant: Many PMOs begin their careers in entry-level positions, where they assist in project management tasks and gain practical experience.
2. Mid-Level Roles:
-
Project Manager: After accumulating experience and acquiring relevant certifications, PMOs may transition into project management roles, responsible for leading and executing projects.
-
Senior Project Manager: With further experience and proven leadership skills, PMs can progress to senior project manager roles, overseeing larger or more complex projects.
3. PMO Roles:
-
PMO Analyst: Junior PMOs often start as analysts, responsible for data analysis, reporting, and supporting PMO functions.
-
PMO Coordinator: PMO coordinators help manage project portfolios, resource allocation, and documentation within the PMO.
-
PMO Manager/Director: More experienced PMOs can advance to managerial or director roles within the PMO, responsible for overseeing the entire PMO function, setting strategic direction, and managing a team of project managers and analysts.
4. Specialization:
-
Portfolio Manager: Focusing on portfolio management, professionals can oversee the alignment of multiple projects with organizational objectives and resource allocation.
-
Risk Manager: Those with expertise in risk management may specialize in identifying, assessing, and mitigating project risks.
-
Agile Coach or Scrum Master: For those interested in Agile methodologies, becoming an Agile coach or Scrum Master is a potential career path.
-
PMO Consultant: Experienced PMOs may choose to work as consultants, advising organizations on PMO setup, optimization, and best practices.
5. Executive Leadership:
-
Chief Project Officer (CPO) or Head of PMO: At the highest level, PMOs can reach executive positions, where they play a strategic role in aligning projects with organizational goals and influencing the overall direction of the company.
Advancement Strategies:
-
Continuous Learning: Staying updated with the latest project management methodologies, technologies, and trends is crucial.
-
Networking: Building relationships within the industry, attending conferences, and joining professional associations can open doors to new opportunities.
-
Certifications: Earning certifications such as PMP, PfMP, or Agile certifications can enhance credibility and career prospects.
-
Leadership Development: Developing leadership skills through courses and mentorship can be essential for advancing into management roles.
-
Broadening Experience: Seeking diverse project management experiences, such as working on different types of projects or in various industries, can enrich one's skill set.
Advancement in a PMO career often involves a combination of experience, education, certifications, and networking. As PMOs gain expertise and take on more significant responsibilities, they can shape their careers to align with their interests and goals, whether that involves becoming a top-level executive or a subject matter expert in a specific area of project management.
Tips for Aspiring PMOs
If you aspire to become a Project Management Officer (PMO), it's essential to prepare and develop the skills and knowledge required for this dynamic role. Here are some valuable tips to help you on your path to becoming a successful PMO:
-
Understand Project Management Fundamentals: Start by building a strong foundation in project management principles, methodologies, and best practices. Consider enrolling in courses or pursuing certifications such as PMP (Project Management Professional) or CAPM (Certified Associate in Project Management) to demonstrate your commitment to the field.
-
Pursue Relevant Education: While not always mandatory, having a relevant educational background, such as a degree in business, project management, or a related field, can give you a competitive edge.
-
Gain Practical Experience: Look for entry-level positions or internships in project management or related roles. Practical experience is invaluable for understanding how projects work in real-world scenarios.
-
Develop Analytical Skills: PMOs often deal with data analysis, metrics, and reporting. Enhance your analytical skills to interpret project data effectively and make data-driven decisions.
-
Improve Communication Skills: Strong written and verbal communication skills are essential for conveying project information, reporting progress, and collaborating with various stakeholders.
-
Get Familiar with Technology: Become proficient in project management software, collaboration tools, and data analytics tools commonly used in the field.
-
Study PMO Frameworks: Familiarize yourself with different PMO frameworks and methodologies, such as PMBOK (Project Management Body of Knowledge) or PRINCE2 (Projects IN Controlled Environments).
-
Build Leadership and Teamwork Skills: PMOs often lead project teams and collaborate with diverse groups of people. Developing leadership and teamwork skills is crucial for success.
-
Network within the Industry: Attend project management conferences, join professional associations, and connect with professionals in the field. Networking can provide valuable insights, mentorship opportunities, and potential job leads.
-
Consider Specialization: Identify areas of project management that interest you the most, whether it's risk management, portfolio management, or Agile methodologies. Specializing in a particular area can help you stand out.
-
Stay Informed: Keep up to date with industry trends, emerging technologies, and changes in project management methodologies. Continuous learning is vital in this evolving field.
-
Seek Feedback and Mentorship: Request feedback on your work and seek mentorship from experienced PMOs or project managers. Learning from others can accelerate your development.
-
Demonstrate Adaptability: The role of a PMO can vary from organization to organization. Be adaptable and open to learning new approaches and methodologies to fit the needs of your employer.
-
Set Clear Career Goals: Define your career goals and create a plan to achieve them. This can help you stay focused and motivated as you work toward your desired PMO role.
-
Show Initiative: Take on additional responsibilities, volunteer for challenging projects, and demonstrate your commitment to the field. Initiative can set you apart from other candidates.
Remember that the path to becoming a PMO can be both challenging and rewarding. Be patient and persistent in your pursuit of this career, and continue to invest in your professional development to excel in the role of a Project Management Officer.
Future Outlook for PMO Roles
The future outlook for Project Management Officer (PMO) roles appears promising and transformative. PMOs are poised to play an increasingly strategic role in organizations, evolving from traditional project oversight to becoming key drivers of business success. This transformation will be underpinned by the integration of advanced technologies, such as artificial intelligence and data analytics, to enhance decision-making and project management processes. PMOs will focus on ensuring that project portfolios align with organizational goals and adapt to the dynamic landscape of project management methodologies, including Agile and hybrid approaches. As organizations continue to navigate complex projects in diverse industries, the demand for skilled PMOs is expected to grow, providing ample career opportunities and the chance to shape the future of project management.
Furthermore, the ongoing trend of remote work and the need for flexibility in project management will challenge PMOs to effectively manage distributed teams and leverage collaboration tools. Sustainability considerations and the increasing importance of change management in projects will also shape the evolving role of PMOs. To thrive in this changing landscape, aspiring PMOs should stay adaptable, invest in continuous learning, and build a strong foundation in project management principles while embracing the technological advancements that will define the future of the field.
Conclusion
In conclusion, the role of a Project Management Officer (PMO) is poised for a dynamic and promising future. PMOs are no longer just administrators of projects but have evolved into strategic leaders driving organizational success. As they embrace advanced technologies, agile methodologies, and data-driven decision-making, PMOs will continue to play a pivotal role in aligning projects with business objectives and optimizing resource management.
The evolving landscape of project management offers a multitude of opportunities for aspiring PMOs. To excel in this field, individuals must acquire a strong foundation in project management principles, invest in continuous learning, and stay adaptable to emerging trends. PMOs will find themselves at the forefront of organizational change, sustainability initiatives, and complex project management in various industries.
As organizations increasingly recognize the value of effective project management, PMOs will be instrumental in guiding them toward success. Their ability to navigate the evolving project management landscape, harness technology, and deliver strategic value will make them indispensable assets to organizations in the years to come.
RECOMMENDED POST:
Key Features of PMP® Certification Training
How To Qualify PM Experience In PMP Application Form
The Step By Step Procedure To Fill The Application Form
Do visit our Corporate Training to know more about core offerings for enterprises in empowering their workforce.
Download Free PMP® Exam Practice Test with 200 PMP® Questions.
Full-length PMP sample test with 200 PMP exam prep questions.
You may also be interested in Sample PMP® Exam Prep Questions before you download the Free PMP® Practice Test.
Download our Free PMP Brochure for more information.
iCert Global conducts Project Management, Quality Management, Business Analysis, Agile, Scrum, and DevOps Certification courses across various locations in the United States.
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1-713-287-1213 / +1-713-287-1214 or e-mail us at info {at} icertglobal {dot} com.
Project Management Training by iCert Global:
Quality Management Training by iCert Global:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training by iCert Global:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training by iCert Global:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training by iCert Global:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
Please Contact Us for more information about our professional certification training courses to accelerate your career in the new year. Wish you all the best for your learning initiatives in the new year.
Which certifications are you aiming to achieve in the New Year? Let us know your thoughts in the 'Comments' section below. Thank you.
Lean Methodology Essentials: A Guide with Examples
Welcome to "Lean Methodology Essentials: A Guide with Examples." In a world where businesses must continually innovate, optimize, and adapt to remain competitive, Lean Methodology has emerged as a transformative approach to achieving operational excellence. This guide serves as your essential companion on a journey into the heart of Lean, offering a clear and practical understanding of its principles, techniques, and real-world applications.
Lean Methodology is more than a management philosophy; it's a mindset that emphasizes efficiency, waste reduction, and a relentless focus on delivering value to customers. In the pages that follow, we will break down the core tenets of Lean, demystify its terminology, and provide you with concrete examples that illustrate how Lean principles can be implemented across various industries. Whether you are a seasoned professional seeking to refine your Lean expertise or a newcomer eager to embrace its principles, this guide equips you with the knowledge and tools to embark on a journey of continuous improvement, setting you on the path to organizational excellence.
Table of Contents
-
What is Lean Methodology?
-
How Did Lean Methodology Originate?
-
Fundamentals of Lean Methodology
-
What Makes the Lean Methodology Unique?
-
Pillars of Lean Methodology
-
Why Should You Choose Lean Methodology?
-
Lean Methodology in Software Development
-
Lean Methodology Examples
-
Master the Concepts of Lean Methodology Today
-
Conclusion
What is Lean Methodology?
Lean Methodology is a systematic approach to process improvement that aims to maximize customer value while minimizing waste. Rooted in the principles of efficiency and continuous improvement, Lean emphasizes the identification and elimination of non-value-added activities, streamlining processes for smoother flow, adopting a pull system based on actual customer demand, and the relentless pursuit of perfection. By optimizing operations and reducing waste in industries ranging from manufacturing to healthcare and software development, Lean Methodology enhances quality, efficiency, and customer satisfaction, making it a cornerstone of modern business improvement strategies.
How Did Lean Methodology Originate?
Lean Methodology, originating in post-World War II Japan, owes its genesis to the innovative response of Japanese manufacturers, particularly Toyota, to the challenging economic environment of the time. Scarce resources, a damaged infrastructure, and a competitive landscape compelled Japanese companies to devise more efficient and economical production methods. Central to Lean's origins is the Toyota Production System (TPS), developed by Taiichi Ohno and Shigeo Shingo in the mid-20th century. TPS emphasized core Lean principles such as Just-In-Time (JIT) production, which aimed to reduce waste by producing only what was needed when it was needed. Another foundational concept was continuous improvement (Kaizen), which encouraged ongoing refinement of processes to enhance efficiency and quality. This systematic approach revolutionized manufacturing by minimizing waste, optimizing resource utilization, and improving product quality.
The adoption of Lean principles extended beyond manufacturing and became a global phenomenon in the late 20th century as Western companies recognized its effectiveness in improving operational efficiency and product quality. Lean's success in industries such as automotive manufacturing led to its widespread application across various sectors, including healthcare, services, and software development. Lean's ability to adapt and deliver results in diverse fields is a testament to its universal appeal and the enduring legacy of its Japanese origins, which continue to shape modern approaches to process optimization and waste reduction.
Fundamentals of Lean Methodology
The fundamentals of Lean Methodology are rooted in a set of core principles and practices that aim to maximize value while minimizing waste. These principles guide organizations in their pursuit of operational excellence and continuous improvement. Here are the key fundamentals of Lean Methodology:
-
Value: Identify what is valuable from the customer's perspective. Value represents any activity or process step that directly contributes to meeting customer needs or requirements.
-
Value Stream Mapping: Analyze and map the entire value stream, which is the end-to-end sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: Optimize the flow of work or materials through the value stream. This involves reducing interruptions, delays, and excess inventory that can hinder the smooth progression of tasks. Creating a continuous flow is a key objective.
-
Pull: Implement a pull system, where work is initiated or products are produced based on actual customer demand. This contrasts with a push system, where items are produced in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Embrace a culture of continuous improvement (Kaizen) with the goal of achieving perfection, even though it may never be fully attainable. Continuously seek ways to eliminate waste, enhance processes, and deliver greater value to customers.
-
Customer Focus: Place the customer at the center of all decisions and activities. Understand customer needs and preferences to drive value creation.
-
Employee Involvement: Involve and empower employees at all levels of the organization to identify and solve problems, make improvements, and contribute to the Lean culture.
-
Standardization: Establish standardized work processes and procedures to ensure consistency, reduce variation, and enable easier identification of abnormalities.
-
Visual Management: Use visual cues and tools, such as Kanban boards and Andon systems, to make information and the status of processes readily visible, facilitating better communication and decision-making.
-
Waste Reduction: Identify and eliminate the eight types of waste in Lean, often remembered by the acronym "TIMWOODS":
-
Transportation
-
Inventory
-
Motion
-
Waiting
-
Overproduction
-
Overprocessing
-
Defects
-
Skills (underutilized)
-
Continuous Improvement: Promote a culture of continuous learning and improvement. Encourage teams to regularly assess processes, gather feedback, and make incremental changes to enhance efficiency and quality.
-
Respect for People: Recognize the value of every employee and treat them with respect. Lean encourages collaboration, teamwork, and the involvement of employees in decision-making.
By adhering to these fundamentals, organizations can achieve greater efficiency, improved quality, reduced costs, and increased customer satisfaction, making Lean Methodology a powerful approach for achieving operational excellence.
What Makes the Lean Methodology Unique?
The Lean Methodology is distinctive due to several key factors:
-
Customer-Centric Philosophy: Lean is fundamentally centered on delivering value to the customer. It places a primary focus on understanding and meeting customer needs, which drives all decision-making and process improvements.
-
Waste Elimination: A core principle of Lean is the systematic identification and elimination of waste in all forms, including overproduction, unnecessary inventory, defects, waiting times, and more. This relentless pursuit of waste reduction sets Lean apart from many other methodologies.
-
Continuous Improvement Culture: Lean fosters a culture of continuous improvement (Kaizen) throughout an organization. It encourages employees at all levels to continuously seek ways to enhance processes, products, and services, leading to ongoing innovation and optimization.
-
Pull System: Lean employs a pull system where work is initiated based on actual customer demand rather than pushing products or services onto the market. This minimizes overproduction and excess inventory, reducing waste and improving efficiency.
-
Visual Management: Lean uses visual tools like Kanban boards and Andon systems to make information and process status highly visible. This transparency enhances communication, problem-solving, and decision-making.
-
Respect for People: Lean places a strong emphasis on respecting and engaging employees. It recognizes that employees often hold valuable insights for process improvement and encourages their active participation in decision-making.
-
Standardization and Documentation: Lean promotes the development and documentation of standardized work processes and procedures. This ensures consistency, reduces variation, and simplifies problem identification and resolution.
-
Flow Optimization: Lean focuses on optimizing the flow of work or materials through a value stream. This minimizes interruptions, delays, and inefficiencies, creating a smoother and more efficient workflow.
-
Pursuit of Perfection: While perfection may be an aspirational goal, Lean embraces the concept as a continuous improvement objective. Organizations continually strive for higher levels of efficiency, quality, and customer satisfaction.
-
Global Applicability: Lean has transcended its origins in Japan and has been successfully applied across industries and geographies, demonstrating its universal applicability and effectiveness.
In summary, the Lean Methodology's unique characteristics include its customer-centricity, waste reduction focus, commitment to continuous improvement, pull-based systems, visual management practices, respect for people, and adaptability to various contexts. These features have contributed to Lean's widespread adoption and its reputation for driving efficiency, quality, and competitiveness in organizations worldwide.
Pillars of Lean Methodology
The "pillars" of Lean Methodology typically refer to the foundational principles and concepts that underpin the Lean approach to process improvement and waste reduction. While there isn't a universal agreement on a fixed set of pillars, the following are commonly recognized as the core pillars of Lean Methodology:
-
Value: Understanding and defining value from the customer's perspective is the first pillar of Lean. Value represents any activity or process step that directly contributes to meeting customer needs or requirements. Everything else is considered waste.
-
Value Stream Mapping: This pillar involves analyzing and mapping the entire value stream, which is the sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: The flow pillar emphasizes optimizing the flow of work or materials through the value stream. It aims to reduce interruptions, delays, and excess inventory that can impede the smooth progression of tasks.
-
Pull: The pull pillar involves implementing a pull system where work is initiated or products are produced based on actual customer demand. This contrasts with push systems, which produce items in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Perfection is the continuous improvement pillar of Lean. While perfection may be an unattainable ideal, Lean encourages organizations to relentlessly pursue it by continuously seeking ways to eliminate waste, improve processes, and deliver greater value to customers.
These five pillars are often represented as the foundation of Lean Thinking and provide the guiding principles for organizations to achieve greater efficiency, reduce waste, and enhance customer satisfaction. Additional concepts and tools, such as standardized work, visual management, and respect for people, are integrated into Lean practices to support these pillars and drive continuous improvement.
Why Should You Choose Lean Methodology?
Choosing Lean Methodology is a strategic decision for organizations seeking to thrive in today's competitive landscape. Lean's central focus on waste reduction, coupled with a relentless commitment to improving processes and delivering customer value, positions companies for sustainable success. By minimizing non-value-added activities, Lean enhances efficiency, reduces costs, and bolsters quality. It fosters a culture of continuous improvement, empowering employees at all levels to identify and address operational inefficiencies, ultimately driving innovation and adaptability. Lean is not confined to a specific industry, making it versatile and adaptable to diverse organizational contexts, from manufacturing to healthcare, services, and software development. Its global recognition and proven track record of delivering tangible results underscore its status as a transformative methodology for organizations striving to achieve operational excellence, customer satisfaction, and a competitive edge.
Lean Methodology in Software Development
Lean Methodology, when applied to software development, is often referred to as "Lean Software Development." It adapts the principles and practices of Lean thinking to the unique challenges of creating software products and managing software projects. Here are key aspects of Lean Software Development:
-
Customer Value: Lean Software Development starts by identifying and prioritizing customer value. It involves understanding user needs and focusing on features or functionalities that directly contribute to customer satisfaction and business goals.
-
Eliminating Waste: Lean principles of waste reduction are applied rigorously in software development. This includes reducing unnecessary code complexity, eliminating duplication, and avoiding overproduction of features that may not be needed.
-
Pull System: Lean Software Development often employs a pull system, where features or tasks are pulled into the development process based on real customer demand or project priorities. This prevents overloading teams with excessive work.
-
Continuous Improvement: Like other Lean applications, Lean Software Development encourages continuous improvement. Teams regularly review their processes and seek ways to streamline workflows, enhance collaboration, and reduce cycle times.
-
Small Batch Sizes: Lean promotes working in small, manageable batches. This means breaking down large projects into smaller, deliverable units, allowing for quicker feedback and adjustment.
-
Visual Management: Visual tools like Kanban boards are frequently used to make the status of work visible, helping teams track progress, identify bottlenecks, and manage their work effectively.
-
Lean Metrics: Lean Software Development relies on key performance indicators (KPIs) that measure the flow of work, cycle times, and other relevant metrics to identify areas for improvement.
-
Empowering Teams: Lean principles emphasize giving teams autonomy and responsibility. Teams are encouraged to self-organize, make decisions, and take ownership of their work.
-
Minimal Viable Product (MVP): Lean encourages the development of Minimum Viable Products that can be quickly delivered to customers for feedback. This iterative approach allows for faster learning and adaptation.
-
Customer Feedback Loop: Lean Software Development relies on frequent customer feedback to validate assumptions, refine requirements, and make course corrections. This feedback loop is essential for delivering software that aligns with customer expectations.
-
Respect for People: As with all Lean applications, Lean Software Development places a strong emphasis on respecting and valuing the contributions of team members, recognizing that they are essential to the success of the project.
By applying Lean principles to software development, organizations can achieve greater efficiency, reduce the risk of building unnecessary features, and deliver software products that align more closely with customer needs. It's an adaptable and effective approach that has gained popularity in Agile development methodologies, such as Scrum and Kanban, which incorporate Lean principles to varying degrees.
Lean Methodology Examples
Lean Methodology is applied across various industries and functions to optimize processes, reduce waste, and enhance overall efficiency. Here are some examples of Lean Methodology in action:
-
Manufacturing:
-
Toyota Production System (TPS): Toyota is often credited as the originator of Lean principles. TPS emphasizes Just-In-Time (JIT) production, pull systems, and continuous improvement to minimize waste, reduce inventory, and enhance production efficiency.
-
Healthcare:
-
Reducing Patient Wait Times: Lean principles have been applied in hospitals to reduce patient wait times, optimize appointment scheduling, and improve the efficiency of healthcare delivery.
-
Software Development:
-
Kanban: Software development teams often use Kanban boards to visualize and manage their work, limit work in progress (WIP), and optimize workflow processes.
-
Service Industry:
-
Lean Banking: Banks have applied Lean principles to streamline processes such as loan approvals, customer service, and account management, reducing wait times and improving customer satisfaction.
-
Supply Chain Management:
-
Lean Supply Chain: Organizations apply Lean principles to supply chain management to reduce excess inventory, eliminate bottlenecks, and improve overall supply chain efficiency.
-
Retail:
-
Inventory Management: Retailers use Lean principles to optimize inventory management, reducing carrying costs, minimizing stockouts, and ensuring products are available when customers need them.
-
Education:
-
Lean Education: Lean principles have been adapted to education to improve classroom processes, curriculum development, and administrative tasks, resulting in more efficient and effective educational institutions.
-
Construction:
-
Lean Construction: The construction industry has adopted Lean principles to optimize project planning, reduce project delays, eliminate waste, and enhance overall project management.
-
Aerospace and Aviation:
-
Lean Aerospace: Companies in the aerospace and aviation sectors use Lean principles to improve manufacturing processes, reduce production lead times, and increase aircraft production efficiency.
-
Food Industry:
-
Lean in Restaurants: Restaurants have implemented Lean practices to optimize kitchen processes, reduce food waste, and improve customer service.
-
Government:
-
Lean Government: Some government agencies have adopted Lean principles to streamline administrative processes, reduce paperwork, and enhance citizen services.
-
Small Businesses:
-
Lean Startup: Small businesses and startups often use Lean principles to validate business ideas, develop minimal viable products (MVPs), and iterate based on customer feedback.
Master the Concepts of Lean Methodology Today
Mastering the concepts of Lean Methodology requires a combination of study, practical application, and continuous learning. Here's a step-by-step guide to help you get started:
-
Study Lean Principles:
-
Begin by reading books and articles on Lean Methodology to understand its core principles and concepts. Some recommended books include "The Lean Startup" by Eric Ries and "Lean Thinking" by James P. Womack and Daniel T. Jones.
-
Enroll in Lean Training:
-
Consider enrolling in Lean training programs or workshops offered by accredited organizations. These programs provide structured learning and often include real-world case studies and exercises.
-
Online Courses and Tutorials:
-
Many online platforms offer free and paid courses on Lean Methodology. Websites like Coursera, edX, and LinkedIn Learning provide access to comprehensive courses on Lean principles and their application.
-
Certification:
-
If you're looking to establish your expertise, consider pursuing Lean certification. Organizations like the Lean Enterprise Institute (LEI) offer certification programs, including Lean Green Belt and Lean Black Belt certifications.
-
Practice Lean Tools and Techniques:
-
To truly understand Lean, apply its tools and techniques in real-world scenarios. Implement practices like value stream mapping, Kanban, and 5S in your workplace or personal projects.
-
Join Lean Communities:
-
Participate in Lean forums, online communities, and social media groups. Engaging with Lean practitioners and enthusiasts can provide valuable insights and opportunities for discussion.
-
Read Case Studies:
-
Read case studies and success stories of organizations that have effectively implemented Lean Methodology. Analyze their experiences and learn from their challenges and solutions.
-
Continuous Improvement:
-
Embrace the Lean philosophy of continuous improvement. Regularly assess your own processes and workflows, and apply Lean principles to make incremental enhancements.
-
Lean Workshops and Seminars:
-
Attend Lean workshops, seminars, and conferences to gain exposure to the latest developments in Lean Methodology and learn from industry experts.
-
Teach Others:
-
Teaching Lean concepts to others can deepen your own understanding. Consider sharing your knowledge through presentations, workshops, or writing articles or blog posts.
-
Problem-Solving Practice:
-
Lean is fundamentally about problem-solving. Practice structured problem-solving techniques like the PDCA (Plan-Do-Check-Act) cycle to address challenges effectively.
-
Stay Informed:
-
Stay updated on Lean trends, research, and best practices through books, journals, blogs, and industry publications.
-
Networking:
-
Build a network of Lean professionals and mentors who can offer guidance and support in your Lean journey.
-
Apply Lean to Your Life:
-
Extend Lean principles beyond the workplace. Apply them to personal projects, time management, and daily routines to enhance your problem-solving skills and efficiency.
Remember that mastering Lean Methodology is an ongoing process. It requires a commitment to continuous learning, experimentation, and the application of Lean principles in various contexts. As you gain experience and expertise, you'll be better equipped to drive operational excellence and improve processes in your organization or projects.
How to obtain the Lean Six Sigma Green Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Green Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, the fundamentals of Lean Methodology represent a powerful framework for organizations seeking to thrive in today's dynamic and competitive landscape. By understanding and applying the principles of value, waste reduction, continuous improvement, and customer-centricity, businesses can unlock remarkable benefits. The real-world examples showcased in this blog highlight the versatility of Lean, demonstrating its effectiveness across diverse industries, from manufacturing and healthcare to software development and services.
As we wrap up our exploration of Lean, it's important to remember that Lean is not a one-time initiative but a journey of ongoing improvement. Embracing a Lean mindset, fostering a culture of innovation, and empowering employees to identify and eliminate waste are essential for sustained success. By integrating Lean into the DNA of your organization, you can optimize processes, reduce costs, enhance quality, and ultimately deliver greater value to your customers, setting the stage for a prosperous and efficient future.
Read More
Welcome to "Lean Methodology Essentials: A Guide with Examples." In a world where businesses must continually innovate, optimize, and adapt to remain competitive, Lean Methodology has emerged as a transformative approach to achieving operational excellence. This guide serves as your essential companion on a journey into the heart of Lean, offering a clear and practical understanding of its principles, techniques, and real-world applications.
Lean Methodology is more than a management philosophy; it's a mindset that emphasizes efficiency, waste reduction, and a relentless focus on delivering value to customers. In the pages that follow, we will break down the core tenets of Lean, demystify its terminology, and provide you with concrete examples that illustrate how Lean principles can be implemented across various industries. Whether you are a seasoned professional seeking to refine your Lean expertise or a newcomer eager to embrace its principles, this guide equips you with the knowledge and tools to embark on a journey of continuous improvement, setting you on the path to organizational excellence.
Table of Contents
-
What is Lean Methodology?
-
How Did Lean Methodology Originate?
-
Fundamentals of Lean Methodology
-
What Makes the Lean Methodology Unique?
-
Pillars of Lean Methodology
-
Why Should You Choose Lean Methodology?
-
Lean Methodology in Software Development
-
Lean Methodology Examples
-
Master the Concepts of Lean Methodology Today
-
Conclusion
What is Lean Methodology?
Lean Methodology is a systematic approach to process improvement that aims to maximize customer value while minimizing waste. Rooted in the principles of efficiency and continuous improvement, Lean emphasizes the identification and elimination of non-value-added activities, streamlining processes for smoother flow, adopting a pull system based on actual customer demand, and the relentless pursuit of perfection. By optimizing operations and reducing waste in industries ranging from manufacturing to healthcare and software development, Lean Methodology enhances quality, efficiency, and customer satisfaction, making it a cornerstone of modern business improvement strategies.
How Did Lean Methodology Originate?
Lean Methodology, originating in post-World War II Japan, owes its genesis to the innovative response of Japanese manufacturers, particularly Toyota, to the challenging economic environment of the time. Scarce resources, a damaged infrastructure, and a competitive landscape compelled Japanese companies to devise more efficient and economical production methods. Central to Lean's origins is the Toyota Production System (TPS), developed by Taiichi Ohno and Shigeo Shingo in the mid-20th century. TPS emphasized core Lean principles such as Just-In-Time (JIT) production, which aimed to reduce waste by producing only what was needed when it was needed. Another foundational concept was continuous improvement (Kaizen), which encouraged ongoing refinement of processes to enhance efficiency and quality. This systematic approach revolutionized manufacturing by minimizing waste, optimizing resource utilization, and improving product quality.
The adoption of Lean principles extended beyond manufacturing and became a global phenomenon in the late 20th century as Western companies recognized its effectiveness in improving operational efficiency and product quality. Lean's success in industries such as automotive manufacturing led to its widespread application across various sectors, including healthcare, services, and software development. Lean's ability to adapt and deliver results in diverse fields is a testament to its universal appeal and the enduring legacy of its Japanese origins, which continue to shape modern approaches to process optimization and waste reduction.
Fundamentals of Lean Methodology
The fundamentals of Lean Methodology are rooted in a set of core principles and practices that aim to maximize value while minimizing waste. These principles guide organizations in their pursuit of operational excellence and continuous improvement. Here are the key fundamentals of Lean Methodology:
-
Value: Identify what is valuable from the customer's perspective. Value represents any activity or process step that directly contributes to meeting customer needs or requirements.
-
Value Stream Mapping: Analyze and map the entire value stream, which is the end-to-end sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: Optimize the flow of work or materials through the value stream. This involves reducing interruptions, delays, and excess inventory that can hinder the smooth progression of tasks. Creating a continuous flow is a key objective.
-
Pull: Implement a pull system, where work is initiated or products are produced based on actual customer demand. This contrasts with a push system, where items are produced in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Embrace a culture of continuous improvement (Kaizen) with the goal of achieving perfection, even though it may never be fully attainable. Continuously seek ways to eliminate waste, enhance processes, and deliver greater value to customers.
-
Customer Focus: Place the customer at the center of all decisions and activities. Understand customer needs and preferences to drive value creation.
-
Employee Involvement: Involve and empower employees at all levels of the organization to identify and solve problems, make improvements, and contribute to the Lean culture.
-
Standardization: Establish standardized work processes and procedures to ensure consistency, reduce variation, and enable easier identification of abnormalities.
-
Visual Management: Use visual cues and tools, such as Kanban boards and Andon systems, to make information and the status of processes readily visible, facilitating better communication and decision-making.
-
Waste Reduction: Identify and eliminate the eight types of waste in Lean, often remembered by the acronym "TIMWOODS":
-
Transportation
-
Inventory
-
Motion
-
Waiting
-
Overproduction
-
Overprocessing
-
Defects
-
Skills (underutilized)
-
-
Continuous Improvement: Promote a culture of continuous learning and improvement. Encourage teams to regularly assess processes, gather feedback, and make incremental changes to enhance efficiency and quality.
-
Respect for People: Recognize the value of every employee and treat them with respect. Lean encourages collaboration, teamwork, and the involvement of employees in decision-making.
By adhering to these fundamentals, organizations can achieve greater efficiency, improved quality, reduced costs, and increased customer satisfaction, making Lean Methodology a powerful approach for achieving operational excellence.
What Makes the Lean Methodology Unique?
The Lean Methodology is distinctive due to several key factors:
-
Customer-Centric Philosophy: Lean is fundamentally centered on delivering value to the customer. It places a primary focus on understanding and meeting customer needs, which drives all decision-making and process improvements.
-
Waste Elimination: A core principle of Lean is the systematic identification and elimination of waste in all forms, including overproduction, unnecessary inventory, defects, waiting times, and more. This relentless pursuit of waste reduction sets Lean apart from many other methodologies.
-
Continuous Improvement Culture: Lean fosters a culture of continuous improvement (Kaizen) throughout an organization. It encourages employees at all levels to continuously seek ways to enhance processes, products, and services, leading to ongoing innovation and optimization.
-
Pull System: Lean employs a pull system where work is initiated based on actual customer demand rather than pushing products or services onto the market. This minimizes overproduction and excess inventory, reducing waste and improving efficiency.
-
Visual Management: Lean uses visual tools like Kanban boards and Andon systems to make information and process status highly visible. This transparency enhances communication, problem-solving, and decision-making.
-
Respect for People: Lean places a strong emphasis on respecting and engaging employees. It recognizes that employees often hold valuable insights for process improvement and encourages their active participation in decision-making.
-
Standardization and Documentation: Lean promotes the development and documentation of standardized work processes and procedures. This ensures consistency, reduces variation, and simplifies problem identification and resolution.
-
Flow Optimization: Lean focuses on optimizing the flow of work or materials through a value stream. This minimizes interruptions, delays, and inefficiencies, creating a smoother and more efficient workflow.
-
Pursuit of Perfection: While perfection may be an aspirational goal, Lean embraces the concept as a continuous improvement objective. Organizations continually strive for higher levels of efficiency, quality, and customer satisfaction.
-
Global Applicability: Lean has transcended its origins in Japan and has been successfully applied across industries and geographies, demonstrating its universal applicability and effectiveness.
In summary, the Lean Methodology's unique characteristics include its customer-centricity, waste reduction focus, commitment to continuous improvement, pull-based systems, visual management practices, respect for people, and adaptability to various contexts. These features have contributed to Lean's widespread adoption and its reputation for driving efficiency, quality, and competitiveness in organizations worldwide.
Pillars of Lean Methodology
The "pillars" of Lean Methodology typically refer to the foundational principles and concepts that underpin the Lean approach to process improvement and waste reduction. While there isn't a universal agreement on a fixed set of pillars, the following are commonly recognized as the core pillars of Lean Methodology:
-
Value: Understanding and defining value from the customer's perspective is the first pillar of Lean. Value represents any activity or process step that directly contributes to meeting customer needs or requirements. Everything else is considered waste.
-
Value Stream Mapping: This pillar involves analyzing and mapping the entire value stream, which is the sequence of activities and processes that deliver a product or service to the customer. Value stream mapping helps identify bottlenecks, inefficiencies, and areas of waste.
-
Flow: The flow pillar emphasizes optimizing the flow of work or materials through the value stream. It aims to reduce interruptions, delays, and excess inventory that can impede the smooth progression of tasks.
-
Pull: The pull pillar involves implementing a pull system where work is initiated or products are produced based on actual customer demand. This contrasts with push systems, which produce items in anticipation of demand, often leading to overproduction and waste.
-
Perfection: Perfection is the continuous improvement pillar of Lean. While perfection may be an unattainable ideal, Lean encourages organizations to relentlessly pursue it by continuously seeking ways to eliminate waste, improve processes, and deliver greater value to customers.
These five pillars are often represented as the foundation of Lean Thinking and provide the guiding principles for organizations to achieve greater efficiency, reduce waste, and enhance customer satisfaction. Additional concepts and tools, such as standardized work, visual management, and respect for people, are integrated into Lean practices to support these pillars and drive continuous improvement.
Why Should You Choose Lean Methodology?
Choosing Lean Methodology is a strategic decision for organizations seeking to thrive in today's competitive landscape. Lean's central focus on waste reduction, coupled with a relentless commitment to improving processes and delivering customer value, positions companies for sustainable success. By minimizing non-value-added activities, Lean enhances efficiency, reduces costs, and bolsters quality. It fosters a culture of continuous improvement, empowering employees at all levels to identify and address operational inefficiencies, ultimately driving innovation and adaptability. Lean is not confined to a specific industry, making it versatile and adaptable to diverse organizational contexts, from manufacturing to healthcare, services, and software development. Its global recognition and proven track record of delivering tangible results underscore its status as a transformative methodology for organizations striving to achieve operational excellence, customer satisfaction, and a competitive edge.
Lean Methodology in Software Development
Lean Methodology, when applied to software development, is often referred to as "Lean Software Development." It adapts the principles and practices of Lean thinking to the unique challenges of creating software products and managing software projects. Here are key aspects of Lean Software Development:
-
Customer Value: Lean Software Development starts by identifying and prioritizing customer value. It involves understanding user needs and focusing on features or functionalities that directly contribute to customer satisfaction and business goals.
-
Eliminating Waste: Lean principles of waste reduction are applied rigorously in software development. This includes reducing unnecessary code complexity, eliminating duplication, and avoiding overproduction of features that may not be needed.
-
Pull System: Lean Software Development often employs a pull system, where features or tasks are pulled into the development process based on real customer demand or project priorities. This prevents overloading teams with excessive work.
-
Continuous Improvement: Like other Lean applications, Lean Software Development encourages continuous improvement. Teams regularly review their processes and seek ways to streamline workflows, enhance collaboration, and reduce cycle times.
-
Small Batch Sizes: Lean promotes working in small, manageable batches. This means breaking down large projects into smaller, deliverable units, allowing for quicker feedback and adjustment.
-
Visual Management: Visual tools like Kanban boards are frequently used to make the status of work visible, helping teams track progress, identify bottlenecks, and manage their work effectively.
-
Lean Metrics: Lean Software Development relies on key performance indicators (KPIs) that measure the flow of work, cycle times, and other relevant metrics to identify areas for improvement.
-
Empowering Teams: Lean principles emphasize giving teams autonomy and responsibility. Teams are encouraged to self-organize, make decisions, and take ownership of their work.
-
Minimal Viable Product (MVP): Lean encourages the development of Minimum Viable Products that can be quickly delivered to customers for feedback. This iterative approach allows for faster learning and adaptation.
-
Customer Feedback Loop: Lean Software Development relies on frequent customer feedback to validate assumptions, refine requirements, and make course corrections. This feedback loop is essential for delivering software that aligns with customer expectations.
-
Respect for People: As with all Lean applications, Lean Software Development places a strong emphasis on respecting and valuing the contributions of team members, recognizing that they are essential to the success of the project.
By applying Lean principles to software development, organizations can achieve greater efficiency, reduce the risk of building unnecessary features, and deliver software products that align more closely with customer needs. It's an adaptable and effective approach that has gained popularity in Agile development methodologies, such as Scrum and Kanban, which incorporate Lean principles to varying degrees.
Lean Methodology Examples
Lean Methodology is applied across various industries and functions to optimize processes, reduce waste, and enhance overall efficiency. Here are some examples of Lean Methodology in action:
-
Manufacturing:
-
Toyota Production System (TPS): Toyota is often credited as the originator of Lean principles. TPS emphasizes Just-In-Time (JIT) production, pull systems, and continuous improvement to minimize waste, reduce inventory, and enhance production efficiency.
-
-
Healthcare:
-
Reducing Patient Wait Times: Lean principles have been applied in hospitals to reduce patient wait times, optimize appointment scheduling, and improve the efficiency of healthcare delivery.
-
-
Software Development:
-
Kanban: Software development teams often use Kanban boards to visualize and manage their work, limit work in progress (WIP), and optimize workflow processes.
-
-
Service Industry:
-
Lean Banking: Banks have applied Lean principles to streamline processes such as loan approvals, customer service, and account management, reducing wait times and improving customer satisfaction.
-
-
Supply Chain Management:
-
Lean Supply Chain: Organizations apply Lean principles to supply chain management to reduce excess inventory, eliminate bottlenecks, and improve overall supply chain efficiency.
-
-
Retail:
-
Inventory Management: Retailers use Lean principles to optimize inventory management, reducing carrying costs, minimizing stockouts, and ensuring products are available when customers need them.
-
-
Education:
-
Lean Education: Lean principles have been adapted to education to improve classroom processes, curriculum development, and administrative tasks, resulting in more efficient and effective educational institutions.
-
-
Construction:
-
Lean Construction: The construction industry has adopted Lean principles to optimize project planning, reduce project delays, eliminate waste, and enhance overall project management.
-
-
Aerospace and Aviation:
-
Lean Aerospace: Companies in the aerospace and aviation sectors use Lean principles to improve manufacturing processes, reduce production lead times, and increase aircraft production efficiency.
-
-
Food Industry:
-
Lean in Restaurants: Restaurants have implemented Lean practices to optimize kitchen processes, reduce food waste, and improve customer service.
-
-
Government:
-
Lean Government: Some government agencies have adopted Lean principles to streamline administrative processes, reduce paperwork, and enhance citizen services.
-
-
Small Businesses:
-
Lean Startup: Small businesses and startups often use Lean principles to validate business ideas, develop minimal viable products (MVPs), and iterate based on customer feedback.
-
Master the Concepts of Lean Methodology Today
Mastering the concepts of Lean Methodology requires a combination of study, practical application, and continuous learning. Here's a step-by-step guide to help you get started:
-
Study Lean Principles:
-
Begin by reading books and articles on Lean Methodology to understand its core principles and concepts. Some recommended books include "The Lean Startup" by Eric Ries and "Lean Thinking" by James P. Womack and Daniel T. Jones.
-
-
Enroll in Lean Training:
-
Consider enrolling in Lean training programs or workshops offered by accredited organizations. These programs provide structured learning and often include real-world case studies and exercises.
-
-
Online Courses and Tutorials:
-
Many online platforms offer free and paid courses on Lean Methodology. Websites like Coursera, edX, and LinkedIn Learning provide access to comprehensive courses on Lean principles and their application.
-
-
Certification:
-
If you're looking to establish your expertise, consider pursuing Lean certification. Organizations like the Lean Enterprise Institute (LEI) offer certification programs, including Lean Green Belt and Lean Black Belt certifications.
-
-
Practice Lean Tools and Techniques:
-
To truly understand Lean, apply its tools and techniques in real-world scenarios. Implement practices like value stream mapping, Kanban, and 5S in your workplace or personal projects.
-
-
Join Lean Communities:
-
Participate in Lean forums, online communities, and social media groups. Engaging with Lean practitioners and enthusiasts can provide valuable insights and opportunities for discussion.
-
-
Read Case Studies:
-
Read case studies and success stories of organizations that have effectively implemented Lean Methodology. Analyze their experiences and learn from their challenges and solutions.
-
-
Continuous Improvement:
-
Embrace the Lean philosophy of continuous improvement. Regularly assess your own processes and workflows, and apply Lean principles to make incremental enhancements.
-
-
Lean Workshops and Seminars:
-
Attend Lean workshops, seminars, and conferences to gain exposure to the latest developments in Lean Methodology and learn from industry experts.
-
-
Teach Others:
-
Teaching Lean concepts to others can deepen your own understanding. Consider sharing your knowledge through presentations, workshops, or writing articles or blog posts.
-
-
Problem-Solving Practice:
-
Lean is fundamentally about problem-solving. Practice structured problem-solving techniques like the PDCA (Plan-Do-Check-Act) cycle to address challenges effectively.
-
-
Stay Informed:
-
Stay updated on Lean trends, research, and best practices through books, journals, blogs, and industry publications.
-
-
Networking:
-
Build a network of Lean professionals and mentors who can offer guidance and support in your Lean journey.
-
-
Apply Lean to Your Life:
-
Extend Lean principles beyond the workplace. Apply them to personal projects, time management, and daily routines to enhance your problem-solving skills and efficiency.
-
Remember that mastering Lean Methodology is an ongoing process. It requires a commitment to continuous learning, experimentation, and the application of Lean principles in various contexts. As you gain experience and expertise, you'll be better equipped to drive operational excellence and improve processes in your organization or projects.
How to obtain the Lean Six Sigma Green Belt certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Green Belt ,Lean Six Sigma Green Belt, Lean Six Sigma Black Belt
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
IT Service Management & Governance: COBIT, ISO
Conclusion
In conclusion, the fundamentals of Lean Methodology represent a powerful framework for organizations seeking to thrive in today's dynamic and competitive landscape. By understanding and applying the principles of value, waste reduction, continuous improvement, and customer-centricity, businesses can unlock remarkable benefits. The real-world examples showcased in this blog highlight the versatility of Lean, demonstrating its effectiveness across diverse industries, from manufacturing and healthcare to software development and services.
As we wrap up our exploration of Lean, it's important to remember that Lean is not a one-time initiative but a journey of ongoing improvement. Embracing a Lean mindset, fostering a culture of innovation, and empowering employees to identify and eliminate waste are essential for sustained success. By integrating Lean into the DNA of your organization, you can optimize processes, reduce costs, enhance quality, and ultimately deliver greater value to your customers, setting the stage for a prosperous and efficient future.
Salesforce Pardot: A Complete Overview, Pricing Breakdown, and Benefits Analysis
In today's fast-paced business landscape, effective marketing automation has become the cornerstone of successful customer engagement and lead nurturing. Among the multitude of tools available, Salesforce Pardot stands out as a powerful and versatile solution for businesses seeking to streamline their marketing efforts, personalize customer interactions, and ultimately drive growth.
In this blog post, we'll take a deep dive into Salesforce Pardot, exploring what it is, its key features, and the benefits it offers to businesses of all sizes and industries. We'll also delve into the pricing structure, helping you understand the investment required for incorporating Pardot into your marketing strategy.
Whether you're a seasoned marketer looking to enhance your automation capabilities or a business owner curious about the potential of marketing automation, this comprehensive guide will provide you with valuable insights to make informed decisions. Let's embark on this journey to discover Salesforce Pardot's incredible potential and the advantages it can bring to your marketing efforts.
Table of Contents
-
What is Salesforce Pardot
-
Benefits of Using Salesforce Pardot
-
Salesforce Pardot Pricing
-
Use Cases and Success Stories
-
Getting Started with Salesforce Pardot
-
Alternatives to Salesforce Pardot
-
Conclusion
What is Salesforce Pardot
Salesforce Pardot is a versatile marketing automation solution that empowers businesses to streamline their marketing efforts and engage with leads more effectively. With its robust features, Pardot enables businesses to automate various marketing tasks, such as email marketing, lead nurturing, and lead scoring. It facilitates personalized communication with leads, ensuring that the right message reaches the right audience at the right time. Furthermore, its seamless integration with Salesforce CRM enhances collaboration between marketing and sales teams, enabling a smoother lead handoff process. Pardot's analytics and reporting capabilities provide valuable insights, helping businesses refine their marketing strategies and boost ROI. Whether you're a small startup or a large enterprise, Pardot offers scalability and customization to meet your unique marketing automation needs.
One of the key strengths of Salesforce Pardot is its ability to deliver tangible benefits to businesses. By automating repetitive marketing tasks, it saves valuable time and resources, allowing marketing teams to focus on strategic activities. Its lead scoring and nurturing features increase the efficiency of lead management, ensuring that sales teams engage with leads that are more likely to convert. Pardot's data-driven approach enhances decision-making, as businesses can analyze campaign performance and make adjustments in real-time. Additionally, its integration with Salesforce CRM enhances customer relationship management, promoting a unified and efficient sales and marketing process. Overall, Salesforce Pardot is a powerful tool for businesses looking to drive revenue and improve marketing effectiveness through automation and data-driven insights.
Benefits of Using Salesforce Pardot
Using Salesforce Pardot offers a wide range of benefits to businesses seeking to enhance their marketing efforts, improve lead management, and drive revenue growth. Here are some key advantages of incorporating Salesforce Pardot into your marketing strategy:
-
Efficient Lead Generation and Nurturing: Pardot enables businesses to capture leads seamlessly through web forms, landing pages, and other channels. It also automates lead nurturing through personalized email campaigns, ensuring that leads are engaged and nurtured at every stage of the buyer's journey.
-
Improved Lead Scoring: With Pardot's lead scoring capabilities, you can prioritize leads based on their behavior and engagement with your content. This ensures that your sales team focuses their efforts on the most qualified leads, increasing conversion rates and sales efficiency.
-
Personalization: Pardot allows you to create highly targeted and personalized marketing campaigns. You can segment your audience based on various criteria, ensuring that each lead receives content tailored to their interests and needs.
-
Seamless CRM Integration: As part of the Salesforce ecosystem, Pardot seamlessly integrates with Salesforce CRM. This integration ensures that all lead and customer data is synchronized, providing a 360-degree view of your customers and prospects. It also streamlines the lead handoff process between marketing and sales teams.
-
Automation and Efficiency: Pardot automates various marketing tasks, such as email marketing, lead scoring, and lead assignment. This automation saves time and reduces the risk of human errors, allowing your marketing team to focus on strategic initiatives.
-
Advanced Analytics and Reporting: Pardot provides in-depth analytics and reporting tools to track the performance of your marketing campaigns. You can measure key metrics, such as email open rates, click-through rates, and conversion rates, and use these insights to refine your marketing strategies for better results.
-
Scalability: Pardot is scalable, making it suitable for businesses of all sizes. Whether you're a small startup or a large enterprise, you can customize Pardot to meet your specific marketing automation needs and scale as your business grows.
-
Enhanced Social Media Engagement: Pardot helps you manage and track your social media marketing efforts, allowing you to monitor social engagement and incorporate it into your lead nurturing strategies.
-
Cost Savings: By automating marketing tasks and improving lead conversion rates, Pardot can lead to cost savings in both time and resources. It maximizes the efficiency of your marketing team while delivering tangible results.
-
Competitive Advantage: Leveraging Pardot's advanced features can give your business a competitive edge in a crowded marketplace. It enables you to stay ahead of the curve in terms of marketing automation and customer engagement.
Salesforce Pardot Pricing
Salesforce Pardot offers various pricing tiers to accommodate the needs and budgets of different businesses. The pricing structure is typically based on the number of users, the number of contacts or leads you want to manage, and the features you require. It's important to note that pricing may change over time, so it's advisable to visit the Salesforce Pardot website or contact their sales team for the most up-to-date information.
Pardot Edition
Features Included
Starting Price (Approximate)*
Growth Edition
- Basic marketing automation
Starting at $1,250/month
- Email marketing
- Lead scoring
- CRM integration
Plus Edition
- Advanced email analytics
Starting at $2,500/month
- Dynamic content
- A/B testing
- CRM integration
Advanced Edition
- AI-powered analytics
Custom pricing
- Custom user roles
- Marketing assets
- CRM integration
Premium Edition
- Custom analytics
Custom pricing
- Event-based segmentation
- Advanced features tailored to needs
Add-Ons
- B2B Marketing Analytics (Additional)
Custom pricing
- Engagement History (Additional)
- Additional services, training, and support
*Note: Pricing is typically based on factors such as the number of contacts or leads and additional features and services required. Actual prices may vary depending on specific business needs.
Use Cases and Success Stories
Use Cases and Success Stories of Salesforce Pardot
Salesforce Pardot has been employed by businesses across various industries to achieve marketing automation excellence and drive significant results. Below are some use cases and success stories that showcase the versatility and impact of Pardot:
1. Lead Nurturing and Conversion: A technology company that sells complex software solutions used Salesforce Pardot to nurture leads and increase conversions. By creating personalized email campaigns and automating lead scoring, they reduced the sales cycle by 30%. This resulted in a 20% increase in revenue in the first year of implementing Pardot.
2. B2B E-commerce: An e-commerce company specializing in B2B sales adopted Pardot to better understand its customers' needs. By tracking customer interactions and using Pardot's lead scoring, they were able to send targeted product recommendations, leading to a 15% increase in upsell and cross-sell revenue.
3. Event Promotion: An event management company utilized Pardot for event promotion. They automated email marketing campaigns and personalized event invitations based on attendee preferences. This resulted in a 40% increase in event attendance and a 25% boost in post-event engagement.
4. Higher Education: A university employed Pardot to streamline its student recruitment efforts. By automating email communication and tracking prospect engagement, they achieved a 50% increase in the number of enrolled students. Pardot's integration with Salesforce CRM also improved communication between admissions and academic departments.
5. Healthcare: A healthcare organization implemented Pardot to improve patient engagement and appointment scheduling. They sent automated appointment reminders and health tips to patients, resulting in a 25% reduction in missed appointments and improved patient satisfaction.
6. Manufacturing: A manufacturing company used Pardot to enhance its distributor engagement. By automating lead nurturing and providing distributors with tailored marketing collateral, they saw a 30% increase in distributor-generated sales leads within six months.
7. Non-Profit Fundraising: A non-profit organization leveraged Pardot for donor outreach and fundraising campaigns. They personalized donation requests and automated follow-up emails. As a result, they experienced a 40% increase in online donations and donor retention rates.
8. Financial Services: A financial services firm integrated Pardot with its CRM to improve lead management. They automated lead assignment to financial advisors, resulting in a 15% increase in lead conversion rates and a 20% reduction in response time.
These use cases highlight the adaptability of Salesforce Pardot across different industries and functions. Whether it's lead nurturing, event promotion, student recruitment, healthcare engagement, distributor management, non-profit fundraising, or financial services, Pardot has consistently delivered tangible benefits such as increased revenue, improved customer engagement, and enhanced operational efficiency. These success stories underscore the effectiveness of Pardot in helping businesses achieve their marketing and sales objectives.
Getting Started with Salesforce Pardot
Getting started with Salesforce Pardot involves several key steps to ensure a successful implementation of the marketing automation platform. Here's a step-by-step guide on how to get started with Salesforce Pardot:
1. Set Clear Goals and Objectives:
-
Define your marketing automation goals and objectives. What do you aim to achieve with Pardot? Whether it's lead generation, lead nurturing, improving conversions, or increasing ROI, having clear goals will guide your implementation.
2. Sign Up for Pardot:
-
Visit the Salesforce Pardot website and sign up for the edition that best suits your business needs. You may also request a demo or contact Salesforce for more information.
3. Assign an Administrator:
-
Designate an internal administrator or team responsible for managing Pardot. This individual should be trained in Pardot's features and functionality.
4. Set Up Salesforce Integration:
-
If you're already using Salesforce CRM, ensure that Pardot is properly integrated with Salesforce. This step is crucial for syncing data between the two platforms seamlessly.
5. Define Your Lead Scoring Model:
-
Develop a lead scoring model that assigns values to various lead interactions and behaviors. This model helps prioritize leads for your sales team.
6. Import Your Contacts and Data:
-
Import your existing leads and contacts into Pardot. Ensure that data is clean, accurate, and well-segmented for effective targeting.
7. Create Landing Pages and Forms:
-
Build custom landing pages and forms to capture lead information. Pardot provides templates and a user-friendly interface for this purpose.
8. Design Email Templates:
-
Create email templates that align with your branding and messaging. Pardot allows for responsive and personalized email design.
9. Set Up Drip Campaigns:
-
Create automated drip email campaigns for lead nurturing. Map out the content and timing of these campaigns based on your lead's journey.
10. Implement Lead Scoring and Grading: - Configure lead scoring rules and grading criteria to identify the most engaged and qualified leads.
11. Test Automation Workflows: - Before going live, thoroughly test your automation workflows, including email sequences and landing page forms, to ensure they function as intended.
12. Train Your Team: - Provide training to your marketing and sales teams on how to use Pardot effectively. Ensure they understand lead management processes and how to interpret lead scoring data.
13. Monitor and Analyze: - Regularly monitor the performance of your campaigns and use Pardot's analytics and reporting tools to gain insights into what's working and what needs improvement.
14. Optimize and Iterate: - Continuously optimize your marketing strategies based on data and feedback. Adjust your automation workflows, content, and targeting as needed to achieve better results.
15. Seek Professional Assistance: - If needed, consider consulting with Salesforce Pardot experts or attending training sessions to maximize the value of the platform.
Remember that Salesforce Pardot is a powerful marketing automation tool, and its effectiveness often grows over time as you become more familiar with its features and capabilities. Regularly reviewing your strategies and adapting to changing market conditions will help you get the most out of Pardot and drive success in your marketing efforts.
Alternatives to Salesforce Pardot
There are several alternatives to Salesforce Pardot, each offering its own set of features and capabilities for marketing automation and lead management. The choice of an alternative depends on your specific business needs, budget, and existing technology stack. Here are some popular alternatives to Salesforce Pardot:
-
HubSpot Marketing Hub:
-
HubSpot offers a comprehensive suite of marketing tools, including automation, email marketing, lead nurturing, and analytics. It's known for its user-friendly interface and is suitable for both small businesses and larger enterprises.
-
Marketo:
-
Marketo, now part of Adobe Experience Cloud, provides a robust marketing automation platform. It's ideal for B2B marketers and offers features such as lead scoring, advanced analytics, and integration with Adobe's creative tools.
-
Mailchimp:
-
While traditionally known for email marketing, Mailchimp has expanded its offerings to include marketing automation features. It's a cost-effective solution for small to medium-sized businesses.
-
ActiveCampaign:
-
ActiveCampaign combines email marketing, automation, and CRM capabilities. It's known for its advanced automation features and is suitable for businesses of all sizes.
-
Eloqua (Oracle Marketing Cloud):
-
Oracle Eloqua is a high-end marketing automation solution with a focus on enterprise-level marketing. It offers advanced lead scoring, campaign orchestration, and robust analytics.
-
SharpSpring:
-
SharpSpring is a marketing automation platform that caters to agencies and small to medium-sized businesses. It offers email marketing, CRM integration, and lead tracking features.
-
GetResponse:
-
GetResponse provides email marketing, automation, and landing page creation tools. It's a versatile solution for businesses looking to automate marketing tasks.
-
Infusionsoft by Keap:
-
Infusionsoft (now part of Keap) is a small business-focused marketing automation platform that offers CRM, email marketing, and automation capabilities.
-
Zoho MarketingHub:
-
Zoho MarketingHub is part of the Zoho suite of business tools and offers marketing automation features, email marketing, and CRM integration.
-
SendinBlue:
-
SendinBlue offers email marketing, marketing automation, and transactional email services. It's known for its affordability and ease of use.
-
Drip:
-
Drip is an e-commerce-focused marketing automation platform that specializes in personalized email marketing and automation for online retailers.
When evaluating alternatives to Salesforce Pardot, consider factors such as the size of your business, your budget, your specific marketing automation needs, and how well the platform integrates with your existing software stack, including your CRM. Additionally, take advantage of free trials and demos to test the platforms and see which one aligns best with your goals and workflows.
How to obtain Salesforce Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Blockchain Certification
Salesforce : Salesforce Administration Certification
Conclusion
In conclusion, Salesforce Pardot presents a compelling solution for businesses seeking to elevate their marketing strategies through efficient automation. Its versatile feature set, encompassing lead generation, nurturing, and seamless CRM integration, offers tangible benefits such as increased lead conversion rates and streamlined processes. While Pardot's pricing structure varies to accommodate businesses of all sizes, its value lies in the potential for personalized engagement, data-driven insights, and scalable marketing campaigns, making it a noteworthy contender in the competitive landscape of marketing automation platforms.
Read More
In today's fast-paced business landscape, effective marketing automation has become the cornerstone of successful customer engagement and lead nurturing. Among the multitude of tools available, Salesforce Pardot stands out as a powerful and versatile solution for businesses seeking to streamline their marketing efforts, personalize customer interactions, and ultimately drive growth.
In this blog post, we'll take a deep dive into Salesforce Pardot, exploring what it is, its key features, and the benefits it offers to businesses of all sizes and industries. We'll also delve into the pricing structure, helping you understand the investment required for incorporating Pardot into your marketing strategy.
Whether you're a seasoned marketer looking to enhance your automation capabilities or a business owner curious about the potential of marketing automation, this comprehensive guide will provide you with valuable insights to make informed decisions. Let's embark on this journey to discover Salesforce Pardot's incredible potential and the advantages it can bring to your marketing efforts.
Table of Contents
-
What is Salesforce Pardot
-
Benefits of Using Salesforce Pardot
-
Salesforce Pardot Pricing
-
Use Cases and Success Stories
-
Getting Started with Salesforce Pardot
-
Alternatives to Salesforce Pardot
-
Conclusion
What is Salesforce Pardot
Salesforce Pardot is a versatile marketing automation solution that empowers businesses to streamline their marketing efforts and engage with leads more effectively. With its robust features, Pardot enables businesses to automate various marketing tasks, such as email marketing, lead nurturing, and lead scoring. It facilitates personalized communication with leads, ensuring that the right message reaches the right audience at the right time. Furthermore, its seamless integration with Salesforce CRM enhances collaboration between marketing and sales teams, enabling a smoother lead handoff process. Pardot's analytics and reporting capabilities provide valuable insights, helping businesses refine their marketing strategies and boost ROI. Whether you're a small startup or a large enterprise, Pardot offers scalability and customization to meet your unique marketing automation needs.
One of the key strengths of Salesforce Pardot is its ability to deliver tangible benefits to businesses. By automating repetitive marketing tasks, it saves valuable time and resources, allowing marketing teams to focus on strategic activities. Its lead scoring and nurturing features increase the efficiency of lead management, ensuring that sales teams engage with leads that are more likely to convert. Pardot's data-driven approach enhances decision-making, as businesses can analyze campaign performance and make adjustments in real-time. Additionally, its integration with Salesforce CRM enhances customer relationship management, promoting a unified and efficient sales and marketing process. Overall, Salesforce Pardot is a powerful tool for businesses looking to drive revenue and improve marketing effectiveness through automation and data-driven insights.
Benefits of Using Salesforce Pardot
Using Salesforce Pardot offers a wide range of benefits to businesses seeking to enhance their marketing efforts, improve lead management, and drive revenue growth. Here are some key advantages of incorporating Salesforce Pardot into your marketing strategy:
-
Efficient Lead Generation and Nurturing: Pardot enables businesses to capture leads seamlessly through web forms, landing pages, and other channels. It also automates lead nurturing through personalized email campaigns, ensuring that leads are engaged and nurtured at every stage of the buyer's journey.
-
Improved Lead Scoring: With Pardot's lead scoring capabilities, you can prioritize leads based on their behavior and engagement with your content. This ensures that your sales team focuses their efforts on the most qualified leads, increasing conversion rates and sales efficiency.
-
Personalization: Pardot allows you to create highly targeted and personalized marketing campaigns. You can segment your audience based on various criteria, ensuring that each lead receives content tailored to their interests and needs.
-
Seamless CRM Integration: As part of the Salesforce ecosystem, Pardot seamlessly integrates with Salesforce CRM. This integration ensures that all lead and customer data is synchronized, providing a 360-degree view of your customers and prospects. It also streamlines the lead handoff process between marketing and sales teams.
-
Automation and Efficiency: Pardot automates various marketing tasks, such as email marketing, lead scoring, and lead assignment. This automation saves time and reduces the risk of human errors, allowing your marketing team to focus on strategic initiatives.
-
Advanced Analytics and Reporting: Pardot provides in-depth analytics and reporting tools to track the performance of your marketing campaigns. You can measure key metrics, such as email open rates, click-through rates, and conversion rates, and use these insights to refine your marketing strategies for better results.
-
Scalability: Pardot is scalable, making it suitable for businesses of all sizes. Whether you're a small startup or a large enterprise, you can customize Pardot to meet your specific marketing automation needs and scale as your business grows.
-
Enhanced Social Media Engagement: Pardot helps you manage and track your social media marketing efforts, allowing you to monitor social engagement and incorporate it into your lead nurturing strategies.
-
Cost Savings: By automating marketing tasks and improving lead conversion rates, Pardot can lead to cost savings in both time and resources. It maximizes the efficiency of your marketing team while delivering tangible results.
-
Competitive Advantage: Leveraging Pardot's advanced features can give your business a competitive edge in a crowded marketplace. It enables you to stay ahead of the curve in terms of marketing automation and customer engagement.
Salesforce Pardot Pricing
Salesforce Pardot offers various pricing tiers to accommodate the needs and budgets of different businesses. The pricing structure is typically based on the number of users, the number of contacts or leads you want to manage, and the features you require. It's important to note that pricing may change over time, so it's advisable to visit the Salesforce Pardot website or contact their sales team for the most up-to-date information.
|
Pardot Edition |
Features Included |
Starting Price (Approximate)* |
|
Growth Edition |
- Basic marketing automation |
Starting at $1,250/month |
|
- Email marketing |
||
|
- Lead scoring |
||
|
- CRM integration |
||
|
Plus Edition |
- Advanced email analytics |
Starting at $2,500/month |
|
- Dynamic content |
||
|
- A/B testing |
||
|
- CRM integration |
||
|
Advanced Edition |
- AI-powered analytics |
Custom pricing |
|
- Custom user roles |
||
|
- Marketing assets |
||
|
- CRM integration |
||
|
Premium Edition |
- Custom analytics |
Custom pricing |
|
- Event-based segmentation |
||
|
- Advanced features tailored to needs |
||
|
Add-Ons |
- B2B Marketing Analytics (Additional) |
Custom pricing |
|
- Engagement History (Additional) |
||
|
- Additional services, training, and support |
*Note: Pricing is typically based on factors such as the number of contacts or leads and additional features and services required. Actual prices may vary depending on specific business needs.
Use Cases and Success Stories
Use Cases and Success Stories of Salesforce Pardot
Salesforce Pardot has been employed by businesses across various industries to achieve marketing automation excellence and drive significant results. Below are some use cases and success stories that showcase the versatility and impact of Pardot:
1. Lead Nurturing and Conversion: A technology company that sells complex software solutions used Salesforce Pardot to nurture leads and increase conversions. By creating personalized email campaigns and automating lead scoring, they reduced the sales cycle by 30%. This resulted in a 20% increase in revenue in the first year of implementing Pardot.
2. B2B E-commerce: An e-commerce company specializing in B2B sales adopted Pardot to better understand its customers' needs. By tracking customer interactions and using Pardot's lead scoring, they were able to send targeted product recommendations, leading to a 15% increase in upsell and cross-sell revenue.
3. Event Promotion: An event management company utilized Pardot for event promotion. They automated email marketing campaigns and personalized event invitations based on attendee preferences. This resulted in a 40% increase in event attendance and a 25% boost in post-event engagement.
4. Higher Education: A university employed Pardot to streamline its student recruitment efforts. By automating email communication and tracking prospect engagement, they achieved a 50% increase in the number of enrolled students. Pardot's integration with Salesforce CRM also improved communication between admissions and academic departments.
5. Healthcare: A healthcare organization implemented Pardot to improve patient engagement and appointment scheduling. They sent automated appointment reminders and health tips to patients, resulting in a 25% reduction in missed appointments and improved patient satisfaction.
6. Manufacturing: A manufacturing company used Pardot to enhance its distributor engagement. By automating lead nurturing and providing distributors with tailored marketing collateral, they saw a 30% increase in distributor-generated sales leads within six months.
7. Non-Profit Fundraising: A non-profit organization leveraged Pardot for donor outreach and fundraising campaigns. They personalized donation requests and automated follow-up emails. As a result, they experienced a 40% increase in online donations and donor retention rates.
8. Financial Services: A financial services firm integrated Pardot with its CRM to improve lead management. They automated lead assignment to financial advisors, resulting in a 15% increase in lead conversion rates and a 20% reduction in response time.
These use cases highlight the adaptability of Salesforce Pardot across different industries and functions. Whether it's lead nurturing, event promotion, student recruitment, healthcare engagement, distributor management, non-profit fundraising, or financial services, Pardot has consistently delivered tangible benefits such as increased revenue, improved customer engagement, and enhanced operational efficiency. These success stories underscore the effectiveness of Pardot in helping businesses achieve their marketing and sales objectives.
Getting Started with Salesforce Pardot
Getting started with Salesforce Pardot involves several key steps to ensure a successful implementation of the marketing automation platform. Here's a step-by-step guide on how to get started with Salesforce Pardot:
1. Set Clear Goals and Objectives:
-
Define your marketing automation goals and objectives. What do you aim to achieve with Pardot? Whether it's lead generation, lead nurturing, improving conversions, or increasing ROI, having clear goals will guide your implementation.
2. Sign Up for Pardot:
-
Visit the Salesforce Pardot website and sign up for the edition that best suits your business needs. You may also request a demo or contact Salesforce for more information.
3. Assign an Administrator:
-
Designate an internal administrator or team responsible for managing Pardot. This individual should be trained in Pardot's features and functionality.
4. Set Up Salesforce Integration:
-
If you're already using Salesforce CRM, ensure that Pardot is properly integrated with Salesforce. This step is crucial for syncing data between the two platforms seamlessly.
5. Define Your Lead Scoring Model:
-
Develop a lead scoring model that assigns values to various lead interactions and behaviors. This model helps prioritize leads for your sales team.
6. Import Your Contacts and Data:
-
Import your existing leads and contacts into Pardot. Ensure that data is clean, accurate, and well-segmented for effective targeting.
7. Create Landing Pages and Forms:
-
Build custom landing pages and forms to capture lead information. Pardot provides templates and a user-friendly interface for this purpose.
8. Design Email Templates:
-
Create email templates that align with your branding and messaging. Pardot allows for responsive and personalized email design.
9. Set Up Drip Campaigns:
-
Create automated drip email campaigns for lead nurturing. Map out the content and timing of these campaigns based on your lead's journey.
10. Implement Lead Scoring and Grading: - Configure lead scoring rules and grading criteria to identify the most engaged and qualified leads.
11. Test Automation Workflows: - Before going live, thoroughly test your automation workflows, including email sequences and landing page forms, to ensure they function as intended.
12. Train Your Team: - Provide training to your marketing and sales teams on how to use Pardot effectively. Ensure they understand lead management processes and how to interpret lead scoring data.
13. Monitor and Analyze: - Regularly monitor the performance of your campaigns and use Pardot's analytics and reporting tools to gain insights into what's working and what needs improvement.
14. Optimize and Iterate: - Continuously optimize your marketing strategies based on data and feedback. Adjust your automation workflows, content, and targeting as needed to achieve better results.
15. Seek Professional Assistance: - If needed, consider consulting with Salesforce Pardot experts or attending training sessions to maximize the value of the platform.
Remember that Salesforce Pardot is a powerful marketing automation tool, and its effectiveness often grows over time as you become more familiar with its features and capabilities. Regularly reviewing your strategies and adapting to changing market conditions will help you get the most out of Pardot and drive success in your marketing efforts.
Alternatives to Salesforce Pardot
There are several alternatives to Salesforce Pardot, each offering its own set of features and capabilities for marketing automation and lead management. The choice of an alternative depends on your specific business needs, budget, and existing technology stack. Here are some popular alternatives to Salesforce Pardot:
-
HubSpot Marketing Hub:
-
HubSpot offers a comprehensive suite of marketing tools, including automation, email marketing, lead nurturing, and analytics. It's known for its user-friendly interface and is suitable for both small businesses and larger enterprises.
-
-
Marketo:
-
Marketo, now part of Adobe Experience Cloud, provides a robust marketing automation platform. It's ideal for B2B marketers and offers features such as lead scoring, advanced analytics, and integration with Adobe's creative tools.
-
-
Mailchimp:
-
While traditionally known for email marketing, Mailchimp has expanded its offerings to include marketing automation features. It's a cost-effective solution for small to medium-sized businesses.
-
-
ActiveCampaign:
-
ActiveCampaign combines email marketing, automation, and CRM capabilities. It's known for its advanced automation features and is suitable for businesses of all sizes.
-
-
Eloqua (Oracle Marketing Cloud):
-
Oracle Eloqua is a high-end marketing automation solution with a focus on enterprise-level marketing. It offers advanced lead scoring, campaign orchestration, and robust analytics.
-
-
SharpSpring:
-
SharpSpring is a marketing automation platform that caters to agencies and small to medium-sized businesses. It offers email marketing, CRM integration, and lead tracking features.
-
-
GetResponse:
-
GetResponse provides email marketing, automation, and landing page creation tools. It's a versatile solution for businesses looking to automate marketing tasks.
-
-
Infusionsoft by Keap:
-
Infusionsoft (now part of Keap) is a small business-focused marketing automation platform that offers CRM, email marketing, and automation capabilities.
-
-
Zoho MarketingHub:
-
Zoho MarketingHub is part of the Zoho suite of business tools and offers marketing automation features, email marketing, and CRM integration.
-
-
SendinBlue:
-
SendinBlue offers email marketing, marketing automation, and transactional email services. It's known for its affordability and ease of use.
-
-
Drip:
-
Drip is an e-commerce-focused marketing automation platform that specializes in personalized email marketing and automation for online retailers.
-
When evaluating alternatives to Salesforce Pardot, consider factors such as the size of your business, your budget, your specific marketing automation needs, and how well the platform integrates with your existing software stack, including your CRM. Additionally, take advantage of free trials and demos to test the platforms and see which one aligns best with your goals and workflows.
How to obtain Salesforce Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Blockchain Certification
Salesforce : Salesforce Administration Certification
Conclusion
In conclusion, Salesforce Pardot presents a compelling solution for businesses seeking to elevate their marketing strategies through efficient automation. Its versatile feature set, encompassing lead generation, nurturing, and seamless CRM integration, offers tangible benefits such as increased lead conversion rates and streamlined processes. While Pardot's pricing structure varies to accommodate businesses of all sizes, its value lies in the potential for personalized engagement, data-driven insights, and scalable marketing campaigns, making it a noteworthy contender in the competitive landscape of marketing automation platforms.
Cloud Engineer Salary Trends: Freshers vs. Experienced
In the rapidly advancing domain of cloud computing, the role of a Cloud Engineer stands as a linchpin in modern tech operations. As businesses continue to embrace the benefits of cloud technologies, the demand for skilled professionals to design, manage, and optimize these infrastructures has soared. This has sparked a fascinating comparison between the salaries of freshers, those new to the cloud engineering scene, and experienced professionals who have weathered the dynamic landscape for some time.
This examination of "Cloud Engineer Salary Trends: Freshers vs. Experienced" embarks on a journey through the intricacies of compensation packages in the cloud engineering sphere. Whether you're a recent graduate, eager to step into this promising career path, or a seasoned expert, curious about how your experience impacts your earning potential, our exploration will dissect the factors that shape these trends. By shedding light on the compensation distinctions, we aim to empower both newcomers and veterans in the field to navigate their cloud engineering careers effectively, making informed decisions in this ever-evolving and rewarding landscape.
Table of Contents
What Does a Cloud Engineer Do?
Skills Required to Be a Cloud Engineer
Roles and Responsibilities of a Cloud Engineer
Companies That Hire Cloud Engineers
Cloud Engineer Salaries for Freshers and Experienced Professionals
FAQs
Choose The Right Cloud Computing Program
Conclusion
What Does a Cloud Engineer Do?
A Cloud Engineer is responsible for architecting, implementing, and maintaining an organization's cloud computing infrastructure. They design the cloud environment, selecting the most suitable cloud service providers and configuring resources to meet business needs. Cloud Engineers also focus on automation, using tools like Infrastructure as Code (IaC) to efficiently provision and manage cloud resources. Security is a top priority, as they establish robust security measures, monitor for threats, and ensure compliance with industry regulations. Additionally, they optimize cloud performance, manage costs, and collaborate with cross-functional teams to align cloud infrastructure with application requirements. In essence, Cloud Engineers are crucial for enabling businesses to leverage the benefits of cloud technology while ensuring reliability, security, and cost-effectiveness.
Continuous maintenance and improvement are key aspects of a Cloud Engineer's role. They regularly update and patch cloud systems, implement backup and disaster recovery plans to ensure data availability, and monitor cloud resources for performance and security. By staying abreast of emerging cloud technologies and best practices, Cloud Engineers help organizations harness the full potential of the cloud, driving innovation, scalability, and efficiency in their operations.
Skills Required to Be a Cloud Engineer
To excel as a Cloud Engineer, you need a diverse set of technical skills and non-technical skills. Here is a list of key skills required to be successful in this role:
1. Cloud Platform Proficiency: A deep understanding of one or more major cloud platforms like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), or others is essential. This includes knowledge of their services, capabilities, and pricing models.
2. Infrastructure as Code (IaC): Proficiency in IaC tools like Terraform, AWS CloudFormation, or Azure Resource Manager is crucial for automating the provisioning and management of cloud resources.
3. Networking: Knowledge of cloud networking concepts, including Virtual Private Cloud (VPC), subnets, load balancers, and VPN configurations, is necessary for designing and securing cloud architectures.
4. Security: An understanding of cloud security best practices, identity and access management (IAM), encryption, firewalls, and compliance standards is vital to protect cloud environments from cyber threats.
5. DevOps Tools: Familiarity with DevOps principles and tools such as Docker, Kubernetes, Jenkins, and Git is important for implementing continuous integration and continuous deployment (CI/CD) pipelines.
6. Scripting and Automation: Proficiency in scripting languages like Python, PowerShell, or Bash is essential for writing automation scripts and managing cloud resources programmatically.
7. Monitoring and Logging: Experience with monitoring and logging tools like Amazon CloudWatch, Azure Monitor, or Prometheus is necessary for tracking the health and performance of cloud services.
8. Database Management: Knowledge of cloud database services (e.g., AWS RDS, Azure SQL Database, Google Cloud SQL) and database administration skills are important for managing data in the cloud.
9. Cost Management: The ability to manage cloud costs effectively by analyzing usage patterns, optimizing resource allocation, and implementing cost-saving strategies is critical.
10. Troubleshooting and Problem Solving: Strong analytical and problem-solving skills are essential for identifying and resolving issues in cloud environments.
11. Collaboration: Effective communication and collaboration skills are vital for working with cross-functional teams, including developers, sysadmins, and security professionals.
12. Project Management: Basic project management skills can help Cloud Engineers plan and execute cloud projects effectively, ensuring they meet deadlines and objectives.
13. Continuous Learning: Cloud technology evolves rapidly, so a willingness to continuously learn and adapt to new tools and best practices is crucial to stay up-to-date in this field.
14. Soft Skills: Soft skills such as adaptability, teamwork, and attention to detail are important for working in a dynamic and collaborative environment.
Overall, Cloud Engineers need to combine technical expertise with a proactive and problem-solving mindset to design, implement, and manage robust and scalable cloud infrastructures that meet the needs of their organizations.
Roles and Responsibilities of a Cloud Engineer
The roles and responsibilities of a Cloud Engineer can vary depending on the organization's size, industry, and specific needs. However, here are the common roles and responsibilities associated with this role:
-
Cloud Infrastructure Design: Collaborate with architects and developers to design and plan cloud infrastructure that aligns with the organization's goals. This includes selecting appropriate cloud services, defining network architecture, and designing security measures.
-
Cloud Deployment: Implement cloud solutions by provisioning resources, setting up virtual machines, databases, storage, and configuring networking components. Ensure that the deployment meets scalability and performance requirements.
-
Automation: Develop and maintain Infrastructure as Code (IaC) scripts using tools like Terraform, AWS CloudFormation, or Azure Resource Manager to automate the provisioning and management of cloud resources.
-
Security Management: Implement security best practices and configure access controls (IAM policies) to protect cloud environments. Regularly assess and monitor security, perform vulnerability assessments, and ensure compliance with industry standards.
-
Performance Optimization: Continuously monitor cloud resources to ensure optimal performance. Scale resources as needed to meet demand and implement performance tuning strategies.
-
Backup and Disaster Recovery: Set up backup solutions and disaster recovery plans to ensure data availability and minimize downtime in case of system failures or disasters.
-
Monitoring and Logging: Implement monitoring and logging solutions (e.g., AWS CloudWatch, Azure Monitor) to track the health and performance of cloud services. Configure alerts and dashboards to respond to issues promptly.
-
Cost Management: Monitor and manage cloud costs effectively by analyzing usage patterns, optimizing resource allocation, and implementing cost-saving strategies to stay within budget.
-
Collaboration: Work closely with other teams, such as development, DevOps, and security teams, to ensure that cloud infrastructure supports application requirements and security standards.
-
Documentation: Maintain comprehensive documentation of cloud infrastructure, configurations, and processes. This documentation is crucial for knowledge sharing and troubleshooting.
-
Compliance: Ensure that cloud resources and configurations adhere to industry regulations and company policies, implementing necessary controls to meet compliance requirements.
-
Upgrades and Maintenance: Regularly apply updates, patches, and system upgrades to keep cloud infrastructure secure and up-to-date.
-
Problem Resolution: Troubleshoot and resolve issues related to cloud infrastructure and services, working to minimize downtime and impact on operations.
-
Education and Training: Stay current with cloud technology trends and provide training and guidance to team members and other stakeholders.
-
Innovation: Explore and implement new cloud services and technologies to drive innovation and improve infrastructure efficiency.
In summary, Cloud Engineers play a critical role in designing, deploying, and maintaining cloud infrastructure that supports an organization's IT needs. They are responsible for ensuring the security, performance, and cost-effectiveness of cloud environments while collaborating with various teams to deliver efficient and reliable cloud solutions.
Companies That Hire Cloud Engineers
Cloud Engineers are in high demand across various industries as organizations increasingly rely on cloud computing for their IT infrastructure. Many companies, ranging from tech giants to startups and enterprises, hire Cloud Engineers to design, implement, and manage their cloud environments. Here are some notable companies that commonly hire Cloud Engineers:
-
Amazon Web Services (AWS): As a leading cloud service provider, AWS often hires Cloud Engineers to work on their own cloud infrastructure and to support AWS customers in optimizing their cloud environments.
-
Microsoft: Microsoft Azure is another major cloud platform, and the company hires Cloud Engineers to develop and manage Azure-based solutions.
-
Google Cloud Platform (GCP): Google Cloud offers various cloud services, and they hire Cloud Engineers to work on GCP infrastructure and assist customers in building cloud-native applications.
-
IBM: IBM Cloud provides cloud computing solutions, and they hire Cloud Engineers to work on their cloud platform and offer cloud consulting services.
-
Oracle: Oracle Cloud is a growing cloud provider, and they hire Cloud Engineers to help customers migrate to and manage their cloud services.
-
Salesforce: Salesforce offers cloud-based customer relationship management (CRM) solutions and often hires Cloud Engineers to work on their cloud infrastructure and applications.
-
Cisco: Cisco provides cloud networking and infrastructure solutions and hires Cloud Engineers to work on cloud-based networking and security technologies.
-
Netflix: As a popular streaming service, Netflix relies heavily on cloud computing and hires Cloud Engineers to manage its cloud infrastructure and improve streaming capabilities.
-
Uber: Uber utilizes cloud computing for its ride-sharing platform and hires Cloud Engineers to manage and optimize its cloud resources.
-
Airbnb: Airbnb relies on cloud services for its accommodation platform, and Cloud Engineers are responsible for ensuring the reliability and scalability of their cloud infrastructure.
-
Tesla: Tesla uses cloud computing for various purposes, including over-the-air updates and autonomous driving, and hires Cloud Engineers to support these initiatives.
-
SpaceX: SpaceX leverages cloud technology for its space missions, and Cloud Engineers play a crucial role in managing cloud resources for data analysis and mission control.
-
Startups: Many startups across industries rely on cloud technology to scale their businesses quickly, and they often hire Cloud Engineers to build and manage their cloud-based applications and infrastructure.
-
Consulting Firms: Consulting firms like Deloitte, Accenture, and Capgemini offer cloud consulting services and hire Cloud Engineers to work on a wide range of client projects.
-
Financial Institutions: Banks and financial organizations are increasingly moving to the cloud, and they hire Cloud Engineers to ensure the security and compliance of their cloud-based systems.
These are just a few examples, and the demand for Cloud Engineers continues to grow as more companies adopt cloud computing solutions to improve agility, scalability, and cost-efficiency in their IT operations. Keep in mind that the specific skills and qualifications required may vary depending on the company and the nature of the job.
Cloud Engineer Salaries for Freshers and Experienced Professionals
The salary of a Cloud Engineer can vary significantly based on several factors, including location, level of experience, the specific company, and the demand for cloud skills in the job market. Here is a rough overview of the salary ranges for Cloud Engineers at different career stages:
1. Freshers/Entry-Level Cloud Engineers:
-
In the United States, entry-level Cloud Engineers can expect an annual salary in the range of $60,000 to $90,000 on average.
-
In other countries, the salaries for entry-level Cloud Engineers may vary widely, but they often align with the cost of living in the respective region.
2. Mid-Level Cloud Engineers (2-5 years of experience):
-
Mid-level Cloud Engineers typically earn more than entry-level professionals. In the United States, their salaries can range from $90,000 to $130,000 or more per year.
-
Salaries for mid-level Cloud Engineers in other countries will depend on local market conditions and demand for cloud skills.
3. Experienced Cloud Engineers (5+ years of experience):
-
Experienced Cloud Engineers with five or more years of experience can command higher salaries. In the United States, they can earn anywhere from $120,000 to $180,000 or even higher annually.
-
Salaries for experienced Cloud Engineers in other countries will also depend on factors like location and the specific industry.
4. Senior Cloud Engineers and Cloud Architects:
-
Senior Cloud Engineers and Cloud Architects, who have extensive experience and often hold advanced certifications, can earn significantly higher salaries. In the United States, their salaries can range from $150,000 to $250,000 or more per year.
It's important to note that the figures mentioned above are approximate averages and can vary considerably based on regional cost of living, the organization's size and industry, and the engineer's level of expertise and certifications. Additionally, professionals with specialized skills in specific cloud platforms (e.g., AWS, Azure, GCP) or emerging technologies may command higher salaries.
Certifications, such as AWS Certified Solutions Architect, Microsoft Certified: Azure Solutions Architect Expert, or Google Cloud Professional Cloud Architect, can also positively impact a Cloud Engineer's earning potential, as they demonstrate expertise in a particular cloud platform.
As the demand for cloud skills continues to grow and the cloud computing industry evolves, salaries for Cloud Engineers are expected to remain competitive and may even increase over time. It's essential for individuals in this field to stay updated with the latest cloud technologies and certifications to maximize their career growth and earning potential.
FAQs
What is the average salary for a fresher or entry-level Cloud Engineer?
-
The average salary for a fresher or entry-level Cloud Engineer can vary by location and organization. However, it typically ranges from $60,000 to $90,000 per year in the United States.
2. Do Cloud Engineers with certifications earn higher salaries?
-
Yes, Cloud Engineers with certifications, such as AWS Certified Solutions Architect or Azure Administrator, often earn higher salaries as these certifications demonstrate expertise in specific cloud platforms.
3. What factors influence the salary of an experienced Cloud Engineer?
-
Several factors influence the salary of an experienced Cloud Engineer, including years of experience, geographic location, the organization's size, industry, and the engineer's specific skills and certifications.
4. Are Cloud Engineers in high demand in the job market?
-
Yes, Cloud Engineers are in high demand as organizations increasingly adopt cloud computing solutions. This high demand often leads to competitive salaries and job opportunities.
5. How can Cloud Engineers increase their earning potential?
-
Cloud Engineers can increase their earning potential by acquiring advanced certifications, gaining expertise in specific cloud platforms, staying updated with emerging cloud technologies, and pursuing leadership roles.
6. Are there regional variations in Cloud Engineer salaries?
-
Yes, Cloud Engineer salaries vary significantly by region due to differences in the cost of living and demand for cloud skills. Salaries in major tech hubs like San Francisco and New York tend to be higher than in other areas.
7. What are some of the most lucrative industries for Cloud Engineers?
-
Cloud Engineers can find lucrative opportunities in various industries, including technology, finance, healthcare, and e-commerce, as many organizations across sectors are migrating to the cloud.
8. Do Cloud Architects earn higher salaries than Cloud Engineers?
-
Yes, Cloud Architects, who design complex cloud solutions and architectures, often earn higher salaries than Cloud Engineers due to their specialized skills and responsibilities.
9. Is there a significant salary difference between AWS, Azure, and GCP Cloud Engineers?
-
Salary differences among AWS, Azure, and GCP Cloud Engineers can vary, but generally, the choice of cloud platform may have a moderate impact on salary. Other factors like skills and experience play a more significant role.
10. How can entry-level Cloud Engineers negotiate a competitive salary offer?
Entry-level Cloud Engineers can negotiate a competitive salary offer by researching industry salary benchmarks, highlighting their relevant skills and certifications, and effectively communicating their value to the employer during negotiations.
Choose The Right Cloud Computing Program
Choosing the right cloud computing program is a pivotal step in advancing your career in the ever-evolving world of technology. Start by clearly defining your objectives and assessing your current skill level. Research reputable training providers and examine their programs in terms of content, format, and flexibility. Ensure that the curriculum covers essential cloud computing concepts and aligns with any specific certifications you may be targeting. Look for programs that offer practical, hands-on experience and access to knowledgeable instructors who can provide guidance. Additionally, consider the program's cost, financial aid options, and its alumni success rate in securing cloud-related positions. Seeking recommendations and reading reviews can provide valuable insights to aid in your decision-making process. Ultimately, the right cloud computing program will empower you with the skills and knowledge needed to thrive in this dynamic field.
Remember that cloud computing is a technology domain that evolves rapidly. Therefore, choosing a program that not only imparts fundamental knowledge but also keeps pace with industry trends and updates is essential for staying competitive in the job market. The right program should provide a solid foundation, hands-on experience, and the flexibility to accommodate your learning style and schedule, all while aligning with your career aspirations in cloud computing.
How to obtain Cloud Technology Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: EXIN Cloud Computing Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
In conclusion, the world of cloud computing offers promising career opportunities for both freshers and experienced professionals, with salaries that reflect the increasing demand for cloud expertise. For newcomers to the field, the potential for growth is evident as entry-level salaries provide a solid foundation for a rewarding career in cloud engineering. As one gains experience and expertise, the earning potential expands, with mid-level and experienced Cloud Engineers commanding competitive salaries.
However, it's important to recognize that salary figures can vary widely based on factors such as location, certification, industry, and specific skills. Therefore, continuous learning, staying updated with the latest cloud technologies, and investing in certifications are crucial steps to maximize earning potential. Whether you're at the beginning of your cloud engineering journey or an experienced professional seeking to further your career, the cloud computing landscape offers ample opportunities for growth and financial rewards, making it an exciting and lucrative field to explore.
Read More
In the rapidly advancing domain of cloud computing, the role of a Cloud Engineer stands as a linchpin in modern tech operations. As businesses continue to embrace the benefits of cloud technologies, the demand for skilled professionals to design, manage, and optimize these infrastructures has soared. This has sparked a fascinating comparison between the salaries of freshers, those new to the cloud engineering scene, and experienced professionals who have weathered the dynamic landscape for some time.
This examination of "Cloud Engineer Salary Trends: Freshers vs. Experienced" embarks on a journey through the intricacies of compensation packages in the cloud engineering sphere. Whether you're a recent graduate, eager to step into this promising career path, or a seasoned expert, curious about how your experience impacts your earning potential, our exploration will dissect the factors that shape these trends. By shedding light on the compensation distinctions, we aim to empower both newcomers and veterans in the field to navigate their cloud engineering careers effectively, making informed decisions in this ever-evolving and rewarding landscape.
Table of Contents
What Does a Cloud Engineer Do?
Skills Required to Be a Cloud Engineer
Roles and Responsibilities of a Cloud Engineer
Companies That Hire Cloud Engineers
Cloud Engineer Salaries for Freshers and Experienced Professionals
FAQs
Choose The Right Cloud Computing Program
Conclusion
What Does a Cloud Engineer Do?
A Cloud Engineer is responsible for architecting, implementing, and maintaining an organization's cloud computing infrastructure. They design the cloud environment, selecting the most suitable cloud service providers and configuring resources to meet business needs. Cloud Engineers also focus on automation, using tools like Infrastructure as Code (IaC) to efficiently provision and manage cloud resources. Security is a top priority, as they establish robust security measures, monitor for threats, and ensure compliance with industry regulations. Additionally, they optimize cloud performance, manage costs, and collaborate with cross-functional teams to align cloud infrastructure with application requirements. In essence, Cloud Engineers are crucial for enabling businesses to leverage the benefits of cloud technology while ensuring reliability, security, and cost-effectiveness.
Continuous maintenance and improvement are key aspects of a Cloud Engineer's role. They regularly update and patch cloud systems, implement backup and disaster recovery plans to ensure data availability, and monitor cloud resources for performance and security. By staying abreast of emerging cloud technologies and best practices, Cloud Engineers help organizations harness the full potential of the cloud, driving innovation, scalability, and efficiency in their operations.
Skills Required to Be a Cloud Engineer
To excel as a Cloud Engineer, you need a diverse set of technical skills and non-technical skills. Here is a list of key skills required to be successful in this role:
1. Cloud Platform Proficiency: A deep understanding of one or more major cloud platforms like Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), or others is essential. This includes knowledge of their services, capabilities, and pricing models.
2. Infrastructure as Code (IaC): Proficiency in IaC tools like Terraform, AWS CloudFormation, or Azure Resource Manager is crucial for automating the provisioning and management of cloud resources.
3. Networking: Knowledge of cloud networking concepts, including Virtual Private Cloud (VPC), subnets, load balancers, and VPN configurations, is necessary for designing and securing cloud architectures.
4. Security: An understanding of cloud security best practices, identity and access management (IAM), encryption, firewalls, and compliance standards is vital to protect cloud environments from cyber threats.
5. DevOps Tools: Familiarity with DevOps principles and tools such as Docker, Kubernetes, Jenkins, and Git is important for implementing continuous integration and continuous deployment (CI/CD) pipelines.
6. Scripting and Automation: Proficiency in scripting languages like Python, PowerShell, or Bash is essential for writing automation scripts and managing cloud resources programmatically.
7. Monitoring and Logging: Experience with monitoring and logging tools like Amazon CloudWatch, Azure Monitor, or Prometheus is necessary for tracking the health and performance of cloud services.
8. Database Management: Knowledge of cloud database services (e.g., AWS RDS, Azure SQL Database, Google Cloud SQL) and database administration skills are important for managing data in the cloud.
9. Cost Management: The ability to manage cloud costs effectively by analyzing usage patterns, optimizing resource allocation, and implementing cost-saving strategies is critical.
10. Troubleshooting and Problem Solving: Strong analytical and problem-solving skills are essential for identifying and resolving issues in cloud environments.
11. Collaboration: Effective communication and collaboration skills are vital for working with cross-functional teams, including developers, sysadmins, and security professionals.
12. Project Management: Basic project management skills can help Cloud Engineers plan and execute cloud projects effectively, ensuring they meet deadlines and objectives.
13. Continuous Learning: Cloud technology evolves rapidly, so a willingness to continuously learn and adapt to new tools and best practices is crucial to stay up-to-date in this field.
14. Soft Skills: Soft skills such as adaptability, teamwork, and attention to detail are important for working in a dynamic and collaborative environment.
Overall, Cloud Engineers need to combine technical expertise with a proactive and problem-solving mindset to design, implement, and manage robust and scalable cloud infrastructures that meet the needs of their organizations.
Roles and Responsibilities of a Cloud Engineer
The roles and responsibilities of a Cloud Engineer can vary depending on the organization's size, industry, and specific needs. However, here are the common roles and responsibilities associated with this role:
-
Cloud Infrastructure Design: Collaborate with architects and developers to design and plan cloud infrastructure that aligns with the organization's goals. This includes selecting appropriate cloud services, defining network architecture, and designing security measures.
-
Cloud Deployment: Implement cloud solutions by provisioning resources, setting up virtual machines, databases, storage, and configuring networking components. Ensure that the deployment meets scalability and performance requirements.
-
Automation: Develop and maintain Infrastructure as Code (IaC) scripts using tools like Terraform, AWS CloudFormation, or Azure Resource Manager to automate the provisioning and management of cloud resources.
-
Security Management: Implement security best practices and configure access controls (IAM policies) to protect cloud environments. Regularly assess and monitor security, perform vulnerability assessments, and ensure compliance with industry standards.
-
Performance Optimization: Continuously monitor cloud resources to ensure optimal performance. Scale resources as needed to meet demand and implement performance tuning strategies.
-
Backup and Disaster Recovery: Set up backup solutions and disaster recovery plans to ensure data availability and minimize downtime in case of system failures or disasters.
-
Monitoring and Logging: Implement monitoring and logging solutions (e.g., AWS CloudWatch, Azure Monitor) to track the health and performance of cloud services. Configure alerts and dashboards to respond to issues promptly.
-
Cost Management: Monitor and manage cloud costs effectively by analyzing usage patterns, optimizing resource allocation, and implementing cost-saving strategies to stay within budget.
-
Collaboration: Work closely with other teams, such as development, DevOps, and security teams, to ensure that cloud infrastructure supports application requirements and security standards.
-
Documentation: Maintain comprehensive documentation of cloud infrastructure, configurations, and processes. This documentation is crucial for knowledge sharing and troubleshooting.
-
Compliance: Ensure that cloud resources and configurations adhere to industry regulations and company policies, implementing necessary controls to meet compliance requirements.
-
Upgrades and Maintenance: Regularly apply updates, patches, and system upgrades to keep cloud infrastructure secure and up-to-date.
-
Problem Resolution: Troubleshoot and resolve issues related to cloud infrastructure and services, working to minimize downtime and impact on operations.
-
Education and Training: Stay current with cloud technology trends and provide training and guidance to team members and other stakeholders.
-
Innovation: Explore and implement new cloud services and technologies to drive innovation and improve infrastructure efficiency.
In summary, Cloud Engineers play a critical role in designing, deploying, and maintaining cloud infrastructure that supports an organization's IT needs. They are responsible for ensuring the security, performance, and cost-effectiveness of cloud environments while collaborating with various teams to deliver efficient and reliable cloud solutions.
Companies That Hire Cloud Engineers
Cloud Engineers are in high demand across various industries as organizations increasingly rely on cloud computing for their IT infrastructure. Many companies, ranging from tech giants to startups and enterprises, hire Cloud Engineers to design, implement, and manage their cloud environments. Here are some notable companies that commonly hire Cloud Engineers:
-
Amazon Web Services (AWS): As a leading cloud service provider, AWS often hires Cloud Engineers to work on their own cloud infrastructure and to support AWS customers in optimizing their cloud environments.
-
Microsoft: Microsoft Azure is another major cloud platform, and the company hires Cloud Engineers to develop and manage Azure-based solutions.
-
Google Cloud Platform (GCP): Google Cloud offers various cloud services, and they hire Cloud Engineers to work on GCP infrastructure and assist customers in building cloud-native applications.
-
IBM: IBM Cloud provides cloud computing solutions, and they hire Cloud Engineers to work on their cloud platform and offer cloud consulting services.
-
Oracle: Oracle Cloud is a growing cloud provider, and they hire Cloud Engineers to help customers migrate to and manage their cloud services.
-
Salesforce: Salesforce offers cloud-based customer relationship management (CRM) solutions and often hires Cloud Engineers to work on their cloud infrastructure and applications.
-
Cisco: Cisco provides cloud networking and infrastructure solutions and hires Cloud Engineers to work on cloud-based networking and security technologies.
-
Netflix: As a popular streaming service, Netflix relies heavily on cloud computing and hires Cloud Engineers to manage its cloud infrastructure and improve streaming capabilities.
-
Uber: Uber utilizes cloud computing for its ride-sharing platform and hires Cloud Engineers to manage and optimize its cloud resources.
-
Airbnb: Airbnb relies on cloud services for its accommodation platform, and Cloud Engineers are responsible for ensuring the reliability and scalability of their cloud infrastructure.
-
Tesla: Tesla uses cloud computing for various purposes, including over-the-air updates and autonomous driving, and hires Cloud Engineers to support these initiatives.
-
SpaceX: SpaceX leverages cloud technology for its space missions, and Cloud Engineers play a crucial role in managing cloud resources for data analysis and mission control.
-
Startups: Many startups across industries rely on cloud technology to scale their businesses quickly, and they often hire Cloud Engineers to build and manage their cloud-based applications and infrastructure.
-
Consulting Firms: Consulting firms like Deloitte, Accenture, and Capgemini offer cloud consulting services and hire Cloud Engineers to work on a wide range of client projects.
-
Financial Institutions: Banks and financial organizations are increasingly moving to the cloud, and they hire Cloud Engineers to ensure the security and compliance of their cloud-based systems.
These are just a few examples, and the demand for Cloud Engineers continues to grow as more companies adopt cloud computing solutions to improve agility, scalability, and cost-efficiency in their IT operations. Keep in mind that the specific skills and qualifications required may vary depending on the company and the nature of the job.
Cloud Engineer Salaries for Freshers and Experienced Professionals
The salary of a Cloud Engineer can vary significantly based on several factors, including location, level of experience, the specific company, and the demand for cloud skills in the job market. Here is a rough overview of the salary ranges for Cloud Engineers at different career stages:
1. Freshers/Entry-Level Cloud Engineers:
-
In the United States, entry-level Cloud Engineers can expect an annual salary in the range of $60,000 to $90,000 on average.
-
In other countries, the salaries for entry-level Cloud Engineers may vary widely, but they often align with the cost of living in the respective region.
2. Mid-Level Cloud Engineers (2-5 years of experience):
-
Mid-level Cloud Engineers typically earn more than entry-level professionals. In the United States, their salaries can range from $90,000 to $130,000 or more per year.
-
Salaries for mid-level Cloud Engineers in other countries will depend on local market conditions and demand for cloud skills.
3. Experienced Cloud Engineers (5+ years of experience):
-
Experienced Cloud Engineers with five or more years of experience can command higher salaries. In the United States, they can earn anywhere from $120,000 to $180,000 or even higher annually.
-
Salaries for experienced Cloud Engineers in other countries will also depend on factors like location and the specific industry.
4. Senior Cloud Engineers and Cloud Architects:
-
Senior Cloud Engineers and Cloud Architects, who have extensive experience and often hold advanced certifications, can earn significantly higher salaries. In the United States, their salaries can range from $150,000 to $250,000 or more per year.
It's important to note that the figures mentioned above are approximate averages and can vary considerably based on regional cost of living, the organization's size and industry, and the engineer's level of expertise and certifications. Additionally, professionals with specialized skills in specific cloud platforms (e.g., AWS, Azure, GCP) or emerging technologies may command higher salaries.
Certifications, such as AWS Certified Solutions Architect, Microsoft Certified: Azure Solutions Architect Expert, or Google Cloud Professional Cloud Architect, can also positively impact a Cloud Engineer's earning potential, as they demonstrate expertise in a particular cloud platform.
As the demand for cloud skills continues to grow and the cloud computing industry evolves, salaries for Cloud Engineers are expected to remain competitive and may even increase over time. It's essential for individuals in this field to stay updated with the latest cloud technologies and certifications to maximize their career growth and earning potential.
FAQs
What is the average salary for a fresher or entry-level Cloud Engineer?
-
The average salary for a fresher or entry-level Cloud Engineer can vary by location and organization. However, it typically ranges from $60,000 to $90,000 per year in the United States.
2. Do Cloud Engineers with certifications earn higher salaries?
-
Yes, Cloud Engineers with certifications, such as AWS Certified Solutions Architect or Azure Administrator, often earn higher salaries as these certifications demonstrate expertise in specific cloud platforms.
3. What factors influence the salary of an experienced Cloud Engineer?
-
Several factors influence the salary of an experienced Cloud Engineer, including years of experience, geographic location, the organization's size, industry, and the engineer's specific skills and certifications.
4. Are Cloud Engineers in high demand in the job market?
-
Yes, Cloud Engineers are in high demand as organizations increasingly adopt cloud computing solutions. This high demand often leads to competitive salaries and job opportunities.
5. How can Cloud Engineers increase their earning potential?
-
Cloud Engineers can increase their earning potential by acquiring advanced certifications, gaining expertise in specific cloud platforms, staying updated with emerging cloud technologies, and pursuing leadership roles.
6. Are there regional variations in Cloud Engineer salaries?
-
Yes, Cloud Engineer salaries vary significantly by region due to differences in the cost of living and demand for cloud skills. Salaries in major tech hubs like San Francisco and New York tend to be higher than in other areas.
7. What are some of the most lucrative industries for Cloud Engineers?
-
Cloud Engineers can find lucrative opportunities in various industries, including technology, finance, healthcare, and e-commerce, as many organizations across sectors are migrating to the cloud.
8. Do Cloud Architects earn higher salaries than Cloud Engineers?
-
Yes, Cloud Architects, who design complex cloud solutions and architectures, often earn higher salaries than Cloud Engineers due to their specialized skills and responsibilities.
9. Is there a significant salary difference between AWS, Azure, and GCP Cloud Engineers?
-
Salary differences among AWS, Azure, and GCP Cloud Engineers can vary, but generally, the choice of cloud platform may have a moderate impact on salary. Other factors like skills and experience play a more significant role.
10. How can entry-level Cloud Engineers negotiate a competitive salary offer?
Entry-level Cloud Engineers can negotiate a competitive salary offer by researching industry salary benchmarks, highlighting their relevant skills and certifications, and effectively communicating their value to the employer during negotiations.
Choose The Right Cloud Computing Program
Choosing the right cloud computing program is a pivotal step in advancing your career in the ever-evolving world of technology. Start by clearly defining your objectives and assessing your current skill level. Research reputable training providers and examine their programs in terms of content, format, and flexibility. Ensure that the curriculum covers essential cloud computing concepts and aligns with any specific certifications you may be targeting. Look for programs that offer practical, hands-on experience and access to knowledgeable instructors who can provide guidance. Additionally, consider the program's cost, financial aid options, and its alumni success rate in securing cloud-related positions. Seeking recommendations and reading reviews can provide valuable insights to aid in your decision-making process. Ultimately, the right cloud computing program will empower you with the skills and knowledge needed to thrive in this dynamic field.
Remember that cloud computing is a technology domain that evolves rapidly. Therefore, choosing a program that not only imparts fundamental knowledge but also keeps pace with industry trends and updates is essential for staying competitive in the job market. The right program should provide a solid foundation, hands-on experience, and the flexibility to accommodate your learning style and schedule, all while aligning with your career aspirations in cloud computing.
How to obtain Cloud Technology Certifications?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: EXIN Cloud Computing Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
In conclusion, the world of cloud computing offers promising career opportunities for both freshers and experienced professionals, with salaries that reflect the increasing demand for cloud expertise. For newcomers to the field, the potential for growth is evident as entry-level salaries provide a solid foundation for a rewarding career in cloud engineering. As one gains experience and expertise, the earning potential expands, with mid-level and experienced Cloud Engineers commanding competitive salaries.
However, it's important to recognize that salary figures can vary widely based on factors such as location, certification, industry, and specific skills. Therefore, continuous learning, staying updated with the latest cloud technologies, and investing in certifications are crucial steps to maximize earning potential. Whether you're at the beginning of your cloud engineering journey or an experienced professional seeking to further your career, the cloud computing landscape offers ample opportunities for growth and financial rewards, making it an exciting and lucrative field to explore.
Career Advancement Through Top Network Security Certifications
In today's digitally interconnected world, where data breaches and cyber threats have become increasingly prevalent, the demand for skilled network security professionals has never been higher. If you're looking to establish or advance your career in the field of network security, you'll find that acquiring relevant certifications is not just a valuable asset but often a necessity. These certifications not only validate your expertise but also serve as a testament to your commitment to maintaining the integrity and security of critical digital infrastructure.
In this comprehensive guide, we will delve into the realm of network security certifications, providing you with valuable insights into the top certifications that can propel your career to new heights. Whether you're an aspiring cybersecurity enthusiast, a seasoned professional looking to upskill, or simply someone intrigued by the dynamic world of network security, this exploration will shed light on the certifications that matter most, the skills they encompass, and how they can open doors to lucrative and fulfilling career opportunities. So, fasten your digital seatbelt as we embark on a journey through the realm of "Top Network Security Certifications for Career Advancement."
Table of Contents
-
What is Network Security?
-
Why is Network Security Needed?
-
What Are the Types of Network Security?
-
Which are the Best Network Security Certifications?
-
Conclusion
What is Network Security?
Network security is a critical aspect of modern computing and communications. It encompasses a wide range of measures and practices aimed at safeguarding the integrity, confidentiality, and availability of data and resources within a computer network. In an era where digital information plays an increasingly pivotal role in businesses, governments, and personal lives, the importance of network security cannot be overstated. It involves a multifaceted approach, incorporating both technological solutions and human behaviors, to protect against an ever-evolving landscape of cyber threats. Whether it's the protection of sensitive corporate data, the privacy of personal information, or the reliability of critical network services, network security serves as the frontline defense against malicious actors and potential disasters. It is a dynamic and continuously evolving field, driven by the need to stay one step ahead of those who seek to compromise the security and functionality of our interconnected world.
Why is Network Security Needed?
Network security is an indispensable element of our modern digital landscape for several compelling reasons. Firstly, it acts as a safeguard against data breaches, protecting valuable assets such as customer information, financial records, and intellectual property from unauthorized access and theft. In an era where data is a precious commodity, these protections are essential to mitigate the severe financial and reputational repercussions of a breach. Additionally, network security ensures the privacy of individuals and organizations, preventing the unauthorized interception of personal data and confidential business communications.
Secondly, network security is vital for business continuity. Cyberattacks, ranging from Distributed Denial of Service (DDoS) assaults to ransomware, can disrupt essential services and operations, causing significant downtime and financial losses. Network security measures help maintain the availability of critical systems and services, ensuring uninterrupted business operations and mitigating potential financial harm. Furthermore, network security is a key component of regulatory compliance, as many industries and jurisdictions have strict rules governing data security and privacy. Adherence to these regulations is imperative to avoid legal penalties and protect the reputation of organizations. In summary, network security is an essential bulwark against data breaches, preserves privacy, ensures business continuity, supports regulatory compliance, and helps organizations withstand the ever-evolving landscape of cyber threats.
What Are the Types of Network Security?
Network security encompasses various measures and strategies to safeguard computer networks from unauthorized access, data breaches, and other cyber threats. Here are the key types of network security:
-
Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They analyze incoming and outgoing traffic, based on predetermined security rules, to allow or block data packets.
-
Intrusion Prevention Systems (IPS): IPSs monitor network and/or system activities for malicious exploits or security policy violations. They can identify and block suspicious traffic in real-time.
-
Intrusion Detection Systems (IDS): IDSs detect and alert on suspicious activities or patterns within a network. They provide notifications about potential security breaches, but they do not actively prevent them.
-
Virtual Private Networks (VPNs): VPNs establish secure connections over the internet, allowing remote users or branch offices to access a private network securely. They use encryption protocols to ensure data confidentiality.
-
Access Control Lists (ACLs): ACLs are a set of rules defined on a network device (e.g., router, firewall) that dictate which types of traffic are allowed or denied based on factors like source, destination, and protocol.
-
Wireless Security: This includes measures like Wi-Fi Protected Access (WPA) and WPA2 protocols, which secure wireless networks from unauthorized access.
-
Network Segmentation: This involves dividing a network into smaller, isolated segments to limit the scope of a potential breach. Each segment may have its own security policies.
-
Anti-virus and Anti-malware Software: These programs detect, prevent, and remove malicious software (viruses, worms, Trojans, etc.) from devices and networks.
-
Email Security: This includes spam filters, antivirus scanning, and encryption to protect email communications from phishing attacks, malware, and other threats.
-
Web Security: Web security solutions filter and monitor web traffic, blocking access to malicious websites and scanning downloads for malware.
-
Security Information and Event Management (SIEM): SIEM tools aggregate and analyze data from various network and security devices to detect and respond to security incidents.
-
Data Loss Prevention (DLP): DLP solutions monitor and control data transfers to prevent unauthorized access or sharing of sensitive information.
-
Security Policies and Procedures: Establishing and enforcing security policies, along with educating employees on security best practices, are crucial elements of network security.
-
Biometric Authentication: This includes fingerprint scanning, facial recognition, and other biometric methods to ensure secure access to devices and networks.
-
Backup and Disaster Recovery: Regularly backing up data and having a robust disaster recovery plan in place helps mitigate the impact of data breaches or system failures.
Implementing a combination of these network security measures provides a layered defense against a wide range of cyber threats, helping to create a more resilient and secure network environment.
Which are the Best Network Security Certifications?
To unlock significant earning potential in the field of network security, a solid grasp of essential tools and skills is imperative. This is precisely where network security education assumes a pivotal role. Enrolling in network security certification courses not only equips you with the fundamental knowledge and skills required for these careers but also furnishes you with a valuable credential, serving as a tangible validation of your qualifications to prospective employers.
-
CEH: Certified Ethical Hacker
-
Also known as "white hat hacking," ethical hacking involves legally probing businesses to identify vulnerabilities before malicious actors do.
-
The CEH certification, offered by the EC-Council, validates your expertise in penetration testing, attack detection, vectors, and prevention.
-
Ethical hackers, or "white hat hackers," are hired to uncover system flaws and propose solutions, making this certification highly valuable in today's cybersecurity landscape.
-
CEH teaches you to think like a hacker, making it ideal for roles such as penetration testers, cyber incident analysts, threat intelligence analysts, and cloud security architects.
-
Requirements: Two years of information security job experience or completion of an authorized EC-Council program.
-
Cost: Varies between $950 and $1,199 depending on the testing location.
-
CISSP: Certified Information Systems Security Professional
-
CISSP, from (ISC)², is a prestigious certification for experienced security professionals responsible for developing and managing security processes, policies, and standards.
-
This certification is highly sought after in the industry, validating your expertise in IT security, cybersecurity program design, implementation, and monitoring.
-
CISSP is suitable for roles like Chief Information Security Officer, security administrators, IT security engineers, and senior security consultants.
-
Requirements: Five or more years of cumulative work experience in at least two of the eight cybersecurity domains or becoming an Associate of (ISC)² if you're new to cybersecurity.
-
Cost: $749
-
CISA: Certified Information Systems Auditor
-
CISA, offered by ISACA, is designed for information security professionals specializing in audit control, assurance, and security.
-
It equips you with the skills needed to manage IT, conduct comprehensive security audits, and identify vulnerabilities.
-
Valued in cybersecurity auditing, it's suitable for roles like IT audit managers, cybersecurity auditors, information security analysts, and IT security engineers.
-
Requirements: At least five years of experience in IT or IS audit, control, security, or assurance, with exceptions for degrees and certifications.
-
Cost: $575 for members, $760 for non-members.
-
CISM: Certified Information Security Manager
-
CISM, also from ISACA, focuses on the management aspects of information security, including governance, program creation, and risk management.
-
Ideal for transitioning from technical to managerial roles in cybersecurity.
-
Relevant for positions like IT managers, information risk consultants, directors of information security, and data governance managers.
-
Requirements: At least five years of information security management experience, with possible substitutions.
-
Cost: $575 for members, $760 for non-members.
-
CompTIA Security+
-
An entry-level certification covering essential cybersecurity skills.
-
Validates your ability to assess security, secure cloud and IoT environments, understand risk and compliance, and respond to security issues.
-
Suitable for roles like systems administrators, help desk managers, security engineers, and IT auditors.
-
Requirements: Recommended to have CompTIA Network+ and two years of IT experience with a security focus.
-
Cost: $370.
-
GIAC Security Essentials (GSEC)
-
An entry-level certification for individuals with a background in information systems and networking.
-
Validates skills in active defense, network security, cryptography, incident response, and cloud security.
-
Relevant for roles like IT security managers, computer forensic analysts, penetration testers, and security administrators.
-
Requirements: No specific prerequisites, but IT experience is beneficial.
-
Cost: $2,499 (includes two practice tests).
-
SSCP: Systems Security Certified Practitioner
-
Focuses on designing, deploying, and maintaining secure IT infrastructures.
-
Suitable for roles like network security engineers, system administrators, and security analysts.
-
Requirements: One year of work experience in one of the testing areas or relevant degrees or certifications.
-
Cost: $249.
-
CompTIA Advanced Security Practitioner (CASP+)
-
Covers advanced topics like enterprise security, risk analysis, and cryptographic approaches.
-
Relevant for positions such as security architects, security engineers, and IT project managers.
-
Requirements: CompTIA recommends ten years of IT experience with five years of hands-on security experience.
-
Cost: $466.
-
GIAC Certified Incident Handler (GCIH)
-
Focuses on identifying, responding to, and defending against cyberattacks.
-
Suitable for incident handlers, security analysts, and system administrators.
-
Requirements: No specific prerequisites, but familiarity with security principles and networking protocols is helpful.
-
Cost: $2,499 (includes two practice tests).
-
Offensive Security Certified Professional (OSCP)
-
A highly sought-after certification for penetration testers.
-
Requires compromising target devices using various exploitation techniques and providing detailed penetration test reports.
-
Relevant for roles like penetration testers, ethical hackers, and threat researchers.
-
Requirements: No formal prerequisites, but prior knowledge of networking and scripting is recommended.
-
Cost: $999 (includes training, lab access, and one test attempt).
Conclusion
In conclusion, the world of cybersecurity is dynamic and ever-evolving, and staying ahead of the curve is essential in defending against the ever-present threats in the digital realm. The array of certifications available provides a roadmap for professionals at every stage of their cybersecurity journey.
Whether you're a newcomer looking to establish a foothold or a seasoned expert seeking to advance your career, these certifications offer a structured path to sharpen your skills, validate your knowledge, and enhance your professional prospects. From ethical hacking to security management, each certification serves a specific purpose and opens doors to various rewarding roles within the cybersecurity landscape.
In this rapidly changing field, continuous learning is paramount, and acquiring certifications is not just a one-time achievement but an ongoing commitment to excellence. Regardless of where you are in your career, investing in these certifications not only elevates your expertise but also fortifies your ability to protect organizations and individuals from the ever-evolving threat landscape.
Remember that the ideal certification depends on your career goals, interests, and experience level. Combining multiple certifications can create a well-rounded skill set, making you a valuable asset in the ever-expanding realm of cybersecurity. So, choose wisely, invest in your professional development, and stay committed to the pursuit of knowledge in the ever-important field of cybersecurity.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Cyber Security Training:
- Certified Ethical Hacker Training Courses
- Certified Information Systems Security Professional Training Courses
- Certified inrisk and Information Systems Control Training Courses
- Certified Information Security Manager Training Courses
- Certified Information Systems Auditor
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1(713)-518-1187 / +1(713)-287-1214 or e-mail us at info@icertglobal.com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Read More
In today's digitally interconnected world, where data breaches and cyber threats have become increasingly prevalent, the demand for skilled network security professionals has never been higher. If you're looking to establish or advance your career in the field of network security, you'll find that acquiring relevant certifications is not just a valuable asset but often a necessity. These certifications not only validate your expertise but also serve as a testament to your commitment to maintaining the integrity and security of critical digital infrastructure.
In this comprehensive guide, we will delve into the realm of network security certifications, providing you with valuable insights into the top certifications that can propel your career to new heights. Whether you're an aspiring cybersecurity enthusiast, a seasoned professional looking to upskill, or simply someone intrigued by the dynamic world of network security, this exploration will shed light on the certifications that matter most, the skills they encompass, and how they can open doors to lucrative and fulfilling career opportunities. So, fasten your digital seatbelt as we embark on a journey through the realm of "Top Network Security Certifications for Career Advancement."
Table of Contents
-
What is Network Security?
-
Why is Network Security Needed?
-
What Are the Types of Network Security?
-
Which are the Best Network Security Certifications?
-
Conclusion
What is Network Security?
Network security is a critical aspect of modern computing and communications. It encompasses a wide range of measures and practices aimed at safeguarding the integrity, confidentiality, and availability of data and resources within a computer network. In an era where digital information plays an increasingly pivotal role in businesses, governments, and personal lives, the importance of network security cannot be overstated. It involves a multifaceted approach, incorporating both technological solutions and human behaviors, to protect against an ever-evolving landscape of cyber threats. Whether it's the protection of sensitive corporate data, the privacy of personal information, or the reliability of critical network services, network security serves as the frontline defense against malicious actors and potential disasters. It is a dynamic and continuously evolving field, driven by the need to stay one step ahead of those who seek to compromise the security and functionality of our interconnected world.
Why is Network Security Needed?
Network security is an indispensable element of our modern digital landscape for several compelling reasons. Firstly, it acts as a safeguard against data breaches, protecting valuable assets such as customer information, financial records, and intellectual property from unauthorized access and theft. In an era where data is a precious commodity, these protections are essential to mitigate the severe financial and reputational repercussions of a breach. Additionally, network security ensures the privacy of individuals and organizations, preventing the unauthorized interception of personal data and confidential business communications.
Secondly, network security is vital for business continuity. Cyberattacks, ranging from Distributed Denial of Service (DDoS) assaults to ransomware, can disrupt essential services and operations, causing significant downtime and financial losses. Network security measures help maintain the availability of critical systems and services, ensuring uninterrupted business operations and mitigating potential financial harm. Furthermore, network security is a key component of regulatory compliance, as many industries and jurisdictions have strict rules governing data security and privacy. Adherence to these regulations is imperative to avoid legal penalties and protect the reputation of organizations. In summary, network security is an essential bulwark against data breaches, preserves privacy, ensures business continuity, supports regulatory compliance, and helps organizations withstand the ever-evolving landscape of cyber threats.
What Are the Types of Network Security?
Network security encompasses various measures and strategies to safeguard computer networks from unauthorized access, data breaches, and other cyber threats. Here are the key types of network security:
-
Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They analyze incoming and outgoing traffic, based on predetermined security rules, to allow or block data packets.
-
Intrusion Prevention Systems (IPS): IPSs monitor network and/or system activities for malicious exploits or security policy violations. They can identify and block suspicious traffic in real-time.
-
Intrusion Detection Systems (IDS): IDSs detect and alert on suspicious activities or patterns within a network. They provide notifications about potential security breaches, but they do not actively prevent them.
-
Virtual Private Networks (VPNs): VPNs establish secure connections over the internet, allowing remote users or branch offices to access a private network securely. They use encryption protocols to ensure data confidentiality.
-
Access Control Lists (ACLs): ACLs are a set of rules defined on a network device (e.g., router, firewall) that dictate which types of traffic are allowed or denied based on factors like source, destination, and protocol.
-
Wireless Security: This includes measures like Wi-Fi Protected Access (WPA) and WPA2 protocols, which secure wireless networks from unauthorized access.
-
Network Segmentation: This involves dividing a network into smaller, isolated segments to limit the scope of a potential breach. Each segment may have its own security policies.
-
Anti-virus and Anti-malware Software: These programs detect, prevent, and remove malicious software (viruses, worms, Trojans, etc.) from devices and networks.
-
Email Security: This includes spam filters, antivirus scanning, and encryption to protect email communications from phishing attacks, malware, and other threats.
-
Web Security: Web security solutions filter and monitor web traffic, blocking access to malicious websites and scanning downloads for malware.
-
Security Information and Event Management (SIEM): SIEM tools aggregate and analyze data from various network and security devices to detect and respond to security incidents.
-
Data Loss Prevention (DLP): DLP solutions monitor and control data transfers to prevent unauthorized access or sharing of sensitive information.
-
Security Policies and Procedures: Establishing and enforcing security policies, along with educating employees on security best practices, are crucial elements of network security.
-
Biometric Authentication: This includes fingerprint scanning, facial recognition, and other biometric methods to ensure secure access to devices and networks.
-
Backup and Disaster Recovery: Regularly backing up data and having a robust disaster recovery plan in place helps mitigate the impact of data breaches or system failures.
Implementing a combination of these network security measures provides a layered defense against a wide range of cyber threats, helping to create a more resilient and secure network environment.
Which are the Best Network Security Certifications?
To unlock significant earning potential in the field of network security, a solid grasp of essential tools and skills is imperative. This is precisely where network security education assumes a pivotal role. Enrolling in network security certification courses not only equips you with the fundamental knowledge and skills required for these careers but also furnishes you with a valuable credential, serving as a tangible validation of your qualifications to prospective employers.
-
CEH: Certified Ethical Hacker
-
Also known as "white hat hacking," ethical hacking involves legally probing businesses to identify vulnerabilities before malicious actors do.
-
The CEH certification, offered by the EC-Council, validates your expertise in penetration testing, attack detection, vectors, and prevention.
-
Ethical hackers, or "white hat hackers," are hired to uncover system flaws and propose solutions, making this certification highly valuable in today's cybersecurity landscape.
-
CEH teaches you to think like a hacker, making it ideal for roles such as penetration testers, cyber incident analysts, threat intelligence analysts, and cloud security architects.
-
Requirements: Two years of information security job experience or completion of an authorized EC-Council program.
-
Cost: Varies between $950 and $1,199 depending on the testing location.
-
-
CISSP: Certified Information Systems Security Professional
-
CISSP, from (ISC)², is a prestigious certification for experienced security professionals responsible for developing and managing security processes, policies, and standards.
-
This certification is highly sought after in the industry, validating your expertise in IT security, cybersecurity program design, implementation, and monitoring.
-
CISSP is suitable for roles like Chief Information Security Officer, security administrators, IT security engineers, and senior security consultants.
-
Requirements: Five or more years of cumulative work experience in at least two of the eight cybersecurity domains or becoming an Associate of (ISC)² if you're new to cybersecurity.
-
Cost: $749
-
-
CISA: Certified Information Systems Auditor
-
CISA, offered by ISACA, is designed for information security professionals specializing in audit control, assurance, and security.
-
It equips you with the skills needed to manage IT, conduct comprehensive security audits, and identify vulnerabilities.
-
Valued in cybersecurity auditing, it's suitable for roles like IT audit managers, cybersecurity auditors, information security analysts, and IT security engineers.
-
Requirements: At least five years of experience in IT or IS audit, control, security, or assurance, with exceptions for degrees and certifications.
-
Cost: $575 for members, $760 for non-members.
-
-
CISM: Certified Information Security Manager
-
CISM, also from ISACA, focuses on the management aspects of information security, including governance, program creation, and risk management.
-
Ideal for transitioning from technical to managerial roles in cybersecurity.
-
Relevant for positions like IT managers, information risk consultants, directors of information security, and data governance managers.
-
Requirements: At least five years of information security management experience, with possible substitutions.
-
Cost: $575 for members, $760 for non-members.
-
-
CompTIA Security+
-
An entry-level certification covering essential cybersecurity skills.
-
Validates your ability to assess security, secure cloud and IoT environments, understand risk and compliance, and respond to security issues.
-
Suitable for roles like systems administrators, help desk managers, security engineers, and IT auditors.
-
Requirements: Recommended to have CompTIA Network+ and two years of IT experience with a security focus.
-
Cost: $370.
-
-
GIAC Security Essentials (GSEC)
-
An entry-level certification for individuals with a background in information systems and networking.
-
Validates skills in active defense, network security, cryptography, incident response, and cloud security.
-
Relevant for roles like IT security managers, computer forensic analysts, penetration testers, and security administrators.
-
Requirements: No specific prerequisites, but IT experience is beneficial.
-
Cost: $2,499 (includes two practice tests).
-
-
SSCP: Systems Security Certified Practitioner
-
Focuses on designing, deploying, and maintaining secure IT infrastructures.
-
Suitable for roles like network security engineers, system administrators, and security analysts.
-
Requirements: One year of work experience in one of the testing areas or relevant degrees or certifications.
-
Cost: $249.
-
-
CompTIA Advanced Security Practitioner (CASP+)
-
Covers advanced topics like enterprise security, risk analysis, and cryptographic approaches.
-
Relevant for positions such as security architects, security engineers, and IT project managers.
-
Requirements: CompTIA recommends ten years of IT experience with five years of hands-on security experience.
-
Cost: $466.
-
-
GIAC Certified Incident Handler (GCIH)
-
Focuses on identifying, responding to, and defending against cyberattacks.
-
Suitable for incident handlers, security analysts, and system administrators.
-
Requirements: No specific prerequisites, but familiarity with security principles and networking protocols is helpful.
-
Cost: $2,499 (includes two practice tests).
-
-
Offensive Security Certified Professional (OSCP)
-
A highly sought-after certification for penetration testers.
-
Requires compromising target devices using various exploitation techniques and providing detailed penetration test reports.
-
Relevant for roles like penetration testers, ethical hackers, and threat researchers.
-
Requirements: No formal prerequisites, but prior knowledge of networking and scripting is recommended.
-
Cost: $999 (includes training, lab access, and one test attempt).
-
Conclusion
In conclusion, the world of cybersecurity is dynamic and ever-evolving, and staying ahead of the curve is essential in defending against the ever-present threats in the digital realm. The array of certifications available provides a roadmap for professionals at every stage of their cybersecurity journey.
Whether you're a newcomer looking to establish a foothold or a seasoned expert seeking to advance your career, these certifications offer a structured path to sharpen your skills, validate your knowledge, and enhance your professional prospects. From ethical hacking to security management, each certification serves a specific purpose and opens doors to various rewarding roles within the cybersecurity landscape.
In this rapidly changing field, continuous learning is paramount, and acquiring certifications is not just a one-time achievement but an ongoing commitment to excellence. Regardless of where you are in your career, investing in these certifications not only elevates your expertise but also fortifies your ability to protect organizations and individuals from the ever-evolving threat landscape.
Remember that the ideal certification depends on your career goals, interests, and experience level. Combining multiple certifications can create a well-rounded skill set, making you a valuable asset in the ever-expanding realm of cybersecurity. So, choose wisely, invest in your professional development, and stay committed to the pursuit of knowledge in the ever-important field of cybersecurity.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
The company conducts both Instructor-led Classroom training workshops and Instructor-led Live Online Training sessions for learners from across the United States and around the world.
We also provide Corporate Training for enterprise workforce development.
Professional Certification Training:
Quality Management Training:
- Lean Six Sigma Yellow Belt (LSSYB) Certification Training Courses
- Lean Six Sigma Green Belt (LSSGB) Certification Training Courses
- Lean Six Sigma Black Belt (LSSBB) Certification Training Courses
Scrum Training:
- CSM (Certified ScrumMaster) Certification Training Courses
Agile Training:
- PMI-ACP (Agile Certified Professional) Certification Training Courses
DevOps Training:
- DevOps Certification Training Courses
Business Analysis Training by iCert Global:
- ECBA (Entry Certificate in Business Analysis) Certification Training Courses
- CCBA (Certificate of Capability in Business Analysis) Certification Training Courses
- CBAP (Certified Business Analysis Professional) Certification Training Courses
Cyber Security Training:
- Certified Ethical Hacker Training Courses
- Certified Information Systems Security Professional Training Courses
- Certified inrisk and Information Systems Control Training Courses
- Certified Information Security Manager Training Courses
- Certified Information Systems Auditor
Connect with us:
- Subscribe to our YouTube Channel
Visit us at https://www.icertglobal.com/ for more information about our professional certification training courses or Call Now! on +1(713)-518-1187 / +1(713)-287-1214 or e-mail us at info@icertglobal.com.
Please Contact Us for more information about our professional certification training courses to accelerate your career. Let us know your thoughts in the 'Comments' section below.
Digital Marketing Role in 2023: Responsibilities and Skill Requirements
Welcome to the ever-evolving landscape of digital marketing in 2023! In today's fast-paced, technology-driven world, the role of digital marketing has become more pivotal than ever for businesses seeking to thrive in the online realm. As we delve into the "Digital Marketing Job Description: Responsibilities and Skills in 2023," we will explore the dynamic and multifaceted nature of this profession. In this digital era, where consumers are increasingly connected, informed, and discerning, the demands on digital marketers have grown exponentially. This comprehensive guide will not only outline the core responsibilities of a digital marketer but also shed light on the essential skills and competencies required to excel in this exciting and competitive field. Whether you are a seasoned marketing professional looking to adapt to the latest trends or someone aspiring to launch a career in digital marketing, this exploration will serve as your compass through the ever-changing digital marketing landscape of 2023. Join us on this journey to discover what it takes to succeed in the world of digital marketing and stay ahead of the curve in this dynamic and ever-evolving industry.
Table of Contents
-
Growth of Digital Marketing Jobs
-
The Role of a Digital Marketer
-
Digital Marketing Job Description (Sample)
-
Specialist Digital Marketing Skills
-
The Common Elements of a Digital Marketing Job Description
-
Conclusion
Growth of Digital Marketing Jobs
The growth of digital marketing jobs over the past decade has been nothing short of remarkable. As the world becomes increasingly connected and reliant on digital technologies, the demand for skilled professionals in this field has surged. Several key factors can be attributed to this growth
-
Digital Transformation: Businesses across various industries are undergoing digital transformation efforts to stay competitive and reach their target audiences effectively. This has led to an increased demand for digital marketing professionals who can navigate and leverage the digital landscape.
-
Shift in Consumer Behavior: Consumers are spending more time online, from shopping and socializing to seeking information. Companies are keen to capitalize on this trend by employing digital marketing strategies to connect with their target customers where they spend the most time.
-
Data-Driven Decision-Making: The availability of vast amounts of data and analytics tools has made it possible for companies to measure the effectiveness of their marketing campaigns with precision. Digital marketing professionals who can analyze and interpret data are in high demand to drive data-driven decision-making.
-
E-commerce Boom: The growth of e-commerce has been exponential, especially in the wake of global events like the COVID-19 pandemic. Digital marketing plays a critical role in helping e-commerce businesses reach wider audiences, optimize their websites, and drive sales.
-
Social Media Dominance: Social media platforms have become powerful marketing tools. Companies are hiring digital marketers to create and execute social media strategies that engage audiences, build brand awareness, and drive conversions.
-
Search Engine Optimization (SEO): As the competition for online visibility intensifies, SEO expertise is invaluable. Digital marketers skilled in SEO are sought after to improve a website's ranking on search engines like Google.
-
Content Marketing: High-quality content is essential for online success. Content marketing professionals are needed to create compelling, relevant content that resonates with audiences and drives traffic.
-
Specialization: The field of digital marketing has diversified, with various specializations such as email marketing, influencer marketing, and affiliate marketing. This specialization has opened up more career opportunities for professionals with specific expertise.
-
Remote Work: The digital nature of these jobs has made remote work more feasible, allowing companies to tap into a global talent pool and professionals to work from virtually anywhere.
In summary, the growth of digital marketing jobs can be attributed to the ever-increasing importance of digital channels in reaching and engaging with consumers. As businesses continue to invest in their online presence and marketing efforts, the demand for skilled digital marketing professionals is expected to remain robust in the years to come.
The Role of a Digital Marketer
The role of a digital marketer is dynamic, multifaceted, and central to the success of businesses in the digital age. Digital marketers are responsible for developing, implementing, and managing online marketing strategies to achieve various business objectives. Here are some key aspects of the role of a digital marketer:
-
Strategy Development: Digital marketers begin by creating comprehensive digital marketing strategies tailored to their organization's goals. This involves identifying target audiences, defining key performance indicators (KPIs), and selecting the most suitable digital channels and tactics.
-
Content Creation: Content is at the heart of digital marketing. Digital marketers often create a wide range of content, including blog posts, social media updates, videos, infographics, and more. They ensure that content is engaging, relevant, and aligned with the brand's messaging.
-
Search Engine Optimization (SEO): Digital marketers optimize web content and websites to improve their visibility on search engines like Google. This involves keyword research, on-page optimization, and backlink building to drive organic traffic.
-
Social Media Management: Managing and growing a brand's presence on social media platforms is a critical aspect of the role. Digital marketers develop content calendars, engage with followers, run paid advertising campaigns, and track performance metrics.
-
Email Marketing: Email still stands as a potent marketing instrument. Digital marketers create and execute email campaigns to nurture leads, retain customers, and drive conversions. They also segment email lists for targeted messaging.
-
Paid Advertising: Digital marketers manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and LinkedIn Ads. They set budgets, create ad creatives, and continuously optimize campaigns to maximize ROI.
-
Analytics and Data Analysis: The foundation of digital marketing relies on data. Marketers use analytics tools to track website traffic, user behavior, and campaign performance. They analyze this data to make informed decisions and adjust strategies as needed.
-
Conversion Rate Optimization (CRO): Improving the conversion rate of website visitors into customers or leads is a key responsibility. Digital marketers conduct A/B testing and implement changes to enhance the user experience and drive conversions.
-
Affiliate Marketing: Some digital marketers work on affiliate marketing programs, where they collaborate with affiliates to promote products or services in exchange for commissions.
-
Influencer Marketing: Digital marketers identify and partner with influencers or industry experts to promote their brand or products to a wider audience.
-
Online Reputation Management: Monitoring and managing the online reputation of a brand is crucial. Digital marketers address negative feedback and promote positive reviews and content.
-
Marketing Automation: Digital marketers often use marketing automation tools to streamline repetitive tasks, such as email sending, lead nurturing, and campaign tracking.
-
Compliance and Privacy: Staying informed about digital marketing regulations and ensuring compliance with data privacy laws (e.g., GDPR, CCPA) is essential.
-
Continuous Learning: Given the rapidly evolving nature of digital marketing, professionals in this role must stay updated on industry trends, emerging technologies, and best practices.
In conclusion, the role of a digital marketer is multifaceted and ever-evolving. Success in this field requires a combination of creativity, analytical skills, adaptability, and a deep understanding of digital tools and platforms. Digital marketers play a pivotal role in helping businesses connect with their target audiences, drive growth, and stay competitive in the digital landscape.
Digital Marketing Job Description (Sample)
Job Title: Digital Marketer
Job Description:
As a Digital Marketing Specialist you will be responsible for planning, executing, and optimizing our digital marketing campaigns across various online platforms. Your goal will be to enhance our online presence, engage with our target audience, and ultimately drive business growth.
Key Responsibilities:
-
Digital Strategy: Develop and implement comprehensive digital marketing strategies that align with company goals and objectives.
-
Content Creation: Create, edit, and curate compelling and relevant content for various digital channels, including blog posts, social media updates, emails, and more.
-
SEO Optimization: Conduct keyword research, optimize website content, and monitor and improve search engine rankings to increase organic traffic.
-
Social Media Management: Manage and grow our social media presence by creating content calendars, running paid campaigns, and engaging with our online community.
-
Email Marketing: Plan and execute email marketing campaigns, segment audiences, create engaging email content, and monitor campaign performance.
-
Paid Advertising: Manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and others to drive traffic, conversions, and ROI.
-
Analytics and Reporting: Monitor website analytics, user behavior, and campaign performance using tools like Google Analytics. Offer consistent reports and insights to steer decision-making.
-
Conversion Rate Optimization (CRO): Identify opportunities to improve website conversion rates through A/B testing, user experience enhancements, and other strategies.
-
Affiliate Marketing: Collaborate with affiliates and partners to promote products or services and track affiliate performance.
-
Online Reputation Management: Monitor online reviews and comments, address negative feedback, and encourage positive reviews and brand mentions.
Qualifications:
-
A Bachelor's degree in Marketing, Digital Marketing, or a related field is required.
-
Demonstrated expertise in digital marketing, substantiated by a robust portfolio of successful campaigns.
-
Proficiency in utilizing digital marketing tools and platforms, such as Google Analytics, social media management tools, and email marketing software.
-
Profound knowledge of SEO best practices and strategies is essential.
-
Exceptional written and verbal communication skills are a must.
-
Capable of working autonomously and as part of a collaborative team.
-
Possesses an analytical mindset, enabling the interpretation of data and the formulation of data-driven decisions.
-
Certifications in digital marketing (e.g., Google Ads, HubSpot, or similar) are a plus.
Specialist Digital Marketing Skills
Specialist digital marketing skills are essential for professionals who want to excel in the field and stand out in an increasingly competitive landscape. Here are some specialized digital marketing skills that can make a significant difference in your career:
-
Search Engine Optimization (SEO):
-
Technical SEO: Understanding and optimizing website structure, crawlability, and performance.
-
On-Page SEO: Mastering keyword research, optimization, and content quality.
-
Off-Page SEO: Building high-quality backlinks and managing link-building strategies.
-
Content Marketing:
-
Content Strategy: Creating content strategies that align with business goals.
-
Content Creation: Writing, editing, and producing various content types, such as blog posts, videos, infographics, and eBooks.
-
Content Promotion: Effective distribution and promotion of content across channels.
-
Social Media Marketing:
-
Social Media Advertising: Creating and managing paid ad campaigns on platforms like Facebook Ads, Instagram Ads, and LinkedIn Ads.
-
Community Management: Engaging with the audience, responding to comments, and managing brand reputation.
-
Social Media Analytics: Analyzing and interpreting social media data to refine strategies.
-
Email Marketing:
-
Email Automation: Designing and implementing automated email campaigns.
-
Segmentation: Creating targeted email lists for personalized messaging.
-
A/B Testing: Experimenting with subject lines, content, and CTAs to optimize email performance.
-
Pay-Per-Click (PPC) Advertising:
-
Google Ads: Overseeing and enhancing Google Ads campaigns.
-
Display Advertising: Creating and optimizing banner ads for display networks.
-
Remarketing: Implementing strategies to target previous website visitors.
-
Analytics and Data Analysis:
-
Google Analytics: Proficiency in using Google Analytics to track website performance and user behavior.
-
Data Interpretation: Analyzing data to derive actionable insights and make data-driven decisions.
-
Conversion Rate Optimization (CRO): Optimizing websites and landing pages for improved conversion rates.
-
Marketing Automation:
-
Marketing Automation Platforms: Familiarity with tools like HubSpot, Marketo, or Salesforce for automated marketing workflows.
-
Lead Nurturing: Creating and managing lead nurturing campaigns to guide prospects through the sales funnel.
-
Affiliate Marketing:
-
Partner Outreach: Building and managing relationships with affiliate partners.
-
Program Management: Running affiliate marketing programs and tracking partner performance.
-
Influencer Marketing:
-
Influencer Selection: Identifying and partnering with influencers who align with the brand.
-
Campaign Management: Planning and executing influencer marketing campaigns.
-
E-commerce Optimization:
-
E-commerce SEO: Executing e-commerce website-focused SEO strategies.
-
Conversion Optimization: Enhancing product pages, checkout processes, and user experience to boost sales.
-
Mobile Marketing:
-
Mobile App Marketing: Promoting mobile apps through app stores and in-app advertising.
-
Mobile Website Optimization: Ensuring websites are mobile-friendly and load quickly on mobile devices.
-
Data Privacy and Compliance:
-
Comprehending and complying with data privacy regulations such as GDPR and CCPA.
-
Ensuring marketing practices comply with legal requirements.
Remember that digital marketing is a dynamic field, and staying updated with the latest trends, tools, and techniques is crucial to maintaining and enhancing your specialist skills in the long term. Continual learning and adaptation are key to success in digital marketing.
The Common Elements of a Digital Marketing Job Description
Digital marketing job descriptions typically share common elements that help define the role, responsibilities, qualifications, and expectations for candidates. Here are the common elements you can find in a digital marketing job description:
-
Job Title: The job title, such as "Digital Marketing Specialist," "Digital Marketing Manager," or "Digital Marketing Coordinator," indicates the specific role within the digital marketing field.
-
Company Overview: A brief introduction to the hiring company, including its industry, mission, and values, sets the context for the role.
-
Job Location: Specifies where the position is based, which can be in a specific city, state, or country, or may indicate whether it's a remote position.
-
Job Summary/Objective: A concise statement outlining the primary purpose of the role and what the candidate is expected to achieve in the position.
-
Responsibilities/Duties: A detailed list of the day-to-day tasks and responsibilities expected of the candidate. This section often includes items such as content creation, SEO optimization, social media management, and email marketing.
-
Qualifications/Skills: Lists the education, experience, and skills required or preferred for the role. This section may include qualifications like a bachelor's degree in marketing, proficiency in specific tools or platforms, and soft skills like communication and teamwork.
-
Experience: Often divided into "required experience" and "preferred experience," this section outlines the level of experience the company is seeking in candidates.
-
Certifications: If specific certifications (e.g., Google Ads, HubSpot, Facebook Blueprint) are required or preferred, they are listed here.
-
Competencies: Describes the competencies or attributes the ideal candidate should possess, such as analytical skills, creativity, adaptability, and attention to detail.
-
Work Environment: Provides information about the work environment, team size, and any unique aspects of the workplace.
-
Salary and Benefits: In some job descriptions, you may find information about the salary range or compensation package offered, as well as details about benefits like health insurance, retirement plans, and bonuses.
-
How to Apply: Instructions on how candidates should apply, which often include submitting a resume, cover letter, and portfolio, and providing contact details for application submission.
-
Application Deadline: If there's a specific deadline for applications, it's mentioned here.
-
Equal Opportunity Statement: Many job descriptions include a statement about the company's commitment to diversity and equal opportunity employment.
-
Contact Information: Provides contact details for inquiries or questions related to the job posting.
-
Company Culture: Some job descriptions may include information about the company's culture, values, or mission to help candidates understand the work environment and ethos.
These common elements help candidates understand the role, evaluate their qualifications, and prepare their applications accordingly. Employers use them to communicate their expectations clearly and attract candidates who are the best fit for the position and the company.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
The landscape of digital marketing in 2023 is more dynamic and critical than ever before. As this guide has illuminated, the responsibilities and skills required of digital marketers have evolved to meet the demands of a rapidly changing digital ecosystem. In a world where businesses are vying for online visibility and customer engagement, digital marketers play a pivotal role in shaping strategies that drive success. Whether it's mastering the intricacies of SEO, creating compelling content, or leveraging emerging technologies, the digital marketer of 2023 must be adaptable, data-savvy, and customer-centric. As we navigate this ever-shifting terrain, it becomes clear that digital marketing is not just a profession; it's an art and science, and those who embrace its challenges and opportunities will continue to be at the forefront of the digital revolution. So, whether you're a seasoned professional or just beginning your journey in this field, the world of digital marketing in 2023 is ripe with possibilities for those who are willing to learn, adapt, and innovate.
Read More
Welcome to the ever-evolving landscape of digital marketing in 2023! In today's fast-paced, technology-driven world, the role of digital marketing has become more pivotal than ever for businesses seeking to thrive in the online realm. As we delve into the "Digital Marketing Job Description: Responsibilities and Skills in 2023," we will explore the dynamic and multifaceted nature of this profession. In this digital era, where consumers are increasingly connected, informed, and discerning, the demands on digital marketers have grown exponentially. This comprehensive guide will not only outline the core responsibilities of a digital marketer but also shed light on the essential skills and competencies required to excel in this exciting and competitive field. Whether you are a seasoned marketing professional looking to adapt to the latest trends or someone aspiring to launch a career in digital marketing, this exploration will serve as your compass through the ever-changing digital marketing landscape of 2023. Join us on this journey to discover what it takes to succeed in the world of digital marketing and stay ahead of the curve in this dynamic and ever-evolving industry.
Table of Contents
-
Growth of Digital Marketing Jobs
-
The Role of a Digital Marketer
-
Digital Marketing Job Description (Sample)
-
Specialist Digital Marketing Skills
-
The Common Elements of a Digital Marketing Job Description
-
Conclusion
Growth of Digital Marketing Jobs
The growth of digital marketing jobs over the past decade has been nothing short of remarkable. As the world becomes increasingly connected and reliant on digital technologies, the demand for skilled professionals in this field has surged. Several key factors can be attributed to this growth
-
Digital Transformation: Businesses across various industries are undergoing digital transformation efforts to stay competitive and reach their target audiences effectively. This has led to an increased demand for digital marketing professionals who can navigate and leverage the digital landscape.
-
Shift in Consumer Behavior: Consumers are spending more time online, from shopping and socializing to seeking information. Companies are keen to capitalize on this trend by employing digital marketing strategies to connect with their target customers where they spend the most time.
-
Data-Driven Decision-Making: The availability of vast amounts of data and analytics tools has made it possible for companies to measure the effectiveness of their marketing campaigns with precision. Digital marketing professionals who can analyze and interpret data are in high demand to drive data-driven decision-making.
-
E-commerce Boom: The growth of e-commerce has been exponential, especially in the wake of global events like the COVID-19 pandemic. Digital marketing plays a critical role in helping e-commerce businesses reach wider audiences, optimize their websites, and drive sales.
-
Social Media Dominance: Social media platforms have become powerful marketing tools. Companies are hiring digital marketers to create and execute social media strategies that engage audiences, build brand awareness, and drive conversions.
-
Search Engine Optimization (SEO): As the competition for online visibility intensifies, SEO expertise is invaluable. Digital marketers skilled in SEO are sought after to improve a website's ranking on search engines like Google.
-
Content Marketing: High-quality content is essential for online success. Content marketing professionals are needed to create compelling, relevant content that resonates with audiences and drives traffic.
-
Specialization: The field of digital marketing has diversified, with various specializations such as email marketing, influencer marketing, and affiliate marketing. This specialization has opened up more career opportunities for professionals with specific expertise.
-
Remote Work: The digital nature of these jobs has made remote work more feasible, allowing companies to tap into a global talent pool and professionals to work from virtually anywhere.
In summary, the growth of digital marketing jobs can be attributed to the ever-increasing importance of digital channels in reaching and engaging with consumers. As businesses continue to invest in their online presence and marketing efforts, the demand for skilled digital marketing professionals is expected to remain robust in the years to come.
The Role of a Digital Marketer
The role of a digital marketer is dynamic, multifaceted, and central to the success of businesses in the digital age. Digital marketers are responsible for developing, implementing, and managing online marketing strategies to achieve various business objectives. Here are some key aspects of the role of a digital marketer:
-
Strategy Development: Digital marketers begin by creating comprehensive digital marketing strategies tailored to their organization's goals. This involves identifying target audiences, defining key performance indicators (KPIs), and selecting the most suitable digital channels and tactics.
-
Content Creation: Content is at the heart of digital marketing. Digital marketers often create a wide range of content, including blog posts, social media updates, videos, infographics, and more. They ensure that content is engaging, relevant, and aligned with the brand's messaging.
-
Search Engine Optimization (SEO): Digital marketers optimize web content and websites to improve their visibility on search engines like Google. This involves keyword research, on-page optimization, and backlink building to drive organic traffic.
-
Social Media Management: Managing and growing a brand's presence on social media platforms is a critical aspect of the role. Digital marketers develop content calendars, engage with followers, run paid advertising campaigns, and track performance metrics.
-
Email Marketing: Email still stands as a potent marketing instrument. Digital marketers create and execute email campaigns to nurture leads, retain customers, and drive conversions. They also segment email lists for targeted messaging.
-
Paid Advertising: Digital marketers manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and LinkedIn Ads. They set budgets, create ad creatives, and continuously optimize campaigns to maximize ROI.
-
Analytics and Data Analysis: The foundation of digital marketing relies on data. Marketers use analytics tools to track website traffic, user behavior, and campaign performance. They analyze this data to make informed decisions and adjust strategies as needed.
-
Conversion Rate Optimization (CRO): Improving the conversion rate of website visitors into customers or leads is a key responsibility. Digital marketers conduct A/B testing and implement changes to enhance the user experience and drive conversions.
-
Affiliate Marketing: Some digital marketers work on affiliate marketing programs, where they collaborate with affiliates to promote products or services in exchange for commissions.
-
Influencer Marketing: Digital marketers identify and partner with influencers or industry experts to promote their brand or products to a wider audience.
-
Online Reputation Management: Monitoring and managing the online reputation of a brand is crucial. Digital marketers address negative feedback and promote positive reviews and content.
-
Marketing Automation: Digital marketers often use marketing automation tools to streamline repetitive tasks, such as email sending, lead nurturing, and campaign tracking.
-
Compliance and Privacy: Staying informed about digital marketing regulations and ensuring compliance with data privacy laws (e.g., GDPR, CCPA) is essential.
-
Continuous Learning: Given the rapidly evolving nature of digital marketing, professionals in this role must stay updated on industry trends, emerging technologies, and best practices.
In conclusion, the role of a digital marketer is multifaceted and ever-evolving. Success in this field requires a combination of creativity, analytical skills, adaptability, and a deep understanding of digital tools and platforms. Digital marketers play a pivotal role in helping businesses connect with their target audiences, drive growth, and stay competitive in the digital landscape.
Digital Marketing Job Description (Sample)
Job Title: Digital Marketer
Job Description:
As a Digital Marketing Specialist you will be responsible for planning, executing, and optimizing our digital marketing campaigns across various online platforms. Your goal will be to enhance our online presence, engage with our target audience, and ultimately drive business growth.
Key Responsibilities:
-
Digital Strategy: Develop and implement comprehensive digital marketing strategies that align with company goals and objectives.
-
Content Creation: Create, edit, and curate compelling and relevant content for various digital channels, including blog posts, social media updates, emails, and more.
-
SEO Optimization: Conduct keyword research, optimize website content, and monitor and improve search engine rankings to increase organic traffic.
-
Social Media Management: Manage and grow our social media presence by creating content calendars, running paid campaigns, and engaging with our online community.
-
Email Marketing: Plan and execute email marketing campaigns, segment audiences, create engaging email content, and monitor campaign performance.
-
Paid Advertising: Manage paid advertising campaigns on platforms like Google Ads, Facebook Ads, and others to drive traffic, conversions, and ROI.
-
Analytics and Reporting: Monitor website analytics, user behavior, and campaign performance using tools like Google Analytics. Offer consistent reports and insights to steer decision-making.
-
Conversion Rate Optimization (CRO): Identify opportunities to improve website conversion rates through A/B testing, user experience enhancements, and other strategies.
-
Affiliate Marketing: Collaborate with affiliates and partners to promote products or services and track affiliate performance.
-
Online Reputation Management: Monitor online reviews and comments, address negative feedback, and encourage positive reviews and brand mentions.
Qualifications:
-
A Bachelor's degree in Marketing, Digital Marketing, or a related field is required.
-
Demonstrated expertise in digital marketing, substantiated by a robust portfolio of successful campaigns.
-
Proficiency in utilizing digital marketing tools and platforms, such as Google Analytics, social media management tools, and email marketing software.
-
Profound knowledge of SEO best practices and strategies is essential.
-
Exceptional written and verbal communication skills are a must.
-
Capable of working autonomously and as part of a collaborative team.
-
Possesses an analytical mindset, enabling the interpretation of data and the formulation of data-driven decisions.
-
Certifications in digital marketing (e.g., Google Ads, HubSpot, or similar) are a plus.
Specialist Digital Marketing Skills
Specialist digital marketing skills are essential for professionals who want to excel in the field and stand out in an increasingly competitive landscape. Here are some specialized digital marketing skills that can make a significant difference in your career:
-
Search Engine Optimization (SEO):
-
Technical SEO: Understanding and optimizing website structure, crawlability, and performance.
-
On-Page SEO: Mastering keyword research, optimization, and content quality.
-
Off-Page SEO: Building high-quality backlinks and managing link-building strategies.
-
-
Content Marketing:
-
Content Strategy: Creating content strategies that align with business goals.
-
Content Creation: Writing, editing, and producing various content types, such as blog posts, videos, infographics, and eBooks.
-
Content Promotion: Effective distribution and promotion of content across channels.
-
-
Social Media Marketing:
-
Social Media Advertising: Creating and managing paid ad campaigns on platforms like Facebook Ads, Instagram Ads, and LinkedIn Ads.
-
Community Management: Engaging with the audience, responding to comments, and managing brand reputation.
-
Social Media Analytics: Analyzing and interpreting social media data to refine strategies.
-
-
Email Marketing:
-
Email Automation: Designing and implementing automated email campaigns.
-
Segmentation: Creating targeted email lists for personalized messaging.
-
A/B Testing: Experimenting with subject lines, content, and CTAs to optimize email performance.
-
-
Pay-Per-Click (PPC) Advertising:
-
Google Ads: Overseeing and enhancing Google Ads campaigns.
-
Display Advertising: Creating and optimizing banner ads for display networks.
-
Remarketing: Implementing strategies to target previous website visitors.
-
-
Analytics and Data Analysis:
-
Google Analytics: Proficiency in using Google Analytics to track website performance and user behavior.
-
Data Interpretation: Analyzing data to derive actionable insights and make data-driven decisions.
-
Conversion Rate Optimization (CRO): Optimizing websites and landing pages for improved conversion rates.
-
-
Marketing Automation:
-
Marketing Automation Platforms: Familiarity with tools like HubSpot, Marketo, or Salesforce for automated marketing workflows.
-
Lead Nurturing: Creating and managing lead nurturing campaigns to guide prospects through the sales funnel.
-
-
Affiliate Marketing:
-
Partner Outreach: Building and managing relationships with affiliate partners.
-
Program Management: Running affiliate marketing programs and tracking partner performance.
-
-
Influencer Marketing:
-
Influencer Selection: Identifying and partnering with influencers who align with the brand.
-
Campaign Management: Planning and executing influencer marketing campaigns.
-
-
E-commerce Optimization:
-
E-commerce SEO: Executing e-commerce website-focused SEO strategies.
-
Conversion Optimization: Enhancing product pages, checkout processes, and user experience to boost sales.
-
-
Mobile Marketing:
-
Mobile App Marketing: Promoting mobile apps through app stores and in-app advertising.
-
Mobile Website Optimization: Ensuring websites are mobile-friendly and load quickly on mobile devices.
-
-
Data Privacy and Compliance:
-
Comprehending and complying with data privacy regulations such as GDPR and CCPA.
-
Ensuring marketing practices comply with legal requirements.
Remember that digital marketing is a dynamic field, and staying updated with the latest trends, tools, and techniques is crucial to maintaining and enhancing your specialist skills in the long term. Continual learning and adaptation are key to success in digital marketing.
The Common Elements of a Digital Marketing Job Description
Digital marketing job descriptions typically share common elements that help define the role, responsibilities, qualifications, and expectations for candidates. Here are the common elements you can find in a digital marketing job description:
-
Job Title: The job title, such as "Digital Marketing Specialist," "Digital Marketing Manager," or "Digital Marketing Coordinator," indicates the specific role within the digital marketing field.
-
Company Overview: A brief introduction to the hiring company, including its industry, mission, and values, sets the context for the role.
-
Job Location: Specifies where the position is based, which can be in a specific city, state, or country, or may indicate whether it's a remote position.
-
Job Summary/Objective: A concise statement outlining the primary purpose of the role and what the candidate is expected to achieve in the position.
-
Responsibilities/Duties: A detailed list of the day-to-day tasks and responsibilities expected of the candidate. This section often includes items such as content creation, SEO optimization, social media management, and email marketing.
-
Qualifications/Skills: Lists the education, experience, and skills required or preferred for the role. This section may include qualifications like a bachelor's degree in marketing, proficiency in specific tools or platforms, and soft skills like communication and teamwork.
-
Experience: Often divided into "required experience" and "preferred experience," this section outlines the level of experience the company is seeking in candidates.
-
Certifications: If specific certifications (e.g., Google Ads, HubSpot, Facebook Blueprint) are required or preferred, they are listed here.
-
Competencies: Describes the competencies or attributes the ideal candidate should possess, such as analytical skills, creativity, adaptability, and attention to detail.
-
Work Environment: Provides information about the work environment, team size, and any unique aspects of the workplace.
-
Salary and Benefits: In some job descriptions, you may find information about the salary range or compensation package offered, as well as details about benefits like health insurance, retirement plans, and bonuses.
-
How to Apply: Instructions on how candidates should apply, which often include submitting a resume, cover letter, and portfolio, and providing contact details for application submission.
-
Application Deadline: If there's a specific deadline for applications, it's mentioned here.
-
Equal Opportunity Statement: Many job descriptions include a statement about the company's commitment to diversity and equal opportunity employment.
-
Contact Information: Provides contact details for inquiries or questions related to the job posting.
-
Company Culture: Some job descriptions may include information about the company's culture, values, or mission to help candidates understand the work environment and ethos.
These common elements help candidates understand the role, evaluate their qualifications, and prepare their applications accordingly. Employers use them to communicate their expectations clearly and attract candidates who are the best fit for the position and the company.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
Project Management: PMP, CAPM ,PMI RMP
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
Business Analysis: CBAP, CCBA, ECBA
Agile Training: PMI-ACP , CSM , CSPO
Scrum Training: CSM
DevOps
Program Management: PgMP
Cloud Technology: SMAC Certication
Big Data: Big Data and Hadoop Administrator
Digital Marketing : Digital Marketing Certification
Data Science : Power BI Certification
Cyber Security : CISA Certification
Emerging Technologies : Robotic Process Automation
Conclusion
The landscape of digital marketing in 2023 is more dynamic and critical than ever before. As this guide has illuminated, the responsibilities and skills required of digital marketers have evolved to meet the demands of a rapidly changing digital ecosystem. In a world where businesses are vying for online visibility and customer engagement, digital marketers play a pivotal role in shaping strategies that drive success. Whether it's mastering the intricacies of SEO, creating compelling content, or leveraging emerging technologies, the digital marketer of 2023 must be adaptable, data-savvy, and customer-centric. As we navigate this ever-shifting terrain, it becomes clear that digital marketing is not just a profession; it's an art and science, and those who embrace its challenges and opportunities will continue to be at the forefront of the digital revolution. So, whether you're a seasoned professional or just beginning your journey in this field, the world of digital marketing in 2023 is ripe with possibilities for those who are willing to learn, adapt, and innovate.
Mastering RPA: Your Blueprint for Success in 2023
In the rapidly evolving world of technology and automation, Robotic Process Automation (RPA) has emerged as a transformative force, reshaping the way organizations operate and streamline their workflows. As we step into 2023, the demand for skilled RPA developers is at an all-time high, making it an opportune moment to embark on a journey of mastering this cutting-edge field. "Mastering RPA: Your Blueprint for Success in 2023" is your guide to navigating the intricate landscape of RPA, offering insights, strategies, and practical advice for those aspiring to become proficient RPA developers. This blueprint is not just about acquiring technical skills but also understanding the broader context of automation, soft skills, and the ever-changing trends that will define the RPA landscape this year and beyond. Whether you're a newcomer or a seasoned professional, this guide is designed to equip you with the knowledge and tools needed to thrive in the world of RPA and make a meaningful impact in the digital age.
Table of Contents
-
Introduction to RPA (Robotic Process Automation)
-
Choosing the Right RPA Tool
-
Programming Skills
-
RPA Certification
-
Advanced RPA Techniques
-
Best Practices in RPA Development
-
Soft Skills for RPA Developers
-
Networking and Community Involvement
-
Keeping Up with RPA Trends
-
Building a Career as an RPA Developer
-
Conclusion
Introduction to RPA (Robotic Process Automation)
Robotic Process Automation (RPA) is a transformative technology that employs software bots to automate repetitive, rule-based tasks within organizations. These digital workers, though not physical robots, replicate human actions in interacting with software applications, aiming to streamline and optimize business processes. RPA offers unparalleled accuracy, scalability, and cost-efficiency, making it a crucial tool for various industries, from finance to healthcare. In 2023, as RPA's role in digital transformation grows, aspiring RPA developers have a promising career opportunity in harnessing this technology's potential for efficiency and innovation.
Choosing the Right RPA Tool
Selecting the appropriate Robotic Process Automation (RPA) tool is a critical decision on your path to becoming an RPA developer. In 2023, there is a plethora of RPA tools available, each with its unique strengths and capabilities. To make an informed choice, start by assessing your specific automation needs and objectives. Consider factors such as the complexity of tasks you want to automate, the compatibility of the tool with your existing systems, scalability requirements, and your budget. Popular RPA tools like UiPath, Automation Anywhere, and Blue Prism offer robust features and strong developer communities, but it's essential to evaluate them in terms of ease of use, extensibility, and the support they provide for your chosen programming languages. Additionally, look for trial versions or free community editions to gain hands-on experience and ensure a seamless fit for your automation projects. Keep in mind that the right RPA tool can significantly impact your efficiency and success as an RPA developer in 2023 and beyond.
Programming Skills
Becoming a proficient RPA (Robotic Process Automation) developer in 2023 requires a solid foundation in programming. While RPA tools provide a user-friendly interface for automation, understanding programming concepts is essential for building complex and customized automation solutions. Here are some key programming skills you should focus on:
-
Scripting Languages: Mastery of scripting languages such as Python, JavaScript, or PowerShell is invaluable. Python, in particular, is widely used in RPA development due to its simplicity and versatility.
-
Object-Oriented Programming (OOP): Understanding OOP principles is beneficial for creating reusable and well-structured code, especially when working with more advanced RPA projects.
-
Basic Algorithms and Data Structures: A grasp of fundamental algorithms and data structures like arrays, lists, and dictionaries is essential for efficiently manipulating data in your automation workflows.
-
Error Handling: Learn to handle exceptions and errors gracefully in your code, ensuring that your RPA bots can recover from unexpected issues during automation processes.
-
Debugging Skills: Proficiency in debugging tools and techniques is crucial for identifying and resolving issues in your automation scripts.
-
Regular Expressions: Regular expressions (regex) are essential for text manipulation and pattern matching, which are common tasks in RPA.
-
Version Control: Familiarize yourself with version control systems like Git to manage and track changes in your codebase, promoting collaboration and code stability.
-
API Integration: Understanding how to interact with APIs (Application Programming Interfaces) is essential for connecting RPA bots with external systems and services.
-
Database Basics: Knowledge of database concepts and SQL (Structured Query Language) can be valuable when working with data-driven automation processes.
-
Web Development Skills: Basic web development knowledge, including HTML, CSS, and JavaScript, can be beneficial for automating tasks involving web interfaces and browser interactions.
-
Security Awareness: Be aware of security best practices and potential vulnerabilities, especially when dealing with sensitive data or automation in secure environments.
-
Continual Learning: Stay updated with programming languages and frameworks relevant to RPA, as the field is continually evolving.
By honing these programming skills, you'll be better equipped to create efficient, reliable, and customized RPA solutions that address the specific automation needs of your organization or clients in 2023 and beyond.
RPA Certification
RPA certification is a pivotal career move in the thriving field of Robotic Process Automation, especially in 2023, as it validates your expertise with specific RPA tools like UiPath, Automation Anywhere, or Blue Prism. Earning such credentials not only enhances your job prospects and earning potential but also positions you as a credible RPA professional in high demand by organizations worldwide. With certification, you gain access to exclusive networks, stay updated on industry trends, and continually expand your skill set, making it an essential step for anyone looking to excel in the dynamic world of RPA.
Advanced RPA Techniques
As a burgeoning RPA (Robotic Process Automation) developer in 2023, advancing your skills beyond the basics is crucial for tackling complex automation challenges and delivering exceptional value to your organization. To excel in the field, delve into advanced RPA techniques:
-
Exception Handling: Master the art of handling exceptions and errors gracefully, enabling your bots to recover autonomously when unexpected situations arise during automation processes.
-
Integration with APIs: Go beyond basic automation by learning how to seamlessly integrate RPA bots with various application programming interfaces (APIs) to exchange data and execute actions across multiple systems.
-
Data Manipulation: Explore advanced data manipulation techniques, including complex data transformations, parsing unstructured data, and handling large datasets efficiently.
-
Orchestrator and Queue Management: Learn how to use RPA orchestrators effectively to manage bot execution, schedule tasks, and monitor automation workflows. Understand queue management for efficient task distribution.
-
Machine Learning and AI Integration: Combine RPA with machine learning and artificial intelligence to create intelligent automation solutions that can make data-driven decisions and adapt to changing conditions.
-
Citizen Developer Enablement: Develop strategies for involving non-technical stakeholders or citizen developers in the RPA development process while maintaining governance and control.
-
Advanced Debugging and Testing: Hone your debugging skills and implement robust testing practices to ensure the reliability and stability of your automation solutions.
-
Scalability and Performance Optimization: Discover techniques for scaling up your RPA deployments and optimizing bot performance, allowing your solutions to handle larger workloads efficiently.
-
Security Best Practices: Deepen your understanding of security considerations in RPA, including data encryption, access controls, and compliance with industry regulations.
-
Governance and Compliance: Establish governance frameworks to manage the lifecycle of automation projects, maintain documentation, and ensure compliance with organizational policies.
-
Continuous Learning: Stay at the forefront of RPA by keeping up with emerging trends, attending advanced training programs, and participating in RPA communities.
By embracing these advanced RPA techniques, you position yourself as a versatile and skilled developer capable of addressing complex automation scenarios and driving innovation within your organization. In 2023, as RPA continues to evolve, your mastery of these advanced skills will be invaluable in delivering efficiency and automation excellence.
Best Practices in RPA Development
In the dynamic landscape of Robotic Process Automation (RPA), adhering to best practices is essential for creating robust, maintainable, and efficient automation solutions. In 2023, as RPA adoption continues to surge, consider the following best practices for successful RPA development:
-
Requirements Analysis: Begin with a thorough understanding of the business process you aim to automate, involving stakeholders to define clear objectives and expected outcomes.
-
Modularity and Reusability: Design your RPA workflows in a modular fashion, promoting code reusability to save time and effort in future automation projects.
-
Error Handling: Implement comprehensive error handling mechanisms to gracefully manage exceptions, log errors, and ensure the reliability of your bots.
-
Documentation: Maintain detailed documentation for your automation projects, including process maps, code comments, and version histories, to facilitate collaboration and troubleshooting.
-
Testing and Validation: Rigorously test your automation workflows in a controlled environment to verify accuracy, and conduct user acceptance testing (UAT) to ensure alignment with business requirements.
-
Security Protocols: Prioritize security by encrypting sensitive data, adhering to access controls, and complying with industry-specific regulations to safeguard critical information.
-
Code Review: Collaborate with peers for code reviews to identify potential improvements, maintain code quality, and ensure adherence to coding standards.
-
Version Control: Employ version control systems like Git to manage changes, track revisions, and enable collaboration with team members.
-
Scalability: Design your RPA solutions with scalability in mind to accommodate increasing workloads and future process enhancements.
-
Monitoring and Analytics: Implement monitoring tools and analytics dashboards to gain insights into bot performance, detect anomalies, and identify areas for optimization.
-
Compliance and Governance: Establish governance frameworks that align with organizational policies, ensuring proper management and oversight of automation projects.
-
Training and Knowledge Sharing: Invest in continuous learning for your team and foster a culture of knowledge sharing to keep abreast of RPA advancements and best practices.
-
Change Management: Develop a change management strategy to prepare employees for the adoption of RPA and address any potential resistance to automation.
-
Robust Data Handling: Pay special attention to data input and output, validate data integrity, and handle data securely throughout the automation process.
-
Performance Optimization: Continually analyze and optimize your automation workflows to enhance efficiency and minimize resource consumption.
By incorporating these best practices into your RPA development process, you'll not only ensure the success of your automation initiatives but also contribute to the long-term growth and stability of your organization's RPA ecosystem in the dynamic landscape of 2023 and beyond.
Soft Skills for RPA Developers
In the ever-evolving world of Robotic Process Automation (RPA), technical prowess alone is not sufficient for success. As an RPA developer in 2023, honing soft skills is equally critical to navigate the complexities of human-machine collaboration and excel in this dynamic field. Here are the essential soft skills for RPA developers:
-
Communication Skills: Effective communication with both technical and non-technical stakeholders is vital for understanding automation requirements, explaining technical concepts, and ensuring alignment with business objectives.
-
Problem-Solving and Critical Thinking: Develop strong problem-solving and critical thinking abilities to identify automation opportunities, troubleshoot issues, and optimize RPA solutions.
-
Adaptability: Embrace change and adapt to evolving technologies, tools, and methodologies in the fast-paced RPA landscape, as well as to shifting business priorities.
-
Attention to Detail: Pay meticulous attention to detail when designing, coding, and testing RPA workflows to ensure accuracy and reliability in automated processes.
-
Time Management: Efficiently manage your time and prioritize tasks to meet project deadlines, especially when handling multiple automation projects simultaneously.
-
Collaboration: Foster collaboration within cross-functional teams, as RPA often requires cooperation between developers, business analysts, and end-users to achieve successful automation outcomes.
-
Empathy: Understand end-users' needs and concerns, empathize with their challenges, and design RPA solutions that enhance their work experience rather than replace it.
-
Customer-Centric Approach: Keep the customer's perspective at the forefront of RPA development, striving to deliver solutions that align with business goals and improve customer experiences.
-
Creativity and Innovation: Cultivate creativity to find innovative ways to automate processes and drive business efficiencies, going beyond the obvious solutions.
-
Resilience: Stay resilient in the face of setbacks or challenges during the development and implementation of RPA projects, persistently seeking solutions.
-
Leadership: Develop leadership skills to guide teams, mentor junior developers, and take ownership of complex RPA projects.
-
Ethical Considerations: Navigate ethical dilemmas that may arise when automating tasks and handling sensitive data, ensuring compliance with ethical guidelines and data protection regulations.
-
Cultural Awareness: Recognize and respect cultural differences, as RPA is deployed in organizations with diverse workforces and global reach.
-
Client-Facing Skills: If working in an RPA consulting role, strong client-facing skills are essential for understanding client needs, managing expectations, and building lasting client relationships.
-
Continuous Learning: Cultivate a growth mindset and commit to continuous learning, staying updated on RPA trends, emerging technologies, and best practices.
These soft skills complement your technical expertise, making you a well-rounded and effective RPA developer capable of collaborating seamlessly in human-machine partnerships and driving meaningful automation outcomes in 2023's dynamic RPA landscape.
Networking and Community Involvement
Networking and community involvement are essential for RPA developers in 2023, as they play a pivotal role in personal and professional growth within the dynamic realm of Robotic Process Automation. Engaging with online forums, professional associations, meetups, and conferences allows developers to connect with peers, stay abreast of industry trends, and share valuable insights. These interactions provide opportunities to discuss best practices, explore real-world use cases, and even collaborate on projects. Additionally, contributing to open-source RPA initiatives, blogging, or offering mentorship not only showcases expertise but also strengthens the RPA community. By actively participating in the RPA network, developers can cultivate a rich support system, access a wealth of knowledge, and establish themselves as respected figures in the field. This collaborative spirit not only fosters personal growth but also contributes to the advancement of RPA as a transformative technology.
Keeping Up with RPA Trends
In the fast-paced world of Robotic Process Automation (RPA), staying abreast of the latest trends is essential for RPA developers and professionals in 2023. As the technology continually evolves, here are some strategies to ensure you remain informed and adaptable:
-
Continuous Learning: Dedicate time to ongoing education through online courses, webinars, and workshops offered by RPA tool providers, industry organizations, and educational platforms. Through this, you have the opportunity to acquire new skills and knowledge.
-
Professional Networks: Engage with RPA-focused communities, forums, and LinkedIn groups where experts and enthusiasts share insights, news, and emerging trends. Actively participating in discussions can provide valuable insights.
-
Industry Publications: Regularly read RPA-related publications, blogs, and news outlets to stay updated on the latest developments, case studies, and best practices in the field.
-
RPA Vendor Updates: Subscribe to newsletters and updates from RPA tool vendors, as they often provide information about new features, product releases, and upcoming enhancements.
-
Conferences and Events: Attend RPA conferences, summits, and industry events where thought leaders and practitioners discuss cutting-edge trends, share success stories, and unveil future strategies.
-
Thought Leadership: Follow thought leaders and experts in the RPA space on social media platforms like Twitter and LinkedIn, where they often share insights, articles, and predictions about the future of RPA.
-
Experimentation: Stay hands-on by exploring new RPA tools, features, and functionalities through personal projects or within a controlled environment at work. Practical experience is a powerful learning tool.
-
Mentorship: Seek mentorship from seasoned RPA professionals who can provide guidance on emerging trends and offer career advice based on their experiences.
-
Market Research: Analyze market reports and research studies related to RPA to understand the broader industry landscape, market dynamics, and emerging use cases.
-
Cross-Training: Explore adjacent technologies and fields such as artificial intelligence, machine learning, and process optimization, as these areas often intersect with RPA and can offer valuable insights.
-
Certifications: Consider pursuing advanced RPA certifications or specialization courses that focus on specific trends or industry niches within automation.
By diligently following these strategies, you can keep pace with the dynamic RPA trends of 2023 and position yourself as a knowledgeable and adaptable professional capable of driving innovation in the automation landscape.
Building a Career as an RPA Developer
Building a successful career as an RPA (Robotic Process Automation) developer in 2023 necessitates a deliberate approach. Start by mastering RPA fundamentals, including popular automation tools and programming languages, and consider formal education or relevant certifications to bolster your knowledge. Gain practical experience through hands-on projects, connect with industry professionals for networking opportunities, and invest in soft skills like communication and problem-solving. RPA certifications can validate your expertise, while continuous learning ensures you stay updated with the rapidly evolving field. Building a portfolio of your automation projects showcases your abilities to potential employers. Tailor your job search, prepare for interviews, and consider joining consulting firms for diverse experiences. As you progress, explore leadership roles and stay adaptable by embracing emerging technologies related to RPA. Contributing to the RPA community and keeping an eye on broader industry trends will help you thrive in this promising career path.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : CISA Certification
-
Emerging Technologies : Robotic Process Automation
Conclusion
The world of Robotic Process Automation (RPA) in 2023 offers abundant opportunities for those seeking to excel in automation technology. From mastering technical skills to cultivating soft skills and staying abreast of the latest trends, the journey of becoming an RPA developer is both challenging and rewarding. Embracing continuous learning, networking, and community involvement is key to thriving in this dynamic field. By following best practices, earning certifications, and building a portfolio of successful projects, you can establish yourself as a proficient RPA developer. Remember, adaptability and a commitment to ongoing growth are crucial in an ever-evolving industry. With dedication and a strategic approach, you can forge a successful career in RPA, contributing to the transformative impact of automation technology in organizations across various industries.
Read More
In the rapidly evolving world of technology and automation, Robotic Process Automation (RPA) has emerged as a transformative force, reshaping the way organizations operate and streamline their workflows. As we step into 2023, the demand for skilled RPA developers is at an all-time high, making it an opportune moment to embark on a journey of mastering this cutting-edge field. "Mastering RPA: Your Blueprint for Success in 2023" is your guide to navigating the intricate landscape of RPA, offering insights, strategies, and practical advice for those aspiring to become proficient RPA developers. This blueprint is not just about acquiring technical skills but also understanding the broader context of automation, soft skills, and the ever-changing trends that will define the RPA landscape this year and beyond. Whether you're a newcomer or a seasoned professional, this guide is designed to equip you with the knowledge and tools needed to thrive in the world of RPA and make a meaningful impact in the digital age.
Table of Contents
-
Introduction to RPA (Robotic Process Automation)
-
Choosing the Right RPA Tool
-
Programming Skills
-
RPA Certification
-
Advanced RPA Techniques
-
Best Practices in RPA Development
-
Soft Skills for RPA Developers
-
Networking and Community Involvement
-
Keeping Up with RPA Trends
-
Building a Career as an RPA Developer
-
Conclusion
Introduction to RPA (Robotic Process Automation)
Robotic Process Automation (RPA) is a transformative technology that employs software bots to automate repetitive, rule-based tasks within organizations. These digital workers, though not physical robots, replicate human actions in interacting with software applications, aiming to streamline and optimize business processes. RPA offers unparalleled accuracy, scalability, and cost-efficiency, making it a crucial tool for various industries, from finance to healthcare. In 2023, as RPA's role in digital transformation grows, aspiring RPA developers have a promising career opportunity in harnessing this technology's potential for efficiency and innovation.
Choosing the Right RPA Tool
Selecting the appropriate Robotic Process Automation (RPA) tool is a critical decision on your path to becoming an RPA developer. In 2023, there is a plethora of RPA tools available, each with its unique strengths and capabilities. To make an informed choice, start by assessing your specific automation needs and objectives. Consider factors such as the complexity of tasks you want to automate, the compatibility of the tool with your existing systems, scalability requirements, and your budget. Popular RPA tools like UiPath, Automation Anywhere, and Blue Prism offer robust features and strong developer communities, but it's essential to evaluate them in terms of ease of use, extensibility, and the support they provide for your chosen programming languages. Additionally, look for trial versions or free community editions to gain hands-on experience and ensure a seamless fit for your automation projects. Keep in mind that the right RPA tool can significantly impact your efficiency and success as an RPA developer in 2023 and beyond.
Programming Skills
Becoming a proficient RPA (Robotic Process Automation) developer in 2023 requires a solid foundation in programming. While RPA tools provide a user-friendly interface for automation, understanding programming concepts is essential for building complex and customized automation solutions. Here are some key programming skills you should focus on:
-
Scripting Languages: Mastery of scripting languages such as Python, JavaScript, or PowerShell is invaluable. Python, in particular, is widely used in RPA development due to its simplicity and versatility.
-
Object-Oriented Programming (OOP): Understanding OOP principles is beneficial for creating reusable and well-structured code, especially when working with more advanced RPA projects.
-
Basic Algorithms and Data Structures: A grasp of fundamental algorithms and data structures like arrays, lists, and dictionaries is essential for efficiently manipulating data in your automation workflows.
-
Error Handling: Learn to handle exceptions and errors gracefully in your code, ensuring that your RPA bots can recover from unexpected issues during automation processes.
-
Debugging Skills: Proficiency in debugging tools and techniques is crucial for identifying and resolving issues in your automation scripts.
-
Regular Expressions: Regular expressions (regex) are essential for text manipulation and pattern matching, which are common tasks in RPA.
-
Version Control: Familiarize yourself with version control systems like Git to manage and track changes in your codebase, promoting collaboration and code stability.
-
API Integration: Understanding how to interact with APIs (Application Programming Interfaces) is essential for connecting RPA bots with external systems and services.
-
Database Basics: Knowledge of database concepts and SQL (Structured Query Language) can be valuable when working with data-driven automation processes.
-
Web Development Skills: Basic web development knowledge, including HTML, CSS, and JavaScript, can be beneficial for automating tasks involving web interfaces and browser interactions.
-
Security Awareness: Be aware of security best practices and potential vulnerabilities, especially when dealing with sensitive data or automation in secure environments.
-
Continual Learning: Stay updated with programming languages and frameworks relevant to RPA, as the field is continually evolving.
By honing these programming skills, you'll be better equipped to create efficient, reliable, and customized RPA solutions that address the specific automation needs of your organization or clients in 2023 and beyond.
RPA Certification
RPA certification is a pivotal career move in the thriving field of Robotic Process Automation, especially in 2023, as it validates your expertise with specific RPA tools like UiPath, Automation Anywhere, or Blue Prism. Earning such credentials not only enhances your job prospects and earning potential but also positions you as a credible RPA professional in high demand by organizations worldwide. With certification, you gain access to exclusive networks, stay updated on industry trends, and continually expand your skill set, making it an essential step for anyone looking to excel in the dynamic world of RPA.
Advanced RPA Techniques
As a burgeoning RPA (Robotic Process Automation) developer in 2023, advancing your skills beyond the basics is crucial for tackling complex automation challenges and delivering exceptional value to your organization. To excel in the field, delve into advanced RPA techniques:
-
Exception Handling: Master the art of handling exceptions and errors gracefully, enabling your bots to recover autonomously when unexpected situations arise during automation processes.
-
Integration with APIs: Go beyond basic automation by learning how to seamlessly integrate RPA bots with various application programming interfaces (APIs) to exchange data and execute actions across multiple systems.
-
Data Manipulation: Explore advanced data manipulation techniques, including complex data transformations, parsing unstructured data, and handling large datasets efficiently.
-
Orchestrator and Queue Management: Learn how to use RPA orchestrators effectively to manage bot execution, schedule tasks, and monitor automation workflows. Understand queue management for efficient task distribution.
-
Machine Learning and AI Integration: Combine RPA with machine learning and artificial intelligence to create intelligent automation solutions that can make data-driven decisions and adapt to changing conditions.
-
Citizen Developer Enablement: Develop strategies for involving non-technical stakeholders or citizen developers in the RPA development process while maintaining governance and control.
-
Advanced Debugging and Testing: Hone your debugging skills and implement robust testing practices to ensure the reliability and stability of your automation solutions.
-
Scalability and Performance Optimization: Discover techniques for scaling up your RPA deployments and optimizing bot performance, allowing your solutions to handle larger workloads efficiently.
-
Security Best Practices: Deepen your understanding of security considerations in RPA, including data encryption, access controls, and compliance with industry regulations.
-
Governance and Compliance: Establish governance frameworks to manage the lifecycle of automation projects, maintain documentation, and ensure compliance with organizational policies.
-
Continuous Learning: Stay at the forefront of RPA by keeping up with emerging trends, attending advanced training programs, and participating in RPA communities.
By embracing these advanced RPA techniques, you position yourself as a versatile and skilled developer capable of addressing complex automation scenarios and driving innovation within your organization. In 2023, as RPA continues to evolve, your mastery of these advanced skills will be invaluable in delivering efficiency and automation excellence.
Best Practices in RPA Development
In the dynamic landscape of Robotic Process Automation (RPA), adhering to best practices is essential for creating robust, maintainable, and efficient automation solutions. In 2023, as RPA adoption continues to surge, consider the following best practices for successful RPA development:
-
Requirements Analysis: Begin with a thorough understanding of the business process you aim to automate, involving stakeholders to define clear objectives and expected outcomes.
-
Modularity and Reusability: Design your RPA workflows in a modular fashion, promoting code reusability to save time and effort in future automation projects.
-
Error Handling: Implement comprehensive error handling mechanisms to gracefully manage exceptions, log errors, and ensure the reliability of your bots.
-
Documentation: Maintain detailed documentation for your automation projects, including process maps, code comments, and version histories, to facilitate collaboration and troubleshooting.
-
Testing and Validation: Rigorously test your automation workflows in a controlled environment to verify accuracy, and conduct user acceptance testing (UAT) to ensure alignment with business requirements.
-
Security Protocols: Prioritize security by encrypting sensitive data, adhering to access controls, and complying with industry-specific regulations to safeguard critical information.
-
Code Review: Collaborate with peers for code reviews to identify potential improvements, maintain code quality, and ensure adherence to coding standards.
-
Version Control: Employ version control systems like Git to manage changes, track revisions, and enable collaboration with team members.
-
Scalability: Design your RPA solutions with scalability in mind to accommodate increasing workloads and future process enhancements.
-
Monitoring and Analytics: Implement monitoring tools and analytics dashboards to gain insights into bot performance, detect anomalies, and identify areas for optimization.
-
Compliance and Governance: Establish governance frameworks that align with organizational policies, ensuring proper management and oversight of automation projects.
-
Training and Knowledge Sharing: Invest in continuous learning for your team and foster a culture of knowledge sharing to keep abreast of RPA advancements and best practices.
-
Change Management: Develop a change management strategy to prepare employees for the adoption of RPA and address any potential resistance to automation.
-
Robust Data Handling: Pay special attention to data input and output, validate data integrity, and handle data securely throughout the automation process.
-
Performance Optimization: Continually analyze and optimize your automation workflows to enhance efficiency and minimize resource consumption.
By incorporating these best practices into your RPA development process, you'll not only ensure the success of your automation initiatives but also contribute to the long-term growth and stability of your organization's RPA ecosystem in the dynamic landscape of 2023 and beyond.
Soft Skills for RPA Developers
In the ever-evolving world of Robotic Process Automation (RPA), technical prowess alone is not sufficient for success. As an RPA developer in 2023, honing soft skills is equally critical to navigate the complexities of human-machine collaboration and excel in this dynamic field. Here are the essential soft skills for RPA developers:
-
Communication Skills: Effective communication with both technical and non-technical stakeholders is vital for understanding automation requirements, explaining technical concepts, and ensuring alignment with business objectives.
-
Problem-Solving and Critical Thinking: Develop strong problem-solving and critical thinking abilities to identify automation opportunities, troubleshoot issues, and optimize RPA solutions.
-
Adaptability: Embrace change and adapt to evolving technologies, tools, and methodologies in the fast-paced RPA landscape, as well as to shifting business priorities.
-
Attention to Detail: Pay meticulous attention to detail when designing, coding, and testing RPA workflows to ensure accuracy and reliability in automated processes.
-
Time Management: Efficiently manage your time and prioritize tasks to meet project deadlines, especially when handling multiple automation projects simultaneously.
-
Collaboration: Foster collaboration within cross-functional teams, as RPA often requires cooperation between developers, business analysts, and end-users to achieve successful automation outcomes.
-
Empathy: Understand end-users' needs and concerns, empathize with their challenges, and design RPA solutions that enhance their work experience rather than replace it.
-
Customer-Centric Approach: Keep the customer's perspective at the forefront of RPA development, striving to deliver solutions that align with business goals and improve customer experiences.
-
Creativity and Innovation: Cultivate creativity to find innovative ways to automate processes and drive business efficiencies, going beyond the obvious solutions.
-
Resilience: Stay resilient in the face of setbacks or challenges during the development and implementation of RPA projects, persistently seeking solutions.
-
Leadership: Develop leadership skills to guide teams, mentor junior developers, and take ownership of complex RPA projects.
-
Ethical Considerations: Navigate ethical dilemmas that may arise when automating tasks and handling sensitive data, ensuring compliance with ethical guidelines and data protection regulations.
-
Cultural Awareness: Recognize and respect cultural differences, as RPA is deployed in organizations with diverse workforces and global reach.
-
Client-Facing Skills: If working in an RPA consulting role, strong client-facing skills are essential for understanding client needs, managing expectations, and building lasting client relationships.
-
Continuous Learning: Cultivate a growth mindset and commit to continuous learning, staying updated on RPA trends, emerging technologies, and best practices.
These soft skills complement your technical expertise, making you a well-rounded and effective RPA developer capable of collaborating seamlessly in human-machine partnerships and driving meaningful automation outcomes in 2023's dynamic RPA landscape.
Networking and Community Involvement
Networking and community involvement are essential for RPA developers in 2023, as they play a pivotal role in personal and professional growth within the dynamic realm of Robotic Process Automation. Engaging with online forums, professional associations, meetups, and conferences allows developers to connect with peers, stay abreast of industry trends, and share valuable insights. These interactions provide opportunities to discuss best practices, explore real-world use cases, and even collaborate on projects. Additionally, contributing to open-source RPA initiatives, blogging, or offering mentorship not only showcases expertise but also strengthens the RPA community. By actively participating in the RPA network, developers can cultivate a rich support system, access a wealth of knowledge, and establish themselves as respected figures in the field. This collaborative spirit not only fosters personal growth but also contributes to the advancement of RPA as a transformative technology.
Keeping Up with RPA Trends
In the fast-paced world of Robotic Process Automation (RPA), staying abreast of the latest trends is essential for RPA developers and professionals in 2023. As the technology continually evolves, here are some strategies to ensure you remain informed and adaptable:
-
Continuous Learning: Dedicate time to ongoing education through online courses, webinars, and workshops offered by RPA tool providers, industry organizations, and educational platforms. Through this, you have the opportunity to acquire new skills and knowledge.
-
Professional Networks: Engage with RPA-focused communities, forums, and LinkedIn groups where experts and enthusiasts share insights, news, and emerging trends. Actively participating in discussions can provide valuable insights.
-
Industry Publications: Regularly read RPA-related publications, blogs, and news outlets to stay updated on the latest developments, case studies, and best practices in the field.
-
RPA Vendor Updates: Subscribe to newsletters and updates from RPA tool vendors, as they often provide information about new features, product releases, and upcoming enhancements.
-
Conferences and Events: Attend RPA conferences, summits, and industry events where thought leaders and practitioners discuss cutting-edge trends, share success stories, and unveil future strategies.
-
Thought Leadership: Follow thought leaders and experts in the RPA space on social media platforms like Twitter and LinkedIn, where they often share insights, articles, and predictions about the future of RPA.
-
Experimentation: Stay hands-on by exploring new RPA tools, features, and functionalities through personal projects or within a controlled environment at work. Practical experience is a powerful learning tool.
-
Mentorship: Seek mentorship from seasoned RPA professionals who can provide guidance on emerging trends and offer career advice based on their experiences.
-
Market Research: Analyze market reports and research studies related to RPA to understand the broader industry landscape, market dynamics, and emerging use cases.
-
Cross-Training: Explore adjacent technologies and fields such as artificial intelligence, machine learning, and process optimization, as these areas often intersect with RPA and can offer valuable insights.
-
Certifications: Consider pursuing advanced RPA certifications or specialization courses that focus on specific trends or industry niches within automation.
By diligently following these strategies, you can keep pace with the dynamic RPA trends of 2023 and position yourself as a knowledgeable and adaptable professional capable of driving innovation in the automation landscape.
Building a Career as an RPA Developer
Building a successful career as an RPA (Robotic Process Automation) developer in 2023 necessitates a deliberate approach. Start by mastering RPA fundamentals, including popular automation tools and programming languages, and consider formal education or relevant certifications to bolster your knowledge. Gain practical experience through hands-on projects, connect with industry professionals for networking opportunities, and invest in soft skills like communication and problem-solving. RPA certifications can validate your expertise, while continuous learning ensures you stay updated with the rapidly evolving field. Building a portfolio of your automation projects showcases your abilities to potential employers. Tailor your job search, prepare for interviews, and consider joining consulting firms for diverse experiences. As you progress, explore leadership roles and stay adaptable by embracing emerging technologies related to RPA. Contributing to the RPA community and keeping an eye on broader industry trends will help you thrive in this promising career path.
How to obtain Robotic Process Automation Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Power BI Certification
-
Cyber Security : CISA Certification
-
Emerging Technologies : Robotic Process Automation
Conclusion
The world of Robotic Process Automation (RPA) in 2023 offers abundant opportunities for those seeking to excel in automation technology. From mastering technical skills to cultivating soft skills and staying abreast of the latest trends, the journey of becoming an RPA developer is both challenging and rewarding. Embracing continuous learning, networking, and community involvement is key to thriving in this dynamic field. By following best practices, earning certifications, and building a portfolio of successful projects, you can establish yourself as a proficient RPA developer. Remember, adaptability and a commitment to ongoing growth are crucial in an ever-evolving industry. With dedication and a strategic approach, you can forge a successful career in RPA, contributing to the transformative impact of automation technology in organizations across various industries.
Navigating Your Career Path: Is DevOps the Right Choice in 2023?
As we step into 2023, the tech industry is undergoing dynamic changes, and the question on the minds of many professionals is whether DevOps remains a viable and rewarding career choice. DevOps, which merges development and operations to enhance collaboration and streamline software delivery, has been a buzzword in modern tech circles, promising efficiency and innovation. In this exploration of "Navigating Your Career Path: Is DevOps the Right Choice in 2023?" we will assess the current DevOps landscape, the requisite skills, and the factors shaping its relevance in today's tech world, helping both newcomers and experienced practitioners make informed decisions about their career paths in this fast-paced industry.
Table of Contents
1. Rising Demand for DevOps Talent
2. DevOps Offers a Definite Career Path that Promises Steady Growth
3. Your Key Responsibility Areas (KRA) as DevOps Expert
4. Technical Skills Needed to Build a DevOps Career
5. Where Can You Start Your Journey in DevOps?
6. How Far Would You Like to Go in DevOps?
Get Started Today
Rising Demand for DevOps Talent
The "Rising Demand for DevOps Talent" is a compelling phenomenon in the technology industry, reflecting the growing need for professionals well-versed in DevOps practices. DevOps, short for Development and Operations, represents a set of principles and practices that emphasize collaboration and automation between software development and IT operations teams. This approach is designed to enhance the efficiency, reliability, and speed of software delivery. Here are some key insights into the increasing demand for DevOps talent:
-
Business Agility: In today's fast-paced digital landscape, businesses need to be agile and responsive to market changes. DevOps facilitates quicker software development, testing, and deployment, enabling organizations to adapt swiftly to evolving customer demands and market trends.
-
Automation: Automation is a central pillar of DevOps. By automating repetitive tasks, such as code testing and deployment, organizations can reduce manual errors, save time, and ensure consistent processes. DevOps professionals are responsible for implementing and maintaining these automation pipelines.
-
Continuous Integration and Continuous Delivery (CI/CD): DevOps practices encourage the implementation of CI/CD pipelines. These pipelines automate the integration of code changes, testing, and deployment, leading to more frequent and reliable software releases. Experts in CI/CD are highly sought after to optimize these critical processes.
-
Cloud Computing: The widespread adoption of cloud platforms, such as AWS, Azure, and Google Cloud, has further accelerated the demand for DevOps expertise. DevOps practices are essential for managing and optimizing cloud infrastructure and services effectively.
-
Security: Security is paramount in today's technology landscape. DevOps teams are increasingly integrating security practices into their workflows, giving rise to the DevSecOps approach. DevOps professionals with security expertise are in high demand to ensure that software is developed and deployed securely.
-
Cost Efficiency: DevOps can lead to cost savings by reducing downtime, optimizing resource usage, and streamlining development and deployment processes. Organizations are eager to hire DevOps professionals who can help them achieve these cost benefits.
-
Scalability: DevOps practices are essential for organizations experiencing growth or dealing with variable workloads. DevOps enables scalable infrastructure and supports the efficient management of resources.
-
Cultural Transformation: Beyond tools and processes, DevOps represents a cultural shift within organizations. It emphasizes collaboration, communication, and shared responsibility among development and operations teams. DevOps professionals play a vital role in fostering this cultural change.
DevOps Offers a Definite Career Path that Promises Steady Growth
DevOps is undeniably offering a well-defined career path with the assurance of steady growth. In recent years, it has evolved into a transformative field within the technology industry, creating a multitude of opportunities for professionals seeking a dynamic and promising career trajectory. The reasons behind this career's appeal are numerous and compelling.
First and foremost, the demand for DevOps professionals is soaring. Across various industries, companies are recognizing the significant value that DevOps practices bring to the table. These practices accelerate software development, enhance product quality, and optimize operational efficiency. This sustained demand ensures a consistent flow of job opportunities for those entering the DevOps arena, providing a sense of job security and stability.
One of the remarkable aspects of a DevOps career is its versatility. DevOps is not a one-size-fits-all discipline; it encompasses a broad spectrum of skills and practices. Professionals can specialize in areas such as automation, continuous integration/continuous delivery (CI/CD), cloud computing, security (DevSecOps), or infrastructure as code (IaC). This versatility empowers individuals to tailor their career paths to align with their personal interests and strengths, offering a diverse array of potential avenues for growth.
Furthermore, DevOps places a strong emphasis on continuous learning and improvement. In a rapidly evolving technological landscape, staying up-to-date with the latest tools, technologies, and best practices is not just encouraged but essential. This commitment to lifelong learning ensures that DevOps practitioners remain relevant and marketable, making it possible to continuously advance in their careers.
A DevOps career is also financially rewarding. Due to the specialized skills and expertise required, DevOps roles often come with competitive salaries and attractive benefit packages. Professionals in this field can command higher compensation compared to more traditional IT roles, making it an appealing choice for those who seek both intellectual and financial gratification.
Moreover, DevOps professionals are well-positioned for cross-functional collaboration. DevOps practices encourage close cooperation between development and operations teams, providing opportunities to work with diverse stakeholders and gain exposure to different aspects of an organization's technology ecosystem. This interdisciplinary experience enhances their skill set and opens up various career possibilities.
Over time, many DevOps professionals transition into leadership roles. With their accumulated experience and expertise, they often find themselves overseeing DevOps teams, shaping an organization's DevOps strategy, and driving cultural and technical transformations within their workplaces. This pathway into leadership roles adds a layer of professional growth and leadership development to the DevOps career trajectory.
Furthermore, DevOps offers global opportunities. The demand for DevOps talent is not confined to specific geographic regions, allowing professionals in this field to explore remote work options or even international employment opportunities. This global perspective can enrich their career experiences and broaden their horizons.
Lastly, DevOps professionals find deep satisfaction in their work. They play a pivotal role in enabling organizations to deliver software more swiftly and with higher quality. This direct impact on an organization's ability to innovate, compete, and respond to customer needs can be intrinsically rewarding and fulfilling.
Your Key Responsibility Areas (KRA) as DevOps Expert
As a DevOps expert, your Key Responsibility Areas (KRAs) encompass a wide range of tasks and responsibilities that are vital for the successful implementation of DevOps practices and the efficient operation of software development and IT infrastructure. Here are some of the key areas you might be responsible for:
-
Infrastructure Automation:
-
Designing, building, and maintaining infrastructure as code (IaC) to automate the provisioning and management of servers, networks, and storage.
-
Implementing and managing configuration management tools (e.g., Ansible, Puppet, Chef) to ensure consistency and scalability in infrastructure.
-
Continuous Integration and Continuous Delivery (CI/CD):
-
Developing and maintaining CI/CD pipelines to automate the build, test, and deployment processes.
-
Ensuring that code changes are integrated, tested, and deployed efficiently, with a focus on quality and reliability.
-
Cloud Services:
-
Managing cloud infrastructure (e.g., AWS, Azure, Google Cloud) and optimizing resource usage for scalability and cost-efficiency.
-
Implementing cloud-native DevOps practices and leveraging cloud services for application deployment and scaling.
-
Version Control:
-
Implementing and managing version control systems (e.g., Git) to track code changes, collaborate with development teams, and ensure code quality.
-
Monitoring and Logging:
-
Setting up monitoring and logging tools (e.g., Prometheus, ELK stack) to track system performance, identify issues, and troubleshoot problems proactively.
-
Creating dashboards and alerts to ensure real-time visibility into system health.
-
Security (DevSecOps):
-
Integrating security practices into the DevOps pipeline to identify and mitigate security vulnerabilities.
-
Collaborating with security teams to implement best practices for securing infrastructure and applications.
-
Collaboration and Communication:
-
Fostering a culture of collaboration between development and operations teams to ensure smooth workflows and alignment with business goals.
-
Facilitating communication and knowledge sharing among cross-functional teams.
-
Release Management:
-
Managing software releases, including versioning, deployment scheduling, and rollback procedures.
-
Coordinating release activities to minimize downtime and disruptions.
-
Performance Optimization:
-
Identifying and addressing performance bottlenecks in applications and infrastructure.
-
Implementing optimizations to enhance system speed and efficiency.
-
Disaster Recovery and Backup:
-
Developing and testing disaster recovery plans to ensure data integrity and system availability in case of unexpected failures.
-
Regularly backing up critical data and systems to prevent data loss.
-
Documentation and Training:
-
Maintaining detailed documentation of infrastructure, processes, and configurations.
-
Providing training and guidance to team members and stakeholders on DevOps practices and tools.
-
Tool Evaluation and Selection:
-
Assessing and selecting the most appropriate DevOps tools and technologies for the organization's needs.
-
Staying updated on emerging DevOps tools and trends to ensure the use of modern and effective solutions.
-
Continuous Improvement:
-
Continuously assessing and optimizing DevOps processes to enhance efficiency and effectiveness.
-
Conducting post-implementation reviews and retrospectives to identify areas for improvement.
-
Compliance and Governance:
-
Ensuring that infrastructure and processes comply with industry regulations and organizational governance policies.
-
Implementing controls and audits as needed.
-
Team Leadership and Mentoring (for senior roles):
-
Leading DevOps teams, setting strategic goals, and mentoring team members.
-
Overseeing project execution, resource allocation, and performance evaluations.
These KRAs represent the core responsibilities of a DevOps expert. The specific duties may vary depending on the organization's size, industry, and the maturity of its DevOps practices. DevOps professionals play a pivotal role in enabling organizations to deliver software more efficiently, reliably, and securely, making their contributions critical to the success of the business.
Technical Skills Needed to Build a DevOps Career
Here are the key technical skills needed for a DevOps career in simple points:
-
Version Control: Understand how to use tools like Git for code management.
-
Scripting: Be proficient in scripting languages like Bash, PowerShell, or Python.
-
Operating Systems: Familiarity with both Linux/Unix and Windows systems.
-
Infrastructure as Code (IaC): Ability to use IaC tools like Terraform or Ansible for automating infrastructure setup.
-
Containers: Know how to work with containers, especially Docker.
-
Container Orchestration: Familiarity with Kubernetes for managing containerized applications.
-
CI/CD: Understand continuous integration and continuous delivery principles and use CI/CD tools like Jenkins or GitLab CI/CD.
-
Cloud Services: Be comfortable with major cloud providers (AWS, Azure, Google Cloud).
-
Monitoring and Logging: Proficiency in tools like Prometheus, Grafana, and ELK stack.
-
Networking: Basic understanding of network protocols and security.
-
Security (DevSecOps): Implement security measures within the DevOps pipeline and use security scanning tools.
-
Database Management: Know how to manage databases like MySQL or MongoDB.
-
Collaboration Tools: Use tools like Slack or Microsoft Teams for team communication.
-
Continuous Learning: Stay updated with evolving DevOps trends and technologies.
-
Problem-Solving: Be a good troubleshooter and problem solver.
-
Automation: Automate repetitive tasks using tools like Ansible or Puppet.
-
GitOps: Understand GitOps principles and tools like ArgoCD.
-
Container Security: Know how to secure containers and scan for vulnerabilities.
-
Serverless Computing: Understand serverless platforms like AWS Lambda or Azure Functions.
-
Microservices: Learn about microservices architecture and related technologies.
-
Automation Testing: Use automated testing frameworks to ensure code quality.
These skills form the foundation for a successful DevOps career, allowing you to streamline software development, deployment, and operations efficiently.
Where Can You Start Your Journey in DevOps?
To begin your journey in DevOps, start by understanding its core principles and then delve into practical skills. Learn version control with Git and acquire basic scripting abilities in languages like Bash or PowerShell. Familiarize yourself with Linux and grasp networking fundamentals. Decide on a specific area of focus within DevOps, whether it's automation, cloud, or security. Enroll in online courses, consider certifications, and engage with DevOps communities. Practice by working on personal projects and join open-source initiatives. Attend meetups, conferences, and build a portfolio to showcase your skills. Collaborate with IT professionals, apply for entry-level roles, and seek mentorship. Developing both technical and soft skills while staying patient and persistent will pave your way to a rewarding DevOps career.
How Far Would You Like to Go in DevOps?
By choosing a DevOps training course that offers a complete learning path, you can take your DevOps career as high as your ambition goes. You can enroll in the DevOps Engineer Master’s Program that adds six more courses beyond the DevOps Certification Training Course and several in-depth Capstone projects. You’ll also want to make sure you have a certification that will take you all the way in your career. DevOps certificates vary in status in the industry. DevOps certifications that have been accredited by important tech giants or relevant bodies will demonstrate to employers that you’ve achieved an expert level of skills and knowledge for continuous integration and development. iCert Global provides industry-recognized DevOps course completion certificates that have lifelong validity and are recognized by tech giants like Amazon Web Services and Microsoft Azure.
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Data Science with R programming
Get Started Today
DevOps certification training Course
People working in the following roles will benefit the most from DevOps certification:
-
IT Team Leaders and technical project managers
-
Systems Administrators and IT Managers
-
Software Developers
-
Deployment engineers
-
Operations support
-
Architects
-
Cloud Engineers
Your career as a DevOps engineer has excellent prospects for growth as businesses are embracing DevOps for the speedy delivery of software features and security updates. iCert Global, as one of the education technology company, offers certified and industry-recognized course in DevOps . Our DevOps Certification will teach you a complete set of DevOps skills .
Read More
As we step into 2023, the tech industry is undergoing dynamic changes, and the question on the minds of many professionals is whether DevOps remains a viable and rewarding career choice. DevOps, which merges development and operations to enhance collaboration and streamline software delivery, has been a buzzword in modern tech circles, promising efficiency and innovation. In this exploration of "Navigating Your Career Path: Is DevOps the Right Choice in 2023?" we will assess the current DevOps landscape, the requisite skills, and the factors shaping its relevance in today's tech world, helping both newcomers and experienced practitioners make informed decisions about their career paths in this fast-paced industry.
Table of Contents
1. Rising Demand for DevOps Talent
2. DevOps Offers a Definite Career Path that Promises Steady Growth
3. Your Key Responsibility Areas (KRA) as DevOps Expert
4. Technical Skills Needed to Build a DevOps Career
5. Where Can You Start Your Journey in DevOps?
6. How Far Would You Like to Go in DevOps?
Get Started Today
Rising Demand for DevOps Talent
The "Rising Demand for DevOps Talent" is a compelling phenomenon in the technology industry, reflecting the growing need for professionals well-versed in DevOps practices. DevOps, short for Development and Operations, represents a set of principles and practices that emphasize collaboration and automation between software development and IT operations teams. This approach is designed to enhance the efficiency, reliability, and speed of software delivery. Here are some key insights into the increasing demand for DevOps talent:
-
Business Agility: In today's fast-paced digital landscape, businesses need to be agile and responsive to market changes. DevOps facilitates quicker software development, testing, and deployment, enabling organizations to adapt swiftly to evolving customer demands and market trends.
-
Automation: Automation is a central pillar of DevOps. By automating repetitive tasks, such as code testing and deployment, organizations can reduce manual errors, save time, and ensure consistent processes. DevOps professionals are responsible for implementing and maintaining these automation pipelines.
-
Continuous Integration and Continuous Delivery (CI/CD): DevOps practices encourage the implementation of CI/CD pipelines. These pipelines automate the integration of code changes, testing, and deployment, leading to more frequent and reliable software releases. Experts in CI/CD are highly sought after to optimize these critical processes.
-
Cloud Computing: The widespread adoption of cloud platforms, such as AWS, Azure, and Google Cloud, has further accelerated the demand for DevOps expertise. DevOps practices are essential for managing and optimizing cloud infrastructure and services effectively.
-
Security: Security is paramount in today's technology landscape. DevOps teams are increasingly integrating security practices into their workflows, giving rise to the DevSecOps approach. DevOps professionals with security expertise are in high demand to ensure that software is developed and deployed securely.
-
Cost Efficiency: DevOps can lead to cost savings by reducing downtime, optimizing resource usage, and streamlining development and deployment processes. Organizations are eager to hire DevOps professionals who can help them achieve these cost benefits.
-
Scalability: DevOps practices are essential for organizations experiencing growth or dealing with variable workloads. DevOps enables scalable infrastructure and supports the efficient management of resources.
-
Cultural Transformation: Beyond tools and processes, DevOps represents a cultural shift within organizations. It emphasizes collaboration, communication, and shared responsibility among development and operations teams. DevOps professionals play a vital role in fostering this cultural change.
DevOps Offers a Definite Career Path that Promises Steady Growth
DevOps is undeniably offering a well-defined career path with the assurance of steady growth. In recent years, it has evolved into a transformative field within the technology industry, creating a multitude of opportunities for professionals seeking a dynamic and promising career trajectory. The reasons behind this career's appeal are numerous and compelling.
First and foremost, the demand for DevOps professionals is soaring. Across various industries, companies are recognizing the significant value that DevOps practices bring to the table. These practices accelerate software development, enhance product quality, and optimize operational efficiency. This sustained demand ensures a consistent flow of job opportunities for those entering the DevOps arena, providing a sense of job security and stability.
One of the remarkable aspects of a DevOps career is its versatility. DevOps is not a one-size-fits-all discipline; it encompasses a broad spectrum of skills and practices. Professionals can specialize in areas such as automation, continuous integration/continuous delivery (CI/CD), cloud computing, security (DevSecOps), or infrastructure as code (IaC). This versatility empowers individuals to tailor their career paths to align with their personal interests and strengths, offering a diverse array of potential avenues for growth.
Furthermore, DevOps places a strong emphasis on continuous learning and improvement. In a rapidly evolving technological landscape, staying up-to-date with the latest tools, technologies, and best practices is not just encouraged but essential. This commitment to lifelong learning ensures that DevOps practitioners remain relevant and marketable, making it possible to continuously advance in their careers.
A DevOps career is also financially rewarding. Due to the specialized skills and expertise required, DevOps roles often come with competitive salaries and attractive benefit packages. Professionals in this field can command higher compensation compared to more traditional IT roles, making it an appealing choice for those who seek both intellectual and financial gratification.
Moreover, DevOps professionals are well-positioned for cross-functional collaboration. DevOps practices encourage close cooperation between development and operations teams, providing opportunities to work with diverse stakeholders and gain exposure to different aspects of an organization's technology ecosystem. This interdisciplinary experience enhances their skill set and opens up various career possibilities.
Over time, many DevOps professionals transition into leadership roles. With their accumulated experience and expertise, they often find themselves overseeing DevOps teams, shaping an organization's DevOps strategy, and driving cultural and technical transformations within their workplaces. This pathway into leadership roles adds a layer of professional growth and leadership development to the DevOps career trajectory.
Furthermore, DevOps offers global opportunities. The demand for DevOps talent is not confined to specific geographic regions, allowing professionals in this field to explore remote work options or even international employment opportunities. This global perspective can enrich their career experiences and broaden their horizons.
Lastly, DevOps professionals find deep satisfaction in their work. They play a pivotal role in enabling organizations to deliver software more swiftly and with higher quality. This direct impact on an organization's ability to innovate, compete, and respond to customer needs can be intrinsically rewarding and fulfilling.
Your Key Responsibility Areas (KRA) as DevOps Expert
As a DevOps expert, your Key Responsibility Areas (KRAs) encompass a wide range of tasks and responsibilities that are vital for the successful implementation of DevOps practices and the efficient operation of software development and IT infrastructure. Here are some of the key areas you might be responsible for:
-
Infrastructure Automation:
-
Designing, building, and maintaining infrastructure as code (IaC) to automate the provisioning and management of servers, networks, and storage.
-
Implementing and managing configuration management tools (e.g., Ansible, Puppet, Chef) to ensure consistency and scalability in infrastructure.
-
-
Continuous Integration and Continuous Delivery (CI/CD):
-
Developing and maintaining CI/CD pipelines to automate the build, test, and deployment processes.
-
Ensuring that code changes are integrated, tested, and deployed efficiently, with a focus on quality and reliability.
-
-
Cloud Services:
-
Managing cloud infrastructure (e.g., AWS, Azure, Google Cloud) and optimizing resource usage for scalability and cost-efficiency.
-
Implementing cloud-native DevOps practices and leveraging cloud services for application deployment and scaling.
-
-
Version Control:
-
Implementing and managing version control systems (e.g., Git) to track code changes, collaborate with development teams, and ensure code quality.
-
-
Monitoring and Logging:
-
Setting up monitoring and logging tools (e.g., Prometheus, ELK stack) to track system performance, identify issues, and troubleshoot problems proactively.
-
Creating dashboards and alerts to ensure real-time visibility into system health.
-
-
Security (DevSecOps):
-
Integrating security practices into the DevOps pipeline to identify and mitigate security vulnerabilities.
-
Collaborating with security teams to implement best practices for securing infrastructure and applications.
-
-
Collaboration and Communication:
-
Fostering a culture of collaboration between development and operations teams to ensure smooth workflows and alignment with business goals.
-
Facilitating communication and knowledge sharing among cross-functional teams.
-
-
Release Management:
-
Managing software releases, including versioning, deployment scheduling, and rollback procedures.
-
Coordinating release activities to minimize downtime and disruptions.
-
-
Performance Optimization:
-
Identifying and addressing performance bottlenecks in applications and infrastructure.
-
Implementing optimizations to enhance system speed and efficiency.
-
-
Disaster Recovery and Backup:
-
Developing and testing disaster recovery plans to ensure data integrity and system availability in case of unexpected failures.
-
Regularly backing up critical data and systems to prevent data loss.
-
-
Documentation and Training:
-
Maintaining detailed documentation of infrastructure, processes, and configurations.
-
Providing training and guidance to team members and stakeholders on DevOps practices and tools.
-
-
Tool Evaluation and Selection:
-
Assessing and selecting the most appropriate DevOps tools and technologies for the organization's needs.
-
Staying updated on emerging DevOps tools and trends to ensure the use of modern and effective solutions.
-
-
Continuous Improvement:
-
Continuously assessing and optimizing DevOps processes to enhance efficiency and effectiveness.
-
Conducting post-implementation reviews and retrospectives to identify areas for improvement.
-
-
Compliance and Governance:
-
Ensuring that infrastructure and processes comply with industry regulations and organizational governance policies.
-
Implementing controls and audits as needed.
-
-
Team Leadership and Mentoring (for senior roles):
-
Leading DevOps teams, setting strategic goals, and mentoring team members.
-
Overseeing project execution, resource allocation, and performance evaluations.
-
These KRAs represent the core responsibilities of a DevOps expert. The specific duties may vary depending on the organization's size, industry, and the maturity of its DevOps practices. DevOps professionals play a pivotal role in enabling organizations to deliver software more efficiently, reliably, and securely, making their contributions critical to the success of the business.
Technical Skills Needed to Build a DevOps Career
Here are the key technical skills needed for a DevOps career in simple points:
-
Version Control: Understand how to use tools like Git for code management.
-
Scripting: Be proficient in scripting languages like Bash, PowerShell, or Python.
-
Operating Systems: Familiarity with both Linux/Unix and Windows systems.
-
Infrastructure as Code (IaC): Ability to use IaC tools like Terraform or Ansible for automating infrastructure setup.
-
Containers: Know how to work with containers, especially Docker.
-
Container Orchestration: Familiarity with Kubernetes for managing containerized applications.
-
CI/CD: Understand continuous integration and continuous delivery principles and use CI/CD tools like Jenkins or GitLab CI/CD.
-
Cloud Services: Be comfortable with major cloud providers (AWS, Azure, Google Cloud).
-
Monitoring and Logging: Proficiency in tools like Prometheus, Grafana, and ELK stack.
-
Networking: Basic understanding of network protocols and security.
-
Security (DevSecOps): Implement security measures within the DevOps pipeline and use security scanning tools.
-
Database Management: Know how to manage databases like MySQL or MongoDB.
-
Collaboration Tools: Use tools like Slack or Microsoft Teams for team communication.
-
Continuous Learning: Stay updated with evolving DevOps trends and technologies.
-
Problem-Solving: Be a good troubleshooter and problem solver.
-
Automation: Automate repetitive tasks using tools like Ansible or Puppet.
-
GitOps: Understand GitOps principles and tools like ArgoCD.
-
Container Security: Know how to secure containers and scan for vulnerabilities.
-
Serverless Computing: Understand serverless platforms like AWS Lambda or Azure Functions.
-
Microservices: Learn about microservices architecture and related technologies.
-
Automation Testing: Use automated testing frameworks to ensure code quality.
These skills form the foundation for a successful DevOps career, allowing you to streamline software development, deployment, and operations efficiently.
Where Can You Start Your Journey in DevOps?
To begin your journey in DevOps, start by understanding its core principles and then delve into practical skills. Learn version control with Git and acquire basic scripting abilities in languages like Bash or PowerShell. Familiarize yourself with Linux and grasp networking fundamentals. Decide on a specific area of focus within DevOps, whether it's automation, cloud, or security. Enroll in online courses, consider certifications, and engage with DevOps communities. Practice by working on personal projects and join open-source initiatives. Attend meetups, conferences, and build a portfolio to showcase your skills. Collaborate with IT professionals, apply for entry-level roles, and seek mentorship. Developing both technical and soft skills while staying patient and persistent will pave your way to a rewarding DevOps career.
How Far Would You Like to Go in DevOps?
By choosing a DevOps training course that offers a complete learning path, you can take your DevOps career as high as your ambition goes. You can enroll in the DevOps Engineer Master’s Program that adds six more courses beyond the DevOps Certification Training Course and several in-depth Capstone projects. You’ll also want to make sure you have a certification that will take you all the way in your career. DevOps certificates vary in status in the industry. DevOps certifications that have been accredited by important tech giants or relevant bodies will demonstrate to employers that you’ve achieved an expert level of skills and knowledge for continuous integration and development. iCert Global provides industry-recognized DevOps course completion certificates that have lifelong validity and are recognized by tech giants like Amazon Web Services and Microsoft Azure.
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Data Science with R programming
Get Started Today
DevOps certification training Course
People working in the following roles will benefit the most from DevOps certification:
-
IT Team Leaders and technical project managers
-
Systems Administrators and IT Managers
-
Software Developers
-
Deployment engineers
-
Operations support
-
Architects
-
Cloud Engineers
Your career as a DevOps engineer has excellent prospects for growth as businesses are embracing DevOps for the speedy delivery of software features and security updates. iCert Global, as one of the education technology company, offers certified and industry-recognized course in DevOps . Our DevOps Certification will teach you a complete set of DevOps skills .
Data Collection Methods, Types, and Tools: A Deep Dive
In today's data-driven world, understanding the intricacies of data collection methods, types, and tools is essential for individuals and organizations alike. "Data Collection Methods, Types, and Tools: A Deep Dive" offers a comprehensive exploration of this vital subject. This deep dive navigates the diverse landscape of data collection, from traditional methodologies like surveys to cutting-edge techniques such as web scraping and IoT sensors, covering a wide spectrum of data types along the way. Additionally, it unveils a rich array of tools and technologies that empower data collectors to efficiently gather and transform raw information into actionable insights. Whether you are a data enthusiast, researcher, business professional, or simply curious about the world of data, this deep dive promises to equip you with the knowledge to harness the power of data effectively.
Table of Contents
-
What is Data Collection?
-
Why Do We Need Data Collection?
-
What Are the Different Methods of Data Collection?
-
Data Collection Tools
-
The Importance of Ensuring Accurate and Appropriate Data Collection
-
Issues Related to Maintaining the Integrity of Data Collection
-
What are Common Challenges in Data Collection?
-
What are the Key Steps in the Data Collection Process?
-
Data Collection Considerations and Best Practices
-
FAQs
What is Data Collection?
Data collection is the process of gathering and capturing information or data from various sources, such as individuals, instruments, sensors, or documents, for the purpose of analysis, research, decision-making, or record-keeping. It is a fundamental step in the data management and analysis pipeline and plays a crucial role in various fields, including science, business, healthcare, social sciences, and many others.
Data collection can involve various methods and techniques, depending on the nature of the data, the research objectives, and the available resources. Some common methods of data collection include:
-
Surveys and Questionnaires: Gathering information by asking structured questions to individuals or groups.
-
Interviews: Conducting one-on-one or group interviews to collect qualitative data through open-ended or structured questions.
-
Observations: Directly observing and recording information about a particular subject or event.
-
Experiments: Manipulating variables under controlled conditions to collect data on their effects.
-
Sensors and Instruments: Using specialized devices or sensors to collect data, such as temperature, pressure, or GPS coordinates.
-
Document Analysis: Reviewing and extracting data from written or digital documents, such as reports, articles, or social media posts.
-
Web Scraping: Automated extraction of data from websites and online sources.
-
Social Media Monitoring: Collecting data from social media platforms to analyze trends, sentiments, or user behavior.
-
Data Logging: Continuous recording of data over time, often used in fields like environmental monitoring or industrial processes.
-
Sampling: Collecting data from a subset of a larger population or dataset to make inferences about the whole.
-
Mobile Apps and Surveys: Collecting data through mobile applications or surveys conducted on smartphones and tablets.
Effective data collection involves careful planning, the use of appropriate methods, ensuring data quality and accuracy, and often adhering to ethical and privacy considerations. Once collected, data can be processed, analyzed, and interpreted to extract valuable insights and support decision-making processes.
Why Do We Need Data Collection?
Data collection is a crucial component of modern society, serving as the foundation for informed decision-making, problem-solving, and progress across various domains. It provides the empirical evidence needed to understand complex issues, whether in healthcare, business, government, or scientific research. By systematically gathering data, individuals and organizations can assess performance, identify challenges, and formulate effective strategies. In healthcare, for example, data collection helps doctors diagnose diseases, researchers develop new treatments, and policymakers allocate resources to improve public health outcomes. In business, it guides market strategies, enables personalized customer experiences, and enhances efficiency through data-driven analytics. Ultimately, data collection empowers individuals, institutions, and societies to adapt, innovate, and thrive in an ever-evolving world.
Furthermore, data collection is essential for accountability and transparency. It creates a record of actions and outcomes, allowing for scrutiny and accountability of individuals, organizations, and governments. This transparency promotes ethical behavior and helps prevent fraud and corruption. In today's interconnected world, data collection also plays a pivotal role in addressing global challenges like climate change, where data on environmental trends is essential for informed policy decisions. In summary, data collection is not just a technical process; it's a cornerstone of informed decision-making, accountability, and progress across diverse sectors, shaping the way we understand and interact with the world around us.
What Are the Different Methods of Data Collection?
There are various methods of data collection, each suited to specific research objectives, types of data, and practical considerations. Here are some of the different methods commonly used:
-
Surveys and Questionnaires: Surveys involve asking individuals or groups a set of structured questions. Questionnaires can be administered in person, by phone, through email, or online. They are useful for collecting quantitative data on opinions, preferences, and demographics.
-
Interviews: Interviews involve one-on-one or group interactions where researchers ask questions and record responses. Interviews can be structured (with predetermined questions) or unstructured (more open-ended) and are often used to gather qualitative data.
-
Observations: This method involves directly observing and recording behavior, events, or phenomena. It can be done in a controlled environment (e.g., a laboratory) or in the field (e.g., naturalistic observations in a public space).
-
Experiments: Experiments involve manipulating one or more variables under controlled conditions to observe their effects. Experimental research aims to establish cause-and-effect relationships and is common in scientific studies.
-
Secondary Data Analysis: Researchers analyze existing data collected by others. This method is cost-effective and can involve various types of data, such as government statistics, academic studies, or historical records.
-
Document Analysis: Researchers review and extract information from written or digital documents, including reports, articles, social media posts, and historical texts. This is often used in content analysis and textual research.
-
Web Scraping: Automated tools are used to extract data from websites, forums, and social media platforms. Web scraping is common for collecting large datasets from the internet.
-
Sensors and Instruments: Specialized devices and sensors are used to collect data automatically. Examples include temperature sensors, GPS devices, heart rate monitors, and satellite imagery.
-
Sampling: Rather than collecting data from an entire population, researchers collect data from a representative subset (sample). Sampling methods include random sampling, stratified sampling, and convenience sampling.
-
Mobile Apps and Surveys: Data can be collected through mobile applications or surveys administered on smartphones and tablets. This method is convenient and allows for real-time data collection.
-
Social Media Monitoring: Data is collected from social media platforms to analyze trends, sentiments, user behavior, and public opinion. Social media APIs (Application Programming Interfaces) are often used for data access.
-
Data Logging: Continuous recording of data over time is used in various fields, including environmental monitoring (e.g., weather stations), industrial processes, and performance monitoring (e.g., athletes' heart rate during a race).
-
Focus Groups: A moderator leads a discussion with a small group of participants to gather insights, opinions, and perceptions on a particular topic. Focus groups are common in market research and qualitative studies.
-
Diaries and Journals: Participants keep records of their experiences, thoughts, or behaviors over a specified period. This method is often used to study daily routines or personal reflections.
The choice of data collection method depends on research goals, the type of data needed (quantitative or qualitative), available resources, ethical considerations, and practical constraints. Researchers often employ a combination of methods to triangulate data and enhance the validity and reliability of their findings.
Data Collection Tools
Data collection tools are software or hardware solutions designed to facilitate the process of gathering, storing, and managing data from various sources. These tools are used in research, business, and various other fields to streamline data collection and improve its accuracy and efficiency. Here are some common types of data collection tools:
-
Online Survey Tools: Online survey platforms like SurveyMonkey, Google Forms, and Qualtrics allow users to create and distribute surveys and questionnaires over the internet. They offer features for designing surveys, collecting responses, and analyzing results.
-
Mobile Data Collection Apps: Mobile apps like Survey123 (Esri), Fulcrum, and QuickTapSurvey enable data collection in the field using smartphones and tablets. Users can design custom forms, collect data offline, and sync it when connected to the internet.
-
Data Analytics Software: Tools like Microsoft Excel, R, Python (with libraries like Pandas), and SPSS are used to analyze and visualize data collected from various sources. They help in extracting insights and patterns from datasets.
-
Database Management Systems (DBMS): Systems like MySQL, PostgreSQL, Microsoft SQL Server, and MongoDB are used to store, organize, and manage large volumes of structured data. They are commonly employed in businesses and research institutions.
-
Geographic Information Systems (GIS): GIS software such as ArcGIS and QGIS is used for collecting and analyzing spatial data, including maps, GPS coordinates, and geographic features.
-
Data Collection APIs: Some online platforms and services offer APIs (Application Programming Interfaces) that allow developers to integrate data collection capabilities into custom applications. For example, social media platforms like Twitter and Facebook offer APIs for data retrieval.
-
Data Logger Devices: Physical devices like data loggers and sensors are used in various industries to automatically collect data, such as temperature, humidity, and pressure, and store it for later analysis.
-
Document Scanners and OCR Software: Tools like Adobe Acrobat and OCR (Optical Character Recognition) software can be used to digitize and collect data from paper documents, such as forms, invoices, and contracts.
-
Web Scraping Tools: Tools like Beautiful Soup, Scrapy, and Octoparse automate the extraction of data from websites and web pages. They are commonly used for web-based data collection.
-
Audio and Video Recording Software: Researchers and professionals often use audio and video recording tools to capture interviews, meetings, and events. Transcription software can convert spoken words into text data for analysis.
-
Qualitative Data Analysis Software: Software like NVivo and MAXQDA is specifically designed for researchers collecting qualitative data (e.g., interviews, focus groups). They assist in organizing, coding, and analyzing textual or multimedia data.
-
Biometric Data Collection Tools: Devices like fingerprint scanners, facial recognition cameras, and heart rate monitors are used to collect biometric data for security, healthcare, and other applications.
-
Blockchain Technology: Blockchain-based tools can ensure the secure and transparent collection and storage of data, making them suitable for applications where data integrity and immutability are critical.
-
Machine Learning and AI Platforms: Advanced machine learning and AI platforms can assist in data collection by automating processes, recognizing patterns, and making predictions based on existing data.
The choice of data collection tools depends on the specific requirements of a project, the type of data being collected, and the available resources. In many cases, a combination of tools may be used to capture, store, and analyze data effectively.
The Importance of Ensuring Accurate and Appropriate Data Collection
Ensuring accurate and appropriate data collection is of paramount importance in research, decision-making, and various fields for several compelling reasons:
-
Reliable Results: Accurate data leads to trustworthy research findings and better decision-making.
-
Credibility: Accurate data enhances the credibility of reports and studies.
-
Effective Decisions: It supports informed and effective decision-making.
-
Efficiency: Appropriate data collection saves time and resources.
-
Ethics and Privacy: It respects ethical standards and privacy concerns.
-
Reducing Bias: It helps reduce bias in research and analysis.
-
Long-Term Impact: Inaccurate data can have lasting consequences.
-
Resource Allocation: Guides efficient resource allocation.
-
Reproducibility: Facilitates the reproducibility of experiments.
-
Customer Satisfaction: Improves customer satisfaction in businesses.
-
Public Health and Safety: Crucial for public health and safety monitoring.
-
Environmental Conservation: Supports conservation efforts.
-
Innovation: Drives innovation and improvement in various fields.
Issues Related to Maintaining the Integrity of Data Collection
Maintaining the integrity of data collection is essential to ensure that data is accurate, reliable, and free from bias or manipulation. However, several issues can compromise data integrity. Here are some common issues related to maintaining data collection integrity:
-
Sampling Bias: When the sample used for data collection is not representative of the larger population, it can introduce bias into the results. This can occur due to non-random sampling methods or inadequate sample sizes.
-
Selection Bias: Researchers or data collectors may inadvertently favor certain groups or individuals when selecting participants or data sources, leading to biased data.
-
Non-Response Bias: If a significant portion of the selected participants does not respond to surveys or data requests, the results may not accurately represent the entire population.
-
Measurement Error: Errors in data measurement or data entry can occur due to human error, faulty equipment, or inconsistent measurement standards. These errors can introduce inaccuracies into the collected data.
-
Data Tampering: Deliberate manipulation or tampering with data can occur for various reasons, such as fraud, academic misconduct, or political motives. Maintaining data security and access controls is crucial to prevent such issues.
-
Data Privacy Concerns: Collecting sensitive or personally identifiable information without proper consent or security measures can lead to privacy breaches and ethical dilemmas.
-
Response Bias: Respondents may provide inaccurate or socially desirable responses, especially in surveys or interviews, leading to biased data.
-
Observer Bias: When data is collected through observations, the observer's personal biases and interpretations can influence the data collected.
-
Researcher Bias: Researchers' own beliefs, preferences, or expectations can inadvertently influence data collection, analysis, or interpretation, leading to bias.
-
Missing Data: Incomplete or missing data points can impact the overall integrity of the dataset, potentially leading to incomplete or biased conclusions.
-
Survey Question Bias: Poorly constructed survey questions or leading questions can unintentionally guide respondents toward certain answers, skewing the results.
-
Temporal Bias: Data collected at specific times or seasons may not accurately represent long-term trends or conditions.
-
Cross-Cultural Bias: Data collected in one cultural context may not be applicable or relevant in another, leading to cultural bias.
-
Lack of Data Documentation: Inadequate documentation of data collection methods, protocols, and procedures can hinder transparency and replication efforts.
-
Conflict of Interest: Financial or personal interests of data collectors or researchers can compromise the objectivity and integrity of data collection.
To address these issues and maintain data collection integrity, it is essential to implement rigorous data collection protocols, ensure transparency, use standardized measurement tools, conduct thorough data validation and verification, and adhere to ethical guidelines. Additionally, peer review, data audits, and data quality assessments can help identify and mitigate potential problems related to data integrity.
What are Common Challenges in Data Collection?
Data collection can be a complex and challenging process, and researchers, organizations, and individuals often encounter various obstacles. Here are some common challenges in data collection:
-
Selection Bias: It can be challenging to ensure that the data collected is representative of the entire population or target group. Biased sampling methods or non-response bias can lead to skewed results.
-
Data Quality: Maintaining data accuracy, completeness, and consistency can be difficult. Data may be prone to errors, duplications, or missing values, affecting its reliability.
-
Resource Constraints: Limited time, budget, and human resources can hinder data collection efforts, especially in large-scale projects.
-
Privacy Concerns: Collecting sensitive or personally identifiable information must be done with care to ensure data privacy and compliance with relevant regulations.
-
Ethical Considerations: Researchers must adhere to ethical guidelines when collecting data, which can be challenging when dealing with vulnerable populations or sensitive topics.
-
Data Security: Safeguarding data against breaches, theft, or unauthorized access is crucial. Data breaches can have serious consequences for individuals and organizations.
-
Data Collection Instruments: Developing and testing data collection instruments, such as surveys or questionnaires, requires careful consideration to ensure they are valid and reliable.
-
Technological Challenges: Implementing data collection technologies, especially in remote or resource-constrained areas, can be challenging. Issues like connectivity and compatibility may arise.
-
Non-Response: Collecting data from reluctant or uncooperative participants can be difficult, leading to missing or incomplete data.
-
Data Entry Errors: Manual data entry can introduce errors, especially when transcribing data from paper to digital formats.
-
Language and Cultural Barriers: In cross-cultural research, language and cultural differences may affect data collection and interpretation.
-
Data Verification: Verifying the accuracy of collected data can be time-consuming and resource-intensive.
-
Data Bias: Data may be influenced by the bias or subjectivity of the data collector, respondent, or observer.
-
Data Volume: Dealing with large volumes of data can be challenging, requiring efficient storage, processing, and analysis solutions.
-
Temporal Changes: Data collected at different times may not be directly comparable due to changing conditions or external factors.
-
Data Ownership: Clarifying data ownership and usage rights can be a challenge, especially in collaborative research or data-sharing initiatives.
-
Data Governance: Establishing clear data governance policies and procedures is essential for managing data collection efforts effectively.
-
Environmental Factors: In some cases, data collection may be affected by weather conditions, natural disasters, or other environmental factors.
-
Human Error: Mistakes made during the data collection process, such as misreading instruments or making errors in data recording, can impact data quality.
-
Legal and Regulatory Compliance: Ensuring that data collection activities comply with relevant laws and regulations can be complex, especially when conducting research across borders.
Addressing these challenges often requires careful planning, well-defined data collection protocols, the use of appropriate technology, rigorous quality control measures, and ongoing monitoring and evaluation of the data collection process. Collaborative efforts and expertise in data collection methodologies can also help overcome many of these challenges.
What are the Key Steps in the Data Collection Process?
The data collection process involves a series of key steps to gather information systematically and ensure the data's accuracy and reliability. Here are the fundamental steps in the data collection process:
-
Define Objectives: Clearly define the research or data collection objectives. Understand the purpose, scope, and goals of the data collection effort.
-
Select Data Sources: Identify the sources of data, which can include surveys, interviews, observations, existing databases, sensors, documents, or any other relevant sources.
-
Design Data Collection Instruments: Develop data collection instruments, such as surveys, questionnaires, interview guides, or observation protocols. Ensure they are clear, unbiased, and aligned with the research objectives.
-
Select Sampling Methods: If applicable, choose the appropriate sampling method (e.g., random sampling, stratified sampling) to select a representative subset of the population or dataset.
-
Pilot Testing: Test the data collection instruments and procedures with a small, representative group to identify and address any issues, such as unclear questions or logistical challenges.
-
Data Collection: Conduct the actual data collection activities according to the established protocols. Ensure consistency and uniformity in data collection procedures.
-
Data Entry: If data is collected in paper form, enter it into digital format. Implement quality control measures to minimize data entry errors.
-
Data Verification: Verify the accuracy and completeness of the collected data. This step may involve data cleaning and validation to identify and correct errors or inconsistencies.
-
Data Storage: Safely store the collected data in a secure and organized manner, whether in physical or digital format. Implement data security measures to protect sensitive information.
-
Data Documentation: Maintain detailed documentation of the data collection process, including protocols, instruments, and any modifications made during the collection.
-
Data Analysis: If applicable, perform data analysis using appropriate statistical or analytical methods. Transform raw data into meaningful insights and findings.
-
Data Interpretation: Interpret the results of data analysis in the context of research objectives. Draw conclusions and make recommendations based on the data.
-
Report Findings: Communicate the results and findings through reports, presentations, or other appropriate channels. Clearly and transparently convey the insights derived from the data.
-
Data Archiving: Store the data for future reference or potential replication of the study. Ensure data is accessible and properly archived for compliance and transparency.
-
Ethical Considerations: Adhere to ethical standards throughout the data collection process, respecting privacy, informed consent, and any relevant legal or institutional requirements.
-
Quality Control: Implement quality control measures at various stages of data collection to minimize errors, bias, and inconsistencies.
-
Continuous Monitoring: Continuously monitor the data collection process to identify and address any issues promptly. Make necessary adjustments as needed.
-
Feedback and Iteration: Collect feedback from stakeholders and team members involved in data collection. Use feedback to improve data collection procedures for future efforts.
-
Data Governance: Establish clear data governance policies and procedures to manage data collection, storage, and access effectively.
-
Documentation of Assumptions and Limitations: Clearly document any assumptions, limitations, or potential biases in the data collection process to provide context for the data's interpretation.
Effective data collection requires careful planning, attention to detail, and adherence to best practices. Following these key steps helps ensure that the data collected is of high quality, reliable, and suitable for analysis and decision-making.
Data Collection Considerations and Best Practices
Effective data collection involves careful consideration of various factors and adherence to best practices to ensure that the collected data is of high quality, reliable, and ethically sound. Here are some key data collection considerations and best practices:
-
Clearly Define Objectives: Begin by precisely defining the research or data collection objectives. Understand what information is needed and why it is important.
-
Ethical Considerations: Always prioritize ethical principles when collecting data. Obtain informed consent from participants, ensure data privacy and confidentiality, and comply with relevant ethical guidelines and regulations.
-
Select Appropriate Data Sources: Choose the most suitable data sources and methods for your research objectives. Consider whether primary data collection (gathering data firsthand) or secondary data (using existing data) is more appropriate.
-
Pilot Testing: Before full-scale data collection, conduct pilot tests or pre-tests to identify and rectify any issues with data collection instruments, such as surveys or questionnaires.
-
Sampling: If using sampling, select a representative sample that accurately reflects the population of interest. Ensure randomness and minimize selection bias.
-
Standardize Procedures: Maintain consistency in data collection procedures. Ensure that all data collectors follow the same protocols to reduce bias and increase data reliability.
-
Training: Properly train data collectors on data collection methods, instruments, and ethical considerations. Regularly update their training to stay informed about best practices.
-
Data Collection Tools: Use appropriate data collection tools and technologies. Ensure that instruments are clear, unbiased, and suitable for the target audience.
-
Data Entry and Validation: If collecting data manually, establish data entry protocols and validation procedures to minimize errors and ensure data accuracy.
-
Data Security: Safeguard data throughout the collection process. Use encryption, access controls, and secure storage methods to protect data from unauthorized access or breaches.
-
Documentation: Maintain detailed documentation of the data collection process, including data collection protocols, instruments, and any modifications or issues encountered during collection.
-
Quality Control: Implement quality control measures at different stages of data collection to identify and rectify errors or inconsistencies promptly.
-
Continuous Monitoring: Continuously monitor the data collection process for adherence to protocols, completeness, and quality. Address issues as they arise.
-
Data Validation: Cross-check data entries, validate data against predefined criteria, and ensure data is consistent and accurate.
-
Data Cleaning: After data collection, thoroughly clean and preprocess the data to handle missing values, outliers, and inconsistencies.
-
Data Storage and Archiving: Store data securely, ensuring backup and redundancy. Archive data for future reference and compliance with data retention policies.
-
Data Governance: Establish clear data governance policies and procedures to manage data collection, storage, and access effectively.
-
Feedback and Iteration: Gather feedback from data collectors and stakeholders to identify areas for improvement in data collection processes. Continuously refine methods based on feedback.
-
Data Documentation: Document any assumptions, limitations, or potential biases in the data collection process. Transparency is essential for the data's interpretation.
-
Data Reporting: Clearly report the methods, procedures, and findings of the data collection effort, allowing for transparency and reproducibility.
-
Data Dissemination: Share data appropriately, considering data-sharing agreements, copyrights, and licensing requirements.
-
Compliance: Ensure compliance with legal, regulatory, and institutional requirements related to data collection, especially when dealing with sensitive or personal information.
By carefully considering these factors and following best practices, data collectors can enhance the quality and reliability of the data collected, ultimately leading to more robust research findings and informed decision-making.
How to get course?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Data Science with R programming
FAQs
-
What is data collection, and why is it important?
Data collection is the process of gathering and capturing information or data from various sources for analysis, research, decision-making, or record-keeping. It is important because it provides the foundation for informed decisions, research, and problem-solving in various fields.
-
What are the common methods of data collection?
Common methods of data collection include surveys, interviews, observations, experiments, sensors and instruments, document analysis, web scraping, social media monitoring, sampling, and more.
-
What are the different types of data collected in research?
Data in research can be categorized as quantitative (numeric) or qualitative (non-numeric). Quantitative data includes numerical values, while qualitative data includes descriptions, narratives, and observations.
-
What are the essential steps in the data collection process?
Key steps include defining objectives, selecting data sources, designing data collection instruments, sampling (if applicable), pilot testing, data collection, data entry, data verification, data storage, analysis, interpretation, reporting, archiving, and addressing ethical considerations.
-
What tools and software are commonly used for data collection?
Common data collection tools and software include online survey platforms (e.g., SurveyMonkey), mobile data collection apps (e.g., Fulcrum), data analytics software (e.g., Excel, R), and geographic information systems (GIS) software (e.g., ArcGIS).
-
What are the challenges in data collection?
Challenges in data collection include issues related to sampling bias, data quality, resource constraints, privacy concerns, ethical considerations, data security, and potential biases in data collection methods.
-
What are some best practices for maintaining data collection integrity?
Best practices include defining clear objectives, ensuring ethical conduct, selecting appropriate data sources, pilot testing, proper training, data validation, documentation, quality control, and continuous monitoring.
-
How can data collection tools help streamline the process?
Data collection tools automate and streamline data capture, reduce errors, improve data accuracy, and provide efficient ways to gather and manage data, making the process more efficient and reliable.
-
What is the role of data collection in decision-making and research?
Data collection provides the evidence and insights necessary for informed decision-making, problem-solving, scientific research, and the generation of knowledge in various fields.
-
What precautions should be taken when collecting sensitive data?
When collecting sensitive data, it's essential to obtain informed consent, implement strong data security measures, adhere to ethical guidelines, and comply with privacy regulations to protect individuals' information.
Read More
In today's data-driven world, understanding the intricacies of data collection methods, types, and tools is essential for individuals and organizations alike. "Data Collection Methods, Types, and Tools: A Deep Dive" offers a comprehensive exploration of this vital subject. This deep dive navigates the diverse landscape of data collection, from traditional methodologies like surveys to cutting-edge techniques such as web scraping and IoT sensors, covering a wide spectrum of data types along the way. Additionally, it unveils a rich array of tools and technologies that empower data collectors to efficiently gather and transform raw information into actionable insights. Whether you are a data enthusiast, researcher, business professional, or simply curious about the world of data, this deep dive promises to equip you with the knowledge to harness the power of data effectively.
Table of Contents
-
What is Data Collection?
-
Why Do We Need Data Collection?
-
What Are the Different Methods of Data Collection?
-
Data Collection Tools
-
The Importance of Ensuring Accurate and Appropriate Data Collection
-
Issues Related to Maintaining the Integrity of Data Collection
-
What are Common Challenges in Data Collection?
-
What are the Key Steps in the Data Collection Process?
-
Data Collection Considerations and Best Practices
-
FAQs
What is Data Collection?
Data collection is the process of gathering and capturing information or data from various sources, such as individuals, instruments, sensors, or documents, for the purpose of analysis, research, decision-making, or record-keeping. It is a fundamental step in the data management and analysis pipeline and plays a crucial role in various fields, including science, business, healthcare, social sciences, and many others.
Data collection can involve various methods and techniques, depending on the nature of the data, the research objectives, and the available resources. Some common methods of data collection include:
-
Surveys and Questionnaires: Gathering information by asking structured questions to individuals or groups.
-
Interviews: Conducting one-on-one or group interviews to collect qualitative data through open-ended or structured questions.
-
Observations: Directly observing and recording information about a particular subject or event.
-
Experiments: Manipulating variables under controlled conditions to collect data on their effects.
-
Sensors and Instruments: Using specialized devices or sensors to collect data, such as temperature, pressure, or GPS coordinates.
-
Document Analysis: Reviewing and extracting data from written or digital documents, such as reports, articles, or social media posts.
-
Web Scraping: Automated extraction of data from websites and online sources.
-
Social Media Monitoring: Collecting data from social media platforms to analyze trends, sentiments, or user behavior.
-
Data Logging: Continuous recording of data over time, often used in fields like environmental monitoring or industrial processes.
-
Sampling: Collecting data from a subset of a larger population or dataset to make inferences about the whole.
-
Mobile Apps and Surveys: Collecting data through mobile applications or surveys conducted on smartphones and tablets.
Effective data collection involves careful planning, the use of appropriate methods, ensuring data quality and accuracy, and often adhering to ethical and privacy considerations. Once collected, data can be processed, analyzed, and interpreted to extract valuable insights and support decision-making processes.
Why Do We Need Data Collection?
Data collection is a crucial component of modern society, serving as the foundation for informed decision-making, problem-solving, and progress across various domains. It provides the empirical evidence needed to understand complex issues, whether in healthcare, business, government, or scientific research. By systematically gathering data, individuals and organizations can assess performance, identify challenges, and formulate effective strategies. In healthcare, for example, data collection helps doctors diagnose diseases, researchers develop new treatments, and policymakers allocate resources to improve public health outcomes. In business, it guides market strategies, enables personalized customer experiences, and enhances efficiency through data-driven analytics. Ultimately, data collection empowers individuals, institutions, and societies to adapt, innovate, and thrive in an ever-evolving world.
Furthermore, data collection is essential for accountability and transparency. It creates a record of actions and outcomes, allowing for scrutiny and accountability of individuals, organizations, and governments. This transparency promotes ethical behavior and helps prevent fraud and corruption. In today's interconnected world, data collection also plays a pivotal role in addressing global challenges like climate change, where data on environmental trends is essential for informed policy decisions. In summary, data collection is not just a technical process; it's a cornerstone of informed decision-making, accountability, and progress across diverse sectors, shaping the way we understand and interact with the world around us.
What Are the Different Methods of Data Collection?
There are various methods of data collection, each suited to specific research objectives, types of data, and practical considerations. Here are some of the different methods commonly used:
-
Surveys and Questionnaires: Surveys involve asking individuals or groups a set of structured questions. Questionnaires can be administered in person, by phone, through email, or online. They are useful for collecting quantitative data on opinions, preferences, and demographics.
-
Interviews: Interviews involve one-on-one or group interactions where researchers ask questions and record responses. Interviews can be structured (with predetermined questions) or unstructured (more open-ended) and are often used to gather qualitative data.
-
Observations: This method involves directly observing and recording behavior, events, or phenomena. It can be done in a controlled environment (e.g., a laboratory) or in the field (e.g., naturalistic observations in a public space).
-
Experiments: Experiments involve manipulating one or more variables under controlled conditions to observe their effects. Experimental research aims to establish cause-and-effect relationships and is common in scientific studies.
-
Secondary Data Analysis: Researchers analyze existing data collected by others. This method is cost-effective and can involve various types of data, such as government statistics, academic studies, or historical records.
-
Document Analysis: Researchers review and extract information from written or digital documents, including reports, articles, social media posts, and historical texts. This is often used in content analysis and textual research.
-
Web Scraping: Automated tools are used to extract data from websites, forums, and social media platforms. Web scraping is common for collecting large datasets from the internet.
-
Sensors and Instruments: Specialized devices and sensors are used to collect data automatically. Examples include temperature sensors, GPS devices, heart rate monitors, and satellite imagery.
-
Sampling: Rather than collecting data from an entire population, researchers collect data from a representative subset (sample). Sampling methods include random sampling, stratified sampling, and convenience sampling.
-
Mobile Apps and Surveys: Data can be collected through mobile applications or surveys administered on smartphones and tablets. This method is convenient and allows for real-time data collection.
-
Social Media Monitoring: Data is collected from social media platforms to analyze trends, sentiments, user behavior, and public opinion. Social media APIs (Application Programming Interfaces) are often used for data access.
-
Data Logging: Continuous recording of data over time is used in various fields, including environmental monitoring (e.g., weather stations), industrial processes, and performance monitoring (e.g., athletes' heart rate during a race).
-
Focus Groups: A moderator leads a discussion with a small group of participants to gather insights, opinions, and perceptions on a particular topic. Focus groups are common in market research and qualitative studies.
-
Diaries and Journals: Participants keep records of their experiences, thoughts, or behaviors over a specified period. This method is often used to study daily routines or personal reflections.
The choice of data collection method depends on research goals, the type of data needed (quantitative or qualitative), available resources, ethical considerations, and practical constraints. Researchers often employ a combination of methods to triangulate data and enhance the validity and reliability of their findings.
Data Collection Tools
Data collection tools are software or hardware solutions designed to facilitate the process of gathering, storing, and managing data from various sources. These tools are used in research, business, and various other fields to streamline data collection and improve its accuracy and efficiency. Here are some common types of data collection tools:
-
Online Survey Tools: Online survey platforms like SurveyMonkey, Google Forms, and Qualtrics allow users to create and distribute surveys and questionnaires over the internet. They offer features for designing surveys, collecting responses, and analyzing results.
-
Mobile Data Collection Apps: Mobile apps like Survey123 (Esri), Fulcrum, and QuickTapSurvey enable data collection in the field using smartphones and tablets. Users can design custom forms, collect data offline, and sync it when connected to the internet.
-
Data Analytics Software: Tools like Microsoft Excel, R, Python (with libraries like Pandas), and SPSS are used to analyze and visualize data collected from various sources. They help in extracting insights and patterns from datasets.
-
Database Management Systems (DBMS): Systems like MySQL, PostgreSQL, Microsoft SQL Server, and MongoDB are used to store, organize, and manage large volumes of structured data. They are commonly employed in businesses and research institutions.
-
Geographic Information Systems (GIS): GIS software such as ArcGIS and QGIS is used for collecting and analyzing spatial data, including maps, GPS coordinates, and geographic features.
-
Data Collection APIs: Some online platforms and services offer APIs (Application Programming Interfaces) that allow developers to integrate data collection capabilities into custom applications. For example, social media platforms like Twitter and Facebook offer APIs for data retrieval.
-
Data Logger Devices: Physical devices like data loggers and sensors are used in various industries to automatically collect data, such as temperature, humidity, and pressure, and store it for later analysis.
-
Document Scanners and OCR Software: Tools like Adobe Acrobat and OCR (Optical Character Recognition) software can be used to digitize and collect data from paper documents, such as forms, invoices, and contracts.
-
Web Scraping Tools: Tools like Beautiful Soup, Scrapy, and Octoparse automate the extraction of data from websites and web pages. They are commonly used for web-based data collection.
-
Audio and Video Recording Software: Researchers and professionals often use audio and video recording tools to capture interviews, meetings, and events. Transcription software can convert spoken words into text data for analysis.
-
Qualitative Data Analysis Software: Software like NVivo and MAXQDA is specifically designed for researchers collecting qualitative data (e.g., interviews, focus groups). They assist in organizing, coding, and analyzing textual or multimedia data.
-
Biometric Data Collection Tools: Devices like fingerprint scanners, facial recognition cameras, and heart rate monitors are used to collect biometric data for security, healthcare, and other applications.
-
Blockchain Technology: Blockchain-based tools can ensure the secure and transparent collection and storage of data, making them suitable for applications where data integrity and immutability are critical.
-
Machine Learning and AI Platforms: Advanced machine learning and AI platforms can assist in data collection by automating processes, recognizing patterns, and making predictions based on existing data.
The choice of data collection tools depends on the specific requirements of a project, the type of data being collected, and the available resources. In many cases, a combination of tools may be used to capture, store, and analyze data effectively.
The Importance of Ensuring Accurate and Appropriate Data Collection
Ensuring accurate and appropriate data collection is of paramount importance in research, decision-making, and various fields for several compelling reasons:
-
Reliable Results: Accurate data leads to trustworthy research findings and better decision-making.
-
Credibility: Accurate data enhances the credibility of reports and studies.
-
Effective Decisions: It supports informed and effective decision-making.
-
Efficiency: Appropriate data collection saves time and resources.
-
Ethics and Privacy: It respects ethical standards and privacy concerns.
-
Reducing Bias: It helps reduce bias in research and analysis.
-
Long-Term Impact: Inaccurate data can have lasting consequences.
-
Resource Allocation: Guides efficient resource allocation.
-
Reproducibility: Facilitates the reproducibility of experiments.
-
Customer Satisfaction: Improves customer satisfaction in businesses.
-
Public Health and Safety: Crucial for public health and safety monitoring.
-
Environmental Conservation: Supports conservation efforts.
-
Innovation: Drives innovation and improvement in various fields.
Issues Related to Maintaining the Integrity of Data Collection
Maintaining the integrity of data collection is essential to ensure that data is accurate, reliable, and free from bias or manipulation. However, several issues can compromise data integrity. Here are some common issues related to maintaining data collection integrity:
-
Sampling Bias: When the sample used for data collection is not representative of the larger population, it can introduce bias into the results. This can occur due to non-random sampling methods or inadequate sample sizes.
-
Selection Bias: Researchers or data collectors may inadvertently favor certain groups or individuals when selecting participants or data sources, leading to biased data.
-
Non-Response Bias: If a significant portion of the selected participants does not respond to surveys or data requests, the results may not accurately represent the entire population.
-
Measurement Error: Errors in data measurement or data entry can occur due to human error, faulty equipment, or inconsistent measurement standards. These errors can introduce inaccuracies into the collected data.
-
Data Tampering: Deliberate manipulation or tampering with data can occur for various reasons, such as fraud, academic misconduct, or political motives. Maintaining data security and access controls is crucial to prevent such issues.
-
Data Privacy Concerns: Collecting sensitive or personally identifiable information without proper consent or security measures can lead to privacy breaches and ethical dilemmas.
-
Response Bias: Respondents may provide inaccurate or socially desirable responses, especially in surveys or interviews, leading to biased data.
-
Observer Bias: When data is collected through observations, the observer's personal biases and interpretations can influence the data collected.
-
Researcher Bias: Researchers' own beliefs, preferences, or expectations can inadvertently influence data collection, analysis, or interpretation, leading to bias.
-
Missing Data: Incomplete or missing data points can impact the overall integrity of the dataset, potentially leading to incomplete or biased conclusions.
-
Survey Question Bias: Poorly constructed survey questions or leading questions can unintentionally guide respondents toward certain answers, skewing the results.
-
Temporal Bias: Data collected at specific times or seasons may not accurately represent long-term trends or conditions.
-
Cross-Cultural Bias: Data collected in one cultural context may not be applicable or relevant in another, leading to cultural bias.
-
Lack of Data Documentation: Inadequate documentation of data collection methods, protocols, and procedures can hinder transparency and replication efforts.
-
Conflict of Interest: Financial or personal interests of data collectors or researchers can compromise the objectivity and integrity of data collection.
To address these issues and maintain data collection integrity, it is essential to implement rigorous data collection protocols, ensure transparency, use standardized measurement tools, conduct thorough data validation and verification, and adhere to ethical guidelines. Additionally, peer review, data audits, and data quality assessments can help identify and mitigate potential problems related to data integrity.
What are Common Challenges in Data Collection?
Data collection can be a complex and challenging process, and researchers, organizations, and individuals often encounter various obstacles. Here are some common challenges in data collection:
-
Selection Bias: It can be challenging to ensure that the data collected is representative of the entire population or target group. Biased sampling methods or non-response bias can lead to skewed results.
-
Data Quality: Maintaining data accuracy, completeness, and consistency can be difficult. Data may be prone to errors, duplications, or missing values, affecting its reliability.
-
Resource Constraints: Limited time, budget, and human resources can hinder data collection efforts, especially in large-scale projects.
-
Privacy Concerns: Collecting sensitive or personally identifiable information must be done with care to ensure data privacy and compliance with relevant regulations.
-
Ethical Considerations: Researchers must adhere to ethical guidelines when collecting data, which can be challenging when dealing with vulnerable populations or sensitive topics.
-
Data Security: Safeguarding data against breaches, theft, or unauthorized access is crucial. Data breaches can have serious consequences for individuals and organizations.
-
Data Collection Instruments: Developing and testing data collection instruments, such as surveys or questionnaires, requires careful consideration to ensure they are valid and reliable.
-
Technological Challenges: Implementing data collection technologies, especially in remote or resource-constrained areas, can be challenging. Issues like connectivity and compatibility may arise.
-
Non-Response: Collecting data from reluctant or uncooperative participants can be difficult, leading to missing or incomplete data.
-
Data Entry Errors: Manual data entry can introduce errors, especially when transcribing data from paper to digital formats.
-
Language and Cultural Barriers: In cross-cultural research, language and cultural differences may affect data collection and interpretation.
-
Data Verification: Verifying the accuracy of collected data can be time-consuming and resource-intensive.
-
Data Bias: Data may be influenced by the bias or subjectivity of the data collector, respondent, or observer.
-
Data Volume: Dealing with large volumes of data can be challenging, requiring efficient storage, processing, and analysis solutions.
-
Temporal Changes: Data collected at different times may not be directly comparable due to changing conditions or external factors.
-
Data Ownership: Clarifying data ownership and usage rights can be a challenge, especially in collaborative research or data-sharing initiatives.
-
Data Governance: Establishing clear data governance policies and procedures is essential for managing data collection efforts effectively.
-
Environmental Factors: In some cases, data collection may be affected by weather conditions, natural disasters, or other environmental factors.
-
Human Error: Mistakes made during the data collection process, such as misreading instruments or making errors in data recording, can impact data quality.
-
Legal and Regulatory Compliance: Ensuring that data collection activities comply with relevant laws and regulations can be complex, especially when conducting research across borders.
Addressing these challenges often requires careful planning, well-defined data collection protocols, the use of appropriate technology, rigorous quality control measures, and ongoing monitoring and evaluation of the data collection process. Collaborative efforts and expertise in data collection methodologies can also help overcome many of these challenges.
What are the Key Steps in the Data Collection Process?
The data collection process involves a series of key steps to gather information systematically and ensure the data's accuracy and reliability. Here are the fundamental steps in the data collection process:
-
Define Objectives: Clearly define the research or data collection objectives. Understand the purpose, scope, and goals of the data collection effort.
-
Select Data Sources: Identify the sources of data, which can include surveys, interviews, observations, existing databases, sensors, documents, or any other relevant sources.
-
Design Data Collection Instruments: Develop data collection instruments, such as surveys, questionnaires, interview guides, or observation protocols. Ensure they are clear, unbiased, and aligned with the research objectives.
-
Select Sampling Methods: If applicable, choose the appropriate sampling method (e.g., random sampling, stratified sampling) to select a representative subset of the population or dataset.
-
Pilot Testing: Test the data collection instruments and procedures with a small, representative group to identify and address any issues, such as unclear questions or logistical challenges.
-
Data Collection: Conduct the actual data collection activities according to the established protocols. Ensure consistency and uniformity in data collection procedures.
-
Data Entry: If data is collected in paper form, enter it into digital format. Implement quality control measures to minimize data entry errors.
-
Data Verification: Verify the accuracy and completeness of the collected data. This step may involve data cleaning and validation to identify and correct errors or inconsistencies.
-
Data Storage: Safely store the collected data in a secure and organized manner, whether in physical or digital format. Implement data security measures to protect sensitive information.
-
Data Documentation: Maintain detailed documentation of the data collection process, including protocols, instruments, and any modifications made during the collection.
-
Data Analysis: If applicable, perform data analysis using appropriate statistical or analytical methods. Transform raw data into meaningful insights and findings.
-
Data Interpretation: Interpret the results of data analysis in the context of research objectives. Draw conclusions and make recommendations based on the data.
-
Report Findings: Communicate the results and findings through reports, presentations, or other appropriate channels. Clearly and transparently convey the insights derived from the data.
-
Data Archiving: Store the data for future reference or potential replication of the study. Ensure data is accessible and properly archived for compliance and transparency.
-
Ethical Considerations: Adhere to ethical standards throughout the data collection process, respecting privacy, informed consent, and any relevant legal or institutional requirements.
-
Quality Control: Implement quality control measures at various stages of data collection to minimize errors, bias, and inconsistencies.
-
Continuous Monitoring: Continuously monitor the data collection process to identify and address any issues promptly. Make necessary adjustments as needed.
-
Feedback and Iteration: Collect feedback from stakeholders and team members involved in data collection. Use feedback to improve data collection procedures for future efforts.
-
Data Governance: Establish clear data governance policies and procedures to manage data collection, storage, and access effectively.
-
Documentation of Assumptions and Limitations: Clearly document any assumptions, limitations, or potential biases in the data collection process to provide context for the data's interpretation.
Effective data collection requires careful planning, attention to detail, and adherence to best practices. Following these key steps helps ensure that the data collected is of high quality, reliable, and suitable for analysis and decision-making.
Data Collection Considerations and Best Practices
Effective data collection involves careful consideration of various factors and adherence to best practices to ensure that the collected data is of high quality, reliable, and ethically sound. Here are some key data collection considerations and best practices:
-
Clearly Define Objectives: Begin by precisely defining the research or data collection objectives. Understand what information is needed and why it is important.
-
Ethical Considerations: Always prioritize ethical principles when collecting data. Obtain informed consent from participants, ensure data privacy and confidentiality, and comply with relevant ethical guidelines and regulations.
-
Select Appropriate Data Sources: Choose the most suitable data sources and methods for your research objectives. Consider whether primary data collection (gathering data firsthand) or secondary data (using existing data) is more appropriate.
-
Pilot Testing: Before full-scale data collection, conduct pilot tests or pre-tests to identify and rectify any issues with data collection instruments, such as surveys or questionnaires.
-
Sampling: If using sampling, select a representative sample that accurately reflects the population of interest. Ensure randomness and minimize selection bias.
-
Standardize Procedures: Maintain consistency in data collection procedures. Ensure that all data collectors follow the same protocols to reduce bias and increase data reliability.
-
Training: Properly train data collectors on data collection methods, instruments, and ethical considerations. Regularly update their training to stay informed about best practices.
-
Data Collection Tools: Use appropriate data collection tools and technologies. Ensure that instruments are clear, unbiased, and suitable for the target audience.
-
Data Entry and Validation: If collecting data manually, establish data entry protocols and validation procedures to minimize errors and ensure data accuracy.
-
Data Security: Safeguard data throughout the collection process. Use encryption, access controls, and secure storage methods to protect data from unauthorized access or breaches.
-
Documentation: Maintain detailed documentation of the data collection process, including data collection protocols, instruments, and any modifications or issues encountered during collection.
-
Quality Control: Implement quality control measures at different stages of data collection to identify and rectify errors or inconsistencies promptly.
-
Continuous Monitoring: Continuously monitor the data collection process for adherence to protocols, completeness, and quality. Address issues as they arise.
-
Data Validation: Cross-check data entries, validate data against predefined criteria, and ensure data is consistent and accurate.
-
Data Cleaning: After data collection, thoroughly clean and preprocess the data to handle missing values, outliers, and inconsistencies.
-
Data Storage and Archiving: Store data securely, ensuring backup and redundancy. Archive data for future reference and compliance with data retention policies.
-
Data Governance: Establish clear data governance policies and procedures to manage data collection, storage, and access effectively.
-
Feedback and Iteration: Gather feedback from data collectors and stakeholders to identify areas for improvement in data collection processes. Continuously refine methods based on feedback.
-
Data Documentation: Document any assumptions, limitations, or potential biases in the data collection process. Transparency is essential for the data's interpretation.
-
Data Reporting: Clearly report the methods, procedures, and findings of the data collection effort, allowing for transparency and reproducibility.
-
Data Dissemination: Share data appropriately, considering data-sharing agreements, copyrights, and licensing requirements.
-
Compliance: Ensure compliance with legal, regulatory, and institutional requirements related to data collection, especially when dealing with sensitive or personal information.
By carefully considering these factors and following best practices, data collectors can enhance the quality and reliability of the data collected, ultimately leading to more robust research findings and informed decision-making.
How to get course?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: SMAC Certication
-
Big Data: Big Data and Hadoop Administrator
-
Digital Marketing : Digital Marketing Certification
-
Data Science : Data Science with R programming
FAQs
-
What is data collection, and why is it important?
Data collection is the process of gathering and capturing information or data from various sources for analysis, research, decision-making, or record-keeping. It is important because it provides the foundation for informed decisions, research, and problem-solving in various fields.
-
What are the common methods of data collection?
Common methods of data collection include surveys, interviews, observations, experiments, sensors and instruments, document analysis, web scraping, social media monitoring, sampling, and more.
-
What are the different types of data collected in research?
Data in research can be categorized as quantitative (numeric) or qualitative (non-numeric). Quantitative data includes numerical values, while qualitative data includes descriptions, narratives, and observations.
-
What are the essential steps in the data collection process?
Key steps include defining objectives, selecting data sources, designing data collection instruments, sampling (if applicable), pilot testing, data collection, data entry, data verification, data storage, analysis, interpretation, reporting, archiving, and addressing ethical considerations.
-
What tools and software are commonly used for data collection?
Common data collection tools and software include online survey platforms (e.g., SurveyMonkey), mobile data collection apps (e.g., Fulcrum), data analytics software (e.g., Excel, R), and geographic information systems (GIS) software (e.g., ArcGIS).
-
What are the challenges in data collection?
Challenges in data collection include issues related to sampling bias, data quality, resource constraints, privacy concerns, ethical considerations, data security, and potential biases in data collection methods.
-
What are some best practices for maintaining data collection integrity?
Best practices include defining clear objectives, ensuring ethical conduct, selecting appropriate data sources, pilot testing, proper training, data validation, documentation, quality control, and continuous monitoring.
-
How can data collection tools help streamline the process?
Data collection tools automate and streamline data capture, reduce errors, improve data accuracy, and provide efficient ways to gather and manage data, making the process more efficient and reliable.
-
What is the role of data collection in decision-making and research?
Data collection provides the evidence and insights necessary for informed decision-making, problem-solving, scientific research, and the generation of knowledge in various fields.
-
What precautions should be taken when collecting sensitive data?
When collecting sensitive data, it's essential to obtain informed consent, implement strong data security measures, adhere to ethical guidelines, and comply with privacy regulations to protect individuals' information.
Feasibility Study and Its Importance in Project Management
In the dynamic landscape of project management and business endeavors, the path to success is often paved with uncertainty. For every visionary project or entrepreneurial venture, there exists an inherent risk that can lead to unforeseen challenges, setbacks, or even failure. In this complex terrain, the beacon of clarity and guidance comes in the form of a "Feasibility Study." It is the compass that not only points to the direction of project viability but also illuminates the obstacles that lie ahead. This journey into the realm of feasibility studies unveils their pivotal role in project management, where informed decisions, meticulous analysis, and calculated risk mitigation converge to shape the destiny of projects and businesses. Join us as we delve into the significance of feasibility studies, understanding their multifaceted importance in steering the course of success.
Table of Contents
What is a Feasibility Study?
Understanding A Feasibility Study
Types of Feasibility Study
Importance of Feasibility Study
Benefits of a Feasibility Study
What Is Included in a Feasibility Study Report?
Tools for Conducting a Feasibility Study
Examples of a Feasibility Study
What is the Purpose of a Feasibility Study?
How Do You Write a Feasibility Study?
7 Steps to Do a Feasibility Study
How to Conduct a Feasibility Study
Feasibility Study vs. Business Plan
Reasons to Do or Not to Do a Feasibility Study
Conclusion
FAQs
What is a Feasibility Study?
A feasibility study is a thorough examination of whether a proposed project or business idea is practical and likely to succeed. It involves analyzing factors like market demand, technical capabilities, financial viability, operational logistics, legal requirements, environmental impact, and potential risks. The study helps decision-makers determine whether it's worth pursuing the project or if adjustments are needed. Ultimately, it provides a clear recommendation on whether to go ahead with the project or not, based on a comprehensive assessment of all relevant factors.
Understanding A Feasibility Study
A feasibility study is a comprehensive analysis conducted during the early stages of project planning to determine the practicality and viability of a proposed project or business endeavor. It involves assessing various factors such as market demand, technical feasibility, financial considerations, operational logistics, legal and regulatory requirements, environmental impacts, and potential risks. The goal is to answer the fundamental question of whether the project is feasible and worth pursuing. A well-executed feasibility study provides decision-makers with valuable insights to make informed choices about whether to invest resources, time, and effort into the project or explore alternative options. Ultimately, it helps prevent costly mistakes by identifying potential challenges and opportunities early in the project's development.
Types of Feasibility Study
-
Market Feasibility Study: This type of study is essential when considering a new product or service. It assesses whether there is enough demand in the market for the proposed offering. Market feasibility examines factors such as target demographics, customer preferences, market trends, competition, and potential market size. The goal is to determine if there is a substantial and sustainable market for the product or service.
-
Technical Feasibility Study: When a project relies on specific technology or technical processes, a technical feasibility study is conducted. It evaluates whether the required technology and expertise are available or can be developed within the project's scope. This study also looks at potential technical challenges and obstacles that might hinder project implementation.
-
Financial Feasibility Study: Financial feasibility is crucial to assess the project's profitability and financial viability. It involves estimating all costs associated with the project, including initial investments, operating expenses, and maintenance costs. Revenue projections and cash flow analysis are also conducted to determine if the project can generate a positive return on investment (ROI).
-
Operational Feasibility Study: This study focuses on how the proposed project will operate in practical terms. It assesses whether the project can be effectively integrated into existing operations or if it requires significant changes to processes, staffing, and logistics. Operational feasibility helps ensure that the project can be executed smoothly and efficiently.
-
Legal and Regulatory Feasibility Study: Projects often need to navigate complex legal and regulatory landscapes. A legal and regulatory feasibility study examines whether the project complies with all relevant laws, regulations, permits, and industry-specific requirements. It identifies potential legal obstacles and outlines the steps necessary for legal and regulatory compliance.
Importance of Feasibility Study
The importance of a feasibility study in the context of project management and business decision-making cannot be overstated. Here are several key reasons why conducting a feasibility study is crucial:
-
Risk Identification and Mitigation: A feasibility study helps identify potential risks and challenges associated with a project. By recognizing these risks early, project managers and stakeholders can develop strategies to mitigate them effectively. This proactive approach minimizes the likelihood of unforeseen issues derailing the project later on.
-
Cost-Benefit Analysis: One of the primary purposes of a feasibility study is to assess the financial feasibility of a project. It involves estimating the costs of implementing the project and comparing them to the expected benefits. This analysis helps in determining whether the project will yield a positive return on investment (ROI). If the costs outweigh the benefits, it may not be financially viable.
-
Resource Allocation: Resource allocation is a critical aspect of project management. A feasibility study outlines the resources required for the project, including manpower, equipment, and materials. This information allows project managers to allocate resources efficiently and ensure that they are available when needed, reducing delays and cost overruns.
-
Alignment with Strategic Goals: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses how the proposed project aligns with these strategic goals. If there is a mismatch, it provides an opportunity to refine the project's scope or reconsider its importance in the context of the organization's overarching strategy.
-
Stakeholder Buy-In: Feasibility studies involve engaging with key stakeholders, including sponsors, investors, and end-users. These stakeholders play a crucial role in the success of the project. The study helps in gaining their buy-in and support by providing them with a clear understanding of the project's goals, benefits, and potential risks.
-
Decision-Making Tool: A feasibility study serves as a decision-making tool for project sponsors and stakeholders. It provides them with the information needed to make an informed decision about whether to proceed with the project, revise its scope, or abandon it altogether. This ensures that resources are allocated to projects with a higher likelihood of success.
-
Project Viability Assessment: Feasibility studies assess the overall viability of a project. They consider various aspects, including market demand, technical feasibility, financial considerations, and operational logistics. This comprehensive evaluation helps in determining whether the project is worth pursuing and has a realistic chance of success.
-
Cost Control: By estimating project costs and potential cost overruns during the feasibility study, project managers can develop effective cost control measures. This proactive approach allows for better financial management throughout the project's lifecycle.
-
Time Efficiency: A feasibility study helps in setting realistic project timelines. By identifying potential delays and obstacles early on, project managers can plan and allocate resources more effectively, reducing the likelihood of project schedule disruptions.
-
Alternative Evaluation: Feasibility studies often explore alternative solutions or approaches to achieve project objectives. This allows decision-makers to compare different options and select the most feasible and cost-effective one.
In conclusion, a well-conducted feasibility study is an indispensable tool in project management and business decision-making. It provides a structured and systematic approach to assess a project's feasibility, risks, costs, and benefits, ultimately leading to more informed and successful project outcomes.
Benefits of a Feasibility Study
A feasibility study offers a multitude of benefits that are invaluable to organizations and stakeholders contemplating new projects or business ventures. Firstly, it serves as a risk mitigation tool by uncovering potential challenges and obstacles early in the project's conceptualization phase, enabling the development of strategies to address these concerns proactively. Furthermore, a well-executed feasibility study empowers decision-makers with comprehensive information and data, facilitating informed choices regarding whether to proceed with the project, modify its scope, or abandon it altogether. Financial feasibility studies, a key component, provide financial clarity by estimating costs, revenue projections, and profitability prospects, ensuring alignment with budget constraints. Resource allocation becomes more efficient, as the study identifies the resources needed and helps prevent delays or shortages. Additionally, it ensures that the project aligns with an organization's strategic goals, fosters stakeholder buy-in, and assesses environmental and social responsibility. In essence, a feasibility study is an essential compass guiding project success by minimizing risks, optimizing resources, and ensuring strategic alignment.
What Is Included in a Feasibility Study Report?
A comprehensive feasibility study report typically includes the following key sections and information:
-
Executive Summary: This section provides a concise overview of the entire feasibility study, summarizing its main findings and recommendations. It is often the first section decision-makers read, so it should effectively convey the project's viability and key takeaways.
-
Introduction: The introduction sets the stage for the study by explaining the purpose, scope, and objectives of the feasibility study. It also introduces the project or business idea being evaluated.
-
Project Description: This section provides a detailed description of the proposed project, including its goals, objectives, and scope. It outlines what the project aims to achieve and its intended outcomes.
-
Market Analysis: In this section, the study delves into the market feasibility, examining factors such as market size, growth potential, target demographics, competition, and customer demand. It also assesses market trends and dynamics.
-
Technical Analysis: The technical analysis evaluates the technical feasibility of the project. It considers the technology, equipment, and infrastructure required, as well as potential technical challenges and solutions. It may also include information on suppliers and technology partners.
-
Financial Analysis: The financial analysis is a critical component. It includes detailed financial projections, cost estimates, revenue forecasts, and cash flow analysis. It assesses the project's financial feasibility, including its return on investment (ROI) and payback period.
-
Operational Analysis: This section focuses on the operational feasibility of the project. It looks at how the project will function in practical terms, including staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Considerations: Here, the study addresses legal and regulatory feasibility by identifying the legal requirements, permits, licenses, and compliance issues relevant to the project. It also outlines strategies for ensuring compliance.
-
Environmental and Social Impact Assessment: This section assesses the potential environmental and social impacts of the project, including its sustainability, community acceptance, and corporate social responsibility considerations.
-
Risk Analysis: The risk analysis identifies potential risks and uncertainties associated with the project and provides recommendations for risk mitigation. It may include a risk matrix or assessment of key risks.
-
Alternative Solutions: Feasibility studies often explore alternative approaches or solutions to achieve the project's objectives. This section compares different options and provides rationale for the chosen approach.
-
Recommendations: Based on the analysis conducted throughout the study, this section presents clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. It outlines the rationale for the recommended course of action.
-
Appendices: The appendices contain supplementary information, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the findings and conclusions of the feasibility study.
-
References: If the study includes external sources or references, a list of these sources should be provided in a reference section.
A well-structured feasibility study report serves as a comprehensive document that guides decision-makers in assessing the viability of a project or business venture. It should be clear, well-organized, and supported by data and analysis to ensure that stakeholders have the information needed to make informed decisions.
Tools for Conducting a Feasibility Study
-
Microsoft Excel: Use it for financial calculations and modeling.
-
Survey Software: Collect market data through tools like SurveyMonkey or Google Forms.
-
Market Research Tools: Access industry reports and trends with tools like Statista.
-
Project Management Software: Create timelines and track progress with tools like Trello.
-
Financial Software: For detailed financial projections, use QuickBooks or specialized financial modeling tools.
-
Research Databases: Access academic and industry data from online libraries and databases.
-
GIS Software: Analyze spatial data and site selection with tools like ArcGIS.
-
Risk Management Tools: Identify and manage project risks using tools like RiskWatch.
-
Business Plan Software: Structure your findings into a business plan with tools like LivePlan.
-
Presentation Tools: Communicate study results visually with software like PowerPoint.
-
Collaboration Tools: Facilitate teamwork with platforms like Microsoft Teams or Slack.
-
Document Management Systems: Organize and store project documents using software like SharePoint.
-
Decision Support Tools: Enhance decision-making with software like DecisionTools Suite for scenario analysis.
Examples of a Feasibility Study
Feasibility studies are conducted in various industries and for diverse purposes. Here are some examples of feasibility studies:
-
Real Estate Development: Before embarking on a real estate project, such as constructing a residential or commercial building, a feasibility study is conducted. It assesses the market demand for the property, construction costs, potential revenue from rentals or sales, and factors like zoning regulations and environmental impact.
-
Product Launch: When a company plans to launch a new product, a feasibility study is conducted to determine if there's a market for it. It includes market research to gauge customer interest, pricing strategies, manufacturing or production costs, and potential profitability.
-
Restaurant Opening: Before opening a new restaurant, a feasibility study is conducted to assess factors like location, target market, competition, menu pricing, and operating costs. It helps in understanding whether the restaurant can be profitable in a specific area.
-
Technology Start-up: Tech entrepreneurs often conduct feasibility studies to evaluate the viability of their software or app ideas. This includes assessing market demand, development costs, potential revenue streams, and competition in the tech sector.
-
Infrastructure Projects: Large-scale infrastructure projects like bridges, highways, or public transportation systems require feasibility studies to assess technical, financial, and environmental factors. These studies help determine if the project is practical and cost-effective.
-
Hotel Expansion: When a hotel chain plans to expand by building a new location, a feasibility study examines the market conditions, demand for hotel rooms in the area, construction and operational costs, and the potential return on investment.
-
Agricultural Ventures: Farmers and agricultural entrepreneurs may conduct feasibility studies before starting a new crop or livestock farming operation. The study evaluates factors like soil quality, market demand for the products, input costs, and expected yields.
-
Renewable Energy Projects: Feasibility studies are essential for renewable energy projects like wind farms or solar power plants. They assess factors such as available resources, technology feasibility, regulatory requirements, and financial viability.
-
Healthcare Facilities: Hospitals and healthcare organizations may conduct feasibility studies when planning to build new medical facilities. These studies analyze factors such as patient demand, location suitability, construction costs, and long-term operational expenses.
-
Manufacturing Plants: Before setting up a new manufacturing plant, businesses conduct feasibility studies to determine the feasibility of production, supply chain logistics, labor costs, and market demand for the products.
-
Educational Institutions: Feasibility studies are used by educational institutions to assess whether it's viable to expand or build new facilities, launch new academic programs, or enter new markets. These studies consider factors like enrollment projections, budget requirements, and competitive landscape.
-
Tourism and Hospitality: In the tourism sector, feasibility studies are conducted to evaluate the potential of opening new resorts, amusement parks, or tourist attractions. These studies analyze market demand, location, infrastructure requirements, and investment costs.
These are just a few examples of feasibility studies in different domains. The specific elements and focus of a feasibility study can vary widely depending on the nature of the project or business venture.
What is the Purpose of a Feasibility Study?
The primary purpose of a feasibility study is to comprehensively evaluate the viability and potential success of a proposed project or business endeavor. This study serves as a crucial decision-making tool, enabling stakeholders to assess the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study helps mitigate risks and develop effective strategies for success. It aligns the project with an organization's strategic goals, facilitates resource allocation, and ensures that resources are directed toward projects with a high likelihood of achieving positive returns on investment. Additionally, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes.
How Do You Write a Feasibility Study?
Writing a feasibility study involves a structured and systematic approach to assessing the viability of a proposed project or business venture. Here's a step-by-step guide on how to write a feasibility study:
-
Project Introduction:
-
Begin with an introduction that provides context for the study. Explain the purpose of the study, the project's objectives, and its significance.
-
Executive Summary:
-
Create an executive summary that offers a concise overview of the entire feasibility study, summarizing key findings, recommendations, and conclusions. This section should be clear and compelling as it's often the first part decision-makers read.
-
Background Information:
-
Provide background information on the project, including its history, the problem it aims to address, and any relevant historical data or context.
-
Scope of Work:
-
Clearly define the scope of the feasibility study. Specify the boundaries and limitations of the study, including what will and will not be included.
-
Methodology:
-
Explain the research methods and tools used to collect and analyze data. This section should outline the approach to market research, financial analysis, risk assessment, and other key aspects of the study.
-
Market Analysis:
-
Evaluate the market feasibility of the project by examining factors such as market size, growth potential, target demographics, competition, and customer demand. Present relevant market research data and trends.
-
Technical Analysis:
-
Assess the technical feasibility of the project, focusing on the required technology, equipment, and infrastructure. Address potential technical challenges and outline solutions.
-
Financial Analysis:
-
Conduct a detailed financial analysis, including cost estimations, revenue projections, cash flow analysis, and return on investment (ROI) calculations. Evaluate the project's financial viability.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Assessment:
-
Examine legal and regulatory requirements relevant to the project. Identify permits, licenses, compliance issues, and strategies for ensuring legal conformity.
-
Environmental and Social Impact Assessment:
-
Assess the potential environmental and social impacts of the project, including sustainability considerations and community acceptance.
-
Risk Analysis:
-
Identify and evaluate potential risks and uncertainties associated with the project. Develop risk mitigation strategies and present them in this section.
-
Alternative Solutions:
-
Explore alternative approaches or solutions to achieve the project's objectives. Compare different options and provide a rationale for the chosen approach.
-
Recommendations:
-
Based on the analysis conducted throughout the study, present clear and well-supported recommendations regarding whether to proceed with the project, modify its scope, or abandon it. Provide a summary of the key findings that support the recommendations.
-
Appendices:
-
Include supplementary information in the appendices, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the study's findings.
-
References:
-
If the study includes external sources or references, provide a list of these sources in a reference section.
-
Conclusion:
-
Conclude the feasibility study by summarizing the main findings, highlighting the recommended course of action, and reiterating the importance of the study's conclusions.
-
Final Review:
-
Before finalizing the report, conduct a thorough review for accuracy, clarity, and coherence. Ensure that the report is well-organized and follows a logical flow.
7 Steps to Do a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
How to Conduct a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
Feasibility Study vs. Business Plan
Feasibility Study vs. Business Plan:
Feasibility Study:
-
Purpose: The primary purpose of a feasibility study is to assess the viability and feasibility of a proposed project or business idea. It aims to answer the question, "Is this project or business concept feasible?"
-
Timing: Feasibility studies are typically conducted in the early stages of project development, often before significant resources are invested.
-
Scope: Feasibility studies have a broader scope and focus on evaluating various aspects of the project, including market feasibility, technical feasibility, financial feasibility, legal and regulatory considerations, operational feasibility, and risk assessment.
-
Analysis: Feasibility studies involve in-depth analysis of data and information related to the project, such as market research, cost estimation, revenue projections, and risk assessment.
-
Outcome: The primary outcome of a feasibility study is to provide stakeholders with a recommendation on whether to proceed with the project, modify its scope, or abandon it. It helps stakeholders make informed decisions.
Business Plan:
-
Purpose: A business plan serves as a detailed blueprint for the actual operation and management of a business. It outlines the goals, strategies, and operations of the business and provides a roadmap for its growth and development.
-
Timing: Business plans are typically developed after the feasibility study, once the decision to proceed with the project has been made. They are often used when seeking financing or as a guide for day-to-day operations.
-
Scope: Business plans focus on the specific strategies, tactics, and operations required to run the business successfully. They include detailed information on marketing, sales, organizational structure, funding requirements, revenue and expense projections, and long-term goals.
-
Analysis: While business plans incorporate the findings from the feasibility study, they go beyond feasibility analysis and delve into the practical aspects of running the business. Business plans include detailed financial projections and operational plans.
-
Outcome: The primary outcome of a business plan is to provide a comprehensive and actionable roadmap for the business. It is used for securing financing, attracting investors, guiding day-to-day operations, and measuring the business's performance against its objectives.
In summary, a feasibility study assesses the initial viability of a project or business idea and informs the decision to proceed or not, while a business plan is a detailed document that outlines how a business will operate, grow, and achieve its goals once the decision to move forward has been made. Both documents are crucial in the lifecycle of a business or project, with the feasibility study informing the business plan's foundation.
Reasons to Do or Not to Do a Feasibility Study
Reasons to Do a Feasibility Study:
-
Risk Assessment: A feasibility study helps identify potential risks and challenges associated with the project. It provides an opportunity to assess and mitigate these risks proactively.
-
Informed Decision-Making: Conducting a feasibility study ensures that decision-makers have comprehensive information to make informed choices about whether to proceed with the project, make modifications, or abandon it.
-
Financial Clarity: Financial feasibility studies estimate costs, revenue projections, and potential profitability. This clarity ensures that the project aligns with budget constraints and has a potential for positive returns on investment.
-
Resource Optimization: Feasibility studies outline the resources required for the project, such as personnel, equipment, materials, and technology. This allows for efficient resource allocation and prevents delays or resource shortages.
-
Strategic Alignment: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses this alignment, ensuring that the project supports the organization's overarching strategy.
Reasons Not to Do a Feasibility Study:
-
Low Complexity: For very simple projects with minimal investment and known market demand, a full-scale feasibility study may be unnecessary. However, even small projects can benefit from some form of preliminary assessment.
-
Urgency: In cases where time is of the essence, such as responding to rapidly changing market conditions, conducting a lengthy feasibility study may not be feasible. In such situations, a rapid assessment or a simpler analysis may be more appropriate.
-
Cost Concerns: Some organizations may be hesitant to invest in a feasibility study due to budget constraints. However, failing to conduct a feasibility study can lead to much higher costs if the project encounters unforeseen issues.
-
Obvious Viability: In rare cases where the viability of a project is self-evident and unquestionable, skipping a feasibility study might be considered. However, a cursory assessment is still advisable to confirm assumptions.
Conclusion
In conclusion, a feasibility study is an indispensable tool in the process of evaluating the potential success and viability of a proposed project or business venture. It serves as a critical decision-making guide, providing stakeholders with a comprehensive understanding of the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study enables proactive risk mitigation and the development of effective strategies for success. It aligns the project with an organization's strategic objectives, facilitates resource allocation, and ensures that resources are directed toward endeavors with a high likelihood of achieving positive returns. Furthermore, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes. In essence, a well-executed feasibility study lays the foundation for a project's success and serves as a cornerstone for prudent decision-making in the world of business and project management.
FAQs
1. What is a feasibility study?
A feasibility study is an in-depth analysis and evaluation of a proposed project or business venture to determine its viability and potential for success. It assesses various aspects such as market feasibility, technical feasibility, financial feasibility, and operational feasibility.
2. Why is a feasibility study important?
A feasibility study is crucial because it helps stakeholders make informed decisions about whether to proceed with a project, modify its scope, or abandon it. It identifies risks, assesses costs, and evaluates the potential for profitability, thereby reducing uncertainty and minimizing the likelihood of project failure.
3. What are the key components of a feasibility study?
A feasibility study typically includes sections on market analysis, technical analysis, financial analysis, operational analysis, legal and regulatory considerations, environmental and social impact assessment, risk analysis, and recommendations.
4. How is a feasibility study different from a business plan?
A feasibility study assesses the initial viability of a project, while a business plan provides a detailed roadmap for running and growing a business after the decision to proceed has been made. Feasibility studies inform the foundation of a business plan.
5. When should you conduct a feasibility study?
Feasibility studies are typically conducted in the early stages of project development, before significant resources are invested. However, they can also be conducted at any point when there is uncertainty about the feasibility of a project.
6. What is the role of market research in a feasibility study?
Market research is a crucial component of a feasibility study as it assesses market demand, competition, customer preferences, and trends. It helps determine if there is a market for the project's products or services.
7. How do you assess financial feasibility in a feasibility study?
Financial feasibility is assessed by estimating project costs, revenue projections, cash flow analysis, and calculating metrics like return on investment (ROI) and payback period. It determines if the project is financially viable.
8. What are the benefits of conducting a feasibility study?
Benefits of a feasibility study include risk mitigation, informed decision-making, financial clarity, efficient resource allocation, strategic alignment, stakeholder buy-in, and the identification of potential issues early in the project.
9. Are there situations where a feasibility study may not be necessary?
In some cases, for very simple projects with minimal investment and known market demand, a full-scale feasibility study may be considered unnecessary. However, even small projects can benefit from a preliminary assessment.
10. How do you present the findings of a feasibility study to stakeholders? -
The findings of a feasibility study are typically presented in a structured report format, with clear sections covering each aspect of the study. An executive summary is often included to provide a concise overview of the key findings and recommendations. Presentations and discussions with stakeholders may also be part of the communication process.
Read More
In the dynamic landscape of project management and business endeavors, the path to success is often paved with uncertainty. For every visionary project or entrepreneurial venture, there exists an inherent risk that can lead to unforeseen challenges, setbacks, or even failure. In this complex terrain, the beacon of clarity and guidance comes in the form of a "Feasibility Study." It is the compass that not only points to the direction of project viability but also illuminates the obstacles that lie ahead. This journey into the realm of feasibility studies unveils their pivotal role in project management, where informed decisions, meticulous analysis, and calculated risk mitigation converge to shape the destiny of projects and businesses. Join us as we delve into the significance of feasibility studies, understanding their multifaceted importance in steering the course of success.
Table of Contents
What is a Feasibility Study?
Understanding A Feasibility Study
Types of Feasibility Study
Importance of Feasibility Study
Benefits of a Feasibility Study
What Is Included in a Feasibility Study Report?
Tools for Conducting a Feasibility Study
Examples of a Feasibility Study
What is the Purpose of a Feasibility Study?
How Do You Write a Feasibility Study?
7 Steps to Do a Feasibility Study
How to Conduct a Feasibility Study
Feasibility Study vs. Business Plan
Reasons to Do or Not to Do a Feasibility Study
Conclusion
FAQs
What is a Feasibility Study?
A feasibility study is a thorough examination of whether a proposed project or business idea is practical and likely to succeed. It involves analyzing factors like market demand, technical capabilities, financial viability, operational logistics, legal requirements, environmental impact, and potential risks. The study helps decision-makers determine whether it's worth pursuing the project or if adjustments are needed. Ultimately, it provides a clear recommendation on whether to go ahead with the project or not, based on a comprehensive assessment of all relevant factors.
Understanding A Feasibility Study
A feasibility study is a comprehensive analysis conducted during the early stages of project planning to determine the practicality and viability of a proposed project or business endeavor. It involves assessing various factors such as market demand, technical feasibility, financial considerations, operational logistics, legal and regulatory requirements, environmental impacts, and potential risks. The goal is to answer the fundamental question of whether the project is feasible and worth pursuing. A well-executed feasibility study provides decision-makers with valuable insights to make informed choices about whether to invest resources, time, and effort into the project or explore alternative options. Ultimately, it helps prevent costly mistakes by identifying potential challenges and opportunities early in the project's development.
Types of Feasibility Study
-
Market Feasibility Study: This type of study is essential when considering a new product or service. It assesses whether there is enough demand in the market for the proposed offering. Market feasibility examines factors such as target demographics, customer preferences, market trends, competition, and potential market size. The goal is to determine if there is a substantial and sustainable market for the product or service.
-
Technical Feasibility Study: When a project relies on specific technology or technical processes, a technical feasibility study is conducted. It evaluates whether the required technology and expertise are available or can be developed within the project's scope. This study also looks at potential technical challenges and obstacles that might hinder project implementation.
-
Financial Feasibility Study: Financial feasibility is crucial to assess the project's profitability and financial viability. It involves estimating all costs associated with the project, including initial investments, operating expenses, and maintenance costs. Revenue projections and cash flow analysis are also conducted to determine if the project can generate a positive return on investment (ROI).
-
Operational Feasibility Study: This study focuses on how the proposed project will operate in practical terms. It assesses whether the project can be effectively integrated into existing operations or if it requires significant changes to processes, staffing, and logistics. Operational feasibility helps ensure that the project can be executed smoothly and efficiently.
-
Legal and Regulatory Feasibility Study: Projects often need to navigate complex legal and regulatory landscapes. A legal and regulatory feasibility study examines whether the project complies with all relevant laws, regulations, permits, and industry-specific requirements. It identifies potential legal obstacles and outlines the steps necessary for legal and regulatory compliance.
Importance of Feasibility Study
The importance of a feasibility study in the context of project management and business decision-making cannot be overstated. Here are several key reasons why conducting a feasibility study is crucial:
-
Risk Identification and Mitigation: A feasibility study helps identify potential risks and challenges associated with a project. By recognizing these risks early, project managers and stakeholders can develop strategies to mitigate them effectively. This proactive approach minimizes the likelihood of unforeseen issues derailing the project later on.
-
Cost-Benefit Analysis: One of the primary purposes of a feasibility study is to assess the financial feasibility of a project. It involves estimating the costs of implementing the project and comparing them to the expected benefits. This analysis helps in determining whether the project will yield a positive return on investment (ROI). If the costs outweigh the benefits, it may not be financially viable.
-
Resource Allocation: Resource allocation is a critical aspect of project management. A feasibility study outlines the resources required for the project, including manpower, equipment, and materials. This information allows project managers to allocate resources efficiently and ensure that they are available when needed, reducing delays and cost overruns.
-
Alignment with Strategic Goals: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses how the proposed project aligns with these strategic goals. If there is a mismatch, it provides an opportunity to refine the project's scope or reconsider its importance in the context of the organization's overarching strategy.
-
Stakeholder Buy-In: Feasibility studies involve engaging with key stakeholders, including sponsors, investors, and end-users. These stakeholders play a crucial role in the success of the project. The study helps in gaining their buy-in and support by providing them with a clear understanding of the project's goals, benefits, and potential risks.
-
Decision-Making Tool: A feasibility study serves as a decision-making tool for project sponsors and stakeholders. It provides them with the information needed to make an informed decision about whether to proceed with the project, revise its scope, or abandon it altogether. This ensures that resources are allocated to projects with a higher likelihood of success.
-
Project Viability Assessment: Feasibility studies assess the overall viability of a project. They consider various aspects, including market demand, technical feasibility, financial considerations, and operational logistics. This comprehensive evaluation helps in determining whether the project is worth pursuing and has a realistic chance of success.
-
Cost Control: By estimating project costs and potential cost overruns during the feasibility study, project managers can develop effective cost control measures. This proactive approach allows for better financial management throughout the project's lifecycle.
-
Time Efficiency: A feasibility study helps in setting realistic project timelines. By identifying potential delays and obstacles early on, project managers can plan and allocate resources more effectively, reducing the likelihood of project schedule disruptions.
-
Alternative Evaluation: Feasibility studies often explore alternative solutions or approaches to achieve project objectives. This allows decision-makers to compare different options and select the most feasible and cost-effective one.
In conclusion, a well-conducted feasibility study is an indispensable tool in project management and business decision-making. It provides a structured and systematic approach to assess a project's feasibility, risks, costs, and benefits, ultimately leading to more informed and successful project outcomes.
Benefits of a Feasibility Study
A feasibility study offers a multitude of benefits that are invaluable to organizations and stakeholders contemplating new projects or business ventures. Firstly, it serves as a risk mitigation tool by uncovering potential challenges and obstacles early in the project's conceptualization phase, enabling the development of strategies to address these concerns proactively. Furthermore, a well-executed feasibility study empowers decision-makers with comprehensive information and data, facilitating informed choices regarding whether to proceed with the project, modify its scope, or abandon it altogether. Financial feasibility studies, a key component, provide financial clarity by estimating costs, revenue projections, and profitability prospects, ensuring alignment with budget constraints. Resource allocation becomes more efficient, as the study identifies the resources needed and helps prevent delays or shortages. Additionally, it ensures that the project aligns with an organization's strategic goals, fosters stakeholder buy-in, and assesses environmental and social responsibility. In essence, a feasibility study is an essential compass guiding project success by minimizing risks, optimizing resources, and ensuring strategic alignment.
What Is Included in a Feasibility Study Report?
A comprehensive feasibility study report typically includes the following key sections and information:
-
Executive Summary: This section provides a concise overview of the entire feasibility study, summarizing its main findings and recommendations. It is often the first section decision-makers read, so it should effectively convey the project's viability and key takeaways.
-
Introduction: The introduction sets the stage for the study by explaining the purpose, scope, and objectives of the feasibility study. It also introduces the project or business idea being evaluated.
-
Project Description: This section provides a detailed description of the proposed project, including its goals, objectives, and scope. It outlines what the project aims to achieve and its intended outcomes.
-
Market Analysis: In this section, the study delves into the market feasibility, examining factors such as market size, growth potential, target demographics, competition, and customer demand. It also assesses market trends and dynamics.
-
Technical Analysis: The technical analysis evaluates the technical feasibility of the project. It considers the technology, equipment, and infrastructure required, as well as potential technical challenges and solutions. It may also include information on suppliers and technology partners.
-
Financial Analysis: The financial analysis is a critical component. It includes detailed financial projections, cost estimates, revenue forecasts, and cash flow analysis. It assesses the project's financial feasibility, including its return on investment (ROI) and payback period.
-
Operational Analysis: This section focuses on the operational feasibility of the project. It looks at how the project will function in practical terms, including staffing requirements, processes, logistics, and supply chain considerations.
-
Legal and Regulatory Considerations: Here, the study addresses legal and regulatory feasibility by identifying the legal requirements, permits, licenses, and compliance issues relevant to the project. It also outlines strategies for ensuring compliance.
-
Environmental and Social Impact Assessment: This section assesses the potential environmental and social impacts of the project, including its sustainability, community acceptance, and corporate social responsibility considerations.
-
Risk Analysis: The risk analysis identifies potential risks and uncertainties associated with the project and provides recommendations for risk mitigation. It may include a risk matrix or assessment of key risks.
-
Alternative Solutions: Feasibility studies often explore alternative approaches or solutions to achieve the project's objectives. This section compares different options and provides rationale for the chosen approach.
-
Recommendations: Based on the analysis conducted throughout the study, this section presents clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. It outlines the rationale for the recommended course of action.
-
Appendices: The appendices contain supplementary information, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the findings and conclusions of the feasibility study.
-
References: If the study includes external sources or references, a list of these sources should be provided in a reference section.
A well-structured feasibility study report serves as a comprehensive document that guides decision-makers in assessing the viability of a project or business venture. It should be clear, well-organized, and supported by data and analysis to ensure that stakeholders have the information needed to make informed decisions.
Tools for Conducting a Feasibility Study
-
Microsoft Excel: Use it for financial calculations and modeling.
-
Survey Software: Collect market data through tools like SurveyMonkey or Google Forms.
-
Market Research Tools: Access industry reports and trends with tools like Statista.
-
Project Management Software: Create timelines and track progress with tools like Trello.
-
Financial Software: For detailed financial projections, use QuickBooks or specialized financial modeling tools.
-
Research Databases: Access academic and industry data from online libraries and databases.
-
GIS Software: Analyze spatial data and site selection with tools like ArcGIS.
-
Risk Management Tools: Identify and manage project risks using tools like RiskWatch.
-
Business Plan Software: Structure your findings into a business plan with tools like LivePlan.
-
Presentation Tools: Communicate study results visually with software like PowerPoint.
-
Collaboration Tools: Facilitate teamwork with platforms like Microsoft Teams or Slack.
-
Document Management Systems: Organize and store project documents using software like SharePoint.
-
Decision Support Tools: Enhance decision-making with software like DecisionTools Suite for scenario analysis.
Examples of a Feasibility Study
Feasibility studies are conducted in various industries and for diverse purposes. Here are some examples of feasibility studies:
-
Real Estate Development: Before embarking on a real estate project, such as constructing a residential or commercial building, a feasibility study is conducted. It assesses the market demand for the property, construction costs, potential revenue from rentals or sales, and factors like zoning regulations and environmental impact.
-
Product Launch: When a company plans to launch a new product, a feasibility study is conducted to determine if there's a market for it. It includes market research to gauge customer interest, pricing strategies, manufacturing or production costs, and potential profitability.
-
Restaurant Opening: Before opening a new restaurant, a feasibility study is conducted to assess factors like location, target market, competition, menu pricing, and operating costs. It helps in understanding whether the restaurant can be profitable in a specific area.
-
Technology Start-up: Tech entrepreneurs often conduct feasibility studies to evaluate the viability of their software or app ideas. This includes assessing market demand, development costs, potential revenue streams, and competition in the tech sector.
-
Infrastructure Projects: Large-scale infrastructure projects like bridges, highways, or public transportation systems require feasibility studies to assess technical, financial, and environmental factors. These studies help determine if the project is practical and cost-effective.
-
Hotel Expansion: When a hotel chain plans to expand by building a new location, a feasibility study examines the market conditions, demand for hotel rooms in the area, construction and operational costs, and the potential return on investment.
-
Agricultural Ventures: Farmers and agricultural entrepreneurs may conduct feasibility studies before starting a new crop or livestock farming operation. The study evaluates factors like soil quality, market demand for the products, input costs, and expected yields.
-
Renewable Energy Projects: Feasibility studies are essential for renewable energy projects like wind farms or solar power plants. They assess factors such as available resources, technology feasibility, regulatory requirements, and financial viability.
-
Healthcare Facilities: Hospitals and healthcare organizations may conduct feasibility studies when planning to build new medical facilities. These studies analyze factors such as patient demand, location suitability, construction costs, and long-term operational expenses.
-
Manufacturing Plants: Before setting up a new manufacturing plant, businesses conduct feasibility studies to determine the feasibility of production, supply chain logistics, labor costs, and market demand for the products.
-
Educational Institutions: Feasibility studies are used by educational institutions to assess whether it's viable to expand or build new facilities, launch new academic programs, or enter new markets. These studies consider factors like enrollment projections, budget requirements, and competitive landscape.
-
Tourism and Hospitality: In the tourism sector, feasibility studies are conducted to evaluate the potential of opening new resorts, amusement parks, or tourist attractions. These studies analyze market demand, location, infrastructure requirements, and investment costs.
These are just a few examples of feasibility studies in different domains. The specific elements and focus of a feasibility study can vary widely depending on the nature of the project or business venture.
What is the Purpose of a Feasibility Study?
The primary purpose of a feasibility study is to comprehensively evaluate the viability and potential success of a proposed project or business endeavor. This study serves as a crucial decision-making tool, enabling stakeholders to assess the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study helps mitigate risks and develop effective strategies for success. It aligns the project with an organization's strategic goals, facilitates resource allocation, and ensures that resources are directed toward projects with a high likelihood of achieving positive returns on investment. Additionally, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes.
How Do You Write a Feasibility Study?
Writing a feasibility study involves a structured and systematic approach to assessing the viability of a proposed project or business venture. Here's a step-by-step guide on how to write a feasibility study:
-
Project Introduction:
-
Begin with an introduction that provides context for the study. Explain the purpose of the study, the project's objectives, and its significance.
-
-
Executive Summary:
-
Create an executive summary that offers a concise overview of the entire feasibility study, summarizing key findings, recommendations, and conclusions. This section should be clear and compelling as it's often the first part decision-makers read.
-
-
Background Information:
-
Provide background information on the project, including its history, the problem it aims to address, and any relevant historical data or context.
-
-
Scope of Work:
-
Clearly define the scope of the feasibility study. Specify the boundaries and limitations of the study, including what will and will not be included.
-
-
Methodology:
-
Explain the research methods and tools used to collect and analyze data. This section should outline the approach to market research, financial analysis, risk assessment, and other key aspects of the study.
-
-
Market Analysis:
-
Evaluate the market feasibility of the project by examining factors such as market size, growth potential, target demographics, competition, and customer demand. Present relevant market research data and trends.
-
-
Technical Analysis:
-
Assess the technical feasibility of the project, focusing on the required technology, equipment, and infrastructure. Address potential technical challenges and outline solutions.
-
-
Financial Analysis:
-
Conduct a detailed financial analysis, including cost estimations, revenue projections, cash flow analysis, and return on investment (ROI) calculations. Evaluate the project's financial viability.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing requirements, processes, logistics, and supply chain considerations.
-
-
Legal and Regulatory Assessment:
-
Examine legal and regulatory requirements relevant to the project. Identify permits, licenses, compliance issues, and strategies for ensuring legal conformity.
-
-
Environmental and Social Impact Assessment:
-
Assess the potential environmental and social impacts of the project, including sustainability considerations and community acceptance.
-
-
Risk Analysis:
-
Identify and evaluate potential risks and uncertainties associated with the project. Develop risk mitigation strategies and present them in this section.
-
-
Alternative Solutions:
-
Explore alternative approaches or solutions to achieve the project's objectives. Compare different options and provide a rationale for the chosen approach.
-
-
Recommendations:
-
Based on the analysis conducted throughout the study, present clear and well-supported recommendations regarding whether to proceed with the project, modify its scope, or abandon it. Provide a summary of the key findings that support the recommendations.
-
-
Appendices:
-
Include supplementary information in the appendices, such as detailed financial spreadsheets, market research data, technical specifications, and any other relevant documents that support the study's findings.
-
-
References:
-
If the study includes external sources or references, provide a list of these sources in a reference section.
-
-
Conclusion:
-
Conclude the feasibility study by summarizing the main findings, highlighting the recommended course of action, and reiterating the importance of the study's conclusions.
-
-
Final Review:
-
Before finalizing the report, conduct a thorough review for accuracy, clarity, and coherence. Ensure that the report is well-organized and follows a logical flow.
-
7 Steps to Do a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
-
How to Conduct a Feasibility Study
Performing a feasibility study involves a systematic process to assess the viability of a project or business idea. Here are seven essential steps to conduct a feasibility study:
-
Define the Project Scope and Objectives:
-
Clearly outline the purpose, goals, and objectives of the feasibility study. Determine the specific questions the study should answer and the key aspects to be evaluated.
-
-
Gather Information and Data:
-
Collect all relevant data and information needed for the study. This includes market research, technical specifications, financial data, legal and regulatory requirements, and any other pertinent details.
-
-
Market Research and Analysis:
-
Evaluate the market feasibility by researching and analyzing factors like market size, growth trends, competition, customer preferences, and demand for the product or service.
-
-
Technical Analysis:
-
Assess the technical feasibility by examining the required technology, equipment, and infrastructure. Identify potential technical challenges and determine if they can be overcome.
-
-
Financial Analysis:
-
Conduct a comprehensive financial analysis, including cost estimations, revenue projections, cash flow analysis, and ROI calculations. Determine if the project is financially viable and can yield positive returns.
-
-
Operational Analysis:
-
Evaluate the operational feasibility of the project by analyzing how it will function in practical terms. Consider staffing needs, processes, logistics, and supply chain requirements.
-
-
Risk Assessment and Recommendations:
-
Identify and assess potential risks and uncertainties associated with the project. Develop strategies for risk mitigation. Based on the analysis, make clear and well-supported recommendations regarding whether to proceed with the project, make modifications, or abandon it. Summarize key findings and provide a concise roadmap for decision-makers.
-
Feasibility Study vs. Business Plan
Feasibility Study vs. Business Plan:
Feasibility Study:
-
Purpose: The primary purpose of a feasibility study is to assess the viability and feasibility of a proposed project or business idea. It aims to answer the question, "Is this project or business concept feasible?"
-
Timing: Feasibility studies are typically conducted in the early stages of project development, often before significant resources are invested.
-
Scope: Feasibility studies have a broader scope and focus on evaluating various aspects of the project, including market feasibility, technical feasibility, financial feasibility, legal and regulatory considerations, operational feasibility, and risk assessment.
-
Analysis: Feasibility studies involve in-depth analysis of data and information related to the project, such as market research, cost estimation, revenue projections, and risk assessment.
-
Outcome: The primary outcome of a feasibility study is to provide stakeholders with a recommendation on whether to proceed with the project, modify its scope, or abandon it. It helps stakeholders make informed decisions.
Business Plan:
-
Purpose: A business plan serves as a detailed blueprint for the actual operation and management of a business. It outlines the goals, strategies, and operations of the business and provides a roadmap for its growth and development.
-
Timing: Business plans are typically developed after the feasibility study, once the decision to proceed with the project has been made. They are often used when seeking financing or as a guide for day-to-day operations.
-
Scope: Business plans focus on the specific strategies, tactics, and operations required to run the business successfully. They include detailed information on marketing, sales, organizational structure, funding requirements, revenue and expense projections, and long-term goals.
-
Analysis: While business plans incorporate the findings from the feasibility study, they go beyond feasibility analysis and delve into the practical aspects of running the business. Business plans include detailed financial projections and operational plans.
-
Outcome: The primary outcome of a business plan is to provide a comprehensive and actionable roadmap for the business. It is used for securing financing, attracting investors, guiding day-to-day operations, and measuring the business's performance against its objectives.
In summary, a feasibility study assesses the initial viability of a project or business idea and informs the decision to proceed or not, while a business plan is a detailed document that outlines how a business will operate, grow, and achieve its goals once the decision to move forward has been made. Both documents are crucial in the lifecycle of a business or project, with the feasibility study informing the business plan's foundation.
Reasons to Do or Not to Do a Feasibility Study
Reasons to Do a Feasibility Study:
-
Risk Assessment: A feasibility study helps identify potential risks and challenges associated with the project. It provides an opportunity to assess and mitigate these risks proactively.
-
Informed Decision-Making: Conducting a feasibility study ensures that decision-makers have comprehensive information to make informed choices about whether to proceed with the project, make modifications, or abandon it.
-
Financial Clarity: Financial feasibility studies estimate costs, revenue projections, and potential profitability. This clarity ensures that the project aligns with budget constraints and has a potential for positive returns on investment.
-
Resource Optimization: Feasibility studies outline the resources required for the project, such as personnel, equipment, materials, and technology. This allows for efficient resource allocation and prevents delays or resource shortages.
-
Strategic Alignment: Projects should align with an organization's strategic goals and objectives. A feasibility study assesses this alignment, ensuring that the project supports the organization's overarching strategy.
Reasons Not to Do a Feasibility Study:
-
Low Complexity: For very simple projects with minimal investment and known market demand, a full-scale feasibility study may be unnecessary. However, even small projects can benefit from some form of preliminary assessment.
-
Urgency: In cases where time is of the essence, such as responding to rapidly changing market conditions, conducting a lengthy feasibility study may not be feasible. In such situations, a rapid assessment or a simpler analysis may be more appropriate.
-
Cost Concerns: Some organizations may be hesitant to invest in a feasibility study due to budget constraints. However, failing to conduct a feasibility study can lead to much higher costs if the project encounters unforeseen issues.
-
Obvious Viability: In rare cases where the viability of a project is self-evident and unquestionable, skipping a feasibility study might be considered. However, a cursory assessment is still advisable to confirm assumptions.
Conclusion
In conclusion, a feasibility study is an indispensable tool in the process of evaluating the potential success and viability of a proposed project or business venture. It serves as a critical decision-making guide, providing stakeholders with a comprehensive understanding of the project's feasibility, risks, and financial viability. By identifying potential challenges and opportunities early on, a feasibility study enables proactive risk mitigation and the development of effective strategies for success. It aligns the project with an organization's strategic objectives, facilitates resource allocation, and ensures that resources are directed toward endeavors with a high likelihood of achieving positive returns. Furthermore, it fosters stakeholder buy-in and provides a clear roadmap for project execution. Ultimately, the overarching goal of a feasibility study is to inform well-informed decisions about whether to pursue, modify, or abandon the project, thereby promoting efficiency, cost-effectiveness, and the likelihood of successful outcomes. In essence, a well-executed feasibility study lays the foundation for a project's success and serves as a cornerstone for prudent decision-making in the world of business and project management.
FAQs
1. What is a feasibility study?
A feasibility study is an in-depth analysis and evaluation of a proposed project or business venture to determine its viability and potential for success. It assesses various aspects such as market feasibility, technical feasibility, financial feasibility, and operational feasibility.
2. Why is a feasibility study important?
A feasibility study is crucial because it helps stakeholders make informed decisions about whether to proceed with a project, modify its scope, or abandon it. It identifies risks, assesses costs, and evaluates the potential for profitability, thereby reducing uncertainty and minimizing the likelihood of project failure.
3. What are the key components of a feasibility study?
A feasibility study typically includes sections on market analysis, technical analysis, financial analysis, operational analysis, legal and regulatory considerations, environmental and social impact assessment, risk analysis, and recommendations.
4. How is a feasibility study different from a business plan?
A feasibility study assesses the initial viability of a project, while a business plan provides a detailed roadmap for running and growing a business after the decision to proceed has been made. Feasibility studies inform the foundation of a business plan.
5. When should you conduct a feasibility study?
Feasibility studies are typically conducted in the early stages of project development, before significant resources are invested. However, they can also be conducted at any point when there is uncertainty about the feasibility of a project.
6. What is the role of market research in a feasibility study?
Market research is a crucial component of a feasibility study as it assesses market demand, competition, customer preferences, and trends. It helps determine if there is a market for the project's products or services.
7. How do you assess financial feasibility in a feasibility study?
Financial feasibility is assessed by estimating project costs, revenue projections, cash flow analysis, and calculating metrics like return on investment (ROI) and payback period. It determines if the project is financially viable.
8. What are the benefits of conducting a feasibility study?
Benefits of a feasibility study include risk mitigation, informed decision-making, financial clarity, efficient resource allocation, strategic alignment, stakeholder buy-in, and the identification of potential issues early in the project.
9. Are there situations where a feasibility study may not be necessary?
In some cases, for very simple projects with minimal investment and known market demand, a full-scale feasibility study may be considered unnecessary. However, even small projects can benefit from a preliminary assessment.
10. How do you present the findings of a feasibility study to stakeholders? -
The findings of a feasibility study are typically presented in a structured report format, with clear sections covering each aspect of the study. An executive summary is often included to provide a concise overview of the key findings and recommendations. Presentations and discussions with stakeholders may also be part of the communication process.
A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?
Welcome to "A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?" In this comprehensive exploration, we demystify ITIL, the Information Technology Infrastructure Library, offering you a compass to navigate the intricate realm of IT Service Management (ITSM). Discover the core concepts of ITIL, unravel its summary processes, and understand its pivotal role in optimizing IT service delivery, enhancing customer satisfaction, and reshaping modern business operations. Whether you're an IT professional, a business leader, or simply curious about ITIL's impact, this guide equips you with essential knowledge, transforming the way you perceive and implement IT service management practices, all within a single paragraph.
Table of Contents
What is ITIL?
What's in the ITIL?
Benefits of ITIL:
Drawbacks of ITIL:
What are the ITIL Concepts?
What are ITIL's Guiding Principles?
Key ITIL Terms
ITIL Framework
1. Service Strategy
2. Service Design
3. Service Transition
4. Service Operations
5. Continual Service Improvement (CSI)
How Do I Put ITIL into Practice?
What is ITIL Certification, and is it Worth it?
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
How Does ITIL Help Business?
What Will ITIL Cost?
How Does ITIL Reduce Costs?
ITIL Processes and Functions
History of ITIL
ITIL Processes and Stages: Summary
What is ITIL?
ITIL, or Information Technology Infrastructure Library, is a widely adopted framework for IT service management. It offers a structured approach to aligning IT services with business objectives and delivering high-quality services to customers. ITIL encompasses various phases, including service strategy, design, transition, operation, and continual service improvement. It provides best practices and guidelines to enhance the efficiency, reliability, and customer-centricity of IT processes and services, making it a valuable resource for organizations seeking to improve their IT operations.
What's in the ITIL?
ITIL consists of a structured framework for IT service management, including a service lifecycle with stages like Service Strategy, Design, Transition, Operation, and Continual Service Improvement. It defines processes, roles, and functions within IT organizations, guiding how services are designed, delivered, and improved. ITIL emphasizes aligning IT with business goals, offering best practices for incident and problem management, change control, and more. It also provides certification options for IT professionals to validate their expertise. Overall, ITIL offers a holistic approach to managing IT services effectively and efficiently.
Benefits of ITIL
Implementing ITIL (Information Technology Infrastructure Library) in an organization can bring several significant benefits, including:
-
Improved Service Quality: ITIL promotes best practices and standardized processes, leading to more consistent and reliable IT service delivery. This, in turn, enhances the overall quality of IT services, reducing downtime and customer dissatisfaction.
-
Better Alignment with Business Goals: ITIL encourages the alignment of IT services with the objectives and needs of the business. This ensures that IT investments and efforts contribute directly to the organization's success.
-
Cost Efficiency: By optimizing processes and resources, ITIL helps organizations reduce operational costs. Effective incident management, problem resolution, and resource allocation lead to cost savings.
-
Enhanced Customer Satisfaction: ITIL's customer-centric approach ensures that IT services are designed and delivered with the customer's experience in mind. Meeting or exceeding customer expectations leads to higher satisfaction levels.
-
Reduced Risk: ITIL's focus on change management and risk mitigation helps organizations minimize the potential for disruptions and security breaches during service transitions or changes.
Drawbacks of ITIL
While ITIL (Information Technology Infrastructure Library) offers many advantages, it also has some potential drawbacks and challenges:
-
Complexity: ITIL is a comprehensive framework with a multitude of processes, roles, and functions. Implementing the full framework can be complex and resource-intensive, especially for small organizations.
-
Cost: The implementation of ITIL may involve significant upfront costs, including training, software, and process redesign. These expenses can be a barrier for some organizations.
-
Resource Intensive: ITIL requires dedicated resources, including personnel, tools, and time for training and implementation. Smaller organizations may struggle to allocate these resources.
-
Resistance to Change: Employees may resist changes in processes and procedures that ITIL mandates, especially if they have been accustomed to their current ways of working. This can slow down adoption.
-
Overstandardization: In some cases, ITIL's emphasis on standardization can stifle innovation and adaptability. Organizations may become too rigid in their processes and struggle to respond to rapidly changing business needs.
What are the ITIL Concepts?
ITIL (Information Technology Infrastructure Library) encompasses several key concepts that form the foundation of its framework for IT service management. These concepts help organizations understand and implement effective IT service management practices. Here are the core ITIL concepts:
-
Service: ITIL views services as a means of delivering value to customers without the ownership of specific costs and risks.
-
Service Management: ITIL involves specialized organizational capabilities to deliver value through IT services, encompassing processes, functions, roles, and responsibilities.
-
Service Lifecycle: ITIL's framework revolves around five stages: Service Strategy, Design, Transition, Operation, and Continual Service Improvement.
-
Process: ITIL defines a set of processes, each with specific activities, inputs, outputs, and roles, essential for effective IT service management.
-
SLA and KPI: ITIL uses Service Level Agreements (SLAs) to define service quality and Key Performance Indicators (KPIs) to measure and monitor service performance and effectiveness.
What are ITIL's Guiding Principles?
Here are the seven simplified guiding principles of ITIL:
-
Value-Centric: Focus on delivering value to customers and the business.
-
Start Where You Are: Build on your existing processes and capabilities.
-
Feedback-Driven Progress: Continuously improve through feedback and small changes.
-
Collaborate and Communicate: Work together and share information for better results.
-
Think Holistically: Consider the big picture and interconnectedness of services.
-
Keep it Simple: Avoid complexity and prioritize practicality.
-
Optimize and Automate: Streamline processes and use automation to improve efficiency.
Key ITIL Terms
ITIL (Information Technology Infrastructure Library) uses specific terminology to describe its concepts and processes. Here are some key ITIL terms:
-
Service: The means by which value is delivered to customers, often in the form of intangible deliverables like email or network connectivity.
-
Service Management: The set of organizational capabilities for delivering value to customers in the form of services.
-
Service Lifecycle: The stages of a service's existence, including Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement.
-
Process: A structured set of activities designed to accomplish a specific objective. ITIL defines numerous processes for IT service management.
-
Function: A team or group of people with specific skills and resources responsible for carrying out one or more processes or activities.
-
Role: A defined set of responsibilities and activities assigned to an individual or group, such as a Service Owner or Incident Manager.
-
Stakeholder: Individuals or groups with an interest in or an impact on the services provided by an organization. This can include customers, users, suppliers, and employees.
-
Service Provider: The organization delivering IT services to customers. It can be an internal IT department or an external service provider.
-
Customer: The person or group that defines requirements for IT services and receives the value provided by those services.
-
User: Individuals who utilize IT services to carry out their tasks and achieve their goals, which may or may not be the same as the customer.
ITIL Framework
The ITIL (Information Technology Infrastructure Library) framework is a comprehensive set of best practices and guidelines for IT service management (ITSM). It provides a structured approach for organizations to plan, design, deliver, operate, and continually improve their IT services. The framework is designed to align IT services with the needs of the business and ensure the efficient and effective delivery of those services. Here are the key components and aspects of the ITIL framework:
-
Service Strategy: Defining the organization's IT service strategy, considering business objectives and customer needs.
-
Service Design: Designing IT services, processes, and supporting infrastructure.
-
Service Transition: Managing the transition of new or changed services into the production environment.
-
Service Operation: Ensuring the day-to-day delivery and management of IT services.
-
Continual Service Improvement (CSI): Identifying and implementing improvements to services and processes.
Service Strategy
Service Strategy in ITIL is the critical phase where an organization aligns its IT services with its business objectives and needs. It involves defining a clear service strategy, managing a portfolio of IT services, ensuring financial viability, understanding and influencing customer demand, coordinating service design, managing risks, and nurturing strong business relationships. The goal is to create a roadmap that ensures IT services provide value to the business, support its success, and remain cost-effective, thus guiding subsequent phases of service management and helping the organization make informed decisions about service design, transition, and operation.
Service Design
Service Design, a pivotal phase within the ITIL service lifecycle, focuses on crafting IT services that are not only technically robust but also perfectly aligned with the organization's strategic goals and customer needs. It encompasses the meticulous planning and design of services, including service catalogs, service levels, capacity, availability, continuity, security, and supplier relationships. By adhering to ITIL principles and leveraging design coordination, it ensures that services are both cost-effective and poised for seamless transition into the operational environment. Service Design plays a vital role in delivering services that deliver value to the business while maintaining high levels of quality and customer satisfaction.
Service Transition
Service Transition, a critical phase within the ITIL service lifecycle, orchestrates the controlled and efficient movement of new or modified IT services from development and testing into the operational environment. It encompasses comprehensive change management, configuration control, rigorous testing and validation, and knowledge management to minimize risks and disruptions while maximizing the value and quality of services. By adhering to ITIL principles and detailed transition planning, it ensures that services meet customer expectations, business requirements, and service levels. Service Transition plays a pivotal role in the successful delivery of IT services, fostering agility and adaptability within the organization's IT landscape.
Service Operations
Service Operation, a pivotal phase within the ITIL service lifecycle, is responsible for the continuous and efficient delivery of IT services to meet agreed-upon service levels and customer needs. It encompasses incident and problem management to swiftly resolve issues, event management for proactive monitoring and response, request fulfillment, access management, and the critical role of the service desk as a central point of user support. Technical and IT operations management ensure infrastructure reliability, while application management oversees the lifecycle of business-critical software. By adhering to ITIL principles and promoting continual service improvement, Service Operation plays a vital role in maintaining service quality, minimizing disruptions, and contributing to overall customer satisfaction and business resilience.
Continual Service Improvement (CSI)
Continual Service Improvement (CSI) is a fundamental phase within the ITIL service lifecycle, dedicated to the ongoing enhancement of IT services and processes. It involves systematically measuring service performance, analyzing results, and identifying areas for improvement. By establishing clear metrics, conducting regular reviews, and creating action plans, organizations can drive efficiency, reduce costs, and align IT services with evolving business needs. CSI fosters a culture of continuous improvement, ensuring that IT services remain adaptable and responsive to changing customer requirements and market dynamics, ultimately delivering greater value and quality to the organization and its stakeholders.
How Do I Put ITIL into Practice?
-
Assessment and Alignment: Begin by assessing your organization's existing IT service management practices and identifying areas that need improvement. Determine how well your current practices align with ITIL principles and the organization's business objectives. This assessment provides a baseline for your ITIL implementation efforts.
-
Customization and Planning: ITIL is not a one-size-fits-all framework. Customize ITIL practices to match your organization's specific needs and constraints. Create a clear implementation plan that outlines objectives, milestones, roles, responsibilities, and timelines. Ensure that the plan aligns with your business's strategic goals and secures the necessary resources.
-
Education and Training: Equip your IT teams and staff with the knowledge and skills required for ITIL adoption. Offer training and awareness programs to help them understand the ITIL framework and its benefits. It's essential to create a shared understanding and commitment among team members.
-
Process Redesign and Automation: Redesign or adapt your IT service management processes to align with ITIL best practices. Ensure that these processes are well-documented and easily accessible to all relevant parties. Invest in IT service management tools and technologies that support ITIL processes and automate repetitive tasks to improve efficiency.
-
Continuous Improvement: ITIL is built on the concept of continual service improvement (CSI). Establish a culture of continuous improvement within your organization, where regular reviews and evaluations of ITIL implementation are conducted. Use performance metrics and feedback to identify areas for enhancement and make adjustments to your ITIL practices accordingly. CSI ensures that your IT services remain aligned with evolving business needs and industry best practices.
What is ITIL Certification, and is it Worth it?
ITIL certification is a valuable credential for individuals working in IT service management and related fields. It offers a structured and globally recognized framework for understanding and implementing best practices in IT service delivery and management. Achieving ITIL certification demonstrates your commitment to improving IT service quality and aligning IT with business goals. It can open doors to career advancement and higher earning potential, as many employers value ITIL certification when hiring or promoting IT professionals. However, it's important to consider the cost and time investment required for training and exams, as well as whether ITIL aligns with your specific career path and goals. Continuous learning and staying updated with the latest ITIL practices are also necessary for maintaining the certification's value. Ultimately, the worth of ITIL certification depends on your career aspirations and the relevance of IT service management in your professional journey.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
ITIL V3 and ITIL V4 certifications represent two distinct iterations of the ITIL framework. While ITIL V3 followed a process-oriented service lifecycle model with a structured certification scheme, ITIL V4 introduced a more flexible and holistic approach to IT service management. V4 emphasizes value co-creation, incorporates guiding principles, and introduces a simplified certification structure with practical orientation. It addresses modern trends like digital transformation and agile practices, making it more adaptable to the evolving needs of organizations in the digital age. The transition from V3 to V4 signifies a shift from a process-centric framework to one that focuses on delivering value, enhancing customer experience, and embracing emerging practices, reflecting the changing landscape of IT service management.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
-
Certification Structure:
-
ITIL® V3: V3 had a certification structure consisting of Foundation, Intermediate (Lifecycle and Capability modules), Expert, and Master levels.
-
ITIL® V4: V4 introduced a simplified certification scheme with four levels: Foundation, Practitioner, Specialist, and Strategist. The Master level remains the highest certification but is more accessible under V4.
-
Practical Orientation:
-
ITIL® V3: V3 certification focused on theoretical knowledge of ITIL processes and practices.
-
ITIL® V4: V4 places a stronger emphasis on practical application and adaptation of ITIL principles in real-world scenarios. The Practitioner and Specialist levels are designed to help professionals apply ITIL concepts effectively.
-
Guiding Principles:
-
ITIL® V3: V3 did not have a specific set of guiding principles.
-
ITIL® V4: V4 introduces seven guiding principles (e.g., Focus on Value, Start Where You Are, Collaborate and Promote Visibility) that underpin the framework and guide decision-making.
-
Service Value Chain:
-
ITIL® V3: V3 organized processes into a service lifecycle with five stages: Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement (CSI).
-
ITIL® V4: V4 introduces the Service Value System, which includes the Service Value Chain (a set of interconnected activities) and emphasizes value co-creation with customers.
-
Flexibility and Adaptability:
-
ITIL® V3: V3 had a more rigid and process-centric approach.
-
ITIL® V4: V4 is designed to be more flexible and adaptable, allowing organizations to tailor ITIL practices to their unique needs and circumstances.
-
Digital Transformation and Agile Practices:
-
ITIL® V3: V3 did not specifically address emerging trends like digital transformation and agile practices.
-
ITIL® V4: V4 incorporates modern concepts and practices, making it more relevant in the digital age, including considerations for DevOps, Agile, and lean principles.
How Does ITIL Help Business?
ITIL benefits businesses by offering a structured framework for IT service management, resulting in improved service quality, cost efficiency, and alignment with business objectives. It reduces downtime, enhances change management, and facilitates effective risk mitigation. ITIL's customer-centric approach strengthens customer satisfaction, while its emphasis on continual improvement ensures adaptability and competitiveness in the evolving digital landscape. Additionally, it aids in regulatory compliance, fosters effective communication, and establishes transparent IT governance, ultimately contributing to business resilience, growth, and a competitive edge in the market.
What Will ITIL Cost?
The cost of ITIL can vary significantly depending on factors such as the level of certification, training format, study materials, and the size and complexity of ITIL implementation within an organization. ITIL certification exams range from $150 to $700 or more, with associated training and study materials adding to the expenses. Implementing ITIL practices within an organization involves costs related to training, consulting, process redesign, ITSM tools, and ongoing maintenance. It's crucial to budget carefully, considering both certification and implementation costs, while also weighing the long-term benefits of improved IT service quality, efficiency, and alignment with business objectives that ITIL can bring to the organization.
How Does ITIL Reduce Costs?
ITIL reduces costs for organizations by fostering efficiency, standardizing processes, and minimizing the risks and disruptions associated with IT service management. It achieves this through proactive problem management, rigorous change control, optimized resource allocation, meticulous documentation, and a continual focus on improvement. ITIL's emphasis on aligning IT services with business needs ensures that resources are directed towards activities that generate value, avoiding unnecessary expenses. By preventing service outages and incidents, streamlining workflows, and promoting cost transparency, ITIL helps organizations optimize their IT operations, resulting in significant cost reductions and improved cost-effectiveness.
ITIL Processes and Functions
In ITIL (Information Technology Infrastructure Library), processes and functions are key components of the framework, serving different roles in managing IT services effectively. Here's an overview of ITIL processes and functions:
ITIL Processes: ITIL defines several processes that are essential for IT service management. These processes are organized into five core lifecycle stages:
-
Service Strategy: This stage focuses on defining the overall strategy for IT services, including understanding customer needs, defining service portfolios, and aligning IT goals with business objectives. Key processes include Service Portfolio Management and Financial Management.
-
Service Design: In this stage, ITIL defines processes for designing IT services, ensuring they meet business requirements and are manageable. Processes include Service Catalog Management, Service Level Management, Capacity Management, and Availability Management.
-
Service Transition: This stage involves transitioning new or modified services into the production environment. Key processes include Change Management, Release and Deployment Management, and Service Validation and Testing.
-
Service Operation: Service Operation is responsible for the daily delivery and management of IT services to meet service levels and customer expectations. Processes here include Incident Management, Problem Management, Event Management, and Request Fulfillment.
-
Continual Service Improvement (CSI): CSI focuses on ongoing improvement of IT services and processes. It includes processes like Service Measurement and Reporting, Service Review, and Process Evaluation.
ITIL Functions: Functions in ITIL represent organizational units or groups responsible for specific activities or roles within the IT service management framework. While not all functions are required in every organization, they provide structure and accountability in managing IT services. Key ITIL functions include:
-
Service Desk: The Service Desk function acts as a central point of contact for users to report incidents, request services, and seek assistance. It plays a critical role in providing support and ensuring efficient communication.
-
Technical Management: This function provides technical expertise and support for IT infrastructure and services. It ensures that technical resources are available and properly maintained.
-
IT Operations Management: Responsible for the day-to-day operational activities required to deliver IT services. This includes data center management, network operations, and hardware maintenance.
-
Application Management: The Application Management function manages the lifecycle of applications, ensuring they are designed, developed, tested, and maintained to support business needs.
-
IT Security Management: While not always defined as a separate function, ITIL emphasizes the importance of security throughout the service lifecycle. This involves managing security policies, access controls, and compliance.
-
Supplier Management: Supplier Management ensures that external suppliers and vendors are effectively managed to deliver the required IT services and support.
These functions and processes work together to ensure that IT services are delivered efficiently, reliably, and in alignment with business goals and customer expectations. They provide a structured approach to managing IT services throughout their lifecycle, from strategy and design to operation and improvement.
History of ITIL
The history of ITIL (Information Technology Infrastructure Library) traces its origins to the late 1980s when it was developed by the UK's Central Computer and Telecommunications Agency (CCTA). Initially conceived to standardize and improve IT service management within the UK government, ITIL soon gained recognition for its best-practice guidelines. ITIL V1, released in the late 1980s and early 1990s, laid the foundation with a comprehensive set of 31 books. However, it was in 2000 with the launch of ITIL V2 that ITIL's global impact began to take shape. V2 consolidated the framework into eight core books and gained widespread adoption. ITIL V3, introduced in 2007 and updated in 2011 (ITIL 2011), brought a service lifecycle approach and a focus on aligning IT services with business processes. In 2019, ITIL V4 marked a major shift, emphasizing value co-creation, the Service Value System, and modern IT practices. It continues to evolve, reflecting the changing landscape of IT service management and digital transformation. Throughout its history, ITIL has become a globally recognized framework for enhancing IT service quality and alignment with business objectives.
ITIL Processes and Stages: Summary
ITIL, or the Information Technology Infrastructure Library, encompasses a set of well-defined processes and stages designed to help organizations manage their IT services effectively. The core processes include Service Strategy, which aligns IT services with business goals; Service Design, which focuses on designing services that meet business requirements; Service Transition, which ensures a smooth transition of services into the production environment; Service Operation, responsible for daily service delivery and support; and Continual Service Improvement, which drives ongoing enhancements in service quality and efficiency. These processes are organized into stages that reflect the IT service lifecycle, from aligning IT with business objectives to designing, transitioning, operating, and continually improving services. By following the ITIL framework, organizations can deliver IT services that are not only reliable and cost-effective but also aligned with evolving business needs and customer expectations, ultimately contributing to improved overall business performance and competitiveness.
Read More
Welcome to "A Complete Guide to ITIL Concepts and Summary Process: What is ITIL?" In this comprehensive exploration, we demystify ITIL, the Information Technology Infrastructure Library, offering you a compass to navigate the intricate realm of IT Service Management (ITSM). Discover the core concepts of ITIL, unravel its summary processes, and understand its pivotal role in optimizing IT service delivery, enhancing customer satisfaction, and reshaping modern business operations. Whether you're an IT professional, a business leader, or simply curious about ITIL's impact, this guide equips you with essential knowledge, transforming the way you perceive and implement IT service management practices, all within a single paragraph.
Table of Contents
What is ITIL?
What's in the ITIL?
Benefits of ITIL:
Drawbacks of ITIL:
What are the ITIL Concepts?
What are ITIL's Guiding Principles?
Key ITIL Terms
ITIL Framework
1. Service Strategy
2. Service Design
3. Service Transition
4. Service Operations
5. Continual Service Improvement (CSI)
How Do I Put ITIL into Practice?
What is ITIL Certification, and is it Worth it?
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
How Does ITIL Help Business?
What Will ITIL Cost?
How Does ITIL Reduce Costs?
ITIL Processes and Functions
History of ITIL
ITIL Processes and Stages: Summary
What is ITIL?
ITIL, or Information Technology Infrastructure Library, is a widely adopted framework for IT service management. It offers a structured approach to aligning IT services with business objectives and delivering high-quality services to customers. ITIL encompasses various phases, including service strategy, design, transition, operation, and continual service improvement. It provides best practices and guidelines to enhance the efficiency, reliability, and customer-centricity of IT processes and services, making it a valuable resource for organizations seeking to improve their IT operations.
What's in the ITIL?
ITIL consists of a structured framework for IT service management, including a service lifecycle with stages like Service Strategy, Design, Transition, Operation, and Continual Service Improvement. It defines processes, roles, and functions within IT organizations, guiding how services are designed, delivered, and improved. ITIL emphasizes aligning IT with business goals, offering best practices for incident and problem management, change control, and more. It also provides certification options for IT professionals to validate their expertise. Overall, ITIL offers a holistic approach to managing IT services effectively and efficiently.
Benefits of ITIL
Implementing ITIL (Information Technology Infrastructure Library) in an organization can bring several significant benefits, including:
-
Improved Service Quality: ITIL promotes best practices and standardized processes, leading to more consistent and reliable IT service delivery. This, in turn, enhances the overall quality of IT services, reducing downtime and customer dissatisfaction.
-
Better Alignment with Business Goals: ITIL encourages the alignment of IT services with the objectives and needs of the business. This ensures that IT investments and efforts contribute directly to the organization's success.
-
Cost Efficiency: By optimizing processes and resources, ITIL helps organizations reduce operational costs. Effective incident management, problem resolution, and resource allocation lead to cost savings.
-
Enhanced Customer Satisfaction: ITIL's customer-centric approach ensures that IT services are designed and delivered with the customer's experience in mind. Meeting or exceeding customer expectations leads to higher satisfaction levels.
-
Reduced Risk: ITIL's focus on change management and risk mitigation helps organizations minimize the potential for disruptions and security breaches during service transitions or changes.
Drawbacks of ITIL
While ITIL (Information Technology Infrastructure Library) offers many advantages, it also has some potential drawbacks and challenges:
-
Complexity: ITIL is a comprehensive framework with a multitude of processes, roles, and functions. Implementing the full framework can be complex and resource-intensive, especially for small organizations.
-
Cost: The implementation of ITIL may involve significant upfront costs, including training, software, and process redesign. These expenses can be a barrier for some organizations.
-
Resource Intensive: ITIL requires dedicated resources, including personnel, tools, and time for training and implementation. Smaller organizations may struggle to allocate these resources.
-
Resistance to Change: Employees may resist changes in processes and procedures that ITIL mandates, especially if they have been accustomed to their current ways of working. This can slow down adoption.
-
Overstandardization: In some cases, ITIL's emphasis on standardization can stifle innovation and adaptability. Organizations may become too rigid in their processes and struggle to respond to rapidly changing business needs.
What are the ITIL Concepts?
ITIL (Information Technology Infrastructure Library) encompasses several key concepts that form the foundation of its framework for IT service management. These concepts help organizations understand and implement effective IT service management practices. Here are the core ITIL concepts:
-
Service: ITIL views services as a means of delivering value to customers without the ownership of specific costs and risks.
-
Service Management: ITIL involves specialized organizational capabilities to deliver value through IT services, encompassing processes, functions, roles, and responsibilities.
-
Service Lifecycle: ITIL's framework revolves around five stages: Service Strategy, Design, Transition, Operation, and Continual Service Improvement.
-
Process: ITIL defines a set of processes, each with specific activities, inputs, outputs, and roles, essential for effective IT service management.
-
SLA and KPI: ITIL uses Service Level Agreements (SLAs) to define service quality and Key Performance Indicators (KPIs) to measure and monitor service performance and effectiveness.
What are ITIL's Guiding Principles?
Here are the seven simplified guiding principles of ITIL:
-
Value-Centric: Focus on delivering value to customers and the business.
-
Start Where You Are: Build on your existing processes and capabilities.
-
Feedback-Driven Progress: Continuously improve through feedback and small changes.
-
Collaborate and Communicate: Work together and share information for better results.
-
Think Holistically: Consider the big picture and interconnectedness of services.
-
Keep it Simple: Avoid complexity and prioritize practicality.
-
Optimize and Automate: Streamline processes and use automation to improve efficiency.
Key ITIL Terms
ITIL (Information Technology Infrastructure Library) uses specific terminology to describe its concepts and processes. Here are some key ITIL terms:
-
Service: The means by which value is delivered to customers, often in the form of intangible deliverables like email or network connectivity.
-
Service Management: The set of organizational capabilities for delivering value to customers in the form of services.
-
Service Lifecycle: The stages of a service's existence, including Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement.
-
Process: A structured set of activities designed to accomplish a specific objective. ITIL defines numerous processes for IT service management.
-
Function: A team or group of people with specific skills and resources responsible for carrying out one or more processes or activities.
-
Role: A defined set of responsibilities and activities assigned to an individual or group, such as a Service Owner or Incident Manager.
-
Stakeholder: Individuals or groups with an interest in or an impact on the services provided by an organization. This can include customers, users, suppliers, and employees.
-
Service Provider: The organization delivering IT services to customers. It can be an internal IT department or an external service provider.
-
Customer: The person or group that defines requirements for IT services and receives the value provided by those services.
-
User: Individuals who utilize IT services to carry out their tasks and achieve their goals, which may or may not be the same as the customer.
ITIL Framework
The ITIL (Information Technology Infrastructure Library) framework is a comprehensive set of best practices and guidelines for IT service management (ITSM). It provides a structured approach for organizations to plan, design, deliver, operate, and continually improve their IT services. The framework is designed to align IT services with the needs of the business and ensure the efficient and effective delivery of those services. Here are the key components and aspects of the ITIL framework:
-
Service Strategy: Defining the organization's IT service strategy, considering business objectives and customer needs.
-
Service Design: Designing IT services, processes, and supporting infrastructure.
-
Service Transition: Managing the transition of new or changed services into the production environment.
-
Service Operation: Ensuring the day-to-day delivery and management of IT services.
-
Continual Service Improvement (CSI): Identifying and implementing improvements to services and processes.
Service Strategy
Service Strategy in ITIL is the critical phase where an organization aligns its IT services with its business objectives and needs. It involves defining a clear service strategy, managing a portfolio of IT services, ensuring financial viability, understanding and influencing customer demand, coordinating service design, managing risks, and nurturing strong business relationships. The goal is to create a roadmap that ensures IT services provide value to the business, support its success, and remain cost-effective, thus guiding subsequent phases of service management and helping the organization make informed decisions about service design, transition, and operation.
Service Design
Service Design, a pivotal phase within the ITIL service lifecycle, focuses on crafting IT services that are not only technically robust but also perfectly aligned with the organization's strategic goals and customer needs. It encompasses the meticulous planning and design of services, including service catalogs, service levels, capacity, availability, continuity, security, and supplier relationships. By adhering to ITIL principles and leveraging design coordination, it ensures that services are both cost-effective and poised for seamless transition into the operational environment. Service Design plays a vital role in delivering services that deliver value to the business while maintaining high levels of quality and customer satisfaction.
Service Transition
Service Transition, a critical phase within the ITIL service lifecycle, orchestrates the controlled and efficient movement of new or modified IT services from development and testing into the operational environment. It encompasses comprehensive change management, configuration control, rigorous testing and validation, and knowledge management to minimize risks and disruptions while maximizing the value and quality of services. By adhering to ITIL principles and detailed transition planning, it ensures that services meet customer expectations, business requirements, and service levels. Service Transition plays a pivotal role in the successful delivery of IT services, fostering agility and adaptability within the organization's IT landscape.
Service Operations
Service Operation, a pivotal phase within the ITIL service lifecycle, is responsible for the continuous and efficient delivery of IT services to meet agreed-upon service levels and customer needs. It encompasses incident and problem management to swiftly resolve issues, event management for proactive monitoring and response, request fulfillment, access management, and the critical role of the service desk as a central point of user support. Technical and IT operations management ensure infrastructure reliability, while application management oversees the lifecycle of business-critical software. By adhering to ITIL principles and promoting continual service improvement, Service Operation plays a vital role in maintaining service quality, minimizing disruptions, and contributing to overall customer satisfaction and business resilience.
Continual Service Improvement (CSI)
Continual Service Improvement (CSI) is a fundamental phase within the ITIL service lifecycle, dedicated to the ongoing enhancement of IT services and processes. It involves systematically measuring service performance, analyzing results, and identifying areas for improvement. By establishing clear metrics, conducting regular reviews, and creating action plans, organizations can drive efficiency, reduce costs, and align IT services with evolving business needs. CSI fosters a culture of continuous improvement, ensuring that IT services remain adaptable and responsive to changing customer requirements and market dynamics, ultimately delivering greater value and quality to the organization and its stakeholders.
How Do I Put ITIL into Practice?
-
Assessment and Alignment: Begin by assessing your organization's existing IT service management practices and identifying areas that need improvement. Determine how well your current practices align with ITIL principles and the organization's business objectives. This assessment provides a baseline for your ITIL implementation efforts.
-
Customization and Planning: ITIL is not a one-size-fits-all framework. Customize ITIL practices to match your organization's specific needs and constraints. Create a clear implementation plan that outlines objectives, milestones, roles, responsibilities, and timelines. Ensure that the plan aligns with your business's strategic goals and secures the necessary resources.
-
Education and Training: Equip your IT teams and staff with the knowledge and skills required for ITIL adoption. Offer training and awareness programs to help them understand the ITIL framework and its benefits. It's essential to create a shared understanding and commitment among team members.
-
Process Redesign and Automation: Redesign or adapt your IT service management processes to align with ITIL best practices. Ensure that these processes are well-documented and easily accessible to all relevant parties. Invest in IT service management tools and technologies that support ITIL processes and automate repetitive tasks to improve efficiency.
-
Continuous Improvement: ITIL is built on the concept of continual service improvement (CSI). Establish a culture of continuous improvement within your organization, where regular reviews and evaluations of ITIL implementation are conducted. Use performance metrics and feedback to identify areas for enhancement and make adjustments to your ITIL practices accordingly. CSI ensures that your IT services remain aligned with evolving business needs and industry best practices.
What is ITIL Certification, and is it Worth it?
ITIL certification is a valuable credential for individuals working in IT service management and related fields. It offers a structured and globally recognized framework for understanding and implementing best practices in IT service delivery and management. Achieving ITIL certification demonstrates your commitment to improving IT service quality and aligning IT with business goals. It can open doors to career advancement and higher earning potential, as many employers value ITIL certification when hiring or promoting IT professionals. However, it's important to consider the cost and time investment required for training and exams, as well as whether ITIL aligns with your specific career path and goals. Continuous learning and staying updated with the latest ITIL practices are also necessary for maintaining the certification's value. Ultimately, the worth of ITIL certification depends on your career aspirations and the relevance of IT service management in your professional journey.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
ITIL V3 and ITIL V4 certifications represent two distinct iterations of the ITIL framework. While ITIL V3 followed a process-oriented service lifecycle model with a structured certification scheme, ITIL V4 introduced a more flexible and holistic approach to IT service management. V4 emphasizes value co-creation, incorporates guiding principles, and introduces a simplified certification structure with practical orientation. It addresses modern trends like digital transformation and agile practices, making it more adaptable to the evolving needs of organizations in the digital age. The transition from V3 to V4 signifies a shift from a process-centric framework to one that focuses on delivering value, enhancing customer experience, and embracing emerging practices, reflecting the changing landscape of IT service management.
Major Differences Between ITIL® V3 vs. ITIL® V4 Certification
-
Certification Structure:
-
ITIL® V3: V3 had a certification structure consisting of Foundation, Intermediate (Lifecycle and Capability modules), Expert, and Master levels.
-
ITIL® V4: V4 introduced a simplified certification scheme with four levels: Foundation, Practitioner, Specialist, and Strategist. The Master level remains the highest certification but is more accessible under V4.
-
-
Practical Orientation:
-
ITIL® V3: V3 certification focused on theoretical knowledge of ITIL processes and practices.
-
ITIL® V4: V4 places a stronger emphasis on practical application and adaptation of ITIL principles in real-world scenarios. The Practitioner and Specialist levels are designed to help professionals apply ITIL concepts effectively.
-
-
Guiding Principles:
-
ITIL® V3: V3 did not have a specific set of guiding principles.
-
ITIL® V4: V4 introduces seven guiding principles (e.g., Focus on Value, Start Where You Are, Collaborate and Promote Visibility) that underpin the framework and guide decision-making.
-
-
Service Value Chain:
-
ITIL® V3: V3 organized processes into a service lifecycle with five stages: Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement (CSI).
-
ITIL® V4: V4 introduces the Service Value System, which includes the Service Value Chain (a set of interconnected activities) and emphasizes value co-creation with customers.
-
-
Flexibility and Adaptability:
-
ITIL® V3: V3 had a more rigid and process-centric approach.
-
ITIL® V4: V4 is designed to be more flexible and adaptable, allowing organizations to tailor ITIL practices to their unique needs and circumstances.
-
-
Digital Transformation and Agile Practices:
-
ITIL® V3: V3 did not specifically address emerging trends like digital transformation and agile practices.
-
ITIL® V4: V4 incorporates modern concepts and practices, making it more relevant in the digital age, including considerations for DevOps, Agile, and lean principles.
-
How Does ITIL Help Business?
ITIL benefits businesses by offering a structured framework for IT service management, resulting in improved service quality, cost efficiency, and alignment with business objectives. It reduces downtime, enhances change management, and facilitates effective risk mitigation. ITIL's customer-centric approach strengthens customer satisfaction, while its emphasis on continual improvement ensures adaptability and competitiveness in the evolving digital landscape. Additionally, it aids in regulatory compliance, fosters effective communication, and establishes transparent IT governance, ultimately contributing to business resilience, growth, and a competitive edge in the market.
What Will ITIL Cost?
The cost of ITIL can vary significantly depending on factors such as the level of certification, training format, study materials, and the size and complexity of ITIL implementation within an organization. ITIL certification exams range from $150 to $700 or more, with associated training and study materials adding to the expenses. Implementing ITIL practices within an organization involves costs related to training, consulting, process redesign, ITSM tools, and ongoing maintenance. It's crucial to budget carefully, considering both certification and implementation costs, while also weighing the long-term benefits of improved IT service quality, efficiency, and alignment with business objectives that ITIL can bring to the organization.
How Does ITIL Reduce Costs?
ITIL reduces costs for organizations by fostering efficiency, standardizing processes, and minimizing the risks and disruptions associated with IT service management. It achieves this through proactive problem management, rigorous change control, optimized resource allocation, meticulous documentation, and a continual focus on improvement. ITIL's emphasis on aligning IT services with business needs ensures that resources are directed towards activities that generate value, avoiding unnecessary expenses. By preventing service outages and incidents, streamlining workflows, and promoting cost transparency, ITIL helps organizations optimize their IT operations, resulting in significant cost reductions and improved cost-effectiveness.
ITIL Processes and Functions
In ITIL (Information Technology Infrastructure Library), processes and functions are key components of the framework, serving different roles in managing IT services effectively. Here's an overview of ITIL processes and functions:
ITIL Processes: ITIL defines several processes that are essential for IT service management. These processes are organized into five core lifecycle stages:
-
Service Strategy: This stage focuses on defining the overall strategy for IT services, including understanding customer needs, defining service portfolios, and aligning IT goals with business objectives. Key processes include Service Portfolio Management and Financial Management.
-
Service Design: In this stage, ITIL defines processes for designing IT services, ensuring they meet business requirements and are manageable. Processes include Service Catalog Management, Service Level Management, Capacity Management, and Availability Management.
-
Service Transition: This stage involves transitioning new or modified services into the production environment. Key processes include Change Management, Release and Deployment Management, and Service Validation and Testing.
-
Service Operation: Service Operation is responsible for the daily delivery and management of IT services to meet service levels and customer expectations. Processes here include Incident Management, Problem Management, Event Management, and Request Fulfillment.
-
Continual Service Improvement (CSI): CSI focuses on ongoing improvement of IT services and processes. It includes processes like Service Measurement and Reporting, Service Review, and Process Evaluation.
ITIL Functions: Functions in ITIL represent organizational units or groups responsible for specific activities or roles within the IT service management framework. While not all functions are required in every organization, they provide structure and accountability in managing IT services. Key ITIL functions include:
-
Service Desk: The Service Desk function acts as a central point of contact for users to report incidents, request services, and seek assistance. It plays a critical role in providing support and ensuring efficient communication.
-
Technical Management: This function provides technical expertise and support for IT infrastructure and services. It ensures that technical resources are available and properly maintained.
-
IT Operations Management: Responsible for the day-to-day operational activities required to deliver IT services. This includes data center management, network operations, and hardware maintenance.
-
Application Management: The Application Management function manages the lifecycle of applications, ensuring they are designed, developed, tested, and maintained to support business needs.
-
IT Security Management: While not always defined as a separate function, ITIL emphasizes the importance of security throughout the service lifecycle. This involves managing security policies, access controls, and compliance.
-
Supplier Management: Supplier Management ensures that external suppliers and vendors are effectively managed to deliver the required IT services and support.
These functions and processes work together to ensure that IT services are delivered efficiently, reliably, and in alignment with business goals and customer expectations. They provide a structured approach to managing IT services throughout their lifecycle, from strategy and design to operation and improvement.
History of ITIL
The history of ITIL (Information Technology Infrastructure Library) traces its origins to the late 1980s when it was developed by the UK's Central Computer and Telecommunications Agency (CCTA). Initially conceived to standardize and improve IT service management within the UK government, ITIL soon gained recognition for its best-practice guidelines. ITIL V1, released in the late 1980s and early 1990s, laid the foundation with a comprehensive set of 31 books. However, it was in 2000 with the launch of ITIL V2 that ITIL's global impact began to take shape. V2 consolidated the framework into eight core books and gained widespread adoption. ITIL V3, introduced in 2007 and updated in 2011 (ITIL 2011), brought a service lifecycle approach and a focus on aligning IT services with business processes. In 2019, ITIL V4 marked a major shift, emphasizing value co-creation, the Service Value System, and modern IT practices. It continues to evolve, reflecting the changing landscape of IT service management and digital transformation. Throughout its history, ITIL has become a globally recognized framework for enhancing IT service quality and alignment with business objectives.
ITIL Processes and Stages: Summary
ITIL, or the Information Technology Infrastructure Library, encompasses a set of well-defined processes and stages designed to help organizations manage their IT services effectively. The core processes include Service Strategy, which aligns IT services with business goals; Service Design, which focuses on designing services that meet business requirements; Service Transition, which ensures a smooth transition of services into the production environment; Service Operation, responsible for daily service delivery and support; and Continual Service Improvement, which drives ongoing enhancements in service quality and efficiency. These processes are organized into stages that reflect the IT service lifecycle, from aligning IT with business objectives to designing, transitioning, operating, and continually improving services. By following the ITIL framework, organizations can deliver IT services that are not only reliable and cost-effective but also aligned with evolving business needs and customer expectations, ultimately contributing to improved overall business performance and competitiveness.
Artificial Intelligence: What Lies Ahead for the Future
In an era where science fiction is fast becoming our reality, the realm of Artificial Intelligence (AI) stands at the forefront of innovation and transformation. The question that lingers in the minds of technologists, futurists, and curious minds alike is, "What Lies Ahead for the Future of Artificial Intelligence?" This blog embarks on a journey through the landscapes of AI, aiming to dissect its growth, evolution, and the profound impact it has had on our world.
Table of Contents
-
Growth of AI
-
What Did the Future of AI Look Like 10 Years Ago?
-
Evolution of AI
-
Future of Artificial Intelligence
-
Impact of AI
-
Myths About Advanced Artificial Intelligence
-
AI and the Future of Work
-
Master AI Today
Growth of AI
The growth of AI, or Artificial Intelligence, signifies the relentless advancement and proliferation of intelligent technologies that are reshaping our world. This growth is fueled by technological breakthroughs, with increasingly powerful hardware and sophisticated algorithms driving the development of AI systems. Coupled with the explosion of data availability, AI has found its way into various industries, from healthcare to finance, revolutionizing processes and decision-making. In our everyday lives, AI-driven virtual assistants and recommendation systems have become ubiquitous. Global investment in AI research and development continues to soar, further accelerating AI's expansion. Nevertheless, this journey is not without its challenges, such as data privacy concerns and ethical dilemmas, which need to be addressed as we navigate the ever-expanding horizons of AI.
What Did the Future of AI Look Like 10 Years Ago?
The perception of the future of AI 10 years ago, around 2013, was a mixture of excitement, optimism, and uncertainty. While AI had already made significant strides in areas like natural language processing, machine learning, and computer vision, it had not yet achieved the widespread integration and prominence we see today. Here are some key aspects of how the future of AI was envisioned a decade ago:
-
Rise of Personal Assistants: Virtual personal assistants like Siri and Google Assistant were beginning to gain popularity. The vision was that these AI-driven assistants would become even more capable, understanding natural language and providing personalized assistance in various aspects of our lives.
-
Autonomous Vehicles: The concept of self-driving cars and their potential to revolutionize transportation was emerging. AI was seen as a critical technology in making autonomous vehicles a reality.
-
Healthcare and Diagnostics: There was optimism about AI's potential to assist doctors in diagnosing diseases more accurately and efficiently. Medical imaging and diagnostic tools powered by AI were on the horizon.
-
AI in Business: In the business world, AI was anticipated to improve decision-making through advanced analytics and predictive modeling. Automation of routine tasks in industries like customer service and data entry was also anticipated.
-
Challenges and Concerns: Alongside the excitement, there were concerns about the ethical and societal implications of AI, such as job displacement, algorithmic bias, and privacy issues. These concerns were seen as important topics to address in the future.
-
Limited Understanding of Deep Learning: While deep learning had made significant progress, it had not yet become the dominant AI paradigm it is today. Many people were still exploring other machine learning approaches and algorithms.
Overall, the future of AI 10 years ago was characterized by high expectations for its transformative potential in various domains. However, there was a level of uncertainty about how rapidly these advancements would occur and how society would adapt to the changes brought about by AI technologies. In hindsight, many of these early predictions have materialized to a significant extent, but AI's growth and impact have also presented new challenges and opportunities beyond what was imagined a decade ago.
Evolution of AI
Early Foundations and Optimism (1950s-1960s): The evolution of AI began in the 1950s when computer scientists and mathematicians first contemplated the idea of creating machines that could exhibit human-like intelligence. Pioneers like Alan Turing, John McCarthy, and Marvin Minsky laid the groundwork for AI by developing concepts of computational intelligence and symbolic reasoning. During this period, optimism ran high as researchers believed that AI could solve complex problems, automate decision-making, and simulate human cognitive processes. However, computational limitations and the complexity of human intelligence led to early challenges and set the stage for the first "AI winter" in the 1970s.
Setbacks and Stagnation (1970s-1980s): The 1970s and 1980s witnessed a slowdown in AI research, commonly referred to as the "AI winter." High expectations collided with the reality that AI technologies were not yet capable of delivering on their promises. Funding for AI projects dwindled, and progress stagnated. Expert systems, one of the prominent approaches during this era, demonstrated limited adaptability and struggled to handle real-world complexities. The lack of practical AI applications and unmet expectations contributed to a degree of skepticism about the field's prospects.
Resurgence and Breakthroughs (1990s-Present): AI experienced a resurgence in the 1990s, transitioning from symbolic reasoning to machine learning approaches. Researchers shifted their focus to developing algorithms that could learn from data, resulting in significant progress. The advent of big data, powerful computing resources, and deep learning techniques in the 2010s propelled AI to new heights. Deep neural networks became the foundation for transformative breakthroughs in areas like image recognition, natural language understanding, and autonomous systems. AI is now deeply integrated into various industries and aspects of daily life, reshaping how we work, interact, and solve complex problems. As AI continues to evolve, the quest for Artificial General Intelligence (AGI) and the responsible development of AI technologies remain central to discussions about its future.
Future of Artificial Intelligence
The future of Artificial Intelligence (AI) is a topic of great fascination and speculation due to the rapid advancements and transformative potential of this field. Here are some key aspects to consider when contemplating the future of AI:
-
Enhanced Automation: AI will continue to play a significant role in automating routine and repetitive tasks across various industries. This includes manufacturing, customer service, data analysis, and more. As AI algorithms become more sophisticated, they will enable greater levels of efficiency, cost savings, and accuracy in these domains.
-
Personalization and Recommendation: AI-driven recommendation systems will become even more personalized, offering tailored content, products, and services to individuals. This level of personalization will enhance user experiences in e-commerce, content streaming, and marketing, among other areas.
-
Healthcare Revolution: AI's impact on healthcare will be profound. AI-powered diagnostic tools, predictive analytics, and drug discovery processes will lead to earlier disease detection, more effective treatments, and improved patient outcomes. Telemedicine and remote monitoring will become more common, especially in remote or underserved areas.
-
Autonomous Systems: AI will continue to advance autonomous systems, particularly in self-driving cars, drones, and robotics. These technologies will reshape transportation, logistics, and manufacturing, potentially leading to safer and more efficient operations.
-
Natural Language Processing: AI's capabilities in understanding and generating human language will expand. Conversational AI, chatbots, and virtual assistants will become more sophisticated and capable of handling complex interactions. This will have applications in customer service, healthcare, education, and more.
The future of AI is dynamic and full of promise, but it also poses challenges related to ethics, regulation, and the impact on employment. As AI continues to evolve, it will require careful stewardship to harness its potential for the benefit of humanity while addressing its associated risks.
Impact of AI
AI's impact on society is twofold, offering significant benefits and presenting complex challenges. On one hand, AI has ushered in a new era of efficiency and productivity by automating routine tasks, leading to cost savings and improved operational performance across industries. It has also revolutionized healthcare, enhancing diagnostic accuracy and patient care. Furthermore, AI-driven personalization and recommendation systems have transformed the way businesses engage with customers, offering tailored experiences and boosting user satisfaction. In sectors like finance and education, AI is streamlining processes, making financial decisions more informed, and personalizing learning experiences for students. The creative possibilities of AI and its potential to address global challenges, such as climate change, highlight its role in advancing innovation and research.
Conversely, AI's impact raises concerns regarding ethics and social implications. Issues like algorithmic bias, which can perpetuate discrimination, have come to the forefront. The widespread automation enabled by AI has sparked debates about job displacement and the need for reskilling and upskilling the workforce. Privacy concerns arise from the vast amount of data AI systems collect and analyze, necessitating robust data protection measures. Moreover, as AI technologies continue to advance, there is a need for clear ethical guidelines and regulations to ensure that AI serves humanity's best interests and does not compromise fundamental values. Balancing AI's tremendous potential with these challenges is essential for a harmonious integration of AI into our society.
Myths About Advanced Artificial Intelligence
As advanced artificial intelligence (AI) continues to develop, several myths and misconceptions have emerged that can hinder our understanding of its capabilities and limitations. Here are some common myths about advanced AI:
-
AI Possesses Human-Like General Intelligence: One of the most pervasive myths is that advanced AI systems, even those using deep learning and neural networks, possess human-like general intelligence. In reality, AI today is primarily narrow or specialized, excelling at specific tasks but lacking the broad cognitive abilities and common-sense reasoning that humans have.
-
AI is Infallible: There's a misconception that AI is always accurate and error-free. While AI can perform exceptionally well in certain tasks, it's not immune to errors, especially in situations where it encounters novel or ambiguous data. Additionally, AI can be influenced by biased training data, leading to biased outcomes.
-
AI Understands Like Humans: AI systems can process and generate human language, but they don't truly understand it. They rely on statistical patterns and data, lacking genuine comprehension or consciousness. This myth can lead to overestimating AI's comprehension and reasoning abilities.
-
AI Will Replace All Jobs: While AI automation is transforming some industries, it won't replace all jobs. Instead, it's more likely to augment human work by automating repetitive tasks and allowing humans to focus on creative, strategic, and complex problem-solving roles.
-
AI is a Silver Bullet: Expecting AI to solve all problems is unrealistic. AI is a tool, and its effectiveness depends on the quality of data, the appropriateness of algorithms, and the problem it's applied to. It's not a one-size-fits-all solution.
AI and the Future of Work Top of Form
AI is ushering in a transformative era for the future of work. It promises to revolutionize industries by automating routine tasks and augmenting human capabilities. While automation may lead to concerns about job displacement, it also opens up opportunities for upskilling and reskilling the workforce, with an emphasis on jobs that require creativity, empathy, and complex problem-solving—areas where AI currently falls short. The synergy between humans and AI, along with the responsible development and ethical implementation of AI technologies, will be pivotal in shaping the future of work, enhancing productivity, and improving job quality. It is a dynamic landscape that requires adaptability, lifelong learning, and a balance between efficiency and preserving the human element in the workplace.
Additionally, AI facilitates remote work and flexible arrangements, changing the traditional workplace dynamic. This shift, accelerated by the COVID-19 pandemic, offers benefits such as work-life balance and access to a global talent pool but also presents challenges related to cybersecurity and employee well-being. As AI continues to evolve, its impact on the future of work will be determined by how well individuals, organizations, and governments navigate these changes, foster innovation, and ensure that AI technologies contribute to a more equitable and productive workforce.
Master AI Today
Mastering AI today requires a multifaceted approach, encompassing education, hands-on experience, and a commitment to staying updated with the field's rapid advancements. Begin by acquiring a solid foundation in AI fundamentals through courses and self-study, with a focus on programming languages like Python, deep learning concepts, and data handling skills. Engage in practical projects, experiment with AI frameworks, and build a portfolio that showcases your abilities. Stay attuned to ethical considerations in AI, and actively participate in the AI community through networking and knowledge-sharing. Continuous learning, persistence, and the application of AI to real-world challenges are key to becoming proficient in this dynamic and transformative field.
Read More
In an era where science fiction is fast becoming our reality, the realm of Artificial Intelligence (AI) stands at the forefront of innovation and transformation. The question that lingers in the minds of technologists, futurists, and curious minds alike is, "What Lies Ahead for the Future of Artificial Intelligence?" This blog embarks on a journey through the landscapes of AI, aiming to dissect its growth, evolution, and the profound impact it has had on our world.
Table of Contents
-
Growth of AI
-
What Did the Future of AI Look Like 10 Years Ago?
-
Evolution of AI
-
Future of Artificial Intelligence
-
Impact of AI
-
Myths About Advanced Artificial Intelligence
-
AI and the Future of Work
-
Master AI Today
Growth of AI
The growth of AI, or Artificial Intelligence, signifies the relentless advancement and proliferation of intelligent technologies that are reshaping our world. This growth is fueled by technological breakthroughs, with increasingly powerful hardware and sophisticated algorithms driving the development of AI systems. Coupled with the explosion of data availability, AI has found its way into various industries, from healthcare to finance, revolutionizing processes and decision-making. In our everyday lives, AI-driven virtual assistants and recommendation systems have become ubiquitous. Global investment in AI research and development continues to soar, further accelerating AI's expansion. Nevertheless, this journey is not without its challenges, such as data privacy concerns and ethical dilemmas, which need to be addressed as we navigate the ever-expanding horizons of AI.
What Did the Future of AI Look Like 10 Years Ago?
The perception of the future of AI 10 years ago, around 2013, was a mixture of excitement, optimism, and uncertainty. While AI had already made significant strides in areas like natural language processing, machine learning, and computer vision, it had not yet achieved the widespread integration and prominence we see today. Here are some key aspects of how the future of AI was envisioned a decade ago:
-
Rise of Personal Assistants: Virtual personal assistants like Siri and Google Assistant were beginning to gain popularity. The vision was that these AI-driven assistants would become even more capable, understanding natural language and providing personalized assistance in various aspects of our lives.
-
Autonomous Vehicles: The concept of self-driving cars and their potential to revolutionize transportation was emerging. AI was seen as a critical technology in making autonomous vehicles a reality.
-
Healthcare and Diagnostics: There was optimism about AI's potential to assist doctors in diagnosing diseases more accurately and efficiently. Medical imaging and diagnostic tools powered by AI were on the horizon.
-
AI in Business: In the business world, AI was anticipated to improve decision-making through advanced analytics and predictive modeling. Automation of routine tasks in industries like customer service and data entry was also anticipated.
-
Challenges and Concerns: Alongside the excitement, there were concerns about the ethical and societal implications of AI, such as job displacement, algorithmic bias, and privacy issues. These concerns were seen as important topics to address in the future.
-
Limited Understanding of Deep Learning: While deep learning had made significant progress, it had not yet become the dominant AI paradigm it is today. Many people were still exploring other machine learning approaches and algorithms.
Overall, the future of AI 10 years ago was characterized by high expectations for its transformative potential in various domains. However, there was a level of uncertainty about how rapidly these advancements would occur and how society would adapt to the changes brought about by AI technologies. In hindsight, many of these early predictions have materialized to a significant extent, but AI's growth and impact have also presented new challenges and opportunities beyond what was imagined a decade ago.
Evolution of AI
Early Foundations and Optimism (1950s-1960s): The evolution of AI began in the 1950s when computer scientists and mathematicians first contemplated the idea of creating machines that could exhibit human-like intelligence. Pioneers like Alan Turing, John McCarthy, and Marvin Minsky laid the groundwork for AI by developing concepts of computational intelligence and symbolic reasoning. During this period, optimism ran high as researchers believed that AI could solve complex problems, automate decision-making, and simulate human cognitive processes. However, computational limitations and the complexity of human intelligence led to early challenges and set the stage for the first "AI winter" in the 1970s.
Setbacks and Stagnation (1970s-1980s): The 1970s and 1980s witnessed a slowdown in AI research, commonly referred to as the "AI winter." High expectations collided with the reality that AI technologies were not yet capable of delivering on their promises. Funding for AI projects dwindled, and progress stagnated. Expert systems, one of the prominent approaches during this era, demonstrated limited adaptability and struggled to handle real-world complexities. The lack of practical AI applications and unmet expectations contributed to a degree of skepticism about the field's prospects.
Resurgence and Breakthroughs (1990s-Present): AI experienced a resurgence in the 1990s, transitioning from symbolic reasoning to machine learning approaches. Researchers shifted their focus to developing algorithms that could learn from data, resulting in significant progress. The advent of big data, powerful computing resources, and deep learning techniques in the 2010s propelled AI to new heights. Deep neural networks became the foundation for transformative breakthroughs in areas like image recognition, natural language understanding, and autonomous systems. AI is now deeply integrated into various industries and aspects of daily life, reshaping how we work, interact, and solve complex problems. As AI continues to evolve, the quest for Artificial General Intelligence (AGI) and the responsible development of AI technologies remain central to discussions about its future.
Future of Artificial Intelligence
The future of Artificial Intelligence (AI) is a topic of great fascination and speculation due to the rapid advancements and transformative potential of this field. Here are some key aspects to consider when contemplating the future of AI:
-
Enhanced Automation: AI will continue to play a significant role in automating routine and repetitive tasks across various industries. This includes manufacturing, customer service, data analysis, and more. As AI algorithms become more sophisticated, they will enable greater levels of efficiency, cost savings, and accuracy in these domains.
-
Personalization and Recommendation: AI-driven recommendation systems will become even more personalized, offering tailored content, products, and services to individuals. This level of personalization will enhance user experiences in e-commerce, content streaming, and marketing, among other areas.
-
Healthcare Revolution: AI's impact on healthcare will be profound. AI-powered diagnostic tools, predictive analytics, and drug discovery processes will lead to earlier disease detection, more effective treatments, and improved patient outcomes. Telemedicine and remote monitoring will become more common, especially in remote or underserved areas.
-
Autonomous Systems: AI will continue to advance autonomous systems, particularly in self-driving cars, drones, and robotics. These technologies will reshape transportation, logistics, and manufacturing, potentially leading to safer and more efficient operations.
-
Natural Language Processing: AI's capabilities in understanding and generating human language will expand. Conversational AI, chatbots, and virtual assistants will become more sophisticated and capable of handling complex interactions. This will have applications in customer service, healthcare, education, and more.
The future of AI is dynamic and full of promise, but it also poses challenges related to ethics, regulation, and the impact on employment. As AI continues to evolve, it will require careful stewardship to harness its potential for the benefit of humanity while addressing its associated risks.
Impact of AI
AI's impact on society is twofold, offering significant benefits and presenting complex challenges. On one hand, AI has ushered in a new era of efficiency and productivity by automating routine tasks, leading to cost savings and improved operational performance across industries. It has also revolutionized healthcare, enhancing diagnostic accuracy and patient care. Furthermore, AI-driven personalization and recommendation systems have transformed the way businesses engage with customers, offering tailored experiences and boosting user satisfaction. In sectors like finance and education, AI is streamlining processes, making financial decisions more informed, and personalizing learning experiences for students. The creative possibilities of AI and its potential to address global challenges, such as climate change, highlight its role in advancing innovation and research.
Conversely, AI's impact raises concerns regarding ethics and social implications. Issues like algorithmic bias, which can perpetuate discrimination, have come to the forefront. The widespread automation enabled by AI has sparked debates about job displacement and the need for reskilling and upskilling the workforce. Privacy concerns arise from the vast amount of data AI systems collect and analyze, necessitating robust data protection measures. Moreover, as AI technologies continue to advance, there is a need for clear ethical guidelines and regulations to ensure that AI serves humanity's best interests and does not compromise fundamental values. Balancing AI's tremendous potential with these challenges is essential for a harmonious integration of AI into our society.
Myths About Advanced Artificial Intelligence
As advanced artificial intelligence (AI) continues to develop, several myths and misconceptions have emerged that can hinder our understanding of its capabilities and limitations. Here are some common myths about advanced AI:
-
AI Possesses Human-Like General Intelligence: One of the most pervasive myths is that advanced AI systems, even those using deep learning and neural networks, possess human-like general intelligence. In reality, AI today is primarily narrow or specialized, excelling at specific tasks but lacking the broad cognitive abilities and common-sense reasoning that humans have.
-
AI is Infallible: There's a misconception that AI is always accurate and error-free. While AI can perform exceptionally well in certain tasks, it's not immune to errors, especially in situations where it encounters novel or ambiguous data. Additionally, AI can be influenced by biased training data, leading to biased outcomes.
-
AI Understands Like Humans: AI systems can process and generate human language, but they don't truly understand it. They rely on statistical patterns and data, lacking genuine comprehension or consciousness. This myth can lead to overestimating AI's comprehension and reasoning abilities.
-
AI Will Replace All Jobs: While AI automation is transforming some industries, it won't replace all jobs. Instead, it's more likely to augment human work by automating repetitive tasks and allowing humans to focus on creative, strategic, and complex problem-solving roles.
-
AI is a Silver Bullet: Expecting AI to solve all problems is unrealistic. AI is a tool, and its effectiveness depends on the quality of data, the appropriateness of algorithms, and the problem it's applied to. It's not a one-size-fits-all solution.
AI and the Future of Work Top of Form
AI is ushering in a transformative era for the future of work. It promises to revolutionize industries by automating routine tasks and augmenting human capabilities. While automation may lead to concerns about job displacement, it also opens up opportunities for upskilling and reskilling the workforce, with an emphasis on jobs that require creativity, empathy, and complex problem-solving—areas where AI currently falls short. The synergy between humans and AI, along with the responsible development and ethical implementation of AI technologies, will be pivotal in shaping the future of work, enhancing productivity, and improving job quality. It is a dynamic landscape that requires adaptability, lifelong learning, and a balance between efficiency and preserving the human element in the workplace.
Additionally, AI facilitates remote work and flexible arrangements, changing the traditional workplace dynamic. This shift, accelerated by the COVID-19 pandemic, offers benefits such as work-life balance and access to a global talent pool but also presents challenges related to cybersecurity and employee well-being. As AI continues to evolve, its impact on the future of work will be determined by how well individuals, organizations, and governments navigate these changes, foster innovation, and ensure that AI technologies contribute to a more equitable and productive workforce.
Master AI Today
Mastering AI today requires a multifaceted approach, encompassing education, hands-on experience, and a commitment to staying updated with the field's rapid advancements. Begin by acquiring a solid foundation in AI fundamentals through courses and self-study, with a focus on programming languages like Python, deep learning concepts, and data handling skills. Engage in practical projects, experiment with AI frameworks, and build a portfolio that showcases your abilities. Stay attuned to ethical considerations in AI, and actively participate in the AI community through networking and knowledge-sharing. Continuous learning, persistence, and the application of AI to real-world challenges are key to becoming proficient in this dynamic and transformative field.
Six Sigma or Lean Six Sigma: Which Certification Path Should You Take?
In the quest for professional development and career advancement, the world of certifications stands as an essential crossroads, offering a multitude of paths to choose from. Among the many options, "Six Sigma" and "Lean Six Sigma" certifications shine as beacons of quality and process improvement, coveted by industries far and wide. However, faced with these two formidable choices, aspiring professionals often find themselves at a crossroads, pondering the critical question: "Six Sigma or Lean Six Sigma: Which Certification Path Should You Take?" This decision is no trifling matter, as it can significantly impact one's career trajectory and skill set. In this exploration, we delve into the nuances of both certification paths, shedding light on their differences, similarities, and the factors that can guide you toward making an informed and rewarding choice. Whether you're navigating the intricacies of quality management or seeking to optimize processes, this guide aims to equip you with the insights necessary to embark on the certification journey that aligns best with your aspirations and ambitions.
Table of Contents
-
What is Six Sigma?
-
What is Lean?
-
What is Lean Six Sigma?
-
Lean vs Six Sigma: Similarities and Differences
-
Certification Eligibilities, Examinations, and Responsibilities
-
Which is Right for You?
-
FAQs
What is Six Sigma?
Six Sigma is a data-driven methodology and set of tools and techniques used to improve processes and reduce defects in various industries, with a primary focus on achieving higher levels of quality and efficiency. It was originally developed by Motorola in the 1980s and later popularized by companies like General Electric.
The term "Six Sigma" refers to a statistical measure of process performance, which signifies that a process is capable of producing fewer than 3.4 defects per million opportunities (DPMO). In essence, it represents a high level of process accuracy and consistency.
Six Sigma is used in various industries, including manufacturing, healthcare, finance, and service sectors, to streamline processes, reduce costs, improve quality, and increase customer satisfaction. It offers a systematic approach to problem-solving and process improvement, making it a valuable tool for organizations seeking operational excellence.
What is Lean?
Lean, often referred to as Lean Thinking or Lean Management, is a methodology and philosophy that focuses on eliminating waste and maximizing value in processes. It originated from the manufacturing practices developed by Toyota in Japan and is often associated with the Toyota Production System (TPS). However, Lean principles have since been applied to various industries and sectors beyond manufacturing, including healthcare, service, and software development.
Lean principles aim to create more efficient, responsive, and customer-focused organizations. By eliminating waste and optimizing processes, Lean helps organizations deliver higher quality products and services while reducing costs and lead times. It's a holistic approach to operational excellence that goes beyond specific tools and techniques to instill a culture of continuous improvement throughout an organization.
What is Lean Six Sigma?
Lean Six Sigma is a hybrid approach that combines the principles and methodologies of Lean and Six Sigma. It is a comprehensive strategy for process improvement that seeks to eliminate waste and defects while optimizing efficiency and quality. Lean focuses on reducing waste and increasing flow, while Six Sigma emphasizes reducing defects and variations in processes. By integrating these two approaches, Lean Six Sigma aims to create a powerful framework for achieving operational excellence and improving organizational performance.
Lean Six Sigma is widely used in various industries, including manufacturing, healthcare, finance, and service sectors, to enhance process efficiency, reduce defects, minimize waste, and improve overall organizational performance. It offers a structured and data-driven approach to achieving excellence in both processes and outcomes.
Lean vs Six Sigma: Similarities and Differences
Lean and Six Sigma are two distinct methodologies for process improvement, but they share some similarities while also having key differences. Here's an overview of their similarities and differences:
Similarities:
-
Focus on Process Improvement: Both Lean and Six Sigma are centered on improving processes to achieve better outcomes, whether that's reducing defects, minimizing waste, enhancing efficiency, or improving overall quality.
-
Data-Driven: Both methodologies rely on data and statistical analysis to identify problems, measure process performance, and make informed decisions. Data is used to quantify issues and track progress.
-
Customer-Centric: Both Lean and Six Sigma emphasize meeting and exceeding customer expectations. They aim to deliver products or services that align with customer needs and preferences.
-
Continuous Improvement: Continuous improvement is a core principle of both Lean and Six Sigma. They advocate for an ongoing commitment to identifying and addressing issues, making incremental improvements, and striving for excellence.
-
Team-Based Approach: Both methodologies often involve cross-functional teams that collaborate to solve problems and drive improvements. This encourages a diversity of perspectives and expertise.
-
Root Cause Analysis: Both Lean and Six Sigma seek to identify and address the root causes of problems rather than just treating symptoms. This helps prevent issues from recurring.
Differences:
-
Primary Focus:
-
Lean primarily concentrates on the elimination of waste and the optimization of processes for efficiency and flow. Its main goal is to deliver value to customers while minimizing non-value-added activities.
-
Six Sigma primarily focuses on reducing process variation and defects. It aims to achieve a level of quality where the probability of defects is extremely low (less than 3.4 defects per million opportunities).
-
Methodologies:
-
Lean often uses tools like Value Stream Mapping, 5S, Kanban, and visual management techniques to improve processes and reduce waste.
-
Six Sigma employs statistical tools and techniques, such as DMAIC (Define, Measure, Analyze, Improve, Control), to measure and analyze process performance and drive improvements.
-
Waste Reduction:
-
Lean places a strong emphasis on identifying and eliminating various types of waste, including overproduction, transportation, waiting, and more.
-
Six Sigma focuses on reducing defects and minimizing process variation, which can lead to defects or deviations from desired outcomes.
-
Speed vs. Precision:
-
Lean is often associated with faster improvements and quicker results due to its focus on reducing waste and improving flow.
-
Six Sigma can take longer to implement, as it involves a more rigorous and data-intensive approach to reducing defects and variation.
-
Tools and Techniques:
-
Lean tools are geared toward process optimization and include techniques for visual management and rapid problem-solving.
-
Six Sigma tools are statistical in nature and are used to measure, analyze, and control processes to reduce variation and defects.
Certification Eligibilities, Examinations, and Responsibilities
Certification eligibility, examinations, and responsibilities can vary significantly depending on the specific certification program and the organization or governing body that administers it. Here is a general overview of what these aspects typically involve:
Certification Eligibility:
Eligibility for Six Sigma and Lean Six Sigma certifications varies based on the certification level and the certifying organization. Generally, Yellow Belt certifications have minimal prerequisites, while Green Belt certifications often require a bachelor's degree or equivalent experience. Black Belt certifications typically demand both a bachelor's degree and relevant work experience, with some programs expecting Green Belt certification as well. Master Black Belt certifications are typically reserved for highly experienced professionals who have completed numerous successful projects and demonstrated leadership in Six Sigma initiatives. While the specific requirements may vary, a solid understanding of Six Sigma concepts and, for Lean Six Sigma, familiarity with Lean principles are essential for pursuing these certifications. Candidates should always refer to the certifying organization's guidelines for precise eligibility criteria.
Examinations:
Examinations for Six Sigma and Lean Six Sigma certifications are comprehensive assessments that evaluate candidates' knowledge and expertise in quality management, process improvement, statistical analysis, and Lean methodologies. These exams vary in content, format, duration, and passing score based on the certification level (e.g., Yellow Belt, Green Belt, Black Belt) and the certifying organization. Typically, they encompass a range of question types, such as multiple-choice and true/false questions, and are administered through authorized testing centers or online proctoring services. Achieving a passing score is a critical milestone in earning these prestigious certifications, demonstrating proficiency in problem-solving, process optimization, and quality enhancement within an organization.
Responsibilities:
Responsibilities associated with Six Sigma and Lean Six Sigma certifications encompass various stages of the certification process and ongoing professional practice. Candidates pursuing these certifications are first responsible for thorough preparation, including studying the relevant materials and attending training if necessary. They must then take the initiative to register for the certification exam and adhere to the rules and procedures on exam day. During the exam, candidates must demonstrate their knowledge and problem-solving abilities. Afterward, successful candidates receive their certifications, but the responsibility doesn't end there. Certified professionals have a duty to apply their knowledge in the workplace, contributing to process improvement initiatives and ethical conduct. Continuous learning and maintaining ethical standards are also ongoing responsibilities associated with these certifications, reflecting a commitment to excellence and the promotion of quality within organizations.
It's important for individuals seeking certification to carefully review the specific eligibility requirements, examination details, and responsibilities outlined by the certifying organization to ensure they are fully prepared and compliant with the certification process.
Which is Right for You?
Determining whether Six Sigma or Lean Six Sigma is right for you depends on your specific career goals, the industry you work in or plan to work in, and your preferences for process improvement methodologies. Here are some considerations to help you decide which path might be more suitable:
Choose Six Sigma if:
-
You prioritize reducing defects: Six Sigma is particularly effective for industries where reducing defects and achieving near-perfect quality is critical, such as manufacturing and healthcare.
-
You enjoy statistical analysis: Six Sigma places a strong emphasis on statistical tools and data analysis. If you have a passion for data-driven decision-making and enjoy working with statistical techniques, Six Sigma might align well with your interests.
-
You want a structured problem-solving framework: Six Sigma provides a highly structured problem-solving approach through the DMAIC (Define, Measure, Analyze, Improve, Control) methodology, making it suitable for complex process improvement projects.
-
Your industry values traditional quality management: Some industries have a long history of using Six Sigma for quality management, making it a respected certification in those sectors.
Choose Lean Six Sigma if:
-
You seek to minimize waste: Lean Six Sigma excels at waste reduction and process optimization. If you are interested in eliminating non-value-added activities, improving efficiency, and enhancing flow within processes, Lean Six Sigma is a strong choice.
-
You prefer a holistic approach: Lean Six Sigma combines the principles of both Lean and Six Sigma, offering a more comprehensive framework that addresses both defects and waste. It's a versatile methodology suitable for a wide range of industries.
-
Your industry values efficiency and customer satisfaction: Lean Six Sigma's focus on improving processes and delivering value to customers aligns well with industries that prioritize efficiency, such as manufacturing, service, and healthcare.
-
You enjoy visual management and rapid problem-solving: Lean tools like Kanban, 5S, and visual management techniques can make problem-solving more intuitive and efficient.
Ultimately, the decision between Six Sigma and Lean Six Sigma should align with your career aspirations, interests, and the specific needs of the industry you are or plan to be a part of. It's worth noting that some professionals choose to pursue both certifications to have a well-rounded skill set that covers both defect reduction and waste elimination, allowing them to be more versatile problem solvers in various professional settings.
FAQs
Q1: What is the difference between Six Sigma and Lean Six Sigma certifications?
A: Six Sigma primarily focuses on reducing defects and process variation, while Lean Six Sigma combines Six Sigma principles with Lean methodology, emphasizing waste reduction and process optimization. The choice between them depends on your specific career goals and the nature of the industry you're interested in.
Q2: Which certification is more suitable for a career in manufacturing?
A: Both Six Sigma and Lean Six Sigma certifications are valuable in manufacturing. Six Sigma may be more suitable for quality control and defect reduction, while Lean Six Sigma can help streamline processes and reduce waste in manufacturing.
Q3: Are there any prerequisites for Six Sigma or Lean Six Sigma certifications?
A: Prerequisites can vary depending on the certification level and the certifying organization. Some certifications may require prior work experience or completion of specific training courses. Check the requirements of the certification program you're interested in.
Q4: Can I pursue both Six Sigma and Lean Six Sigma certifications simultaneously?
A: Yes, it's possible to pursue both certifications. Some individuals choose to earn both to have a well-rounded skill set that combines defect reduction and process optimization.
Q5: Do I need to choose between Six Sigma and Lean Six Sigma, or can I combine both approaches in my career?
A: You can certainly combine both approaches in your career. In fact, many organizations adopt Lean Six Sigma principles to benefit from both defect reduction and waste elimination.
Q6: How do I decide which certification path is right for me?
A: Consider your career goals, industry preferences, and the specific skills you want to develop. If you're interested in quality control and statistical analysis, Six Sigma may be a better fit. If you're more focused on process efficiency and waste reduction, Lean Six Sigma may be the way to go.
Q7: Which certification is more recognized by employers?
A: The recognition of Six Sigma and Lean Six Sigma certifications can vary by industry and region. It's essential to research the specific demands of your desired job market. Both certifications are widely recognized and respected.
Q8: Can I switch from Six Sigma to Lean Six Sigma or vice versa after obtaining one certification?
A: Yes, you can switch between the two paths. Many concepts and tools overlap between the two methodologies, making it relatively easy to transition.
Q9: How long does it typically take to earn a Six Sigma or Lean Six Sigma certification?
A: The duration varies based on the certification level (e.g., Green Belt, Black Belt) and the training program. Some certifications can be completed in a few weeks, while others may take several months or longer.
Q10: What is the average cost of obtaining a Six Sigma or Lean Six Sigma certification?
A: Certification costs can vary widely depending on the level, the certifying organization, and whether you choose to undergo training. It's essential to research the specific program and its associated costs.
Read More
In the quest for professional development and career advancement, the world of certifications stands as an essential crossroads, offering a multitude of paths to choose from. Among the many options, "Six Sigma" and "Lean Six Sigma" certifications shine as beacons of quality and process improvement, coveted by industries far and wide. However, faced with these two formidable choices, aspiring professionals often find themselves at a crossroads, pondering the critical question: "Six Sigma or Lean Six Sigma: Which Certification Path Should You Take?" This decision is no trifling matter, as it can significantly impact one's career trajectory and skill set. In this exploration, we delve into the nuances of both certification paths, shedding light on their differences, similarities, and the factors that can guide you toward making an informed and rewarding choice. Whether you're navigating the intricacies of quality management or seeking to optimize processes, this guide aims to equip you with the insights necessary to embark on the certification journey that aligns best with your aspirations and ambitions.
Table of Contents
-
What is Six Sigma?
-
What is Lean?
-
What is Lean Six Sigma?
-
Lean vs Six Sigma: Similarities and Differences
-
Certification Eligibilities, Examinations, and Responsibilities
-
Which is Right for You?
-
FAQs
What is Six Sigma?
Six Sigma is a data-driven methodology and set of tools and techniques used to improve processes and reduce defects in various industries, with a primary focus on achieving higher levels of quality and efficiency. It was originally developed by Motorola in the 1980s and later popularized by companies like General Electric.
The term "Six Sigma" refers to a statistical measure of process performance, which signifies that a process is capable of producing fewer than 3.4 defects per million opportunities (DPMO). In essence, it represents a high level of process accuracy and consistency.
Six Sigma is used in various industries, including manufacturing, healthcare, finance, and service sectors, to streamline processes, reduce costs, improve quality, and increase customer satisfaction. It offers a systematic approach to problem-solving and process improvement, making it a valuable tool for organizations seeking operational excellence.
What is Lean?
Lean, often referred to as Lean Thinking or Lean Management, is a methodology and philosophy that focuses on eliminating waste and maximizing value in processes. It originated from the manufacturing practices developed by Toyota in Japan and is often associated with the Toyota Production System (TPS). However, Lean principles have since been applied to various industries and sectors beyond manufacturing, including healthcare, service, and software development.
Lean principles aim to create more efficient, responsive, and customer-focused organizations. By eliminating waste and optimizing processes, Lean helps organizations deliver higher quality products and services while reducing costs and lead times. It's a holistic approach to operational excellence that goes beyond specific tools and techniques to instill a culture of continuous improvement throughout an organization.
What is Lean Six Sigma?
Lean Six Sigma is a hybrid approach that combines the principles and methodologies of Lean and Six Sigma. It is a comprehensive strategy for process improvement that seeks to eliminate waste and defects while optimizing efficiency and quality. Lean focuses on reducing waste and increasing flow, while Six Sigma emphasizes reducing defects and variations in processes. By integrating these two approaches, Lean Six Sigma aims to create a powerful framework for achieving operational excellence and improving organizational performance.
Lean Six Sigma is widely used in various industries, including manufacturing, healthcare, finance, and service sectors, to enhance process efficiency, reduce defects, minimize waste, and improve overall organizational performance. It offers a structured and data-driven approach to achieving excellence in both processes and outcomes.
Lean vs Six Sigma: Similarities and Differences
Lean and Six Sigma are two distinct methodologies for process improvement, but they share some similarities while also having key differences. Here's an overview of their similarities and differences:
Similarities:
-
Focus on Process Improvement: Both Lean and Six Sigma are centered on improving processes to achieve better outcomes, whether that's reducing defects, minimizing waste, enhancing efficiency, or improving overall quality.
-
Data-Driven: Both methodologies rely on data and statistical analysis to identify problems, measure process performance, and make informed decisions. Data is used to quantify issues and track progress.
-
Customer-Centric: Both Lean and Six Sigma emphasize meeting and exceeding customer expectations. They aim to deliver products or services that align with customer needs and preferences.
-
Continuous Improvement: Continuous improvement is a core principle of both Lean and Six Sigma. They advocate for an ongoing commitment to identifying and addressing issues, making incremental improvements, and striving for excellence.
-
Team-Based Approach: Both methodologies often involve cross-functional teams that collaborate to solve problems and drive improvements. This encourages a diversity of perspectives and expertise.
-
Root Cause Analysis: Both Lean and Six Sigma seek to identify and address the root causes of problems rather than just treating symptoms. This helps prevent issues from recurring.
Differences:
-
Primary Focus:
-
Lean primarily concentrates on the elimination of waste and the optimization of processes for efficiency and flow. Its main goal is to deliver value to customers while minimizing non-value-added activities.
-
Six Sigma primarily focuses on reducing process variation and defects. It aims to achieve a level of quality where the probability of defects is extremely low (less than 3.4 defects per million opportunities).
-
-
Methodologies:
-
Lean often uses tools like Value Stream Mapping, 5S, Kanban, and visual management techniques to improve processes and reduce waste.
-
Six Sigma employs statistical tools and techniques, such as DMAIC (Define, Measure, Analyze, Improve, Control), to measure and analyze process performance and drive improvements.
-
-
Waste Reduction:
-
Lean places a strong emphasis on identifying and eliminating various types of waste, including overproduction, transportation, waiting, and more.
-
Six Sigma focuses on reducing defects and minimizing process variation, which can lead to defects or deviations from desired outcomes.
-
-
Speed vs. Precision:
-
Lean is often associated with faster improvements and quicker results due to its focus on reducing waste and improving flow.
-
Six Sigma can take longer to implement, as it involves a more rigorous and data-intensive approach to reducing defects and variation.
-
-
Tools and Techniques:
-
Lean tools are geared toward process optimization and include techniques for visual management and rapid problem-solving.
-
Six Sigma tools are statistical in nature and are used to measure, analyze, and control processes to reduce variation and defects.
-
Certification Eligibilities, Examinations, and Responsibilities
Certification eligibility, examinations, and responsibilities can vary significantly depending on the specific certification program and the organization or governing body that administers it. Here is a general overview of what these aspects typically involve:
Certification Eligibility:
Eligibility for Six Sigma and Lean Six Sigma certifications varies based on the certification level and the certifying organization. Generally, Yellow Belt certifications have minimal prerequisites, while Green Belt certifications often require a bachelor's degree or equivalent experience. Black Belt certifications typically demand both a bachelor's degree and relevant work experience, with some programs expecting Green Belt certification as well. Master Black Belt certifications are typically reserved for highly experienced professionals who have completed numerous successful projects and demonstrated leadership in Six Sigma initiatives. While the specific requirements may vary, a solid understanding of Six Sigma concepts and, for Lean Six Sigma, familiarity with Lean principles are essential for pursuing these certifications. Candidates should always refer to the certifying organization's guidelines for precise eligibility criteria.
Examinations:
Examinations for Six Sigma and Lean Six Sigma certifications are comprehensive assessments that evaluate candidates' knowledge and expertise in quality management, process improvement, statistical analysis, and Lean methodologies. These exams vary in content, format, duration, and passing score based on the certification level (e.g., Yellow Belt, Green Belt, Black Belt) and the certifying organization. Typically, they encompass a range of question types, such as multiple-choice and true/false questions, and are administered through authorized testing centers or online proctoring services. Achieving a passing score is a critical milestone in earning these prestigious certifications, demonstrating proficiency in problem-solving, process optimization, and quality enhancement within an organization.
Responsibilities:
Responsibilities associated with Six Sigma and Lean Six Sigma certifications encompass various stages of the certification process and ongoing professional practice. Candidates pursuing these certifications are first responsible for thorough preparation, including studying the relevant materials and attending training if necessary. They must then take the initiative to register for the certification exam and adhere to the rules and procedures on exam day. During the exam, candidates must demonstrate their knowledge and problem-solving abilities. Afterward, successful candidates receive their certifications, but the responsibility doesn't end there. Certified professionals have a duty to apply their knowledge in the workplace, contributing to process improvement initiatives and ethical conduct. Continuous learning and maintaining ethical standards are also ongoing responsibilities associated with these certifications, reflecting a commitment to excellence and the promotion of quality within organizations.
It's important for individuals seeking certification to carefully review the specific eligibility requirements, examination details, and responsibilities outlined by the certifying organization to ensure they are fully prepared and compliant with the certification process.
Which is Right for You?
Determining whether Six Sigma or Lean Six Sigma is right for you depends on your specific career goals, the industry you work in or plan to work in, and your preferences for process improvement methodologies. Here are some considerations to help you decide which path might be more suitable:
Choose Six Sigma if:
-
You prioritize reducing defects: Six Sigma is particularly effective for industries where reducing defects and achieving near-perfect quality is critical, such as manufacturing and healthcare.
-
You enjoy statistical analysis: Six Sigma places a strong emphasis on statistical tools and data analysis. If you have a passion for data-driven decision-making and enjoy working with statistical techniques, Six Sigma might align well with your interests.
-
You want a structured problem-solving framework: Six Sigma provides a highly structured problem-solving approach through the DMAIC (Define, Measure, Analyze, Improve, Control) methodology, making it suitable for complex process improvement projects.
-
Your industry values traditional quality management: Some industries have a long history of using Six Sigma for quality management, making it a respected certification in those sectors.
Choose Lean Six Sigma if:
-
You seek to minimize waste: Lean Six Sigma excels at waste reduction and process optimization. If you are interested in eliminating non-value-added activities, improving efficiency, and enhancing flow within processes, Lean Six Sigma is a strong choice.
-
You prefer a holistic approach: Lean Six Sigma combines the principles of both Lean and Six Sigma, offering a more comprehensive framework that addresses both defects and waste. It's a versatile methodology suitable for a wide range of industries.
-
Your industry values efficiency and customer satisfaction: Lean Six Sigma's focus on improving processes and delivering value to customers aligns well with industries that prioritize efficiency, such as manufacturing, service, and healthcare.
-
You enjoy visual management and rapid problem-solving: Lean tools like Kanban, 5S, and visual management techniques can make problem-solving more intuitive and efficient.
Ultimately, the decision between Six Sigma and Lean Six Sigma should align with your career aspirations, interests, and the specific needs of the industry you are or plan to be a part of. It's worth noting that some professionals choose to pursue both certifications to have a well-rounded skill set that covers both defect reduction and waste elimination, allowing them to be more versatile problem solvers in various professional settings.
FAQs
Q1: What is the difference between Six Sigma and Lean Six Sigma certifications?
A: Six Sigma primarily focuses on reducing defects and process variation, while Lean Six Sigma combines Six Sigma principles with Lean methodology, emphasizing waste reduction and process optimization. The choice between them depends on your specific career goals and the nature of the industry you're interested in.
Q2: Which certification is more suitable for a career in manufacturing?
A: Both Six Sigma and Lean Six Sigma certifications are valuable in manufacturing. Six Sigma may be more suitable for quality control and defect reduction, while Lean Six Sigma can help streamline processes and reduce waste in manufacturing.
Q3: Are there any prerequisites for Six Sigma or Lean Six Sigma certifications?
A: Prerequisites can vary depending on the certification level and the certifying organization. Some certifications may require prior work experience or completion of specific training courses. Check the requirements of the certification program you're interested in.
Q4: Can I pursue both Six Sigma and Lean Six Sigma certifications simultaneously?
A: Yes, it's possible to pursue both certifications. Some individuals choose to earn both to have a well-rounded skill set that combines defect reduction and process optimization.
Q5: Do I need to choose between Six Sigma and Lean Six Sigma, or can I combine both approaches in my career?
A: You can certainly combine both approaches in your career. In fact, many organizations adopt Lean Six Sigma principles to benefit from both defect reduction and waste elimination.
Q6: How do I decide which certification path is right for me?
A: Consider your career goals, industry preferences, and the specific skills you want to develop. If you're interested in quality control and statistical analysis, Six Sigma may be a better fit. If you're more focused on process efficiency and waste reduction, Lean Six Sigma may be the way to go.
Q7: Which certification is more recognized by employers?
A: The recognition of Six Sigma and Lean Six Sigma certifications can vary by industry and region. It's essential to research the specific demands of your desired job market. Both certifications are widely recognized and respected.
Q8: Can I switch from Six Sigma to Lean Six Sigma or vice versa after obtaining one certification?
A: Yes, you can switch between the two paths. Many concepts and tools overlap between the two methodologies, making it relatively easy to transition.
Q9: How long does it typically take to earn a Six Sigma or Lean Six Sigma certification?
A: The duration varies based on the certification level (e.g., Green Belt, Black Belt) and the training program. Some certifications can be completed in a few weeks, while others may take several months or longer.
Q10: What is the average cost of obtaining a Six Sigma or Lean Six Sigma certification?
A: Certification costs can vary widely depending on the level, the certifying organization, and whether you choose to undergo training. It's essential to research the specific program and its associated costs.
What is Big Data Analytics and What is Its Significance in the Modern World?
Welcome to our comprehensive guide on 'What is Big Data Analytics and What is Its Significance in the Modern World?' In this in-depth exploration, we delve into the realm of big data analytics, shedding light on its fundamental concepts, applications, and its paramount importance in our contemporary data-driven society. Join us as we unravel the intricacies of this transformative technology and unveil its profound impact on businesses, industries, and society as a whole.
Table of Contents
What is Big Data Analytics?
Why is big data analytics important?
What is Big Data?
Uses and Examples of Big Data Analytics
History of Big Data Analytics
Benefits and Advantages of Big Data Analytics
The Lifecycle Phases of Big Data Analytics
Different Types of Big Data Analytics
Big Data Analytics Tools
Big Data Industry Applications
FAQs
What is Big Data Analytics?
Big Data Analytics is the process of extracting valuable insights from vast and complex data sets, enabling organizations to make data-driven decisions, enhance operational efficiency, improve customer experiences, manage risks effectively, and foster innovation across various industries. This transformative discipline combines data collection, storage, processing, analysis, visualization, and the utilization of machine learning techniques, empowering businesses to thrive in our data-centric modern world by leveraging the wealth of information available to them.
Why is big data analytics important?
Big Data Analytics is vital in today's digital age because it provides organizations with the ability to extract valuable insights from the vast volumes of data generated daily. This data, often referred to as "big data," encompasses a wide range of information from various sources, such as customer transactions, social media interactions, sensor data, and more. Without effective analytics, this data would remain largely untapped potential. By employing advanced techniques and technologies, organizations can uncover hidden patterns, trends, and correlations within their data, allowing for informed decision-making, improved operational efficiency, and the ability to gain a competitive edge in rapidly evolving markets.
Furthermore, Big Data Analytics has a profound impact on innovation and problem-solving across industries. It enables businesses to innovate in their product offerings, marketing strategies, and operational processes by providing a data-driven foundation for experimentation and improvement. Moreover, it plays a critical role in fields like healthcare, where it can lead to advancements in patient care, drug discovery, and disease prevention. In essence, Big Data Analytics is essential because it transforms data into actionable knowledge, fostering smarter decisions, greater efficiency, and continuous innovation in both the private and public sectors.
What is Big Data?
Big Data refers to extremely large and complex sets of data that exceed the capabilities of traditional data processing tools and methods. These data sets are characterized by what is often referred to as the "3Vs": volume, velocity, and variety.
-
Volume: Big Data typically involves massive amounts of data, often ranging from terabytes to petabytes or more. This data can be generated from various sources, including sensors, social media, business transactions, and more.
-
Velocity: Data is generated at an unprecedented speed in today's digital world. This real-time or near-real-time data flow requires rapid processing and analysis to derive meaningful insights and make timely decisions.
-
Variety: Big Data comes in various formats, including structured data (such as databases and spreadsheets), semi-structured data (like XML and JSON files), and unstructured data (such as text documents, social media posts, and multimedia content). Analyzing and making sense of this diverse data landscape is a fundamental challenge in Big Data.
In addition to the 3Vs, Big Data is often associated with two more characteristics:
-
Variability: Data can be inconsistent and vary in its format and quality over time.
-
Veracity: Ensuring the accuracy and reliability of Big Data can be a challenge, as data may contain errors or inconsistencies.
Effectively managing, storing, processing, and analyzing Big Data is crucial for organizations looking to gain valuable insights, make data-driven decisions, and derive business value from this wealth of information. This has led to the development of specialized technologies and tools, such as distributed computing frameworks like Hadoop and advanced analytics techniques like machine learning, to handle the unique challenges posed by Big Data.
Uses and Examples of Big Data Analytics
Big Data Analytics serves as a powerful tool across various industries by harnessing the vast volumes of data generated in today's digital age. One of its primary applications is in the realm of business intelligence and analytics, where organizations leverage it to gain a deeper understanding of their operations, customers, and markets. For instance, retail companies employ Big Data Analytics to analyze sales data and customer purchase patterns, enabling them to optimize inventory management and design personalized marketing campaigns. This data-driven approach enhances decision-making, helping businesses remain competitive and agile in rapidly evolving markets.
Another significant use of Big Data Analytics is in healthcare, where it aids in patient care and disease management. By analyzing electronic health records and medical data, healthcare providers can make more accurate diagnoses, recommend tailored treatment plans, and predict disease outbreaks. This application not only improves patient outcomes but also contributes to the overall efficiency of healthcare systems. In essence, Big Data Analytics is a multidimensional tool that empowers organizations to transform raw data into actionable insights, driving innovation, efficiency, and informed decision-making across a wide spectrum of industries and sectors.
History of Big Data Analytics
The history of Big Data Analytics can be traced back to the early days of computing, but it has evolved significantly over time. Here's an overview of its key milestones:
-
1950s-1960s: The concept of data processing and analysis emerged with the advent of computers. Early mainframe computers were used for basic data processing tasks, such as sorting and aggregating large volumes of data.
-
1970s-1980s: The development of relational database management systems (RDBMS) marked a significant step forward. SQL (Structured Query Language) became the standard for querying and managing structured data. However, these systems had limitations in handling large and complex datasets.
-
1990s: Data warehousing gained prominence as organizations started collecting and storing vast amounts of data. Data warehousing solutions allowed for the consolidation of data from various sources, making it easier to analyze and report on.
-
Early 2000s: The term "Big Data" began to gain traction as companies like Google and Yahoo faced challenges in managing and analyzing massive datasets. Google's MapReduce and the Hadoop Distributed File System (HDFS) were pivotal in developing scalable solutions for processing Big Data.
-
Mid-2000s: Apache Hadoop, an open-source framework, emerged as a leading platform for processing and analyzing large datasets. It popularized the idea of distributed computing and laid the foundation for Big Data Analytics.
-
Late 2000s-2010s: As organizations generated more data from various sources, technologies for Big Data Analytics continued to advance. Companies like Amazon, Facebook, and Netflix demonstrated the power of data-driven decision-making and personalized user experiences.
-
2010s-Present: Machine learning and artificial intelligence (AI) have become integral to Big Data Analytics. These technologies enable predictive analytics, anomaly detection, and automation of data analysis tasks. Cloud computing services, such as Amazon Web Services (AWS) and Microsoft Azure, offer scalable platforms for Big Data processing and storage.
-
2020s: Big Data Analytics continues to evolve with a focus on real-time data processing, edge computing, and privacy considerations. Data governance and ethical use of data have also gained prominence.
Throughout its history, Big Data Analytics has transformed from a niche concept to a critical component of decision-making in various industries, ranging from finance and healthcare to e-commerce and entertainment. As data continues to grow in volume and complexity, the field of Big Data Analytics will likely continue to evolve and adapt to meet the ever-expanding demands of the digital age.
Benefits and Advantages of Big Data Analytics
Big Data Analytics offers numerous benefits and advantages to organizations across various industries. Here are some of the key advantages:
-
Data-Driven Decision-Making: Big Data Analytics empowers organizations to make informed decisions based on real data rather than intuition or guesswork. This leads to more accurate and effective choices in various aspects of business operations.
-
Competitive Advantage: Companies that leverage Big Data Analytics gain a competitive edge by identifying market trends, customer preferences, and emerging opportunities faster and more accurately than their competitors.
-
Improved Operational Efficiency: By analyzing processes and operations, organizations can identify bottlenecks, inefficiencies, and areas for improvement. This optimization leads to cost reduction and enhanced productivity.
-
Enhanced Customer Experiences: Understanding customer behavior and preferences allows businesses to personalize products, services, and marketing campaigns. This leads to higher customer satisfaction and loyalty.
-
Risk Management: In industries like finance and insurance, Big Data Analytics aids in assessing and mitigating risks more effectively. It can detect anomalies and potential issues early, helping prevent financial losses.
The Lifecycle Phases of Big Data Analytics
The eight key stages in the lifecycle of Big Data Analytics:
-
Data Collection: Gather data from various sources, such as databases, sensors, or social media.
-
Data Storage: Organize and store the data in suitable repositories like data lakes or warehouses.
-
Data Preprocessing: Clean, transform, and prepare the data for analysis to ensure quality and consistency.
-
Data Analysis: Apply statistical and machine learning techniques to extract insights from the data.
-
Data Visualization: Present the results through charts, graphs, and dashboards for better understanding.
-
Deployment: Implement analytical models into production systems for real-time decision-making.
-
Monitoring: Continuously oversee model performance and data quality.
-
Optimization: Fine-tune models and scale infrastructure to handle increased data demands.
Different Types of Big Data Analytics
Big Data Analytics encompasses various types of analytical approaches, each tailored to address specific business or data challenges. Here are different types of Big Data Analytics:
-
Descriptive Analytics:
-
Purpose: Descriptive analytics focuses on summarizing historical data to provide insights into past trends and events.
-
Use Cases: It helps organizations understand what has happened in the past, such as sales trends, customer behavior, or website traffic patterns.
-
Diagnostic Analytics:
-
Purpose: Diagnostic analytics aims to identify the reasons behind past events or trends.
-
Use Cases: It helps uncover the causes of specific outcomes, such as understanding why sales dropped in a particular region or why a marketing campaign failed.
-
Predictive Analytics:
-
Purpose: Predictive analytics uses historical data and statistical algorithms to forecast future outcomes or trends.
-
Use Cases: Organizations use predictive analytics for demand forecasting, customer churn prediction, fraud detection, and inventory optimization.
-
Prescriptive Analytics:
-
Purpose: Prescriptive analytics goes beyond prediction by suggesting the best course of action to optimize outcomes.
-
Use Cases: It helps organizations make data-driven decisions by recommending actions based on predictive models. For instance, it can suggest pricing strategies to maximize profits.
Top of Form
Big Data Analytics Tools
Big Data Analytics tools are essential for processing, analyzing, and deriving insights from large and complex datasets. There are numerous tools available, each with its own strengths and capabilities. Here's a list of some popular Big Data Analytics tools:
-
Hadoop:
-
Description: Hadoop is an open-source framework that facilitates distributed storage and processing of large datasets across clusters of commodity hardware.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for storage and MapReduce for parallel processing. Additionally, it offers various ecosystem components like Hive, Pig, and Spark for advanced analytics.
-
Apache Spark:
-
Description: Apache Spark is an open-source, distributed computing framework that provides high-speed, in-memory data processing capabilities.
-
Key Features: Spark offers libraries for machine learning (MLlib), graph processing (GraphX), and stream processing (Structured Streaming). It's known for its speed and versatility in processing both batch and real-time data.
-
Apache Flink:
-
Description: Apache Flink is an open-source stream processing framework designed for real-time data analytics.
-
Key Features: Flink provides event time processing, support for batch and stream processing, and stateful computations. It's commonly used in applications requiring low-latency, high-throughput data processing.
-
Apache Kafka:
-
Description: Apache Kafka is a distributed streaming platform used for building real-time data pipelines and event-driven applications.
-
Key Features: Kafka is known for its high throughput, fault tolerance, and scalability. It allows for the ingestion and processing of large volumes of streaming data.
-
Hive:
-
Description: Hive is a data warehousing and SQL-like query language system built on top of Hadoop for structured data analysis.
-
Key Features: Hive provides a familiar SQL interface for querying data stored in Hadoop, making it accessible to analysts and data scientists.
-
Pig:
-
Description: Apache Pig is a high-level scripting platform for data analysis and processing in Hadoop.
-
Key Features: Pig provides a simple scripting language called Pig Latin, which allows users to express data transformations and processing logic.
-
R and RStudio:
-
Description: R is a programming language and environment specifically designed for statistical analysis and data visualization.
-
Key Features: R, along with RStudio as an integrated development environment (IDE), offers a rich ecosystem of packages and libraries for data analysis, statistical modeling, and data visualization.
Big Data Industry Applications
The applications of Big Data analytics span across a wide range of industries, offering transformative solutions to various challenges. Here are some notable industry-specific applications:
-
Healthcare:
-
Electronic Health Records (EHRs): Analyzing patient data in EHRs to improve diagnoses, treatment plans, and patient outcomes.
-
Disease Prediction: Predicting disease outbreaks, identifying high-risk populations, and improving public health strategies.
-
Drug Discovery: Accelerating drug development by analyzing genomics data and identifying potential drug candidates.
-
Finance:
-
Risk Assessment: Using data analytics to assess credit risks, detect fraudulent transactions, and manage investment portfolios.
-
Algorithmic Trading: Employing data-driven algorithms to make real-time trading decisions in financial markets.
-
Customer Segmentation: Analyzing customer data to tailor financial products and services for different segments.
-
Retail and E-commerce:
-
Recommendation Systems: Offering personalized product recommendations based on customer behavior and preferences.
-
Inventory Management: Optimizing inventory levels to reduce costs and prevent stockouts.
-
Pricing Optimization: Dynamically adjusting prices based on demand and market conditions.
-
Manufacturing:
-
Predictive Maintenance: Monitoring equipment sensors to predict and prevent machine failures and reduce downtime.
-
Quality Control: Analyzing production data to identify defects and improve product quality.
-
Supply Chain Optimization: Optimizing logistics and supply chain operations to reduce costs and improve efficiency.
-
Telecommunications:
-
Network Optimization: Analyzing network data to improve network performance, reduce downtime, and enhance customer experiences.
-
Churn Prediction: Identifying and retaining at-risk customers by analyzing usage patterns and customer behavior.
FAQs
-
What is Big Data Analytics?
Big Data Analytics is the process of examining and deriving valuable insights from large and complex datasets, often referred to as "big data." It involves various techniques and technologies to uncover hidden patterns, trends, and valuable information within massive data sets.
-
Why is Big Data Analytics important in the modern world?
Big Data Analytics is crucial in the modern world because it empowers organizations to make data-driven decisions, improve operational efficiency, enhance customer experiences, manage risks effectively, and foster innovation. It enables businesses to thrive in a data-centric environment.
-
What are the key components of Big Data Analytics?
The key components of Big Data Analytics include data collection, storage, processing, analysis, visualization, machine learning and AI, scalability, real-time analytics, and more.
-
What industries benefit from Big Data Analytics?
Big Data Analytics is beneficial in various industries, including finance, healthcare, retail, manufacturing, marketing, transportation, government, and many others. It helps organizations across sectors make data-driven decisions and gain a competitive edge.
-
What are the challenges in implementing Big Data Analytics?
Challenges in implementing Big Data Analytics include data quality issues, data privacy and security concerns, the need for specialized skills and resources, and the complexity of managing and processing large volumes of data.
-
How does Big Data Analytics impact innovation?
Big Data Analytics can lead to innovation by uncovering insights, trends, and opportunities that drive new product development, marketing strategies, and business models. It fosters innovation through data-driven decision-making.
-
What role does machine learning play in Big Data Analytics?
Machine learning is a crucial component of Big Data Analytics. It automates and enhances data analysis, enabling predictive modeling, classification, and the discovery of patterns and anomalies in large datasets.
-
What is the significance of real-time analytics in Big Data?
Real-time analytics in Big Data enables organizations to analyze and act on data as it's generated, allowing for immediate decision-making, such as fraud detection, customer support, and monitoring of critical systems.
-
How can organizations get started with Big Data Analytics?
Organizations can start with Big Data Analytics by defining their goals, assessing data needs, building the necessary infrastructure, acquiring analytical tools and talent, and formulating a data strategy aligned with their business objectives.
-
What are the ethical considerations in Big Data Analytics?
Ethical considerations in Big Data Analytics include data privacy, transparency, fairness, and responsible data handling. Organizations should adhere to ethical guidelines to ensure the responsible use of data.
Read More
Welcome to our comprehensive guide on 'What is Big Data Analytics and What is Its Significance in the Modern World?' In this in-depth exploration, we delve into the realm of big data analytics, shedding light on its fundamental concepts, applications, and its paramount importance in our contemporary data-driven society. Join us as we unravel the intricacies of this transformative technology and unveil its profound impact on businesses, industries, and society as a whole.
Table of Contents
What is Big Data Analytics?
Why is big data analytics important?
What is Big Data?
Uses and Examples of Big Data Analytics
History of Big Data Analytics
Benefits and Advantages of Big Data Analytics
The Lifecycle Phases of Big Data Analytics
Different Types of Big Data Analytics
Big Data Analytics Tools
Big Data Industry Applications
FAQs
What is Big Data Analytics?
Big Data Analytics is the process of extracting valuable insights from vast and complex data sets, enabling organizations to make data-driven decisions, enhance operational efficiency, improve customer experiences, manage risks effectively, and foster innovation across various industries. This transformative discipline combines data collection, storage, processing, analysis, visualization, and the utilization of machine learning techniques, empowering businesses to thrive in our data-centric modern world by leveraging the wealth of information available to them.
Why is big data analytics important?
Big Data Analytics is vital in today's digital age because it provides organizations with the ability to extract valuable insights from the vast volumes of data generated daily. This data, often referred to as "big data," encompasses a wide range of information from various sources, such as customer transactions, social media interactions, sensor data, and more. Without effective analytics, this data would remain largely untapped potential. By employing advanced techniques and technologies, organizations can uncover hidden patterns, trends, and correlations within their data, allowing for informed decision-making, improved operational efficiency, and the ability to gain a competitive edge in rapidly evolving markets.
Furthermore, Big Data Analytics has a profound impact on innovation and problem-solving across industries. It enables businesses to innovate in their product offerings, marketing strategies, and operational processes by providing a data-driven foundation for experimentation and improvement. Moreover, it plays a critical role in fields like healthcare, where it can lead to advancements in patient care, drug discovery, and disease prevention. In essence, Big Data Analytics is essential because it transforms data into actionable knowledge, fostering smarter decisions, greater efficiency, and continuous innovation in both the private and public sectors.
What is Big Data?
Big Data refers to extremely large and complex sets of data that exceed the capabilities of traditional data processing tools and methods. These data sets are characterized by what is often referred to as the "3Vs": volume, velocity, and variety.
-
Volume: Big Data typically involves massive amounts of data, often ranging from terabytes to petabytes or more. This data can be generated from various sources, including sensors, social media, business transactions, and more.
-
Velocity: Data is generated at an unprecedented speed in today's digital world. This real-time or near-real-time data flow requires rapid processing and analysis to derive meaningful insights and make timely decisions.
-
Variety: Big Data comes in various formats, including structured data (such as databases and spreadsheets), semi-structured data (like XML and JSON files), and unstructured data (such as text documents, social media posts, and multimedia content). Analyzing and making sense of this diverse data landscape is a fundamental challenge in Big Data.
In addition to the 3Vs, Big Data is often associated with two more characteristics:
-
Variability: Data can be inconsistent and vary in its format and quality over time.
-
Veracity: Ensuring the accuracy and reliability of Big Data can be a challenge, as data may contain errors or inconsistencies.
Effectively managing, storing, processing, and analyzing Big Data is crucial for organizations looking to gain valuable insights, make data-driven decisions, and derive business value from this wealth of information. This has led to the development of specialized technologies and tools, such as distributed computing frameworks like Hadoop and advanced analytics techniques like machine learning, to handle the unique challenges posed by Big Data.
Uses and Examples of Big Data Analytics
Big Data Analytics serves as a powerful tool across various industries by harnessing the vast volumes of data generated in today's digital age. One of its primary applications is in the realm of business intelligence and analytics, where organizations leverage it to gain a deeper understanding of their operations, customers, and markets. For instance, retail companies employ Big Data Analytics to analyze sales data and customer purchase patterns, enabling them to optimize inventory management and design personalized marketing campaigns. This data-driven approach enhances decision-making, helping businesses remain competitive and agile in rapidly evolving markets.
Another significant use of Big Data Analytics is in healthcare, where it aids in patient care and disease management. By analyzing electronic health records and medical data, healthcare providers can make more accurate diagnoses, recommend tailored treatment plans, and predict disease outbreaks. This application not only improves patient outcomes but also contributes to the overall efficiency of healthcare systems. In essence, Big Data Analytics is a multidimensional tool that empowers organizations to transform raw data into actionable insights, driving innovation, efficiency, and informed decision-making across a wide spectrum of industries and sectors.
History of Big Data Analytics
The history of Big Data Analytics can be traced back to the early days of computing, but it has evolved significantly over time. Here's an overview of its key milestones:
-
1950s-1960s: The concept of data processing and analysis emerged with the advent of computers. Early mainframe computers were used for basic data processing tasks, such as sorting and aggregating large volumes of data.
-
1970s-1980s: The development of relational database management systems (RDBMS) marked a significant step forward. SQL (Structured Query Language) became the standard for querying and managing structured data. However, these systems had limitations in handling large and complex datasets.
-
1990s: Data warehousing gained prominence as organizations started collecting and storing vast amounts of data. Data warehousing solutions allowed for the consolidation of data from various sources, making it easier to analyze and report on.
-
Early 2000s: The term "Big Data" began to gain traction as companies like Google and Yahoo faced challenges in managing and analyzing massive datasets. Google's MapReduce and the Hadoop Distributed File System (HDFS) were pivotal in developing scalable solutions for processing Big Data.
-
Mid-2000s: Apache Hadoop, an open-source framework, emerged as a leading platform for processing and analyzing large datasets. It popularized the idea of distributed computing and laid the foundation for Big Data Analytics.
-
Late 2000s-2010s: As organizations generated more data from various sources, technologies for Big Data Analytics continued to advance. Companies like Amazon, Facebook, and Netflix demonstrated the power of data-driven decision-making and personalized user experiences.
-
2010s-Present: Machine learning and artificial intelligence (AI) have become integral to Big Data Analytics. These technologies enable predictive analytics, anomaly detection, and automation of data analysis tasks. Cloud computing services, such as Amazon Web Services (AWS) and Microsoft Azure, offer scalable platforms for Big Data processing and storage.
-
2020s: Big Data Analytics continues to evolve with a focus on real-time data processing, edge computing, and privacy considerations. Data governance and ethical use of data have also gained prominence.
Throughout its history, Big Data Analytics has transformed from a niche concept to a critical component of decision-making in various industries, ranging from finance and healthcare to e-commerce and entertainment. As data continues to grow in volume and complexity, the field of Big Data Analytics will likely continue to evolve and adapt to meet the ever-expanding demands of the digital age.
Benefits and Advantages of Big Data Analytics
Big Data Analytics offers numerous benefits and advantages to organizations across various industries. Here are some of the key advantages:
-
Data-Driven Decision-Making: Big Data Analytics empowers organizations to make informed decisions based on real data rather than intuition or guesswork. This leads to more accurate and effective choices in various aspects of business operations.
-
Competitive Advantage: Companies that leverage Big Data Analytics gain a competitive edge by identifying market trends, customer preferences, and emerging opportunities faster and more accurately than their competitors.
-
Improved Operational Efficiency: By analyzing processes and operations, organizations can identify bottlenecks, inefficiencies, and areas for improvement. This optimization leads to cost reduction and enhanced productivity.
-
Enhanced Customer Experiences: Understanding customer behavior and preferences allows businesses to personalize products, services, and marketing campaigns. This leads to higher customer satisfaction and loyalty.
-
Risk Management: In industries like finance and insurance, Big Data Analytics aids in assessing and mitigating risks more effectively. It can detect anomalies and potential issues early, helping prevent financial losses.
The Lifecycle Phases of Big Data Analytics
The eight key stages in the lifecycle of Big Data Analytics:
-
Data Collection: Gather data from various sources, such as databases, sensors, or social media.
-
Data Storage: Organize and store the data in suitable repositories like data lakes or warehouses.
-
Data Preprocessing: Clean, transform, and prepare the data for analysis to ensure quality and consistency.
-
Data Analysis: Apply statistical and machine learning techniques to extract insights from the data.
-
Data Visualization: Present the results through charts, graphs, and dashboards for better understanding.
-
Deployment: Implement analytical models into production systems for real-time decision-making.
-
Monitoring: Continuously oversee model performance and data quality.
-
Optimization: Fine-tune models and scale infrastructure to handle increased data demands.
Different Types of Big Data Analytics
Big Data Analytics encompasses various types of analytical approaches, each tailored to address specific business or data challenges. Here are different types of Big Data Analytics:
-
Descriptive Analytics:
-
Purpose: Descriptive analytics focuses on summarizing historical data to provide insights into past trends and events.
-
Use Cases: It helps organizations understand what has happened in the past, such as sales trends, customer behavior, or website traffic patterns.
-
-
Diagnostic Analytics:
-
Purpose: Diagnostic analytics aims to identify the reasons behind past events or trends.
-
Use Cases: It helps uncover the causes of specific outcomes, such as understanding why sales dropped in a particular region or why a marketing campaign failed.
-
-
Predictive Analytics:
-
Purpose: Predictive analytics uses historical data and statistical algorithms to forecast future outcomes or trends.
-
Use Cases: Organizations use predictive analytics for demand forecasting, customer churn prediction, fraud detection, and inventory optimization.
-
-
Prescriptive Analytics:
-
Purpose: Prescriptive analytics goes beyond prediction by suggesting the best course of action to optimize outcomes.
-
Use Cases: It helps organizations make data-driven decisions by recommending actions based on predictive models. For instance, it can suggest pricing strategies to maximize profits.
-
Top of Form
Big Data Analytics Tools
Big Data Analytics tools are essential for processing, analyzing, and deriving insights from large and complex datasets. There are numerous tools available, each with its own strengths and capabilities. Here's a list of some popular Big Data Analytics tools:
-
Hadoop:
-
Description: Hadoop is an open-source framework that facilitates distributed storage and processing of large datasets across clusters of commodity hardware.
-
Key Features: Hadoop includes the Hadoop Distributed File System (HDFS) for storage and MapReduce for parallel processing. Additionally, it offers various ecosystem components like Hive, Pig, and Spark for advanced analytics.
-
-
Apache Spark:
-
Description: Apache Spark is an open-source, distributed computing framework that provides high-speed, in-memory data processing capabilities.
-
Key Features: Spark offers libraries for machine learning (MLlib), graph processing (GraphX), and stream processing (Structured Streaming). It's known for its speed and versatility in processing both batch and real-time data.
-
-
Apache Flink:
-
Description: Apache Flink is an open-source stream processing framework designed for real-time data analytics.
-
Key Features: Flink provides event time processing, support for batch and stream processing, and stateful computations. It's commonly used in applications requiring low-latency, high-throughput data processing.
-
-
Apache Kafka:
-
Description: Apache Kafka is a distributed streaming platform used for building real-time data pipelines and event-driven applications.
-
Key Features: Kafka is known for its high throughput, fault tolerance, and scalability. It allows for the ingestion and processing of large volumes of streaming data.
-
-
Hive:
-
Description: Hive is a data warehousing and SQL-like query language system built on top of Hadoop for structured data analysis.
-
Key Features: Hive provides a familiar SQL interface for querying data stored in Hadoop, making it accessible to analysts and data scientists.
-
-
Pig:
-
Description: Apache Pig is a high-level scripting platform for data analysis and processing in Hadoop.
-
Key Features: Pig provides a simple scripting language called Pig Latin, which allows users to express data transformations and processing logic.
-
-
R and RStudio:
-
Description: R is a programming language and environment specifically designed for statistical analysis and data visualization.
-
Key Features: R, along with RStudio as an integrated development environment (IDE), offers a rich ecosystem of packages and libraries for data analysis, statistical modeling, and data visualization.
-
Big Data Industry Applications
The applications of Big Data analytics span across a wide range of industries, offering transformative solutions to various challenges. Here are some notable industry-specific applications:
-
Healthcare:
-
Electronic Health Records (EHRs): Analyzing patient data in EHRs to improve diagnoses, treatment plans, and patient outcomes.
-
Disease Prediction: Predicting disease outbreaks, identifying high-risk populations, and improving public health strategies.
-
Drug Discovery: Accelerating drug development by analyzing genomics data and identifying potential drug candidates.
-
-
Finance:
-
Risk Assessment: Using data analytics to assess credit risks, detect fraudulent transactions, and manage investment portfolios.
-
Algorithmic Trading: Employing data-driven algorithms to make real-time trading decisions in financial markets.
-
Customer Segmentation: Analyzing customer data to tailor financial products and services for different segments.
-
-
Retail and E-commerce:
-
Recommendation Systems: Offering personalized product recommendations based on customer behavior and preferences.
-
Inventory Management: Optimizing inventory levels to reduce costs and prevent stockouts.
-
Pricing Optimization: Dynamically adjusting prices based on demand and market conditions.
-
-
Manufacturing:
-
Predictive Maintenance: Monitoring equipment sensors to predict and prevent machine failures and reduce downtime.
-
Quality Control: Analyzing production data to identify defects and improve product quality.
-
Supply Chain Optimization: Optimizing logistics and supply chain operations to reduce costs and improve efficiency.
-
-
Telecommunications:
-
Network Optimization: Analyzing network data to improve network performance, reduce downtime, and enhance customer experiences.
-
Churn Prediction: Identifying and retaining at-risk customers by analyzing usage patterns and customer behavior.
-
FAQs
-
What is Big Data Analytics?
Big Data Analytics is the process of examining and deriving valuable insights from large and complex datasets, often referred to as "big data." It involves various techniques and technologies to uncover hidden patterns, trends, and valuable information within massive data sets.
-
Why is Big Data Analytics important in the modern world?
Big Data Analytics is crucial in the modern world because it empowers organizations to make data-driven decisions, improve operational efficiency, enhance customer experiences, manage risks effectively, and foster innovation. It enables businesses to thrive in a data-centric environment.
-
What are the key components of Big Data Analytics?
The key components of Big Data Analytics include data collection, storage, processing, analysis, visualization, machine learning and AI, scalability, real-time analytics, and more.
-
What industries benefit from Big Data Analytics?
Big Data Analytics is beneficial in various industries, including finance, healthcare, retail, manufacturing, marketing, transportation, government, and many others. It helps organizations across sectors make data-driven decisions and gain a competitive edge.
-
What are the challenges in implementing Big Data Analytics?
Challenges in implementing Big Data Analytics include data quality issues, data privacy and security concerns, the need for specialized skills and resources, and the complexity of managing and processing large volumes of data.
-
How does Big Data Analytics impact innovation?
Big Data Analytics can lead to innovation by uncovering insights, trends, and opportunities that drive new product development, marketing strategies, and business models. It fosters innovation through data-driven decision-making.
-
What role does machine learning play in Big Data Analytics?
Machine learning is a crucial component of Big Data Analytics. It automates and enhances data analysis, enabling predictive modeling, classification, and the discovery of patterns and anomalies in large datasets.
-
What is the significance of real-time analytics in Big Data?
Real-time analytics in Big Data enables organizations to analyze and act on data as it's generated, allowing for immediate decision-making, such as fraud detection, customer support, and monitoring of critical systems.
-
How can organizations get started with Big Data Analytics?
Organizations can start with Big Data Analytics by defining their goals, assessing data needs, building the necessary infrastructure, acquiring analytical tools and talent, and formulating a data strategy aligned with their business objectives.
-
What are the ethical considerations in Big Data Analytics?
Ethical considerations in Big Data Analytics include data privacy, transparency, fairness, and responsible data handling. Organizations should adhere to ethical guidelines to ensure the responsible use of data.
What is AWS Devops? - A Comprehensive Guide
In today's fast-paced digital landscape, businesses strive to deliver high-quality software products and services with utmost efficiency and speed. To achieve this goal, organizations increasingly turn to cloud computing and automation tools that enable seamless collaboration between development and operations teams. One such powerful combination is Amazon Web Services (AWS) and DevOps.
AWS, the leading cloud services provider, offers a wide array of scalable and flexible solutions that can empower businesses to innovate, deploy, and operate applications more efficiently. DevOps, on the other hand, is a set of practices that fosters collaboration, integration, and automation between software development and IT operations teams. It aims to streamline the software delivery process and enhance the overall agility and reliability of applications.
In this comprehensive guide, we will delve into the world of AWS DevOps and explore how these two concepts intersect to revolutionize the software development lifecycle. We will provide you with a solid understanding of the core principles, tools, and best practices that underpin AWS DevOps, equipping you with the knowledge to leverage this powerful combination in your own organization.
Throughout this guide, we will cover a wide range of topics, including:
Introduction to AWS: We will introduce you to the key services and features provided by AWS, emphasizing their relevance and impact on the DevOps philosophy.
Fundamentals of DevOps: We will explore the core principles and values of DevOps, highlighting the benefits of adopting this culture and methodology in your organization.
AWS DevOps Tools and Services: We will dive into the various AWS tools and services that facilitate the implementation of DevOps practices. From version control and continuous integration to infrastructure automation and monitoring, we will explore how these tools can enhance your development and operational workflows.
Continuous Integration and Continuous Delivery (CI/CD): We will examine the concepts and practices of CI/CD, demonstrating how AWS services can enable seamless automation and rapid deployment of software changes.
Infrastructure as Code (IaC): We will delve into the concept of IaC, exploring how AWS CloudFormation and other tools can help you define and manage your infrastructure as easily reproducible code.
Scalability and Resilience: We will discuss how AWS's elastic and scalable infrastructure can help you build resilient and highly available systems, ensuring your applications can handle varying workloads and remain operational even in the face of failures.
Security and Compliance: We will address the crucial aspects of security and compliance in the AWS DevOps environment, covering best practices, tools, and services to ensure the protection of your applications and data.
Table of Contents
- Understanding AWS DevOps
- Key components of AWS DevOps
- AWS DevOps tools
- Implementing AWS DevOps
- Benefits of AWS DevOps
- Limitations of AWS DevOps
- Future of AWS DevOps
- Conclusion
Understanding AWS DevOps
AWS DevOps is a powerful combination of Amazon Web Services (AWS) cloud services and DevOps practices that enables organizations to streamline their software development and deployment processes. It brings together the benefits of AWS's scalable and flexible infrastructure with the collaborative and automated principles of DevOps, resulting in increased agility, faster time-to-market, and improved operational efficiency.
At its core, DevOps is a cultural and operational philosophy that encourages close collaboration between software development teams and IT operations teams. It aims to break down the traditional silos between these two groups, promoting a shared responsibility for the entire software lifecycle, from development and testing to deployment and monitoring. DevOps emphasizes automation, continuous integration, continuous delivery, and infrastructure as code to achieve faster and more reliable software delivery.
AWS, as one of the leading cloud service providers, offers a comprehensive suite of services and tools that align perfectly with DevOps principles. These services enable organizations to build, deploy, and operate applications and infrastructure in a highly scalable, secure, and reliable manner. Some of the key AWS services that play a vital role in AWS DevOps are:
Amazon Elastic Compute Cloud (EC2): EC2 provides resizable compute capacity in the cloud, allowing organizations to quickly provision virtual servers and scale their infrastructure up or down as needed.
AWS Lambda: Lambda is a serverless computing service that enables developers to run code without provisioning or managing servers. It facilitates the creation of highly scalable and event-driven applications.
AWS Elastic Beanstalk: Elastic Beanstalk simplifies the deployment and management of applications by automatically handling the underlying infrastructure and platform configuration. It supports multiple programming languages and frameworks.
AWS CodePipeline: CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service that automates the release process for applications. It integrates with various AWS services and third-party tools to build, test, and deploy code changes.
AWS CloudFormation: CloudFormation allows you to define and provision AWS infrastructure resources using declarative templates. It enables infrastructure as code, making it easier to manage and reproduce environments.
Amazon CloudWatch: CloudWatch provides monitoring and observability for AWS resources and applications. It collects and analyzes log files, sets alarms, and generates metrics, enabling proactive monitoring and troubleshooting.
Key components of AWS DevOps
AWS DevOps encompasses a range of components that work together to enable organizations to implement DevOps practices in an AWS environment. These components provide the foundation for collaboration, automation, and continuous delivery. Let's explore some of the key components of AWS DevOps:
Infrastructure as Code (IaC): Infrastructure as Code is a fundamental concept in AWS DevOps. It involves defining and provisioning infrastructure resources using code, typically in the form of templates. AWS CloudFormation is a popular service that enables you to create and manage infrastructure as code, allowing for consistent and repeatable deployments.
Continuous Integration and Continuous Delivery (CI/CD): CI/CD is a set of practices that automate the build, testing, and deployment of software changes. AWS provides various services to facilitate CI/CD pipelines. AWS CodePipeline is a fully managed service that orchestrates the continuous delivery workflow, integrating with other AWS services such as AWS CodeBuild for build automation and AWS CodeDeploy for application deployment.
Configuration Management: Configuration management tools enable organizations to manage and automate the configuration of their infrastructure and applications. AWS provides AWS Systems Manager, which allows you to manage and configure EC2 instances at scale. It also offers integration with popular configuration management tools like Chef and Puppet.
Monitoring and Logging: Monitoring and logging are crucial aspects of DevOps. AWS CloudWatch is a monitoring service that collects and tracks metrics, sets alarms, and provides insights into the performance and health of AWS resources and applications. AWS X-Ray is a service that helps trace and debug distributed applications, providing valuable insights into requests and latency.
Security and Compliance: Security and compliance are paramount in any DevOps environment. AWS provides a wide range of security services and features, including AWS Identity and Access Management (IAM) for access control, AWS Key Management Service (KMS) for encryption, and AWS Security Hub for centralized security monitoring and compliance checks.
Containerization and Orchestration: Containerization technologies like Docker and container orchestration platforms like Amazon Elastic Kubernetes Service (EKS) allow organizations to package and deploy applications in a portable and scalable manner. These tools enable the efficient management of containerized applications within the AWS ecosystem.
Serverless Computing: Serverless computing, exemplified by AWS Lambda, allows developers to run code without provisioning or managing servers. It enables rapid development and deployment of event-driven functions and microservices, promoting scalability and cost optimization.
AWS DevOps tools
AWS provides a wide range of tools and services that are specifically designed to support DevOps practices and workflows. These tools cover various aspects of the software development lifecycle, from code management and build automation to deployment and monitoring. Here are some key AWS DevOps tools:
AWS CodePipeline: CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service that enables you to automate the release process for your applications. It integrates with other AWS services and third-party tools, allowing you to build, test, and deploy code changes seamlessly.
AWS CodeCommit: CodeCommit is a fully managed source code control service that hosts private Git repositories. It provides a secure and scalable platform for collaborating on code and managing version control.
AWS CodeBuild: CodeBuild is a fully managed build service that compiles source code, runs tests, and produces ready-to-deploy software packages. It supports a wide range of programming languages and build configurations.
AWS CodeDeploy: CodeDeploy automates application deployments to various compute services, including EC2 instances, AWS Lambda functions, and on-premises servers. It simplifies the process of releasing new features and updates, ensuring consistency and minimizing downtime.
AWS CloudFormation: CloudFormation allows you to define and provision AWS infrastructure resources using templates. It enables infrastructure as code, making it easier to manage and reproduce environments consistently.
AWS Elastic Beanstalk: Elastic Beanstalk is a fully managed service that makes it easy to deploy and run applications in multiple languages and frameworks. It handles the underlying infrastructure and platform configuration, allowing developers to focus on writing code.
AWS OpsWorks: OpsWorks provides a configuration management service that uses Chef or Puppet for automating the setup and management of infrastructure resources. It simplifies the process of deploying and managing applications and server configurations.
AWS X-Ray: X-Ray is a distributed tracing service that helps developers analyze and debug applications in a microservices architecture. It provides insights into request flows and performance bottlenecks, allowing for efficient troubleshooting.
AWS Systems Manager: Systems Manager offers a unified interface for managing and configuring AWS resources at scale. It provides features such as run command, patch management, and inventory management, simplifying the operational tasks associated with maintaining infrastructure and applications.
AWS CloudWatch: CloudWatch is a monitoring and observability service that collects and tracks metrics, logs, and events from various AWS resources and applications. It provides valuable insights into system performance, availability, and resource utilization.
Implementing AWS DevOps
Implementing AWS DevOps involves a systematic approach to leverage AWS services and adopt DevOps practices to streamline software development and deployment processes. Here are some steps to consider when implementing AWS DevOps:
Define DevOps Goals: Start by identifying your organization's goals and objectives for implementing DevOps. Determine the specific areas where you want to improve, such as faster time-to-market, increased agility, or improved operational efficiency.
Assess Current Processes: Evaluate your existing software development and deployment processes. Identify bottlenecks, pain points, and areas for improvement. This assessment will help you prioritize the implementation of AWS DevOps practices.
Establish a DevOps Culture: DevOps is not just about tools; it's a cultural shift that emphasizes collaboration, shared responsibility, and continuous improvement. Foster a culture of collaboration and open communication between development and operations teams.
Plan for Infrastructure as Code: Adopt the practice of infrastructure as code (IaC) to define and provision your AWS infrastructure resources. Utilize AWS CloudFormation or other IaC tools to create declarative templates that can be version-controlled and easily reproduced.
Implement Continuous Integration and Continuous Delivery (CI/CD): Automate the build, testing, and deployment processes with CI/CD pipelines. Utilize AWS CodePipeline to orchestrate the workflow and integrate it with other AWS services like AWS CodeCommit for version control and AWS CodeBuild for building artifacts.
Embrace Automation: Automate repetitive and manual tasks using AWS services like AWS Systems Manager or AWS Lambda. Automate the provisioning and configuration of infrastructure, deployment of applications, and operational tasks to reduce errors and save time.
Implement Infrastructure Monitoring and Observability: Utilize AWS CloudWatch to monitor and gain insights into the performance, availability, and health of your infrastructure and applications. Configure alarms and notifications to proactively respond to issues.
Ensure Security and Compliance: Implement security best practices and utilize AWS security services like AWS Identity and Access Management (IAM) for access control and AWS Security Hub for centralized security monitoring. Ensure compliance with relevant regulations and industry standards.
Foster Continuous Learning and Improvement: Encourage a culture of learning and continuous improvement. Conduct post-mortems, gather feedback, and use metrics and data to identify areas for optimization. Implement feedback loops to iterate and refine your DevOps processes.
Provide Training and Support: Offer training and support to teams to ensure they have the necessary skills and knowledge to effectively utilize AWS DevOps tools and services. Provide resources, documentation, and hands-on training to enable successful adoption.
Benefits of AWS DevOps
Implementing AWS DevOps offers several significant benefits for organizations. Here are some key advantages of adopting AWS DevOps practices:
Faster Time-to-Market: AWS DevOps enables organizations to deliver software products and updates at a faster pace. Automation and streamlined processes reduce manual effort, enabling rapid development, testing, and deployment. This accelerated time-to-market allows organizations to respond quickly to market demands and gain a competitive edge.
Increased Agility and Flexibility: AWS's cloud services provide a scalable and flexible infrastructure, allowing organizations to rapidly adapt to changing business needs. With AWS DevOps, teams can dynamically provision resources, scale applications, and efficiently manage workloads, enabling them to respond swiftly to fluctuating customer demands and market conditions.
Improved Collaboration and Communication: DevOps encourages close collaboration and communication between development and operations teams. By breaking down silos and fostering a culture of shared responsibility, AWS DevOps promotes efficient information sharing, reducing misunderstandings and bottlenecks. This collaboration leads to smoother workflows, faster issue resolution, and improved overall productivity.
Enhanced Quality and Reliability: DevOps practices, such as continuous integration, automated testing, and continuous delivery, help improve the quality and reliability of software products. By automating testing and deployment processes, organizations can catch bugs and issues early, reducing the risk of defects and improving software stability. This results in higher customer satisfaction and increased confidence in the software being delivered.
Cost Optimization: AWS DevOps enables organizations to optimize their costs by leveraging cloud services efficiently. With dynamic resource provisioning and scaling, teams can optimize resource usage and pay only for what they need, avoiding overprovisioning. Additionally, automated processes and reduced manual effort lead to cost savings in terms of time and labor.
Infrastructure as Code (IaC): AWS DevOps promotes the use of infrastructure as code (IaC), which allows organizations to define and manage their infrastructure through code. This approach brings consistency, repeatability, and version control to infrastructure deployments, reducing human errors and ensuring reproducibility across different environments.
Improved Security and Compliance: AWS provides a robust security framework, and when combined with DevOps practices, organizations can enhance their overall security posture. AWS DevOps enables the implementation of security best practices, such as automated security testing, continuous monitoring, and identity and access management (IAM). This helps organizations achieve and maintain compliance with relevant regulations and standards.
Continuous Improvement: AWS DevOps promotes a culture of continuous learning and improvement. With feedback loops, monitoring, and analytics provided by AWS services, organizations can collect valuable insights and data to drive optimization. This data-driven approach allows teams to identify areas for improvement, make data-backed decisions, and iterate on their processes to achieve greater efficiency and effectiveness over time.
Limitations of AWS DevOps
While AWS DevOps offers numerous benefits, it's important to be aware of its limitations. Here are some potential limitations of AWS DevOps:
Learning Curve: Implementing AWS DevOps practices requires a certain level of knowledge and expertise in both AWS services and DevOps principles. Teams may need to invest time and resources in training and upskilling to effectively leverage AWS DevOps tools and services.
Complexity: AWS provides a vast array of services, and navigating through the various options and configurations can be complex. Designing and implementing a robust AWS DevOps architecture may require careful planning and expertise to ensure the optimal use of resources and services.
Cost Management: While AWS offers flexibility and scalability, it's important to carefully manage costs. Organizations need to monitor resource usage, optimize deployments, and select the appropriate pricing models to avoid unexpected expenses.
Dependency on Internet Connectivity: AWS is a cloud-based platform, which means it relies on internet connectivity for access and operations. Organizations should consider potential downtime or performance issues caused by internet outages or network connectivity problems.
Vendor Lock-In: Adopting AWS DevOps practices may create a dependency on AWS services and infrastructure. Migrating to an alternative cloud provider or making significant changes to the infrastructure architecture could be challenging and time-consuming.
Security and Compliance Considerations: While AWS provides robust security features, organizations are responsible for configuring and managing the security of their applications and data. Proper security configurations and compliance measures need to be implemented to ensure data protection and regulatory compliance.
Cultural Shift: Implementing DevOps practices requires a cultural shift within the organization. It may involve breaking down silos between development and operations teams, promoting collaboration, and embracing change. Overcoming resistance to change and ensuring buy-in from stakeholders can be a challenge.
Maintenance and Support: AWS DevOps requires ongoing maintenance and support to ensure the stability and performance of the infrastructure and applications. Organizations should allocate resources for monitoring, managing updates, and addressing issues that arise in the AWS environment.
Future of AWS DevOps
The future of AWS DevOps looks promising, with continued advancements and innovations expected to further enhance its capabilities. Here are some potential trends and developments that may shape the future of AWS DevOps:
Serverless Computing: Serverless architectures, exemplified by AWS Lambda, are gaining popularity as they offer scalability, reduced operational overhead, and cost efficiency. In the future, we can expect further advancements in serverless computing, enabling organizations to build and deploy applications without managing underlying infrastructure.
AI and Machine Learning Integration: AI and machine learning are increasingly being integrated into various aspects of software development and operations. In the context of AWS DevOps, we can expect AI-driven insights and automation tools that help optimize CI/CD pipelines, enhance monitoring and observability, and improve incident response and remediation processes.
Infrastructure Automation and Orchestration: As infrastructure as code (IaC) becomes more prevalent, we can expect advancements in infrastructure automation and orchestration tools within AWS DevOps. This includes more sophisticated features, improved support for multi-cloud environments, and enhanced integration with popular IaC frameworks.
Enhanced Security and Compliance: Security and compliance will remain a key focus area for AWS DevOps. We can expect further advancements in security automation, threat detection, and compliance management tools within the AWS ecosystem. Integration with AI-driven security solutions may help organizations identify and mitigate security risks more effectively.
Integration of DevOps with DataOps: The integration of DevOps and DataOps practices is likely to gain traction as organizations increasingly focus on managing and leveraging their data assets. AWS services like Amazon Redshift, AWS Glue, and Amazon EMR will play a crucial role in enabling efficient data operations within DevOps workflows.
Advanced Observability and Monitoring: Observability and monitoring will continue to evolve, providing more granular insights into applications and infrastructure performance. Advanced tracing, logging, and distributed tracing capabilities will be integrated into AWS DevOps tools, allowing organizations to identify and resolve issues more efficiently.
Focus on Developer Experience: AWS DevOps tools and services will likely prioritize the developer experience, providing improved user interfaces, better integration with popular development tools, and enhanced collaboration features. The goal will be to make it easier and more efficient for developers to adopt and utilize AWS DevOps practices.
Cross-platform and Hybrid Cloud Support: As organizations increasingly adopt hybrid and multi-cloud strategies, AWS DevOps will likely evolve to provide better support for managing and orchestrating deployments across different cloud platforms. Integration with other cloud providers and on-premises environments will be enhanced, enabling seamless workflows and deployments.
Conclusion
In conclusion, AWS DevOps offers organizations a powerful set of tools and practices to streamline software development and deployment processes. By leveraging AWS services, organizations can achieve faster time-to-market, increased agility, improved collaboration, and enhanced quality and reliability.
While there are limitations to consider, such as the learning curve and complexity of AWS services, proper planning, training, and expertise can help mitigate these challenges.
Looking towards the future, AWS DevOps is expected to evolve and embrace trends such as serverless computing, AI integration, advanced observability, and enhanced security and compliance. The focus on developer experience and support for hybrid and multi-cloud environments will also play a significant role in shaping the future of AWS DevOps.
Overall, AWS DevOps enables organizations to deliver software products with speed, scalability, and reliability, empowering them to stay competitive in today's rapidly changing digital landscape. By embracing AWS DevOps practices and staying informed about emerging trends, organizations can maximize the benefits and drive continuous improvement in their software development and deployment processes.
Read More
In today's fast-paced digital landscape, businesses strive to deliver high-quality software products and services with utmost efficiency and speed. To achieve this goal, organizations increasingly turn to cloud computing and automation tools that enable seamless collaboration between development and operations teams. One such powerful combination is Amazon Web Services (AWS) and DevOps.
AWS, the leading cloud services provider, offers a wide array of scalable and flexible solutions that can empower businesses to innovate, deploy, and operate applications more efficiently. DevOps, on the other hand, is a set of practices that fosters collaboration, integration, and automation between software development and IT operations teams. It aims to streamline the software delivery process and enhance the overall agility and reliability of applications.
In this comprehensive guide, we will delve into the world of AWS DevOps and explore how these two concepts intersect to revolutionize the software development lifecycle. We will provide you with a solid understanding of the core principles, tools, and best practices that underpin AWS DevOps, equipping you with the knowledge to leverage this powerful combination in your own organization.
Throughout this guide, we will cover a wide range of topics, including:
Introduction to AWS: We will introduce you to the key services and features provided by AWS, emphasizing their relevance and impact on the DevOps philosophy.
Fundamentals of DevOps: We will explore the core principles and values of DevOps, highlighting the benefits of adopting this culture and methodology in your organization.
AWS DevOps Tools and Services: We will dive into the various AWS tools and services that facilitate the implementation of DevOps practices. From version control and continuous integration to infrastructure automation and monitoring, we will explore how these tools can enhance your development and operational workflows.
Continuous Integration and Continuous Delivery (CI/CD): We will examine the concepts and practices of CI/CD, demonstrating how AWS services can enable seamless automation and rapid deployment of software changes.
Infrastructure as Code (IaC): We will delve into the concept of IaC, exploring how AWS CloudFormation and other tools can help you define and manage your infrastructure as easily reproducible code.
Scalability and Resilience: We will discuss how AWS's elastic and scalable infrastructure can help you build resilient and highly available systems, ensuring your applications can handle varying workloads and remain operational even in the face of failures.
Security and Compliance: We will address the crucial aspects of security and compliance in the AWS DevOps environment, covering best practices, tools, and services to ensure the protection of your applications and data.
Table of Contents
- Understanding AWS DevOps
- Key components of AWS DevOps
- AWS DevOps tools
- Implementing AWS DevOps
- Benefits of AWS DevOps
- Limitations of AWS DevOps
- Future of AWS DevOps
- Conclusion
Understanding AWS DevOps
AWS DevOps is a powerful combination of Amazon Web Services (AWS) cloud services and DevOps practices that enables organizations to streamline their software development and deployment processes. It brings together the benefits of AWS's scalable and flexible infrastructure with the collaborative and automated principles of DevOps, resulting in increased agility, faster time-to-market, and improved operational efficiency.
At its core, DevOps is a cultural and operational philosophy that encourages close collaboration between software development teams and IT operations teams. It aims to break down the traditional silos between these two groups, promoting a shared responsibility for the entire software lifecycle, from development and testing to deployment and monitoring. DevOps emphasizes automation, continuous integration, continuous delivery, and infrastructure as code to achieve faster and more reliable software delivery.
AWS, as one of the leading cloud service providers, offers a comprehensive suite of services and tools that align perfectly with DevOps principles. These services enable organizations to build, deploy, and operate applications and infrastructure in a highly scalable, secure, and reliable manner. Some of the key AWS services that play a vital role in AWS DevOps are:
Amazon Elastic Compute Cloud (EC2): EC2 provides resizable compute capacity in the cloud, allowing organizations to quickly provision virtual servers and scale their infrastructure up or down as needed.
AWS Lambda: Lambda is a serverless computing service that enables developers to run code without provisioning or managing servers. It facilitates the creation of highly scalable and event-driven applications.
AWS Elastic Beanstalk: Elastic Beanstalk simplifies the deployment and management of applications by automatically handling the underlying infrastructure and platform configuration. It supports multiple programming languages and frameworks.
AWS CodePipeline: CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service that automates the release process for applications. It integrates with various AWS services and third-party tools to build, test, and deploy code changes.
AWS CloudFormation: CloudFormation allows you to define and provision AWS infrastructure resources using declarative templates. It enables infrastructure as code, making it easier to manage and reproduce environments.
Amazon CloudWatch: CloudWatch provides monitoring and observability for AWS resources and applications. It collects and analyzes log files, sets alarms, and generates metrics, enabling proactive monitoring and troubleshooting.
Key components of AWS DevOps
AWS DevOps encompasses a range of components that work together to enable organizations to implement DevOps practices in an AWS environment. These components provide the foundation for collaboration, automation, and continuous delivery. Let's explore some of the key components of AWS DevOps:
Infrastructure as Code (IaC): Infrastructure as Code is a fundamental concept in AWS DevOps. It involves defining and provisioning infrastructure resources using code, typically in the form of templates. AWS CloudFormation is a popular service that enables you to create and manage infrastructure as code, allowing for consistent and repeatable deployments.
Continuous Integration and Continuous Delivery (CI/CD): CI/CD is a set of practices that automate the build, testing, and deployment of software changes. AWS provides various services to facilitate CI/CD pipelines. AWS CodePipeline is a fully managed service that orchestrates the continuous delivery workflow, integrating with other AWS services such as AWS CodeBuild for build automation and AWS CodeDeploy for application deployment.
Configuration Management: Configuration management tools enable organizations to manage and automate the configuration of their infrastructure and applications. AWS provides AWS Systems Manager, which allows you to manage and configure EC2 instances at scale. It also offers integration with popular configuration management tools like Chef and Puppet.
Monitoring and Logging: Monitoring and logging are crucial aspects of DevOps. AWS CloudWatch is a monitoring service that collects and tracks metrics, sets alarms, and provides insights into the performance and health of AWS resources and applications. AWS X-Ray is a service that helps trace and debug distributed applications, providing valuable insights into requests and latency.
Security and Compliance: Security and compliance are paramount in any DevOps environment. AWS provides a wide range of security services and features, including AWS Identity and Access Management (IAM) for access control, AWS Key Management Service (KMS) for encryption, and AWS Security Hub for centralized security monitoring and compliance checks.
Containerization and Orchestration: Containerization technologies like Docker and container orchestration platforms like Amazon Elastic Kubernetes Service (EKS) allow organizations to package and deploy applications in a portable and scalable manner. These tools enable the efficient management of containerized applications within the AWS ecosystem.
Serverless Computing: Serverless computing, exemplified by AWS Lambda, allows developers to run code without provisioning or managing servers. It enables rapid development and deployment of event-driven functions and microservices, promoting scalability and cost optimization.
AWS DevOps tools
AWS provides a wide range of tools and services that are specifically designed to support DevOps practices and workflows. These tools cover various aspects of the software development lifecycle, from code management and build automation to deployment and monitoring. Here are some key AWS DevOps tools:
AWS CodePipeline: CodePipeline is a fully managed continuous integration and continuous delivery (CI/CD) service that enables you to automate the release process for your applications. It integrates with other AWS services and third-party tools, allowing you to build, test, and deploy code changes seamlessly.
AWS CodeCommit: CodeCommit is a fully managed source code control service that hosts private Git repositories. It provides a secure and scalable platform for collaborating on code and managing version control.
AWS CodeBuild: CodeBuild is a fully managed build service that compiles source code, runs tests, and produces ready-to-deploy software packages. It supports a wide range of programming languages and build configurations.
AWS CodeDeploy: CodeDeploy automates application deployments to various compute services, including EC2 instances, AWS Lambda functions, and on-premises servers. It simplifies the process of releasing new features and updates, ensuring consistency and minimizing downtime.
AWS CloudFormation: CloudFormation allows you to define and provision AWS infrastructure resources using templates. It enables infrastructure as code, making it easier to manage and reproduce environments consistently.
AWS Elastic Beanstalk: Elastic Beanstalk is a fully managed service that makes it easy to deploy and run applications in multiple languages and frameworks. It handles the underlying infrastructure and platform configuration, allowing developers to focus on writing code.
AWS OpsWorks: OpsWorks provides a configuration management service that uses Chef or Puppet for automating the setup and management of infrastructure resources. It simplifies the process of deploying and managing applications and server configurations.
AWS X-Ray: X-Ray is a distributed tracing service that helps developers analyze and debug applications in a microservices architecture. It provides insights into request flows and performance bottlenecks, allowing for efficient troubleshooting.
AWS Systems Manager: Systems Manager offers a unified interface for managing and configuring AWS resources at scale. It provides features such as run command, patch management, and inventory management, simplifying the operational tasks associated with maintaining infrastructure and applications.
AWS CloudWatch: CloudWatch is a monitoring and observability service that collects and tracks metrics, logs, and events from various AWS resources and applications. It provides valuable insights into system performance, availability, and resource utilization.
Implementing AWS DevOps
Implementing AWS DevOps involves a systematic approach to leverage AWS services and adopt DevOps practices to streamline software development and deployment processes. Here are some steps to consider when implementing AWS DevOps:
Define DevOps Goals: Start by identifying your organization's goals and objectives for implementing DevOps. Determine the specific areas where you want to improve, such as faster time-to-market, increased agility, or improved operational efficiency.
Assess Current Processes: Evaluate your existing software development and deployment processes. Identify bottlenecks, pain points, and areas for improvement. This assessment will help you prioritize the implementation of AWS DevOps practices.
Establish a DevOps Culture: DevOps is not just about tools; it's a cultural shift that emphasizes collaboration, shared responsibility, and continuous improvement. Foster a culture of collaboration and open communication between development and operations teams.
Plan for Infrastructure as Code: Adopt the practice of infrastructure as code (IaC) to define and provision your AWS infrastructure resources. Utilize AWS CloudFormation or other IaC tools to create declarative templates that can be version-controlled and easily reproduced.
Implement Continuous Integration and Continuous Delivery (CI/CD): Automate the build, testing, and deployment processes with CI/CD pipelines. Utilize AWS CodePipeline to orchestrate the workflow and integrate it with other AWS services like AWS CodeCommit for version control and AWS CodeBuild for building artifacts.
Embrace Automation: Automate repetitive and manual tasks using AWS services like AWS Systems Manager or AWS Lambda. Automate the provisioning and configuration of infrastructure, deployment of applications, and operational tasks to reduce errors and save time.
Implement Infrastructure Monitoring and Observability: Utilize AWS CloudWatch to monitor and gain insights into the performance, availability, and health of your infrastructure and applications. Configure alarms and notifications to proactively respond to issues.
Ensure Security and Compliance: Implement security best practices and utilize AWS security services like AWS Identity and Access Management (IAM) for access control and AWS Security Hub for centralized security monitoring. Ensure compliance with relevant regulations and industry standards.
Foster Continuous Learning and Improvement: Encourage a culture of learning and continuous improvement. Conduct post-mortems, gather feedback, and use metrics and data to identify areas for optimization. Implement feedback loops to iterate and refine your DevOps processes.
Provide Training and Support: Offer training and support to teams to ensure they have the necessary skills and knowledge to effectively utilize AWS DevOps tools and services. Provide resources, documentation, and hands-on training to enable successful adoption.
Benefits of AWS DevOps
Implementing AWS DevOps offers several significant benefits for organizations. Here are some key advantages of adopting AWS DevOps practices:
Faster Time-to-Market: AWS DevOps enables organizations to deliver software products and updates at a faster pace. Automation and streamlined processes reduce manual effort, enabling rapid development, testing, and deployment. This accelerated time-to-market allows organizations to respond quickly to market demands and gain a competitive edge.
Increased Agility and Flexibility: AWS's cloud services provide a scalable and flexible infrastructure, allowing organizations to rapidly adapt to changing business needs. With AWS DevOps, teams can dynamically provision resources, scale applications, and efficiently manage workloads, enabling them to respond swiftly to fluctuating customer demands and market conditions.
Improved Collaboration and Communication: DevOps encourages close collaboration and communication between development and operations teams. By breaking down silos and fostering a culture of shared responsibility, AWS DevOps promotes efficient information sharing, reducing misunderstandings and bottlenecks. This collaboration leads to smoother workflows, faster issue resolution, and improved overall productivity.
Enhanced Quality and Reliability: DevOps practices, such as continuous integration, automated testing, and continuous delivery, help improve the quality and reliability of software products. By automating testing and deployment processes, organizations can catch bugs and issues early, reducing the risk of defects and improving software stability. This results in higher customer satisfaction and increased confidence in the software being delivered.
Cost Optimization: AWS DevOps enables organizations to optimize their costs by leveraging cloud services efficiently. With dynamic resource provisioning and scaling, teams can optimize resource usage and pay only for what they need, avoiding overprovisioning. Additionally, automated processes and reduced manual effort lead to cost savings in terms of time and labor.
Infrastructure as Code (IaC): AWS DevOps promotes the use of infrastructure as code (IaC), which allows organizations to define and manage their infrastructure through code. This approach brings consistency, repeatability, and version control to infrastructure deployments, reducing human errors and ensuring reproducibility across different environments.
Improved Security and Compliance: AWS provides a robust security framework, and when combined with DevOps practices, organizations can enhance their overall security posture. AWS DevOps enables the implementation of security best practices, such as automated security testing, continuous monitoring, and identity and access management (IAM). This helps organizations achieve and maintain compliance with relevant regulations and standards.
Continuous Improvement: AWS DevOps promotes a culture of continuous learning and improvement. With feedback loops, monitoring, and analytics provided by AWS services, organizations can collect valuable insights and data to drive optimization. This data-driven approach allows teams to identify areas for improvement, make data-backed decisions, and iterate on their processes to achieve greater efficiency and effectiveness over time.
Limitations of AWS DevOps
While AWS DevOps offers numerous benefits, it's important to be aware of its limitations. Here are some potential limitations of AWS DevOps:
Learning Curve: Implementing AWS DevOps practices requires a certain level of knowledge and expertise in both AWS services and DevOps principles. Teams may need to invest time and resources in training and upskilling to effectively leverage AWS DevOps tools and services.
Complexity: AWS provides a vast array of services, and navigating through the various options and configurations can be complex. Designing and implementing a robust AWS DevOps architecture may require careful planning and expertise to ensure the optimal use of resources and services.
Cost Management: While AWS offers flexibility and scalability, it's important to carefully manage costs. Organizations need to monitor resource usage, optimize deployments, and select the appropriate pricing models to avoid unexpected expenses.
Dependency on Internet Connectivity: AWS is a cloud-based platform, which means it relies on internet connectivity for access and operations. Organizations should consider potential downtime or performance issues caused by internet outages or network connectivity problems.
Vendor Lock-In: Adopting AWS DevOps practices may create a dependency on AWS services and infrastructure. Migrating to an alternative cloud provider or making significant changes to the infrastructure architecture could be challenging and time-consuming.
Security and Compliance Considerations: While AWS provides robust security features, organizations are responsible for configuring and managing the security of their applications and data. Proper security configurations and compliance measures need to be implemented to ensure data protection and regulatory compliance.
Cultural Shift: Implementing DevOps practices requires a cultural shift within the organization. It may involve breaking down silos between development and operations teams, promoting collaboration, and embracing change. Overcoming resistance to change and ensuring buy-in from stakeholders can be a challenge.
Maintenance and Support: AWS DevOps requires ongoing maintenance and support to ensure the stability and performance of the infrastructure and applications. Organizations should allocate resources for monitoring, managing updates, and addressing issues that arise in the AWS environment.
Future of AWS DevOps
The future of AWS DevOps looks promising, with continued advancements and innovations expected to further enhance its capabilities. Here are some potential trends and developments that may shape the future of AWS DevOps:
Serverless Computing: Serverless architectures, exemplified by AWS Lambda, are gaining popularity as they offer scalability, reduced operational overhead, and cost efficiency. In the future, we can expect further advancements in serverless computing, enabling organizations to build and deploy applications without managing underlying infrastructure.
AI and Machine Learning Integration: AI and machine learning are increasingly being integrated into various aspects of software development and operations. In the context of AWS DevOps, we can expect AI-driven insights and automation tools that help optimize CI/CD pipelines, enhance monitoring and observability, and improve incident response and remediation processes.
Infrastructure Automation and Orchestration: As infrastructure as code (IaC) becomes more prevalent, we can expect advancements in infrastructure automation and orchestration tools within AWS DevOps. This includes more sophisticated features, improved support for multi-cloud environments, and enhanced integration with popular IaC frameworks.
Enhanced Security and Compliance: Security and compliance will remain a key focus area for AWS DevOps. We can expect further advancements in security automation, threat detection, and compliance management tools within the AWS ecosystem. Integration with AI-driven security solutions may help organizations identify and mitigate security risks more effectively.
Integration of DevOps with DataOps: The integration of DevOps and DataOps practices is likely to gain traction as organizations increasingly focus on managing and leveraging their data assets. AWS services like Amazon Redshift, AWS Glue, and Amazon EMR will play a crucial role in enabling efficient data operations within DevOps workflows.
Advanced Observability and Monitoring: Observability and monitoring will continue to evolve, providing more granular insights into applications and infrastructure performance. Advanced tracing, logging, and distributed tracing capabilities will be integrated into AWS DevOps tools, allowing organizations to identify and resolve issues more efficiently.
Focus on Developer Experience: AWS DevOps tools and services will likely prioritize the developer experience, providing improved user interfaces, better integration with popular development tools, and enhanced collaboration features. The goal will be to make it easier and more efficient for developers to adopt and utilize AWS DevOps practices.
Cross-platform and Hybrid Cloud Support: As organizations increasingly adopt hybrid and multi-cloud strategies, AWS DevOps will likely evolve to provide better support for managing and orchestrating deployments across different cloud platforms. Integration with other cloud providers and on-premises environments will be enhanced, enabling seamless workflows and deployments.
Conclusion
In conclusion, AWS DevOps offers organizations a powerful set of tools and practices to streamline software development and deployment processes. By leveraging AWS services, organizations can achieve faster time-to-market, increased agility, improved collaboration, and enhanced quality and reliability.
While there are limitations to consider, such as the learning curve and complexity of AWS services, proper planning, training, and expertise can help mitigate these challenges.
Looking towards the future, AWS DevOps is expected to evolve and embrace trends such as serverless computing, AI integration, advanced observability, and enhanced security and compliance. The focus on developer experience and support for hybrid and multi-cloud environments will also play a significant role in shaping the future of AWS DevOps.
Overall, AWS DevOps enables organizations to deliver software products with speed, scalability, and reliability, empowering them to stay competitive in today's rapidly changing digital landscape. By embracing AWS DevOps practices and staying informed about emerging trends, organizations can maximize the benefits and drive continuous improvement in their software development and deployment processes.
Key Cloud Skills for Success in 2023
In the fast-evolving landscape of technology, cloud computing has emerged as a transformative force that underpins the modern digital economy. As we step into 2023, the demand for cloud expertise continues to soar, making it a pivotal year for professionals aspiring to excel in the field. To navigate this dynamic and competitive landscape, one must possess a precise set of skills that enable them to harness the power of cloud computing effectively. This article delves into the key cloud skills that are essential for success in 2023, offering insights into the competencies that will empower individuals and organizations to thrive in the ever-expanding realm of cloud technology. Whether you are a seasoned cloud professional looking to stay at the forefront of industry trends or a newcomer eager to embark on a cloud-focused career path, these skills will be your guiding light in the journey ahead.
Table of Contents
Cloud Security
Machine Learning and AI
Cloud Deployment and Migration Across Multiple Platforms
Technical Skills Required for Cloud Computing
Other Skills Required for Cloud Computing
Get Certified and Make Yourself Indispensable
Cloud Security
Cloud security involves protecting data, applications, and infrastructure hosted in cloud computing environments from various threats and vulnerabilities. It encompasses a range of practices and technologies aimed at ensuring the confidentiality, integrity, and availability of cloud-based resources. This is particularly important because cloud computing involves the storage and access of data and services through third-party providers over the internet. Key aspects of cloud security include safeguarding data through encryption and access controls, managing user identities and access permissions, complying with regulatory requirements, securing network infrastructure, and monitoring for security incidents. It's an ongoing process that requires continuous vigilance and adaptation to address evolving cyber threats in the ever-changing cloud landscape.
In the shared responsibility model of cloud security, cloud service providers are responsible for securing the underlying infrastructure, while customers are responsible for securing their data and applications. This means that organizations must carefully assess their specific security needs and implement a combination of security measures, such as identity and access management, application security, and data encryption, to protect their assets in the cloud. Additionally, employee training and awareness play a crucial role in mitigating security risks, as human error and social engineering attacks remain significant threats to cloud security. Overall, cloud security is essential to build trust in cloud services and to ensure the safe and reliable operation of cloud-based systems and data.
Machine Learning and AI
Machine Learning (ML) is a branch of Artificial Intelligence (AI) that concentrates on creating algorithms and models enabling computers to learn from data and improve their performance on specific tasks without being explicitly programmed. ML algorithms can analyze and identify patterns in large datasets, enabling them to make predictions, recognize objects, understand natural language, and even make decisions. This technology has numerous real-world applications, including virtual assistants like Siri and recommendation systems on platforms like Netflix and Amazon. It's a pivotal component of AI that's transforming industries by automating tasks, enhancing decision-making processes, and powering various intelligent applications.
Artificial Intelligence, on the other hand, is a broader field encompassing the development of machines and systems that can simulate human-like intelligence across a wide range of tasks. While ML is a critical component of AI, AI also encompasses other approaches like expert systems, natural language processing, robotics, and computer vision. AI seeks to create systems that can reason, understand context, adapt to new situations, and exhibit general intelligence. Achieving strong AI, which has human-like cognitive abilities, remains an aspirational goal, while narrow AI, which excels in specific domains, is what we commonly encounter in today's applications.
Cloud Deployment and Migration Across Multiple Platforms
Cloud deployment and migration across multiple platforms involve the strategic use of different cloud service providers or deployment models to meet an organization's IT needs effectively. This approach recognizes that not all cloud providers or services are created equal, and by using a combination of public, private, or hybrid clouds, organizations can optimize their cloud infrastructure. Public cloud services offer scalability and cost-effectiveness, while private clouds provide control and security. Hybrid clouds combine the best of both worlds, allowing data and applications to flow seamlessly between them, offering greater flexibility and resource allocation options.
Cloud migration across multiple platforms is the process of transitioning applications, data, and workloads between different cloud providers or environments. This strategy allows organizations to avoid vendor lock-in and optimize their cloud resources based on specific requirements. However, it comes with challenges related to data transfer, integration, security, and cost management. To successfully navigate these complexities, organizations must carefully plan their cloud migration strategy, choosing the right mix of cloud platforms, and implementing robust management and monitoring practices to ensure the seamless operation of their multi-platform cloud environment.
Technical Skills Required for Cloud Computing
To thrive in your cloud computing career, being skilled in databases, DevOps, and other related technologies is essential. As a cloud computing professional, you should cultivate these additional technical skills to succeed and grow in the industry.
Data Base Skills
Database skills are critical in today's digital age, as they enable professionals to effectively manage and harness the power of data. Proficiency in database management systems (DBMS), such as MySQL, PostgreSQL, and NoSQL databases like MongoDB, allows individuals to create, organize, and query data efficiently. A solid grasp of SQL, the universal language for working with databases, enables users to retrieve, manipulate, and maintain data, making it an indispensable skill for developers, data analysts, and database administrators. Furthermore, expertise in database design, indexing, and normalization ensures that data is organized logically and accessed with optimal efficiency, while knowledge of database security and backup procedures safeguards valuable information.
In today's data-driven world, database skills are indispensable across various industries, from IT to finance and healthcare. Whether it's designing scalable databases to support large-scale applications, ensuring data security and compliance, or optimizing database performance for real-time decision-making, a strong foundation in database management empowers professionals to make informed data-driven choices and contribute significantly to their organizations' success.
Devops
DevOps, short for Development (Dev) and Operations (Ops), is a modern approach to software development and IT operations that emphasizes collaboration, automation, and efficiency. It breaks down traditional silos between development and IT teams, promoting a culture of shared responsibility and constant communication. In the DevOps model, software development and deployment processes are automated, allowing for faster and more reliable releases. Continuous Integration (CI) ensures that code changes are frequently integrated and tested, while Continuous Delivery (CD) automates the deployment of these changes into production or staging environments. This automation not only accelerates the software development lifecycle but also enhances quality by reducing human error.
Moreover, DevOps encourages a feedback-driven approach. Teams monitor application performance, gather user feedback, and use this data to make informed decisions for continuous improvement. By embracing practices like Infrastructure as Code (IaC) and containerization, DevOps enables consistent and repeatable infrastructure provisioning, making it easier to manage and scale complex systems. Overall, DevOps has become an essential philosophy and set of practices for organizations seeking agility, efficiency, and reliability in their software development and IT operations.
Other Skills Required for Cloud Computing
In addition to technical skills, there are several other skills and attributes that are valuable for professionals in the field of cloud computing. These skills are essential for success in cloud-related roles and for effectively managing cloud resources and projects. Here are some of the key non-technical skills and attributes required for cloud computing:
- Communication Skills: Effective communication is crucial for conveying complex technical concepts to non-technical stakeholders. Cloud professionals often need to collaborate with different teams, including business, finance, and management, to align cloud strategies with organizational goals.
- Problem-Solving and Critical Thinking: The ability to analyze complex problems, identify root causes, and devise innovative solutions is essential in cloud computing. Cloud professionals often encounter technical challenges and must find efficient and creative ways to address them.
- Project Management: Proficiency in project management methodologies and tools helps in planning, executing, and monitoring cloud projects effectively. This skill is particularly valuable for cloud architects and project managers overseeing cloud migrations or implementations.
- Adaptability: The cloud computing landscape is continuously evolving with new technologies and services. Being adaptable and open to learning about emerging trends and tools is essential for staying current in the field.
- Cost Management: Understanding cloud cost structures and optimizing cloud spending is critical for organizations to maximize their return on investment (ROI). Cloud professionals with skills in cost analysis and optimization can help control expenses.
- Vendor Management: As cloud environments often involve multiple cloud service providers, the ability to manage vendor relationships, negotiate contracts, and assess service-level agreements (SLAs) is valuable in ensuring that the chosen cloud solutions meet organizational needs.
- Ethical and Security Awareness: A strong sense of ethics and security consciousness is crucial for protecting sensitive data and ensuring compliance with industry regulations. Cloud professionals should be aware of ethical considerations related to data privacy and security.
- Time Management: Cloud projects often involve multiple tasks and deadlines. Effective time management skills are essential for keeping projects on track and meeting objectives within specified timeframes.
- Leadership and Teamwork: Cloud professionals in leadership roles need strong leadership and team-building skills to guide teams and foster collaboration. Effective teamwork is vital for the successful implementation and management of cloud solutions.
- Customer Service Orientation: Cloud professionals who work with internal or external clients should possess strong customer service skills. Being responsive to customer needs and providing excellent support fosters positive relationships and user satisfaction.
- Legal and Compliance Knowledge: Familiarity with legal and compliance requirements in the cloud computing space, such as data protection laws and industry-specific regulations, is essential for ensuring that cloud solutions are compliant and risk-free.
- Strategic Thinking: Cloud architects and strategists should have a strategic mindset to align cloud initiatives with long-term business objectives. This includes considering scalability, disaster recovery, and future technology trends in cloud planning.
In summary, cloud computing professionals require a blend of technical expertise and soft skills to navigate the complex and ever-changing landscape of cloud technology. Developing and honing these non-technical skills enhances an individual's ability to contribute effectively to cloud projects and drive successful cloud adoption within organizations.
Get Certified and Make Yourself Indispensable
If you just graduated with a four-year degree, you may not have all the right skills for your chosen discipline. The rapid acceleration of technology and the sheer complexity of the digital age mean that if you are interested in pursuing a career in cloud computing, you can gain the latest cloud computing skills, including AWS skills, through iCert Global’s Cloud Architect Master’s Program. iCert Global’s industry-leading courses blend live, instructor-led coursework with hands-on projects and self-guided tutorials to help you achieve your goals.
Enroll in our Cloud Computing and learn all the skills that are needed to become a cloud computing expert in the industry.
Read More
In the fast-evolving landscape of technology, cloud computing has emerged as a transformative force that underpins the modern digital economy. As we step into 2023, the demand for cloud expertise continues to soar, making it a pivotal year for professionals aspiring to excel in the field. To navigate this dynamic and competitive landscape, one must possess a precise set of skills that enable them to harness the power of cloud computing effectively. This article delves into the key cloud skills that are essential for success in 2023, offering insights into the competencies that will empower individuals and organizations to thrive in the ever-expanding realm of cloud technology. Whether you are a seasoned cloud professional looking to stay at the forefront of industry trends or a newcomer eager to embark on a cloud-focused career path, these skills will be your guiding light in the journey ahead.
Table of Contents
Cloud Security
Machine Learning and AI
Cloud Deployment and Migration Across Multiple Platforms
Technical Skills Required for Cloud Computing
Other Skills Required for Cloud Computing
Get Certified and Make Yourself Indispensable
Cloud Security
Cloud security involves protecting data, applications, and infrastructure hosted in cloud computing environments from various threats and vulnerabilities. It encompasses a range of practices and technologies aimed at ensuring the confidentiality, integrity, and availability of cloud-based resources. This is particularly important because cloud computing involves the storage and access of data and services through third-party providers over the internet. Key aspects of cloud security include safeguarding data through encryption and access controls, managing user identities and access permissions, complying with regulatory requirements, securing network infrastructure, and monitoring for security incidents. It's an ongoing process that requires continuous vigilance and adaptation to address evolving cyber threats in the ever-changing cloud landscape.
In the shared responsibility model of cloud security, cloud service providers are responsible for securing the underlying infrastructure, while customers are responsible for securing their data and applications. This means that organizations must carefully assess their specific security needs and implement a combination of security measures, such as identity and access management, application security, and data encryption, to protect their assets in the cloud. Additionally, employee training and awareness play a crucial role in mitigating security risks, as human error and social engineering attacks remain significant threats to cloud security. Overall, cloud security is essential to build trust in cloud services and to ensure the safe and reliable operation of cloud-based systems and data.
Machine Learning and AI
Machine Learning (ML) is a branch of Artificial Intelligence (AI) that concentrates on creating algorithms and models enabling computers to learn from data and improve their performance on specific tasks without being explicitly programmed. ML algorithms can analyze and identify patterns in large datasets, enabling them to make predictions, recognize objects, understand natural language, and even make decisions. This technology has numerous real-world applications, including virtual assistants like Siri and recommendation systems on platforms like Netflix and Amazon. It's a pivotal component of AI that's transforming industries by automating tasks, enhancing decision-making processes, and powering various intelligent applications.
Artificial Intelligence, on the other hand, is a broader field encompassing the development of machines and systems that can simulate human-like intelligence across a wide range of tasks. While ML is a critical component of AI, AI also encompasses other approaches like expert systems, natural language processing, robotics, and computer vision. AI seeks to create systems that can reason, understand context, adapt to new situations, and exhibit general intelligence. Achieving strong AI, which has human-like cognitive abilities, remains an aspirational goal, while narrow AI, which excels in specific domains, is what we commonly encounter in today's applications.
Cloud Deployment and Migration Across Multiple Platforms
Cloud deployment and migration across multiple platforms involve the strategic use of different cloud service providers or deployment models to meet an organization's IT needs effectively. This approach recognizes that not all cloud providers or services are created equal, and by using a combination of public, private, or hybrid clouds, organizations can optimize their cloud infrastructure. Public cloud services offer scalability and cost-effectiveness, while private clouds provide control and security. Hybrid clouds combine the best of both worlds, allowing data and applications to flow seamlessly between them, offering greater flexibility and resource allocation options.
Cloud migration across multiple platforms is the process of transitioning applications, data, and workloads between different cloud providers or environments. This strategy allows organizations to avoid vendor lock-in and optimize their cloud resources based on specific requirements. However, it comes with challenges related to data transfer, integration, security, and cost management. To successfully navigate these complexities, organizations must carefully plan their cloud migration strategy, choosing the right mix of cloud platforms, and implementing robust management and monitoring practices to ensure the seamless operation of their multi-platform cloud environment.
Technical Skills Required for Cloud Computing
To thrive in your cloud computing career, being skilled in databases, DevOps, and other related technologies is essential. As a cloud computing professional, you should cultivate these additional technical skills to succeed and grow in the industry.
Data Base Skills
Database skills are critical in today's digital age, as they enable professionals to effectively manage and harness the power of data. Proficiency in database management systems (DBMS), such as MySQL, PostgreSQL, and NoSQL databases like MongoDB, allows individuals to create, organize, and query data efficiently. A solid grasp of SQL, the universal language for working with databases, enables users to retrieve, manipulate, and maintain data, making it an indispensable skill for developers, data analysts, and database administrators. Furthermore, expertise in database design, indexing, and normalization ensures that data is organized logically and accessed with optimal efficiency, while knowledge of database security and backup procedures safeguards valuable information.
In today's data-driven world, database skills are indispensable across various industries, from IT to finance and healthcare. Whether it's designing scalable databases to support large-scale applications, ensuring data security and compliance, or optimizing database performance for real-time decision-making, a strong foundation in database management empowers professionals to make informed data-driven choices and contribute significantly to their organizations' success.
Devops
DevOps, short for Development (Dev) and Operations (Ops), is a modern approach to software development and IT operations that emphasizes collaboration, automation, and efficiency. It breaks down traditional silos between development and IT teams, promoting a culture of shared responsibility and constant communication. In the DevOps model, software development and deployment processes are automated, allowing for faster and more reliable releases. Continuous Integration (CI) ensures that code changes are frequently integrated and tested, while Continuous Delivery (CD) automates the deployment of these changes into production or staging environments. This automation not only accelerates the software development lifecycle but also enhances quality by reducing human error.
Moreover, DevOps encourages a feedback-driven approach. Teams monitor application performance, gather user feedback, and use this data to make informed decisions for continuous improvement. By embracing practices like Infrastructure as Code (IaC) and containerization, DevOps enables consistent and repeatable infrastructure provisioning, making it easier to manage and scale complex systems. Overall, DevOps has become an essential philosophy and set of practices for organizations seeking agility, efficiency, and reliability in their software development and IT operations.
Other Skills Required for Cloud Computing
In addition to technical skills, there are several other skills and attributes that are valuable for professionals in the field of cloud computing. These skills are essential for success in cloud-related roles and for effectively managing cloud resources and projects. Here are some of the key non-technical skills and attributes required for cloud computing:
- Communication Skills: Effective communication is crucial for conveying complex technical concepts to non-technical stakeholders. Cloud professionals often need to collaborate with different teams, including business, finance, and management, to align cloud strategies with organizational goals.
- Problem-Solving and Critical Thinking: The ability to analyze complex problems, identify root causes, and devise innovative solutions is essential in cloud computing. Cloud professionals often encounter technical challenges and must find efficient and creative ways to address them.
- Project Management: Proficiency in project management methodologies and tools helps in planning, executing, and monitoring cloud projects effectively. This skill is particularly valuable for cloud architects and project managers overseeing cloud migrations or implementations.
- Adaptability: The cloud computing landscape is continuously evolving with new technologies and services. Being adaptable and open to learning about emerging trends and tools is essential for staying current in the field.
- Cost Management: Understanding cloud cost structures and optimizing cloud spending is critical for organizations to maximize their return on investment (ROI). Cloud professionals with skills in cost analysis and optimization can help control expenses.
- Vendor Management: As cloud environments often involve multiple cloud service providers, the ability to manage vendor relationships, negotiate contracts, and assess service-level agreements (SLAs) is valuable in ensuring that the chosen cloud solutions meet organizational needs.
- Ethical and Security Awareness: A strong sense of ethics and security consciousness is crucial for protecting sensitive data and ensuring compliance with industry regulations. Cloud professionals should be aware of ethical considerations related to data privacy and security.
- Time Management: Cloud projects often involve multiple tasks and deadlines. Effective time management skills are essential for keeping projects on track and meeting objectives within specified timeframes.
- Leadership and Teamwork: Cloud professionals in leadership roles need strong leadership and team-building skills to guide teams and foster collaboration. Effective teamwork is vital for the successful implementation and management of cloud solutions.
- Customer Service Orientation: Cloud professionals who work with internal or external clients should possess strong customer service skills. Being responsive to customer needs and providing excellent support fosters positive relationships and user satisfaction.
- Legal and Compliance Knowledge: Familiarity with legal and compliance requirements in the cloud computing space, such as data protection laws and industry-specific regulations, is essential for ensuring that cloud solutions are compliant and risk-free.
- Strategic Thinking: Cloud architects and strategists should have a strategic mindset to align cloud initiatives with long-term business objectives. This includes considering scalability, disaster recovery, and future technology trends in cloud planning.
In summary, cloud computing professionals require a blend of technical expertise and soft skills to navigate the complex and ever-changing landscape of cloud technology. Developing and honing these non-technical skills enhances an individual's ability to contribute effectively to cloud projects and drive successful cloud adoption within organizations.
Get Certified and Make Yourself Indispensable
If you just graduated with a four-year degree, you may not have all the right skills for your chosen discipline. The rapid acceleration of technology and the sheer complexity of the digital age mean that if you are interested in pursuing a career in cloud computing, you can gain the latest cloud computing skills, including AWS skills, through iCert Global’s Cloud Architect Master’s Program. iCert Global’s industry-leading courses blend live, instructor-led coursework with hands-on projects and self-guided tutorials to help you achieve your goals.
Enroll in our Cloud Computing and learn all the skills that are needed to become a cloud computing expert in the industry.
Essential Excel Skills for 2023: A Must-Know Guide
In the fast-paced world of 2023, proficiency in Microsoft Excel is more essential than ever. Excel remains a cornerstone of productivity and data management, indispensable across various industries and professions. Whether you're a seasoned professional or just starting your journey, understanding its core features and mastering essential Excel skills is a must. In this comprehensive guide, we will delve into the vital Excel skills that can empower you to excel in your endeavors throughout the year 2023 and beyond. From basic functions to advanced techniques, this guide will equip you with the knowledge and capabilities needed to navigate the evolving landscape of data analysis, financial modeling, and effective spreadsheet management. Join us as we explore the world of Excel and uncover the skills that are bound to make a difference in your personal and professional life.
Table of Contents
What Is Microsoft Excel?
Excel Skills You Must Know
1. Master the Shortcuts
2. Import Data from a Website
3. Filter Your Results
4. Calculate the Sum
5. AutoCorrect and AutoFill
6. Display Formulas
7. Manage Page Layout
The Bottom Line
What Is Microsoft Excel?
Microsoft Excel is a versatile and widely-used spreadsheet application developed by Microsoft, forming an integral part of the Microsoft Office suite. This software empowers users to create, organize, and analyze data within a grid-like interface, making it an invaluable tool for a myriad of tasks. Excel's robust features encompass the ability to perform complex calculations using built-in functions, visualize data through charts and graphs, and facilitate data analysis with tools like pivot tables. Its automation capabilities, data validation, and collaborative functionality further enhance its utility. Excel serves as a vital resource across various industries, aiding professionals in financial modeling, data analysis, project management, and countless other applications, thanks to its adaptability and rich feature set.
Excel Skills You Must Know
Excel proficiency spans a spectrum from basic to advanced, accommodating a diverse range of applications, from simple data entry to intricate formula calculations. In the following sections, we'll explore key Excel skills worth mastering, starting with essential elements of basic Excel training to help you enhance your Excel proficiency.
There is a wide range of Excel skills from the basic to the advanced. Excel can be used to input numbers as well as calculate complex formulas.
-
Master the Shortcuts
-
Import Data from a Website
-
Filter Your Results
-
Calculate the Sum
-
AutoCorrect and AutoFill
-
Display Formulas
-
Manage Page Layout
Master the Shortcuts
Mastering keyboard shortcuts in Excel is a great way to boost your productivity. These shortcuts can help you perform tasks quickly and efficiently. Here are some essential Excel keyboard shortcuts to get you started:
-
Ctrl + C: Copy selected cells or text.
-
Ctrl + X: Cut selected cells or text.
-
Ctrl + V: Paste copied or cut cells or text.
-
Ctrl + Z: Undo the last action.
-
Ctrl + Y: Redo the last undone action.
-
Ctrl + S: Save your Excel workbook.
-
Ctrl + P: Print the active sheet.
-
Ctrl + F: Open the Find and Replace dialog box.
-
Ctrl + A: Select all cells in the current worksheet.
-
Ctrl + arrow keys: Move to the edge of data regions.
-
Ctrl + Space: Select the entire column of the active cell.
-
Shift + Space: Select the entire row of the active cell.
-
**Ctrl + Shift + "+": Insert new cells, rows, or columns.
-
**Ctrl + "-": Delete cells, rows, or columns.
-
F2: Edit the active cell.
-
Alt + Enter: Start a new line within a cell.
-
Ctrl + Tab: Switch between open Excel workbooks.
-
Ctrl + Page Up/Page Down: Navigate between worksheets.
-
Ctrl + Shift + L: Apply or remove filters.
-
Alt + E, S, V: Paste special options.
-
Ctrl + 1: Format cells dialog box.
-
Alt + H, O, I: Autofit column width.
These are just a few examples, but there are many more Excel shortcuts available. Learning and using these shortcuts can significantly speed up your work and make you more proficient in Excel.
Import Data from a Website
To import data from a website into Excel, you can utilize the "From Web" feature, which is available in most versions of Excel. Begin by opening Excel and selecting the cell in your worksheet where you want the imported data to start. Next, navigate to the "Data" tab on the Excel ribbon, where you'll find an option like "Get Data" or "Get External Data." Click on this option and choose "From Web." In the dialog box that appears, enter the URL of the website containing the data you wish to import. Excel will then establish a connection to the website, presenting you with a web browser-like interface to interact with the site. Navigate to the specific data you want to import and click to select it. Afterward, click the "Import" or "Load" button, depending on your Excel version, to bring the data into your worksheet. You may need to specify import options, such as header rows, depending on the structure of the data. Once imported, you can work with and format the data as needed within Excel. Keep in mind that data import from websites should be conducted in compliance with the website's terms and policies, and some sites may have restrictions in place to prevent automated scraping.
Filter Your Results
Filtering data in Excel is an essential skill that allows you to refine and extract specific information from a dataset with ease. To initiate the process, select any cell within the dataset you want to filter, and then head to the "Data" tab on the Excel ribbon. There, you'll find the filter icon, resembling a funnel, which you should click to activate. Once activated, drop-down arrows will appear in the header row of each column in your dataset. Clicking on one of these arrows opens a menu where you can set filter criteria, whether by selecting specific values, specifying text or number conditions, or setting date ranges. After defining your criteria, simply click "OK" or "Apply," and Excel will instantly display only the rows that meet your filtering requirements, effectively tailoring your dataset to your needs. You can apply filters to multiple columns simultaneously and remove them just as easily. This functionality proves invaluable when working with large datasets, as it streamlines analysis and decision-making by enabling you to focus exclusively on the data that matters most.
Calculate the Sum
Calculating the sum of values in Excel is a fundamental operation that can be accomplished in a couple of ways. First, you can use the SUM function, which is particularly useful when you're working with a large set of numbers. To do this, select the cell where you want the sum to appear, then enter "=SUM(" and choose the range of cells you want to add up, closing the parenthesis before pressing Enter. Alternatively, you can use the AutoSum button, which simplifies the process by automatically suggesting a range based on adjacent cells with numerical data. Once you select the appropriate range, press Enter to calculate the sum. For smaller calculations, you can manually enter values separated by plus signs directly into a cell. Excel's flexibility in performing these calculations makes it a versatile tool for summing up data, whether it's for budgeting, financial analysis, or any task requiring mathematical aggregation.
AutoCorrect and AutoFill
AutoCorrect and AutoFill are two convenient features within Microsoft Excel that enhance efficiency and accuracy when working with data. AutoCorrect functions as a real-time proofreader, automatically fixing common spelling errors and typos as you type. It recognizes frequent mistakes and replaces them with the correct text, helping you maintain clean and error-free spreadsheets. Additionally, you can customize AutoCorrect to handle specific words or acronyms that you commonly use.
On the other hand, AutoFill is a time-saving tool that simplifies the input of recurring or sequential data. For example, if you're entering a series of dates, months, or numeric patterns, Excel can predict and complete the pattern for you. By entering the initial value and dragging the fill handle, you can instantly populate adjacent cells with the desired series, eliminating the need for manual input. Both AutoCorrect and AutoFill are valuable aids that not only boost your productivity but also contribute to the accuracy and professionalism of your Excel documents.
Display Formulas
In Microsoft Excel, the ability to display formulas provides a valuable tool for spreadsheet users, especially when dealing with intricate calculations or when auditing a spreadsheet for errors. By pressing Ctrl + ` or clicking the "Show Formulas" button in the "Formulas" tab, you can toggle between viewing the actual formulas used in each cell and seeing their calculated results. This feature allows you to review and understand the underlying logic of your spreadsheet, which is particularly helpful for troubleshooting and debugging complex formulas. It's also beneficial when you need to verify that your formulas are working as intended, as it ensures transparency and accuracy in your calculations. Whether you're an Excel novice or an experienced user, the ability to easily display formulas is an essential tool for maintaining the integrity and reliability of your spreadsheet data.
Manage Page Layout
Managing page layout in Microsoft Excel is a critical aspect of creating well-organized and professional-looking documents. With the ability to control page orientation, size, margins, and page breaks, you can ensure that your printed or saved worksheets are presented exactly as you intend. Additionally, Excel provides options for adding headers and footers, scaling content to fit the page, and specifying the print area to include only the necessary data. You can also choose whether to display gridlines, row, and column headings in your printouts, enhancing readability. The background feature allows you to add visual elements, while print titles ensure that specific rows or columns are repeated on each page, providing valuable context. By effectively managing page layout in Excel, you can tailor your documents to suit various printing or sharing needs, making your data more accessible and professional.
The Bottom Line
If you're looking to simplify your daily tasks and perhaps leave a lasting impression among your colleagues, delving into these fundamental Excel skills is a wise move. It's worth noting that Excel, despite its widespread use, remains a versatile and evolving tool. Regardless of your current proficiency level, there are always fresh techniques and features to explore in this robust application. So, consider taking the initiative to enhance your Excel proficiency—it's not just about managing personal finances more efficiently; it could open doors to exciting career prospects down the road. Eager to dive deeper into the world of Excel? iCert Global offers a variety of Excel online training courses ie Microsoft Excel foundation , Microsoft Excel Intermediate , Microsoft Excel Advanced Certification.
Read More
In the fast-paced world of 2023, proficiency in Microsoft Excel is more essential than ever. Excel remains a cornerstone of productivity and data management, indispensable across various industries and professions. Whether you're a seasoned professional or just starting your journey, understanding its core features and mastering essential Excel skills is a must. In this comprehensive guide, we will delve into the vital Excel skills that can empower you to excel in your endeavors throughout the year 2023 and beyond. From basic functions to advanced techniques, this guide will equip you with the knowledge and capabilities needed to navigate the evolving landscape of data analysis, financial modeling, and effective spreadsheet management. Join us as we explore the world of Excel and uncover the skills that are bound to make a difference in your personal and professional life.
Table of Contents
What Is Microsoft Excel?
Excel Skills You Must Know
1. Master the Shortcuts
2. Import Data from a Website
3. Filter Your Results
4. Calculate the Sum
5. AutoCorrect and AutoFill
6. Display Formulas
7. Manage Page Layout
The Bottom Line
What Is Microsoft Excel?
Microsoft Excel is a versatile and widely-used spreadsheet application developed by Microsoft, forming an integral part of the Microsoft Office suite. This software empowers users to create, organize, and analyze data within a grid-like interface, making it an invaluable tool for a myriad of tasks. Excel's robust features encompass the ability to perform complex calculations using built-in functions, visualize data through charts and graphs, and facilitate data analysis with tools like pivot tables. Its automation capabilities, data validation, and collaborative functionality further enhance its utility. Excel serves as a vital resource across various industries, aiding professionals in financial modeling, data analysis, project management, and countless other applications, thanks to its adaptability and rich feature set.
Excel Skills You Must Know
Excel proficiency spans a spectrum from basic to advanced, accommodating a diverse range of applications, from simple data entry to intricate formula calculations. In the following sections, we'll explore key Excel skills worth mastering, starting with essential elements of basic Excel training to help you enhance your Excel proficiency.
There is a wide range of Excel skills from the basic to the advanced. Excel can be used to input numbers as well as calculate complex formulas.
-
Master the Shortcuts
-
Import Data from a Website
-
Filter Your Results
-
Calculate the Sum
-
AutoCorrect and AutoFill
-
Display Formulas
-
Manage Page Layout
Master the Shortcuts
Mastering keyboard shortcuts in Excel is a great way to boost your productivity. These shortcuts can help you perform tasks quickly and efficiently. Here are some essential Excel keyboard shortcuts to get you started:
-
Ctrl + C: Copy selected cells or text.
-
Ctrl + X: Cut selected cells or text.
-
Ctrl + V: Paste copied or cut cells or text.
-
Ctrl + Z: Undo the last action.
-
Ctrl + Y: Redo the last undone action.
-
Ctrl + S: Save your Excel workbook.
-
Ctrl + P: Print the active sheet.
-
Ctrl + F: Open the Find and Replace dialog box.
-
Ctrl + A: Select all cells in the current worksheet.
-
Ctrl + arrow keys: Move to the edge of data regions.
-
Ctrl + Space: Select the entire column of the active cell.
-
Shift + Space: Select the entire row of the active cell.
-
**Ctrl + Shift + "+": Insert new cells, rows, or columns.
-
**Ctrl + "-": Delete cells, rows, or columns.
-
F2: Edit the active cell.
-
Alt + Enter: Start a new line within a cell.
-
Ctrl + Tab: Switch between open Excel workbooks.
-
Ctrl + Page Up/Page Down: Navigate between worksheets.
-
Ctrl + Shift + L: Apply or remove filters.
-
Alt + E, S, V: Paste special options.
-
Ctrl + 1: Format cells dialog box.
-
Alt + H, O, I: Autofit column width.
These are just a few examples, but there are many more Excel shortcuts available. Learning and using these shortcuts can significantly speed up your work and make you more proficient in Excel.
Import Data from a Website
To import data from a website into Excel, you can utilize the "From Web" feature, which is available in most versions of Excel. Begin by opening Excel and selecting the cell in your worksheet where you want the imported data to start. Next, navigate to the "Data" tab on the Excel ribbon, where you'll find an option like "Get Data" or "Get External Data." Click on this option and choose "From Web." In the dialog box that appears, enter the URL of the website containing the data you wish to import. Excel will then establish a connection to the website, presenting you with a web browser-like interface to interact with the site. Navigate to the specific data you want to import and click to select it. Afterward, click the "Import" or "Load" button, depending on your Excel version, to bring the data into your worksheet. You may need to specify import options, such as header rows, depending on the structure of the data. Once imported, you can work with and format the data as needed within Excel. Keep in mind that data import from websites should be conducted in compliance with the website's terms and policies, and some sites may have restrictions in place to prevent automated scraping.
Filter Your Results
Filtering data in Excel is an essential skill that allows you to refine and extract specific information from a dataset with ease. To initiate the process, select any cell within the dataset you want to filter, and then head to the "Data" tab on the Excel ribbon. There, you'll find the filter icon, resembling a funnel, which you should click to activate. Once activated, drop-down arrows will appear in the header row of each column in your dataset. Clicking on one of these arrows opens a menu where you can set filter criteria, whether by selecting specific values, specifying text or number conditions, or setting date ranges. After defining your criteria, simply click "OK" or "Apply," and Excel will instantly display only the rows that meet your filtering requirements, effectively tailoring your dataset to your needs. You can apply filters to multiple columns simultaneously and remove them just as easily. This functionality proves invaluable when working with large datasets, as it streamlines analysis and decision-making by enabling you to focus exclusively on the data that matters most.
Calculate the Sum
Calculating the sum of values in Excel is a fundamental operation that can be accomplished in a couple of ways. First, you can use the SUM function, which is particularly useful when you're working with a large set of numbers. To do this, select the cell where you want the sum to appear, then enter "=SUM(" and choose the range of cells you want to add up, closing the parenthesis before pressing Enter. Alternatively, you can use the AutoSum button, which simplifies the process by automatically suggesting a range based on adjacent cells with numerical data. Once you select the appropriate range, press Enter to calculate the sum. For smaller calculations, you can manually enter values separated by plus signs directly into a cell. Excel's flexibility in performing these calculations makes it a versatile tool for summing up data, whether it's for budgeting, financial analysis, or any task requiring mathematical aggregation.
AutoCorrect and AutoFill
AutoCorrect and AutoFill are two convenient features within Microsoft Excel that enhance efficiency and accuracy when working with data. AutoCorrect functions as a real-time proofreader, automatically fixing common spelling errors and typos as you type. It recognizes frequent mistakes and replaces them with the correct text, helping you maintain clean and error-free spreadsheets. Additionally, you can customize AutoCorrect to handle specific words or acronyms that you commonly use.
On the other hand, AutoFill is a time-saving tool that simplifies the input of recurring or sequential data. For example, if you're entering a series of dates, months, or numeric patterns, Excel can predict and complete the pattern for you. By entering the initial value and dragging the fill handle, you can instantly populate adjacent cells with the desired series, eliminating the need for manual input. Both AutoCorrect and AutoFill are valuable aids that not only boost your productivity but also contribute to the accuracy and professionalism of your Excel documents.
Display Formulas
In Microsoft Excel, the ability to display formulas provides a valuable tool for spreadsheet users, especially when dealing with intricate calculations or when auditing a spreadsheet for errors. By pressing Ctrl + ` or clicking the "Show Formulas" button in the "Formulas" tab, you can toggle between viewing the actual formulas used in each cell and seeing their calculated results. This feature allows you to review and understand the underlying logic of your spreadsheet, which is particularly helpful for troubleshooting and debugging complex formulas. It's also beneficial when you need to verify that your formulas are working as intended, as it ensures transparency and accuracy in your calculations. Whether you're an Excel novice or an experienced user, the ability to easily display formulas is an essential tool for maintaining the integrity and reliability of your spreadsheet data.
Manage Page Layout
Managing page layout in Microsoft Excel is a critical aspect of creating well-organized and professional-looking documents. With the ability to control page orientation, size, margins, and page breaks, you can ensure that your printed or saved worksheets are presented exactly as you intend. Additionally, Excel provides options for adding headers and footers, scaling content to fit the page, and specifying the print area to include only the necessary data. You can also choose whether to display gridlines, row, and column headings in your printouts, enhancing readability. The background feature allows you to add visual elements, while print titles ensure that specific rows or columns are repeated on each page, providing valuable context. By effectively managing page layout in Excel, you can tailor your documents to suit various printing or sharing needs, making your data more accessible and professional.
The Bottom Line
If you're looking to simplify your daily tasks and perhaps leave a lasting impression among your colleagues, delving into these fundamental Excel skills is a wise move. It's worth noting that Excel, despite its widespread use, remains a versatile and evolving tool. Regardless of your current proficiency level, there are always fresh techniques and features to explore in this robust application. So, consider taking the initiative to enhance your Excel proficiency—it's not just about managing personal finances more efficiently; it could open doors to exciting career prospects down the road. Eager to dive deeper into the world of Excel? iCert Global offers a variety of Excel online training courses ie Microsoft Excel foundation , Microsoft Excel Intermediate , Microsoft Excel Advanced Certification.
Exploring Data Encryption: Unveiling Types, Algorithms, Techniques, and Approaches
In an increasingly interconnected digital world, where data is both the lifeblood and the target of modern endeavors, the need for robust data protection has never been more critical. At the heart of this defense lies the art and science of data encryption—an intricate process that transforms information into an unreadable code, rendering it impervious to prying eyes. This exploration into the realm of data encryption aims to unravel its intricacies, unveiling the diverse types, sophisticated algorithms, ingenious techniques, and strategic approaches that together fortify the security of our digital landscape. From the symmetrical dance of keys to the asymmetric harmony of secure communications, from the impenetrable armor of Advanced Encryption Standard (AES) to the mathematical elegance of RSA and Elliptic Curve Cryptography (ECC), this journey will delve into the mechanisms that power our defenses against data breaches and unauthorized access. We will navigate through the labyrinth of encryption methods, discerning the nuanced interplay of confidentiality, integrity, and authenticity that they orchestrate. Whether you're a curious explorer of technology or an ardent guardian of data integrity, join us as we embark on an enlightening expedition into the world of data encryption, where each layer of knowledge adds another layer of protection.
Table of Contents
What is Data Encryption?
How Does Data Encryption Work?
Why Do We Need Data Encryption?
What are the 2 Types of Data Encryption Techniques?
What is Hashing?
What is an Encryption Algorithm?
Best Encryption Algorithms
3DES
The Future of Data Encryption
Should You Use Symmetric or Asymmetric Encryption?
Businesses Use Encryption For Many Purposes
Steps to Implement an Effective Encryption Strategy
What Is a Key in Cryptography?
Do You Want to Learn More About Cybersecurity?
FAQs
What is Data Encryption?
Data encryption is the process of converting understandable data into an unreadable form, known as ciphertext, using complex algorithms and a secret key. This transformation ensures that even if unauthorized parties gain access to the encrypted data, they cannot comprehend its original meaning without the corresponding decryption key. Encryption serves as a vital mechanism for safeguarding sensitive information during storage, transmission, and processing, thwarting unauthorized access and maintaining data confidentiality. It finds application in various realms such as online transactions, secure communication, and data protection, offering varying levels of security through different encryption methods and algorithms tailored to specific needs.
How Does Data Encryption Work?
Data encryption functions by utilizing complex algorithms to convert plain data into an unintelligible form known as ciphertext. This process involves an encryption key that serves as the foundation for the transformation. The chosen algorithm determines how the encryption and decryption keys interact. During encryption, the algorithm combines the encryption key with the plaintext, generating ciphertext that appears as random characters. This ciphertext can be safely transmitted or stored without revealing the original information. To reverse the process, decryption employs the corresponding decryption key, allowing the recipient to transform the ciphertext back into readable plaintext. The security of encrypted data hinges on robust algorithms, secure key management, and effective protection against unauthorized access to the encryption keys.
Why Do We Need Data Encryption?
Data encryption is a vital necessity due to its role in shielding sensitive information from unauthorized access and maintaining confidentiality. It acts as a bulwark against privacy breaches by converting data into an unreadable format, making it indecipherable without the appropriate decryption key. This protection is essential across diverse domains, from safeguarding personal data and financial records to upholding regulatory compliance and mitigating the impact of data breaches. Encryption not only secures communication over networks and cloud storage but also fortifies authentication procedures and shields intellectual property from prying eyes. In an era of global connectivity, encryption stands as a cornerstone of cybersecurity, ensuring the security and privacy of digital interactions and sensitive information.
What are the 2 Types of Data Encryption Techniques?
Data encryption techniques can be broadly categorized into two main types: Symmetric Encryption and Asymmetric Encryption.
-
Symmetric Encryption: In symmetric encryption, a single encryption key is used for both the encryption and decryption processes. The same key is shared between the sender and the recipient. The main advantage of symmetric encryption is its speed and efficiency, as the algorithms used are generally faster than their asymmetric counterparts. However, the challenge lies in securely exchanging the encryption key between parties without it being intercepted by unauthorized individuals. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
-
Asymmetric Encryption: Asymmetric encryption, also known as public-key encryption, employs a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. The keys are mathematically related but cannot be practically derived from each other. This setup addresses the key exchange challenge of symmetric encryption, as the public key can be freely shared without compromising the security of the private key. Asymmetric encryption provides a higher level of security for tasks like secure communication and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are examples of asymmetric encryption algorithms.
Both types of encryption techniques have their advantages and are often used together to address specific security needs. Symmetric encryption is suitable for encrypting large amounts of data quickly, while asymmetric encryption is valuable for secure key exchange and ensuring the authenticity of communication parties.
What is Hashing?
Hashing is a cryptographic technique that involves transforming input data into a fixed-length string of characters, known as a hash value. This process is designed to be fast and deterministic, meaning the same input will always produce the same hash value. Hashing serves various purposes, such as verifying data integrity and authenticity. It ensures data integrity by generating a unique representation of the input data, making it easy to detect even minor changes in the data. Hashing is commonly used for tasks like password storage, where passwords are hashed and stored to enhance security. Additionally, hashing underpins digital signatures, providing a way to confirm the authenticity of digital documents and messages. However, it's important to choose secure and collision-resistant hash functions to prevent vulnerabilities and ensure the reliability of hash-based applications.
What is an Encryption Algorithm?
An encryption algorithm is a set of mathematical rules and procedures used to transform data from its original, readable form (plaintext) into an unreadable and secure format (ciphertext) during encryption, and to revert it back to plaintext during decryption. It dictates how the encryption key interacts with the data to produce the ciphertext and how the decryption key is used to reverse the process. Encryption algorithms play a pivotal role in maintaining data security and confidentiality, ensuring that sensitive information remains protected from unauthorized access and interception. These algorithms come in two main types: symmetric, which use the same key for both encryption and decryption, and asymmetric (public-key), which employ a pair of keys for these operations. The selection of an encryption algorithm depends on factors such as security requirements, key management, and the specific application's needs.
Best Encryption Algorithms
The "best" encryption algorithm depends on the specific use case, security requirements, and the state of current cryptographic research. However, as of my last knowledge update in September 2021, I can mention some widely recognized and respected encryption algorithms that were considered strong at that time:
-
AES (Advanced Encryption Standard): AES is one of the most widely used symmetric encryption algorithms. It offers strong security and efficiency and is considered secure for a wide range of applications. AES operates with varying key lengths, including 128-bit, 192-bit, and 256-bit.
-
RSA (Rivest-Shamir-Adleman): RSA is a well-known asymmetric encryption algorithm used for secure key exchange, digital signatures, and other cryptographic tasks. It relies on the difficulty of factoring large prime numbers to provide security.
-
ECC (Elliptic Curve Cryptography): ECC is another asymmetric encryption algorithm known for its strong security and relatively shorter key lengths compared to RSA. It is particularly well-suited for resource-constrained environments, such as mobile devices.
-
SHA-256 (Secure Hash Algorithm 256-bit): While not an encryption algorithm per se, SHA-256 is a widely used cryptographic hash function. It's used for various purposes, including generating digital signatures and verifying data integrity.
-
ChaCha20 and Poly1305: These are modern cryptographic algorithms designed to provide encryption and data integrity in a combined mode. They are becoming popular choices, especially for use in stream cipher constructions.
It's important to note that cryptographic algorithms and best practices can evolve over time due to advances in technology and cryptanalysis. Organizations should stay updated with the latest recommendations from reputable sources, such as NIST (National Institute of Standards and Technology), to ensure they are using algorithms that meet current security standards. Additionally, the strength of encryption also relies on proper key management, implementation, and the overall security of the system in which it is used.
3DES
Triple Data Encryption Standard (3DES), also known as TDEA (Triple Data Encryption Algorithm), is a symmetric encryption algorithm that provides a higher level of security compared to the original Data Encryption Standard (DES) algorithm. 3DES applies the DES algorithm three times in a cascade, using multiple keys. This process significantly increases the effective key length and enhances security.
Here's how 3DES works:
-
Key Generation: Three separate keys are generated, often referred to as Key 1, Key 2, and Key 3.
-
Encryption: The plaintext data undergoes three consecutive rounds of encryption using the three keys. The data is first encrypted with Key 1, then decrypted using Key 2, and finally encrypted again using Key 3.
-
Decryption: To decrypt the data, the process is reversed. The ciphertext is decrypted with Key 3, then encrypted with Key 2, and finally decrypted using Key 1.
3DES provides an effective key length of 168 bits, as each of the three keys is 56 bits long. This makes it significantly more secure than the original DES, which had a 56-bit key length and became susceptible to brute-force attacks as computing power increased. However, it's worth noting that 3DES is not as efficient as more modern symmetric encryption algorithms like AES, which offer better performance and security with shorter key lengths.
3DES was widely adopted as an interim solution when transitioning from DES to more secure algorithms. However, due to its relatively slower performance and the availability of more efficient encryption algorithms, such as AES, it's recommended to use AES for new implementations requiring strong symmetric encryption.
The Future of Data Encryption
The future of data encryption holds several promising trends and challenges. Post-Quantum Cryptography is actively being researched to ensure encryption methods remain secure against the potential threat of quantum computers. Homomorphic encryption presents opportunities for processing data while it remains encrypted, enhancing privacy and security. Zero-knowledge proofs could revolutionize authentication and digital identity, while encryption's role in securing blockchain networks will continue to be paramount. Enhanced key management practices, such as hardware security modules and secure key distribution, will strengthen encryption protocols. Quantum Key Distribution offers ultra-secure methods for key exchange. The synergy of AI and encryption is likely to optimize processes and enhance overall security. As regulations evolve, encryption laws may adapt to balance security and law enforcement needs. Usability improvements and broader integration into applications and devices will be pivotal for increasing encryption adoption. Staying abreast of these developments will be essential as the landscape of data encryption continues to evolve dynamically.
Should You Use Symmetric or Asymmetric Encryption?
The decision to use symmetric or asymmetric encryption hinges on the context and security requirements of the scenario. Symmetric encryption offers speed and efficiency, making it suitable for encrypting large data volumes. However, it demands a secure method of distributing the shared key among parties. Asymmetric encryption, while slower, addresses the challenge of secure key exchange and is pivotal for scenarios where parties don't share a pre-established secret key. Asymmetric encryption's application extends to digital signatures and secure communication with key exchange. Often, a hybrid approach is employed, utilizing both encryption types to leverage their strengths. In such cases, asymmetric encryption may be used to securely establish a symmetric encryption key, enabling efficient data encryption. Ultimately, the choice should align with specific security needs, key management complexity, and the speed requirements of the given use case, ensuring an appropriate balance between security and practicality.
Businesses Use Encryption For Many Purposes
Businesses leverage encryption for a multitude of purposes to reinforce their data security measures and uphold the integrity of their operations. Encryption is extensively employed to shield sensitive customer data, proprietary information, and financial records, thereby thwarting unauthorized access and data breaches. It's pivotal in securing communication channels, such as emails and instant messaging, ensuring that confidential information remains private during transmission. Encryption also underpins secure financial transactions on e-commerce platforms and online banking systems. It bolsters password security by storing user credentials securely and helps businesses adhere to regulatory frameworks like GDPR and HIPAA, safeguarding them from legal consequences and maintaining customer trust. Additionally, encryption is paramount for cloud security, remote work scenarios, secure file sharing, digital signatures, IoT security, and preserving the confidentiality of sensitive data within supply chains. Overall, encryption is a cornerstone of modern business strategies, fostering data protection and bolstering organizational reputation.
Steps to Implement an Effective Encryption Strategy
Implementing an effective encryption strategy involves a systematic approach to ensure the security of sensitive data. Here are five key steps to guide the process:
-
Data Classification and Assessment: Begin by identifying and classifying the types of data that require encryption. Conduct a thorough assessment of your organization's data landscape to determine which data is sensitive and where it resides. This includes data at rest, in transit, and during processing.
-
Security Requirements Definition: Define your security requirements based on the sensitivity of the data. Determine which encryption algorithms and key lengths are appropriate for different data types and use cases. Consider compliance regulations and industry standards that apply to your organization.
-
Encryption Implementation: Select suitable encryption solutions and tools that align with your requirements. Implement encryption mechanisms for data at rest and in transit. For data at rest, utilize encryption features provided by databases, operating systems, or storage solutions. For data in transit, employ secure protocols such as TLS/SSL for network communication.
-
Key Management and Access Control: Develop a robust key management strategy. Establish procedures for generating, storing, rotating, and revoking encryption keys. Ensure that only authorized personnel have access to encryption keys. Implement strong access controls to prevent unauthorized users from accessing encrypted data.
-
Testing, Monitoring, and Compliance: Thoroughly test your encryption implementation to ensure its effectiveness and compatibility with your systems. Regularly monitor encryption processes, access logs, and audit trails to detect any anomalies or unauthorized access attempts. Conduct periodic security assessments and audits to ensure compliance with encryption policies and regulations.
By following these steps, you can create a structured and comprehensive encryption strategy that safeguards sensitive data, mitigates risks, and aligns with industry best practices and compliance standards.
What Is a Key in Cryptography?
In cryptography, a key refers to a specific piece of information, often a sequence of characters, numbers, or bits, that is used to control the encryption and decryption processes. Keys play a central role in cryptographic operations by determining how data is transformed from its original form (plaintext) to an encrypted form (ciphertext) and back to plaintext.
There are two main types of keys in cryptography:
-
Encryption Key: This key is used during the encryption process to convert plaintext into ciphertext. The encryption key is known only to authorized parties involved in secure communication or data protection.
-
Decryption Key: This key is used during the decryption process to revert the ciphertext back to its original plaintext. In symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption (public-key cryptography), there is a pair of keys: a public key for encryption and a private key for decryption.
Keys are kept confidential to ensure the security of encrypted data. The strength and security of a cryptographic system often depend on the length and complexity of the encryption keys. Longer keys are generally more secure because they increase the number of possible combinations that an attacker would need to try in order to break the encryption.
Effective key management is essential to maintain the integrity of cryptographic systems. This includes secure key generation, distribution, storage, rotation, and disposal. In many cases, hardware security modules (HSMs) are used to securely store and manage encryption keys to prevent unauthorized access or theft.
Do You Want to Learn More About Cybersecurity?
Are you interested in delving deeper into the realm of cybersecurity? With the ever-growing importance of safeguarding digital systems and data, gaining expertise in this field is invaluable. Notable certifications such as Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), and CompTIA Security+ offer comprehensive knowledge and skills that can elevate your understanding of cybersecurity principles and practices. Furthermore, exploring frameworks like COBIT 2019 can provide you with a structured approach to governance and management of enterprise information technology. These certifications and frameworks encompass a wide range of topics, from risk management and security controls to compliance and governance. Whether you're just beginning your journey or seeking to advance your career, these resources can serve as essential guides on your path to becoming a proficient cybersecurity professional.
FAQs
-
What is Data Encryption?
Data encryption is the process of converting plaintext data into ciphertext using cryptographic algorithms. It ensures the confidentiality and security of sensitive information by rendering it unreadable to unauthorized parties.
-
Why is Data Encryption Important?
Data encryption is crucial for protecting sensitive information from unauthorized access and breaches. It helps maintain privacy, prevents data leaks, and ensures the integrity of transmitted and stored data.
-
What are the Types of Data Encryption?
There are two main types of data encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
-
What Are Some Common Symmetric Encryption Algorithms?
Common symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). AES, in particular, is widely used due to its security and efficiency.
-
What Are Some Common Asymmetric Encryption Algorithms?
Well-known asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC). These algorithms are used for secure key exchange, digital signatures, and ensuring data confidentiality.
-
How Does Data Encryption Work in Secure Communications?
In secure communications, asymmetric encryption is often used. The sender encrypts the data with the recipient's public key, and the recipient decrypts it using their private key. This ensures that only the intended recipient can read the message.
-
What is the Role of Data Encryption in Cloud Security?
Data encryption plays a vital role in cloud security by ensuring that data stored in cloud servers remains protected from unauthorized access. Encryption helps mitigate risks associated with data breaches and unauthorized data exposure.
-
Can Encrypted Data Be Hacked?
Encrypted data can be decrypted, but the process is highly complex and requires extensive computational resources and time. Strong encryption algorithms with long key lengths make it exceedingly difficult for attackers to break the encryption.
-
What is End-to-End Encryption?
End-to-end encryption is a form of communication encryption where data is encrypted on the sender's side and decrypted only on the recipient's side. This prevents intermediaries, including service providers, from accessing the plaintext data.
-
What Are the Best Practices for Data Encryption Implementation?
Effective data encryption implementation involves key management, using strong encryption algorithms, securing keys with hardware modules, regular security audits, and keeping up with advancements in encryption technologies.
-
Is Data Encryption Used Only for Confidentiality?
While confidentiality is a primary goal of data encryption, it also ensures data integrity, authenticity, and non-repudiation. Encryption plays a significant role in ensuring the overall security of digital transactions and communications.
Read More
In an increasingly interconnected digital world, where data is both the lifeblood and the target of modern endeavors, the need for robust data protection has never been more critical. At the heart of this defense lies the art and science of data encryption—an intricate process that transforms information into an unreadable code, rendering it impervious to prying eyes. This exploration into the realm of data encryption aims to unravel its intricacies, unveiling the diverse types, sophisticated algorithms, ingenious techniques, and strategic approaches that together fortify the security of our digital landscape. From the symmetrical dance of keys to the asymmetric harmony of secure communications, from the impenetrable armor of Advanced Encryption Standard (AES) to the mathematical elegance of RSA and Elliptic Curve Cryptography (ECC), this journey will delve into the mechanisms that power our defenses against data breaches and unauthorized access. We will navigate through the labyrinth of encryption methods, discerning the nuanced interplay of confidentiality, integrity, and authenticity that they orchestrate. Whether you're a curious explorer of technology or an ardent guardian of data integrity, join us as we embark on an enlightening expedition into the world of data encryption, where each layer of knowledge adds another layer of protection.
Table of Contents
What is Data Encryption?
How Does Data Encryption Work?
Why Do We Need Data Encryption?
What are the 2 Types of Data Encryption Techniques?
What is Hashing?
What is an Encryption Algorithm?
Best Encryption Algorithms
3DES
The Future of Data Encryption
Should You Use Symmetric or Asymmetric Encryption?
Businesses Use Encryption For Many Purposes
Steps to Implement an Effective Encryption Strategy
What Is a Key in Cryptography?
Do You Want to Learn More About Cybersecurity?
FAQs
What is Data Encryption?
Data encryption is the process of converting understandable data into an unreadable form, known as ciphertext, using complex algorithms and a secret key. This transformation ensures that even if unauthorized parties gain access to the encrypted data, they cannot comprehend its original meaning without the corresponding decryption key. Encryption serves as a vital mechanism for safeguarding sensitive information during storage, transmission, and processing, thwarting unauthorized access and maintaining data confidentiality. It finds application in various realms such as online transactions, secure communication, and data protection, offering varying levels of security through different encryption methods and algorithms tailored to specific needs.
How Does Data Encryption Work?
Data encryption functions by utilizing complex algorithms to convert plain data into an unintelligible form known as ciphertext. This process involves an encryption key that serves as the foundation for the transformation. The chosen algorithm determines how the encryption and decryption keys interact. During encryption, the algorithm combines the encryption key with the plaintext, generating ciphertext that appears as random characters. This ciphertext can be safely transmitted or stored without revealing the original information. To reverse the process, decryption employs the corresponding decryption key, allowing the recipient to transform the ciphertext back into readable plaintext. The security of encrypted data hinges on robust algorithms, secure key management, and effective protection against unauthorized access to the encryption keys.
Why Do We Need Data Encryption?
Data encryption is a vital necessity due to its role in shielding sensitive information from unauthorized access and maintaining confidentiality. It acts as a bulwark against privacy breaches by converting data into an unreadable format, making it indecipherable without the appropriate decryption key. This protection is essential across diverse domains, from safeguarding personal data and financial records to upholding regulatory compliance and mitigating the impact of data breaches. Encryption not only secures communication over networks and cloud storage but also fortifies authentication procedures and shields intellectual property from prying eyes. In an era of global connectivity, encryption stands as a cornerstone of cybersecurity, ensuring the security and privacy of digital interactions and sensitive information.
What are the 2 Types of Data Encryption Techniques?
Data encryption techniques can be broadly categorized into two main types: Symmetric Encryption and Asymmetric Encryption.
-
Symmetric Encryption: In symmetric encryption, a single encryption key is used for both the encryption and decryption processes. The same key is shared between the sender and the recipient. The main advantage of symmetric encryption is its speed and efficiency, as the algorithms used are generally faster than their asymmetric counterparts. However, the challenge lies in securely exchanging the encryption key between parties without it being intercepted by unauthorized individuals. Common symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
-
Asymmetric Encryption: Asymmetric encryption, also known as public-key encryption, employs a pair of keys: a public key and a private key. The public key is used for encryption, while the private key is used for decryption. The keys are mathematically related but cannot be practically derived from each other. This setup addresses the key exchange challenge of symmetric encryption, as the public key can be freely shared without compromising the security of the private key. Asymmetric encryption provides a higher level of security for tasks like secure communication and digital signatures. RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are examples of asymmetric encryption algorithms.
Both types of encryption techniques have their advantages and are often used together to address specific security needs. Symmetric encryption is suitable for encrypting large amounts of data quickly, while asymmetric encryption is valuable for secure key exchange and ensuring the authenticity of communication parties.
What is Hashing?
Hashing is a cryptographic technique that involves transforming input data into a fixed-length string of characters, known as a hash value. This process is designed to be fast and deterministic, meaning the same input will always produce the same hash value. Hashing serves various purposes, such as verifying data integrity and authenticity. It ensures data integrity by generating a unique representation of the input data, making it easy to detect even minor changes in the data. Hashing is commonly used for tasks like password storage, where passwords are hashed and stored to enhance security. Additionally, hashing underpins digital signatures, providing a way to confirm the authenticity of digital documents and messages. However, it's important to choose secure and collision-resistant hash functions to prevent vulnerabilities and ensure the reliability of hash-based applications.
What is an Encryption Algorithm?
An encryption algorithm is a set of mathematical rules and procedures used to transform data from its original, readable form (plaintext) into an unreadable and secure format (ciphertext) during encryption, and to revert it back to plaintext during decryption. It dictates how the encryption key interacts with the data to produce the ciphertext and how the decryption key is used to reverse the process. Encryption algorithms play a pivotal role in maintaining data security and confidentiality, ensuring that sensitive information remains protected from unauthorized access and interception. These algorithms come in two main types: symmetric, which use the same key for both encryption and decryption, and asymmetric (public-key), which employ a pair of keys for these operations. The selection of an encryption algorithm depends on factors such as security requirements, key management, and the specific application's needs.
Best Encryption Algorithms
The "best" encryption algorithm depends on the specific use case, security requirements, and the state of current cryptographic research. However, as of my last knowledge update in September 2021, I can mention some widely recognized and respected encryption algorithms that were considered strong at that time:
-
AES (Advanced Encryption Standard): AES is one of the most widely used symmetric encryption algorithms. It offers strong security and efficiency and is considered secure for a wide range of applications. AES operates with varying key lengths, including 128-bit, 192-bit, and 256-bit.
-
RSA (Rivest-Shamir-Adleman): RSA is a well-known asymmetric encryption algorithm used for secure key exchange, digital signatures, and other cryptographic tasks. It relies on the difficulty of factoring large prime numbers to provide security.
-
ECC (Elliptic Curve Cryptography): ECC is another asymmetric encryption algorithm known for its strong security and relatively shorter key lengths compared to RSA. It is particularly well-suited for resource-constrained environments, such as mobile devices.
-
SHA-256 (Secure Hash Algorithm 256-bit): While not an encryption algorithm per se, SHA-256 is a widely used cryptographic hash function. It's used for various purposes, including generating digital signatures and verifying data integrity.
-
ChaCha20 and Poly1305: These are modern cryptographic algorithms designed to provide encryption and data integrity in a combined mode. They are becoming popular choices, especially for use in stream cipher constructions.
It's important to note that cryptographic algorithms and best practices can evolve over time due to advances in technology and cryptanalysis. Organizations should stay updated with the latest recommendations from reputable sources, such as NIST (National Institute of Standards and Technology), to ensure they are using algorithms that meet current security standards. Additionally, the strength of encryption also relies on proper key management, implementation, and the overall security of the system in which it is used.
3DES
Triple Data Encryption Standard (3DES), also known as TDEA (Triple Data Encryption Algorithm), is a symmetric encryption algorithm that provides a higher level of security compared to the original Data Encryption Standard (DES) algorithm. 3DES applies the DES algorithm three times in a cascade, using multiple keys. This process significantly increases the effective key length and enhances security.
Here's how 3DES works:
-
Key Generation: Three separate keys are generated, often referred to as Key 1, Key 2, and Key 3.
-
Encryption: The plaintext data undergoes three consecutive rounds of encryption using the three keys. The data is first encrypted with Key 1, then decrypted using Key 2, and finally encrypted again using Key 3.
-
Decryption: To decrypt the data, the process is reversed. The ciphertext is decrypted with Key 3, then encrypted with Key 2, and finally decrypted using Key 1.
3DES provides an effective key length of 168 bits, as each of the three keys is 56 bits long. This makes it significantly more secure than the original DES, which had a 56-bit key length and became susceptible to brute-force attacks as computing power increased. However, it's worth noting that 3DES is not as efficient as more modern symmetric encryption algorithms like AES, which offer better performance and security with shorter key lengths.
3DES was widely adopted as an interim solution when transitioning from DES to more secure algorithms. However, due to its relatively slower performance and the availability of more efficient encryption algorithms, such as AES, it's recommended to use AES for new implementations requiring strong symmetric encryption.
The Future of Data Encryption
The future of data encryption holds several promising trends and challenges. Post-Quantum Cryptography is actively being researched to ensure encryption methods remain secure against the potential threat of quantum computers. Homomorphic encryption presents opportunities for processing data while it remains encrypted, enhancing privacy and security. Zero-knowledge proofs could revolutionize authentication and digital identity, while encryption's role in securing blockchain networks will continue to be paramount. Enhanced key management practices, such as hardware security modules and secure key distribution, will strengthen encryption protocols. Quantum Key Distribution offers ultra-secure methods for key exchange. The synergy of AI and encryption is likely to optimize processes and enhance overall security. As regulations evolve, encryption laws may adapt to balance security and law enforcement needs. Usability improvements and broader integration into applications and devices will be pivotal for increasing encryption adoption. Staying abreast of these developments will be essential as the landscape of data encryption continues to evolve dynamically.
Should You Use Symmetric or Asymmetric Encryption?
The decision to use symmetric or asymmetric encryption hinges on the context and security requirements of the scenario. Symmetric encryption offers speed and efficiency, making it suitable for encrypting large data volumes. However, it demands a secure method of distributing the shared key among parties. Asymmetric encryption, while slower, addresses the challenge of secure key exchange and is pivotal for scenarios where parties don't share a pre-established secret key. Asymmetric encryption's application extends to digital signatures and secure communication with key exchange. Often, a hybrid approach is employed, utilizing both encryption types to leverage their strengths. In such cases, asymmetric encryption may be used to securely establish a symmetric encryption key, enabling efficient data encryption. Ultimately, the choice should align with specific security needs, key management complexity, and the speed requirements of the given use case, ensuring an appropriate balance between security and practicality.
Businesses Use Encryption For Many Purposes
Businesses leverage encryption for a multitude of purposes to reinforce their data security measures and uphold the integrity of their operations. Encryption is extensively employed to shield sensitive customer data, proprietary information, and financial records, thereby thwarting unauthorized access and data breaches. It's pivotal in securing communication channels, such as emails and instant messaging, ensuring that confidential information remains private during transmission. Encryption also underpins secure financial transactions on e-commerce platforms and online banking systems. It bolsters password security by storing user credentials securely and helps businesses adhere to regulatory frameworks like GDPR and HIPAA, safeguarding them from legal consequences and maintaining customer trust. Additionally, encryption is paramount for cloud security, remote work scenarios, secure file sharing, digital signatures, IoT security, and preserving the confidentiality of sensitive data within supply chains. Overall, encryption is a cornerstone of modern business strategies, fostering data protection and bolstering organizational reputation.
Steps to Implement an Effective Encryption Strategy
Implementing an effective encryption strategy involves a systematic approach to ensure the security of sensitive data. Here are five key steps to guide the process:
-
Data Classification and Assessment: Begin by identifying and classifying the types of data that require encryption. Conduct a thorough assessment of your organization's data landscape to determine which data is sensitive and where it resides. This includes data at rest, in transit, and during processing.
-
Security Requirements Definition: Define your security requirements based on the sensitivity of the data. Determine which encryption algorithms and key lengths are appropriate for different data types and use cases. Consider compliance regulations and industry standards that apply to your organization.
-
Encryption Implementation: Select suitable encryption solutions and tools that align with your requirements. Implement encryption mechanisms for data at rest and in transit. For data at rest, utilize encryption features provided by databases, operating systems, or storage solutions. For data in transit, employ secure protocols such as TLS/SSL for network communication.
-
Key Management and Access Control: Develop a robust key management strategy. Establish procedures for generating, storing, rotating, and revoking encryption keys. Ensure that only authorized personnel have access to encryption keys. Implement strong access controls to prevent unauthorized users from accessing encrypted data.
-
Testing, Monitoring, and Compliance: Thoroughly test your encryption implementation to ensure its effectiveness and compatibility with your systems. Regularly monitor encryption processes, access logs, and audit trails to detect any anomalies or unauthorized access attempts. Conduct periodic security assessments and audits to ensure compliance with encryption policies and regulations.
By following these steps, you can create a structured and comprehensive encryption strategy that safeguards sensitive data, mitigates risks, and aligns with industry best practices and compliance standards.
What Is a Key in Cryptography?
In cryptography, a key refers to a specific piece of information, often a sequence of characters, numbers, or bits, that is used to control the encryption and decryption processes. Keys play a central role in cryptographic operations by determining how data is transformed from its original form (plaintext) to an encrypted form (ciphertext) and back to plaintext.
There are two main types of keys in cryptography:
-
Encryption Key: This key is used during the encryption process to convert plaintext into ciphertext. The encryption key is known only to authorized parties involved in secure communication or data protection.
-
Decryption Key: This key is used during the decryption process to revert the ciphertext back to its original plaintext. In symmetric encryption, the same key is used for both encryption and decryption. In asymmetric encryption (public-key cryptography), there is a pair of keys: a public key for encryption and a private key for decryption.
Keys are kept confidential to ensure the security of encrypted data. The strength and security of a cryptographic system often depend on the length and complexity of the encryption keys. Longer keys are generally more secure because they increase the number of possible combinations that an attacker would need to try in order to break the encryption.
Effective key management is essential to maintain the integrity of cryptographic systems. This includes secure key generation, distribution, storage, rotation, and disposal. In many cases, hardware security modules (HSMs) are used to securely store and manage encryption keys to prevent unauthorized access or theft.
Do You Want to Learn More About Cybersecurity?
Are you interested in delving deeper into the realm of cybersecurity? With the ever-growing importance of safeguarding digital systems and data, gaining expertise in this field is invaluable. Notable certifications such as Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), Certified Information Systems Auditor (CISA), and CompTIA Security+ offer comprehensive knowledge and skills that can elevate your understanding of cybersecurity principles and practices. Furthermore, exploring frameworks like COBIT 2019 can provide you with a structured approach to governance and management of enterprise information technology. These certifications and frameworks encompass a wide range of topics, from risk management and security controls to compliance and governance. Whether you're just beginning your journey or seeking to advance your career, these resources can serve as essential guides on your path to becoming a proficient cybersecurity professional.
FAQs
-
What is Data Encryption?
Data encryption is the process of converting plaintext data into ciphertext using cryptographic algorithms. It ensures the confidentiality and security of sensitive information by rendering it unreadable to unauthorized parties.
-
Why is Data Encryption Important?
Data encryption is crucial for protecting sensitive information from unauthorized access and breaches. It helps maintain privacy, prevents data leaks, and ensures the integrity of transmitted and stored data.
-
What are the Types of Data Encryption?
There are two main types of data encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption.
-
What Are Some Common Symmetric Encryption Algorithms?
Common symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES). AES, in particular, is widely used due to its security and efficiency.
-
What Are Some Common Asymmetric Encryption Algorithms?
Well-known asymmetric encryption algorithms include RSA (Rivest-Shamir-Adleman) and Elliptic Curve Cryptography (ECC). These algorithms are used for secure key exchange, digital signatures, and ensuring data confidentiality.
-
How Does Data Encryption Work in Secure Communications?
In secure communications, asymmetric encryption is often used. The sender encrypts the data with the recipient's public key, and the recipient decrypts it using their private key. This ensures that only the intended recipient can read the message.
-
What is the Role of Data Encryption in Cloud Security?
Data encryption plays a vital role in cloud security by ensuring that data stored in cloud servers remains protected from unauthorized access. Encryption helps mitigate risks associated with data breaches and unauthorized data exposure.
-
Can Encrypted Data Be Hacked?
Encrypted data can be decrypted, but the process is highly complex and requires extensive computational resources and time. Strong encryption algorithms with long key lengths make it exceedingly difficult for attackers to break the encryption.
-
What is End-to-End Encryption?
End-to-end encryption is a form of communication encryption where data is encrypted on the sender's side and decrypted only on the recipient's side. This prevents intermediaries, including service providers, from accessing the plaintext data.
-
What Are the Best Practices for Data Encryption Implementation?
Effective data encryption implementation involves key management, using strong encryption algorithms, securing keys with hardware modules, regular security audits, and keeping up with advancements in encryption technologies.
-
Is Data Encryption Used Only for Confidentiality?
While confidentiality is a primary goal of data encryption, it also ensures data integrity, authenticity, and non-repudiation. Encryption plays a significant role in ensuring the overall security of digital transactions and communications.
Exploring the Pros and Cons of Scrum Project Management
In the dynamic realm of modern project management, the Scrum methodology has risen to prominence as a game-changing approach. Rooted in Agile principles, Scrum offers a framework that thrives on collaboration, adaptability, and iterative progress. Amidst this landscape, professionals seeking to refine their project management skills have found value in specialized training courses like PMI-ACP, CSM, and CSPO.
Join us in this exploration as we navigate the intricacies of Scrum project management, delving into its advantages and drawbacks. With a keen focus on the PMI-ACP, CSM, and CSPO training courses, we will uncover how these certifications equip individuals with the knowledge and tools to excel within the Scrum framework. By evaluating the pros and cons of Scrum and its interplay with these training pathways, we empower professionals to make strategic choices aligning with their career ambitions and project management objectives.
Whether you're an established project management expert or a newcomer to the field, this journey promises valuable insights into the synergy between Scrum, project management certifications, and professional development. Let's embark on this illuminating expedition, unraveling the potential that emerges at the crossroads of Scrum methodology and specialized training.
Table of Contents
- What is Scrum?
- What Is Scrum Framework?
- What is Scrum in Project Management?
- The Application of Scrum in Project Management
- Advantages and Disadvantages of Scrum Project Management
- Scrum Roles
- Comprehending the Role of Project Manager in Scrum – The Scrum Master vs. the Project Manager
- 6 Steps of Scrum Process
- Key Scrum Tools to Get You Through Your Next Sprint
- Becoming a Certified Scrum Master
What is Scrum?
Scrum is an agile framework used in project management and software development to help teams work collaboratively and efficiently on complex projects. It emphasizes flexibility, adaptability, and iterative progress. Scrum provides a structured approach to managing tasks and delivering valuable outcomes in a dynamic and ever-changing environment.
Key characteristics of Scrum include:
- Iterative and Incremental Development: Scrum breaks down the project into smaller iterations called "sprints." Each sprint typically lasts 1 to 4 weeks and results in a potentially shippable product increment. This allows for continuous feedback and the ability to adapt to changing requirements.
- Roles and Responsibilities: Scrum defines specific roles within the team. The key roles are the Product Owner, who represents the stakeholders and defines the product backlog, the Scrum Master, who facilitates the Scrum process and supports the team, and the Development Team, responsible for delivering the product increment.
- Product Backlog: The product backlog is a prioritized list of features, enhancements, and fixes that need to be addressed in the project. The Product Owner is responsible for maintaining and prioritizing this list.
- Sprint Planning: At the beginning of each sprint, the team conducts a sprint planning meeting to select items from the product backlog to work on during the sprint. The team then defines the tasks required to complete those items.
- Daily Scrum (Standup): The team holds a daily standup meeting where each member briefly discusses what they've done since the last meeting, what they're working on, and any obstacles they're facing. This fosters transparency and collaboration within the team.
- Sprint Review: At the end of each sprint, the team holds a sprint review to demonstrate the completed work to stakeholders. This provides an opportunity for feedback and helps the team make adjustments based on that feedback.
- Sprint Retrospective: After the sprint review, the team holds a retrospective to reflect on the sprint process and identify areas for improvement. This continuous improvement cycle is a core aspect of Scrum.
- Time-Boxing: Scrum uses time-boxing to limit the duration of meetings and activities, ensuring that they don't drag on indefinitely.
Scrum encourages a culture of collaboration, self-organization, and continuous improvement. It's particularly well-suited for projects where requirements are likely to change or evolve, as the framework allows teams to pivot and adapt quickly. Scrum is widely used in various industries, not just software development, to manage projects of varying complexity.
What Is Scrum Framework?
The Scrum framework is an agile methodology used in project management and product development to deliver value incrementally and iteratively. It provides a structured approach for teams to work collaboratively and efficiently, especially in environments where requirements are dynamic and subject to change. The framework is designed to promote flexibility, transparency, and continuous improvement.
The Scrum framework consists of several key components and practices:
- Roles:
- Product Owner: Represents the stakeholders and is responsible for defining and prioritizing the product backlog, which contains the list of features, enhancements, and fixes to be addressed.
- Scrum Master: Facilitates the Scrum process, ensures adherence to Scrum principles, and helps remove any obstacles that the team encounters.
- Development Team: Cross-functional group responsible for delivering the product increment. The team self-organizes and collaborates to complete the work within each sprint.
- Artifacts:
- Product Backlog: A prioritized list of items that need to be addressed in the project. These items can include user stories, bug fixes, technical tasks, and more.
- Sprint Backlog: The subset of items from the product backlog that the team commits to completing during a specific sprint.
- Increment: The sum of completed items at the end of a sprint. It should be a potentially shippable product that adds value to the product.
- Events:
- Sprint: A time-boxed iteration, typically lasting 1 to 4 weeks, during which the team works on completing items from the sprint backlog.
- Sprint Planning: A meeting held at the beginning of each sprint where the team selects items from the product backlog to work on and defines the tasks required to complete them.
- Daily Scrum (Standup): A brief daily meeting where team members share updates on their progress, plans, and any obstacles they are facing.
- Sprint Review: A meeting at the end of each sprint where the team demonstrates the completed work to stakeholders and gathers feedback.
- Sprint Retrospective: A meeting held after the sprint review to reflect on the sprint process, identify strengths and areas for improvement, and make adjustments.
- Principles:
- Empirical Process Control: Scrum is based on transparency, inspection, and adaptation. It encourages teams to learn from their experiences and adjust their processes accordingly.
- Self-Organization: Teams are responsible for organizing themselves and making decisions, which fosters ownership and accountability.
- Collaboration: Scrum emphasizes close collaboration among team members, stakeholders, and customers to ensure the best possible outcome.
- Incremental Delivery: Value is delivered in small increments, allowing for faster feedback and the ability to respond to changing requirements.
Overall, the Scrum framework provides a structured way to manage projects by breaking them down into smaller, manageable chunks and continuously improving the process based on feedback and real-world results. It's widely used in various industries and sectors for its adaptability and focus on delivering value to customers.
What is Scrum in Project Management?
Scrum in project management is an agile framework that focuses on delivering projects in a flexible and iterative manner. It was originally developed for software development but has since been applied to various types of projects in different industries. Scrum aims to address the challenges of managing projects in dynamic and rapidly changing environments by promoting collaboration, adaptability, and continuous improvement.
In the context of project management, Scrum provides a structured approach to planning, executing, and delivering projects by breaking them into smaller, manageable components. These smaller components are called sprints, and each sprint involves a defined set of tasks and goals. Here's how Scrum works in project management:
- Product Owner: The product owner is responsible for representing the interests of stakeholders, understanding project requirements, and prioritizing the work that needs to be done. The product owner maintains the product backlog, which is a dynamic list of features, tasks, and changes that need to be addressed.
- Scrum Team: The Scrum team is a cross-functional group of individuals responsible for delivering the project increment. This team includes developers, designers, testers, and other relevant roles. The team collectively decides how much work they can commit to during a sprint.
- Sprint Planning: At the beginning of each sprint, the team holds a sprint planning meeting. During this meeting, they review the items in the product backlog, select the items they will work on during the sprint, and create a sprint backlog—a list of tasks required to complete the selected items.
- Sprint: A sprint is a time-boxed iteration that typically lasts 1 to 4 weeks. The team works on the tasks identified in the sprint backlog. At the end of the sprint, they aim to deliver a potentially shippable product increment—a working piece of the project that adds value.
- Daily Scrum (Standup): The team holds a daily standup meeting to discuss progress, obstacles, and plans for the day. Each team member shares what they accomplished, what they plan to work on next, and if they're facing any challenges.
- Sprint Review: At the end of each sprint, the team holds a sprint review. They demonstrate the completed work to stakeholders and gather feedback. This helps ensure that the project is on the right track and that any necessary adjustments can be made.
- Sprint Retrospective: After the sprint review, the team conducts a retrospective meeting to reflect on the sprint process. They discuss what went well, what could be improved, and any changes they want to implement in the next sprint.
- Continuous Improvement: One of the core principles of Scrum is continuous improvement. Teams regularly analyze their processes and make adjustments to enhance efficiency, collaboration, and overall project delivery.
Scrum's iterative and incremental approach allows for flexibility and responsiveness to changing requirements and priorities. It's especially effective for projects where the initial requirements may evolve over time, as the framework supports adapting to new information and customer feedback.
The Application of Scrum in Project Management
Scrum is widely applied in project management, especially in software development, due to its adaptability and focus on iterative progress. However, its principles and practices can be extended to various types of projects in different industries. Here are some key applications of Scrum in project management:
- Software Development: The most common application of Scrum is in software development. It allows development teams to work on small, manageable chunks of functionality in each sprint, ensuring that valuable features are delivered regularly and enabling quick responses to changing requirements.
- Product Development: Beyond software, Scrum can be applied to the development of physical products. It enables cross-functional teams to collaborate on designing, prototyping, testing, and delivering products in iterations, ensuring that customer needs are met effectively.
- Marketing Campaigns: Scrum can be used in marketing projects where campaigns are broken down into sprints. Marketing teams can work on individual tasks like content creation, social media engagement, and analytics, delivering measurable results at the end of each sprint.
- Event Planning: For event management projects, Scrum can help organize tasks such as venue selection, logistics planning, participant engagement, and post-event analysis. Sprints can align with the various phases of event preparation.
- Research and Development: In R&D projects, Scrum allows researchers and developers to focus on specific aspects of a project, quickly experiment with new ideas, and pivot based on the results obtained within short iterations.
- Construction Projects: Construction projects can benefit from Scrum by dividing complex tasks like site preparation, foundation construction, and building phases into sprints. This helps manage resources, track progress, and adapt to unexpected challenges.
- Educational Programs: Scrum can be used to structure educational programs and courses. Each sprint corresponds to a learning module, and students make incremental progress, receive feedback, and adapt their learning journey based on their understanding.
- Content Creation: Content projects, such as writing articles, producing videos, or designing graphics, can benefit from Scrum's iterative approach. Sprints can focus on different content pieces, and regular reviews ensure content quality.
- Healthcare Projects: Scrum principles can be applied to healthcare projects, such as implementing new medical technologies, improving patient care processes, or developing healthcare apps. This approach promotes collaboration among medical professionals, developers, and other stakeholders.
- Consulting and Professional Services: Scrum can be used in consulting projects, where each sprint focuses on specific deliverables or recommendations for clients, ensuring that value is provided incrementally and allowing for client feedback.
When applying Scrum in project management, it's important to tailor the practices to suit the specific needs and context of the project. The framework encourages adaptability and continuous improvement, so teams can experiment with different approaches to find the best fit for their project's goals and requirements.
Advantages and Disadvantages of Scrum Project Management
Scrum project management offers several advantages and disadvantages, which can impact its suitability for different projects and teams. Here's an overview of the pros and cons of using the Scrum framework:
Advantages:
- Flexibility: Scrum's iterative approach allows teams to adapt to changing requirements and priorities, making it well-suited for projects with evolving needs.
- Customer Satisfaction: Regularly delivering working increments of the project allows stakeholders to see progress and provide feedback, ensuring the final product meets their expectations.
- Collaboration: Scrum encourages close collaboration among team members, stakeholders, and customers, fostering a sense of ownership and shared responsibility.
- Transparency: The framework promotes transparency through daily standup meetings, sprint reviews, and sprint retrospectives, ensuring everyone is aware of the project's status and challenges.
- Faster Time-to-Market: Incremental delivery means that features can be released more quickly, enabling a shorter time-to-market compared to traditional project management approaches.
- Risk Mitigation: Frequent reviews and adaptability help identify and address risks early in the project, reducing the likelihood of major setbacks.
- Continuous Improvement: Regular sprint retrospectives encourage teams to reflect on their processes and make adjustments, leading to ongoing process improvement.
- Motivated Teams: Scrum empowers teams to self-organize and make decisions, fostering a sense of ownership and motivation among team members.
Disadvantages:
- Complexity: Scrum has several roles, events, and artifacts, which can be overwhelming for teams new to the framework or for smaller projects.
- Lack of Predictability: The adaptive nature of Scrum can make it challenging to predict exact project timelines and outcomes, which might be problematic for projects with strict deadlines.
- Requires Skilled Team Members: Effective Scrum implementation requires skilled team members who understand the framework and its principles.
- High Dependency on Product Owner: The product owner's availability and decision-making play a critical role in prioritizing and clarifying tasks. Their absence or lack of involvement can impact the project.
- Inaccurate Initial Estimates: Because Scrum focuses on delivering small increments, it might be challenging to provide accurate estimates for the entire project at the outset.
- Lack of Documentation: The focus on working increments can sometimes lead to inadequate documentation, which might be required for compliance or future maintenance.
- Need for Continuous Involvement: Scrum requires consistent participation from all team members throughout the project, which might not be feasible in certain environments.
- Resistance to Change: Teams accustomed to traditional project management methods may face resistance in transitioning to the agile practices of Scrum.
Ultimately, the decision to use Scrum in project management depends on factors like project complexity, team composition, stakeholder involvement, and the organization's culture. It's important to carefully evaluate the advantages and disadvantages to determine whether Scrum aligns with the project's needs and objectives.
Top of Form
Scrum Roles
In the Scrum framework, there are three key roles that contribute to the successful implementation of the methodology within a project. These roles promote collaboration, responsibility, and effective communication within the team. Here are the three Scrum roles:
- Product Owner:
- The Product Owner represents the stakeholders, customers, and users of the product being developed. They are responsible for maximizing the value delivered by the team.
- Key responsibilities include defining and maintaining the product backlog, prioritizing items within it, and ensuring that the team understands the requirements and goals.
- The Product Owner makes decisions about what features or items should be worked on, and their decisions guide the team's work during each sprint.
- Scrum Master:
- The Scrum Master is a servant-leader who ensures that the Scrum framework is understood, followed, and continuously improved by the team.
- They act as a facilitator and coach, helping the team to self-organize and make decisions collectively. They also remove obstacles and impediments that the team might encounter.
- The Scrum Master fosters a collaborative and productive environment, guides the team in adhering to Scrum practices, and helps improve the team's effectiveness.
- Development Team:
- The Development Team is a cross-functional group of professionals responsible for delivering the product increment during each sprint.
- The team members collectively have the skills and expertise needed to design, develop, test, and deliver the product features.
- They collaborate closely, self-organize to manage their work, and collectively commit to achieving the goals of each sprint.
It's important to note that in Scrum, these roles are distinct, and individuals typically do not hold multiple roles simultaneously. Each role has specific responsibilities that contribute to the successful implementation of the framework. Additionally, Scrum emphasizes collaboration among the roles, as well as with stakeholders, to ensure that the project's goals and requirements are met.
Comprehending the Role of Project Manager in Scrum – The Scrum Master vs. the Project Manager
In the Scrum framework, the role of a Project Manager is quite distinct from the role of a Scrum Master. Both roles play important parts in project management, but their responsibilities, focus, and approach can differ significantly. Here's a comparison of the two roles:
Scrum Master:
- Responsibilities:
- Facilitating the Scrum Process: The Scrum Master ensures that the Scrum framework is understood and followed by the team, helping to maintain the Scrum events, roles, and artifacts.
- Coaching and Mentoring: They coach the team on self-organization, cross-functionality, and effective collaboration. They help the team continuously improve and achieve their best potential.
- Removing Obstacles: The Scrum Master identifies and removes impediments that hinder the team's progress, ensuring that the team can work smoothly.
- Promoting Empowerment: They empower the team to make their own decisions and self-organize, fostering a sense of ownership and accountability.
- Shielding from External Interference: The Scrum Master helps protect the team from external disruptions and influences to maintain focus during sprints.
- Focus:
- Team Dynamics: The Scrum Master's primary focus is on fostering a productive and collaborative team environment, ensuring that the team can work efficiently and effectively.
- Process Adherence: They ensure that the Scrum process is followed and adapted appropriately to suit the team's needs while upholding Scrum principles.
Project Manager:
- Responsibilities:
- Planning and Scheduling: The Project Manager is responsible for planning the project, defining tasks, setting timelines, and creating a project schedule.
- Resource Management: They allocate resources, assign tasks, and ensure that the project is adequately staffed to meet its goals.
- Budget Management: The Project Manager handles budgeting, cost estimation, and resource allocation to ensure the project stays within budget.
- Risk Management: They identify potential risks, develop mitigation strategies, and manage any issues that arise during the project.
- Stakeholder Communication: The Project Manager communicates with stakeholders, updates them on project progress, and manages their expectations.
- Focus:
- Deliverables and Objectives: The Project Manager's primary focus is on meeting project goals, delivering the desired outcome, and ensuring that the project aligns with business objectives.
- Planning and Execution: They oversee the overall project planning and execution, ensuring that tasks are completed according to the plan.
In the context of Scrum, the Scrum Master's role is more about enabling the team to work effectively within the Scrum framework, while the Project Manager's role is broader and encompasses the overall management of the project. In many Scrum implementations, the traditional role of a Project Manager may shift to other roles (such as Product Owner or team member) or may be less prominent, as Scrum promotes self-organization and collaborative decision-making within the team. However, in organizations that use both traditional project management and Scrum, the Project Manager might still have a role to play in coordinating higher-level activities and aligning multiple Scrum teams with organizational goals.
6 Steps of Scrum Process
The Scrum process consists of several iterative and recurring steps that help teams deliver value incrementally and adapt to changing requirements. Here are the six key steps of the Scrum process:
- Product Backlog Creation:
- The process begins with the creation of the product backlog, which is a dynamic list of items that need to be addressed in the project. These items can include features, bug fixes, technical tasks, and more.
- The Product Owner is responsible for maintaining and prioritizing the product backlog based on input from stakeholders, customers, and the team.
- Sprint Planning:
- Before the start of each sprint, the team holds a sprint planning meeting.
- During this meeting, the Product Owner presents the items from the product backlog that are of the highest priority and have been refined to a sufficient level.
- The Development Team works with the Product Owner to select items from the product backlog that they believe they can complete during the sprint.
- The team breaks down the selected items into smaller tasks and estimates the effort required for each task.
- Sprint Execution:
- The sprint execution phase begins after the sprint planning meeting and typically lasts 1 to 4 weeks.
- The Development Team works on the tasks identified during the sprint planning, collaboratively building and testing the product increment.
- Daily standup meetings are held to provide updates on progress, discuss obstacles, and align the team.
- Daily Scrum (Standup):
- Each day during the sprint, the team holds a brief daily standup meeting, known as the Daily Scrum.
- Team members answer three questions: What did I accomplish yesterday? What will I work on today? Are there any obstacles in my way?
- This meeting helps the team stay synchronized, identify potential issues, and make real-time adjustments.
- Sprint Review:
- At the end of the sprint, the team holds a sprint review meeting.
- The team demonstrates the completed work to stakeholders and the Product Owner.
- Feedback is gathered, and stakeholders have an opportunity to evaluate the product increment and suggest changes.
- Sprint Retrospective:
- Following the sprint review, the team conducts a sprint retrospective meeting.
- The team reflects on the sprint process and discusses what went well, what could be improved, and what actions should be taken to enhance future sprints.
- The retrospective helps the team identify and implement process improvements, fostering a culture of continuous learning.
After the sprint retrospective, the process begins again with the creation of a new sprint and the selection of items from the product backlog. This cyclical process allows the team to continuously improve and refine their work based on feedback, making Scrum a highly adaptive and iterative framework.
Key Scrum Tools to Get You Through Your Next Sprint
Scrum emphasizes people and interactions over tools, but using the right tools can certainly enhance collaboration, communication, and productivity during sprints. Here are some key Scrum tools that can help you manage your next sprint effectively:
- Scrum Board or Kanban Board:
- A visual representation of the sprint backlog and its tasks.
- Helps the team track the progress of tasks, identify bottlenecks, and visualize the flow of work.
- Tools: Trello, Jira, Asana, Microsoft Planner.
- Digital Task Tracking and Management:
- Software tools that allow you to create, assign, and track tasks.
- Enables team members to update task status, add comments, and collaborate in real time.
- Tools: Jira, Microsoft Azure DevOps, Monday.com, ClickUp.
- Video Conferencing and Communication:
- Facilitates remote collaboration, daily standup meetings, sprint reviews, and sprint retrospectives.
- Enables clear communication among distributed teams.
- Tools: Zoom, Microsoft Teams, Slack, Google Meet.
- Documentation and Knowledge Sharing:
- Centralized platforms for storing project documentation, user stories, and sprint goals.
- Ensures that information is accessible and up to date for the team.
- Tools: Confluence, Microsoft SharePoint, Google Docs.
- Collaboration and Chat Platforms:
- Real-time chat platforms for quick communication, questions, and discussions.
- Helps team members stay connected and informed throughout the sprint.
- Tools: Slack, Microsoft Teams, Mattermost, Discord.
- Continuous Integration and Deployment:
- Tools that automate code integration, testing, and deployment.
- Ensures that code changes are integrated smoothly and tested continuously.
- Tools: Jenkins, Travis CI, CircleCI, GitLab CI/CD.
- Version Control System:
- Manages code repositories, tracks changes, and enables collaboration among developers.
- Ensures that code changes are properly tracked and managed.
- Tools: Git (GitHub, GitLab, Bitbucket), Subversion.
- Burndown Chart and Reporting:
- Provides visual representation of sprint progress, comparing completed work with remaining work.
- Helps the team and stakeholders understand the pace of work and make adjustments if needed.
- Tools: Jira, Trello (with Power-Ups), Microsoft Azure DevOps.
- Retrospective Tools:
- Online platforms that facilitate sprint retrospective meetings.
- Helps teams capture feedback, identify improvements, and track action items.
- Tools: FunRetro, Retrium, Miro, Stormboard.
- Test and Quality Management:
- Tools for managing test cases, executing tests, and tracking defects.
- Ensures that product quality is maintained throughout the sprint.
- Tools: Zephyr, TestRail, qTest, PractiTest.
Remember that the effectiveness of these tools depends on the team's familiarity with them and how well they integrate into your workflow. Choose tools that align with your team's preferences, needs, and the specific requirements of your project.
Becoming a Certified Scrum Master
Becoming a Certified ScrumMaster (CSM) involves completing a certification process offered by the Scrum Alliance. The CSM certification validates your knowledge of Scrum principles, practices, and your ability to serve as an effective Scrum Master. Here's a general outline of the steps you would take to become a Certified Scrum Master:
- Gain Familiarity with Scrum:
- Before pursuing the certification, ensure you have a solid understanding of Scrum principles, roles, events, and artifacts. Familiarize yourself with the Scrum Guide and recommended Scrum resources.
- Participate in Training:
- Attend a two-day Certified ScrumMaster training course conducted by a certified Scrum trainer. This course covers Scrum principles, practices, and real-world applications.
- Complete the Training:
- Participate actively in the training, engage in discussions, exercises, and workshops.
- Ensure you understand the Scrum framework, its roles, responsibilities, events, and values.
- Pass the Exam:
- After completing the training, you'll receive an email invitation from the Scrum Alliance to take the CSM exam.
- The exam is an online, multiple-choice test that assesses your knowledge of Scrum principles and practices.
- You have up to 90 days from the date of completing the training to pass the exam.
- Pass the Scrum Alliance CSM Exam:
- To pass the CSM exam, you'll need to correctly answer a certain percentage of questions.
- Passing the exam demonstrates your understanding of Scrum concepts and your ability to apply them in real-world scenarios.
- Complete the Scrum Alliance Membership:
- Once you've passed the exam, you need to create a Scrum Alliance account (if you don't already have one) and complete your membership profile.
- Agree to the License Agreement:
- As part of your certification process, you'll need to agree to the Scrum Alliance's certification license agreement.
- Claim Your Certification:
- After completing the exam and agreeing to the license agreement, you'll be able to claim your CSM certification.
- Maintain Your Certification:
- The CSM certification is valid for two years. To maintain it, you need to earn Scrum Education Units (SEUs) and renew your certification by paying a renewal fee.
It's important to note that the process and requirements may change, so it's recommended to check the Scrum Alliance's official website for the most up-to-date information on the CSM certification process, training opportunities, and exam details. The certification can enhance your understanding of Scrum and your ability to facilitate Scrum practices within your team or organization.
Read More
In the dynamic realm of modern project management, the Scrum methodology has risen to prominence as a game-changing approach. Rooted in Agile principles, Scrum offers a framework that thrives on collaboration, adaptability, and iterative progress. Amidst this landscape, professionals seeking to refine their project management skills have found value in specialized training courses like PMI-ACP, CSM, and CSPO.
Join us in this exploration as we navigate the intricacies of Scrum project management, delving into its advantages and drawbacks. With a keen focus on the PMI-ACP, CSM, and CSPO training courses, we will uncover how these certifications equip individuals with the knowledge and tools to excel within the Scrum framework. By evaluating the pros and cons of Scrum and its interplay with these training pathways, we empower professionals to make strategic choices aligning with their career ambitions and project management objectives.
Whether you're an established project management expert or a newcomer to the field, this journey promises valuable insights into the synergy between Scrum, project management certifications, and professional development. Let's embark on this illuminating expedition, unraveling the potential that emerges at the crossroads of Scrum methodology and specialized training.
Table of Contents
- What is Scrum?
- What Is Scrum Framework?
- What is Scrum in Project Management?
- The Application of Scrum in Project Management
- Advantages and Disadvantages of Scrum Project Management
- Scrum Roles
- Comprehending the Role of Project Manager in Scrum – The Scrum Master vs. the Project Manager
- 6 Steps of Scrum Process
- Key Scrum Tools to Get You Through Your Next Sprint
- Becoming a Certified Scrum Master
What is Scrum?
Scrum is an agile framework used in project management and software development to help teams work collaboratively and efficiently on complex projects. It emphasizes flexibility, adaptability, and iterative progress. Scrum provides a structured approach to managing tasks and delivering valuable outcomes in a dynamic and ever-changing environment.
Key characteristics of Scrum include:
- Iterative and Incremental Development: Scrum breaks down the project into smaller iterations called "sprints." Each sprint typically lasts 1 to 4 weeks and results in a potentially shippable product increment. This allows for continuous feedback and the ability to adapt to changing requirements.
- Roles and Responsibilities: Scrum defines specific roles within the team. The key roles are the Product Owner, who represents the stakeholders and defines the product backlog, the Scrum Master, who facilitates the Scrum process and supports the team, and the Development Team, responsible for delivering the product increment.
- Product Backlog: The product backlog is a prioritized list of features, enhancements, and fixes that need to be addressed in the project. The Product Owner is responsible for maintaining and prioritizing this list.
- Sprint Planning: At the beginning of each sprint, the team conducts a sprint planning meeting to select items from the product backlog to work on during the sprint. The team then defines the tasks required to complete those items.
- Daily Scrum (Standup): The team holds a daily standup meeting where each member briefly discusses what they've done since the last meeting, what they're working on, and any obstacles they're facing. This fosters transparency and collaboration within the team.
- Sprint Review: At the end of each sprint, the team holds a sprint review to demonstrate the completed work to stakeholders. This provides an opportunity for feedback and helps the team make adjustments based on that feedback.
- Sprint Retrospective: After the sprint review, the team holds a retrospective to reflect on the sprint process and identify areas for improvement. This continuous improvement cycle is a core aspect of Scrum.
- Time-Boxing: Scrum uses time-boxing to limit the duration of meetings and activities, ensuring that they don't drag on indefinitely.
Scrum encourages a culture of collaboration, self-organization, and continuous improvement. It's particularly well-suited for projects where requirements are likely to change or evolve, as the framework allows teams to pivot and adapt quickly. Scrum is widely used in various industries, not just software development, to manage projects of varying complexity.
What Is Scrum Framework?
The Scrum framework is an agile methodology used in project management and product development to deliver value incrementally and iteratively. It provides a structured approach for teams to work collaboratively and efficiently, especially in environments where requirements are dynamic and subject to change. The framework is designed to promote flexibility, transparency, and continuous improvement.
The Scrum framework consists of several key components and practices:
- Roles:
- Product Owner: Represents the stakeholders and is responsible for defining and prioritizing the product backlog, which contains the list of features, enhancements, and fixes to be addressed.
- Scrum Master: Facilitates the Scrum process, ensures adherence to Scrum principles, and helps remove any obstacles that the team encounters.
- Development Team: Cross-functional group responsible for delivering the product increment. The team self-organizes and collaborates to complete the work within each sprint.
- Artifacts:
- Product Backlog: A prioritized list of items that need to be addressed in the project. These items can include user stories, bug fixes, technical tasks, and more.
- Sprint Backlog: The subset of items from the product backlog that the team commits to completing during a specific sprint.
- Increment: The sum of completed items at the end of a sprint. It should be a potentially shippable product that adds value to the product.
- Events:
- Sprint: A time-boxed iteration, typically lasting 1 to 4 weeks, during which the team works on completing items from the sprint backlog.
- Sprint Planning: A meeting held at the beginning of each sprint where the team selects items from the product backlog to work on and defines the tasks required to complete them.
- Daily Scrum (Standup): A brief daily meeting where team members share updates on their progress, plans, and any obstacles they are facing.
- Sprint Review: A meeting at the end of each sprint where the team demonstrates the completed work to stakeholders and gathers feedback.
- Sprint Retrospective: A meeting held after the sprint review to reflect on the sprint process, identify strengths and areas for improvement, and make adjustments.
- Principles:
- Empirical Process Control: Scrum is based on transparency, inspection, and adaptation. It encourages teams to learn from their experiences and adjust their processes accordingly.
- Self-Organization: Teams are responsible for organizing themselves and making decisions, which fosters ownership and accountability.
- Collaboration: Scrum emphasizes close collaboration among team members, stakeholders, and customers to ensure the best possible outcome.
- Incremental Delivery: Value is delivered in small increments, allowing for faster feedback and the ability to respond to changing requirements.
Overall, the Scrum framework provides a structured way to manage projects by breaking them down into smaller, manageable chunks and continuously improving the process based on feedback and real-world results. It's widely used in various industries and sectors for its adaptability and focus on delivering value to customers.
What is Scrum in Project Management?
Scrum in project management is an agile framework that focuses on delivering projects in a flexible and iterative manner. It was originally developed for software development but has since been applied to various types of projects in different industries. Scrum aims to address the challenges of managing projects in dynamic and rapidly changing environments by promoting collaboration, adaptability, and continuous improvement.
In the context of project management, Scrum provides a structured approach to planning, executing, and delivering projects by breaking them into smaller, manageable components. These smaller components are called sprints, and each sprint involves a defined set of tasks and goals. Here's how Scrum works in project management:
- Product Owner: The product owner is responsible for representing the interests of stakeholders, understanding project requirements, and prioritizing the work that needs to be done. The product owner maintains the product backlog, which is a dynamic list of features, tasks, and changes that need to be addressed.
- Scrum Team: The Scrum team is a cross-functional group of individuals responsible for delivering the project increment. This team includes developers, designers, testers, and other relevant roles. The team collectively decides how much work they can commit to during a sprint.
- Sprint Planning: At the beginning of each sprint, the team holds a sprint planning meeting. During this meeting, they review the items in the product backlog, select the items they will work on during the sprint, and create a sprint backlog—a list of tasks required to complete the selected items.
- Sprint: A sprint is a time-boxed iteration that typically lasts 1 to 4 weeks. The team works on the tasks identified in the sprint backlog. At the end of the sprint, they aim to deliver a potentially shippable product increment—a working piece of the project that adds value.
- Daily Scrum (Standup): The team holds a daily standup meeting to discuss progress, obstacles, and plans for the day. Each team member shares what they accomplished, what they plan to work on next, and if they're facing any challenges.
- Sprint Review: At the end of each sprint, the team holds a sprint review. They demonstrate the completed work to stakeholders and gather feedback. This helps ensure that the project is on the right track and that any necessary adjustments can be made.
- Sprint Retrospective: After the sprint review, the team conducts a retrospective meeting to reflect on the sprint process. They discuss what went well, what could be improved, and any changes they want to implement in the next sprint.
- Continuous Improvement: One of the core principles of Scrum is continuous improvement. Teams regularly analyze their processes and make adjustments to enhance efficiency, collaboration, and overall project delivery.
Scrum's iterative and incremental approach allows for flexibility and responsiveness to changing requirements and priorities. It's especially effective for projects where the initial requirements may evolve over time, as the framework supports adapting to new information and customer feedback.
The Application of Scrum in Project Management
Scrum is widely applied in project management, especially in software development, due to its adaptability and focus on iterative progress. However, its principles and practices can be extended to various types of projects in different industries. Here are some key applications of Scrum in project management:
- Software Development: The most common application of Scrum is in software development. It allows development teams to work on small, manageable chunks of functionality in each sprint, ensuring that valuable features are delivered regularly and enabling quick responses to changing requirements.
- Product Development: Beyond software, Scrum can be applied to the development of physical products. It enables cross-functional teams to collaborate on designing, prototyping, testing, and delivering products in iterations, ensuring that customer needs are met effectively.
- Marketing Campaigns: Scrum can be used in marketing projects where campaigns are broken down into sprints. Marketing teams can work on individual tasks like content creation, social media engagement, and analytics, delivering measurable results at the end of each sprint.
- Event Planning: For event management projects, Scrum can help organize tasks such as venue selection, logistics planning, participant engagement, and post-event analysis. Sprints can align with the various phases of event preparation.
- Research and Development: In R&D projects, Scrum allows researchers and developers to focus on specific aspects of a project, quickly experiment with new ideas, and pivot based on the results obtained within short iterations.
- Construction Projects: Construction projects can benefit from Scrum by dividing complex tasks like site preparation, foundation construction, and building phases into sprints. This helps manage resources, track progress, and adapt to unexpected challenges.
- Educational Programs: Scrum can be used to structure educational programs and courses. Each sprint corresponds to a learning module, and students make incremental progress, receive feedback, and adapt their learning journey based on their understanding.
- Content Creation: Content projects, such as writing articles, producing videos, or designing graphics, can benefit from Scrum's iterative approach. Sprints can focus on different content pieces, and regular reviews ensure content quality.
- Healthcare Projects: Scrum principles can be applied to healthcare projects, such as implementing new medical technologies, improving patient care processes, or developing healthcare apps. This approach promotes collaboration among medical professionals, developers, and other stakeholders.
- Consulting and Professional Services: Scrum can be used in consulting projects, where each sprint focuses on specific deliverables or recommendations for clients, ensuring that value is provided incrementally and allowing for client feedback.
When applying Scrum in project management, it's important to tailor the practices to suit the specific needs and context of the project. The framework encourages adaptability and continuous improvement, so teams can experiment with different approaches to find the best fit for their project's goals and requirements.
Advantages and Disadvantages of Scrum Project Management
Scrum project management offers several advantages and disadvantages, which can impact its suitability for different projects and teams. Here's an overview of the pros and cons of using the Scrum framework:
Advantages:
- Flexibility: Scrum's iterative approach allows teams to adapt to changing requirements and priorities, making it well-suited for projects with evolving needs.
- Customer Satisfaction: Regularly delivering working increments of the project allows stakeholders to see progress and provide feedback, ensuring the final product meets their expectations.
- Collaboration: Scrum encourages close collaboration among team members, stakeholders, and customers, fostering a sense of ownership and shared responsibility.
- Transparency: The framework promotes transparency through daily standup meetings, sprint reviews, and sprint retrospectives, ensuring everyone is aware of the project's status and challenges.
- Faster Time-to-Market: Incremental delivery means that features can be released more quickly, enabling a shorter time-to-market compared to traditional project management approaches.
- Risk Mitigation: Frequent reviews and adaptability help identify and address risks early in the project, reducing the likelihood of major setbacks.
- Continuous Improvement: Regular sprint retrospectives encourage teams to reflect on their processes and make adjustments, leading to ongoing process improvement.
- Motivated Teams: Scrum empowers teams to self-organize and make decisions, fostering a sense of ownership and motivation among team members.
Disadvantages:
- Complexity: Scrum has several roles, events, and artifacts, which can be overwhelming for teams new to the framework or for smaller projects.
- Lack of Predictability: The adaptive nature of Scrum can make it challenging to predict exact project timelines and outcomes, which might be problematic for projects with strict deadlines.
- Requires Skilled Team Members: Effective Scrum implementation requires skilled team members who understand the framework and its principles.
- High Dependency on Product Owner: The product owner's availability and decision-making play a critical role in prioritizing and clarifying tasks. Their absence or lack of involvement can impact the project.
- Inaccurate Initial Estimates: Because Scrum focuses on delivering small increments, it might be challenging to provide accurate estimates for the entire project at the outset.
- Lack of Documentation: The focus on working increments can sometimes lead to inadequate documentation, which might be required for compliance or future maintenance.
- Need for Continuous Involvement: Scrum requires consistent participation from all team members throughout the project, which might not be feasible in certain environments.
- Resistance to Change: Teams accustomed to traditional project management methods may face resistance in transitioning to the agile practices of Scrum.
Ultimately, the decision to use Scrum in project management depends on factors like project complexity, team composition, stakeholder involvement, and the organization's culture. It's important to carefully evaluate the advantages and disadvantages to determine whether Scrum aligns with the project's needs and objectives.
Top of Form
Scrum Roles
In the Scrum framework, there are three key roles that contribute to the successful implementation of the methodology within a project. These roles promote collaboration, responsibility, and effective communication within the team. Here are the three Scrum roles:
- Product Owner:
- The Product Owner represents the stakeholders, customers, and users of the product being developed. They are responsible for maximizing the value delivered by the team.
- Key responsibilities include defining and maintaining the product backlog, prioritizing items within it, and ensuring that the team understands the requirements and goals.
- The Product Owner makes decisions about what features or items should be worked on, and their decisions guide the team's work during each sprint.
- Scrum Master:
- The Scrum Master is a servant-leader who ensures that the Scrum framework is understood, followed, and continuously improved by the team.
- They act as a facilitator and coach, helping the team to self-organize and make decisions collectively. They also remove obstacles and impediments that the team might encounter.
- The Scrum Master fosters a collaborative and productive environment, guides the team in adhering to Scrum practices, and helps improve the team's effectiveness.
- Development Team:
- The Development Team is a cross-functional group of professionals responsible for delivering the product increment during each sprint.
- The team members collectively have the skills and expertise needed to design, develop, test, and deliver the product features.
- They collaborate closely, self-organize to manage their work, and collectively commit to achieving the goals of each sprint.
It's important to note that in Scrum, these roles are distinct, and individuals typically do not hold multiple roles simultaneously. Each role has specific responsibilities that contribute to the successful implementation of the framework. Additionally, Scrum emphasizes collaboration among the roles, as well as with stakeholders, to ensure that the project's goals and requirements are met.
Comprehending the Role of Project Manager in Scrum – The Scrum Master vs. the Project Manager
In the Scrum framework, the role of a Project Manager is quite distinct from the role of a Scrum Master. Both roles play important parts in project management, but their responsibilities, focus, and approach can differ significantly. Here's a comparison of the two roles:
Scrum Master:
- Responsibilities:
- Facilitating the Scrum Process: The Scrum Master ensures that the Scrum framework is understood and followed by the team, helping to maintain the Scrum events, roles, and artifacts.
- Coaching and Mentoring: They coach the team on self-organization, cross-functionality, and effective collaboration. They help the team continuously improve and achieve their best potential.
- Removing Obstacles: The Scrum Master identifies and removes impediments that hinder the team's progress, ensuring that the team can work smoothly.
- Promoting Empowerment: They empower the team to make their own decisions and self-organize, fostering a sense of ownership and accountability.
- Shielding from External Interference: The Scrum Master helps protect the team from external disruptions and influences to maintain focus during sprints.
- Focus:
- Team Dynamics: The Scrum Master's primary focus is on fostering a productive and collaborative team environment, ensuring that the team can work efficiently and effectively.
- Process Adherence: They ensure that the Scrum process is followed and adapted appropriately to suit the team's needs while upholding Scrum principles.
Project Manager:
- Responsibilities:
- Planning and Scheduling: The Project Manager is responsible for planning the project, defining tasks, setting timelines, and creating a project schedule.
- Resource Management: They allocate resources, assign tasks, and ensure that the project is adequately staffed to meet its goals.
- Budget Management: The Project Manager handles budgeting, cost estimation, and resource allocation to ensure the project stays within budget.
- Risk Management: They identify potential risks, develop mitigation strategies, and manage any issues that arise during the project.
- Stakeholder Communication: The Project Manager communicates with stakeholders, updates them on project progress, and manages their expectations.
- Focus:
- Deliverables and Objectives: The Project Manager's primary focus is on meeting project goals, delivering the desired outcome, and ensuring that the project aligns with business objectives.
- Planning and Execution: They oversee the overall project planning and execution, ensuring that tasks are completed according to the plan.
In the context of Scrum, the Scrum Master's role is more about enabling the team to work effectively within the Scrum framework, while the Project Manager's role is broader and encompasses the overall management of the project. In many Scrum implementations, the traditional role of a Project Manager may shift to other roles (such as Product Owner or team member) or may be less prominent, as Scrum promotes self-organization and collaborative decision-making within the team. However, in organizations that use both traditional project management and Scrum, the Project Manager might still have a role to play in coordinating higher-level activities and aligning multiple Scrum teams with organizational goals.
6 Steps of Scrum Process
The Scrum process consists of several iterative and recurring steps that help teams deliver value incrementally and adapt to changing requirements. Here are the six key steps of the Scrum process:
- Product Backlog Creation:
- The process begins with the creation of the product backlog, which is a dynamic list of items that need to be addressed in the project. These items can include features, bug fixes, technical tasks, and more.
- The Product Owner is responsible for maintaining and prioritizing the product backlog based on input from stakeholders, customers, and the team.
- Sprint Planning:
- Before the start of each sprint, the team holds a sprint planning meeting.
- During this meeting, the Product Owner presents the items from the product backlog that are of the highest priority and have been refined to a sufficient level.
- The Development Team works with the Product Owner to select items from the product backlog that they believe they can complete during the sprint.
- The team breaks down the selected items into smaller tasks and estimates the effort required for each task.
- Sprint Execution:
- The sprint execution phase begins after the sprint planning meeting and typically lasts 1 to 4 weeks.
- The Development Team works on the tasks identified during the sprint planning, collaboratively building and testing the product increment.
- Daily standup meetings are held to provide updates on progress, discuss obstacles, and align the team.
- Daily Scrum (Standup):
- Each day during the sprint, the team holds a brief daily standup meeting, known as the Daily Scrum.
- Team members answer three questions: What did I accomplish yesterday? What will I work on today? Are there any obstacles in my way?
- This meeting helps the team stay synchronized, identify potential issues, and make real-time adjustments.
- Sprint Review:
- At the end of the sprint, the team holds a sprint review meeting.
- The team demonstrates the completed work to stakeholders and the Product Owner.
- Feedback is gathered, and stakeholders have an opportunity to evaluate the product increment and suggest changes.
- Sprint Retrospective:
- Following the sprint review, the team conducts a sprint retrospective meeting.
- The team reflects on the sprint process and discusses what went well, what could be improved, and what actions should be taken to enhance future sprints.
- The retrospective helps the team identify and implement process improvements, fostering a culture of continuous learning.
After the sprint retrospective, the process begins again with the creation of a new sprint and the selection of items from the product backlog. This cyclical process allows the team to continuously improve and refine their work based on feedback, making Scrum a highly adaptive and iterative framework.
Key Scrum Tools to Get You Through Your Next Sprint
Scrum emphasizes people and interactions over tools, but using the right tools can certainly enhance collaboration, communication, and productivity during sprints. Here are some key Scrum tools that can help you manage your next sprint effectively:
- Scrum Board or Kanban Board:
- A visual representation of the sprint backlog and its tasks.
- Helps the team track the progress of tasks, identify bottlenecks, and visualize the flow of work.
- Tools: Trello, Jira, Asana, Microsoft Planner.
- Digital Task Tracking and Management:
- Software tools that allow you to create, assign, and track tasks.
- Enables team members to update task status, add comments, and collaborate in real time.
- Tools: Jira, Microsoft Azure DevOps, Monday.com, ClickUp.
- Video Conferencing and Communication:
- Facilitates remote collaboration, daily standup meetings, sprint reviews, and sprint retrospectives.
- Enables clear communication among distributed teams.
- Tools: Zoom, Microsoft Teams, Slack, Google Meet.
- Documentation and Knowledge Sharing:
- Centralized platforms for storing project documentation, user stories, and sprint goals.
- Ensures that information is accessible and up to date for the team.
- Tools: Confluence, Microsoft SharePoint, Google Docs.
- Collaboration and Chat Platforms:
- Real-time chat platforms for quick communication, questions, and discussions.
- Helps team members stay connected and informed throughout the sprint.
- Tools: Slack, Microsoft Teams, Mattermost, Discord.
- Continuous Integration and Deployment:
- Tools that automate code integration, testing, and deployment.
- Ensures that code changes are integrated smoothly and tested continuously.
- Tools: Jenkins, Travis CI, CircleCI, GitLab CI/CD.
- Version Control System:
- Manages code repositories, tracks changes, and enables collaboration among developers.
- Ensures that code changes are properly tracked and managed.
- Tools: Git (GitHub, GitLab, Bitbucket), Subversion.
- Burndown Chart and Reporting:
- Provides visual representation of sprint progress, comparing completed work with remaining work.
- Helps the team and stakeholders understand the pace of work and make adjustments if needed.
- Tools: Jira, Trello (with Power-Ups), Microsoft Azure DevOps.
- Retrospective Tools:
- Online platforms that facilitate sprint retrospective meetings.
- Helps teams capture feedback, identify improvements, and track action items.
- Tools: FunRetro, Retrium, Miro, Stormboard.
- Test and Quality Management:
- Tools for managing test cases, executing tests, and tracking defects.
- Ensures that product quality is maintained throughout the sprint.
- Tools: Zephyr, TestRail, qTest, PractiTest.
Remember that the effectiveness of these tools depends on the team's familiarity with them and how well they integrate into your workflow. Choose tools that align with your team's preferences, needs, and the specific requirements of your project.
Becoming a Certified Scrum Master
Becoming a Certified ScrumMaster (CSM) involves completing a certification process offered by the Scrum Alliance. The CSM certification validates your knowledge of Scrum principles, practices, and your ability to serve as an effective Scrum Master. Here's a general outline of the steps you would take to become a Certified Scrum Master:
- Gain Familiarity with Scrum:
- Before pursuing the certification, ensure you have a solid understanding of Scrum principles, roles, events, and artifacts. Familiarize yourself with the Scrum Guide and recommended Scrum resources.
- Participate in Training:
- Attend a two-day Certified ScrumMaster training course conducted by a certified Scrum trainer. This course covers Scrum principles, practices, and real-world applications.
- Complete the Training:
- Participate actively in the training, engage in discussions, exercises, and workshops.
- Ensure you understand the Scrum framework, its roles, responsibilities, events, and values.
- Pass the Exam:
- After completing the training, you'll receive an email invitation from the Scrum Alliance to take the CSM exam.
- The exam is an online, multiple-choice test that assesses your knowledge of Scrum principles and practices.
- You have up to 90 days from the date of completing the training to pass the exam.
- Pass the Scrum Alliance CSM Exam:
- To pass the CSM exam, you'll need to correctly answer a certain percentage of questions.
- Passing the exam demonstrates your understanding of Scrum concepts and your ability to apply them in real-world scenarios.
- Complete the Scrum Alliance Membership:
- Once you've passed the exam, you need to create a Scrum Alliance account (if you don't already have one) and complete your membership profile.
- Agree to the License Agreement:
- As part of your certification process, you'll need to agree to the Scrum Alliance's certification license agreement.
- Claim Your Certification:
- After completing the exam and agreeing to the license agreement, you'll be able to claim your CSM certification.
- Maintain Your Certification:
- The CSM certification is valid for two years. To maintain it, you need to earn Scrum Education Units (SEUs) and renew your certification by paying a renewal fee.
It's important to note that the process and requirements may change, so it's recommended to check the Scrum Alliance's official website for the most up-to-date information on the CSM certification process, training opportunities, and exam details. The certification can enhance your understanding of Scrum and your ability to facilitate Scrum practices within your team or organization.




.jpg)


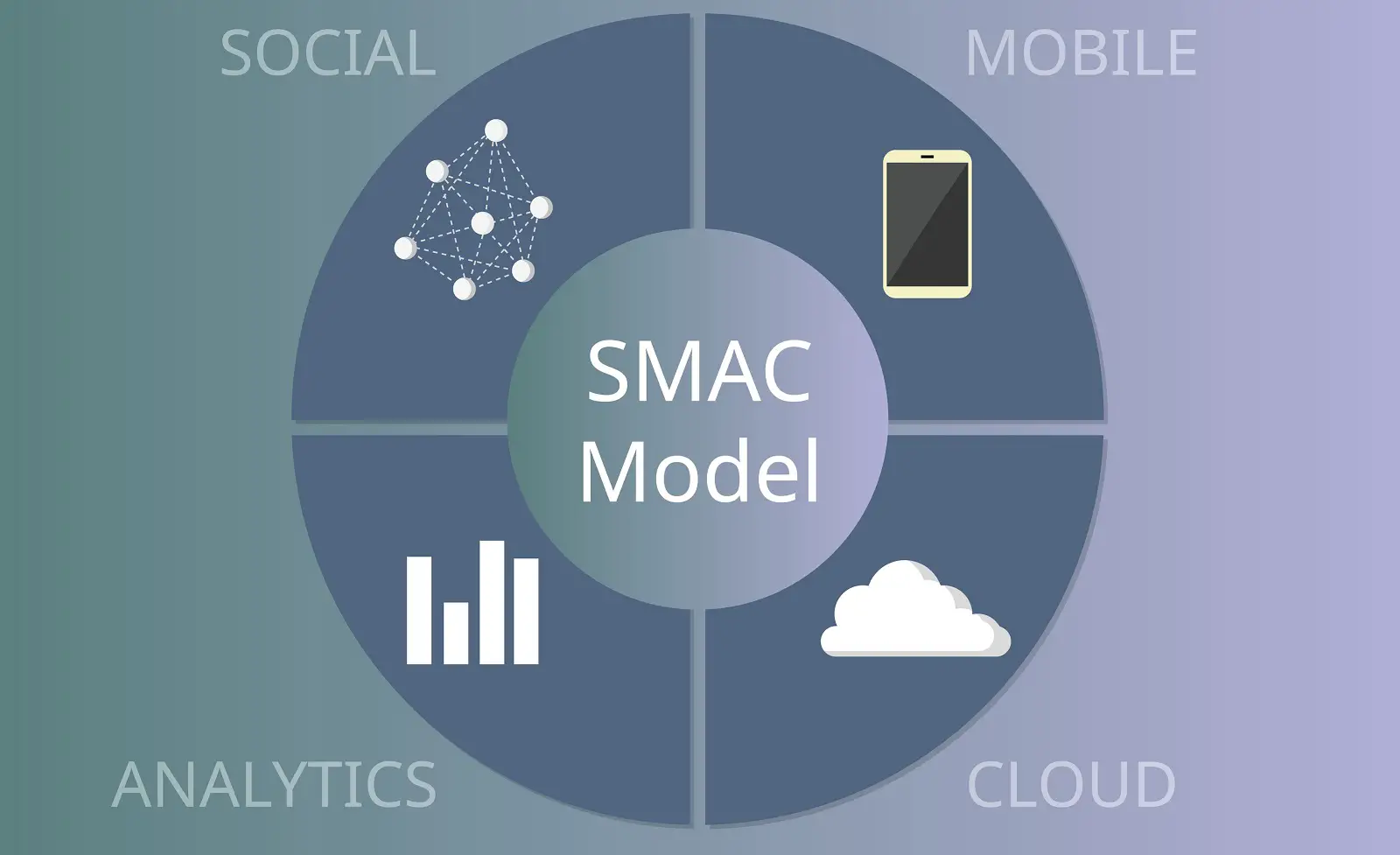









.jpg)




.jpg)