Quick Enquiry Form
Categories
- Agile and Scrum (187)
- BigData (21)
- Business Analysis (87)
- Cirtix Client Administration (51)
- Cisco (59)
- Cloud Technology (71)
- Cyber Security (41)
- Data Science and Business Intelligence (35)
- Developement Courses (46)
- DevOps (15)
- Digital Marketing (50)
- Emerging Technology (172)
- IT Service Management (70)
- Microsoft (52)
- Other (393)
- Project Management (471)
- Quality Management (127)
- salesforce (62)
Latest posts
Mastering Cisco UCS Management The..
CCNP Ultimate Path to Networking..
Understanding CISS Key Concepts and..
Free Resources
Subscribe to Newsletter
Top 10 Salesforce App Builder Best Practices
Salesforce App Builder is a powerful tool that enables users to design and create custom applications on the Salesforce platform without the need for extensive coding. As organizations increasingly leverage Salesforce to streamline their business processes, the demand for skilled app builders has surged. In this dynamic ecosystem, understanding and implementing best practices becomes crucial to ensure the development of robust, efficient, and scalable applications. Whether you are a seasoned Salesforce App Builder or a newcomer to the platform, staying abreast of the top practices is essential to maximize the potential of your applications.
In this comprehensive guide, we delve into the "Top 10 Salesforce App Builder Best Practices You Should Know." By examining these best practices, developers and administrators can enhance their proficiency in building applications that not only meet immediate business requirements but also align with long-term strategic goals. From optimizing user experience to ensuring data security and maintaining application performance, each best practice contributes to the overall success of Salesforce app development. Let's explore these key principles that will empower you to create high-quality, customized solutions within the Salesforce ecosystem.
Table of contents
-
Effective Use of Declarative Tools
-
Mastering Apex Code Best Practices
-
Customization without Compromising Upgradability
-
User Permission and Access Management
-
Testing and Quality Assurance Strategies
-
Conclusion
Effective Use of Declarative Tools
In the realm of Salesforce app development, mastering the effective use of declarative tools is paramount for App Builders seeking to create robust applications without delving extensively into coding. Declarative tools, including Process Builder, Flow, and Lightning App Builder, empower developers to design and customize applications through point-and-click interfaces, significantly reducing the need for custom code. One key best practice involves understanding the strengths and limitations of each declarative tool, selecting the most appropriate tool for a given task, and recognizing scenarios where declarative development is more efficient than traditional coding.
Process Builder, for instance, is a powerful tool for automating business processes by defining a series of if/then statements. Best practices in using Process Builder involve keeping processes simple, focusing on one goal per process, and avoiding unnecessary complexity to ensure clarity and maintainability. Similarly, Flow allows developers to create complex, multi-step processes and collect data from users through a guided interface. Effective use of Flow includes designing well-organized flows, utilizing variables judiciously, and considering the impact on user experience.
Lightning App Builder provides a user-friendly interface for building custom Lightning pages without writing code. Best practices for Lightning App Builder encompass creating responsive and intuitive user interfaces, optimizing page layouts for different devices, and leveraging dynamic components to enhance user experience. App Builders should also consider the broader architectural implications of declarative tools, ensuring that their solutions align with the overall design and scalability goals of the Salesforce application.
Mastering the effective use of declarative tools in Salesforce involves a strategic understanding of each tool's capabilities, thoughtful selection based on the task at hand, and an awareness of the broader implications on the application's architecture. By adhering to these best practices, App Builders can harness the full potential of declarative tools to create powerful, scalable, and maintainable applications on the Salesforce platform.
Mastering Apex Code Best Practices
Mastering Apex Code, Salesforce's proprietary programming language, is a crucial aspect of becoming a proficient Salesforce App Builder. Apex allows developers to create custom business logic, manipulate data, and extend the capabilities of the Salesforce platform. To ensure the development of efficient, scalable, and maintainable applications, adhering to a set of best practices in Apex coding is essential.
One fundamental principle in mastering Apex Code is understanding and respecting Salesforce's governor limits. These are predefined limits to ensure the efficient use of resources and prevent monopolization of system resources by individual applications. App Builders should be mindful of these limits, designing their code to handle bulk processing efficiently, avoiding unnecessary queries, and optimizing data manipulation operations to stay within the specified boundaries.
Error handling is another critical aspect of Apex coding best practices. Effective error handling ensures that applications gracefully handle unexpected scenarios and provide meaningful error messages. This involves using try-catch blocks, logging errors for analysis, and communicating issues to end-users in a user-friendly manner. A well-structured error-handling strategy contributes to the overall reliability and user satisfaction of the Salesforce application.
Mastering Apex Code involves a holistic approach encompassing adherence to governor limits, robust error handling, scalability considerations, and maintaining a clean codebase. By following these best practices, App Builders can harness the full potential of Apex to create powerful, reliable, and scalable applications on the Salesforce platform.
Customization without Compromising Upgradability
Striking a delicate balance between customization and upgradability is a crucial challenge for Salesforce App Builders aiming to create tailored solutions while ensuring seamless future platform upgrades. Customization is often essential to meet specific business requirements, but it must be approached thoughtfully to avoid hindering the ability to adopt new features and enhancements released by Salesforce. A fundamental best practice in this context is to evaluate the necessity of customization against the potential impact on upgradability, making informed decisions that prioritize long-term sustainability.
One key consideration in customization without compromising upgradability is to leverage standard Salesforce functionality whenever possible. The platform provides a rich set of out-of-the-box features that can often fulfill business requirements without the need for extensive customization. App Builders should thoroughly explore these standard functionalities before resorting to custom development, ensuring that their solutions align with the natural evolution of the Salesforce platform.
A critical aspect of customization and upgradability is maintaining a comprehensive documentation strategy. Documenting the rationale behind each customization, the specific requirements it addresses, and any potential impacts on future upgrades provides a roadmap for administrators and developers. This documentation becomes invaluable during upgrade planning, ensuring a smooth transition and reducing the likelihood of post-upgrade issues.
User Permission and Access Management
User permission and access management play a pivotal role in the design and security of Salesforce applications, making it imperative for App Builders to implement robust strategies that align with business requirements and uphold data integrity. At the core of this best practice is the principle of least privilege, which entails granting users the minimum level of access necessary to perform their job functions. This approach minimizes the risk of unauthorized data exposure and helps maintain a secure Salesforce environment.
Salesforce offers a versatile set of tools for defining user permissions and access controls. One key aspect of effective access management involves configuring profiles and permission sets thoughtfully. Profiles establish the baseline permissions for a user, while permission sets allow for additional granular permissions as needed. App Builders should carefully define profiles based on job roles and responsibilities, ensuring that users have access only to the specific objects and fields required for their tasks.
Record-level security is another critical dimension of user permission management. Utilizing features such as sharing rules, role hierarchies, and manual sharing, App Builders can restrict access to specific records based on user roles and responsibilities. By implementing record-level security effectively, they can strike a balance between providing users with the necessary information and safeguarding sensitive data from unauthorized access.
User permission and access management is a critical best practice for Salesforce App Builders. By adhering to the principle of least privilege, configuring profiles and permission sets judiciously, implementing effective record-level security, and conducting regular audits, App Builders contribute to the creation of a secure and efficient Salesforce application environment that aligns with the organization's data privacy and security goals.
Testing and Quality Assurance Strategies
Testing and quality assurance are integral components of the Salesforce app development lifecycle, ensuring that applications function reliably, perform efficiently, and meet user expectations. Salesforce App Builders must adopt robust testing strategies to identify and rectify issues early in the development process, fostering a culture of quality and reliability.
Integration testing is equally critical, as it validates the interaction between different components within the Salesforce ecosystem and ensures that the application behaves as expected in a holistic environment. This involves testing various integration points, such as API connections and third-party integrations, to identify and resolve potential issues that may arise during real-world usage.
User acceptance testing (UAT) is a pivotal phase in quality assurance, involving end-users validating that the application meets their requirements and expectations. App Builders should collaborate closely with stakeholders to define test cases and scenarios that align with the business objectives. UAT not only serves as a final check before deployment but also provides valuable insights into user satisfaction and the application's overall usability.
Testing and quality assurance strategies are indispensable for Salesforce App Builders. Incorporating thorough unit testing, integration testing, user acceptance testing, and leveraging automation tools contribute to the creation of high-quality, reliable applications that meet both user expectations and business objectives.
Conclusion
In conclusion, mastering the art of Salesforce app development involves a careful blend of best practices that span various facets of the development lifecycle. From the effective use of declarative tools, such as Process Builder and Lightning App Builder, to the meticulous coding practices in Apex, App Builders must navigate a dynamic landscape to ensure their applications are not only tailored to business needs but are also scalable, maintainable, and align with Salesforce's continuous evolution.
The delicate balance between customization and upgradability is a key consideration, urging developers to make informed decisions about when and how to tailor solutions to meet specific requirements. Thoughtful customization, coupled with a keen eye for documentation and adherence to best practices, enables applications to seamlessly evolve with the Salesforce platform's advancements.
User permission and access management, another critical aspect, demand a strategic approach grounded in the principle of least privilege. By configuring profiles, permission sets, and record-level security with precision, App Builders create a secure environment that respects data privacy while providing users with the necessary tools to perform their roles effectively.
Testing and quality assurance emerge as linchpins in the development process, ensuring the reliability and efficiency of applications. Rigorous unit testing, comprehensive integration testing, and user acceptance testing contribute to the creation of robust solutions. Automation becomes a force multiplier in this context, enabling App Builders to maintain consistency and efficiency in testing processes.
The journey of a Salesforce App Builder is one of continuous learning, adaptation, and refinement. By embracing these best practices and remaining attuned to the ever-evolving Salesforce ecosystem, developers can navigate the complexities of app development with confidence, ultimately delivering solutions that stand the test of time and contribute to the success of the organizations they serve.
Read More
Salesforce App Builder is a powerful tool that enables users to design and create custom applications on the Salesforce platform without the need for extensive coding. As organizations increasingly leverage Salesforce to streamline their business processes, the demand for skilled app builders has surged. In this dynamic ecosystem, understanding and implementing best practices becomes crucial to ensure the development of robust, efficient, and scalable applications. Whether you are a seasoned Salesforce App Builder or a newcomer to the platform, staying abreast of the top practices is essential to maximize the potential of your applications.
In this comprehensive guide, we delve into the "Top 10 Salesforce App Builder Best Practices You Should Know." By examining these best practices, developers and administrators can enhance their proficiency in building applications that not only meet immediate business requirements but also align with long-term strategic goals. From optimizing user experience to ensuring data security and maintaining application performance, each best practice contributes to the overall success of Salesforce app development. Let's explore these key principles that will empower you to create high-quality, customized solutions within the Salesforce ecosystem.
Table of contents
-
Effective Use of Declarative Tools
-
Mastering Apex Code Best Practices
-
Customization without Compromising Upgradability
-
User Permission and Access Management
-
Testing and Quality Assurance Strategies
-
Conclusion
Effective Use of Declarative Tools
In the realm of Salesforce app development, mastering the effective use of declarative tools is paramount for App Builders seeking to create robust applications without delving extensively into coding. Declarative tools, including Process Builder, Flow, and Lightning App Builder, empower developers to design and customize applications through point-and-click interfaces, significantly reducing the need for custom code. One key best practice involves understanding the strengths and limitations of each declarative tool, selecting the most appropriate tool for a given task, and recognizing scenarios where declarative development is more efficient than traditional coding.
Process Builder, for instance, is a powerful tool for automating business processes by defining a series of if/then statements. Best practices in using Process Builder involve keeping processes simple, focusing on one goal per process, and avoiding unnecessary complexity to ensure clarity and maintainability. Similarly, Flow allows developers to create complex, multi-step processes and collect data from users through a guided interface. Effective use of Flow includes designing well-organized flows, utilizing variables judiciously, and considering the impact on user experience.
Lightning App Builder provides a user-friendly interface for building custom Lightning pages without writing code. Best practices for Lightning App Builder encompass creating responsive and intuitive user interfaces, optimizing page layouts for different devices, and leveraging dynamic components to enhance user experience. App Builders should also consider the broader architectural implications of declarative tools, ensuring that their solutions align with the overall design and scalability goals of the Salesforce application.
Mastering the effective use of declarative tools in Salesforce involves a strategic understanding of each tool's capabilities, thoughtful selection based on the task at hand, and an awareness of the broader implications on the application's architecture. By adhering to these best practices, App Builders can harness the full potential of declarative tools to create powerful, scalable, and maintainable applications on the Salesforce platform.
Mastering Apex Code Best Practices
Mastering Apex Code, Salesforce's proprietary programming language, is a crucial aspect of becoming a proficient Salesforce App Builder. Apex allows developers to create custom business logic, manipulate data, and extend the capabilities of the Salesforce platform. To ensure the development of efficient, scalable, and maintainable applications, adhering to a set of best practices in Apex coding is essential.
One fundamental principle in mastering Apex Code is understanding and respecting Salesforce's governor limits. These are predefined limits to ensure the efficient use of resources and prevent monopolization of system resources by individual applications. App Builders should be mindful of these limits, designing their code to handle bulk processing efficiently, avoiding unnecessary queries, and optimizing data manipulation operations to stay within the specified boundaries.
Error handling is another critical aspect of Apex coding best practices. Effective error handling ensures that applications gracefully handle unexpected scenarios and provide meaningful error messages. This involves using try-catch blocks, logging errors for analysis, and communicating issues to end-users in a user-friendly manner. A well-structured error-handling strategy contributes to the overall reliability and user satisfaction of the Salesforce application.
Mastering Apex Code involves a holistic approach encompassing adherence to governor limits, robust error handling, scalability considerations, and maintaining a clean codebase. By following these best practices, App Builders can harness the full potential of Apex to create powerful, reliable, and scalable applications on the Salesforce platform.
Customization without Compromising Upgradability
Striking a delicate balance between customization and upgradability is a crucial challenge for Salesforce App Builders aiming to create tailored solutions while ensuring seamless future platform upgrades. Customization is often essential to meet specific business requirements, but it must be approached thoughtfully to avoid hindering the ability to adopt new features and enhancements released by Salesforce. A fundamental best practice in this context is to evaluate the necessity of customization against the potential impact on upgradability, making informed decisions that prioritize long-term sustainability.
One key consideration in customization without compromising upgradability is to leverage standard Salesforce functionality whenever possible. The platform provides a rich set of out-of-the-box features that can often fulfill business requirements without the need for extensive customization. App Builders should thoroughly explore these standard functionalities before resorting to custom development, ensuring that their solutions align with the natural evolution of the Salesforce platform.
A critical aspect of customization and upgradability is maintaining a comprehensive documentation strategy. Documenting the rationale behind each customization, the specific requirements it addresses, and any potential impacts on future upgrades provides a roadmap for administrators and developers. This documentation becomes invaluable during upgrade planning, ensuring a smooth transition and reducing the likelihood of post-upgrade issues.
User Permission and Access Management
User permission and access management play a pivotal role in the design and security of Salesforce applications, making it imperative for App Builders to implement robust strategies that align with business requirements and uphold data integrity. At the core of this best practice is the principle of least privilege, which entails granting users the minimum level of access necessary to perform their job functions. This approach minimizes the risk of unauthorized data exposure and helps maintain a secure Salesforce environment.
Salesforce offers a versatile set of tools for defining user permissions and access controls. One key aspect of effective access management involves configuring profiles and permission sets thoughtfully. Profiles establish the baseline permissions for a user, while permission sets allow for additional granular permissions as needed. App Builders should carefully define profiles based on job roles and responsibilities, ensuring that users have access only to the specific objects and fields required for their tasks.
Record-level security is another critical dimension of user permission management. Utilizing features such as sharing rules, role hierarchies, and manual sharing, App Builders can restrict access to specific records based on user roles and responsibilities. By implementing record-level security effectively, they can strike a balance between providing users with the necessary information and safeguarding sensitive data from unauthorized access.
User permission and access management is a critical best practice for Salesforce App Builders. By adhering to the principle of least privilege, configuring profiles and permission sets judiciously, implementing effective record-level security, and conducting regular audits, App Builders contribute to the creation of a secure and efficient Salesforce application environment that aligns with the organization's data privacy and security goals.
Testing and Quality Assurance Strategies
Testing and quality assurance are integral components of the Salesforce app development lifecycle, ensuring that applications function reliably, perform efficiently, and meet user expectations. Salesforce App Builders must adopt robust testing strategies to identify and rectify issues early in the development process, fostering a culture of quality and reliability.
Integration testing is equally critical, as it validates the interaction between different components within the Salesforce ecosystem and ensures that the application behaves as expected in a holistic environment. This involves testing various integration points, such as API connections and third-party integrations, to identify and resolve potential issues that may arise during real-world usage.
User acceptance testing (UAT) is a pivotal phase in quality assurance, involving end-users validating that the application meets their requirements and expectations. App Builders should collaborate closely with stakeholders to define test cases and scenarios that align with the business objectives. UAT not only serves as a final check before deployment but also provides valuable insights into user satisfaction and the application's overall usability.
Testing and quality assurance strategies are indispensable for Salesforce App Builders. Incorporating thorough unit testing, integration testing, user acceptance testing, and leveraging automation tools contribute to the creation of high-quality, reliable applications that meet both user expectations and business objectives.
Conclusion
In conclusion, mastering the art of Salesforce app development involves a careful blend of best practices that span various facets of the development lifecycle. From the effective use of declarative tools, such as Process Builder and Lightning App Builder, to the meticulous coding practices in Apex, App Builders must navigate a dynamic landscape to ensure their applications are not only tailored to business needs but are also scalable, maintainable, and align with Salesforce's continuous evolution.
The delicate balance between customization and upgradability is a key consideration, urging developers to make informed decisions about when and how to tailor solutions to meet specific requirements. Thoughtful customization, coupled with a keen eye for documentation and adherence to best practices, enables applications to seamlessly evolve with the Salesforce platform's advancements.
User permission and access management, another critical aspect, demand a strategic approach grounded in the principle of least privilege. By configuring profiles, permission sets, and record-level security with precision, App Builders create a secure environment that respects data privacy while providing users with the necessary tools to perform their roles effectively.
Testing and quality assurance emerge as linchpins in the development process, ensuring the reliability and efficiency of applications. Rigorous unit testing, comprehensive integration testing, and user acceptance testing contribute to the creation of robust solutions. Automation becomes a force multiplier in this context, enabling App Builders to maintain consistency and efficiency in testing processes.
The journey of a Salesforce App Builder is one of continuous learning, adaptation, and refinement. By embracing these best practices and remaining attuned to the ever-evolving Salesforce ecosystem, developers can navigate the complexities of app development with confidence, ultimately delivering solutions that stand the test of time and contribute to the success of the organizations they serve.
Top 10 Artificial Intelligence Project Ideas in 2024
AI permeates diverse sectors, including marketing, automation, transport, supply chain, and communication, showcasing its versatility across a spectrum of applications. This exploration delves into a myriad of artificial intelligence projects, spanning from cutting-edge research endeavors to practical, real-world implementations. Whether you're a technology enthusiast or someone intrigued by the future implications of AI, this article aims to unveil a wealth of captivating ideas and insights. Artificial intelligence has become an integral part of our daily lives, leaving its mark as we scroll through social media, stream music on Spotify, or swiftly search the vast realms of Google. Amidst this technological landscape, many students and professionals are opting for a Data Science Course, facilitating a seamless transition into the ever-evolving field of data science. The focus of this article lies in unraveling intriguing artificial intelligence project topics – a journey that begins now!
In this article
-
What are Artificial Intelligence Projects?
-
List of Top AI Projects with Source Code
-
AI Project Ideas: Beginner and Intermediate
-
AI Project Ideas: For Advanced Level
-
Why Should You Work on AI-Based Projects?
-
Frequently Asked Questions (FAQs)
What are Artificial Intelligence Projects?
Artificial Intelligence (AI) projects encompass a broad spectrum of initiatives that leverage machine learning algorithms, data analysis, and computational models to simulate intelligent behavior. These projects are designed to imbue machines or systems with the ability to learn, reason, and make decisions, often mirroring human cognitive functions. The scope of AI projects is vast and can range from developing advanced chatbots and virtual assistants to creating sophisticated predictive analytics models.
In essence, Artificial Intelligence Projects involve the application of AI techniques to solve real-world problems or enhance existing processes across various domains. These initiatives can be classified into categories such as natural language processing, computer vision, robotics, and machine learning applications. AI projects are not confined to specific industries; they find relevance in healthcare, finance, education, and beyond, contributing to the evolution of technology-driven solutions.
These projects typically begin with defining a problem or task that requires intelligent automation or decision-making capabilities. The subsequent phases involve data collection, preprocessing, and the selection of suitable algorithms. Throughout the development cycle, continuous testing, refinement, and optimization are essential to ensure the project's success. The ultimate goal of Artificial Intelligence Projects is to create systems that can adapt, improve their performance over time, and provide valuable insights or functionality in a manner that was previously unattainable without the integration of intelligent technologies.
List of Top AI Projects with Source Code
A plethora of innovative AI projects with available source code has emerged, providing enthusiasts and developers with valuable resources to explore, learn, and contribute to the field. One notable project is TensorFlow, an open-source machine learning library developed by Google. TensorFlow offers a range of tutorials and examples, making it a valuable asset for those diving into the world of deep learning and neural networks.
Another prominent project is OpenCV (Open Source Computer Vision Library), which facilitates computer vision applications. With its extensive collection of algorithms, OpenCV allows developers to delve into image and video processing, object detection, and facial recognition, among other computer vision tasks.
For natural language processing enthusiasts, the Natural Language Toolkit (NLTK) is a compelling project. NLTK, written in Python, provides tools for processing and analyzing human language data. It's widely used for tasks such as text classification, sentiment analysis, and language translation.
PyTorch, an open-source machine learning framework, has gained significant popularity for its dynamic computational graph, making it suitable for dynamic neural networks. With an active community and numerous tutorials, PyTorch is an excellent choice for projects involving deep learning.
The list wouldn't be complete without mentioning scikit-learn, a versatile machine learning library in Python. Scikit-learn offers tools for data mining and data analysis, making it an invaluable resource for building and deploying machine learning models in various applications.
These projects represent just a fraction of the rich ecosystem of AI projects with available source code. Whether you're interested in computer vision, natural language processing, or deep learning, exploring these projects can provide valuable insights and hands-on experience in the dynamic field of artificial intelligence.
AI Project Ideas: Beginner and Intermediate
Embarking on an AI project can be an exciting journey, especially for beginners and those at an intermediate level looking to expand their skills. For novices, a great starting point is a sentiment analysis project using natural language processing (NLP). This task involves analyzing and determining the sentiment expressed in text data, providing insights into whether the text conveys a positive, negative, or neutral sentiment. Utilizing Python and libraries like NLTK or spaCy, beginners can gain hands-on experience in text processing and machine learning.
Moving on to an intermediate level, a recommendation system project presents an engaging challenge. Recommendation systems are widely used in e-commerce, streaming platforms, and various online services to suggest relevant items or content to users. By delving into collaborative filtering or content-based filtering techniques, intermediate-level enthusiasts can implement personalized recommendation systems using tools like TensorFlow or PyTorch. This project allows for a deeper understanding of machine learning algorithms and their application in real-world scenarios.
For both beginners and those seeking an intermediate challenge, image classification projects offer a captivating avenue. Starting with basic image recognition tasks using pre-trained models like those provided by TensorFlow's Keras API can provide a solid foundation. As skills progress, enthusiasts can delve into more complex image classification challenges, perhaps even exploring the world of convolutional neural networks (CNNs) for enhanced accuracy.
Ultimately, the key is to choose AI project ideas that align with your current skill level and push you slightly beyond your comfort zone. Whether you're just starting or have some experience, these projects offer practical insights, allowing you to apply theoretical knowledge to tangible applications and gradually build your expertise in the dynamic field of artificial intelligence.
AI Project Ideas: For Advanced Level
For those at an advanced level in the realm of artificial intelligence, engaging in projects that push the boundaries of complexity and innovation can be both intellectually stimulating and professionally rewarding. One advanced AI project idea is the development of a generative adversarial network (GAN) for image synthesis. GANs are cutting-edge models that consist of two neural networks – a generator and a discriminator – engaged in a competitive process to create realistic images. Tackling this project allows advanced practitioners to delve into the nuances of deep learning architectures, training strategies, and fine-tuning models for high-quality image generation.
Natural language processing (NLP) enthusiasts at an advanced level might find developing a question-answering system powered by a deep learning model to be a challenging yet rewarding endeavor. This project involves building a system capable of comprehending and responding to user queries based on a given context. Leveraging advanced NLP models like BERT or GPT-3, participants can explore the complexities of language understanding, contextual embeddings, and the intricate interplay between question formulation and information retrieval.
Another intriguing project for advanced AI practitioners is reinforcement learning applied to robotic control. This involves training an autonomous agent to navigate and perform tasks in a simulated or real-world environment. Through the implementation of reinforcement learning algorithms, such as deep Q-learning or policy gradients, participants can explore the challenges of training agents to make sequential decisions, adapt to dynamic environments, and optimize their behavior over time.
These advanced AI project ideas not only push the boundaries of technological capabilities but also provide opportunities for contributing to cutting-edge research in the field. Engaging in such projects fosters a deeper understanding of complex algorithms, model architectures, and the practical applications of artificial intelligence in solving intricate problems.
Why Should You Work on AI-Based Projects?
Embarking on AI-based projects offers a myriad of compelling reasons for individuals interested in technology, innovation, and problem-solving. First and foremost, working on AI projects provides an avenue to contribute to the forefront of technological advancements. Artificial Intelligence represents a rapidly evolving field, and by actively participating in projects, individuals can stay abreast of the latest developments, contribute to the community, and be part of the transformative impact AI has on various industries.
Furthermore, engaging in AI-based projects enhances practical skill development. The hands-on experience gained through project work allows individuals to apply theoretical knowledge to real-world scenarios, honing their programming, data analysis, and machine learning skills. This experiential learning is invaluable for those looking to transition into roles where AI expertise is increasingly in demand.
AI projects also foster creativity and innovation. The challenges encountered while working on these projects often require out-of-the-box thinking and problem-solving. Whether it's developing advanced algorithms, creating novel applications, or optimizing existing models, the process of innovation inherent in AI projects contributes to personal growth and the expansion of one's intellectual capabilities.
The demand for AI expertise in the job market is on the rise. Engaging in AI-based projects not only adds depth to one's portfolio but also positions individuals favorably in a competitive job market. Employers increasingly seek professionals with practical experience in AI, making project work a valuable asset for career advancement and job opportunities in a variety of industries. In essence, working on AI-based projects is a multifaceted journey that combines personal enrichment, skill development, innovation, societal impact, and enhanced career prospects.
Frequently Asked Questions (FAQs)
Q1: What is Artificial Intelligence (AI)?
A1: Artificial Intelligence (AI) refers to the development of computer systems that can perform tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, understanding natural language, and perception.
Q2: How is Machine Learning different from Artificial Intelligence?
A2: Machine Learning (ML) is a subset of AI that focuses on the development of algorithms allowing computers to learn patterns from data. AI is a broader concept that encompasses various approaches, including ML, to simulate intelligent behavior.
Q3: What are some common applications of AI?
A3: AI finds applications in various fields, such as natural language processing (NLP), computer vision, speech recognition, robotics, healthcare, finance, and autonomous vehicles.
Q4: Can you provide examples of AI-based technologies in everyday life?
A4: Certainly! Examples include virtual assistants like Siri and Alexa, recommendation systems on platforms like Netflix, predictive text on smartphones, and facial recognition in photo applications.
Q5: How can someone get started with learning AI?
A5: Beginners can start with online courses and resources available on platforms like Coursera, edX, and Khan Academy. Learning programming languages like Python is also essential, as it is widely used in AI development.
Read More
AI permeates diverse sectors, including marketing, automation, transport, supply chain, and communication, showcasing its versatility across a spectrum of applications. This exploration delves into a myriad of artificial intelligence projects, spanning from cutting-edge research endeavors to practical, real-world implementations. Whether you're a technology enthusiast or someone intrigued by the future implications of AI, this article aims to unveil a wealth of captivating ideas and insights. Artificial intelligence has become an integral part of our daily lives, leaving its mark as we scroll through social media, stream music on Spotify, or swiftly search the vast realms of Google. Amidst this technological landscape, many students and professionals are opting for a Data Science Course, facilitating a seamless transition into the ever-evolving field of data science. The focus of this article lies in unraveling intriguing artificial intelligence project topics – a journey that begins now!
In this article
-
What are Artificial Intelligence Projects?
-
List of Top AI Projects with Source Code
-
AI Project Ideas: Beginner and Intermediate
-
AI Project Ideas: For Advanced Level
-
Why Should You Work on AI-Based Projects?
-
Frequently Asked Questions (FAQs)
What are Artificial Intelligence Projects?
Artificial Intelligence (AI) projects encompass a broad spectrum of initiatives that leverage machine learning algorithms, data analysis, and computational models to simulate intelligent behavior. These projects are designed to imbue machines or systems with the ability to learn, reason, and make decisions, often mirroring human cognitive functions. The scope of AI projects is vast and can range from developing advanced chatbots and virtual assistants to creating sophisticated predictive analytics models.
In essence, Artificial Intelligence Projects involve the application of AI techniques to solve real-world problems or enhance existing processes across various domains. These initiatives can be classified into categories such as natural language processing, computer vision, robotics, and machine learning applications. AI projects are not confined to specific industries; they find relevance in healthcare, finance, education, and beyond, contributing to the evolution of technology-driven solutions.
These projects typically begin with defining a problem or task that requires intelligent automation or decision-making capabilities. The subsequent phases involve data collection, preprocessing, and the selection of suitable algorithms. Throughout the development cycle, continuous testing, refinement, and optimization are essential to ensure the project's success. The ultimate goal of Artificial Intelligence Projects is to create systems that can adapt, improve their performance over time, and provide valuable insights or functionality in a manner that was previously unattainable without the integration of intelligent technologies.
List of Top AI Projects with Source Code
A plethora of innovative AI projects with available source code has emerged, providing enthusiasts and developers with valuable resources to explore, learn, and contribute to the field. One notable project is TensorFlow, an open-source machine learning library developed by Google. TensorFlow offers a range of tutorials and examples, making it a valuable asset for those diving into the world of deep learning and neural networks.
Another prominent project is OpenCV (Open Source Computer Vision Library), which facilitates computer vision applications. With its extensive collection of algorithms, OpenCV allows developers to delve into image and video processing, object detection, and facial recognition, among other computer vision tasks.
For natural language processing enthusiasts, the Natural Language Toolkit (NLTK) is a compelling project. NLTK, written in Python, provides tools for processing and analyzing human language data. It's widely used for tasks such as text classification, sentiment analysis, and language translation.
PyTorch, an open-source machine learning framework, has gained significant popularity for its dynamic computational graph, making it suitable for dynamic neural networks. With an active community and numerous tutorials, PyTorch is an excellent choice for projects involving deep learning.
The list wouldn't be complete without mentioning scikit-learn, a versatile machine learning library in Python. Scikit-learn offers tools for data mining and data analysis, making it an invaluable resource for building and deploying machine learning models in various applications.
These projects represent just a fraction of the rich ecosystem of AI projects with available source code. Whether you're interested in computer vision, natural language processing, or deep learning, exploring these projects can provide valuable insights and hands-on experience in the dynamic field of artificial intelligence.
AI Project Ideas: Beginner and Intermediate
Embarking on an AI project can be an exciting journey, especially for beginners and those at an intermediate level looking to expand their skills. For novices, a great starting point is a sentiment analysis project using natural language processing (NLP). This task involves analyzing and determining the sentiment expressed in text data, providing insights into whether the text conveys a positive, negative, or neutral sentiment. Utilizing Python and libraries like NLTK or spaCy, beginners can gain hands-on experience in text processing and machine learning.
Moving on to an intermediate level, a recommendation system project presents an engaging challenge. Recommendation systems are widely used in e-commerce, streaming platforms, and various online services to suggest relevant items or content to users. By delving into collaborative filtering or content-based filtering techniques, intermediate-level enthusiasts can implement personalized recommendation systems using tools like TensorFlow or PyTorch. This project allows for a deeper understanding of machine learning algorithms and their application in real-world scenarios.
For both beginners and those seeking an intermediate challenge, image classification projects offer a captivating avenue. Starting with basic image recognition tasks using pre-trained models like those provided by TensorFlow's Keras API can provide a solid foundation. As skills progress, enthusiasts can delve into more complex image classification challenges, perhaps even exploring the world of convolutional neural networks (CNNs) for enhanced accuracy.
Ultimately, the key is to choose AI project ideas that align with your current skill level and push you slightly beyond your comfort zone. Whether you're just starting or have some experience, these projects offer practical insights, allowing you to apply theoretical knowledge to tangible applications and gradually build your expertise in the dynamic field of artificial intelligence.
AI Project Ideas: For Advanced Level
For those at an advanced level in the realm of artificial intelligence, engaging in projects that push the boundaries of complexity and innovation can be both intellectually stimulating and professionally rewarding. One advanced AI project idea is the development of a generative adversarial network (GAN) for image synthesis. GANs are cutting-edge models that consist of two neural networks – a generator and a discriminator – engaged in a competitive process to create realistic images. Tackling this project allows advanced practitioners to delve into the nuances of deep learning architectures, training strategies, and fine-tuning models for high-quality image generation.
Natural language processing (NLP) enthusiasts at an advanced level might find developing a question-answering system powered by a deep learning model to be a challenging yet rewarding endeavor. This project involves building a system capable of comprehending and responding to user queries based on a given context. Leveraging advanced NLP models like BERT or GPT-3, participants can explore the complexities of language understanding, contextual embeddings, and the intricate interplay between question formulation and information retrieval.
Another intriguing project for advanced AI practitioners is reinforcement learning applied to robotic control. This involves training an autonomous agent to navigate and perform tasks in a simulated or real-world environment. Through the implementation of reinforcement learning algorithms, such as deep Q-learning or policy gradients, participants can explore the challenges of training agents to make sequential decisions, adapt to dynamic environments, and optimize their behavior over time.
These advanced AI project ideas not only push the boundaries of technological capabilities but also provide opportunities for contributing to cutting-edge research in the field. Engaging in such projects fosters a deeper understanding of complex algorithms, model architectures, and the practical applications of artificial intelligence in solving intricate problems.
Why Should You Work on AI-Based Projects?
Embarking on AI-based projects offers a myriad of compelling reasons for individuals interested in technology, innovation, and problem-solving. First and foremost, working on AI projects provides an avenue to contribute to the forefront of technological advancements. Artificial Intelligence represents a rapidly evolving field, and by actively participating in projects, individuals can stay abreast of the latest developments, contribute to the community, and be part of the transformative impact AI has on various industries.
Furthermore, engaging in AI-based projects enhances practical skill development. The hands-on experience gained through project work allows individuals to apply theoretical knowledge to real-world scenarios, honing their programming, data analysis, and machine learning skills. This experiential learning is invaluable for those looking to transition into roles where AI expertise is increasingly in demand.
AI projects also foster creativity and innovation. The challenges encountered while working on these projects often require out-of-the-box thinking and problem-solving. Whether it's developing advanced algorithms, creating novel applications, or optimizing existing models, the process of innovation inherent in AI projects contributes to personal growth and the expansion of one's intellectual capabilities.
The demand for AI expertise in the job market is on the rise. Engaging in AI-based projects not only adds depth to one's portfolio but also positions individuals favorably in a competitive job market. Employers increasingly seek professionals with practical experience in AI, making project work a valuable asset for career advancement and job opportunities in a variety of industries. In essence, working on AI-based projects is a multifaceted journey that combines personal enrichment, skill development, innovation, societal impact, and enhanced career prospects.
Frequently Asked Questions (FAQs)
Q1: What is Artificial Intelligence (AI)?
A1: Artificial Intelligence (AI) refers to the development of computer systems that can perform tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, understanding natural language, and perception.
Q2: How is Machine Learning different from Artificial Intelligence?
A2: Machine Learning (ML) is a subset of AI that focuses on the development of algorithms allowing computers to learn patterns from data. AI is a broader concept that encompasses various approaches, including ML, to simulate intelligent behavior.
Q3: What are some common applications of AI?
A3: AI finds applications in various fields, such as natural language processing (NLP), computer vision, speech recognition, robotics, healthcare, finance, and autonomous vehicles.
Q4: Can you provide examples of AI-based technologies in everyday life?
A4: Certainly! Examples include virtual assistants like Siri and Alexa, recommendation systems on platforms like Netflix, predictive text on smartphones, and facial recognition in photo applications.
Q5: How can someone get started with learning AI?
A5: Beginners can start with online courses and resources available on platforms like Coursera, edX, and Khan Academy. Learning programming languages like Python is also essential, as it is widely used in AI development.
Types of Cyber Attacks You Should Be Aware of in 2024
The advent of digital devices and the widespread availability of the internet have significantly enhanced the comfort and convenience in our daily lives. However, every silver lining has its cloud, and in the digital realm, safeguarding personal data has emerged as a critical challenge. While the internet has undeniably ushered in positive transformations, the looming threat of cyber attacks necessitates a closer examination of data protection strategies. In this piece, we delve into various cyber threats and explore effective measures to counteract them.
The contemporary era is marked by unparalleled comfort, courtesy of an array of digital devices seamlessly integrated with the internet. Yet, the conveniences offered by this digital landscape come hand in hand with a potential drawback – the vulnerability of personal data. While the internet contributes positively to our lives, the looming specter of cyber attacks demands our attention. This article sheds light on the diverse forms of cyber threats and offers insights into preventive measures to fortify our digital defenses.
Our present-day existence is characterized by an unprecedented level of comfort, driven by the synergy of digital devices and the omnipresent internet. However, within this digital utopia lies a darker reality – the constant threat to our data security. Despite the positive impact of the internet on our lives, the surge in cyber attacks poses a formidable challenge. This article aims to dissect various cyber threats and provide valuable guidance on fortifying your digital fortress against potential breaches.
Table of Contents
-
What is a Cyber Attack?
-
Types of Cyber Attacks
-
How to Prevent Cyber Attacks?
-
Evolution of Cyber Security
-
Conclusion
-
FAQs
What is a Cyber Attack?
A cyber attack is a malicious and deliberate attempt to exploit vulnerabilities in computer systems, networks, or digital infrastructure. It is an umbrella term that encompasses a wide range of activities with the common goal of unauthorized access, disruption, or manipulation of digital assets. Cyber attacks can target individuals, businesses, governments, or even critical infrastructure, posing significant risks to the confidentiality, integrity, and availability of sensitive information.
Cyber attacks can manifest in various forms, each with its distinct objectives and methodologies. Common types include malware attacks, where malicious software is deployed to compromise systems; phishing attacks, involving deceptive tactics to trick individuals into revealing sensitive information; and denial-of-service attacks, which overwhelm a system or network to disrupt its normal functioning. Additionally, more sophisticated attacks, such as advanced persistent threats (APTs), involve stealthy and prolonged efforts by hackers to infiltrate and maintain unauthorized access to a target's systems.
Preventing and mitigating the impact of cyber attacks requires a multifaceted approach, including robust cybersecurity measures, user education and awareness, and timely detection and response mechanisms. Organizations and individuals alike must stay vigilant and proactive in adapting their defenses to the evolving nature of cyber threats to safeguard against potential breaches and protect the digital infrastructure that has become integral to modern life.
Types of Cyber Attacks
Cyber attacks come in various forms, each exploiting different vulnerabilities in digital systems to achieve specific objectives. One prevalent type is the malware attack, where malicious software is introduced into a system to compromise its functionality. This can include viruses, worms, ransomware, and other forms of intrusive code designed to steal data, disrupt operations, or hold information hostage until a ransom is paid. Malware attacks often target both individuals and organizations, taking advantage of security lapses to infiltrate systems.
Phishing attacks represent another common cyber threat, relying on deceptive tactics to trick individuals into divulging sensitive information such as passwords, credit card numbers, or personal details. These attacks typically involve fraudulent emails, messages, or websites that mimic legitimate entities, aiming to exploit human trust and compromise security. Through clever social engineering, attackers can manipulate users into unknowingly providing access to confidential data.
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks focus on overwhelming a system, network, or service to the point of disruption. These attacks flood the target with an excessive volume of traffic, rendering it incapable of handling legitimate requests. By saturating resources, DoS and DDoS attacks can lead to service outages, hindering access to websites or online services and causing significant disruptions for the targeted entities.
Advanced persistent threats (APTs) represent a more sophisticated form of cyber attack characterized by a prolonged and stealthy approach. APTs involve persistent, targeted efforts by hackers to infiltrate and maintain unauthorized access to a specific target's systems. These attacks often involve meticulous planning, utilizing advanced techniques to evade detection and remain undetected over an extended period. APTs are typically associated with state-sponsored or highly organized cybercriminal groups seeking valuable information or strategic advantages.
Understanding the diverse landscape of cyber attacks is crucial for individuals, businesses, and governments to implement effective cybersecurity measures. By staying informed about emerging threats and adopting proactive defense strategies, entities can better protect themselves against the evolving and dynamic nature of cyber threats.
How to Prevent Cyber Attacks?
Preventing cyber attacks is a multifaceted process that requires a combination of proactive measures, robust cybersecurity practices, and user awareness. One fundamental step in enhancing cybersecurity is keeping software and systems up-to-date. Regularly applying security patches and updates helps address known vulnerabilities, reducing the risk of exploitation by cybercriminals. Organizations and individuals alike should prioritize the use of reputable antivirus and anti-malware software to provide an additional layer of defense against various forms of malicious code.
Implementing strong and unique passwords, as well as enabling multi-factor authentication (MFA), is crucial for enhancing access controls and preventing unauthorized access to accounts and systems. Cyber attackers often exploit weak or easily guessable passwords, making the use of complex, unique combinations essential for bolstering security. MFA adds an extra layer of protection by requiring multiple forms of verification, such as a password and a temporary code sent to a mobile device.
Education and awareness play a vital role in preventing cyber attacks. Training employees and users on recognizing phishing attempts, social engineering tactics, and other common cyber threats can significantly reduce the likelihood of falling victim to such attacks. Cybersecurity awareness programs empower individuals to make informed decisions and identify potential risks, contributing to an overall security-conscious environment.
Regular data backups are an essential part of a robust cybersecurity strategy. In the event of a ransomware attack or data loss, having up-to-date backups ensures that critical information can be restored without succumbing to extortion demands. Additionally, organizations should establish and regularly test an incident response plan to efficiently address and mitigate the impact of a cyber attack if one occurs.
Collaboration and information sharing within the cybersecurity community can also enhance collective defenses against evolving threats. Staying informed about the latest cyber threats, vulnerabilities, and best practices allows organizations to adapt their security measures to the dynamic nature of the digital landscape.
Preventing cyber attacks requires a comprehensive and proactive approach that encompasses technological solutions, user education, and a commitment to staying informed about emerging threats. By adopting a holistic cybersecurity strategy, individuals and organizations can significantly reduce their susceptibility to cyber attacks and better safeguard their digital assets.
Evolution of Cyber Security
The evolution of cybersecurity is a dynamic and ongoing process driven by the continuous advancements in technology and the corresponding evolution of cyber threats. In the early days of computing, security measures were relatively basic, focusing primarily on physical access controls and rudimentary password systems. As computing systems became more widespread and interconnected, the need for more sophisticated cybersecurity measures became evident.
The 1980s marked a significant turning point with the emergence of computer viruses, leading to the development of the first antivirus programs. As the internet gained prominence in the 1990s, cybersecurity efforts expanded to address the challenges posed by online connectivity. Firewalls, intrusion detection systems, and encryption technologies became essential components of safeguarding networks and data from unauthorized access.
The early 2000s saw a surge in cyber threats, including high-profile incidents like the Code Red and Nimda worms. This prompted a renewed focus on cybersecurity, with increased investment in research and development to create more robust defense mechanisms. The concept of a layered security approach gained traction, emphasizing the importance of combining various technologies and strategies to create a comprehensive defense against evolving threats.
Looking forward, the evolution of cybersecurity is expected to continue in response to emerging technologies, such as the Internet of Things (IoT) and 5G. The need for adaptive, resilient, and intelligent cybersecurity measures remains critical to stay ahead of the ever-evolving tactics employed by cyber adversaries. As the digital landscape evolves, so too must our approach to cybersecurity to ensure the protection of sensitive information and the integrity of interconnected systems.
Conclusion
In conclusion, the evolution of cybersecurity reflects a continuous and dynamic response to the ever-changing landscape of technology and cyber threats. From the rudimentary security measures of the early computing era to the sophisticated, adaptive systems of today, the journey has been marked by a relentless pursuit of resilience against malicious activities. As our reliance on interconnected technologies grows, so does the complexity of the challenges faced by cybersecurity professionals.
The timeline of cybersecurity reveals a progression from basic access controls to the development of antivirus programs, firewalls, and encryption technologies. The rise of the internet in the 1990s spurred further advancements, with a focus on protecting networks and data from online threats. The 2010s witnessed a paradigm shift with the integration of AI and ML, enhancing threat detection and response capabilities. This era also brought about the necessity of addressing challenges posed by cloud computing, mobile technologies, and sophisticated cyber attacks.
Looking ahead, the future of cybersecurity will undoubtedly be shaped by emerging technologies like IoT and 5G, presenting new opportunities and risks. The concept of Zero Trust, emphasizing continuous verification and security at every level, underscores the need for a proactive and adaptive approach. As cyber threats evolve, so must our strategies to ensure the confidentiality, integrity, and availability of digital assets.
In this ongoing journey, collaboration, education, and information sharing within the cybersecurity community will remain crucial. The collective efforts of individuals, organizations, and governments are essential to staying ahead of cyber adversaries. As we navigate the evolving digital landscape, the evolution of cybersecurity serves as a testament to our commitment to securing the interconnected world we inhabit. By staying vigilant, innovative, and united, we can continue to fortify our defenses against emerging threats and safeguard the integrity of our digital future.
FAQs
1.What is artificial intelligence (AI)?
A.AI refers to the development of computer systems capable of performing tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, perception, and language understanding.
2.How does machine learning work?
A.Machine learning is a subset of AI that involves training algorithms on data to make predictions or decisions without being explicitly programmed. The algorithms learn patterns from data and improve their performance over time.
3.What is the Internet of Things (IoT)?
A.IoT refers to the network of interconnected devices that can communicate and exchange data. These devices, ranging from household appliances to industrial machinery, are embedded with sensors and connected to the internet for enhanced functionality.
4.How can I protect my computer from viruses and malware?
A.To protect your computer, ensure you have reputable antivirus software installed, keep your operating system and software up-to-date with the latest security patches, and exercise caution when clicking on links or downloading files from unknown sources.
5.What is cybersecurity?
A.Cybersecurity involves practices, technologies, and processes designed to safeguard computer systems, networks, and data from unauthorized access, attacks, and damage.
Read More
The advent of digital devices and the widespread availability of the internet have significantly enhanced the comfort and convenience in our daily lives. However, every silver lining has its cloud, and in the digital realm, safeguarding personal data has emerged as a critical challenge. While the internet has undeniably ushered in positive transformations, the looming threat of cyber attacks necessitates a closer examination of data protection strategies. In this piece, we delve into various cyber threats and explore effective measures to counteract them.
The contemporary era is marked by unparalleled comfort, courtesy of an array of digital devices seamlessly integrated with the internet. Yet, the conveniences offered by this digital landscape come hand in hand with a potential drawback – the vulnerability of personal data. While the internet contributes positively to our lives, the looming specter of cyber attacks demands our attention. This article sheds light on the diverse forms of cyber threats and offers insights into preventive measures to fortify our digital defenses.
Our present-day existence is characterized by an unprecedented level of comfort, driven by the synergy of digital devices and the omnipresent internet. However, within this digital utopia lies a darker reality – the constant threat to our data security. Despite the positive impact of the internet on our lives, the surge in cyber attacks poses a formidable challenge. This article aims to dissect various cyber threats and provide valuable guidance on fortifying your digital fortress against potential breaches.
Table of Contents
-
What is a Cyber Attack?
-
Types of Cyber Attacks
-
How to Prevent Cyber Attacks?
-
Evolution of Cyber Security
-
Conclusion
-
FAQs
What is a Cyber Attack?
A cyber attack is a malicious and deliberate attempt to exploit vulnerabilities in computer systems, networks, or digital infrastructure. It is an umbrella term that encompasses a wide range of activities with the common goal of unauthorized access, disruption, or manipulation of digital assets. Cyber attacks can target individuals, businesses, governments, or even critical infrastructure, posing significant risks to the confidentiality, integrity, and availability of sensitive information.
Cyber attacks can manifest in various forms, each with its distinct objectives and methodologies. Common types include malware attacks, where malicious software is deployed to compromise systems; phishing attacks, involving deceptive tactics to trick individuals into revealing sensitive information; and denial-of-service attacks, which overwhelm a system or network to disrupt its normal functioning. Additionally, more sophisticated attacks, such as advanced persistent threats (APTs), involve stealthy and prolonged efforts by hackers to infiltrate and maintain unauthorized access to a target's systems.
Preventing and mitigating the impact of cyber attacks requires a multifaceted approach, including robust cybersecurity measures, user education and awareness, and timely detection and response mechanisms. Organizations and individuals alike must stay vigilant and proactive in adapting their defenses to the evolving nature of cyber threats to safeguard against potential breaches and protect the digital infrastructure that has become integral to modern life.
Types of Cyber Attacks
Cyber attacks come in various forms, each exploiting different vulnerabilities in digital systems to achieve specific objectives. One prevalent type is the malware attack, where malicious software is introduced into a system to compromise its functionality. This can include viruses, worms, ransomware, and other forms of intrusive code designed to steal data, disrupt operations, or hold information hostage until a ransom is paid. Malware attacks often target both individuals and organizations, taking advantage of security lapses to infiltrate systems.
Phishing attacks represent another common cyber threat, relying on deceptive tactics to trick individuals into divulging sensitive information such as passwords, credit card numbers, or personal details. These attacks typically involve fraudulent emails, messages, or websites that mimic legitimate entities, aiming to exploit human trust and compromise security. Through clever social engineering, attackers can manipulate users into unknowingly providing access to confidential data.
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks focus on overwhelming a system, network, or service to the point of disruption. These attacks flood the target with an excessive volume of traffic, rendering it incapable of handling legitimate requests. By saturating resources, DoS and DDoS attacks can lead to service outages, hindering access to websites or online services and causing significant disruptions for the targeted entities.
Advanced persistent threats (APTs) represent a more sophisticated form of cyber attack characterized by a prolonged and stealthy approach. APTs involve persistent, targeted efforts by hackers to infiltrate and maintain unauthorized access to a specific target's systems. These attacks often involve meticulous planning, utilizing advanced techniques to evade detection and remain undetected over an extended period. APTs are typically associated with state-sponsored or highly organized cybercriminal groups seeking valuable information or strategic advantages.
Understanding the diverse landscape of cyber attacks is crucial for individuals, businesses, and governments to implement effective cybersecurity measures. By staying informed about emerging threats and adopting proactive defense strategies, entities can better protect themselves against the evolving and dynamic nature of cyber threats.
How to Prevent Cyber Attacks?
Preventing cyber attacks is a multifaceted process that requires a combination of proactive measures, robust cybersecurity practices, and user awareness. One fundamental step in enhancing cybersecurity is keeping software and systems up-to-date. Regularly applying security patches and updates helps address known vulnerabilities, reducing the risk of exploitation by cybercriminals. Organizations and individuals alike should prioritize the use of reputable antivirus and anti-malware software to provide an additional layer of defense against various forms of malicious code.
Implementing strong and unique passwords, as well as enabling multi-factor authentication (MFA), is crucial for enhancing access controls and preventing unauthorized access to accounts and systems. Cyber attackers often exploit weak or easily guessable passwords, making the use of complex, unique combinations essential for bolstering security. MFA adds an extra layer of protection by requiring multiple forms of verification, such as a password and a temporary code sent to a mobile device.
Education and awareness play a vital role in preventing cyber attacks. Training employees and users on recognizing phishing attempts, social engineering tactics, and other common cyber threats can significantly reduce the likelihood of falling victim to such attacks. Cybersecurity awareness programs empower individuals to make informed decisions and identify potential risks, contributing to an overall security-conscious environment.
Regular data backups are an essential part of a robust cybersecurity strategy. In the event of a ransomware attack or data loss, having up-to-date backups ensures that critical information can be restored without succumbing to extortion demands. Additionally, organizations should establish and regularly test an incident response plan to efficiently address and mitigate the impact of a cyber attack if one occurs.
Collaboration and information sharing within the cybersecurity community can also enhance collective defenses against evolving threats. Staying informed about the latest cyber threats, vulnerabilities, and best practices allows organizations to adapt their security measures to the dynamic nature of the digital landscape.
Preventing cyber attacks requires a comprehensive and proactive approach that encompasses technological solutions, user education, and a commitment to staying informed about emerging threats. By adopting a holistic cybersecurity strategy, individuals and organizations can significantly reduce their susceptibility to cyber attacks and better safeguard their digital assets.
Evolution of Cyber Security
The evolution of cybersecurity is a dynamic and ongoing process driven by the continuous advancements in technology and the corresponding evolution of cyber threats. In the early days of computing, security measures were relatively basic, focusing primarily on physical access controls and rudimentary password systems. As computing systems became more widespread and interconnected, the need for more sophisticated cybersecurity measures became evident.
The 1980s marked a significant turning point with the emergence of computer viruses, leading to the development of the first antivirus programs. As the internet gained prominence in the 1990s, cybersecurity efforts expanded to address the challenges posed by online connectivity. Firewalls, intrusion detection systems, and encryption technologies became essential components of safeguarding networks and data from unauthorized access.
The early 2000s saw a surge in cyber threats, including high-profile incidents like the Code Red and Nimda worms. This prompted a renewed focus on cybersecurity, with increased investment in research and development to create more robust defense mechanisms. The concept of a layered security approach gained traction, emphasizing the importance of combining various technologies and strategies to create a comprehensive defense against evolving threats.
Looking forward, the evolution of cybersecurity is expected to continue in response to emerging technologies, such as the Internet of Things (IoT) and 5G. The need for adaptive, resilient, and intelligent cybersecurity measures remains critical to stay ahead of the ever-evolving tactics employed by cyber adversaries. As the digital landscape evolves, so too must our approach to cybersecurity to ensure the protection of sensitive information and the integrity of interconnected systems.
Conclusion
In conclusion, the evolution of cybersecurity reflects a continuous and dynamic response to the ever-changing landscape of technology and cyber threats. From the rudimentary security measures of the early computing era to the sophisticated, adaptive systems of today, the journey has been marked by a relentless pursuit of resilience against malicious activities. As our reliance on interconnected technologies grows, so does the complexity of the challenges faced by cybersecurity professionals.
The timeline of cybersecurity reveals a progression from basic access controls to the development of antivirus programs, firewalls, and encryption technologies. The rise of the internet in the 1990s spurred further advancements, with a focus on protecting networks and data from online threats. The 2010s witnessed a paradigm shift with the integration of AI and ML, enhancing threat detection and response capabilities. This era also brought about the necessity of addressing challenges posed by cloud computing, mobile technologies, and sophisticated cyber attacks.
Looking ahead, the future of cybersecurity will undoubtedly be shaped by emerging technologies like IoT and 5G, presenting new opportunities and risks. The concept of Zero Trust, emphasizing continuous verification and security at every level, underscores the need for a proactive and adaptive approach. As cyber threats evolve, so must our strategies to ensure the confidentiality, integrity, and availability of digital assets.
In this ongoing journey, collaboration, education, and information sharing within the cybersecurity community will remain crucial. The collective efforts of individuals, organizations, and governments are essential to staying ahead of cyber adversaries. As we navigate the evolving digital landscape, the evolution of cybersecurity serves as a testament to our commitment to securing the interconnected world we inhabit. By staying vigilant, innovative, and united, we can continue to fortify our defenses against emerging threats and safeguard the integrity of our digital future.
FAQs
1.What is artificial intelligence (AI)?
A.AI refers to the development of computer systems capable of performing tasks that typically require human intelligence. These tasks include learning, reasoning, problem-solving, perception, and language understanding.
2.How does machine learning work?
A.Machine learning is a subset of AI that involves training algorithms on data to make predictions or decisions without being explicitly programmed. The algorithms learn patterns from data and improve their performance over time.
3.What is the Internet of Things (IoT)?
A.IoT refers to the network of interconnected devices that can communicate and exchange data. These devices, ranging from household appliances to industrial machinery, are embedded with sensors and connected to the internet for enhanced functionality.
4.How can I protect my computer from viruses and malware?
A.To protect your computer, ensure you have reputable antivirus software installed, keep your operating system and software up-to-date with the latest security patches, and exercise caution when clicking on links or downloading files from unknown sources.
5.What is cybersecurity?
A.Cybersecurity involves practices, technologies, and processes designed to safeguard computer systems, networks, and data from unauthorized access, attacks, and damage.
10 Trending Business Management Research Topics in 2024
Navigating the complexities of today's dynamic business landscape is imperative for sustained competitiveness and profitability. A comprehensive grasp of business intricacies, ranging from organizational structure to financial dynamics, marketing tactics, and strategic planning, is indispensable. Undertaking a postgraduate program in business management, such as PGDM, demands the creation of a meticulously researched paper as a stepping stone to a successful career.
Yet, the primary hurdle lies in identifying a pertinent and contemporary research subject. To assist in overcoming this challenge, we present a curated compilation of ten trending business management research paper topics in 2024, encompassing technological advancements and groundbreaking leadership strategies. Complementing academic pursuits with enrollment in Business Management training courses can significantly augment your proficiency and understanding, propelling your career to unprecedented heights. Join us as we explore these avant-garde topics together, gaining valuable insights for professional advancement.
The primary challenge, however, lies in the selection of a relevant and up-to-date research topic. To facilitate this crucial decision-making process, we've compiled a list of ten trending business management research paper topics in 2024, covering the latest technological advancements and innovative leadership approaches. Enrolling in specialized Business Management training courses can further refine your skill set, empowering you to elevate your career to unprecedented levels. Join us as we delve into these cutting-edge topics together, unraveling insights that pave the way for professional growth.
In this article
-
What are some Good Business Management Research Topics?
-
Business Research: Types and Methodologies
-
How to Find Business Research Topics?
-
Conclusion
-
Frequently Asked Questions (FAQs)
What are some Good Business Management Research Topics?
Selecting a compelling and relevant research topic is a critical first step in the journey of exploring business management concepts. One promising avenue could be investigating the impact of digital transformation on traditional business models, exploring how companies adapt to emerging technologies and navigate the evolving landscape. Additionally, delving into sustainable business practices provides an opportunity to explore the intersection of profitability and environmental responsibility, addressing the growing importance of corporate social responsibility in today's business world.
Another intriguing research topic could revolve around the role of leadership in fostering innovation within organizations. Examining successful case studies and identifying key leadership strategies that drive creativity and adaptability could offer valuable insights for both academic understanding and practical application in the business realm. Moreover, studying the implications of remote work on team dynamics and productivity in the post-pandemic era presents a timely and relevant research avenue, given the transformative changes in work structures.
In the realm of marketing, exploring the effectiveness of personalized marketing strategies in the age of big data and artificial intelligence could shed light on the evolving relationship between businesses and consumers. Investigating how companies leverage data to tailor their marketing efforts and enhance customer engagement is a dynamic field ripe for exploration. Lastly, a research focus on the challenges and opportunities presented by global supply chain disruptions can provide valuable insights into risk management and resilience strategies adopted by businesses in an interconnected world.
These research topics offer diverse opportunities to explore and contribute to the evolving field of business management, providing a foundation for in-depth analysis and meaningful contributions to the business community.
Business Research: Types and Methodologies
Business research is a multifaceted field encompassing various types and methodologies, each tailored to address specific inquiries and objectives. One prevalent classification of business research types includes exploratory, descriptive, and explanatory research.
Exploratory research serves as an initial investigation into a poorly understood problem or phenomenon, providing insights and formulating hypotheses for further exploration. Descriptive research, on the other hand, focuses on detailing the characteristics of a particular subject, shedding light on its current state. Explanatory research seeks to establish cause-and-effect relationships, delving deeper into the understanding of why certain phenomena occur.
In terms of methodologies, quantitative and qualitative research stand as prominent approaches. Quantitative research involves the collection and analysis of numerical data, facilitating statistical interpretations and generalizable findings. This method is often employed to measure and quantify variables, enabling researchers to draw statistical inferences. Conversely, qualitative research centers on non-numerical data, utilizing methods such as interviews, focus groups, and case studies to gather rich, in-depth insights into complex phenomena. Qualitative research is particularly useful for exploring subjective experiences, attitudes, and behaviors.
Survey research is a widely employed method in business research, utilizing structured questionnaires to gather information from a sample of individuals. This method is valuable for studying large populations and collecting standardized data. Case studies, involving an in-depth analysis of a specific case or situation, offer a detailed understanding of complex business phenomena in their real-world context. Experimental research involves manipulating variables to observe their effect on an outcome, providing a controlled environment for testing hypotheses and establishing causal relationships.
Business research encompasses a variety of types and methodologies, allowing researchers to tailor their approaches to the specific nature of their inquiries and the context in which they operate. The choice of research type and methodology depends on the research question, objectives, and the depth of understanding required for informed decision-making in the business domain.
How to Find Business Research Topics?
Discovering compelling business research topics is a crucial initial step in the research process. A fruitful approach is to start by staying attuned to current trends and issues within the business world. This involves keeping abreast of industry news, market reports, and emerging technologies. By identifying gaps or controversies in existing knowledge, researchers can pinpoint areas where their contributions would be most valuable.
Engaging in academic literature is another effective method to uncover potential business research topics. Reading relevant journals, articles, and research papers can expose researchers to ongoing conversations and debates in the field. It also aids in understanding the existing body of knowledge, enabling scholars to identify gaps or areas where additional investigation is warranted. Paying attention to the methodologies employed in previous studies can inspire innovative research approaches.
Networking with professionals and academics in the business domain can provide valuable insights and suggestions for potential research topics. Attending conferences, workshops, and seminars allows researchers to interact with experts, exchange ideas, and gain a deeper understanding of current challenges and opportunities in the business landscape. Conversations with industry practitioners can reveal practical problems that merit scholarly attention.
Considering the interdisciplinary nature of business, researchers may find inspiration by exploring connections with other fields such as psychology, sociology, economics, or technology. These interdisciplinary intersections often present unique research opportunities that contribute to a more holistic understanding of business phenomena.
Finding business research topics involves a combination of staying informed about industry developments, engaging with existing literature, networking with professionals, exploring interdisciplinary connections, considering preferred research methodologies, and fostering creative brainstorming sessions. This holistic approach ensures that researchers identify relevant, impactful, and innovative topics that contribute meaningfully to the business research landscape.
Conclusion
In conclusion, the process of finding compelling business research topics is a dynamic and multifaceted endeavor that requires a strategic and informed approach. Researchers can start by immersing themselves in the current landscape of business through staying updated on industry trends, market reports, and emerging technologies. Exploring academic literature not only helps in understanding existing knowledge but also reveals gaps or areas that warrant further investigation. Networking with professionals and academics, attending conferences, and engaging in interdisciplinary exploration provide valuable perspectives and potential research avenues.
Considering the preferred research methodologies and experimenting with different approaches is essential in aligning research topics with the researcher's expertise and interests. The collaborative power of brainstorming sessions fosters creative thinking, helping generate innovative ideas for research projects. Ultimately, the process involves a blend of staying informed, critically analyzing existing knowledge, seeking diverse perspectives, and embracing creativity.
By adopting this comprehensive approach, researchers can identify relevant, impactful, and timely business research topics that contribute meaningfully to the academic and practical understanding of the business domain. The journey of finding research topics is not only a precursor to the research itself but also a continuous process of staying attuned to the evolving dynamics of the business world and contributing to its progressive development.
Frequently Asked Questions (FAQs)
1. What is business research?
A.Business research is a systematic inquiry conducted to gain insights, solve problems, or make informed decisions in the business domain. It involves the collection, analysis, and interpretation of data to address specific business-related questions.
2. How do I choose a business research topic?
A.Choose a business research topic by staying informed about industry trends, exploring academic literature, networking with professionals, considering interdisciplinary connections, reflecting on preferred methodologies, and engaging in collaborative brainstorming sessions.
3. What are the types of business research?
A.Business research can be classified into exploratory, descriptive, and explanatory types. Exploratory research investigates poorly understood problems, descriptive research details characteristics of a subject, and explanatory research establishes cause-and-effect relationships.
4. What are common research methodologies in business?
A.Common research methodologies in business include quantitative approaches (surveys, experiments) and qualitative approaches (interviews, case studies). Researchers choose methods based on their research questions and objectives.
5. How can I stay updated on business trends?
A.Stay updated on business trends by regularly reading industry news, market reports, academic journals, and attending conferences and seminars. Networking with professionals and engaging in interdisciplinary exploration also helps.
Read More
Navigating the complexities of today's dynamic business landscape is imperative for sustained competitiveness and profitability. A comprehensive grasp of business intricacies, ranging from organizational structure to financial dynamics, marketing tactics, and strategic planning, is indispensable. Undertaking a postgraduate program in business management, such as PGDM, demands the creation of a meticulously researched paper as a stepping stone to a successful career.
Yet, the primary hurdle lies in identifying a pertinent and contemporary research subject. To assist in overcoming this challenge, we present a curated compilation of ten trending business management research paper topics in 2024, encompassing technological advancements and groundbreaking leadership strategies. Complementing academic pursuits with enrollment in Business Management training courses can significantly augment your proficiency and understanding, propelling your career to unprecedented heights. Join us as we explore these avant-garde topics together, gaining valuable insights for professional advancement.
The primary challenge, however, lies in the selection of a relevant and up-to-date research topic. To facilitate this crucial decision-making process, we've compiled a list of ten trending business management research paper topics in 2024, covering the latest technological advancements and innovative leadership approaches. Enrolling in specialized Business Management training courses can further refine your skill set, empowering you to elevate your career to unprecedented levels. Join us as we delve into these cutting-edge topics together, unraveling insights that pave the way for professional growth.
In this article
-
What are some Good Business Management Research Topics?
-
Business Research: Types and Methodologies
-
How to Find Business Research Topics?
-
Conclusion
-
Frequently Asked Questions (FAQs)
What are some Good Business Management Research Topics?
Selecting a compelling and relevant research topic is a critical first step in the journey of exploring business management concepts. One promising avenue could be investigating the impact of digital transformation on traditional business models, exploring how companies adapt to emerging technologies and navigate the evolving landscape. Additionally, delving into sustainable business practices provides an opportunity to explore the intersection of profitability and environmental responsibility, addressing the growing importance of corporate social responsibility in today's business world.
Another intriguing research topic could revolve around the role of leadership in fostering innovation within organizations. Examining successful case studies and identifying key leadership strategies that drive creativity and adaptability could offer valuable insights for both academic understanding and practical application in the business realm. Moreover, studying the implications of remote work on team dynamics and productivity in the post-pandemic era presents a timely and relevant research avenue, given the transformative changes in work structures.
In the realm of marketing, exploring the effectiveness of personalized marketing strategies in the age of big data and artificial intelligence could shed light on the evolving relationship between businesses and consumers. Investigating how companies leverage data to tailor their marketing efforts and enhance customer engagement is a dynamic field ripe for exploration. Lastly, a research focus on the challenges and opportunities presented by global supply chain disruptions can provide valuable insights into risk management and resilience strategies adopted by businesses in an interconnected world.
These research topics offer diverse opportunities to explore and contribute to the evolving field of business management, providing a foundation for in-depth analysis and meaningful contributions to the business community.
Business Research: Types and Methodologies
Business research is a multifaceted field encompassing various types and methodologies, each tailored to address specific inquiries and objectives. One prevalent classification of business research types includes exploratory, descriptive, and explanatory research.
Exploratory research serves as an initial investigation into a poorly understood problem or phenomenon, providing insights and formulating hypotheses for further exploration. Descriptive research, on the other hand, focuses on detailing the characteristics of a particular subject, shedding light on its current state. Explanatory research seeks to establish cause-and-effect relationships, delving deeper into the understanding of why certain phenomena occur.
In terms of methodologies, quantitative and qualitative research stand as prominent approaches. Quantitative research involves the collection and analysis of numerical data, facilitating statistical interpretations and generalizable findings. This method is often employed to measure and quantify variables, enabling researchers to draw statistical inferences. Conversely, qualitative research centers on non-numerical data, utilizing methods such as interviews, focus groups, and case studies to gather rich, in-depth insights into complex phenomena. Qualitative research is particularly useful for exploring subjective experiences, attitudes, and behaviors.
Survey research is a widely employed method in business research, utilizing structured questionnaires to gather information from a sample of individuals. This method is valuable for studying large populations and collecting standardized data. Case studies, involving an in-depth analysis of a specific case or situation, offer a detailed understanding of complex business phenomena in their real-world context. Experimental research involves manipulating variables to observe their effect on an outcome, providing a controlled environment for testing hypotheses and establishing causal relationships.
Business research encompasses a variety of types and methodologies, allowing researchers to tailor their approaches to the specific nature of their inquiries and the context in which they operate. The choice of research type and methodology depends on the research question, objectives, and the depth of understanding required for informed decision-making in the business domain.
How to Find Business Research Topics?
Discovering compelling business research topics is a crucial initial step in the research process. A fruitful approach is to start by staying attuned to current trends and issues within the business world. This involves keeping abreast of industry news, market reports, and emerging technologies. By identifying gaps or controversies in existing knowledge, researchers can pinpoint areas where their contributions would be most valuable.
Engaging in academic literature is another effective method to uncover potential business research topics. Reading relevant journals, articles, and research papers can expose researchers to ongoing conversations and debates in the field. It also aids in understanding the existing body of knowledge, enabling scholars to identify gaps or areas where additional investigation is warranted. Paying attention to the methodologies employed in previous studies can inspire innovative research approaches.
Networking with professionals and academics in the business domain can provide valuable insights and suggestions for potential research topics. Attending conferences, workshops, and seminars allows researchers to interact with experts, exchange ideas, and gain a deeper understanding of current challenges and opportunities in the business landscape. Conversations with industry practitioners can reveal practical problems that merit scholarly attention.
Considering the interdisciplinary nature of business, researchers may find inspiration by exploring connections with other fields such as psychology, sociology, economics, or technology. These interdisciplinary intersections often present unique research opportunities that contribute to a more holistic understanding of business phenomena.
Finding business research topics involves a combination of staying informed about industry developments, engaging with existing literature, networking with professionals, exploring interdisciplinary connections, considering preferred research methodologies, and fostering creative brainstorming sessions. This holistic approach ensures that researchers identify relevant, impactful, and innovative topics that contribute meaningfully to the business research landscape.
Conclusion
In conclusion, the process of finding compelling business research topics is a dynamic and multifaceted endeavor that requires a strategic and informed approach. Researchers can start by immersing themselves in the current landscape of business through staying updated on industry trends, market reports, and emerging technologies. Exploring academic literature not only helps in understanding existing knowledge but also reveals gaps or areas that warrant further investigation. Networking with professionals and academics, attending conferences, and engaging in interdisciplinary exploration provide valuable perspectives and potential research avenues.
Considering the preferred research methodologies and experimenting with different approaches is essential in aligning research topics with the researcher's expertise and interests. The collaborative power of brainstorming sessions fosters creative thinking, helping generate innovative ideas for research projects. Ultimately, the process involves a blend of staying informed, critically analyzing existing knowledge, seeking diverse perspectives, and embracing creativity.
By adopting this comprehensive approach, researchers can identify relevant, impactful, and timely business research topics that contribute meaningfully to the academic and practical understanding of the business domain. The journey of finding research topics is not only a precursor to the research itself but also a continuous process of staying attuned to the evolving dynamics of the business world and contributing to its progressive development.
Frequently Asked Questions (FAQs)
1. What is business research?
A.Business research is a systematic inquiry conducted to gain insights, solve problems, or make informed decisions in the business domain. It involves the collection, analysis, and interpretation of data to address specific business-related questions.
2. How do I choose a business research topic?
A.Choose a business research topic by staying informed about industry trends, exploring academic literature, networking with professionals, considering interdisciplinary connections, reflecting on preferred methodologies, and engaging in collaborative brainstorming sessions.
3. What are the types of business research?
A.Business research can be classified into exploratory, descriptive, and explanatory types. Exploratory research investigates poorly understood problems, descriptive research details characteristics of a subject, and explanatory research establishes cause-and-effect relationships.
4. What are common research methodologies in business?
A.Common research methodologies in business include quantitative approaches (surveys, experiments) and qualitative approaches (interviews, case studies). Researchers choose methods based on their research questions and objectives.
5. How can I stay updated on business trends?
A.Stay updated on business trends by regularly reading industry news, market reports, academic journals, and attending conferences and seminars. Networking with professionals and engaging in interdisciplinary exploration also helps.
5 Innovative IoT Applications Transforming Industries Today
In the fast-evolving landscape of technology, the Internet of Things (IoT) has emerged as a transformative force, reshaping industries and revolutionizing the way businesses operate. This interconnected network of devices, sensors, and machines has given rise to a plethora of innovative applications that are making a substantial impact on various sectors. In this blog post, we will explore "5 Innovative IoT Applications Transforming Industries Today," delving into the cutting-edge solutions that are driving efficiency, enhancing productivity, and fostering unprecedented advancements across diverse domains. From smart manufacturing to healthcare, agriculture, and beyond, these real-world applications showcase the tangible benefits of incorporating IoT into everyday processes. As we navigate through these transformative use cases, it becomes evident that IoT is not just a buzzword but a tangible force driving a new era of interconnected intelligence and industrial optimization. Let's dive into the exciting realm where technology meets innovation, reshaping the present and defining the future.
Table of contents
-
Smart Manufacturing: Revolutionizing Production Processes
-
IoT in Healthcare: Enhancing Patient Care and Remote Monitoring
-
Precision Agriculture: IoT's Impact on Sustainable Farming
-
Supply Chain Visibility: Transformative IoT Solutions for Logistics
-
Smart Cities: IoT's Contribution to Urban Development
-
Conclusion
Smart Manufacturing: Revolutionizing Production Processes
Smart manufacturing represents a revolutionary approach to traditional production processes, fundamentally transforming the landscape of industrial production. At its core, this paradigm shift integrates advanced technologies such as the Internet of Things (IoT), artificial intelligence (AI), machine learning, big data analytics, and robotics into conventional manufacturing systems. The synergy of these cutting-edge elements brings about a new era in manufacturing, where efficiency, flexibility, and productivity are greatly enhanced.
One pivotal aspect of smart manufacturing is the incorporation of the Internet of Things (IoT). This involves connecting physical devices, sensors, and machines to the internet, fostering real-time communication and data exchange. The seamless connectivity achieved through IoT enables a holistic view of the manufacturing environment, facilitating improved control and decision-making throughout the production chain.
Data analytics and big data play a crucial role in the smart manufacturing landscape. The copious amounts of data generated by sensors and devices are analyzed to derive meaningful insights. This analytical prowess aids in identifying patterns, predicting maintenance requirements, optimizing production schedules, and making informed decisions. The intelligent use of data becomes a cornerstone in the quest for heightened operational efficiency.
Artificial intelligence (AI) and machine learning bring an unprecedented level of automation and adaptability to manufacturing processes. These technologies empower machines to learn from data, optimize performance, and make real-time adjustments. AI algorithms can predict equipment failures, automate complex tasks, and continuously improve efficiency, marking a significant departure from traditional, static manufacturing methodologies.
The integration of advanced robotics is another key facet of smart manufacturing. Robots are deployed to perform tasks with precision, speed, and consistency, freeing human workers from mundane and repetitive activities. This not only enhances the overall efficiency of production but also allows human workers to focus on more intricate and creative aspects of the manufacturing process.
The transformative impact of smart manufacturing is evident in its array of benefits. Increased efficiency is achieved through the automation and optimization of processes, resulting in higher production output and reduced waste. The flexibility and adaptability inherent in smart manufacturing allow for quick adjustments to changing market demands, facilitating the production of customized products with ease. Predictive maintenance, made possible by real-time data analysis, minimizes downtime by addressing equipment issues before they escalate. Improved product quality, achieved through constant monitoring and control mechanisms, ensures that the end products meet or exceed desired standards. Additionally, the cost reduction is a natural outcome of automation, minimizing manual labor, reducing waste, and optimizing resource utilization.
IoT in Healthcare: Enhancing Patient Care and Remote Monitoring
The integration of the Internet of Things (IoT) into healthcare is ushering in a new era of patient care and remote monitoring, offering unprecedented opportunities to enhance medical services and improve health outcomes. IoT in healthcare involves the interconnection of medical devices, wearables, and sensors, creating a network that facilitates real-time data collection, analysis, and communication. This technological integration has the potential to revolutionize patient care by providing healthcare professionals with timely and actionable information, as well as empowering individuals to actively manage their health.
One of the primary applications of IoT in healthcare is in remote patient monitoring. Wearable devices equipped with sensors can continuously collect vital signs, such as heart rate, blood pressure, and oxygen levels, allowing healthcare providers to monitor patients' health remotely. This is particularly beneficial for individuals with chronic conditions, as it enables early detection of abnormalities and timely intervention, reducing the need for frequent hospital visits and improving overall quality of life.
The advent of IoT in healthcare has also led to the development of smart medical devices that can be integrated into the patient care ecosystem. These devices, ranging from smart insulin pumps to medication adherence trackers, contribute to more personalized and efficient healthcare delivery. Through seamless connectivity, healthcare professionals can access real-time data, enabling them to tailor treatment plans to individual patient needs, enhance medication management, and optimize therapeutic outcomes.
IoT in healthcare is reshaping the landscape of patient care and remote monitoring, offering a wealth of possibilities to improve health outcomes and enhance the patient experience. As technology continues to advance, the integration of IoT into healthcare practices holds tremendous potential for creating a more connected, efficient, and patient-centric healthcare ecosystem.
Precision Agriculture: IoT's Impact on Sustainable Farming
Precision agriculture, propelled by the Internet of Things (IoT), stands as a transformative force in the realm of sustainable farming. This innovative approach leverages a network of interconnected devices, sensors, and data analytics to optimize various aspects of agricultural processes. At its core, precision agriculture aims to enhance the efficiency of farming practices, reduce environmental impact, and promote sustainability in food production.
The integration of IoT technologies into precision agriculture introduces a level of connectivity that was previously unimaginable. Sensors embedded in the soil, on machinery, and even on crops collect real-time data on various environmental factors, including soil moisture, temperature, and nutrient levels. This wealth of information is then transmitted to a centralized system where advanced analytics and algorithms process the data, providing farmers with valuable insights into their fields' conditions.
The impact of precision agriculture on sustainable farming extends beyond resource management. The data-driven insights provided by IoT technologies enable farmers to make informed decisions regarding pest control and disease management. Early detection of potential issues allows for timely intervention, reducing the need for excessive pesticide use and minimizing the environmental impact associated with traditional, indiscriminate application methods.
The impact of IoT on sustainable farming through precision agriculture is profound. The integration of interconnected devices, sensors, and data analytics empowers farmers to make data-driven decisions, optimize resource usage, and mitigate environmental impact. As the global population continues to grow, the adoption of precision agriculture becomes increasingly critical for ensuring food security, economic sustainability, and environmental stewardship in the agricultural sector.
Supply Chain Visibility: Transformative IoT Solutions for Logistics
Supply chain visibility has undergone a transformative shift with the integration of Internet of Things (IoT) solutions, bringing unprecedented efficiency and transparency to logistics processes. Traditionally, supply chain management has grappled with challenges such as limited real-time information, inefficient inventory tracking, and a lack of visibility into the movement of goods. IoT technologies address these issues by establishing a network of interconnected devices and sensors that continuously gather and transmit data throughout the supply chain.
One of the key contributions of IoT to supply chain visibility is real-time tracking. Sensors attached to shipments, containers, and vehicles provide accurate and up-to-the-minute location data. This not only allows logistics professionals to monitor the progress of shipments in real-time but also enables predictive analytics for more accurate estimations of arrival times. The result is improved responsiveness, reduced delays, and enhanced overall efficiency in supply chain operations.
IoT solutions also play a pivotal role in inventory management. Smart sensors embedded in storage facilities and on individual products provide real-time data on inventory levels, conditions, and potential issues such as damage or theft. This level of visibility enables companies to optimize stock levels, reduce the risk of stockouts or overstock situations, and enhance demand forecasting accuracy, ultimately leading to cost savings and improved customer satisfaction.
Predictive maintenance is another valuable application of IoT in logistics. Sensors on vehicles and machinery in the supply chain can detect signs of wear or potential malfunctions before they escalate into serious issues. By anticipating maintenance needs, companies can schedule repairs or replacements proactively, minimizing downtime, reducing maintenance costs, and ensuring the reliability of their transportation assets.
Supply chain visibility has been revolutionized by the adoption of IoT solutions in logistics. Real-time tracking, enhanced inventory management, condition monitoring, predictive maintenance, and data-driven decision-making are just a few examples of how IoT is transforming traditional supply chain processes. As businesses increasingly recognize the value of these technologies, the logistics industry is poised for continued advancements that will drive efficiency, reduce costs, and improve the resilience of supply chains in an ever-evolving global marketplace.
Smart Cities: IoT's Contribution to Urban Development
The advent of smart cities, driven by the integration of Internet of Things (IoT) technologies, marks a significant milestone in urban development. Smart cities leverage a network of connected devices, sensors, and data analytics to enhance the efficiency, sustainability, and overall quality of urban living. This transformative approach represents a response to the complex challenges faced by growing urban populations, ranging from traffic congestion and energy consumption to waste management and public safety.
IoT plays a pivotal role in enhancing public services and utilities within smart cities. Smart meters, for instance, allow for more accurate monitoring and management of water and energy consumption. This not only helps in conserving resources but also enables more precise billing and responsiveness to fluctuations in demand. Additionally, waste management systems benefit from IoT, with sensors placed in trash bins providing real-time data on fill levels. This information optimizes waste collection routes, reducing operational costs and promoting environmental sustainability.
The integration of IoT in smart cities is not without challenges, including data security and privacy concerns. As cities amass vast amounts of data from various sources, ensuring the protection of sensitive information becomes paramount. Robust cybersecurity measures and privacy regulations are crucial to building and maintaining public trust in the deployment of IoT technologies for urban development.
The contribution of IoT to smart cities is multifaceted, ushering in a new era of urban development characterized by efficiency, sustainability, and enhanced quality of life. By leveraging connected devices and data analytics, smart cities are better equipped to address the complexities of urban living, offering innovative solutions to challenges and paving the way for a more connected, resilient, and sustainable urban future.
How to obtain INTERNET OF THINGS certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, the integration of the Internet of Things (IoT) into various domains, such as manufacturing, healthcare, logistics, and urban development, has ushered in a transformative era of innovation and efficiency. These applications showcase the versatile impact of IoT technologies, highlighting their ability to enhance processes, optimize resource utilization, and improve overall quality of life.
Healthcare, IoT has paved the way for a new era of patient care and remote monitoring. Wearable devices, smart medical equipment, and health apps empower individuals to actively engage in their well-being, while healthcare professionals benefit from real-time data insights that enable more personalized and effective treatment plans.
Logistics has witnessed a significant transformation through supply chain visibility powered by IoT solutions. Real-time tracking, condition monitoring, and predictive maintenance have streamlined operations, reduced costs, and improved the reliability and efficiency of supply chain processes. This has implications not only for businesses but also for environmental sustainability through optimized resource usage.
Smart cities represent the convergence of IoT technologies in urban development, addressing challenges related to infrastructure, utilities, public services, and safety. The implementation of intelligent systems and connected devices allows cities to make data-driven decisions, creating more efficient, sustainable, and livable urban environments.
While the benefits of IoT applications are substantial, challenges such as data security and privacy must be addressed to ensure the responsible and ethical deployment of these technologies. As industries continue to embrace and adapt to the opportunities presented by IoT, ongoing research, collaboration, and regulatory frameworks will be essential to maximize the positive impact while mitigating potential risks.
The evolution of IoT continues to shape the way we live, work, and interact with the world around us. As technology advances and new possibilities emerge, the ongoing integration of IoT promises to drive further innovation, redefine industry standards, and contribute to a more connected, intelligent, and sustainable future.
Read More
In the fast-evolving landscape of technology, the Internet of Things (IoT) has emerged as a transformative force, reshaping industries and revolutionizing the way businesses operate. This interconnected network of devices, sensors, and machines has given rise to a plethora of innovative applications that are making a substantial impact on various sectors. In this blog post, we will explore "5 Innovative IoT Applications Transforming Industries Today," delving into the cutting-edge solutions that are driving efficiency, enhancing productivity, and fostering unprecedented advancements across diverse domains. From smart manufacturing to healthcare, agriculture, and beyond, these real-world applications showcase the tangible benefits of incorporating IoT into everyday processes. As we navigate through these transformative use cases, it becomes evident that IoT is not just a buzzword but a tangible force driving a new era of interconnected intelligence and industrial optimization. Let's dive into the exciting realm where technology meets innovation, reshaping the present and defining the future.
Table of contents
-
Smart Manufacturing: Revolutionizing Production Processes
-
IoT in Healthcare: Enhancing Patient Care and Remote Monitoring
-
Precision Agriculture: IoT's Impact on Sustainable Farming
-
Supply Chain Visibility: Transformative IoT Solutions for Logistics
-
Smart Cities: IoT's Contribution to Urban Development
-
Conclusion
Smart Manufacturing: Revolutionizing Production Processes
Smart manufacturing represents a revolutionary approach to traditional production processes, fundamentally transforming the landscape of industrial production. At its core, this paradigm shift integrates advanced technologies such as the Internet of Things (IoT), artificial intelligence (AI), machine learning, big data analytics, and robotics into conventional manufacturing systems. The synergy of these cutting-edge elements brings about a new era in manufacturing, where efficiency, flexibility, and productivity are greatly enhanced.
One pivotal aspect of smart manufacturing is the incorporation of the Internet of Things (IoT). This involves connecting physical devices, sensors, and machines to the internet, fostering real-time communication and data exchange. The seamless connectivity achieved through IoT enables a holistic view of the manufacturing environment, facilitating improved control and decision-making throughout the production chain.
Data analytics and big data play a crucial role in the smart manufacturing landscape. The copious amounts of data generated by sensors and devices are analyzed to derive meaningful insights. This analytical prowess aids in identifying patterns, predicting maintenance requirements, optimizing production schedules, and making informed decisions. The intelligent use of data becomes a cornerstone in the quest for heightened operational efficiency.
Artificial intelligence (AI) and machine learning bring an unprecedented level of automation and adaptability to manufacturing processes. These technologies empower machines to learn from data, optimize performance, and make real-time adjustments. AI algorithms can predict equipment failures, automate complex tasks, and continuously improve efficiency, marking a significant departure from traditional, static manufacturing methodologies.
The integration of advanced robotics is another key facet of smart manufacturing. Robots are deployed to perform tasks with precision, speed, and consistency, freeing human workers from mundane and repetitive activities. This not only enhances the overall efficiency of production but also allows human workers to focus on more intricate and creative aspects of the manufacturing process.
The transformative impact of smart manufacturing is evident in its array of benefits. Increased efficiency is achieved through the automation and optimization of processes, resulting in higher production output and reduced waste. The flexibility and adaptability inherent in smart manufacturing allow for quick adjustments to changing market demands, facilitating the production of customized products with ease. Predictive maintenance, made possible by real-time data analysis, minimizes downtime by addressing equipment issues before they escalate. Improved product quality, achieved through constant monitoring and control mechanisms, ensures that the end products meet or exceed desired standards. Additionally, the cost reduction is a natural outcome of automation, minimizing manual labor, reducing waste, and optimizing resource utilization.
IoT in Healthcare: Enhancing Patient Care and Remote Monitoring
The integration of the Internet of Things (IoT) into healthcare is ushering in a new era of patient care and remote monitoring, offering unprecedented opportunities to enhance medical services and improve health outcomes. IoT in healthcare involves the interconnection of medical devices, wearables, and sensors, creating a network that facilitates real-time data collection, analysis, and communication. This technological integration has the potential to revolutionize patient care by providing healthcare professionals with timely and actionable information, as well as empowering individuals to actively manage their health.
One of the primary applications of IoT in healthcare is in remote patient monitoring. Wearable devices equipped with sensors can continuously collect vital signs, such as heart rate, blood pressure, and oxygen levels, allowing healthcare providers to monitor patients' health remotely. This is particularly beneficial for individuals with chronic conditions, as it enables early detection of abnormalities and timely intervention, reducing the need for frequent hospital visits and improving overall quality of life.
The advent of IoT in healthcare has also led to the development of smart medical devices that can be integrated into the patient care ecosystem. These devices, ranging from smart insulin pumps to medication adherence trackers, contribute to more personalized and efficient healthcare delivery. Through seamless connectivity, healthcare professionals can access real-time data, enabling them to tailor treatment plans to individual patient needs, enhance medication management, and optimize therapeutic outcomes.
IoT in healthcare is reshaping the landscape of patient care and remote monitoring, offering a wealth of possibilities to improve health outcomes and enhance the patient experience. As technology continues to advance, the integration of IoT into healthcare practices holds tremendous potential for creating a more connected, efficient, and patient-centric healthcare ecosystem.
Precision Agriculture: IoT's Impact on Sustainable Farming
Precision agriculture, propelled by the Internet of Things (IoT), stands as a transformative force in the realm of sustainable farming. This innovative approach leverages a network of interconnected devices, sensors, and data analytics to optimize various aspects of agricultural processes. At its core, precision agriculture aims to enhance the efficiency of farming practices, reduce environmental impact, and promote sustainability in food production.
The integration of IoT technologies into precision agriculture introduces a level of connectivity that was previously unimaginable. Sensors embedded in the soil, on machinery, and even on crops collect real-time data on various environmental factors, including soil moisture, temperature, and nutrient levels. This wealth of information is then transmitted to a centralized system where advanced analytics and algorithms process the data, providing farmers with valuable insights into their fields' conditions.
The impact of precision agriculture on sustainable farming extends beyond resource management. The data-driven insights provided by IoT technologies enable farmers to make informed decisions regarding pest control and disease management. Early detection of potential issues allows for timely intervention, reducing the need for excessive pesticide use and minimizing the environmental impact associated with traditional, indiscriminate application methods.
The impact of IoT on sustainable farming through precision agriculture is profound. The integration of interconnected devices, sensors, and data analytics empowers farmers to make data-driven decisions, optimize resource usage, and mitigate environmental impact. As the global population continues to grow, the adoption of precision agriculture becomes increasingly critical for ensuring food security, economic sustainability, and environmental stewardship in the agricultural sector.
Supply Chain Visibility: Transformative IoT Solutions for Logistics
Supply chain visibility has undergone a transformative shift with the integration of Internet of Things (IoT) solutions, bringing unprecedented efficiency and transparency to logistics processes. Traditionally, supply chain management has grappled with challenges such as limited real-time information, inefficient inventory tracking, and a lack of visibility into the movement of goods. IoT technologies address these issues by establishing a network of interconnected devices and sensors that continuously gather and transmit data throughout the supply chain.
One of the key contributions of IoT to supply chain visibility is real-time tracking. Sensors attached to shipments, containers, and vehicles provide accurate and up-to-the-minute location data. This not only allows logistics professionals to monitor the progress of shipments in real-time but also enables predictive analytics for more accurate estimations of arrival times. The result is improved responsiveness, reduced delays, and enhanced overall efficiency in supply chain operations.
IoT solutions also play a pivotal role in inventory management. Smart sensors embedded in storage facilities and on individual products provide real-time data on inventory levels, conditions, and potential issues such as damage or theft. This level of visibility enables companies to optimize stock levels, reduce the risk of stockouts or overstock situations, and enhance demand forecasting accuracy, ultimately leading to cost savings and improved customer satisfaction.
Predictive maintenance is another valuable application of IoT in logistics. Sensors on vehicles and machinery in the supply chain can detect signs of wear or potential malfunctions before they escalate into serious issues. By anticipating maintenance needs, companies can schedule repairs or replacements proactively, minimizing downtime, reducing maintenance costs, and ensuring the reliability of their transportation assets.
Supply chain visibility has been revolutionized by the adoption of IoT solutions in logistics. Real-time tracking, enhanced inventory management, condition monitoring, predictive maintenance, and data-driven decision-making are just a few examples of how IoT is transforming traditional supply chain processes. As businesses increasingly recognize the value of these technologies, the logistics industry is poised for continued advancements that will drive efficiency, reduce costs, and improve the resilience of supply chains in an ever-evolving global marketplace.
Smart Cities: IoT's Contribution to Urban Development
The advent of smart cities, driven by the integration of Internet of Things (IoT) technologies, marks a significant milestone in urban development. Smart cities leverage a network of connected devices, sensors, and data analytics to enhance the efficiency, sustainability, and overall quality of urban living. This transformative approach represents a response to the complex challenges faced by growing urban populations, ranging from traffic congestion and energy consumption to waste management and public safety.
IoT plays a pivotal role in enhancing public services and utilities within smart cities. Smart meters, for instance, allow for more accurate monitoring and management of water and energy consumption. This not only helps in conserving resources but also enables more precise billing and responsiveness to fluctuations in demand. Additionally, waste management systems benefit from IoT, with sensors placed in trash bins providing real-time data on fill levels. This information optimizes waste collection routes, reducing operational costs and promoting environmental sustainability.
The integration of IoT in smart cities is not without challenges, including data security and privacy concerns. As cities amass vast amounts of data from various sources, ensuring the protection of sensitive information becomes paramount. Robust cybersecurity measures and privacy regulations are crucial to building and maintaining public trust in the deployment of IoT technologies for urban development.
The contribution of IoT to smart cities is multifaceted, ushering in a new era of urban development characterized by efficiency, sustainability, and enhanced quality of life. By leveraging connected devices and data analytics, smart cities are better equipped to address the complexities of urban living, offering innovative solutions to challenges and paving the way for a more connected, resilient, and sustainable urban future.
How to obtain INTERNET OF THINGS certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, the integration of the Internet of Things (IoT) into various domains, such as manufacturing, healthcare, logistics, and urban development, has ushered in a transformative era of innovation and efficiency. These applications showcase the versatile impact of IoT technologies, highlighting their ability to enhance processes, optimize resource utilization, and improve overall quality of life.
Healthcare, IoT has paved the way for a new era of patient care and remote monitoring. Wearable devices, smart medical equipment, and health apps empower individuals to actively engage in their well-being, while healthcare professionals benefit from real-time data insights that enable more personalized and effective treatment plans.
Logistics has witnessed a significant transformation through supply chain visibility powered by IoT solutions. Real-time tracking, condition monitoring, and predictive maintenance have streamlined operations, reduced costs, and improved the reliability and efficiency of supply chain processes. This has implications not only for businesses but also for environmental sustainability through optimized resource usage.
Smart cities represent the convergence of IoT technologies in urban development, addressing challenges related to infrastructure, utilities, public services, and safety. The implementation of intelligent systems and connected devices allows cities to make data-driven decisions, creating more efficient, sustainable, and livable urban environments.
While the benefits of IoT applications are substantial, challenges such as data security and privacy must be addressed to ensure the responsible and ethical deployment of these technologies. As industries continue to embrace and adapt to the opportunities presented by IoT, ongoing research, collaboration, and regulatory frameworks will be essential to maximize the positive impact while mitigating potential risks.
The evolution of IoT continues to shape the way we live, work, and interact with the world around us. As technology advances and new possibilities emerge, the ongoing integration of IoT promises to drive further innovation, redefine industry standards, and contribute to a more connected, intelligent, and sustainable future.
COBIT® 5 Implementation Best Practices: Tips for Success
"COBIT® 5 Implementation Best Practices: Tips for Success" serves as a comprehensive guide for organizations looking to adopt and implement COBIT® 5, a globally recognized framework for enterprise IT governance. In the rapidly evolving landscape of information technology, effective governance is critical for ensuring that organizations achieve their strategic objectives while managing risks and optimizing resource utilization. This guide delves into the key principles and methodologies that underpin COBIT® 5, providing practical insights and best practices to facilitate a successful implementation process.
As organizations grapple with the complexities of IT governance, the COBIT® 5 framework emerges as a robust solution, offering a systematic approach to aligning business goals with IT processes. The guide not only introduces readers to the core concepts of COBIT® 5 but also provides actionable tips and strategies to overcome common challenges encountered during implementation. It emphasizes the importance of tailoring COBIT® 5 to the unique needs and context of each organization, ensuring a customized and effective application of the framework.
Readers will gain valuable insights into how COBIT® 5 can enhance overall business performance, drive innovation, and foster a culture of continuous improvement within their IT governance structures. With a focus on real-world scenarios and practical examples, the guide equips organizations with the knowledge and tools necessary to navigate the intricacies of COBIT® 5 implementation, promoting a seamless integration that maximizes benefits and minimizes disruptions. Whether an organization is embarking on its initial COBIT® 5 implementation or seeking to optimize existing processes, this guide serves as an invaluable resource for achieving success in the dynamic realmof IT governance.
Table of contents
-
Customization Strategies for COBIT® 5 Implementation
-
Overcoming Common Implementation Challenges
-
Effective Stakeholder Engagement in COBIT® 5 Implementation
-
Measuring and Monitoring Success Metrics
-
Integration of COBIT® 5 with Other IT Management Frameworks
-
Conclusion
Customization Strategies for COBIT® 5 Implementation
Customization is a pivotal aspect of successful COBIT® 5 implementation, recognizing that a one-size-fits-all approach may not align with the unique characteristics of every organization. This sub-topic delves into the strategies and considerations involved in tailoring COBIT® 5 to meet the specific needs and context of each organization. One essential element of customization is the acknowledgment of industry-specific requirements, understanding that different sectors may have distinct governance and compliance demands. This section will guide organizations in identifying these sector-specific nuances and adapting COBIT® 5 principles accordingly.
Additionally, organizational size plays a crucial role in customization strategies. Small and large enterprises may have different resource capabilities and structures, necessitating an adaptable approach to COBIT® 5 implementation. Practical tips will be provided on how organizations can scale and tailor the framework to suit their size, ensuring that it remains a practical and effective tool for governance in any organizational context.
Balancing adherence to COBIT® 5 principles with the flexibility to adapt to organizational goals is another critical consideration. This section will offer insights into finding the equilibrium between following the established framework and modifying it to address unique challenges or opportunities. Examples of successful customization efforts, drawn from diverse industries, will be explored to illustrate how organizations have effectively personalized COBIT® 5 to suit their specific needs without compromising its integrity.
Overcoming Common Implementation Challenges
The successful implementation of COBIT® 5 is not without its share of challenges, and this sub-topic addresses key obstacles that organizations commonly encounter during the implementation process. One prevalent challenge is the resistance to change, as employees may be accustomed to existing processes and may view the adoption of COBIT® 5 as disruptive. This section provides practical insights into fostering a positive attitude towards change, offering strategies to communicate the benefits of COBIT® 5 clearly and engage employees in the transition process.
Resource constraints represent another significant hurdle in COBIT® 5 implementation. Organizations often face limitations in terms of time, budget, and skilled personnel. Here, the discussion focuses on innovative approaches to maximize resources efficiently, such as prioritizing critical areas of implementation, leveraging existing skill sets, and exploring partnerships or collaborations. Real-world examples of organizations successfully navigating resource challenges during COBIT® 5 implementation will be explored to inspire effective strategies.
By addressing these common challenges head-on, organizations can better prepare for the hurdles associated with COBIT® 5 implementation. Practical tips, case studies, and lessons learned from organizations that have successfully navigated these challenges will provide valuable insights, offering a roadmap for others to overcome obstacles and ensure a smoother implementation journey for COBIT® 5.
Effective Stakeholder Engagement in COBIT® 5 Implementation
Effective stakeholder engagement is a critical element in the successful implementation of COBIT® 5, recognizing the importance of garnering support from key individuals and groups throughout the process. This sub-topic explores strategies for engaging stakeholders at various levels within the organization, starting with top-level executives. It emphasizes the need for executive buy-in, as their support is instrumental in providing the necessary resources and leadership to drive COBIT® 5 implementation. The discussion delves into effective communication strategies to convey the value proposition of COBIT® 5 to executives, aligning the framework with overarching business goals.
Moving beyond executives, this section also addresses the involvement of IT teams and other relevant stakeholders. It explores the creation of targeted training programs to enhance stakeholder understanding of COBIT® 5 principles and their role in the implementation journey. The importance of establishing clear lines of communication, feedback mechanisms, and collaborative decision-making processes is highlighted to foster a sense of ownership and commitment among stakeholders.
It discusses how effective stakeholder engagement can contribute to shaping a positive organizational culture that embraces the principles of COBIT® 5. Real-world examples of successful stakeholder engagement initiatives will be provided to illustrate how organizations have effectively mobilized support and collaboration across various levels, ensuring a collective effort towards COBIT® 5 implementation.
Measuring and Monitoring Success Metrics
Measuring and monitoring success metrics constitute a fundamental component of a robust COBIT® 5 implementation, serving as the compass to navigate the effectiveness and impact of the framework on an organization's IT governance. This sub-topic underscores the significance of methodically selecting key performance indicators (KPIs) that align with the organization's strategic objectives. By establishing clear, measurable goals, organizations can evaluate the tangible outcomes of COBIT® 5 implementation, ensuring a tangible link between IT governance practices and overarching business goals.
Continuous monitoring is pivotal in maintaining the health and efficacy of COBIT® 5 processes. This section advocates for a proactive and systematic approach to tracking performance, leveraging automated tools and reporting mechanisms to gather real-time data. Through diligent monitoring, organizations can identify deviations from expected outcomes, address potential issues promptly, and fine-tune processes to align with the evolving needs of the organization. Practical insights into setting up a robust monitoring framework within the COBIT® 5 context will be provided, drawing on successful examples of organizations that have effectively utilized monitoring mechanisms.
As organizational priorities shift, technological landscapes evolve, and industry standards change, the measurement framework should be flexible enough to accommodate these fluctuations. Organizations will gain insights into strategies for adjusting success metrics, ensuring their continued relevance in assessing the impact of COBIT® 5 on the IT governance landscape.
By implementing a comprehensive system for performance evaluation and remaining agile in adapting metrics, organizations can not only gauge the success of COBIT® 5 but also lay the groundwork for continuous improvement and strategic alignment with evolving business objectives.
Integration of COBIT® 5 with Other IT Management Frameworks
The integration of COBIT® 5 with other IT management frameworks represents a strategic approach to creating a cohesive and comprehensive governance structure within organizations. This sub-topic delves into the synergy between COBIT® 5 and other frameworks, such as ITIL (Information Technology Infrastructure Library) or ISO/IEC 27001. It acknowledges that organizations often leverage multiple frameworks to address various aspects of IT management and governance, and explores how COBIT® 5 can seamlessly complement and enhance existing practices.
The discussion highlights the importance of identifying areas of alignment and potential overlaps between COBIT® 5 and other frameworks. By recognizing the synergies, organizations can avoid duplication of efforts and create a unified governance framework that optimally addresses their unique needs. This involves a nuanced understanding of the strengths and focus areas of each framework, allowing for a harmonious integration that leverages the best aspects of each.
Practical guidance is provided on how organizations can navigate the integration process, emphasizing the need for collaboration among stakeholders involved in different frameworks. This collaboration ensures that integration efforts are well-coordinated, fostering a shared understanding of objectives and methodologies across the organization. Real-world examples will illustrate successful instances of organizations integrating COBIT® 5 with other frameworks, showcasing the positive outcomes and enhanced efficiency resulting from this holistic approach.
The integration of COBIT® 5 with other IT management frameworks is presented as a strategic imperative for organizations aiming to build a robust and harmonized governance ecosystem. Through careful consideration, collaboration, and a nuanced approach to integration, organizations can harness the collective strengths of multiple frameworks to achieve a more comprehensive and effective IT governance strategy.
How to obtain COBIT 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "COBIT® 5 Implementation Best Practices: Tips for Success" encapsulates a comprehensive guide for organizations navigating the intricacies of adopting and implementing the COBIT® 5 framework for IT governance. The exploration of customization strategies underscores the importance of tailoring COBIT® 5 to suit the unique needs and context of each organization, providing practical insights into industry-specific requirements and organizational size considerations. Recognizing and addressing common implementation challenges, from resistance to change to resource constraints, empowers organizations to navigate these hurdles effectively, drawing inspiration from real-world examples of successful implementations.
The sub-topic on effective stakeholder engagement establishes a crucial aspect of COBIT® 5 implementation by emphasizing the need for buy-in from top executives and active involvement of IT teams. Through clear communication, targeted training, and a collaborative approach, organizations can foster a positive organizational culture that aligns with COBIT® 5 principles. Measuring and monitoring success metrics form the backbone of the implementation journey, guiding organizations in selecting relevant KPIs, leveraging automation, and embracing adaptability to ensure continuous improvement and alignment with evolving business objectives.
Finally, the exploration of the integration of COBIT® 5 with other IT management frameworks highlights the strategic advantage of creating a unified governance structure. By identifying synergies and avoiding duplication, organizations can harness the strengths of multiple frameworks, resulting in improved risk management, streamlined processes, and enhanced overall IT governance.
Collectively, the insights provided in this guide empower organizations with the knowledge, strategies, and practical tips needed to navigate the multifaceted landscape of COBIT® 5 implementation. As organizations embark on this journey, the guide serves as a valuable resource, offering a roadmap for success and fostering a culture of continuous improvement within the realm of IT governance.
Read More
"COBIT® 5 Implementation Best Practices: Tips for Success" serves as a comprehensive guide for organizations looking to adopt and implement COBIT® 5, a globally recognized framework for enterprise IT governance. In the rapidly evolving landscape of information technology, effective governance is critical for ensuring that organizations achieve their strategic objectives while managing risks and optimizing resource utilization. This guide delves into the key principles and methodologies that underpin COBIT® 5, providing practical insights and best practices to facilitate a successful implementation process.
As organizations grapple with the complexities of IT governance, the COBIT® 5 framework emerges as a robust solution, offering a systematic approach to aligning business goals with IT processes. The guide not only introduces readers to the core concepts of COBIT® 5 but also provides actionable tips and strategies to overcome common challenges encountered during implementation. It emphasizes the importance of tailoring COBIT® 5 to the unique needs and context of each organization, ensuring a customized and effective application of the framework.
Readers will gain valuable insights into how COBIT® 5 can enhance overall business performance, drive innovation, and foster a culture of continuous improvement within their IT governance structures. With a focus on real-world scenarios and practical examples, the guide equips organizations with the knowledge and tools necessary to navigate the intricacies of COBIT® 5 implementation, promoting a seamless integration that maximizes benefits and minimizes disruptions. Whether an organization is embarking on its initial COBIT® 5 implementation or seeking to optimize existing processes, this guide serves as an invaluable resource for achieving success in the dynamic realmof IT governance.
Table of contents
-
Customization Strategies for COBIT® 5 Implementation
-
Overcoming Common Implementation Challenges
-
Effective Stakeholder Engagement in COBIT® 5 Implementation
-
Measuring and Monitoring Success Metrics
-
Integration of COBIT® 5 with Other IT Management Frameworks
-
Conclusion
Customization Strategies for COBIT® 5 Implementation
Customization is a pivotal aspect of successful COBIT® 5 implementation, recognizing that a one-size-fits-all approach may not align with the unique characteristics of every organization. This sub-topic delves into the strategies and considerations involved in tailoring COBIT® 5 to meet the specific needs and context of each organization. One essential element of customization is the acknowledgment of industry-specific requirements, understanding that different sectors may have distinct governance and compliance demands. This section will guide organizations in identifying these sector-specific nuances and adapting COBIT® 5 principles accordingly.
Additionally, organizational size plays a crucial role in customization strategies. Small and large enterprises may have different resource capabilities and structures, necessitating an adaptable approach to COBIT® 5 implementation. Practical tips will be provided on how organizations can scale and tailor the framework to suit their size, ensuring that it remains a practical and effective tool for governance in any organizational context.
Balancing adherence to COBIT® 5 principles with the flexibility to adapt to organizational goals is another critical consideration. This section will offer insights into finding the equilibrium between following the established framework and modifying it to address unique challenges or opportunities. Examples of successful customization efforts, drawn from diverse industries, will be explored to illustrate how organizations have effectively personalized COBIT® 5 to suit their specific needs without compromising its integrity.
Overcoming Common Implementation Challenges
The successful implementation of COBIT® 5 is not without its share of challenges, and this sub-topic addresses key obstacles that organizations commonly encounter during the implementation process. One prevalent challenge is the resistance to change, as employees may be accustomed to existing processes and may view the adoption of COBIT® 5 as disruptive. This section provides practical insights into fostering a positive attitude towards change, offering strategies to communicate the benefits of COBIT® 5 clearly and engage employees in the transition process.
Resource constraints represent another significant hurdle in COBIT® 5 implementation. Organizations often face limitations in terms of time, budget, and skilled personnel. Here, the discussion focuses on innovative approaches to maximize resources efficiently, such as prioritizing critical areas of implementation, leveraging existing skill sets, and exploring partnerships or collaborations. Real-world examples of organizations successfully navigating resource challenges during COBIT® 5 implementation will be explored to inspire effective strategies.
By addressing these common challenges head-on, organizations can better prepare for the hurdles associated with COBIT® 5 implementation. Practical tips, case studies, and lessons learned from organizations that have successfully navigated these challenges will provide valuable insights, offering a roadmap for others to overcome obstacles and ensure a smoother implementation journey for COBIT® 5.
Effective Stakeholder Engagement in COBIT® 5 Implementation
Effective stakeholder engagement is a critical element in the successful implementation of COBIT® 5, recognizing the importance of garnering support from key individuals and groups throughout the process. This sub-topic explores strategies for engaging stakeholders at various levels within the organization, starting with top-level executives. It emphasizes the need for executive buy-in, as their support is instrumental in providing the necessary resources and leadership to drive COBIT® 5 implementation. The discussion delves into effective communication strategies to convey the value proposition of COBIT® 5 to executives, aligning the framework with overarching business goals.
Moving beyond executives, this section also addresses the involvement of IT teams and other relevant stakeholders. It explores the creation of targeted training programs to enhance stakeholder understanding of COBIT® 5 principles and their role in the implementation journey. The importance of establishing clear lines of communication, feedback mechanisms, and collaborative decision-making processes is highlighted to foster a sense of ownership and commitment among stakeholders.
It discusses how effective stakeholder engagement can contribute to shaping a positive organizational culture that embraces the principles of COBIT® 5. Real-world examples of successful stakeholder engagement initiatives will be provided to illustrate how organizations have effectively mobilized support and collaboration across various levels, ensuring a collective effort towards COBIT® 5 implementation.
Measuring and Monitoring Success Metrics
Measuring and monitoring success metrics constitute a fundamental component of a robust COBIT® 5 implementation, serving as the compass to navigate the effectiveness and impact of the framework on an organization's IT governance. This sub-topic underscores the significance of methodically selecting key performance indicators (KPIs) that align with the organization's strategic objectives. By establishing clear, measurable goals, organizations can evaluate the tangible outcomes of COBIT® 5 implementation, ensuring a tangible link between IT governance practices and overarching business goals.
Continuous monitoring is pivotal in maintaining the health and efficacy of COBIT® 5 processes. This section advocates for a proactive and systematic approach to tracking performance, leveraging automated tools and reporting mechanisms to gather real-time data. Through diligent monitoring, organizations can identify deviations from expected outcomes, address potential issues promptly, and fine-tune processes to align with the evolving needs of the organization. Practical insights into setting up a robust monitoring framework within the COBIT® 5 context will be provided, drawing on successful examples of organizations that have effectively utilized monitoring mechanisms.
As organizational priorities shift, technological landscapes evolve, and industry standards change, the measurement framework should be flexible enough to accommodate these fluctuations. Organizations will gain insights into strategies for adjusting success metrics, ensuring their continued relevance in assessing the impact of COBIT® 5 on the IT governance landscape.
By implementing a comprehensive system for performance evaluation and remaining agile in adapting metrics, organizations can not only gauge the success of COBIT® 5 but also lay the groundwork for continuous improvement and strategic alignment with evolving business objectives.
Integration of COBIT® 5 with Other IT Management Frameworks
The integration of COBIT® 5 with other IT management frameworks represents a strategic approach to creating a cohesive and comprehensive governance structure within organizations. This sub-topic delves into the synergy between COBIT® 5 and other frameworks, such as ITIL (Information Technology Infrastructure Library) or ISO/IEC 27001. It acknowledges that organizations often leverage multiple frameworks to address various aspects of IT management and governance, and explores how COBIT® 5 can seamlessly complement and enhance existing practices.
The discussion highlights the importance of identifying areas of alignment and potential overlaps between COBIT® 5 and other frameworks. By recognizing the synergies, organizations can avoid duplication of efforts and create a unified governance framework that optimally addresses their unique needs. This involves a nuanced understanding of the strengths and focus areas of each framework, allowing for a harmonious integration that leverages the best aspects of each.
Practical guidance is provided on how organizations can navigate the integration process, emphasizing the need for collaboration among stakeholders involved in different frameworks. This collaboration ensures that integration efforts are well-coordinated, fostering a shared understanding of objectives and methodologies across the organization. Real-world examples will illustrate successful instances of organizations integrating COBIT® 5 with other frameworks, showcasing the positive outcomes and enhanced efficiency resulting from this holistic approach.
The integration of COBIT® 5 with other IT management frameworks is presented as a strategic imperative for organizations aiming to build a robust and harmonized governance ecosystem. Through careful consideration, collaboration, and a nuanced approach to integration, organizations can harness the collective strengths of multiple frameworks to achieve a more comprehensive and effective IT governance strategy.
How to obtain COBIT 5 Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "COBIT® 5 Implementation Best Practices: Tips for Success" encapsulates a comprehensive guide for organizations navigating the intricacies of adopting and implementing the COBIT® 5 framework for IT governance. The exploration of customization strategies underscores the importance of tailoring COBIT® 5 to suit the unique needs and context of each organization, providing practical insights into industry-specific requirements and organizational size considerations. Recognizing and addressing common implementation challenges, from resistance to change to resource constraints, empowers organizations to navigate these hurdles effectively, drawing inspiration from real-world examples of successful implementations.
The sub-topic on effective stakeholder engagement establishes a crucial aspect of COBIT® 5 implementation by emphasizing the need for buy-in from top executives and active involvement of IT teams. Through clear communication, targeted training, and a collaborative approach, organizations can foster a positive organizational culture that aligns with COBIT® 5 principles. Measuring and monitoring success metrics form the backbone of the implementation journey, guiding organizations in selecting relevant KPIs, leveraging automation, and embracing adaptability to ensure continuous improvement and alignment with evolving business objectives.
Finally, the exploration of the integration of COBIT® 5 with other IT management frameworks highlights the strategic advantage of creating a unified governance structure. By identifying synergies and avoiding duplication, organizations can harness the strengths of multiple frameworks, resulting in improved risk management, streamlined processes, and enhanced overall IT governance.
Collectively, the insights provided in this guide empower organizations with the knowledge, strategies, and practical tips needed to navigate the multifaceted landscape of COBIT® 5 implementation. As organizations embark on this journey, the guide serves as a valuable resource, offering a roadmap for success and fostering a culture of continuous improvement within the realm of IT governance.
The Impact of Privacy Changes on Digital Marketing Strategies
In an era dominated by digital advancements and rapidly evolving technology, the landscape of digital marketing is continually shaped by various factors. One of the most influential and dynamic aspects currently affecting the digital marketing realm is the ongoing transformation in privacy policies and practices. As individuals become more conscientious about their online privacy, governments and technology companies are responding with heightened regulations and updates to safeguard personal information. These privacy changes, often implemented through legislation or platform updates, have profound implications for businesses and marketers who rely on digital channels to reach their target audiences.
The evolving privacy landscape is marked by significant shifts in consumer attitudes, regulatory frameworks, and technological innovations. With increasing awareness and concerns regarding data security, individuals are becoming more cautious about sharing their personal information online. Governments worldwide are responding to these concerns by introducing and updating privacy laws, such as the General Data Protection Regulation (GDPR) in Europe and similar initiatives in other regions. These regulations impose stricter requirements on how businesses collect, process, and store user data, forcing marketers to adapt their strategies to ensure compliance while still effectively reaching their audiences.
Moreover, major tech platforms are also playing a pivotal role in shaping the privacy narrative. Companies like Apple and Google have implemented changes to their operating systems and browser functionalities, emphasizing user privacy and giving individuals more control over their data. These alterations, while commendable in terms of user empowerment, pose challenges for digital marketers who heavily rely on targeted advertising and personalized campaigns. As tracking capabilities diminish and the collection of certain user data becomes more restricted, marketers must rethink their approaches to maintain the effectiveness of their digital marketing strategies.
In this complex and rapidly changing landscape, businesses find themselves at a crossroads, navigating the delicate balance between delivering personalized, targeted content and respecting user privacy. The impact of privacy changes on digital marketing strategies is multi-faceted, influencing not only how data is collected and utilized but also challenging marketers to explore innovative approaches that prioritize transparency, consent, and ethical practices. This evolving scenario prompts a critical examination of the strategies employed by businesses, encouraging them to adapt to the changing dynamics of digital marketing while upholding the principles of privacy and user trust.
Table of contents
-
Adaptation to Cookie-Free Environments
-
User-Centric Data Governance
-
Impact on Social Media Advertising
-
Emergence of Privacy-Focused Marketing Tools
-
Legal and Reputational Risks
-
Conclusion
Adaptation to Cookie-Free Environments
The transition towards a cookie-free environment represents a seismic shift in the digital marketing landscape, challenging businesses to reevaluate their strategies in the absence of traditional tracking mechanisms. With increasing privacy concerns and browser updates restricting the use of third-party cookies, marketers are compelled to adapt to a new era of data-driven advertising. The reliance on cookies for user tracking, retargeting, and personalized advertising is diminishing, necessitating innovative approaches to maintain effective audience targeting and campaign performance.
In response to the diminishing role of cookies, marketers are exploring alternative tracking methods that align with privacy regulations and user expectations. First-party data utilization has emerged as a key strategy, leveraging the direct information collected from users who willingly engage with a brand's platforms. This approach not only respects user privacy preferences but also enables businesses to create more personalized experiences based on the data voluntarily shared by their audience.
As digital marketers navigate the challenges of adapting to cookie-free environments, a fundamental rethinking of advertising strategies is underway. The emphasis on transparent data practices, user consent, and ethical data governance is not only a response to regulatory requirements but also a recognition of the growing demand for privacy-conscious digital experiences. In this evolving landscape, businesses that successfully navigate the transition to cookie-free environments stand to build stronger relationships with their audiences while ensuring compliance with the changing norms of digital privacy.
User-Centric Data Governance
The paradigm shift towards user-centric data governance is reshaping the landscape of digital marketing, placing the control and privacy of user data at the forefront. In response to heightened concerns over data security and privacy breaches, businesses are undergoing a fundamental transformation in their approach to data management. This shift emphasizes the empowerment of users in controlling their personal information and dictates a new set of standards for ethical and transparent data practices.
Central to user-centric data governance is the explicit and informed consent of individuals regarding the collection, processing, and utilization of their data. As privacy regulations become more stringent, businesses are reevaluating their data acquisition strategies to ensure compliance with these standards. This involves implementing robust consent mechanisms that clearly communicate the purpose of data collection and provide users with the ability to opt-in or opt-out of specific data processing activities.
The transition to user-centric data governance reflects a broader societal shift towards recognizing the importance of individual privacy rights. By placing users at the center of the data governance framework, businesses are not only ensuring compliance with evolving regulations but also fostering a culture of respect for user privacy, thus building a foundation for sustainable and trust-based digital interactions.
Impact on Social Media Advertising
The landscape of social media advertising is undergoing a profound transformation in response to the impactful changes in privacy policies and user preferences. Social media platforms, serving as vital hubs for digital marketing, are adapting to new privacy-centric paradigms that seek to strike a balance between targeted advertising and safeguarding user information. The evolving privacy landscape is compelling marketers to reevaluate their strategies as major platforms implement updates aimed at providing users with more control over their data.
The impact on social media advertising extends beyond targeting capabilities to the measurement and analysis of campaign effectiveness. As the availability of granular user data diminishes, businesses are exploring alternative methods for assessing the performance of their social media campaigns. Key performance indicators (KPIs) are being adjusted, and analytics tools are evolving to accommodate these changes, emphasizing the importance of engagement metrics and user interactions over traditional tracking metrics.
The impact of privacy changes on social media advertising necessitates a paradigm shift in how marketers approach audience engagement. The focus on user consent, transparency, and the exploration of alternative targeting methods is shaping a more privacy-conscious era for social media advertising. As marketers navigate this evolving landscape, they are compelled to strike a delicate balance between delivering effective campaigns and respecting the privacy expectations of their target audiences.
Emergence of Privacy-Focused Marketing Tools
The emergence of privacy-focused marketing tools is a direct response to the evolving landscape of digital marketing, where privacy considerations have taken center stage. As businesses navigate the complexities of data protection regulations and changing user expectations, a new generation of tools is evolving to help marketers maintain the effectiveness of their campaigns while prioritizing user privacy. These tools aim to strike a balance between data-driven insights and ethical, transparent practices.
One significant development in this space is the rise of privacy-focused analytics platforms. These tools are designed to provide marketers with valuable insights into user behavior without compromising individual privacy. By employing techniques such as aggregated data analysis and anonymized tracking, these platforms enable businesses to gather meaningful information about audience engagement while respecting user confidentiality and adhering to privacy regulations.
Consent management tools represent another pivotal aspect of the privacy-focused marketing toolkit. With regulations like GDPR emphasizing the importance of explicit user consent, these tools streamline the process of obtaining and managing user permissions for data processing. They empower businesses to implement clear and user-friendly consent mechanisms, fostering a more transparent and accountable approach to data collection.
The emergence of privacy-focused marketing tools signifies a conscientious shift within the industry towards ethical data practices and user-centricity. These tools empower marketers to navigate the challenges posed by evolving privacy regulations, enabling them to create targeted, effective campaigns without compromising the privacy and trust of their audiences. As businesses increasingly prioritize transparency and user consent, the adoption of privacy-focused marketing tools is becoming integral to maintaining a sustainable and responsible approach to digital marketing.
Legal and Reputational Risks
The evolving landscape of digital marketing in the context of privacy changes brings forth not only opportunities but also a set of profound legal and reputational risks that businesses must navigate with diligence. As governments worldwide enact stringent privacy regulations, non-compliance can expose companies to significant legal consequences. Privacy breaches, unauthorized data usage, or failure to adhere to regulatory standards may result in hefty fines, legal actions, and damaged reputations. In this scenario, staying abreast of and ensuring compliance with evolving privacy laws has become a paramount concern for businesses engaged in digital marketing.
Beyond the legal realm, the reputational risks associated with privacy lapses are equally formidable. In an era where consumer trust is a precious commodity, a single instance of mishandling personal data can lead to a severe erosion of brand credibility. Instances of data breaches or unethical data practices can quickly become public relations nightmares, causing lasting damage to a company's reputation and eroding the trust that consumers place in their chosen brands. Consequently, businesses operating in the digital sphere are compelled to prioritize stringent data protection measures to safeguard not only legal standing but also the trust and confidence of their customer base.
The potential legal and reputational risks amplify the importance of implementing robust data protection strategies and transparent communication. Businesses are investing in comprehensive privacy policies that not only adhere to legal standards but are also easily accessible and comprehensible for users. Clear articulation of data handling practices and a commitment to user privacy not only aids in compliance but also serves as a proactive measure to mitigate potential legal and reputational pitfalls.
How to obtain DIGITAL MARKETING Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the impact of privacy changes on digital marketing strategies is reshaping the landscape in profound ways, ushering in a new era where user privacy takes center stage. The evolving regulatory frameworks, technological shifts, and changing consumer attitudes have necessitated a fundamental reevaluation of how businesses approach digital marketing. As third-party cookies face restrictions and data tracking becomes more limited, marketers are challenged to adapt their strategies to maintain effectiveness while respecting user privacy preferences.
The emergence of privacy-focused marketing tools reflects a commitment to ethical data practices and transparent communication. From analytics platforms that prioritize user confidentiality to consent management tools that empower users with control over their data, businesses are navigating the complexities of a digital environment that demands privacy-conscious approaches. The shift towards user-centric data governance, overseen by data protection officers, underscores the importance of obtaining explicit user consent and fostering a culture of responsible data management.
Social media advertising, a cornerstone of digital marketing, is undergoing a transformation as platforms implement updates to provide users with more control over their data. Marketers are adjusting their strategies to align with these changes, focusing on contextual targeting and exploring innovative advertising formats that prioritize user privacy.
In this evolving digital marketing landscape, the convergence of legal, technological, and consumer-driven changes demands a holistic approach. By embracing privacy-focused tools, adhering to user-centric data governance, and proactively addressing legal and reputational risks, businesses can not only navigate the challenges but also position themselves as trustworthy stewards of user data. As the digital marketing realm continues to evolve, those who prioritize user privacy and ethical data practices will likely thrive in building lasting connections with their audiences.
Read More
In an era dominated by digital advancements and rapidly evolving technology, the landscape of digital marketing is continually shaped by various factors. One of the most influential and dynamic aspects currently affecting the digital marketing realm is the ongoing transformation in privacy policies and practices. As individuals become more conscientious about their online privacy, governments and technology companies are responding with heightened regulations and updates to safeguard personal information. These privacy changes, often implemented through legislation or platform updates, have profound implications for businesses and marketers who rely on digital channels to reach their target audiences.
The evolving privacy landscape is marked by significant shifts in consumer attitudes, regulatory frameworks, and technological innovations. With increasing awareness and concerns regarding data security, individuals are becoming more cautious about sharing their personal information online. Governments worldwide are responding to these concerns by introducing and updating privacy laws, such as the General Data Protection Regulation (GDPR) in Europe and similar initiatives in other regions. These regulations impose stricter requirements on how businesses collect, process, and store user data, forcing marketers to adapt their strategies to ensure compliance while still effectively reaching their audiences.
Moreover, major tech platforms are also playing a pivotal role in shaping the privacy narrative. Companies like Apple and Google have implemented changes to their operating systems and browser functionalities, emphasizing user privacy and giving individuals more control over their data. These alterations, while commendable in terms of user empowerment, pose challenges for digital marketers who heavily rely on targeted advertising and personalized campaigns. As tracking capabilities diminish and the collection of certain user data becomes more restricted, marketers must rethink their approaches to maintain the effectiveness of their digital marketing strategies.
In this complex and rapidly changing landscape, businesses find themselves at a crossroads, navigating the delicate balance between delivering personalized, targeted content and respecting user privacy. The impact of privacy changes on digital marketing strategies is multi-faceted, influencing not only how data is collected and utilized but also challenging marketers to explore innovative approaches that prioritize transparency, consent, and ethical practices. This evolving scenario prompts a critical examination of the strategies employed by businesses, encouraging them to adapt to the changing dynamics of digital marketing while upholding the principles of privacy and user trust.
Table of contents
-
Adaptation to Cookie-Free Environments
-
User-Centric Data Governance
-
Impact on Social Media Advertising
-
Emergence of Privacy-Focused Marketing Tools
-
Legal and Reputational Risks
-
Conclusion
Adaptation to Cookie-Free Environments
The transition towards a cookie-free environment represents a seismic shift in the digital marketing landscape, challenging businesses to reevaluate their strategies in the absence of traditional tracking mechanisms. With increasing privacy concerns and browser updates restricting the use of third-party cookies, marketers are compelled to adapt to a new era of data-driven advertising. The reliance on cookies for user tracking, retargeting, and personalized advertising is diminishing, necessitating innovative approaches to maintain effective audience targeting and campaign performance.
In response to the diminishing role of cookies, marketers are exploring alternative tracking methods that align with privacy regulations and user expectations. First-party data utilization has emerged as a key strategy, leveraging the direct information collected from users who willingly engage with a brand's platforms. This approach not only respects user privacy preferences but also enables businesses to create more personalized experiences based on the data voluntarily shared by their audience.
As digital marketers navigate the challenges of adapting to cookie-free environments, a fundamental rethinking of advertising strategies is underway. The emphasis on transparent data practices, user consent, and ethical data governance is not only a response to regulatory requirements but also a recognition of the growing demand for privacy-conscious digital experiences. In this evolving landscape, businesses that successfully navigate the transition to cookie-free environments stand to build stronger relationships with their audiences while ensuring compliance with the changing norms of digital privacy.
User-Centric Data Governance
The paradigm shift towards user-centric data governance is reshaping the landscape of digital marketing, placing the control and privacy of user data at the forefront. In response to heightened concerns over data security and privacy breaches, businesses are undergoing a fundamental transformation in their approach to data management. This shift emphasizes the empowerment of users in controlling their personal information and dictates a new set of standards for ethical and transparent data practices.
Central to user-centric data governance is the explicit and informed consent of individuals regarding the collection, processing, and utilization of their data. As privacy regulations become more stringent, businesses are reevaluating their data acquisition strategies to ensure compliance with these standards. This involves implementing robust consent mechanisms that clearly communicate the purpose of data collection and provide users with the ability to opt-in or opt-out of specific data processing activities.
The transition to user-centric data governance reflects a broader societal shift towards recognizing the importance of individual privacy rights. By placing users at the center of the data governance framework, businesses are not only ensuring compliance with evolving regulations but also fostering a culture of respect for user privacy, thus building a foundation for sustainable and trust-based digital interactions.
Impact on Social Media Advertising
The landscape of social media advertising is undergoing a profound transformation in response to the impactful changes in privacy policies and user preferences. Social media platforms, serving as vital hubs for digital marketing, are adapting to new privacy-centric paradigms that seek to strike a balance between targeted advertising and safeguarding user information. The evolving privacy landscape is compelling marketers to reevaluate their strategies as major platforms implement updates aimed at providing users with more control over their data.
The impact on social media advertising extends beyond targeting capabilities to the measurement and analysis of campaign effectiveness. As the availability of granular user data diminishes, businesses are exploring alternative methods for assessing the performance of their social media campaigns. Key performance indicators (KPIs) are being adjusted, and analytics tools are evolving to accommodate these changes, emphasizing the importance of engagement metrics and user interactions over traditional tracking metrics.
The impact of privacy changes on social media advertising necessitates a paradigm shift in how marketers approach audience engagement. The focus on user consent, transparency, and the exploration of alternative targeting methods is shaping a more privacy-conscious era for social media advertising. As marketers navigate this evolving landscape, they are compelled to strike a delicate balance between delivering effective campaigns and respecting the privacy expectations of their target audiences.
Emergence of Privacy-Focused Marketing Tools
The emergence of privacy-focused marketing tools is a direct response to the evolving landscape of digital marketing, where privacy considerations have taken center stage. As businesses navigate the complexities of data protection regulations and changing user expectations, a new generation of tools is evolving to help marketers maintain the effectiveness of their campaigns while prioritizing user privacy. These tools aim to strike a balance between data-driven insights and ethical, transparent practices.
One significant development in this space is the rise of privacy-focused analytics platforms. These tools are designed to provide marketers with valuable insights into user behavior without compromising individual privacy. By employing techniques such as aggregated data analysis and anonymized tracking, these platforms enable businesses to gather meaningful information about audience engagement while respecting user confidentiality and adhering to privacy regulations.
Consent management tools represent another pivotal aspect of the privacy-focused marketing toolkit. With regulations like GDPR emphasizing the importance of explicit user consent, these tools streamline the process of obtaining and managing user permissions for data processing. They empower businesses to implement clear and user-friendly consent mechanisms, fostering a more transparent and accountable approach to data collection.
The emergence of privacy-focused marketing tools signifies a conscientious shift within the industry towards ethical data practices and user-centricity. These tools empower marketers to navigate the challenges posed by evolving privacy regulations, enabling them to create targeted, effective campaigns without compromising the privacy and trust of their audiences. As businesses increasingly prioritize transparency and user consent, the adoption of privacy-focused marketing tools is becoming integral to maintaining a sustainable and responsible approach to digital marketing.
Legal and Reputational Risks
The evolving landscape of digital marketing in the context of privacy changes brings forth not only opportunities but also a set of profound legal and reputational risks that businesses must navigate with diligence. As governments worldwide enact stringent privacy regulations, non-compliance can expose companies to significant legal consequences. Privacy breaches, unauthorized data usage, or failure to adhere to regulatory standards may result in hefty fines, legal actions, and damaged reputations. In this scenario, staying abreast of and ensuring compliance with evolving privacy laws has become a paramount concern for businesses engaged in digital marketing.
Beyond the legal realm, the reputational risks associated with privacy lapses are equally formidable. In an era where consumer trust is a precious commodity, a single instance of mishandling personal data can lead to a severe erosion of brand credibility. Instances of data breaches or unethical data practices can quickly become public relations nightmares, causing lasting damage to a company's reputation and eroding the trust that consumers place in their chosen brands. Consequently, businesses operating in the digital sphere are compelled to prioritize stringent data protection measures to safeguard not only legal standing but also the trust and confidence of their customer base.
The potential legal and reputational risks amplify the importance of implementing robust data protection strategies and transparent communication. Businesses are investing in comprehensive privacy policies that not only adhere to legal standards but are also easily accessible and comprehensible for users. Clear articulation of data handling practices and a commitment to user privacy not only aids in compliance but also serves as a proactive measure to mitigate potential legal and reputational pitfalls.
How to obtain DIGITAL MARKETING Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the impact of privacy changes on digital marketing strategies is reshaping the landscape in profound ways, ushering in a new era where user privacy takes center stage. The evolving regulatory frameworks, technological shifts, and changing consumer attitudes have necessitated a fundamental reevaluation of how businesses approach digital marketing. As third-party cookies face restrictions and data tracking becomes more limited, marketers are challenged to adapt their strategies to maintain effectiveness while respecting user privacy preferences.
The emergence of privacy-focused marketing tools reflects a commitment to ethical data practices and transparent communication. From analytics platforms that prioritize user confidentiality to consent management tools that empower users with control over their data, businesses are navigating the complexities of a digital environment that demands privacy-conscious approaches. The shift towards user-centric data governance, overseen by data protection officers, underscores the importance of obtaining explicit user consent and fostering a culture of responsible data management.
Social media advertising, a cornerstone of digital marketing, is undergoing a transformation as platforms implement updates to provide users with more control over their data. Marketers are adjusting their strategies to align with these changes, focusing on contextual targeting and exploring innovative advertising formats that prioritize user privacy.
In this evolving digital marketing landscape, the convergence of legal, technological, and consumer-driven changes demands a holistic approach. By embracing privacy-focused tools, adhering to user-centric data governance, and proactively addressing legal and reputational risks, businesses can not only navigate the challenges but also position themselves as trustworthy stewards of user data. As the digital marketing realm continues to evolve, those who prioritize user privacy and ethical data practices will likely thrive in building lasting connections with their audiences.
demystifying the ecba certification process
Embarking on the journey to become a certified Entry Certificate in Business Analysis (ECBA) professional can be a daunting task for many aspiring business analysts. As organizations increasingly recognize the value of skilled individuals in driving business success through effective analysis, the ECBA certification has emerged as a pivotal credential in the field. This step-by-step guide aims to demystify the ECBA certification process, providing a comprehensive roadmap for individuals seeking to navigate the intricacies of the certification journey.
The ECBA certification, offered by the International Institute of Business Analysis (IIBA), serves as a foundational credential for those entering the field of business analysis. This guide will break down the entire process into manageable steps, offering clarity on the eligibility criteria, application procedure, and the essential knowledge areas covered in the ECBA exam. By unraveling the complexities surrounding the certification, this guide aims to empower aspiring business analysts with the information and confidence needed to embark on this transformative professional journey.
Whether you are a recent graduate aspiring to enter the field or a seasoned professional looking to formalize your business analysis skills, understanding the ECBA certification process is crucial. From outlining the prerequisites and recommended study resources to providing tips for exam preparation, this guide will equip you with the insights necessary to navigate the certification process with ease. Join us as we unravel the layers of the ECBA certification, helping you embark on a path of professional growth and success in the dynamic field of business analysis.
Table of contents
-
Understanding ECBA Eligibility Requirements
-
Navigating the ECBA Application Process
-
Mastering the ECBA Exam Structure and Content
-
Effective Study Strategies and Resources
-
Tips for a Successful ECBA Exam Day
-
Conclusion
Understanding ECBA Eligibility Requirements
Embarking on the journey towards ECBA certification begins with a clear understanding of the eligibility requirements set by the International Institute of Business Analysis (IIBA). Aspiring candidates need to grasp the foundational criteria that form the basis for qualification. Generally, the ECBA certification is designed for individuals who are at the early stages of their business analysis careers, making it accessible to a broad range of professionals.
The eligibility criteria typically revolve around educational qualifications and work experience. Candidates are required to have a minimum of a high school diploma or equivalent, ensuring that the certification is accessible to individuals at various stages of their academic journey. Additionally, candidates should possess a certain amount of work experience in business analysis-related tasks, providing a practical foundation for those seeking to earn the ECBA credential. Understanding these criteria is crucial for prospective candidates to evaluate their readiness for the certification process.
Furthermore, the ECBA eligibility requirements may include professional development hours, reflecting the IIBA's commitment to fostering continuous learning and growth within the business analysis community. Candidates are often required to complete a specified number of professional development hours in areas related to business analysis before applying for the certification. This requirement emphasizes the importance of staying updated on industry best practices and emerging trends, contributing to the professional development of ECBA candidates.
Clear comprehension of the ECBA eligibility requirements sets the stage for a successful certification journey. Prospective candidates should thoroughly review these criteria to determine their eligibility, and if necessary, take proactive steps to meet the educational and experiential prerequisites. This foundational understanding is a crucial first step in demystifying the ECBA certification process, providing a solid foundation for those seeking to enhance their careers in business analysis.
Navigating the ECBA Application Process
Once aspiring candidates have a solid understanding of the eligibility requirements, the next pivotal step in the journey towards ECBA certification is navigating the application process. This phase demands meticulous attention to detail and adherence to the guidelines set by the International Institute of Business Analysis (IIBA). The ECBA application process is designed to ensure that candidates meet the necessary criteria and are well-prepared to take on the challenges of the certification.
The first key aspect of the application process involves the submission of relevant documentation. Candidates are typically required to provide evidence of their educational qualifications, such as transcripts or certificates, validating that they meet the minimum educational requirements. Additionally, documentation of work experience in business analysis-related tasks is essential, emphasizing the practical application of skills in a professional setting. Prospective ECBA candidates should gather and organize these documents to streamline the application process.
Timeliness is of the essence throughout the application process. Candidates should be aware of application deadlines and aim to submit their materials well in advance. Procrastination can lead to unnecessary stress and potentially jeopardize the opportunity to take the ECBA exam within the desired timeframe. A proactive approach to the application process is, therefore, fundamental for success.
In summary, navigating the ECBA application process requires a methodical approach and attention to detail. By understanding the documentation requirements, adhering to application deadlines, and ensuring timely payment, candidates can navigate this phase with confidence. This subtopic serves as a guide for prospective ECBA professionals, assisting them in managing the intricacies of the application process as they progress towards achieving their certification goals.
Mastering the ECBA Exam Structure and Content
A crucial aspect of the ECBA certification journey is gaining a comprehensive understanding of the exam structure and content. The International Institute of Business Analysis (IIBA) has meticulously designed the ECBA exam to assess candidates' knowledge and proficiency in various business analysis domains. Familiarity with the exam structure is fundamental for effective preparation.
The ECBA exam typically consists of multiple-choice questions that evaluate candidates across different knowledge areas. Understanding these knowledge areas is paramount, as they cover essential aspects of business analysis, such as business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, and strategy analysis. By delving into the specifics of each knowledge area, candidates can tailor their study plans to focus on areas where they may need additional preparation.
Mastering the ECBA exam structure and content is an integral part of exam preparation. By comprehending the knowledge areas, understanding the exam format, and practicing effective time management, candidates can approach the exam with confidence, increasing their likelihood of success in obtaining the ECBA certification. This subtopic serves as a guide to empower candidates with the insights necessary to navigate the intricacies of the ECBA exam.
Effective Study Strategies and Resources
Embarking on the journey to attain the Entry Certificate in Business Analysis (ECBA) certification demands not only dedication but also a well-structured and effective study plan. This subtopic explores key strategies and resources to optimize study sessions, ensuring candidates are well-prepared for the challenges presented by the ECBA exam.
Firstly, candidates should create a personalized study plan tailored to their learning preferences and schedules. Breaking down the vast body of knowledge into manageable sections and allocating specific time slots for study sessions helps maintain focus and consistency. Consideration of personal strengths and areas needing improvement allows for a balanced and targeted approach to exam preparation.
Utilizing a variety of study resources is essential for a well-rounded understanding of the ECBA exam content. Official IIBA materials, including the BABOK Guide (Business Analysis Body of Knowledge), are foundational resources that align directly with the exam content. Supplementing these with textbooks, online courses, and practice exams from reputable sources provides a broader perspective and reinforces key concepts.
Interactive study methods, such as group discussions and study groups, can enhance comprehension by allowing candidates to share insights and clarify doubts. Engaging with peers or mentors who have already earned their ECBA certification can offer valuable perspectives and advice. Online forums and communities dedicated to business analysis certification can serve as platforms for exchanging ideas and seeking support.
Effective study strategies and resources encompass a holistic approach that combines careful planning, diverse learning materials, interactive engagement, and the incorporation of practice exams. By adopting these strategies, candidates can navigate the complexities of the ECBA certification process with confidence, equipping themselves for success in the challenging field of business analysis.
Tips for a Successful ECBA Exam Day
As the culmination of diligent preparation, the ECBA exam day is a pivotal moment in the certification journey. Implementing a set of well-thought-out strategies can help candidates approach the day with confidence and enhance their chances of success.
First and foremost, arriving at the exam center well-rested and mentally prepared is crucial. Adequate sleep in the days leading up to the exam and a healthy breakfast on the morning of the test contribute to optimal cognitive function and concentration. Managing stress through relaxation techniques, such as deep breathing or meditation, can also promote a focused and composed mindset.
Familiarizing oneself with the logistics of the exam day is equally important. Knowing the location of the test center, understanding check-in procedures, and being aware of any specific requirements or restrictions are essential for a smooth start to the day. Arriving early allows for unexpected delays and helps alleviate any last-minute stressors.
During the exam, effective time management is paramount. Candidates should allocate time wisely, aiming to answer each question within the allotted timeframe. It's advisable not to dwell on challenging questions excessively; instead, marking them for review and moving forward ensures that all questions receive attention, maximizing the opportunity for earning points.
Tips for a successful ECBA exam day encompass physical and mental preparation, logistical awareness, effective time management, and maintaining a positive mindset. By implementing these strategies, candidates can navigate the exam with composure and increase their likelihood of achieving a favorable outcome, marking the successful completion of their ECBA certification journey.
How to obtain ECBA CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, demystifying the ECBA certification process is an essential endeavor for aspiring business analysts seeking to elevate their professional standing. This step-by-step guide has provided valuable insights into the various facets of the ECBA certification journey. From understanding eligibility requirements to navigating the application process, mastering the exam structure and content, adopting effective study strategies, and embracing tips for a successful exam day, this guide serves as a comprehensive roadmap.
The ECBA certification, offered by the International Institute of Business Analysis (IIBA), holds immense value in today's competitive business landscape. It not only validates the foundational skills of entry-level business analysts but also opens doors to career advancement and opportunities for professional growth. Aspiring ECBA candidates are encouraged to approach the certification process with a proactive mindset, leveraging the knowledge and strategies shared in this guide.
As candidates embark on this transformative journey, they are encouraged to view the ECBA certification not just as a credential but as a stepping stone toward becoming adept contributors to organizational success. Through dedication, preparation, and a strategic approach, individuals can confidently navigate the ECBA certification process and emerge as certified business analysts ready to make a meaningful impact in the ever-evolving world of business analysis.
Read More
Embarking on the journey to become a certified Entry Certificate in Business Analysis (ECBA) professional can be a daunting task for many aspiring business analysts. As organizations increasingly recognize the value of skilled individuals in driving business success through effective analysis, the ECBA certification has emerged as a pivotal credential in the field. This step-by-step guide aims to demystify the ECBA certification process, providing a comprehensive roadmap for individuals seeking to navigate the intricacies of the certification journey.
The ECBA certification, offered by the International Institute of Business Analysis (IIBA), serves as a foundational credential for those entering the field of business analysis. This guide will break down the entire process into manageable steps, offering clarity on the eligibility criteria, application procedure, and the essential knowledge areas covered in the ECBA exam. By unraveling the complexities surrounding the certification, this guide aims to empower aspiring business analysts with the information and confidence needed to embark on this transformative professional journey.
Whether you are a recent graduate aspiring to enter the field or a seasoned professional looking to formalize your business analysis skills, understanding the ECBA certification process is crucial. From outlining the prerequisites and recommended study resources to providing tips for exam preparation, this guide will equip you with the insights necessary to navigate the certification process with ease. Join us as we unravel the layers of the ECBA certification, helping you embark on a path of professional growth and success in the dynamic field of business analysis.
Table of contents
-
Understanding ECBA Eligibility Requirements
-
Navigating the ECBA Application Process
-
Mastering the ECBA Exam Structure and Content
-
Effective Study Strategies and Resources
-
Tips for a Successful ECBA Exam Day
-
Conclusion
Understanding ECBA Eligibility Requirements
Embarking on the journey towards ECBA certification begins with a clear understanding of the eligibility requirements set by the International Institute of Business Analysis (IIBA). Aspiring candidates need to grasp the foundational criteria that form the basis for qualification. Generally, the ECBA certification is designed for individuals who are at the early stages of their business analysis careers, making it accessible to a broad range of professionals.
The eligibility criteria typically revolve around educational qualifications and work experience. Candidates are required to have a minimum of a high school diploma or equivalent, ensuring that the certification is accessible to individuals at various stages of their academic journey. Additionally, candidates should possess a certain amount of work experience in business analysis-related tasks, providing a practical foundation for those seeking to earn the ECBA credential. Understanding these criteria is crucial for prospective candidates to evaluate their readiness for the certification process.
Furthermore, the ECBA eligibility requirements may include professional development hours, reflecting the IIBA's commitment to fostering continuous learning and growth within the business analysis community. Candidates are often required to complete a specified number of professional development hours in areas related to business analysis before applying for the certification. This requirement emphasizes the importance of staying updated on industry best practices and emerging trends, contributing to the professional development of ECBA candidates.
Clear comprehension of the ECBA eligibility requirements sets the stage for a successful certification journey. Prospective candidates should thoroughly review these criteria to determine their eligibility, and if necessary, take proactive steps to meet the educational and experiential prerequisites. This foundational understanding is a crucial first step in demystifying the ECBA certification process, providing a solid foundation for those seeking to enhance their careers in business analysis.
Navigating the ECBA Application Process
Once aspiring candidates have a solid understanding of the eligibility requirements, the next pivotal step in the journey towards ECBA certification is navigating the application process. This phase demands meticulous attention to detail and adherence to the guidelines set by the International Institute of Business Analysis (IIBA). The ECBA application process is designed to ensure that candidates meet the necessary criteria and are well-prepared to take on the challenges of the certification.
The first key aspect of the application process involves the submission of relevant documentation. Candidates are typically required to provide evidence of their educational qualifications, such as transcripts or certificates, validating that they meet the minimum educational requirements. Additionally, documentation of work experience in business analysis-related tasks is essential, emphasizing the practical application of skills in a professional setting. Prospective ECBA candidates should gather and organize these documents to streamline the application process.
Timeliness is of the essence throughout the application process. Candidates should be aware of application deadlines and aim to submit their materials well in advance. Procrastination can lead to unnecessary stress and potentially jeopardize the opportunity to take the ECBA exam within the desired timeframe. A proactive approach to the application process is, therefore, fundamental for success.
In summary, navigating the ECBA application process requires a methodical approach and attention to detail. By understanding the documentation requirements, adhering to application deadlines, and ensuring timely payment, candidates can navigate this phase with confidence. This subtopic serves as a guide for prospective ECBA professionals, assisting them in managing the intricacies of the application process as they progress towards achieving their certification goals.
Mastering the ECBA Exam Structure and Content
A crucial aspect of the ECBA certification journey is gaining a comprehensive understanding of the exam structure and content. The International Institute of Business Analysis (IIBA) has meticulously designed the ECBA exam to assess candidates' knowledge and proficiency in various business analysis domains. Familiarity with the exam structure is fundamental for effective preparation.
The ECBA exam typically consists of multiple-choice questions that evaluate candidates across different knowledge areas. Understanding these knowledge areas is paramount, as they cover essential aspects of business analysis, such as business analysis planning and monitoring, elicitation and collaboration, requirements life cycle management, and strategy analysis. By delving into the specifics of each knowledge area, candidates can tailor their study plans to focus on areas where they may need additional preparation.
Mastering the ECBA exam structure and content is an integral part of exam preparation. By comprehending the knowledge areas, understanding the exam format, and practicing effective time management, candidates can approach the exam with confidence, increasing their likelihood of success in obtaining the ECBA certification. This subtopic serves as a guide to empower candidates with the insights necessary to navigate the intricacies of the ECBA exam.
Effective Study Strategies and Resources
Embarking on the journey to attain the Entry Certificate in Business Analysis (ECBA) certification demands not only dedication but also a well-structured and effective study plan. This subtopic explores key strategies and resources to optimize study sessions, ensuring candidates are well-prepared for the challenges presented by the ECBA exam.
Firstly, candidates should create a personalized study plan tailored to their learning preferences and schedules. Breaking down the vast body of knowledge into manageable sections and allocating specific time slots for study sessions helps maintain focus and consistency. Consideration of personal strengths and areas needing improvement allows for a balanced and targeted approach to exam preparation.
Utilizing a variety of study resources is essential for a well-rounded understanding of the ECBA exam content. Official IIBA materials, including the BABOK Guide (Business Analysis Body of Knowledge), are foundational resources that align directly with the exam content. Supplementing these with textbooks, online courses, and practice exams from reputable sources provides a broader perspective and reinforces key concepts.
Interactive study methods, such as group discussions and study groups, can enhance comprehension by allowing candidates to share insights and clarify doubts. Engaging with peers or mentors who have already earned their ECBA certification can offer valuable perspectives and advice. Online forums and communities dedicated to business analysis certification can serve as platforms for exchanging ideas and seeking support.
Effective study strategies and resources encompass a holistic approach that combines careful planning, diverse learning materials, interactive engagement, and the incorporation of practice exams. By adopting these strategies, candidates can navigate the complexities of the ECBA certification process with confidence, equipping themselves for success in the challenging field of business analysis.
Tips for a Successful ECBA Exam Day
As the culmination of diligent preparation, the ECBA exam day is a pivotal moment in the certification journey. Implementing a set of well-thought-out strategies can help candidates approach the day with confidence and enhance their chances of success.
First and foremost, arriving at the exam center well-rested and mentally prepared is crucial. Adequate sleep in the days leading up to the exam and a healthy breakfast on the morning of the test contribute to optimal cognitive function and concentration. Managing stress through relaxation techniques, such as deep breathing or meditation, can also promote a focused and composed mindset.
Familiarizing oneself with the logistics of the exam day is equally important. Knowing the location of the test center, understanding check-in procedures, and being aware of any specific requirements or restrictions are essential for a smooth start to the day. Arriving early allows for unexpected delays and helps alleviate any last-minute stressors.
During the exam, effective time management is paramount. Candidates should allocate time wisely, aiming to answer each question within the allotted timeframe. It's advisable not to dwell on challenging questions excessively; instead, marking them for review and moving forward ensures that all questions receive attention, maximizing the opportunity for earning points.
Tips for a successful ECBA exam day encompass physical and mental preparation, logistical awareness, effective time management, and maintaining a positive mindset. By implementing these strategies, candidates can navigate the exam with composure and increase their likelihood of achieving a favorable outcome, marking the successful completion of their ECBA certification journey.
How to obtain ECBA CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, demystifying the ECBA certification process is an essential endeavor for aspiring business analysts seeking to elevate their professional standing. This step-by-step guide has provided valuable insights into the various facets of the ECBA certification journey. From understanding eligibility requirements to navigating the application process, mastering the exam structure and content, adopting effective study strategies, and embracing tips for a successful exam day, this guide serves as a comprehensive roadmap.
The ECBA certification, offered by the International Institute of Business Analysis (IIBA), holds immense value in today's competitive business landscape. It not only validates the foundational skills of entry-level business analysts but also opens doors to career advancement and opportunities for professional growth. Aspiring ECBA candidates are encouraged to approach the certification process with a proactive mindset, leveraging the knowledge and strategies shared in this guide.
As candidates embark on this transformative journey, they are encouraged to view the ECBA certification not just as a credential but as a stepping stone toward becoming adept contributors to organizational success. Through dedication, preparation, and a strategic approach, individuals can confidently navigate the ECBA certification process and emerge as certified business analysts ready to make a meaningful impact in the ever-evolving world of business analysis.
The Importance of RPA Certification in Todays Job Market
In today's rapidly evolving job market, staying ahead of the curve and acquiring relevant skills has become imperative for professionals across various industries. The rise of automation and technological advancements has led to a significant demand for individuals proficient in Robotic Process Automation (RPA). As organizations increasingly adopt RPA to streamline and enhance their business processes, the need for certified professionals in this field has grown exponentially. RPA Certification has emerged as a critical validation of an individual's expertise in deploying automation solutions, making it a key factor in securing and advancing one's career in the contemporary job landscape.
RPA, a technology that utilizes software robots or "bots" to perform repetitive tasks, has proven to be a game-changer in improving operational efficiency and reducing manual errors. With its widespread adoption, employers seek professionals who not only understand the theoretical aspects of RPA but also possess hands-on experience and a recognized certification. The significance of RPA Certification extends beyond showcasing technical proficiency; it serves as a tangible proof of an individual's commitment to staying current in their field and adapting to the evolving demands of the digital age.
As businesses continue to prioritize cost-effectiveness and productivity, RPA Certification has become a distinguishing factor for job seekers and a prerequisite for those aspiring to climb the corporate ladder. This article delves into the various facets of RPA Certification, exploring its relevance in today's job market and shedding light on the tangible benefits it brings to both professionals and the organizations they serve. From gaining a competitive edge in job applications to contributing to organizational success, the importance of RPA Certification cannot be overstated in a world where automation is reshaping the dynamics of the workplace.
Table of contents
-
Emergence of Robotic Process Automation (RPA) in Modern Business
-
Strategic Career Planning in the Age of Automation
-
RPA Certification Programs and Industry Recognition
-
Addressing the Skills Gap
-
Economic Impact and Return on Investment (ROI) for Individuals
-
Conclusion
Emergence of Robotic Process Automation (RPA) in Modern Business
In the ever-evolving landscape of modern business, the adoption of cutting-edge technologies is imperative for staying competitive and maximizing operational efficiency. One such technological paradigm that has rapidly gained prominence is Robotic Process Automation (RPA). Defined by the deployment of software robots to automate repetitive and rule-based tasks, RPA represents a transformative force reshaping the way organizations conduct their day-to-day operations. This introduction sets the stage for an exploration into the profound implications of the emergence of RPA in modern business and underscores its pivotal role in driving efficiency, reducing costs, and revolutionizing traditional workflows.
The advent of RPA marks a significant departure from conventional business processes, offering a scalable and flexible solution to the challenges posed by repetitive manual tasks. As businesses increasingly recognize the potential of RPA to enhance productivity and accuracy while minimizing human intervention, the technology has become a cornerstone of digital transformation strategies across diverse industries. This paradigm shift not only underscores the adaptability of organizations but also underscores the need for a skilled workforce capable of harnessing the full potential of RPA solutions. In this context, understanding the emergence of RPA becomes crucial for professionals seeking to navigate the evolving landscape of modern business and for businesses aiming to harness the advantages of automation in a dynamic and competitive market.
Strategic Career Planning in the Age of Automation
In the contemporary landscape shaped by rapid technological advancements, strategic career planning has become more imperative than ever, particularly in the age of automation. The increasing integration of automation technologies, such as Robotic Process Automation (RPA), is transforming the nature of work across industries. As routine tasks are automated to enhance efficiency, professionals are compelled to reevaluate their skill sets and strategically position themselves in the workforce. Strategic career planning in the age of automation involves a proactive approach to skill acquisition, with a keen focus on fields that not only align with current industry trends but also hold promise for the future.
RPA, with its ability to streamline repetitive tasks and improve operational efficiency, has become a focal point in the strategic career plans of individuals aiming to thrive in the age of automation. The technology offers professionals an opportunity to specialize in roles that involve designing, implementing, and managing automated processes, thereby positioning themselves as valuable assets in their respective industries. Additionally, strategic career planning entails continuous learning and adaptability to stay ahead of the curve in an environment where the skills demanded by the job market are subject to frequent evolution.
Strategic career planning in the age of automation requires a forward-thinking mindset, a commitment to skill development in areas resistant to automation, and an understanding of emerging technologies like RPA. Professionals who strategically align their skill sets with the demands of an automated workplace are not only better positioned for success in their current roles but also equipped to navigate the dynamic landscape of future employment opportunities.
RPA Certification Programs and Industry Recognition
The increasing prevalence of Robotic Process Automation (RPA) in modern business has underscored the importance of staying abreast of evolving technologies through specialized training. RPA Certification programs have emerged as pivotal instruments for individuals seeking to validate their expertise in deploying automation solutions. These programs not only impart essential theoretical knowledge but also provide hands-on experience, ensuring that certified professionals are well-equipped to navigate the intricacies of RPA implementation. As a testament to the industry's acknowledgment of the significance of RPA Certification, a myriad of well-recognized certification programs has gained prominence, garnering respect and credibility among employers across various sectors.
Prominent RPA Certification programs, such as those offered by industry leaders and recognized institutions, play a crucial role in standardizing skill sets and establishing a benchmark for proficiency in the field. These programs typically cover a range of topics, including RPA tools and platforms, process automation best practices, and real-world application scenarios. The comprehensive nature of these certifications ensures that individuals not only grasp the theoretical underpinnings of RPA but also develop the practical skills necessary for successful implementation.
Industry recognition of RPA Certification holds considerable weight in the hiring and promotion processes. Employers are increasingly prioritizing candidates who possess validated expertise in RPA, as certified professionals are perceived as having a proven track record of competence and commitment to staying current in their field. In a competitive job market, holding an RPA Certification serves as a tangible differentiator, setting certified individuals apart and signaling to employers that they bring a valuable skill set to the table.
RPA Certification programs and the industry recognition they garner are integral components in the professional development of individuals and the strategic planning of organizations. As RPA continues to reshape the business landscape, the acknowledgment of certified professionals underscores the critical role they play in driving successful automation initiatives and contributing to the overall efficiency and competitiveness of the modern workplace.
Addressing the Skills Gap
In the era of rapid technological advancement, the pervasive integration of automation technologies like Robotic Process Automation (RPA) has unveiled a pressing challenge in the form of a skills gap. This gap arises from the growing disparity between the skills demanded by the job market and the existing skill sets of the workforce. Addressing the skills gap in the context of RPA involves a strategic and collaborative effort from educational institutions, employers, and individuals alike to ensure that the workforce is adequately equipped to harness the full potential of this transformative technology.
Employers, too, play a pivotal role in addressing the skills gap by investing in training programs and fostering a culture of continuous learning within their organizations. Recognizing that the success of RPA initiatives is contingent on the expertise of their workforce, companies are increasingly supporting employees in obtaining RPA certifications and staying abreast of emerging trends in automation. By actively addressing the skills gap, employers not only enhance the capabilities of their teams but also position themselves as industry leaders capable of leveraging the full potential of RPA for operational excellence.
Addressing the skills gap in the context of RPA requires a collaborative effort from educational institutions, employers, and individuals. By aligning educational curricula with industry demands, fostering a culture of continuous learning within organizations, and adopting a proactive stance toward skill development, stakeholders can collectively contribute to closing the skills gap and ensuring a workforce that is well-prepared to navigate the transformative landscape of RPA and automation technologies.
Economic Impact and Return on Investment (ROI) for Individuals
The decision to pursue Robotic Process Automation (RPA) certification is not merely an investment in professional development; it is a strategic move with profound economic implications for individuals. In the contemporary job market, where technological skills are increasingly valued, RPA certification stands out as a catalyst for economic advancement. The economic impact is evident in the heightened demand for individuals possessing RPA expertise, translating into a myriad of tangible benefits, including improved career prospects and increased earning potential.
Certification in RPA often yields a considerable return on investment (ROI) for individuals in the form of enhanced income opportunities. Employers, recognizing the specialized knowledge and practical skills acquired through certification, are willing to remunerate certified professionals at a premium. The ability to contribute to the design and implementation of automation solutions positions individuals as key contributors to organizational success, justifying higher salaries and more lucrative compensation packages.
The economic impact and ROI of RPA certification for individuals are multi-faceted, encompassing increased earning potential, job security, long-term career growth, and broader contributions to economic productivity. In a job market increasingly shaped by technological advancements, the decision to invest in RPA certification emerges as a strategic and lucrative pathway for individuals seeking to navigate and thrive in an evolving professional landscape.
How to obtain RPA (ROBOTIC PROCESS AUTOMATION) CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the economic impact and return on investment (ROI) associated with Robotic Process Automation (RPA) certification underscore its pivotal role in shaping the professional landscape of individuals in today's dynamic job market. The decision to pursue RPA certification extends beyond skill acquisition; it represents a strategic investment that yields tangible benefits, enhancing career prospects, and contributing to long-term economic stability.
RPA-certified professionals find themselves well-positioned to capitalize on the burgeoning demand for automation expertise. The certification not only commands higher salaries but also acts as a shield against industry disruptions, ensuring job security in the face of technological advancements. The ability to actively contribute to automation initiatives positions individuals as indispensable assets within their organizations, fostering not only personal growth but also elevating their standing in the broader professional community.
In essence, RPA certification serves as a strategic enabler for individuals navigating the complexities of the modern job market. Its economic impact is manifested in enhanced earning potential, job security, and a trajectory of long-term career growth. As industries continue to embrace automation, the value of RPA certification becomes increasingly pronounced, positioning certified professionals not only as beneficiaries of economic rewards but as integral contributors to the transformative journey of organizations in an era defined by technological innovation. As professionals strategically invest in RPA certification, they are not only future-proofing their careers but also actively shaping the economic landscape of the industries they serve.
Read More
In today's rapidly evolving job market, staying ahead of the curve and acquiring relevant skills has become imperative for professionals across various industries. The rise of automation and technological advancements has led to a significant demand for individuals proficient in Robotic Process Automation (RPA). As organizations increasingly adopt RPA to streamline and enhance their business processes, the need for certified professionals in this field has grown exponentially. RPA Certification has emerged as a critical validation of an individual's expertise in deploying automation solutions, making it a key factor in securing and advancing one's career in the contemporary job landscape.
RPA, a technology that utilizes software robots or "bots" to perform repetitive tasks, has proven to be a game-changer in improving operational efficiency and reducing manual errors. With its widespread adoption, employers seek professionals who not only understand the theoretical aspects of RPA but also possess hands-on experience and a recognized certification. The significance of RPA Certification extends beyond showcasing technical proficiency; it serves as a tangible proof of an individual's commitment to staying current in their field and adapting to the evolving demands of the digital age.
As businesses continue to prioritize cost-effectiveness and productivity, RPA Certification has become a distinguishing factor for job seekers and a prerequisite for those aspiring to climb the corporate ladder. This article delves into the various facets of RPA Certification, exploring its relevance in today's job market and shedding light on the tangible benefits it brings to both professionals and the organizations they serve. From gaining a competitive edge in job applications to contributing to organizational success, the importance of RPA Certification cannot be overstated in a world where automation is reshaping the dynamics of the workplace.
Table of contents
-
Emergence of Robotic Process Automation (RPA) in Modern Business
-
Strategic Career Planning in the Age of Automation
-
RPA Certification Programs and Industry Recognition
-
Addressing the Skills Gap
-
Economic Impact and Return on Investment (ROI) for Individuals
-
Conclusion
Emergence of Robotic Process Automation (RPA) in Modern Business
In the ever-evolving landscape of modern business, the adoption of cutting-edge technologies is imperative for staying competitive and maximizing operational efficiency. One such technological paradigm that has rapidly gained prominence is Robotic Process Automation (RPA). Defined by the deployment of software robots to automate repetitive and rule-based tasks, RPA represents a transformative force reshaping the way organizations conduct their day-to-day operations. This introduction sets the stage for an exploration into the profound implications of the emergence of RPA in modern business and underscores its pivotal role in driving efficiency, reducing costs, and revolutionizing traditional workflows.
The advent of RPA marks a significant departure from conventional business processes, offering a scalable and flexible solution to the challenges posed by repetitive manual tasks. As businesses increasingly recognize the potential of RPA to enhance productivity and accuracy while minimizing human intervention, the technology has become a cornerstone of digital transformation strategies across diverse industries. This paradigm shift not only underscores the adaptability of organizations but also underscores the need for a skilled workforce capable of harnessing the full potential of RPA solutions. In this context, understanding the emergence of RPA becomes crucial for professionals seeking to navigate the evolving landscape of modern business and for businesses aiming to harness the advantages of automation in a dynamic and competitive market.
Strategic Career Planning in the Age of Automation
In the contemporary landscape shaped by rapid technological advancements, strategic career planning has become more imperative than ever, particularly in the age of automation. The increasing integration of automation technologies, such as Robotic Process Automation (RPA), is transforming the nature of work across industries. As routine tasks are automated to enhance efficiency, professionals are compelled to reevaluate their skill sets and strategically position themselves in the workforce. Strategic career planning in the age of automation involves a proactive approach to skill acquisition, with a keen focus on fields that not only align with current industry trends but also hold promise for the future.
RPA, with its ability to streamline repetitive tasks and improve operational efficiency, has become a focal point in the strategic career plans of individuals aiming to thrive in the age of automation. The technology offers professionals an opportunity to specialize in roles that involve designing, implementing, and managing automated processes, thereby positioning themselves as valuable assets in their respective industries. Additionally, strategic career planning entails continuous learning and adaptability to stay ahead of the curve in an environment where the skills demanded by the job market are subject to frequent evolution.
Strategic career planning in the age of automation requires a forward-thinking mindset, a commitment to skill development in areas resistant to automation, and an understanding of emerging technologies like RPA. Professionals who strategically align their skill sets with the demands of an automated workplace are not only better positioned for success in their current roles but also equipped to navigate the dynamic landscape of future employment opportunities.
RPA Certification Programs and Industry Recognition
The increasing prevalence of Robotic Process Automation (RPA) in modern business has underscored the importance of staying abreast of evolving technologies through specialized training. RPA Certification programs have emerged as pivotal instruments for individuals seeking to validate their expertise in deploying automation solutions. These programs not only impart essential theoretical knowledge but also provide hands-on experience, ensuring that certified professionals are well-equipped to navigate the intricacies of RPA implementation. As a testament to the industry's acknowledgment of the significance of RPA Certification, a myriad of well-recognized certification programs has gained prominence, garnering respect and credibility among employers across various sectors.
Prominent RPA Certification programs, such as those offered by industry leaders and recognized institutions, play a crucial role in standardizing skill sets and establishing a benchmark for proficiency in the field. These programs typically cover a range of topics, including RPA tools and platforms, process automation best practices, and real-world application scenarios. The comprehensive nature of these certifications ensures that individuals not only grasp the theoretical underpinnings of RPA but also develop the practical skills necessary for successful implementation.
Industry recognition of RPA Certification holds considerable weight in the hiring and promotion processes. Employers are increasingly prioritizing candidates who possess validated expertise in RPA, as certified professionals are perceived as having a proven track record of competence and commitment to staying current in their field. In a competitive job market, holding an RPA Certification serves as a tangible differentiator, setting certified individuals apart and signaling to employers that they bring a valuable skill set to the table.
RPA Certification programs and the industry recognition they garner are integral components in the professional development of individuals and the strategic planning of organizations. As RPA continues to reshape the business landscape, the acknowledgment of certified professionals underscores the critical role they play in driving successful automation initiatives and contributing to the overall efficiency and competitiveness of the modern workplace.
Addressing the Skills Gap
In the era of rapid technological advancement, the pervasive integration of automation technologies like Robotic Process Automation (RPA) has unveiled a pressing challenge in the form of a skills gap. This gap arises from the growing disparity between the skills demanded by the job market and the existing skill sets of the workforce. Addressing the skills gap in the context of RPA involves a strategic and collaborative effort from educational institutions, employers, and individuals alike to ensure that the workforce is adequately equipped to harness the full potential of this transformative technology.
Employers, too, play a pivotal role in addressing the skills gap by investing in training programs and fostering a culture of continuous learning within their organizations. Recognizing that the success of RPA initiatives is contingent on the expertise of their workforce, companies are increasingly supporting employees in obtaining RPA certifications and staying abreast of emerging trends in automation. By actively addressing the skills gap, employers not only enhance the capabilities of their teams but also position themselves as industry leaders capable of leveraging the full potential of RPA for operational excellence.
Addressing the skills gap in the context of RPA requires a collaborative effort from educational institutions, employers, and individuals. By aligning educational curricula with industry demands, fostering a culture of continuous learning within organizations, and adopting a proactive stance toward skill development, stakeholders can collectively contribute to closing the skills gap and ensuring a workforce that is well-prepared to navigate the transformative landscape of RPA and automation technologies.
Economic Impact and Return on Investment (ROI) for Individuals
The decision to pursue Robotic Process Automation (RPA) certification is not merely an investment in professional development; it is a strategic move with profound economic implications for individuals. In the contemporary job market, where technological skills are increasingly valued, RPA certification stands out as a catalyst for economic advancement. The economic impact is evident in the heightened demand for individuals possessing RPA expertise, translating into a myriad of tangible benefits, including improved career prospects and increased earning potential.
Certification in RPA often yields a considerable return on investment (ROI) for individuals in the form of enhanced income opportunities. Employers, recognizing the specialized knowledge and practical skills acquired through certification, are willing to remunerate certified professionals at a premium. The ability to contribute to the design and implementation of automation solutions positions individuals as key contributors to organizational success, justifying higher salaries and more lucrative compensation packages.
The economic impact and ROI of RPA certification for individuals are multi-faceted, encompassing increased earning potential, job security, long-term career growth, and broader contributions to economic productivity. In a job market increasingly shaped by technological advancements, the decision to invest in RPA certification emerges as a strategic and lucrative pathway for individuals seeking to navigate and thrive in an evolving professional landscape.
How to obtain RPA (ROBOTIC PROCESS AUTOMATION) CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the economic impact and return on investment (ROI) associated with Robotic Process Automation (RPA) certification underscore its pivotal role in shaping the professional landscape of individuals in today's dynamic job market. The decision to pursue RPA certification extends beyond skill acquisition; it represents a strategic investment that yields tangible benefits, enhancing career prospects, and contributing to long-term economic stability.
RPA-certified professionals find themselves well-positioned to capitalize on the burgeoning demand for automation expertise. The certification not only commands higher salaries but also acts as a shield against industry disruptions, ensuring job security in the face of technological advancements. The ability to actively contribute to automation initiatives positions individuals as indispensable assets within their organizations, fostering not only personal growth but also elevating their standing in the broader professional community.
In essence, RPA certification serves as a strategic enabler for individuals navigating the complexities of the modern job market. Its economic impact is manifested in enhanced earning potential, job security, and a trajectory of long-term career growth. As industries continue to embrace automation, the value of RPA certification becomes increasingly pronounced, positioning certified professionals not only as beneficiaries of economic rewards but as integral contributors to the transformative journey of organizations in an era defined by technological innovation. As professionals strategically invest in RPA certification, they are not only future-proofing their careers but also actively shaping the economic landscape of the industries they serve.
The Role of Data Science in Fraud Detection and Prevention
The pervasive growth of digital transactions and the increasing reliance on technology in various sectors have led to a parallel rise in fraudulent activities, making the role of data science in fraud detection and prevention more crucial than ever. In this era of information overload, organizations are inundated with vast amounts of data, providing both an opportunity and a challenge in the fight against fraud.
Data science, with its advanced analytics and machine learning techniques, has emerged as a powerful tool to sift through this sea of information, identifying patterns, anomalies, and potential indicators of fraudulent behavior. This interdisciplinary field amalgamates statistics, computer science, and domain expertise to develop sophisticated models that can recognize and predict fraudulent activities with high accuracy.
As fraudsters continually evolve their tactics, the adaptive nature of data science allows for the continuous refinement of detection models, ensuring organizations stay one step ahead in the ongoing battle against financial and cyber threats. This paper delves into the multifaceted role of data science in fraud detection and prevention, exploring its methodologies, challenges, and real-world applications across diverse industries.
Table of contents
-
Algorithmic Approaches in Fraud Detection
-
Real-Time Fraud Monitoring
-
Challenges and Ethical Considerations in Data-Driven Fraud Prevention
-
Integration of Big Data in Fraud Detection
-
Case Studies and Industry Applications
-
Conclusion
Algorithmic Approaches in Fraud Detection
In the intricate landscape of fraud detection, Algorithmic Approaches play a pivotal role in harnessing the power of data science to identify and mitigate fraudulent activities effectively. Leveraging a diverse array of machine learning algorithms and statistical models, organizations can analyze vast datasets to discern subtle patterns indicative of fraudulent behavior.
Anomalies, outliers, and deviations from expected norms are systematically detected through these algorithms, allowing for the swift identification of potential fraud risks. Supervised learning models, such as logistic regression and decision trees, are commonly employed to classify transactions as either legitimate or suspicious based on historical data. Meanwhile, unsupervised learning techniques, including clustering and outlier detection, enable the identification of novel fraud patterns without predefined labels.
The adaptive nature of these algorithms allows for continuous learning and refinement, ensuring that fraud detection systems remain resilient against evolving tactics employed by fraudsters. Furthermore, advancements in deep learning, including neural networks, contribute to the development of more intricate models capable of capturing complex relationships within data, further enhancing the accuracy and efficiency of fraud detection processes. Algorithmic approaches, therefore, form the bedrock of data science in the ongoing battle against fraudulent activities, providing organizations with the analytical prowess needed to safeguard their operations in an increasingly digital and interconnected world.
Real-Time Fraud Monitoring
In the fast-paced landscape of financial transactions and digital interactions, Real-Time Fraud Monitoring has emerged as a critical component in the arsenal of fraud detection and prevention strategies. Data science plays a pivotal role in enabling organizations to monitor transactions and activities in real-time, providing a dynamic defense against evolving fraud tactics. The essence of real-time monitoring lies in the ability to swiftly analyze and assess incoming data streams to identify anomalies and patterns associated with fraudulent behavior. This proactive approach allows organizations to respond rapidly to emerging threats, preventing potential financial losses and safeguarding the integrity of their systems. An integral aspect of real-time fraud monitoring is the application of sophisticated anomaly detection algorithms, which continuously evaluate transactional data against established baselines to flag suspicious activities as they occur.
Predictive modeling also contributes significantly to real-time monitoring, enabling organizations to anticipate potential fraud risks based on historical data and current trends. The implementation of machine learning algorithms, such as decision trees and ensemble methods, aids in the identification of subtle patterns that may elude traditional rule-based systems. The agility provided by real-time monitoring not only enhances the speed of fraud detection but also minimizes the impact of fraudulent activities, as organizations can take immediate corrective actions, such as blocking transactions or alerting stakeholders. In essence, the integration of data science into real-time fraud monitoring empowers organizations to stay ahead of sophisticated fraudsters, fortifying their defenses in an era where the speed of response is paramount to maintaining financial security and trust.
Challenges and Ethical Considerations in Data-Driven Fraud Prevention
As organizations increasingly rely on data-driven approaches for fraud prevention, they are confronted with a myriad of Challenges and Ethical Considerations that warrant careful examination. One primary challenge lies in the balance between the effectiveness of fraud prevention measures and the preservation of individual privacy. The vast amounts of personal data required for comprehensive fraud detection raise concerns regarding potential breaches of privacy and the responsible use of sensitive information. Striking the right balance between safeguarding against fraud and respecting privacy rights becomes a delicate task for organizations leveraging data science.
Another substantial challenge involves the inherent biases within the data used to train fraud detection models. Biases present in historical datasets may lead to discriminatory outcomes, disproportionately affecting certain demographic groups. Addressing these biases is not only crucial for ethical reasons but also for the accuracy and fairness of fraud prevention systems. Ethical considerations also extend to the transparency and interpretability of algorithms, ensuring that decisions made by these systems can be understood and scrutinized by stakeholders, thereby fostering accountability.
Furthermore, as fraud detection systems become more sophisticated, the potential for false positives and negatives introduces a pragmatic challenge. Balancing the need for accurate fraud detection with minimizing false alarms is critical to avoiding unnecessary disruptions to legitimate transactions and maintaining user trust. Organizations must grapple with optimizing algorithms to achieve the delicate equilibrium between precision and recall.
The deployment of data-driven approaches in fraud prevention demands a conscientious consideration of the associated challenges and ethical implications. Organizations must proactively address these concerns to ensure that their fraud prevention strategies are not only effective but also aligned with principles of privacy, fairness, and accountability.
Integration of Big Data in Fraud Detection
The Integration of Big Data in Fraud Detection represents a transformative shift in how organizations tackle the complex landscape of financial malfeasance. Big Data, characterized by its volume, velocity, and variety, provides a wealth of information that, when harnessed effectively through data science, significantly enhances the capacity for fraud detection. The sheer volume of transactions and data generated in modern digital ecosystems necessitates scalable and robust solutions, making Big Data technologies indispensable in the fight against fraud.
One key aspect of integrating Big Data into fraud detection involves the aggregation and analysis of diverse data sources. By amalgamating transactional data, user behavior patterns, and external datasets, organizations can create a comprehensive view of their ecosystem. This holistic approach enables the identification of subtle patterns and anomalies that may signal fraudulent activities, offering a more nuanced understanding of potential threats.
The variety of data sources, including structured and unstructured data, adds another layer of richness to fraud detection efforts. Textual data from sources such as social media or customer communications, when integrated with transactional data, provides a more comprehensive view of user behavior and potential risks. Advanced analytics, such as natural language processing and sentiment analysis, can extract valuable insights from unstructured data, contributing to a more robust fraud prevention strategy.
However, the integration of Big Data in fraud detection is not without its challenges. Managing the vast amounts of data, ensuring data quality, and addressing privacy concerns are critical considerations. Nevertheless, when navigated effectively, the integration of Big Data stands as a powerful ally in the ongoing battle against fraud, empowering organizations with unparalleled insights and capabilities to safeguard their financial ecosystems.
Case Studies and Industry Applications
Examining Case Studies and Industry Applications provides a tangible glimpse into the real-world impact of data science in fraud detection across diverse sectors. In the financial industry, for instance, banks and financial institutions leverage advanced analytics and machine learning algorithms to identify unusual patterns in transactions, swiftly flagging potentially fraudulent activities. These systems analyze vast datasets of customer transactions, enabling quick response mechanisms to mitigate risks and protect clients from financial harm.
E-commerce platforms employ data science to combat fraudulent transactions, utilizing algorithms that assess user behavior, purchase history, and device fingerprints to detect anomalies. By scrutinizing patterns indicative of fraudulent activities, such as rapid changes in purchasing behavior or multiple account logins from different locations, these platforms can enhance their fraud prevention strategies and protect both merchants and consumers.
Healthcare organizations also benefit from data science in fraud detection, where sophisticated algorithms analyze insurance claims and billing data to identify irregularities. By scrutinizing patterns in billing codes, claim amounts, and provider behavior, these systems can flag potential instances of healthcare fraud, ensuring that resources are allocated efficiently and healthcare funds are safeguarded.
The telecommunications industry utilizes data science to combat subscription fraud, where criminals exploit identity information to obtain mobile services illegitimately. Advanced analytics help identify unusual patterns in subscriber behavior and usage, enabling telecommunications companies to proactively detect and prevent fraudulent activities.
These case studies underscore the versatility of data science in fraud detection and prevention across various industries. They highlight the adaptability of algorithms and analytical techniques in addressing sector-specific challenges, emphasizing the importance of a tailored and dynamic approach to safeguarding against evolving fraud threats.
How to obtain DATA SCIENCE CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the role of data science in fraud detection and prevention is undeniably paramount in today's interconnected and technology-driven landscape. As organizations grapple with the escalating sophistication of fraudulent activities, data science emerges as a powerful ally, offering advanced analytical tools and algorithms to decipher patterns, anomalies, and potential risks within vast datasets. The algorithmic approaches, real-time monitoring, integration of big data, and ethical considerations collectively contribute to the robustness of fraud prevention strategies.
Algorithmic approaches harness machine learning and statistical models to discern intricate patterns, enabling organizations to stay ahead of evolving fraud tactics. Real-time monitoring provides a dynamic defense against emerging threats, allowing for swift intervention and mitigation. The integration of big data enriches fraud detection with comprehensive insights derived from diverse data sources, enhancing the precision and agility of preventive measures. Ethical considerations ensure responsible data usage, respecting privacy and promoting fairness in fraud prevention efforts.
As we navigate the evolving landscape of fraud, organizations must continue to invest in research and development, staying attuned to emerging technologies and evolving threats. The interdisciplinary nature of data science, combining statistical analysis, machine learning, and domain expertise, positions it as a dynamic and essential tool in the ongoing battle against financial and cyber threats. By embracing and refining data-driven fraud prevention strategies, organizations can not only fortify their defenses but also contribute to the broader goal of creating a secure and trustworthy digital ecosystem.
Read More
The pervasive growth of digital transactions and the increasing reliance on technology in various sectors have led to a parallel rise in fraudulent activities, making the role of data science in fraud detection and prevention more crucial than ever. In this era of information overload, organizations are inundated with vast amounts of data, providing both an opportunity and a challenge in the fight against fraud.
Data science, with its advanced analytics and machine learning techniques, has emerged as a powerful tool to sift through this sea of information, identifying patterns, anomalies, and potential indicators of fraudulent behavior. This interdisciplinary field amalgamates statistics, computer science, and domain expertise to develop sophisticated models that can recognize and predict fraudulent activities with high accuracy.
As fraudsters continually evolve their tactics, the adaptive nature of data science allows for the continuous refinement of detection models, ensuring organizations stay one step ahead in the ongoing battle against financial and cyber threats. This paper delves into the multifaceted role of data science in fraud detection and prevention, exploring its methodologies, challenges, and real-world applications across diverse industries.
Table of contents
-
Algorithmic Approaches in Fraud Detection
-
Real-Time Fraud Monitoring
-
Challenges and Ethical Considerations in Data-Driven Fraud Prevention
-
Integration of Big Data in Fraud Detection
-
Case Studies and Industry Applications
-
Conclusion
Algorithmic Approaches in Fraud Detection
In the intricate landscape of fraud detection, Algorithmic Approaches play a pivotal role in harnessing the power of data science to identify and mitigate fraudulent activities effectively. Leveraging a diverse array of machine learning algorithms and statistical models, organizations can analyze vast datasets to discern subtle patterns indicative of fraudulent behavior.
Anomalies, outliers, and deviations from expected norms are systematically detected through these algorithms, allowing for the swift identification of potential fraud risks. Supervised learning models, such as logistic regression and decision trees, are commonly employed to classify transactions as either legitimate or suspicious based on historical data. Meanwhile, unsupervised learning techniques, including clustering and outlier detection, enable the identification of novel fraud patterns without predefined labels.
The adaptive nature of these algorithms allows for continuous learning and refinement, ensuring that fraud detection systems remain resilient against evolving tactics employed by fraudsters. Furthermore, advancements in deep learning, including neural networks, contribute to the development of more intricate models capable of capturing complex relationships within data, further enhancing the accuracy and efficiency of fraud detection processes. Algorithmic approaches, therefore, form the bedrock of data science in the ongoing battle against fraudulent activities, providing organizations with the analytical prowess needed to safeguard their operations in an increasingly digital and interconnected world.
Real-Time Fraud Monitoring
In the fast-paced landscape of financial transactions and digital interactions, Real-Time Fraud Monitoring has emerged as a critical component in the arsenal of fraud detection and prevention strategies. Data science plays a pivotal role in enabling organizations to monitor transactions and activities in real-time, providing a dynamic defense against evolving fraud tactics. The essence of real-time monitoring lies in the ability to swiftly analyze and assess incoming data streams to identify anomalies and patterns associated with fraudulent behavior. This proactive approach allows organizations to respond rapidly to emerging threats, preventing potential financial losses and safeguarding the integrity of their systems. An integral aspect of real-time fraud monitoring is the application of sophisticated anomaly detection algorithms, which continuously evaluate transactional data against established baselines to flag suspicious activities as they occur.
Predictive modeling also contributes significantly to real-time monitoring, enabling organizations to anticipate potential fraud risks based on historical data and current trends. The implementation of machine learning algorithms, such as decision trees and ensemble methods, aids in the identification of subtle patterns that may elude traditional rule-based systems. The agility provided by real-time monitoring not only enhances the speed of fraud detection but also minimizes the impact of fraudulent activities, as organizations can take immediate corrective actions, such as blocking transactions or alerting stakeholders. In essence, the integration of data science into real-time fraud monitoring empowers organizations to stay ahead of sophisticated fraudsters, fortifying their defenses in an era where the speed of response is paramount to maintaining financial security and trust.
Challenges and Ethical Considerations in Data-Driven Fraud Prevention
As organizations increasingly rely on data-driven approaches for fraud prevention, they are confronted with a myriad of Challenges and Ethical Considerations that warrant careful examination. One primary challenge lies in the balance between the effectiveness of fraud prevention measures and the preservation of individual privacy. The vast amounts of personal data required for comprehensive fraud detection raise concerns regarding potential breaches of privacy and the responsible use of sensitive information. Striking the right balance between safeguarding against fraud and respecting privacy rights becomes a delicate task for organizations leveraging data science.
Another substantial challenge involves the inherent biases within the data used to train fraud detection models. Biases present in historical datasets may lead to discriminatory outcomes, disproportionately affecting certain demographic groups. Addressing these biases is not only crucial for ethical reasons but also for the accuracy and fairness of fraud prevention systems. Ethical considerations also extend to the transparency and interpretability of algorithms, ensuring that decisions made by these systems can be understood and scrutinized by stakeholders, thereby fostering accountability.
Furthermore, as fraud detection systems become more sophisticated, the potential for false positives and negatives introduces a pragmatic challenge. Balancing the need for accurate fraud detection with minimizing false alarms is critical to avoiding unnecessary disruptions to legitimate transactions and maintaining user trust. Organizations must grapple with optimizing algorithms to achieve the delicate equilibrium between precision and recall.
The deployment of data-driven approaches in fraud prevention demands a conscientious consideration of the associated challenges and ethical implications. Organizations must proactively address these concerns to ensure that their fraud prevention strategies are not only effective but also aligned with principles of privacy, fairness, and accountability.
Integration of Big Data in Fraud Detection
The Integration of Big Data in Fraud Detection represents a transformative shift in how organizations tackle the complex landscape of financial malfeasance. Big Data, characterized by its volume, velocity, and variety, provides a wealth of information that, when harnessed effectively through data science, significantly enhances the capacity for fraud detection. The sheer volume of transactions and data generated in modern digital ecosystems necessitates scalable and robust solutions, making Big Data technologies indispensable in the fight against fraud.
One key aspect of integrating Big Data into fraud detection involves the aggregation and analysis of diverse data sources. By amalgamating transactional data, user behavior patterns, and external datasets, organizations can create a comprehensive view of their ecosystem. This holistic approach enables the identification of subtle patterns and anomalies that may signal fraudulent activities, offering a more nuanced understanding of potential threats.
The variety of data sources, including structured and unstructured data, adds another layer of richness to fraud detection efforts. Textual data from sources such as social media or customer communications, when integrated with transactional data, provides a more comprehensive view of user behavior and potential risks. Advanced analytics, such as natural language processing and sentiment analysis, can extract valuable insights from unstructured data, contributing to a more robust fraud prevention strategy.
However, the integration of Big Data in fraud detection is not without its challenges. Managing the vast amounts of data, ensuring data quality, and addressing privacy concerns are critical considerations. Nevertheless, when navigated effectively, the integration of Big Data stands as a powerful ally in the ongoing battle against fraud, empowering organizations with unparalleled insights and capabilities to safeguard their financial ecosystems.
Case Studies and Industry Applications
Examining Case Studies and Industry Applications provides a tangible glimpse into the real-world impact of data science in fraud detection across diverse sectors. In the financial industry, for instance, banks and financial institutions leverage advanced analytics and machine learning algorithms to identify unusual patterns in transactions, swiftly flagging potentially fraudulent activities. These systems analyze vast datasets of customer transactions, enabling quick response mechanisms to mitigate risks and protect clients from financial harm.
E-commerce platforms employ data science to combat fraudulent transactions, utilizing algorithms that assess user behavior, purchase history, and device fingerprints to detect anomalies. By scrutinizing patterns indicative of fraudulent activities, such as rapid changes in purchasing behavior or multiple account logins from different locations, these platforms can enhance their fraud prevention strategies and protect both merchants and consumers.
Healthcare organizations also benefit from data science in fraud detection, where sophisticated algorithms analyze insurance claims and billing data to identify irregularities. By scrutinizing patterns in billing codes, claim amounts, and provider behavior, these systems can flag potential instances of healthcare fraud, ensuring that resources are allocated efficiently and healthcare funds are safeguarded.
The telecommunications industry utilizes data science to combat subscription fraud, where criminals exploit identity information to obtain mobile services illegitimately. Advanced analytics help identify unusual patterns in subscriber behavior and usage, enabling telecommunications companies to proactively detect and prevent fraudulent activities.
These case studies underscore the versatility of data science in fraud detection and prevention across various industries. They highlight the adaptability of algorithms and analytical techniques in addressing sector-specific challenges, emphasizing the importance of a tailored and dynamic approach to safeguarding against evolving fraud threats.
How to obtain DATA SCIENCE CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the role of data science in fraud detection and prevention is undeniably paramount in today's interconnected and technology-driven landscape. As organizations grapple with the escalating sophistication of fraudulent activities, data science emerges as a powerful ally, offering advanced analytical tools and algorithms to decipher patterns, anomalies, and potential risks within vast datasets. The algorithmic approaches, real-time monitoring, integration of big data, and ethical considerations collectively contribute to the robustness of fraud prevention strategies.
Algorithmic approaches harness machine learning and statistical models to discern intricate patterns, enabling organizations to stay ahead of evolving fraud tactics. Real-time monitoring provides a dynamic defense against emerging threats, allowing for swift intervention and mitigation. The integration of big data enriches fraud detection with comprehensive insights derived from diverse data sources, enhancing the precision and agility of preventive measures. Ethical considerations ensure responsible data usage, respecting privacy and promoting fairness in fraud prevention efforts.
As we navigate the evolving landscape of fraud, organizations must continue to invest in research and development, staying attuned to emerging technologies and evolving threats. The interdisciplinary nature of data science, combining statistical analysis, machine learning, and domain expertise, positions it as a dynamic and essential tool in the ongoing battle against financial and cyber threats. By embracing and refining data-driven fraud prevention strategies, organizations can not only fortify their defenses but also contribute to the broader goal of creating a secure and trustworthy digital ecosystem.
Key Benefits of Achieving ISO 20000 Certification for Your IT Services
Achieving ISO 20000 certification for your IT services is a significant milestone that demonstrates your commitment to excellence in managing information technology processes. ISO 20000 is an international standard specifically designed for IT service management systems, providing a framework for organizations to establish, implement, maintain, and continually improve their IT service delivery. This certification not only signifies compliance with industry best practices but also brings forth a multitude of key benefits for businesses operating in the ever-evolving digital landscape.
ISO 20000 certification also promotes a culture of continual improvement within the organization. The standard emphasizes the importance of regularly monitoring and evaluating IT service management processes, fostering a mindset of adaptability and responsiveness to changing technological landscapes. This proactive approach not only ensures the alignment of IT services with business objectives but also equips organizations to stay ahead of industry trends and emerging technologies.
In summary, attaining ISO 20000 certification for your IT services is a strategic investment that goes beyond mere compliance. It serves as a powerful tool for enhancing service quality, fostering a culture of continual improvement, and gaining a competitive edge in the dynamic realm of IT service management. As organizations increasingly rely on technology for their operations, ISO 20000 certification stands as a testament to a commitment to excellence, reliability, and customer satisfaction in the provision of IT services.
Table of contents
-
Process Standardization and Consistency
-
Enhanced Service Delivery and Customer Confidence
-
Cost Savings and Resource Optimization
-
Alignment with Business Objectives
-
Market Recognition and Competitive Edge
-
Conclusion
Process Standardization and Consistency
Process Standardization and Consistency are pivotal benefits derived from achieving ISO 20000 certification for IT services. The certification instills a disciplined approach to IT service management, emphasizing the need for standardized processes across the organization. Standardization involves establishing uniform procedures, protocols, and guidelines, ensuring that every aspect of IT service delivery adheres to a consistent framework. This systematic approach not only minimizes the risk of errors but also promotes operational efficiency by streamlining workflows and eliminating redundancies.
Consistency is a key byproduct of process standardization within the ISO 20000 framework. It ensures that IT services are delivered in a uniform manner, regardless of the specific circumstances or individuals involved. This uniformity is crucial for fostering predictability and reliability in service delivery. Clients and stakeholders can have confidence that the IT services they receive will consistently meet or exceed established standards, leading to increased trust and satisfaction.
Moreover, process standardization and consistency contribute to improved communication and collaboration within the IT service management team. With everyone following the same set of procedures, there is a common language and understanding of how tasks should be executed. This not only reduces the likelihood of misunderstandings but also facilitates the seamless integration of new team members into existing workflows.
From a strategic perspective, the emphasis on process standardization and consistency aligns with the broader goal of achieving operational excellence. Organizations that attain ISO 20000 certification position themselves to operate more efficiently, respond more effectively to challenges, and adapt to evolving technological landscapes with agility. Ultimately, the benefits of process standardization and consistency extend beyond mere compliance; they lay the foundation for a resilient and high-performing IT service management system.
Enhanced Service Delivery and Customer Confidence
ISO 20000 certification plays a pivotal role in enhancing service delivery within IT organizations, leading to increased customer confidence and satisfaction. By adhering to the rigorous standards set by ISO 20000, organizations commit to a systematic and customer-focused approach to IT service management. This commitment translates into tangible improvements in the quality and reliability of services, directly impacting the overall customer experience.
Achieving enhanced service delivery begins with a comprehensive understanding of customer requirements and expectations. ISO 20000 encourages organizations to align their IT services with customer needs, ensuring that the delivered solutions are not only technically sound but also relevant and valuable to the end-users. This customer-centric approach fosters a culture of continuous improvement, with organizations actively seeking feedback to refine and optimize their service offerings.
The certification also emphasizes the establishment of service level agreements (SLAs) and key performance indicators (KPIs) to measure and monitor service delivery. This transparency in performance metrics not only allows organizations to track their own efficiency but also provides customers with clear insights into the quality and reliability of the services they are receiving. This increased transparency contributes to customer confidence, as clients can make informed decisions based on measurable and verifiable data.
The pursuit of ISO 20000 certification not only elevates the overall quality of service delivery but also establishes a foundation for building and maintaining customer confidence. By systematically aligning IT services with customer expectations, actively monitoring performance, and fostering a culture of continuous improvement, organizations can position themselves as reliable and customer-focused partners in the dynamic landscape of IT service management.
Cost Savings and Resource Optimization
ISO 20000 certification offers organizations a pathway to significant cost savings and resource optimization in the realm of IT services. The certification's emphasis on efficient IT service management processes directly contributes to streamlining operations and reducing unnecessary expenditures. Through the adoption of standardized procedures and the elimination of redundant activities, organizations can achieve notable improvements in resource utilization, ultimately leading to cost-effectiveness.
Cost savings are also realized through improved efficiency in service delivery processes. ISO 20000 encourages organizations to identify and eliminate inefficiencies, ensuring that tasks are completed with maximum productivity. This focus on efficiency not only saves time but also reduces operational costs, enhancing the overall cost-effectiveness of IT service management.
Resource optimization extends beyond the realm of technology to include human resources. ISO 20000 emphasizes training and development initiatives to enhance the skills and competencies of IT personnel. Well-trained teams are not only more productive but also better equipped to handle diverse challenges, reducing the likelihood of errors and costly rework.
Alignment with Business Objectives
ISO 20000 certification serves as a powerful catalyst for aligning IT services with the broader strategic objectives of an organization. One of the key benefits is the establishment of a seamless connection between IT processes and the overarching business goals. The certification framework emphasizes the need for a comprehensive understanding of the organization's objectives, enabling IT service providers to tailor their services to directly contribute to the achievement of those objectives.
By aligning IT services with business objectives, organizations can ensure that technology is not just a support function but a strategic enabler. ISO 20000 encourages IT service management to become an integral part of the business strategy, facilitating a collaborative approach that considers both technological and business perspectives. This alignment fosters a holistic understanding of how IT supports and enhances various business functions, ultimately driving overall organizational success.
ISO 20000's focus on alignment extends to the continuous monitoring and improvement of IT services in relation to changing business needs. Organizations that achieve and maintain certification demonstrate a commitment to staying adaptable and responsive to evolving business objectives. This adaptability is crucial in a dynamic business environment where technological advancements and market conditions can rapidly change, requiring IT services to evolve in tandem with organizational goals.
ISO 20000 certification serves as a guide for organizations seeking to align their IT services with overarching business objectives. This alignment ensures that IT is not a siloed function but an integral part of the organizational strategy, fostering collaboration, transparency, and continuous improvement in the pursuit of shared business goals.
Market Recognition and Competitive Edge
Market recognition stems from the credibility and prestige associated with ISO 20000 certification. Clients and businesses often view this certification as a validation of an organization's dedication to quality, reliability, and continuous improvement in delivering IT services. As a result, organizations that have achieved ISO 20000 certification are more likely to be recognized as reliable and trustworthy partners in the competitive IT services sector.
The competitive edge gained through ISO 20000 certification extends beyond mere recognition. It positions organizations to meet or exceed industry benchmarks, demonstrating a commitment to excellence that sets them apart from competitors. Clients, when faced with a choice between service providers, are more inclined to select those with a proven track record of adherence to international standards, viewing it as an assurance of superior service quality and reliability.
ISO 20000 certification not only enhances market recognition but also provides a tangible competitive edge in the dynamic and competitive field of IT services. It positions organizations as leaders who prioritize quality and efficiency, contributing to increased trust, customer loyalty, and ultimately, business success in a globally competitive market.
How to obtain ISO 20000 IT SERVICE MANAGEMENT CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, achieving ISO 20000 certification for IT services yields a spectrum of key benefits that extend far beyond compliance. The certification's emphasis on process standardization and consistency ensures a streamlined and error-resistant approach to IT service management, fostering operational efficiency. Enhanced service delivery, coupled with a customer-centric focus, elevates the overall customer experience, instilling confidence and loyalty.
Cost savings and resource optimization emerge as significant advantages, driven by the systematic and efficient processes encouraged by ISO 20000. Aligning IT services with business objectives not only positions technology as a strategic enabler but also strengthens collaboration between IT and other business functions. This alignment ensures that IT services are not just technically sound but actively contribute to the realization of broader organizational goals.
ISO 20000 certification transcends the realm of IT service management, becoming a strategic investment that positively impacts an organization's overall performance, client relationships, and competitive positioning. As businesses navigate the ever-evolving landscape of technology and service delivery, the benefits of ISO 20000 certification stand as a testament to an organization's commitment to excellence, adaptability, and long-term success in the dynamic field of IT services.
Read More
Achieving ISO 20000 certification for your IT services is a significant milestone that demonstrates your commitment to excellence in managing information technology processes. ISO 20000 is an international standard specifically designed for IT service management systems, providing a framework for organizations to establish, implement, maintain, and continually improve their IT service delivery. This certification not only signifies compliance with industry best practices but also brings forth a multitude of key benefits for businesses operating in the ever-evolving digital landscape.
ISO 20000 certification also promotes a culture of continual improvement within the organization. The standard emphasizes the importance of regularly monitoring and evaluating IT service management processes, fostering a mindset of adaptability and responsiveness to changing technological landscapes. This proactive approach not only ensures the alignment of IT services with business objectives but also equips organizations to stay ahead of industry trends and emerging technologies.
In summary, attaining ISO 20000 certification for your IT services is a strategic investment that goes beyond mere compliance. It serves as a powerful tool for enhancing service quality, fostering a culture of continual improvement, and gaining a competitive edge in the dynamic realm of IT service management. As organizations increasingly rely on technology for their operations, ISO 20000 certification stands as a testament to a commitment to excellence, reliability, and customer satisfaction in the provision of IT services.
Table of contents
-
Process Standardization and Consistency
-
Enhanced Service Delivery and Customer Confidence
-
Cost Savings and Resource Optimization
-
Alignment with Business Objectives
-
Market Recognition and Competitive Edge
-
Conclusion
Process Standardization and Consistency
Process Standardization and Consistency are pivotal benefits derived from achieving ISO 20000 certification for IT services. The certification instills a disciplined approach to IT service management, emphasizing the need for standardized processes across the organization. Standardization involves establishing uniform procedures, protocols, and guidelines, ensuring that every aspect of IT service delivery adheres to a consistent framework. This systematic approach not only minimizes the risk of errors but also promotes operational efficiency by streamlining workflows and eliminating redundancies.
Consistency is a key byproduct of process standardization within the ISO 20000 framework. It ensures that IT services are delivered in a uniform manner, regardless of the specific circumstances or individuals involved. This uniformity is crucial for fostering predictability and reliability in service delivery. Clients and stakeholders can have confidence that the IT services they receive will consistently meet or exceed established standards, leading to increased trust and satisfaction.
Moreover, process standardization and consistency contribute to improved communication and collaboration within the IT service management team. With everyone following the same set of procedures, there is a common language and understanding of how tasks should be executed. This not only reduces the likelihood of misunderstandings but also facilitates the seamless integration of new team members into existing workflows.
From a strategic perspective, the emphasis on process standardization and consistency aligns with the broader goal of achieving operational excellence. Organizations that attain ISO 20000 certification position themselves to operate more efficiently, respond more effectively to challenges, and adapt to evolving technological landscapes with agility. Ultimately, the benefits of process standardization and consistency extend beyond mere compliance; they lay the foundation for a resilient and high-performing IT service management system.
Enhanced Service Delivery and Customer Confidence
ISO 20000 certification plays a pivotal role in enhancing service delivery within IT organizations, leading to increased customer confidence and satisfaction. By adhering to the rigorous standards set by ISO 20000, organizations commit to a systematic and customer-focused approach to IT service management. This commitment translates into tangible improvements in the quality and reliability of services, directly impacting the overall customer experience.
Achieving enhanced service delivery begins with a comprehensive understanding of customer requirements and expectations. ISO 20000 encourages organizations to align their IT services with customer needs, ensuring that the delivered solutions are not only technically sound but also relevant and valuable to the end-users. This customer-centric approach fosters a culture of continuous improvement, with organizations actively seeking feedback to refine and optimize their service offerings.
The certification also emphasizes the establishment of service level agreements (SLAs) and key performance indicators (KPIs) to measure and monitor service delivery. This transparency in performance metrics not only allows organizations to track their own efficiency but also provides customers with clear insights into the quality and reliability of the services they are receiving. This increased transparency contributes to customer confidence, as clients can make informed decisions based on measurable and verifiable data.
The pursuit of ISO 20000 certification not only elevates the overall quality of service delivery but also establishes a foundation for building and maintaining customer confidence. By systematically aligning IT services with customer expectations, actively monitoring performance, and fostering a culture of continuous improvement, organizations can position themselves as reliable and customer-focused partners in the dynamic landscape of IT service management.
Cost Savings and Resource Optimization
ISO 20000 certification offers organizations a pathway to significant cost savings and resource optimization in the realm of IT services. The certification's emphasis on efficient IT service management processes directly contributes to streamlining operations and reducing unnecessary expenditures. Through the adoption of standardized procedures and the elimination of redundant activities, organizations can achieve notable improvements in resource utilization, ultimately leading to cost-effectiveness.
Cost savings are also realized through improved efficiency in service delivery processes. ISO 20000 encourages organizations to identify and eliminate inefficiencies, ensuring that tasks are completed with maximum productivity. This focus on efficiency not only saves time but also reduces operational costs, enhancing the overall cost-effectiveness of IT service management.
Resource optimization extends beyond the realm of technology to include human resources. ISO 20000 emphasizes training and development initiatives to enhance the skills and competencies of IT personnel. Well-trained teams are not only more productive but also better equipped to handle diverse challenges, reducing the likelihood of errors and costly rework.
Alignment with Business Objectives
ISO 20000 certification serves as a powerful catalyst for aligning IT services with the broader strategic objectives of an organization. One of the key benefits is the establishment of a seamless connection between IT processes and the overarching business goals. The certification framework emphasizes the need for a comprehensive understanding of the organization's objectives, enabling IT service providers to tailor their services to directly contribute to the achievement of those objectives.
By aligning IT services with business objectives, organizations can ensure that technology is not just a support function but a strategic enabler. ISO 20000 encourages IT service management to become an integral part of the business strategy, facilitating a collaborative approach that considers both technological and business perspectives. This alignment fosters a holistic understanding of how IT supports and enhances various business functions, ultimately driving overall organizational success.
ISO 20000's focus on alignment extends to the continuous monitoring and improvement of IT services in relation to changing business needs. Organizations that achieve and maintain certification demonstrate a commitment to staying adaptable and responsive to evolving business objectives. This adaptability is crucial in a dynamic business environment where technological advancements and market conditions can rapidly change, requiring IT services to evolve in tandem with organizational goals.
ISO 20000 certification serves as a guide for organizations seeking to align their IT services with overarching business objectives. This alignment ensures that IT is not a siloed function but an integral part of the organizational strategy, fostering collaboration, transparency, and continuous improvement in the pursuit of shared business goals.
Market Recognition and Competitive Edge
Market recognition stems from the credibility and prestige associated with ISO 20000 certification. Clients and businesses often view this certification as a validation of an organization's dedication to quality, reliability, and continuous improvement in delivering IT services. As a result, organizations that have achieved ISO 20000 certification are more likely to be recognized as reliable and trustworthy partners in the competitive IT services sector.
The competitive edge gained through ISO 20000 certification extends beyond mere recognition. It positions organizations to meet or exceed industry benchmarks, demonstrating a commitment to excellence that sets them apart from competitors. Clients, when faced with a choice between service providers, are more inclined to select those with a proven track record of adherence to international standards, viewing it as an assurance of superior service quality and reliability.
ISO 20000 certification not only enhances market recognition but also provides a tangible competitive edge in the dynamic and competitive field of IT services. It positions organizations as leaders who prioritize quality and efficiency, contributing to increased trust, customer loyalty, and ultimately, business success in a globally competitive market.
How to obtain ISO 20000 IT SERVICE MANAGEMENT CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, achieving ISO 20000 certification for IT services yields a spectrum of key benefits that extend far beyond compliance. The certification's emphasis on process standardization and consistency ensures a streamlined and error-resistant approach to IT service management, fostering operational efficiency. Enhanced service delivery, coupled with a customer-centric focus, elevates the overall customer experience, instilling confidence and loyalty.
Cost savings and resource optimization emerge as significant advantages, driven by the systematic and efficient processes encouraged by ISO 20000. Aligning IT services with business objectives not only positions technology as a strategic enabler but also strengthens collaboration between IT and other business functions. This alignment ensures that IT services are not just technically sound but actively contribute to the realization of broader organizational goals.
ISO 20000 certification transcends the realm of IT service management, becoming a strategic investment that positively impacts an organization's overall performance, client relationships, and competitive positioning. As businesses navigate the ever-evolving landscape of technology and service delivery, the benefits of ISO 20000 certification stand as a testament to an organization's commitment to excellence, adaptability, and long-term success in the dynamic field of IT services.
Navigating the CISA Certification Process: A Step-by-Step Guide
In today's dynamic and ever-evolving field of information technology and cybersecurity, professionals seek recognized certifications to validate their expertise and enhance their career prospects. Among the sought-after credentials in this realm is the Certified Information Systems Auditor (CISA) certification, widely regarded as a benchmark for proficiency in auditing, controlling, and securing information systems.
This comprehensive guide aims to demystify and streamline the often intricate process of obtaining the CISA certification. As organizations increasingly prioritize robust information security measures, individuals equipped with CISA certification stand out as valuable assets in safeguarding sensitive data and ensuring compliance with industry standards. Understanding the step-by-step journey towards obtaining the CISA certification is not only essential for aspiring candidates but also serves as a roadmap for current IT professionals looking to fortify their skillset and advance in their careers.
Navigating through the intricacies of the CISA certification process involves not only acquiring theoretical knowledge but also gaining practical experience in auditing information systems. This guide will break down each step, offering insights into the exam structure, recommended study resources, and strategies for success. Whether you are a seasoned IT professional or a newcomer to the field, embarking on the CISA certification journey requires a well-informed and systematic approach, and this guide aims to be your companion throughout this rewarding expedition.
Table of contents
-
Understanding the CISA Certification
-
Eligibility Criteria and Application Process
-
Strategizing Your CISA Exam Preparation
-
Practical Experience and Skill Development
-
Exam Day Strategies and Post-Certification Considerations
-
Conclusion
Understanding the CISA Certification
In the realm of information technology and cybersecurity, the Certified Information Systems Auditor (CISA) certification stands as a pillar of professional validation. Understanding the essence of the CISA certification involves recognizing its role as a globally recognized standard for individuals engaged in auditing, controlling, and securing information systems within organizations. This certification, bestowed by the Information Systems Audit and Control Association (ISACA), signifies a profound level of expertise and competence in the critical domains of information systems auditing and assurance.
The CISA certification is designed to equip professionals with the knowledge and skills required to assess vulnerabilities, ensure compliance with regulations, and bolster the overall integrity of information systems. As organizations increasingly prioritize the protection of sensitive data, CISA-certified individuals become instrumental in steering these efforts. Moreover, the certification serves as a testament to an individual's commitment to maintaining the highest standards of professional conduct, ethics, and ongoing education in the rapidly evolving landscape of cybersecurity.
Recognizing the significance of CISA in the context of career development, professionals seek this certification to enhance their marketability and credibility. Employers, in turn, often prioritize candidates with CISA certification, viewing them as assets capable of fortifying organizational resilience against cyber threats. The journey towards obtaining CISA involves a comprehensive understanding of the certification's foundations, its evolution over time, and its role in shaping the landscape of information systems auditing. Aspiring candidates must delve into the intricacies of CISA to fully grasp its impact on professional growth and its contribution to the broader field of information security.
Eligibility Criteria and Application Process
Embarking on the path to obtaining the Certified Information Systems Auditor (CISA) certification necessitates a comprehensive understanding of the eligibility criteria and a systematic navigation through the application process. The eligibility criteria, stipulated by the Information Systems Audit and Control Association (ISACA), serve as a foundational benchmark to ensure that candidates possess the requisite knowledge and experience in information systems auditing and control.
To qualify for the CISA certification, candidates typically need a minimum of five years of professional work experience in information systems, with at least three years specifically focused on information systems auditing, control, or security. It is crucial for potential candidates to review these requirements carefully, as ISACA allows for substitutions and waivers based on certain educational backgrounds and other recognized certifications. A detailed examination of individual qualifications against these criteria is a crucial initial step for those aspiring to pursue CISA certification.
Successfully navigating the application process requires attention to detail and meticulous documentation. Candidates should allocate sufficient time to compile accurate and complete information, anticipating potential challenges along the way. Understanding the intricacies of the eligibility criteria and application requirements is not only essential for a successful application but also contributes to a smoother initiation into the CISA certification process. Aspiring candidates are encouraged to approach this phase with diligence and a commitment to meeting the high standards set by ISACA.
Strategizing Your CISA Exam Preparation
Strategizing for the Certified Information Systems Auditor (CISA) exam preparation is a critical component of ensuring success in this rigorous certification process. As candidates delve into the intricacies of the CISA exam, understanding its structure and content domains is paramount. The exam is typically divided into four domains: Information Systems Auditing Process, Governance and Management of IT, Information Systems Acquisition, Development, and Implementation, and Information Systems Operations, Maintenance, and Service Management. Recognizing the weight assigned to each domain and comprehending the specific knowledge areas within them is crucial for formulating an effective study plan.
Recommendations for study materials and resources play a pivotal role in successful exam preparation. Aspiring candidates should explore reputable CISA review manuals, practice exams, and online forums to gain a comprehensive understanding of the exam format and question types. Leveraging official ISACA resources, such as the CISA Review Manual and the QAE (Question, Answer, and Explanation) Database, provides candidates with authoritative insights into the exam's content and format, enhancing their overall readiness.
Strategizing for CISA exam preparation involves a multifaceted approach encompassing domain-specific understanding, resource selection, effective time management, and stress reduction techniques. By adopting a well-rounded strategy tailored to individual needs, candidates can navigate the complexities of the CISA exam with confidence and increase their likelihood of achieving success.
Practical Experience and Skill Development
Practical experience and skill development are integral components of the Certified Information Systems Auditor (CISA) certification journey, emphasizing the real-world application of knowledge in information systems auditing. While theoretical understanding forms the foundation, hands-on experience is indispensable for mastering the nuances of auditing processes, controls, and security measures.
CISA candidates are encouraged to actively seek opportunities to engage in practical scenarios that mirror the challenges faced in information systems auditing. This involves actively participating in audits, assessments, and security evaluations within the workplace or through specialized projects. By immersing themselves in these practical experiences, candidates can refine their skills in identifying vulnerabilities, evaluating controls, and proposing effective risk mitigation strategies.
Recognizing the importance of continuous improvement, CISA candidates should engage in ongoing professional development to stay abreast of emerging technologies, evolving cybersecurity threats, and updated auditing methodologies. This commitment to lifelong learning not only ensures the sustainability of skills but also positions CISA professionals as adaptable and valuable assets in the ever-changing landscape of information security.
Practical experience and skill development are pivotal elements in the CISA certification process, contributing to a well-rounded and effective auditor. By actively participating in hands-on experiences, refining communication skills, and staying attuned to industry developments, candidates can not only meet the certification requirements but also thrive in their roles as information systems auditors.
Exam Day Strategies and Post-Certification Considerations
As the pivotal moment of examination day approaches for those pursuing the Certified Information Systems Auditor (CISA) certification, strategic planning becomes essential. On exam day, candidates should prioritize mental and physical well-being. Ensuring a good night's sleep, maintaining a healthy diet, and arriving well in advance to the examination venue are fundamental components of a successful start. Familiarity with the exam format, rules, and identification requirements helps alleviate unnecessary stress, allowing candidates to focus their energy on the examination content.
Time management stands out as a critical aspect of success during the CISA exam. Candidates should be mindful of the allocated time for each section and plan accordingly. Prioritizing questions based on familiarity and complexity can optimize time utilization. If faced with challenging questions, a strategic approach involves temporarily moving on to other items and revisiting them later, preventing time constraints from impacting overall performance.
Post-exam considerations mark a transitional phase for candidates, regardless of the examination outcome. During the waiting period for results, self-reflection on the exam experience can offer insights into strengths and areas for improvement. This period provides an opportunity for candidates to identify potential areas of further study and skill development, reinforcing a commitment to professional growth.
Effective exam day strategies, encompassing physical preparation and time management, are essential for success in obtaining the CISA certification. Post-certification considerations involve thoughtful reflection on the examination experience and proactive steps to leverage the certification for continued professional growth and career advancement. By adopting a holistic approach to the certification journey, individuals can position themselves for a successful and fulfilling career in the dynamic field of information systems auditing.
How to obtain CISA CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, navigating the Certified Information Systems Auditor (CISA) certification process demands a well-orchestrated approach from understanding the foundational concepts to strategic exam day preparation and thoughtful post-certification considerations. The journey begins with a recognition of the CISA certification's significance as a global benchmark for proficiency in information systems auditing and control, playing a pivotal role in career development within the rapidly evolving landscape of cybersecurity.
Understanding the eligibility criteria and meticulously navigating the application process is crucial for aspiring candidates, setting the stage for a seamless entry into the certification journey. As individuals progress into exam preparation, a strategic approach that encompasses domain-specific understanding, resource selection, effective time management, and stress reduction techniques becomes imperative for success.
Exam day strategies, including meticulous planning, time management, and maintaining composure under pressure, are pivotal for success in the final hurdle. Post-certification considerations involve a period of reflection and strategic planning, ensuring that the newly certified individuals leverage their accomplishment for continued professional growth, career advancement, and contribution to the broader field of information systems auditing.
The CISA certification journey is not merely a process but a transformative experience that equips individuals with the knowledge, skills, and recognition to excel in the critical realm of information systems auditing. As candidates evolve into certified professionals, their commitment to excellence, continuous improvement, and ethical conduct positions them as valuable assets in safeguarding information systems and navigating the ever-changing landscape of cybersecurity.
Read More
In today's dynamic and ever-evolving field of information technology and cybersecurity, professionals seek recognized certifications to validate their expertise and enhance their career prospects. Among the sought-after credentials in this realm is the Certified Information Systems Auditor (CISA) certification, widely regarded as a benchmark for proficiency in auditing, controlling, and securing information systems.
This comprehensive guide aims to demystify and streamline the often intricate process of obtaining the CISA certification. As organizations increasingly prioritize robust information security measures, individuals equipped with CISA certification stand out as valuable assets in safeguarding sensitive data and ensuring compliance with industry standards. Understanding the step-by-step journey towards obtaining the CISA certification is not only essential for aspiring candidates but also serves as a roadmap for current IT professionals looking to fortify their skillset and advance in their careers.
Navigating through the intricacies of the CISA certification process involves not only acquiring theoretical knowledge but also gaining practical experience in auditing information systems. This guide will break down each step, offering insights into the exam structure, recommended study resources, and strategies for success. Whether you are a seasoned IT professional or a newcomer to the field, embarking on the CISA certification journey requires a well-informed and systematic approach, and this guide aims to be your companion throughout this rewarding expedition.
Table of contents
-
Understanding the CISA Certification
-
Eligibility Criteria and Application Process
-
Strategizing Your CISA Exam Preparation
-
Practical Experience and Skill Development
-
Exam Day Strategies and Post-Certification Considerations
-
Conclusion
Understanding the CISA Certification
In the realm of information technology and cybersecurity, the Certified Information Systems Auditor (CISA) certification stands as a pillar of professional validation. Understanding the essence of the CISA certification involves recognizing its role as a globally recognized standard for individuals engaged in auditing, controlling, and securing information systems within organizations. This certification, bestowed by the Information Systems Audit and Control Association (ISACA), signifies a profound level of expertise and competence in the critical domains of information systems auditing and assurance.
The CISA certification is designed to equip professionals with the knowledge and skills required to assess vulnerabilities, ensure compliance with regulations, and bolster the overall integrity of information systems. As organizations increasingly prioritize the protection of sensitive data, CISA-certified individuals become instrumental in steering these efforts. Moreover, the certification serves as a testament to an individual's commitment to maintaining the highest standards of professional conduct, ethics, and ongoing education in the rapidly evolving landscape of cybersecurity.
Recognizing the significance of CISA in the context of career development, professionals seek this certification to enhance their marketability and credibility. Employers, in turn, often prioritize candidates with CISA certification, viewing them as assets capable of fortifying organizational resilience against cyber threats. The journey towards obtaining CISA involves a comprehensive understanding of the certification's foundations, its evolution over time, and its role in shaping the landscape of information systems auditing. Aspiring candidates must delve into the intricacies of CISA to fully grasp its impact on professional growth and its contribution to the broader field of information security.
Eligibility Criteria and Application Process
Embarking on the path to obtaining the Certified Information Systems Auditor (CISA) certification necessitates a comprehensive understanding of the eligibility criteria and a systematic navigation through the application process. The eligibility criteria, stipulated by the Information Systems Audit and Control Association (ISACA), serve as a foundational benchmark to ensure that candidates possess the requisite knowledge and experience in information systems auditing and control.
To qualify for the CISA certification, candidates typically need a minimum of five years of professional work experience in information systems, with at least three years specifically focused on information systems auditing, control, or security. It is crucial for potential candidates to review these requirements carefully, as ISACA allows for substitutions and waivers based on certain educational backgrounds and other recognized certifications. A detailed examination of individual qualifications against these criteria is a crucial initial step for those aspiring to pursue CISA certification.
Successfully navigating the application process requires attention to detail and meticulous documentation. Candidates should allocate sufficient time to compile accurate and complete information, anticipating potential challenges along the way. Understanding the intricacies of the eligibility criteria and application requirements is not only essential for a successful application but also contributes to a smoother initiation into the CISA certification process. Aspiring candidates are encouraged to approach this phase with diligence and a commitment to meeting the high standards set by ISACA.
Strategizing Your CISA Exam Preparation
Strategizing for the Certified Information Systems Auditor (CISA) exam preparation is a critical component of ensuring success in this rigorous certification process. As candidates delve into the intricacies of the CISA exam, understanding its structure and content domains is paramount. The exam is typically divided into four domains: Information Systems Auditing Process, Governance and Management of IT, Information Systems Acquisition, Development, and Implementation, and Information Systems Operations, Maintenance, and Service Management. Recognizing the weight assigned to each domain and comprehending the specific knowledge areas within them is crucial for formulating an effective study plan.
Recommendations for study materials and resources play a pivotal role in successful exam preparation. Aspiring candidates should explore reputable CISA review manuals, practice exams, and online forums to gain a comprehensive understanding of the exam format and question types. Leveraging official ISACA resources, such as the CISA Review Manual and the QAE (Question, Answer, and Explanation) Database, provides candidates with authoritative insights into the exam's content and format, enhancing their overall readiness.
Strategizing for CISA exam preparation involves a multifaceted approach encompassing domain-specific understanding, resource selection, effective time management, and stress reduction techniques. By adopting a well-rounded strategy tailored to individual needs, candidates can navigate the complexities of the CISA exam with confidence and increase their likelihood of achieving success.
Practical Experience and Skill Development
Practical experience and skill development are integral components of the Certified Information Systems Auditor (CISA) certification journey, emphasizing the real-world application of knowledge in information systems auditing. While theoretical understanding forms the foundation, hands-on experience is indispensable for mastering the nuances of auditing processes, controls, and security measures.
CISA candidates are encouraged to actively seek opportunities to engage in practical scenarios that mirror the challenges faced in information systems auditing. This involves actively participating in audits, assessments, and security evaluations within the workplace or through specialized projects. By immersing themselves in these practical experiences, candidates can refine their skills in identifying vulnerabilities, evaluating controls, and proposing effective risk mitigation strategies.
Recognizing the importance of continuous improvement, CISA candidates should engage in ongoing professional development to stay abreast of emerging technologies, evolving cybersecurity threats, and updated auditing methodologies. This commitment to lifelong learning not only ensures the sustainability of skills but also positions CISA professionals as adaptable and valuable assets in the ever-changing landscape of information security.
Practical experience and skill development are pivotal elements in the CISA certification process, contributing to a well-rounded and effective auditor. By actively participating in hands-on experiences, refining communication skills, and staying attuned to industry developments, candidates can not only meet the certification requirements but also thrive in their roles as information systems auditors.
Exam Day Strategies and Post-Certification Considerations
As the pivotal moment of examination day approaches for those pursuing the Certified Information Systems Auditor (CISA) certification, strategic planning becomes essential. On exam day, candidates should prioritize mental and physical well-being. Ensuring a good night's sleep, maintaining a healthy diet, and arriving well in advance to the examination venue are fundamental components of a successful start. Familiarity with the exam format, rules, and identification requirements helps alleviate unnecessary stress, allowing candidates to focus their energy on the examination content.
Time management stands out as a critical aspect of success during the CISA exam. Candidates should be mindful of the allocated time for each section and plan accordingly. Prioritizing questions based on familiarity and complexity can optimize time utilization. If faced with challenging questions, a strategic approach involves temporarily moving on to other items and revisiting them later, preventing time constraints from impacting overall performance.
Post-exam considerations mark a transitional phase for candidates, regardless of the examination outcome. During the waiting period for results, self-reflection on the exam experience can offer insights into strengths and areas for improvement. This period provides an opportunity for candidates to identify potential areas of further study and skill development, reinforcing a commitment to professional growth.
Effective exam day strategies, encompassing physical preparation and time management, are essential for success in obtaining the CISA certification. Post-certification considerations involve thoughtful reflection on the examination experience and proactive steps to leverage the certification for continued professional growth and career advancement. By adopting a holistic approach to the certification journey, individuals can position themselves for a successful and fulfilling career in the dynamic field of information systems auditing.
How to obtain CISA CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, navigating the Certified Information Systems Auditor (CISA) certification process demands a well-orchestrated approach from understanding the foundational concepts to strategic exam day preparation and thoughtful post-certification considerations. The journey begins with a recognition of the CISA certification's significance as a global benchmark for proficiency in information systems auditing and control, playing a pivotal role in career development within the rapidly evolving landscape of cybersecurity.
Understanding the eligibility criteria and meticulously navigating the application process is crucial for aspiring candidates, setting the stage for a seamless entry into the certification journey. As individuals progress into exam preparation, a strategic approach that encompasses domain-specific understanding, resource selection, effective time management, and stress reduction techniques becomes imperative for success.
Exam day strategies, including meticulous planning, time management, and maintaining composure under pressure, are pivotal for success in the final hurdle. Post-certification considerations involve a period of reflection and strategic planning, ensuring that the newly certified individuals leverage their accomplishment for continued professional growth, career advancement, and contribution to the broader field of information systems auditing.
The CISA certification journey is not merely a process but a transformative experience that equips individuals with the knowledge, skills, and recognition to excel in the critical realm of information systems auditing. As candidates evolve into certified professionals, their commitment to excellence, continuous improvement, and ethical conduct positions them as valuable assets in safeguarding information systems and navigating the ever-changing landscape of cybersecurity.
Salesforce Automation Tools A Deep Dive for Admins
In the dynamic landscape of modern business, where customer relationship management (CRM) plays a pivotal role, Salesforce has emerged as a powerhouse. At the heart of Salesforce's effectiveness lies its sophisticated automation tools, revolutionizing how organizations manage and streamline their sales processes. For administrators tasked with overseeing the Salesforce environment, understanding and harnessing these automation tools is not just a skill; it's a strategic imperative.
Salesforce Automation Tools empower administrators to design and implement intricate workflows, enabling a seamless orchestration of tasks and processes within the CRM platform. From lead generation to deal closure, these tools offer a comprehensive suite of features that can transform manual and time-consuming tasks into efficient, automated processes. As businesses strive for agility and efficiency in their operations, administrators serve as the architects, leveraging Salesforce automation tools to build a foundation for success.
This deep dive into Salesforce Automation Tools is designed to equip administrators with the knowledge and insights needed to navigate the intricacies of the platform. We will explore the core components of automation, including workflow rules, process builder, and flow builder, unraveling their functionalities and demonstrating how they can be tailored to meet specific business needs. With real-world examples and practical guidance, this exploration aims to empower administrators to unlock the full potential of Salesforce Automation Tools, ensuring they become adept orchestrators of the CRM symphony.
As we embark on this journey, administrators will gain a comprehensive understanding of the automation capabilities that Salesforce offers, allowing them to optimize processes, boost productivity, and enhance the overall user experience. Whether you're a seasoned Salesforce administrator or a newcomer to the platform, this deep dive will provide valuable insights and hands-on knowledge to navigate the evolving landscape of Salesforce automation with confidence and proficiency.
Table of contents
-
Foundations of Salesforce Automation
-
Advanced Automation: Unleashing the Power of Process Builder
-
User-Centric Automation: Enhancing Experiences with Flow Builder
-
Integration Strategies: Creating a Unified Automation Ecosystem
-
Optimizing Performance and Governance in Automation
-
Conclusion
Foundations of Salesforce Automation
In the realm of customer relationship management (CRM), Salesforce stands out as a leader, providing organizations with powerful tools to streamline their processes and enhance efficiency. At the core of Salesforce's effectiveness lies the concept of automation, a fundamental pillar that empowers businesses to move beyond manual tasks and embrace a more dynamic and responsive approach to managing their data and workflows.
The foundation of Salesforce automation often begins with the implementation of workflow rules. These rules serve as the building blocks for automating routine tasks and processes within the platform. Administrators can define specific criteria that, when met, trigger automated actions, such as updating fields, sending email notifications, or even creating new records. This foundational aspect of Salesforce automation not only reduces the burden of manual work but also ensures data accuracy and consistency across the CRM environment.
Workflow rules enable organizations to design and enforce business processes systematically. For example, as leads progress through the sales pipeline, workflow rules can automatically assign tasks to sales representatives, update opportunity stages, and notify relevant stakeholders. By establishing these rules, administrators lay the groundwork for a more streamlined and error-resistant workflow, allowing teams to focus on high-impact activities while the system handles routine, rule-based tasks.
Understanding the foundations of Salesforce automation through workflow rules is crucial for administrators seeking to optimize their CRM environment. As businesses evolve, the ability to adapt and scale automation becomes paramount. This foundational knowledge not only empowers administrators to create efficient workflows but also sets the stage for exploring more advanced automation tools within the Salesforce ecosystem, ensuring a robust and responsive foundation for the dynamic world of CRM.
Advanced Automation: Unleashing the Power of Process Builder
In the ever-evolving landscape of Salesforce, administrators are continually seeking ways to elevate their automation capabilities beyond the basics. Enter the Process Builder, a sophisticated tool that takes automation to a new level by providing a visual interface to design and execute complex processes. This advanced feature allows administrators to unleash the full power of Salesforce automation, catering to intricate business scenarios and demanding workflows.
The Process Builder is a game-changer for administrators aiming to create dynamic, multi-step processes without delving into intricate code. With its intuitive point-and-click interface, administrators can define processes that respond to a variety of conditions, making it possible to automate tasks that would traditionally require extensive customization. From updating multiple records simultaneously to orchestrating intricate business logic, the Process Builder offers a versatile solution for automating nuanced processes within the Salesforce ecosystem.
In the realm of Salesforce automation, the Process Builder stands as a testament to the platform's commitment to providing powerful yet accessible tools for administrators. As organizations evolve, the Process Builder empowers administrators to adapt and innovate, ensuring their Salesforce environment remains a dynamic and responsive force within their broader business strategy.
User-Centric Automation: Enhancing Experiences with Flow Builder
In the realm of Salesforce automation, the focus on user experience has become increasingly paramount. Enter Flow Builder, a tool designed to empower administrators to create dynamic and user-friendly workflows within the Salesforce platform. Unlike traditional automation tools, Flow Builder provides a visual canvas for designing flows, making it accessible to administrators with diverse levels of technical expertise and enabling them to craft processes that prioritize the end-user experience.
Flow Builder serves as a catalyst for user-centric automation by offering a versatile set of features. Administrators can design flows that guide users through specific processes, collecting and updating data along the way. This visual, point-and-click tool enables the creation of interactive screens, allowing users to input information seamlessly and participate in complex workflows without the need for extensive training. By prioritizing ease of use, Flow Builder enhances user adoption and engagement within the Salesforce environment.
As organizations strive to optimize their Salesforce environments, the emphasis on user-centric automation becomes a strategic imperative. Flow Builder not only empowers administrators to design workflows that align with the unique needs of their users but also contributes to a more intuitive and enjoyable experience within the CRM platform. By prioritizing user-centric automation, organizations can ensure that their Salesforce environment not only meets business objectives but also fosters a positive and productive user experience.
Integration Strategies: Creating a Unified Automation Ecosystem
In the complex landscape of modern business operations, the seamless integration of Salesforce automation tools with external systems has become a critical aspect of maximizing efficiency and functionality. Integration strategies play a pivotal role in creating a unified automation ecosystem, allowing organizations to harness the collective power of Salesforce alongside other applications and databases.
A fundamental consideration in integration is the need to establish a cohesive environment where data flows seamlessly between Salesforce and external systems. This requires a strategic approach to connecting disparate platforms, ensuring that information is not only transferred accurately but also remains synchronized in real-time. Administrators must evaluate the specific requirements of their organization, identifying key touchpoints where integration can eliminate silos and enhance the overall workflow.
Salesforce's robust set of APIs and connectors facilitates integration with a wide array of third-party applications, ERPs, and databases. Whether it's synchronizing customer data, connecting with marketing automation platforms, or streamlining financial processes, the integration capabilities of Salesforce automation tools provide a foundation for creating a unified and interconnected automation ecosystem. This interconnectedness empowers organizations to leverage the strengths of different tools cohesively, enhancing the overall effectiveness of their business processes.
Integration strategies within the Salesforce automation landscape are pivotal in creating a unified automation ecosystem. Administrators equipped with a strategic mindset can leverage these integration capabilities to build a connected and responsive environment that optimizes business processes, fosters collaboration, and positions the organization for sustained success in an increasingly interconnected business landscape.
Optimizing Performance and Governance in Automation
Performance optimization begins with a meticulous evaluation of automation processes to identify potential bottlenecks and resource-intensive operations. Administrators must implement best practices, such as bulk processing and selective automation, to ensure that workflows operate efficiently, particularly in scenarios involving large datasets. Monitoring system performance metrics and employing tools like Salesforce Optimizer can further aid administrators in identifying areas for improvement and fine-tuning their automation processes.
Effective governance in automation involves setting up rules and policies that govern how data is manipulated and accessed within the Salesforce platform. This includes defining roles and permissions to restrict access to sensitive information, ensuring compliance with regulatory standards. Administrators must strike a balance between enabling automation to enhance productivity and maintaining governance to mitigate risks associated with data misuse or unauthorized access.
Governance mechanisms extend to version control and change management, ensuring that updates to automation processes are tracked, documented, and implemented in a controlled manner. Regular audits of automation configurations, periodic reviews of access controls, and adherence to Salesforce release management best practices contribute to a robust governance framework. This not only safeguards the integrity of automated processes but also instills confidence in users regarding the reliability and security of the Salesforce environment.
By embracing optimization and governance hand in hand, administrators can ensure that Salesforce automation tools not only enhance operational efficiency but also adhere to the highest standards of data security and compliance. Striking this delicate balance enables organizations to derive maximum value from their automated workflows while maintaining a stable and trustworthy Salesforce environment that aligns with business objectives and regulatory requirements.
How to obtain SALESFORCE ADMINISTRATION CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Salesforce Automation Tools provide administrators with a robust framework to drive innovation, efficiency, and user satisfaction within their organizations. By mastering the intricacies of workflow rules, Process Builder, Flow Builder, integration strategies, and optimization measures, administrators can not only streamline operations but also future-proof their Salesforce environments. The journey through this deep dive serves as a guide for administrators to not only harness the full potential of Salesforce automation but also become architects of transformative change within their organizations. Armed with this knowledge, administrators are well-equipped to navigate the ever-evolving landscape of CRM, ensuring that Salesforce remains a cornerstone in driving business success.
In the dynamic world of Salesforce Automation Tools, administrators play a pivotal role in shaping the efficiency and effectiveness of an organization's CRM strategy. This deep dive into the foundations, advanced features, user-centric approaches, integration strategies, and optimization measures underscores the multifaceted nature of Salesforce automation, providing administrators with a comprehensive toolkit to navigate the complexities of their roles.
As administrators chart their course through the Salesforce automation landscape, optimization strategies become paramount. Balancing performance enhancements with governance measures ensures that the automation ecosystem remains responsive, reliable, and compliant with data security standards. This delicate equilibrium is crucial for sustaining the long-term success of Salesforce implementations.
Read More
In the dynamic landscape of modern business, where customer relationship management (CRM) plays a pivotal role, Salesforce has emerged as a powerhouse. At the heart of Salesforce's effectiveness lies its sophisticated automation tools, revolutionizing how organizations manage and streamline their sales processes. For administrators tasked with overseeing the Salesforce environment, understanding and harnessing these automation tools is not just a skill; it's a strategic imperative.
Salesforce Automation Tools empower administrators to design and implement intricate workflows, enabling a seamless orchestration of tasks and processes within the CRM platform. From lead generation to deal closure, these tools offer a comprehensive suite of features that can transform manual and time-consuming tasks into efficient, automated processes. As businesses strive for agility and efficiency in their operations, administrators serve as the architects, leveraging Salesforce automation tools to build a foundation for success.
This deep dive into Salesforce Automation Tools is designed to equip administrators with the knowledge and insights needed to navigate the intricacies of the platform. We will explore the core components of automation, including workflow rules, process builder, and flow builder, unraveling their functionalities and demonstrating how they can be tailored to meet specific business needs. With real-world examples and practical guidance, this exploration aims to empower administrators to unlock the full potential of Salesforce Automation Tools, ensuring they become adept orchestrators of the CRM symphony.
As we embark on this journey, administrators will gain a comprehensive understanding of the automation capabilities that Salesforce offers, allowing them to optimize processes, boost productivity, and enhance the overall user experience. Whether you're a seasoned Salesforce administrator or a newcomer to the platform, this deep dive will provide valuable insights and hands-on knowledge to navigate the evolving landscape of Salesforce automation with confidence and proficiency.
Table of contents
-
Foundations of Salesforce Automation
-
Advanced Automation: Unleashing the Power of Process Builder
-
User-Centric Automation: Enhancing Experiences with Flow Builder
-
Integration Strategies: Creating a Unified Automation Ecosystem
-
Optimizing Performance and Governance in Automation
-
Conclusion
Foundations of Salesforce Automation
In the realm of customer relationship management (CRM), Salesforce stands out as a leader, providing organizations with powerful tools to streamline their processes and enhance efficiency. At the core of Salesforce's effectiveness lies the concept of automation, a fundamental pillar that empowers businesses to move beyond manual tasks and embrace a more dynamic and responsive approach to managing their data and workflows.
The foundation of Salesforce automation often begins with the implementation of workflow rules. These rules serve as the building blocks for automating routine tasks and processes within the platform. Administrators can define specific criteria that, when met, trigger automated actions, such as updating fields, sending email notifications, or even creating new records. This foundational aspect of Salesforce automation not only reduces the burden of manual work but also ensures data accuracy and consistency across the CRM environment.
Workflow rules enable organizations to design and enforce business processes systematically. For example, as leads progress through the sales pipeline, workflow rules can automatically assign tasks to sales representatives, update opportunity stages, and notify relevant stakeholders. By establishing these rules, administrators lay the groundwork for a more streamlined and error-resistant workflow, allowing teams to focus on high-impact activities while the system handles routine, rule-based tasks.
Understanding the foundations of Salesforce automation through workflow rules is crucial for administrators seeking to optimize their CRM environment. As businesses evolve, the ability to adapt and scale automation becomes paramount. This foundational knowledge not only empowers administrators to create efficient workflows but also sets the stage for exploring more advanced automation tools within the Salesforce ecosystem, ensuring a robust and responsive foundation for the dynamic world of CRM.
Advanced Automation: Unleashing the Power of Process Builder
In the ever-evolving landscape of Salesforce, administrators are continually seeking ways to elevate their automation capabilities beyond the basics. Enter the Process Builder, a sophisticated tool that takes automation to a new level by providing a visual interface to design and execute complex processes. This advanced feature allows administrators to unleash the full power of Salesforce automation, catering to intricate business scenarios and demanding workflows.
The Process Builder is a game-changer for administrators aiming to create dynamic, multi-step processes without delving into intricate code. With its intuitive point-and-click interface, administrators can define processes that respond to a variety of conditions, making it possible to automate tasks that would traditionally require extensive customization. From updating multiple records simultaneously to orchestrating intricate business logic, the Process Builder offers a versatile solution for automating nuanced processes within the Salesforce ecosystem.
In the realm of Salesforce automation, the Process Builder stands as a testament to the platform's commitment to providing powerful yet accessible tools for administrators. As organizations evolve, the Process Builder empowers administrators to adapt and innovate, ensuring their Salesforce environment remains a dynamic and responsive force within their broader business strategy.
User-Centric Automation: Enhancing Experiences with Flow Builder
In the realm of Salesforce automation, the focus on user experience has become increasingly paramount. Enter Flow Builder, a tool designed to empower administrators to create dynamic and user-friendly workflows within the Salesforce platform. Unlike traditional automation tools, Flow Builder provides a visual canvas for designing flows, making it accessible to administrators with diverse levels of technical expertise and enabling them to craft processes that prioritize the end-user experience.
Flow Builder serves as a catalyst for user-centric automation by offering a versatile set of features. Administrators can design flows that guide users through specific processes, collecting and updating data along the way. This visual, point-and-click tool enables the creation of interactive screens, allowing users to input information seamlessly and participate in complex workflows without the need for extensive training. By prioritizing ease of use, Flow Builder enhances user adoption and engagement within the Salesforce environment.
As organizations strive to optimize their Salesforce environments, the emphasis on user-centric automation becomes a strategic imperative. Flow Builder not only empowers administrators to design workflows that align with the unique needs of their users but also contributes to a more intuitive and enjoyable experience within the CRM platform. By prioritizing user-centric automation, organizations can ensure that their Salesforce environment not only meets business objectives but also fosters a positive and productive user experience.
Integration Strategies: Creating a Unified Automation Ecosystem
In the complex landscape of modern business operations, the seamless integration of Salesforce automation tools with external systems has become a critical aspect of maximizing efficiency and functionality. Integration strategies play a pivotal role in creating a unified automation ecosystem, allowing organizations to harness the collective power of Salesforce alongside other applications and databases.
A fundamental consideration in integration is the need to establish a cohesive environment where data flows seamlessly between Salesforce and external systems. This requires a strategic approach to connecting disparate platforms, ensuring that information is not only transferred accurately but also remains synchronized in real-time. Administrators must evaluate the specific requirements of their organization, identifying key touchpoints where integration can eliminate silos and enhance the overall workflow.
Salesforce's robust set of APIs and connectors facilitates integration with a wide array of third-party applications, ERPs, and databases. Whether it's synchronizing customer data, connecting with marketing automation platforms, or streamlining financial processes, the integration capabilities of Salesforce automation tools provide a foundation for creating a unified and interconnected automation ecosystem. This interconnectedness empowers organizations to leverage the strengths of different tools cohesively, enhancing the overall effectiveness of their business processes.
Integration strategies within the Salesforce automation landscape are pivotal in creating a unified automation ecosystem. Administrators equipped with a strategic mindset can leverage these integration capabilities to build a connected and responsive environment that optimizes business processes, fosters collaboration, and positions the organization for sustained success in an increasingly interconnected business landscape.
Optimizing Performance and Governance in Automation
Performance optimization begins with a meticulous evaluation of automation processes to identify potential bottlenecks and resource-intensive operations. Administrators must implement best practices, such as bulk processing and selective automation, to ensure that workflows operate efficiently, particularly in scenarios involving large datasets. Monitoring system performance metrics and employing tools like Salesforce Optimizer can further aid administrators in identifying areas for improvement and fine-tuning their automation processes.
Effective governance in automation involves setting up rules and policies that govern how data is manipulated and accessed within the Salesforce platform. This includes defining roles and permissions to restrict access to sensitive information, ensuring compliance with regulatory standards. Administrators must strike a balance between enabling automation to enhance productivity and maintaining governance to mitigate risks associated with data misuse or unauthorized access.
Governance mechanisms extend to version control and change management, ensuring that updates to automation processes are tracked, documented, and implemented in a controlled manner. Regular audits of automation configurations, periodic reviews of access controls, and adherence to Salesforce release management best practices contribute to a robust governance framework. This not only safeguards the integrity of automated processes but also instills confidence in users regarding the reliability and security of the Salesforce environment.
By embracing optimization and governance hand in hand, administrators can ensure that Salesforce automation tools not only enhance operational efficiency but also adhere to the highest standards of data security and compliance. Striking this delicate balance enables organizations to derive maximum value from their automated workflows while maintaining a stable and trustworthy Salesforce environment that aligns with business objectives and regulatory requirements.
How to obtain SALESFORCE ADMINISTRATION CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Salesforce Automation Tools provide administrators with a robust framework to drive innovation, efficiency, and user satisfaction within their organizations. By mastering the intricacies of workflow rules, Process Builder, Flow Builder, integration strategies, and optimization measures, administrators can not only streamline operations but also future-proof their Salesforce environments. The journey through this deep dive serves as a guide for administrators to not only harness the full potential of Salesforce automation but also become architects of transformative change within their organizations. Armed with this knowledge, administrators are well-equipped to navigate the ever-evolving landscape of CRM, ensuring that Salesforce remains a cornerstone in driving business success.
In the dynamic world of Salesforce Automation Tools, administrators play a pivotal role in shaping the efficiency and effectiveness of an organization's CRM strategy. This deep dive into the foundations, advanced features, user-centric approaches, integration strategies, and optimization measures underscores the multifaceted nature of Salesforce automation, providing administrators with a comprehensive toolkit to navigate the complexities of their roles.
As administrators chart their course through the Salesforce automation landscape, optimization strategies become paramount. Balancing performance enhancements with governance measures ensures that the automation ecosystem remains responsive, reliable, and compliant with data security standards. This delicate equilibrium is crucial for sustaining the long-term success of Salesforce implementations.
Navigating the CTFL Certification Journey: A Step-by-Step Guide
Embarking on the Certified Tester Foundation Level (CTFL) certification journey can be both an exciting and challenging endeavor for individuals aspiring to establish their expertise in software testing. In an ever-evolving technological landscape, where software quality is paramount, obtaining the CTFL certification is a valuable credential that demonstrates a comprehensive understanding of fundamental testing concepts and principles.
This step-by-step guide aims to provide aspiring candidates with a clear roadmap to navigate the CTFL certification journey successfully. From understanding the core concepts and objectives of the certification to preparing for the exam through effective study strategies, this guide aims to equip individuals with the necessary knowledge and skills to excel in the CTFL examination.
The CTFL certification, offered by the International Software Testing Qualifications Board (ISTQB), serves as a globally recognized standard for entry-level testing professionals. As organizations increasingly prioritize software quality and reliability, the demand for certified testers continues to grow. Therefore, this guide becomes an invaluable resource for those looking to differentiate themselves in the competitive field of software testing and enhance their career prospects.
Throughout this guide, we will delve into the key components of the CTFL certification process, offering insights into the examination structure, study materials, and recommended practices for effective preparation. By breaking down the journey into manageable steps, individuals can approach the certification process with confidence, ensuring a solid foundation in software testing principles that will serve them well throughout their careers.
Whether you are a recent graduate seeking to kickstart your career in software testing or an experienced professional looking to validate your expertise, this guide aims to be your companion in navigating the CTFL certification journey. As we explore each step, from understanding the exam syllabus to leveraging practical examples, our goal is to empower you with the knowledge and skills needed to succeed in obtaining the CTFL certification and establishing yourself as a competent and certified software tester.
Table of contents
-
Understanding the CTFL Certification Landscape
-
Decoding the CTFL Exam Structure
-
Effective Study Strategies for CTFL Success
-
Practical Application of CTFL Concepts
-
Navigating Challenges and Overcoming Exam Anxiety
-
Conclusion
Understanding the CTFL Certification Landscape
In the landscape of software testing, the Certified Tester Foundation Level (CTFL) certification stands as a beacon for individuals seeking to establish their competence in this critical domain. Understanding the CTFL certification landscape is paramount, as it not only validates one's knowledge but also serves as a globally recognized standard for entry-level testing professionals. In this section, we will delve into the significance of the CTFL certification within the software testing industry and explore the foundational concepts that make it a cornerstone for those aspiring to build a career in testing.
The CTFL certification, offered by the International Software Testing Qualifications Board (ISTQB), represents a comprehensive and standardized approach to testing methodologies and practices. Recognized across industries and geographical boundaries, it attests to an individual's proficiency in fundamental testing principles. As organizations increasingly prioritize the quality and reliability of their software products, the CTFL certification has become a valuable asset for professionals seeking to distinguish themselves in the competitive field of software testing.
For individuals contemplating the CTFL certification, grasping the broader landscape involves recognizing the doors it opens for career growth and advancement. Aspiring testers can expect to gain a foundational understanding of testing concepts, positioning themselves as valuable contributors to software quality assurance initiatives. Whether you are a recent graduate or a seasoned professional, comprehending the significance of the CTFL certification sets the stage for a purposeful and rewarding journey toward becoming a certified software tester.
Decoding the CTFL Exam Structure
Decoding the CTFL exam structure is a crucial step in preparing for success in this certification journey. The CTFL exam is designed to evaluate a candidate's understanding of fundamental testing concepts, and a thorough understanding of its structure is essential for effective preparation. In this section, we will dissect the key components of the CTFL exam, providing insights into its format, question types, and the skills assessed to empower candidates with the knowledge needed to navigate the examination confidently.
The CTFL exam typically consists of multiple-choice questions that assess a candidate's knowledge across various testing domains. Understanding the distribution of questions across these domains is essential for creating a well-rounded study plan. Typically, the exam covers areas such as testing fundamentals, testing levels, test design techniques, and static testing, among others. Decoding the weightage of each domain ensures that candidates allocate their study time effectively based on the importance of each topic in the examination.
Decoding the CTFL exam structure is akin to unraveling the blueprint of success. By comprehending the distribution of topics, time constraints, and question types, candidates can fine-tune their preparation strategies, ensuring a comprehensive and targeted approach. As we delve into this section, aspiring CTFL candidates will gain valuable insights to navigate the exam structure and optimize their performance on the path to certification success.
Effective Study Strategies for CTFL Success
Navigating the CTFL certification journey requires not only a deep understanding of testing concepts but also effective study strategies to ensure success. In this section, we will delve into proven methods and recommendations that aspiring candidates can adopt to optimize their preparation for the CTFL exam. A well-structured study plan is fundamental to mastering the diverse topics covered in the CTFL syllabus and building the confidence needed to excel on exam day.
To begin, aspiring CTFL candidates should gather a comprehensive set of study materials. This may include textbooks, online resources, practice exams, and any official ISTQB documentation. Creating a curated study resource library ensures that candidates have access to diverse learning materials that cater to their individual preferences and learning styles.
Organizing a study plan is equally crucial. Breaking down the CTFL syllabus into manageable sections and allocating specific timeframes for each topic helps candidates maintain a structured approach to their preparation. Consistency is key, and a well-paced study plan ensures that candidates cover all essential areas without feeling overwhelmed.
Engaging in active learning methods is another effective strategy. Instead of passively reading through materials, candidates should actively participate in exercises, discussions, and practical applications of testing concepts. This hands-on approach enhances understanding and retention, allowing for a more profound grasp of the material.
Effective study strategies for CTFL success involve a combination of resourcefulness, organization, active learning, practice, and collaboration. As candidates embrace these strategies, they pave the way for a thorough and confident preparation, ensuring that they are well-equipped to tackle the challenges presented by the CTFL certification journey.
Practical Application of CTFL Concepts
Understanding the practical application of Certified Tester Foundation Level (CTFL) concepts is essential for aspiring testing professionals to bridge the gap between theoretical knowledge and real-world scenarios. In this section, we will explore how the foundational principles covered in the CTFL syllabus are not just theoretical constructs but are, in fact, crucial tools for effective software testing in practical settings.
One key aspect of practical application involves illustrating how CTFL concepts align with the software development life cycle. From requirements gathering to design, implementation, testing, and maintenance, CTFL principles guide testing activities at every stage. By examining case studies and practical examples, candidates can gain insights into how these concepts are seamlessly integrated into the development process, ensuring the delivery of high-quality software products.
Furthermore, the application of CTFL concepts extends to test design techniques. Candidates will explore how to create effective test cases, select appropriate test data, and design tests that cover a range of scenarios. Real-world examples help candidates understand the importance of thorough test planning and execution in identifying and rectifying defects early in the software development life cycle.
This section aims to bridge the gap between theoretical knowledge and practical application by immersing candidates in real-world examples. By exploring how CTFL concepts are not abstract notions but are actively applied in software testing processes, aspiring testing professionals can develop a deeper understanding of the relevance and significance of the CTFL certification in their day-to-day roles. This practical application ensures that CTFL-certified individuals are well-prepared to contribute effectively to the enhancement of software quality within their professional environments.
Navigating Challenges and Overcoming Exam Anxiety
The process of overcoming challenges involves cultivating a positive mindset. Rather than viewing obstacles as insurmountable barriers, candidates should approach them as opportunities for growth and learning. Embracing a growth mindset fosters adaptability and resilience, enabling candidates to face challenges with determination and a belief in their capacity to improve. This mindset shift not only positively influences the preparation phase but also contributes to a more confident and composed demeanor during the actual exam.
It is crucial for candidates to recognize that seeking help is not a sign of weakness but a proactive measure towards success. If certain concepts prove particularly challenging, reaching out to tutors, instructors, or fellow candidates can provide valuable insights and clarification. Collaboration with peers can lead to a shared understanding of difficult topics, reinforcing the collective learning experience and diminishing individual apprehensions.
As candidates delve into the intricacies of the CTFL certification, they should also be mindful of maintaining a healthy work-life-study balance. Burning out due to prolonged study sessions without adequate breaks can hinder overall performance. Incorporating regular breaks, physical activities, and sufficient sleep into the routine contributes to improved concentration, memory retention, and overall well-being. A balanced lifestyle ensures that candidates approach their studies with refreshed energy, mitigating the risk of stress and burnout.
Additionally, candidates should capitalize on the diverse range of resources available. Exploring alternative study materials, participating in webinars, and utilizing online forums can offer varied perspectives and approaches to understanding CTFL concepts. The exposure to different learning styles can enrich the overall preparation process, making it more engaging and effective.
Navigating challenges and overcoming exam anxiety in the CTFL certification journey demands a holistic and proactive approach. By cultivating a positive mindset, seeking assistance when needed, maintaining a healthy balance, and leveraging a variety of resources, candidates can navigate the complexities of the certification process with resilience and confidence. This comprehensive strategy not only aids in exam preparation but also equips individuals with the skills and mindset necessary for a successful career in software testing.
How to obtain CTFL CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the journey towards achieving the Certified Tester Foundation Level (CTFL) certification is both rewarding and challenging, requiring a strategic and proactive approach. Understanding the significance of the CTFL certification in the software testing industry sets the stage for a purposeful pursuit of knowledge and professional development. Decoding the CTFL exam structure is essential for candidates to formulate effective study plans, enabling them to navigate the examination confidently.
Effective study strategies play a pivotal role in ensuring success in the CTFL certification journey. From comprehensive resource acquisition to the creation of structured study plans, candidates are equipped with the tools to master the diverse topics covered in the CTFL syllabus. Practical application of CTFL concepts further enhances the learning experience, illustrating how theoretical knowledge seamlessly integrates into real-world testing scenarios.
In navigating the CTFL certification journey, candidates are not merely preparing for an exam; they are investing in their expertise and credibility as software testing professionals. The culmination of effective study strategies, practical application of concepts, and resilience in overcoming challenges positions individuals not only for success in the CTFL examination but also for a fulfilling and impactful career in the dynamic field of software testing. By embracing the knowledge gained and the skills honed throughout this journey, individuals are well-prepared to contribute meaningfully to the pursuit of software quality and innovation in the ever-evolving landscape of technology.
Read More
Embarking on the Certified Tester Foundation Level (CTFL) certification journey can be both an exciting and challenging endeavor for individuals aspiring to establish their expertise in software testing. In an ever-evolving technological landscape, where software quality is paramount, obtaining the CTFL certification is a valuable credential that demonstrates a comprehensive understanding of fundamental testing concepts and principles.
This step-by-step guide aims to provide aspiring candidates with a clear roadmap to navigate the CTFL certification journey successfully. From understanding the core concepts and objectives of the certification to preparing for the exam through effective study strategies, this guide aims to equip individuals with the necessary knowledge and skills to excel in the CTFL examination.
The CTFL certification, offered by the International Software Testing Qualifications Board (ISTQB), serves as a globally recognized standard for entry-level testing professionals. As organizations increasingly prioritize software quality and reliability, the demand for certified testers continues to grow. Therefore, this guide becomes an invaluable resource for those looking to differentiate themselves in the competitive field of software testing and enhance their career prospects.
Throughout this guide, we will delve into the key components of the CTFL certification process, offering insights into the examination structure, study materials, and recommended practices for effective preparation. By breaking down the journey into manageable steps, individuals can approach the certification process with confidence, ensuring a solid foundation in software testing principles that will serve them well throughout their careers.
Whether you are a recent graduate seeking to kickstart your career in software testing or an experienced professional looking to validate your expertise, this guide aims to be your companion in navigating the CTFL certification journey. As we explore each step, from understanding the exam syllabus to leveraging practical examples, our goal is to empower you with the knowledge and skills needed to succeed in obtaining the CTFL certification and establishing yourself as a competent and certified software tester.
Table of contents
-
Understanding the CTFL Certification Landscape
-
Decoding the CTFL Exam Structure
-
Effective Study Strategies for CTFL Success
-
Practical Application of CTFL Concepts
-
Navigating Challenges and Overcoming Exam Anxiety
-
Conclusion
Understanding the CTFL Certification Landscape
In the landscape of software testing, the Certified Tester Foundation Level (CTFL) certification stands as a beacon for individuals seeking to establish their competence in this critical domain. Understanding the CTFL certification landscape is paramount, as it not only validates one's knowledge but also serves as a globally recognized standard for entry-level testing professionals. In this section, we will delve into the significance of the CTFL certification within the software testing industry and explore the foundational concepts that make it a cornerstone for those aspiring to build a career in testing.
The CTFL certification, offered by the International Software Testing Qualifications Board (ISTQB), represents a comprehensive and standardized approach to testing methodologies and practices. Recognized across industries and geographical boundaries, it attests to an individual's proficiency in fundamental testing principles. As organizations increasingly prioritize the quality and reliability of their software products, the CTFL certification has become a valuable asset for professionals seeking to distinguish themselves in the competitive field of software testing.
For individuals contemplating the CTFL certification, grasping the broader landscape involves recognizing the doors it opens for career growth and advancement. Aspiring testers can expect to gain a foundational understanding of testing concepts, positioning themselves as valuable contributors to software quality assurance initiatives. Whether you are a recent graduate or a seasoned professional, comprehending the significance of the CTFL certification sets the stage for a purposeful and rewarding journey toward becoming a certified software tester.
Decoding the CTFL Exam Structure
Decoding the CTFL exam structure is a crucial step in preparing for success in this certification journey. The CTFL exam is designed to evaluate a candidate's understanding of fundamental testing concepts, and a thorough understanding of its structure is essential for effective preparation. In this section, we will dissect the key components of the CTFL exam, providing insights into its format, question types, and the skills assessed to empower candidates with the knowledge needed to navigate the examination confidently.
The CTFL exam typically consists of multiple-choice questions that assess a candidate's knowledge across various testing domains. Understanding the distribution of questions across these domains is essential for creating a well-rounded study plan. Typically, the exam covers areas such as testing fundamentals, testing levels, test design techniques, and static testing, among others. Decoding the weightage of each domain ensures that candidates allocate their study time effectively based on the importance of each topic in the examination.
Decoding the CTFL exam structure is akin to unraveling the blueprint of success. By comprehending the distribution of topics, time constraints, and question types, candidates can fine-tune their preparation strategies, ensuring a comprehensive and targeted approach. As we delve into this section, aspiring CTFL candidates will gain valuable insights to navigate the exam structure and optimize their performance on the path to certification success.
Effective Study Strategies for CTFL Success
Navigating the CTFL certification journey requires not only a deep understanding of testing concepts but also effective study strategies to ensure success. In this section, we will delve into proven methods and recommendations that aspiring candidates can adopt to optimize their preparation for the CTFL exam. A well-structured study plan is fundamental to mastering the diverse topics covered in the CTFL syllabus and building the confidence needed to excel on exam day.
To begin, aspiring CTFL candidates should gather a comprehensive set of study materials. This may include textbooks, online resources, practice exams, and any official ISTQB documentation. Creating a curated study resource library ensures that candidates have access to diverse learning materials that cater to their individual preferences and learning styles.
Organizing a study plan is equally crucial. Breaking down the CTFL syllabus into manageable sections and allocating specific timeframes for each topic helps candidates maintain a structured approach to their preparation. Consistency is key, and a well-paced study plan ensures that candidates cover all essential areas without feeling overwhelmed.
Engaging in active learning methods is another effective strategy. Instead of passively reading through materials, candidates should actively participate in exercises, discussions, and practical applications of testing concepts. This hands-on approach enhances understanding and retention, allowing for a more profound grasp of the material.
Effective study strategies for CTFL success involve a combination of resourcefulness, organization, active learning, practice, and collaboration. As candidates embrace these strategies, they pave the way for a thorough and confident preparation, ensuring that they are well-equipped to tackle the challenges presented by the CTFL certification journey.
Practical Application of CTFL Concepts
Understanding the practical application of Certified Tester Foundation Level (CTFL) concepts is essential for aspiring testing professionals to bridge the gap between theoretical knowledge and real-world scenarios. In this section, we will explore how the foundational principles covered in the CTFL syllabus are not just theoretical constructs but are, in fact, crucial tools for effective software testing in practical settings.
One key aspect of practical application involves illustrating how CTFL concepts align with the software development life cycle. From requirements gathering to design, implementation, testing, and maintenance, CTFL principles guide testing activities at every stage. By examining case studies and practical examples, candidates can gain insights into how these concepts are seamlessly integrated into the development process, ensuring the delivery of high-quality software products.
Furthermore, the application of CTFL concepts extends to test design techniques. Candidates will explore how to create effective test cases, select appropriate test data, and design tests that cover a range of scenarios. Real-world examples help candidates understand the importance of thorough test planning and execution in identifying and rectifying defects early in the software development life cycle.
This section aims to bridge the gap between theoretical knowledge and practical application by immersing candidates in real-world examples. By exploring how CTFL concepts are not abstract notions but are actively applied in software testing processes, aspiring testing professionals can develop a deeper understanding of the relevance and significance of the CTFL certification in their day-to-day roles. This practical application ensures that CTFL-certified individuals are well-prepared to contribute effectively to the enhancement of software quality within their professional environments.
Navigating Challenges and Overcoming Exam Anxiety
The process of overcoming challenges involves cultivating a positive mindset. Rather than viewing obstacles as insurmountable barriers, candidates should approach them as opportunities for growth and learning. Embracing a growth mindset fosters adaptability and resilience, enabling candidates to face challenges with determination and a belief in their capacity to improve. This mindset shift not only positively influences the preparation phase but also contributes to a more confident and composed demeanor during the actual exam.
It is crucial for candidates to recognize that seeking help is not a sign of weakness but a proactive measure towards success. If certain concepts prove particularly challenging, reaching out to tutors, instructors, or fellow candidates can provide valuable insights and clarification. Collaboration with peers can lead to a shared understanding of difficult topics, reinforcing the collective learning experience and diminishing individual apprehensions.
As candidates delve into the intricacies of the CTFL certification, they should also be mindful of maintaining a healthy work-life-study balance. Burning out due to prolonged study sessions without adequate breaks can hinder overall performance. Incorporating regular breaks, physical activities, and sufficient sleep into the routine contributes to improved concentration, memory retention, and overall well-being. A balanced lifestyle ensures that candidates approach their studies with refreshed energy, mitigating the risk of stress and burnout.
Additionally, candidates should capitalize on the diverse range of resources available. Exploring alternative study materials, participating in webinars, and utilizing online forums can offer varied perspectives and approaches to understanding CTFL concepts. The exposure to different learning styles can enrich the overall preparation process, making it more engaging and effective.
Navigating challenges and overcoming exam anxiety in the CTFL certification journey demands a holistic and proactive approach. By cultivating a positive mindset, seeking assistance when needed, maintaining a healthy balance, and leveraging a variety of resources, candidates can navigate the complexities of the certification process with resilience and confidence. This comprehensive strategy not only aids in exam preparation but also equips individuals with the skills and mindset necessary for a successful career in software testing.
How to obtain CTFL CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the journey towards achieving the Certified Tester Foundation Level (CTFL) certification is both rewarding and challenging, requiring a strategic and proactive approach. Understanding the significance of the CTFL certification in the software testing industry sets the stage for a purposeful pursuit of knowledge and professional development. Decoding the CTFL exam structure is essential for candidates to formulate effective study plans, enabling them to navigate the examination confidently.
Effective study strategies play a pivotal role in ensuring success in the CTFL certification journey. From comprehensive resource acquisition to the creation of structured study plans, candidates are equipped with the tools to master the diverse topics covered in the CTFL syllabus. Practical application of CTFL concepts further enhances the learning experience, illustrating how theoretical knowledge seamlessly integrates into real-world testing scenarios.
In navigating the CTFL certification journey, candidates are not merely preparing for an exam; they are investing in their expertise and credibility as software testing professionals. The culmination of effective study strategies, practical application of concepts, and resilience in overcoming challenges positions individuals not only for success in the CTFL examination but also for a fulfilling and impactful career in the dynamic field of software testing. By embracing the knowledge gained and the skills honed throughout this journey, individuals are well-prepared to contribute meaningfully to the pursuit of software quality and innovation in the ever-evolving landscape of technology.
The Impact of Artificial Intelligence on Digital Marketing Campaigns
The rapid evolution of technology has ushered in an era where Artificial Intelligence (AI) plays a pivotal role in transforming various industries, and one such domain experiencing significant change is digital marketing. As businesses navigate the dynamic landscape of online interactions, consumer behavior, and data analytics, AI has emerged as a powerful ally in optimizing and enhancing digital marketing campaigns. This synergy between AI and digital marketing holds the potential to revolutionize the way companies connect with their target audiences, streamline processes, and achieve unprecedented levels of efficiency.
At its core, AI empowers digital marketers with the ability to leverage data-driven insights and predictive analytics, allowing for more accurate and personalized targeting. Through machine learning algorithms, AI analyzes vast datasets to discern patterns and trends, providing marketers with valuable information about consumer preferences, behaviors, and purchasing patterns. This newfound understanding enables businesses to create highly targeted and relevant content, delivering a more personalized and engaging experience to their audience. Consequently, AI-driven digital marketing campaigns have the potential to significantly improve customer satisfaction and loyalty.
As AI continues to evolve, the integration of technologies like natural language processing and chatbots further revolutionizes the way brands interact with consumers. Chatbots powered by AI can engage in real-time conversations, addressing customer queries, providing information, and even facilitating transactions. This not only enhances customer engagement but also ensures a seamless and responsive communication channel, fostering a positive brand image.
The impact of artificial intelligence on digital marketing campaigns is profound and multifaceted. From data-driven insights and predictive analytics to automation and personalized interactions, AI is reshaping the landscape of digital marketing, offering new possibilities and efficiencies for businesses. As the technology continues to advance, striking the right balance between innovation and ethical considerations will be key to unlocking the full potential of AI in digital marketing.
Table of contents
-
Personalization through AI in Digital Marketing
-
Automation and Operational Efficiency
-
Enhancing Customer Engagement with AI-Powered Chatbots
-
Ethical Considerations in AI-Driven Digital Marketing
-
Measuring and Analyzing AI-Enhanced Marketing Performance
-
Conclusion
Personalization through AI in Digital Marketing
The advent of Artificial Intelligence (AI) has ushered in a new era of personalization in the realm of digital marketing, fundamentally altering the way businesses engage with their target audiences. At the heart of this transformation lies the capability of AI, particularly machine learning algorithms, to analyze vast datasets and derive actionable insights about individual consumer behavior. This level of granular understanding enables marketers to create highly personalized and targeted content that resonates with the unique preferences and interests of each consumer.
AI-driven personalization in digital marketing goes beyond traditional demographic segmentation. Instead, it focuses on the analysis of real-time data, online behaviors, and previous interactions to tailor marketing messages at an individual level. Through predictive analytics, AI can anticipate consumer needs, preferences, and even the likelihood of specific actions, allowing marketers to deliver timely and relevant content that significantly enhances the user experience.
One of the key benefits of AI-powered personalization is the ability to create dynamic and adaptive content. By continuously learning from user interactions, AI algorithms can optimize content in real-time, ensuring that marketing messages remain current and resonate with the evolving preferences of the audience. This dynamic adaptation contributes to increased engagement and, ultimately, a higher likelihood of conversion.
Moreover, personalization through AI extends beyond content customization to include personalized recommendations and product offerings. E-commerce platforms, for example, leverage AI algorithms to analyze past purchase history and user behavior, providing customers with tailored product recommendations. This not only facilitates a more efficient and enjoyable shopping experience but also enhances the likelihood of cross-selling and upselling opportunities.
Automation and Operational Efficiency
The infusion of Artificial Intelligence (AI) into digital marketing has brought about a profound transformation in operational efficiency, reshaping the way marketing tasks are executed and optimizing resource allocation. At its core, AI-driven automation is revolutionizing how marketing teams handle repetitive and time-consuming tasks. This shift is particularly evident in data analysis, where machine learning algorithms can swiftly process vast datasets, providing real-time insights and empowering marketers to make informed decisions with unparalleled efficiency.
One of the central advantages of automation in digital marketing is its capacity to liberate marketing professionals from mundane activities, allowing them to redirect their focus toward strategic endeavors. Routine tasks such as email marketing, social media posting, and ad placement can be automated, enabling teams to dedicate more time and creativity to high-level aspects of campaign management. This not only enhances overall efficiency but also fosters an environment conducive to strategic thinking and innovation within marketing departments.
AI-driven automation not only expedites tasks but also enhances the agility and responsiveness of marketing campaigns. Machine learning algorithms adapt to changing market conditions and consumer behaviors in real-time, facilitating rapid adjustments to marketing strategies. In an era where the digital landscape evolves swiftly, this dynamic responsiveness ensures that campaigns remain relevant and effective.
Moreover, the impact of AI-driven automation extends to the realm of personalization, allowing marketers to tailor content and experiences for individual consumers. By analyzing user behaviors and preferences, AI algorithms can deliver highly targeted and relevant content, cultivating a more profound connection between brands and their audiences. This heightened level of personalization contributes not only to increased customer engagement but also to higher conversion rates.
As marketing campaigns become increasingly intricate, AI-driven automation facilitates comprehensive campaign orchestration. Marketers can seamlessly integrate various channels, ensuring a synchronized approach across platforms. This holistic perspective enables marketers to track the customer journey more accurately, identify crucial touchpoints, and allocate resources effectively.
The integration of AI-driven automation in digital marketing not only enhances operational efficiency but also redefines customer engagement and campaign management. A thoughtful and ethical approach ensures that AI becomes an enabler, fostering a harmonious relationship between human creativity and AI capabilities in the pursuit of marketing excellence.
Enhancing Customer Engagement with AI-Powered Chatbots
The landscape of customer engagement has undergone a transformative shift with the integration of Artificial Intelligence (AI), particularly through the implementation of AI-powered chatbots. These intelligent conversational agents are revolutionizing the way businesses interact with their customers, providing real-time communication and personalized assistance. At the forefront of this change is the ability of AI-powered chatbots to engage with users in natural language, facilitating seamless and instant communication.
One of the key contributions of AI-powered chatbots to customer engagement lies in their availability and responsiveness. Unlike traditional customer service channels that operate within specific hours, chatbots are available 24/7, providing customers with immediate assistance whenever they require it. This around-the-clock availability not only enhances customer satisfaction but also addresses issues promptly, contributing to a positive overall customer experience.
Moreover, AI-powered chatbots excel in handling routine and frequently asked queries, allowing human customer service representatives to focus on more complex and nuanced issues. By automating these routine tasks, chatbots streamline the customer support process, reducing response times and increasing efficiency. This ensures that customers receive quick and accurate information, leading to improved satisfaction and a more positive perception of the brand.
The personalization capabilities of AI-powered chatbots further elevate customer engagement. These chatbots can analyze customer data, past interactions, and preferences to tailor responses and recommendations. This level of personalization not only enhances the relevance of interactions but also contributes to a more individualized and customer-centric experience, fostering a deeper connection between the customer and the brand.
AI-powered chatbots are reshaping the landscape of customer engagement by providing instantaneous, personalized, and efficient interactions. As businesses continue to adopt these intelligent conversational agents, the focus remains on optimizing customer experiences, building brand loyalty, and staying at the forefront of technological advancements in customer service.
Ethical Considerations in AI-Driven Digital Marketing
As Artificial Intelligence (AI) becomes increasingly integrated into digital marketing strategies, a critical dimension that demands careful attention is the ethical considerations surrounding its implementation. Ethical concerns in AI-driven digital marketing encompass a range of issues, including user privacy, responsible data usage, and the potential biases embedded in algorithms.
One of the foremost ethical considerations is the protection of user privacy. As AI algorithms analyze vast amounts of data to generate insights and personalize marketing content, there is a heightened risk of infringing on individual privacy. Marketers must be vigilant in adhering to data protection regulations, obtaining informed consent, and ensuring that user information is handled with the utmost security to build and maintain trust with consumers.
Responsible data usage is another ethical imperative in AI-driven digital marketing. Collecting and utilizing consumer data should be done transparently and ethically. It is essential to strike a balance between personalization for improved user experiences and avoiding the exploitation of sensitive information. Marketers must communicate clearly about the data they collect, how it will be used, and provide users with options to control their preferences.
Biases in AI algorithms present a complex ethical challenge. Machine learning models learn from historical data, which may contain biases. If these biases are not identified and addressed, AI-driven marketing campaigns can inadvertently perpetuate or amplify existing societal prejudices. Businesses must invest in diverse and inclusive datasets, regularly audit algorithms for biases, and implement measures to correct and prevent discriminatory outcomes to ensure fair and equitable treatment for all users.
Transparency is a cornerstone of ethical AI in digital marketing. Marketers should be open about the use of AI in their campaigns, communicating to consumers how algorithms influence content recommendations, personalization, and decision-making processes. Transparent practices build trust, empowering users to make informed choices about their engagement with digital platforms.
Measuring and Analyzing AI-Enhanced Marketing Performance
The integration of Artificial Intelligence (AI) into digital marketing has ushered in a new era of sophisticated measurement and analysis of marketing performance. The capabilities of AI go beyond traditional metrics, offering marketers powerful tools to gain deeper insights into campaign effectiveness, consumer behavior, and overall ROI. The use of AI for measuring and analyzing marketing performance contributes to a more data-driven and strategic approach to decision-making.
One of the primary benefits of AI in marketing performance analysis is its ability to process and interpret vast datasets at an unprecedented speed. Machine learning algorithms can sift through large volumes of data, identifying patterns and correlations that may be elusive to human analysis. This enables marketers to gain a comprehensive understanding of consumer behavior, preferences, and the impact of various marketing initiatives on key performance indicators (KPIs).
Predictive analytics, powered by AI, plays a pivotal role in forecasting future trends and outcomes based on historical data. Marketers can leverage these insights to optimize campaign strategies, allocate resources more efficiently, and proactively address potential challenges. The predictive capabilities of AI contribute to a more agile and adaptive approach to marketing, ensuring that campaigns are not only responsive to current trends but also well-positioned for future success.
AI-enhanced marketing performance measurement represents a significant leap forward in the digital marketing landscape. The ability to harness the power of AI for data analysis and predictive insights empowers marketers to make informed decisions, optimize campaigns, and deliver more personalized and impactful experiences to their target audience. As technology continues to advance, the synergy between human expertise and AI capabilities will be essential for unlocking the full potential of data-driven marketing strategies.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Digital Marketing : Digital Marketing Certification
Conclusion
In conclusion, the impact of Artificial Intelligence (AI) on digital marketing campaigns is undeniably transformative, touching various aspects of strategy, execution, and customer engagement. AI's ability to analyze vast datasets, personalize content, and automate tasks has ushered in a new era of efficiency and innovation in the digital marketing landscape.
Personalization through AI has elevated the customer experience, allowing businesses to tailor their content and recommendations with unprecedented precision. This not only enhances engagement but also contributes to building stronger and more meaningful connections with the target audience. The efficiency gains from automation have liberated marketers from routine tasks, enabling them to focus on strategic thinking and creative endeavors. From data analysis to social media management, AI-driven automation streamlines processes and ensures campaigns remain agile and responsive to dynamic market conditions.
The integration of AI-powered chatbots has revolutionized customer engagement by providing instant and personalized interactions. These intelligent conversational agents operate around the clock, offering real-time assistance and contributing to enhanced customer satisfaction. However, it is crucial to maintain a balance between automation and the human touch, preserving the authenticity that is vital for genuine customer relationships.
As AI becomes an integral part of digital marketing, ethical considerations take center stage. Protecting user privacy, ensuring responsible data usage, and addressing biases in algorithms are paramount. Transparent communication about AI usage and fostering a commitment to ethical practices are essential for building and maintaining trust with consumers.
Read More
The rapid evolution of technology has ushered in an era where Artificial Intelligence (AI) plays a pivotal role in transforming various industries, and one such domain experiencing significant change is digital marketing. As businesses navigate the dynamic landscape of online interactions, consumer behavior, and data analytics, AI has emerged as a powerful ally in optimizing and enhancing digital marketing campaigns. This synergy between AI and digital marketing holds the potential to revolutionize the way companies connect with their target audiences, streamline processes, and achieve unprecedented levels of efficiency.
At its core, AI empowers digital marketers with the ability to leverage data-driven insights and predictive analytics, allowing for more accurate and personalized targeting. Through machine learning algorithms, AI analyzes vast datasets to discern patterns and trends, providing marketers with valuable information about consumer preferences, behaviors, and purchasing patterns. This newfound understanding enables businesses to create highly targeted and relevant content, delivering a more personalized and engaging experience to their audience. Consequently, AI-driven digital marketing campaigns have the potential to significantly improve customer satisfaction and loyalty.
As AI continues to evolve, the integration of technologies like natural language processing and chatbots further revolutionizes the way brands interact with consumers. Chatbots powered by AI can engage in real-time conversations, addressing customer queries, providing information, and even facilitating transactions. This not only enhances customer engagement but also ensures a seamless and responsive communication channel, fostering a positive brand image.
The impact of artificial intelligence on digital marketing campaigns is profound and multifaceted. From data-driven insights and predictive analytics to automation and personalized interactions, AI is reshaping the landscape of digital marketing, offering new possibilities and efficiencies for businesses. As the technology continues to advance, striking the right balance between innovation and ethical considerations will be key to unlocking the full potential of AI in digital marketing.
Table of contents
-
Personalization through AI in Digital Marketing
-
Automation and Operational Efficiency
-
Enhancing Customer Engagement with AI-Powered Chatbots
-
Ethical Considerations in AI-Driven Digital Marketing
-
Measuring and Analyzing AI-Enhanced Marketing Performance
-
Conclusion
Personalization through AI in Digital Marketing
The advent of Artificial Intelligence (AI) has ushered in a new era of personalization in the realm of digital marketing, fundamentally altering the way businesses engage with their target audiences. At the heart of this transformation lies the capability of AI, particularly machine learning algorithms, to analyze vast datasets and derive actionable insights about individual consumer behavior. This level of granular understanding enables marketers to create highly personalized and targeted content that resonates with the unique preferences and interests of each consumer.
AI-driven personalization in digital marketing goes beyond traditional demographic segmentation. Instead, it focuses on the analysis of real-time data, online behaviors, and previous interactions to tailor marketing messages at an individual level. Through predictive analytics, AI can anticipate consumer needs, preferences, and even the likelihood of specific actions, allowing marketers to deliver timely and relevant content that significantly enhances the user experience.
One of the key benefits of AI-powered personalization is the ability to create dynamic and adaptive content. By continuously learning from user interactions, AI algorithms can optimize content in real-time, ensuring that marketing messages remain current and resonate with the evolving preferences of the audience. This dynamic adaptation contributes to increased engagement and, ultimately, a higher likelihood of conversion.
Moreover, personalization through AI extends beyond content customization to include personalized recommendations and product offerings. E-commerce platforms, for example, leverage AI algorithms to analyze past purchase history and user behavior, providing customers with tailored product recommendations. This not only facilitates a more efficient and enjoyable shopping experience but also enhances the likelihood of cross-selling and upselling opportunities.
Automation and Operational Efficiency
The infusion of Artificial Intelligence (AI) into digital marketing has brought about a profound transformation in operational efficiency, reshaping the way marketing tasks are executed and optimizing resource allocation. At its core, AI-driven automation is revolutionizing how marketing teams handle repetitive and time-consuming tasks. This shift is particularly evident in data analysis, where machine learning algorithms can swiftly process vast datasets, providing real-time insights and empowering marketers to make informed decisions with unparalleled efficiency.
One of the central advantages of automation in digital marketing is its capacity to liberate marketing professionals from mundane activities, allowing them to redirect their focus toward strategic endeavors. Routine tasks such as email marketing, social media posting, and ad placement can be automated, enabling teams to dedicate more time and creativity to high-level aspects of campaign management. This not only enhances overall efficiency but also fosters an environment conducive to strategic thinking and innovation within marketing departments.
AI-driven automation not only expedites tasks but also enhances the agility and responsiveness of marketing campaigns. Machine learning algorithms adapt to changing market conditions and consumer behaviors in real-time, facilitating rapid adjustments to marketing strategies. In an era where the digital landscape evolves swiftly, this dynamic responsiveness ensures that campaigns remain relevant and effective.
Moreover, the impact of AI-driven automation extends to the realm of personalization, allowing marketers to tailor content and experiences for individual consumers. By analyzing user behaviors and preferences, AI algorithms can deliver highly targeted and relevant content, cultivating a more profound connection between brands and their audiences. This heightened level of personalization contributes not only to increased customer engagement but also to higher conversion rates.
As marketing campaigns become increasingly intricate, AI-driven automation facilitates comprehensive campaign orchestration. Marketers can seamlessly integrate various channels, ensuring a synchronized approach across platforms. This holistic perspective enables marketers to track the customer journey more accurately, identify crucial touchpoints, and allocate resources effectively.
The integration of AI-driven automation in digital marketing not only enhances operational efficiency but also redefines customer engagement and campaign management. A thoughtful and ethical approach ensures that AI becomes an enabler, fostering a harmonious relationship between human creativity and AI capabilities in the pursuit of marketing excellence.
Enhancing Customer Engagement with AI-Powered Chatbots
The landscape of customer engagement has undergone a transformative shift with the integration of Artificial Intelligence (AI), particularly through the implementation of AI-powered chatbots. These intelligent conversational agents are revolutionizing the way businesses interact with their customers, providing real-time communication and personalized assistance. At the forefront of this change is the ability of AI-powered chatbots to engage with users in natural language, facilitating seamless and instant communication.
One of the key contributions of AI-powered chatbots to customer engagement lies in their availability and responsiveness. Unlike traditional customer service channels that operate within specific hours, chatbots are available 24/7, providing customers with immediate assistance whenever they require it. This around-the-clock availability not only enhances customer satisfaction but also addresses issues promptly, contributing to a positive overall customer experience.
Moreover, AI-powered chatbots excel in handling routine and frequently asked queries, allowing human customer service representatives to focus on more complex and nuanced issues. By automating these routine tasks, chatbots streamline the customer support process, reducing response times and increasing efficiency. This ensures that customers receive quick and accurate information, leading to improved satisfaction and a more positive perception of the brand.
The personalization capabilities of AI-powered chatbots further elevate customer engagement. These chatbots can analyze customer data, past interactions, and preferences to tailor responses and recommendations. This level of personalization not only enhances the relevance of interactions but also contributes to a more individualized and customer-centric experience, fostering a deeper connection between the customer and the brand.
AI-powered chatbots are reshaping the landscape of customer engagement by providing instantaneous, personalized, and efficient interactions. As businesses continue to adopt these intelligent conversational agents, the focus remains on optimizing customer experiences, building brand loyalty, and staying at the forefront of technological advancements in customer service.
Ethical Considerations in AI-Driven Digital Marketing
As Artificial Intelligence (AI) becomes increasingly integrated into digital marketing strategies, a critical dimension that demands careful attention is the ethical considerations surrounding its implementation. Ethical concerns in AI-driven digital marketing encompass a range of issues, including user privacy, responsible data usage, and the potential biases embedded in algorithms.
One of the foremost ethical considerations is the protection of user privacy. As AI algorithms analyze vast amounts of data to generate insights and personalize marketing content, there is a heightened risk of infringing on individual privacy. Marketers must be vigilant in adhering to data protection regulations, obtaining informed consent, and ensuring that user information is handled with the utmost security to build and maintain trust with consumers.
Responsible data usage is another ethical imperative in AI-driven digital marketing. Collecting and utilizing consumer data should be done transparently and ethically. It is essential to strike a balance between personalization for improved user experiences and avoiding the exploitation of sensitive information. Marketers must communicate clearly about the data they collect, how it will be used, and provide users with options to control their preferences.
Biases in AI algorithms present a complex ethical challenge. Machine learning models learn from historical data, which may contain biases. If these biases are not identified and addressed, AI-driven marketing campaigns can inadvertently perpetuate or amplify existing societal prejudices. Businesses must invest in diverse and inclusive datasets, regularly audit algorithms for biases, and implement measures to correct and prevent discriminatory outcomes to ensure fair and equitable treatment for all users.
Transparency is a cornerstone of ethical AI in digital marketing. Marketers should be open about the use of AI in their campaigns, communicating to consumers how algorithms influence content recommendations, personalization, and decision-making processes. Transparent practices build trust, empowering users to make informed choices about their engagement with digital platforms.
Measuring and Analyzing AI-Enhanced Marketing Performance
The integration of Artificial Intelligence (AI) into digital marketing has ushered in a new era of sophisticated measurement and analysis of marketing performance. The capabilities of AI go beyond traditional metrics, offering marketers powerful tools to gain deeper insights into campaign effectiveness, consumer behavior, and overall ROI. The use of AI for measuring and analyzing marketing performance contributes to a more data-driven and strategic approach to decision-making.
One of the primary benefits of AI in marketing performance analysis is its ability to process and interpret vast datasets at an unprecedented speed. Machine learning algorithms can sift through large volumes of data, identifying patterns and correlations that may be elusive to human analysis. This enables marketers to gain a comprehensive understanding of consumer behavior, preferences, and the impact of various marketing initiatives on key performance indicators (KPIs).
Predictive analytics, powered by AI, plays a pivotal role in forecasting future trends and outcomes based on historical data. Marketers can leverage these insights to optimize campaign strategies, allocate resources more efficiently, and proactively address potential challenges. The predictive capabilities of AI contribute to a more agile and adaptive approach to marketing, ensuring that campaigns are not only responsive to current trends but also well-positioned for future success.
AI-enhanced marketing performance measurement represents a significant leap forward in the digital marketing landscape. The ability to harness the power of AI for data analysis and predictive insights empowers marketers to make informed decisions, optimize campaigns, and deliver more personalized and impactful experiences to their target audience. As technology continues to advance, the synergy between human expertise and AI capabilities will be essential for unlocking the full potential of data-driven marketing strategies.
How to obtain Digital Marketing Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Digital Marketing : Digital Marketing Certification
Conclusion
In conclusion, the impact of Artificial Intelligence (AI) on digital marketing campaigns is undeniably transformative, touching various aspects of strategy, execution, and customer engagement. AI's ability to analyze vast datasets, personalize content, and automate tasks has ushered in a new era of efficiency and innovation in the digital marketing landscape.
Personalization through AI has elevated the customer experience, allowing businesses to tailor their content and recommendations with unprecedented precision. This not only enhances engagement but also contributes to building stronger and more meaningful connections with the target audience. The efficiency gains from automation have liberated marketers from routine tasks, enabling them to focus on strategic thinking and creative endeavors. From data analysis to social media management, AI-driven automation streamlines processes and ensures campaigns remain agile and responsive to dynamic market conditions.
The integration of AI-powered chatbots has revolutionized customer engagement by providing instant and personalized interactions. These intelligent conversational agents operate around the clock, offering real-time assistance and contributing to enhanced customer satisfaction. However, it is crucial to maintain a balance between automation and the human touch, preserving the authenticity that is vital for genuine customer relationships.
As AI becomes an integral part of digital marketing, ethical considerations take center stage. Protecting user privacy, ensuring responsible data usage, and addressing biases in algorithms are paramount. Transparent communication about AI usage and fostering a commitment to ethical practices are essential for building and maintaining trust with consumers.
How Much Does CCBA Certification Cost in 2024
Business analysis certifications have become increasingly vital in 2024, with professionals seeking to validate their expertise in a competitive job market. The cost of obtaining these certifications can vary based on factors such as membership status, chosen testing venue, and the inclusion of course materials. Typically, the expenses cover application, testing, and relevant study materials.
Investing in a business analysis certification, like CCBA, proves to be a strategic move for individuals in the field. This certification serves as a tangible demonstration of a professional's skills and in-depth knowledge in business assessment, reinforcing their credibility among peers and employers.
Beyond the immediate recognition, CCBA certification significantly impacts career prospects. It opens doors to new opportunities, often leading to higher salaries and expanded job responsibilities. Professionals holding a CCBA certificate are better positioned for career advancement, as employers increasingly recognize the value of hiring individuals with proven expertise in business analysis.
Moreover, CCBA certification reflects a commitment to ongoing professional development and a dedication to improving one's performance. This commitment not only boosts confidence but also provides a competitive edge in the job market. Employers actively seek out certified individuals, understanding that they bring a heightened level of competence and proficiency to the workplace. In essence, the investment in a CCBA certification is a strategic step towards long-term career success in the dynamic field of business analysis.
In this article
-
What is CCBA Certification?
-
CCBA Certification Eligibility
-
What is CCBA Certification Cost?
-
CCBA Region-wise Certification Cost
-
Benefits of CCBA Certification
-
Conclusion
-
Frequently Asked Questions (FAQs)
What is CCBA Certification?
CCBA, or the Certification of Capability in Business Analysis, is a professional certification offered by the International Institute of Business Analysis (IIBA). It is designed to recognize individuals who demonstrate a solid understanding of business analysis principles and practices. The CCBA certification is particularly geared towards professionals with a few years of practical business analysis experience, aiming to validate and enhance their skills.
To attain CCBA certification, candidates must meet specific eligibility criteria, including a minimum number of hours of hands-on business analysis work experience. They are also required to have completed a certain number of professional development hours in related areas. Once the eligibility criteria are met, candidates can proceed with the application process, which involves submitting their educational and work experience details for verification.
The CCBA certification exam assesses candidates on their comprehension of key business analysis concepts, tools, and techniques. Successful completion of the exam indicates a candidate's ability to analyze and evaluate business needs, facilitating effective communication between stakeholders, and contributing to overall project success.
Holding a CCBA certification not only validates a professional's expertise in business analysis but also demonstrates a commitment to ongoing professional development and adherence to industry-recognized standards. It is a valuable credential for individuals seeking to advance their careers in the field of business analysis, providing a benchmark of excellence that is recognized globally. Overall, CCBA certification serves as a significant milestone in the career progression of business analysts, helping them stand out in a competitive and dynamic professional landscape.
CCBA Certification Eligibility
CCBA (Certification of Capability in Business Analysis) is a distinguished certification offered by the International Institute of Business Analysis (IIBA), and achieving this credential requires meeting specific eligibility criteria. To be eligible for the CCBA certification, candidates must have a minimum of 3,750 hours of business analysis work experience within the last seven years. This work experience should align with the Business Analysis Body of Knowledge (BABOK) Guide, which is a comprehensive framework outlining the fundamental knowledge areas in business analysis.
In addition to the hands-on experience, candidates must also have completed a minimum of 21 hours of Professional Development in the last four years. These professional development hours contribute to the ongoing education and skill enhancement of business analysts, ensuring that candidates are up-to-date with the latest industry trends and best practices.
Once the eligibility criteria are met, candidates can proceed with the application process. This involves submitting details about their educational background, work experience, and professional development hours. It's important to note that the IIBA carefully reviews and verifies the information provided during the application process to ensure that candidates meet the stringent standards set for CCBA certification.
By adhering to these eligibility requirements, candidates demonstrate their commitment to the profession and their dedication to mastering the core competencies of business analysis. The CCBA certification, therefore, not only signifies a certain level of expertise but also underscores a candidate's practical experience and ongoing commitment to professional development in the dynamic field of business analysis.
What is CCBA Certification Cost?
The cost of obtaining CCBA (Certification of Capability in Business Analysis) certification encompasses several factors, making it essential for aspiring candidates to plan their investment strategically. The CCBA certification cost varies based on factors such as membership status, testing venue, and the inclusion of course materials. The International Institute of Business Analysis (IIBA) typically charges fees for the application process, the certification exam, and any associated study materials.
The application fee is a one-time expense that covers the evaluation of a candidate's eligibility for the CCBA certification. This fee may vary for IIBA members and non-members, with members often enjoying discounted rates. Once the application is approved, candidates can proceed to the next stage, which involves the examination.
The CCBA certification exam fee is another component of the overall cost. Similar to the application fee, this cost may differ for IIBA members and non-members. The exam fee reflects the investment required to undergo the rigorous assessment that evaluates a candidate's knowledge and proficiency in business analysis according to the standards outlined in the Business Analysis Body of Knowledge (BABOK) Guide.
Candidates should also consider potential expenses related to study materials, such as preparation guides and practice exams, which can aid in the successful completion of the CCBA exam. These materials are often available for purchase separately or may be included in a comprehensive exam preparation package.
While the exact CCBA certification cost can vary, it's crucial for candidates to view it as an investment in their professional development. The certification not only validates their skills in business analysis but also enhances their career prospects by opening doors to new opportunities, higher salaries, and increased responsibilities. Aspiring business analysts should carefully weigh the costs against the potential benefits of obtaining CCBA certification, recognizing it as a strategic step toward advancing their careers in the field.
CCBA Region-wise Certification Cost
As of my last knowledge update in January 2022, the specific region-wise certification cost for CCBA (Certification of Capability in Business Analysis) may not be readily available due to variations and updates. The International Institute of Business Analysis (IIBA) often establishes standardized fees for its certifications; however, these fees may differ for IIBA members and non-members.
Typically, IIBA membership offers certain benefits, including discounted rates for certification fees. It's important for individuals considering CCBA certification to review the latest fee structure on the official IIBA website or contact the IIBA directly for the most accurate and up-to-date information. The certification cost can also vary based on factors such as testing venue, application process, and the inclusion of study materials.
IIBA is a global organization, and its certification fees are usually consistent across various regions. However, local taxes, currency exchange rates, and other regional factors can influence the overall cost for candidates in different parts of the world. To obtain precise and region-specific details, individuals are advised to consult the IIBA's official resources or reach out to their local IIBA chapters.
While CCBA certification fees are generally standardized by the IIBA, candidates should be aware of potential variations based on membership status and regional factors. Accessing the latest information directly from the IIBA ensures accurate and current details regarding the certification cost, allowing individuals to plan their certification journey effectively and make informed decisions about their investment in professional development.
Benefits of CCBA Certification
Earning the Certification of Capability in Business Analysis (CCBA) comes with a myriad of benefits that extend beyond the validation of one's skills. One of the foremost advantages is the recognition of a professional's proficiency in business analysis. CCBA certification serves as a formal acknowledgment of an individual's understanding of key concepts, methodologies, and best practices in the field, as outlined in the Business Analysis Body of Knowledge (BABOK) Guide.
The CCBA designation enhances career prospects significantly. It opens doors to new opportunities by signaling to employers that the certified individual possesses a comprehensive skill set and is well-equipped to contribute effectively to business analysis initiatives. This, in turn, often leads to higher salaries and increased responsibilities, positioning CCBA-certified professionals for career advancement.
Moreover, CCBA certification demonstrates a commitment to ongoing professional development. The certification process involves rigorous preparation and the accumulation of professional development hours, showcasing a dedication to staying current with industry trends. This commitment not only boosts the individual's confidence but also establishes credibility among peers and employers.
In the competitive job market, having a CCBA certification provides a distinct advantage. Employers recognize the value of certified business analysts and appreciate the standardized knowledge and skill set that comes with the certification. CCBA-certified professionals stand out as reliable contributors to projects and initiatives, making them sought-after assets in the workforce.
Beyond individual benefits, CCBA certification also contributes to the overall maturation and standardization of the business analysis profession. It sets a benchmark for excellence and encourages a culture of continuous improvement within the industry. As a globally recognized certification, CCBA elevates the status of business analysts and promotes the importance of their role in driving successful business outcomes. In essence, the benefits of CCBA certification extend far beyond personal and professional gains, positively impacting both individuals and the broader business analysis community.
How to obtain CCBA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, pursuing the Certification of Capability in Business Analysis (CCBA) is a strategic investment for professionals in the field, offering a range of tangible and intangible benefits. The rigorous certification process not only validates the skills and knowledge of business analysts but also enhances their career prospects. The CCBA designation serves as a powerful signal to employers, indicating a commitment to excellence and a readiness to contribute effectively to business analysis initiatives.
The financial investment required for CCBA certification, encompassing application fees, exam fees, and potential study material costs, should be viewed as a valuable step toward personal and professional development. The return on this investment is evident in the form of increased job opportunities, higher earning potential, and greater responsibilities within the workplace.
Beyond individual gains, CCBA certification contributes to the overall advancement of the business analysis profession. It sets a standard for excellence, fostering a culture of continuous improvement and reinforcing the importance of well-qualified business analysts in driving successful business outcomes. The global recognition of CCBA certification further underscores its significance, positioning certified professionals as valuable assets in a competitive job market.
As professionals consider their career trajectories and seek avenues for growth, CCBA certification stands out as a pivotal milestone. It not only validates their expertise but also aligns them with a community of skilled practitioners dedicated to elevating the standards of business analysis. In essence, CCBA certification is more than a credential; it is a gateway to enhanced professional standing, increased opportunities, and a lasting impact on the dynamic field of business analysis.
Read More
Business analysis certifications have become increasingly vital in 2024, with professionals seeking to validate their expertise in a competitive job market. The cost of obtaining these certifications can vary based on factors such as membership status, chosen testing venue, and the inclusion of course materials. Typically, the expenses cover application, testing, and relevant study materials.
Investing in a business analysis certification, like CCBA, proves to be a strategic move for individuals in the field. This certification serves as a tangible demonstration of a professional's skills and in-depth knowledge in business assessment, reinforcing their credibility among peers and employers.
Beyond the immediate recognition, CCBA certification significantly impacts career prospects. It opens doors to new opportunities, often leading to higher salaries and expanded job responsibilities. Professionals holding a CCBA certificate are better positioned for career advancement, as employers increasingly recognize the value of hiring individuals with proven expertise in business analysis.
Moreover, CCBA certification reflects a commitment to ongoing professional development and a dedication to improving one's performance. This commitment not only boosts confidence but also provides a competitive edge in the job market. Employers actively seek out certified individuals, understanding that they bring a heightened level of competence and proficiency to the workplace. In essence, the investment in a CCBA certification is a strategic step towards long-term career success in the dynamic field of business analysis.
In this article
-
What is CCBA Certification?
-
CCBA Certification Eligibility
-
What is CCBA Certification Cost?
-
CCBA Region-wise Certification Cost
-
Benefits of CCBA Certification
-
Conclusion
-
Frequently Asked Questions (FAQs)
What is CCBA Certification?
CCBA, or the Certification of Capability in Business Analysis, is a professional certification offered by the International Institute of Business Analysis (IIBA). It is designed to recognize individuals who demonstrate a solid understanding of business analysis principles and practices. The CCBA certification is particularly geared towards professionals with a few years of practical business analysis experience, aiming to validate and enhance their skills.
To attain CCBA certification, candidates must meet specific eligibility criteria, including a minimum number of hours of hands-on business analysis work experience. They are also required to have completed a certain number of professional development hours in related areas. Once the eligibility criteria are met, candidates can proceed with the application process, which involves submitting their educational and work experience details for verification.
The CCBA certification exam assesses candidates on their comprehension of key business analysis concepts, tools, and techniques. Successful completion of the exam indicates a candidate's ability to analyze and evaluate business needs, facilitating effective communication between stakeholders, and contributing to overall project success.
Holding a CCBA certification not only validates a professional's expertise in business analysis but also demonstrates a commitment to ongoing professional development and adherence to industry-recognized standards. It is a valuable credential for individuals seeking to advance their careers in the field of business analysis, providing a benchmark of excellence that is recognized globally. Overall, CCBA certification serves as a significant milestone in the career progression of business analysts, helping them stand out in a competitive and dynamic professional landscape.
CCBA Certification Eligibility
CCBA (Certification of Capability in Business Analysis) is a distinguished certification offered by the International Institute of Business Analysis (IIBA), and achieving this credential requires meeting specific eligibility criteria. To be eligible for the CCBA certification, candidates must have a minimum of 3,750 hours of business analysis work experience within the last seven years. This work experience should align with the Business Analysis Body of Knowledge (BABOK) Guide, which is a comprehensive framework outlining the fundamental knowledge areas in business analysis.
In addition to the hands-on experience, candidates must also have completed a minimum of 21 hours of Professional Development in the last four years. These professional development hours contribute to the ongoing education and skill enhancement of business analysts, ensuring that candidates are up-to-date with the latest industry trends and best practices.
Once the eligibility criteria are met, candidates can proceed with the application process. This involves submitting details about their educational background, work experience, and professional development hours. It's important to note that the IIBA carefully reviews and verifies the information provided during the application process to ensure that candidates meet the stringent standards set for CCBA certification.
By adhering to these eligibility requirements, candidates demonstrate their commitment to the profession and their dedication to mastering the core competencies of business analysis. The CCBA certification, therefore, not only signifies a certain level of expertise but also underscores a candidate's practical experience and ongoing commitment to professional development in the dynamic field of business analysis.
What is CCBA Certification Cost?
The cost of obtaining CCBA (Certification of Capability in Business Analysis) certification encompasses several factors, making it essential for aspiring candidates to plan their investment strategically. The CCBA certification cost varies based on factors such as membership status, testing venue, and the inclusion of course materials. The International Institute of Business Analysis (IIBA) typically charges fees for the application process, the certification exam, and any associated study materials.
The application fee is a one-time expense that covers the evaluation of a candidate's eligibility for the CCBA certification. This fee may vary for IIBA members and non-members, with members often enjoying discounted rates. Once the application is approved, candidates can proceed to the next stage, which involves the examination.
The CCBA certification exam fee is another component of the overall cost. Similar to the application fee, this cost may differ for IIBA members and non-members. The exam fee reflects the investment required to undergo the rigorous assessment that evaluates a candidate's knowledge and proficiency in business analysis according to the standards outlined in the Business Analysis Body of Knowledge (BABOK) Guide.
Candidates should also consider potential expenses related to study materials, such as preparation guides and practice exams, which can aid in the successful completion of the CCBA exam. These materials are often available for purchase separately or may be included in a comprehensive exam preparation package.
While the exact CCBA certification cost can vary, it's crucial for candidates to view it as an investment in their professional development. The certification not only validates their skills in business analysis but also enhances their career prospects by opening doors to new opportunities, higher salaries, and increased responsibilities. Aspiring business analysts should carefully weigh the costs against the potential benefits of obtaining CCBA certification, recognizing it as a strategic step toward advancing their careers in the field.
CCBA Region-wise Certification Cost
As of my last knowledge update in January 2022, the specific region-wise certification cost for CCBA (Certification of Capability in Business Analysis) may not be readily available due to variations and updates. The International Institute of Business Analysis (IIBA) often establishes standardized fees for its certifications; however, these fees may differ for IIBA members and non-members.
Typically, IIBA membership offers certain benefits, including discounted rates for certification fees. It's important for individuals considering CCBA certification to review the latest fee structure on the official IIBA website or contact the IIBA directly for the most accurate and up-to-date information. The certification cost can also vary based on factors such as testing venue, application process, and the inclusion of study materials.
IIBA is a global organization, and its certification fees are usually consistent across various regions. However, local taxes, currency exchange rates, and other regional factors can influence the overall cost for candidates in different parts of the world. To obtain precise and region-specific details, individuals are advised to consult the IIBA's official resources or reach out to their local IIBA chapters.
While CCBA certification fees are generally standardized by the IIBA, candidates should be aware of potential variations based on membership status and regional factors. Accessing the latest information directly from the IIBA ensures accurate and current details regarding the certification cost, allowing individuals to plan their certification journey effectively and make informed decisions about their investment in professional development.
Benefits of CCBA Certification
Earning the Certification of Capability in Business Analysis (CCBA) comes with a myriad of benefits that extend beyond the validation of one's skills. One of the foremost advantages is the recognition of a professional's proficiency in business analysis. CCBA certification serves as a formal acknowledgment of an individual's understanding of key concepts, methodologies, and best practices in the field, as outlined in the Business Analysis Body of Knowledge (BABOK) Guide.
The CCBA designation enhances career prospects significantly. It opens doors to new opportunities by signaling to employers that the certified individual possesses a comprehensive skill set and is well-equipped to contribute effectively to business analysis initiatives. This, in turn, often leads to higher salaries and increased responsibilities, positioning CCBA-certified professionals for career advancement.
Moreover, CCBA certification demonstrates a commitment to ongoing professional development. The certification process involves rigorous preparation and the accumulation of professional development hours, showcasing a dedication to staying current with industry trends. This commitment not only boosts the individual's confidence but also establishes credibility among peers and employers.
In the competitive job market, having a CCBA certification provides a distinct advantage. Employers recognize the value of certified business analysts and appreciate the standardized knowledge and skill set that comes with the certification. CCBA-certified professionals stand out as reliable contributors to projects and initiatives, making them sought-after assets in the workforce.
Beyond individual benefits, CCBA certification also contributes to the overall maturation and standardization of the business analysis profession. It sets a benchmark for excellence and encourages a culture of continuous improvement within the industry. As a globally recognized certification, CCBA elevates the status of business analysts and promotes the importance of their role in driving successful business outcomes. In essence, the benefits of CCBA certification extend far beyond personal and professional gains, positively impacting both individuals and the broader business analysis community.
How to obtain CCBA Certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, pursuing the Certification of Capability in Business Analysis (CCBA) is a strategic investment for professionals in the field, offering a range of tangible and intangible benefits. The rigorous certification process not only validates the skills and knowledge of business analysts but also enhances their career prospects. The CCBA designation serves as a powerful signal to employers, indicating a commitment to excellence and a readiness to contribute effectively to business analysis initiatives.
The financial investment required for CCBA certification, encompassing application fees, exam fees, and potential study material costs, should be viewed as a valuable step toward personal and professional development. The return on this investment is evident in the form of increased job opportunities, higher earning potential, and greater responsibilities within the workplace.
Beyond individual gains, CCBA certification contributes to the overall advancement of the business analysis profession. It sets a standard for excellence, fostering a culture of continuous improvement and reinforcing the importance of well-qualified business analysts in driving successful business outcomes. The global recognition of CCBA certification further underscores its significance, positioning certified professionals as valuable assets in a competitive job market.
As professionals consider their career trajectories and seek avenues for growth, CCBA certification stands out as a pivotal milestone. It not only validates their expertise but also aligns them with a community of skilled practitioners dedicated to elevating the standards of business analysis. In essence, CCBA certification is more than a credential; it is a gateway to enhanced professional standing, increased opportunities, and a lasting impact on the dynamic field of business analysis.
Decentralized Autonomous Organizations DAOs
Decentralized Autonomous Organizations (DAOs) represent a groundbreaking paradigm in the realm of blockchain technology and decentralized governance. Born out of the evolution of cryptocurrencies like Bitcoin and Ethereum, DAOs are innovative organizational structures that leverage smart contracts and blockchain technology to create autonomous entities without a centralized authority. The concept of DAOs challenges traditional hierarchical models of governance by distributing decision-making power among their participants in a transparent and trustless manner.
At their core, DAOs are self-executing and self-enforcing smart contracts that encode the rules and regulations governing an organization's operations. These rules are executed automatically, eliminating the need for intermediaries and central control. This decentralized nature empowers participants to have a direct say in the decision-making processes of the organization, fostering a more democratic and inclusive approach to governance. DAOs hold the potential to revolutionize various industries by providing a secure and efficient framework for collaboration and coordination on a global scale.
The rise of DAOs has not been without challenges and controversies, as seen in notable incidents and debates surrounding security vulnerabilities and contentious decision-making. However, these challenges have spurred continuous refinement and improvement within the DAO ecosystem, leading to the development of more robust and resilient structures.
As the landscape of decentralized finance (DeFi) and blockchain technology continues to evolve, DAOs are increasingly gaining attention for their potential to reshape how organizations operate, collaborate, and make decisions. This introduction sets the stage for exploring the fundamental principles, applications, and implications of Decentralized Autonomous Organizations in the rapidly changing landscape of decentralized systems.
Table of contents
-
Technical Foundations of DAOs
-
Governance Mechanisms in DAOs
-
Applications of DAOs Across Industries
-
Security and Risks in DAOs
-
Legal and Regulatory Landscape
-
Conclusion
Technical Foundations of DAOs
The Technical Foundations of Decentralized Autonomous Organizations (DAOs) lie at the intersection of blockchain technology and smart contracts. At their core, DAOs leverage the transparent and tamper-resistant nature of blockchain to establish trust and eliminate the need for a centralized authority. Smart contracts, self-executing pieces of code deployed on blockchain networks like Ethereum, serve as the backbone of DAOs, encoding the rules and protocols that govern the organization's functions. These contracts facilitate automated decision-making, enabling participants to engage in a trustless environment.
Blockchain, the distributed and decentralized ledger technology that underpins DAOs, ensures transparency and immutability. The use of consensus mechanisms, such as proof-of-work or proof-of-stake, adds an additional layer of security by preventing malicious actors from manipulating the organization's records. The technical architecture of DAOs is designed to create a resilient and censorship-resistant framework, allowing participants to interact without relying on a central point of control.
Despite the innovative potential of DAOs, challenges persist within their technical foundations. Issues such as scalability, interoperability, and the potential for smart contract vulnerabilities require ongoing research and development. Innovations in blockchain protocols and advancements in smart contract auditing aim to address these challenges and enhance the robustness of DAOs as they continue to evolve.
The Technical Foundations of DAOs represent a pioneering integration of blockchain and smart contract technologies. The combination of transparency, decentralization, and automation forms the bedrock of these novel organizational structures, offering a glimpse into the potential future of more efficient, inclusive, and transparent systems of governance and collaboration.
Governance Mechanisms in DAOs
Governance Mechanisms in Decentralized Autonomous Organizations (DAOs) play a pivotal role in defining how decisions are made within these innovative structures. Unlike traditional centralized organizations with hierarchical governance models, DAOs distribute decision-making power among their participants in a decentralized and often token-weighted fashion. Token holders, individuals who own a stake in the DAO, typically have the ability to propose and vote on changes, thereby influencing the organization's direction.
The core of DAO governance lies in the concept of on-chain governance, where decisions are recorded and executed through smart contracts on the blockchain. This ensures transparency and trustlessness, as all participants can independently verify the outcomes of governance proposals. Voting mechanisms vary among DAOs and may include simple majority voting, quadratic voting, or other innovative models designed to prevent manipulation and ensure a fair distribution of influence.
One of the challenges in DAO governance is finding a balance between decentralization and efficiency. While decentralization aims to include a wide range of perspectives and prevent concentration of power, it can sometimes result in slow decision-making processes. DAOs continuously experiment with governance models to strike this balance, evolving their structures over time based on the lessons learned from various decentralized experiments.
Evolution is evident in the development of decentralized autonomous organizations, with many moving towards more sophisticated governance frameworks. Some DAOs introduce layers of decision-making, incorporating delegated voting and liquid democracy principles to enhance flexibility and responsiveness. Others explore mechanisms to incentivize active participation and penalize malicious behavior.
Governance Mechanisms in DAOs represent a dynamic and evolving field, exploring innovative ways to distribute decision-making authority in decentralized systems. The journey involves addressing challenges, embracing experimentation, and refining governance models to shape the future of organizational structures in a decentralized world.
Applications of DAOs Across Industries
The applications of Decentralized Autonomous Organizations (DAOs) extend across a diverse array of industries, marking a paradigm shift in how organizations collaborate, coordinate, and make decisions. In the realm of decentralized finance (DeFi), DAOs have emerged as powerful tools for managing decentralized investment funds, liquidity pools, and governance of financial protocols. These financial DAOs enable participants to collectively govern and manage assets, providing a transparent and efficient alternative to traditional financial institutions.
Beyond DeFi, DAOs are making significant strides in supply chain management. By utilizing smart contracts and blockchain technology, DAOs enhance transparency and traceability in supply chains, reducing inefficiencies and combating issues such as fraud and counterfeiting. Participants in the supply chain can collaboratively govern and enforce rules, ensuring fair and ethical practices.
DAOs are fostering new models of player engagement and ownership. Gaming DAOs allow players to influence in-game decisions, contribute to the development process, and even own virtual assets through tokenized representations. This transformative approach challenges the traditional publisher-centric model, empowering gamers with a direct stake in the games they play.
DAOs also find application in content creation and intellectual property management. Decentralized content creation platforms enable artists, writers, and musicians to collaborate, share revenues, and collectively govern the platforms themselves. This ensures fair compensation and a more equitable distribution of value among creators, mitigating the challenges often associated with centralized intermediaries.
While the applications of DAOs are expanding rapidly, challenges such as scalability, legal considerations, and user experience remain areas of active exploration. As DAOs continue to gain traction, their potential to reshape industries by providing transparent, inclusive, and democratic frameworks for collaboration becomes increasingly evident, signaling a transformative era in organizational structures and decision-making processes across various sectors.
Security and Risks in DAOs
Security and Risks in Decentralized Autonomous Organizations (DAOs) are critical aspects that demand careful consideration as these innovative structures become integral parts of the blockchain ecosystem. While DAOs aim to provide transparency, efficiency, and decentralization, they are not immune to security challenges and risks.
One prominent concern in the realm of DAOs is the susceptibility to smart contract vulnerabilities. Smart contracts, the self-executing pieces of code that underpin DAO operations, are subject to coding errors and bugs. Exploiting these vulnerabilities can result in financial losses or manipulation of governance processes. The DAO ecosystem continually grapples with the need for rigorous auditing and testing protocols to mitigate these risks and ensure the robustness of smart contracts.
The evolving regulatory landscape adds an additional layer of complexity to the security and risk considerations associated with DAOs. Navigating compliance issues and legal uncertainties poses challenges for DAOs and their participants, necessitating ongoing efforts to align with existing regulations and contribute to the development of regulatory frameworks for decentralized organizations.
In response to these challenges, the DAO community actively engages in collaborative efforts to enhance security measures, conduct comprehensive audits, and establish best practices. The development of insurance solutions, decentralized insurance pools, and security-focused DAOs that specialize in auditing and securing smart contracts contribute to the ongoing efforts to fortify the security posture of DAOs.
DAOs continue to evolve and proliferate, addressing security concerns and mitigating risks is paramount to their sustained success. The dynamic nature of the blockchain space demands a proactive approach to security, where continuous innovation and collaboration are essential to build resilient and secure DAO ecosystems.
Legal and Regulatory Landscape
The legal and regulatory landscape surrounding Decentralized Autonomous Organizations (DAOs) is an evolving and complex terrain that reflects the intersection of decentralized technologies with traditional legal frameworks. As DAOs challenge traditional notions of corporate structures and governance, regulators globally are grappling with how to classify and regulate these innovative entities.
One of the primary challenges in the legal realm pertains to the ambiguous status of DAOs. Existing legal structures are often designed for centralized entities with identifiable points of control, making it challenging to fit decentralized and autonomous organizations into established regulatory frameworks. The lack of a centralized authority raises questions about legal liability, accountability, and the enforcement of regulations within DAOs.
Jurisdictions around the world are adopting varied approaches to the regulation of DAOs. Some countries are embracing a permissive stance, fostering an environment that encourages innovation and the development of decentralized technologies. Others are taking a more cautious approach, emphasizing the need for clear legal frameworks to address potential risks such as fraud, money laundering, and market manipulation associated with DAO activities.
The regulatory challenges extend beyond the DAOs themselves to encompass the broader ecosystem, including cryptocurrency transactions, token issuance, and decentralized finance (DeFi) platforms. Regulatory bodies are exploring ways to strike a balance between fostering innovation and protecting investors and consumers. As the landscape evolves, legal frameworks are expected to adapt to accommodate the unique features of DAOs, such as decentralized decision-making and ownership structures.
Certain legal considerations, such as intellectual property rights, contract enforcement, and dispute resolution, also come to the forefront in the context of DAOs. The absence of a centralized authority to arbitrate disputes raises questions about how legal remedies can be pursued in the event of contractual breaches or disagreements among DAO participants.
As the legal and regulatory landscape continues to take shape, collaboration between the DAO community, legal professionals, and regulators becomes crucial. The ongoing dialogue aims to establish clear guidelines that balance innovation with legal compliance, ensuring the responsible development and integration of DAOs into the broader economic and legal systems. The evolving nature of these discussions underscores the need for a flexible and adaptive approach to accommodate the dynamic nature of decentralized technologies and their impact on traditional legal paradigms.
How to obtain Block Chain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, Decentralized Autonomous Organizations (DAOs) represent a transformative force at the intersection of blockchain technology, decentralized governance, and organizational structures. The technical foundations of DAOs, rooted in smart contracts and blockchain technology, provide a transparent and trustless framework for automated decision-making, challenging traditional hierarchical models. The exploration of governance mechanisms reveals the dynamic evolution of decentralized decision-making, with token holders actively participating in shaping the direction of DAOs.
DAOs find diverse applications across industries, from reshaping decentralized finance (DeFi) and supply chain management to revolutionizing gaming and content creation. As these applications continue to expand, DAOs are driving innovation, fostering collaboration, and redefining how value is created and distributed.
The future of DAOs holds immense promise, with ongoing efforts to enhance security, navigate legal complexities, and refine governance models. The journey towards decentralized, inclusive, and transparent organizational structures is marked by a commitment to overcoming challenges, learning from experiences, and contributing to the broader discourse on the future of decentralized technologies.
As DAOs continue to evolve, the collaboration between technologists, legal experts, regulators, and the broader community becomes increasingly critical. The dynamic nature of this ecosystem calls for a balanced and adaptable approach to ensure that DAOs contribute positively to innovation, governance, and collaboration in the rapidly changing landscape of decentralized systems.
Read More
Decentralized Autonomous Organizations (DAOs) represent a groundbreaking paradigm in the realm of blockchain technology and decentralized governance. Born out of the evolution of cryptocurrencies like Bitcoin and Ethereum, DAOs are innovative organizational structures that leverage smart contracts and blockchain technology to create autonomous entities without a centralized authority. The concept of DAOs challenges traditional hierarchical models of governance by distributing decision-making power among their participants in a transparent and trustless manner.
At their core, DAOs are self-executing and self-enforcing smart contracts that encode the rules and regulations governing an organization's operations. These rules are executed automatically, eliminating the need for intermediaries and central control. This decentralized nature empowers participants to have a direct say in the decision-making processes of the organization, fostering a more democratic and inclusive approach to governance. DAOs hold the potential to revolutionize various industries by providing a secure and efficient framework for collaboration and coordination on a global scale.
The rise of DAOs has not been without challenges and controversies, as seen in notable incidents and debates surrounding security vulnerabilities and contentious decision-making. However, these challenges have spurred continuous refinement and improvement within the DAO ecosystem, leading to the development of more robust and resilient structures.
As the landscape of decentralized finance (DeFi) and blockchain technology continues to evolve, DAOs are increasingly gaining attention for their potential to reshape how organizations operate, collaborate, and make decisions. This introduction sets the stage for exploring the fundamental principles, applications, and implications of Decentralized Autonomous Organizations in the rapidly changing landscape of decentralized systems.
Table of contents
-
Technical Foundations of DAOs
-
Governance Mechanisms in DAOs
-
Applications of DAOs Across Industries
-
Security and Risks in DAOs
-
Legal and Regulatory Landscape
-
Conclusion
Technical Foundations of DAOs
The Technical Foundations of Decentralized Autonomous Organizations (DAOs) lie at the intersection of blockchain technology and smart contracts. At their core, DAOs leverage the transparent and tamper-resistant nature of blockchain to establish trust and eliminate the need for a centralized authority. Smart contracts, self-executing pieces of code deployed on blockchain networks like Ethereum, serve as the backbone of DAOs, encoding the rules and protocols that govern the organization's functions. These contracts facilitate automated decision-making, enabling participants to engage in a trustless environment.
Blockchain, the distributed and decentralized ledger technology that underpins DAOs, ensures transparency and immutability. The use of consensus mechanisms, such as proof-of-work or proof-of-stake, adds an additional layer of security by preventing malicious actors from manipulating the organization's records. The technical architecture of DAOs is designed to create a resilient and censorship-resistant framework, allowing participants to interact without relying on a central point of control.
Despite the innovative potential of DAOs, challenges persist within their technical foundations. Issues such as scalability, interoperability, and the potential for smart contract vulnerabilities require ongoing research and development. Innovations in blockchain protocols and advancements in smart contract auditing aim to address these challenges and enhance the robustness of DAOs as they continue to evolve.
The Technical Foundations of DAOs represent a pioneering integration of blockchain and smart contract technologies. The combination of transparency, decentralization, and automation forms the bedrock of these novel organizational structures, offering a glimpse into the potential future of more efficient, inclusive, and transparent systems of governance and collaboration.
Governance Mechanisms in DAOs
Governance Mechanisms in Decentralized Autonomous Organizations (DAOs) play a pivotal role in defining how decisions are made within these innovative structures. Unlike traditional centralized organizations with hierarchical governance models, DAOs distribute decision-making power among their participants in a decentralized and often token-weighted fashion. Token holders, individuals who own a stake in the DAO, typically have the ability to propose and vote on changes, thereby influencing the organization's direction.
The core of DAO governance lies in the concept of on-chain governance, where decisions are recorded and executed through smart contracts on the blockchain. This ensures transparency and trustlessness, as all participants can independently verify the outcomes of governance proposals. Voting mechanisms vary among DAOs and may include simple majority voting, quadratic voting, or other innovative models designed to prevent manipulation and ensure a fair distribution of influence.
One of the challenges in DAO governance is finding a balance between decentralization and efficiency. While decentralization aims to include a wide range of perspectives and prevent concentration of power, it can sometimes result in slow decision-making processes. DAOs continuously experiment with governance models to strike this balance, evolving their structures over time based on the lessons learned from various decentralized experiments.
Evolution is evident in the development of decentralized autonomous organizations, with many moving towards more sophisticated governance frameworks. Some DAOs introduce layers of decision-making, incorporating delegated voting and liquid democracy principles to enhance flexibility and responsiveness. Others explore mechanisms to incentivize active participation and penalize malicious behavior.
Governance Mechanisms in DAOs represent a dynamic and evolving field, exploring innovative ways to distribute decision-making authority in decentralized systems. The journey involves addressing challenges, embracing experimentation, and refining governance models to shape the future of organizational structures in a decentralized world.
Applications of DAOs Across Industries
The applications of Decentralized Autonomous Organizations (DAOs) extend across a diverse array of industries, marking a paradigm shift in how organizations collaborate, coordinate, and make decisions. In the realm of decentralized finance (DeFi), DAOs have emerged as powerful tools for managing decentralized investment funds, liquidity pools, and governance of financial protocols. These financial DAOs enable participants to collectively govern and manage assets, providing a transparent and efficient alternative to traditional financial institutions.
Beyond DeFi, DAOs are making significant strides in supply chain management. By utilizing smart contracts and blockchain technology, DAOs enhance transparency and traceability in supply chains, reducing inefficiencies and combating issues such as fraud and counterfeiting. Participants in the supply chain can collaboratively govern and enforce rules, ensuring fair and ethical practices.
DAOs are fostering new models of player engagement and ownership. Gaming DAOs allow players to influence in-game decisions, contribute to the development process, and even own virtual assets through tokenized representations. This transformative approach challenges the traditional publisher-centric model, empowering gamers with a direct stake in the games they play.
DAOs also find application in content creation and intellectual property management. Decentralized content creation platforms enable artists, writers, and musicians to collaborate, share revenues, and collectively govern the platforms themselves. This ensures fair compensation and a more equitable distribution of value among creators, mitigating the challenges often associated with centralized intermediaries.
While the applications of DAOs are expanding rapidly, challenges such as scalability, legal considerations, and user experience remain areas of active exploration. As DAOs continue to gain traction, their potential to reshape industries by providing transparent, inclusive, and democratic frameworks for collaboration becomes increasingly evident, signaling a transformative era in organizational structures and decision-making processes across various sectors.
Security and Risks in DAOs
Security and Risks in Decentralized Autonomous Organizations (DAOs) are critical aspects that demand careful consideration as these innovative structures become integral parts of the blockchain ecosystem. While DAOs aim to provide transparency, efficiency, and decentralization, they are not immune to security challenges and risks.
One prominent concern in the realm of DAOs is the susceptibility to smart contract vulnerabilities. Smart contracts, the self-executing pieces of code that underpin DAO operations, are subject to coding errors and bugs. Exploiting these vulnerabilities can result in financial losses or manipulation of governance processes. The DAO ecosystem continually grapples with the need for rigorous auditing and testing protocols to mitigate these risks and ensure the robustness of smart contracts.
The evolving regulatory landscape adds an additional layer of complexity to the security and risk considerations associated with DAOs. Navigating compliance issues and legal uncertainties poses challenges for DAOs and their participants, necessitating ongoing efforts to align with existing regulations and contribute to the development of regulatory frameworks for decentralized organizations.
In response to these challenges, the DAO community actively engages in collaborative efforts to enhance security measures, conduct comprehensive audits, and establish best practices. The development of insurance solutions, decentralized insurance pools, and security-focused DAOs that specialize in auditing and securing smart contracts contribute to the ongoing efforts to fortify the security posture of DAOs.
DAOs continue to evolve and proliferate, addressing security concerns and mitigating risks is paramount to their sustained success. The dynamic nature of the blockchain space demands a proactive approach to security, where continuous innovation and collaboration are essential to build resilient and secure DAO ecosystems.
Legal and Regulatory Landscape
The legal and regulatory landscape surrounding Decentralized Autonomous Organizations (DAOs) is an evolving and complex terrain that reflects the intersection of decentralized technologies with traditional legal frameworks. As DAOs challenge traditional notions of corporate structures and governance, regulators globally are grappling with how to classify and regulate these innovative entities.
One of the primary challenges in the legal realm pertains to the ambiguous status of DAOs. Existing legal structures are often designed for centralized entities with identifiable points of control, making it challenging to fit decentralized and autonomous organizations into established regulatory frameworks. The lack of a centralized authority raises questions about legal liability, accountability, and the enforcement of regulations within DAOs.
Jurisdictions around the world are adopting varied approaches to the regulation of DAOs. Some countries are embracing a permissive stance, fostering an environment that encourages innovation and the development of decentralized technologies. Others are taking a more cautious approach, emphasizing the need for clear legal frameworks to address potential risks such as fraud, money laundering, and market manipulation associated with DAO activities.
The regulatory challenges extend beyond the DAOs themselves to encompass the broader ecosystem, including cryptocurrency transactions, token issuance, and decentralized finance (DeFi) platforms. Regulatory bodies are exploring ways to strike a balance between fostering innovation and protecting investors and consumers. As the landscape evolves, legal frameworks are expected to adapt to accommodate the unique features of DAOs, such as decentralized decision-making and ownership structures.
Certain legal considerations, such as intellectual property rights, contract enforcement, and dispute resolution, also come to the forefront in the context of DAOs. The absence of a centralized authority to arbitrate disputes raises questions about how legal remedies can be pursued in the event of contractual breaches or disagreements among DAO participants.
As the legal and regulatory landscape continues to take shape, collaboration between the DAO community, legal professionals, and regulators becomes crucial. The ongoing dialogue aims to establish clear guidelines that balance innovation with legal compliance, ensuring the responsible development and integration of DAOs into the broader economic and legal systems. The evolving nature of these discussions underscores the need for a flexible and adaptive approach to accommodate the dynamic nature of decentralized technologies and their impact on traditional legal paradigms.
How to obtain Block Chain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, Decentralized Autonomous Organizations (DAOs) represent a transformative force at the intersection of blockchain technology, decentralized governance, and organizational structures. The technical foundations of DAOs, rooted in smart contracts and blockchain technology, provide a transparent and trustless framework for automated decision-making, challenging traditional hierarchical models. The exploration of governance mechanisms reveals the dynamic evolution of decentralized decision-making, with token holders actively participating in shaping the direction of DAOs.
DAOs find diverse applications across industries, from reshaping decentralized finance (DeFi) and supply chain management to revolutionizing gaming and content creation. As these applications continue to expand, DAOs are driving innovation, fostering collaboration, and redefining how value is created and distributed.
The future of DAOs holds immense promise, with ongoing efforts to enhance security, navigate legal complexities, and refine governance models. The journey towards decentralized, inclusive, and transparent organizational structures is marked by a commitment to overcoming challenges, learning from experiences, and contributing to the broader discourse on the future of decentralized technologies.
As DAOs continue to evolve, the collaboration between technologists, legal experts, regulators, and the broader community becomes increasingly critical. The dynamic nature of this ecosystem calls for a balanced and adaptable approach to ensure that DAOs contribute positively to innovation, governance, and collaboration in the rapidly changing landscape of decentralized systems.
Understanding the Global Interpreter Lock GIL in Python Multithreading
Python is a versatile and widely-used programming language known for its simplicity, readability, and extensive standard libraries. However, when it comes to concurrent programming and multithreading, developers often encounter a significant challenge known as the Global Interpreter Lock (GIL). The GIL has been a topic of discussion and debate within the Python community for years, as it plays a crucial role in shaping the language's behavior in a multi-threaded environment.
At its core, the Global Interpreter Lock is a mechanism implemented in the CPython interpreter, which is the default and most widely used implementation of Python. The GIL ensures that only one thread executes Python bytecode at a time, effectively serializing the execution of threads. While this design simplifies memory management and makes certain aspects of programming more straightforward, it also introduces limitations and trade-offs, particularly in scenarios where parallelism is crucial for performance optimization.
In this exploration of the Global Interpreter Lock, we will delve into the reasons behind its existence, its impact on Python multithreading, and the implications for developers seeking to harness the power of concurrent processing. Understanding the nuances of the GIL is essential for Python developers aiming to build efficient and scalable applications, as it directly influences the language's ability to fully leverage the capabilities of modern multi-core processors. As we navigate through the complexities of the Global Interpreter Lock, we will uncover strategies, alternatives, and best practices for mitigating its effects and achieving better performance in multi-threaded Python programs.
Table of contents
-
The Role of the Global Interpreter Lock (GIL)
-
GIL Limitations and Performance Challenges
-
Strategies for GIL Mitigation
-
Concurrency Patterns and Best Practices
-
Future Directions: GIL and Python's Evolution
-
Conclusion
The Role of the Global Interpreter Lock (GIL)
The Global Interpreter Lock (GIL) serves as a critical component within the CPython interpreter, the default and most widely used implementation of the Python programming language. Its primary role is to safeguard access to Python objects, preventing multiple native threads from executing Python bytecode simultaneously. The GIL essentially acts as a mutex, ensuring that only one thread can execute Python bytecode within a single process at any given moment. This mechanism simplifies memory management and alleviates certain complexities associated with multithreading, as it helps avoid race conditions and ensures thread safety in the CPython interpreter.
While the GIL serves a valuable purpose in terms of simplicity and ease of memory management, it introduces limitations in scenarios where parallelism is a key consideration. In a multi-threaded environment, the GIL can become a bottleneck, hindering the effective utilization of multiple processor cores. This limitation is particularly noteworthy in performance-critical applications, such as those involving computationally intensive tasks or data processing, where the ability to leverage concurrent execution for improved speed is highly desirable.
The GIL's role extends beyond its technical aspects; it has become a topic of ongoing discussion and debate within the Python community. Developers and language designers grapple with the trade-offs associated with the GIL, weighing the benefits of simplicity against the drawbacks of restricted parallelism. As Python continues to evolve, so does the discourse around potential modifications to the GIL or the exploration of alternative strategies that could maintain simplicity while enhancing concurrency. Understanding the role of the GIL lays the foundation for comprehending its impact on multithreading in Python and motivates the exploration of strategies to optimize performance within its constraints.
GIL Limitations and Performance Challenges
The Global Interpreter Lock (GIL) in Python, while serving its purpose of simplifying memory management and ensuring thread safety, introduces significant limitations and performance challenges in the realm of multithreading. One of the key drawbacks of the GIL is its tendency to become a performance bottleneck, particularly in scenarios where parallelism is crucial for optimal execution. The GIL restricts the execution of Python bytecode to a single thread at a time, effectively serializing the operations even in the presence of multiple threads. As a consequence, the full potential of multi-core processors remains largely untapped, and applications may fail to achieve the expected performance gains through parallelism.
In performance-critical applications, such as scientific computing or data-intensive tasks, the GIL can pose substantial challenges. Computations that could otherwise benefit from concurrent execution are hindered by the lock, leading to suboptimal resource utilization. The limitations become particularly evident in applications that require extensive CPU-bound processing, where the inability to efficiently distribute work across multiple cores can result in slower execution times and decreased overall system performance.
Developers often encounter scenarios where the GIL's impact is felt acutely, prompting the exploration of alternative concurrency models or the adoption of strategies to mitigate its effects. While certain types of applications, such as those centered around I/O-bound tasks, may experience less pronounced limitations, the GIL remains a central consideration in the performance tuning and optimization of Python programs. As the Python community strives for both simplicity and improved parallelism, addressing the limitations and performance challenges posed by the GIL remains an ongoing area of exploration and innovation.
Strategies for GIL Mitigation
In response to the challenges posed by the Global Interpreter Lock (GIL) in Python multithreading, developers employ various strategies to mitigate its impact and enhance concurrency.One common approach involves leveraging the multiprocessing module instead of multithreading. Unlike threads, separate processes in Python run in their own interpreter and have independent memory space, circumventing the GIL limitations. While this introduces inter-process communication complexities, it allows for parallel execution of Python code on multi-core systems, enabling better utilization of available resources.
Another strategy involves adopting asynchronous programming, which utilizes coroutines and the asyncio library. Instead of relying on multiple threads, asynchronous programming allows a single thread to efficiently switch between different tasks when waiting for I/O operations. While this approach doesn't eliminate the GIL, it mitigates its impact by focusing on non-blocking I/O operations, making it particularly effective for I/O-bound tasks such as networking.
Furthermore, developers may explore alternative interpreters like Jython or IronPython, which are implementations of Python for the Java Virtual Machine (JVM) and the .NET Framework, respectively. These interpreters operate on different concurrency models and lack a GIL, offering an avenue for achieving better parallelism in specific environments.
Thread pools and parallel processing libraries, such as concurrent.futures, provide a higher-level abstraction for managing parallel tasks without directly dealing with threads. These abstractions allow developers to write concurrent code without the need to explicitly manage threads, offering a more straightforward approach to harnessing parallelism.
While each strategy has its merits and trade-offs, the choice depends on the specific requirements of the application. Successful GIL mitigation often involves a combination of these approaches, tailored to the characteristics of the workload and the desired performance outcomes. As Python evolves, the community continues to explore innovative ways to address GIL-related challenges, seeking a balance between simplicity and effective parallelism.
Concurrency Patterns and Best Practices
Navigating the intricacies of the Global Interpreter Lock (GIL) in Python multithreading necessitates the adoption of specific concurrency patterns and best practices. One fundamental approach involves the use of thread pools, which efficiently manage a pool of worker threads to execute tasks concurrently. Thread pools encapsulate the complexities of thread creation and management, providing a more controlled and scalable solution for applications that require parallelism.
Concurrency patterns such as the Producer-Consumer pattern can be beneficial in scenarios where multiple threads need to collaborate on shared resources. This pattern involves a producer thread generating data and placing it into a shared buffer, while one or more consumer threads retrieve and process the data. Careful synchronization mechanisms, such as locks or semaphores, can be employed to ensure the integrity of shared data structures.
Asynchronous programming, facilitated by the asyncio library, has become increasingly popular for managing concurrency in Python. By using coroutines and an event loop, asynchronous programming allows tasks to yield control to the event loop when waiting for external resources, maximizing the efficiency of single-threaded execution and reducing the impact of the GIL. This approach is particularly effective in I/O-bound scenarios, where threads spend a significant amount of time waiting for input or output operations to complete.
Thread-local storage is a crucial best practice for mitigating GIL-related challenges. By minimizing shared data between threads and utilizing thread-local storage for certain variables, developers can reduce contention for shared resources. This approach enhances thread isolation and minimizes the risk of race conditions, contributing to the overall reliability of multithreaded applications.
Effective concurrency patterns and best practices in Python involve a thoughtful combination of thread pools, synchronization mechanisms, asynchronous programming, thread-local storage, and judicious use of thread-safe data structures. Tailoring these techniques to the specific requirements of the application allows developers to create responsive, scalable, and reliable multithreaded Python applications, optimizing performance within the confines of the GIL.
Future Directions: GIL and Python's Evolution
The Global Interpreter Lock (GIL) in Python has long been a subject of discussion and debate within the programming community, prompting a keen interest in the future directions of Python's evolution and its relationship with the GIL. As Python continues to evolve as a language, developers and language designers are exploring avenues to address or potentially eliminate the limitations imposed by the GIL on concurrent execution.
One notable initiative in this context is the Global Interpreter Lock Removal (GILR) project. This ongoing effort seeks to explore the feasibility of removing the GIL from the CPython interpreter, thereby allowing multiple threads to execute Python bytecode simultaneously. While this endeavor presents numerous technical challenges, the potential benefits in terms of improved parallelism and performance have sparked enthusiasm within the Python community. Developers are closely monitoring the progress of the GILR project as it represents a significant step towards unlocking the full potential of Python in multi-core environments.
In addition to GIL removal efforts, other proposals and discussions revolve around alternative concurrency models that could coexist with or replace the GIL. These include exploring more fine-grained locking mechanisms, promoting the adoption of multiprocessing over multithreading, and enhancing support for asynchronous programming. The goal is to strike a delicate balance between simplicity, which has been a hallmark of Python, and providing developers with the tools needed to harness the power of modern hardware effectively.
The evolution of Python's concurrency capabilities is not only a technical consideration but also a reflection of the evolving landscape of computing architectures. As hardware trends emphasize increasing core counts and parallel processing capabilities, the Python community is driven to adapt the language to fully exploit these advancements. In the years to come, the trajectory of Python's evolution and its handling of concurrency will likely shape how developers approach parallelism, making it a pivotal aspect of the language's ongoing development. As these discussions unfold, the Python community remains committed to preserving the language's strengths while continually striving to enhance its concurrency features and mitigate the challenges posed by the Global Interpreter Lock.
How to obtain python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Global Interpreter Lock (GIL) stands as a double-edged sword in the realm of Python multithreading, offering simplicity in memory management while presenting challenges in achieving efficient parallelism. As we've explored the role of the GIL, its limitations, and various strategies for mitigation, it is evident that the Python community is actively engaged in addressing these challenges.
While the GIL has been a longstanding aspect of CPython, ongoing initiatives like the Global Interpreter Lock Removal (GILR) project signify a commitment to evolving Python's concurrency model. The pursuit of GIL removal underscores the community's dedication to unlocking the full potential of Python in the face of modern multi-core architectures.
In essence, the story of the GIL in Python is one of continuous adaptation and innovation. As Python evolves, so too will the strategies employed by developers to overcome the challenges posed by the GIL. The journey involves not only technical considerations but also a deeper exploration of how concurrency aligns with the broader goals and principles of the Python language. In this ever-evolving landscape, the Python community remains steadfast in its commitment to providing developers with tools that enable them to write efficient, scalable, and reliable code, even as it navigates the complexities of the Global Interpreter Lock.
Read More
Python is a versatile and widely-used programming language known for its simplicity, readability, and extensive standard libraries. However, when it comes to concurrent programming and multithreading, developers often encounter a significant challenge known as the Global Interpreter Lock (GIL). The GIL has been a topic of discussion and debate within the Python community for years, as it plays a crucial role in shaping the language's behavior in a multi-threaded environment.
At its core, the Global Interpreter Lock is a mechanism implemented in the CPython interpreter, which is the default and most widely used implementation of Python. The GIL ensures that only one thread executes Python bytecode at a time, effectively serializing the execution of threads. While this design simplifies memory management and makes certain aspects of programming more straightforward, it also introduces limitations and trade-offs, particularly in scenarios where parallelism is crucial for performance optimization.
In this exploration of the Global Interpreter Lock, we will delve into the reasons behind its existence, its impact on Python multithreading, and the implications for developers seeking to harness the power of concurrent processing. Understanding the nuances of the GIL is essential for Python developers aiming to build efficient and scalable applications, as it directly influences the language's ability to fully leverage the capabilities of modern multi-core processors. As we navigate through the complexities of the Global Interpreter Lock, we will uncover strategies, alternatives, and best practices for mitigating its effects and achieving better performance in multi-threaded Python programs.
Table of contents
-
The Role of the Global Interpreter Lock (GIL)
-
GIL Limitations and Performance Challenges
-
Strategies for GIL Mitigation
-
Concurrency Patterns and Best Practices
-
Future Directions: GIL and Python's Evolution
-
Conclusion
The Role of the Global Interpreter Lock (GIL)
The Global Interpreter Lock (GIL) serves as a critical component within the CPython interpreter, the default and most widely used implementation of the Python programming language. Its primary role is to safeguard access to Python objects, preventing multiple native threads from executing Python bytecode simultaneously. The GIL essentially acts as a mutex, ensuring that only one thread can execute Python bytecode within a single process at any given moment. This mechanism simplifies memory management and alleviates certain complexities associated with multithreading, as it helps avoid race conditions and ensures thread safety in the CPython interpreter.
While the GIL serves a valuable purpose in terms of simplicity and ease of memory management, it introduces limitations in scenarios where parallelism is a key consideration. In a multi-threaded environment, the GIL can become a bottleneck, hindering the effective utilization of multiple processor cores. This limitation is particularly noteworthy in performance-critical applications, such as those involving computationally intensive tasks or data processing, where the ability to leverage concurrent execution for improved speed is highly desirable.
The GIL's role extends beyond its technical aspects; it has become a topic of ongoing discussion and debate within the Python community. Developers and language designers grapple with the trade-offs associated with the GIL, weighing the benefits of simplicity against the drawbacks of restricted parallelism. As Python continues to evolve, so does the discourse around potential modifications to the GIL or the exploration of alternative strategies that could maintain simplicity while enhancing concurrency. Understanding the role of the GIL lays the foundation for comprehending its impact on multithreading in Python and motivates the exploration of strategies to optimize performance within its constraints.
GIL Limitations and Performance Challenges
The Global Interpreter Lock (GIL) in Python, while serving its purpose of simplifying memory management and ensuring thread safety, introduces significant limitations and performance challenges in the realm of multithreading. One of the key drawbacks of the GIL is its tendency to become a performance bottleneck, particularly in scenarios where parallelism is crucial for optimal execution. The GIL restricts the execution of Python bytecode to a single thread at a time, effectively serializing the operations even in the presence of multiple threads. As a consequence, the full potential of multi-core processors remains largely untapped, and applications may fail to achieve the expected performance gains through parallelism.
In performance-critical applications, such as scientific computing or data-intensive tasks, the GIL can pose substantial challenges. Computations that could otherwise benefit from concurrent execution are hindered by the lock, leading to suboptimal resource utilization. The limitations become particularly evident in applications that require extensive CPU-bound processing, where the inability to efficiently distribute work across multiple cores can result in slower execution times and decreased overall system performance.
Developers often encounter scenarios where the GIL's impact is felt acutely, prompting the exploration of alternative concurrency models or the adoption of strategies to mitigate its effects. While certain types of applications, such as those centered around I/O-bound tasks, may experience less pronounced limitations, the GIL remains a central consideration in the performance tuning and optimization of Python programs. As the Python community strives for both simplicity and improved parallelism, addressing the limitations and performance challenges posed by the GIL remains an ongoing area of exploration and innovation.
Strategies for GIL Mitigation
In response to the challenges posed by the Global Interpreter Lock (GIL) in Python multithreading, developers employ various strategies to mitigate its impact and enhance concurrency.One common approach involves leveraging the multiprocessing module instead of multithreading. Unlike threads, separate processes in Python run in their own interpreter and have independent memory space, circumventing the GIL limitations. While this introduces inter-process communication complexities, it allows for parallel execution of Python code on multi-core systems, enabling better utilization of available resources.
Another strategy involves adopting asynchronous programming, which utilizes coroutines and the asyncio library. Instead of relying on multiple threads, asynchronous programming allows a single thread to efficiently switch between different tasks when waiting for I/O operations. While this approach doesn't eliminate the GIL, it mitigates its impact by focusing on non-blocking I/O operations, making it particularly effective for I/O-bound tasks such as networking.
Furthermore, developers may explore alternative interpreters like Jython or IronPython, which are implementations of Python for the Java Virtual Machine (JVM) and the .NET Framework, respectively. These interpreters operate on different concurrency models and lack a GIL, offering an avenue for achieving better parallelism in specific environments.
Thread pools and parallel processing libraries, such as concurrent.futures, provide a higher-level abstraction for managing parallel tasks without directly dealing with threads. These abstractions allow developers to write concurrent code without the need to explicitly manage threads, offering a more straightforward approach to harnessing parallelism.
While each strategy has its merits and trade-offs, the choice depends on the specific requirements of the application. Successful GIL mitigation often involves a combination of these approaches, tailored to the characteristics of the workload and the desired performance outcomes. As Python evolves, the community continues to explore innovative ways to address GIL-related challenges, seeking a balance between simplicity and effective parallelism.
Concurrency Patterns and Best Practices
Navigating the intricacies of the Global Interpreter Lock (GIL) in Python multithreading necessitates the adoption of specific concurrency patterns and best practices. One fundamental approach involves the use of thread pools, which efficiently manage a pool of worker threads to execute tasks concurrently. Thread pools encapsulate the complexities of thread creation and management, providing a more controlled and scalable solution for applications that require parallelism.
Concurrency patterns such as the Producer-Consumer pattern can be beneficial in scenarios where multiple threads need to collaborate on shared resources. This pattern involves a producer thread generating data and placing it into a shared buffer, while one or more consumer threads retrieve and process the data. Careful synchronization mechanisms, such as locks or semaphores, can be employed to ensure the integrity of shared data structures.
Asynchronous programming, facilitated by the asyncio library, has become increasingly popular for managing concurrency in Python. By using coroutines and an event loop, asynchronous programming allows tasks to yield control to the event loop when waiting for external resources, maximizing the efficiency of single-threaded execution and reducing the impact of the GIL. This approach is particularly effective in I/O-bound scenarios, where threads spend a significant amount of time waiting for input or output operations to complete.
Thread-local storage is a crucial best practice for mitigating GIL-related challenges. By minimizing shared data between threads and utilizing thread-local storage for certain variables, developers can reduce contention for shared resources. This approach enhances thread isolation and minimizes the risk of race conditions, contributing to the overall reliability of multithreaded applications.
Effective concurrency patterns and best practices in Python involve a thoughtful combination of thread pools, synchronization mechanisms, asynchronous programming, thread-local storage, and judicious use of thread-safe data structures. Tailoring these techniques to the specific requirements of the application allows developers to create responsive, scalable, and reliable multithreaded Python applications, optimizing performance within the confines of the GIL.
Future Directions: GIL and Python's Evolution
The Global Interpreter Lock (GIL) in Python has long been a subject of discussion and debate within the programming community, prompting a keen interest in the future directions of Python's evolution and its relationship with the GIL. As Python continues to evolve as a language, developers and language designers are exploring avenues to address or potentially eliminate the limitations imposed by the GIL on concurrent execution.
One notable initiative in this context is the Global Interpreter Lock Removal (GILR) project. This ongoing effort seeks to explore the feasibility of removing the GIL from the CPython interpreter, thereby allowing multiple threads to execute Python bytecode simultaneously. While this endeavor presents numerous technical challenges, the potential benefits in terms of improved parallelism and performance have sparked enthusiasm within the Python community. Developers are closely monitoring the progress of the GILR project as it represents a significant step towards unlocking the full potential of Python in multi-core environments.
In addition to GIL removal efforts, other proposals and discussions revolve around alternative concurrency models that could coexist with or replace the GIL. These include exploring more fine-grained locking mechanisms, promoting the adoption of multiprocessing over multithreading, and enhancing support for asynchronous programming. The goal is to strike a delicate balance between simplicity, which has been a hallmark of Python, and providing developers with the tools needed to harness the power of modern hardware effectively.
The evolution of Python's concurrency capabilities is not only a technical consideration but also a reflection of the evolving landscape of computing architectures. As hardware trends emphasize increasing core counts and parallel processing capabilities, the Python community is driven to adapt the language to fully exploit these advancements. In the years to come, the trajectory of Python's evolution and its handling of concurrency will likely shape how developers approach parallelism, making it a pivotal aspect of the language's ongoing development. As these discussions unfold, the Python community remains committed to preserving the language's strengths while continually striving to enhance its concurrency features and mitigate the challenges posed by the Global Interpreter Lock.
How to obtain python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Global Interpreter Lock (GIL) stands as a double-edged sword in the realm of Python multithreading, offering simplicity in memory management while presenting challenges in achieving efficient parallelism. As we've explored the role of the GIL, its limitations, and various strategies for mitigation, it is evident that the Python community is actively engaged in addressing these challenges.
While the GIL has been a longstanding aspect of CPython, ongoing initiatives like the Global Interpreter Lock Removal (GILR) project signify a commitment to evolving Python's concurrency model. The pursuit of GIL removal underscores the community's dedication to unlocking the full potential of Python in the face of modern multi-core architectures.
In essence, the story of the GIL in Python is one of continuous adaptation and innovation. As Python evolves, so too will the strategies employed by developers to overcome the challenges posed by the GIL. The journey involves not only technical considerations but also a deeper exploration of how concurrency aligns with the broader goals and principles of the Python language. In this ever-evolving landscape, the Python community remains steadfast in its commitment to providing developers with tools that enable them to write efficient, scalable, and reliable code, even as it navigates the complexities of the Global Interpreter Lock.
Explainable AI (XAI): Understanding and Interpreting Machine Learning Models
In recent years, the rapid advancement of machine learning technologies has propelled artificial intelligence (AI) into various facets of our daily lives. From healthcare diagnostics to financial predictions, AI-powered systems are making critical decisions that significantly impact individuals and society at large. However, the inherent complexity of many machine learning models has given rise to a pressing concern: the lack of transparency and interpretability in AI decision-making processes. Enter Explainable AI (XAI), a field dedicated to unraveling the black box nature of these models and providing a clearer understanding of their functioning.
Explainable AI represents a paradigm shift in the AI community, acknowledging the need for more than just predictive accuracy. While highly intricate neural networks and sophisticated algorithms have demonstrated remarkable capabilities, the inability to comprehend and explain their decision-making mechanisms poses significant challenges. XAI seeks to address this challenge by developing methodologies that shed light on the intricate inner workings of machine learning models, allowing stakeholders to decipher the rationale behind AI-driven predictions and classifications.
The demand for explainability in AI arises from various sectors, including healthcare, finance, and legal systems, where the consequences of algorithmic decisions can be profound. In medical diagnoses, for instance, understanding why a particular treatment recommendation was made by an AI system is crucial for gaining the trust of medical practitioners and ensuring patient safety. This necessity for transparency extends beyond expert users to encompass a broader audience, emphasizing the importance of creating AI systems that are not only accurate but also interpretable by individuals with varying degrees of technical expertise. This introduction sets the stage for delving into the realm of Explainable AI, exploring the significance of understanding and interpreting machine learning models in an increasingly AI-driven world
Table of contents
-
Model-Agnostic Explainability Techniques
-
Inherent Explainability in Machine Learning Models
-
Applications of Explainable AI in Healthcare
-
Challenges and Trade-offs in Explainable AI
-
User-Centric Perspectives on Explainable AI
-
Conclusion
Model-Agnostic Explainability Techniques
In the landscape of Explainable AI (XAI), model-agnostic techniques have emerged as powerful tools for unraveling the complexities of machine learning models, regardless of their underlying algorithms. Unlike methods that are intricately tied to specific model architectures, model-agnostic approaches provide a universal lens through which the inner workings of black-box models can be examined and understood.
One prominent example of model-agnostic explainability is the Local Interpretable Model-agnostic Explanations (LIME) framework. LIME operates by generating locally faithful explanations for individual predictions, perturbing the input data and observing the model's response. By fitting an interpretable model to these perturbations, LIME produces a simplified explanation that mirrors the decision-making process of the complex model. This not only makes the prediction more transparent but also facilitates human comprehension of the features driving the model's output.
Another noteworthy model-agnostic technique is SHapley Additive exPlanations (SHAP), which draws inspiration from cooperative game theory to allocate contributions of each feature to a given prediction. SHAP values provide a fair way to distribute the importance of features, allowing stakeholders to discern the impact of individual factors on the model's decision. This approach is particularly valuable in scenarios where understanding the relative influence of different features is critical.
Model-agnostic explainability techniques offer several advantages, including their applicability to a wide range of machine learning models, from traditional linear models to complex deep neural networks. This universality enables their use across diverse domains and industries, providing a standardized approach to interpretability. However, challenges such as computational complexity and potential information loss during the explanation process underscore the ongoing research efforts to refine and extend these techniques.
Model-agnostic explainability techniques serve as indispensable tools in the pursuit of transparency and interpretability in AI. By fostering a model-agnostic perspective, these approaches contribute to building trust in AI systems and empowering stakeholders to make informed decisions based on a deeper understanding of complex machine learning models.
Inherent Explainability in Machine Learning Models
In the realm of Explainable AI (XAI), the concept of inherent explainability refers to the natural transparency and interpretability embedded within certain machine learning models. Unlike model-agnostic techniques, which aim to provide explanations for any model, inherently explainable models possess features in their design and architecture that make their decision-making processes more accessible and understandable to humans.
Decision trees stand out as a prime example of inherently explainable models. These structures, consisting of a series of hierarchical decisions based on input features, inherently create a decision-making path that can be easily visualized and interpreted. Each node in the tree represents a decision based on a specific feature, allowing users to trace the logic behind the model's predictions. This simplicity and transparency make decision trees especially valuable in applications where a clear rationale for predictions is essential.
Similarly, linear regression models offer inherent explainability due to their straightforward mathematical formulation. The coefficients assigned to each input feature directly indicate the impact of that feature on the model's output. This simplicity not only facilitates interpretation but also allows users to grasp the direction and magnitude of the influence each feature has on the final prediction.
While inherently explainable models have their advantages, they may not always match the predictive performance of more complex, black-box models. Striking a balance between interpretability and accuracy is a crucial consideration, especially in domains where both factors are pivotal. Researchers continue to explore hybrid models that leverage the inherent explainability of simpler models while incorporating elements of complexity to enhance predictive capabilities.
Understanding the nuances of inherently explainable machine learning models provides insights into how transparency can be designed into algorithms. These models play a crucial role in domains where interpretability is paramount, offering a trade-off between simplicity and predictive power. As the AI community navigates the intricacies of building trustworthy and interpretable systems, the exploration of inherently explainable models remains a cornerstone in achieving this delicate balance.
Applications of Explainable AI in Healthcare
Explainable AI (XAI) has emerged as a transformative force within the healthcare sector, promising to enhance the transparency and interpretability of complex machine learning models used in medical applications. One of the primary applications of XAI in healthcare is in diagnostic systems, where decisions regarding disease identification and patient prognosis can have profound implications. By employing model-agnostic techniques or leveraging the inherent explainability of certain models, healthcare practitioners gain insights into the reasoning behind AI-generated predictions.
In medical imaging, XAI plays a pivotal role by elucidating the features and patterns driving a particular diagnosis. For example, in the interpretation of radiological images, XAI techniques can highlight specific regions of interest or provide saliency maps, enabling radiologists to understand which image features contribute most to the AI system's decision. This not only aids in corroborating AI-generated diagnoses but also fosters trust among healthcare professionals who may be skeptical of black-box models.
Furthermore, XAI is instrumental in personalized medicine, where treatment plans are tailored to individual patient characteristics. Explainable models help elucidate the factors influencing treatment recommendations, providing clinicians with a rationale for specific therapeutic interventions. This transparency is particularly crucial when dealing with novel treatments or medications, allowing healthcare providers to weigh the AI-generated insights against their clinical expertise.
However, the adoption of XAI in healthcare is not without challenges, including the need to balance accuracy with interpretability and to ensure that explanations are comprehensible to a diverse audience of healthcare professionals. As the field continues to evolve, the integration of explainable AI into healthcare systems holds promise for improving diagnostic accuracy, personalized treatment plans, and overall trust in the increasingly sophisticated AI tools deployed in the medical domain.
Challenges and Trade-offs in Explainable AI
machine learning models, the pursuit of transparency and interpretability is not without its challenges and trade-offs. One of the primary challenges lies in the inherent tension between model complexity and interpretability. As models become more sophisticated, often transitioning from linear methods to complex neural networks, their ability to capture intricate patterns improves, but at the cost of increased opacity. Striking a balance between the accuracy of predictions and the transparency of the model remains a central challenge in the XAI landscape.
A significant trade-off arises in the choice between model-agnostic and model-specific approaches. Model-agnostic techniques, such as LIME and SHAP, offer a universal solution applicable to various model architectures but may struggle with faithfully representing the intricacies of certain complex models. On the other hand, model-specific methods integrate interpretability directly into the learning process, potentially sacrificing the broad applicability offered by model-agnostic approaches.
The challenge of defining what constitutes a meaningful and comprehensible explanation is another hurdle in the XAI journey. Human-understandable explanations may oversimplify the underlying complexity of a model, leading to information loss, while highly detailed explanations may overwhelm non-expert users. Designing explanations that strike the right balance, conveying essential insights without sacrificing accuracy, remains a nuanced challenge.
Additionally, there is the computational challenge associated with generating explanations, especially in real-time or resource-constrained environments. Model-agnostic techniques often involve the generation of perturbed samples or surrogate models, which can be computationally expensive, limiting their feasibility in certain applications. Balancing the need for detailed explanations with the computational resources available is a practical challenge that researchers and practitioners grapple with.
Addressing these challenges requires a multidisciplinary approach, involving collaboration between researchers, machine learning practitioners, and domain experts. Ongoing research efforts focus on refining existing XAI techniques, developing hybrid models that balance complexity and interpretability, and establishing standards for evaluating the quality of explanations. As the field evolves, understanding and mitigating these challenges will be instrumental in realizing the full potential of Explainable AI across diverse applications and industries.
User-Centric Perspectives on Explainable AI
In the evolving landscape of artificial intelligence, the importance of user-centric perspectives on Explainable AI (XAI) cannot be overstated. As AI systems find their way into various aspects of our lives, ranging from decision support tools to personal assistants, understanding and interpreting machine learning models become crucial for users with varying levels of technical expertise. User-centric XAI places the emphasis on designing systems that not only provide transparent insights into model decisions but also cater to the cognitive and emotional needs of end-users.
Trust is a cornerstone of user acceptance in AI systems, and XAI plays a pivotal role in fostering trust between users and machine learning models. Users are more likely to embrace AI recommendations when they can grasp the rationale behind them. Building trust involves not only providing explanations but also communicating uncertainty and limitations transparently. User-centric XAI thus involves a delicate balance between showcasing the capabilities of AI systems and acknowledging their boundaries.
The ethical dimension of user-centric XAI is paramount. As AI systems impact sensitive domains like finance, healthcare, and criminal justice, ensuring that explanations are fair, unbiased, and free from discriminatory elements becomes imperative. Users should have confidence not only in the accuracy of AI predictions but also in the fairness and ethical considerations embedded within the decision-making process.
User-centric perspectives on Explainable AI acknowledge the pivotal role that end-users play in the deployment and adoption of AI technologies. By prioritizing clear and accessible explanations, building trust, addressing ethical considerations, and involving users in the design process, XAI can transform the perception of AI from a black box to a tool that aligns with human values and preferences.
How to obtain Machine Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Explainable AI (XAI) stands at the forefront of addressing the challenges posed by complex, black-box machine learning models. The quest for transparency and interpretability in AI systems is driven by the need for user trust, accountability, and ethical considerations across diverse applications. Model-agnostic techniques, inherent explainability, and user-centric design principles contribute to a multifaceted approach in unraveling the intricacies of AI decision-making.
Despite the progress made in XAI, challenges persist. The delicate balance between model complexity and interpretability poses an ongoing dilemma, and the trade-offs between model-agnostic and model-specific approaches necessitate careful consideration. Challenges also extend to defining meaningful and comprehensible explanations, managing computational complexities, and ensuring ethical practices in AI deployments.
The application of XAI in specific domains, such as healthcare, illustrates its transformative potential in providing insights into decision-making processes critical to human well-being. By shedding light on the black box, XAI not only enhances the accuracy and reliability of AI systems but also empowers end-users, whether they are healthcare professionals, financial analysts, or individuals interacting with intelligent applications in their daily lives.
Looking forward, the collaborative efforts of researchers, practitioners, and users are pivotal in advancing the field of XAI. As technology continues to evolve, the journey towards explainability must be marked by continual refinement of existing techniques, the exploration of hybrid models, and the establishment of ethical and user-centric standards. Ultimately, the success of XAI lies not only in its technical prowess but also in its ability to humanize the interaction between individuals and artificial intelligence, fostering a future where AI is not merely a black box but a trusted and understandable companion in decision-making processes.
Read More
In recent years, the rapid advancement of machine learning technologies has propelled artificial intelligence (AI) into various facets of our daily lives. From healthcare diagnostics to financial predictions, AI-powered systems are making critical decisions that significantly impact individuals and society at large. However, the inherent complexity of many machine learning models has given rise to a pressing concern: the lack of transparency and interpretability in AI decision-making processes. Enter Explainable AI (XAI), a field dedicated to unraveling the black box nature of these models and providing a clearer understanding of their functioning.
Explainable AI represents a paradigm shift in the AI community, acknowledging the need for more than just predictive accuracy. While highly intricate neural networks and sophisticated algorithms have demonstrated remarkable capabilities, the inability to comprehend and explain their decision-making mechanisms poses significant challenges. XAI seeks to address this challenge by developing methodologies that shed light on the intricate inner workings of machine learning models, allowing stakeholders to decipher the rationale behind AI-driven predictions and classifications.
The demand for explainability in AI arises from various sectors, including healthcare, finance, and legal systems, where the consequences of algorithmic decisions can be profound. In medical diagnoses, for instance, understanding why a particular treatment recommendation was made by an AI system is crucial for gaining the trust of medical practitioners and ensuring patient safety. This necessity for transparency extends beyond expert users to encompass a broader audience, emphasizing the importance of creating AI systems that are not only accurate but also interpretable by individuals with varying degrees of technical expertise. This introduction sets the stage for delving into the realm of Explainable AI, exploring the significance of understanding and interpreting machine learning models in an increasingly AI-driven world
Table of contents
-
Model-Agnostic Explainability Techniques
-
Inherent Explainability in Machine Learning Models
-
Applications of Explainable AI in Healthcare
-
Challenges and Trade-offs in Explainable AI
-
User-Centric Perspectives on Explainable AI
-
Conclusion
Model-Agnostic Explainability Techniques
In the landscape of Explainable AI (XAI), model-agnostic techniques have emerged as powerful tools for unraveling the complexities of machine learning models, regardless of their underlying algorithms. Unlike methods that are intricately tied to specific model architectures, model-agnostic approaches provide a universal lens through which the inner workings of black-box models can be examined and understood.
One prominent example of model-agnostic explainability is the Local Interpretable Model-agnostic Explanations (LIME) framework. LIME operates by generating locally faithful explanations for individual predictions, perturbing the input data and observing the model's response. By fitting an interpretable model to these perturbations, LIME produces a simplified explanation that mirrors the decision-making process of the complex model. This not only makes the prediction more transparent but also facilitates human comprehension of the features driving the model's output.
Another noteworthy model-agnostic technique is SHapley Additive exPlanations (SHAP), which draws inspiration from cooperative game theory to allocate contributions of each feature to a given prediction. SHAP values provide a fair way to distribute the importance of features, allowing stakeholders to discern the impact of individual factors on the model's decision. This approach is particularly valuable in scenarios where understanding the relative influence of different features is critical.
Model-agnostic explainability techniques offer several advantages, including their applicability to a wide range of machine learning models, from traditional linear models to complex deep neural networks. This universality enables their use across diverse domains and industries, providing a standardized approach to interpretability. However, challenges such as computational complexity and potential information loss during the explanation process underscore the ongoing research efforts to refine and extend these techniques.
Model-agnostic explainability techniques serve as indispensable tools in the pursuit of transparency and interpretability in AI. By fostering a model-agnostic perspective, these approaches contribute to building trust in AI systems and empowering stakeholders to make informed decisions based on a deeper understanding of complex machine learning models.
Inherent Explainability in Machine Learning Models
In the realm of Explainable AI (XAI), the concept of inherent explainability refers to the natural transparency and interpretability embedded within certain machine learning models. Unlike model-agnostic techniques, which aim to provide explanations for any model, inherently explainable models possess features in their design and architecture that make their decision-making processes more accessible and understandable to humans.
Decision trees stand out as a prime example of inherently explainable models. These structures, consisting of a series of hierarchical decisions based on input features, inherently create a decision-making path that can be easily visualized and interpreted. Each node in the tree represents a decision based on a specific feature, allowing users to trace the logic behind the model's predictions. This simplicity and transparency make decision trees especially valuable in applications where a clear rationale for predictions is essential.
Similarly, linear regression models offer inherent explainability due to their straightforward mathematical formulation. The coefficients assigned to each input feature directly indicate the impact of that feature on the model's output. This simplicity not only facilitates interpretation but also allows users to grasp the direction and magnitude of the influence each feature has on the final prediction.
While inherently explainable models have their advantages, they may not always match the predictive performance of more complex, black-box models. Striking a balance between interpretability and accuracy is a crucial consideration, especially in domains where both factors are pivotal. Researchers continue to explore hybrid models that leverage the inherent explainability of simpler models while incorporating elements of complexity to enhance predictive capabilities.
Understanding the nuances of inherently explainable machine learning models provides insights into how transparency can be designed into algorithms. These models play a crucial role in domains where interpretability is paramount, offering a trade-off between simplicity and predictive power. As the AI community navigates the intricacies of building trustworthy and interpretable systems, the exploration of inherently explainable models remains a cornerstone in achieving this delicate balance.
Applications of Explainable AI in Healthcare
Explainable AI (XAI) has emerged as a transformative force within the healthcare sector, promising to enhance the transparency and interpretability of complex machine learning models used in medical applications. One of the primary applications of XAI in healthcare is in diagnostic systems, where decisions regarding disease identification and patient prognosis can have profound implications. By employing model-agnostic techniques or leveraging the inherent explainability of certain models, healthcare practitioners gain insights into the reasoning behind AI-generated predictions.
In medical imaging, XAI plays a pivotal role by elucidating the features and patterns driving a particular diagnosis. For example, in the interpretation of radiological images, XAI techniques can highlight specific regions of interest or provide saliency maps, enabling radiologists to understand which image features contribute most to the AI system's decision. This not only aids in corroborating AI-generated diagnoses but also fosters trust among healthcare professionals who may be skeptical of black-box models.
Furthermore, XAI is instrumental in personalized medicine, where treatment plans are tailored to individual patient characteristics. Explainable models help elucidate the factors influencing treatment recommendations, providing clinicians with a rationale for specific therapeutic interventions. This transparency is particularly crucial when dealing with novel treatments or medications, allowing healthcare providers to weigh the AI-generated insights against their clinical expertise.
However, the adoption of XAI in healthcare is not without challenges, including the need to balance accuracy with interpretability and to ensure that explanations are comprehensible to a diverse audience of healthcare professionals. As the field continues to evolve, the integration of explainable AI into healthcare systems holds promise for improving diagnostic accuracy, personalized treatment plans, and overall trust in the increasingly sophisticated AI tools deployed in the medical domain.
Challenges and Trade-offs in Explainable AI
machine learning models, the pursuit of transparency and interpretability is not without its challenges and trade-offs. One of the primary challenges lies in the inherent tension between model complexity and interpretability. As models become more sophisticated, often transitioning from linear methods to complex neural networks, their ability to capture intricate patterns improves, but at the cost of increased opacity. Striking a balance between the accuracy of predictions and the transparency of the model remains a central challenge in the XAI landscape.
A significant trade-off arises in the choice between model-agnostic and model-specific approaches. Model-agnostic techniques, such as LIME and SHAP, offer a universal solution applicable to various model architectures but may struggle with faithfully representing the intricacies of certain complex models. On the other hand, model-specific methods integrate interpretability directly into the learning process, potentially sacrificing the broad applicability offered by model-agnostic approaches.
The challenge of defining what constitutes a meaningful and comprehensible explanation is another hurdle in the XAI journey. Human-understandable explanations may oversimplify the underlying complexity of a model, leading to information loss, while highly detailed explanations may overwhelm non-expert users. Designing explanations that strike the right balance, conveying essential insights without sacrificing accuracy, remains a nuanced challenge.
Additionally, there is the computational challenge associated with generating explanations, especially in real-time or resource-constrained environments. Model-agnostic techniques often involve the generation of perturbed samples or surrogate models, which can be computationally expensive, limiting their feasibility in certain applications. Balancing the need for detailed explanations with the computational resources available is a practical challenge that researchers and practitioners grapple with.
Addressing these challenges requires a multidisciplinary approach, involving collaboration between researchers, machine learning practitioners, and domain experts. Ongoing research efforts focus on refining existing XAI techniques, developing hybrid models that balance complexity and interpretability, and establishing standards for evaluating the quality of explanations. As the field evolves, understanding and mitigating these challenges will be instrumental in realizing the full potential of Explainable AI across diverse applications and industries.
User-Centric Perspectives on Explainable AI
In the evolving landscape of artificial intelligence, the importance of user-centric perspectives on Explainable AI (XAI) cannot be overstated. As AI systems find their way into various aspects of our lives, ranging from decision support tools to personal assistants, understanding and interpreting machine learning models become crucial for users with varying levels of technical expertise. User-centric XAI places the emphasis on designing systems that not only provide transparent insights into model decisions but also cater to the cognitive and emotional needs of end-users.
Trust is a cornerstone of user acceptance in AI systems, and XAI plays a pivotal role in fostering trust between users and machine learning models. Users are more likely to embrace AI recommendations when they can grasp the rationale behind them. Building trust involves not only providing explanations but also communicating uncertainty and limitations transparently. User-centric XAI thus involves a delicate balance between showcasing the capabilities of AI systems and acknowledging their boundaries.
The ethical dimension of user-centric XAI is paramount. As AI systems impact sensitive domains like finance, healthcare, and criminal justice, ensuring that explanations are fair, unbiased, and free from discriminatory elements becomes imperative. Users should have confidence not only in the accuracy of AI predictions but also in the fairness and ethical considerations embedded within the decision-making process.
User-centric perspectives on Explainable AI acknowledge the pivotal role that end-users play in the deployment and adoption of AI technologies. By prioritizing clear and accessible explanations, building trust, addressing ethical considerations, and involving users in the design process, XAI can transform the perception of AI from a black box to a tool that aligns with human values and preferences.
How to obtain Machine Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, Explainable AI (XAI) stands at the forefront of addressing the challenges posed by complex, black-box machine learning models. The quest for transparency and interpretability in AI systems is driven by the need for user trust, accountability, and ethical considerations across diverse applications. Model-agnostic techniques, inherent explainability, and user-centric design principles contribute to a multifaceted approach in unraveling the intricacies of AI decision-making.
Despite the progress made in XAI, challenges persist. The delicate balance between model complexity and interpretability poses an ongoing dilemma, and the trade-offs between model-agnostic and model-specific approaches necessitate careful consideration. Challenges also extend to defining meaningful and comprehensible explanations, managing computational complexities, and ensuring ethical practices in AI deployments.
The application of XAI in specific domains, such as healthcare, illustrates its transformative potential in providing insights into decision-making processes critical to human well-being. By shedding light on the black box, XAI not only enhances the accuracy and reliability of AI systems but also empowers end-users, whether they are healthcare professionals, financial analysts, or individuals interacting with intelligent applications in their daily lives.
Looking forward, the collaborative efforts of researchers, practitioners, and users are pivotal in advancing the field of XAI. As technology continues to evolve, the journey towards explainability must be marked by continual refinement of existing techniques, the exploration of hybrid models, and the establishment of ethical and user-centric standards. Ultimately, the success of XAI lies not only in its technical prowess but also in its ability to humanize the interaction between individuals and artificial intelligence, fostering a future where AI is not merely a black box but a trusted and understandable companion in decision-making processes.
Lean Games and Simulations: Interactive Learning for Lean Principles
In the dynamic landscape of modern business and industry, organizations continually seek innovative approaches to enhance employee learning and development. One such approach gaining widespread recognition is the integration of Lean Games and Simulations as interactive tools for imparting Lean Principles. Lean, rooted in the Toyota Production System, emphasizes efficiency, waste reduction, and continuous improvement. Traditional training methods often fall short in capturing the essence of Lean thinking, making it imperative to explore alternative avenues that engage participants in a more immersive and experiential learning environment.
Lean Games and Simulations represent a departure from conventional training methodologies by providing a hands-on and interactive platform. These activities emulate real-world scenarios, allowing participants to navigate challenges, make decisions, and witness the immediate consequences of their actions. This experiential learning approach not only fosters a deeper understanding of Lean Principles but also cultivates a culture of problem-solving and collaboration within the organization.
The significance of interactive learning in the context of Lean Principles lies in its ability to bridge the gap between theory and practice. Traditional classroom instruction often struggles to convey the practical nuances of Lean thinking, whereas Lean Games and Simulations offer a dynamic space for participants to apply theoretical knowledge in simulated business contexts. This not only enhances comprehension but also equips individuals with the skills to implement Lean practices effectively in their day-to-day work.
Moreover, as organizations increasingly recognize the value of employee engagement in the learning process, Lean Games and Simulations emerge as powerful tools for fostering active participation. The gamification elements inherent in these activities, such as competition, challenges, and rewards, add an element of fun to the learning experience. This not only keeps participants motivated but also contributes to a positive and collaborative learning culture, essential for the successful adoption of Lean Principles.
In this exploration of Lean Games and Simulations, we delve into their role as catalysts for interactive learning, dissecting their impact on participant engagement, skill acquisition, and the overall integration of Lean thinking into organizational practices. As we navigate the interactive landscape of Lean education, we unveil the potential of these tools to revolutionize the way organizations approach training and development in the pursuit of Lean excellence.
Table of contents
-
Design Principles of Lean Games and Simulations
-
Engaging Participants in Lean Simulations
-
Real-world Application and Transferability
-
Measuring the Impact of Interactive Learning
-
Overcoming Challenges in Implementing Lean Games
-
Conclusion
Design Principles of Lean Games and Simulations
Creating effective Lean Games and Simulations requires a thoughtful and strategic approach that aligns with the core principles of Lean thinking. The design process encompasses various elements aimed at delivering an engaging and educational experience for participants. One fundamental principle involves the alignment of simulation scenarios with real-world Lean challenges. By mirroring actual workplace situations, participants can gain hands-on experience in applying Lean Principles to problem-solving, fostering a direct connection between theoretical concepts and practical applications.
Instructional design plays a pivotal role in shaping the effectiveness of Lean Games and Simulations. Sequencing learning activities to reflect the logical progression of Lean Principles ensures that participants grasp foundational concepts before advancing to more complex scenarios. Additionally, the inclusion of interactive elements such as decision-making exercises, problem-solving challenges, and team collaboration activities enhances the overall learning experience. Striking a balance between theoretical content and interactive engagement is crucial to maintaining participant interest and facilitating effective knowledge retention.
Simulation mechanics, including realistic feedback mechanisms, are integral to the design principles of Lean Games. Providing timely and constructive feedback allows participants to understand the consequences of their decisions within the simulated environment. This not only reinforces learning but also encourages a continuous improvement mindset, a cornerstone of Lean thinking. The incorporation of gamification elements, such as scorekeeping, rewards, and competition, adds an element of excitement to the learning process, motivating participants to actively participate and excel in Lean simulations.
Flexibility is another key design principle, allowing for adaptability to diverse learning styles and organizational contexts. Lean Games and Simulations should be scalable and customizable to accommodate various industries, business models, and levels of organizational maturity. This flexibility ensures that the interactive learning experience remains relevant and impactful, irrespective of the specific challenges or nuances faced by different participants or organizations.
The design principles of Lean Games and Simulations revolve around authenticity, instructional design, interactive engagement, feedback mechanisms, flexibility, and the judicious use of technology. When these principles are thoughtfully applied, Lean Games and Simulations become powerful tools for imparting Lean Principles, offering participants a dynamic and immersive learning journey that translates theory into practical skills within the context of their daily work.
Engaging Participants in Lean Simulations
The success of Lean Games and Simulations hinges on the ability to captivate participants and immerse them in a dynamic learning experience. Engaging participants in Lean simulations involves the strategic integration of gamification elements, collaborative activities, and mechanisms that sustain motivation throughout the training process. One crucial aspect is the incorporation of gamification, where game-like elements such as point systems, rewards, and friendly competition are seamlessly woven into the learning framework. This not only injects an element of fun but also incentivizes participants to actively participate, compete, and strive for continuous improvement in their understanding and application of Lean Principles.
Collaboration is a cornerstone of Lean thinking, and Lean Simulations provide an ideal platform to reinforce this principle. Group activities and team-based challenges foster a sense of camaraderie among participants, encouraging them to collaborate and collectively tackle simulated Lean scenarios. This collaborative approach not only mirrors real-world Lean implementations but also cultivates a culture of shared responsibility and problem-solving within the organization.
Furthermore, the dynamic nature of Lean Simulations keeps participants on their toes, preventing monotony and ensuring sustained engagement. By presenting diverse scenarios and challenges that mimic the complexities of real-world Lean environments, participants are compelled to think critically, make informed decisions, and witness the immediate impact of their actions within the simulated context. This active participation not only enhances learning retention but also instills a sense of empowerment, as participants see the tangible results of their contributions to Lean processes.
Engaging participants in Lean Simulations requires a multi-faceted approach that combines gamification, collaboration, dynamic challenges, effective communication, and timely feedback. By immersing participants in an interactive and stimulating learning environment, organizations can ensure that Lean training is not only informative but also enjoyable and conducive to the development of practical skills essential for Lean implementations in the workplace.
Real-world Application and Transferability
The effectiveness of Lean Games and Simulations lies not only in their ability to create engaging learning experiences but also in their potential to bridge the gap between theoretical knowledge and real-world application. Exploring the real-world application and transferability of skills acquired through these interactive learning methods reveals their impact on organizational efficiency and the successful implementation of Lean Principles.
One significant aspect of real-world application is the direct correlation between the scenarios presented in Lean Simulations and the challenges faced in actual workplace environments. Participants gain practical insights into applying Lean Principles to their daily tasks, making informed decisions, and addressing inefficiencies. The simulated experiences serve as a microcosm of real-world complexities, allowing individuals to navigate and understand the intricacies of Lean implementations within the context of their specific roles and responsibilities.
Case studies and success stories provide tangible evidence of how skills cultivated in Lean Games and Simulations seamlessly translate into improved processes and outcomes. Examining instances where organizations have leveraged the acquired knowledge to streamline operations, reduce waste, and enhance overall efficiency underscores the practical impact of interactive learning. The transferability of skills becomes evident as participants bring their newfound understanding of Lean thinking into their roles, contributing to a culture of continuous improvement.
The scalability and adaptability of skills learned in Lean Simulations across diverse contexts and industries underscore the transferability of these competencies. Whether applied in manufacturing, healthcare, finance, or other sectors, the fundamental principles of Lean remain relevant. Organizations can leverage the broad applicability of Lean Games and Simulations to train employees with varied backgrounds, ensuring a consistent and standardized understanding of Lean Principles across the entire workforce.
The real-world application and transferability of skills acquired through Lean Games and Simulations are pivotal in determining the success of these interactive learning methods. The seamless integration of theoretical knowledge into practical skills, the influence on organizational culture, and the adaptability of Lean thinking across diverse industries collectively contribute to the enduring impact of these simulations on organizational efficiency and excellence.
Measuring the Impact of Interactive Learning
Assessing the impact of interactive learning, particularly in the context of Lean Games and Simulations, is a crucial step in determining the effectiveness of these innovative training methods. The measurement process involves a multifaceted approach that encompasses various dimensions to provide a comprehensive understanding of the learning outcomes and their implications for organizational performance.
One primary aspect of impact measurement is the analysis of quantitative data derived from key performance indicators (KPIs) aligned with organizational goals. These KPIs may include metrics such as improved process efficiency, reduced cycle time, decreased waste, or increased employee productivity. By establishing a clear link between the interactive learning experience and tangible organizational improvements, stakeholders can quantify the direct benefits derived from the application of Lean Principles.
Evaluation metrics, both quantitative and qualitative, offer insights into the effectiveness of Lean Games and Simulations at an individual and group level. Pre- and post-assessment tools, quizzes, and surveys provide quantitative data on knowledge acquisition and retention. Additionally, qualitative feedback mechanisms, such as participant testimonials and focus group discussions, capture the subjective experiences and perceived value of the interactive learning journey, offering a more nuanced understanding of its impact.
Long-term behavioral changes represent a critical dimension of impact measurement. Observing how participants integrate Lean thinking into their daily work, collaborate with colleagues, and contribute to continuous improvement initiatives over an extended period provides valuable insights into the lasting influence of interactive learning. This behavioral shift is indicative of a successful transfer of knowledge from simulation environments to the actual workplace.
Learning analytics and data visualization tools play a pivotal role in streamlining the impact measurement process. These tools facilitate the analysis of participant progress, engagement levels, and performance trends over time. By leveraging these data-driven insights, organizations can gain a deeper understanding of how individuals and teams evolve in their application of Lean Principles, enabling informed decisions regarding the optimization of future interactive learning initiatives.
The triangulation of quantitative and qualitative data, along with the observation of long-term behavioral changes, creates a holistic picture of the impact of interactive learning. This comprehensive approach not only validates the efficacy of Lean Games and Simulations but also informs continuous improvement efforts. Organizations can refine and tailor their interactive learning strategies based on the insights gained, ensuring the sustained development of a Lean culture and the continuous enhancement of organizational processes.
Measuring the impact of interactive learning involves a strategic combination of quantitative and qualitative assessments, behavioral observations, and the utilization of learning analytics. By adopting a comprehensive approach to impact measurement, organizations can gauge the success of Lean Games and Simulations in achieving their educational objectives and contributing to tangible improvements in organizational efficiency and performance.
Overcoming Challenges in Implementing Lean Games
The implementation of Lean Games and Simulations, while promising for interactive learning, confronts a series of challenges that organizations must adeptly navigate to optimize their effectiveness. One primary hurdle lies in the resistance to change among employees accustomed to conventional training methodologies. Introducing a paradigm shift through interactive learning necessitates a comprehensive change management plan. Clear communication of the benefits, addressing concerns, and emphasizing the practical relevance of Lean Games are essential components in overcoming this initial resistance. Engaging key stakeholders as advocates for the adoption of Lean Games contributes to building a positive narrative around this transformative learning approach.
Another critical challenge involves technological barriers that may impede the seamless integration of Lean Games. Outdated or incompatible systems can adversely affect accessibility and user experience. To overcome this, organizations should invest in user-friendly, accessible technologies aligned with the capabilities of their workforce. Simultaneously, providing comprehensive training and support ensures participants can effectively navigate the technological platforms, promoting a smoother implementation process.
Customizing Lean Games to suit diverse industry contexts and organizational nuances poses another notable challenge. To address this, organizations must develop Lean Games that are adaptable and customizable. This flexibility allows for the tailoring of scenarios to specific industry challenges, ensuring that the interactive learning experience remains relevant across varied sectors. Collaborating with subject matter experts from different domains during the design phase ensures the incorporation of industry-specific nuances.
Widespread accessibility, especially in organizations with geographically dispersed teams, presents a logistical challenge. Virtual collaboration tools can help facilitate remote participation, but additional considerations, such as scheduling sessions to accommodate different time zones and ensuring user-friendly technology, are crucial. The incorporation of asynchronous elements enables self-paced learning, addressing accessibility issues and promoting inclusivity.
Sustaining participant engagement over time is a challenge that requires ongoing attention. Participants may experience fatigue or disinterest, impacting the effectiveness of Lean Games. Regular updates to simulation scenarios, introduction of new challenges, and incorporation of participant feedback are strategies to maintain interest. Implementing a gamification strategy, including rewards, recognition, and friendly competition, serves to motivate continued engagement and reinforces the enjoyment of the learning process.
Overcoming challenges in implementing Lean Games demands a strategic and holistic approach. By addressing resistance to change, tackling technological barriers, ensuring customization for diverse contexts, promoting accessibility, and sustaining participant engagement, organizations can successfully integrate Lean Games and Simulations into their training programs. These efforts not only enhance the learning experience but also contribute to the broader goal of instilling a Lean mindset and improving organizational efficiency.
Conclusion
The exploration of Lean Games and Simulations as interactive learning tools for Lean Principles reveals a landscape rich with potential and transformative opportunities. As organizations strive to cultivate a culture of continuous improvement and operational excellence, the challenges encountered in implementing these innovative methods underscore the importance of a strategic and adaptive approach.
the journey through Lean Games and Simulations is a dynamic and evolving one. By navigating and overcoming challenges, organizations position themselves at the forefront of innovative training methodologies, fostering a culture of continuous improvement and adaptability. The commitment to addressing resistance, technological barriers, customization needs, accessibility, and sustained engagement ensures that Lean Games become not just a training tool but a catalyst for transformative change within organizations. Through these efforts, organizations can pave the way for a future where Lean thinking is ingrained in the fabric of the workforce, driving excellence and efficiency across all facets of the organizational landscape.
Read More
In the dynamic landscape of modern business and industry, organizations continually seek innovative approaches to enhance employee learning and development. One such approach gaining widespread recognition is the integration of Lean Games and Simulations as interactive tools for imparting Lean Principles. Lean, rooted in the Toyota Production System, emphasizes efficiency, waste reduction, and continuous improvement. Traditional training methods often fall short in capturing the essence of Lean thinking, making it imperative to explore alternative avenues that engage participants in a more immersive and experiential learning environment.
Lean Games and Simulations represent a departure from conventional training methodologies by providing a hands-on and interactive platform. These activities emulate real-world scenarios, allowing participants to navigate challenges, make decisions, and witness the immediate consequences of their actions. This experiential learning approach not only fosters a deeper understanding of Lean Principles but also cultivates a culture of problem-solving and collaboration within the organization.
The significance of interactive learning in the context of Lean Principles lies in its ability to bridge the gap between theory and practice. Traditional classroom instruction often struggles to convey the practical nuances of Lean thinking, whereas Lean Games and Simulations offer a dynamic space for participants to apply theoretical knowledge in simulated business contexts. This not only enhances comprehension but also equips individuals with the skills to implement Lean practices effectively in their day-to-day work.
Moreover, as organizations increasingly recognize the value of employee engagement in the learning process, Lean Games and Simulations emerge as powerful tools for fostering active participation. The gamification elements inherent in these activities, such as competition, challenges, and rewards, add an element of fun to the learning experience. This not only keeps participants motivated but also contributes to a positive and collaborative learning culture, essential for the successful adoption of Lean Principles.
In this exploration of Lean Games and Simulations, we delve into their role as catalysts for interactive learning, dissecting their impact on participant engagement, skill acquisition, and the overall integration of Lean thinking into organizational practices. As we navigate the interactive landscape of Lean education, we unveil the potential of these tools to revolutionize the way organizations approach training and development in the pursuit of Lean excellence.
Table of contents
-
Design Principles of Lean Games and Simulations
-
Engaging Participants in Lean Simulations
-
Real-world Application and Transferability
-
Measuring the Impact of Interactive Learning
-
Overcoming Challenges in Implementing Lean Games
-
Conclusion
Design Principles of Lean Games and Simulations
Creating effective Lean Games and Simulations requires a thoughtful and strategic approach that aligns with the core principles of Lean thinking. The design process encompasses various elements aimed at delivering an engaging and educational experience for participants. One fundamental principle involves the alignment of simulation scenarios with real-world Lean challenges. By mirroring actual workplace situations, participants can gain hands-on experience in applying Lean Principles to problem-solving, fostering a direct connection between theoretical concepts and practical applications.
Instructional design plays a pivotal role in shaping the effectiveness of Lean Games and Simulations. Sequencing learning activities to reflect the logical progression of Lean Principles ensures that participants grasp foundational concepts before advancing to more complex scenarios. Additionally, the inclusion of interactive elements such as decision-making exercises, problem-solving challenges, and team collaboration activities enhances the overall learning experience. Striking a balance between theoretical content and interactive engagement is crucial to maintaining participant interest and facilitating effective knowledge retention.
Simulation mechanics, including realistic feedback mechanisms, are integral to the design principles of Lean Games. Providing timely and constructive feedback allows participants to understand the consequences of their decisions within the simulated environment. This not only reinforces learning but also encourages a continuous improvement mindset, a cornerstone of Lean thinking. The incorporation of gamification elements, such as scorekeeping, rewards, and competition, adds an element of excitement to the learning process, motivating participants to actively participate and excel in Lean simulations.
Flexibility is another key design principle, allowing for adaptability to diverse learning styles and organizational contexts. Lean Games and Simulations should be scalable and customizable to accommodate various industries, business models, and levels of organizational maturity. This flexibility ensures that the interactive learning experience remains relevant and impactful, irrespective of the specific challenges or nuances faced by different participants or organizations.
The design principles of Lean Games and Simulations revolve around authenticity, instructional design, interactive engagement, feedback mechanisms, flexibility, and the judicious use of technology. When these principles are thoughtfully applied, Lean Games and Simulations become powerful tools for imparting Lean Principles, offering participants a dynamic and immersive learning journey that translates theory into practical skills within the context of their daily work.
Engaging Participants in Lean Simulations
The success of Lean Games and Simulations hinges on the ability to captivate participants and immerse them in a dynamic learning experience. Engaging participants in Lean simulations involves the strategic integration of gamification elements, collaborative activities, and mechanisms that sustain motivation throughout the training process. One crucial aspect is the incorporation of gamification, where game-like elements such as point systems, rewards, and friendly competition are seamlessly woven into the learning framework. This not only injects an element of fun but also incentivizes participants to actively participate, compete, and strive for continuous improvement in their understanding and application of Lean Principles.
Collaboration is a cornerstone of Lean thinking, and Lean Simulations provide an ideal platform to reinforce this principle. Group activities and team-based challenges foster a sense of camaraderie among participants, encouraging them to collaborate and collectively tackle simulated Lean scenarios. This collaborative approach not only mirrors real-world Lean implementations but also cultivates a culture of shared responsibility and problem-solving within the organization.
Furthermore, the dynamic nature of Lean Simulations keeps participants on their toes, preventing monotony and ensuring sustained engagement. By presenting diverse scenarios and challenges that mimic the complexities of real-world Lean environments, participants are compelled to think critically, make informed decisions, and witness the immediate impact of their actions within the simulated context. This active participation not only enhances learning retention but also instills a sense of empowerment, as participants see the tangible results of their contributions to Lean processes.
Engaging participants in Lean Simulations requires a multi-faceted approach that combines gamification, collaboration, dynamic challenges, effective communication, and timely feedback. By immersing participants in an interactive and stimulating learning environment, organizations can ensure that Lean training is not only informative but also enjoyable and conducive to the development of practical skills essential for Lean implementations in the workplace.
Real-world Application and Transferability
The effectiveness of Lean Games and Simulations lies not only in their ability to create engaging learning experiences but also in their potential to bridge the gap between theoretical knowledge and real-world application. Exploring the real-world application and transferability of skills acquired through these interactive learning methods reveals their impact on organizational efficiency and the successful implementation of Lean Principles.
One significant aspect of real-world application is the direct correlation between the scenarios presented in Lean Simulations and the challenges faced in actual workplace environments. Participants gain practical insights into applying Lean Principles to their daily tasks, making informed decisions, and addressing inefficiencies. The simulated experiences serve as a microcosm of real-world complexities, allowing individuals to navigate and understand the intricacies of Lean implementations within the context of their specific roles and responsibilities.
Case studies and success stories provide tangible evidence of how skills cultivated in Lean Games and Simulations seamlessly translate into improved processes and outcomes. Examining instances where organizations have leveraged the acquired knowledge to streamline operations, reduce waste, and enhance overall efficiency underscores the practical impact of interactive learning. The transferability of skills becomes evident as participants bring their newfound understanding of Lean thinking into their roles, contributing to a culture of continuous improvement.
The scalability and adaptability of skills learned in Lean Simulations across diverse contexts and industries underscore the transferability of these competencies. Whether applied in manufacturing, healthcare, finance, or other sectors, the fundamental principles of Lean remain relevant. Organizations can leverage the broad applicability of Lean Games and Simulations to train employees with varied backgrounds, ensuring a consistent and standardized understanding of Lean Principles across the entire workforce.
The real-world application and transferability of skills acquired through Lean Games and Simulations are pivotal in determining the success of these interactive learning methods. The seamless integration of theoretical knowledge into practical skills, the influence on organizational culture, and the adaptability of Lean thinking across diverse industries collectively contribute to the enduring impact of these simulations on organizational efficiency and excellence.
Measuring the Impact of Interactive Learning
Assessing the impact of interactive learning, particularly in the context of Lean Games and Simulations, is a crucial step in determining the effectiveness of these innovative training methods. The measurement process involves a multifaceted approach that encompasses various dimensions to provide a comprehensive understanding of the learning outcomes and their implications for organizational performance.
One primary aspect of impact measurement is the analysis of quantitative data derived from key performance indicators (KPIs) aligned with organizational goals. These KPIs may include metrics such as improved process efficiency, reduced cycle time, decreased waste, or increased employee productivity. By establishing a clear link between the interactive learning experience and tangible organizational improvements, stakeholders can quantify the direct benefits derived from the application of Lean Principles.
Evaluation metrics, both quantitative and qualitative, offer insights into the effectiveness of Lean Games and Simulations at an individual and group level. Pre- and post-assessment tools, quizzes, and surveys provide quantitative data on knowledge acquisition and retention. Additionally, qualitative feedback mechanisms, such as participant testimonials and focus group discussions, capture the subjective experiences and perceived value of the interactive learning journey, offering a more nuanced understanding of its impact.
Long-term behavioral changes represent a critical dimension of impact measurement. Observing how participants integrate Lean thinking into their daily work, collaborate with colleagues, and contribute to continuous improvement initiatives over an extended period provides valuable insights into the lasting influence of interactive learning. This behavioral shift is indicative of a successful transfer of knowledge from simulation environments to the actual workplace.
Learning analytics and data visualization tools play a pivotal role in streamlining the impact measurement process. These tools facilitate the analysis of participant progress, engagement levels, and performance trends over time. By leveraging these data-driven insights, organizations can gain a deeper understanding of how individuals and teams evolve in their application of Lean Principles, enabling informed decisions regarding the optimization of future interactive learning initiatives.
The triangulation of quantitative and qualitative data, along with the observation of long-term behavioral changes, creates a holistic picture of the impact of interactive learning. This comprehensive approach not only validates the efficacy of Lean Games and Simulations but also informs continuous improvement efforts. Organizations can refine and tailor their interactive learning strategies based on the insights gained, ensuring the sustained development of a Lean culture and the continuous enhancement of organizational processes.
Measuring the impact of interactive learning involves a strategic combination of quantitative and qualitative assessments, behavioral observations, and the utilization of learning analytics. By adopting a comprehensive approach to impact measurement, organizations can gauge the success of Lean Games and Simulations in achieving their educational objectives and contributing to tangible improvements in organizational efficiency and performance.
Overcoming Challenges in Implementing Lean Games
The implementation of Lean Games and Simulations, while promising for interactive learning, confronts a series of challenges that organizations must adeptly navigate to optimize their effectiveness. One primary hurdle lies in the resistance to change among employees accustomed to conventional training methodologies. Introducing a paradigm shift through interactive learning necessitates a comprehensive change management plan. Clear communication of the benefits, addressing concerns, and emphasizing the practical relevance of Lean Games are essential components in overcoming this initial resistance. Engaging key stakeholders as advocates for the adoption of Lean Games contributes to building a positive narrative around this transformative learning approach.
Another critical challenge involves technological barriers that may impede the seamless integration of Lean Games. Outdated or incompatible systems can adversely affect accessibility and user experience. To overcome this, organizations should invest in user-friendly, accessible technologies aligned with the capabilities of their workforce. Simultaneously, providing comprehensive training and support ensures participants can effectively navigate the technological platforms, promoting a smoother implementation process.
Customizing Lean Games to suit diverse industry contexts and organizational nuances poses another notable challenge. To address this, organizations must develop Lean Games that are adaptable and customizable. This flexibility allows for the tailoring of scenarios to specific industry challenges, ensuring that the interactive learning experience remains relevant across varied sectors. Collaborating with subject matter experts from different domains during the design phase ensures the incorporation of industry-specific nuances.
Widespread accessibility, especially in organizations with geographically dispersed teams, presents a logistical challenge. Virtual collaboration tools can help facilitate remote participation, but additional considerations, such as scheduling sessions to accommodate different time zones and ensuring user-friendly technology, are crucial. The incorporation of asynchronous elements enables self-paced learning, addressing accessibility issues and promoting inclusivity.
Sustaining participant engagement over time is a challenge that requires ongoing attention. Participants may experience fatigue or disinterest, impacting the effectiveness of Lean Games. Regular updates to simulation scenarios, introduction of new challenges, and incorporation of participant feedback are strategies to maintain interest. Implementing a gamification strategy, including rewards, recognition, and friendly competition, serves to motivate continued engagement and reinforces the enjoyment of the learning process.
Overcoming challenges in implementing Lean Games demands a strategic and holistic approach. By addressing resistance to change, tackling technological barriers, ensuring customization for diverse contexts, promoting accessibility, and sustaining participant engagement, organizations can successfully integrate Lean Games and Simulations into their training programs. These efforts not only enhance the learning experience but also contribute to the broader goal of instilling a Lean mindset and improving organizational efficiency.
Conclusion
The exploration of Lean Games and Simulations as interactive learning tools for Lean Principles reveals a landscape rich with potential and transformative opportunities. As organizations strive to cultivate a culture of continuous improvement and operational excellence, the challenges encountered in implementing these innovative methods underscore the importance of a strategic and adaptive approach.
the journey through Lean Games and Simulations is a dynamic and evolving one. By navigating and overcoming challenges, organizations position themselves at the forefront of innovative training methodologies, fostering a culture of continuous improvement and adaptability. The commitment to addressing resistance, technological barriers, customization needs, accessibility, and sustained engagement ensures that Lean Games become not just a training tool but a catalyst for transformative change within organizations. Through these efforts, organizations can pave the way for a future where Lean thinking is ingrained in the fabric of the workforce, driving excellence and efficiency across all facets of the organizational landscape.
EXIN Cloud Computing and Compliance: Ensuring Regulatory Adherence in the Cloud
Cloud computing has emerged as a transformative force in the realm of information technology, revolutionizing the way organizations manage and deploy their digital infrastructure. As businesses increasingly migrate to cloud-based solutions to enhance agility, scalability, and cost-efficiency, the need for comprehensive regulatory adherence within the cloud environment becomes paramount. The intersection of cloud computing and compliance brings forth a unique set of challenges and opportunities, necessitating a thorough understanding of the regulatory landscape and the implementation of robust frameworks to ensure adherence.
In this context, EXIN Cloud Computing and Compliance stands out as a critical domain where organizations navigate the complexities of regulatory requirements while harnessing the benefits of cloud technologies. EXIN, a globally recognized certification and accreditation body, plays a pivotal role in establishing industry standards and best practices, providing professionals with the knowledge and skills required to effectively address the intricate relationship between cloud computing and regulatory compliance.
This exploration delves into the core principles and practices encompassed by EXIN Cloud Computing and Compliance. From the fundamental concepts of cloud computing to the intricacies of diverse regulatory frameworks, this examination aims to shed light on how organizations can successfully navigate the regulatory landscape within the dynamic and ever-evolving cloud environment. By ensuring regulatory adherence in the cloud, businesses can not only mitigate legal and security risks but also foster trust among stakeholders and demonstrate a commitment to ethical and responsible data management practices.
Table of contents
-
Security Measures in Cloud Compliance
-
Continuous Compliance Monitoring and Auditing
-
Legal and Ethical Considerations in Cloud Computing
-
Risk Management in Cloud Compliance
-
Future Trends in Cloud Compliance
-
Conclusion
Security Measures in Cloud Compliance
In the ever-expanding realm of cloud computing, the integration of robust security measures plays a pivotal role in ensuring regulatory compliance and fortifying the protection of sensitive data. Security considerations within the context of cloud compliance extend beyond conventional approaches, addressing the challenges posed by the dynamic and distributed nature of cloud environments. A fundamental aspect of this security strategy involves the implementation of encryption protocols, safeguarding data both during transit and while at rest, thereby forming a critical foundation within compliance frameworks.
w. Regular assessments not only validate conformity to regulatory standards but also empower organizations to swiftly identify and rectify potential vulnerabilities. This proactive stance is essential for maintaining a secure cloud infrastructure and responding effectively to the constantly evolving threat landscape. Augmenting these efforts are advanced threat detection mechanisms and robust incident response plans, which collectively reinforce organizations against security breaches, contributing to a more secure and compliant cloud environment.
The nexus of legal and ethical considerations further underscores the significance of security in cloud compliance. Compliance efforts extend beyond technical safeguards to encompass contractual agreements and ethical standards related to data ownership and privacy. The alignment of legal requirements with robust security protocols ensures a comprehensive framework that meets regulatory expectations while fostering a trustworthy and responsible cloud ecosystem.
Looking forward, the trajectory of security measures in cloud compliance involves a keen awareness of emerging trends and technologies. The evolution of cloud computing introduces new challenges and opportunities in securing cloud-based infrastructures. Proactive adoption of cutting-edge security technologies, anticipation of regulatory changes, and adaptive security postures position organizations to navigate the dynamic cybersecurity landscape in the cloud effectively. Through a holistic and adaptive approach to security measures, organizations not only ensure compliance but also bolster their resilience against the evolving threats in the cloud.
Continuous Compliance Monitoring and Auditing
Continuous compliance monitoring and auditing represent crucial components of an organization's strategy to maintain a secure and regulatory-compliant cloud computing environment. Traditional compliance assessments conducted at fixed intervals are insufficient in the dynamic and ever-evolving landscape of the cloud. Therefore, adopting continuous monitoring practices becomes imperative to promptly identify and address potential compliance issues, ensuring a proactive and responsive stance.
Continuous compliance monitoring involves the real-time assessment of cloud infrastructure, applications, and data to ensure adherence to regulatory standards. This ongoing scrutiny enables organizations to detect deviations from compliance norms as they occur, reducing the time window for potential security vulnerabilities. Automated tools and systems play a pivotal role in this process, constantly scanning for anomalies, unauthorized access, and other indicators of non-compliance.
Auditing, in the context of cloud computing, is a systematic examination of an organization's cloud-based processes, controls, and data to validate compliance with established standards and regulations. While traditional audits may have been periodic, the cloud demands a more agile and iterative approach. Continuous auditing leverages automation to conduct regular assessments, providing real-time insights into compliance levels and allowing organizations to make timely adjustments.
Continuous compliance monitoring and auditing in the cloud reflect a paradigm shift towards a more proactive and responsive security strategy. By embracing real-time assessment and leveraging automated tools, organizations can navigate the complexities of the cloud environment while meeting regulatory requirements and enhancing overall cybersecurity resilience. This dynamic approach aligns with the agile nature of cloud computing and positions organizations to adapt swiftly to the evolving threat landscape.
Legal and Ethical Considerations in Cloud Computing
Legal and ethical considerations in cloud computing constitute a critical dimension of the evolving digital landscape, requiring organizations to navigate complex frameworks to ensure responsible and compliant practices. From a legal standpoint, cloud computing intersects with various jurisdictions, each with its own set of regulations governing data protection, privacy, and intellectual property. Compliance with these legal requirements is not only a legal obligation but also a crucial element in building trust among users, customers, and regulatory bodies. Legal considerations encompass contractual agreements with cloud service providers, defining the terms of data ownership, access, and compliance with specific regulatory standards.
Ethical considerations in cloud computing extend beyond legal obligations and delve into the broader ethical implications of data management, privacy, and artificial intelligence. Organizations operating in the cloud must grapple with questions of transparency, fairness, and accountability in their use of technology. Ethical practices involve ensuring that data is handled responsibly, respecting user privacy rights, and incorporating fairness and accountability into algorithms and decision-making processes. Striking a balance between leveraging the benefits of cloud computing and upholding ethical standards is essential for building a sustainable and trustworthy digital ecosystem.
The intersection of legal and ethical considerations also encompasses issues such as data sovereignty and cross-border data transfers. Organizations must navigate international laws and regulations to determine where data is stored and processed, ensuring compliance with diverse legal frameworks. Ethical considerations in this context involve respecting cultural norms and values, acknowledging the potential impact of technology on society, and avoiding practices that may lead to discriminatory outcomes.
Legal and ethical considerations are integral to the responsible adoption of cloud computing. By navigating the complex legal landscape, respecting user privacy, and upholding ethical principles, organizations can foster a trustworthy and sustainable cloud environment. Achieving a balance between legal compliance and ethical conduct not only mitigates legal risks but also contributes to building a positive reputation and maintaining the integrity of the digital ecosystem.
Risk Management in Cloud Compliance
Risk management in the context of cloud compliance is a fundamental and strategic approach that organizations employ to navigate the intricate landscape of potential threats and vulnerabilities associated with cloud computing. As businesses increasingly rely on cloud services, understanding and mitigating risks become paramount to ensure the security and compliance of sensitive data. Risk management involves the systematic identification, assessment, and prioritization of potential risks, followed by the implementation of strategies to minimize, control, or transfer these risks.
An essential aspect of risk management in cloud compliance is the continuous monitoring and assessment of potential risks. This involves the implementation of advanced threat detection mechanisms, real-time monitoring tools, and regular audits to identify emerging risks promptly. By adopting a proactive stance, organizations can address vulnerabilities in their cloud infrastructure before they escalate into significant security or compliance incidents.
Effective risk management in cloud compliance is a dynamic and proactive process that empowers organizations to identify, assess, and address potential risks in the cloud environment. By integrating risk management practices into their compliance strategies, organizations can fortify their security postures, meet regulatory requirements, and foster a resilient and secure cloud infrastructure.
Future Trends in Cloud Compliance
Anticipating the future trends in cloud compliance reveals a landscape shaped by technological advancements and a growing need for organizations to seamlessly align with regulatory standards. One of the prominent trends is the integration of edge computing into compliance frameworks. As edge computing becomes more prevalent, compliance measures are likely to evolve to accommodate the distributed nature of data processing at the edge. Organizations will need to adapt their strategies to ensure that compliance remains robust and effective in these decentralized computing environments.
Blockchain technology is expected to play a transformative role in enhancing both security and transparency in cloud compliance. The decentralized and tamper-resistant nature of blockchain can be leveraged to create immutable audit trails, providing transparent reporting and ensuring the integrity of data stored in the cloud. As smart contracts on blockchain platforms gain prominence, there is potential for automating specific compliance processes, streamlining and enhancing the overall compliance lifecycle.
Artificial intelligence (AI) and machine learning (ML) are poised to take center stage in the future of cloud compliance, particularly in the realm of continuous monitoring and risk assessment. Advanced analytics powered by AI and ML algorithms can offer real-time insights into compliance status, detect anomalies, and even predict potential risks. The integration of automated compliance monitoring driven by intelligent technologies has the potential to significantly improve the efficiency and accuracy of compliance management processes.
The future trends in cloud compliance are marked by a convergence of technologies, including edge computing, blockchain, AI, and automation. Adapting to these trends will not only be essential for maintaining regulatory adherence but also for harnessing the full potential of cloud technologies in a secure and compliant manner. Organizations that embrace these trends proactively will be better positioned to navigate the complexities of the evolving compliance landscape in the digital age.
How to obtain EXIN Cloud Computing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the landscape of cloud computing and compliance is evolving rapidly, driven by technological innovations, regulatory developments, and the increasing complexity of the digital environment. The intersection of these factors necessitates a strategic and adaptive approach to ensure the secure and compliant utilization of cloud technologies. The exploration of EXIN Cloud Computing and Compliance has shed light on key facets, from foundational principles and regulatory landscapes to the integration of security measures, continuous monitoring, and future trends.
Security measures in the cloud are paramount, requiring robust encryption, continuous monitoring, and proactive incident response to safeguard sensitive data. Continuous compliance monitoring and auditing have emerged as indispensable practices, offering real-time insights and ensuring organizations stay ahead of potential compliance risks. Legal and ethical considerations underscore the importance of transparent data practices, responsible use of technology, and adherence to diverse regulatory frameworks.
Risk management in cloud compliance is a dynamic and proactive process, essential for identifying, assessing, and addressing potential threats and vulnerabilities. As organizations navigate the complexities of cloud computing, future trends, including edge computing integration, blockchain for enhanced security, AI-driven compliance monitoring, and the adoption of Compliance as Code, are poised to shape the landscape.
Looking ahead, the convergence of these trends presents both challenges and opportunities. Organizations that embrace these changes stand to enhance their cybersecurity resilience, meet evolving regulatory requirements, and leverage the transformative potential of cloud technologies. The future of cloud compliance lies in a balanced and adaptive approach, where innovation and regulatory adherence coexist seamlessly, fostering a trustworthy and sustainable digital ecosystem. As organizations navigate this evolving landscape, the synergy between technological advancements and compliance best practices will be paramount to ensuring a secure, compliant, and resilient future in the cloud.
Read More
Cloud computing has emerged as a transformative force in the realm of information technology, revolutionizing the way organizations manage and deploy their digital infrastructure. As businesses increasingly migrate to cloud-based solutions to enhance agility, scalability, and cost-efficiency, the need for comprehensive regulatory adherence within the cloud environment becomes paramount. The intersection of cloud computing and compliance brings forth a unique set of challenges and opportunities, necessitating a thorough understanding of the regulatory landscape and the implementation of robust frameworks to ensure adherence.
In this context, EXIN Cloud Computing and Compliance stands out as a critical domain where organizations navigate the complexities of regulatory requirements while harnessing the benefits of cloud technologies. EXIN, a globally recognized certification and accreditation body, plays a pivotal role in establishing industry standards and best practices, providing professionals with the knowledge and skills required to effectively address the intricate relationship between cloud computing and regulatory compliance.
This exploration delves into the core principles and practices encompassed by EXIN Cloud Computing and Compliance. From the fundamental concepts of cloud computing to the intricacies of diverse regulatory frameworks, this examination aims to shed light on how organizations can successfully navigate the regulatory landscape within the dynamic and ever-evolving cloud environment. By ensuring regulatory adherence in the cloud, businesses can not only mitigate legal and security risks but also foster trust among stakeholders and demonstrate a commitment to ethical and responsible data management practices.
Table of contents
-
Security Measures in Cloud Compliance
-
Continuous Compliance Monitoring and Auditing
-
Legal and Ethical Considerations in Cloud Computing
-
Risk Management in Cloud Compliance
-
Future Trends in Cloud Compliance
-
Conclusion
Security Measures in Cloud Compliance
In the ever-expanding realm of cloud computing, the integration of robust security measures plays a pivotal role in ensuring regulatory compliance and fortifying the protection of sensitive data. Security considerations within the context of cloud compliance extend beyond conventional approaches, addressing the challenges posed by the dynamic and distributed nature of cloud environments. A fundamental aspect of this security strategy involves the implementation of encryption protocols, safeguarding data both during transit and while at rest, thereby forming a critical foundation within compliance frameworks.
w. Regular assessments not only validate conformity to regulatory standards but also empower organizations to swiftly identify and rectify potential vulnerabilities. This proactive stance is essential for maintaining a secure cloud infrastructure and responding effectively to the constantly evolving threat landscape. Augmenting these efforts are advanced threat detection mechanisms and robust incident response plans, which collectively reinforce organizations against security breaches, contributing to a more secure and compliant cloud environment.
The nexus of legal and ethical considerations further underscores the significance of security in cloud compliance. Compliance efforts extend beyond technical safeguards to encompass contractual agreements and ethical standards related to data ownership and privacy. The alignment of legal requirements with robust security protocols ensures a comprehensive framework that meets regulatory expectations while fostering a trustworthy and responsible cloud ecosystem.
Looking forward, the trajectory of security measures in cloud compliance involves a keen awareness of emerging trends and technologies. The evolution of cloud computing introduces new challenges and opportunities in securing cloud-based infrastructures. Proactive adoption of cutting-edge security technologies, anticipation of regulatory changes, and adaptive security postures position organizations to navigate the dynamic cybersecurity landscape in the cloud effectively. Through a holistic and adaptive approach to security measures, organizations not only ensure compliance but also bolster their resilience against the evolving threats in the cloud.
Continuous Compliance Monitoring and Auditing
Continuous compliance monitoring and auditing represent crucial components of an organization's strategy to maintain a secure and regulatory-compliant cloud computing environment. Traditional compliance assessments conducted at fixed intervals are insufficient in the dynamic and ever-evolving landscape of the cloud. Therefore, adopting continuous monitoring practices becomes imperative to promptly identify and address potential compliance issues, ensuring a proactive and responsive stance.
Continuous compliance monitoring involves the real-time assessment of cloud infrastructure, applications, and data to ensure adherence to regulatory standards. This ongoing scrutiny enables organizations to detect deviations from compliance norms as they occur, reducing the time window for potential security vulnerabilities. Automated tools and systems play a pivotal role in this process, constantly scanning for anomalies, unauthorized access, and other indicators of non-compliance.
Auditing, in the context of cloud computing, is a systematic examination of an organization's cloud-based processes, controls, and data to validate compliance with established standards and regulations. While traditional audits may have been periodic, the cloud demands a more agile and iterative approach. Continuous auditing leverages automation to conduct regular assessments, providing real-time insights into compliance levels and allowing organizations to make timely adjustments.
Continuous compliance monitoring and auditing in the cloud reflect a paradigm shift towards a more proactive and responsive security strategy. By embracing real-time assessment and leveraging automated tools, organizations can navigate the complexities of the cloud environment while meeting regulatory requirements and enhancing overall cybersecurity resilience. This dynamic approach aligns with the agile nature of cloud computing and positions organizations to adapt swiftly to the evolving threat landscape.
Legal and Ethical Considerations in Cloud Computing
Legal and ethical considerations in cloud computing constitute a critical dimension of the evolving digital landscape, requiring organizations to navigate complex frameworks to ensure responsible and compliant practices. From a legal standpoint, cloud computing intersects with various jurisdictions, each with its own set of regulations governing data protection, privacy, and intellectual property. Compliance with these legal requirements is not only a legal obligation but also a crucial element in building trust among users, customers, and regulatory bodies. Legal considerations encompass contractual agreements with cloud service providers, defining the terms of data ownership, access, and compliance with specific regulatory standards.
Ethical considerations in cloud computing extend beyond legal obligations and delve into the broader ethical implications of data management, privacy, and artificial intelligence. Organizations operating in the cloud must grapple with questions of transparency, fairness, and accountability in their use of technology. Ethical practices involve ensuring that data is handled responsibly, respecting user privacy rights, and incorporating fairness and accountability into algorithms and decision-making processes. Striking a balance between leveraging the benefits of cloud computing and upholding ethical standards is essential for building a sustainable and trustworthy digital ecosystem.
The intersection of legal and ethical considerations also encompasses issues such as data sovereignty and cross-border data transfers. Organizations must navigate international laws and regulations to determine where data is stored and processed, ensuring compliance with diverse legal frameworks. Ethical considerations in this context involve respecting cultural norms and values, acknowledging the potential impact of technology on society, and avoiding practices that may lead to discriminatory outcomes.
Legal and ethical considerations are integral to the responsible adoption of cloud computing. By navigating the complex legal landscape, respecting user privacy, and upholding ethical principles, organizations can foster a trustworthy and sustainable cloud environment. Achieving a balance between legal compliance and ethical conduct not only mitigates legal risks but also contributes to building a positive reputation and maintaining the integrity of the digital ecosystem.
Risk Management in Cloud Compliance
Risk management in the context of cloud compliance is a fundamental and strategic approach that organizations employ to navigate the intricate landscape of potential threats and vulnerabilities associated with cloud computing. As businesses increasingly rely on cloud services, understanding and mitigating risks become paramount to ensure the security and compliance of sensitive data. Risk management involves the systematic identification, assessment, and prioritization of potential risks, followed by the implementation of strategies to minimize, control, or transfer these risks.
An essential aspect of risk management in cloud compliance is the continuous monitoring and assessment of potential risks. This involves the implementation of advanced threat detection mechanisms, real-time monitoring tools, and regular audits to identify emerging risks promptly. By adopting a proactive stance, organizations can address vulnerabilities in their cloud infrastructure before they escalate into significant security or compliance incidents.
Effective risk management in cloud compliance is a dynamic and proactive process that empowers organizations to identify, assess, and address potential risks in the cloud environment. By integrating risk management practices into their compliance strategies, organizations can fortify their security postures, meet regulatory requirements, and foster a resilient and secure cloud infrastructure.
Future Trends in Cloud Compliance
Anticipating the future trends in cloud compliance reveals a landscape shaped by technological advancements and a growing need for organizations to seamlessly align with regulatory standards. One of the prominent trends is the integration of edge computing into compliance frameworks. As edge computing becomes more prevalent, compliance measures are likely to evolve to accommodate the distributed nature of data processing at the edge. Organizations will need to adapt their strategies to ensure that compliance remains robust and effective in these decentralized computing environments.
Blockchain technology is expected to play a transformative role in enhancing both security and transparency in cloud compliance. The decentralized and tamper-resistant nature of blockchain can be leveraged to create immutable audit trails, providing transparent reporting and ensuring the integrity of data stored in the cloud. As smart contracts on blockchain platforms gain prominence, there is potential for automating specific compliance processes, streamlining and enhancing the overall compliance lifecycle.
Artificial intelligence (AI) and machine learning (ML) are poised to take center stage in the future of cloud compliance, particularly in the realm of continuous monitoring and risk assessment. Advanced analytics powered by AI and ML algorithms can offer real-time insights into compliance status, detect anomalies, and even predict potential risks. The integration of automated compliance monitoring driven by intelligent technologies has the potential to significantly improve the efficiency and accuracy of compliance management processes.
The future trends in cloud compliance are marked by a convergence of technologies, including edge computing, blockchain, AI, and automation. Adapting to these trends will not only be essential for maintaining regulatory adherence but also for harnessing the full potential of cloud technologies in a secure and compliant manner. Organizations that embrace these trends proactively will be better positioned to navigate the complexities of the evolving compliance landscape in the digital age.
How to obtain EXIN Cloud Computing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the landscape of cloud computing and compliance is evolving rapidly, driven by technological innovations, regulatory developments, and the increasing complexity of the digital environment. The intersection of these factors necessitates a strategic and adaptive approach to ensure the secure and compliant utilization of cloud technologies. The exploration of EXIN Cloud Computing and Compliance has shed light on key facets, from foundational principles and regulatory landscapes to the integration of security measures, continuous monitoring, and future trends.
Security measures in the cloud are paramount, requiring robust encryption, continuous monitoring, and proactive incident response to safeguard sensitive data. Continuous compliance monitoring and auditing have emerged as indispensable practices, offering real-time insights and ensuring organizations stay ahead of potential compliance risks. Legal and ethical considerations underscore the importance of transparent data practices, responsible use of technology, and adherence to diverse regulatory frameworks.
Risk management in cloud compliance is a dynamic and proactive process, essential for identifying, assessing, and addressing potential threats and vulnerabilities. As organizations navigate the complexities of cloud computing, future trends, including edge computing integration, blockchain for enhanced security, AI-driven compliance monitoring, and the adoption of Compliance as Code, are poised to shape the landscape.
Looking ahead, the convergence of these trends presents both challenges and opportunities. Organizations that embrace these changes stand to enhance their cybersecurity resilience, meet evolving regulatory requirements, and leverage the transformative potential of cloud technologies. The future of cloud compliance lies in a balanced and adaptive approach, where innovation and regulatory adherence coexist seamlessly, fostering a trustworthy and sustainable digital ecosystem. As organizations navigate this evolving landscape, the synergy between technological advancements and compliance best practices will be paramount to ensuring a secure, compliant, and resilient future in the cloud.
COBIT® 5 Foundation and IT Service Management (ITSM): Achieving Synergy
The convergence of COBIT® 5 Foundation and IT Service Management (ITSM) represents a dynamic and synergistic approach to enhancing organizational governance and optimizing IT service delivery. COBIT® 5, developed by the Information Systems Audit and Control Association (ISACA), is a globally recognized framework that provides a comprehensive set of principles, practices, and analytical tools for the effective governance and management of enterprise IT. On the other hand, IT Service Management focuses on aligning IT services with the needs of the business, emphasizing the delivery of high-quality services that meet customer expectations.
In recent years, organizations have increasingly recognized the need to integrate and harmonize their governance and service management practices. The collaboration between COBIT® 5 Foundation and ITSM offers a strategic alignment that enables businesses to achieve a more seamless and efficient IT environment. This integration is particularly crucial in today's complex and rapidly evolving digital landscape, where organizations must navigate challenges such as cybersecurity threats, regulatory compliance, and the ever-growing demand for innovative IT services.
The foundational principles of COBIT® 5, which include a focus on stakeholder value, risk management, and continual improvement, align seamlessly with the core objectives of IT Service Management. By combining these frameworks, organizations can establish a robust foundation for achieving not only compliance and risk mitigation but also the delivery of high-quality, customer-centric IT services. This synergy empowers businesses to streamline their processes, enhance decision-making, and foster a culture of collaboration across different functional areas.
Table of contents
-
Overview of COBIT® 5 Foundation
-
Essentials of IT Service Management (ITSM)
-
Governance and Risk Management Integration
-
Implementing the Synergy: Step-by-Step Guide
-
Measuring Success: Key Performance Indicators (KPIs)
-
Conclusion
Overview of COBIT® 5 Foundation
COBIT® 5 Foundation serves as a comprehensive framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in achieving effective governance and management of information technology (IT). At its core, COBIT® (Control Objectives for Information and Related Technologies) emphasizes the importance of aligning IT processes with business objectives, ensuring that IT activities contribute directly to organizational success. The framework provides a set of principles, practices, and enablers that support enterprises in optimizing their IT capabilities while managing associated risks and ensuring the delivery of value to stakeholders.
The COBIT® 5 Foundation framework is structured around five key principles, each contributing to the achievement of effective IT governance. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Together, these principles guide organizations in establishing a governance and management system that is both efficient and adaptable to the evolving landscape of IT and business.
COBIT® 5 Foundation offers a structured and comprehensive approach to IT governance, emphasizing stakeholder value, principled practices, and adaptability to the ever-changing IT landscape. By leveraging this framework, organizations can establish a robust foundation for effective governance, risk management, and the continuous improvement of their IT processes, ultimately contributing to enhanced overall business performance.
Essentials of IT Service Management (ITSM)
Essentials of IT Service Management (ITSM) form the foundational principles and practices that organizations adopt to ensure the effective delivery and support of IT services aligned with business objectives. At its core, ITSM revolves around meeting the needs of users, optimizing service quality, and enhancing overall organizational efficiency. The following components encapsulate the key essentials of ITSM:
Service Strategy constitutes a critical pillar of ITSM, involving the development of a comprehensive strategy aligned with business goals. This phase entails understanding customer needs, defining service offerings, and formulating a strategic roadmap for delivering IT services that contribute directly to the success of the organization.
In the Service Design phase, the focus shifts to creating service solutions that meet the requirements outlined in the service strategy. This encompasses designing processes, technologies, and other essential elements necessary for the efficient and effective delivery of high-quality services. Service design ensures that IT services are not only functional but also meet the broader objectives of the organization.
Service Transition is a crucial aspect of ITSM that involves planning and managing changes to services and service management processes. This phase ensures a smooth transition of new or modified services into the operational environment while minimizing disruptions. It encompasses activities such as change management, release and deployment management, and knowledge management.
Continual Service Improvement (CSI) serves as a guiding principle within ITSM, emphasizing the necessity of ongoing enhancement and optimization of services and processes. Through regular assessments, feedback mechanisms, and a commitment to learning from experiences, organizations practicing ITSM can identify areas for improvement and ensure a cycle of continuous enhancement in service delivery and operational efficiency. Together, these essentials form a holistic framework for organizations seeking to align their IT services with business goals, enhance customer satisfaction, and adapt to the dynamic landscape of technology and user expectations.
Governance and Risk Management Integration
In the realm of governance and risk management integration, organizations benefit from fostering a culture of risk awareness and accountability. This cultural shift encourages employees at all levels to recognize and report risks, fostering a collective responsibility for risk mitigation. By incorporating risk considerations into the organization's values and day-to-day operations, companies can create a more proactive and resilient stance toward potential challenges.
Integration also involves the development and implementation of robust risk management frameworks that seamlessly align with governance structures. This includes defining clear roles and responsibilities for risk management at various levels of the organization, establishing effective communication channels for sharing risk information, and integrating risk assessments into strategic planning processes. Such frameworks not only identify potential risks but also provide a structured approach to managing and monitoring these risks over time.
Continuous learning and improvement are inherent components of successful integration. Organizations should conduct periodic reviews and audits to evaluate the effectiveness of their integrated governance and risk management approach. Lessons learned from incidents and successes should be incorporated into future strategies, fostering a dynamic and adaptive governance structure that evolves in tandem with the changing risk landscape.
Governance and risk management integration is a multifaceted and ongoing process that requires a commitment to cultural change, technological innovation, and continuous improvement. By weaving risk considerations into the fabric of governance structures, organizations can enhance their resilience, make more informed decisions, and navigate an increasingly complex and uncertain business environment.
Implementing the Synergy: Step-by-Step Guide
Implementing the synergy between COBIT® 5 Foundation and IT Service Management (ITSM) is a strategic imperative that demands a methodical and well-coordinated approach. Commencing with a thorough assessment of the current state of IT governance and service management, organizations gain a foundational understanding of existing processes and their maturity. This assessment sets the stage for subsequent integration efforts, providing valuable insights into the organization's strengths and areas for improvement.
Precise definition of integration objectives and scope follows, as organizations articulate the desired outcomes and benefits to be derived from the amalgamation of COBIT® 5 Foundation and ITSM. A clear scope ensures that efforts remain focused on specific goals, preventing potential deviations and ensuring a streamlined implementation process. Stakeholder engagement becomes paramount, involving key representatives from IT and business units to gather diverse perspectives and ensure alignment with overarching organizational goals. This collaborative engagement fosters buy-in and support crucial for the successful integration.
Key performance indicators (KPIs) are established to measure the success of the integration, encompassing governance effectiveness, service delivery efficiency, and overall alignment with organizational objectives. Regular monitoring and assessment of these indicators offer valuable insights into the performance and impact of the integrated framework, guiding ongoing improvements.
Implementation efforts extend to training programs and change management initiatives, ensuring that teams are equipped with the necessary knowledge and skills to operate within the integrated framework. Pilot programs may be initiated in specific departments or business units to test the integrated framework in a controlled environment, allowing for the identification and resolution of potential challenges before full-scale deployment. Continuous monitoring and evaluation mechanisms are established to assess the ongoing effectiveness of the integrated COBIT® 5 Foundation and ITSM framework, incorporating feedback from users and stakeholders to drive necessary adjustments.
Cultivating a culture of continuous improvement is emphasized, encouraging teams to identify opportunities for enhancement and establishing mechanisms for regular reviews and refinements to the integrated framework. This adaptive approach ensures the sustained success of the integration, aligning IT services seamlessly with business objectives while fostering a dynamic and resilient organizational environment. In conclusion, this step-by-step guide serves as a comprehensive and structured approach to implementing the synergy between COBIT® 5 Foundation and IT Service Management, ultimately enhancing governance practices and optimizing the delivery of IT services.
Measuring Success: Key Performance Indicators (KPIs)
Measuring the success of the integration between COBIT® 5 Foundation and IT Service Management (ITSM) relies on a thoughtful selection of Key Performance Indicators (KPIs) that encompass various aspects critical to the alignment of governance and service delivery. One pivotal category of KPIs revolves around strategic alignment, evaluating how effectively the integrated framework contributes to organizational objectives. These indicators provide a holistic view of whether the governance practices and IT service delivery align with and support the broader strategic vision of the organization, emphasizing the symbiotic relationship between IT initiatives and overall business goals.
Governance effectiveness serves as another crucial dimension for assessing success. KPIs within this category focus on evaluating the efficiency and efficacy of governance processes. Metrics such as the speed of decision-making, compliance levels, and the responsiveness of governance structures offer insights into how well the organization is managing its IT resources and risks. These indicators serve as a barometer for the overall health and effectiveness of the governance component within the integrated framework.
User satisfaction and experience KPIs form a vital component, providing insights into the impact of the integrated framework on end-users. Metrics such as user satisfaction surveys, feedback on service quality, and user adoption rates offer a qualitative assessment of how well the integrated approach meets stakeholder expectations. These indicators are crucial for ensuring a positive and productive user experience, as the success of the integration is ultimately measured by the satisfaction and engagement of the end-users.
A continuous improvement mindset is integral to sustained success, and corresponding KPIs focus on the organization's ability to adapt and refine the integrated framework over time. Metrics related to the frequency and effectiveness of updates and refinements, as well as the organization's agility in responding to emerging challenges, highlight the dynamic nature of governance and service management integration. Success, in this context, is not merely a destination but an ongoing journey of refinement and adaptation to ensure that governance and service management practices evolve in tandem with organizational goals and the evolving IT landscape.
How to obtain COBIT® 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the pursuit of synergy between COBIT® 5 Foundation and IT Service Management (ITSM) stands as a transformative endeavor, poised to elevate organizational effectiveness in IT governance and service delivery. This convergence represents a strategic alignment that, when carefully implemented, holds the promise of harmonizing IT processes, optimizing risk management, and enhancing the delivery of IT services in line with business objectives.
The step-by-step guide provided for achieving this synergy emphasizes the importance of a systematic and collaborative approach. From the initial assessment of the current state to the establishment of key performance indicators (KPIs) for ongoing measurement, the guide offers a structured pathway for organizations to navigate the integration process. Defining clear objectives, engaging stakeholders, and fostering a culture of continuous improvement emerge as pivotal elements, ensuring that the integration is purposeful, inclusive, and adaptable to the evolving landscape of IT and business dynamics.
The seamless alignment of COBIT® 5 Foundation and ITSM processes contributes not only to operational efficiency but also to a more resilient and responsive IT ecosystem. By integrating governance and service management, organizations are better equipped to meet the ever-changing needs of stakeholders, enhance risk mitigation strategies, and cultivate a customer-centric approach to IT services.
As organizations embark on this journey of achieving synergy between COBIT® 5 Foundation and ITSM, the ultimate goal is to create a dynamic and adaptive IT environment. This integration is not a static achievement but a continuous process of refinement and optimization. Success is measured not just by the integration itself but by the sustained ability to deliver value, align with strategic goals, and proactively respond to the challenges and opportunities inherent in the digital landscape. In essence, achieving synergy between COBIT® 5 Foundation and ITSM is a strategic imperative that positions organizations to thrive in an era where effective governance and agile service management are essential for sustained success.
Read More
The convergence of COBIT® 5 Foundation and IT Service Management (ITSM) represents a dynamic and synergistic approach to enhancing organizational governance and optimizing IT service delivery. COBIT® 5, developed by the Information Systems Audit and Control Association (ISACA), is a globally recognized framework that provides a comprehensive set of principles, practices, and analytical tools for the effective governance and management of enterprise IT. On the other hand, IT Service Management focuses on aligning IT services with the needs of the business, emphasizing the delivery of high-quality services that meet customer expectations.
In recent years, organizations have increasingly recognized the need to integrate and harmonize their governance and service management practices. The collaboration between COBIT® 5 Foundation and ITSM offers a strategic alignment that enables businesses to achieve a more seamless and efficient IT environment. This integration is particularly crucial in today's complex and rapidly evolving digital landscape, where organizations must navigate challenges such as cybersecurity threats, regulatory compliance, and the ever-growing demand for innovative IT services.
The foundational principles of COBIT® 5, which include a focus on stakeholder value, risk management, and continual improvement, align seamlessly with the core objectives of IT Service Management. By combining these frameworks, organizations can establish a robust foundation for achieving not only compliance and risk mitigation but also the delivery of high-quality, customer-centric IT services. This synergy empowers businesses to streamline their processes, enhance decision-making, and foster a culture of collaboration across different functional areas.
Table of contents
-
Overview of COBIT® 5 Foundation
-
Essentials of IT Service Management (ITSM)
-
Governance and Risk Management Integration
-
Implementing the Synergy: Step-by-Step Guide
-
Measuring Success: Key Performance Indicators (KPIs)
-
Conclusion
Overview of COBIT® 5 Foundation
COBIT® 5 Foundation serves as a comprehensive framework developed by the Information Systems Audit and Control Association (ISACA) to guide organizations in achieving effective governance and management of information technology (IT). At its core, COBIT® (Control Objectives for Information and Related Technologies) emphasizes the importance of aligning IT processes with business objectives, ensuring that IT activities contribute directly to organizational success. The framework provides a set of principles, practices, and enablers that support enterprises in optimizing their IT capabilities while managing associated risks and ensuring the delivery of value to stakeholders.
The COBIT® 5 Foundation framework is structured around five key principles, each contributing to the achievement of effective IT governance. These principles include meeting stakeholder needs, covering the enterprise end-to-end, applying a single integrated framework, enabling a holistic approach, and separating governance from management. Together, these principles guide organizations in establishing a governance and management system that is both efficient and adaptable to the evolving landscape of IT and business.
COBIT® 5 Foundation offers a structured and comprehensive approach to IT governance, emphasizing stakeholder value, principled practices, and adaptability to the ever-changing IT landscape. By leveraging this framework, organizations can establish a robust foundation for effective governance, risk management, and the continuous improvement of their IT processes, ultimately contributing to enhanced overall business performance.
Essentials of IT Service Management (ITSM)
Essentials of IT Service Management (ITSM) form the foundational principles and practices that organizations adopt to ensure the effective delivery and support of IT services aligned with business objectives. At its core, ITSM revolves around meeting the needs of users, optimizing service quality, and enhancing overall organizational efficiency. The following components encapsulate the key essentials of ITSM:
Service Strategy constitutes a critical pillar of ITSM, involving the development of a comprehensive strategy aligned with business goals. This phase entails understanding customer needs, defining service offerings, and formulating a strategic roadmap for delivering IT services that contribute directly to the success of the organization.
In the Service Design phase, the focus shifts to creating service solutions that meet the requirements outlined in the service strategy. This encompasses designing processes, technologies, and other essential elements necessary for the efficient and effective delivery of high-quality services. Service design ensures that IT services are not only functional but also meet the broader objectives of the organization.
Service Transition is a crucial aspect of ITSM that involves planning and managing changes to services and service management processes. This phase ensures a smooth transition of new or modified services into the operational environment while minimizing disruptions. It encompasses activities such as change management, release and deployment management, and knowledge management.
Continual Service Improvement (CSI) serves as a guiding principle within ITSM, emphasizing the necessity of ongoing enhancement and optimization of services and processes. Through regular assessments, feedback mechanisms, and a commitment to learning from experiences, organizations practicing ITSM can identify areas for improvement and ensure a cycle of continuous enhancement in service delivery and operational efficiency. Together, these essentials form a holistic framework for organizations seeking to align their IT services with business goals, enhance customer satisfaction, and adapt to the dynamic landscape of technology and user expectations.
Governance and Risk Management Integration
In the realm of governance and risk management integration, organizations benefit from fostering a culture of risk awareness and accountability. This cultural shift encourages employees at all levels to recognize and report risks, fostering a collective responsibility for risk mitigation. By incorporating risk considerations into the organization's values and day-to-day operations, companies can create a more proactive and resilient stance toward potential challenges.
Integration also involves the development and implementation of robust risk management frameworks that seamlessly align with governance structures. This includes defining clear roles and responsibilities for risk management at various levels of the organization, establishing effective communication channels for sharing risk information, and integrating risk assessments into strategic planning processes. Such frameworks not only identify potential risks but also provide a structured approach to managing and monitoring these risks over time.
Continuous learning and improvement are inherent components of successful integration. Organizations should conduct periodic reviews and audits to evaluate the effectiveness of their integrated governance and risk management approach. Lessons learned from incidents and successes should be incorporated into future strategies, fostering a dynamic and adaptive governance structure that evolves in tandem with the changing risk landscape.
Governance and risk management integration is a multifaceted and ongoing process that requires a commitment to cultural change, technological innovation, and continuous improvement. By weaving risk considerations into the fabric of governance structures, organizations can enhance their resilience, make more informed decisions, and navigate an increasingly complex and uncertain business environment.
Implementing the Synergy: Step-by-Step Guide
Implementing the synergy between COBIT® 5 Foundation and IT Service Management (ITSM) is a strategic imperative that demands a methodical and well-coordinated approach. Commencing with a thorough assessment of the current state of IT governance and service management, organizations gain a foundational understanding of existing processes and their maturity. This assessment sets the stage for subsequent integration efforts, providing valuable insights into the organization's strengths and areas for improvement.
Precise definition of integration objectives and scope follows, as organizations articulate the desired outcomes and benefits to be derived from the amalgamation of COBIT® 5 Foundation and ITSM. A clear scope ensures that efforts remain focused on specific goals, preventing potential deviations and ensuring a streamlined implementation process. Stakeholder engagement becomes paramount, involving key representatives from IT and business units to gather diverse perspectives and ensure alignment with overarching organizational goals. This collaborative engagement fosters buy-in and support crucial for the successful integration.
Key performance indicators (KPIs) are established to measure the success of the integration, encompassing governance effectiveness, service delivery efficiency, and overall alignment with organizational objectives. Regular monitoring and assessment of these indicators offer valuable insights into the performance and impact of the integrated framework, guiding ongoing improvements.
Implementation efforts extend to training programs and change management initiatives, ensuring that teams are equipped with the necessary knowledge and skills to operate within the integrated framework. Pilot programs may be initiated in specific departments or business units to test the integrated framework in a controlled environment, allowing for the identification and resolution of potential challenges before full-scale deployment. Continuous monitoring and evaluation mechanisms are established to assess the ongoing effectiveness of the integrated COBIT® 5 Foundation and ITSM framework, incorporating feedback from users and stakeholders to drive necessary adjustments.
Cultivating a culture of continuous improvement is emphasized, encouraging teams to identify opportunities for enhancement and establishing mechanisms for regular reviews and refinements to the integrated framework. This adaptive approach ensures the sustained success of the integration, aligning IT services seamlessly with business objectives while fostering a dynamic and resilient organizational environment. In conclusion, this step-by-step guide serves as a comprehensive and structured approach to implementing the synergy between COBIT® 5 Foundation and IT Service Management, ultimately enhancing governance practices and optimizing the delivery of IT services.
Measuring Success: Key Performance Indicators (KPIs)
Measuring the success of the integration between COBIT® 5 Foundation and IT Service Management (ITSM) relies on a thoughtful selection of Key Performance Indicators (KPIs) that encompass various aspects critical to the alignment of governance and service delivery. One pivotal category of KPIs revolves around strategic alignment, evaluating how effectively the integrated framework contributes to organizational objectives. These indicators provide a holistic view of whether the governance practices and IT service delivery align with and support the broader strategic vision of the organization, emphasizing the symbiotic relationship between IT initiatives and overall business goals.
Governance effectiveness serves as another crucial dimension for assessing success. KPIs within this category focus on evaluating the efficiency and efficacy of governance processes. Metrics such as the speed of decision-making, compliance levels, and the responsiveness of governance structures offer insights into how well the organization is managing its IT resources and risks. These indicators serve as a barometer for the overall health and effectiveness of the governance component within the integrated framework.
User satisfaction and experience KPIs form a vital component, providing insights into the impact of the integrated framework on end-users. Metrics such as user satisfaction surveys, feedback on service quality, and user adoption rates offer a qualitative assessment of how well the integrated approach meets stakeholder expectations. These indicators are crucial for ensuring a positive and productive user experience, as the success of the integration is ultimately measured by the satisfaction and engagement of the end-users.
A continuous improvement mindset is integral to sustained success, and corresponding KPIs focus on the organization's ability to adapt and refine the integrated framework over time. Metrics related to the frequency and effectiveness of updates and refinements, as well as the organization's agility in responding to emerging challenges, highlight the dynamic nature of governance and service management integration. Success, in this context, is not merely a destination but an ongoing journey of refinement and adaptation to ensure that governance and service management practices evolve in tandem with organizational goals and the evolving IT landscape.
How to obtain COBIT® 5 Foundation certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the pursuit of synergy between COBIT® 5 Foundation and IT Service Management (ITSM) stands as a transformative endeavor, poised to elevate organizational effectiveness in IT governance and service delivery. This convergence represents a strategic alignment that, when carefully implemented, holds the promise of harmonizing IT processes, optimizing risk management, and enhancing the delivery of IT services in line with business objectives.
The step-by-step guide provided for achieving this synergy emphasizes the importance of a systematic and collaborative approach. From the initial assessment of the current state to the establishment of key performance indicators (KPIs) for ongoing measurement, the guide offers a structured pathway for organizations to navigate the integration process. Defining clear objectives, engaging stakeholders, and fostering a culture of continuous improvement emerge as pivotal elements, ensuring that the integration is purposeful, inclusive, and adaptable to the evolving landscape of IT and business dynamics.
The seamless alignment of COBIT® 5 Foundation and ITSM processes contributes not only to operational efficiency but also to a more resilient and responsive IT ecosystem. By integrating governance and service management, organizations are better equipped to meet the ever-changing needs of stakeholders, enhance risk mitigation strategies, and cultivate a customer-centric approach to IT services.
As organizations embark on this journey of achieving synergy between COBIT® 5 Foundation and ITSM, the ultimate goal is to create a dynamic and adaptive IT environment. This integration is not a static achievement but a continuous process of refinement and optimization. Success is measured not just by the integration itself but by the sustained ability to deliver value, align with strategic goals, and proactively respond to the challenges and opportunities inherent in the digital landscape. In essence, achieving synergy between COBIT® 5 Foundation and ITSM is a strategic imperative that positions organizations to thrive in an era where effective governance and agile service management are essential for sustained success.
Mastering Lightning Web Components: A Guide for Salesforce Administrators and App Builders
"Mastering Lightning Web Components: A Guide for Salesforce Administrators and App Builders" is a comprehensive and authoritative resource designed to empower individuals within the Salesforce ecosystem to harness the full potential of Lightning Web Components (LWC). In the rapidly evolving landscape of Salesforce development, LWC has emerged as a powerful and modern framework for building dynamic and responsive user interfaces. This book is tailored specifically for Salesforce administrators and app builders, providing them with the knowledge and skills needed to elevate their capabilities and streamline the development process.
The introduction of Lightning Web Components has marked a paradigm shift in how applications are built on the Salesforce platform. With a focus on reusability, performance, and enhanced developer productivity, LWC enables users to create lightning-fast, scalable, and modular applications. "Mastering Lightning Web Components" serves as a roadmap for navigating this transformative technology, offering clear and practical guidance to navigate the intricacies of LWC development.
Written by seasoned experts in the Salesforce ecosystem, this guide strikes a balance between technical depth and accessibility, making it an ideal companion for both newcomers and experienced professionals seeking to deepen their understanding of Lightning Web Components. The book not only covers the fundamentals of LWC but also delves into advanced topics, best practices, and real-world scenarios, providing readers with a holistic understanding of how to leverage LWC to meet the unique needs of their Salesforce projects.
Whether you are a Salesforce administrator looking to enhance your declarative skills or an app builder aiming to extend your development prowess, "Mastering Lightning Web Components" equips you with the knowledge and insights needed to thrive in the dynamic world of Salesforce application development. From building custom components to optimizing performance and ensuring seamless integration with existing workflows, this guide is your key to unlocking the full potential of Lightning Web Components within the Salesforce ecosystem.
Table of contents
-
Foundations of Lightning Web Components (LWC)
-
Declarative Development with LWC for Administrators
-
Advanced LWC Development for App Builders
-
Optimizing Performance in Lightning Web Components
-
Integration and Extensibility in LWC
-
Conclusion
Foundations of Lightning Web Components (LWC)
In the realm of Salesforce development, a solid understanding of the foundations of Lightning Web Components (LWC) is essential for any administrator or app builder seeking to harness the full potential of this modern framework. At its core, LWC introduces a component-based architecture that leverages web standards to enable the creation of dynamic and responsive user interfaces. This section of the guide delves into the fundamental concepts that underpin LWC, providing readers with a comprehensive overview of the building blocks that define this framework.
At the heart of LWC lie key elements such as templates, JavaScript classes, and decorators. The guide explores the role of templates in defining the structure of components, allowing developers to seamlessly blend HTML with dynamic data rendering. JavaScript classes, on the other hand, provide the logic behind these components, facilitating the creation of interactive and data-driven user experiences. Decorators act as the glue that binds it all together, allowing developers to enhance their components with metadata that defines specific behaviors.
Understanding how LWC fits into the broader Salesforce Lightning framework is crucial for practitioners looking to navigate the Salesforce ecosystem effectively. This section elucidates the relationships between Lightning Web Components and other Lightning technologies, shedding light on how LWC integrates seamlessly into the broader Lightning Experience. By grasping these foundational concepts, readers are equipped with the knowledge needed to embark on a journey of effective and efficient Lightning Web Component development.
Declarative Development with LWC for Administrators
In the rapidly evolving landscape of Salesforce, administrators play a pivotal role in shaping user experiences and streamlining processes. This section of the guide focuses on how administrators can leverage the power of Lightning Web Components (LWC) for declarative development, empowering them to create sophisticated user interfaces without delving into extensive code.
One key aspect explored is the integration of LWC components into the Lightning App Builder and Community Builder interfaces. Administrators gain insights into the seamless incorporation of custom Lightning Web Components into Lightning pages, providing a visual and intuitive approach to enhancing user interfaces. Through a step-by-step exploration, administrators learn how to harness the declarative capabilities of these builders to tailor user experiences to specific business requirements.
Furthermore, the guide delves into best practices for designing and configuring Lightning pages with LWC components. Administrators gain an understanding of the declarative tools at their disposal, such as page layouts, dynamic forms, and component properties. This knowledge enables them to efficiently customize user interfaces, ensuring a cohesive and user-friendly experience for their Salesforce users.
By the end of this section, administrators not only grasp the essentials of declarative development with LWC but also acquire the skills to implement powerful and customized solutions within the Salesforce platform. The combination of visual tools and Lightning Web Components empowers administrators to take their declarative development capabilities to new heights, providing a bridge between code-driven development and intuitive, user-friendly interfaces.
Advanced LWC Development for App Builders
As app builders strive for innovation and sophistication in their Salesforce applications, a mastery of advanced Lightning Web Components (LWC) development becomes imperative. This section of the guide immerses app builders in the intricacies of LWC, going beyond the basics to explore techniques that enhance scalability, maintainability, and overall development efficiency.
The journey into advanced LWC development begins with a focus on creating reusable components and modules. App builders discover how to design components that transcend individual use cases, fostering modularity and extensibility in their applications. By understanding the principles of component reusability, builders gain the tools to construct scalable and maintainable solutions that adapt to evolving business needs.
A significant emphasis is placed on navigating the complexities of data handling in LWC. This includes in-depth exploration of asynchronous operations, efficient client-side caching, and strategic server-side communication. App builders learn how to optimize data flow within their applications, ensuring responsiveness and minimizing latency for an optimal user experience.
The guide also delves into advanced topics such as event-driven architectures, enabling app builders to design applications that respond dynamically to user interactions and external events. Through real-world examples and best practices, builders gain insights into leveraging custom events, understanding the publish-subscribe pattern, and orchestrating seamless communication between Lightning Web Components.
App builders emerge with a heightened proficiency in advanced LWC development. Armed with the knowledge to create modular, efficient, and responsive applications, they are well-equipped to tackle the complexities of modern Salesforce development, delivering solutions that not only meet but exceed the expectations of users and stakeholders.
Optimizing Performance in Lightning Web Components
Performance optimization is a critical facet of Lightning Web Components (LWC) development, ensuring that Salesforce applications deliver a seamless and responsive user experience. This section of the guide delves into the strategies and techniques employed to maximize the efficiency of LWC applications, covering aspects from rendering speed to minimizing server calls.
The exploration begins with a focus on efficient rendering techniques, where developers gain insights into best practices for structuring components to enhance page load times. This includes understanding the lifecycle hooks in LWC, optimizing template structures, and employing techniques like lazy loading to prioritize critical content. By mastering these rendering optimizations, developers can significantly enhance the perceived performance of their applications.
A significant portion of the section is dedicated to minimizing Apex calls and optimizing server-side communication. Developers learn how to design LWC components that communicate efficiently with the server, reducing the payload and minimizing latency. Techniques such as caching and asynchronous operations are explored in detail, allowing developers to strike a balance between data freshness and performance.
Developers are equipped with a robust set of tools and techniques to optimize the performance of their Lightning Web Components. Whether it's through rendering optimizations, efficient server communication, or client-side strategies, this knowledge empowers developers to deliver Lightning-fast applications that meet the high standards of modern user expectations in the Salesforce
Integration and Extensibility in LWC
In the ever-evolving landscape of Salesforce development, the ability to seamlessly integrate Lightning Web Components (LWC) with various Salesforce technologies and extend their functionality is crucial for creating versatile and interconnected applications. This section of the guide provides a comprehensive exploration of the strategies and techniques that developers can employ to achieve robust integration and enhance the extensibility of their LWC solutions.
The integration journey begins by delving into the role of Apex controllers in connecting LWC components with the Salesforce server. Developers gain insights into leveraging server-side logic for data retrieval, manipulation, and other operations, fostering a cohesive and efficient data flow within their applications. Additionally, the guide explores the nuances of integrating LWC components into existing Lightning components, offering a roadmap for creating a unified user experience across diverse Salesforce functionalities.
Extensibility, a key aspect of effective application development, is addressed through a deep dive into the use of custom events in LWC. Developers learn how to implement event-driven architectures, enabling seamless communication and collaboration between components. This section also covers advanced topics such as dynamic component creation and composition, allowing developers to design flexible and adaptable solutions that can be easily extended to meet evolving business requirements.
This section equips developers with a holistic understanding of integration and extensibility in LWC, fostering the creation of applications that seamlessly connect within the Salesforce ecosystem while providing the flexibility to adapt and scale to the unique demands of diverse business landscapes. By mastering these integration and extensibility strategies, developers unlock the full potential of Lightning Web Components in building interconnected, dynamic, and future-proof Salesforce solutions.
How to obtain Salesforce Administrators and App Builders certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In the journey of "Mastering Lightning Web Components: A Guide for Salesforce Administrators and App Builders," we have traversed the intricate landscape of LWC development, covering foundational concepts, declarative development, advanced techniques, performance optimization, and seamless integration. As we conclude this guide, it is evident that Lightning Web Components stand at the forefront of modern Salesforce development, offering a powerful and flexible framework for crafting dynamic and responsive applications.
Throughout the guide, administrators have gained insights into declarative development, learning how to wield the visual tools of Lightning App Builder and Community Builder to enhance user interfaces. App builders have delved into advanced LWC development, acquiring the skills to create modular, scalable, and innovative applications that transcend the basics. Developers have explored performance optimization strategies, ensuring their applications meet the high standards of responsiveness expected in the digital era. Integration and extensibility have been demystified, empowering developers to seamlessly connect LWC components within the Salesforce ecosystem and extend their functionality to meet diverse business needs.
As the Salesforce ecosystem continues to evolve, embracing Lightning Web Components as a cornerstone of development opens doors to innovation and agility. The guide's comprehensive coverage equips individuals to not only meet but exceed the expectations of users, stakeholders, and the dynamic Salesforce platform itself. Whether crafting intuitive user interfaces, optimizing for performance, or seamlessly integrating with external systems, the skills acquired in this guide are a testament to the empowerment that comes with mastering Lightning Web Components in the ever-expanding Salesforce universe.
Read More
"Mastering Lightning Web Components: A Guide for Salesforce Administrators and App Builders" is a comprehensive and authoritative resource designed to empower individuals within the Salesforce ecosystem to harness the full potential of Lightning Web Components (LWC). In the rapidly evolving landscape of Salesforce development, LWC has emerged as a powerful and modern framework for building dynamic and responsive user interfaces. This book is tailored specifically for Salesforce administrators and app builders, providing them with the knowledge and skills needed to elevate their capabilities and streamline the development process.
The introduction of Lightning Web Components has marked a paradigm shift in how applications are built on the Salesforce platform. With a focus on reusability, performance, and enhanced developer productivity, LWC enables users to create lightning-fast, scalable, and modular applications. "Mastering Lightning Web Components" serves as a roadmap for navigating this transformative technology, offering clear and practical guidance to navigate the intricacies of LWC development.
Written by seasoned experts in the Salesforce ecosystem, this guide strikes a balance between technical depth and accessibility, making it an ideal companion for both newcomers and experienced professionals seeking to deepen their understanding of Lightning Web Components. The book not only covers the fundamentals of LWC but also delves into advanced topics, best practices, and real-world scenarios, providing readers with a holistic understanding of how to leverage LWC to meet the unique needs of their Salesforce projects.
Whether you are a Salesforce administrator looking to enhance your declarative skills or an app builder aiming to extend your development prowess, "Mastering Lightning Web Components" equips you with the knowledge and insights needed to thrive in the dynamic world of Salesforce application development. From building custom components to optimizing performance and ensuring seamless integration with existing workflows, this guide is your key to unlocking the full potential of Lightning Web Components within the Salesforce ecosystem.
Table of contents
-
Foundations of Lightning Web Components (LWC)
-
Declarative Development with LWC for Administrators
-
Advanced LWC Development for App Builders
-
Optimizing Performance in Lightning Web Components
-
Integration and Extensibility in LWC
-
Conclusion
Foundations of Lightning Web Components (LWC)
In the realm of Salesforce development, a solid understanding of the foundations of Lightning Web Components (LWC) is essential for any administrator or app builder seeking to harness the full potential of this modern framework. At its core, LWC introduces a component-based architecture that leverages web standards to enable the creation of dynamic and responsive user interfaces. This section of the guide delves into the fundamental concepts that underpin LWC, providing readers with a comprehensive overview of the building blocks that define this framework.
At the heart of LWC lie key elements such as templates, JavaScript classes, and decorators. The guide explores the role of templates in defining the structure of components, allowing developers to seamlessly blend HTML with dynamic data rendering. JavaScript classes, on the other hand, provide the logic behind these components, facilitating the creation of interactive and data-driven user experiences. Decorators act as the glue that binds it all together, allowing developers to enhance their components with metadata that defines specific behaviors.
Understanding how LWC fits into the broader Salesforce Lightning framework is crucial for practitioners looking to navigate the Salesforce ecosystem effectively. This section elucidates the relationships between Lightning Web Components and other Lightning technologies, shedding light on how LWC integrates seamlessly into the broader Lightning Experience. By grasping these foundational concepts, readers are equipped with the knowledge needed to embark on a journey of effective and efficient Lightning Web Component development.
Declarative Development with LWC for Administrators
In the rapidly evolving landscape of Salesforce, administrators play a pivotal role in shaping user experiences and streamlining processes. This section of the guide focuses on how administrators can leverage the power of Lightning Web Components (LWC) for declarative development, empowering them to create sophisticated user interfaces without delving into extensive code.
One key aspect explored is the integration of LWC components into the Lightning App Builder and Community Builder interfaces. Administrators gain insights into the seamless incorporation of custom Lightning Web Components into Lightning pages, providing a visual and intuitive approach to enhancing user interfaces. Through a step-by-step exploration, administrators learn how to harness the declarative capabilities of these builders to tailor user experiences to specific business requirements.
Furthermore, the guide delves into best practices for designing and configuring Lightning pages with LWC components. Administrators gain an understanding of the declarative tools at their disposal, such as page layouts, dynamic forms, and component properties. This knowledge enables them to efficiently customize user interfaces, ensuring a cohesive and user-friendly experience for their Salesforce users.
By the end of this section, administrators not only grasp the essentials of declarative development with LWC but also acquire the skills to implement powerful and customized solutions within the Salesforce platform. The combination of visual tools and Lightning Web Components empowers administrators to take their declarative development capabilities to new heights, providing a bridge between code-driven development and intuitive, user-friendly interfaces.
Advanced LWC Development for App Builders
As app builders strive for innovation and sophistication in their Salesforce applications, a mastery of advanced Lightning Web Components (LWC) development becomes imperative. This section of the guide immerses app builders in the intricacies of LWC, going beyond the basics to explore techniques that enhance scalability, maintainability, and overall development efficiency.
The journey into advanced LWC development begins with a focus on creating reusable components and modules. App builders discover how to design components that transcend individual use cases, fostering modularity and extensibility in their applications. By understanding the principles of component reusability, builders gain the tools to construct scalable and maintainable solutions that adapt to evolving business needs.
A significant emphasis is placed on navigating the complexities of data handling in LWC. This includes in-depth exploration of asynchronous operations, efficient client-side caching, and strategic server-side communication. App builders learn how to optimize data flow within their applications, ensuring responsiveness and minimizing latency for an optimal user experience.
The guide also delves into advanced topics such as event-driven architectures, enabling app builders to design applications that respond dynamically to user interactions and external events. Through real-world examples and best practices, builders gain insights into leveraging custom events, understanding the publish-subscribe pattern, and orchestrating seamless communication between Lightning Web Components.
App builders emerge with a heightened proficiency in advanced LWC development. Armed with the knowledge to create modular, efficient, and responsive applications, they are well-equipped to tackle the complexities of modern Salesforce development, delivering solutions that not only meet but exceed the expectations of users and stakeholders.
Optimizing Performance in Lightning Web Components
Performance optimization is a critical facet of Lightning Web Components (LWC) development, ensuring that Salesforce applications deliver a seamless and responsive user experience. This section of the guide delves into the strategies and techniques employed to maximize the efficiency of LWC applications, covering aspects from rendering speed to minimizing server calls.
The exploration begins with a focus on efficient rendering techniques, where developers gain insights into best practices for structuring components to enhance page load times. This includes understanding the lifecycle hooks in LWC, optimizing template structures, and employing techniques like lazy loading to prioritize critical content. By mastering these rendering optimizations, developers can significantly enhance the perceived performance of their applications.
A significant portion of the section is dedicated to minimizing Apex calls and optimizing server-side communication. Developers learn how to design LWC components that communicate efficiently with the server, reducing the payload and minimizing latency. Techniques such as caching and asynchronous operations are explored in detail, allowing developers to strike a balance between data freshness and performance.
Developers are equipped with a robust set of tools and techniques to optimize the performance of their Lightning Web Components. Whether it's through rendering optimizations, efficient server communication, or client-side strategies, this knowledge empowers developers to deliver Lightning-fast applications that meet the high standards of modern user expectations in the Salesforce
Integration and Extensibility in LWC
In the ever-evolving landscape of Salesforce development, the ability to seamlessly integrate Lightning Web Components (LWC) with various Salesforce technologies and extend their functionality is crucial for creating versatile and interconnected applications. This section of the guide provides a comprehensive exploration of the strategies and techniques that developers can employ to achieve robust integration and enhance the extensibility of their LWC solutions.
The integration journey begins by delving into the role of Apex controllers in connecting LWC components with the Salesforce server. Developers gain insights into leveraging server-side logic for data retrieval, manipulation, and other operations, fostering a cohesive and efficient data flow within their applications. Additionally, the guide explores the nuances of integrating LWC components into existing Lightning components, offering a roadmap for creating a unified user experience across diverse Salesforce functionalities.
Extensibility, a key aspect of effective application development, is addressed through a deep dive into the use of custom events in LWC. Developers learn how to implement event-driven architectures, enabling seamless communication and collaboration between components. This section also covers advanced topics such as dynamic component creation and composition, allowing developers to design flexible and adaptable solutions that can be easily extended to meet evolving business requirements.
This section equips developers with a holistic understanding of integration and extensibility in LWC, fostering the creation of applications that seamlessly connect within the Salesforce ecosystem while providing the flexibility to adapt and scale to the unique demands of diverse business landscapes. By mastering these integration and extensibility strategies, developers unlock the full potential of Lightning Web Components in building interconnected, dynamic, and future-proof Salesforce solutions.
How to obtain Salesforce Administrators and App Builders certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In the journey of "Mastering Lightning Web Components: A Guide for Salesforce Administrators and App Builders," we have traversed the intricate landscape of LWC development, covering foundational concepts, declarative development, advanced techniques, performance optimization, and seamless integration. As we conclude this guide, it is evident that Lightning Web Components stand at the forefront of modern Salesforce development, offering a powerful and flexible framework for crafting dynamic and responsive applications.
Throughout the guide, administrators have gained insights into declarative development, learning how to wield the visual tools of Lightning App Builder and Community Builder to enhance user interfaces. App builders have delved into advanced LWC development, acquiring the skills to create modular, scalable, and innovative applications that transcend the basics. Developers have explored performance optimization strategies, ensuring their applications meet the high standards of responsiveness expected in the digital era. Integration and extensibility have been demystified, empowering developers to seamlessly connect LWC components within the Salesforce ecosystem and extend their functionality to meet diverse business needs.
As the Salesforce ecosystem continues to evolve, embracing Lightning Web Components as a cornerstone of development opens doors to innovation and agility. The guide's comprehensive coverage equips individuals to not only meet but exceed the expectations of users, stakeholders, and the dynamic Salesforce platform itself. Whether crafting intuitive user interfaces, optimizing for performance, or seamlessly integrating with external systems, the skills acquired in this guide are a testament to the empowerment that comes with mastering Lightning Web Components in the ever-expanding Salesforce universe.
5G and IoT: A Powerful Combination for Connectivity
The advent of 5G technology has marked a transformative era in the realm of connectivity, promising unprecedented speed, low latency, and enhanced network capabilities. This fifth-generation wireless technology goes beyond merely improving our browsing experiences; it forms the backbone of a digital revolution that extends its influence to various industries and technologies. One of the most promising synergies emerging from the 5G landscape is its integration with the Internet of Things (IoT), creating a powerful alliance that has the potential to redefine how devices communicate, share data, and contribute to a seamlessly connected world.
As we delve into the intersection of 5G and IoT, it becomes evident that their combined capabilities unlock a new dimension of possibilities. The Internet of Things, characterized by interconnected devices exchanging information and performing tasks autonomously, gains a significant boost with the high-speed, low-latency nature of 5G networks. This synergy is poised to propel the growth of smart cities, autonomous vehicles, industrial automation, and countless other applications that demand rapid and reliable data transmission.
Moreover, the amalgamation of 5G and IoT is not confined to elevating the speed of data transfer. It brings forth a paradigm shift in how devices interact and collaborate, fostering an environment where real-time communication becomes the norm rather than the exception. This real-time connectivity has far-reaching implications, from enabling critical applications in healthcare to enhancing the efficiency of supply chain management. The seamless integration of 5G and IoT creates a robust foundation for innovation, paving the way for novel solutions and services that were once constrained by the limitations of previous-generation networks.
In this exploration of the powerful combination of 5G and IoT, it is essential to recognize the potential challenges and considerations that come with such technological advancements. From security concerns to the need for standardized protocols, navigating the intricacies of this evolving landscape requires a holistic understanding of the implications and a commitment to addressing the associated complexities. As we navigate this transformative journey, the fusion of 5G and IoT stands as a beacon guiding us toward a future where connectivity transcends its current boundaries, opening doors to unparalleled possibilities in the digital age.
Table of contents
-
Technical Foundations of 5G and IoT Integration
-
Enhancing Industrial Processes with 5G and IoT
-
Smart Cities and Urban Connectivity
-
Security Challenges and Solutions
-
Consumer Electronics and 5G
-
Edge Computing in the 5G-IoT Ecosystem
-
Conclusion
Technical Foundations of 5G and IoT Integration
The integration of 5G and the Internet of Things (IoT) is underpinned by a robust set of technical foundations that collectively redefine the landscape of connectivity. At the core of this integration lies the high-speed data transfer capabilities of 5G networks. With significantly increased data rates compared to its predecessors, 5G facilitates the rapid exchange of information between IoT devices, enabling them to communicate seamlessly and efficiently. This enhanced data transfer speed is a critical factor in supporting the diverse range of applications and services that rely on real-time data processing.
Low latency, another key element of 5G's technical prowess, plays a pivotal role in the integration with IoT. The near-instantaneous response times achieved by 5G networks reduce communication delays between devices, a crucial requirement for applications demanding real-time interactions. This is particularly relevant in scenarios such as autonomous vehicles, where split-second decision-making is imperative for safety and efficiency. The low-latency aspect of 5G is thus instrumental in unlocking the full potential of IoT applications that necessitate swift and reliable communication.
The technical foundations of 5G and IoT integration rest upon the pillars of high-speed data transfer, low latency, and the adaptability afforded by network slicing. This synergy not only addresses the connectivity needs of current IoT applications but also lays the groundwork for the emergence of innovative and transformative technologies that will shape the future of interconnected devices and services.
Enhancing Industrial Processes with 5G and IoT
The integration of 5G and the Internet of Things (IoT) holds profound implications for the industrial landscape, ushering in a new era marked by heightened efficiency, precision, and automation. One of the primary ways this synergy enhances industrial processes is through the concept of smart factories. With 5G's high-speed data transfer and low latency, IoT-enabled devices within manufacturing plants can communicate in real-time, optimizing production processes and reducing downtime. From predictive maintenance of machinery to the coordination of robotic systems, the integration of 5G and IoT empowers industries to operate with unprecedented levels of agility and responsiveness.
Predictive maintenance, enabled by the continuous monitoring and analysis of equipment through IoT sensors, stands as a transformative application in industrial settings. The timely detection of potential issues allows for proactive maintenance, minimizing unplanned downtime and extending the lifespan of machinery. The real-time insights provided by 5G-connected IoT devices contribute to a paradigm shift from reactive to proactive maintenance strategies, fundamentally altering how industries manage their assets.
The marriage of 5G and IoT is a catalyst for the transformation of industrial processes. The seamless connectivity, high data speeds, and low latency provided by 5G empower IoT devices to revolutionize manufacturing and operational practices. As industries continue to embrace these technologies, the prospect of smart factories and agile, data-driven decision-making emerges as a cornerstone in the evolution of modern industrial processes.
Smart Cities and Urban Connectivity
The fusion of 5G and the Internet of Things (IoT) is reshaping the urban landscape, giving rise to the concept of smart cities characterized by interconnected and intelligent infrastructure. This transformative synergy addresses the growing challenges faced by urban centers and propels cities into a future where efficiency, sustainability, and quality of life are paramount. At the heart of this evolution is the enhancement of urban connectivity through the deployment of 5G networks and the integration of IoT devices.
In the realm of smart cities, 5G's high-speed data transfer capabilities and low latency redefine the way urban systems operate. From traffic management and public safety to energy distribution and waste management, the integration of IoT sensors and devices leverages 5G connectivity to enable real-time data collection and analysis. This real-time responsiveness facilitates adaptive urban planning, allowing city authorities to make informed decisions promptly and address emerging challenges swiftly.
The collaboration between 5G and IoT is at the forefront of revolutionizing urban connectivity, giving rise to smart cities that are efficient, sustainable, and responsive to the needs of their residents. As this integration continues to evolve, the vision of interconnected urban environments holds the promise of enhancing the quality of life, promoting sustainability, and addressing the complex challenges faced by modern cities.
Security Challenges and Solutions
The integration of 5G and the Internet of Things (IoT) brings forth a myriad of opportunities, but it also introduces a complex array of security challenges that demand careful consideration and innovative solutions. As the number of interconnected devices increases exponentially, so does the attack surface, making the entire ecosystem susceptible to various cyber threats. One prominent challenge is the vulnerability of IoT devices, often characterized by limited computational capabilities and inadequate security measures. These devices, ranging from smart home appliances to industrial sensors, can become entry points for malicious actors if not adequately protected.
The nature of 5G networks introduces additional security concerns, particularly in the context of their virtualized and software-driven architecture. The reliance on software-defined processes and virtualized network functions creates potential points of entry for cyber threats. Moreover, the increased complexity of 5G networks amplifies the difficulty of monitoring and securing the vast number of connections and devices, making it essential to fortify the network against potential breaches.
While the integration of 5G and IoT brings unprecedented connectivity, addressing security challenges is paramount to ensuring the reliability and integrity of these advanced networks. By adopting a holistic and collaborative approach that encompasses encryption, authentication, secure development practices, and ongoing vigilance, stakeholders can build a resilient foundation for the secure coexistence of 5G and IoT technologies.
Consumer Electronics and 5G
The marriage of 5G technology with the Internet of Things (IoT) is reshaping the landscape of consumer electronics, ushering in a new era of connectivity and innovation. 5G's high-speed data transfer capabilities and low latency are revolutionizing the way consumers interact with their electronic devices, from smart homes to wearables and beyond. In the realm of consumer electronics, the integration of 5G brings forth a paradigm shift, offering enhanced experiences, increased device interactivity, and a broader scope of applications.
One of the notable impacts of 5G on consumer electronics is evident in the realm of smart homes. With the proliferation of IoT devices within households, ranging from smart thermostats and security cameras to connected appliances, 5G provides the bandwidth and responsiveness required for these devices to communicate seamlessly. Home automation becomes more sophisticated, allowing users to control and monitor various aspects of their homes remotely. The integration of 5G enables near-instantaneous responses, creating a more responsive and interactive smart home environment.
Entertainment experiences are elevated through 5G connectivity in consumer electronics. Streaming high-definition content, immersive virtual reality (VR), and augmented reality (AR) applications become more seamless and responsive, offering users a more immersive and engaging entertainment landscape. The integration of 5G enables faster downloads, reduced lag, and an overall improvement in the quality of multimedia experiences.
The fusion of 5G and consumer electronics marks a transformative moment in the way individuals interact with their devices. The high-speed, low-latency capabilities of 5G contribute to the evolution of smart homes, wearables, and entertainment systems, offering users enhanced connectivity, responsiveness, and a plethora of innovative applications. As consumer electronics continue to evolve within this interconnected ecosystem, the synergy between 5G and IoT is poised to redefine the possibilities of daily technological interactions.
Edge Computing in the 5G-IoT Ecosystem
Edge computing plays a pivotal role in the seamless integration of 5G and the Internet of Things (IoT), ushering in a paradigm shift in how data is processed and utilized within this dynamic ecosystem. At its core, edge computing involves the decentralization of computing resources, bringing data processing closer to the source of data generation. In the context of the 5G-IoT ecosystem, this approach becomes increasingly critical as it addresses the need for real-time data analysis, reduced latency, and efficient bandwidth utilization.
One of the key advantages of edge computing in the 5G-IoT landscape is its ability to alleviate latency concerns. By processing data closer to where it is generated, edge computing significantly reduces the time it takes for information to travel from IoT devices to centralized data centers and back. This is particularly crucial for applications that demand near-instantaneous responses, such as autonomous vehicles, smart grids, and industrial automation. The low-latency benefits of edge computing contribute to enhanced system responsiveness and overall efficiency.
The security implications of edge computing in the 5G-IoT ecosystem are noteworthy as well. By processing sensitive data locally, at the edge, organizations can mitigate potential risks associated with transmitting sensitive information across networks. This localized approach to data processing enhances privacy and security, aligning with the growing concerns surrounding the protection of IoT-generated data.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the intersection of 5G and the Internet of Things (IoT) represents a powerful symbiosis that is reshaping the landscape of connectivity and technological innovation. The technical foundations of 5G, including high-speed data transfer, low latency, and network slicing, provide the essential framework for the seamless integration of IoT devices, unlocking a new realm of possibilities across various industries and applications.
The enhanced connectivity facilitated by 5G and IoT is particularly evident in key domains such as industrial processes, where smart factories and predictive maintenance redefine efficiency, and in the development of smart cities, where urban connectivity is transforming the way cities operate, plan, and evolve. In healthcare, consumer electronics, and transportation, the amalgamation of 5G and IoT is driving advancements that were once constrained by the limitations of previous-generation networks.
As the integration of 5G and IoT continues to evolve, the promise of real-time connectivity, advanced automation, and data-driven decision-making comes to the forefront. Edge computing emerges as a critical enabler, addressing the need for reduced latency and efficient bandwidth utilization, while also enhancing the security posture of the interconnected ecosystem.
Looking forward, the collaborative efforts of industry stakeholders, ongoing research, and a commitment to addressing challenges will be instrumental in realizing the full potential of the 5G-IoT ecosystem. The journey towards a connected, intelligent, and responsive world is well underway, driven by the powerful combination of 5G and the Internet of Things. As these technologies continue to mature, the possibilities for innovation and positive societal impact are boundless, heralding a future where connectivity transcends current limitations, creating a foundation for a truly interconnected and intelligent world.
Read More
The advent of 5G technology has marked a transformative era in the realm of connectivity, promising unprecedented speed, low latency, and enhanced network capabilities. This fifth-generation wireless technology goes beyond merely improving our browsing experiences; it forms the backbone of a digital revolution that extends its influence to various industries and technologies. One of the most promising synergies emerging from the 5G landscape is its integration with the Internet of Things (IoT), creating a powerful alliance that has the potential to redefine how devices communicate, share data, and contribute to a seamlessly connected world.
As we delve into the intersection of 5G and IoT, it becomes evident that their combined capabilities unlock a new dimension of possibilities. The Internet of Things, characterized by interconnected devices exchanging information and performing tasks autonomously, gains a significant boost with the high-speed, low-latency nature of 5G networks. This synergy is poised to propel the growth of smart cities, autonomous vehicles, industrial automation, and countless other applications that demand rapid and reliable data transmission.
Moreover, the amalgamation of 5G and IoT is not confined to elevating the speed of data transfer. It brings forth a paradigm shift in how devices interact and collaborate, fostering an environment where real-time communication becomes the norm rather than the exception. This real-time connectivity has far-reaching implications, from enabling critical applications in healthcare to enhancing the efficiency of supply chain management. The seamless integration of 5G and IoT creates a robust foundation for innovation, paving the way for novel solutions and services that were once constrained by the limitations of previous-generation networks.
In this exploration of the powerful combination of 5G and IoT, it is essential to recognize the potential challenges and considerations that come with such technological advancements. From security concerns to the need for standardized protocols, navigating the intricacies of this evolving landscape requires a holistic understanding of the implications and a commitment to addressing the associated complexities. As we navigate this transformative journey, the fusion of 5G and IoT stands as a beacon guiding us toward a future where connectivity transcends its current boundaries, opening doors to unparalleled possibilities in the digital age.
Table of contents
-
Technical Foundations of 5G and IoT Integration
-
Enhancing Industrial Processes with 5G and IoT
-
Smart Cities and Urban Connectivity
-
Security Challenges and Solutions
-
Consumer Electronics and 5G
-
Edge Computing in the 5G-IoT Ecosystem
-
Conclusion
Technical Foundations of 5G and IoT Integration
The integration of 5G and the Internet of Things (IoT) is underpinned by a robust set of technical foundations that collectively redefine the landscape of connectivity. At the core of this integration lies the high-speed data transfer capabilities of 5G networks. With significantly increased data rates compared to its predecessors, 5G facilitates the rapid exchange of information between IoT devices, enabling them to communicate seamlessly and efficiently. This enhanced data transfer speed is a critical factor in supporting the diverse range of applications and services that rely on real-time data processing.
Low latency, another key element of 5G's technical prowess, plays a pivotal role in the integration with IoT. The near-instantaneous response times achieved by 5G networks reduce communication delays between devices, a crucial requirement for applications demanding real-time interactions. This is particularly relevant in scenarios such as autonomous vehicles, where split-second decision-making is imperative for safety and efficiency. The low-latency aspect of 5G is thus instrumental in unlocking the full potential of IoT applications that necessitate swift and reliable communication.
The technical foundations of 5G and IoT integration rest upon the pillars of high-speed data transfer, low latency, and the adaptability afforded by network slicing. This synergy not only addresses the connectivity needs of current IoT applications but also lays the groundwork for the emergence of innovative and transformative technologies that will shape the future of interconnected devices and services.
Enhancing Industrial Processes with 5G and IoT
The integration of 5G and the Internet of Things (IoT) holds profound implications for the industrial landscape, ushering in a new era marked by heightened efficiency, precision, and automation. One of the primary ways this synergy enhances industrial processes is through the concept of smart factories. With 5G's high-speed data transfer and low latency, IoT-enabled devices within manufacturing plants can communicate in real-time, optimizing production processes and reducing downtime. From predictive maintenance of machinery to the coordination of robotic systems, the integration of 5G and IoT empowers industries to operate with unprecedented levels of agility and responsiveness.
Predictive maintenance, enabled by the continuous monitoring and analysis of equipment through IoT sensors, stands as a transformative application in industrial settings. The timely detection of potential issues allows for proactive maintenance, minimizing unplanned downtime and extending the lifespan of machinery. The real-time insights provided by 5G-connected IoT devices contribute to a paradigm shift from reactive to proactive maintenance strategies, fundamentally altering how industries manage their assets.
The marriage of 5G and IoT is a catalyst for the transformation of industrial processes. The seamless connectivity, high data speeds, and low latency provided by 5G empower IoT devices to revolutionize manufacturing and operational practices. As industries continue to embrace these technologies, the prospect of smart factories and agile, data-driven decision-making emerges as a cornerstone in the evolution of modern industrial processes.
Smart Cities and Urban Connectivity
The fusion of 5G and the Internet of Things (IoT) is reshaping the urban landscape, giving rise to the concept of smart cities characterized by interconnected and intelligent infrastructure. This transformative synergy addresses the growing challenges faced by urban centers and propels cities into a future where efficiency, sustainability, and quality of life are paramount. At the heart of this evolution is the enhancement of urban connectivity through the deployment of 5G networks and the integration of IoT devices.
In the realm of smart cities, 5G's high-speed data transfer capabilities and low latency redefine the way urban systems operate. From traffic management and public safety to energy distribution and waste management, the integration of IoT sensors and devices leverages 5G connectivity to enable real-time data collection and analysis. This real-time responsiveness facilitates adaptive urban planning, allowing city authorities to make informed decisions promptly and address emerging challenges swiftly.
The collaboration between 5G and IoT is at the forefront of revolutionizing urban connectivity, giving rise to smart cities that are efficient, sustainable, and responsive to the needs of their residents. As this integration continues to evolve, the vision of interconnected urban environments holds the promise of enhancing the quality of life, promoting sustainability, and addressing the complex challenges faced by modern cities.
Security Challenges and Solutions
The integration of 5G and the Internet of Things (IoT) brings forth a myriad of opportunities, but it also introduces a complex array of security challenges that demand careful consideration and innovative solutions. As the number of interconnected devices increases exponentially, so does the attack surface, making the entire ecosystem susceptible to various cyber threats. One prominent challenge is the vulnerability of IoT devices, often characterized by limited computational capabilities and inadequate security measures. These devices, ranging from smart home appliances to industrial sensors, can become entry points for malicious actors if not adequately protected.
The nature of 5G networks introduces additional security concerns, particularly in the context of their virtualized and software-driven architecture. The reliance on software-defined processes and virtualized network functions creates potential points of entry for cyber threats. Moreover, the increased complexity of 5G networks amplifies the difficulty of monitoring and securing the vast number of connections and devices, making it essential to fortify the network against potential breaches.
While the integration of 5G and IoT brings unprecedented connectivity, addressing security challenges is paramount to ensuring the reliability and integrity of these advanced networks. By adopting a holistic and collaborative approach that encompasses encryption, authentication, secure development practices, and ongoing vigilance, stakeholders can build a resilient foundation for the secure coexistence of 5G and IoT technologies.
Consumer Electronics and 5G
The marriage of 5G technology with the Internet of Things (IoT) is reshaping the landscape of consumer electronics, ushering in a new era of connectivity and innovation. 5G's high-speed data transfer capabilities and low latency are revolutionizing the way consumers interact with their electronic devices, from smart homes to wearables and beyond. In the realm of consumer electronics, the integration of 5G brings forth a paradigm shift, offering enhanced experiences, increased device interactivity, and a broader scope of applications.
One of the notable impacts of 5G on consumer electronics is evident in the realm of smart homes. With the proliferation of IoT devices within households, ranging from smart thermostats and security cameras to connected appliances, 5G provides the bandwidth and responsiveness required for these devices to communicate seamlessly. Home automation becomes more sophisticated, allowing users to control and monitor various aspects of their homes remotely. The integration of 5G enables near-instantaneous responses, creating a more responsive and interactive smart home environment.
Entertainment experiences are elevated through 5G connectivity in consumer electronics. Streaming high-definition content, immersive virtual reality (VR), and augmented reality (AR) applications become more seamless and responsive, offering users a more immersive and engaging entertainment landscape. The integration of 5G enables faster downloads, reduced lag, and an overall improvement in the quality of multimedia experiences.
The fusion of 5G and consumer electronics marks a transformative moment in the way individuals interact with their devices. The high-speed, low-latency capabilities of 5G contribute to the evolution of smart homes, wearables, and entertainment systems, offering users enhanced connectivity, responsiveness, and a plethora of innovative applications. As consumer electronics continue to evolve within this interconnected ecosystem, the synergy between 5G and IoT is poised to redefine the possibilities of daily technological interactions.
Edge Computing in the 5G-IoT Ecosystem
Edge computing plays a pivotal role in the seamless integration of 5G and the Internet of Things (IoT), ushering in a paradigm shift in how data is processed and utilized within this dynamic ecosystem. At its core, edge computing involves the decentralization of computing resources, bringing data processing closer to the source of data generation. In the context of the 5G-IoT ecosystem, this approach becomes increasingly critical as it addresses the need for real-time data analysis, reduced latency, and efficient bandwidth utilization.
One of the key advantages of edge computing in the 5G-IoT landscape is its ability to alleviate latency concerns. By processing data closer to where it is generated, edge computing significantly reduces the time it takes for information to travel from IoT devices to centralized data centers and back. This is particularly crucial for applications that demand near-instantaneous responses, such as autonomous vehicles, smart grids, and industrial automation. The low-latency benefits of edge computing contribute to enhanced system responsiveness and overall efficiency.
The security implications of edge computing in the 5G-IoT ecosystem are noteworthy as well. By processing sensitive data locally, at the edge, organizations can mitigate potential risks associated with transmitting sensitive information across networks. This localized approach to data processing enhances privacy and security, aligning with the growing concerns surrounding the protection of IoT-generated data.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the intersection of 5G and the Internet of Things (IoT) represents a powerful symbiosis that is reshaping the landscape of connectivity and technological innovation. The technical foundations of 5G, including high-speed data transfer, low latency, and network slicing, provide the essential framework for the seamless integration of IoT devices, unlocking a new realm of possibilities across various industries and applications.
The enhanced connectivity facilitated by 5G and IoT is particularly evident in key domains such as industrial processes, where smart factories and predictive maintenance redefine efficiency, and in the development of smart cities, where urban connectivity is transforming the way cities operate, plan, and evolve. In healthcare, consumer electronics, and transportation, the amalgamation of 5G and IoT is driving advancements that were once constrained by the limitations of previous-generation networks.
As the integration of 5G and IoT continues to evolve, the promise of real-time connectivity, advanced automation, and data-driven decision-making comes to the forefront. Edge computing emerges as a critical enabler, addressing the need for reduced latency and efficient bandwidth utilization, while also enhancing the security posture of the interconnected ecosystem.
Looking forward, the collaborative efforts of industry stakeholders, ongoing research, and a commitment to addressing challenges will be instrumental in realizing the full potential of the 5G-IoT ecosystem. The journey towards a connected, intelligent, and responsive world is well underway, driven by the powerful combination of 5G and the Internet of Things. As these technologies continue to mature, the possibilities for innovation and positive societal impact are boundless, heralding a future where connectivity transcends current limitations, creating a foundation for a truly interconnected and intelligent world.
Next-Gen Authentication: Ethical Hacking Perspectives
The landscape of cybersecurity is undergoing constant evolution as technology advances and cyber threats become more sophisticated. In this dynamic environment, the traditional methods of authentication are proving to be inadequate in ensuring the security of sensitive information and systems. As a response to this challenge, the concept of Next-Gen Authentication has emerged, ushering in a new era of securing digital assets.
Next-Gen Authentication goes beyond traditional username-password combinations, exploring innovative and multifaceted approaches to verify user identity. This paradigm shift is driven by the recognition that cyber attackers continually devise new methods to exploit vulnerabilities in existing authentication systems. Ethical hacking, a practice where security professionals simulate cyber attacks to identify weaknesses, plays a pivotal role in shaping Next-Gen Authentication strategies. By adopting an ethical hacking perspective, organizations can proactively identify and address potential vulnerabilities, fortifying their defenses against malicious actors.
This introduction sets the stage for an exploration of Next-Gen Authentication from the vantage point of ethical hacking. As we delve into the intricacies of this evolving field, we will uncover the principles, technologies, and ethical considerations that guide the development and implementation of robust authentication mechanisms. The journey into Next-Gen Authentication promises to unveil a spectrum of innovative solutions that not only enhance security but also challenge the traditional boundaries of authentication in the digital realm.
Table of contents
-
Biometric Authentication Advancements
-
Behavioral Authentication
-
Blockchain in Authentication
-
Multi-Factor Authentication (MFA)
-
Passwordless Authentication
-
Regulatory Compliance in Next-Gen Authentication
-
Conclusion
Biometric Authentication Advancements
Biometric authentication, once confined to the realms of science fiction, has rapidly become a mainstream component of Next-Gen Authentication, revolutionizing the way users prove their identity. This sub-topic delves into the forefront of advancements within the field, exploring cutting-edge technologies that leverage unique physical or behavioral attributes for user verification. From fingerprint recognition and facial scanning to iris and voice recognition, the evolution of biometric authentication is characterized by its ability to provide a more secure and convenient user experience.
One key aspect to examine within biometric authentication advancements is the constant refinement of accuracy and reliability. Ethical hacking perspectives in this context involve scrutinizing the vulnerabilities associated with specific biometric modalities, testing for potential exploits, and evaluating the robustness of the authentication system. As biometric databases grow in scale and complexity, ethical hackers play a crucial role in identifying weaknesses that could be exploited by malicious actors seeking unauthorized access.
Additionally, the integration of artificial intelligence (AI) and machine learning (ML) algorithms has significantly enhanced the performance of biometric systems. These technologies enable systems to adapt and improve over time, learning from user interactions and continuously refining the authentication process. However, ethical hacking considerations become essential in assessing the resilience of these AI-driven biometric authentication systems, ensuring they are not susceptible to adversarial attacks or unauthorized manipulations.
The exploration of biometric authentication advancements provides a comprehensive understanding of the technological strides made in the realm of user identification. Ethical hacking perspectives are crucial for uncovering potential vulnerabilities, ensuring the reliability of these systems, and contributing to the ongoing dialogue on balancing technological innovation with robust security measures. As biometric authentication continues to evolve, its integration within the broader landscape of Next-Gen Authentication reflects a paradigm shift towards more secure and user-friendly methods of proving identity.
Behavioral Authentication
Behavioral authentication represents a cutting-edge approach to Next-Gen Authentication, shifting the focus from physical attributes to individual patterns of behavior. This innovative method harnesses unique characteristics in how users interact with digital systems, adding an additional layer of security to the authentication process. Unlike traditional methods that rely on static information like passwords or fingerprints, behavioral authentication analyzes dynamic patterns, such as keystroke dynamics, mouse movements, and even the way a user holds their device.
The concept of behavioral authentication stems from the understanding that individuals exhibit consistent and distinguishable behaviors when interacting with technology. Ethical hacking perspectives within this domain involve critically evaluating the effectiveness of such behavioral biometrics in preventing unauthorized access. Ethical hackers explore potential vulnerabilities, testing the resilience of behavioral authentication systems against various attack vectors to ensure their robustness in real-world scenarios.
One notable advantage of behavioral authentication lies in its continuous authentication capabilities. Traditional methods often require users to authenticate themselves periodically, but behavioral authentication continuously monitors user interactions, providing a seamless and non-intrusive security layer. Ethical hacking practices play a critical role in ensuring that this continuous monitoring does not compromise user privacy and that potential weaknesses are identified and addressed.
Behavioral authentication represents a significant advancement in the quest for more secure and user-friendly authentication methods. Ethical hacking perspectives play a crucial role in refining and fortifying these systems, ensuring that they meet the dual objectives of enhancing security while respecting user privacy and consent. As the digital landscape continues to evolve, behavioral authentication stands as a testament to the ongoing innovation in Next-Gen Authentication solutions.
Blockchain in Authentication
Blockchain technology, renowned for its foundational role in cryptocurrencies, is increasingly making inroads into the realm of authentication, offering a decentralized and tamper-resistant approach to verifying user identity. In the context of Next-Gen Authentication, the integration of blockchain holds the promise of enhancing security by providing a transparent and immutable ledger for recording authentication transactions. This sub-topic explores the opportunities and risks associated with leveraging blockchain for authentication purposes.
One of the key advantages of utilizing blockchain in authentication lies in its ability to create a decentralized and distributed ledger. Instead of relying on a central authority to verify and authenticate users, blockchain allows for a network of nodes to reach a consensus, enhancing the resilience against single points of failure and minimizing the risk of unauthorized access. Ethical hacking perspectives in this domain involve assessing the robustness of blockchain-based authentication protocols, scrutinizing smart contracts and consensus mechanisms to identify potential vulnerabilities.
The tamper-resistant nature of blockchain ensures that once an authentication transaction is recorded, it cannot be altered retroactively. This immutability is particularly valuable in preventing unauthorized changes to user identity records, mitigating the risks associated with identity theft and fraudulent activities. Ethical hackers play a critical role in stress-testing the blockchain infrastructure, aiming to uncover any potential weaknesses that could compromise the integrity of the authentication ledger.
The exploration of blockchain in authentication represents a paradigm shift towards decentralized, transparent, and tamper-resistant identity verification. Ethical hacking perspectives are instrumental in ensuring that the implementation of blockchain technology for authentication not only enhances security but also addresses potential risks and challenges, ultimately contributing to the evolution of more robust Next-Gen Authentication solutions.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) stands as a cornerstone in the landscape of Next-Gen Authentication, addressing the inherent vulnerabilities of single-factor methods. This authentication paradigm requires users to provide two or more types of identification credentials before granting access, typically combining something the user knows (like a password) with something they have (such as a security token) or something they are (biometric data). This sub-topic explores the evolution of MFA, its role in bolstering security, and the ethical hacking considerations involved in its implementation.
MFA's fundamental strength lies in its ability to add layers of complexity, significantly reducing the likelihood of unauthorized access. Ethical hacking perspectives in the realm of MFA involve rigorous testing of these layers, probing for potential weaknesses and vulnerabilities that could be exploited by malicious actors. Assessments often include evaluating the effectiveness of each authentication factor and their combined resilience in thwarting various attack vectors.
Multi-Factor Authentication represents a pivotal advancement in fortifying digital security, offering a versatile and layered approach to user authentication. Ethical hacking perspectives contribute to the ongoing refinement of MFA systems, addressing vulnerabilities, and ensuring that the balance between security and user experience is maintained in the ever-evolving landscape of Next-Gen Authentication.
Passwordless Authentication
Passwordless authentication marks a paradigm shift in the landscape of digital security, challenging the conventional reliance on traditional passwords for user verification. This innovative approach seeks to eliminate the vulnerabilities associated with password-based systems, such as weak passwords, password reuse, and susceptibility to phishing attacks. In a passwordless authentication framework, users gain access to their accounts or systems without the need to remember complex passwords. This sub-topic delves into the principles, opportunities, and ethical hacking considerations surrounding the adoption of passwordless authentication.
The principle behind passwordless authentication lies in utilizing alternative factors for user verification, such as biometrics, security tokens, or device-based authentication. Ethical hacking perspectives within this domain involve scrutinizing the implementation of these alternative authentication methods, ensuring that they are resilient to various attack vectors and provide a secure means of user verification. Assessments often focus on the interoperability and reliability of the chosen passwordless authentication factors.
Passwordless authentication represents a transformative approach to securing digital identities by eliminating the vulnerabilities inherent in traditional password systems. Ethical hacking perspectives contribute to the ongoing evolution of passwordless authentication, ensuring that security is not compromised in the pursuit of a more user-friendly and resilient authentication framework.
Regulatory Compliance in Next-Gen Authentication
The integration of Next-Gen Authentication technologies is not only a matter of technological advancement but also requires careful consideration of regulatory compliance. This sub-topic explores the crucial intersection between Next-Gen Authentication and the regulatory landscape, emphasizing the ethical implications and considerations involved in ensuring alignment with applicable laws and standards.
In many industries and regions, there exist stringent regulations governing the protection of sensitive data and the methods used for user authentication. As organizations adopt Next-Gen Authentication solutions, they must navigate and comply with these regulatory frameworks. Ethical hacking perspectives in this domain involve conducting assessments to ensure that authentication systems adhere to the specific requirements set forth by regulatory bodies, whether it be GDPR in Europe, HIPAA in healthcare, or other industry-specific standards.
The ethical considerations encompass the transparent communication of data usage policies to end-users and obtaining their informed consent. Ethical hackers play a critical role in evaluating the clarity and accessibility of privacy policies, ensuring that users are well-informed about how their authentication data is collected, stored, and processed. This scrutiny extends to the mechanisms in place to protect user data against unauthorized access and breaches.
The intertwining of Next-Gen Authentication and regulatory compliance underscores the need for a holistic approach to security. Ethical hacking perspectives contribute to the ongoing commitment to compliance by assessing not only the technical robustness of authentication systems but also the ethical and legal considerations associated with user data protection. As organizations strive to stay ahead in the dynamic landscape of authentication technologies, maintaining regulatory compliance becomes an ethical imperative to safeguard user privacy and trust.
How to obtain Cyber Security CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the exploration of "Next-Gen Authentication: Ethical Hacking Perspectives" reveals a dynamic and evolving landscape at the intersection of cutting-edge security measures and ethical considerations. As technology advances, so do the methodologies employed by cyber adversaries, necessitating the development and implementation of innovative authentication solutions. Ethical hacking emerges as a pivotal force in shaping the trajectory of Next-Gen Authentication, playing a critical role in identifying vulnerabilities, testing resilience, and ensuring the ethical and regulatory compliance of these advanced systems.
The sub-topics covered, ranging from biometric authentication advancements to the integration of blockchain, behavioral authentication, and passwordless authentication, underscore the diverse and multifaceted nature of Next-Gen Authentication. Each of these areas presents opportunities for strengthening security while posing unique challenges that demand ethical scrutiny. Ethical hackers, acting as vigilant guardians, contribute by conducting thorough assessments, scrutinizing protocols, and providing insights that enable organizations to fortify their authentication mechanisms.
The journey into Next-Gen Authentication is ongoing, marked by a commitment to continuous improvement and adaptability in the face of emerging threats. As ethical hackers continue to collaborate with organizations, the evolution of authentication mechanisms will be guided not only by technological innovation but also by a steadfast commitment to ethical practices that prioritize the protection of user information, respect for privacy, and compliance with regulatory standards. In this symbiotic relationship between security and ethics, the realm of Next-Gen Authentication charts a course towards a more secure, resilient, and ethically grounded digital future.
Read More
The landscape of cybersecurity is undergoing constant evolution as technology advances and cyber threats become more sophisticated. In this dynamic environment, the traditional methods of authentication are proving to be inadequate in ensuring the security of sensitive information and systems. As a response to this challenge, the concept of Next-Gen Authentication has emerged, ushering in a new era of securing digital assets.
Next-Gen Authentication goes beyond traditional username-password combinations, exploring innovative and multifaceted approaches to verify user identity. This paradigm shift is driven by the recognition that cyber attackers continually devise new methods to exploit vulnerabilities in existing authentication systems. Ethical hacking, a practice where security professionals simulate cyber attacks to identify weaknesses, plays a pivotal role in shaping Next-Gen Authentication strategies. By adopting an ethical hacking perspective, organizations can proactively identify and address potential vulnerabilities, fortifying their defenses against malicious actors.
This introduction sets the stage for an exploration of Next-Gen Authentication from the vantage point of ethical hacking. As we delve into the intricacies of this evolving field, we will uncover the principles, technologies, and ethical considerations that guide the development and implementation of robust authentication mechanisms. The journey into Next-Gen Authentication promises to unveil a spectrum of innovative solutions that not only enhance security but also challenge the traditional boundaries of authentication in the digital realm.
Table of contents
-
Biometric Authentication Advancements
-
Behavioral Authentication
-
Blockchain in Authentication
-
Multi-Factor Authentication (MFA)
-
Passwordless Authentication
-
Regulatory Compliance in Next-Gen Authentication
-
Conclusion
Biometric Authentication Advancements
Biometric authentication, once confined to the realms of science fiction, has rapidly become a mainstream component of Next-Gen Authentication, revolutionizing the way users prove their identity. This sub-topic delves into the forefront of advancements within the field, exploring cutting-edge technologies that leverage unique physical or behavioral attributes for user verification. From fingerprint recognition and facial scanning to iris and voice recognition, the evolution of biometric authentication is characterized by its ability to provide a more secure and convenient user experience.
One key aspect to examine within biometric authentication advancements is the constant refinement of accuracy and reliability. Ethical hacking perspectives in this context involve scrutinizing the vulnerabilities associated with specific biometric modalities, testing for potential exploits, and evaluating the robustness of the authentication system. As biometric databases grow in scale and complexity, ethical hackers play a crucial role in identifying weaknesses that could be exploited by malicious actors seeking unauthorized access.
Additionally, the integration of artificial intelligence (AI) and machine learning (ML) algorithms has significantly enhanced the performance of biometric systems. These technologies enable systems to adapt and improve over time, learning from user interactions and continuously refining the authentication process. However, ethical hacking considerations become essential in assessing the resilience of these AI-driven biometric authentication systems, ensuring they are not susceptible to adversarial attacks or unauthorized manipulations.
The exploration of biometric authentication advancements provides a comprehensive understanding of the technological strides made in the realm of user identification. Ethical hacking perspectives are crucial for uncovering potential vulnerabilities, ensuring the reliability of these systems, and contributing to the ongoing dialogue on balancing technological innovation with robust security measures. As biometric authentication continues to evolve, its integration within the broader landscape of Next-Gen Authentication reflects a paradigm shift towards more secure and user-friendly methods of proving identity.
Behavioral Authentication
Behavioral authentication represents a cutting-edge approach to Next-Gen Authentication, shifting the focus from physical attributes to individual patterns of behavior. This innovative method harnesses unique characteristics in how users interact with digital systems, adding an additional layer of security to the authentication process. Unlike traditional methods that rely on static information like passwords or fingerprints, behavioral authentication analyzes dynamic patterns, such as keystroke dynamics, mouse movements, and even the way a user holds their device.
The concept of behavioral authentication stems from the understanding that individuals exhibit consistent and distinguishable behaviors when interacting with technology. Ethical hacking perspectives within this domain involve critically evaluating the effectiveness of such behavioral biometrics in preventing unauthorized access. Ethical hackers explore potential vulnerabilities, testing the resilience of behavioral authentication systems against various attack vectors to ensure their robustness in real-world scenarios.
One notable advantage of behavioral authentication lies in its continuous authentication capabilities. Traditional methods often require users to authenticate themselves periodically, but behavioral authentication continuously monitors user interactions, providing a seamless and non-intrusive security layer. Ethical hacking practices play a critical role in ensuring that this continuous monitoring does not compromise user privacy and that potential weaknesses are identified and addressed.
Behavioral authentication represents a significant advancement in the quest for more secure and user-friendly authentication methods. Ethical hacking perspectives play a crucial role in refining and fortifying these systems, ensuring that they meet the dual objectives of enhancing security while respecting user privacy and consent. As the digital landscape continues to evolve, behavioral authentication stands as a testament to the ongoing innovation in Next-Gen Authentication solutions.
Blockchain in Authentication
Blockchain technology, renowned for its foundational role in cryptocurrencies, is increasingly making inroads into the realm of authentication, offering a decentralized and tamper-resistant approach to verifying user identity. In the context of Next-Gen Authentication, the integration of blockchain holds the promise of enhancing security by providing a transparent and immutable ledger for recording authentication transactions. This sub-topic explores the opportunities and risks associated with leveraging blockchain for authentication purposes.
One of the key advantages of utilizing blockchain in authentication lies in its ability to create a decentralized and distributed ledger. Instead of relying on a central authority to verify and authenticate users, blockchain allows for a network of nodes to reach a consensus, enhancing the resilience against single points of failure and minimizing the risk of unauthorized access. Ethical hacking perspectives in this domain involve assessing the robustness of blockchain-based authentication protocols, scrutinizing smart contracts and consensus mechanisms to identify potential vulnerabilities.
The tamper-resistant nature of blockchain ensures that once an authentication transaction is recorded, it cannot be altered retroactively. This immutability is particularly valuable in preventing unauthorized changes to user identity records, mitigating the risks associated with identity theft and fraudulent activities. Ethical hackers play a critical role in stress-testing the blockchain infrastructure, aiming to uncover any potential weaknesses that could compromise the integrity of the authentication ledger.
The exploration of blockchain in authentication represents a paradigm shift towards decentralized, transparent, and tamper-resistant identity verification. Ethical hacking perspectives are instrumental in ensuring that the implementation of blockchain technology for authentication not only enhances security but also addresses potential risks and challenges, ultimately contributing to the evolution of more robust Next-Gen Authentication solutions.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) stands as a cornerstone in the landscape of Next-Gen Authentication, addressing the inherent vulnerabilities of single-factor methods. This authentication paradigm requires users to provide two or more types of identification credentials before granting access, typically combining something the user knows (like a password) with something they have (such as a security token) or something they are (biometric data). This sub-topic explores the evolution of MFA, its role in bolstering security, and the ethical hacking considerations involved in its implementation.
MFA's fundamental strength lies in its ability to add layers of complexity, significantly reducing the likelihood of unauthorized access. Ethical hacking perspectives in the realm of MFA involve rigorous testing of these layers, probing for potential weaknesses and vulnerabilities that could be exploited by malicious actors. Assessments often include evaluating the effectiveness of each authentication factor and their combined resilience in thwarting various attack vectors.
Multi-Factor Authentication represents a pivotal advancement in fortifying digital security, offering a versatile and layered approach to user authentication. Ethical hacking perspectives contribute to the ongoing refinement of MFA systems, addressing vulnerabilities, and ensuring that the balance between security and user experience is maintained in the ever-evolving landscape of Next-Gen Authentication.
Passwordless Authentication
Passwordless authentication marks a paradigm shift in the landscape of digital security, challenging the conventional reliance on traditional passwords for user verification. This innovative approach seeks to eliminate the vulnerabilities associated with password-based systems, such as weak passwords, password reuse, and susceptibility to phishing attacks. In a passwordless authentication framework, users gain access to their accounts or systems without the need to remember complex passwords. This sub-topic delves into the principles, opportunities, and ethical hacking considerations surrounding the adoption of passwordless authentication.
The principle behind passwordless authentication lies in utilizing alternative factors for user verification, such as biometrics, security tokens, or device-based authentication. Ethical hacking perspectives within this domain involve scrutinizing the implementation of these alternative authentication methods, ensuring that they are resilient to various attack vectors and provide a secure means of user verification. Assessments often focus on the interoperability and reliability of the chosen passwordless authentication factors.
Passwordless authentication represents a transformative approach to securing digital identities by eliminating the vulnerabilities inherent in traditional password systems. Ethical hacking perspectives contribute to the ongoing evolution of passwordless authentication, ensuring that security is not compromised in the pursuit of a more user-friendly and resilient authentication framework.
Regulatory Compliance in Next-Gen Authentication
The integration of Next-Gen Authentication technologies is not only a matter of technological advancement but also requires careful consideration of regulatory compliance. This sub-topic explores the crucial intersection between Next-Gen Authentication and the regulatory landscape, emphasizing the ethical implications and considerations involved in ensuring alignment with applicable laws and standards.
In many industries and regions, there exist stringent regulations governing the protection of sensitive data and the methods used for user authentication. As organizations adopt Next-Gen Authentication solutions, they must navigate and comply with these regulatory frameworks. Ethical hacking perspectives in this domain involve conducting assessments to ensure that authentication systems adhere to the specific requirements set forth by regulatory bodies, whether it be GDPR in Europe, HIPAA in healthcare, or other industry-specific standards.
The ethical considerations encompass the transparent communication of data usage policies to end-users and obtaining their informed consent. Ethical hackers play a critical role in evaluating the clarity and accessibility of privacy policies, ensuring that users are well-informed about how their authentication data is collected, stored, and processed. This scrutiny extends to the mechanisms in place to protect user data against unauthorized access and breaches.
The intertwining of Next-Gen Authentication and regulatory compliance underscores the need for a holistic approach to security. Ethical hacking perspectives contribute to the ongoing commitment to compliance by assessing not only the technical robustness of authentication systems but also the ethical and legal considerations associated with user data protection. As organizations strive to stay ahead in the dynamic landscape of authentication technologies, maintaining regulatory compliance becomes an ethical imperative to safeguard user privacy and trust.
How to obtain Cyber Security CERTIFICATION?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the exploration of "Next-Gen Authentication: Ethical Hacking Perspectives" reveals a dynamic and evolving landscape at the intersection of cutting-edge security measures and ethical considerations. As technology advances, so do the methodologies employed by cyber adversaries, necessitating the development and implementation of innovative authentication solutions. Ethical hacking emerges as a pivotal force in shaping the trajectory of Next-Gen Authentication, playing a critical role in identifying vulnerabilities, testing resilience, and ensuring the ethical and regulatory compliance of these advanced systems.
The sub-topics covered, ranging from biometric authentication advancements to the integration of blockchain, behavioral authentication, and passwordless authentication, underscore the diverse and multifaceted nature of Next-Gen Authentication. Each of these areas presents opportunities for strengthening security while posing unique challenges that demand ethical scrutiny. Ethical hackers, acting as vigilant guardians, contribute by conducting thorough assessments, scrutinizing protocols, and providing insights that enable organizations to fortify their authentication mechanisms.
The journey into Next-Gen Authentication is ongoing, marked by a commitment to continuous improvement and adaptability in the face of emerging threats. As ethical hackers continue to collaborate with organizations, the evolution of authentication mechanisms will be guided not only by technological innovation but also by a steadfast commitment to ethical practices that prioritize the protection of user information, respect for privacy, and compliance with regulatory standards. In this symbiotic relationship between security and ethics, the realm of Next-Gen Authentication charts a course towards a more secure, resilient, and ethically grounded digital future.
Understanding the Core Concepts of Capability Maturity Model Integration (CMMI)
In the dynamic landscape of today's global business environment, organizations face the perpetual challenge of delivering high-quality products and services while striving for operational efficiency. To navigate this complex terrain, many enterprises turn to established frameworks and models that provide a structured approach to process improvement. One such powerful and widely adopted framework is the Capability Maturity Model Integration (CMMI).
CMMI stands as a beacon for organizations aspiring to enhance their capabilities and achieve a higher level of maturity in their processes. It offers a comprehensive and integrated set of best practices that guide organizations in developing and improving their processes, ultimately leading to increased performance, reliability, and customer satisfaction.
This exploration delves into the core concepts of CMMI, unraveling its intricacies and shedding light on the transformative journey that organizations embark upon when embracing this model. From understanding the fundamental principles that underpin CMMI to exploring its maturity levels and process areas, we will navigate through the key components that make CMMI a cornerstone in the pursuit of organizational excellence.
As we embark on this journey, we will demystify the terminology, delve into the rationale behind CMMI, and highlight the practical implications for organizations seeking to elevate their capabilities. Join us in unraveling the layers of CMMI, as we uncover the essence of this model and its profound impact on shaping robust, resilient, and high-performance organizations in the modern business landscape.
Table Of Contents
-
Foundations of CMMI: Defining Capability and Maturity
-
CMMI Framework Components: Processes, Practices, and Goals
-
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
-
Process Areas: Building Blocks for Effective Performance
-
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
-
CMMI Models for Different Domains: Customizing Excellence
-
Appraisals in CMMI: Evaluating and Improving Organizational Capability
-
Measuring Success: Key Performance Indicators in CMMI
-
CMMI and Agile: Bridging the Gap for Dynamic Environments
-
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
-
Conclusion
Foundations of CMMI: Defining Capability and Maturity
The foundations of the Capability Maturity Model Integration (CMMI) lie in its dual emphasis on capability and maturity, which together form the bedrock of organizational excellence. In the CMMI context, capability refers to an organization's inherent ability to reliably and predictably achieve its business objectives through well-defined processes. This involves understanding and harnessing the organization's resources, processes, and technology to consistently produce desired outcomes. On the other hand, maturity signifies the evolutionary progression of an organization's processes from ad-hoc and chaotic states to well-defined, measured, and optimized levels. It encapsulates the organization's journey toward process improvement and the establishment of best practices. By defining capability and maturity as intertwined aspects, CMMI provides a holistic framework that empowers organizations to assess, enhance, and continually evolve their processes, ensuring they are not only capable of meeting current demands but are also on a trajectory of continual improvement. This foundational understanding sets the stage for organizations to embark on a purposeful journey towards operational excellence and sustained success.
CMMI Framework Components: Processes, Practices, and Goals
The Capability Maturity Model Integration (CMMI) is a robust framework built upon key components, each playing a pivotal role in guiding organizations toward process improvement and excellence. At its core are processes, the dynamic sequences of activities that transform inputs into valuable outputs. CMMI emphasizes the definition, implementation, and continuous refinement of these processes to ensure consistency, efficiency, and adaptability within an organization.
Embedded within the framework are best practices, collectively known as practices, which encapsulate the distilled wisdom of successful processes. Practices serve as guidelines, outlining the specific activities, methods, and techniques that contribute to the effective execution of processes. They provide organizations with a roadmap for achieving desired outcomes and for adapting to evolving business needs.
Furthermore, CMMI incorporates the concept of goals, which represent the high-level objectives that organizations aspire to achieve. Goals guide the selection and implementation of practices, aligning them with the organization's strategic objectives. These goals serve as benchmarks, enabling organizations to measure their progress and maturity levels across different areas.
In essence, the synergy among processes, practices, and goals within the CMMI framework forms a dynamic triad. Processes provide the operational backbone, practices offer actionable insights, and goals steer organizations towards overarching excellence. Understanding and optimizing this interconnected framework empowers organizations to systematically elevate their capabilities and achieve maturity in a structured and sustainable manner.
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
Navigating through the Maturity Levels within the Capability Maturity Model Integration (CMMI) unveils a transformative journey, guiding organizations from the tumultuous realm of chaos towards a state of perpetual enhancement. Commencing at Level 1, organizations grapple with ad-hoc processes, characterized by unpredictability and disorder. The transition to Level 2 signifies a pivotal step, introducing foundational project management practices and instilling a semblance of control.
As organizations ascend to Level 3, a culture of standardization emerges. Processes become not only defined but also tailored to specific project needs, fostering a proactive approach to process management. The journey intensifies at Level 4, where organizations employ quantitative techniques, utilizing data to gain insights and enhance predictability. This meticulous control sets the stage for the pinnacle, Level 5, characterized by an unwavering commitment to continual improvement.
At Level 5, organizations go beyond control to actively monitor, adapt, and innovate. A culture of perpetual enhancement becomes ingrained, enabling organizations not only to navigate complexity but to thrive amidst change. The narrative of progression through these maturity levels encapsulates more than a refinement of processes; it signifies a profound organizational evolution, positioning entities as dynamic and resilient contributors to the ever-evolving business landscape.
Process Areas: Building Blocks for Effective Performance
Process areas stand as the foundational building blocks within the Capability Maturity Model Integration (CMMI), forming the essential elements that underpin an organization's capability to deliver effective performance. These areas define clusters of related activities that, when executed cohesively, contribute to the achievement of specific objectives and the overall success of the organization.
Each process area within CMMI encapsulates a set of best practices and guidelines tailored to address particular aspects of an organization's operations. They serve as a roadmap, providing a structured approach for organizations to develop, implement, and continually improve their processes. These building blocks are instrumental in aligning organizational goals with practical, actionable steps, fostering consistency, efficiency, and ultimately, superior performance.
By focusing on process areas, organizations can systematically enhance their capabilities in critical areas such as project management, requirements development, and process improvement. The comprehensive nature of these areas ensures that organizations not only meet their immediate objectives but also cultivate a culture of continuous improvement, adaptability, and resilience.
Process areas within CMMI are the linchpin of effective performance. They enable organizations to elevate their processes beyond mere compliance to standards, driving them towards operational excellence and ensuring sustained success in today's dynamic and competitive business environment.
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
In the realm of Capability Maturity Model Integration (CMMI), organizations are presented with two distinct yet flexible approaches: the Continuous Representation and the Staged Representation. These representations serve as adaptable frameworks, allowing organizations to tailor their CMMI adoption to align precisely with their unique operational needs, preferences, and strategic objectives.
The Staged Representation offers a structured, milestone-oriented approach, where maturity levels are attained sequentially. This method provides a clear roadmap, guiding organizations from one level to the next, each level building upon the achievements of the previous one. It is particularly beneficial for organizations seeking a well-defined, step-by-step approach to maturity.
Conversely, the Continuous Representation allows for a more tailored and flexible adoption. Instead of following a strict sequence of maturity levels, organizations can choose to focus on specific process areas that align with their immediate priorities. This approach provides the freedom to address targeted areas of improvement without the constraint of a predetermined sequence.
The decision between these representations hinges on an organization's unique context, goals, and existing processes. The Staged Representation may be preferable for those seeking a systematic, comprehensive approach to maturity, while the Continuous Representation offers a more agile and customizable route.
Ultimately, whether an organization opts for the Staged or Continuous Representation, the key lies in aligning CMMI adoption with organizational needs. This strategic alignment empowers organizations to leverage the power of CMMI in a way that not only improves processes but also seamlessly integrates with their broader business objectives and operational landscape.
CMMI Models for Different Domains: Customizing Excellence
In the dynamic landscape of industries spanning from software development to manufacturing and beyond, a one-size-fits-all approach to process improvement may not be optimal. Recognizing this diversity, the Capability Maturity Model Integration (CMMI) provides specialized models tailored to meet the unique challenges and nuances of different domains. These domain-specific adaptations empower organizations to customize their journey toward excellence, aligning CMMI principles with the specific requirements of their industry.
For software and systems engineering, the CMMI for Development (CMMI-DEV) model offers a targeted framework. It emphasizes best practices for managing and improving development processes, ensuring the delivery of high-quality software and systems.
In the realm of services, the CMMI for Services (CMMI-SVC) model takes center stage. It addresses the distinctive aspects of service delivery, focusing on processes that enhance customer satisfaction, manage service delivery risks, and optimize service provider performance.
For organizations in the acquisition and supply chain domain, the CMMI for Acquisition (CMMI-ACQ) model becomes instrumental. It provides guidelines for effective acquisition processes, ensuring that organizations can seamlessly integrate suppliers and acquisitions into their overall improvement strategy.
The adaptability of CMMI models for different domains extends beyond these examples, encompassing areas such as product development, people management, and cybersecurity. Each tailored model incorporates industry-specific best practices while retaining the core CMMI principles, allowing organizations to reap the benefits of a proven framework while addressing the unique challenges within their domain.
Appraisals in CMMI: Evaluating and Improving Organizational Capability
In the realm of Capability Maturity Model Integration (CMMI), appraisals serve as pivotal mechanisms for evaluating and enhancing an organization's capability and maturity levels. An appraisal is a structured and rigorous assessment process conducted by certified professionals, providing organizations with insights into the effectiveness of their processes and identifying areas for improvement.
The CMMI appraisal process follows a systematic approach, examining how well an organization's processes align with the CMMI model's best practices. There are various types of appraisals, with the Standard CMMI Appraisal Method for Process Improvement (SCAMPI) being one of the most widely utilized. SCAMPI appraisals can be Class A, B, or C, each differing in scope, depth, and purpose.
Crucially, the insights gained from appraisals contribute to a continuous improvement cycle. Organizations can leverage appraisal findings to refine their processes, enhance capabilities, and align with strategic objectives. By identifying and addressing areas for improvement, organizations can systematically progress through the maturity levels of CMMI, ultimately enhancing their ability to deliver high-quality products and services.
CMMI appraisals play a dual role in evaluating and improving organizational capability. They offer a comprehensive assessment of an organization's adherence to CMMI best practices and provide a roadmap for continual enhancement, fostering a culture of proactive improvement and ensuring sustained success in today's competitive business landscape.
Measuring Success: Key Performance Indicators in CMMI
In the dynamic landscape of process improvement, the Capability Maturity Model Integration (CMMI) places a significant emphasis on quantifiable success through the use of Key Performance Indicators (KPIs). KPIs in CMMI act as essential metrics, offering organizations tangible and measurable insights into the effectiveness of their processes, the achievement of goals, and the overall progress in their journey towards maturity.
Key Performance Indicators within the CMMI framework are diverse and tailored to specific process areas. They are designed to provide a clear picture of an organization's performance, allowing for informed decision-making and targeted improvements. Some common KPIs include metrics related to project schedule adherence, defect density, and customer satisfaction.
The strategic use of KPIs extends beyond mere measurement; it serves as a catalyst for continuous improvement. By regularly assessing and analyzing these indicators, organizations can identify trends, areas of excellence, and potential challenges. This proactive approach enables them to make data-driven decisions, refine processes, and address issues promptly, fostering a culture of continual enhancement.
In summary, measuring success in CMMI relies on the strategic implementation of Key Performance Indicators. These metrics not only gauge the effectiveness of processes but also drive continuous improvement, enabling organizations to navigate the complexities of their industries with precision and ensuring a sustained trajectory of success.
CMMI and Agile: Bridging the Gap for Dynamic Environments
In the ever-evolving landscape of software development and project management, the integration of Capability Maturity Model Integration (CMMI) and Agile methodologies represents a strategic synergy aimed at addressing the challenges of dynamic and rapidly changing environments.
Agile, known for its flexibility, collaboration, and iterative approach, is favored in environments where responsiveness to change is paramount. CMMI, on the other hand, provides a structured framework for process improvement and maturity. Bridging the gap between these two seemingly distinct approaches holds the key to unlocking a holistic and adaptive model for organizational success.
Agile practices are inherently compatible with certain CMMI principles, particularly in the areas of continuous improvement, stakeholder engagement, and incremental development. By integrating Agile practices with CMMI, organizations can harness the iterative nature of Agile for rapid development cycles while leveraging CMMI's structure to ensure robust processes, measurement, and organizational learning.
This integration is not about compromising the agility of Agile or stifling innovation with rigid processes. Instead, it involves tailoring and adapting CMMI practices to complement and enhance Agile methodologies. The goal is to create a dynamic and resilient organizational culture that embraces change, values collaboration, and continually improves processes.
Ultimately, the combination of CMMI and Agile represents a powerful approach for organizations operating in dynamic environments. It harmonizes the best of both worlds, providing the structure needed for maturity and process improvement while preserving the agility required to navigate the uncertainties of today's fast-paced business landscape.
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
Embarking on the journey of implementing Capability Maturity Model Integration (CMMI) is a transformative endeavor for any organization, and it comes with its unique set of challenges and valuable lessons. Drawing insights from real-world experiences, we explore both the common challenges faced during CMMI implementation and the best practices that organizations have employed to navigate these hurdles successfully.
Challenges:
Resistance to Change:
Challenge: Employees may resist changes to established processes and workflows.
Lesson: Clear communication about the benefits of CMMI, coupled with employee involvement in the process, helps alleviate resistance.
Resource Constraints:
Challenge: Limited time, budget, and personnel resources can hinder implementation efforts.
Lesson: Prioritize initiatives based on their impact and feasibility, and seek executive support for resource allocation.
Tailoring the Model:
Challenge: Adapting CMMI practices to the specific needs of the organization can be challenging.
Lesson: Tailor CMMI to fit the organization's context, ensuring relevance without compromising the integrity of the model.
Documentation Overload:
Challenge: Excessive documentation requirements can be perceived as burdensome.
Lesson: Streamline documentation processes, focusing on value-added documentation and avoiding unnecessary bureaucracy.
Lack of Organizational Buy-In:
Challenge: If the entire organization does not buy into the CMMI initiative, implementation may face resistance.
Lesson: Engage key stakeholders early, demonstrate the benefits, and foster a culture that values continuous improvement.
Best Practices:
Executive Sponsorship:
Practice: Secure executive sponsorship to drive commitment and allocate necessary resources.
Pilot Projects:
Practice: Start with pilot projects to test CMMI practices in a controlled environment before full-scale implementation.
Training and Skill Development:
Practice: Invest in training programs to enhance the skills of employees and build a competent workforce.
Continuous Communication:
Practice: Maintain open and continuous communication channels to address concerns, share successes, and reinforce the importance of CMMI.
Iterative Implementation:
Practice: Adopt an iterative approach to implementation, allowing for incremental improvements and learning from each cycle.
By acknowledging these challenges and implementing best practices derived from real-world experiences, organizations can not only overcome obstacles in their CMMI journey but also cultivate a culture of continuous improvement and excellence. These lessons from the field serve as a guide for organizations aspiring to enhance their processes and achieve greater maturity.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) stands as a powerful framework for organizations seeking to enhance their processes, achieve higher maturity levels, and thrive in today's competitive business landscape. Our exploration into the core concepts of CMMI has unveiled its foundational principles, the significance of maturity levels, the importance of process areas, and the adaptability of representations.
As organizations progress through the maturity levels, transitioning from chaos to continual improvement, they gain not only a structured approach to process enhancement but also a cultural transformation that fosters resilience and adaptability. The tailored CMMI models for different domains further emphasize the versatility of this framework, allowing organizations to customize their pursuit of excellence.
Appraisals serve as crucial checkpoints, evaluating and refining organizational capabilities. Key Performance Indicators provide tangible metrics, offering a clear gauge of success and driving continuous improvement. Integrating CMMI with Agile methodologies creates a harmonious balance between structure and agility, vital for success in dynamic environments.
The challenges and best practices discussed reflect the real-world lessons learned by organizations navigating the CMMI implementation journey. Overcoming resistance to change, addressing resource constraints, and ensuring organizational buy-in are pivotal elements, while executive sponsorship, iterative implementation, and effective communication emerge as best practices for success.
As organizations embrace CMMI, they embark on a transformative journey towards operational maturity, guided by a framework that not only elevates their processes but also instills a culture of excellence and adaptability. By leveraging the core concepts, overcoming challenges, and embracing best practices, organizations can position themselves as industry leaders, capable of navigating the complexities of today's ever-changing business environment with confidence and success.
Read More
In the dynamic landscape of today's global business environment, organizations face the perpetual challenge of delivering high-quality products and services while striving for operational efficiency. To navigate this complex terrain, many enterprises turn to established frameworks and models that provide a structured approach to process improvement. One such powerful and widely adopted framework is the Capability Maturity Model Integration (CMMI).
CMMI stands as a beacon for organizations aspiring to enhance their capabilities and achieve a higher level of maturity in their processes. It offers a comprehensive and integrated set of best practices that guide organizations in developing and improving their processes, ultimately leading to increased performance, reliability, and customer satisfaction.
This exploration delves into the core concepts of CMMI, unraveling its intricacies and shedding light on the transformative journey that organizations embark upon when embracing this model. From understanding the fundamental principles that underpin CMMI to exploring its maturity levels and process areas, we will navigate through the key components that make CMMI a cornerstone in the pursuit of organizational excellence.
As we embark on this journey, we will demystify the terminology, delve into the rationale behind CMMI, and highlight the practical implications for organizations seeking to elevate their capabilities. Join us in unraveling the layers of CMMI, as we uncover the essence of this model and its profound impact on shaping robust, resilient, and high-performance organizations in the modern business landscape.
Table Of Contents
-
Foundations of CMMI: Defining Capability and Maturity
-
CMMI Framework Components: Processes, Practices, and Goals
-
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
-
Process Areas: Building Blocks for Effective Performance
-
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
-
CMMI Models for Different Domains: Customizing Excellence
-
Appraisals in CMMI: Evaluating and Improving Organizational Capability
-
Measuring Success: Key Performance Indicators in CMMI
-
CMMI and Agile: Bridging the Gap for Dynamic Environments
-
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
-
Conclusion
Foundations of CMMI: Defining Capability and Maturity
The foundations of the Capability Maturity Model Integration (CMMI) lie in its dual emphasis on capability and maturity, which together form the bedrock of organizational excellence. In the CMMI context, capability refers to an organization's inherent ability to reliably and predictably achieve its business objectives through well-defined processes. This involves understanding and harnessing the organization's resources, processes, and technology to consistently produce desired outcomes. On the other hand, maturity signifies the evolutionary progression of an organization's processes from ad-hoc and chaotic states to well-defined, measured, and optimized levels. It encapsulates the organization's journey toward process improvement and the establishment of best practices. By defining capability and maturity as intertwined aspects, CMMI provides a holistic framework that empowers organizations to assess, enhance, and continually evolve their processes, ensuring they are not only capable of meeting current demands but are also on a trajectory of continual improvement. This foundational understanding sets the stage for organizations to embark on a purposeful journey towards operational excellence and sustained success.
CMMI Framework Components: Processes, Practices, and Goals
The Capability Maturity Model Integration (CMMI) is a robust framework built upon key components, each playing a pivotal role in guiding organizations toward process improvement and excellence. At its core are processes, the dynamic sequences of activities that transform inputs into valuable outputs. CMMI emphasizes the definition, implementation, and continuous refinement of these processes to ensure consistency, efficiency, and adaptability within an organization.
Embedded within the framework are best practices, collectively known as practices, which encapsulate the distilled wisdom of successful processes. Practices serve as guidelines, outlining the specific activities, methods, and techniques that contribute to the effective execution of processes. They provide organizations with a roadmap for achieving desired outcomes and for adapting to evolving business needs.
Furthermore, CMMI incorporates the concept of goals, which represent the high-level objectives that organizations aspire to achieve. Goals guide the selection and implementation of practices, aligning them with the organization's strategic objectives. These goals serve as benchmarks, enabling organizations to measure their progress and maturity levels across different areas.
In essence, the synergy among processes, practices, and goals within the CMMI framework forms a dynamic triad. Processes provide the operational backbone, practices offer actionable insights, and goals steer organizations towards overarching excellence. Understanding and optimizing this interconnected framework empowers organizations to systematically elevate their capabilities and achieve maturity in a structured and sustainable manner.
Maturity Levels Demystified: Progressing from Chaos to Continual Improvement
Navigating through the Maturity Levels within the Capability Maturity Model Integration (CMMI) unveils a transformative journey, guiding organizations from the tumultuous realm of chaos towards a state of perpetual enhancement. Commencing at Level 1, organizations grapple with ad-hoc processes, characterized by unpredictability and disorder. The transition to Level 2 signifies a pivotal step, introducing foundational project management practices and instilling a semblance of control.
As organizations ascend to Level 3, a culture of standardization emerges. Processes become not only defined but also tailored to specific project needs, fostering a proactive approach to process management. The journey intensifies at Level 4, where organizations employ quantitative techniques, utilizing data to gain insights and enhance predictability. This meticulous control sets the stage for the pinnacle, Level 5, characterized by an unwavering commitment to continual improvement.
At Level 5, organizations go beyond control to actively monitor, adapt, and innovate. A culture of perpetual enhancement becomes ingrained, enabling organizations not only to navigate complexity but to thrive amidst change. The narrative of progression through these maturity levels encapsulates more than a refinement of processes; it signifies a profound organizational evolution, positioning entities as dynamic and resilient contributors to the ever-evolving business landscape.
Process Areas: Building Blocks for Effective Performance
Process areas stand as the foundational building blocks within the Capability Maturity Model Integration (CMMI), forming the essential elements that underpin an organization's capability to deliver effective performance. These areas define clusters of related activities that, when executed cohesively, contribute to the achievement of specific objectives and the overall success of the organization.
Each process area within CMMI encapsulates a set of best practices and guidelines tailored to address particular aspects of an organization's operations. They serve as a roadmap, providing a structured approach for organizations to develop, implement, and continually improve their processes. These building blocks are instrumental in aligning organizational goals with practical, actionable steps, fostering consistency, efficiency, and ultimately, superior performance.
By focusing on process areas, organizations can systematically enhance their capabilities in critical areas such as project management, requirements development, and process improvement. The comprehensive nature of these areas ensures that organizations not only meet their immediate objectives but also cultivate a culture of continuous improvement, adaptability, and resilience.
Process areas within CMMI are the linchpin of effective performance. They enable organizations to elevate their processes beyond mere compliance to standards, driving them towards operational excellence and ensuring sustained success in today's dynamic and competitive business environment.
Continuous and Staged Representations: Tailoring CMMI to Organizational Needs
In the realm of Capability Maturity Model Integration (CMMI), organizations are presented with two distinct yet flexible approaches: the Continuous Representation and the Staged Representation. These representations serve as adaptable frameworks, allowing organizations to tailor their CMMI adoption to align precisely with their unique operational needs, preferences, and strategic objectives.
The Staged Representation offers a structured, milestone-oriented approach, where maturity levels are attained sequentially. This method provides a clear roadmap, guiding organizations from one level to the next, each level building upon the achievements of the previous one. It is particularly beneficial for organizations seeking a well-defined, step-by-step approach to maturity.
Conversely, the Continuous Representation allows for a more tailored and flexible adoption. Instead of following a strict sequence of maturity levels, organizations can choose to focus on specific process areas that align with their immediate priorities. This approach provides the freedom to address targeted areas of improvement without the constraint of a predetermined sequence.
The decision between these representations hinges on an organization's unique context, goals, and existing processes. The Staged Representation may be preferable for those seeking a systematic, comprehensive approach to maturity, while the Continuous Representation offers a more agile and customizable route.
Ultimately, whether an organization opts for the Staged or Continuous Representation, the key lies in aligning CMMI adoption with organizational needs. This strategic alignment empowers organizations to leverage the power of CMMI in a way that not only improves processes but also seamlessly integrates with their broader business objectives and operational landscape.
CMMI Models for Different Domains: Customizing Excellence
In the dynamic landscape of industries spanning from software development to manufacturing and beyond, a one-size-fits-all approach to process improvement may not be optimal. Recognizing this diversity, the Capability Maturity Model Integration (CMMI) provides specialized models tailored to meet the unique challenges and nuances of different domains. These domain-specific adaptations empower organizations to customize their journey toward excellence, aligning CMMI principles with the specific requirements of their industry.
For software and systems engineering, the CMMI for Development (CMMI-DEV) model offers a targeted framework. It emphasizes best practices for managing and improving development processes, ensuring the delivery of high-quality software and systems.
In the realm of services, the CMMI for Services (CMMI-SVC) model takes center stage. It addresses the distinctive aspects of service delivery, focusing on processes that enhance customer satisfaction, manage service delivery risks, and optimize service provider performance.
For organizations in the acquisition and supply chain domain, the CMMI for Acquisition (CMMI-ACQ) model becomes instrumental. It provides guidelines for effective acquisition processes, ensuring that organizations can seamlessly integrate suppliers and acquisitions into their overall improvement strategy.
The adaptability of CMMI models for different domains extends beyond these examples, encompassing areas such as product development, people management, and cybersecurity. Each tailored model incorporates industry-specific best practices while retaining the core CMMI principles, allowing organizations to reap the benefits of a proven framework while addressing the unique challenges within their domain.
Appraisals in CMMI: Evaluating and Improving Organizational Capability
In the realm of Capability Maturity Model Integration (CMMI), appraisals serve as pivotal mechanisms for evaluating and enhancing an organization's capability and maturity levels. An appraisal is a structured and rigorous assessment process conducted by certified professionals, providing organizations with insights into the effectiveness of their processes and identifying areas for improvement.
The CMMI appraisal process follows a systematic approach, examining how well an organization's processes align with the CMMI model's best practices. There are various types of appraisals, with the Standard CMMI Appraisal Method for Process Improvement (SCAMPI) being one of the most widely utilized. SCAMPI appraisals can be Class A, B, or C, each differing in scope, depth, and purpose.
Crucially, the insights gained from appraisals contribute to a continuous improvement cycle. Organizations can leverage appraisal findings to refine their processes, enhance capabilities, and align with strategic objectives. By identifying and addressing areas for improvement, organizations can systematically progress through the maturity levels of CMMI, ultimately enhancing their ability to deliver high-quality products and services.
CMMI appraisals play a dual role in evaluating and improving organizational capability. They offer a comprehensive assessment of an organization's adherence to CMMI best practices and provide a roadmap for continual enhancement, fostering a culture of proactive improvement and ensuring sustained success in today's competitive business landscape.
Measuring Success: Key Performance Indicators in CMMI
In the dynamic landscape of process improvement, the Capability Maturity Model Integration (CMMI) places a significant emphasis on quantifiable success through the use of Key Performance Indicators (KPIs). KPIs in CMMI act as essential metrics, offering organizations tangible and measurable insights into the effectiveness of their processes, the achievement of goals, and the overall progress in their journey towards maturity.
Key Performance Indicators within the CMMI framework are diverse and tailored to specific process areas. They are designed to provide a clear picture of an organization's performance, allowing for informed decision-making and targeted improvements. Some common KPIs include metrics related to project schedule adherence, defect density, and customer satisfaction.
The strategic use of KPIs extends beyond mere measurement; it serves as a catalyst for continuous improvement. By regularly assessing and analyzing these indicators, organizations can identify trends, areas of excellence, and potential challenges. This proactive approach enables them to make data-driven decisions, refine processes, and address issues promptly, fostering a culture of continual enhancement.
In summary, measuring success in CMMI relies on the strategic implementation of Key Performance Indicators. These metrics not only gauge the effectiveness of processes but also drive continuous improvement, enabling organizations to navigate the complexities of their industries with precision and ensuring a sustained trajectory of success.
CMMI and Agile: Bridging the Gap for Dynamic Environments
In the ever-evolving landscape of software development and project management, the integration of Capability Maturity Model Integration (CMMI) and Agile methodologies represents a strategic synergy aimed at addressing the challenges of dynamic and rapidly changing environments.
Agile, known for its flexibility, collaboration, and iterative approach, is favored in environments where responsiveness to change is paramount. CMMI, on the other hand, provides a structured framework for process improvement and maturity. Bridging the gap between these two seemingly distinct approaches holds the key to unlocking a holistic and adaptive model for organizational success.
Agile practices are inherently compatible with certain CMMI principles, particularly in the areas of continuous improvement, stakeholder engagement, and incremental development. By integrating Agile practices with CMMI, organizations can harness the iterative nature of Agile for rapid development cycles while leveraging CMMI's structure to ensure robust processes, measurement, and organizational learning.
This integration is not about compromising the agility of Agile or stifling innovation with rigid processes. Instead, it involves tailoring and adapting CMMI practices to complement and enhance Agile methodologies. The goal is to create a dynamic and resilient organizational culture that embraces change, values collaboration, and continually improves processes.
Ultimately, the combination of CMMI and Agile represents a powerful approach for organizations operating in dynamic environments. It harmonizes the best of both worlds, providing the structure needed for maturity and process improvement while preserving the agility required to navigate the uncertainties of today's fast-paced business landscape.
Challenges and Best Practices in CMMI Implementation: Lessons from the Field
Embarking on the journey of implementing Capability Maturity Model Integration (CMMI) is a transformative endeavor for any organization, and it comes with its unique set of challenges and valuable lessons. Drawing insights from real-world experiences, we explore both the common challenges faced during CMMI implementation and the best practices that organizations have employed to navigate these hurdles successfully.
Challenges:
Resistance to Change:
Challenge: Employees may resist changes to established processes and workflows.
Lesson: Clear communication about the benefits of CMMI, coupled with employee involvement in the process, helps alleviate resistance.
Resource Constraints:
Challenge: Limited time, budget, and personnel resources can hinder implementation efforts.
Lesson: Prioritize initiatives based on their impact and feasibility, and seek executive support for resource allocation.
Tailoring the Model:
Challenge: Adapting CMMI practices to the specific needs of the organization can be challenging.
Lesson: Tailor CMMI to fit the organization's context, ensuring relevance without compromising the integrity of the model.
Documentation Overload:
Challenge: Excessive documentation requirements can be perceived as burdensome.
Lesson: Streamline documentation processes, focusing on value-added documentation and avoiding unnecessary bureaucracy.
Lack of Organizational Buy-In:
Challenge: If the entire organization does not buy into the CMMI initiative, implementation may face resistance.
Lesson: Engage key stakeholders early, demonstrate the benefits, and foster a culture that values continuous improvement.
Best Practices:
Executive Sponsorship:
Practice: Secure executive sponsorship to drive commitment and allocate necessary resources.
Pilot Projects:
Practice: Start with pilot projects to test CMMI practices in a controlled environment before full-scale implementation.
Training and Skill Development:
Practice: Invest in training programs to enhance the skills of employees and build a competent workforce.
Continuous Communication:
Practice: Maintain open and continuous communication channels to address concerns, share successes, and reinforce the importance of CMMI.
Iterative Implementation:
Practice: Adopt an iterative approach to implementation, allowing for incremental improvements and learning from each cycle.
By acknowledging these challenges and implementing best practices derived from real-world experiences, organizations can not only overcome obstacles in their CMMI journey but also cultivate a culture of continuous improvement and excellence. These lessons from the field serve as a guide for organizations aspiring to enhance their processes and achieve greater maturity.
How to obtain Project Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) stands as a powerful framework for organizations seeking to enhance their processes, achieve higher maturity levels, and thrive in today's competitive business landscape. Our exploration into the core concepts of CMMI has unveiled its foundational principles, the significance of maturity levels, the importance of process areas, and the adaptability of representations.
As organizations progress through the maturity levels, transitioning from chaos to continual improvement, they gain not only a structured approach to process enhancement but also a cultural transformation that fosters resilience and adaptability. The tailored CMMI models for different domains further emphasize the versatility of this framework, allowing organizations to customize their pursuit of excellence.
Appraisals serve as crucial checkpoints, evaluating and refining organizational capabilities. Key Performance Indicators provide tangible metrics, offering a clear gauge of success and driving continuous improvement. Integrating CMMI with Agile methodologies creates a harmonious balance between structure and agility, vital for success in dynamic environments.
The challenges and best practices discussed reflect the real-world lessons learned by organizations navigating the CMMI implementation journey. Overcoming resistance to change, addressing resource constraints, and ensuring organizational buy-in are pivotal elements, while executive sponsorship, iterative implementation, and effective communication emerge as best practices for success.
As organizations embrace CMMI, they embark on a transformative journey towards operational maturity, guided by a framework that not only elevates their processes but also instills a culture of excellence and adaptability. By leveraging the core concepts, overcoming challenges, and embracing best practices, organizations can position themselves as industry leaders, capable of navigating the complexities of today's ever-changing business environment with confidence and success.
In-Demand Business Analyst Career Paths in 2023
Embarking on the journey of a business analyst opens doors to a dynamic and stimulating career, requiring adept skills in information analysis, stakeholder communication, and the formulation of strategic recommendations to enhance overall business performance. This role finds relevance across diverse industries such as healthcare, education, finance, retail, and hospitality, making it a versatile and sought-after profession.
The escalating demand for Business Analysts is propelled by the universal necessity for strong analytical capabilities in virtually every sector. This piece delves into the trajectory of a business analyst's career, elucidating its inherent benefits. For those eager to explore this field further, the option of pursuing the ECBA Certification online is available, offering an in-depth understanding of the multifaceted dimensions within the domain. Join us as we unravel the intricate journey of business analyst career progression in the subsequent sections.
In this article
- A Step-by-Step Guide on Pursuing a Business Analyst Career Path
- Career Path of a Business Analyst
- Best Business Analyst Career Paths
- How Long Does It Take to Get Promoted to Senior Level?
- Conclusion
- Frequently Asked Questions (FAQs)
What is a Business Analyst?
If you're contemplating a path in the realm of Business Analysis, gaining a profound understanding of the intricacies of this role is paramount. A Business Analyst plays a pivotal role in the development of business solutions, starting from the crucial phase of gathering requirements to meticulously testing the solutions post-creation. Collaborating closely with business users, they decipher their needs and translate these insights into tailored solutions that align seamlessly with their objectives.
In addition to their core responsibilities, these professionals actively engage in quality assurance activities throughout various project phases. Beyond the technical aspects, Business Analysts also nurture enduring relationships with key stakeholders, ensuring a continuous exchange of insights and perspectives throughout the entire project lifecycle. In the forthcoming discussion, we will delve into the comprehensive career roadmap of a Business Analyst, shedding light on the nuanced aspects that define this dynamic profession.
A Step-by-Step Guide on Pursuing a Business Analyst Career Path
Embarking on a career as a business analyst is an exciting journey filled with opportunities for growth and impact. To guide you through this transformative path, consider the following step-by-step guide.
1.Understand the Role and Responsibilities: Begin by gaining a comprehensive understanding of the business analyst role. This involves analyzing information, identifying stakeholder needs, and formulating recommendations to enhance business performance. Familiarize yourself with the diverse industries where business analysts play a crucial role, such as healthcare, education, finance, retail, and hospitality.
2.Acquire Relevant Education and Skills: Equip yourself with the necessary education and skills. Many business analysts hold degrees in fields like business administration, finance, or information technology. Additionally, develop analytical skills, communication prowess, and a keen understanding of technology tools commonly used in the industry.
3.Gain Practical Experience: Practical experience is invaluable in the business analyst field. Seek internships, entry-level positions, or projects that allow you to apply theoretical knowledge in real-world scenarios. This hands-on experience will not only enhance your skills but also make you more appealing to potential employers.
4.Networking and Building Professional Connections: Establish a network within the business analysis community. Attend industry events, join professional associations, and engage with experienced business analysts. Networking provides valuable insights, mentorship opportunities, and a platform to stay updated on industry trends.
5.Consider Certification Programs: Explore relevant certification programs to validate your skills and knowledge. The Entry Certificate in Business Analysis (ECBA) is a notable certification that can boost your credibility as a business analyst. Online platforms offer convenient ways to pursue such certifications while balancing other commitments.
6.Prepare for Interviews: Anticipate common business analyst interview questions and prepare thoughtful responses. Emphasize your problem-solving abilities, communication skills, and experience in collaborating with diverse stakeholders. Showcase your understanding of industry-specific challenges and how you can contribute to addressing them.
Career Path of a Business Analyst
The career path of a business analyst is a dynamic journey characterized by progressive growth and skill development. It typically begins with entry-level positions, where individuals engage in foundational tasks such as data analysis and stakeholder communication. This initial phase serves as a crucial learning ground, providing exposure to the fundamentals of the business analyst role.
As professionals accumulate experience, they often pursue further education and skill enhancement to stay competitive in the field. This may involve obtaining relevant certifications like the Entry Certificate in Business Analysis (ECBA) and acquiring specialized knowledge through advanced degrees. This educational investment lays the groundwork for more sophisticated analytical responsibilities in mid-level roles.
In the mid-level phase, business analysts find themselves taking on more complex projects and assuming leadership within analytical teams. This stage involves a deeper understanding of industry intricacies and the application of specialized expertise to address organizational challenges. Business analysts may choose to specialize in particular industries or domains, contributing to their proficiency and effectiveness in their chosen field.
The career path of a business analyst is a continuous evolution marked by a commitment to learning, adaptability, and strategic thinking. The ability to navigate through diverse roles and responsibilities positions business analysts as valuable assets in organizations across various industries.
Best Business Analyst Career Paths
The field of business analysis offers diverse career paths, allowing professionals to tailor their trajectories based on their interests, skills, and aspirations. Here are some of the best business analyst career paths:
1.Specialization in Industries: Business analysts often find rewarding career paths by specializing in specific industries. Whether it's finance, healthcare, technology, or any other sector, becoming an industry expert allows professionals to contribute valuable insights tailored to the unique challenges and opportunities within that domain. This specialization enhances their impact and opens doors to leadership roles within industry-specific organizations.
2.Data Analysis and Business Intelligence: With the increasing importance of data-driven decision-making, business analysts can carve out a career path in data analysis and business intelligence. This involves mastering advanced analytics tools, developing predictive models, and extracting meaningful insights from large datasets. Professionals in this path are integral to organizations seeking to leverage data for strategic advantage.
3.Project Management: Business analysts with strong organizational and project management skills often transition into project management roles. In this career path, individuals lead and oversee the implementation of projects, ensuring that business objectives are met on time and within budget. This transition aligns with the business analyst's role in driving change and optimizing processes.
4.Consultancy and Advisory Services: Many experienced business analysts choose to offer consultancy and advisory services. This career path involves working independently or with consulting firms, providing expertise to clients seeking insights to improve their business processes. Consultants may tackle diverse projects, offering solutions ranging from process optimization to technology implementations.
5.Business Process Improvement: Business analysts can focus on business process improvement, specializing in streamlining workflows, enhancing efficiency, and optimizing organizational processes. This path involves collaborating with stakeholders to identify areas for improvement, implementing changes, and measuring the impact on overall business performance.
6.Entrepreneurship: Some business analysts opt for entrepreneurial ventures, establishing their consulting firms or startups. This career path allows individuals to apply their analytical skills to address specific market needs. Entrepreneurial business analysts may offer specialized services, develop innovative products, or create solutions to address industry gaps.
Strategic Planning and Leadership: Advancing into strategic planning and leadership roles is a natural progression for seasoned business analysts. In these positions, professionals contribute to the development and execution of organizational strategies. Their analytical insights play a pivotal role in shaping the overall direction of the company, and they collaborate closely with executive teams to achieve long-term goals.
How Long Does It Take to Get Promoted to Senior Level?
The timeline for getting promoted to a senior-level position varies widely and is influenced by several factors, including the industry, company policies, individual performance, and the overall organizational structure. In many professions, the journey to a senior-level role is characterized by a combination of experience, expertise, and demonstrated leadership.
In general, professionals often spend several years accumulating experience and honing their skills before being considered for promotion to a senior-level position. This period can range from five to ten years or more, depending on the complexity of the industry and the specific requirements of the role.
Individual performance and achievements play a crucial role in the promotion process. Employees who consistently excel in their responsibilities, take on additional challenges, and demonstrate leadership qualities may progress more rapidly through the ranks. Proactive efforts to expand one's skill set, pursue further education, and contribute to the success of the team and organization can expedite the journey to a senior-level role.
Company policies and structures also impact the timeline for promotions. Some organizations have clear and structured career paths with defined milestones, while others may adopt a more flexible approach based on individual merit and accomplishments. Additionally, organizational growth and the availability of senior-level positions can influence the timing of promotions.
Networking, mentorship, and visibility within the organization are essential components that can accelerate the promotion process. Building strong professional relationships, seeking guidance from mentors, and actively participating in cross-functional projects can enhance one's visibility and increase the likelihood of being recognized for advancement opportunities.
While there is no one-size-fits-all answer to the question of how long it takes to get promoted to a senior level, it is important for individuals to have open communication with their supervisors and human resources to understand the expectations and criteria for advancement within their specific organization. Regular performance evaluations, feedback sessions, and goal-setting discussions can provide valuable insights into the progression of one's career and the potential timeline for reaching senior-level positions.
Conclusion
In 2023, the landscape for business analysts is marked by a multitude of in-demand career paths, reflecting the evolving needs of industries in a rapidly changing global environment. The versatility of business analysts positions them at the forefront of crucial decision-making processes across various sectors.
One of the prominent career paths is the specialization in industries, where business analysts delve deep into sectors such as finance, healthcare, technology, and more. This specialization allows them to provide targeted insights and solutions to industry-specific challenges, making them invaluable assets to organizations seeking a competitive edge.
The increasing importance of data-driven decision-making has elevated the role of business analysts in data analysis and business intelligence. Professionals who master advanced analytics tools and can extract meaningful insights from vast datasets are in high demand, driving this career path to new heights.
As organizations continue to focus on process optimization and efficiency, business analysts specializing in business process improvement play a pivotal role. Streamlining workflows and optimizing organizational processes require a keen understanding of business operations, making these analysts instrumental in driving positive change within their organizations.
In conclusion, the in-demand business analyst career paths in 2023 showcase the adaptability and significance of this role in navigating the complexities of modern business. Whether specializing in industries, diving into data analytics, optimizing processes, providing consultancy services, assuming leadership roles, or embracing continuous learning, business analysts are poised to make enduring contributions to organizational success in the dynamic landscape of 2023 and beyond.
Frequently Asked Questions (FAQs)
Q: What are the key trends influencing business analyst career paths in 2023?
A: In 2023, key trends shaping business analyst career paths include industry specialization, increased demand for data analytics and business intelligence, a focus on business process improvement, rising opportunities in consultancy and advisory services, and the growing importance of strategic planning and leadership roles.
Q: How can I specialize in a specific industry as a business analyst?
A: Specializing in a specific industry involves gaining in-depth knowledge of that sector's dynamics, challenges, and opportunities. Consider pursuing relevant certifications, attending industry conferences, and actively seeking projects within the chosen industry. Networking with professionals in that field can also provide valuable insights and opportunities.
Q: What skills are crucial for a business analyst pursuing a career in data analytics and business intelligence?
A: Business analysts in data analytics and business intelligence should possess strong analytical skills, proficiency in data visualization tools, and the ability to derive meaningful insights from complex datasets. Technical skills in data manipulation and statistical analysis, coupled with effective communication, are also essential.
Q: How can I transition into a leadership role as a business analyst?
A: Transitioning into a leadership role involves showcasing strong analytical and strategic thinking skills, demonstrating leadership qualities in projects, and actively seeking opportunities to lead initiatives. Pursuing advanced certifications, acquiring additional management skills, and effectively communicating your vision for organizational success are key steps.
Read More
Embarking on the journey of a business analyst opens doors to a dynamic and stimulating career, requiring adept skills in information analysis, stakeholder communication, and the formulation of strategic recommendations to enhance overall business performance. This role finds relevance across diverse industries such as healthcare, education, finance, retail, and hospitality, making it a versatile and sought-after profession.
The escalating demand for Business Analysts is propelled by the universal necessity for strong analytical capabilities in virtually every sector. This piece delves into the trajectory of a business analyst's career, elucidating its inherent benefits. For those eager to explore this field further, the option of pursuing the ECBA Certification online is available, offering an in-depth understanding of the multifaceted dimensions within the domain. Join us as we unravel the intricate journey of business analyst career progression in the subsequent sections.
In this article
- A Step-by-Step Guide on Pursuing a Business Analyst Career Path
- Career Path of a Business Analyst
- Best Business Analyst Career Paths
- How Long Does It Take to Get Promoted to Senior Level?
- Conclusion
- Frequently Asked Questions (FAQs)
What is a Business Analyst?
If you're contemplating a path in the realm of Business Analysis, gaining a profound understanding of the intricacies of this role is paramount. A Business Analyst plays a pivotal role in the development of business solutions, starting from the crucial phase of gathering requirements to meticulously testing the solutions post-creation. Collaborating closely with business users, they decipher their needs and translate these insights into tailored solutions that align seamlessly with their objectives.
In addition to their core responsibilities, these professionals actively engage in quality assurance activities throughout various project phases. Beyond the technical aspects, Business Analysts also nurture enduring relationships with key stakeholders, ensuring a continuous exchange of insights and perspectives throughout the entire project lifecycle. In the forthcoming discussion, we will delve into the comprehensive career roadmap of a Business Analyst, shedding light on the nuanced aspects that define this dynamic profession.
A Step-by-Step Guide on Pursuing a Business Analyst Career Path
Embarking on a career as a business analyst is an exciting journey filled with opportunities for growth and impact. To guide you through this transformative path, consider the following step-by-step guide.
1.Understand the Role and Responsibilities: Begin by gaining a comprehensive understanding of the business analyst role. This involves analyzing information, identifying stakeholder needs, and formulating recommendations to enhance business performance. Familiarize yourself with the diverse industries where business analysts play a crucial role, such as healthcare, education, finance, retail, and hospitality.
2.Acquire Relevant Education and Skills: Equip yourself with the necessary education and skills. Many business analysts hold degrees in fields like business administration, finance, or information technology. Additionally, develop analytical skills, communication prowess, and a keen understanding of technology tools commonly used in the industry.
3.Gain Practical Experience: Practical experience is invaluable in the business analyst field. Seek internships, entry-level positions, or projects that allow you to apply theoretical knowledge in real-world scenarios. This hands-on experience will not only enhance your skills but also make you more appealing to potential employers.
4.Networking and Building Professional Connections: Establish a network within the business analysis community. Attend industry events, join professional associations, and engage with experienced business analysts. Networking provides valuable insights, mentorship opportunities, and a platform to stay updated on industry trends.
5.Consider Certification Programs: Explore relevant certification programs to validate your skills and knowledge. The Entry Certificate in Business Analysis (ECBA) is a notable certification that can boost your credibility as a business analyst. Online platforms offer convenient ways to pursue such certifications while balancing other commitments.
6.Prepare for Interviews: Anticipate common business analyst interview questions and prepare thoughtful responses. Emphasize your problem-solving abilities, communication skills, and experience in collaborating with diverse stakeholders. Showcase your understanding of industry-specific challenges and how you can contribute to addressing them.
Career Path of a Business Analyst
The career path of a business analyst is a dynamic journey characterized by progressive growth and skill development. It typically begins with entry-level positions, where individuals engage in foundational tasks such as data analysis and stakeholder communication. This initial phase serves as a crucial learning ground, providing exposure to the fundamentals of the business analyst role.
As professionals accumulate experience, they often pursue further education and skill enhancement to stay competitive in the field. This may involve obtaining relevant certifications like the Entry Certificate in Business Analysis (ECBA) and acquiring specialized knowledge through advanced degrees. This educational investment lays the groundwork for more sophisticated analytical responsibilities in mid-level roles.
In the mid-level phase, business analysts find themselves taking on more complex projects and assuming leadership within analytical teams. This stage involves a deeper understanding of industry intricacies and the application of specialized expertise to address organizational challenges. Business analysts may choose to specialize in particular industries or domains, contributing to their proficiency and effectiveness in their chosen field.
The career path of a business analyst is a continuous evolution marked by a commitment to learning, adaptability, and strategic thinking. The ability to navigate through diverse roles and responsibilities positions business analysts as valuable assets in organizations across various industries.
Best Business Analyst Career Paths
The field of business analysis offers diverse career paths, allowing professionals to tailor their trajectories based on their interests, skills, and aspirations. Here are some of the best business analyst career paths:
1.Specialization in Industries: Business analysts often find rewarding career paths by specializing in specific industries. Whether it's finance, healthcare, technology, or any other sector, becoming an industry expert allows professionals to contribute valuable insights tailored to the unique challenges and opportunities within that domain. This specialization enhances their impact and opens doors to leadership roles within industry-specific organizations.
2.Data Analysis and Business Intelligence: With the increasing importance of data-driven decision-making, business analysts can carve out a career path in data analysis and business intelligence. This involves mastering advanced analytics tools, developing predictive models, and extracting meaningful insights from large datasets. Professionals in this path are integral to organizations seeking to leverage data for strategic advantage.
3.Project Management: Business analysts with strong organizational and project management skills often transition into project management roles. In this career path, individuals lead and oversee the implementation of projects, ensuring that business objectives are met on time and within budget. This transition aligns with the business analyst's role in driving change and optimizing processes.
4.Consultancy and Advisory Services: Many experienced business analysts choose to offer consultancy and advisory services. This career path involves working independently or with consulting firms, providing expertise to clients seeking insights to improve their business processes. Consultants may tackle diverse projects, offering solutions ranging from process optimization to technology implementations.
5.Business Process Improvement: Business analysts can focus on business process improvement, specializing in streamlining workflows, enhancing efficiency, and optimizing organizational processes. This path involves collaborating with stakeholders to identify areas for improvement, implementing changes, and measuring the impact on overall business performance.
6.Entrepreneurship: Some business analysts opt for entrepreneurial ventures, establishing their consulting firms or startups. This career path allows individuals to apply their analytical skills to address specific market needs. Entrepreneurial business analysts may offer specialized services, develop innovative products, or create solutions to address industry gaps.
Strategic Planning and Leadership: Advancing into strategic planning and leadership roles is a natural progression for seasoned business analysts. In these positions, professionals contribute to the development and execution of organizational strategies. Their analytical insights play a pivotal role in shaping the overall direction of the company, and they collaborate closely with executive teams to achieve long-term goals.
How Long Does It Take to Get Promoted to Senior Level?
The timeline for getting promoted to a senior-level position varies widely and is influenced by several factors, including the industry, company policies, individual performance, and the overall organizational structure. In many professions, the journey to a senior-level role is characterized by a combination of experience, expertise, and demonstrated leadership.
In general, professionals often spend several years accumulating experience and honing their skills before being considered for promotion to a senior-level position. This period can range from five to ten years or more, depending on the complexity of the industry and the specific requirements of the role.
Individual performance and achievements play a crucial role in the promotion process. Employees who consistently excel in their responsibilities, take on additional challenges, and demonstrate leadership qualities may progress more rapidly through the ranks. Proactive efforts to expand one's skill set, pursue further education, and contribute to the success of the team and organization can expedite the journey to a senior-level role.
Company policies and structures also impact the timeline for promotions. Some organizations have clear and structured career paths with defined milestones, while others may adopt a more flexible approach based on individual merit and accomplishments. Additionally, organizational growth and the availability of senior-level positions can influence the timing of promotions.
Networking, mentorship, and visibility within the organization are essential components that can accelerate the promotion process. Building strong professional relationships, seeking guidance from mentors, and actively participating in cross-functional projects can enhance one's visibility and increase the likelihood of being recognized for advancement opportunities.
While there is no one-size-fits-all answer to the question of how long it takes to get promoted to a senior level, it is important for individuals to have open communication with their supervisors and human resources to understand the expectations and criteria for advancement within their specific organization. Regular performance evaluations, feedback sessions, and goal-setting discussions can provide valuable insights into the progression of one's career and the potential timeline for reaching senior-level positions.
Conclusion
In 2023, the landscape for business analysts is marked by a multitude of in-demand career paths, reflecting the evolving needs of industries in a rapidly changing global environment. The versatility of business analysts positions them at the forefront of crucial decision-making processes across various sectors.
One of the prominent career paths is the specialization in industries, where business analysts delve deep into sectors such as finance, healthcare, technology, and more. This specialization allows them to provide targeted insights and solutions to industry-specific challenges, making them invaluable assets to organizations seeking a competitive edge.
The increasing importance of data-driven decision-making has elevated the role of business analysts in data analysis and business intelligence. Professionals who master advanced analytics tools and can extract meaningful insights from vast datasets are in high demand, driving this career path to new heights.
As organizations continue to focus on process optimization and efficiency, business analysts specializing in business process improvement play a pivotal role. Streamlining workflows and optimizing organizational processes require a keen understanding of business operations, making these analysts instrumental in driving positive change within their organizations.
In conclusion, the in-demand business analyst career paths in 2023 showcase the adaptability and significance of this role in navigating the complexities of modern business. Whether specializing in industries, diving into data analytics, optimizing processes, providing consultancy services, assuming leadership roles, or embracing continuous learning, business analysts are poised to make enduring contributions to organizational success in the dynamic landscape of 2023 and beyond.
Frequently Asked Questions (FAQs)
Q: What are the key trends influencing business analyst career paths in 2023?
A: In 2023, key trends shaping business analyst career paths include industry specialization, increased demand for data analytics and business intelligence, a focus on business process improvement, rising opportunities in consultancy and advisory services, and the growing importance of strategic planning and leadership roles.
Q: How can I specialize in a specific industry as a business analyst?
A: Specializing in a specific industry involves gaining in-depth knowledge of that sector's dynamics, challenges, and opportunities. Consider pursuing relevant certifications, attending industry conferences, and actively seeking projects within the chosen industry. Networking with professionals in that field can also provide valuable insights and opportunities.
Q: What skills are crucial for a business analyst pursuing a career in data analytics and business intelligence?
A: Business analysts in data analytics and business intelligence should possess strong analytical skills, proficiency in data visualization tools, and the ability to derive meaningful insights from complex datasets. Technical skills in data manipulation and statistical analysis, coupled with effective communication, are also essential.
Q: How can I transition into a leadership role as a business analyst?
A: Transitioning into a leadership role involves showcasing strong analytical and strategic thinking skills, demonstrating leadership qualities in projects, and actively seeking opportunities to lead initiatives. Pursuing advanced certifications, acquiring additional management skills, and effectively communicating your vision for organizational success are key steps.
Big Data and Hadoop: Past, Present, and Future Trends
The advent of Big Data has heralded a transformative era in the field of information technology, revolutionizing the way organizations handle and analyze vast volumes of data. At the forefront of this data revolution is Hadoop, an open-source framework designed to process and store massive datasets in a distributed and scalable manner. Understanding the evolution of Big Data and the role played by Hadoop provides valuable insights into the past, present, and future trends that continue to shape the landscape of data analytics.
In the past decade, the exponential growth of digital information has outpaced traditional data processing capabilities, necessitating innovative solutions to manage and derive meaningful insights from this deluge of data. Big Data emerged as a paradigm shift, emphasizing the importance of leveraging diverse data sources, including structured and unstructured data, to gain a comprehensive understanding of business operations, customer behavior, and market trends.
The present landscape of Big Data and Hadoop is marked by widespread adoption across various industries, ranging from finance and healthcare to e-commerce and social media. Hadoop, with its distributed storage and processing capabilities, has become a cornerstone in handling the sheer volume and complexity of Big Data. Organizations are using Hadoop to extract valuable patterns, correlations, and trends that were previously challenging to uncover through traditional data processing methods.
Looking ahead, the future of Big Data and Hadoop promises continued innovation and evolution. As technology advances, there is a growing emphasis on enhancing the speed, scalability, and efficiency of Big Data processing. The integration of machine learning and artificial intelligence with Hadoop is expected to further amplify the capabilities of data analytics, enabling organizations to make more informed decisions in real-time. Additionally, the emergence of edge computing and the Internet of Things (IoT) will contribute to the generation of even larger datasets, necessitating advanced tools and frameworks to extract actionable insights.
In this exploration of Big Data and Hadoop, it is essential to delve into the historical context, understand the current landscape, and anticipate the trends that will shape the future. This journey through the evolution of data processing underscores the pivotal role played by these technologies in addressing the challenges and opportunities presented by the ever-expanding realm of Big Data.
Table of contents
-
Origins of Big Data
-
Early Days of Hadoop
-
Evolution of Hadoop Ecosystem
-
Challenges Faced in the Past
-
Current Landscape of Big Data Analytics
-
Future Architectural Trends
-
Sustainability and Green Computing
-
Conclusion
Origins of Big Data
The origins of Big Data can be traced back to the late 20th century, a period marked by a significant increase in the generation and storage of digital information. As the world became more interconnected, the rise of the internet and the proliferation of electronic devices contributed to an unprecedented influx of data. The traditional methods of data processing, which had served well in an era of relatively modest data volumes, began to falter in the face of this data explosion. The sheer scale, variety, and velocity of data generated posed a formidable challenge, necessitating a paradigm shift in how information was handled.
The early 2000s witnessed the formal recognition of this burgeoning challenge as industry experts and academics began to coin the term "Big Data" to describe datasets that surpassed the capacity of traditional databases and tools. The key characteristics of Big Data, often summarized as the three Vs—Volume, Variety, and Velocity—captured the essence of the data deluge that organizations were grappling with. The need for innovative solutions to manage, process, and extract insights from these vast datasets became increasingly apparent.
The emergence of open-source technologies played a pivotal role in addressing the complexities of Big Data. One of the foundational milestones in this journey was the development of the Hadoop framework by Doug Cutting and Mike Cafarella in the early 2000s. Named after a toy elephant, Hadoop represented a breakthrough in distributed computing, offering a scalable and fault-tolerant solution for processing large datasets across clusters of commodity hardware. Inspired by Google's MapReduce and Google File System (GFS), Hadoop laid the groundwork for a new era in data processing.
Early Days of Hadoop
The early days of Hadoop mark a significant chapter in the evolution of Big Data processing, representing a response to the escalating challenges posed by the unprecedented growth in data. Hadoop's inception can be traced back to 2004 when Doug Cutting and Mike Cafarella, inspired by Google's pioneering work on distributed computing, developed an open-source framework that would later become the cornerstone of Big Data solutions. The framework was named after a toy elephant owned by Cutting's son, symbolizing robustness and strength in handling large datasets.
In its nascent stages, Hadoop comprised two primary components: the Hadoop Distributed File System (HDFS) for distributed storage and the MapReduce programming model for parallel processing. These components, modeled after Google's GFS and MapReduce, respectively, provided a scalable and fault-tolerant infrastructure capable of processing massive datasets across clusters of commodity hardware. The Hadoop project was initially part of the Apache Nutch web search engine initiative, but it soon gained recognition as an independent and groundbreaking technology.
The early adopters of Hadoop were pioneers in recognizing its potential to revolutionize data processing. Yahoo became one of the first major companies to embrace Hadoop, employing it to index and analyze vast amounts of web data. The open-source nature of Hadoop contributed to its rapid growth as a community-driven project, with developers worldwide contributing to its enhancement and expansion. The Apache Software Foundation took over the project in 2006, fostering collaborative development and ensuring its continued evolution.
Despite its transformative potential, the early days of Hadoop were not without challenges. The framework required a paradigm shift in both technology and mindset, as organizations adapted to the decentralized and parallelized nature of Big Data processing. Nevertheless, Hadoop laid the groundwork for a scalable and cost-effective solution to the challenges posed by the explosion of digital information.
Evolution of Hadoop Ecosystem
The early days of Hadoop mark a significant chapter in the evolution of Big Data processing, representing a response to the escalating challenges posed by the unprecedented growth in data. Hadoop's inception can be traced back to 2004 when Doug Cutting and Mike Cafarella, inspired by Google's pioneering work on distributed computing, developed an open-source framework that would later become the cornerstone of Big Data solutions. The framework was named after a toy elephant owned by Cutting's son, symbolizing robustness and strength in handling large datasets.
In its nascent stages, Hadoop comprised two primary components: the Hadoop Distributed File System (HDFS) for distributed storage and the MapReduce programming model for parallel processing. These components, modeled after Google's GFS and MapReduce, respectively, provided a scalable and fault-tolerant infrastructure capable of processing massive datasets across clusters of commodity hardware. The Hadoop project was initially part of the Apache Nutch web search engine initiative, but it soon gained recognition as an independent and groundbreaking technology.
The early adopters of Hadoop were pioneers in recognizing its potential to revolutionize data processing. Yahoo became one of the first major companies to embrace Hadoop, employing it to index and analyze vast amounts of web data. The open-source nature of Hadoop contributed to its rapid growth as a community-driven project, with developers worldwide contributing to its enhancement and expansion. The Apache Software Foundation took over the project in 2006, fostering collaborative development and ensuring its continued evolution.
Despite its transformative potential, the early days of Hadoop were not without challenges. The framework required a paradigm shift in both technology and mindset, as organizations adapted to the decentralized and parallelized nature of Big Data processing. Nevertheless, Hadoop laid the groundwork for a scalable and cost-effective solution to the challenges posed by the explosion of digital information.
Challenges Faced in the Past
The past witnessed a revolutionary shift in the field of data processing as the world grappled with the challenges posed by the advent of Big Data. Traditional methods of handling data, designed for smaller volumes and simpler structures, proved inadequate in the face of the rapidly expanding datasets characterized by their unprecedented volume, variety, and velocity. Organizations were confronted with the daunting task of extracting meaningful insights from these vast and complex data landscapes, leading to the recognition of the need for innovative solutions.
One of the primary challenges faced in the early days of Big Data was the sheer volume of information generated and collected. Traditional databases struggled to cope with the exponential growth in data, resulting in performance bottlenecks and increased storage costs. The variety of data, encompassing structured and unstructured formats, further compounded the challenge. Relational databases, designed for structured data, were ill-equipped to handle the diverse array of information sources, including text, images, and multimedia.
The learning curve associated with adopting new technologies like Hadoop posed yet another challenge. Organizations faced the task of upskilling their workforce to navigate the complexities of distributed computing, parallel processing, and the unique programming model of MapReduce. Integration with existing infrastructure and the establishment of best practices for implementation added further layers of complexity.
Despite these challenges, early adopters recognized the transformative potential of Big Data technologies, including Hadoop. The successes of those who navigated these obstacles and effectively implemented solutions demonstrated the feasibility and value of embracing new approaches to data processing.
Current Landscape of Big Data Analytics
The current landscape of Big Data analytics is characterized by widespread adoption and integration of advanced technologies, with organizations leveraging sophisticated tools to extract valuable insights from massive datasets. Big Data analytics has become a cornerstone of decision-making processes across diverse industries, fundamentally transforming how businesses operate. At the heart of this transformation lies the prevalence of powerful frameworks and platforms, with Hadoop prominently featured among them.
Organizations today harness the capabilities of Big Data analytics to glean actionable insights from a variety of sources, including structured and unstructured data. The integration of Hadoop into the analytics ecosystem allows for the storage and processing of vast datasets across distributed clusters, enabling a level of scalability and flexibility previously unattainable. Businesses are leveraging these capabilities to gain a deeper understanding of customer behavior, optimize operational efficiency, and identify emerging trends in their respective markets.
Real-world applications of Big Data analytics are abundant, spanning sectors such as finance, healthcare, retail, and beyond. Financial institutions utilize advanced analytics to detect fraudulent activities in real-time, while healthcare organizations leverage predictive analytics to enhance patient outcomes and optimize resource allocation. E-commerce platforms analyze user behavior to personalize recommendations, and social media companies use Big Data analytics to understand user engagement and trends.
The current landscape also witnesses a move towards the democratization of data analytics, with user-friendly tools and platforms allowing individuals with varying levels of technical expertise to engage in data-driven decision-making. Cloud computing has played a pivotal role in this democratization, providing scalable infrastructure and services that facilitate the storage, processing, and analysis of Big Data without the need for extensive on-premises resources.
Future Architectural Trends
The future of Big Data analytics is poised for continual evolution, and the architectural trends shaping its trajectory reflect a commitment to addressing the growing complexities of data processing. One prominent trend is the increasing emphasis on scalability and agility in architectural design. As data volumes continue to soar, architectures must evolve to seamlessly accommodate the expanding requirements of storage, processing, and analytics. Scalable architectures, often facilitated by cloud computing environments, empower organizations to dynamically adjust resources to meet fluctuating demands, ensuring efficiency and cost-effectiveness.
Containerization is emerging as a key architectural trend in the future of Big Data analytics. Technologies like Docker and Kubernetes provide a standardized and portable way to package applications and their dependencies, enhancing the consistency and reproducibility of data processing workflows. This trend promotes agility by facilitating the seamless deployment and scaling of applications across different environments, streamlining the development and operational aspects of Big Data architectures.
Edge computing is playing an increasingly vital role in the architectural landscape, addressing the need for real-time processing and decision-making at the source of data generation. As devices at the edge of networks become more powerful, the integration of edge computing with Big Data architectures enables organizations to process and analyze data closer to its origin. This reduces latency, enhances responsiveness, and supports applications that require immediate insights, such as IoT devices and autonomous systems.
The integration of artificial intelligence (AI) and machine learning (ML) into Big Data architectures is a transformative trend that is expected to gain momentum in the future. AI and ML algorithms enable organizations to move beyond descriptive analytics and embrace predictive and prescriptive analytics, extracting valuable insights from data patterns and facilitating data-driven decision-making. This trend contributes to the evolution of Big Data architectures into intelligent systems capable of autonomously adapting to changing data dynamics.
Sustainability and Green Computing
The increasing scale of data processing and the proliferation of Big Data technologies have brought to the forefront a pressing concern: the environmental impact of data centers and the overall sustainability of data processing practices. As the demand for data storage and computing power continues to rise, the energy consumption associated with data centers has become a significant contributor to carbon emissions. In response to this environmental challenge, the concept of "Green Computing" has gained prominence, seeking to develop more sustainable and eco-friendly approaches to data processing.
Sustainability in the context of Big Data and computing encompasses a multifaceted approach. One key aspect involves the optimization of data center operations to minimize energy consumption. Data centers, which house the servers and infrastructure supporting Big Data processing, often require substantial power for cooling and maintenance. Sustainable data center design focuses on improving energy efficiency, utilizing renewable energy sources, and implementing advanced cooling technologies to reduce the environmental footprint of these facilities.
Efforts to reduce electronic waste (e-waste) also form an integral part of sustainable computing practices. With the rapid pace of technological advancements, electronic devices become obsolete quickly, contributing to the accumulation of e-waste. Sustainable approaches involve recycling and responsible disposal of electronic equipment, as well as designing devices with longevity and recyclability in mind.
The integration of sustainability principles into Big Data and computing practices is not only an environmental imperative but also aligns with corporate social responsibility. Organizations are increasingly recognizing the importance of adopting green computing practices to mitigate environmental impact, meet regulatory requirements, and enhance their reputation as responsible global citizens.
Conclusion
In conclusion, the exploration of "Big Data and Hadoop: Past, Present, and Future Trends" reveals a transformative journey that has reshaped the landscape of data processing and analytics. The historical evolution of Big Data, marked by the challenges posed by escalating data volumes, paved the way for innovative solutions like the Hadoop framework. The early days of Hadoop were characterized by the recognition of the need for scalable and distributed computing to handle large datasets effectively.
The challenges faced in the past, ranging from volume and variety to the need for upskilling and overcoming technological barriers, served as catalysts for advancements in Big Data technologies. Hadoop emerged as a pioneering solution, addressing these challenges and laying the groundwork for a new era in data processing.
Looking to the future, architectural trends in Big Data point towards scalability, agility, and the integration of emerging technologies. Containerization, edge computing, and the infusion of artificial intelligence and machine learning are poised to redefine how organizations approach data processing. The convergence of analytics and data management, along with a commitment to sustainability and green computing practices, underscores a holistic approach to addressing the challenges and opportunities presented by Big Data.
In essence, the narrative of Big Data and Hadoop is one of continuous evolution. From its historical origins as a response to data challenges to its current status as a fundamental component of data analytics, and towards future trends that promise even greater scalability, intelligence, and sustainability, the journey reflects the dynamic nature of technology. As organizations navigate this landscape, the fusion of innovation, adaptability, and ethical considerations will be crucial in shaping a future where Big Data not only informs decision-making but does so responsibly and sustainably.
Read More
The advent of Big Data has heralded a transformative era in the field of information technology, revolutionizing the way organizations handle and analyze vast volumes of data. At the forefront of this data revolution is Hadoop, an open-source framework designed to process and store massive datasets in a distributed and scalable manner. Understanding the evolution of Big Data and the role played by Hadoop provides valuable insights into the past, present, and future trends that continue to shape the landscape of data analytics.
In the past decade, the exponential growth of digital information has outpaced traditional data processing capabilities, necessitating innovative solutions to manage and derive meaningful insights from this deluge of data. Big Data emerged as a paradigm shift, emphasizing the importance of leveraging diverse data sources, including structured and unstructured data, to gain a comprehensive understanding of business operations, customer behavior, and market trends.
The present landscape of Big Data and Hadoop is marked by widespread adoption across various industries, ranging from finance and healthcare to e-commerce and social media. Hadoop, with its distributed storage and processing capabilities, has become a cornerstone in handling the sheer volume and complexity of Big Data. Organizations are using Hadoop to extract valuable patterns, correlations, and trends that were previously challenging to uncover through traditional data processing methods.
Looking ahead, the future of Big Data and Hadoop promises continued innovation and evolution. As technology advances, there is a growing emphasis on enhancing the speed, scalability, and efficiency of Big Data processing. The integration of machine learning and artificial intelligence with Hadoop is expected to further amplify the capabilities of data analytics, enabling organizations to make more informed decisions in real-time. Additionally, the emergence of edge computing and the Internet of Things (IoT) will contribute to the generation of even larger datasets, necessitating advanced tools and frameworks to extract actionable insights.
In this exploration of Big Data and Hadoop, it is essential to delve into the historical context, understand the current landscape, and anticipate the trends that will shape the future. This journey through the evolution of data processing underscores the pivotal role played by these technologies in addressing the challenges and opportunities presented by the ever-expanding realm of Big Data.
Table of contents
-
Origins of Big Data
-
Early Days of Hadoop
-
Evolution of Hadoop Ecosystem
-
Challenges Faced in the Past
-
Current Landscape of Big Data Analytics
-
Future Architectural Trends
-
Sustainability and Green Computing
-
Conclusion
Origins of Big Data
The origins of Big Data can be traced back to the late 20th century, a period marked by a significant increase in the generation and storage of digital information. As the world became more interconnected, the rise of the internet and the proliferation of electronic devices contributed to an unprecedented influx of data. The traditional methods of data processing, which had served well in an era of relatively modest data volumes, began to falter in the face of this data explosion. The sheer scale, variety, and velocity of data generated posed a formidable challenge, necessitating a paradigm shift in how information was handled.
The early 2000s witnessed the formal recognition of this burgeoning challenge as industry experts and academics began to coin the term "Big Data" to describe datasets that surpassed the capacity of traditional databases and tools. The key characteristics of Big Data, often summarized as the three Vs—Volume, Variety, and Velocity—captured the essence of the data deluge that organizations were grappling with. The need for innovative solutions to manage, process, and extract insights from these vast datasets became increasingly apparent.
The emergence of open-source technologies played a pivotal role in addressing the complexities of Big Data. One of the foundational milestones in this journey was the development of the Hadoop framework by Doug Cutting and Mike Cafarella in the early 2000s. Named after a toy elephant, Hadoop represented a breakthrough in distributed computing, offering a scalable and fault-tolerant solution for processing large datasets across clusters of commodity hardware. Inspired by Google's MapReduce and Google File System (GFS), Hadoop laid the groundwork for a new era in data processing.
Early Days of Hadoop
The early days of Hadoop mark a significant chapter in the evolution of Big Data processing, representing a response to the escalating challenges posed by the unprecedented growth in data. Hadoop's inception can be traced back to 2004 when Doug Cutting and Mike Cafarella, inspired by Google's pioneering work on distributed computing, developed an open-source framework that would later become the cornerstone of Big Data solutions. The framework was named after a toy elephant owned by Cutting's son, symbolizing robustness and strength in handling large datasets.
In its nascent stages, Hadoop comprised two primary components: the Hadoop Distributed File System (HDFS) for distributed storage and the MapReduce programming model for parallel processing. These components, modeled after Google's GFS and MapReduce, respectively, provided a scalable and fault-tolerant infrastructure capable of processing massive datasets across clusters of commodity hardware. The Hadoop project was initially part of the Apache Nutch web search engine initiative, but it soon gained recognition as an independent and groundbreaking technology.
The early adopters of Hadoop were pioneers in recognizing its potential to revolutionize data processing. Yahoo became one of the first major companies to embrace Hadoop, employing it to index and analyze vast amounts of web data. The open-source nature of Hadoop contributed to its rapid growth as a community-driven project, with developers worldwide contributing to its enhancement and expansion. The Apache Software Foundation took over the project in 2006, fostering collaborative development and ensuring its continued evolution.
Despite its transformative potential, the early days of Hadoop were not without challenges. The framework required a paradigm shift in both technology and mindset, as organizations adapted to the decentralized and parallelized nature of Big Data processing. Nevertheless, Hadoop laid the groundwork for a scalable and cost-effective solution to the challenges posed by the explosion of digital information.
Evolution of Hadoop Ecosystem
The early days of Hadoop mark a significant chapter in the evolution of Big Data processing, representing a response to the escalating challenges posed by the unprecedented growth in data. Hadoop's inception can be traced back to 2004 when Doug Cutting and Mike Cafarella, inspired by Google's pioneering work on distributed computing, developed an open-source framework that would later become the cornerstone of Big Data solutions. The framework was named after a toy elephant owned by Cutting's son, symbolizing robustness and strength in handling large datasets.
In its nascent stages, Hadoop comprised two primary components: the Hadoop Distributed File System (HDFS) for distributed storage and the MapReduce programming model for parallel processing. These components, modeled after Google's GFS and MapReduce, respectively, provided a scalable and fault-tolerant infrastructure capable of processing massive datasets across clusters of commodity hardware. The Hadoop project was initially part of the Apache Nutch web search engine initiative, but it soon gained recognition as an independent and groundbreaking technology.
The early adopters of Hadoop were pioneers in recognizing its potential to revolutionize data processing. Yahoo became one of the first major companies to embrace Hadoop, employing it to index and analyze vast amounts of web data. The open-source nature of Hadoop contributed to its rapid growth as a community-driven project, with developers worldwide contributing to its enhancement and expansion. The Apache Software Foundation took over the project in 2006, fostering collaborative development and ensuring its continued evolution.
Despite its transformative potential, the early days of Hadoop were not without challenges. The framework required a paradigm shift in both technology and mindset, as organizations adapted to the decentralized and parallelized nature of Big Data processing. Nevertheless, Hadoop laid the groundwork for a scalable and cost-effective solution to the challenges posed by the explosion of digital information.
Challenges Faced in the Past
The past witnessed a revolutionary shift in the field of data processing as the world grappled with the challenges posed by the advent of Big Data. Traditional methods of handling data, designed for smaller volumes and simpler structures, proved inadequate in the face of the rapidly expanding datasets characterized by their unprecedented volume, variety, and velocity. Organizations were confronted with the daunting task of extracting meaningful insights from these vast and complex data landscapes, leading to the recognition of the need for innovative solutions.
One of the primary challenges faced in the early days of Big Data was the sheer volume of information generated and collected. Traditional databases struggled to cope with the exponential growth in data, resulting in performance bottlenecks and increased storage costs. The variety of data, encompassing structured and unstructured formats, further compounded the challenge. Relational databases, designed for structured data, were ill-equipped to handle the diverse array of information sources, including text, images, and multimedia.
The learning curve associated with adopting new technologies like Hadoop posed yet another challenge. Organizations faced the task of upskilling their workforce to navigate the complexities of distributed computing, parallel processing, and the unique programming model of MapReduce. Integration with existing infrastructure and the establishment of best practices for implementation added further layers of complexity.
Despite these challenges, early adopters recognized the transformative potential of Big Data technologies, including Hadoop. The successes of those who navigated these obstacles and effectively implemented solutions demonstrated the feasibility and value of embracing new approaches to data processing.
Current Landscape of Big Data Analytics
The current landscape of Big Data analytics is characterized by widespread adoption and integration of advanced technologies, with organizations leveraging sophisticated tools to extract valuable insights from massive datasets. Big Data analytics has become a cornerstone of decision-making processes across diverse industries, fundamentally transforming how businesses operate. At the heart of this transformation lies the prevalence of powerful frameworks and platforms, with Hadoop prominently featured among them.
Organizations today harness the capabilities of Big Data analytics to glean actionable insights from a variety of sources, including structured and unstructured data. The integration of Hadoop into the analytics ecosystem allows for the storage and processing of vast datasets across distributed clusters, enabling a level of scalability and flexibility previously unattainable. Businesses are leveraging these capabilities to gain a deeper understanding of customer behavior, optimize operational efficiency, and identify emerging trends in their respective markets.
Real-world applications of Big Data analytics are abundant, spanning sectors such as finance, healthcare, retail, and beyond. Financial institutions utilize advanced analytics to detect fraudulent activities in real-time, while healthcare organizations leverage predictive analytics to enhance patient outcomes and optimize resource allocation. E-commerce platforms analyze user behavior to personalize recommendations, and social media companies use Big Data analytics to understand user engagement and trends.
The current landscape also witnesses a move towards the democratization of data analytics, with user-friendly tools and platforms allowing individuals with varying levels of technical expertise to engage in data-driven decision-making. Cloud computing has played a pivotal role in this democratization, providing scalable infrastructure and services that facilitate the storage, processing, and analysis of Big Data without the need for extensive on-premises resources.
Future Architectural Trends
The future of Big Data analytics is poised for continual evolution, and the architectural trends shaping its trajectory reflect a commitment to addressing the growing complexities of data processing. One prominent trend is the increasing emphasis on scalability and agility in architectural design. As data volumes continue to soar, architectures must evolve to seamlessly accommodate the expanding requirements of storage, processing, and analytics. Scalable architectures, often facilitated by cloud computing environments, empower organizations to dynamically adjust resources to meet fluctuating demands, ensuring efficiency and cost-effectiveness.
Containerization is emerging as a key architectural trend in the future of Big Data analytics. Technologies like Docker and Kubernetes provide a standardized and portable way to package applications and their dependencies, enhancing the consistency and reproducibility of data processing workflows. This trend promotes agility by facilitating the seamless deployment and scaling of applications across different environments, streamlining the development and operational aspects of Big Data architectures.
Edge computing is playing an increasingly vital role in the architectural landscape, addressing the need for real-time processing and decision-making at the source of data generation. As devices at the edge of networks become more powerful, the integration of edge computing with Big Data architectures enables organizations to process and analyze data closer to its origin. This reduces latency, enhances responsiveness, and supports applications that require immediate insights, such as IoT devices and autonomous systems.
The integration of artificial intelligence (AI) and machine learning (ML) into Big Data architectures is a transformative trend that is expected to gain momentum in the future. AI and ML algorithms enable organizations to move beyond descriptive analytics and embrace predictive and prescriptive analytics, extracting valuable insights from data patterns and facilitating data-driven decision-making. This trend contributes to the evolution of Big Data architectures into intelligent systems capable of autonomously adapting to changing data dynamics.
Sustainability and Green Computing
The increasing scale of data processing and the proliferation of Big Data technologies have brought to the forefront a pressing concern: the environmental impact of data centers and the overall sustainability of data processing practices. As the demand for data storage and computing power continues to rise, the energy consumption associated with data centers has become a significant contributor to carbon emissions. In response to this environmental challenge, the concept of "Green Computing" has gained prominence, seeking to develop more sustainable and eco-friendly approaches to data processing.
Sustainability in the context of Big Data and computing encompasses a multifaceted approach. One key aspect involves the optimization of data center operations to minimize energy consumption. Data centers, which house the servers and infrastructure supporting Big Data processing, often require substantial power for cooling and maintenance. Sustainable data center design focuses on improving energy efficiency, utilizing renewable energy sources, and implementing advanced cooling technologies to reduce the environmental footprint of these facilities.
Efforts to reduce electronic waste (e-waste) also form an integral part of sustainable computing practices. With the rapid pace of technological advancements, electronic devices become obsolete quickly, contributing to the accumulation of e-waste. Sustainable approaches involve recycling and responsible disposal of electronic equipment, as well as designing devices with longevity and recyclability in mind.
The integration of sustainability principles into Big Data and computing practices is not only an environmental imperative but also aligns with corporate social responsibility. Organizations are increasingly recognizing the importance of adopting green computing practices to mitigate environmental impact, meet regulatory requirements, and enhance their reputation as responsible global citizens.
Conclusion
In conclusion, the exploration of "Big Data and Hadoop: Past, Present, and Future Trends" reveals a transformative journey that has reshaped the landscape of data processing and analytics. The historical evolution of Big Data, marked by the challenges posed by escalating data volumes, paved the way for innovative solutions like the Hadoop framework. The early days of Hadoop were characterized by the recognition of the need for scalable and distributed computing to handle large datasets effectively.
The challenges faced in the past, ranging from volume and variety to the need for upskilling and overcoming technological barriers, served as catalysts for advancements in Big Data technologies. Hadoop emerged as a pioneering solution, addressing these challenges and laying the groundwork for a new era in data processing.
Looking to the future, architectural trends in Big Data point towards scalability, agility, and the integration of emerging technologies. Containerization, edge computing, and the infusion of artificial intelligence and machine learning are poised to redefine how organizations approach data processing. The convergence of analytics and data management, along with a commitment to sustainability and green computing practices, underscores a holistic approach to addressing the challenges and opportunities presented by Big Data.
In essence, the narrative of Big Data and Hadoop is one of continuous evolution. From its historical origins as a response to data challenges to its current status as a fundamental component of data analytics, and towards future trends that promise even greater scalability, intelligence, and sustainability, the journey reflects the dynamic nature of technology. As organizations navigate this landscape, the fusion of innovation, adaptability, and ethical considerations will be crucial in shaping a future where Big Data not only informs decision-making but does so responsibly and sustainably.
Legacy Project Management: Navigating Microsoft Project 2013 in 2023
In the dynamic landscape of project management, the legacy tools that once shaped industry practices continue to play a crucial role in guiding project teams towards success. Among these stalwarts, Microsoft Project 2013 stands out as a timeless instrument that has weathered the evolution of project management methodologies and technological advancements. As we find ourselves in the year 2023, a deep dive into the intricacies of navigating Microsoft Project 2013 reveals its enduring relevance and adaptability. This exploration is not merely a retrospective glance; instead, it serves as a testament to the enduring legacy of a tool that has withstood the test of time, continuing to empower project managers and teams across diverse sectors.
Microsoft Project 2013, initially introduced a decade ago, has been a linchpin in project planning and execution. Its robust features and comprehensive suite of tools have facilitated the management of tasks, resources, and timelines, thereby enhancing project efficiency and ensuring successful outcomes. In an era where newer project management solutions have emerged, Microsoft Project 2013's continued relevance prompts a critical examination of its features, usability, and compatibility with contemporary project management methodologies. This exploration seeks to provide insights into how this venerable project management tool can be effectively harnessed in the current project management landscape, shedding light on its nuanced functionalities and adaptability to the evolving demands of the industry.
As we embark on the journey of navigating Microsoft Project 2013 in 2023, this investigation delves into its interface, capabilities, and integration potential with modern project management methodologies. The intention is not merely to nostalgically revisit a software relic but to unveil its hidden potentials, address challenges, and offer practical insights for project managers who continue to rely on this tool. Whether you are a seasoned project management professional or a newcomer to the field, the exploration of Microsoft Project 2013 in the context of contemporary project management practices promises to be an insightful voyage through the annals of project management history, revealing the enduring legacy of a tool that has left an indelible mark on the way projects are conceived, planned, and executed.
Table of contents
-
Evolution of Project Management Tools
-
Foundations of Microsoft Project 2013
-
Legacy Software in Modern Work Environments
-
Effective Resource Management
-
Integration with Cloud and Collaboration Platforms
-
User Experience and Interface Enhancements
-
Security and Compliance Considerations
-
Conclusion
Evolution of Project Management Tools
The evolution of project management tools represents a dynamic journey that parallels the advancement of technology and the changing needs of project teams. In the early days of project management, pen-and-paper methods and rudimentary scheduling techniques dominated the landscape. However, as projects grew in complexity and scale, a demand emerged for more sophisticated tools to streamline processes and enhance efficiency. This marked the onset of a paradigm shift, leading to the development of digital project management tools.
The introduction of computer-based project management software in the late 20th century marked a transformative moment in the field. Microsoft Project, first released in 1984, played a pivotal role in this evolution by providing a platform that allowed project managers to plan, schedule, and track tasks in a more structured and efficient manner. Over the subsequent decades, the landscape continued to evolve, with the integration of features such as resource management, Gantt charts, and critical path analysis, all of which became integral components of project management methodologies.
The evolution of project management tools continues, with an emphasis on agility, collaboration, and integration with other business systems. The rise of Agile methodologies and hybrid project management approaches has spurred the development of tools that can adapt to changing project dynamics and foster collaboration among cross-functional teams. Despite the influx of newer solutions, the enduring legacy of foundational tools like Microsoft Project 2013 persists, reminding us of the rich history that underlies the project management tools we use today. In navigating the landscape of project management tools in 2023, understanding this evolution provides valuable insights into the strengths and adaptability of these tools in the face of ongoing industry changes.
Foundations of Microsoft Project 2013
The foundations of Microsoft Project 2013 are rooted in a commitment to providing project managers with a comprehensive and intuitive tool for planning, scheduling, and managing projects. Launched as part of the Microsoft Office suite, Project 2013 was designed to facilitate the organization and execution of projects of varying sizes and complexities. At its core, the software embodies the principles of project management by offering a structured framework for defining tasks, allocating resources, and establishing timelines.
One of the key pillars of Microsoft Project 2013 lies in its capability to create Gantt charts, a visual representation that allows project managers to visualize project timelines, dependencies, and critical paths. This feature became fundamental in project planning, enabling teams to understand the sequence of tasks and the overall project schedule. The Gantt chart functionality in Project 2013 has become a hallmark feature, providing project managers with a powerful tool for effective project communication and coordination.
The software's integration with other Microsoft Office applications, such as Excel and SharePoint, further strengthens its foundation. This integration allows for seamless data exchange, fostering collaboration and data consistency across different platforms. The familiar interface and interoperability with widely-used business applications make Microsoft Project 2013 accessible and user-friendly, minimizing the learning curve for project managers and team members.
The foundations of Microsoft Project 2013 rest on its commitment to simplicity, visual clarity, resource efficiency, and adaptability. These core principles continue to resonate in the tool's enduring legacy, providing project managers with a reliable and powerful ally in navigating the complexities of project management in 2023 and beyond.
Legacy Software in Modern Work Environments
The presence of legacy software, such as Microsoft Project 2013, in modern work environments reflects a nuanced intersection of historical continuity and the ever-evolving nature of technology. Legacy software, often defined as older systems that remain in use, holds a unique place in contemporary workplaces, serving as a testament to the enduring reliability and functionality of certain tools. In the context of modern work environments characterized by rapid technological advancements, the continued use of legacy software introduces a layer of complexity and challenges that organizations must navigate.
One of the primary considerations when dealing with legacy software in the present day is its compatibility with modern hardware, operating systems, and security standards. As technology advances, the risk of obsolescence becomes a concern, and organizations using legacy software like Microsoft Project 2013 must address potential issues related to system updates, security patches, and hardware upgrades. Balancing the benefits of familiarity and established workflows with the necessity for contemporary security measures is a delicate task faced by many organizations relying on legacy tools.
The coexistence of legacy software like Microsoft Project 2013 in modern work environments underscores the pragmatic approach that organizations adopt when balancing tradition with innovation. While challenges persist, the strategic integration of legacy tools within the broader framework of modern technology showcases a commitment to efficiency, adaptability, and a recognition of the enduring value that these legacy systems bring to the table. As organizations navigate the complexities of modern work environments, the role of legacy software remains a dynamic and integral part of their technological landscape.
Effective Resource Management
Effective resource management is a cornerstone of successful project execution, and Microsoft Project 2013 provides a robust platform for optimizing the allocation and utilization of resources. At the heart of this capability lies the tool's capacity to offer project managers a comprehensive view of the human, material, and financial resources associated with a project.
Microsoft Project 2013 allows project managers to define and categorize resources, ranging from individual team members to physical assets and budgetary allocations. Through this categorization, the tool enables a granular understanding of the resource landscape, facilitating precise resource allocation based on project requirements and constraints.
Resource leveling, another essential aspect of effective resource management, is facilitated by Microsoft Project 2013. This feature enables project managers to balance workloads across team members and ensure that resources are neither underutilized nor overstretched. By optimizing resource distribution, project managers can enhance project efficiency, reduce the risk of burnout, and maintain a realistic project timeline.
Effective resource management with Microsoft Project 2013 involves the strategic allocation of resources, workload balancing, and real-time tracking of costs and progress. The tool's comprehensive features empower project managers to optimize resource utilization, mitigate risks, and ultimately contribute to the successful delivery of projects in diverse and dynamic work environments.
Integration with Cloud and Collaboration Platforms
Microsoft Project 2013, while originating in an era predating the widespread adoption of cloud computing, exhibits a notable integration with cloud and collaboration platforms, showcasing its adaptability to modern workplace trends. The tool, designed to facilitate project management activities, has evolved to seamlessly incorporate cloud-based functionalities and collaborative features.
The integration of Microsoft Project 2013 with cloud platforms represents a pivotal shift toward enhancing accessibility and fostering real-time collaboration. By leveraging cloud storage solutions, such as Microsoft's OneDrive or SharePoint, project teams can access project data and documents from any location with internet connectivity. This not only promotes flexibility in remote work scenarios but also ensures that project information remains centralized and up-to-date across the entire team.
The compatibility of Microsoft Project 2013 with collaboration platforms extends beyond Microsoft's ecosystem. The tool can often integrate with third-party cloud-based project management and collaboration tools, providing organizations with the flexibility to choose platforms that align with their specific needs and workflows. This interoperability supports a diverse range of project teams and allows for seamless communication and data exchange with stakeholders who may use different collaboration tools.
The integration of Microsoft Project 2013 with cloud and collaboration platforms reflects a strategic response to the evolving needs of modern work environments. By embracing cloud-based storage, real-time collaboration, and compatibility with diverse platforms, the tool demonstrates its commitment to facilitating efficient and collaborative project management practices in the dynamic landscape of 2023 and beyond.
User Experience and Interface Enhancements
User experience (UX) and interface enhancements in Microsoft Project 2013 underscore the commitment to providing project managers and teams with an intuitive and efficient platform for project planning and execution. Recognizing the pivotal role that user-friendliness plays in software adoption, Microsoft invested in refining the interface to create a more streamlined and visually intuitive experience for users. The redesigned interface of Project 2013 reflects a departure from its predecessors, featuring a cleaner and more organized layout that enhances overall usability.
One notable enhancement in the user experience is the ribbon interface, a hallmark of Microsoft Office applications. This interface consolidates key features and commands into a tabbed toolbar, offering a more structured and accessible approach to accessing functionalities. The ribbon's contextual organization aligns with common project management tasks, reducing the learning curve for new users and allowing experienced project managers to navigate tasks efficiently.
The user experience is further refined through the introduction of touch-friendly controls, recognizing the evolving landscape of device usage. With the prevalence of touch-enabled devices, Microsoft Project 2013 adapts its interface to provide a tactile experience, making it more accessible for users working on tablets or other touch-enabled devices. This accommodation of touch controls aligns with the modernization of work practices and the increasing diversity of devices used in project management.
The user experience and interface enhancements in Microsoft Project 2013 signify a deliberate effort to prioritize usability and efficiency. By integrating the ribbon interface, optimizing data visualizations, accommodating touch controls, and offering customization options, the tool not only keeps pace with contemporary UX trends but also positions itself as a user-friendly solution in the evolving landscape of project management software.
Security and Compliance Considerations
Security and compliance considerations are paramount in the deployment and use of project management tools like Microsoft Project 2013, especially in an era where data breaches and regulatory requirements are significant concerns for organizations. Microsoft Project 2013 recognizes the critical importance of safeguarding project data and adhering to industry standards, embedding security features and compliance measures to mitigate risks and ensure the protection of sensitive information.
One of the foundational elements addressing security in Microsoft Project 2013 is access control. The tool incorporates robust authentication mechanisms, allowing organizations to manage user access through secure login credentials. This ensures that only authorized individuals have the appropriate level of access to project data, mitigating the risk of unauthorized modifications or data breaches.
Compliance with industry regulations and data protection laws is another crucial facet addressed by Microsoft Project 2013. Depending on the industry and geographical location, organizations must adhere to various compliance standards such as GDPR, HIPAA, or others. Microsoft, as a provider, often undergoes certifications and audits to ensure that its tools, including Project 2013, align with these regulatory requirements. This commitment to compliance gives organizations confidence in using the tool while meeting their legal obligations.
Microsoft Project 2013 prioritizes security and compliance considerations to provide organizations with a reliable and secure platform for project management. By implementing robust access controls, encryption measures, and compliance features, the tool seeks to address the evolving challenges of information security in the dynamic landscape of project management. Organizations deploying Microsoft Project 2013 can leverage these built-in security measures to protect their sensitive project data and adhere to regulatory requirements.
How to obtain MICROSOFT PROJECT 2013 CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Read More
In the dynamic landscape of project management, the legacy tools that once shaped industry practices continue to play a crucial role in guiding project teams towards success. Among these stalwarts, Microsoft Project 2013 stands out as a timeless instrument that has weathered the evolution of project management methodologies and technological advancements. As we find ourselves in the year 2023, a deep dive into the intricacies of navigating Microsoft Project 2013 reveals its enduring relevance and adaptability. This exploration is not merely a retrospective glance; instead, it serves as a testament to the enduring legacy of a tool that has withstood the test of time, continuing to empower project managers and teams across diverse sectors.
Microsoft Project 2013, initially introduced a decade ago, has been a linchpin in project planning and execution. Its robust features and comprehensive suite of tools have facilitated the management of tasks, resources, and timelines, thereby enhancing project efficiency and ensuring successful outcomes. In an era where newer project management solutions have emerged, Microsoft Project 2013's continued relevance prompts a critical examination of its features, usability, and compatibility with contemporary project management methodologies. This exploration seeks to provide insights into how this venerable project management tool can be effectively harnessed in the current project management landscape, shedding light on its nuanced functionalities and adaptability to the evolving demands of the industry.
As we embark on the journey of navigating Microsoft Project 2013 in 2023, this investigation delves into its interface, capabilities, and integration potential with modern project management methodologies. The intention is not merely to nostalgically revisit a software relic but to unveil its hidden potentials, address challenges, and offer practical insights for project managers who continue to rely on this tool. Whether you are a seasoned project management professional or a newcomer to the field, the exploration of Microsoft Project 2013 in the context of contemporary project management practices promises to be an insightful voyage through the annals of project management history, revealing the enduring legacy of a tool that has left an indelible mark on the way projects are conceived, planned, and executed.
Table of contents
-
Evolution of Project Management Tools
-
Foundations of Microsoft Project 2013
-
Legacy Software in Modern Work Environments
-
Effective Resource Management
-
Integration with Cloud and Collaboration Platforms
-
User Experience and Interface Enhancements
-
Security and Compliance Considerations
-
Conclusion
Evolution of Project Management Tools
The evolution of project management tools represents a dynamic journey that parallels the advancement of technology and the changing needs of project teams. In the early days of project management, pen-and-paper methods and rudimentary scheduling techniques dominated the landscape. However, as projects grew in complexity and scale, a demand emerged for more sophisticated tools to streamline processes and enhance efficiency. This marked the onset of a paradigm shift, leading to the development of digital project management tools.
The introduction of computer-based project management software in the late 20th century marked a transformative moment in the field. Microsoft Project, first released in 1984, played a pivotal role in this evolution by providing a platform that allowed project managers to plan, schedule, and track tasks in a more structured and efficient manner. Over the subsequent decades, the landscape continued to evolve, with the integration of features such as resource management, Gantt charts, and critical path analysis, all of which became integral components of project management methodologies.
The evolution of project management tools continues, with an emphasis on agility, collaboration, and integration with other business systems. The rise of Agile methodologies and hybrid project management approaches has spurred the development of tools that can adapt to changing project dynamics and foster collaboration among cross-functional teams. Despite the influx of newer solutions, the enduring legacy of foundational tools like Microsoft Project 2013 persists, reminding us of the rich history that underlies the project management tools we use today. In navigating the landscape of project management tools in 2023, understanding this evolution provides valuable insights into the strengths and adaptability of these tools in the face of ongoing industry changes.
Foundations of Microsoft Project 2013
The foundations of Microsoft Project 2013 are rooted in a commitment to providing project managers with a comprehensive and intuitive tool for planning, scheduling, and managing projects. Launched as part of the Microsoft Office suite, Project 2013 was designed to facilitate the organization and execution of projects of varying sizes and complexities. At its core, the software embodies the principles of project management by offering a structured framework for defining tasks, allocating resources, and establishing timelines.
One of the key pillars of Microsoft Project 2013 lies in its capability to create Gantt charts, a visual representation that allows project managers to visualize project timelines, dependencies, and critical paths. This feature became fundamental in project planning, enabling teams to understand the sequence of tasks and the overall project schedule. The Gantt chart functionality in Project 2013 has become a hallmark feature, providing project managers with a powerful tool for effective project communication and coordination.
The software's integration with other Microsoft Office applications, such as Excel and SharePoint, further strengthens its foundation. This integration allows for seamless data exchange, fostering collaboration and data consistency across different platforms. The familiar interface and interoperability with widely-used business applications make Microsoft Project 2013 accessible and user-friendly, minimizing the learning curve for project managers and team members.
The foundations of Microsoft Project 2013 rest on its commitment to simplicity, visual clarity, resource efficiency, and adaptability. These core principles continue to resonate in the tool's enduring legacy, providing project managers with a reliable and powerful ally in navigating the complexities of project management in 2023 and beyond.
Legacy Software in Modern Work Environments
The presence of legacy software, such as Microsoft Project 2013, in modern work environments reflects a nuanced intersection of historical continuity and the ever-evolving nature of technology. Legacy software, often defined as older systems that remain in use, holds a unique place in contemporary workplaces, serving as a testament to the enduring reliability and functionality of certain tools. In the context of modern work environments characterized by rapid technological advancements, the continued use of legacy software introduces a layer of complexity and challenges that organizations must navigate.
One of the primary considerations when dealing with legacy software in the present day is its compatibility with modern hardware, operating systems, and security standards. As technology advances, the risk of obsolescence becomes a concern, and organizations using legacy software like Microsoft Project 2013 must address potential issues related to system updates, security patches, and hardware upgrades. Balancing the benefits of familiarity and established workflows with the necessity for contemporary security measures is a delicate task faced by many organizations relying on legacy tools.
The coexistence of legacy software like Microsoft Project 2013 in modern work environments underscores the pragmatic approach that organizations adopt when balancing tradition with innovation. While challenges persist, the strategic integration of legacy tools within the broader framework of modern technology showcases a commitment to efficiency, adaptability, and a recognition of the enduring value that these legacy systems bring to the table. As organizations navigate the complexities of modern work environments, the role of legacy software remains a dynamic and integral part of their technological landscape.
Effective Resource Management
Effective resource management is a cornerstone of successful project execution, and Microsoft Project 2013 provides a robust platform for optimizing the allocation and utilization of resources. At the heart of this capability lies the tool's capacity to offer project managers a comprehensive view of the human, material, and financial resources associated with a project.
Microsoft Project 2013 allows project managers to define and categorize resources, ranging from individual team members to physical assets and budgetary allocations. Through this categorization, the tool enables a granular understanding of the resource landscape, facilitating precise resource allocation based on project requirements and constraints.
Resource leveling, another essential aspect of effective resource management, is facilitated by Microsoft Project 2013. This feature enables project managers to balance workloads across team members and ensure that resources are neither underutilized nor overstretched. By optimizing resource distribution, project managers can enhance project efficiency, reduce the risk of burnout, and maintain a realistic project timeline.
Effective resource management with Microsoft Project 2013 involves the strategic allocation of resources, workload balancing, and real-time tracking of costs and progress. The tool's comprehensive features empower project managers to optimize resource utilization, mitigate risks, and ultimately contribute to the successful delivery of projects in diverse and dynamic work environments.
Integration with Cloud and Collaboration Platforms
Microsoft Project 2013, while originating in an era predating the widespread adoption of cloud computing, exhibits a notable integration with cloud and collaboration platforms, showcasing its adaptability to modern workplace trends. The tool, designed to facilitate project management activities, has evolved to seamlessly incorporate cloud-based functionalities and collaborative features.
The integration of Microsoft Project 2013 with cloud platforms represents a pivotal shift toward enhancing accessibility and fostering real-time collaboration. By leveraging cloud storage solutions, such as Microsoft's OneDrive or SharePoint, project teams can access project data and documents from any location with internet connectivity. This not only promotes flexibility in remote work scenarios but also ensures that project information remains centralized and up-to-date across the entire team.
The compatibility of Microsoft Project 2013 with collaboration platforms extends beyond Microsoft's ecosystem. The tool can often integrate with third-party cloud-based project management and collaboration tools, providing organizations with the flexibility to choose platforms that align with their specific needs and workflows. This interoperability supports a diverse range of project teams and allows for seamless communication and data exchange with stakeholders who may use different collaboration tools.
The integration of Microsoft Project 2013 with cloud and collaboration platforms reflects a strategic response to the evolving needs of modern work environments. By embracing cloud-based storage, real-time collaboration, and compatibility with diverse platforms, the tool demonstrates its commitment to facilitating efficient and collaborative project management practices in the dynamic landscape of 2023 and beyond.
User Experience and Interface Enhancements
User experience (UX) and interface enhancements in Microsoft Project 2013 underscore the commitment to providing project managers and teams with an intuitive and efficient platform for project planning and execution. Recognizing the pivotal role that user-friendliness plays in software adoption, Microsoft invested in refining the interface to create a more streamlined and visually intuitive experience for users. The redesigned interface of Project 2013 reflects a departure from its predecessors, featuring a cleaner and more organized layout that enhances overall usability.
One notable enhancement in the user experience is the ribbon interface, a hallmark of Microsoft Office applications. This interface consolidates key features and commands into a tabbed toolbar, offering a more structured and accessible approach to accessing functionalities. The ribbon's contextual organization aligns with common project management tasks, reducing the learning curve for new users and allowing experienced project managers to navigate tasks efficiently.
The user experience is further refined through the introduction of touch-friendly controls, recognizing the evolving landscape of device usage. With the prevalence of touch-enabled devices, Microsoft Project 2013 adapts its interface to provide a tactile experience, making it more accessible for users working on tablets or other touch-enabled devices. This accommodation of touch controls aligns with the modernization of work practices and the increasing diversity of devices used in project management.
The user experience and interface enhancements in Microsoft Project 2013 signify a deliberate effort to prioritize usability and efficiency. By integrating the ribbon interface, optimizing data visualizations, accommodating touch controls, and offering customization options, the tool not only keeps pace with contemporary UX trends but also positions itself as a user-friendly solution in the evolving landscape of project management software.
Security and Compliance Considerations
Security and compliance considerations are paramount in the deployment and use of project management tools like Microsoft Project 2013, especially in an era where data breaches and regulatory requirements are significant concerns for organizations. Microsoft Project 2013 recognizes the critical importance of safeguarding project data and adhering to industry standards, embedding security features and compliance measures to mitigate risks and ensure the protection of sensitive information.
One of the foundational elements addressing security in Microsoft Project 2013 is access control. The tool incorporates robust authentication mechanisms, allowing organizations to manage user access through secure login credentials. This ensures that only authorized individuals have the appropriate level of access to project data, mitigating the risk of unauthorized modifications or data breaches.
Compliance with industry regulations and data protection laws is another crucial facet addressed by Microsoft Project 2013. Depending on the industry and geographical location, organizations must adhere to various compliance standards such as GDPR, HIPAA, or others. Microsoft, as a provider, often undergoes certifications and audits to ensure that its tools, including Project 2013, align with these regulatory requirements. This commitment to compliance gives organizations confidence in using the tool while meeting their legal obligations.
Microsoft Project 2013 prioritizes security and compliance considerations to provide organizations with a reliable and secure platform for project management. By implementing robust access controls, encryption measures, and compliance features, the tool seeks to address the evolving challenges of information security in the dynamic landscape of project management. Organizations deploying Microsoft Project 2013 can leverage these built-in security measures to protect their sensitive project data and adhere to regulatory requirements.
How to obtain MICROSOFT PROJECT 2013 CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
Machine Learning Integration with MongoDB: Certification Implications
In the rapidly evolving landscape of technology, the integration of Machine Learning (ML) with databases has emerged as a transformative force, unlocking new possibilities for data-driven decision-making and automation. One such pivotal integration lies in the fusion of Machine Learning with MongoDB, a leading NoSQL database platform known for its flexibility and scalability. This convergence not only addresses the challenges of handling vast and complex datasets but also opens avenues for harnessing the power of predictive analytics and pattern recognition.
Machine Learning Integration with MongoDB holds significant implications for professionals seeking to validate their expertise and stay abreast of cutting-edge developments in the field. As organizations increasingly recognize the value of data-driven insights, the demand for skilled individuals capable of seamlessly integrating ML algorithms with databases like MongoDB is on the rise. This burgeoning need has led to the establishment of certification programs that serve as a testament to an individual's proficiency in both machine learning principles and the intricacies of MongoDB implementation.
Certification in Machine Learning Integration with MongoDB signifies a comprehensive understanding of the symbiotic relationship between these two domains. It not only demonstrates mastery over ML algorithms but also validates the ability to leverage MongoDB's document-oriented structure for efficient data storage and retrieval. This certification becomes a badge of competence for professionals aspiring to play pivotal roles in data engineering, business intelligence, and application development, where the amalgamation of ML and MongoDB can propel innovation and drive strategic decision-making.
Table of contents
-
Overview of Machine Learning Integration with MongoDB
-
Certification Importance in the Data Science Landscape
-
Designing ML Models for MongoDB Compatibility
-
Hands-On Practical Exercises in ML-MongoDB Integration
-
Addressing Ethical Considerations in ML-MongoDB Integration
-
Certification Versatility and Career Opportunities
-
Continuous Learning and Upkeep of Certification
-
Conclusion
Overview of Machine Learning Integration with MongoDB
The integration of Machine Learning (ML) with MongoDB represents a pivotal advancement in the realm of data science and database management. At its core, this integration aims to synergize the power of predictive analytics and pattern recognition facilitated by ML with the flexible and scalable architecture of MongoDB, a prominent NoSQL database platform. Unlike traditional relational databases, MongoDB's document-oriented structure proves to be highly compatible with the diverse and unstructured nature of data commonly encountered in ML applications.
MongoDB's versatility in handling large volumes of data and its capacity to scale horizontally make it an ideal companion for ML tasks that often involve processing and analyzing massive datasets. The document-based storage model, where data is stored in BSON (Binary JSON) format, aligns well with the flexible schema requirements of machine learning applications, allowing for seamless adaptation to evolving data structures.
The overview of Machine Learning Integration with MongoDB underscores the symbiotic relationship between two powerful technological domains. It sets the stage for exploring the potential applications, challenges, and transformative implications of combining machine learning capabilities with the robust features of MongoDB, ushering in a new era of data-centric innovation and insight generation.
Certification Importance in the Data Science Landscape
Certifications play a crucial role in the dynamic and rapidly evolving landscape of data science, where the amalgamation of technical skills and domain knowledge is imperative for professional success. In this context, certifications specific to Machine Learning Integration with MongoDB hold particular significance. As organizations increasingly recognize the strategic importance of data-driven decision-making, the need for qualified and proficient individuals capable of navigating the complexities of both machine learning and advanced database management is more pronounced than ever.
Certifications in the field of data science serve as tangible proof of an individual's expertise and competence. They validate not only theoretical knowledge but also practical skills, ensuring that professionals are equipped to handle the intricacies of real-world scenarios. In the context of Machine Learning Integration with MongoDB, certification becomes a testament to an individual's ability to harness the synergies between these two domains, demonstrating proficiency in implementing machine learning models within the MongoDB ecosystem.
The importance of certifications in the data science landscape, particularly in the context of Machine Learning Integration with MongoDB, cannot be overstated. They not only serve as a validation of expertise but also provide professionals with a competitive edge, opening doors to exciting career opportunities in a field that continues to shape the future of technology and decision-making.
Designing ML Models for MongoDB Compatibility
Designing machine learning (ML) models for seamless compatibility with MongoDB involves a thoughtful and strategic approach that considers both the nuances of ML algorithms and the document-oriented nature of MongoDB. The fundamental principles revolve around optimizing the structure of the ML model to align with MongoDB's storage and retrieval capabilities, enhancing overall performance and efficiency.
One key consideration is the representation of data within the ML model. Given MongoDB's BSON format, which is a binary representation of JSON-like documents, designing models with features that naturally map to this structure is essential. This may involve transforming data into a format that aligns with MongoDB's document-based storage, ensuring that the model's output can be easily integrated into the database.
Another crucial aspect is the scalability of ML models, particularly when dealing with large datasets. MongoDB's horizontal scalability allows for the distribution of data across multiple servers, and ML models should be designed to handle parallel processing efficiently. This involves optimizing algorithms and workflows to exploit the parallelization capabilities of MongoDB, ensuring that the integration remains performant as the dataset grows.
Ultimately, designing ML models for MongoDB compatibility necessitates a holistic understanding of both the intricacies of ML algorithms and the unique features of MongoDB. It involves an iterative process of refinement, testing, and optimization to achieve a harmonious integration that maximizes the strengths of both technologies. The goal is to create a symbiotic relationship where ML models leverage MongoDB's scalability and flexibility, resulting in a powerful combination for handling and deriving insights from diverse and voluminous datasets.
Hands-On Practical Exercises in ML-MongoDB Integration
Hands-on practical exercises are essential for mastering the intricacies of integrating Machine Learning (ML) with MongoDB, providing practitioners with a tangible understanding of the integration process. To embark on this journey, the initial exercise involves setting up a MongoDB environment. This includes the installation and configuration of MongoDB on a local machine or a cloud-based platform, offering an introduction to fundamental database commands for data manipulation and retrieval.
A critical aspect of ML-MongoDB integration involves data preprocessing within MongoDB using its aggregation framework. Practitioners can engage in exercises where they filter, transform, and clean data directly within the database, optimizing the information for integration with ML models.
Optimizing for performance, practitioners can experiment with indexing strategies within MongoDB. This exercise sheds light on the impact of indexing on query efficiency, offering insights into how to fine-tune the retrieval of data for ML tasks.
Security implementation exercises address the crucial aspect of safeguarding both the MongoDB database and the integrated ML models. Practitioners gain hands-on experience in implementing access controls, encryption measures, and other security protocols to protect sensitive data.
Model deployment and monitoring exercises simulate real-world scenarios by deploying ML models integrated with MongoDB into a production-like environment. This holistic exercise includes monitoring the performance of deployed models and understanding the considerations for maintaining and updating models over time.
Addressing Ethical Considerations in ML-MongoDB Integration
Addressing ethical considerations in the integration of Machine Learning (ML) with MongoDB is paramount in the era of data-driven technologies. As organizations leverage the power of ML to extract insights from vast datasets stored in MongoDB, ethical concerns arise around issues such as data privacy, transparency, and potential biases embedded in algorithms. An essential first step in addressing these considerations is recognizing the responsibility of practitioners to ensure that the integration aligns with ethical standards and safeguards the rights and privacy of individuals whose data is involved.
One critical ethical consideration is data privacy, as MongoDB may store sensitive information that can be utilized by ML models. Practitioners must implement robust security measures, including encryption and access controls, to protect against unauthorized access and potential breaches. Additionally, transparent communication with users about data collection and utilization becomes imperative, fostering trust and compliance with privacy regulations.
Transparency and interpretability are key ethical principles in ML-MongoDB integration. Practitioners should strive to make ML models and the integration process understandable to stakeholders, promoting accountability and trust. Providing clear documentation on data sources, preprocessing steps, and model decisions contributes to transparency and enables users to comprehend and question the decisions made by the system.
Addressing ethical considerations in ML-MongoDB integration is a multifaceted task that demands a proactive and ongoing commitment to ethical practices. As the technological landscape evolves, practitioners must prioritize transparency, fairness, and privacy to ensure that ML models integrated with MongoDB align with ethical standards, contribute positively to society, and foster trust among users and stakeholders. By upholding these ethical principles, organizations can harness the benefits of ML-MongoDB integration while minimizing the potential risks and ethical pitfalls.
Certification Versatility and Career Opportunities
Certification in Machine Learning Integration with MongoDB opens up a realm of versatility and diverse career opportunities for professionals seeking to carve a niche in the dynamic intersection of data science and database management. The versatility of this certification lies in its ability to equip individuals with a comprehensive skill set, blending the proficiency in machine learning principles with the intricacies of MongoDB implementation. This unique combination positions certified professionals as valuable assets capable of addressing the evolving needs of organizations grappling with complex data challenges.
The certification's versatility is reflected in its applicability across various industries, where the integration of machine learning with MongoDB is becoming increasingly integral to decision-making processes. From healthcare and finance to e-commerce and beyond, certified individuals can leverage their expertise to drive innovation, optimize business operations, and extract meaningful insights from diverse datasets. The adaptability of this certification across sectors ensures that professionals possess skills that remain relevant and in-demand across a spectrum of industries.
In a competitive job market, certification in Machine Learning Integration with MongoDB becomes a valuable asset, enhancing a professional's marketability and employability. It not only demonstrates technical prowess but also underscores a commitment to staying abreast of cutting-edge developments in data science and database management. As organizations increasingly seek individuals with a diverse skill set, the certification opens doors to career advancements and positions certified professionals as leaders in the rapidly evolving landscape of technology.
The versatility and career opportunities associated with certification in Machine Learning Integration with MongoDB position it as a strategic investment for professionals aspiring to thrive in the data-driven era. Beyond imparting technical proficiency, the certification serves as a gateway to a myriad of career paths, where certified individuals can make impactful contributions and shape the future of data science and database management.
Continuous Learning and Upkeep of Certification
Continuous learning and the upkeep of certification in Machine Learning Integration with MongoDB are essential components for professionals aiming to stay at the forefront of the rapidly evolving landscape of data science and database management. In this dynamic field, where technologies and methodologies are in a perpetual state of evolution, the commitment to ongoing learning is paramount. Certified individuals recognize that the journey towards mastery is continuous and extends beyond the initial acquisition of skills.
The field of Machine Learning Integration with MongoDB is marked by constant innovation and emerging best practices. Therefore, professionals holding certifications must engage in continuous learning to stay updated with the latest developments, industry trends, and advancements in both machine learning and MongoDB. This commitment to ongoing education ensures that certified individuals remain well-informed about new tools, frameworks, and methodologies that may enhance their efficiency and efficacy in integrating ML with MongoDB.
Continuous learning and the upkeep of certification are inseparable components of a successful career in Machine Learning Integration with MongoDB. Embracing a mindset of lifelong learning ensures that certified professionals are well-equipped to navigate the complexities of the field, adapt to technological advancements, and contribute meaningfully to the ongoing transformation of data science and database management. By staying curious, connected, and committed to growth, individuals with certifications in ML-MongoDB integration position themselves as agile and resilient professionals in the ever-evolving landscape of technology.
How to obtain MONGODB DEVELOPER AND ADMINISTRATOR CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Machine Learning with MongoDB presents a compelling synergy that has transformative implications across diverse industries. The certification in Machine Learning Integration with MongoDB emerges as a key enabler for professionals seeking to navigate this dynamic intersection of data science and database management. As highlighted in the exploration of foundational concepts, practical exercises, and ethical considerations, this certification equips individuals with the knowledge and skills necessary to harness the full potential of both technologies.
The certification's importance in the data science landscape is underscored by the increasing demand for adept professionals capable of seamlessly integrating machine learning algorithms with MongoDB's flexible and scalable architecture. This recognition positions certified individuals as valuable assets in the data-driven era, where organizations prioritize actionable insights and strategic decision-making.
Addressing ethical considerations in ML-MongoDB integration is a critical aspect of the certification, emphasizing the responsibility of practitioners to uphold privacy, transparency, and fairness. By integrating ethical practices into the certification process, professionals ensure that their contributions align with societal expectations and contribute positively to the evolving landscape of technology.
The journey doesn't end with certification; instead, it is a stepping stone to a commitment to continuous learning. In the ever-evolving field of ML-MongoDB integration, staying informed, engaging in collaborative forums, and upkeeping the certification through ongoing education are crucial for maintaining relevance and competence. This dedication to continuous learning positions certified professionals as adaptable leaders in the face of evolving challenges and opportunities.
In essence, the Machine Learning Integration with MongoDB certification encapsulates not only technical proficiency but also a commitment to ethical practices, continuous learning, and a versatile skill set. As professionals embark on this certification journey, they position themselves at the forefront of innovation, ready to make impactful contributions to the transformative intersection of machine learning and MongoDB.
Read More
In the rapidly evolving landscape of technology, the integration of Machine Learning (ML) with databases has emerged as a transformative force, unlocking new possibilities for data-driven decision-making and automation. One such pivotal integration lies in the fusion of Machine Learning with MongoDB, a leading NoSQL database platform known for its flexibility and scalability. This convergence not only addresses the challenges of handling vast and complex datasets but also opens avenues for harnessing the power of predictive analytics and pattern recognition.
Machine Learning Integration with MongoDB holds significant implications for professionals seeking to validate their expertise and stay abreast of cutting-edge developments in the field. As organizations increasingly recognize the value of data-driven insights, the demand for skilled individuals capable of seamlessly integrating ML algorithms with databases like MongoDB is on the rise. This burgeoning need has led to the establishment of certification programs that serve as a testament to an individual's proficiency in both machine learning principles and the intricacies of MongoDB implementation.
Certification in Machine Learning Integration with MongoDB signifies a comprehensive understanding of the symbiotic relationship between these two domains. It not only demonstrates mastery over ML algorithms but also validates the ability to leverage MongoDB's document-oriented structure for efficient data storage and retrieval. This certification becomes a badge of competence for professionals aspiring to play pivotal roles in data engineering, business intelligence, and application development, where the amalgamation of ML and MongoDB can propel innovation and drive strategic decision-making.
Table of contents
-
Overview of Machine Learning Integration with MongoDB
-
Certification Importance in the Data Science Landscape
-
Designing ML Models for MongoDB Compatibility
-
Hands-On Practical Exercises in ML-MongoDB Integration
-
Addressing Ethical Considerations in ML-MongoDB Integration
-
Certification Versatility and Career Opportunities
-
Continuous Learning and Upkeep of Certification
-
Conclusion
Overview of Machine Learning Integration with MongoDB
The integration of Machine Learning (ML) with MongoDB represents a pivotal advancement in the realm of data science and database management. At its core, this integration aims to synergize the power of predictive analytics and pattern recognition facilitated by ML with the flexible and scalable architecture of MongoDB, a prominent NoSQL database platform. Unlike traditional relational databases, MongoDB's document-oriented structure proves to be highly compatible with the diverse and unstructured nature of data commonly encountered in ML applications.
MongoDB's versatility in handling large volumes of data and its capacity to scale horizontally make it an ideal companion for ML tasks that often involve processing and analyzing massive datasets. The document-based storage model, where data is stored in BSON (Binary JSON) format, aligns well with the flexible schema requirements of machine learning applications, allowing for seamless adaptation to evolving data structures.
The overview of Machine Learning Integration with MongoDB underscores the symbiotic relationship between two powerful technological domains. It sets the stage for exploring the potential applications, challenges, and transformative implications of combining machine learning capabilities with the robust features of MongoDB, ushering in a new era of data-centric innovation and insight generation.
Certification Importance in the Data Science Landscape
Certifications play a crucial role in the dynamic and rapidly evolving landscape of data science, where the amalgamation of technical skills and domain knowledge is imperative for professional success. In this context, certifications specific to Machine Learning Integration with MongoDB hold particular significance. As organizations increasingly recognize the strategic importance of data-driven decision-making, the need for qualified and proficient individuals capable of navigating the complexities of both machine learning and advanced database management is more pronounced than ever.
Certifications in the field of data science serve as tangible proof of an individual's expertise and competence. They validate not only theoretical knowledge but also practical skills, ensuring that professionals are equipped to handle the intricacies of real-world scenarios. In the context of Machine Learning Integration with MongoDB, certification becomes a testament to an individual's ability to harness the synergies between these two domains, demonstrating proficiency in implementing machine learning models within the MongoDB ecosystem.
The importance of certifications in the data science landscape, particularly in the context of Machine Learning Integration with MongoDB, cannot be overstated. They not only serve as a validation of expertise but also provide professionals with a competitive edge, opening doors to exciting career opportunities in a field that continues to shape the future of technology and decision-making.
Designing ML Models for MongoDB Compatibility
Designing machine learning (ML) models for seamless compatibility with MongoDB involves a thoughtful and strategic approach that considers both the nuances of ML algorithms and the document-oriented nature of MongoDB. The fundamental principles revolve around optimizing the structure of the ML model to align with MongoDB's storage and retrieval capabilities, enhancing overall performance and efficiency.
One key consideration is the representation of data within the ML model. Given MongoDB's BSON format, which is a binary representation of JSON-like documents, designing models with features that naturally map to this structure is essential. This may involve transforming data into a format that aligns with MongoDB's document-based storage, ensuring that the model's output can be easily integrated into the database.
Another crucial aspect is the scalability of ML models, particularly when dealing with large datasets. MongoDB's horizontal scalability allows for the distribution of data across multiple servers, and ML models should be designed to handle parallel processing efficiently. This involves optimizing algorithms and workflows to exploit the parallelization capabilities of MongoDB, ensuring that the integration remains performant as the dataset grows.
Ultimately, designing ML models for MongoDB compatibility necessitates a holistic understanding of both the intricacies of ML algorithms and the unique features of MongoDB. It involves an iterative process of refinement, testing, and optimization to achieve a harmonious integration that maximizes the strengths of both technologies. The goal is to create a symbiotic relationship where ML models leverage MongoDB's scalability and flexibility, resulting in a powerful combination for handling and deriving insights from diverse and voluminous datasets.
Hands-On Practical Exercises in ML-MongoDB Integration
Hands-on practical exercises are essential for mastering the intricacies of integrating Machine Learning (ML) with MongoDB, providing practitioners with a tangible understanding of the integration process. To embark on this journey, the initial exercise involves setting up a MongoDB environment. This includes the installation and configuration of MongoDB on a local machine or a cloud-based platform, offering an introduction to fundamental database commands for data manipulation and retrieval.
A critical aspect of ML-MongoDB integration involves data preprocessing within MongoDB using its aggregation framework. Practitioners can engage in exercises where they filter, transform, and clean data directly within the database, optimizing the information for integration with ML models.
Optimizing for performance, practitioners can experiment with indexing strategies within MongoDB. This exercise sheds light on the impact of indexing on query efficiency, offering insights into how to fine-tune the retrieval of data for ML tasks.
Security implementation exercises address the crucial aspect of safeguarding both the MongoDB database and the integrated ML models. Practitioners gain hands-on experience in implementing access controls, encryption measures, and other security protocols to protect sensitive data.
Model deployment and monitoring exercises simulate real-world scenarios by deploying ML models integrated with MongoDB into a production-like environment. This holistic exercise includes monitoring the performance of deployed models and understanding the considerations for maintaining and updating models over time.
Addressing Ethical Considerations in ML-MongoDB Integration
Addressing ethical considerations in the integration of Machine Learning (ML) with MongoDB is paramount in the era of data-driven technologies. As organizations leverage the power of ML to extract insights from vast datasets stored in MongoDB, ethical concerns arise around issues such as data privacy, transparency, and potential biases embedded in algorithms. An essential first step in addressing these considerations is recognizing the responsibility of practitioners to ensure that the integration aligns with ethical standards and safeguards the rights and privacy of individuals whose data is involved.
One critical ethical consideration is data privacy, as MongoDB may store sensitive information that can be utilized by ML models. Practitioners must implement robust security measures, including encryption and access controls, to protect against unauthorized access and potential breaches. Additionally, transparent communication with users about data collection and utilization becomes imperative, fostering trust and compliance with privacy regulations.
Transparency and interpretability are key ethical principles in ML-MongoDB integration. Practitioners should strive to make ML models and the integration process understandable to stakeholders, promoting accountability and trust. Providing clear documentation on data sources, preprocessing steps, and model decisions contributes to transparency and enables users to comprehend and question the decisions made by the system.
Addressing ethical considerations in ML-MongoDB integration is a multifaceted task that demands a proactive and ongoing commitment to ethical practices. As the technological landscape evolves, practitioners must prioritize transparency, fairness, and privacy to ensure that ML models integrated with MongoDB align with ethical standards, contribute positively to society, and foster trust among users and stakeholders. By upholding these ethical principles, organizations can harness the benefits of ML-MongoDB integration while minimizing the potential risks and ethical pitfalls.
Certification Versatility and Career Opportunities
Certification in Machine Learning Integration with MongoDB opens up a realm of versatility and diverse career opportunities for professionals seeking to carve a niche in the dynamic intersection of data science and database management. The versatility of this certification lies in its ability to equip individuals with a comprehensive skill set, blending the proficiency in machine learning principles with the intricacies of MongoDB implementation. This unique combination positions certified professionals as valuable assets capable of addressing the evolving needs of organizations grappling with complex data challenges.
The certification's versatility is reflected in its applicability across various industries, where the integration of machine learning with MongoDB is becoming increasingly integral to decision-making processes. From healthcare and finance to e-commerce and beyond, certified individuals can leverage their expertise to drive innovation, optimize business operations, and extract meaningful insights from diverse datasets. The adaptability of this certification across sectors ensures that professionals possess skills that remain relevant and in-demand across a spectrum of industries.
In a competitive job market, certification in Machine Learning Integration with MongoDB becomes a valuable asset, enhancing a professional's marketability and employability. It not only demonstrates technical prowess but also underscores a commitment to staying abreast of cutting-edge developments in data science and database management. As organizations increasingly seek individuals with a diverse skill set, the certification opens doors to career advancements and positions certified professionals as leaders in the rapidly evolving landscape of technology.
The versatility and career opportunities associated with certification in Machine Learning Integration with MongoDB position it as a strategic investment for professionals aspiring to thrive in the data-driven era. Beyond imparting technical proficiency, the certification serves as a gateway to a myriad of career paths, where certified individuals can make impactful contributions and shape the future of data science and database management.
Continuous Learning and Upkeep of Certification
Continuous learning and the upkeep of certification in Machine Learning Integration with MongoDB are essential components for professionals aiming to stay at the forefront of the rapidly evolving landscape of data science and database management. In this dynamic field, where technologies and methodologies are in a perpetual state of evolution, the commitment to ongoing learning is paramount. Certified individuals recognize that the journey towards mastery is continuous and extends beyond the initial acquisition of skills.
The field of Machine Learning Integration with MongoDB is marked by constant innovation and emerging best practices. Therefore, professionals holding certifications must engage in continuous learning to stay updated with the latest developments, industry trends, and advancements in both machine learning and MongoDB. This commitment to ongoing education ensures that certified individuals remain well-informed about new tools, frameworks, and methodologies that may enhance their efficiency and efficacy in integrating ML with MongoDB.
Continuous learning and the upkeep of certification are inseparable components of a successful career in Machine Learning Integration with MongoDB. Embracing a mindset of lifelong learning ensures that certified professionals are well-equipped to navigate the complexities of the field, adapt to technological advancements, and contribute meaningfully to the ongoing transformation of data science and database management. By staying curious, connected, and committed to growth, individuals with certifications in ML-MongoDB integration position themselves as agile and resilient professionals in the ever-evolving landscape of technology.
How to obtain MONGODB DEVELOPER AND ADMINISTRATOR CERTIFICATION
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Machine Learning with MongoDB presents a compelling synergy that has transformative implications across diverse industries. The certification in Machine Learning Integration with MongoDB emerges as a key enabler for professionals seeking to navigate this dynamic intersection of data science and database management. As highlighted in the exploration of foundational concepts, practical exercises, and ethical considerations, this certification equips individuals with the knowledge and skills necessary to harness the full potential of both technologies.
The certification's importance in the data science landscape is underscored by the increasing demand for adept professionals capable of seamlessly integrating machine learning algorithms with MongoDB's flexible and scalable architecture. This recognition positions certified individuals as valuable assets in the data-driven era, where organizations prioritize actionable insights and strategic decision-making.
Addressing ethical considerations in ML-MongoDB integration is a critical aspect of the certification, emphasizing the responsibility of practitioners to uphold privacy, transparency, and fairness. By integrating ethical practices into the certification process, professionals ensure that their contributions align with societal expectations and contribute positively to the evolving landscape of technology.
The journey doesn't end with certification; instead, it is a stepping stone to a commitment to continuous learning. In the ever-evolving field of ML-MongoDB integration, staying informed, engaging in collaborative forums, and upkeeping the certification through ongoing education are crucial for maintaining relevance and competence. This dedication to continuous learning positions certified professionals as adaptable leaders in the face of evolving challenges and opportunities.
In essence, the Machine Learning Integration with MongoDB certification encapsulates not only technical proficiency but also a commitment to ethical practices, continuous learning, and a versatile skill set. As professionals embark on this certification journey, they position themselves at the forefront of innovation, ready to make impactful contributions to the transformative intersection of machine learning and MongoDB.
Integrating Apache Kafka with Machine Learning Pipelines
The integration of Apache Kafka with machine learning pipelines represents a powerful synergy between two transformative technologies, each playing a pivotal role in the modern data-driven landscape. Apache Kafka, a distributed streaming platform, has gained widespread recognition for its ability to handle real-time data streams at scale, ensuring reliable and efficient communication between disparate systems. On the other hand, machine learning pipelines have emerged as a cornerstone of advanced analytics, enabling organizations to extract valuable insights and predictions from vast datasets. The convergence of these technologies holds the promise of creating a seamless and dynamic ecosystem where real-time data flows seamlessly through machine learning workflows, fostering enhanced decision-making and operational efficiency.
At its core, Apache Kafka facilitates the seamless exchange of data across diverse applications, making it an ideal candidate for bridging the gap between data producers and consumers within machine learning pipelines. The event-driven architecture of Kafka aligns seamlessly with the iterative and continuous nature of machine learning processes, allowing organizations to ingest, process, and disseminate data in real-time. This integration not only addresses the challenges of handling large volumes of data but also establishes a foundation for responsive, adaptive machine learning models capable of evolving with dynamic data streams.
As organizations increasingly recognize the value of real-time insights, the integration of Apache Kafka with machine learning pipelines becomes imperative for staying competitive in today's data-centric landscape. This introduction sets the stage for exploring the various facets of this integration, delving into the technical nuances, practical applications, and potential benefits that arise from combining the strengths of Apache Kafka and machine learning. From streamlining data ingestion to facilitating model deployment and monitoring, this synergy opens up new avenues for organizations to leverage the power of real-time data in enhancing their machine learning capabilities.
Table of contents
-
Data Ingestion and Integration
-
Event-Driven Architecture for Machine Learning
-
Real-time Data Processing in Machine Learning Workflows
-
Ensuring Data Quality and Consistency
-
Monitoring and Management of Integrated Systems
-
Security and Data Privacy in Integrated Systems
-
Future Trends and Innovations
-
Conclusion
Data Ingestion and Integration
Data ingestion and integration form the foundational steps in the symbiotic relationship between Apache Kafka and machine learning pipelines. Apache Kafka, renowned for its distributed streaming capabilities, serves as a robust conduit for ingesting data from disparate sources into the machine learning ecosystem. The platform's ability to handle high-throughput, real-time data streams positions it as a key player in facilitating seamless data flow, acting as a bridge that connects various components within the integrated system.
In this context, data ingestion involves the process of collecting, importing, and organizing data from diverse origins into Kafka topics. These topics act as logical channels where data is partitioned and made available for consumption by downstream components, including machine learning models. Kafka's distributed architecture ensures that the ingestion process is scalable and fault-tolerant, allowing organizations to handle vast volumes of data with reliability and efficiency.
Integration, on the other hand, delves into the orchestration of data movement between Kafka and machine learning components. The integrated system leverages Kafka Connect, a framework that simplifies the development of connectors to bridge Kafka with various data sources and sinks. This integration framework enables a seamless and continuous flow of data, ensuring that machine learning pipelines receive timely updates from the incoming data streams. As a result, organizations can maintain a dynamic and responsive connection between their data sources and the machine learning algorithms that rely on them.
Event-Driven Architecture for Machine Learning
The integration of Apache Kafka with machine learning pipelines brings forth a transformative shift towards an event-driven architecture, redefining the landscape of how data is processed and utilized in the context of machine learning. At its core, event-driven architecture embraces the philosophy of responding to events or changes in real-time, aligning seamlessly with the iterative nature of machine learning processes. This architectural paradigm capitalizes on Kafka's distributed streaming capabilities, offering an efficient and scalable solution to handle the continuous flow of events within the machine learning ecosystem.
In the context of machine learning, events can encompass a spectrum of activities, ranging from data updates and model training triggers to the deployment of updated models. Apache Kafka acts as the backbone of this event-driven approach, serving as the central nervous system that facilitates the communication and coordination of these events. This real-time, bidirectional communication ensures that machine learning models are not only trained on the latest data but also respond dynamically to changing conditions, resulting in more adaptive and accurate predictions.
The event-driven architecture enables a decoupled and modularized system, where components within the machine learning pipeline react autonomously to specific events. This modularity enhances the scalability and maintainability of the overall system, allowing organizations to evolve and scale their machine learning infrastructure with greater agility. As data events propagate through Kafka topics, machine learning algorithms subscribe to these topics, ensuring they are continuously updated and refined based on the latest information.
The adoption of an event-driven architecture, powered by Apache Kafka, propels machine learning pipelines into a realm of responsiveness and adaptability that aligns with the dynamic nature of contemporary data ecosystems. This approach not only optimizes the performance of machine learning models but also paves the way for innovative applications and use cases in the rapidly evolving landscape of data-driven technologies.
Real-time Data Processing in Machine Learning Workflows
Real-time data processing stands as a cornerstone in the integration of Apache Kafka with machine learning workflows, revolutionizing the traditional paradigm of batch processing. Unlike batch processing, which handles data in chunks at scheduled intervals, real-time data processing leverages the continuous flow of data, enabling machine learning models to operate on the freshest information available. Apache Kafka plays a pivotal role in this context, acting as the conduit that seamlessly facilitates the flow of real-time data through the machine learning pipeline.
In a machine learning workflow, real-time data processing begins with the ingestion of data into Kafka topics. These topics serve as dynamic channels where data is partitioned and made available for immediate consumption by downstream machine learning components. The distributed nature of Kafka ensures that data can be processed in parallel across multiple nodes, enhancing the scalability and speed of real-time data processing.
Machine learning algorithms within the integrated system subscribe to these Kafka topics, allowing them to receive and process data updates as soon as they occur. This real-time responsiveness is particularly crucial in applications where the value of predictions diminishes rapidly over time, such as in financial trading, fraud detection, or dynamic pricing models. By continuously processing and updating models in real-time, organizations can derive insights and make decisions at the pace demanded by today's fast-paced and data-intensive environments.
Despite the advantages, real-time data processing in machine learning workflows comes with its set of challenges. Ensuring low-latency data processing, managing data consistency, and handling potential bottlenecks are critical considerations. However, the integration of Apache Kafka provides a robust infrastructure to address these challenges, laying the foundation for organizations to harness the full potential of real-time data processing in their machine learning endeavors. As the demand for timely insights continues to grow, the synergy between Apache Kafka and real-time machine learning processing emerges as a strategic asset for organizations seeking to gain a competitive edge in today's data-centric landscape.
Ensuring Data Quality and Consistency
In the integration of Apache Kafka with machine learning pipelines, the assurance of data quality and consistency emerges as a fundamental imperative. As data traverses the distributed architecture facilitated by Kafka, maintaining the integrity and reliability of information becomes pivotal for the accuracy and effectiveness of downstream machine learning processes.
Ensuring data quality encompasses several key facets, beginning with the validation and cleansing of incoming data streams. Apache Kafka's ability to handle real-time data influxes must be complemented by robust data validation mechanisms to identify and address anomalies, outliers, or inconsistencies in the data. This initial quality check is crucial to prevent inaccuracies from propagating through the machine learning pipeline, ensuring that models are trained on reliable and representative datasets.
Consistency, on the other hand, involves harmonizing data formats, schemas, and semantics across diverse sources and destinations. Kafka's schema registry, a component that manages the evolution of data schemas, plays a pivotal role in maintaining consistency within the data ecosystem. By enforcing schema compatibility and versioning, organizations can navigate changes in data structures without compromising downstream processes, thereby promoting a consistent interpretation of data across the entire machine learning workflow.
Data quality and consistency are also influenced by factors such as data drift and schema evolution, common challenges in dynamic environments. Data drift occurs when the statistical properties of the incoming data change over time, impacting the performance of machine learning models. Apache Kafka's ability to capture and version data enables organizations to monitor and adapt to such drift, allowing for the recalibration of models as needed.
Ensuring data quality and consistency in the context of Apache Kafka and machine learning integration is a multifaceted endeavor. By implementing rigorous validation processes, leveraging schema management capabilities, and addressing challenges like data drift, organizations can cultivate a reliable and coherent data foundation. This, in turn, enhances the robustness of machine learning models, fortifying the integration against potential pitfalls and reinforcing the value derived from real-time, high-throughput data streams.
Monitoring and Management of Integrated Systems
The integration of Apache Kafka with machine learning pipelines necessitates robust monitoring and management practices to ensure the efficiency, reliability, and security of the amalgamated system. In the intricate landscape where real-time data streams converge with machine learning algorithms, effective monitoring serves as a linchpin for maintaining operational integrity.
Central to the monitoring of integrated systems is the meticulous examination of infrastructure performance. Monitoring tools track key metrics within Apache Kafka clusters and machine learning components, providing administrators with real-time insights into throughput, latency, and resource utilization. This visibility enables proactive identification and resolution of potential bottlenecks, allowing for the optimization of configurations to meet the demands of both real-time data processing and machine learning workloads.
Security monitoring and auditing constitute foundational elements in the well-managed integrated system. Monitoring tools diligently track access, authentication, and authorization events within Apache Kafka and machine learning components. The utilization of Security Information and Event Management (SIEM) solutions aids in aggregating and analyzing security-related data, ensuring compliance, and offering insights into potential threats or vulnerabilities.
A comprehensive monitoring and management strategy is imperative for organizations navigating the intricacies of integrating Apache Kafka with machine learning pipelines. Addressing infrastructure performance, data flow tracking, security monitoring, and capacity planning collectively contribute to fostering a resilient and efficient integrated ecosystem, unlocking the full potential of real-time data processing and machine learning capabilities.
Security and Data Privacy in Integrated Systems
The integration of Apache Kafka with machine learning pipelines introduces a complex interplay of real-time data flows and advanced analytics, underscoring the critical need for robust security measures and data privacy safeguards within the integrated environment. As information traverses the interconnected architecture, safeguarding the confidentiality and integrity of data becomes paramount, demanding a comprehensive approach to address potential vulnerabilities and ensure compliance with data protection regulations.
Fundamental to the security framework of integrated systems is the implementation of stringent access controls and authentication mechanisms. Apache Kafka, as the central hub for data exchange, requires meticulous user authentication protocols and encryption methods to control and secure access, mitigating the risk of unauthorized parties infiltrating the system.
Authorization mechanisms play an equally vital role, defining and enforcing fine-grained permissions to ensure that users and components have access only to the data and functionalities essential to their specific roles. This approach minimizes the likelihood of unauthorized data access or manipulation, contributing to a more secure integrated system.
Encryption, both for data in transit and at rest, emerges as a linchpin in securing sensitive information within the integrated environment. The application of encryption protocols ensures that even if intercepted, the data remains indecipherable to unauthorized entities, fortifying the overall security posture of the integrated system.
Securing Apache Kafka and machine learning pipelines within integrated systems requires a multifaceted strategy encompassing authentication, encryption, privacy-preserving techniques, regulatory compliance, and incident response planning. By addressing these aspects, organizations can fortify their integrated environments against security threats while upholding the confidentiality and privacy of sensitive data.
Future Trends and Innovations
The integration of Apache Kafka with machine learning pipelines sets the stage for a landscape of continuous evolution, marked by emerging trends and innovations that promise to reshape the future of data processing and analytics. As organizations strive to extract greater value from their data, several key trajectories are poised to define the future of this dynamic integration.
Decentralized Machine Learning Architectures: Future trends indicate a shift towards decentralized machine learning architectures within integrated systems. This approach distributes the machine learning processing across multiple nodes, enabling more efficient and scalable models. Decentralization not only enhances performance but also aligns with the principles of edge computing, allowing for real-time processing closer to the data source.
Integration with Advanced Analytics: The future holds a convergence of Apache Kafka with advanced analytics techniques, including artificial intelligence (AI) and deep learning. The integration of these technologies within machine learning pipelines promises to unlock new levels of predictive and prescriptive analytics, enabling organizations to make more informed decisions and uncover hidden patterns within their data.
Exponential Growth in Data Governance Solutions: As the volume and complexity of data continue to surge, future trends point to the exponential growth of data governance solutions within integrated systems. Innovations in metadata management, data lineage tracking, and automated governance frameworks will become integral for ensuring data quality, compliance, and accountability across the entire data lifecycle.
Enhanced Security and Privacy Measures: Future innovations in the integration of Apache Kafka and machine learning pipelines will be closely intertwined with heightened security and privacy measures. As the regulatory landscape evolves, organizations will invest in advanced encryption techniques, secure access controls, and privacy-preserving methodologies to safeguard sensitive information and ensure compliance with data protection regulations.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Apache Kafka with machine learning pipelines represents a transformative synergy that propels data processing and analytics into a new era. This amalgamation not only addresses the challenges of handling real-time data streams but also unleashes the potential for organizations to derive actionable insights and drive innovation through advanced machine learning techniques.
The journey from data ingestion and integration to event-driven architectures and real-time data processing underscores the dynamic nature of this integration. As organizations navigate the complexities of monitoring, management, and ensuring data quality, the robust capabilities of Apache Kafka emerge as a linchpin for creating resilient, scalable, and efficient integrated systems.
Furthermore, the emphasis on security and data privacy within integrated systems is paramount. As the regulatory landscape evolves, the integration of Apache Kafka and machine learning pipelines must adhere to stringent security measures, encryption protocols, and privacy-preserving techniques to safeguard sensitive information and ensure compliance.
The integration of Apache Kafka with machine learning pipelines signifies more than just a technological collaboration; it represents a strategic imperative for organizations seeking to thrive in a data-driven world. As this integration continues to evolve, organizations stand to benefit from real-time insights, adaptive machine learning models, and a future-ready infrastructure that positions them at the forefront of innovation in the rapidly changing landscape of data and analytics.
Read More
The integration of Apache Kafka with machine learning pipelines represents a powerful synergy between two transformative technologies, each playing a pivotal role in the modern data-driven landscape. Apache Kafka, a distributed streaming platform, has gained widespread recognition for its ability to handle real-time data streams at scale, ensuring reliable and efficient communication between disparate systems. On the other hand, machine learning pipelines have emerged as a cornerstone of advanced analytics, enabling organizations to extract valuable insights and predictions from vast datasets. The convergence of these technologies holds the promise of creating a seamless and dynamic ecosystem where real-time data flows seamlessly through machine learning workflows, fostering enhanced decision-making and operational efficiency.
At its core, Apache Kafka facilitates the seamless exchange of data across diverse applications, making it an ideal candidate for bridging the gap between data producers and consumers within machine learning pipelines. The event-driven architecture of Kafka aligns seamlessly with the iterative and continuous nature of machine learning processes, allowing organizations to ingest, process, and disseminate data in real-time. This integration not only addresses the challenges of handling large volumes of data but also establishes a foundation for responsive, adaptive machine learning models capable of evolving with dynamic data streams.
As organizations increasingly recognize the value of real-time insights, the integration of Apache Kafka with machine learning pipelines becomes imperative for staying competitive in today's data-centric landscape. This introduction sets the stage for exploring the various facets of this integration, delving into the technical nuances, practical applications, and potential benefits that arise from combining the strengths of Apache Kafka and machine learning. From streamlining data ingestion to facilitating model deployment and monitoring, this synergy opens up new avenues for organizations to leverage the power of real-time data in enhancing their machine learning capabilities.
Table of contents
-
Data Ingestion and Integration
-
Event-Driven Architecture for Machine Learning
-
Real-time Data Processing in Machine Learning Workflows
-
Ensuring Data Quality and Consistency
-
Monitoring and Management of Integrated Systems
-
Security and Data Privacy in Integrated Systems
-
Future Trends and Innovations
-
Conclusion
Data Ingestion and Integration
Data ingestion and integration form the foundational steps in the symbiotic relationship between Apache Kafka and machine learning pipelines. Apache Kafka, renowned for its distributed streaming capabilities, serves as a robust conduit for ingesting data from disparate sources into the machine learning ecosystem. The platform's ability to handle high-throughput, real-time data streams positions it as a key player in facilitating seamless data flow, acting as a bridge that connects various components within the integrated system.
In this context, data ingestion involves the process of collecting, importing, and organizing data from diverse origins into Kafka topics. These topics act as logical channels where data is partitioned and made available for consumption by downstream components, including machine learning models. Kafka's distributed architecture ensures that the ingestion process is scalable and fault-tolerant, allowing organizations to handle vast volumes of data with reliability and efficiency.
Integration, on the other hand, delves into the orchestration of data movement between Kafka and machine learning components. The integrated system leverages Kafka Connect, a framework that simplifies the development of connectors to bridge Kafka with various data sources and sinks. This integration framework enables a seamless and continuous flow of data, ensuring that machine learning pipelines receive timely updates from the incoming data streams. As a result, organizations can maintain a dynamic and responsive connection between their data sources and the machine learning algorithms that rely on them.
Event-Driven Architecture for Machine Learning
The integration of Apache Kafka with machine learning pipelines brings forth a transformative shift towards an event-driven architecture, redefining the landscape of how data is processed and utilized in the context of machine learning. At its core, event-driven architecture embraces the philosophy of responding to events or changes in real-time, aligning seamlessly with the iterative nature of machine learning processes. This architectural paradigm capitalizes on Kafka's distributed streaming capabilities, offering an efficient and scalable solution to handle the continuous flow of events within the machine learning ecosystem.
In the context of machine learning, events can encompass a spectrum of activities, ranging from data updates and model training triggers to the deployment of updated models. Apache Kafka acts as the backbone of this event-driven approach, serving as the central nervous system that facilitates the communication and coordination of these events. This real-time, bidirectional communication ensures that machine learning models are not only trained on the latest data but also respond dynamically to changing conditions, resulting in more adaptive and accurate predictions.
The event-driven architecture enables a decoupled and modularized system, where components within the machine learning pipeline react autonomously to specific events. This modularity enhances the scalability and maintainability of the overall system, allowing organizations to evolve and scale their machine learning infrastructure with greater agility. As data events propagate through Kafka topics, machine learning algorithms subscribe to these topics, ensuring they are continuously updated and refined based on the latest information.
The adoption of an event-driven architecture, powered by Apache Kafka, propels machine learning pipelines into a realm of responsiveness and adaptability that aligns with the dynamic nature of contemporary data ecosystems. This approach not only optimizes the performance of machine learning models but also paves the way for innovative applications and use cases in the rapidly evolving landscape of data-driven technologies.
Real-time Data Processing in Machine Learning Workflows
Real-time data processing stands as a cornerstone in the integration of Apache Kafka with machine learning workflows, revolutionizing the traditional paradigm of batch processing. Unlike batch processing, which handles data in chunks at scheduled intervals, real-time data processing leverages the continuous flow of data, enabling machine learning models to operate on the freshest information available. Apache Kafka plays a pivotal role in this context, acting as the conduit that seamlessly facilitates the flow of real-time data through the machine learning pipeline.
In a machine learning workflow, real-time data processing begins with the ingestion of data into Kafka topics. These topics serve as dynamic channels where data is partitioned and made available for immediate consumption by downstream machine learning components. The distributed nature of Kafka ensures that data can be processed in parallel across multiple nodes, enhancing the scalability and speed of real-time data processing.
Machine learning algorithms within the integrated system subscribe to these Kafka topics, allowing them to receive and process data updates as soon as they occur. This real-time responsiveness is particularly crucial in applications where the value of predictions diminishes rapidly over time, such as in financial trading, fraud detection, or dynamic pricing models. By continuously processing and updating models in real-time, organizations can derive insights and make decisions at the pace demanded by today's fast-paced and data-intensive environments.
Despite the advantages, real-time data processing in machine learning workflows comes with its set of challenges. Ensuring low-latency data processing, managing data consistency, and handling potential bottlenecks are critical considerations. However, the integration of Apache Kafka provides a robust infrastructure to address these challenges, laying the foundation for organizations to harness the full potential of real-time data processing in their machine learning endeavors. As the demand for timely insights continues to grow, the synergy between Apache Kafka and real-time machine learning processing emerges as a strategic asset for organizations seeking to gain a competitive edge in today's data-centric landscape.
Ensuring Data Quality and Consistency
In the integration of Apache Kafka with machine learning pipelines, the assurance of data quality and consistency emerges as a fundamental imperative. As data traverses the distributed architecture facilitated by Kafka, maintaining the integrity and reliability of information becomes pivotal for the accuracy and effectiveness of downstream machine learning processes.
Ensuring data quality encompasses several key facets, beginning with the validation and cleansing of incoming data streams. Apache Kafka's ability to handle real-time data influxes must be complemented by robust data validation mechanisms to identify and address anomalies, outliers, or inconsistencies in the data. This initial quality check is crucial to prevent inaccuracies from propagating through the machine learning pipeline, ensuring that models are trained on reliable and representative datasets.
Consistency, on the other hand, involves harmonizing data formats, schemas, and semantics across diverse sources and destinations. Kafka's schema registry, a component that manages the evolution of data schemas, plays a pivotal role in maintaining consistency within the data ecosystem. By enforcing schema compatibility and versioning, organizations can navigate changes in data structures without compromising downstream processes, thereby promoting a consistent interpretation of data across the entire machine learning workflow.
Data quality and consistency are also influenced by factors such as data drift and schema evolution, common challenges in dynamic environments. Data drift occurs when the statistical properties of the incoming data change over time, impacting the performance of machine learning models. Apache Kafka's ability to capture and version data enables organizations to monitor and adapt to such drift, allowing for the recalibration of models as needed.
Ensuring data quality and consistency in the context of Apache Kafka and machine learning integration is a multifaceted endeavor. By implementing rigorous validation processes, leveraging schema management capabilities, and addressing challenges like data drift, organizations can cultivate a reliable and coherent data foundation. This, in turn, enhances the robustness of machine learning models, fortifying the integration against potential pitfalls and reinforcing the value derived from real-time, high-throughput data streams.
Monitoring and Management of Integrated Systems
The integration of Apache Kafka with machine learning pipelines necessitates robust monitoring and management practices to ensure the efficiency, reliability, and security of the amalgamated system. In the intricate landscape where real-time data streams converge with machine learning algorithms, effective monitoring serves as a linchpin for maintaining operational integrity.
Central to the monitoring of integrated systems is the meticulous examination of infrastructure performance. Monitoring tools track key metrics within Apache Kafka clusters and machine learning components, providing administrators with real-time insights into throughput, latency, and resource utilization. This visibility enables proactive identification and resolution of potential bottlenecks, allowing for the optimization of configurations to meet the demands of both real-time data processing and machine learning workloads.
Security monitoring and auditing constitute foundational elements in the well-managed integrated system. Monitoring tools diligently track access, authentication, and authorization events within Apache Kafka and machine learning components. The utilization of Security Information and Event Management (SIEM) solutions aids in aggregating and analyzing security-related data, ensuring compliance, and offering insights into potential threats or vulnerabilities.
A comprehensive monitoring and management strategy is imperative for organizations navigating the intricacies of integrating Apache Kafka with machine learning pipelines. Addressing infrastructure performance, data flow tracking, security monitoring, and capacity planning collectively contribute to fostering a resilient and efficient integrated ecosystem, unlocking the full potential of real-time data processing and machine learning capabilities.
Security and Data Privacy in Integrated Systems
The integration of Apache Kafka with machine learning pipelines introduces a complex interplay of real-time data flows and advanced analytics, underscoring the critical need for robust security measures and data privacy safeguards within the integrated environment. As information traverses the interconnected architecture, safeguarding the confidentiality and integrity of data becomes paramount, demanding a comprehensive approach to address potential vulnerabilities and ensure compliance with data protection regulations.
Fundamental to the security framework of integrated systems is the implementation of stringent access controls and authentication mechanisms. Apache Kafka, as the central hub for data exchange, requires meticulous user authentication protocols and encryption methods to control and secure access, mitigating the risk of unauthorized parties infiltrating the system.
Authorization mechanisms play an equally vital role, defining and enforcing fine-grained permissions to ensure that users and components have access only to the data and functionalities essential to their specific roles. This approach minimizes the likelihood of unauthorized data access or manipulation, contributing to a more secure integrated system.
Encryption, both for data in transit and at rest, emerges as a linchpin in securing sensitive information within the integrated environment. The application of encryption protocols ensures that even if intercepted, the data remains indecipherable to unauthorized entities, fortifying the overall security posture of the integrated system.
Securing Apache Kafka and machine learning pipelines within integrated systems requires a multifaceted strategy encompassing authentication, encryption, privacy-preserving techniques, regulatory compliance, and incident response planning. By addressing these aspects, organizations can fortify their integrated environments against security threats while upholding the confidentiality and privacy of sensitive data.
Future Trends and Innovations
The integration of Apache Kafka with machine learning pipelines sets the stage for a landscape of continuous evolution, marked by emerging trends and innovations that promise to reshape the future of data processing and analytics. As organizations strive to extract greater value from their data, several key trajectories are poised to define the future of this dynamic integration.
Decentralized Machine Learning Architectures: Future trends indicate a shift towards decentralized machine learning architectures within integrated systems. This approach distributes the machine learning processing across multiple nodes, enabling more efficient and scalable models. Decentralization not only enhances performance but also aligns with the principles of edge computing, allowing for real-time processing closer to the data source.
Integration with Advanced Analytics: The future holds a convergence of Apache Kafka with advanced analytics techniques, including artificial intelligence (AI) and deep learning. The integration of these technologies within machine learning pipelines promises to unlock new levels of predictive and prescriptive analytics, enabling organizations to make more informed decisions and uncover hidden patterns within their data.
Exponential Growth in Data Governance Solutions: As the volume and complexity of data continue to surge, future trends point to the exponential growth of data governance solutions within integrated systems. Innovations in metadata management, data lineage tracking, and automated governance frameworks will become integral for ensuring data quality, compliance, and accountability across the entire data lifecycle.
Enhanced Security and Privacy Measures: Future innovations in the integration of Apache Kafka and machine learning pipelines will be closely intertwined with heightened security and privacy measures. As the regulatory landscape evolves, organizations will invest in advanced encryption techniques, secure access controls, and privacy-preserving methodologies to safeguard sensitive information and ensure compliance with data protection regulations.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the integration of Apache Kafka with machine learning pipelines represents a transformative synergy that propels data processing and analytics into a new era. This amalgamation not only addresses the challenges of handling real-time data streams but also unleashes the potential for organizations to derive actionable insights and drive innovation through advanced machine learning techniques.
The journey from data ingestion and integration to event-driven architectures and real-time data processing underscores the dynamic nature of this integration. As organizations navigate the complexities of monitoring, management, and ensuring data quality, the robust capabilities of Apache Kafka emerge as a linchpin for creating resilient, scalable, and efficient integrated systems.
Furthermore, the emphasis on security and data privacy within integrated systems is paramount. As the regulatory landscape evolves, the integration of Apache Kafka and machine learning pipelines must adhere to stringent security measures, encryption protocols, and privacy-preserving techniques to safeguard sensitive information and ensure compliance.
The integration of Apache Kafka with machine learning pipelines signifies more than just a technological collaboration; it represents a strategic imperative for organizations seeking to thrive in a data-driven world. As this integration continues to evolve, organizations stand to benefit from real-time insights, adaptive machine learning models, and a future-ready infrastructure that positions them at the forefront of innovation in the rapidly changing landscape of data and analytics.
Power BI for Hybrid Work Environments
As the dynamics of the modern workplace continue to evolve, the concept of a hybrid work environment has become a cornerstone of organizational flexibility. With teams dispersed across various locations, the need for effective collaboration and data-driven decision-making has never been more critical. In this transformative landscape, Microsoft's Power BI emerges as a catalyst for organizations navigating the complexities of hybrid work environments. Its versatile suite of tools and cloud-powered capabilities are uniquely suited to meet the demands of a workforce that seamlessly blends in-person and remote collaboration.
The essence of hybrid work lies in striking a delicate balance between accessibility and collaboration, and Power BI is at the forefront of facilitating this equilibrium. This introduction delves into the ways in which Power BI serves as a linchpin for businesses seeking to harness the power of data analytics and visualization in a landscape where the boundaries between physical and virtual workspaces blur. From ensuring real-time insights to fostering collaborative decision-making, Power BI is poised to redefine how organizations thrive in the era of hybrid work.
As we explore the multifaceted role of Power BI in this paradigm shift, it becomes evident that the platform's adaptability extends beyond traditional business intelligence. It becomes an enabler of seamless communication, a guardian of data security in a distributed landscape, and a catalyst for innovation. Join us on this journey as we unravel the transformative impact of Power BI in hybrid work environments, where connectivity, collaboration, and insightful decision-making converge to shape the future of work.
Table of contents
-
Collaborative Reporting in Power BI
-
Data Accessibility in Hybrid Work
-
Effective Data Communication in Virtual Teams
-
Power BI Mobile App for On-the-Go Insights
-
Security Measures in Power BI for Remote Work
-
Customizing Power BI for Hybrid Team Workflows
-
Hybrid Work Analytics
-
Conclusion
Collaborative Reporting in Power BI
In the ever-evolving landscape of hybrid work environments, effective collaboration is paramount to the success of dispersed teams. Collaborative reporting in Power BI emerges as a key facet in fostering teamwork and ensuring that decision-makers, whether working in the office or remotely, can collectively engage with and derive insights from shared data. Power BI's robust features for collaboration extend beyond traditional reporting tools, allowing teams to seamlessly interact with reports, provide feedback, and make informed decisions collectively.
Power BI's sharing and collaboration functionalities empower users to distribute reports effortlessly among team members, irrespective of their physical location. With the ability to create workspaces and share dashboards securely, Power BI facilitates a collaborative ecosystem where stakeholders can access real-time data insights and contribute their perspectives. This feature proves invaluable in hybrid work scenarios, where fluid communication and shared understanding are vital components of successful decision-making.
As organizations navigate the intricacies of hybrid work, the collaborative reporting capabilities of Power BI become a linchpin for maintaining a unified approach to data analysis. Through interactive dashboards and shared insights, Power BI not only facilitates collaboration but also enhances the agility of decision-making processes. The platform empowers teams to adapt quickly to changing circumstances, leveraging the collective intelligence of dispersed team members to drive business success in the dynamic landscape of the modern workplace.
Data Accessibility in Hybrid Work
Ensuring seamless data accessibility is a cornerstone in the successful implementation of hybrid work environments, where employees operate from various locations. In this context, Power BI plays a pivotal role in bridging the geographical gaps and providing consistent access to critical data. The platform's cloud-based architecture significantly contributes to breaking down traditional barriers, ensuring that both in-office and remote team members have equal and secure access to the data they need.
Power BI's cloud integration transforms it into a dynamic and accessible hub for business intelligence. This adaptability is particularly crucial in hybrid work scenarios, where employees may switch between working in the office and remotely. With Power BI, data becomes platform-agnostic, allowing users to access reports and dashboards from virtually any device with an internet connection. This flexibility not only enhances the mobility of the workforce but also aligns seamlessly with the fluid nature of hybrid work schedules.
Security, another critical aspect of data accessibility, is addressed through Power BI's robust measures. With data encryption, role-based access controls, and compliance certifications, Power BI ensures that sensitive information remains protected. This not only instills confidence in users but also aligns with the stringent data security requirements inherent in hybrid work environments.
Power BI's role in ensuring data accessibility in hybrid work environments is transformative. By leveraging the cloud and real-time capabilities, the platform transcends physical constraints, providing a unified experience for teams irrespective of where they work. This adaptability positions Power BI as a cornerstone for organizations striving to maintain consistent, secure, and accessible data in the era of hybrid work.
Effective Data Communication in Virtual Teams
Effective data communication is a cornerstone of success in virtual teams, where the ability to convey complex information clearly and engagingly becomes paramount. In this context, Power BI emerges as a powerful tool to facilitate impactful data communication, transcending the challenges of virtual collaboration. The platform's features not only enable the creation of visually compelling reports but also offer tools for collaborative interpretation, ensuring that virtual teams can derive meaningful insights collectively.
Power BI's visual storytelling capabilities play a pivotal role in enhancing data communication within virtual teams. Through a diverse array of customizable charts, graphs, and dashboards, complex datasets can be transformed into visually intuitive representations. This not only simplifies the understanding of intricate data but also makes it more engaging for team members. Whether presenting in a virtual meeting or sharing reports asynchronously, Power BI's visual elements enhance comprehension and retention.
Collaborative interpretation is another dimension where Power BI excels in the realm of virtual teamwork. The platform allows team members to interact with reports in real-time, encouraging discussions and data-driven conversations. Commenting features enable stakeholders to provide insights, ask questions, and offer feedback directly within the reports. This real-time collaboration fosters a sense of shared understanding, replicating the dynamic discussions that would typically occur in a physical workspace.
Power BI Mobile App for On-the-Go Insights
In the dynamic landscape of modern work, the ability to access crucial insights on-the-go has become a cornerstone of operational efficiency. Power BI, Microsoft's powerful business intelligence platform, addresses this need with its feature-rich mobile application, designed to empower users with real-time data access and analytics regardless of their location. The Power BI mobile app serves as a catalyst for seamless decision-making, offering a personalized and intuitive experience that extends the power of data analytics beyond the confines of the office.
One of the defining features of the Power BI mobile app is its adaptability to various devices, including smartphones and tablets. This ensures that decision-makers can carry a wealth of information in their pockets, enabling them to stay connected with key metrics, reports, and dashboards wherever they are. The responsive design of the app optimizes the user experience, allowing for easy navigation and interaction with data visualizations even on smaller screens.
The real-time synchronization capabilities of the Power BI mobile app elevate its utility for professionals on the move. As data is updated in the main Power BI service, the mobile app reflects these changes instantaneously. This ensures that users are always working with the most current information, enhancing the reliability of insights derived while away from the office.
Security is a paramount consideration for mobile business intelligence, and the Power BI mobile app addresses this concern comprehensively. With features such as multi-factor authentication, data encryption, and secure sign-in, the app ensures that sensitive business information remains protected, aligning with the stringent security standards required in today's mobile work environment.
As organizations embrace the flexibility of on-the-go work, the Power BI mobile app emerges as an indispensable tool for professionals seeking to stay connected with their data and analytics. By offering a seamless and secure mobile experience, Power BI empowers decision-makers to make informed choices wherever they may be, revolutionizing the concept of business intelligence in the era of mobile work.
Security Measures in Power BI for Remote Work
In the era of remote work, where data is accessed and shared across diverse locations, ensuring the security of sensitive information has become a paramount concern. Power BI, Microsoft's business intelligence platform, incorporates a robust set of security measures designed to fortify data integrity and confidentiality in the context of remote work environments. These measures encompass a multifaceted approach, addressing encryption, access controls, and compliance standards, providing organizations with the assurance needed to navigate the unique security challenges associated with distributed work settings.
Power BI's role-based access controls (RBAC) offer a granular and flexible approach to managing user permissions. In the context of remote work, where employees access data from various locations, RBAC ensures that only authorized individuals have access to specific reports, dashboards, or datasets. This tailored approach to access management adds a layer of security that is essential in preventing unauthorized access to sensitive business intelligence.
Multi-Factor Authentication (MFA) further enhances the security of remote access to Power BI. By requiring users to provide multiple forms of identification—such as a password combined with a temporary code sent to a mobile device—MFA adds an additional layer of protection against unauthorized access. Particularly in remote work scenarios, where the risk of unauthorized access may be heightened, MFA becomes a crucial safeguard for securing user accounts.
Power BI's commitment to compliance is evident through its adherence to industry-specific standards. Certifications such as ISO/IEC 27001 and SOC 2 attest to Power BI's rigorous adherence to data security and governance protocols. For organizations navigating the regulatory landscape of remote work, these certifications provide confidence that Power BI maintains the highest standards of compliance.
In the dynamic landscape of remote work, where collaboration and data accessibility are imperative, Power BI's security measures provide a robust foundation for organizations. By addressing encryption, access controls, multi-factor authentication, and compliance standards, Power BI not only ensures the secure handling of sensitive information but also empowers remote teams to leverage business intelligence tools with confidence in the integrity and confidentiality of their data.
Customizing Power BI for Hybrid Team Workflows
In the evolving landscape of hybrid work, where teams seamlessly transition between in-office and remote settings, the ability to customize tools to align with unique workflows becomes pivotal. Power BI, Microsoft's versatile business intelligence platform, offers organizations the flexibility to tailor its features, making it an ideal companion for hybrid team workflows. Customization in Power BI extends beyond the creation of insightful reports and dashboards; it enables organizations to adapt the platform to the specific needs and collaborative dynamics of their hybrid teams.
One notable aspect of customizing Power BI for hybrid team workflows is the ability to create personalized dashboards and reports that cater to the diverse requirements of team members. By allowing customization based on roles, preferences, and specific KPIs, Power BI empowers organizations to provide a tailored analytics experience. This level of adaptability ensures that each team member, regardless of their location or role, can access the data most relevant to their responsibilities.
The integration of Power BI with other collaborative tools, such as Microsoft Teams, further enhances customization possibilities. Organizations can embed Power BI reports directly into Teams channels, fostering a cohesive and centralized virtual workspace for hybrid teams. This integration not only streamlines access to critical data but also promotes a collaborative environment where team members can seamlessly transition between discussions and data analysis.
Customized workflows in Power BI also extend to the establishment of automated processes and alerts. Organizations can set up custom alerts based on specific thresholds or changes in data, ensuring that remote and in-office team members are promptly notified of critical developments. This proactive approach enhances real-time decision-making and fosters a responsive environment conducive to the dynamic nature of hybrid work.
Power BI's APIs and extensibility options open avenues for organizations to integrate the platform into their existing applications and workflows. This level of customization allows for a seamless integration of Power BI into the broader technology ecosystem, aligning business intelligence processes with the overarching goals and workflows of hybrid teams.
As organizations navigate the complexities of hybrid work, customizing Power BI emerges as a strategic initiative to optimize workflows and enhance collaboration. The platform's adaptability to unique team dynamics, coupled with integrations and automation capabilities, positions Power BI as a dynamic tool that not only analyzes data but becomes an integral part of how hybrid teams operate, collaborate, and make informed decisions.
Hybrid Work Analytics
In the era of hybrid work, organizations are increasingly turning to analytics to gain valuable insights into the dynamics of their dispersed teams. Hybrid work analytics, facilitated by tools such as Power BI, play a pivotal role in helping businesses understand, measure, and optimize the effectiveness of their hybrid work models. These analytics delve into various aspects of employee engagement, collaboration patterns, and productivity metrics, providing organizations with data-driven insights to navigate the nuances of this evolving work paradigm.
One crucial dimension of hybrid work analytics is the examination of employee engagement. Through the analysis of collaboration tools, communication platforms, and workflow patterns, organizations can gauge the level of engagement among remote and in-office team members. These insights empower leaders to identify trends, address potential challenges, and implement strategies to foster a cohesive and engaged workforce across different work settings.
Collaboration analytics within hybrid work environments offer a closer look at how teams interact and share information. By leveraging data from collaboration tools integrated with Power BI, organizations can assess the frequency and modes of communication, uncover collaboration bottlenecks, and identify opportunities for enhancing teamwork. This granular understanding contributes to creating strategies that promote effective collaboration, irrespective of physical locations.
Productivity metrics form another critical component of hybrid work analytics. Organizations can utilize Power BI to track key performance indicators (KPIs) related to individual and team productivity. This includes metrics such as task completion rates, project timelines, and overall output. Analyzing these metrics allows businesses to identify trends, allocate resources effectively, and implement targeted interventions to optimize productivity in a hybrid work setting.
Hybrid work analytics, powered by tools like Power BI, empower organizations to navigate the complexities of a dispersed workforce. By examining engagement levels, collaboration dynamics, productivity metrics, attendance patterns, and technology infrastructure, businesses can make informed decisions that foster a successful and adaptive hybrid work environment. As organizations continue to refine their hybrid work strategies, the insights derived from these analytics become instrumental in shaping policies, enhancing employee experiences, and driving long-term success in the new era of work.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the advent of hybrid work has ushered in a transformative era for organizations, necessitating innovative approaches to collaboration, decision-making, and data analysis. Power BI, as a dynamic business intelligence platform, emerges as a linchpin in navigating the complexities of this evolving work paradigm. From facilitating collaborative reporting and ensuring data accessibility to enhancing security measures and customizing workflows, Power BI proves itself as a versatile tool aligned with the demands of hybrid teams.
The collaborative reporting features of Power BI provide a real-time, interactive platform for teams, fostering a shared understanding of data and facilitating informed decision-making across dispersed work environments. As teams seamlessly transition between in-office and remote settings, the adaptability and accessibility of Power BI become critical, ensuring that decision-makers have real-time insights at their fingertips, regardless of their physical location.
In the ever-evolving landscape of hybrid work, Power BI stands as a catalyst for driving efficiency, collaboration, and data-driven decision-making. As organizations continue to refine their approaches to hybrid work, Power BI's role as a central hub for business intelligence becomes increasingly pivotal. Through collaborative reporting, robust security, customization options, and analytics, Power BI empowers organizations to thrive in the new era of work, where flexibility, data accessibility, and actionable insights are key to success.
Read More
As the dynamics of the modern workplace continue to evolve, the concept of a hybrid work environment has become a cornerstone of organizational flexibility. With teams dispersed across various locations, the need for effective collaboration and data-driven decision-making has never been more critical. In this transformative landscape, Microsoft's Power BI emerges as a catalyst for organizations navigating the complexities of hybrid work environments. Its versatile suite of tools and cloud-powered capabilities are uniquely suited to meet the demands of a workforce that seamlessly blends in-person and remote collaboration.
The essence of hybrid work lies in striking a delicate balance between accessibility and collaboration, and Power BI is at the forefront of facilitating this equilibrium. This introduction delves into the ways in which Power BI serves as a linchpin for businesses seeking to harness the power of data analytics and visualization in a landscape where the boundaries between physical and virtual workspaces blur. From ensuring real-time insights to fostering collaborative decision-making, Power BI is poised to redefine how organizations thrive in the era of hybrid work.
As we explore the multifaceted role of Power BI in this paradigm shift, it becomes evident that the platform's adaptability extends beyond traditional business intelligence. It becomes an enabler of seamless communication, a guardian of data security in a distributed landscape, and a catalyst for innovation. Join us on this journey as we unravel the transformative impact of Power BI in hybrid work environments, where connectivity, collaboration, and insightful decision-making converge to shape the future of work.
Table of contents
-
Collaborative Reporting in Power BI
-
Data Accessibility in Hybrid Work
-
Effective Data Communication in Virtual Teams
-
Power BI Mobile App for On-the-Go Insights
-
Security Measures in Power BI for Remote Work
-
Customizing Power BI for Hybrid Team Workflows
-
Hybrid Work Analytics
-
Conclusion
Collaborative Reporting in Power BI
In the ever-evolving landscape of hybrid work environments, effective collaboration is paramount to the success of dispersed teams. Collaborative reporting in Power BI emerges as a key facet in fostering teamwork and ensuring that decision-makers, whether working in the office or remotely, can collectively engage with and derive insights from shared data. Power BI's robust features for collaboration extend beyond traditional reporting tools, allowing teams to seamlessly interact with reports, provide feedback, and make informed decisions collectively.
Power BI's sharing and collaboration functionalities empower users to distribute reports effortlessly among team members, irrespective of their physical location. With the ability to create workspaces and share dashboards securely, Power BI facilitates a collaborative ecosystem where stakeholders can access real-time data insights and contribute their perspectives. This feature proves invaluable in hybrid work scenarios, where fluid communication and shared understanding are vital components of successful decision-making.
As organizations navigate the intricacies of hybrid work, the collaborative reporting capabilities of Power BI become a linchpin for maintaining a unified approach to data analysis. Through interactive dashboards and shared insights, Power BI not only facilitates collaboration but also enhances the agility of decision-making processes. The platform empowers teams to adapt quickly to changing circumstances, leveraging the collective intelligence of dispersed team members to drive business success in the dynamic landscape of the modern workplace.
Data Accessibility in Hybrid Work
Ensuring seamless data accessibility is a cornerstone in the successful implementation of hybrid work environments, where employees operate from various locations. In this context, Power BI plays a pivotal role in bridging the geographical gaps and providing consistent access to critical data. The platform's cloud-based architecture significantly contributes to breaking down traditional barriers, ensuring that both in-office and remote team members have equal and secure access to the data they need.
Power BI's cloud integration transforms it into a dynamic and accessible hub for business intelligence. This adaptability is particularly crucial in hybrid work scenarios, where employees may switch between working in the office and remotely. With Power BI, data becomes platform-agnostic, allowing users to access reports and dashboards from virtually any device with an internet connection. This flexibility not only enhances the mobility of the workforce but also aligns seamlessly with the fluid nature of hybrid work schedules.
Security, another critical aspect of data accessibility, is addressed through Power BI's robust measures. With data encryption, role-based access controls, and compliance certifications, Power BI ensures that sensitive information remains protected. This not only instills confidence in users but also aligns with the stringent data security requirements inherent in hybrid work environments.
Power BI's role in ensuring data accessibility in hybrid work environments is transformative. By leveraging the cloud and real-time capabilities, the platform transcends physical constraints, providing a unified experience for teams irrespective of where they work. This adaptability positions Power BI as a cornerstone for organizations striving to maintain consistent, secure, and accessible data in the era of hybrid work.
Effective Data Communication in Virtual Teams
Effective data communication is a cornerstone of success in virtual teams, where the ability to convey complex information clearly and engagingly becomes paramount. In this context, Power BI emerges as a powerful tool to facilitate impactful data communication, transcending the challenges of virtual collaboration. The platform's features not only enable the creation of visually compelling reports but also offer tools for collaborative interpretation, ensuring that virtual teams can derive meaningful insights collectively.
Power BI's visual storytelling capabilities play a pivotal role in enhancing data communication within virtual teams. Through a diverse array of customizable charts, graphs, and dashboards, complex datasets can be transformed into visually intuitive representations. This not only simplifies the understanding of intricate data but also makes it more engaging for team members. Whether presenting in a virtual meeting or sharing reports asynchronously, Power BI's visual elements enhance comprehension and retention.
Collaborative interpretation is another dimension where Power BI excels in the realm of virtual teamwork. The platform allows team members to interact with reports in real-time, encouraging discussions and data-driven conversations. Commenting features enable stakeholders to provide insights, ask questions, and offer feedback directly within the reports. This real-time collaboration fosters a sense of shared understanding, replicating the dynamic discussions that would typically occur in a physical workspace.
Power BI Mobile App for On-the-Go Insights
In the dynamic landscape of modern work, the ability to access crucial insights on-the-go has become a cornerstone of operational efficiency. Power BI, Microsoft's powerful business intelligence platform, addresses this need with its feature-rich mobile application, designed to empower users with real-time data access and analytics regardless of their location. The Power BI mobile app serves as a catalyst for seamless decision-making, offering a personalized and intuitive experience that extends the power of data analytics beyond the confines of the office.
One of the defining features of the Power BI mobile app is its adaptability to various devices, including smartphones and tablets. This ensures that decision-makers can carry a wealth of information in their pockets, enabling them to stay connected with key metrics, reports, and dashboards wherever they are. The responsive design of the app optimizes the user experience, allowing for easy navigation and interaction with data visualizations even on smaller screens.
The real-time synchronization capabilities of the Power BI mobile app elevate its utility for professionals on the move. As data is updated in the main Power BI service, the mobile app reflects these changes instantaneously. This ensures that users are always working with the most current information, enhancing the reliability of insights derived while away from the office.
Security is a paramount consideration for mobile business intelligence, and the Power BI mobile app addresses this concern comprehensively. With features such as multi-factor authentication, data encryption, and secure sign-in, the app ensures that sensitive business information remains protected, aligning with the stringent security standards required in today's mobile work environment.
As organizations embrace the flexibility of on-the-go work, the Power BI mobile app emerges as an indispensable tool for professionals seeking to stay connected with their data and analytics. By offering a seamless and secure mobile experience, Power BI empowers decision-makers to make informed choices wherever they may be, revolutionizing the concept of business intelligence in the era of mobile work.
Security Measures in Power BI for Remote Work
In the era of remote work, where data is accessed and shared across diverse locations, ensuring the security of sensitive information has become a paramount concern. Power BI, Microsoft's business intelligence platform, incorporates a robust set of security measures designed to fortify data integrity and confidentiality in the context of remote work environments. These measures encompass a multifaceted approach, addressing encryption, access controls, and compliance standards, providing organizations with the assurance needed to navigate the unique security challenges associated with distributed work settings.
Power BI's role-based access controls (RBAC) offer a granular and flexible approach to managing user permissions. In the context of remote work, where employees access data from various locations, RBAC ensures that only authorized individuals have access to specific reports, dashboards, or datasets. This tailored approach to access management adds a layer of security that is essential in preventing unauthorized access to sensitive business intelligence.
Multi-Factor Authentication (MFA) further enhances the security of remote access to Power BI. By requiring users to provide multiple forms of identification—such as a password combined with a temporary code sent to a mobile device—MFA adds an additional layer of protection against unauthorized access. Particularly in remote work scenarios, where the risk of unauthorized access may be heightened, MFA becomes a crucial safeguard for securing user accounts.
Power BI's commitment to compliance is evident through its adherence to industry-specific standards. Certifications such as ISO/IEC 27001 and SOC 2 attest to Power BI's rigorous adherence to data security and governance protocols. For organizations navigating the regulatory landscape of remote work, these certifications provide confidence that Power BI maintains the highest standards of compliance.
In the dynamic landscape of remote work, where collaboration and data accessibility are imperative, Power BI's security measures provide a robust foundation for organizations. By addressing encryption, access controls, multi-factor authentication, and compliance standards, Power BI not only ensures the secure handling of sensitive information but also empowers remote teams to leverage business intelligence tools with confidence in the integrity and confidentiality of their data.
Customizing Power BI for Hybrid Team Workflows
In the evolving landscape of hybrid work, where teams seamlessly transition between in-office and remote settings, the ability to customize tools to align with unique workflows becomes pivotal. Power BI, Microsoft's versatile business intelligence platform, offers organizations the flexibility to tailor its features, making it an ideal companion for hybrid team workflows. Customization in Power BI extends beyond the creation of insightful reports and dashboards; it enables organizations to adapt the platform to the specific needs and collaborative dynamics of their hybrid teams.
One notable aspect of customizing Power BI for hybrid team workflows is the ability to create personalized dashboards and reports that cater to the diverse requirements of team members. By allowing customization based on roles, preferences, and specific KPIs, Power BI empowers organizations to provide a tailored analytics experience. This level of adaptability ensures that each team member, regardless of their location or role, can access the data most relevant to their responsibilities.
The integration of Power BI with other collaborative tools, such as Microsoft Teams, further enhances customization possibilities. Organizations can embed Power BI reports directly into Teams channels, fostering a cohesive and centralized virtual workspace for hybrid teams. This integration not only streamlines access to critical data but also promotes a collaborative environment where team members can seamlessly transition between discussions and data analysis.
Customized workflows in Power BI also extend to the establishment of automated processes and alerts. Organizations can set up custom alerts based on specific thresholds or changes in data, ensuring that remote and in-office team members are promptly notified of critical developments. This proactive approach enhances real-time decision-making and fosters a responsive environment conducive to the dynamic nature of hybrid work.
Power BI's APIs and extensibility options open avenues for organizations to integrate the platform into their existing applications and workflows. This level of customization allows for a seamless integration of Power BI into the broader technology ecosystem, aligning business intelligence processes with the overarching goals and workflows of hybrid teams.
As organizations navigate the complexities of hybrid work, customizing Power BI emerges as a strategic initiative to optimize workflows and enhance collaboration. The platform's adaptability to unique team dynamics, coupled with integrations and automation capabilities, positions Power BI as a dynamic tool that not only analyzes data but becomes an integral part of how hybrid teams operate, collaborate, and make informed decisions.
Hybrid Work Analytics
In the era of hybrid work, organizations are increasingly turning to analytics to gain valuable insights into the dynamics of their dispersed teams. Hybrid work analytics, facilitated by tools such as Power BI, play a pivotal role in helping businesses understand, measure, and optimize the effectiveness of their hybrid work models. These analytics delve into various aspects of employee engagement, collaboration patterns, and productivity metrics, providing organizations with data-driven insights to navigate the nuances of this evolving work paradigm.
One crucial dimension of hybrid work analytics is the examination of employee engagement. Through the analysis of collaboration tools, communication platforms, and workflow patterns, organizations can gauge the level of engagement among remote and in-office team members. These insights empower leaders to identify trends, address potential challenges, and implement strategies to foster a cohesive and engaged workforce across different work settings.
Collaboration analytics within hybrid work environments offer a closer look at how teams interact and share information. By leveraging data from collaboration tools integrated with Power BI, organizations can assess the frequency and modes of communication, uncover collaboration bottlenecks, and identify opportunities for enhancing teamwork. This granular understanding contributes to creating strategies that promote effective collaboration, irrespective of physical locations.
Productivity metrics form another critical component of hybrid work analytics. Organizations can utilize Power BI to track key performance indicators (KPIs) related to individual and team productivity. This includes metrics such as task completion rates, project timelines, and overall output. Analyzing these metrics allows businesses to identify trends, allocate resources effectively, and implement targeted interventions to optimize productivity in a hybrid work setting.
Hybrid work analytics, powered by tools like Power BI, empower organizations to navigate the complexities of a dispersed workforce. By examining engagement levels, collaboration dynamics, productivity metrics, attendance patterns, and technology infrastructure, businesses can make informed decisions that foster a successful and adaptive hybrid work environment. As organizations continue to refine their hybrid work strategies, the insights derived from these analytics become instrumental in shaping policies, enhancing employee experiences, and driving long-term success in the new era of work.
How to obtain Data Science and Business Intelligence certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, the advent of hybrid work has ushered in a transformative era for organizations, necessitating innovative approaches to collaboration, decision-making, and data analysis. Power BI, as a dynamic business intelligence platform, emerges as a linchpin in navigating the complexities of this evolving work paradigm. From facilitating collaborative reporting and ensuring data accessibility to enhancing security measures and customizing workflows, Power BI proves itself as a versatile tool aligned with the demands of hybrid teams.
The collaborative reporting features of Power BI provide a real-time, interactive platform for teams, fostering a shared understanding of data and facilitating informed decision-making across dispersed work environments. As teams seamlessly transition between in-office and remote settings, the adaptability and accessibility of Power BI become critical, ensuring that decision-makers have real-time insights at their fingertips, regardless of their physical location.
In the ever-evolving landscape of hybrid work, Power BI stands as a catalyst for driving efficiency, collaboration, and data-driven decision-making. As organizations continue to refine their approaches to hybrid work, Power BI's role as a central hub for business intelligence becomes increasingly pivotal. Through collaborative reporting, robust security, customization options, and analytics, Power BI empowers organizations to thrive in the new era of work, where flexibility, data accessibility, and actionable insights are key to success.
DevOps for Networking: NetOps Best Practices
"DevOps for Networking: NetOps Best Practices" introduces a transformative approach to managing and optimizing network operations through the integration of DevOps principles. In today's dynamic and ever-evolving technological landscape, the intersection of Development (Dev) and Operations (Ops) has proven to be a game-changer in software development, and now it is extending its influence to networking.
This comprehensive guide delves into the emerging discipline of Network Operations (NetOps) within the broader DevOps framework. It explores the synergy between development and network operations, emphasizing collaboration, automation, and continuous improvement. By adopting NetOps best practices, organizations can enhance the agility, scalability, and reliability of their network infrastructure.
The book covers key concepts such as infrastructure as code (IaC), version control for network configurations, automated testing, and continuous integration/continuous deployment (CI/CD) for networking. It provides real-world examples, case studies, and practical insights that empower network professionals to streamline workflows, reduce manual errors, and respond more efficiently to the evolving demands of their IT environments.
Whether you're a seasoned network engineer looking to stay ahead of industry trends or a DevOps enthusiast aiming to extend these principles to networking, "DevOps for Networking: NetOps Best Practices" offers a roadmap for successfully implementing and optimizing NetOps strategies. From fostering collaboration between development and operations teams to implementing automation across the network lifecycle, this book equips readers with the knowledge and tools needed to revolutionize network management in the era of DevOps.
Table of contents
-
Introduction to NetOps and DevOps
-
Collaborative Culture and Communication in NetOps
-
Infrastructure as Code (IaC) for Networking
-
Automated Testing in NetOps
-
Network Monitoring and Observability
-
Security in NetOps
-
Scalability and Resilience in Network Automation
-
Conclusion
Introduction to NetOps and DevOps
The introduction to NetOps and DevOps marks the commencement of a transformative journey in network management, where the fusion of Network Operations (NetOps) and Development Operations (DevOps) promises to reshape the landscape of IT infrastructure. NetOps, within the broader framework of DevOps, embodies a paradigm shift in the way networks are conceived, built, and operated. Unlike traditional approaches that often siloed development and operations teams, NetOps emphasizes collaboration, communication, and shared responsibility across these functions.
NetOps inherits the core principles of DevOps, adapting them to the unique challenges posed by network infrastructure. The central tenets of agility, automation, and continuous improvement form the cornerstone of NetOps, empowering organizations to respond swiftly to evolving business requirements and technological advancements. This introduction aims to unravel the symbiotic relationship between NetOps and DevOps, shedding light on their shared objectives of enhancing efficiency, reducing manual intervention, and fostering a culture of innovation within the realm of network management.
As we embark on this exploration, it becomes evident that the historical evolution of NetOps is deeply intertwined with the rise of DevOps. The convergence of these disciplines is not merely a trend but a strategic response to the increasing complexity and dynamism of modern IT environments. By understanding the roots of NetOps within the broader DevOps narrative, organizations gain insights into the principles that underpin successful implementations and the cultural shifts necessary to maximize the benefits of this holistic approach to network operations.
Collaborative Culture and Communication in NetOps
The success of NetOps hinges significantly on fostering a collaborative culture and establishing effective communication channels within organizations. Unlike traditional models where development and operations teams often operated in isolation, the NetOps paradigm advocates for a unified approach, emphasizing shared goals and responsibilities. In this context, the establishment of a collaborative culture becomes paramount, transcending departmental boundaries and fostering a sense of collective ownership.
Building effective collaboration in NetOps entails breaking down silos and encouraging cross-functional teams. By promoting open communication channels and shared forums, organizations can bridge the historical gap between developers and operations professionals. This collaborative culture is underpinned by a mindset that values the contributions of both development and operations, recognizing that each plays a crucial role in the success of network operations.
Communication strategies form the bedrock of collaborative NetOps cultures. Clear and transparent communication channels enable teams to share insights, coordinate efforts, and troubleshoot issues more effectively. Regular meetings, joint planning sessions, and collaborative tools facilitate the exchange of ideas, ensuring that all team members are aligned with the overarching objectives. Additionally, embracing a culture of continuous feedback fosters an environment of continuous improvement, allowing teams to adapt swiftly to changing requirements and emerging challenges.
Infrastructure as Code (IaC) for Networking
The paradigm of Infrastructure as Code (IaC) has emerged as a transformative force in the realm of network management, redefining how organizations conceptualize, deploy, and manage their network infrastructure. In the context of NetOps, IaC represents a departure from traditional, manual configuration approaches toward a more automated, programmable model.
At its core, IaC involves representing and managing infrastructure configurations through machine-readable script files rather than manual processes. This shift brings numerous advantages to network operations, including increased efficiency, consistency, and scalability. In the context of networking, IaC enables organizations to define and provision network resources, such as routers, switches, and firewalls, in a reproducible and automated manner.
The implementation of IaC for networking involves leveraging declarative or imperative scripts that codify the desired state of the network. Declarative IaC describes the desired outcome without specifying the step-by-step process, allowing the system to determine the most efficient way to achieve the desired state. Imperative IaC, on the other hand, provides specific instructions on how to reach the desired state, offering more control over the configuration process.
Tools like Ansible, Terraform, and Puppet have become integral to the IaC ecosystem, providing network professionals with the means to express, version, and manage network configurations in a manner similar to software development. Version control systems further enhance the IaC workflow by enabling the tracking of changes, collaboration among team members, and the ability to roll back to previous configurations if needed.
The benefits of adopting IaC in NetOps extend beyond efficiency gains. By treating network configurations as code, organizations can enforce versioning, documentation, and collaboration standards that contribute to the overall reliability and maintainability of the network infrastructure. IaC not only accelerates the deployment of network changes but also facilitates better collaboration between development and operations teams, aligning network management with the principles of agility and automation inherent in the broader DevOps philosophy. In the rapidly evolving landscape of network operations, IaC stands as a key enabler for organizations seeking to achieve greater agility, scalability, and reliability in their network infrastructure.
Automated Testing in NetOps
Automated testing is a cornerstone of modern NetOps practices, revolutionizing the way network configurations are validated and ensuring the reliability, security, and performance of network infrastructure. In the dynamic and complex realm of networking, where changes are frequent and the potential impact of errors is significant, automated testing plays a crucial role in mitigating risks and enhancing operational efficiency.
The importance of automated testing in NetOps is underscored by its ability to systematically verify network configurations against predefined criteria. This process helps identify errors, inconsistencies, or vulnerabilities in a timely and consistent manner, reducing the likelihood of manual errors and minimizing the risk of network disruptions. Automated testing is particularly valuable in the context of continuous integration and continuous deployment (CI/CD), where rapid and frequent changes demand a robust validation mechanism.
Network Monitoring and Observability
In the dynamic landscape of network operations (NetOps), effective network monitoring and observability emerge as critical pillars for maintaining optimal performance, identifying issues, and ensuring a seamless end-user experience. Network monitoring involves the systematic collection and analysis of data related to the performance and health of the network, while observability extends this concept by emphasizing the depth of insights into the network's internal state and behavior.
Strategies for network monitoring in NetOps encompass the continuous tracking of key performance indicators (KPIs) such as bandwidth utilization, latency, packet loss, and device health. Monitoring tools provide real-time visibility into the network's status, enabling rapid detection of anomalies and proactive response to potential issues. By leveraging a combination of SNMP (Simple Network Management Protocol), flow data, and other monitoring protocols, NetOps teams gain a comprehensive view of the network's performance metrics.
Observability in NetOps takes monitoring a step further by emphasizing the holistic understanding of the network's internal dynamics. This involves not only tracking traditional metrics but also collecting and analyzing logs, traces, and other telemetry data. Observability tools, such as distributed tracing systems and log aggregators, provide a more nuanced view of network events, facilitating root cause analysis and troubleshooting in complex, distributed environments.
Network monitoring and observability are fundamental components of NetOps, providing the insights and real-time information needed to maintain a resilient and responsive network infrastructure. By leveraging advanced tools, protocols, and analytics, NetOps teams can not only identify and resolve issues swiftly but also gain a deeper understanding of the intricacies of their network, ultimately leading to more efficient and optimized network operations.
Security in NetOps
Security in NetOps is a paramount consideration in today's interconnected and rapidly evolving technological landscape. As network operations (NetOps) becomes more integrated with DevOps practices, ensuring the security of network infrastructure is essential to safeguard against potential threats and vulnerabilities. This holistic approach to security involves adopting proactive measures, implementing security best practices, and leveraging innovative technologies to protect network assets.
One key aspect of security in NetOps is integrating security practices into the development and deployment workflows. This includes conducting security assessments during the development phase, ensuring that security requirements are considered in the design of network architectures, and incorporating security testing into the continuous integration and continuous deployment (CI/CD) pipelines. By making security an integral part of the development process, NetOps teams can identify and address vulnerabilities early in the lifecycle, minimizing the risk of security breaches.
Implementing security policies as code is another crucial element of security in NetOps. This involves codifying security policies and configurations, making them part of the infrastructure-as-code (IaC) paradigm. By treating security policies as code, organizations can enforce consistent and auditable security controls across their network infrastructure. Automation plays a pivotal role in this process, ensuring that security policies are consistently applied and that any deviations are promptly identified and remediated.
Network segmentation and micro-segmentation are essential security strategies in NetOps. By dividing the network into isolated segments and applying access controls at a granular level, organizations can limit the lateral movement of potential attackers and contain security incidents. Micro-segmentation further refines this approach by restricting communication between individual workloads or devices, minimizing the attack surface and enhancing overall network security.
Continuous monitoring and threat intelligence are fundamental to the security posture of NetOps. Real-time monitoring of network traffic, log analysis, and the incorporation of threat intelligence feeds enable rapid detection of suspicious activities and potential security incidents. Security Information and Event Management (SIEM) solutions play a crucial role in aggregating and correlating security-related data, providing NetOps teams with the visibility needed to respond effectively to security threats.
Lastly, employee education and awareness are critical components of security in NetOps. Human factors remain a significant source of security vulnerabilities, and ensuring that personnel are well-informed about security best practices, social engineering threats, and the importance of adhering to security policies contributes to a more resilient security posture.
Security in NetOps is a multifaceted and evolving discipline that requires a proactive and integrated approach. By incorporating security into development processes, leveraging automation, implementing robust access controls, continuously monitoring for threats, and fostering a culture of security awareness, organizations can fortify their network infrastructure against a wide range of potential risks.
Scalability and Resilience in Network Automation
Scalability and resilience are critical considerations in the realm of network automation, where the ability to handle growth, dynamic workloads, and unexpected challenges is essential for maintaining optimal performance. Network automation, within the context of NetOps, seeks to streamline operations, enhance efficiency, and respond agilely to evolving demands. Achieving scalability and resilience in network automation involves strategic planning, robust architecture, and the integration of adaptive technologies.
Scalability in network automation is about designing systems and processes that can grow seamlessly to accommodate increasing demands. This involves creating automation workflows and scripts that are modular, flexible, and capable of handling a growing number of devices, configurations, or tasks. As network infrastructures expand, scalable automation ensures that the management and orchestration of network resources can keep pace without sacrificing performance or reliability.
The use of infrastructure as code (IaC) is instrumental in achieving scalability in network automation. By defining network configurations in code, organizations can easily replicate and scale their infrastructure to meet evolving requirements. Automation tools, such as Ansible, Puppet, or Terraform, play a crucial role in deploying and managing configurations consistently across a large number of devices, promoting scalability while minimizing manual intervention.
Resilience, on the other hand, focuses on the network's ability to maintain operational integrity in the face of disruptions, failures, or unexpected events. Resilient network automation involves implementing failover mechanisms, backup strategies, and proactive measures to ensure that automated processes can recover gracefully from unforeseen issues. Redundancy in critical components and the ability to detect and respond to failures in real-time contribute to the overall resilience of automated network systems.
The adoption of self-healing mechanisms further enhances the resilience of network automation. Automated processes that can detect and automatically remediate issues without human intervention contribute to the overall robustness of the network. This might include automated rollback mechanisms in case of failed changes, predictive analytics to identify potential issues before they escalate, and automated recovery procedures in response to network failures.
Achieving scalability and resilience in network automation requires a holistic approach that encompasses flexible design principles, the use of scalable automation tools, proactive measures for resilience, and the continuous improvement of automated processes. By focusing on scalability and resilience, organizations can build network automation frameworks that not only meet current demands but also adapt and thrive in the face of future challenges and growth.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "DevOps for Networking: NetOps Best Practices" represents a transformative guide to revolutionize network management through the integration of DevOps principles. Throughout this exploration, we've delved into crucial facets of NetOps, from collaborative culture and communication strategies to embracing infrastructure as code (IaC) for networking. The discussion extended to the significance of automated testing, network monitoring, and observability, all essential components in fostering an agile and responsive network infrastructure.
Security emerged as a paramount concern, emphasizing the integration of security practices into NetOps workflows, the implementation of security policies as code, and the adoption of network segmentation strategies. Finally, we addressed the pivotal aspects of scalability and resilience in network automation, highlighting the importance of scalable design principles, self-healing mechanisms, and the continuous improvement of automated processes.
As organizations navigate the complexities of modern network operations, embracing the principles outlined in this guide empowers them to streamline workflows, enhance collaboration, and fortify their network infrastructure. The fusion of NetOps and DevOps principles not only addresses the challenges posed by today's dynamic IT environments but also positions organizations to adapt and thrive in the ever-evolving landscape of network management. By implementing these best practices, organizations can foster a culture of innovation, ensuring that their NetOps strategies remain agile, scalable, and resilient in the face of ongoing technological advancements.
Read More
"DevOps for Networking: NetOps Best Practices" introduces a transformative approach to managing and optimizing network operations through the integration of DevOps principles. In today's dynamic and ever-evolving technological landscape, the intersection of Development (Dev) and Operations (Ops) has proven to be a game-changer in software development, and now it is extending its influence to networking.
This comprehensive guide delves into the emerging discipline of Network Operations (NetOps) within the broader DevOps framework. It explores the synergy between development and network operations, emphasizing collaboration, automation, and continuous improvement. By adopting NetOps best practices, organizations can enhance the agility, scalability, and reliability of their network infrastructure.
The book covers key concepts such as infrastructure as code (IaC), version control for network configurations, automated testing, and continuous integration/continuous deployment (CI/CD) for networking. It provides real-world examples, case studies, and practical insights that empower network professionals to streamline workflows, reduce manual errors, and respond more efficiently to the evolving demands of their IT environments.
Whether you're a seasoned network engineer looking to stay ahead of industry trends or a DevOps enthusiast aiming to extend these principles to networking, "DevOps for Networking: NetOps Best Practices" offers a roadmap for successfully implementing and optimizing NetOps strategies. From fostering collaboration between development and operations teams to implementing automation across the network lifecycle, this book equips readers with the knowledge and tools needed to revolutionize network management in the era of DevOps.
Table of contents
-
Introduction to NetOps and DevOps
-
Collaborative Culture and Communication in NetOps
-
Infrastructure as Code (IaC) for Networking
-
Automated Testing in NetOps
-
Network Monitoring and Observability
-
Security in NetOps
-
Scalability and Resilience in Network Automation
-
Conclusion
Introduction to NetOps and DevOps
The introduction to NetOps and DevOps marks the commencement of a transformative journey in network management, where the fusion of Network Operations (NetOps) and Development Operations (DevOps) promises to reshape the landscape of IT infrastructure. NetOps, within the broader framework of DevOps, embodies a paradigm shift in the way networks are conceived, built, and operated. Unlike traditional approaches that often siloed development and operations teams, NetOps emphasizes collaboration, communication, and shared responsibility across these functions.
NetOps inherits the core principles of DevOps, adapting them to the unique challenges posed by network infrastructure. The central tenets of agility, automation, and continuous improvement form the cornerstone of NetOps, empowering organizations to respond swiftly to evolving business requirements and technological advancements. This introduction aims to unravel the symbiotic relationship between NetOps and DevOps, shedding light on their shared objectives of enhancing efficiency, reducing manual intervention, and fostering a culture of innovation within the realm of network management.
As we embark on this exploration, it becomes evident that the historical evolution of NetOps is deeply intertwined with the rise of DevOps. The convergence of these disciplines is not merely a trend but a strategic response to the increasing complexity and dynamism of modern IT environments. By understanding the roots of NetOps within the broader DevOps narrative, organizations gain insights into the principles that underpin successful implementations and the cultural shifts necessary to maximize the benefits of this holistic approach to network operations.
Collaborative Culture and Communication in NetOps
The success of NetOps hinges significantly on fostering a collaborative culture and establishing effective communication channels within organizations. Unlike traditional models where development and operations teams often operated in isolation, the NetOps paradigm advocates for a unified approach, emphasizing shared goals and responsibilities. In this context, the establishment of a collaborative culture becomes paramount, transcending departmental boundaries and fostering a sense of collective ownership.
Building effective collaboration in NetOps entails breaking down silos and encouraging cross-functional teams. By promoting open communication channels and shared forums, organizations can bridge the historical gap between developers and operations professionals. This collaborative culture is underpinned by a mindset that values the contributions of both development and operations, recognizing that each plays a crucial role in the success of network operations.
Communication strategies form the bedrock of collaborative NetOps cultures. Clear and transparent communication channels enable teams to share insights, coordinate efforts, and troubleshoot issues more effectively. Regular meetings, joint planning sessions, and collaborative tools facilitate the exchange of ideas, ensuring that all team members are aligned with the overarching objectives. Additionally, embracing a culture of continuous feedback fosters an environment of continuous improvement, allowing teams to adapt swiftly to changing requirements and emerging challenges.
Infrastructure as Code (IaC) for Networking
The paradigm of Infrastructure as Code (IaC) has emerged as a transformative force in the realm of network management, redefining how organizations conceptualize, deploy, and manage their network infrastructure. In the context of NetOps, IaC represents a departure from traditional, manual configuration approaches toward a more automated, programmable model.
At its core, IaC involves representing and managing infrastructure configurations through machine-readable script files rather than manual processes. This shift brings numerous advantages to network operations, including increased efficiency, consistency, and scalability. In the context of networking, IaC enables organizations to define and provision network resources, such as routers, switches, and firewalls, in a reproducible and automated manner.
The implementation of IaC for networking involves leveraging declarative or imperative scripts that codify the desired state of the network. Declarative IaC describes the desired outcome without specifying the step-by-step process, allowing the system to determine the most efficient way to achieve the desired state. Imperative IaC, on the other hand, provides specific instructions on how to reach the desired state, offering more control over the configuration process.
Tools like Ansible, Terraform, and Puppet have become integral to the IaC ecosystem, providing network professionals with the means to express, version, and manage network configurations in a manner similar to software development. Version control systems further enhance the IaC workflow by enabling the tracking of changes, collaboration among team members, and the ability to roll back to previous configurations if needed.
The benefits of adopting IaC in NetOps extend beyond efficiency gains. By treating network configurations as code, organizations can enforce versioning, documentation, and collaboration standards that contribute to the overall reliability and maintainability of the network infrastructure. IaC not only accelerates the deployment of network changes but also facilitates better collaboration between development and operations teams, aligning network management with the principles of agility and automation inherent in the broader DevOps philosophy. In the rapidly evolving landscape of network operations, IaC stands as a key enabler for organizations seeking to achieve greater agility, scalability, and reliability in their network infrastructure.
Automated Testing in NetOps
Automated testing is a cornerstone of modern NetOps practices, revolutionizing the way network configurations are validated and ensuring the reliability, security, and performance of network infrastructure. In the dynamic and complex realm of networking, where changes are frequent and the potential impact of errors is significant, automated testing plays a crucial role in mitigating risks and enhancing operational efficiency.
The importance of automated testing in NetOps is underscored by its ability to systematically verify network configurations against predefined criteria. This process helps identify errors, inconsistencies, or vulnerabilities in a timely and consistent manner, reducing the likelihood of manual errors and minimizing the risk of network disruptions. Automated testing is particularly valuable in the context of continuous integration and continuous deployment (CI/CD), where rapid and frequent changes demand a robust validation mechanism.
Network Monitoring and Observability
In the dynamic landscape of network operations (NetOps), effective network monitoring and observability emerge as critical pillars for maintaining optimal performance, identifying issues, and ensuring a seamless end-user experience. Network monitoring involves the systematic collection and analysis of data related to the performance and health of the network, while observability extends this concept by emphasizing the depth of insights into the network's internal state and behavior.
Strategies for network monitoring in NetOps encompass the continuous tracking of key performance indicators (KPIs) such as bandwidth utilization, latency, packet loss, and device health. Monitoring tools provide real-time visibility into the network's status, enabling rapid detection of anomalies and proactive response to potential issues. By leveraging a combination of SNMP (Simple Network Management Protocol), flow data, and other monitoring protocols, NetOps teams gain a comprehensive view of the network's performance metrics.
Observability in NetOps takes monitoring a step further by emphasizing the holistic understanding of the network's internal dynamics. This involves not only tracking traditional metrics but also collecting and analyzing logs, traces, and other telemetry data. Observability tools, such as distributed tracing systems and log aggregators, provide a more nuanced view of network events, facilitating root cause analysis and troubleshooting in complex, distributed environments.
Network monitoring and observability are fundamental components of NetOps, providing the insights and real-time information needed to maintain a resilient and responsive network infrastructure. By leveraging advanced tools, protocols, and analytics, NetOps teams can not only identify and resolve issues swiftly but also gain a deeper understanding of the intricacies of their network, ultimately leading to more efficient and optimized network operations.
Security in NetOps
Security in NetOps is a paramount consideration in today's interconnected and rapidly evolving technological landscape. As network operations (NetOps) becomes more integrated with DevOps practices, ensuring the security of network infrastructure is essential to safeguard against potential threats and vulnerabilities. This holistic approach to security involves adopting proactive measures, implementing security best practices, and leveraging innovative technologies to protect network assets.
One key aspect of security in NetOps is integrating security practices into the development and deployment workflows. This includes conducting security assessments during the development phase, ensuring that security requirements are considered in the design of network architectures, and incorporating security testing into the continuous integration and continuous deployment (CI/CD) pipelines. By making security an integral part of the development process, NetOps teams can identify and address vulnerabilities early in the lifecycle, minimizing the risk of security breaches.
Implementing security policies as code is another crucial element of security in NetOps. This involves codifying security policies and configurations, making them part of the infrastructure-as-code (IaC) paradigm. By treating security policies as code, organizations can enforce consistent and auditable security controls across their network infrastructure. Automation plays a pivotal role in this process, ensuring that security policies are consistently applied and that any deviations are promptly identified and remediated.
Network segmentation and micro-segmentation are essential security strategies in NetOps. By dividing the network into isolated segments and applying access controls at a granular level, organizations can limit the lateral movement of potential attackers and contain security incidents. Micro-segmentation further refines this approach by restricting communication between individual workloads or devices, minimizing the attack surface and enhancing overall network security.
Continuous monitoring and threat intelligence are fundamental to the security posture of NetOps. Real-time monitoring of network traffic, log analysis, and the incorporation of threat intelligence feeds enable rapid detection of suspicious activities and potential security incidents. Security Information and Event Management (SIEM) solutions play a crucial role in aggregating and correlating security-related data, providing NetOps teams with the visibility needed to respond effectively to security threats.
Lastly, employee education and awareness are critical components of security in NetOps. Human factors remain a significant source of security vulnerabilities, and ensuring that personnel are well-informed about security best practices, social engineering threats, and the importance of adhering to security policies contributes to a more resilient security posture.
Security in NetOps is a multifaceted and evolving discipline that requires a proactive and integrated approach. By incorporating security into development processes, leveraging automation, implementing robust access controls, continuously monitoring for threats, and fostering a culture of security awareness, organizations can fortify their network infrastructure against a wide range of potential risks.
Scalability and Resilience in Network Automation
Scalability and resilience are critical considerations in the realm of network automation, where the ability to handle growth, dynamic workloads, and unexpected challenges is essential for maintaining optimal performance. Network automation, within the context of NetOps, seeks to streamline operations, enhance efficiency, and respond agilely to evolving demands. Achieving scalability and resilience in network automation involves strategic planning, robust architecture, and the integration of adaptive technologies.
Scalability in network automation is about designing systems and processes that can grow seamlessly to accommodate increasing demands. This involves creating automation workflows and scripts that are modular, flexible, and capable of handling a growing number of devices, configurations, or tasks. As network infrastructures expand, scalable automation ensures that the management and orchestration of network resources can keep pace without sacrificing performance or reliability.
The use of infrastructure as code (IaC) is instrumental in achieving scalability in network automation. By defining network configurations in code, organizations can easily replicate and scale their infrastructure to meet evolving requirements. Automation tools, such as Ansible, Puppet, or Terraform, play a crucial role in deploying and managing configurations consistently across a large number of devices, promoting scalability while minimizing manual intervention.
Resilience, on the other hand, focuses on the network's ability to maintain operational integrity in the face of disruptions, failures, or unexpected events. Resilient network automation involves implementing failover mechanisms, backup strategies, and proactive measures to ensure that automated processes can recover gracefully from unforeseen issues. Redundancy in critical components and the ability to detect and respond to failures in real-time contribute to the overall resilience of automated network systems.
The adoption of self-healing mechanisms further enhances the resilience of network automation. Automated processes that can detect and automatically remediate issues without human intervention contribute to the overall robustness of the network. This might include automated rollback mechanisms in case of failed changes, predictive analytics to identify potential issues before they escalate, and automated recovery procedures in response to network failures.
Achieving scalability and resilience in network automation requires a holistic approach that encompasses flexible design principles, the use of scalable automation tools, proactive measures for resilience, and the continuous improvement of automated processes. By focusing on scalability and resilience, organizations can build network automation frameworks that not only meet current demands but also adapt and thrive in the face of future challenges and growth.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, "DevOps for Networking: NetOps Best Practices" represents a transformative guide to revolutionize network management through the integration of DevOps principles. Throughout this exploration, we've delved into crucial facets of NetOps, from collaborative culture and communication strategies to embracing infrastructure as code (IaC) for networking. The discussion extended to the significance of automated testing, network monitoring, and observability, all essential components in fostering an agile and responsive network infrastructure.
Security emerged as a paramount concern, emphasizing the integration of security practices into NetOps workflows, the implementation of security policies as code, and the adoption of network segmentation strategies. Finally, we addressed the pivotal aspects of scalability and resilience in network automation, highlighting the importance of scalable design principles, self-healing mechanisms, and the continuous improvement of automated processes.
As organizations navigate the complexities of modern network operations, embracing the principles outlined in this guide empowers them to streamline workflows, enhance collaboration, and fortify their network infrastructure. The fusion of NetOps and DevOps principles not only addresses the challenges posed by today's dynamic IT environments but also positions organizations to adapt and thrive in the ever-evolving landscape of network management. By implementing these best practices, organizations can foster a culture of innovation, ensuring that their NetOps strategies remain agile, scalable, and resilient in the face of ongoing technological advancements.
Salesforce DX (Developer Experience) Updates
Salesforce DX (Developer Experience) has emerged as a pivotal framework within the Salesforce ecosystem, revolutionizing the way developers build and deploy applications on the Salesforce platform. With the relentless pace of technological advancement and the increasing complexity of business requirements, Salesforce DX serves as a cornerstone for empowering developers with a modern and collaborative development environment. This framework goes beyond traditional development methodologies, fostering agility, efficiency, and innovation throughout the application development lifecycle.
The Salesforce DX updates encompass a diverse range of elements, including improvements to development tools, enhanced collaboration capabilities, and streamlined processes for continuous integration and delivery. These updates are designed to provide developers with the flexibility and scalability required to navigate the complexities of modern software development. By staying attuned to the latest Salesforce DX updates, developers can harness the full potential of the platform, enabling them to create robust, scalable, and innovative solutions that drive business success.
In this dynamic landscape of software development, understanding and leveraging Salesforce DX updates are crucial for developers aiming to optimize their workflows, enhance collaboration, and deliver high-quality solutions. This introduction sets the stage for a deeper exploration of the specific updates, innovations, and advancements that Salesforce DX brings to the table, underscoring its significance in shaping a superior developer experience within the Salesforce ecosystem.
Table of contents
-
Enhanced Development Tools
-
Collaboration Features
-
Continuous Integration and Delivery (CI/CD) Enhancements
-
Source Control Integration
-
Salesforce CLI (Command-Line Interface) Updates
-
DevOps Integration and Best Practices
-
Security and Compliance Features
-
Conclusion
Enhanced Development Tools
The realm of Salesforce DX (Developer Experience) has witnessed significant progress with the introduction of enhanced development tools. These tools play a pivotal role in shaping the daily workflows of developers, offering a more intuitive and efficient coding experience. One notable aspect of these updates involves improvements to the integrated development environment (IDE), where developers spend a substantial amount of their time crafting and refining code. The updated IDE provides a more user-friendly interface, streamlined navigation, and enhanced code suggestions, contributing to a more productive and enjoyable development process.
Code editors have also undergone refinements, aligning with the evolving needs of developers working within the Salesforce ecosystem. The updates in this domain often include features such as intelligent code completion, syntax highlighting, and real-time error checking. These improvements not only reduce the likelihood of coding errors but also accelerate the development cycle by providing immediate feedback to developers, allowing them to address issues swiftly.
The enhanced development tools introduced in Salesforce DX updates represent a concerted effort to elevate the overall developer experience. By focusing on the user interface, code editing capabilities, and debugging tools, these updates aim to make the development process more efficient, collaborative, and enjoyable for developers, thereby fostering innovation and excellence within the Salesforce development community.
Collaboration Features
Salesforce DX (Developer Experience) updates have introduced a suite of collaboration features that redefine the way development teams work together, emphasizing communication, coordination, and shared productivity. These updates aim to break down silos and enhance the overall collaborative experience for developers within the Salesforce ecosystem.
One significant facet of these collaboration features is the evolution of version control systems. Salesforce DX updates have strengthened the integration of version control, allowing developers to seamlessly collaborate on projects with a clear and organized history of changes. This not only streamlines collaboration but also promotes code consistency and facilitates the efficient resolution of conflicts in a shared codebase.
Real-time collaboration tools play a crucial role in fostering a sense of unity among developers. Whether through integrated chat systems, collaborative code reviews, or shared development environments, these features enable developers to work synchronously, share insights, and collectively contribute to the evolution of projects. Real-time collaboration tools eliminate the barriers that often arise in distributed teams, ensuring that developers can seamlessly communicate and collaborate regardless of geographical locations.
The collaboration features embedded in Salesforce DX updates reflect a commitment to creating a cohesive and efficient development environment. By addressing version control, real-time collaboration, and communication channels, these updates empower development teams to collaborate seamlessly, resulting in enhanced productivity, higher code quality, and a more enjoyable overall developer experience on the Salesforce platform.
Continuous Integration and Delivery (CI/CD) Enhancements
Salesforce DX (Developer Experience) updates have introduced noteworthy enhancements in the realm of Continuous Integration and Delivery (CI/CD), revolutionizing the way developers manage and deploy their applications. These updates are strategically designed to streamline development workflows, enhance automation, and ensure the consistent and reliable delivery of high-quality code.
One prominent aspect of CI/CD enhancements involves improvements in automation processes throughout the development lifecycle. Automation has been elevated to a new standard, with updates facilitating the seamless integration of automated testing, code analysis, and deployment procedures. This not only accelerates the development cycle but also minimizes the likelihood of human error, ensuring a more robust and error-resistant codebase.
The updates also focus on refining testing frameworks within the CI/CD pipeline. Developers can now leverage more advanced testing tools and methodologies to validate their code changes systematically. This includes comprehensive unit testing, integration testing, and end-to-end testing, contributing to the creation of more resilient and reliable applications. Additionally, updates in this domain often incorporate features that enable parallel testing, further expediting the testing phase of the development process.
The CI/CD enhancements introduced in Salesforce DX updates represent a commitment to advancing the efficiency and reliability of the development and deployment process. By focusing on automation, testing, and deployment strategies, these updates empower developers to deliver high-quality code at a faster pace, ultimately contributing to a more agile, responsive, and innovative development ecosystem on the Salesforce platform.
Source Control Integration
Source Control Integration is a pivotal aspect of Salesforce DX (Developer Experience) updates, playing a crucial role in shaping a more streamlined and collaborative development process. These updates emphasize the integration of robust version control systems, enabling developers to manage their source code efficiently, track changes systematically, and collaborate seamlessly within the Salesforce ecosystem.
One key focus of Source Control Integration in Salesforce DX updates is the facilitation of source-driven development. This approach emphasizes the use of source code as the foundation for development, allowing developers to work on their code locally and then synchronize changes with a version control system. This shift from a traditional metadata-centric approach enhances collaboration, reduces conflicts, and provides developers with greater control over their development environment.
Source Control Integration in Salesforce DX updates underlines the importance of version control in modern development practices. By providing seamless integration with popular version control systems, supporting source-driven development, and facilitating efficient collaboration through clear change tracking, these updates empower developers to manage their source code effectively and contribute to a more agile and collaborative development experience on the Salesforce platform.
Salesforce CLI (Command-Line Interface) Updates
Salesforce DX (Developer Experience) updates have brought significant enhancements to the Salesforce Command-Line Interface (CLI), a critical tool for developers working within the Salesforce ecosystem. These updates are designed to elevate the efficiency, flexibility, and overall experience of developers as they interact with the platform through the command line.
One noteworthy aspect of Salesforce CLI updates is the introduction of new commands and expanded functionality. These additions empower developers with a broader set of tools to perform various tasks, from project setup and metadata retrieval to data manipulation and deployment. This not only simplifies common development workflows but also provides developers with greater control and precision in their command-line interactions.
Updates often focus on improving the user experience by enhancing the overall performance and responsiveness of the CLI. Optimizations in command execution speed and resource utilization contribute to a more seamless and responsive command-line interface, allowing developers to execute tasks more quickly and with reduced latency. This is particularly crucial for developers who rely heavily on the command line for their day-to-day operations.
Salesforce CLI updates signify a commitment to providing developers with a powerful and versatile toolset for interacting with the Salesforce platform. By introducing new commands, optimizing performance, supporting automation, and improving error handling, these updates contribute to a more efficient and developer-friendly command-line experience, empowering developers to navigate and interact with the Salesforce ecosystem effectively.
DevOps Integration and Best Practices
Salesforce DX (Developer Experience) updates underscore a commitment to fostering a DevOps culture within the Salesforce development ecosystem. These updates align with best practices and principles of DevOps, aiming to enhance collaboration, automate workflows, and streamline the development lifecycle. Here's a closer look at how these updates contribute to DevOps integration and best practices:
Automation of Development Processes: Salesforce DX updates prioritize the automation of various development processes, from code integration to testing and deployment. This automation ensures consistency, reduces manual errors, and accelerates the overall development cycle. By adopting continuous integration practices, developers can automatically build, test, and validate their code changes, contributing to a more efficient and reliable development process.
Version Control Integration: A fundamental aspect of DevOps is version control, and Salesforce DX updates emphasize robust integration with popular version control systems like Git. This integration enables teams to manage their source code efficiently, track changes, and collaborate seamlessly. With version control as a core component, developers can work collaboratively, reduce conflicts, and maintain a clear history of code modifications.
Collaborative Development Environments: DevOps encourages collaboration between development, operations, and other stakeholders. Salesforce DX updates introduce features that support team-based development environments, allowing developers to work concurrently on different aspects of a project. This collaborative approach enhances communication and ensures that development efforts align with broader business objectives.
Continuous Testing Practices: Continuous testing is a crucial DevOps practice, and Salesforce DX updates contribute to this by enhancing testing frameworks. Developers can leverage automated testing tools to validate their code changes continuously. This not only ensures code quality but also provides rapid feedback, allowing teams to detect and address issues early in the development process.
Security and Compliance Considerations: Integrating security and compliance practices into the development lifecycle is a crucial aspect of DevOps. Salesforce DX updates may introduce features related to code scanning, vulnerability detection, and adherence to compliance standards. By embedding security into the development process, teams can proactively address potential risks and ensure the integrity of their applications.
Salesforce DX updates contribute to the integration of DevOps practices by automating processes, supporting collaborative development, emphasizing continuous testing and deployment, and addressing security and compliance considerations. These updates empower organizations to embrace a holistic DevOps approach, fostering a culture of collaboration, efficiency, and continuous improvement in Salesforce development workflows.
Security and Compliance Features
Salesforce DX (Developer Experience) updates stand out for their unwavering focus on strengthening the security and compliance facets of the development process within the Salesforce ecosystem. These updates take a holistic approach, integrating features that proactively tackle potential security vulnerabilities and ensure strict adherence to industry compliance standards, forming a solid foundation for building resilient applications.
Secure development best practices constitute another cornerstone of Salesforce DX updates in the context of security and compliance. Developers benefit from features that offer guidance on secure coding techniques and recommendations to steer clear of common security pitfalls. This encourages development teams to adopt security-conscious practices, fostering a culture of heightened security awareness and diligence throughout the entire development process.
Integral components of the security and compliance features in Salesforce DX updates include data encryption and privacy measures. Developers gain access to tools facilitating the encryption of sensitive data in transit and at rest. Features related to data anonymization and compliance with data privacy regulations contribute to a holistic approach to safeguarding user information and upholding privacy norms.
Streamlining compliance reporting and certifications is a key aspect of Salesforce DX updates, providing developers with tools to effortlessly generate compliance reports and demonstrate adherence to industry standards. This transparency is crucial for organizations in regulated sectors, ensuring accountability and simplifying compliance audits, thereby highlighting a commitment to maintaining high standards of security and regulatory compliance.
How to obtain SALESFORCE PLATFORM DEVELOPER certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, the Salesforce DX (Developer Experience) updates represent a transformative evolution in the way developers engage with and optimize their workflows on the Salesforce platform. Through a multifaceted approach, these updates address key aspects of development, including enhanced tools, collaboration features, continuous integration and delivery, source control integration, Salesforce CLI improvements, DevOps integration, and robust security and compliance features.
The emphasis on enhanced development tools underscores a commitment to providing developers with a modern and efficient development environment. This, coupled with collaborative features, fosters a sense of unity among development teams, enabling them to work seamlessly and efficiently on shared projects.
Salesforce DX updates collectively propel the Salesforce development ecosystem forward, empowering developers to create high-quality, secure, and collaborative solutions. By addressing the diverse needs of developers and aligning with best practices, these updates ensure that the Salesforce platform remains at the forefront of innovation, fostering a dynamic and thriving developer community.
Read More
Salesforce DX (Developer Experience) has emerged as a pivotal framework within the Salesforce ecosystem, revolutionizing the way developers build and deploy applications on the Salesforce platform. With the relentless pace of technological advancement and the increasing complexity of business requirements, Salesforce DX serves as a cornerstone for empowering developers with a modern and collaborative development environment. This framework goes beyond traditional development methodologies, fostering agility, efficiency, and innovation throughout the application development lifecycle.
The Salesforce DX updates encompass a diverse range of elements, including improvements to development tools, enhanced collaboration capabilities, and streamlined processes for continuous integration and delivery. These updates are designed to provide developers with the flexibility and scalability required to navigate the complexities of modern software development. By staying attuned to the latest Salesforce DX updates, developers can harness the full potential of the platform, enabling them to create robust, scalable, and innovative solutions that drive business success.
In this dynamic landscape of software development, understanding and leveraging Salesforce DX updates are crucial for developers aiming to optimize their workflows, enhance collaboration, and deliver high-quality solutions. This introduction sets the stage for a deeper exploration of the specific updates, innovations, and advancements that Salesforce DX brings to the table, underscoring its significance in shaping a superior developer experience within the Salesforce ecosystem.
Table of contents
-
Enhanced Development Tools
-
Collaboration Features
-
Continuous Integration and Delivery (CI/CD) Enhancements
-
Source Control Integration
-
Salesforce CLI (Command-Line Interface) Updates
-
DevOps Integration and Best Practices
-
Security and Compliance Features
-
Conclusion
Enhanced Development Tools
The realm of Salesforce DX (Developer Experience) has witnessed significant progress with the introduction of enhanced development tools. These tools play a pivotal role in shaping the daily workflows of developers, offering a more intuitive and efficient coding experience. One notable aspect of these updates involves improvements to the integrated development environment (IDE), where developers spend a substantial amount of their time crafting and refining code. The updated IDE provides a more user-friendly interface, streamlined navigation, and enhanced code suggestions, contributing to a more productive and enjoyable development process.
Code editors have also undergone refinements, aligning with the evolving needs of developers working within the Salesforce ecosystem. The updates in this domain often include features such as intelligent code completion, syntax highlighting, and real-time error checking. These improvements not only reduce the likelihood of coding errors but also accelerate the development cycle by providing immediate feedback to developers, allowing them to address issues swiftly.
The enhanced development tools introduced in Salesforce DX updates represent a concerted effort to elevate the overall developer experience. By focusing on the user interface, code editing capabilities, and debugging tools, these updates aim to make the development process more efficient, collaborative, and enjoyable for developers, thereby fostering innovation and excellence within the Salesforce development community.
Collaboration Features
Salesforce DX (Developer Experience) updates have introduced a suite of collaboration features that redefine the way development teams work together, emphasizing communication, coordination, and shared productivity. These updates aim to break down silos and enhance the overall collaborative experience for developers within the Salesforce ecosystem.
One significant facet of these collaboration features is the evolution of version control systems. Salesforce DX updates have strengthened the integration of version control, allowing developers to seamlessly collaborate on projects with a clear and organized history of changes. This not only streamlines collaboration but also promotes code consistency and facilitates the efficient resolution of conflicts in a shared codebase.
Real-time collaboration tools play a crucial role in fostering a sense of unity among developers. Whether through integrated chat systems, collaborative code reviews, or shared development environments, these features enable developers to work synchronously, share insights, and collectively contribute to the evolution of projects. Real-time collaboration tools eliminate the barriers that often arise in distributed teams, ensuring that developers can seamlessly communicate and collaborate regardless of geographical locations.
The collaboration features embedded in Salesforce DX updates reflect a commitment to creating a cohesive and efficient development environment. By addressing version control, real-time collaboration, and communication channels, these updates empower development teams to collaborate seamlessly, resulting in enhanced productivity, higher code quality, and a more enjoyable overall developer experience on the Salesforce platform.
Continuous Integration and Delivery (CI/CD) Enhancements
Salesforce DX (Developer Experience) updates have introduced noteworthy enhancements in the realm of Continuous Integration and Delivery (CI/CD), revolutionizing the way developers manage and deploy their applications. These updates are strategically designed to streamline development workflows, enhance automation, and ensure the consistent and reliable delivery of high-quality code.
One prominent aspect of CI/CD enhancements involves improvements in automation processes throughout the development lifecycle. Automation has been elevated to a new standard, with updates facilitating the seamless integration of automated testing, code analysis, and deployment procedures. This not only accelerates the development cycle but also minimizes the likelihood of human error, ensuring a more robust and error-resistant codebase.
The updates also focus on refining testing frameworks within the CI/CD pipeline. Developers can now leverage more advanced testing tools and methodologies to validate their code changes systematically. This includes comprehensive unit testing, integration testing, and end-to-end testing, contributing to the creation of more resilient and reliable applications. Additionally, updates in this domain often incorporate features that enable parallel testing, further expediting the testing phase of the development process.
The CI/CD enhancements introduced in Salesforce DX updates represent a commitment to advancing the efficiency and reliability of the development and deployment process. By focusing on automation, testing, and deployment strategies, these updates empower developers to deliver high-quality code at a faster pace, ultimately contributing to a more agile, responsive, and innovative development ecosystem on the Salesforce platform.
Source Control Integration
Source Control Integration is a pivotal aspect of Salesforce DX (Developer Experience) updates, playing a crucial role in shaping a more streamlined and collaborative development process. These updates emphasize the integration of robust version control systems, enabling developers to manage their source code efficiently, track changes systematically, and collaborate seamlessly within the Salesforce ecosystem.
One key focus of Source Control Integration in Salesforce DX updates is the facilitation of source-driven development. This approach emphasizes the use of source code as the foundation for development, allowing developers to work on their code locally and then synchronize changes with a version control system. This shift from a traditional metadata-centric approach enhances collaboration, reduces conflicts, and provides developers with greater control over their development environment.
Source Control Integration in Salesforce DX updates underlines the importance of version control in modern development practices. By providing seamless integration with popular version control systems, supporting source-driven development, and facilitating efficient collaboration through clear change tracking, these updates empower developers to manage their source code effectively and contribute to a more agile and collaborative development experience on the Salesforce platform.
Salesforce CLI (Command-Line Interface) Updates
Salesforce DX (Developer Experience) updates have brought significant enhancements to the Salesforce Command-Line Interface (CLI), a critical tool for developers working within the Salesforce ecosystem. These updates are designed to elevate the efficiency, flexibility, and overall experience of developers as they interact with the platform through the command line.
One noteworthy aspect of Salesforce CLI updates is the introduction of new commands and expanded functionality. These additions empower developers with a broader set of tools to perform various tasks, from project setup and metadata retrieval to data manipulation and deployment. This not only simplifies common development workflows but also provides developers with greater control and precision in their command-line interactions.
Updates often focus on improving the user experience by enhancing the overall performance and responsiveness of the CLI. Optimizations in command execution speed and resource utilization contribute to a more seamless and responsive command-line interface, allowing developers to execute tasks more quickly and with reduced latency. This is particularly crucial for developers who rely heavily on the command line for their day-to-day operations.
Salesforce CLI updates signify a commitment to providing developers with a powerful and versatile toolset for interacting with the Salesforce platform. By introducing new commands, optimizing performance, supporting automation, and improving error handling, these updates contribute to a more efficient and developer-friendly command-line experience, empowering developers to navigate and interact with the Salesforce ecosystem effectively.
DevOps Integration and Best Practices
Salesforce DX (Developer Experience) updates underscore a commitment to fostering a DevOps culture within the Salesforce development ecosystem. These updates align with best practices and principles of DevOps, aiming to enhance collaboration, automate workflows, and streamline the development lifecycle. Here's a closer look at how these updates contribute to DevOps integration and best practices:
Automation of Development Processes: Salesforce DX updates prioritize the automation of various development processes, from code integration to testing and deployment. This automation ensures consistency, reduces manual errors, and accelerates the overall development cycle. By adopting continuous integration practices, developers can automatically build, test, and validate their code changes, contributing to a more efficient and reliable development process.
Version Control Integration: A fundamental aspect of DevOps is version control, and Salesforce DX updates emphasize robust integration with popular version control systems like Git. This integration enables teams to manage their source code efficiently, track changes, and collaborate seamlessly. With version control as a core component, developers can work collaboratively, reduce conflicts, and maintain a clear history of code modifications.
Collaborative Development Environments: DevOps encourages collaboration between development, operations, and other stakeholders. Salesforce DX updates introduce features that support team-based development environments, allowing developers to work concurrently on different aspects of a project. This collaborative approach enhances communication and ensures that development efforts align with broader business objectives.
Continuous Testing Practices: Continuous testing is a crucial DevOps practice, and Salesforce DX updates contribute to this by enhancing testing frameworks. Developers can leverage automated testing tools to validate their code changes continuously. This not only ensures code quality but also provides rapid feedback, allowing teams to detect and address issues early in the development process.
Security and Compliance Considerations: Integrating security and compliance practices into the development lifecycle is a crucial aspect of DevOps. Salesforce DX updates may introduce features related to code scanning, vulnerability detection, and adherence to compliance standards. By embedding security into the development process, teams can proactively address potential risks and ensure the integrity of their applications.
Salesforce DX updates contribute to the integration of DevOps practices by automating processes, supporting collaborative development, emphasizing continuous testing and deployment, and addressing security and compliance considerations. These updates empower organizations to embrace a holistic DevOps approach, fostering a culture of collaboration, efficiency, and continuous improvement in Salesforce development workflows.
Security and Compliance Features
Salesforce DX (Developer Experience) updates stand out for their unwavering focus on strengthening the security and compliance facets of the development process within the Salesforce ecosystem. These updates take a holistic approach, integrating features that proactively tackle potential security vulnerabilities and ensure strict adherence to industry compliance standards, forming a solid foundation for building resilient applications.
Secure development best practices constitute another cornerstone of Salesforce DX updates in the context of security and compliance. Developers benefit from features that offer guidance on secure coding techniques and recommendations to steer clear of common security pitfalls. This encourages development teams to adopt security-conscious practices, fostering a culture of heightened security awareness and diligence throughout the entire development process.
Integral components of the security and compliance features in Salesforce DX updates include data encryption and privacy measures. Developers gain access to tools facilitating the encryption of sensitive data in transit and at rest. Features related to data anonymization and compliance with data privacy regulations contribute to a holistic approach to safeguarding user information and upholding privacy norms.
Streamlining compliance reporting and certifications is a key aspect of Salesforce DX updates, providing developers with tools to effortlessly generate compliance reports and demonstrate adherence to industry standards. This transparency is crucial for organizations in regulated sectors, ensuring accountability and simplifying compliance audits, thereby highlighting a commitment to maintaining high standards of security and regulatory compliance.
How to obtain SALESFORCE PLATFORM DEVELOPER certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Salesforce : SALESFORCE PLATFORM DEVELOPER
Conclusion
In conclusion, the Salesforce DX (Developer Experience) updates represent a transformative evolution in the way developers engage with and optimize their workflows on the Salesforce platform. Through a multifaceted approach, these updates address key aspects of development, including enhanced tools, collaboration features, continuous integration and delivery, source control integration, Salesforce CLI improvements, DevOps integration, and robust security and compliance features.
The emphasis on enhanced development tools underscores a commitment to providing developers with a modern and efficient development environment. This, coupled with collaborative features, fosters a sense of unity among development teams, enabling them to work seamlessly and efficiently on shared projects.
Salesforce DX updates collectively propel the Salesforce development ecosystem forward, empowering developers to create high-quality, secure, and collaborative solutions. By addressing the diverse needs of developers and aligning with best practices, these updates ensure that the Salesforce platform remains at the forefront of innovation, fostering a dynamic and thriving developer community.
The Metaverse and Blockchain: Shaping the Future of Virtual Worlds
In the rapidly evolving landscape of technology, two groundbreaking concepts have emerged as transformative forces that promise to reshape the way we experience and interact with the digital realm: the Metaverse and Blockchain. As we stand on the cusp of a new era, these two phenomena are converging to forge an unprecedented synergy, unlocking possibilities that extend far beyond the boundaries of our current understanding.
The Metaverse, a virtual universe where users can engage with immersive digital environments and each other in real-time, represents a paradigm shift in how we perceive and participate in online spaces. It transcends the limitations of traditional 2D screens, offering a three-dimensional, interconnected world that blurs the lines between the physical and digital realms. As technology advances, the Metaverse is poised to become a ubiquitous extension of our daily lives, revolutionizing communication, commerce, education, and entertainment.
At the heart of this transformative journey lies Blockchain technology, a decentralized and secure system that underpins cryptocurrencies like Bitcoin and Ethereum. Beyond its role in finance, Blockchain is proving to be a catalyst for innovation in the Metaverse, offering solutions to critical challenges such as identity verification, digital asset ownership, and secure transactions. By providing a transparent and tamper-proof ledger, Blockchain ensures trust in the virtual realm, empowering users to truly own and control their digital assets.
"The Metaverse and Blockchain: Shaping the Future of Virtual Worlds" delves into the intersection of these two disruptive forces, exploring the symbiotic relationship that is poised to redefine the possibilities of virtual existence. From the creation of unique digital assets using non-fungible tokens (NFTs) to the establishment of decentralized virtual economies, this exploration navigates the intricate landscape where technology, virtual reality, and decentralized systems converge.
Table of contents
-
Metaverse Architecture: Exploring the Technical Foundations
-
User Identity in the Metaverse: Decentralized Identity Management
-
Privacy in Virtual Spaces: Blockchain's Contribution to Data Security
-
Legal and Ethical Considerations: Navigating the Metaverse Landscape
-
Metaverse Gaming: Blockchain-Powered Virtual Realms
-
Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities
-
Emerging Metaverse Projects: Blockchain Innovations and Startups
-
Conclusion
Metaverse Architecture: Exploring the Technical Foundations
Metaverse Architecture stands as the cornerstone of the virtual landscape, delineating the technical foundations that support the intricate and immersive virtual worlds within this emerging digital realm. At its essence, the architecture of the Metaverse is a complex amalgamation of technological frameworks, protocols, and infrastructures that collectively enable the creation, interaction, and sustenance of virtual environments. These technical underpinnings play a pivotal role in shaping the user experience and determining the possibilities within the Metaverse.
The Metaverse's architectural framework often involves a combination of virtual reality (VR), augmented reality (AR), and mixed reality (MR) technologies. These elements work in tandem to create an environment that transcends the boundaries of traditional 2D digital spaces, offering users a three-dimensional and interactive world. The integration of blockchain technology is a crucial aspect of Metaverse Architecture, ensuring transparency, security, and decentralization across the virtual landscape.
Blockchain's role in the technical foundations of the Metaverse is multifaceted. One of its primary contributions is in the establishment of a decentralized ledger, which serves as a tamper-proof record of transactions, ownership, and interactions within the virtual space. This not only enhances security but also fosters trust among users, as they can verify ownership and authenticity of digital assets through transparent and immutable records.
"Metaverse Architecture: Exploring the Technical Foundations" delves into the intricate details of the technological infrastructure that powers the Metaverse. By examining the convergence of VR, AR, MR, and blockchain technologies, this exploration seeks to unravel the complexities and innovations that define the technical underpinnings of the Metaverse, ultimately shaping the future of virtual worlds.
User Identity in the Metaverse: Decentralized Identity Management
In the evolving landscape of the Metaverse, the management of user identity stands as a pivotal challenge and opportunity, giving rise to the concept of Decentralized Identity Management. Traditional online spaces often grapple with issues of privacy, security, and user control over personal information. In response, the integration of blockchain technology within the Metaverse offers a paradigm shift by decentralizing identity management, providing users with unprecedented control and security over their virtual personas.
Decentralized Identity Management leverages blockchain's inherent characteristics of transparency, immutability, and decentralization to address the vulnerabilities associated with centralized identity systems. In the Metaverse, users are empowered to own and control their identity through cryptographic keys stored on a decentralized ledger. This not only ensures a higher level of security but also gives users the autonomy to manage and share their identity across various virtual platforms without relying on a central authority.
Blockchain's role in user identity extends to the creation of self-sovereign identities, where individuals have full ownership and agency over their personal information. This model allows users to selectively disclose aspects of their identity, granting them the flexibility to engage in virtual spaces with a level of privacy that was previously challenging to achieve in centralized systems.
Privacy in Virtual Spaces: Blockchain's Contribution to Data Security
In the rapidly evolving landscape of virtual spaces, the question of privacy has become a paramount concern, prompting a critical examination of how blockchain technology contributes to data security within these digital realms. As users immerse themselves in the expansive environments of the Metaverse, concerns related to the unauthorized access, misuse, and mishandling of personal information have heightened. Blockchain emerges as a powerful tool, offering a decentralized and secure foundation that reshapes the paradigm of privacy in virtual spaces.
At the heart of blockchain's contribution to data security is its ability to establish a transparent and tamper-proof ledger. In the context of privacy within the Metaverse, this ensures that user data remains immutable and resistant to unauthorized alterations. Each transaction or interaction within the virtual space is recorded in a decentralized manner, fostering trust among users by providing an auditable and verifiable history of data-related activities.
Blockchain's implementation of cryptographic techniques further enhances privacy in virtual spaces. Users can engage in secure and private transactions, communication, and interactions, as the cryptographic principles inherent in blockchain protocols ensure the confidentiality and integrity of the data exchanged. This becomes particularly crucial in the context of sensitive information, such as personal details, financial transactions, and communication logs within the Metaverse.
The exploration of "Privacy in Virtual Spaces: Blockchain's Contribution to Data Security" delves into the transformative role of blockchain technology in establishing robust privacy frameworks within the Metaverse. By combining transparency, cryptographic techniques, decentralization, and interoperability, blockchain contributes significantly to safeguarding user privacy, fostering a secure and trust-centric virtual environment for users to explore and engage in the evolving digital landscape.
Legal and Ethical Considerations: Navigating the Metaverse Landscape
"Legal and Ethical Considerations: Navigating the Metaverse Landscape," delves into the multifaceted challenges and opportunities that arise as users, developers, and stakeholders engage with this evolving digital frontier.
One of the primary legal considerations involves the establishment of a regulatory framework that governs activities within the Metaverse. As virtual worlds increasingly mirror aspects of the physical world, questions arise regarding jurisdiction, digital property rights, and contractual obligations. This exploration involves scrutinizing existing legal frameworks and proposing new regulations to address the unique challenges posed by decentralized, global, and often anonymous interactions within the Metaverse.
Ethical considerations loom large as users and developers navigate the Metaverse. Questions of digital inclusion, accessibility, and the prevention of discriminatory practices within virtual environments become focal points. The exploration of ethical guidelines involves assessing how the Metaverse can be designed and governed to promote diversity, inclusivity, and user well-being, ensuring that the benefits of virtual engagement are distributed equitably.
Blockchain technology contributes significantly to the ethical considerations within the Metaverse by providing transparent and trustless systems. Smart contracts, powered by blockchain, can automate and enforce ethical standards within virtual environments, establishing predefined rules for user interactions, content moderation, and dispute resolution.
The subtopic "Legal and Ethical Considerations: Navigating the Metaverse Landscape" is a comprehensive exploration of the intricate challenges and opportunities at the intersection of law, ethics, and the burgeoning Metaverse. As stakeholders work towards establishing a responsible and sustainable digital frontier, this investigation aims to guide the development of frameworks that foster innovation, protect rights, and uphold ethical standards within the dynamic and transformative realm of the Metaverse.
Metaverse Gaming: Blockchain-Powered Virtual Realms
In the dynamic intersection of the Metaverse and gaming, a groundbreaking synergy is unfolding, ushering in a new era encapsulated by the subtopic "Metaverse Gaming: Blockchain-Powered Virtual Realms." At its core, this exploration delves into the transformative impact of blockchain technology on the immersive experience of gaming within virtual environments, reshaping fundamental aspects of ownership, transactions, and player engagement.
Beyond the notion of asset ownership, blockchain technology redefines the structure of in-game economies. Smart contracts, executable pieces of code on the blockchain, enable transparent and automated transactions, facilitating secure buying, selling, and trading of in-game assets. This not only empowers players with a newfound sense of control over their virtual possessions but also injects a real-world value dynamic into the fabric of virtual realms.
The integration of blockchain in Metaverse gaming addresses longstanding challenges related to interoperability and cross-platform experiences. Through standardized protocols, players can seamlessly carry their blockchain-backed assets across different virtual environments, breaking down barriers that once limited their gaming experiences to specific platforms. This interoperability enhances the fluidity and inclusivity of the gaming landscape within the Metaverse.
"Metaverse Gaming: Blockchain-Powered Virtual Realms" represents a pivotal exploration of the profound impact blockchain technology has on the gaming landscape within the Metaverse. From the introduction of NFTs and the restructuring of in-game economies to the facilitation of interoperability and play-to-earn dynamics, this narrative unfolds a revolutionary chapter in gaming, where blockchain not only enriches player experiences but fundamentally reshapes the economic and participatory aspects of virtual realms within the ever-evolving Metaverse.
Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities
In the evolving landscape of digital experiences, the convergence of the Metaverse and Augmented Reality (AR) marks a transformative juncture where virtual and physical realities seamlessly blend. This subtopic, "Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities," explores the dynamic interplay between these two innovative technologies and the profound impact they have on shaping a hybrid reality that transcends traditional boundaries.
At its essence, augmented reality enhances the physical world by overlaying digital elements onto the real environment, creating an immersive and interactive experience. The integration of AR into the Metaverse takes this concept to new heights, introducing a layer of virtual interactivity that coexists with the physical world. Users equipped with AR-enabled devices can seamlessly transition between the tangible and digital realms, as virtual objects, information, and interactions become an integral part of their everyday surroundings.
The synergy between the Metaverse and AR is particularly evident in the way users engage with the virtual environment. The Metaverse, as a three-dimensional digital universe, gains an added dimensionality through AR, extending its influence into the physical space that users inhabit. This integration goes beyond traditional screen-based interactions, providing a more immersive and contextually relevant experience that blurs the lines between what is real and what is virtual.
One of the key implications of this convergence is the potential for enhanced real-world interactions. Whether for socializing, gaming, or productivity, the combination of the Metaverse and AR enables users to engage with digital content and experiences in a spatially aware manner. Virtual meetings can seamlessly transition into physical spaces, and digital assets within the Metaverse can manifest in the real world through AR, creating a richer and more interconnected user experience.
"Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities" encapsulates the exciting convergence of two transformative technologies, painting a picture of a hybrid reality where the distinctions between the digital and physical realms fade away. As the boundaries blur, users are presented with a new frontier of possibilities that redefine how they perceive and interact with both the tangible world and the vast landscapes of the Metaverse.
Emerging Metaverse Projects: Blockchain Innovations and Startups
In the ever-expanding landscape of the Metaverse, a captivating narrative unfolds through the lens of "Emerging Metaverse Projects: Blockchain Innovations and Startups." This exploration dives into the forefront of technological innovation, spotlighting the pioneering initiatives and startups that harness the synergies between the Metaverse and blockchain technology to reshape the digital landscape.
Blockchain, with its decentralized and transparent architecture, emerges as a catalyst for a wave of entrepreneurial endeavors within the Metaverse. These projects exemplify the transformative potential of blockchain in creating novel, secure, and interconnected virtual experiences. One notable trend among these initiatives is the creation of non-fungible tokens (NFTs), which represent unique digital assets, often ranging from virtual art and collectibles to in-game items.
Startups focusing on NFT marketplaces are carving out spaces within the Metaverse, providing platforms for creators to tokenize and monetize their digital content. The decentralized nature of blockchain ensures transparency and authenticity, fostering a vibrant ecosystem where artists and content creators can directly engage with a global audience, free from traditional gatekeepers.
Virtual real estate projects, another exciting frontier, leverage blockchain to enable users to buy, sell, and trade digital land within the Metaverse. These ventures aim to create decentralized, user-driven virtual worlds, where land ownership is recorded on the blockchain, offering users unprecedented control over their virtual territories.
Blockchain's role in enhancing virtual economies is exemplified by startups that introduce decentralized finance (DeFi) protocols within the Metaverse. These projects enable users to participate in financial activities such as lending, borrowing, and trading using blockchain-based assets, further blurring the lines between the digital and real economies.
The concept of decentralized autonomous organizations (DAOs) is gaining prominence in Metaverse projects. These organizations, powered by blockchain, allow users to collectively make decisions and govern virtual spaces collaboratively. DAOs contribute to the democratization of the Metaverse, giving users a direct say in the development and governance of the digital realms they inhabit.
How to obtain BlockChain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Emerging Technology : Block Chain
Conclusion
In conclusion, "The Metaverse and Blockchain: Shaping the Future of Virtual Worlds" encapsulates a profound journey into the transformative forces that are reshaping our digital existence. The intersection of the Metaverse and blockchain heralds a new era where immersive virtual experiences and decentralized technologies converge to redefine how we interact, transact, and build within digital realms.
The exploration of non-fungible tokens (NFTs) and decentralized virtual economies signifies a departure from traditional models, offering users unprecedented control and ownership over their digital assets. Blockchain's role in ensuring security, transparency, and interoperability serves as a cornerstone, fostering trust and enabling a seamless flow of assets across diverse virtual platforms.
As we stand at the nexus of the Metaverse and blockchain, the possibilities are boundless. The narrative presented here unravels the complexities and innovations shaping the future of virtual worlds, showcasing a landscape where the boundaries between the physical and digital dissolve, and where collaboration, creativity, and user empowerment stand as the guiding principles of a new and exciting digital frontier. The journey has just begun, and the fusion of the Metaverse and blockchain continues to unfold, promising a future where the digital realm mirrors the limitless potential of human imagination and collaboration.
Read More
In the rapidly evolving landscape of technology, two groundbreaking concepts have emerged as transformative forces that promise to reshape the way we experience and interact with the digital realm: the Metaverse and Blockchain. As we stand on the cusp of a new era, these two phenomena are converging to forge an unprecedented synergy, unlocking possibilities that extend far beyond the boundaries of our current understanding.
The Metaverse, a virtual universe where users can engage with immersive digital environments and each other in real-time, represents a paradigm shift in how we perceive and participate in online spaces. It transcends the limitations of traditional 2D screens, offering a three-dimensional, interconnected world that blurs the lines between the physical and digital realms. As technology advances, the Metaverse is poised to become a ubiquitous extension of our daily lives, revolutionizing communication, commerce, education, and entertainment.
At the heart of this transformative journey lies Blockchain technology, a decentralized and secure system that underpins cryptocurrencies like Bitcoin and Ethereum. Beyond its role in finance, Blockchain is proving to be a catalyst for innovation in the Metaverse, offering solutions to critical challenges such as identity verification, digital asset ownership, and secure transactions. By providing a transparent and tamper-proof ledger, Blockchain ensures trust in the virtual realm, empowering users to truly own and control their digital assets.
"The Metaverse and Blockchain: Shaping the Future of Virtual Worlds" delves into the intersection of these two disruptive forces, exploring the symbiotic relationship that is poised to redefine the possibilities of virtual existence. From the creation of unique digital assets using non-fungible tokens (NFTs) to the establishment of decentralized virtual economies, this exploration navigates the intricate landscape where technology, virtual reality, and decentralized systems converge.
Table of contents
-
Metaverse Architecture: Exploring the Technical Foundations
-
User Identity in the Metaverse: Decentralized Identity Management
-
Privacy in Virtual Spaces: Blockchain's Contribution to Data Security
-
Legal and Ethical Considerations: Navigating the Metaverse Landscape
-
Metaverse Gaming: Blockchain-Powered Virtual Realms
-
Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities
-
Emerging Metaverse Projects: Blockchain Innovations and Startups
-
Conclusion
Metaverse Architecture: Exploring the Technical Foundations
Metaverse Architecture stands as the cornerstone of the virtual landscape, delineating the technical foundations that support the intricate and immersive virtual worlds within this emerging digital realm. At its essence, the architecture of the Metaverse is a complex amalgamation of technological frameworks, protocols, and infrastructures that collectively enable the creation, interaction, and sustenance of virtual environments. These technical underpinnings play a pivotal role in shaping the user experience and determining the possibilities within the Metaverse.
The Metaverse's architectural framework often involves a combination of virtual reality (VR), augmented reality (AR), and mixed reality (MR) technologies. These elements work in tandem to create an environment that transcends the boundaries of traditional 2D digital spaces, offering users a three-dimensional and interactive world. The integration of blockchain technology is a crucial aspect of Metaverse Architecture, ensuring transparency, security, and decentralization across the virtual landscape.
Blockchain's role in the technical foundations of the Metaverse is multifaceted. One of its primary contributions is in the establishment of a decentralized ledger, which serves as a tamper-proof record of transactions, ownership, and interactions within the virtual space. This not only enhances security but also fosters trust among users, as they can verify ownership and authenticity of digital assets through transparent and immutable records.
"Metaverse Architecture: Exploring the Technical Foundations" delves into the intricate details of the technological infrastructure that powers the Metaverse. By examining the convergence of VR, AR, MR, and blockchain technologies, this exploration seeks to unravel the complexities and innovations that define the technical underpinnings of the Metaverse, ultimately shaping the future of virtual worlds.
User Identity in the Metaverse: Decentralized Identity Management
In the evolving landscape of the Metaverse, the management of user identity stands as a pivotal challenge and opportunity, giving rise to the concept of Decentralized Identity Management. Traditional online spaces often grapple with issues of privacy, security, and user control over personal information. In response, the integration of blockchain technology within the Metaverse offers a paradigm shift by decentralizing identity management, providing users with unprecedented control and security over their virtual personas.
Decentralized Identity Management leverages blockchain's inherent characteristics of transparency, immutability, and decentralization to address the vulnerabilities associated with centralized identity systems. In the Metaverse, users are empowered to own and control their identity through cryptographic keys stored on a decentralized ledger. This not only ensures a higher level of security but also gives users the autonomy to manage and share their identity across various virtual platforms without relying on a central authority.
Blockchain's role in user identity extends to the creation of self-sovereign identities, where individuals have full ownership and agency over their personal information. This model allows users to selectively disclose aspects of their identity, granting them the flexibility to engage in virtual spaces with a level of privacy that was previously challenging to achieve in centralized systems.
Privacy in Virtual Spaces: Blockchain's Contribution to Data Security
In the rapidly evolving landscape of virtual spaces, the question of privacy has become a paramount concern, prompting a critical examination of how blockchain technology contributes to data security within these digital realms. As users immerse themselves in the expansive environments of the Metaverse, concerns related to the unauthorized access, misuse, and mishandling of personal information have heightened. Blockchain emerges as a powerful tool, offering a decentralized and secure foundation that reshapes the paradigm of privacy in virtual spaces.
At the heart of blockchain's contribution to data security is its ability to establish a transparent and tamper-proof ledger. In the context of privacy within the Metaverse, this ensures that user data remains immutable and resistant to unauthorized alterations. Each transaction or interaction within the virtual space is recorded in a decentralized manner, fostering trust among users by providing an auditable and verifiable history of data-related activities.
Blockchain's implementation of cryptographic techniques further enhances privacy in virtual spaces. Users can engage in secure and private transactions, communication, and interactions, as the cryptographic principles inherent in blockchain protocols ensure the confidentiality and integrity of the data exchanged. This becomes particularly crucial in the context of sensitive information, such as personal details, financial transactions, and communication logs within the Metaverse.
The exploration of "Privacy in Virtual Spaces: Blockchain's Contribution to Data Security" delves into the transformative role of blockchain technology in establishing robust privacy frameworks within the Metaverse. By combining transparency, cryptographic techniques, decentralization, and interoperability, blockchain contributes significantly to safeguarding user privacy, fostering a secure and trust-centric virtual environment for users to explore and engage in the evolving digital landscape.
Legal and Ethical Considerations: Navigating the Metaverse Landscape
"Legal and Ethical Considerations: Navigating the Metaverse Landscape," delves into the multifaceted challenges and opportunities that arise as users, developers, and stakeholders engage with this evolving digital frontier.
One of the primary legal considerations involves the establishment of a regulatory framework that governs activities within the Metaverse. As virtual worlds increasingly mirror aspects of the physical world, questions arise regarding jurisdiction, digital property rights, and contractual obligations. This exploration involves scrutinizing existing legal frameworks and proposing new regulations to address the unique challenges posed by decentralized, global, and often anonymous interactions within the Metaverse.
Ethical considerations loom large as users and developers navigate the Metaverse. Questions of digital inclusion, accessibility, and the prevention of discriminatory practices within virtual environments become focal points. The exploration of ethical guidelines involves assessing how the Metaverse can be designed and governed to promote diversity, inclusivity, and user well-being, ensuring that the benefits of virtual engagement are distributed equitably.
Blockchain technology contributes significantly to the ethical considerations within the Metaverse by providing transparent and trustless systems. Smart contracts, powered by blockchain, can automate and enforce ethical standards within virtual environments, establishing predefined rules for user interactions, content moderation, and dispute resolution.
The subtopic "Legal and Ethical Considerations: Navigating the Metaverse Landscape" is a comprehensive exploration of the intricate challenges and opportunities at the intersection of law, ethics, and the burgeoning Metaverse. As stakeholders work towards establishing a responsible and sustainable digital frontier, this investigation aims to guide the development of frameworks that foster innovation, protect rights, and uphold ethical standards within the dynamic and transformative realm of the Metaverse.
Metaverse Gaming: Blockchain-Powered Virtual Realms
In the dynamic intersection of the Metaverse and gaming, a groundbreaking synergy is unfolding, ushering in a new era encapsulated by the subtopic "Metaverse Gaming: Blockchain-Powered Virtual Realms." At its core, this exploration delves into the transformative impact of blockchain technology on the immersive experience of gaming within virtual environments, reshaping fundamental aspects of ownership, transactions, and player engagement.
Beyond the notion of asset ownership, blockchain technology redefines the structure of in-game economies. Smart contracts, executable pieces of code on the blockchain, enable transparent and automated transactions, facilitating secure buying, selling, and trading of in-game assets. This not only empowers players with a newfound sense of control over their virtual possessions but also injects a real-world value dynamic into the fabric of virtual realms.
The integration of blockchain in Metaverse gaming addresses longstanding challenges related to interoperability and cross-platform experiences. Through standardized protocols, players can seamlessly carry their blockchain-backed assets across different virtual environments, breaking down barriers that once limited their gaming experiences to specific platforms. This interoperability enhances the fluidity and inclusivity of the gaming landscape within the Metaverse.
"Metaverse Gaming: Blockchain-Powered Virtual Realms" represents a pivotal exploration of the profound impact blockchain technology has on the gaming landscape within the Metaverse. From the introduction of NFTs and the restructuring of in-game economies to the facilitation of interoperability and play-to-earn dynamics, this narrative unfolds a revolutionary chapter in gaming, where blockchain not only enriches player experiences but fundamentally reshapes the economic and participatory aspects of virtual realms within the ever-evolving Metaverse.
Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities
In the evolving landscape of digital experiences, the convergence of the Metaverse and Augmented Reality (AR) marks a transformative juncture where virtual and physical realities seamlessly blend. This subtopic, "Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities," explores the dynamic interplay between these two innovative technologies and the profound impact they have on shaping a hybrid reality that transcends traditional boundaries.
At its essence, augmented reality enhances the physical world by overlaying digital elements onto the real environment, creating an immersive and interactive experience. The integration of AR into the Metaverse takes this concept to new heights, introducing a layer of virtual interactivity that coexists with the physical world. Users equipped with AR-enabled devices can seamlessly transition between the tangible and digital realms, as virtual objects, information, and interactions become an integral part of their everyday surroundings.
The synergy between the Metaverse and AR is particularly evident in the way users engage with the virtual environment. The Metaverse, as a three-dimensional digital universe, gains an added dimensionality through AR, extending its influence into the physical space that users inhabit. This integration goes beyond traditional screen-based interactions, providing a more immersive and contextually relevant experience that blurs the lines between what is real and what is virtual.
One of the key implications of this convergence is the potential for enhanced real-world interactions. Whether for socializing, gaming, or productivity, the combination of the Metaverse and AR enables users to engage with digital content and experiences in a spatially aware manner. Virtual meetings can seamlessly transition into physical spaces, and digital assets within the Metaverse can manifest in the real world through AR, creating a richer and more interconnected user experience.
"Metaverse and Augmented Reality (AR): Blurring Virtual and Physical Realities" encapsulates the exciting convergence of two transformative technologies, painting a picture of a hybrid reality where the distinctions between the digital and physical realms fade away. As the boundaries blur, users are presented with a new frontier of possibilities that redefine how they perceive and interact with both the tangible world and the vast landscapes of the Metaverse.
Emerging Metaverse Projects: Blockchain Innovations and Startups
In the ever-expanding landscape of the Metaverse, a captivating narrative unfolds through the lens of "Emerging Metaverse Projects: Blockchain Innovations and Startups." This exploration dives into the forefront of technological innovation, spotlighting the pioneering initiatives and startups that harness the synergies between the Metaverse and blockchain technology to reshape the digital landscape.
Blockchain, with its decentralized and transparent architecture, emerges as a catalyst for a wave of entrepreneurial endeavors within the Metaverse. These projects exemplify the transformative potential of blockchain in creating novel, secure, and interconnected virtual experiences. One notable trend among these initiatives is the creation of non-fungible tokens (NFTs), which represent unique digital assets, often ranging from virtual art and collectibles to in-game items.
Startups focusing on NFT marketplaces are carving out spaces within the Metaverse, providing platforms for creators to tokenize and monetize their digital content. The decentralized nature of blockchain ensures transparency and authenticity, fostering a vibrant ecosystem where artists and content creators can directly engage with a global audience, free from traditional gatekeepers.
Virtual real estate projects, another exciting frontier, leverage blockchain to enable users to buy, sell, and trade digital land within the Metaverse. These ventures aim to create decentralized, user-driven virtual worlds, where land ownership is recorded on the blockchain, offering users unprecedented control over their virtual territories.
Blockchain's role in enhancing virtual economies is exemplified by startups that introduce decentralized finance (DeFi) protocols within the Metaverse. These projects enable users to participate in financial activities such as lending, borrowing, and trading using blockchain-based assets, further blurring the lines between the digital and real economies.
The concept of decentralized autonomous organizations (DAOs) is gaining prominence in Metaverse projects. These organizations, powered by blockchain, allow users to collectively make decisions and govern virtual spaces collaboratively. DAOs contribute to the democratization of the Metaverse, giving users a direct say in the development and governance of the digital realms they inhabit.
How to obtain BlockChain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
-
Emerging Technology : Block Chain
Conclusion
In conclusion, "The Metaverse and Blockchain: Shaping the Future of Virtual Worlds" encapsulates a profound journey into the transformative forces that are reshaping our digital existence. The intersection of the Metaverse and blockchain heralds a new era where immersive virtual experiences and decentralized technologies converge to redefine how we interact, transact, and build within digital realms.
The exploration of non-fungible tokens (NFTs) and decentralized virtual economies signifies a departure from traditional models, offering users unprecedented control and ownership over their digital assets. Blockchain's role in ensuring security, transparency, and interoperability serves as a cornerstone, fostering trust and enabling a seamless flow of assets across diverse virtual platforms.
As we stand at the nexus of the Metaverse and blockchain, the possibilities are boundless. The narrative presented here unravels the complexities and innovations shaping the future of virtual worlds, showcasing a landscape where the boundaries between the physical and digital dissolve, and where collaboration, creativity, and user empowerment stand as the guiding principles of a new and exciting digital frontier. The journey has just begun, and the fusion of the Metaverse and blockchain continues to unfold, promising a future where the digital realm mirrors the limitless potential of human imagination and collaboration.
The Ultimate Guide to CISA Certification: A Step-by-Step Process
In the dynamic landscape of information technology and cybersecurity, professionals seek validation and recognition of their expertise to stay ahead in the field. One such coveted credential is the Certified Information Systems Auditor (CISA) certification. As organizations grapple with increasing cyber threats and the need for robust information systems, the demand for skilled individuals who can assess and secure these systems has never been higher. This guide aims to be the compass for those navigating the challenging yet rewarding journey towards achieving the CISA certification, providing a comprehensive and step-by-step process to empower aspiring professionals with the knowledge and skills required to excel in this critical domain.
At its core, the CISA certification is a testament to an individual's proficiency in auditing, controlling, and ensuring the security of information systems. Whether you are an IT professional looking to enhance your career prospects or a recent graduate aspiring to enter the world of cybersecurity, this guide is designed to demystify the CISA certification process. From understanding the foundational concepts to mastering the intricacies of information system auditing, each section of this guide is crafted to provide clarity and insight. As we embark on this journey together, the goal is not just to pass an exam but to grasp the underlying principles that define effective information system governance and security.
The guide will unfold in a logical sequence, breaking down the CISA certification process into manageable steps. It begins with an exploration of the CISA certification itself – its significance in the industry, the skills it validates, and the career opportunities it opens up. Subsequent chapters will delve into the core domains covered by the CISA exam, offering in-depth insights into information system auditing, control, and security. Practical tips, real-world examples, and interactive exercises will be interspersed throughout the guide to reinforce understanding and facilitate hands-on learning.
Whether you are a seasoned professional seeking to validate your expertise or a newcomer eager to make a mark in the world of cybersecurity, "The Ultimate Guide to CISA Certification: A Step-by-Step Process" is your roadmap to success. As we navigate through the intricacies of the CISA certification journey, this guide will serve as a reliable companion, providing guidance, knowledge, and inspiration to help you achieve your professional aspirations in the realm of information systems auditing and security.
Table of contents
-
Introduction to CISA Certification
-
Creating a Study Plan
-
Eligibility and Exam Registration
-
Recommended Study Materials
-
The Process of Auditing Information Systems
-
Governance and Management of IT
-
Information Systems Acquisition, Development, and Implementation
-
Information Systems Operations and Business Resilience
-
Protection of Information Assets
-
Exam Strategies and Post-Certification Career Planning
-
Conclusion
Introduction to CISA Certification
In the rapidly evolving landscape of cybersecurity, the Certified Information Systems Auditor (CISA) certification stands as a beacon of proficiency and recognition for individuals navigating the complex realm of information systems. CISA, administered by ISACA (Information Systems Audit and Control Association), has become a hallmark for professionals seeking to validate their skills in auditing, controlling, and ensuring the security of information systems. As organizations worldwide grapple with escalating cyber threats, the demand for certified individuals who can effectively assess and fortify information systems has reached unprecedented heights. The introduction to CISA certification serves as the foundational chapter in our guide, shedding light on the significance of this credential within the broader context of the cybersecurity industry.
CISA certification is more than a mere accolade; it is a testament to an individual's dedication and competence in safeguarding vital information assets. In this introductory section, we explore the multifaceted aspects of CISA, delving into its role as a professional milestone and examining the various ways in which it contributes to career advancement. As we embark on this comprehensive guide, the primary objective is to demystify the CISA certification process and empower aspiring professionals with the knowledge and skills essential for success in this critical field. By understanding the fundamental principles that underpin CISA, individuals can not only excel in the certification exam but also apply this knowledge in real-world scenarios, making meaningful contributions to information system governance and security.
Creating a Study Plan
Creating a well-structured and effective study plan is a crucial step in the preparation journey for the Certified Information Systems Auditor (CISA) certification. A thoughtful and organized approach not only optimizes study time but also enhances the retention of critical concepts. In this section, we delve into the key components of crafting a personalized study plan tailored to the unique needs and commitments of each aspiring CISA candidate.
Structure your study plan around the five domains of the CISA exam, dedicating specific blocks of time to each domain. This ensures comprehensive coverage of all topics and prevents overlooking any critical areas. Break down the domains into smaller topics, allowing for a more detailed and manageable study approach.
Consider incorporating a variety of study resources, including official ISACA materials, textbooks, online courses, and practice exams. A diverse range of resources helps cater to different learning styles and provides a more holistic understanding of the subject matter.
Balance your study sessions with breaks to avoid burnout and improve overall concentration. Consistency is key, so establish a routine that aligns with your daily schedule. Whether you choose to study in the morning, afternoon, or evening, maintaining a consistent study routine aids in building a habit and optimizing information retention.
CISA candidates can develop a comprehensive and personalized study plan that aligns with their unique strengths, weaknesses, and schedules. This proactive approach lays the groundwork for a more confident and successful performance on the CISA certification exam.
Eligibility and Exam Registration
Eligibility for the CISA exam is typically contingent on a combination of educational background and professional experience. Candidates commonly hold a bachelor's degree from an accredited institution, preferably in information systems, accounting, or a related field. Additionally, they are required to possess a minimum of five years of professional work experience in information systems, with at least three years spent in roles related to information system auditing, control, or security. Alternatively, a maximum of three years can be waived for individuals with certain degrees or specific professional certifications.
Once eligibility is established, the next crucial step is the exam registration process. ISACA, the governing body overseeing CISA certification, provides a user-friendly online platform for candidates to register. During this process, candidates are required to submit documentation supporting their eligibility, such as proof of education and work experience. It is imperative for candidates to carefully review and adhere to the deadlines and guidelines outlined by ISACA to ensure a smooth registration experience.
As part of the registration, candidates may also need to pay the required examination fees. These fees can vary based on factors such as ISACA membership status, early registration discounts, or exam location. Being aware of these financial aspects is essential for candidates planning their budget for the certification process.
Navigating eligibility requirements and completing the exam registration process sets the stage for a candidate's CISA certification journey. This foundational understanding ensures that individuals meet the necessary criteria and successfully enroll in the examination, providing them with the opportunity to showcase their expertise in information system auditing and security. Aspiring CISA professionals should approach this phase with meticulous attention to detail, as it forms the cornerstone of their pursuit of excellence in the field of cybersecurity.
Recommended Study Materials
Preparing for the Certified Information Systems Auditor (CISA) certification requires a strategic selection of study materials to ensure a thorough understanding of the exam domains. One of the primary resources recommended for candidates is the official ISACA material, which includes the CISA Review Manual. Published by ISACA, this comprehensive guide serves as a foundational reference, covering all five domains extensively. Additionally, the CISA Review Questions, Answers & Explanations Manual, also provided by ISACA, offers valuable practice questions with detailed explanations, allowing candidates to assess their comprehension and hone their problem-solving skills.
Supplementing official ISACA resources, various textbooks contribute to a well-rounded study plan. "CISA Certified Information Systems Auditor Study Guide" by David L. Cannon is widely regarded for its coverage of exam topics, including practical insights and practice questions. Another valuable resource is "CISA Exam Guide" by Peter H. Gregory, providing an in-depth examination of CISA domains alongside real-world examples, aiding candidates in grasping the practical applications of their knowledge.
Online courses and training programs play a crucial role in dynamic and interactive learning. ISACA's official online training courses are led by experienced instructors and offer an engaging way to reinforce key concepts. For those seeking a different approach, Cybrary's CISA Course provides a comprehensive video-based learning experience, covering exam domains and enhancing understanding through visual explanations.
Practice exams are integral to exam preparation, and ISACA's CISA Practice Questions Database offers an official platform to simulate exam conditions. This resource helps candidates familiarize themselves with the exam format, identify areas of weakness, and build confidence in their knowledge. Additionally, leveraging various online platforms that provide CISA practice exams allows candidates to access a diverse range of questions and test their readiness comprehensively.
Lastly, study groups and forums foster a sense of community and shared learning. ISACA's Online Community provides a platform for candidates to connect with each other and certified professionals, offering valuable insights, tips, and support. Local study groups, whether virtual or in-person, allow candidates to discuss challenging topics collaboratively, share experiences, and gain perspectives from peers on effective study strategies.
The Process of Auditing Information Systems
The process of auditing information systems is a critical component of the Certified Information Systems Auditor (CISA) certification and plays a pivotal role in ensuring the effectiveness and security of an organization's information infrastructure. This domain, encompassing the first section of the CISA exam, delves into the methodologies and practices involved in systematically reviewing and evaluating information systems.
At its core, the process of auditing information systems begins with meticulous planning. Audit planning involves defining the scope and objectives of the audit, understanding the business processes, and identifying the key risks associated with the information systems under review. This phase sets the foundation for the entire audit process, guiding auditors in determining the appropriate approach and resources required.
The execution phase involves the systematic examination of controls, procedures, and documentation within the information systems. Auditors assess the design and implementation of controls to ensure they align with industry standards and organizational policies. Throughout this phase, a focus is placed on identifying vulnerabilities, potential risks, and deviations from established best practices. The process involves both technical assessments of IT systems and a broader evaluation of management and operational controls.
Understanding the intricacies of the auditing process is essential for CISA candidates, as it forms the basis for a significant portion of the certification exam. Mastery of this domain not only prepares professionals to excel in the examination but also equips them with the skills necessary to contribute to robust information system governance and security within their respective organizations.
Governance and Management of IT
The domain of "Governance and Management of IT" represents a pivotal aspect of the Certified Information Systems Auditor (CISA) certification, reflecting the broader organizational context in which information systems operate. This domain, constituting a substantial portion of the CISA exam, delves into the governance frameworks, management practices, and strategic alignment of IT within an organization.
Governance, as it relates to IT, involves the establishment and implementation of policies, procedures, and decision-making structures to ensure that IT resources are utilized effectively and aligned with the organization's goals. CISA candidates explore various IT governance frameworks, such as COBIT (Control Objectives for Information and Related Technologies), to understand how these frameworks facilitate the alignment of IT strategies with overall business objectives. Governance practices extend to risk management, ensuring that organizations identify, assess, and manage risks associated with their IT environments.
The management of IT encompasses the day-to-day operational aspects, including project management, resource allocation, and performance monitoring. CISA candidates delve into the principles of IT management to comprehend how organizations optimize their IT resources to meet business requirements. This involves understanding project life cycles, change management processes, and the effective utilization of technology resources to support organizational objectives.
Strategic alignment of IT with business goals is a key theme within this domain. Candidates explore how IT strategies are developed and how they align with and contribute to the achievement of broader organizational objectives. This involves a holistic understanding of the organization's mission, vision, and business strategies, and how IT can be leveraged as an enabler and catalyst for achieving those strategic objectives.
The "Governance and Management of IT" domain within the CISA certification underscores the critical role that effective governance, strategic alignment, and day-to-day management play in the successful integration of IT within an organization. Mastery of these concepts not only positions professionals for success in the CISA exam but equips them to contribute significantly to the development and implementation of robust IT governance practices within their respective organizations.
Information Systems Acquisition, Development, and Implementation
The domain of "Information Systems Acquisition, Development, and Implementation" constitutes a crucial segment of the Certified Information Systems Auditor (CISA) certification, focusing on the life cycle of information systems within an organizational context. This domain encompasses the processes involved in acquiring, developing, and implementing information systems to meet the strategic objectives of the organization while adhering to best practices and industry standards.
Beginning with the acquisition phase, CISA candidates explore the methodologies and considerations involved in procuring information systems. This involves understanding the organization's needs, conducting vendor assessments, and ensuring that the selected systems align with the organization's overall goals. The acquisition process extends to contract management, where candidates delve into the intricacies of negotiating, drafting, and managing contracts to safeguard the interests of the organization.
Moving into the development phase, candidates explore the Software Development Life Cycle (SDLC) and related methodologies. This includes understanding the planning, design, coding, testing, and deployment stages of system development. Emphasis is placed on incorporating security and control measures at every stage to mitigate risks associated with software vulnerabilities and ensure the reliability of the developed systems.
Implementation is a critical phase in which information systems are deployed into the operational environment. Candidates examine strategies for a smooth transition from development to production, considering aspects such as data migration, system integration, and user training. Effective implementation necessitates a keen understanding of change management processes to minimize disruptions and ensure that the new systems align seamlessly with existing organizational structures.
The "Information Systems Acquisition, Development, and Implementation" domain within the CISA certification equips professionals with the knowledge and skills necessary to navigate the complex process of bringing information systems from conceptualization to operational use. Mastery of this domain not only prepares individuals for success in the CISA exam but positions them to contribute effectively to the secure and efficient integration of information systems within their organizations.
Information Systems Operations and Business Resilience
The domain of "Information Systems Operations and Business Resilience" is a pivotal aspect of the Certified Information Systems Auditor (CISA) certification, emphasizing the operational aspects and resilience measures that organizations must implement to ensure the continuous availability and security of their information systems. This domain, a key focus of the CISA exam, explores the critical intersection between IT operations and the ability of a business to withstand and recover from disruptions.
In the realm of information systems operations, CISA candidates delve into the principles of IT service management. This involves understanding how IT services are delivered, monitored, and optimized to meet the organization's business objectives. Candidates explore best practices such as ITIL (Information Technology Infrastructure Library) to enhance the efficiency and effectiveness of IT operations. Attention is given to incident management, problem resolution, and the implementation of service-level agreements to ensure the seamless functioning of information systems.
Business resilience is a core theme within this domain, encompassing the strategies and measures organizations adopt to withstand and recover from disruptions. Candidates study business continuity planning, which involves developing and implementing strategies to maintain essential business functions during and after disruptions. Disaster recovery planning is also explored, focusing on the restoration of IT services and data in the aftermath of a catastrophic event. CISA professionals play a crucial role in evaluating the effectiveness of these plans, ensuring they align with organizational objectives and industry best practices.
Protection of Information Assets
The "Protection of Information Assets" domain is a critical facet of the Certified Information Systems Auditor (CISA) certification, focusing on the safeguarding of information assets against unauthorized access, disclosure, alteration, destruction, and disruption. As a core element of the CISA exam, this domain equips professionals with the knowledge and skills needed to fortify an organization's information security posture and mitigate potential risks.
Central to this domain is the exploration of fundamental principles and concepts related to information security. CISA candidates delve into the core components of information security frameworks, gaining insights into the establishment and maintenance of a robust security infrastructure. Emphasis is placed on understanding the significance of policies, procedures, and standards that govern information security practices within an organization.
Access controls represent a key aspect of protecting information assets, and candidates within this domain learn to assess and enhance these controls effectively. This involves understanding the principles of least privilege, role-based access, and identity management. Additionally, encryption methods and techniques for securing data both in transit and at rest are explored, ensuring the confidentiality and integrity of sensitive information.
Exam Strategies and Post-Certification Career Planning
"Exam Strategies and Post-Certification Career Planning" marks the culmination of the Certified Information Systems Auditor (CISA) certification journey, providing candidates with insights on navigating the final stages of exam preparation and charting a strategic course for their professional future. This crucial section of the guide addresses not only the tactical considerations for success on exam day but also the broader perspective of leveraging the CISA certification for long-term career growth.
In terms of exam strategies, candidates are encouraged to adopt a systematic and organized approach to their final preparations. This involves revisiting key concepts, reinforcing weak areas identified during practice exams, and ensuring a comprehensive review of all domains. Time management is paramount, and candidates should practice effective time allocation to answer each section of the exam thoroughly. Familiarity with the exam format, types of questions, and the pace at which questions should be tackled contributes significantly to confidence on the day of the examination.
Post-certification career planning is a critical aspect that extends beyond the examination room. CISA professionals are equipped with sought-after skills in information systems auditing and security, positioning them for various career paths within the cybersecurity landscape. Candidates are encouraged to identify and pursue avenues that align with their interests and career aspirations, whether it be in roles such as IT auditor, cybersecurity analyst, or information security manager.
In essence, the section on "Exam Strategies and Post-Certification Career Planning" serves as a compass for candidates as they navigate the final leg of their CISA certification journey. Armed with a comprehensive understanding of exam tactics and a strategic mindset for career advancement, certified professionals are well-positioned to contribute significantly to the ever-evolving landscape of information systems auditing and security.
Conclusion
In conclusion, "The Ultimate Guide to CISA Certification: A Step-by-Step Process" provides a comprehensive roadmap for individuals aspiring to achieve the esteemed Certified Information Systems Auditor (CISA) certification. This guide has meticulously navigated through the essential components of the certification journey, offering insights into eligibility criteria, exam registration, and the selection of effective study materials. By breaking down the exam domains, including information system auditing, governance, acquisition, development, operations, and protection of information assets, the guide aims to empower candidates with the knowledge and skills needed to excel in the CISA examination.
The journey begins with understanding the significance of CISA certification in the dynamic landscape of cybersecurity and progresses through creating a personalized study plan, exploring recommended study materials, and honing in on exam strategies. Each step is designed to not only facilitate success in the certification exam but also to cultivate a deep understanding of the principles that underpin effective information system governance and security.
As the guide addresses the post-certification phase, it emphasizes the importance of ethical conduct, networking, and continuous learning in shaping a successful and fulfilling career in the field of information systems auditing and security. The concluding sections provide a holistic view of the CISA certification journey, encouraging individuals not only to pass the exam but also to leverage their certification for ongoing professional growth and contribution to the cybersecurity community.
Read More
In the dynamic landscape of information technology and cybersecurity, professionals seek validation and recognition of their expertise to stay ahead in the field. One such coveted credential is the Certified Information Systems Auditor (CISA) certification. As organizations grapple with increasing cyber threats and the need for robust information systems, the demand for skilled individuals who can assess and secure these systems has never been higher. This guide aims to be the compass for those navigating the challenging yet rewarding journey towards achieving the CISA certification, providing a comprehensive and step-by-step process to empower aspiring professionals with the knowledge and skills required to excel in this critical domain.
At its core, the CISA certification is a testament to an individual's proficiency in auditing, controlling, and ensuring the security of information systems. Whether you are an IT professional looking to enhance your career prospects or a recent graduate aspiring to enter the world of cybersecurity, this guide is designed to demystify the CISA certification process. From understanding the foundational concepts to mastering the intricacies of information system auditing, each section of this guide is crafted to provide clarity and insight. As we embark on this journey together, the goal is not just to pass an exam but to grasp the underlying principles that define effective information system governance and security.
The guide will unfold in a logical sequence, breaking down the CISA certification process into manageable steps. It begins with an exploration of the CISA certification itself – its significance in the industry, the skills it validates, and the career opportunities it opens up. Subsequent chapters will delve into the core domains covered by the CISA exam, offering in-depth insights into information system auditing, control, and security. Practical tips, real-world examples, and interactive exercises will be interspersed throughout the guide to reinforce understanding and facilitate hands-on learning.
Whether you are a seasoned professional seeking to validate your expertise or a newcomer eager to make a mark in the world of cybersecurity, "The Ultimate Guide to CISA Certification: A Step-by-Step Process" is your roadmap to success. As we navigate through the intricacies of the CISA certification journey, this guide will serve as a reliable companion, providing guidance, knowledge, and inspiration to help you achieve your professional aspirations in the realm of information systems auditing and security.
Table of contents
-
Introduction to CISA Certification
-
Creating a Study Plan
-
Eligibility and Exam Registration
-
Recommended Study Materials
-
The Process of Auditing Information Systems
-
Governance and Management of IT
-
Information Systems Acquisition, Development, and Implementation
-
Information Systems Operations and Business Resilience
-
Protection of Information Assets
-
Exam Strategies and Post-Certification Career Planning
-
Conclusion
Introduction to CISA Certification
In the rapidly evolving landscape of cybersecurity, the Certified Information Systems Auditor (CISA) certification stands as a beacon of proficiency and recognition for individuals navigating the complex realm of information systems. CISA, administered by ISACA (Information Systems Audit and Control Association), has become a hallmark for professionals seeking to validate their skills in auditing, controlling, and ensuring the security of information systems. As organizations worldwide grapple with escalating cyber threats, the demand for certified individuals who can effectively assess and fortify information systems has reached unprecedented heights. The introduction to CISA certification serves as the foundational chapter in our guide, shedding light on the significance of this credential within the broader context of the cybersecurity industry.
CISA certification is more than a mere accolade; it is a testament to an individual's dedication and competence in safeguarding vital information assets. In this introductory section, we explore the multifaceted aspects of CISA, delving into its role as a professional milestone and examining the various ways in which it contributes to career advancement. As we embark on this comprehensive guide, the primary objective is to demystify the CISA certification process and empower aspiring professionals with the knowledge and skills essential for success in this critical field. By understanding the fundamental principles that underpin CISA, individuals can not only excel in the certification exam but also apply this knowledge in real-world scenarios, making meaningful contributions to information system governance and security.
Creating a Study Plan
Creating a well-structured and effective study plan is a crucial step in the preparation journey for the Certified Information Systems Auditor (CISA) certification. A thoughtful and organized approach not only optimizes study time but also enhances the retention of critical concepts. In this section, we delve into the key components of crafting a personalized study plan tailored to the unique needs and commitments of each aspiring CISA candidate.
Structure your study plan around the five domains of the CISA exam, dedicating specific blocks of time to each domain. This ensures comprehensive coverage of all topics and prevents overlooking any critical areas. Break down the domains into smaller topics, allowing for a more detailed and manageable study approach.
Consider incorporating a variety of study resources, including official ISACA materials, textbooks, online courses, and practice exams. A diverse range of resources helps cater to different learning styles and provides a more holistic understanding of the subject matter.
Balance your study sessions with breaks to avoid burnout and improve overall concentration. Consistency is key, so establish a routine that aligns with your daily schedule. Whether you choose to study in the morning, afternoon, or evening, maintaining a consistent study routine aids in building a habit and optimizing information retention.
CISA candidates can develop a comprehensive and personalized study plan that aligns with their unique strengths, weaknesses, and schedules. This proactive approach lays the groundwork for a more confident and successful performance on the CISA certification exam.
Eligibility and Exam Registration
Eligibility for the CISA exam is typically contingent on a combination of educational background and professional experience. Candidates commonly hold a bachelor's degree from an accredited institution, preferably in information systems, accounting, or a related field. Additionally, they are required to possess a minimum of five years of professional work experience in information systems, with at least three years spent in roles related to information system auditing, control, or security. Alternatively, a maximum of three years can be waived for individuals with certain degrees or specific professional certifications.
Once eligibility is established, the next crucial step is the exam registration process. ISACA, the governing body overseeing CISA certification, provides a user-friendly online platform for candidates to register. During this process, candidates are required to submit documentation supporting their eligibility, such as proof of education and work experience. It is imperative for candidates to carefully review and adhere to the deadlines and guidelines outlined by ISACA to ensure a smooth registration experience.
As part of the registration, candidates may also need to pay the required examination fees. These fees can vary based on factors such as ISACA membership status, early registration discounts, or exam location. Being aware of these financial aspects is essential for candidates planning their budget for the certification process.
Navigating eligibility requirements and completing the exam registration process sets the stage for a candidate's CISA certification journey. This foundational understanding ensures that individuals meet the necessary criteria and successfully enroll in the examination, providing them with the opportunity to showcase their expertise in information system auditing and security. Aspiring CISA professionals should approach this phase with meticulous attention to detail, as it forms the cornerstone of their pursuit of excellence in the field of cybersecurity.
Recommended Study Materials
Preparing for the Certified Information Systems Auditor (CISA) certification requires a strategic selection of study materials to ensure a thorough understanding of the exam domains. One of the primary resources recommended for candidates is the official ISACA material, which includes the CISA Review Manual. Published by ISACA, this comprehensive guide serves as a foundational reference, covering all five domains extensively. Additionally, the CISA Review Questions, Answers & Explanations Manual, also provided by ISACA, offers valuable practice questions with detailed explanations, allowing candidates to assess their comprehension and hone their problem-solving skills.
Supplementing official ISACA resources, various textbooks contribute to a well-rounded study plan. "CISA Certified Information Systems Auditor Study Guide" by David L. Cannon is widely regarded for its coverage of exam topics, including practical insights and practice questions. Another valuable resource is "CISA Exam Guide" by Peter H. Gregory, providing an in-depth examination of CISA domains alongside real-world examples, aiding candidates in grasping the practical applications of their knowledge.
Online courses and training programs play a crucial role in dynamic and interactive learning. ISACA's official online training courses are led by experienced instructors and offer an engaging way to reinforce key concepts. For those seeking a different approach, Cybrary's CISA Course provides a comprehensive video-based learning experience, covering exam domains and enhancing understanding through visual explanations.
Practice exams are integral to exam preparation, and ISACA's CISA Practice Questions Database offers an official platform to simulate exam conditions. This resource helps candidates familiarize themselves with the exam format, identify areas of weakness, and build confidence in their knowledge. Additionally, leveraging various online platforms that provide CISA practice exams allows candidates to access a diverse range of questions and test their readiness comprehensively.
Lastly, study groups and forums foster a sense of community and shared learning. ISACA's Online Community provides a platform for candidates to connect with each other and certified professionals, offering valuable insights, tips, and support. Local study groups, whether virtual or in-person, allow candidates to discuss challenging topics collaboratively, share experiences, and gain perspectives from peers on effective study strategies.
The Process of Auditing Information Systems
The process of auditing information systems is a critical component of the Certified Information Systems Auditor (CISA) certification and plays a pivotal role in ensuring the effectiveness and security of an organization's information infrastructure. This domain, encompassing the first section of the CISA exam, delves into the methodologies and practices involved in systematically reviewing and evaluating information systems.
At its core, the process of auditing information systems begins with meticulous planning. Audit planning involves defining the scope and objectives of the audit, understanding the business processes, and identifying the key risks associated with the information systems under review. This phase sets the foundation for the entire audit process, guiding auditors in determining the appropriate approach and resources required.
The execution phase involves the systematic examination of controls, procedures, and documentation within the information systems. Auditors assess the design and implementation of controls to ensure they align with industry standards and organizational policies. Throughout this phase, a focus is placed on identifying vulnerabilities, potential risks, and deviations from established best practices. The process involves both technical assessments of IT systems and a broader evaluation of management and operational controls.
Understanding the intricacies of the auditing process is essential for CISA candidates, as it forms the basis for a significant portion of the certification exam. Mastery of this domain not only prepares professionals to excel in the examination but also equips them with the skills necessary to contribute to robust information system governance and security within their respective organizations.
Governance and Management of IT
The domain of "Governance and Management of IT" represents a pivotal aspect of the Certified Information Systems Auditor (CISA) certification, reflecting the broader organizational context in which information systems operate. This domain, constituting a substantial portion of the CISA exam, delves into the governance frameworks, management practices, and strategic alignment of IT within an organization.
Governance, as it relates to IT, involves the establishment and implementation of policies, procedures, and decision-making structures to ensure that IT resources are utilized effectively and aligned with the organization's goals. CISA candidates explore various IT governance frameworks, such as COBIT (Control Objectives for Information and Related Technologies), to understand how these frameworks facilitate the alignment of IT strategies with overall business objectives. Governance practices extend to risk management, ensuring that organizations identify, assess, and manage risks associated with their IT environments.
The management of IT encompasses the day-to-day operational aspects, including project management, resource allocation, and performance monitoring. CISA candidates delve into the principles of IT management to comprehend how organizations optimize their IT resources to meet business requirements. This involves understanding project life cycles, change management processes, and the effective utilization of technology resources to support organizational objectives.
Strategic alignment of IT with business goals is a key theme within this domain. Candidates explore how IT strategies are developed and how they align with and contribute to the achievement of broader organizational objectives. This involves a holistic understanding of the organization's mission, vision, and business strategies, and how IT can be leveraged as an enabler and catalyst for achieving those strategic objectives.
The "Governance and Management of IT" domain within the CISA certification underscores the critical role that effective governance, strategic alignment, and day-to-day management play in the successful integration of IT within an organization. Mastery of these concepts not only positions professionals for success in the CISA exam but equips them to contribute significantly to the development and implementation of robust IT governance practices within their respective organizations.
Information Systems Acquisition, Development, and Implementation
The domain of "Information Systems Acquisition, Development, and Implementation" constitutes a crucial segment of the Certified Information Systems Auditor (CISA) certification, focusing on the life cycle of information systems within an organizational context. This domain encompasses the processes involved in acquiring, developing, and implementing information systems to meet the strategic objectives of the organization while adhering to best practices and industry standards.
Beginning with the acquisition phase, CISA candidates explore the methodologies and considerations involved in procuring information systems. This involves understanding the organization's needs, conducting vendor assessments, and ensuring that the selected systems align with the organization's overall goals. The acquisition process extends to contract management, where candidates delve into the intricacies of negotiating, drafting, and managing contracts to safeguard the interests of the organization.
Moving into the development phase, candidates explore the Software Development Life Cycle (SDLC) and related methodologies. This includes understanding the planning, design, coding, testing, and deployment stages of system development. Emphasis is placed on incorporating security and control measures at every stage to mitigate risks associated with software vulnerabilities and ensure the reliability of the developed systems.
Implementation is a critical phase in which information systems are deployed into the operational environment. Candidates examine strategies for a smooth transition from development to production, considering aspects such as data migration, system integration, and user training. Effective implementation necessitates a keen understanding of change management processes to minimize disruptions and ensure that the new systems align seamlessly with existing organizational structures.
The "Information Systems Acquisition, Development, and Implementation" domain within the CISA certification equips professionals with the knowledge and skills necessary to navigate the complex process of bringing information systems from conceptualization to operational use. Mastery of this domain not only prepares individuals for success in the CISA exam but positions them to contribute effectively to the secure and efficient integration of information systems within their organizations.
Information Systems Operations and Business Resilience
The domain of "Information Systems Operations and Business Resilience" is a pivotal aspect of the Certified Information Systems Auditor (CISA) certification, emphasizing the operational aspects and resilience measures that organizations must implement to ensure the continuous availability and security of their information systems. This domain, a key focus of the CISA exam, explores the critical intersection between IT operations and the ability of a business to withstand and recover from disruptions.
In the realm of information systems operations, CISA candidates delve into the principles of IT service management. This involves understanding how IT services are delivered, monitored, and optimized to meet the organization's business objectives. Candidates explore best practices such as ITIL (Information Technology Infrastructure Library) to enhance the efficiency and effectiveness of IT operations. Attention is given to incident management, problem resolution, and the implementation of service-level agreements to ensure the seamless functioning of information systems.
Business resilience is a core theme within this domain, encompassing the strategies and measures organizations adopt to withstand and recover from disruptions. Candidates study business continuity planning, which involves developing and implementing strategies to maintain essential business functions during and after disruptions. Disaster recovery planning is also explored, focusing on the restoration of IT services and data in the aftermath of a catastrophic event. CISA professionals play a crucial role in evaluating the effectiveness of these plans, ensuring they align with organizational objectives and industry best practices.
Protection of Information Assets
The "Protection of Information Assets" domain is a critical facet of the Certified Information Systems Auditor (CISA) certification, focusing on the safeguarding of information assets against unauthorized access, disclosure, alteration, destruction, and disruption. As a core element of the CISA exam, this domain equips professionals with the knowledge and skills needed to fortify an organization's information security posture and mitigate potential risks.
Central to this domain is the exploration of fundamental principles and concepts related to information security. CISA candidates delve into the core components of information security frameworks, gaining insights into the establishment and maintenance of a robust security infrastructure. Emphasis is placed on understanding the significance of policies, procedures, and standards that govern information security practices within an organization.
Access controls represent a key aspect of protecting information assets, and candidates within this domain learn to assess and enhance these controls effectively. This involves understanding the principles of least privilege, role-based access, and identity management. Additionally, encryption methods and techniques for securing data both in transit and at rest are explored, ensuring the confidentiality and integrity of sensitive information.
Exam Strategies and Post-Certification Career Planning
"Exam Strategies and Post-Certification Career Planning" marks the culmination of the Certified Information Systems Auditor (CISA) certification journey, providing candidates with insights on navigating the final stages of exam preparation and charting a strategic course for their professional future. This crucial section of the guide addresses not only the tactical considerations for success on exam day but also the broader perspective of leveraging the CISA certification for long-term career growth.
In terms of exam strategies, candidates are encouraged to adopt a systematic and organized approach to their final preparations. This involves revisiting key concepts, reinforcing weak areas identified during practice exams, and ensuring a comprehensive review of all domains. Time management is paramount, and candidates should practice effective time allocation to answer each section of the exam thoroughly. Familiarity with the exam format, types of questions, and the pace at which questions should be tackled contributes significantly to confidence on the day of the examination.
Post-certification career planning is a critical aspect that extends beyond the examination room. CISA professionals are equipped with sought-after skills in information systems auditing and security, positioning them for various career paths within the cybersecurity landscape. Candidates are encouraged to identify and pursue avenues that align with their interests and career aspirations, whether it be in roles such as IT auditor, cybersecurity analyst, or information security manager.
In essence, the section on "Exam Strategies and Post-Certification Career Planning" serves as a compass for candidates as they navigate the final leg of their CISA certification journey. Armed with a comprehensive understanding of exam tactics and a strategic mindset for career advancement, certified professionals are well-positioned to contribute significantly to the ever-evolving landscape of information systems auditing and security.
Conclusion
In conclusion, "The Ultimate Guide to CISA Certification: A Step-by-Step Process" provides a comprehensive roadmap for individuals aspiring to achieve the esteemed Certified Information Systems Auditor (CISA) certification. This guide has meticulously navigated through the essential components of the certification journey, offering insights into eligibility criteria, exam registration, and the selection of effective study materials. By breaking down the exam domains, including information system auditing, governance, acquisition, development, operations, and protection of information assets, the guide aims to empower candidates with the knowledge and skills needed to excel in the CISA examination.
The journey begins with understanding the significance of CISA certification in the dynamic landscape of cybersecurity and progresses through creating a personalized study plan, exploring recommended study materials, and honing in on exam strategies. Each step is designed to not only facilitate success in the certification exam but also to cultivate a deep understanding of the principles that underpin effective information system governance and security.
As the guide addresses the post-certification phase, it emphasizes the importance of ethical conduct, networking, and continuous learning in shaping a successful and fulfilling career in the field of information systems auditing and security. The concluding sections provide a holistic view of the CISA certification journey, encouraging individuals not only to pass the exam but also to leverage their certification for ongoing professional growth and contribution to the cybersecurity community.
The Evolution of OpenAI: A Historical Perspective
In the ever-evolving landscape of artificial intelligence, OpenAI stands as a pioneering force that has shaped the trajectory of AI research and development. From its inception to its current stature, tracing the historical journey of OpenAI provides a captivating narrative of innovation, challenges, and breakthroughs that have redefined the possibilities of machine intelligence.
OpenAI emerged with a visionary mission to ensure that artificial general intelligence (AGI) benefits all of humanity. As we delve into the historical tapestry of OpenAI's evolution, we witness the organization's commitment to cutting-edge research, ethical considerations, and collaborative partnerships that have propelled it to the forefront of the AI community.
This historical perspective explores the milestones, key projects, and pivotal moments that have shaped OpenAI's identity. From the early days of formulating its charter to navigating the complexities of AI ethics, the journey unfolds against the backdrop of technological advancements, societal implications, and the dynamic interplay between humans and machines.
"The Evolution of OpenAI: A Historical Perspective" invites readers to explore the fascinating narrative of a trailblazing entity that continues to push the boundaries of what is possible in the realm of artificial intelligence, weaving together a story that goes beyond technological advancements to encompass the broader impact on society and the ethical considerations that accompany the rise of intelligent machines.
Table of contents
-
Inception and Founding Moments
-
Early Research Projects
-
The OpenAI Charter
-
Pioneering Technologies
-
Strategic Collaborations
-
Leadership Transitions and Changes
-
Ethical Considerations and Responsible AI
-
Open Source Initiatives
-
Public Perception and Media Influence
-
The Evolution of AGI Ambitions
-
Conclusion
Inception and Founding Moments
The inception of OpenAI marked a pivotal moment in the landscape of artificial intelligence, arising from a confluence of visionary ideas and a collective commitment to shaping the future of machine intelligence. Founded in [year], OpenAI emerged as a response to the growing recognition of the transformative potential of AI and the need to ensure that its benefits would be universally accessible and beneficial for humanity. The founding moments of OpenAI reflect the amalgamation of the intellects of notable individuals, including [founders' names], who shared a common vision of steering AI development towards ethical, transparent, and globally beneficial outcomes.
The initial impetus for OpenAI stemmed from a deep-seated belief that the trajectory of AI development should be guided by principles aligned with human welfare, safety, and broad societal impact. The founders envisioned an organization capable of navigating the complex terrain of AI research while prioritizing the long-term well-being of humanity. This founding ethos is encapsulated in the OpenAI Charter, a foundational document that articulates the organization's commitment to principles such as broadly distributed benefits, long-term safety, technical leadership, and cooperative orientation.
The early days of OpenAI were characterized by a fervent dedication to groundbreaking research, laying the groundwork for the organization's subsequent influence in the field. Initial projects and research initiatives showcased a commitment to pushing the boundaries of AI capabilities, reflecting the founders' ambition to foster advancements that transcend narrow applications and contribute to the broader understanding of artificial general intelligence (AGI).
Early Research Projects
The early research projects undertaken by OpenAI reflected a diverse range of interests and challenges within the realm of artificial intelligence. From natural language processing to reinforcement learning and robotics, the organization's multidisciplinary approach showcased a holistic understanding of the complexities inherent in developing intelligent systems. These projects not only sought to address immediate technical challenges but also contributed valuable knowledge to the broader scientific community, aligning with OpenAI's commitment to transparency and knowledge sharing.
As OpenAI delved into these early research endeavors, the organization not only honed its technical expertise but also solidified its position as a thought leader in the AI community. The results of these projects not only contributed to advancements in AI but also set the stage for subsequent, more ambitious initiatives, ultimately shaping the trajectory of OpenAI's research agenda and reinforcing its commitment to excellence in artificial intelligence.
In essence, the early research projects of OpenAI were not just scientific pursuits; they were the building blocks of a legacy that would unfold over time, influencing the organization's reputation and impact in the dynamic landscape of artificial intelligence. These projects were a testament to OpenAI's capacity to innovate, learn, and pave the way for the evolution of AI research on a global scale.
The OpenAI Charter
At the heart of OpenAI's guiding principles lies the seminal document known as the OpenAI Charter, a visionary manifesto that articulates the organization's core values, mission, and its unwavering commitment to shaping the trajectory of artificial intelligence for the benefit of humanity. Formulated during the early stages of OpenAI's existence, the charter serves as a compass, providing direction and purpose to the organization's endeavors in the complex and rapidly evolving field of AI.
The OpenAI Charter outlines key tenets that underscore the organization's philosophy. It emphasizes the importance of ensuring that artificial general intelligence (AGI) benefits all of humanity, avoiding uses of AI that could harm humanity or unduly concentrate power. By committing to broadly distributed benefits, OpenAI signals its intention to employ any influence it obtains over AGI's deployment to ensure it is used for the benefit of all and avoids uses that could harm humanity or unduly concentrate power.
The OpenAI Charter serves as a foundational document that not only sets the ethical standards for OpenAI's research and development but also provides a framework for responsible and accountable innovation in the realm of artificial intelligence. It stands as a testament to the organization's commitment to transparency, ethical considerations, and the overarching goal of ensuring that the evolution of AI aligns with the best interests of humanity.
Pioneering Technologies
OpenAI's trajectory in the realm of artificial intelligence is characterized by a series of groundbreaking technologies that have not only redefined the boundaries of machine intelligence but have also positioned the organization as a trailblazer in the global AI landscape. From its inception, OpenAI has consistently demonstrated a commitment to innovation, pushing the envelope in various domains of AI research.
One of OpenAI's pioneering technologies is exemplified in the realm of natural language processing with projects like GPT (Generative Pre-trained Transformer) models. These models have showcased unprecedented language understanding and generation capabilities, enabling applications ranging from language translation to content generation. GPT-3, in particular, represents a culmination of advancements in large-scale pre-training and has garnered attention for its ability to generate human-like text across diverse contexts.
OpenAI's ventures into unsupervised learning and transfer learning have also marked pioneering advancements. By enabling AI models to generalize knowledge from one domain to another and learn from unannotated data, OpenAI contributes to the development of more versatile and adaptable systems. This approach has implications for addressing challenges in diverse fields, such as healthcare, where transfer learning can be applied to leverage knowledge gained in one medical domain for tasks in another.
The organization's commitment to safety and ethical considerations is intertwined with its technological breakthroughs. OpenAI is actively engaged in addressing concerns related to bias in AI systems, interpretability of models, and the potential societal impacts of advanced technologies. This holistic approach reflects OpenAI's recognition that pioneering technologies must be developed responsibly to ensure positive and equitable outcomes for humanity.
OpenAI's portfolio of pioneering technologies stands as a testament to its dedication to advancing the frontiers of AI. As the organization continues to explore the possibilities of Artificial General Intelligence (AGI), these technological milestones not only showcase the current state of the art but also illuminate the path forward in shaping the future of intelligent systems with ethical considerations at the forefront.
Strategic Collaborations
OpenAI's evolution in the landscape of artificial intelligence has been profoundly influenced by a strategic and purposeful approach to collaborations, emphasizing the organization's commitment to fostering innovation, addressing challenges, and shaping the responsible development of AI technologies. These strategic collaborations extend across diverse domains, showcasing OpenAI's recognition that the complexity of AI requires a collaborative and multidisciplinary effort.
OpenAI's engagements with academic and research institutions play a pivotal role in shaping the cutting edge of AI knowledge. Collaborations with universities and research labs foster an environment of knowledge exchange, peer review, and shared exploration of AI's frontiers. Through these partnerships, OpenAI contributes to the academic discourse while staying at the forefront of emerging research trends and methodologies.
OpenAI's cooperative orientation, as outlined in its Charter, extends to collaborations on a global scale. Actively engaging with research and policy institutions worldwide, OpenAI contributes to the establishment of a collaborative international community addressing the challenges and opportunities presented by Artificial General Intelligence (AGI). These collaborations promote the sharing of diverse perspectives and the development of a collective understanding of the global implications of advanced AI technologies.
OpenAI's strategic collaborations are a testament to its holistic and inclusive approach to AI development. By partnering with industry, academia, ethical organizations, and global stakeholders, OpenAI positions itself at the intersection of diverse perspectives and expertise, contributing to the advancement of AI technologies in a manner that aligns with ethical principles and benefits humanity as a whole. These collaborations not only enrich OpenAI's research initiatives but also foster a collaborative ecosystem essential for the responsible evolution of artificial intelligence.
Leadership Transitions and Changes
Leadership transitions within OpenAI have often been pivotal moments, influencing the strategic direction and focus of the organization. Changes in key leadership roles, such as the appointment of new CEOs or the introduction of influential figures to the leadership team, have played a crucial role in shaping OpenAI's response to evolving technological, ethical, and regulatory landscapes.
One notable aspect of OpenAI's leadership transitions is the organization's ability to balance continuity with innovation. As new leaders join the ranks, they often bring fresh perspectives, diverse expertise, and novel approaches to addressing the challenges of AI. These transitions are not merely changes in personnel; they represent strategic decisions aimed at steering OpenAI toward its long-term goals, often aligning with shifts in the broader AI ecosystem.
Organizational changes within OpenAI extend beyond leadership transitions to encompass structural adaptations and shifts in research priorities. These changes are reflective of the organization's commitment to staying at the forefront of AI advancements. As the field evolves, OpenAI has demonstrated a capacity for organizational flexibility, adjusting its structure and focus areas to align with emerging trends and breakthroughs.
Leadership transitions and organizational changes within OpenAI are integral elements of the organization's evolution. These moments reflect not only the adaptability of OpenAI but also its resilience in the face of an ever-changing AI landscape. By embracing new leadership, adjusting organizational structures, and maintaining transparency, OpenAI navigates transitions with a focus on sustained excellence in AI research and development.
Ethical Considerations and Responsible AI
Ethical considerations and the pursuit of responsible artificial intelligence (AI) stand as foundational tenets in OpenAI's mission, providing a moral compass that has guided the organization's trajectory from its inception. Recognizing the far-reaching implications of AI technologies on individuals and society, OpenAI places a paramount emphasis on infusing ethical principles into every facet of its research, development, and deployment processes.
A central element of OpenAI's ethical commitment manifests in its proactive stance toward identifying and rectifying potential biases within AI systems. The organization acknowledges the inherent risk of perpetuating societal biases through algorithms and actively engages in efforts to mitigate these biases. OpenAI's dedication lies in the cultivation of AI systems that prioritize fairness, impartiality, and inclusivity, thereby minimizing the potential for discriminatory outcomes.
OpenAI's ethical considerations extend further to the imperative of ensuring equitable distribution of the benefits arising from AI technologies. The organization actively works to avoid scenarios where AI could be harnessed to the detriment of humanity or concentrated in ways that unduly consolidate power. This commitment aligns with OpenAI's core principle of utilizing any influence over AGI's deployment to guarantee benefits for all of humanity, emphasizing a global perspective that transcends individual interests.
OpenAI's unwavering commitment to ethical considerations and responsible AI reflects a profound awareness of the societal impact of AI technologies. Through a commitment to transparency, fairness, inclusivity, and a proactive stance on safety, OpenAI aspires to not only be a leader in the technological advancements of AI but also to set the ethical standards that should underpin the development of intelligent systems for the collective benefit of humanity.
Open Source Initiatives
Open Source Initiatives form a pivotal aspect of OpenAI's ethos, embodying the organization's commitment to openness, collaboration, and knowledge sharing within the broader artificial intelligence (AI) community. From its inception, OpenAI has actively embraced the principles of open source, recognizing the transformative potential of making AI research and tools accessible to a wider audience.
One significant dimension of OpenAI's open source endeavors is the release of research papers and findings to the public domain. By sharing the outcomes of its research, OpenAI contributes to the collective intelligence of the AI community, fostering an environment where researchers and practitioners can build upon each other's work. This commitment to transparency extends to providing insights into the methodologies, challenges, and breakthroughs, enabling a collaborative discourse that advances the state of the art in AI.
OpenAI's engagement in open source initiatives is not confined solely to its own developments. The organization actively supports and contributes to existing open source projects, reinforcing a collaborative spirit that transcends organizational boundaries. By participating in the wider ecosystem, OpenAI enriches the collective pool of resources, expertise, and ideas, contributing to the growth and maturation of the global AI community.
OpenAI's Open Source Initiatives exemplify a dedication to fostering collaboration, transparency, and inclusivity in the AI landscape. By embracing open source principles, the organization not only contributes to the advancement of AI but also cultivates a vibrant and collaborative ecosystem that transcends organizational boundaries, ultimately shaping the future of artificial intelligence through shared knowledge and innovation.
Public Perception and Media Influence
Public perception and media influence play significant roles in shaping the narrative around OpenAI, influencing how the organization and its endeavors are perceived by the broader community. As a pioneering force in artificial intelligence (AI), OpenAI's impact extends beyond the scientific community, and the organization is keenly aware of the importance of public understanding and support for its mission.
The portrayal of OpenAI in the media serves as a lens through which the public views the organization's contributions and potential implications. Media coverage often reflects the broader societal sentiment towards AI, and as such, OpenAI actively engages with the media to communicate its goals, achievements, and the ethical considerations that underpin its work. Managing public perceptions is crucial for OpenAI as it strives to foster an environment of trust and transparency, dispelling misconceptions and promoting informed discussions about the future of AI.
The media's influence on public perception is intricately tied to how AI is portrayed in popular culture. OpenAI's initiatives and breakthroughs, when covered by the media, contribute to shaping public attitudes towards the capabilities and impact of AI technologies. Positive portrayals can foster excitement and enthusiasm for the possibilities of AI, while negative portrayals can generate apprehension and concerns. OpenAI actively addresses these dynamics by providing accurate information and context, ensuring that the public is informed about the organization's commitment to responsible AI development.
The interplay between public perception and media influence is a dynamic aspect of OpenAI's journey. The organization's commitment to transparency, responsible AI development, and active engagement with the public and media reflects its dedication to shaping a narrative that aligns with ethical principles, fosters trust, and promotes a collective understanding of the transformative potential of artificial intelligence.
The Evolution of AGI Ambitions
The Evolution of Artificial General Intelligence (AGI) Ambitions at OpenAI represents a dynamic narrative that reflects the organization's continual refinement and adaptation of its long-term goals in the ever-evolving landscape of artificial intelligence. From its inception, OpenAI's mission has been deeply intertwined with the pursuit of AGI—an advanced form of artificial intelligence capable of outperforming humans across a wide range of economically valuable tasks.
The early phases of OpenAI's AGI ambitions were marked by a visionary commitment to ensuring that AGI benefits all of humanity. The organization recognized the transformative potential of AGI and aimed to prevent uses that could harm humanity or unduly concentrate power. This foundational principle, enshrined in the OpenAI Charter, set the ethical tone for the organization's trajectory, emphasizing a responsibility to guide AGI development in a manner that prioritizes broad societal benefits.
The evolution of AGI ambitions at OpenAI is a narrative marked by continual refinement, ethical considerations, and a commitment to proactive safety measures. From visionary beginnings to nuanced revisions, OpenAI's trajectory reflects an ongoing dedication to steering AGI development in a manner that aligns with the principles of broad benefit, safety, and global cooperation. As the organization navigates the path towards AGI, its evolution underscores the importance of responsible AI development in shaping the future of artificial intelligence.
Conclusion
In conclusion, the journey of OpenAI, encapsulated in its historical evolution, ethical considerations, and pursuit of responsible artificial intelligence, paints a portrait of an organization at the forefront of the AI landscape. From its inception, OpenAI has not only been a catalyst for groundbreaking research and technological advancements but has also established itself as a standard-bearer for ethical AI development.
The OpenAI Charter, with its foundational principles of broad benefit, safety, technical leadership, and global cooperation, serves as a guiding light in the organization's mission to usher in the era of Artificial General Intelligence (AGI). The commitment to transparency, responsible AI practices, and an unwavering focus on ensuring the benefits of AI are accessible to all of humanity underscores OpenAI's dedication to shaping a future where AI aligns with human values.
Pioneering technologies, such as advanced natural language processing models and cutting-edge reinforcement learning algorithms, stand as testaments to OpenAI's technical leadership and its ability to push the boundaries of AI capabilities. The organization's open-source initiatives further amplify its commitment to collaboration and knowledge sharing, fostering an inclusive ecosystem that transcends organizational boundaries.
OpenAI's narrative is one of purpose, collaboration, and responsible stewardship of artificial intelligence. The organization's evolution mirrors the rapid advancements in the field while emphasizing the importance of a principled, ethical, and inclusive approach. OpenAI's story is not just about the development of AI; it is a narrative that underscores the significance of shaping AI technologies in a manner that is not only technically sophisticated but also ethically sound, transparent, and beneficial for humanity.
Read More
In the ever-evolving landscape of artificial intelligence, OpenAI stands as a pioneering force that has shaped the trajectory of AI research and development. From its inception to its current stature, tracing the historical journey of OpenAI provides a captivating narrative of innovation, challenges, and breakthroughs that have redefined the possibilities of machine intelligence.
OpenAI emerged with a visionary mission to ensure that artificial general intelligence (AGI) benefits all of humanity. As we delve into the historical tapestry of OpenAI's evolution, we witness the organization's commitment to cutting-edge research, ethical considerations, and collaborative partnerships that have propelled it to the forefront of the AI community.
This historical perspective explores the milestones, key projects, and pivotal moments that have shaped OpenAI's identity. From the early days of formulating its charter to navigating the complexities of AI ethics, the journey unfolds against the backdrop of technological advancements, societal implications, and the dynamic interplay between humans and machines.
"The Evolution of OpenAI: A Historical Perspective" invites readers to explore the fascinating narrative of a trailblazing entity that continues to push the boundaries of what is possible in the realm of artificial intelligence, weaving together a story that goes beyond technological advancements to encompass the broader impact on society and the ethical considerations that accompany the rise of intelligent machines.
Table of contents
-
Inception and Founding Moments
-
Early Research Projects
-
The OpenAI Charter
-
Pioneering Technologies
-
Strategic Collaborations
-
Leadership Transitions and Changes
-
Ethical Considerations and Responsible AI
-
Open Source Initiatives
-
Public Perception and Media Influence
-
The Evolution of AGI Ambitions
-
Conclusion
Inception and Founding Moments
The inception of OpenAI marked a pivotal moment in the landscape of artificial intelligence, arising from a confluence of visionary ideas and a collective commitment to shaping the future of machine intelligence. Founded in [year], OpenAI emerged as a response to the growing recognition of the transformative potential of AI and the need to ensure that its benefits would be universally accessible and beneficial for humanity. The founding moments of OpenAI reflect the amalgamation of the intellects of notable individuals, including [founders' names], who shared a common vision of steering AI development towards ethical, transparent, and globally beneficial outcomes.
The initial impetus for OpenAI stemmed from a deep-seated belief that the trajectory of AI development should be guided by principles aligned with human welfare, safety, and broad societal impact. The founders envisioned an organization capable of navigating the complex terrain of AI research while prioritizing the long-term well-being of humanity. This founding ethos is encapsulated in the OpenAI Charter, a foundational document that articulates the organization's commitment to principles such as broadly distributed benefits, long-term safety, technical leadership, and cooperative orientation.
The early days of OpenAI were characterized by a fervent dedication to groundbreaking research, laying the groundwork for the organization's subsequent influence in the field. Initial projects and research initiatives showcased a commitment to pushing the boundaries of AI capabilities, reflecting the founders' ambition to foster advancements that transcend narrow applications and contribute to the broader understanding of artificial general intelligence (AGI).
Early Research Projects
The early research projects undertaken by OpenAI reflected a diverse range of interests and challenges within the realm of artificial intelligence. From natural language processing to reinforcement learning and robotics, the organization's multidisciplinary approach showcased a holistic understanding of the complexities inherent in developing intelligent systems. These projects not only sought to address immediate technical challenges but also contributed valuable knowledge to the broader scientific community, aligning with OpenAI's commitment to transparency and knowledge sharing.
As OpenAI delved into these early research endeavors, the organization not only honed its technical expertise but also solidified its position as a thought leader in the AI community. The results of these projects not only contributed to advancements in AI but also set the stage for subsequent, more ambitious initiatives, ultimately shaping the trajectory of OpenAI's research agenda and reinforcing its commitment to excellence in artificial intelligence.
In essence, the early research projects of OpenAI were not just scientific pursuits; they were the building blocks of a legacy that would unfold over time, influencing the organization's reputation and impact in the dynamic landscape of artificial intelligence. These projects were a testament to OpenAI's capacity to innovate, learn, and pave the way for the evolution of AI research on a global scale.
The OpenAI Charter
At the heart of OpenAI's guiding principles lies the seminal document known as the OpenAI Charter, a visionary manifesto that articulates the organization's core values, mission, and its unwavering commitment to shaping the trajectory of artificial intelligence for the benefit of humanity. Formulated during the early stages of OpenAI's existence, the charter serves as a compass, providing direction and purpose to the organization's endeavors in the complex and rapidly evolving field of AI.
The OpenAI Charter outlines key tenets that underscore the organization's philosophy. It emphasizes the importance of ensuring that artificial general intelligence (AGI) benefits all of humanity, avoiding uses of AI that could harm humanity or unduly concentrate power. By committing to broadly distributed benefits, OpenAI signals its intention to employ any influence it obtains over AGI's deployment to ensure it is used for the benefit of all and avoids uses that could harm humanity or unduly concentrate power.
The OpenAI Charter serves as a foundational document that not only sets the ethical standards for OpenAI's research and development but also provides a framework for responsible and accountable innovation in the realm of artificial intelligence. It stands as a testament to the organization's commitment to transparency, ethical considerations, and the overarching goal of ensuring that the evolution of AI aligns with the best interests of humanity.
Pioneering Technologies
OpenAI's trajectory in the realm of artificial intelligence is characterized by a series of groundbreaking technologies that have not only redefined the boundaries of machine intelligence but have also positioned the organization as a trailblazer in the global AI landscape. From its inception, OpenAI has consistently demonstrated a commitment to innovation, pushing the envelope in various domains of AI research.
One of OpenAI's pioneering technologies is exemplified in the realm of natural language processing with projects like GPT (Generative Pre-trained Transformer) models. These models have showcased unprecedented language understanding and generation capabilities, enabling applications ranging from language translation to content generation. GPT-3, in particular, represents a culmination of advancements in large-scale pre-training and has garnered attention for its ability to generate human-like text across diverse contexts.
OpenAI's ventures into unsupervised learning and transfer learning have also marked pioneering advancements. By enabling AI models to generalize knowledge from one domain to another and learn from unannotated data, OpenAI contributes to the development of more versatile and adaptable systems. This approach has implications for addressing challenges in diverse fields, such as healthcare, where transfer learning can be applied to leverage knowledge gained in one medical domain for tasks in another.
The organization's commitment to safety and ethical considerations is intertwined with its technological breakthroughs. OpenAI is actively engaged in addressing concerns related to bias in AI systems, interpretability of models, and the potential societal impacts of advanced technologies. This holistic approach reflects OpenAI's recognition that pioneering technologies must be developed responsibly to ensure positive and equitable outcomes for humanity.
OpenAI's portfolio of pioneering technologies stands as a testament to its dedication to advancing the frontiers of AI. As the organization continues to explore the possibilities of Artificial General Intelligence (AGI), these technological milestones not only showcase the current state of the art but also illuminate the path forward in shaping the future of intelligent systems with ethical considerations at the forefront.
Strategic Collaborations
OpenAI's evolution in the landscape of artificial intelligence has been profoundly influenced by a strategic and purposeful approach to collaborations, emphasizing the organization's commitment to fostering innovation, addressing challenges, and shaping the responsible development of AI technologies. These strategic collaborations extend across diverse domains, showcasing OpenAI's recognition that the complexity of AI requires a collaborative and multidisciplinary effort.
OpenAI's engagements with academic and research institutions play a pivotal role in shaping the cutting edge of AI knowledge. Collaborations with universities and research labs foster an environment of knowledge exchange, peer review, and shared exploration of AI's frontiers. Through these partnerships, OpenAI contributes to the academic discourse while staying at the forefront of emerging research trends and methodologies.
OpenAI's cooperative orientation, as outlined in its Charter, extends to collaborations on a global scale. Actively engaging with research and policy institutions worldwide, OpenAI contributes to the establishment of a collaborative international community addressing the challenges and opportunities presented by Artificial General Intelligence (AGI). These collaborations promote the sharing of diverse perspectives and the development of a collective understanding of the global implications of advanced AI technologies.
OpenAI's strategic collaborations are a testament to its holistic and inclusive approach to AI development. By partnering with industry, academia, ethical organizations, and global stakeholders, OpenAI positions itself at the intersection of diverse perspectives and expertise, contributing to the advancement of AI technologies in a manner that aligns with ethical principles and benefits humanity as a whole. These collaborations not only enrich OpenAI's research initiatives but also foster a collaborative ecosystem essential for the responsible evolution of artificial intelligence.
Leadership Transitions and Changes
Leadership transitions within OpenAI have often been pivotal moments, influencing the strategic direction and focus of the organization. Changes in key leadership roles, such as the appointment of new CEOs or the introduction of influential figures to the leadership team, have played a crucial role in shaping OpenAI's response to evolving technological, ethical, and regulatory landscapes.
One notable aspect of OpenAI's leadership transitions is the organization's ability to balance continuity with innovation. As new leaders join the ranks, they often bring fresh perspectives, diverse expertise, and novel approaches to addressing the challenges of AI. These transitions are not merely changes in personnel; they represent strategic decisions aimed at steering OpenAI toward its long-term goals, often aligning with shifts in the broader AI ecosystem.
Organizational changes within OpenAI extend beyond leadership transitions to encompass structural adaptations and shifts in research priorities. These changes are reflective of the organization's commitment to staying at the forefront of AI advancements. As the field evolves, OpenAI has demonstrated a capacity for organizational flexibility, adjusting its structure and focus areas to align with emerging trends and breakthroughs.
Leadership transitions and organizational changes within OpenAI are integral elements of the organization's evolution. These moments reflect not only the adaptability of OpenAI but also its resilience in the face of an ever-changing AI landscape. By embracing new leadership, adjusting organizational structures, and maintaining transparency, OpenAI navigates transitions with a focus on sustained excellence in AI research and development.
Ethical Considerations and Responsible AI
Ethical considerations and the pursuit of responsible artificial intelligence (AI) stand as foundational tenets in OpenAI's mission, providing a moral compass that has guided the organization's trajectory from its inception. Recognizing the far-reaching implications of AI technologies on individuals and society, OpenAI places a paramount emphasis on infusing ethical principles into every facet of its research, development, and deployment processes.
A central element of OpenAI's ethical commitment manifests in its proactive stance toward identifying and rectifying potential biases within AI systems. The organization acknowledges the inherent risk of perpetuating societal biases through algorithms and actively engages in efforts to mitigate these biases. OpenAI's dedication lies in the cultivation of AI systems that prioritize fairness, impartiality, and inclusivity, thereby minimizing the potential for discriminatory outcomes.
OpenAI's ethical considerations extend further to the imperative of ensuring equitable distribution of the benefits arising from AI technologies. The organization actively works to avoid scenarios where AI could be harnessed to the detriment of humanity or concentrated in ways that unduly consolidate power. This commitment aligns with OpenAI's core principle of utilizing any influence over AGI's deployment to guarantee benefits for all of humanity, emphasizing a global perspective that transcends individual interests.
OpenAI's unwavering commitment to ethical considerations and responsible AI reflects a profound awareness of the societal impact of AI technologies. Through a commitment to transparency, fairness, inclusivity, and a proactive stance on safety, OpenAI aspires to not only be a leader in the technological advancements of AI but also to set the ethical standards that should underpin the development of intelligent systems for the collective benefit of humanity.
Open Source Initiatives
Open Source Initiatives form a pivotal aspect of OpenAI's ethos, embodying the organization's commitment to openness, collaboration, and knowledge sharing within the broader artificial intelligence (AI) community. From its inception, OpenAI has actively embraced the principles of open source, recognizing the transformative potential of making AI research and tools accessible to a wider audience.
One significant dimension of OpenAI's open source endeavors is the release of research papers and findings to the public domain. By sharing the outcomes of its research, OpenAI contributes to the collective intelligence of the AI community, fostering an environment where researchers and practitioners can build upon each other's work. This commitment to transparency extends to providing insights into the methodologies, challenges, and breakthroughs, enabling a collaborative discourse that advances the state of the art in AI.
OpenAI's engagement in open source initiatives is not confined solely to its own developments. The organization actively supports and contributes to existing open source projects, reinforcing a collaborative spirit that transcends organizational boundaries. By participating in the wider ecosystem, OpenAI enriches the collective pool of resources, expertise, and ideas, contributing to the growth and maturation of the global AI community.
OpenAI's Open Source Initiatives exemplify a dedication to fostering collaboration, transparency, and inclusivity in the AI landscape. By embracing open source principles, the organization not only contributes to the advancement of AI but also cultivates a vibrant and collaborative ecosystem that transcends organizational boundaries, ultimately shaping the future of artificial intelligence through shared knowledge and innovation.
Public Perception and Media Influence
Public perception and media influence play significant roles in shaping the narrative around OpenAI, influencing how the organization and its endeavors are perceived by the broader community. As a pioneering force in artificial intelligence (AI), OpenAI's impact extends beyond the scientific community, and the organization is keenly aware of the importance of public understanding and support for its mission.
The portrayal of OpenAI in the media serves as a lens through which the public views the organization's contributions and potential implications. Media coverage often reflects the broader societal sentiment towards AI, and as such, OpenAI actively engages with the media to communicate its goals, achievements, and the ethical considerations that underpin its work. Managing public perceptions is crucial for OpenAI as it strives to foster an environment of trust and transparency, dispelling misconceptions and promoting informed discussions about the future of AI.
The media's influence on public perception is intricately tied to how AI is portrayed in popular culture. OpenAI's initiatives and breakthroughs, when covered by the media, contribute to shaping public attitudes towards the capabilities and impact of AI technologies. Positive portrayals can foster excitement and enthusiasm for the possibilities of AI, while negative portrayals can generate apprehension and concerns. OpenAI actively addresses these dynamics by providing accurate information and context, ensuring that the public is informed about the organization's commitment to responsible AI development.
The interplay between public perception and media influence is a dynamic aspect of OpenAI's journey. The organization's commitment to transparency, responsible AI development, and active engagement with the public and media reflects its dedication to shaping a narrative that aligns with ethical principles, fosters trust, and promotes a collective understanding of the transformative potential of artificial intelligence.
The Evolution of AGI Ambitions
The Evolution of Artificial General Intelligence (AGI) Ambitions at OpenAI represents a dynamic narrative that reflects the organization's continual refinement and adaptation of its long-term goals in the ever-evolving landscape of artificial intelligence. From its inception, OpenAI's mission has been deeply intertwined with the pursuit of AGI—an advanced form of artificial intelligence capable of outperforming humans across a wide range of economically valuable tasks.
The early phases of OpenAI's AGI ambitions were marked by a visionary commitment to ensuring that AGI benefits all of humanity. The organization recognized the transformative potential of AGI and aimed to prevent uses that could harm humanity or unduly concentrate power. This foundational principle, enshrined in the OpenAI Charter, set the ethical tone for the organization's trajectory, emphasizing a responsibility to guide AGI development in a manner that prioritizes broad societal benefits.
The evolution of AGI ambitions at OpenAI is a narrative marked by continual refinement, ethical considerations, and a commitment to proactive safety measures. From visionary beginnings to nuanced revisions, OpenAI's trajectory reflects an ongoing dedication to steering AGI development in a manner that aligns with the principles of broad benefit, safety, and global cooperation. As the organization navigates the path towards AGI, its evolution underscores the importance of responsible AI development in shaping the future of artificial intelligence.
Conclusion
In conclusion, the journey of OpenAI, encapsulated in its historical evolution, ethical considerations, and pursuit of responsible artificial intelligence, paints a portrait of an organization at the forefront of the AI landscape. From its inception, OpenAI has not only been a catalyst for groundbreaking research and technological advancements but has also established itself as a standard-bearer for ethical AI development.
The OpenAI Charter, with its foundational principles of broad benefit, safety, technical leadership, and global cooperation, serves as a guiding light in the organization's mission to usher in the era of Artificial General Intelligence (AGI). The commitment to transparency, responsible AI practices, and an unwavering focus on ensuring the benefits of AI are accessible to all of humanity underscores OpenAI's dedication to shaping a future where AI aligns with human values.
Pioneering technologies, such as advanced natural language processing models and cutting-edge reinforcement learning algorithms, stand as testaments to OpenAI's technical leadership and its ability to push the boundaries of AI capabilities. The organization's open-source initiatives further amplify its commitment to collaboration and knowledge sharing, fostering an inclusive ecosystem that transcends organizational boundaries.
OpenAI's narrative is one of purpose, collaboration, and responsible stewardship of artificial intelligence. The organization's evolution mirrors the rapid advancements in the field while emphasizing the importance of a principled, ethical, and inclusive approach. OpenAI's story is not just about the development of AI; it is a narrative that underscores the significance of shaping AI technologies in a manner that is not only technically sophisticated but also ethically sound, transparent, and beneficial for humanity.
Exploring Cloud Security in CompTIA Cloud Essentials
"Exploring Cloud Security in CompTIA Cloud Essentials" delves into the critical aspects of securing cloud environments, a fundamental component of the CompTIA Cloud Essentials certification. As organizations increasingly migrate their operations to the cloud, understanding and implementing robust security measures becomes paramount. This comprehensive exploration addresses the unique challenges and solutions associated with securing data, applications, and infrastructure in the cloud landscape.
The exploration begins by laying the groundwork for understanding the core principles of cloud computing. By establishing a solid foundation, participants are better prepared to grasp the nuances of securing cloud-based resources. From shared responsibility models to identity and access management, the course systematically covers the essential components of cloud security. Participants will gain insights into the intricacies of securing data during transit and at rest, as well as the implementation of encryption protocols to safeguard sensitive information.
"Exploring Cloud Security in CompTIA Cloud Essentials" offers a comprehensive and practical approach to understanding and implementing security measures in cloud environments. With a focus on real-world applications and industry-relevant scenarios, participants will emerge from this course equipped with the knowledge and skills necessary to navigate the dynamic landscape of cloud security and contribute to the resilient and secure operation of cloud-based systems.
Table of contents
-
Introduction to Cloud Security
-
Shared Responsibility Model
-
Identity and Access Management (IAM)
-
Data Security in the Cloud
-
Network Security in Cloud Environments
-
Compliance and Legal Considerations
-
Security Best Practices for Cloud Deployments
-
Incident Response and Disaster Recovery in the Cloud
-
Cloud Security Monitoring and Auditing
-
Emerging Trends in Cloud Security
-
Conclusion
Introduction to Cloud Security
In the dynamic landscape of contemporary IT infrastructure, where organizations increasingly rely on cloud computing services, the importance of robust cloud security cannot be overstated. Cloud security encompasses a set of practices, technologies, and policies designed to safeguard data, applications, and infrastructure hosted in cloud environments. As businesses migrate their operations to the cloud, they encounter unique challenges and opportunities, making a comprehensive understanding of cloud security paramount.
Cloud security operates on the foundational principle of the shared responsibility model, where both cloud service providers and their customers play integral roles in maintaining a secure ecosystem. This shared responsibility extends across various service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). By delineating these responsibilities, organizations can effectively implement security measures and mitigate potential risks.
One of the central pillars of cloud security is identity and access management (IAM). Ensuring that only authorized individuals or systems have access to resources in the cloud is fundamental to preventing unauthorized access and data breaches. Encryption also plays a crucial role, safeguarding data both in transit and at rest, providing an additional layer of protection against cyber threats.
As organizations navigate the complex landscape of cloud security, compliance with industry regulations and legal frameworks becomes a pressing concern. Meeting these standards not only mitigates legal risks but also fosters a culture of trust among customers and stakeholders.
Shared Responsibility Model
The Shared Responsibility Model is a fundamental framework within the realm of cloud computing, delineating the specific responsibilities between cloud service providers (CSPs) and their customers. This model serves as a crucial guide, ensuring clarity and accountability for security measures in the dynamic landscape of cloud environments. In the context of Infrastructure as a Service (IaaS), the onus of securing the foundational infrastructure, encompassing data centers, networking, and hardware, falls upon the cloud provider. Meanwhile, customers are tasked with securing their virtual machines, operating systems, applications, and data within this shared space.
Moving to Platform as a Service (PaaS), the Shared Responsibility Model adapts to the unique characteristics of this service model. Cloud providers extend their responsibilities to include the underlying platform, including runtime, middleware, and development frameworks. Customers, in turn, focus their attention on securing their applications and data, with a reduced emphasis on the lower-level infrastructure components, reflecting a more specialized division of labor.
In the realm of Software as a Service (SaaS), the Shared Responsibility Model takes another form. Cloud providers assume the comprehensive responsibility of managing and securing the entire software application, spanning infrastructure, middleware, and application layers. Customers, on the other hand, are entrusted with securing their data and controlling access to the application, acknowledging the shared commitment to maintaining a secure SaaS environment.
Central to this model are the common areas of shared responsibility. The security of the cloud, encompassing aspects such as physical security of data centers, network infrastructure, and hypervisor security, is a responsibility shouldered by the cloud provider. Conversely, security in the cloud, including data protection, encryption, access management, and application-level security, rests in the hands of the customer. This clear demarcation fosters collaboration, allowing customers to adapt security measures to their specific needs while leveraging the provider's expertise in managing the underlying infrastructure.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of cybersecurity that plays a pivotal role in securing digital assets and ensuring that the right individuals or systems have appropriate access to resources within an organization's IT infrastructure. IAM encompasses a set of policies, processes, and technologies designed to manage and control user identities, their access rights, and permissions. This multifaceted approach is fundamental for maintaining the confidentiality, integrity, and availability of sensitive data and applications.
IAM involves several key aspects:
User Authentication: IAM systems implement various authentication methods to verify the identity of users before granting access. This can include traditional username/password combinations, multi-factor authentication (MFA), biometrics, and more. Strong authentication mechanisms enhance overall security.
Authorization and Access Control: Authorization mechanisms within IAM dictate what actions users are allowed to perform and what resources they can access. Role-Based Access Control (RBAC) is commonly employed, assigning specific roles and permissions to individuals based on their responsibilities within the organization.
User Provisioning and De-provisioning: IAM systems facilitate the automated creation, modification, and removal of user accounts, ensuring that employees have the appropriate access during their tenure and that access is promptly revoked upon departure or role changes.
Single Sign-On (SSO): SSO enables users to log in once and gain access to multiple applications or systems without the need to reauthenticate for each one. This enhances user experience while simplifying the management of access credentials.
Audit and Compliance: IAM solutions provide auditing capabilities to track user activities and changes to access rights. This is crucial for compliance purposes, enabling organizations to meet regulatory requirements and conduct internal assessments of security policies.
Password Management: IAM systems often include features for password policy enforcement, password resets, and periodic rotation. These measures contribute to overall security hygiene by mitigating the risk of compromised credentials.
Federation: Federation enables secure and seamless access to resources across different systems, applications, or organizations. This is particularly important in scenarios where users need access to resources beyond their organization's boundaries.
Data Security in the Cloud
Data security in the cloud is a paramount concern as organizations entrust their sensitive information to third-party cloud service providers. The dynamic nature of cloud computing introduces unique challenges and opportunities for safeguarding data, both at rest and in transit. Encryption, a fundamental aspect of data security, plays a crucial role in protecting information from unauthorized access, ensuring that even if data is intercepted, it remains unintelligible to malicious actors.
Securing data at rest involves implementing encryption measures for stored information within the cloud infrastructure. Cloud service providers typically offer robust encryption mechanisms, allowing organizations to protect their data using encryption keys. This ensures that, even in the event of a security breach or unauthorized access, the data remains encrypted and unreadable without the corresponding decryption keys.
Access controls and identity management also play a pivotal role in data security in the cloud. Ensuring that only authorized individuals or systems have access to specific data sets is essential for preventing unauthorized data exposure. Identity and Access Management (IAM) solutions help organizations manage user access, enforce least privilege principles, and monitor user activities to detect and mitigate potential security threats.
Regular audits and compliance checks are essential to verify that data security measures align with industry regulations and organizational policies. Cloud service providers often undergo third-party audits and certifications, providing organizations with assurances regarding the security practices implemented in their cloud environments.
Effective data security in the cloud requires a comprehensive approach that encompasses encryption, access controls, identity management, and ongoing compliance efforts. As organizations continue to leverage the benefits of cloud computing, prioritizing robust data security measures is indispensable to instill trust, mitigate risks, and ensure the confidentiality and integrity of sensitive information in the cloud.
Network Security in Cloud Environments
Network security in cloud environments is a critical facet of ensuring the integrity, confidentiality, and availability of data and applications hosted in the cloud. As organizations increasingly migrate their operations to the cloud, the traditional perimeter-based network security models undergo transformation to adapt to the dynamic and distributed nature of cloud computing. In this evolving landscape, securing cloud networks involves a combination of advanced technologies, robust policies, and continuous monitoring.
Cloud service providers offer virtualized environments where customers can deploy and manage their resources. Securing these environments necessitates the implementation of comprehensive network security measures. Virtual Private Clouds (VPCs) play a pivotal role, allowing organizations to create isolated network spaces within the cloud infrastructure, segregating workloads and enhancing overall security. This isolation prevents unauthorized access and limits the potential impact of security incidents.
Firewalls, both traditional and cloud-native, are fundamental components of network security in the cloud. They act as gatekeepers, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. Cloud providers often offer scalable and dynamically configurable firewall solutions, enabling organizations to adapt their security policies to changing operational requirements.
Monitoring and logging are integral to maintaining network security in the cloud. Cloud providers offer tools that enable real-time monitoring of network activities, allowing organizations to detect and respond to potential threats promptly. Comprehensive logging ensures that security incidents can be investigated thoroughly, contributing to continuous improvement of security postures.
Network security in cloud environments requires a holistic and adaptive approach. Organizations must leverage a combination of traditional and cloud-native security measures, employ isolation and segmentation strategies, and embrace advanced monitoring and response capabilities. By doing so, they can establish resilient and secure network architectures that align with the dynamic nature of cloud computing.
Compliance and Legal Considerations
Compliance and legal considerations are pivotal aspects that organizations must carefully navigate when adopting cloud computing solutions. In the dynamic and interconnected digital landscape, adherence to regulatory frameworks and legal standards is crucial for safeguarding data, ensuring privacy, and maintaining trust among stakeholders.
Data sovereignty and localization requirements add another layer of complexity to compliance considerations. Some jurisdictions have strict laws governing where data can be stored and processed. Organizations must carefully assess these requirements to choose cloud data centers that comply with data residency regulations, thereby mitigating legal risks associated with cross-border data transfers.
Contracts and agreements between organizations and cloud service providers are critical components of compliance efforts. Carefully drafted Service Level Agreements (SLAs) and Terms of Service should outline the responsibilities of both parties, specifying how security measures will be implemented, monitored, and maintained. This contractual clarity is essential for legal transparency and accountability.
Privacy laws, such as the General Data Protection Regulation (GDPR), are increasingly shaping the legal landscape for cloud computing. GDPR, for example, imposes stringent requirements on the processing and protection of personal data. Organizations must adopt measures to ensure compliance with privacy laws, including transparent data processing practices, robust consent mechanisms, and timely data breach notifications.
Compliance and legal considerations are integral to the success and sustainability of cloud adoption. Organizations that prioritize a comprehensive understanding of relevant regulations, engage with compliant cloud service providers, and establish transparent contractual agreements are better positioned to leverage the benefits of cloud computing while navigating the complex landscape of compliance and legal requirements.
Security Best Practices for Cloud Deployments
Implementing robust security practices is essential when deploying applications and data in cloud environments, where the dynamic nature of cloud computing introduces both opportunities and challenges. One critical best practice is the adoption of comprehensive data encryption strategies. This involves encrypting data at rest and in transit, employing industry-standard algorithms, and implementing strong key management practices. By doing so, organizations can safeguard sensitive information from unauthorized access and potential data breaches.
Identity and Access Management (IAM) is another cornerstone of cloud security best practices. Organizations should adhere to the principle of least privilege, ensuring that users have only the minimum access required for their roles. Strong authentication mechanisms, such as multi-factor authentication (MFA), further enhance identity verification, adding an additional layer of security to cloud deployments.
Network security plays a pivotal role in creating a secure cloud environment. Utilizing Virtual Private Clouds (VPCs) helps isolate and segment resources, while configuring firewalls and security groups enables precise control over inbound and outbound traffic. Continuous monitoring and auditing of network activities contribute to the early detection of anomalies, allowing for swift response to potential security incidents.
Regular audits and assessments are integral components of a robust security strategy for cloud deployments. Conducting security audits, penetration testing, and vulnerability scanning helps identify and remediate vulnerabilities before they can be exploited. Additionally, implementing a comprehensive backup strategy ensures data integrity and availability, with backups stored securely in a separate location from the primary data.
Employee training and awareness programs are vital in creating a security-conscious culture within the organization. Ongoing security training ensures that employees are aware of best practices and potential threats, fostering a collective responsibility for security. Finally, organizations should leverage built-in security features provided by cloud service providers and stay informed about updates and new security features to continuously enhance the security posture of their cloud deployments.
Incident Response and Disaster Recovery in the Cloud
Incident response and disaster recovery are integral components of a comprehensive cybersecurity strategy, and when it comes to cloud environments, these processes take on a unique set of considerations. Incident response in the cloud involves the systematic approach to identifying, managing, and mitigating security incidents such as data breaches or unauthorized access. In a cloud context, organizations must be adept at recognizing the dynamic nature of cloud infrastructure and responding swiftly to incidents that may impact data, applications, or the overall security of cloud-hosted resources.
Cloud environments introduce specific challenges to incident response, including the distributed nature of data and the diverse array of services provided by cloud service providers. A well-defined incident response plan tailored for cloud deployments is essential. This plan should include clear roles and responsibilities, communication strategies, and predefined steps to assess, contain, eradicate, recover, and learn from security incidents. Continuous testing and updating of the incident response plan ensure its effectiveness in the rapidly evolving cloud landscape.
Disaster recovery in the cloud extends beyond traditional backup and restoration processes. It involves planning for the restoration of critical systems and data in the event of a catastrophic failure, whether due to natural disasters, cyber-attacks, or other unforeseen circumstances. Cloud-based disaster recovery solutions leverage the flexibility and scalability of cloud infrastructure, allowing organizations to replicate and store data in geographically dispersed locations. This approach enhances data resilience and minimizes downtime, providing a more robust strategy for recovering from significant disruptions.
Incident response and disaster recovery in the cloud require a proactive and adaptive approach. Organizations must develop and regularly test comprehensive plans that address the unique challenges posed by cloud environments. By leveraging automation, fostering clear communication, and staying abreast of evolving threats, organizations can enhance their resilience in the face of security incidents and catastrophic events, ensuring the continuity of business operations in the cloud.
Cloud Security Monitoring and Auditing
Cloud security monitoring and auditing are pivotal components of a robust cybersecurity strategy, especially in the context of organizations leveraging cloud services for their operations. Security monitoring in the cloud involves continuous surveillance and analysis of activities within the cloud environment. This real-time scrutiny aims to detect and respond to potential security threats promptly. By employing monitoring tools and intrusion detection systems, organizations can identify unusual patterns or anomalies in network traffic, user behavior, and system activities. Centralized logging ensures that detailed information about user activities and system events is captured, facilitating comprehensive analysis. Automation plays a crucial role in incident response, allowing organizations to respond swiftly to predefined security incidents, ultimately enhancing the overall security posture.
Identity and access audits are essential in the cloud environment, where user access privileges and roles need meticulous scrutiny. Continuous assessment of identity and access management ensures that permissions are accurate and align with security policies. Furthermore, data protection audits evaluate encryption measures and validate the proper handling of sensitive data. Organizations also engage in third-party assessments to undergo independent evaluations, providing an additional layer of assurance about the security practices both within the organization and from the cloud service provider.
Continuous improvement is a fundamental principle underpinning effective cloud security monitoring and auditing. Regular reviews of monitoring findings and audit outcomes contribute to a dynamic cybersecurity strategy. Learning from security incidents, adjusting security strategies, and staying abreast of emerging threats foster a culture of ongoing enhancement. This iterative approach ensures that organizations not only meet compliance requirements but also adapt and strengthen their security measures in response to the evolving threat landscape in cloud environments.
Cloud security monitoring and auditing form a comprehensive and dynamic duo in the realm of cybersecurity. By embracing real-time threat detection, automated incident response, and rigorous auditing practices, organizations can fortify their cloud environments against an ever-evolving array of security challenges. This proactive approach not only safeguards sensitive data but also ensures the resilience and adaptability of cloud security strategies.
Emerging Trends in Cloud Security
Cloud security is a rapidly evolving domain, shaped by technological advancements, evolving threat landscapes, and the need for more robust protection in an increasingly interconnected digital environment. One prominent trend is the adoption of Zero Trust Architecture, reflecting a shift away from traditional perimeter-based security models. Zero Trust emphasizes continuous verification of identities and stringent access controls, aligning with the dynamic nature of cloud environments where trust is not assumed even among entities within the network perimeter.
As organizations increasingly embrace containerization technologies like Docker and Kubernetes, the need for robust container security is on the rise. Emerging solutions focus on securing containerized applications, ensuring the integrity and safety of workloads in cloud environments. Secure Access Service Edge (SASE) is gaining prominence, particularly in the context of remote work. This integrated security framework combines network security functions with WAN capabilities to accommodate the dynamic and secure access needs of modern organizations.
Artificial intelligence (AI) and machine learning (ML) are playing an expanding role in cloud security. These technologies are employed for threat detection, anomaly analysis, and automated response mechanisms, enhancing the ability to identify and mitigate security incidents in real-time. DevSecOps, the integration of security into the DevOps process, has become a standard practice. By treating security as a shared responsibility throughout the software development lifecycle, organizations can achieve faster and more secure deployment of applications in cloud environments.
Multi-cloud security is gaining traction as organizations adopt multi-cloud strategies to avoid vendor lock-in and enhance resilience. Securing data and applications across multiple cloud providers necessitates specialized security solutions and a consistent security posture. Homomorphic encryption is emerging as a promising technology for secure data processing in the cloud. This encryption technique allows computations on encrypted data without the need for decryption, addressing concerns about maintaining the confidentiality of sensitive information.
Staying informed about these emerging trends is crucial for organizations seeking to fortify their cloud security strategies. As the cloud landscape evolves, security measures must adapt to address new challenges and leverage innovative solutions. The combination of these trends reflects a concerted effort to enhance protection, detection, and response capabilities in the ever-changing landscape of cloud security.
Conclusion
In conclusion, the evolving landscape of cloud security is characterized by a dynamic interplay of technological advancements, emerging threats, and innovative strategies to safeguard digital assets. The adoption of Zero Trust Architecture reflects a paradigm shift towards continuous verification and stringent access controls, acknowledging the dynamic nature of cloud environments. The rise of cloud-native security solutions underscores the need for seamlessly integrated tools that can effectively manage the distributed nature of cloud infrastructures.
As organizations continue to embrace the benefits of cloud computing, a proactive and adaptive approach to security becomes imperative. By staying abreast of these emerging trends and adopting a holistic security posture, organizations can mitigate risks, enhance resilience, and ensure the integrity, confidentiality, and availability of their data and applications in the dynamic realm of cloud computing.
Read More
"Exploring Cloud Security in CompTIA Cloud Essentials" delves into the critical aspects of securing cloud environments, a fundamental component of the CompTIA Cloud Essentials certification. As organizations increasingly migrate their operations to the cloud, understanding and implementing robust security measures becomes paramount. This comprehensive exploration addresses the unique challenges and solutions associated with securing data, applications, and infrastructure in the cloud landscape.
The exploration begins by laying the groundwork for understanding the core principles of cloud computing. By establishing a solid foundation, participants are better prepared to grasp the nuances of securing cloud-based resources. From shared responsibility models to identity and access management, the course systematically covers the essential components of cloud security. Participants will gain insights into the intricacies of securing data during transit and at rest, as well as the implementation of encryption protocols to safeguard sensitive information.
"Exploring Cloud Security in CompTIA Cloud Essentials" offers a comprehensive and practical approach to understanding and implementing security measures in cloud environments. With a focus on real-world applications and industry-relevant scenarios, participants will emerge from this course equipped with the knowledge and skills necessary to navigate the dynamic landscape of cloud security and contribute to the resilient and secure operation of cloud-based systems.
Table of contents
-
Introduction to Cloud Security
-
Shared Responsibility Model
-
Identity and Access Management (IAM)
-
Data Security in the Cloud
-
Network Security in Cloud Environments
-
Compliance and Legal Considerations
-
Security Best Practices for Cloud Deployments
-
Incident Response and Disaster Recovery in the Cloud
-
Cloud Security Monitoring and Auditing
-
Emerging Trends in Cloud Security
-
Conclusion
Introduction to Cloud Security
In the dynamic landscape of contemporary IT infrastructure, where organizations increasingly rely on cloud computing services, the importance of robust cloud security cannot be overstated. Cloud security encompasses a set of practices, technologies, and policies designed to safeguard data, applications, and infrastructure hosted in cloud environments. As businesses migrate their operations to the cloud, they encounter unique challenges and opportunities, making a comprehensive understanding of cloud security paramount.
Cloud security operates on the foundational principle of the shared responsibility model, where both cloud service providers and their customers play integral roles in maintaining a secure ecosystem. This shared responsibility extends across various service models, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). By delineating these responsibilities, organizations can effectively implement security measures and mitigate potential risks.
One of the central pillars of cloud security is identity and access management (IAM). Ensuring that only authorized individuals or systems have access to resources in the cloud is fundamental to preventing unauthorized access and data breaches. Encryption also plays a crucial role, safeguarding data both in transit and at rest, providing an additional layer of protection against cyber threats.
As organizations navigate the complex landscape of cloud security, compliance with industry regulations and legal frameworks becomes a pressing concern. Meeting these standards not only mitigates legal risks but also fosters a culture of trust among customers and stakeholders.
Shared Responsibility Model
The Shared Responsibility Model is a fundamental framework within the realm of cloud computing, delineating the specific responsibilities between cloud service providers (CSPs) and their customers. This model serves as a crucial guide, ensuring clarity and accountability for security measures in the dynamic landscape of cloud environments. In the context of Infrastructure as a Service (IaaS), the onus of securing the foundational infrastructure, encompassing data centers, networking, and hardware, falls upon the cloud provider. Meanwhile, customers are tasked with securing their virtual machines, operating systems, applications, and data within this shared space.
Moving to Platform as a Service (PaaS), the Shared Responsibility Model adapts to the unique characteristics of this service model. Cloud providers extend their responsibilities to include the underlying platform, including runtime, middleware, and development frameworks. Customers, in turn, focus their attention on securing their applications and data, with a reduced emphasis on the lower-level infrastructure components, reflecting a more specialized division of labor.
In the realm of Software as a Service (SaaS), the Shared Responsibility Model takes another form. Cloud providers assume the comprehensive responsibility of managing and securing the entire software application, spanning infrastructure, middleware, and application layers. Customers, on the other hand, are entrusted with securing their data and controlling access to the application, acknowledging the shared commitment to maintaining a secure SaaS environment.
Central to this model are the common areas of shared responsibility. The security of the cloud, encompassing aspects such as physical security of data centers, network infrastructure, and hypervisor security, is a responsibility shouldered by the cloud provider. Conversely, security in the cloud, including data protection, encryption, access management, and application-level security, rests in the hands of the customer. This clear demarcation fosters collaboration, allowing customers to adapt security measures to their specific needs while leveraging the provider's expertise in managing the underlying infrastructure.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is a critical component of cybersecurity that plays a pivotal role in securing digital assets and ensuring that the right individuals or systems have appropriate access to resources within an organization's IT infrastructure. IAM encompasses a set of policies, processes, and technologies designed to manage and control user identities, their access rights, and permissions. This multifaceted approach is fundamental for maintaining the confidentiality, integrity, and availability of sensitive data and applications.
IAM involves several key aspects:
User Authentication: IAM systems implement various authentication methods to verify the identity of users before granting access. This can include traditional username/password combinations, multi-factor authentication (MFA), biometrics, and more. Strong authentication mechanisms enhance overall security.
Authorization and Access Control: Authorization mechanisms within IAM dictate what actions users are allowed to perform and what resources they can access. Role-Based Access Control (RBAC) is commonly employed, assigning specific roles and permissions to individuals based on their responsibilities within the organization.
User Provisioning and De-provisioning: IAM systems facilitate the automated creation, modification, and removal of user accounts, ensuring that employees have the appropriate access during their tenure and that access is promptly revoked upon departure or role changes.
Single Sign-On (SSO): SSO enables users to log in once and gain access to multiple applications or systems without the need to reauthenticate for each one. This enhances user experience while simplifying the management of access credentials.
Audit and Compliance: IAM solutions provide auditing capabilities to track user activities and changes to access rights. This is crucial for compliance purposes, enabling organizations to meet regulatory requirements and conduct internal assessments of security policies.
Password Management: IAM systems often include features for password policy enforcement, password resets, and periodic rotation. These measures contribute to overall security hygiene by mitigating the risk of compromised credentials.
Federation: Federation enables secure and seamless access to resources across different systems, applications, or organizations. This is particularly important in scenarios where users need access to resources beyond their organization's boundaries.
Data Security in the Cloud
Data security in the cloud is a paramount concern as organizations entrust their sensitive information to third-party cloud service providers. The dynamic nature of cloud computing introduces unique challenges and opportunities for safeguarding data, both at rest and in transit. Encryption, a fundamental aspect of data security, plays a crucial role in protecting information from unauthorized access, ensuring that even if data is intercepted, it remains unintelligible to malicious actors.
Securing data at rest involves implementing encryption measures for stored information within the cloud infrastructure. Cloud service providers typically offer robust encryption mechanisms, allowing organizations to protect their data using encryption keys. This ensures that, even in the event of a security breach or unauthorized access, the data remains encrypted and unreadable without the corresponding decryption keys.
Access controls and identity management also play a pivotal role in data security in the cloud. Ensuring that only authorized individuals or systems have access to specific data sets is essential for preventing unauthorized data exposure. Identity and Access Management (IAM) solutions help organizations manage user access, enforce least privilege principles, and monitor user activities to detect and mitigate potential security threats.
Regular audits and compliance checks are essential to verify that data security measures align with industry regulations and organizational policies. Cloud service providers often undergo third-party audits and certifications, providing organizations with assurances regarding the security practices implemented in their cloud environments.
Effective data security in the cloud requires a comprehensive approach that encompasses encryption, access controls, identity management, and ongoing compliance efforts. As organizations continue to leverage the benefits of cloud computing, prioritizing robust data security measures is indispensable to instill trust, mitigate risks, and ensure the confidentiality and integrity of sensitive information in the cloud.
Network Security in Cloud Environments
Network security in cloud environments is a critical facet of ensuring the integrity, confidentiality, and availability of data and applications hosted in the cloud. As organizations increasingly migrate their operations to the cloud, the traditional perimeter-based network security models undergo transformation to adapt to the dynamic and distributed nature of cloud computing. In this evolving landscape, securing cloud networks involves a combination of advanced technologies, robust policies, and continuous monitoring.
Cloud service providers offer virtualized environments where customers can deploy and manage their resources. Securing these environments necessitates the implementation of comprehensive network security measures. Virtual Private Clouds (VPCs) play a pivotal role, allowing organizations to create isolated network spaces within the cloud infrastructure, segregating workloads and enhancing overall security. This isolation prevents unauthorized access and limits the potential impact of security incidents.
Firewalls, both traditional and cloud-native, are fundamental components of network security in the cloud. They act as gatekeepers, monitoring and controlling incoming and outgoing traffic based on predetermined security rules. Cloud providers often offer scalable and dynamically configurable firewall solutions, enabling organizations to adapt their security policies to changing operational requirements.
Monitoring and logging are integral to maintaining network security in the cloud. Cloud providers offer tools that enable real-time monitoring of network activities, allowing organizations to detect and respond to potential threats promptly. Comprehensive logging ensures that security incidents can be investigated thoroughly, contributing to continuous improvement of security postures.
Network security in cloud environments requires a holistic and adaptive approach. Organizations must leverage a combination of traditional and cloud-native security measures, employ isolation and segmentation strategies, and embrace advanced monitoring and response capabilities. By doing so, they can establish resilient and secure network architectures that align with the dynamic nature of cloud computing.
Compliance and Legal Considerations
Compliance and legal considerations are pivotal aspects that organizations must carefully navigate when adopting cloud computing solutions. In the dynamic and interconnected digital landscape, adherence to regulatory frameworks and legal standards is crucial for safeguarding data, ensuring privacy, and maintaining trust among stakeholders.
Data sovereignty and localization requirements add another layer of complexity to compliance considerations. Some jurisdictions have strict laws governing where data can be stored and processed. Organizations must carefully assess these requirements to choose cloud data centers that comply with data residency regulations, thereby mitigating legal risks associated with cross-border data transfers.
Contracts and agreements between organizations and cloud service providers are critical components of compliance efforts. Carefully drafted Service Level Agreements (SLAs) and Terms of Service should outline the responsibilities of both parties, specifying how security measures will be implemented, monitored, and maintained. This contractual clarity is essential for legal transparency and accountability.
Privacy laws, such as the General Data Protection Regulation (GDPR), are increasingly shaping the legal landscape for cloud computing. GDPR, for example, imposes stringent requirements on the processing and protection of personal data. Organizations must adopt measures to ensure compliance with privacy laws, including transparent data processing practices, robust consent mechanisms, and timely data breach notifications.
Compliance and legal considerations are integral to the success and sustainability of cloud adoption. Organizations that prioritize a comprehensive understanding of relevant regulations, engage with compliant cloud service providers, and establish transparent contractual agreements are better positioned to leverage the benefits of cloud computing while navigating the complex landscape of compliance and legal requirements.
Security Best Practices for Cloud Deployments
Implementing robust security practices is essential when deploying applications and data in cloud environments, where the dynamic nature of cloud computing introduces both opportunities and challenges. One critical best practice is the adoption of comprehensive data encryption strategies. This involves encrypting data at rest and in transit, employing industry-standard algorithms, and implementing strong key management practices. By doing so, organizations can safeguard sensitive information from unauthorized access and potential data breaches.
Identity and Access Management (IAM) is another cornerstone of cloud security best practices. Organizations should adhere to the principle of least privilege, ensuring that users have only the minimum access required for their roles. Strong authentication mechanisms, such as multi-factor authentication (MFA), further enhance identity verification, adding an additional layer of security to cloud deployments.
Network security plays a pivotal role in creating a secure cloud environment. Utilizing Virtual Private Clouds (VPCs) helps isolate and segment resources, while configuring firewalls and security groups enables precise control over inbound and outbound traffic. Continuous monitoring and auditing of network activities contribute to the early detection of anomalies, allowing for swift response to potential security incidents.
Regular audits and assessments are integral components of a robust security strategy for cloud deployments. Conducting security audits, penetration testing, and vulnerability scanning helps identify and remediate vulnerabilities before they can be exploited. Additionally, implementing a comprehensive backup strategy ensures data integrity and availability, with backups stored securely in a separate location from the primary data.
Employee training and awareness programs are vital in creating a security-conscious culture within the organization. Ongoing security training ensures that employees are aware of best practices and potential threats, fostering a collective responsibility for security. Finally, organizations should leverage built-in security features provided by cloud service providers and stay informed about updates and new security features to continuously enhance the security posture of their cloud deployments.
Incident Response and Disaster Recovery in the Cloud
Incident response and disaster recovery are integral components of a comprehensive cybersecurity strategy, and when it comes to cloud environments, these processes take on a unique set of considerations. Incident response in the cloud involves the systematic approach to identifying, managing, and mitigating security incidents such as data breaches or unauthorized access. In a cloud context, organizations must be adept at recognizing the dynamic nature of cloud infrastructure and responding swiftly to incidents that may impact data, applications, or the overall security of cloud-hosted resources.
Cloud environments introduce specific challenges to incident response, including the distributed nature of data and the diverse array of services provided by cloud service providers. A well-defined incident response plan tailored for cloud deployments is essential. This plan should include clear roles and responsibilities, communication strategies, and predefined steps to assess, contain, eradicate, recover, and learn from security incidents. Continuous testing and updating of the incident response plan ensure its effectiveness in the rapidly evolving cloud landscape.
Disaster recovery in the cloud extends beyond traditional backup and restoration processes. It involves planning for the restoration of critical systems and data in the event of a catastrophic failure, whether due to natural disasters, cyber-attacks, or other unforeseen circumstances. Cloud-based disaster recovery solutions leverage the flexibility and scalability of cloud infrastructure, allowing organizations to replicate and store data in geographically dispersed locations. This approach enhances data resilience and minimizes downtime, providing a more robust strategy for recovering from significant disruptions.
Incident response and disaster recovery in the cloud require a proactive and adaptive approach. Organizations must develop and regularly test comprehensive plans that address the unique challenges posed by cloud environments. By leveraging automation, fostering clear communication, and staying abreast of evolving threats, organizations can enhance their resilience in the face of security incidents and catastrophic events, ensuring the continuity of business operations in the cloud.
Cloud Security Monitoring and Auditing
Cloud security monitoring and auditing are pivotal components of a robust cybersecurity strategy, especially in the context of organizations leveraging cloud services for their operations. Security monitoring in the cloud involves continuous surveillance and analysis of activities within the cloud environment. This real-time scrutiny aims to detect and respond to potential security threats promptly. By employing monitoring tools and intrusion detection systems, organizations can identify unusual patterns or anomalies in network traffic, user behavior, and system activities. Centralized logging ensures that detailed information about user activities and system events is captured, facilitating comprehensive analysis. Automation plays a crucial role in incident response, allowing organizations to respond swiftly to predefined security incidents, ultimately enhancing the overall security posture.
Identity and access audits are essential in the cloud environment, where user access privileges and roles need meticulous scrutiny. Continuous assessment of identity and access management ensures that permissions are accurate and align with security policies. Furthermore, data protection audits evaluate encryption measures and validate the proper handling of sensitive data. Organizations also engage in third-party assessments to undergo independent evaluations, providing an additional layer of assurance about the security practices both within the organization and from the cloud service provider.
Continuous improvement is a fundamental principle underpinning effective cloud security monitoring and auditing. Regular reviews of monitoring findings and audit outcomes contribute to a dynamic cybersecurity strategy. Learning from security incidents, adjusting security strategies, and staying abreast of emerging threats foster a culture of ongoing enhancement. This iterative approach ensures that organizations not only meet compliance requirements but also adapt and strengthen their security measures in response to the evolving threat landscape in cloud environments.
Cloud security monitoring and auditing form a comprehensive and dynamic duo in the realm of cybersecurity. By embracing real-time threat detection, automated incident response, and rigorous auditing practices, organizations can fortify their cloud environments against an ever-evolving array of security challenges. This proactive approach not only safeguards sensitive data but also ensures the resilience and adaptability of cloud security strategies.
Emerging Trends in Cloud Security
Cloud security is a rapidly evolving domain, shaped by technological advancements, evolving threat landscapes, and the need for more robust protection in an increasingly interconnected digital environment. One prominent trend is the adoption of Zero Trust Architecture, reflecting a shift away from traditional perimeter-based security models. Zero Trust emphasizes continuous verification of identities and stringent access controls, aligning with the dynamic nature of cloud environments where trust is not assumed even among entities within the network perimeter.
As organizations increasingly embrace containerization technologies like Docker and Kubernetes, the need for robust container security is on the rise. Emerging solutions focus on securing containerized applications, ensuring the integrity and safety of workloads in cloud environments. Secure Access Service Edge (SASE) is gaining prominence, particularly in the context of remote work. This integrated security framework combines network security functions with WAN capabilities to accommodate the dynamic and secure access needs of modern organizations.
Artificial intelligence (AI) and machine learning (ML) are playing an expanding role in cloud security. These technologies are employed for threat detection, anomaly analysis, and automated response mechanisms, enhancing the ability to identify and mitigate security incidents in real-time. DevSecOps, the integration of security into the DevOps process, has become a standard practice. By treating security as a shared responsibility throughout the software development lifecycle, organizations can achieve faster and more secure deployment of applications in cloud environments.
Multi-cloud security is gaining traction as organizations adopt multi-cloud strategies to avoid vendor lock-in and enhance resilience. Securing data and applications across multiple cloud providers necessitates specialized security solutions and a consistent security posture. Homomorphic encryption is emerging as a promising technology for secure data processing in the cloud. This encryption technique allows computations on encrypted data without the need for decryption, addressing concerns about maintaining the confidentiality of sensitive information.
Staying informed about these emerging trends is crucial for organizations seeking to fortify their cloud security strategies. As the cloud landscape evolves, security measures must adapt to address new challenges and leverage innovative solutions. The combination of these trends reflects a concerted effort to enhance protection, detection, and response capabilities in the ever-changing landscape of cloud security.
Conclusion
In conclusion, the evolving landscape of cloud security is characterized by a dynamic interplay of technological advancements, emerging threats, and innovative strategies to safeguard digital assets. The adoption of Zero Trust Architecture reflects a paradigm shift towards continuous verification and stringent access controls, acknowledging the dynamic nature of cloud environments. The rise of cloud-native security solutions underscores the need for seamlessly integrated tools that can effectively manage the distributed nature of cloud infrastructures.
As organizations continue to embrace the benefits of cloud computing, a proactive and adaptive approach to security becomes imperative. By staying abreast of these emerging trends and adopting a holistic security posture, organizations can mitigate risks, enhance resilience, and ensure the integrity, confidentiality, and availability of their data and applications in the dynamic realm of cloud computing.
History of project management
Project management is a vital discipline that enables organizations to plan, execute, and complete tasks efficiently and effectively. It has a rich history that has evolved over centuries, reflecting the changing needs of society, technology, and industry. In this introduction, we will embark on a journey through time to explore the key milestones and developments in the history of project management, shedding light on its origins, growth, and transformation.
The 20th century witnessed a significant expansion of project management, particularly during World War II, where it played a critical role in the success of military operations and research endeavors. Post-WWII, the discipline grew further, with notable pioneers like Henry L. Gantt and Henri Fayol contributing to its development.
As we move into the 21st century, project management continues to evolve. The advent of the digital age, information technology, and globalization has revolutionized how projects are planned, executed, and monitored. Agile methodologies, virtual teams, sustainability considerations, and other contemporary factors now play a significant role in shaping the landscape of project management.
Table of contents
-
Ancient Project Management Practices
-
Origins of Modern Project Management
-
Industrial Revolution and Project Management
-
Project Management in World War II
-
Project Management Pioneers
-
The Manhattan Project
-
Post-WWII Expansion of Project Management
-
Project Management Methodologie
-
Project Management in the Information Age
-
Project Management in the 21st Century
-
Conclusion
Ancient Project Management Practices
Long before the formal discipline of project management emerged, ancient civilizations engaged in various activities that could be considered early project management practices. These civilizations used systematic approaches to plan, organize, and execute complex projects. Here are some examples of ancient project management practices:
The Pyramids of Egypt: The construction of the Egyptian pyramids, including the Great Pyramid of Giza, is often cited as an early example of project management. Ancient Egyptians used detailed plans, organized labor forces, and managed resources like limestone, granite, and labor to build these monumental structures. Hieroglyphics on the pyramid walls depicted various phases of construction, highlighting the project's organized nature.
The Great Wall of China: The construction of the Great Wall of China, which spanned centuries and multiple dynasties, involved careful planning and resource management. It required coordinating the efforts of large workforces to build fortifications across vast distances. Additionally, the wall's purpose evolved over time, demonstrating adaptability in project management.
Roman Aqueducts: The Romans are renowned for their engineering feats, including the construction of aqueducts. These water supply systems showcased meticulous planning and precise construction methods. Engineers and laborers worked together to ensure a reliable water supply to Roman cities, and the design and construction were crucial aspects of these projects.
The Silk Road: The development and maintenance of the Silk Road, a vast network of trade routes connecting the East and West, required ongoing project management. It involved managing caravans, security, route maintenance, and diplomatic relationships among various regions. This ancient trade network flourished due to careful planning and execution.
Mayan Temples: Mayan civilization in Central America constructed intricate temples and structures, demonstrating advanced project management skills. They used mathematical precision and astronomical knowledge to align their buildings and effectively manage resources such as stone and labor.
While the ancient world lacked the formal methodologies and terminologies of modern project management, these historical examples demonstrate that the principles of planning, organizing, and executing complex tasks have deep roots in human civilization. The success of these ancient projects depended on effective leadership, resource management, and the ability to adapt to changing circumstances, all of which are core aspects of project management.
Origins of Modern Project Management
The origins of modern project management can be traced back to the mid-20th century, with several key developments and contributors who laid the foundation for the discipline. Here are some crucial points in the origins of modern project management:
Henry L. Gantt and the Gantt Chart (1910s): Henry L. Gantt, an American engineer and management consultant, developed the Gantt chart in the early 1910s. The Gantt chart is a visual representation of a project schedule, which shows tasks and their durations. It was a significant innovation in project management as it allowed for easy tracking of progress and resource allocation.
The Manhattan Project (1940s): The development of the atomic bomb during World War II through the Manhattan Project is often considered a pivotal moment in the history of project management. This massive undertaking required precise planning, coordination of scientific and engineering efforts, and the efficient allocation of resources. It set the stage for the recognition of project management as a crucial discipline.
Project Evaluation and Review Technique (PERT) and Critical Path Method (CPM) (1950s): PERT and CPM are two project management methodologies developed in the 1950s. PERT was developed by the U.S. Navy for the Polaris missile project, while CPM was developed by DuPont for maintenance projects. These techniques helped in scheduling, coordinating, and managing complex projects. They became fundamental tools in project management, particularly for large engineering and construction projects.
Software and Technology Advances: The advent of computer technology in the mid-20th century revolutionized project management. Project management software, like the development of Microsoft Project in the 1980s, made it easier to create and manage project schedules, budgets, and resources, further advancing the field.
These early developments and historical milestones laid the groundwork for modern project management as a distinct discipline. Today, project management is applied across a wide range of industries, from information technology to healthcare and manufacturing, and is considered a critical factor in the success of organizations and the execution of complex projects.
Industrial Revolution and Project Management
The Industrial Revolution had a profound impact on the development of project management as a formal discipline. This period of rapid industrialization, which began in the late 18th century and continued into the 19th century, brought about significant changes in manufacturing, transportation, and technology. As industries grew and became more complex, the need for structured project management practices became increasingly evident. Here's how the Industrial Revolution influenced the evolution of project management:
Complex Manufacturing Projects: The Industrial Revolution introduced new manufacturing processes and technologies, such as the mechanization of factories and the introduction of assembly lines. Managing these complex manufacturing projects required planning, coordination, and resource allocation, which are fundamental aspects of project management.
Growth of Multidisciplinary Teams: Industrialization led to the formation of multidisciplinary teams, with engineers, architects, laborers, and other specialists working together. Effective communication and collaboration among team members became critical, marking the beginning of the teamwork and leadership elements that are central to modern project management.
Time Management: The Industrial Revolution placed a premium on completing projects within specified timeframes, as timely delivery of goods and products was essential for business success. This emphasis on time management laid the foundation for project scheduling and time-based project management methods.
Documentation and Reporting: As projects grew in complexity, documentation and reporting became more essential for tracking progress and decision-making. The practice of recording project details, milestones, and financial data became a precursor to modern project reporting.
Leadership and Supervision: The need for effective leadership and supervision of workers in large factories and construction projects became apparent. Project managers, or individuals with similar roles, were responsible for overseeing operations, coordinating tasks, and ensuring that projects were completed successfully.
The Industrial Revolution, with its profound changes in industry and technology, provided the impetus for the development of project management principles, tools, and methodologies. While project management during this era was not as formalized as it is today, the challenges of managing complex projects in an industrial context laid the groundwork for the discipline's subsequent evolution and refinement.
Project Management in World War II
Project management played a crucial role during World War II, as the global conflict required the planning, coordination, and execution of a wide range of military operations, research projects, and logistical endeavors. The war provided a unique and challenging environment for the development and application of project management principles. Here are some key aspects of project management during World War II:
Manhattan Project: The Manhattan Project is one of the most iconic examples of project management during World War II. It was a top-secret research and development project that led to the creation of the atomic bomb. The project involved a vast and complex collaboration of scientists, engineers, and military personnel, and it required precise planning, resource management, and coordination. The success of the Manhattan Project demonstrated the effectiveness of project management in achieving ambitious and highly classified objectives.
War Production and Industrial Mobilization: The war effort necessitated the rapid expansion of industrial production to supply the military with equipment and weapons. Project management principles were applied to convert civilian factories into war production facilities, plan production schedules, and ensure the timely delivery of goods to the front lines.
Communication and Reporting: Effective communication and reporting systems were essential to keep military leaders informed of the status of various projects and operations. Project managers and officers regularly provided updates on progress and challenges.
Maintenance and Repair: The repair and maintenance of military equipment, including aircraft, tanks, and ships, was a critical project management function. Maintenance schedules, repair teams, and spare parts management were essential to keep the war machine operational.
Medical and Hospital Management: Managing the care of wounded soldiers and establishing field hospitals involved project management principles. This included setting up medical units, managing supplies, and ensuring that medical personnel were available where needed.
World War II served as a testing ground for many project management techniques and practices that would later become fundamental to the field. The successful completion of numerous military and logistical projects during the war demonstrated the value of systematic project management, leading to the continued development and refinement of project management principles in the post-war era.
Project Management Pioneers
The field of project management has been shaped by numerous pioneers who made significant contributions to its development. These individuals introduced concepts, methods, and practices that continue to influence modern project management. Here are some of the notable project management pioneers:
Henry L. Gantt (1861-1919): Henry L. Gantt is perhaps best known for the Gantt chart, a visual representation of project schedules. His work on the Gantt chart, which he developed in the early 1910s, has become an integral tool for project planning, scheduling, and tracking.
Henri Fayol (1841-1925): Henri Fayol was a French mining engineer and management theorist. He is recognized for his principles of management, which include concepts like unity of command, division of labor, and discipline. These principles have relevance in the field of project management.
Frederick Winslow Taylor (1856-1915): Frederick Taylor, an American engineer, is often referred to as the "father of scientific management." His contributions to time and motion studies, standardization, and efficiency in the workplace laid the groundwork for modern project management practices.
Walt W. Rostow (1916-2003): Walt Rostow was an American economist and historian who contributed to project management by developing the Rostow's Stages of Economic Growth model. This model is used to analyze economic and social development in projects and planning.
Lawrence P. Miles (1905-2003): Lawrence P. Miles is known for his work in industrial engineering and the development of the Work Simplification Program. He made significant contributions to work simplification, standardization, and efficiency in project management.
Tom Peters and Robert Waterman: While not strictly project management figures, Tom Peters and Robert Waterman, through their book "In Search of Excellence," popularized the concept of "Management by Walking Around" (MBWA), which emphasized active, on-site management. This concept has relevance in project management for ensuring effective oversight.
These pioneers, through their research, innovations, and contributions, have helped shape the field of project management into the organized discipline it is today. Their ideas and practices have provided a solid foundation for the development of methodologies, standards, and best practices used in project management across various industries.
The Manhattan Project
The Manhattan Project was a top-secret research and development project undertaken during World War II by the United States, the United Kingdom, and Canada. Its primary objective was to develop and produce an atomic bomb, an unprecedented and highly destructive weapon, before Nazi Germany or other Axis powers could do so. The project's name, "Manhattan," was a code name designed to divert attention from the true nature of the work.
Key aspects of the Manhattan Project include:
Origins and Motivation: The project was initiated in response to fears that Nazi Germany was pursuing atomic weapons. Concerns about the potential consequences of such weapons falling into the wrong hands were a significant driving force.
Project Leadership: The Manhattan Project was led by a group of prominent scientists, military leaders, and government officials. Major figures included J. Robert Oppenheimer, General Leslie Groves, and Enrico Fermi.
Research and Development: The project involved extensive scientific research and engineering to develop the necessary technology for atomic weapons. This included advances in nuclear physics, metallurgy, and materials science.
Uranium and Plutonium: The project pursued two parallel approaches to building an atomic bomb, using uranium-235 and plutonium-239. Enrichment methods for obtaining these fissile materials were a central focus of the research.
Legacy: The Manhattan Project not only led to the development of atomic weapons but also contributed to significant advances in nuclear science and technology. After the war, it played a role in the early development of peaceful applications of nuclear energy.
Post-War Developments: The success of the Manhattan Project had profound implications for the post-war world. It marked the beginning of the nuclear arms race between the United States and the Soviet Union and heightened global concerns about the potential for nuclear conflict.
The Manhattan Project is considered one of the most significant scientific and engineering efforts in history. It fundamentally altered the course of World War II and had far-reaching consequences for geopolitics, science, and global security in the post-war era.
Post-WWII Expansion of Project Management
The post-World War II era saw a significant expansion and evolution of project management as a discipline. The experiences of the war, coupled with economic and technological advancements, influenced the development and adoption of project management practices in various industries. Here are some key factors and events that contributed to the post-WWII expansion of project management:
Military and Defense Projects: The success of project management in military and defense projects during World War II highlighted the effectiveness of organized planning, resource allocation, and execution. Many military personnel with project management experience transitioned to civilian roles, bringing their expertise with them.
Economic Growth and Infrastructure Development: The post-war period was marked by substantial economic growth, particularly in the United States. The need to rebuild war-torn countries, improve infrastructure, and meet growing demand for consumer goods led to numerous large-scale projects, which required structured project management.
Construction and Manufacturing Industries: The construction and manufacturing sectors experienced significant expansion and modernization. The development of highways, bridges, dams, and housing projects required project management to ensure efficient execution and quality control.
Space Race: The Cold War rivalry between the United States and the Soviet Union triggered the Space Race, which included the development of space exploration projects such as the Apollo program. These complex, high-stakes projects demanded rigorous project management practices.
Technological Advancements: Advances in technology, including the emergence of computers and software, provided tools to facilitate project planning, scheduling, and tracking. The use of digital computers greatly improved the management of project data.
International Development: The reconstruction of post-war Europe through the Marshall Plan and similar efforts emphasized the need for effective project management to allocate resources, coordinate aid, and drive economic recovery.
Globalization: As businesses expanded their operations across borders, project management played a crucial role in coordinating international projects. The need for standardized approaches to project management became evident in a globalized economy.
The post-WWII expansion of project management is characterized by its growing recognition as a formal discipline and its application in a wide range of industries. The field saw the development of project management associations, the establishment of formal education and training programs, and the evolution of project management methodologies like the Waterfall model, Critical Path Method (CPM), and Program Evaluation and Review Technique (PERT). These developments set the stage for project management's continued growth and adaptation in the 21st century.
Project Management Methodologie
Project management methodologies are structured approaches, processes, and frameworks that guide and support the planning, execution, and control of projects. These methodologies provide a set of best practices, tools, and techniques to ensure that projects are completed efficiently, on time, within scope, and on budget. There are various project management methodologies, and the choice of methodology depends on the specific requirements and characteristics of a project. Here are some commonly used project management methodologies:
Agile: Agile methodologies, including Scrum, Kanban, and Extreme Programming (XP), prioritize flexibility and adaptability. Agile projects are divided into smaller iterations or sprints, and stakeholders frequently collaborate to adapt to changing requirements and deliver incremental results.
Scrum: Scrum is a popular Agile framework that organizes work into time-bound iterations called sprints. It emphasizes close collaboration among team members and stakeholders, regular reviews, and continuous improvement. Scrum is particularly effective for software development projects.
Kanban: Kanban is a visual project management methodology that focuses on managing work in progress. It uses a visual board with columns representing stages of work to control and limit the amount of work in progress. Kanban is beneficial for managing workflow and improving efficiency.
Critical Path Method (CPM): CPM is a network-based methodology used for scheduling and managing complex projects. It identifies the critical path, which represents the sequence of tasks that, if delayed, would delay the entire project. CPM is particularly useful for construction and engineering projects.
Program Evaluation and Review Technique (PERT): PERT is similar to CPM and is used for scheduling and controlling projects. It incorporates probabilistic time estimates to calculate expected project durations and identifies activities with the highest risk.
Six Sigma: Six Sigma is a data-driven methodology aimed at reducing defects and improving process quality. It employs a set of tools, including DMAIC (Define, Measure, Analyze, Improve, Control) and DMADV (Define, Measure, Analyze, Design, Verify), to improve project processes and outcomes.
Selecting the most appropriate project management methodology depends on factors such as project size, complexity, industry, team dynamics, and stakeholder requirements. Many organizations adopt a flexible approach and tailor their methodology to suit the specific needs of each project.
Project Management in the Information Age
Project management in the Information Age has undergone significant transformation due to the rapid advancements in technology, increased connectivity, and the widespread availability of data and information. These changes have reshaped how projects are planned, executed, and monitored across various industries. Here are some key aspects of project management in the Information Age:
Digital Tools and Software: The Information Age has brought a wealth of project management software and digital tools that enhance planning, scheduling, collaboration, and communication. Platforms like Microsoft Project, Trello, Asana, and Jira provide project managers and teams with powerful tools for tracking tasks, managing resources, and visualizing project progress.
Cloud-Based Project Management: Cloud computing allows project teams to access project information and collaborate from anywhere with an internet connection. Cloud-based project management tools offer real-time updates, file sharing, and enhanced mobility, making it easier for teams to work together regardless of geographical location.
Artificial Intelligence (AI) and Machine Learning: AI and machine learning technologies are increasingly used in project management for tasks such as predictive analytics, chatbots for project inquiries, and automated scheduling. These technologies help streamline project processes and improve decision-making.
Real-Time Communication: The Information Age has revolutionized communication through instant messaging, video conferencing, and project management platforms. Real-time communication tools enable project managers and team members to stay connected and share information more efficiently.
Integration of Internet of Things (IoT): IoT devices and sensors are used to collect data in real-time from various sources, including equipment, infrastructure, and the environment. Project managers can use this data for monitoring, predictive maintenance, and improved decision-making in construction, manufacturing, and other industries.
Project management in the Information Age is characterized by a greater emphasis on adaptability, data-driven decision-making, collaboration, and real-time communication. While traditional project management principles remain relevant, the integration of technology and data-driven insights has enhanced the efficiency and effectiveness of project management practices across a wide range of industries.
Project Management in the 21st Century
Project management in the 21st century has evolved significantly due to technological advancements, changes in business dynamics, and the need for more adaptive and efficient project execution. In this era, project management practices have been transformed in several ways:
Digital Transformation: The widespread adoption of digital tools and technologies has revolutionized project management. Cloud-based project management software, collaboration platforms, and data analytics tools have become essential for planning, monitoring, and reporting on projects.
Agile and Iterative Approaches: Agile methodologies, such as Scrum and Kanban, have gained prominence across industries. These approaches prioritize flexibility, customer collaboration, and incremental progress, making them particularly suited for software development and other projects with changing requirements.
Hybrid Project Management: Many organizations use hybrid project management approaches that combine elements of traditional Waterfall methods with Agile principles. This hybrid approach allows for adaptability while maintaining structured planning and control.
Blockchain Technology: Blockchain is increasingly applied to project management to ensure data integrity, enhance security, and provide transparent and immutable records of project activities and transactions.
Sustainability and ESG Integration: In response to growing environmental and social concerns, project managers are integrating Environmental, Social, and Governance (ESG) considerations into project planning and execution. Sustainability is becoming a key project management concern.
Scalability: Project managers in the 21st century must adapt to projects of varying scales, from small, fast-paced initiatives to massive, long-term endeavors, all while maintaining flexibility and agility in their approach.
Security and Privacy: With increasing concerns about data security and privacy, project managers must prioritize and implement robust security measures, especially in industries where sensitive information is involved.
Project management in the 21st century is characterized by its adaptability, integration of technology, and focus on stakeholder collaboration. It has expanded beyond traditional project-based industries like construction and engineering to encompass various sectors, including IT, healthcare, finance, and marketing. As technology continues to evolve, project management practices are expected to evolve along with it, ensuring that projects are delivered more efficiently and effectively in this dynamic era.
Conclusion
In conclusion, the field of project management has evolved significantly over time, driven by historical developments, technological advancements, and changing business landscapes. From ancient project management practices in the construction of the pyramids to the modern, data-driven approaches of the 21st century, project management has continually adapted to meet the demands of complex projects in various industries.
As project management continues to evolve, the importance of effective communication, stakeholder engagement, and adaptability remains paramount. Whether it's the Manhattan Project during World War II or managing remote and distributed teams in today's globalized world, the principles of project management serve as a crucial framework for achieving success in complex endeavors.
In this dynamic and fast-paced era, project managers must remain agile, data-savvy, and committed to continuous improvement. The 21st century's project management landscape is marked by its ability to navigate challenges and leverage opportunities, making it a critical discipline for organizations seeking to deliver projects on time, within budget, and with high quality.
Read More
Project management is a vital discipline that enables organizations to plan, execute, and complete tasks efficiently and effectively. It has a rich history that has evolved over centuries, reflecting the changing needs of society, technology, and industry. In this introduction, we will embark on a journey through time to explore the key milestones and developments in the history of project management, shedding light on its origins, growth, and transformation.
The 20th century witnessed a significant expansion of project management, particularly during World War II, where it played a critical role in the success of military operations and research endeavors. Post-WWII, the discipline grew further, with notable pioneers like Henry L. Gantt and Henri Fayol contributing to its development.
As we move into the 21st century, project management continues to evolve. The advent of the digital age, information technology, and globalization has revolutionized how projects are planned, executed, and monitored. Agile methodologies, virtual teams, sustainability considerations, and other contemporary factors now play a significant role in shaping the landscape of project management.
Table of contents
-
Ancient Project Management Practices
-
Origins of Modern Project Management
-
Industrial Revolution and Project Management
-
Project Management in World War II
-
Project Management Pioneers
-
The Manhattan Project
-
Post-WWII Expansion of Project Management
-
Project Management Methodologie
-
Project Management in the Information Age
-
Project Management in the 21st Century
-
Conclusion
Ancient Project Management Practices
Long before the formal discipline of project management emerged, ancient civilizations engaged in various activities that could be considered early project management practices. These civilizations used systematic approaches to plan, organize, and execute complex projects. Here are some examples of ancient project management practices:
The Pyramids of Egypt: The construction of the Egyptian pyramids, including the Great Pyramid of Giza, is often cited as an early example of project management. Ancient Egyptians used detailed plans, organized labor forces, and managed resources like limestone, granite, and labor to build these monumental structures. Hieroglyphics on the pyramid walls depicted various phases of construction, highlighting the project's organized nature.
The Great Wall of China: The construction of the Great Wall of China, which spanned centuries and multiple dynasties, involved careful planning and resource management. It required coordinating the efforts of large workforces to build fortifications across vast distances. Additionally, the wall's purpose evolved over time, demonstrating adaptability in project management.
Roman Aqueducts: The Romans are renowned for their engineering feats, including the construction of aqueducts. These water supply systems showcased meticulous planning and precise construction methods. Engineers and laborers worked together to ensure a reliable water supply to Roman cities, and the design and construction were crucial aspects of these projects.
The Silk Road: The development and maintenance of the Silk Road, a vast network of trade routes connecting the East and West, required ongoing project management. It involved managing caravans, security, route maintenance, and diplomatic relationships among various regions. This ancient trade network flourished due to careful planning and execution.
Mayan Temples: Mayan civilization in Central America constructed intricate temples and structures, demonstrating advanced project management skills. They used mathematical precision and astronomical knowledge to align their buildings and effectively manage resources such as stone and labor.
While the ancient world lacked the formal methodologies and terminologies of modern project management, these historical examples demonstrate that the principles of planning, organizing, and executing complex tasks have deep roots in human civilization. The success of these ancient projects depended on effective leadership, resource management, and the ability to adapt to changing circumstances, all of which are core aspects of project management.
Origins of Modern Project Management
The origins of modern project management can be traced back to the mid-20th century, with several key developments and contributors who laid the foundation for the discipline. Here are some crucial points in the origins of modern project management:
Henry L. Gantt and the Gantt Chart (1910s): Henry L. Gantt, an American engineer and management consultant, developed the Gantt chart in the early 1910s. The Gantt chart is a visual representation of a project schedule, which shows tasks and their durations. It was a significant innovation in project management as it allowed for easy tracking of progress and resource allocation.
The Manhattan Project (1940s): The development of the atomic bomb during World War II through the Manhattan Project is often considered a pivotal moment in the history of project management. This massive undertaking required precise planning, coordination of scientific and engineering efforts, and the efficient allocation of resources. It set the stage for the recognition of project management as a crucial discipline.
Project Evaluation and Review Technique (PERT) and Critical Path Method (CPM) (1950s): PERT and CPM are two project management methodologies developed in the 1950s. PERT was developed by the U.S. Navy for the Polaris missile project, while CPM was developed by DuPont for maintenance projects. These techniques helped in scheduling, coordinating, and managing complex projects. They became fundamental tools in project management, particularly for large engineering and construction projects.
Software and Technology Advances: The advent of computer technology in the mid-20th century revolutionized project management. Project management software, like the development of Microsoft Project in the 1980s, made it easier to create and manage project schedules, budgets, and resources, further advancing the field.
These early developments and historical milestones laid the groundwork for modern project management as a distinct discipline. Today, project management is applied across a wide range of industries, from information technology to healthcare and manufacturing, and is considered a critical factor in the success of organizations and the execution of complex projects.
Industrial Revolution and Project Management
The Industrial Revolution had a profound impact on the development of project management as a formal discipline. This period of rapid industrialization, which began in the late 18th century and continued into the 19th century, brought about significant changes in manufacturing, transportation, and technology. As industries grew and became more complex, the need for structured project management practices became increasingly evident. Here's how the Industrial Revolution influenced the evolution of project management:
Complex Manufacturing Projects: The Industrial Revolution introduced new manufacturing processes and technologies, such as the mechanization of factories and the introduction of assembly lines. Managing these complex manufacturing projects required planning, coordination, and resource allocation, which are fundamental aspects of project management.
Growth of Multidisciplinary Teams: Industrialization led to the formation of multidisciplinary teams, with engineers, architects, laborers, and other specialists working together. Effective communication and collaboration among team members became critical, marking the beginning of the teamwork and leadership elements that are central to modern project management.
Time Management: The Industrial Revolution placed a premium on completing projects within specified timeframes, as timely delivery of goods and products was essential for business success. This emphasis on time management laid the foundation for project scheduling and time-based project management methods.
Documentation and Reporting: As projects grew in complexity, documentation and reporting became more essential for tracking progress and decision-making. The practice of recording project details, milestones, and financial data became a precursor to modern project reporting.
Leadership and Supervision: The need for effective leadership and supervision of workers in large factories and construction projects became apparent. Project managers, or individuals with similar roles, were responsible for overseeing operations, coordinating tasks, and ensuring that projects were completed successfully.
The Industrial Revolution, with its profound changes in industry and technology, provided the impetus for the development of project management principles, tools, and methodologies. While project management during this era was not as formalized as it is today, the challenges of managing complex projects in an industrial context laid the groundwork for the discipline's subsequent evolution and refinement.
Project Management in World War II
Project management played a crucial role during World War II, as the global conflict required the planning, coordination, and execution of a wide range of military operations, research projects, and logistical endeavors. The war provided a unique and challenging environment for the development and application of project management principles. Here are some key aspects of project management during World War II:
Manhattan Project: The Manhattan Project is one of the most iconic examples of project management during World War II. It was a top-secret research and development project that led to the creation of the atomic bomb. The project involved a vast and complex collaboration of scientists, engineers, and military personnel, and it required precise planning, resource management, and coordination. The success of the Manhattan Project demonstrated the effectiveness of project management in achieving ambitious and highly classified objectives.
War Production and Industrial Mobilization: The war effort necessitated the rapid expansion of industrial production to supply the military with equipment and weapons. Project management principles were applied to convert civilian factories into war production facilities, plan production schedules, and ensure the timely delivery of goods to the front lines.
Communication and Reporting: Effective communication and reporting systems were essential to keep military leaders informed of the status of various projects and operations. Project managers and officers regularly provided updates on progress and challenges.
Maintenance and Repair: The repair and maintenance of military equipment, including aircraft, tanks, and ships, was a critical project management function. Maintenance schedules, repair teams, and spare parts management were essential to keep the war machine operational.
Medical and Hospital Management: Managing the care of wounded soldiers and establishing field hospitals involved project management principles. This included setting up medical units, managing supplies, and ensuring that medical personnel were available where needed.
World War II served as a testing ground for many project management techniques and practices that would later become fundamental to the field. The successful completion of numerous military and logistical projects during the war demonstrated the value of systematic project management, leading to the continued development and refinement of project management principles in the post-war era.
Project Management Pioneers
The field of project management has been shaped by numerous pioneers who made significant contributions to its development. These individuals introduced concepts, methods, and practices that continue to influence modern project management. Here are some of the notable project management pioneers:
Henry L. Gantt (1861-1919): Henry L. Gantt is perhaps best known for the Gantt chart, a visual representation of project schedules. His work on the Gantt chart, which he developed in the early 1910s, has become an integral tool for project planning, scheduling, and tracking.
Henri Fayol (1841-1925): Henri Fayol was a French mining engineer and management theorist. He is recognized for his principles of management, which include concepts like unity of command, division of labor, and discipline. These principles have relevance in the field of project management.
Frederick Winslow Taylor (1856-1915): Frederick Taylor, an American engineer, is often referred to as the "father of scientific management." His contributions to time and motion studies, standardization, and efficiency in the workplace laid the groundwork for modern project management practices.
Walt W. Rostow (1916-2003): Walt Rostow was an American economist and historian who contributed to project management by developing the Rostow's Stages of Economic Growth model. This model is used to analyze economic and social development in projects and planning.
Lawrence P. Miles (1905-2003): Lawrence P. Miles is known for his work in industrial engineering and the development of the Work Simplification Program. He made significant contributions to work simplification, standardization, and efficiency in project management.
Tom Peters and Robert Waterman: While not strictly project management figures, Tom Peters and Robert Waterman, through their book "In Search of Excellence," popularized the concept of "Management by Walking Around" (MBWA), which emphasized active, on-site management. This concept has relevance in project management for ensuring effective oversight.
These pioneers, through their research, innovations, and contributions, have helped shape the field of project management into the organized discipline it is today. Their ideas and practices have provided a solid foundation for the development of methodologies, standards, and best practices used in project management across various industries.
The Manhattan Project
The Manhattan Project was a top-secret research and development project undertaken during World War II by the United States, the United Kingdom, and Canada. Its primary objective was to develop and produce an atomic bomb, an unprecedented and highly destructive weapon, before Nazi Germany or other Axis powers could do so. The project's name, "Manhattan," was a code name designed to divert attention from the true nature of the work.
Key aspects of the Manhattan Project include:
Origins and Motivation: The project was initiated in response to fears that Nazi Germany was pursuing atomic weapons. Concerns about the potential consequences of such weapons falling into the wrong hands were a significant driving force.
Project Leadership: The Manhattan Project was led by a group of prominent scientists, military leaders, and government officials. Major figures included J. Robert Oppenheimer, General Leslie Groves, and Enrico Fermi.
Research and Development: The project involved extensive scientific research and engineering to develop the necessary technology for atomic weapons. This included advances in nuclear physics, metallurgy, and materials science.
Uranium and Plutonium: The project pursued two parallel approaches to building an atomic bomb, using uranium-235 and plutonium-239. Enrichment methods for obtaining these fissile materials were a central focus of the research.
Legacy: The Manhattan Project not only led to the development of atomic weapons but also contributed to significant advances in nuclear science and technology. After the war, it played a role in the early development of peaceful applications of nuclear energy.
Post-War Developments: The success of the Manhattan Project had profound implications for the post-war world. It marked the beginning of the nuclear arms race between the United States and the Soviet Union and heightened global concerns about the potential for nuclear conflict.
The Manhattan Project is considered one of the most significant scientific and engineering efforts in history. It fundamentally altered the course of World War II and had far-reaching consequences for geopolitics, science, and global security in the post-war era.
Post-WWII Expansion of Project Management
The post-World War II era saw a significant expansion and evolution of project management as a discipline. The experiences of the war, coupled with economic and technological advancements, influenced the development and adoption of project management practices in various industries. Here are some key factors and events that contributed to the post-WWII expansion of project management:
Military and Defense Projects: The success of project management in military and defense projects during World War II highlighted the effectiveness of organized planning, resource allocation, and execution. Many military personnel with project management experience transitioned to civilian roles, bringing their expertise with them.
Economic Growth and Infrastructure Development: The post-war period was marked by substantial economic growth, particularly in the United States. The need to rebuild war-torn countries, improve infrastructure, and meet growing demand for consumer goods led to numerous large-scale projects, which required structured project management.
Construction and Manufacturing Industries: The construction and manufacturing sectors experienced significant expansion and modernization. The development of highways, bridges, dams, and housing projects required project management to ensure efficient execution and quality control.
Space Race: The Cold War rivalry between the United States and the Soviet Union triggered the Space Race, which included the development of space exploration projects such as the Apollo program. These complex, high-stakes projects demanded rigorous project management practices.
Technological Advancements: Advances in technology, including the emergence of computers and software, provided tools to facilitate project planning, scheduling, and tracking. The use of digital computers greatly improved the management of project data.
International Development: The reconstruction of post-war Europe through the Marshall Plan and similar efforts emphasized the need for effective project management to allocate resources, coordinate aid, and drive economic recovery.
Globalization: As businesses expanded their operations across borders, project management played a crucial role in coordinating international projects. The need for standardized approaches to project management became evident in a globalized economy.
The post-WWII expansion of project management is characterized by its growing recognition as a formal discipline and its application in a wide range of industries. The field saw the development of project management associations, the establishment of formal education and training programs, and the evolution of project management methodologies like the Waterfall model, Critical Path Method (CPM), and Program Evaluation and Review Technique (PERT). These developments set the stage for project management's continued growth and adaptation in the 21st century.
Project Management Methodologie
Project management methodologies are structured approaches, processes, and frameworks that guide and support the planning, execution, and control of projects. These methodologies provide a set of best practices, tools, and techniques to ensure that projects are completed efficiently, on time, within scope, and on budget. There are various project management methodologies, and the choice of methodology depends on the specific requirements and characteristics of a project. Here are some commonly used project management methodologies:
Agile: Agile methodologies, including Scrum, Kanban, and Extreme Programming (XP), prioritize flexibility and adaptability. Agile projects are divided into smaller iterations or sprints, and stakeholders frequently collaborate to adapt to changing requirements and deliver incremental results.
Scrum: Scrum is a popular Agile framework that organizes work into time-bound iterations called sprints. It emphasizes close collaboration among team members and stakeholders, regular reviews, and continuous improvement. Scrum is particularly effective for software development projects.
Kanban: Kanban is a visual project management methodology that focuses on managing work in progress. It uses a visual board with columns representing stages of work to control and limit the amount of work in progress. Kanban is beneficial for managing workflow and improving efficiency.
Critical Path Method (CPM): CPM is a network-based methodology used for scheduling and managing complex projects. It identifies the critical path, which represents the sequence of tasks that, if delayed, would delay the entire project. CPM is particularly useful for construction and engineering projects.
Program Evaluation and Review Technique (PERT): PERT is similar to CPM and is used for scheduling and controlling projects. It incorporates probabilistic time estimates to calculate expected project durations and identifies activities with the highest risk.
Six Sigma: Six Sigma is a data-driven methodology aimed at reducing defects and improving process quality. It employs a set of tools, including DMAIC (Define, Measure, Analyze, Improve, Control) and DMADV (Define, Measure, Analyze, Design, Verify), to improve project processes and outcomes.
Selecting the most appropriate project management methodology depends on factors such as project size, complexity, industry, team dynamics, and stakeholder requirements. Many organizations adopt a flexible approach and tailor their methodology to suit the specific needs of each project.
Project Management in the Information Age
Project management in the Information Age has undergone significant transformation due to the rapid advancements in technology, increased connectivity, and the widespread availability of data and information. These changes have reshaped how projects are planned, executed, and monitored across various industries. Here are some key aspects of project management in the Information Age:
Digital Tools and Software: The Information Age has brought a wealth of project management software and digital tools that enhance planning, scheduling, collaboration, and communication. Platforms like Microsoft Project, Trello, Asana, and Jira provide project managers and teams with powerful tools for tracking tasks, managing resources, and visualizing project progress.
Cloud-Based Project Management: Cloud computing allows project teams to access project information and collaborate from anywhere with an internet connection. Cloud-based project management tools offer real-time updates, file sharing, and enhanced mobility, making it easier for teams to work together regardless of geographical location.
Artificial Intelligence (AI) and Machine Learning: AI and machine learning technologies are increasingly used in project management for tasks such as predictive analytics, chatbots for project inquiries, and automated scheduling. These technologies help streamline project processes and improve decision-making.
Real-Time Communication: The Information Age has revolutionized communication through instant messaging, video conferencing, and project management platforms. Real-time communication tools enable project managers and team members to stay connected and share information more efficiently.
Integration of Internet of Things (IoT): IoT devices and sensors are used to collect data in real-time from various sources, including equipment, infrastructure, and the environment. Project managers can use this data for monitoring, predictive maintenance, and improved decision-making in construction, manufacturing, and other industries.
Project management in the Information Age is characterized by a greater emphasis on adaptability, data-driven decision-making, collaboration, and real-time communication. While traditional project management principles remain relevant, the integration of technology and data-driven insights has enhanced the efficiency and effectiveness of project management practices across a wide range of industries.
Project Management in the 21st Century
Project management in the 21st century has evolved significantly due to technological advancements, changes in business dynamics, and the need for more adaptive and efficient project execution. In this era, project management practices have been transformed in several ways:
Digital Transformation: The widespread adoption of digital tools and technologies has revolutionized project management. Cloud-based project management software, collaboration platforms, and data analytics tools have become essential for planning, monitoring, and reporting on projects.
Agile and Iterative Approaches: Agile methodologies, such as Scrum and Kanban, have gained prominence across industries. These approaches prioritize flexibility, customer collaboration, and incremental progress, making them particularly suited for software development and other projects with changing requirements.
Hybrid Project Management: Many organizations use hybrid project management approaches that combine elements of traditional Waterfall methods with Agile principles. This hybrid approach allows for adaptability while maintaining structured planning and control.
Blockchain Technology: Blockchain is increasingly applied to project management to ensure data integrity, enhance security, and provide transparent and immutable records of project activities and transactions.
Sustainability and ESG Integration: In response to growing environmental and social concerns, project managers are integrating Environmental, Social, and Governance (ESG) considerations into project planning and execution. Sustainability is becoming a key project management concern.
Scalability: Project managers in the 21st century must adapt to projects of varying scales, from small, fast-paced initiatives to massive, long-term endeavors, all while maintaining flexibility and agility in their approach.
Security and Privacy: With increasing concerns about data security and privacy, project managers must prioritize and implement robust security measures, especially in industries where sensitive information is involved.
Project management in the 21st century is characterized by its adaptability, integration of technology, and focus on stakeholder collaboration. It has expanded beyond traditional project-based industries like construction and engineering to encompass various sectors, including IT, healthcare, finance, and marketing. As technology continues to evolve, project management practices are expected to evolve along with it, ensuring that projects are delivered more efficiently and effectively in this dynamic era.
Conclusion
In conclusion, the field of project management has evolved significantly over time, driven by historical developments, technological advancements, and changing business landscapes. From ancient project management practices in the construction of the pyramids to the modern, data-driven approaches of the 21st century, project management has continually adapted to meet the demands of complex projects in various industries.
As project management continues to evolve, the importance of effective communication, stakeholder engagement, and adaptability remains paramount. Whether it's the Manhattan Project during World War II or managing remote and distributed teams in today's globalized world, the principles of project management serve as a crucial framework for achieving success in complex endeavors.
In this dynamic and fast-paced era, project managers must remain agile, data-savvy, and committed to continuous improvement. The 21st century's project management landscape is marked by its ability to navigate challenges and leverage opportunities, making it a critical discipline for organizations seeking to deliver projects on time, within budget, and with high quality.
Benefits of Implementing CMMI in Your Organization
Implementing the Capability Maturity Model Integration (CMMI) in your organization can bring about a myriad of benefits, enhancing its overall efficiency and competitiveness in today's dynamic business landscape. CMMI serves as a comprehensive framework designed to elevate and optimize an organization's processes, thereby ensuring higher levels of performance, quality, and productivity.
One of the primary advantages of implementing CMMI lies in its ability to provide a structured approach to process improvement. By adopting CMMI practices, organizations can systematically identify, evaluate, and refine their existing processes. This structured methodology not only streamlines operations but also fosters a culture of continuous improvement, ensuring that the organization remains adaptable and responsive to evolving market demands.
CMMI is not merely a tool for process improvement; it also plays a pivotal role in risk management. By identifying and addressing potential risks at early stages, organizations can proactively mitigate challenges that may arise during project execution. This risk mitigation approach not only safeguards project timelines and budgets but also contributes to a more resilient and sustainable business model.
In addition to these operational advantages, implementing CMMI can also enhance communication and collaboration within an organization. The framework encourages cross-functional teams to work cohesively towards common objectives, fostering a collaborative culture that promotes knowledge sharing and innovation. This collaborative mindset is crucial in today's interconnected business environment, where agility and adaptability are key to success.
The benefits of implementing CMMI in an organization are multi-faceted, ranging from improved process efficiency and product quality to enhanced risk management and competitive advantage. As businesses navigate the complexities of a rapidly changing landscape, CMMI stands as a valuable framework that empowers organizations to not only meet current challenges but also to thrive in the future.
Table of contents
-
Enhanced Process Efficiency
-
Quality Assurance and Product Excellence
-
Risk Mitigation Strategies
-
Standardization of Best Practices
-
Collaborative Team Culture
-
Strategic Alignment and Competitive Edge
-
Continuous Improvement Mindset
-
Resource Optimization and Cost Management
-
Employee Development and Engagement
-
Measurable Performance Metrics
-
Conclusion
Enhanced Process Efficiency
Enhanced process efficiency is a key benefit of implementing the Capability Maturity Model Integration (CMMI) in an organization. This aspect revolves around the systematic improvement and optimization of existing processes, leading to increased effectiveness and streamlined workflows.
CMMI provides a structured framework for organizations to assess, refine, and standardize their processes across various departments. Through the identification of best practices and the elimination of redundancies or bottlenecks, CMMI helps organizations achieve a higher level of efficiency in their day-to-day operations.
One way CMMI enhances process efficiency is by promoting a clear understanding of roles, responsibilities, and workflows within the organization. By defining and documenting processes, teams can work more cohesively, reducing the likelihood of misunderstandings or delays. This clarity contributes to smoother collaboration and improved overall efficiency.
Furthermore, CMMI encourages organizations to continuously monitor and evaluate their processes. This ongoing assessment allows for the identification of areas for improvement. By addressing inefficiencies and optimizing processes iteratively, organizations can adapt to changing circumstances and maintain a competitive edge in their respective industries.
Enhanced process efficiency, facilitated by CMMI, involves the systematic improvement of organizational processes through clear documentation, continuous monitoring, and the establishment of performance metrics. By embracing this aspect of CMMI, organizations position themselves to operate more smoothly, respond to challenges more effectively, and deliver high-quality products or services with greater consistency.
Quality Assurance and Product Excellence
Quality assurance and product excellence are fundamental outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that not only ensures the consistency of processes but also places a strong emphasis on delivering high-quality products and services.
CMMI encourages organizations to adopt rigorous quality assurance practices throughout the product or service development lifecycle. This involves defining clear quality standards, conducting thorough reviews, and implementing robust testing procedures. By adhering to these practices, organizations can identify and rectify defects early in the process, preventing issues from escalating and ultimately ensuring the delivery of superior products or services.
One of the ways CMMI contributes to product excellence is through its focus on continuous improvement. The model prompts organizations to regularly assess their processes and make necessary adjustments to enhance efficiency and quality. This iterative approach ensures that products and services evolve over time, meeting or exceeding customer expectations.
CMMI's impact on quality assurance and product excellence is evident through its emphasis on rigorous testing, continuous improvement, customer-centric practices, and the establishment of measurable quality metrics. By integrating these principles into their processes, organizations can consistently produce high-quality products, build customer trust, and gain a competitive advantage in the marketplace.
Risk Mitigation Strategies
Risk mitigation strategies are essential components of effective project and organizational management, and the implementation of the Capability Maturity Model Integration (CMMI) plays a pivotal role in shaping these strategies. One key aspect of risk mitigation within the CMMI framework is the emphasis on early identification. By encouraging organizations to identify risks at the outset of a project or process, CMMI enables teams to assess potential challenges before they escalate. This proactive approach sets the stage for comprehensive risk management throughout the project lifecycle.
CMMI goes beyond qualitative assessments by promoting quantitative risk analysis techniques. Assigning numerical values to risks and their potential impacts allows organizations to prioritize and address the most critical issues. This data-driven approach ensures that resources are allocated efficiently, focusing on mitigating risks that pose the greatest threat to project success.
Effective communication is highlighted within CMMI's risk mitigation strategies. Transparent and open communication about identified risks ensures that relevant stakeholders are informed and can contribute to mitigation efforts. This inclusive communication approach fosters a sense of shared responsibility and promotes a collective effort in addressing and overcoming challenges.
Finally, CMMI promotes a culture of continuous improvement, extending to the organization's risk management processes. Through regular assessments and feedback loops, organizations refine their risk management approaches. This commitment to ongoing improvement ensures that risk mitigation strategies evolve and remain effective in the face of changing circumstances, contributing to overall organizational resilience. In essence, CMMI's risk mitigation strategies provide a comprehensive and adaptable framework for organizations to navigate challenges successfully and enhance project and organizational outcomes.
Standardization of Best Practices
The standardization of best practices is a key benefit derived from implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that emphasizes the identification, documentation, and adherence to proven methodologies across various business functions. This standardization contributes significantly to the overall efficiency, consistency, and quality of organizational processes.
CMMI guides organizations in defining and documenting their best practices, ensuring a clear understanding of established methods and procedures. This documentation serves as a valuable resource for employees, providing a reference point for how tasks and processes should be executed. Standardizing best practices in this manner fosters a shared understanding and promotes consistency across teams, reducing the likelihood of errors or variations in execution.
The standardization of best practices facilitated by CMMI is a cornerstone of organizational excellence. It provides a systematic approach to defining, documenting, and implementing proven methodologies, fostering consistency, efficiency, and quality across the organization. This standardized foundation not only enhances day-to-day operations but also establishes a framework for continuous improvement and organizational resilience.
Collaborative Team Culture
Collaborative team culture is a critical aspect of a thriving and high-performing organization. When teams work together seamlessly and share a common purpose, it not only enhances the quality of work but also contributes to a positive and engaging work environment. In a collaborative team culture, individuals come together, leveraging their diverse skills and experiences to achieve shared goals.
Effective communication lies at the heart of collaborative team culture. It's about more than just conveying information; it's about creating an environment where team members feel comfortable expressing ideas, asking questions, and providing feedback. A culture that values open communication fosters transparency and ensures that everyone is on the same page, reducing the likelihood of misunderstandings and promoting a sense of unity.
Cross-functional collaboration is a key element of collaborative team culture. When individuals from different departments or disciplines collaborate, it brings a richness of perspectives to problem-solving and decision-making. This interdisciplinary approach often leads to innovative solutions that may not have been possible within the confines of a single function. Cross-functional collaboration also breaks down silos, promoting a more holistic understanding of the organization's objectives.
Continuous improvement is a core principle of collaborative team culture. Teams that embrace a mindset of ongoing learning and adaptation are better equipped to navigate challenges and capitalize on opportunities. Regular reflections on successes and setbacks, coupled with a commitment to refining processes, contribute to a culture of growth and development.
In essence, a collaborative team culture is a catalyst for organizational success. It builds a foundation of trust, encourages innovation, and empowers individuals to contribute their best efforts toward shared objectives. As organizations embrace and cultivate collaborative team cultures, they position themselves for sustained excellence and adaptability in a dynamic and ever-evolving landscape.
Strategic Alignment and Competitive Edge
Strategic alignment and gaining a competitive edge are two significant outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that aligns the organization's processes with its strategic objectives, fostering a cohesive approach that enhances competitiveness in the marketplace.
CMMI emphasizes strategic alignment by encouraging organizations to integrate their processes with overarching business goals. This alignment ensures that every process and activity within the organization contributes directly to the strategic objectives. As a result, teams work cohesively towards common goals, minimizing the risk of disjointed efforts and optimizing resources for maximum impact.
CMMI's focus on continuous improvement contributes to sustaining a competitive edge over time. The framework encourages organizations to regularly reassess their processes, incorporating lessons learned and adapting to evolving market conditions. This commitment to ongoing improvement ensures that the organization remains dynamic and responsive, staying ahead of competitors who may be slower to adapt.
Strategic alignment also plays a crucial role in decision-making. When processes are aligned with strategic objectives, decision-makers have a clear understanding of how choices impact overall goals. This clarity reduces the likelihood of decisions that may deviate from the strategic path and ensures that resources are allocated in ways that maximize value.
CMMI's emphasis on strategic alignment helps organizations create a seamless connection between their processes and overarching business objectives. This alignment enhances organizational agility, fosters a data-driven approach to performance measurement, and ultimately contributes to gaining and sustaining a competitive edge in the marketplace. As organizations implement and mature through the CMMI framework, they are better positioned to navigate the complexities of the business landscape while achieving strategic success.
Continuous Improvement Mindset
The continuous improvement mindset is a fundamental principle embedded in the Capability Maturity Model Integration (CMMI) and serves as a guiding philosophy for organizations seeking to enhance their processes and overall performance. CMMI encourages a culture where the pursuit of excellence is ongoing, and teams are committed to refining their practices incrementally over time.
CMMI's continuous improvement mindset involves the systematic identification and implementation of enhancements. Organizations are encouraged to gather data, feedback, and lessons learned from ongoing projects. This information is then analyzed to identify patterns and trends, providing insights that inform strategic decisions for improvement. The focus is not only on fixing immediate issues but on creating a foundation for sustained and long-term advancement.
CMMI's commitment to continuous improvement extends beyond individual projects to encompass the entire organization. It advocates for the establishment of metrics and key performance indicators (KPIs) that provide quantifiable insights into process effectiveness. Regular reviews of these metrics enable organizations to track progress, measure success, and identify areas for further enhancement.
The continuous improvement mindset advocated by CMMI is a cornerstone of organizational success. It instills a culture of reflection, learning, and proactive refinement. By embracing this mindset, organizations position themselves to not only address current challenges but also to navigate future uncertainties with resilience and agility. Continuous improvement becomes a journey, ingrained in the organizational DNA, driving sustained excellence and innovation.
Resource Optimization and Cost Management
Resource optimization and cost management are integral components of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that guides organizations in efficiently managing their resources and controlling costs, contributing to improved overall performance and sustainability.
CMMI emphasizes the importance of optimizing resources by aligning them with organizational objectives. This involves a systematic evaluation of available human, financial, and technological resources and ensuring that they are strategically allocated to projects and processes. By optimizing resource utilization, organizations can enhance productivity, reduce waste, and achieve better outcomes without unnecessary expenditures.
Cost management, within the context of CMMI, involves controlling and optimizing expenses throughout the project lifecycle. This includes not only direct project costs but also indirect costs associated with supporting processes. CMMI encourages organizations to establish clear cost management practices, such as budgeting, monitoring expenditures, and implementing cost-saving measures.
CMMI promotes a proactive approach to resource optimization by emphasizing risk management. By identifying potential risks early in the project or process, organizations can develop contingency plans to address resource-related challenges. This proactive risk management contributes to avoiding cost overruns and disruptions, enhancing the organization's ability to stay within budgetary constraints.
Resource optimization and cost management, as guided by CMMI, are essential for organizations aiming to achieve efficiency, control expenses, and enhance overall performance. The framework's emphasis on quantitative metrics, risk management, standardization of best practices, and continuous improvement contributes to a systematic and strategic approach to resource utilization and cost control. By implementing these principles, organizations can navigate resource challenges effectively, control costs, and position themselves for sustained success in a competitive business environment.
Employee Development and Engagement
Employee development and engagement, as guided by the Capability Maturity Model Integration (CMMI), encompasses various strategic initiatives aimed at fostering a skilled and motivated workforce. CMMI emphasizes the establishment of structured professional development programs, ensuring that employees continuously enhance their skills and stay abreast of industry trends. This commitment to ongoing learning contributes to the organization's adaptability and the individual growth of its employees.
CMMI also advocates for a culture of knowledge sharing and collaboration. Organizations are encouraged to create platforms for employees to share their expertise, fostering a collaborative environment where collective learning is prioritized. This collaborative culture not only enhances employee development but also strengthens the overall knowledge base within the organization.
Recognition and rewards play a pivotal role in employee engagement within CMMI. By establishing systems that acknowledge and reward employees for their contributions, organizations boost morale and reinforce a positive and engaged workforce. This recognition creates a sense of value and appreciation among employees, strengthening their commitment to the organization's success.
Employee involvement in decision-making processes is another key principle of CMMI's approach to engagement. Seeking input from employees at various levels fosters a participatory environment where individuals feel their voices are heard. This inclusion not only improves the quality of decisions but also instills a sense of ownership and commitment among employees.
Measurable Performance Metrics
Implementing measurable performance metrics is a key component of the Capability Maturity Model Integration (CMMI) framework. CMMI emphasizes the importance of quantifiable indicators to assess and improve various aspects of an organization's processes. Measurable performance metrics provide valuable insights into efficiency, effectiveness, and overall success, guiding data-driven decision-making and continuous improvement efforts.
CMMI encourages organizations to define key performance indicators (KPIs) that align with their strategic objectives. These metrics should be specific, measurable, achievable, relevant, and time-bound (SMART), ensuring clarity in measurement and facilitating accurate assessments of performance. Examples of measurable performance metrics may include project completion time, defect rates, customer satisfaction scores, and adherence to schedule and budget.
Measurable performance metrics, as advocated by CMMI, provide a structured and data-driven approach to evaluating organizational processes. By defining clear, SMART indicators, establishing baselines, incorporating both quantitative and qualitative measures, and conducting regular reviews, organizations can gain valuable insights into their performance. These metrics not only guide decision-making but also support a culture of continuous improvement, fostering organizational maturity and resilience in a competitive landscape.
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) serves as a comprehensive and structured framework that empowers organizations to achieve higher levels of performance, maturity, and success. The principles and practices outlined by CMMI touch on various critical aspects of organizational functioning, including process improvement, risk management, quality assurance, and team collaboration.
CMMI's emphasis on measurable performance metrics underscores the importance of data-driven decision-making. By defining clear and SMART key performance indicators, organizations gain the ability to objectively assess their processes and outcomes. This not only facilitates a deeper understanding of current performance but also provides a solid foundation for continuous improvement initiatives.
In essence, CMMI provides organizations with a roadmap for achieving maturity in their processes, fostering a culture of excellence, adaptability, and continuous growth. As organizations embrace and implement the principles of CMMI, they position themselves to navigate complexities, optimize performance, and thrive in an ever-evolving business landscape.
Read More
Implementing the Capability Maturity Model Integration (CMMI) in your organization can bring about a myriad of benefits, enhancing its overall efficiency and competitiveness in today's dynamic business landscape. CMMI serves as a comprehensive framework designed to elevate and optimize an organization's processes, thereby ensuring higher levels of performance, quality, and productivity.
One of the primary advantages of implementing CMMI lies in its ability to provide a structured approach to process improvement. By adopting CMMI practices, organizations can systematically identify, evaluate, and refine their existing processes. This structured methodology not only streamlines operations but also fosters a culture of continuous improvement, ensuring that the organization remains adaptable and responsive to evolving market demands.
CMMI is not merely a tool for process improvement; it also plays a pivotal role in risk management. By identifying and addressing potential risks at early stages, organizations can proactively mitigate challenges that may arise during project execution. This risk mitigation approach not only safeguards project timelines and budgets but also contributes to a more resilient and sustainable business model.
In addition to these operational advantages, implementing CMMI can also enhance communication and collaboration within an organization. The framework encourages cross-functional teams to work cohesively towards common objectives, fostering a collaborative culture that promotes knowledge sharing and innovation. This collaborative mindset is crucial in today's interconnected business environment, where agility and adaptability are key to success.
The benefits of implementing CMMI in an organization are multi-faceted, ranging from improved process efficiency and product quality to enhanced risk management and competitive advantage. As businesses navigate the complexities of a rapidly changing landscape, CMMI stands as a valuable framework that empowers organizations to not only meet current challenges but also to thrive in the future.
Table of contents
-
Enhanced Process Efficiency
-
Quality Assurance and Product Excellence
-
Risk Mitigation Strategies
-
Standardization of Best Practices
-
Collaborative Team Culture
-
Strategic Alignment and Competitive Edge
-
Continuous Improvement Mindset
-
Resource Optimization and Cost Management
-
Employee Development and Engagement
-
Measurable Performance Metrics
-
Conclusion
Enhanced Process Efficiency
Enhanced process efficiency is a key benefit of implementing the Capability Maturity Model Integration (CMMI) in an organization. This aspect revolves around the systematic improvement and optimization of existing processes, leading to increased effectiveness and streamlined workflows.
CMMI provides a structured framework for organizations to assess, refine, and standardize their processes across various departments. Through the identification of best practices and the elimination of redundancies or bottlenecks, CMMI helps organizations achieve a higher level of efficiency in their day-to-day operations.
One way CMMI enhances process efficiency is by promoting a clear understanding of roles, responsibilities, and workflows within the organization. By defining and documenting processes, teams can work more cohesively, reducing the likelihood of misunderstandings or delays. This clarity contributes to smoother collaboration and improved overall efficiency.
Furthermore, CMMI encourages organizations to continuously monitor and evaluate their processes. This ongoing assessment allows for the identification of areas for improvement. By addressing inefficiencies and optimizing processes iteratively, organizations can adapt to changing circumstances and maintain a competitive edge in their respective industries.
Enhanced process efficiency, facilitated by CMMI, involves the systematic improvement of organizational processes through clear documentation, continuous monitoring, and the establishment of performance metrics. By embracing this aspect of CMMI, organizations position themselves to operate more smoothly, respond to challenges more effectively, and deliver high-quality products or services with greater consistency.
Quality Assurance and Product Excellence
Quality assurance and product excellence are fundamental outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that not only ensures the consistency of processes but also places a strong emphasis on delivering high-quality products and services.
CMMI encourages organizations to adopt rigorous quality assurance practices throughout the product or service development lifecycle. This involves defining clear quality standards, conducting thorough reviews, and implementing robust testing procedures. By adhering to these practices, organizations can identify and rectify defects early in the process, preventing issues from escalating and ultimately ensuring the delivery of superior products or services.
One of the ways CMMI contributes to product excellence is through its focus on continuous improvement. The model prompts organizations to regularly assess their processes and make necessary adjustments to enhance efficiency and quality. This iterative approach ensures that products and services evolve over time, meeting or exceeding customer expectations.
CMMI's impact on quality assurance and product excellence is evident through its emphasis on rigorous testing, continuous improvement, customer-centric practices, and the establishment of measurable quality metrics. By integrating these principles into their processes, organizations can consistently produce high-quality products, build customer trust, and gain a competitive advantage in the marketplace.
Risk Mitigation Strategies
Risk mitigation strategies are essential components of effective project and organizational management, and the implementation of the Capability Maturity Model Integration (CMMI) plays a pivotal role in shaping these strategies. One key aspect of risk mitigation within the CMMI framework is the emphasis on early identification. By encouraging organizations to identify risks at the outset of a project or process, CMMI enables teams to assess potential challenges before they escalate. This proactive approach sets the stage for comprehensive risk management throughout the project lifecycle.
CMMI goes beyond qualitative assessments by promoting quantitative risk analysis techniques. Assigning numerical values to risks and their potential impacts allows organizations to prioritize and address the most critical issues. This data-driven approach ensures that resources are allocated efficiently, focusing on mitigating risks that pose the greatest threat to project success.
Effective communication is highlighted within CMMI's risk mitigation strategies. Transparent and open communication about identified risks ensures that relevant stakeholders are informed and can contribute to mitigation efforts. This inclusive communication approach fosters a sense of shared responsibility and promotes a collective effort in addressing and overcoming challenges.
Finally, CMMI promotes a culture of continuous improvement, extending to the organization's risk management processes. Through regular assessments and feedback loops, organizations refine their risk management approaches. This commitment to ongoing improvement ensures that risk mitigation strategies evolve and remain effective in the face of changing circumstances, contributing to overall organizational resilience. In essence, CMMI's risk mitigation strategies provide a comprehensive and adaptable framework for organizations to navigate challenges successfully and enhance project and organizational outcomes.
Standardization of Best Practices
The standardization of best practices is a key benefit derived from implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that emphasizes the identification, documentation, and adherence to proven methodologies across various business functions. This standardization contributes significantly to the overall efficiency, consistency, and quality of organizational processes.
CMMI guides organizations in defining and documenting their best practices, ensuring a clear understanding of established methods and procedures. This documentation serves as a valuable resource for employees, providing a reference point for how tasks and processes should be executed. Standardizing best practices in this manner fosters a shared understanding and promotes consistency across teams, reducing the likelihood of errors or variations in execution.
The standardization of best practices facilitated by CMMI is a cornerstone of organizational excellence. It provides a systematic approach to defining, documenting, and implementing proven methodologies, fostering consistency, efficiency, and quality across the organization. This standardized foundation not only enhances day-to-day operations but also establishes a framework for continuous improvement and organizational resilience.
Collaborative Team Culture
Collaborative team culture is a critical aspect of a thriving and high-performing organization. When teams work together seamlessly and share a common purpose, it not only enhances the quality of work but also contributes to a positive and engaging work environment. In a collaborative team culture, individuals come together, leveraging their diverse skills and experiences to achieve shared goals.
Effective communication lies at the heart of collaborative team culture. It's about more than just conveying information; it's about creating an environment where team members feel comfortable expressing ideas, asking questions, and providing feedback. A culture that values open communication fosters transparency and ensures that everyone is on the same page, reducing the likelihood of misunderstandings and promoting a sense of unity.
Cross-functional collaboration is a key element of collaborative team culture. When individuals from different departments or disciplines collaborate, it brings a richness of perspectives to problem-solving and decision-making. This interdisciplinary approach often leads to innovative solutions that may not have been possible within the confines of a single function. Cross-functional collaboration also breaks down silos, promoting a more holistic understanding of the organization's objectives.
Continuous improvement is a core principle of collaborative team culture. Teams that embrace a mindset of ongoing learning and adaptation are better equipped to navigate challenges and capitalize on opportunities. Regular reflections on successes and setbacks, coupled with a commitment to refining processes, contribute to a culture of growth and development.
In essence, a collaborative team culture is a catalyst for organizational success. It builds a foundation of trust, encourages innovation, and empowers individuals to contribute their best efforts toward shared objectives. As organizations embrace and cultivate collaborative team cultures, they position themselves for sustained excellence and adaptability in a dynamic and ever-evolving landscape.
Strategic Alignment and Competitive Edge
Strategic alignment and gaining a competitive edge are two significant outcomes of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that aligns the organization's processes with its strategic objectives, fostering a cohesive approach that enhances competitiveness in the marketplace.
CMMI emphasizes strategic alignment by encouraging organizations to integrate their processes with overarching business goals. This alignment ensures that every process and activity within the organization contributes directly to the strategic objectives. As a result, teams work cohesively towards common goals, minimizing the risk of disjointed efforts and optimizing resources for maximum impact.
CMMI's focus on continuous improvement contributes to sustaining a competitive edge over time. The framework encourages organizations to regularly reassess their processes, incorporating lessons learned and adapting to evolving market conditions. This commitment to ongoing improvement ensures that the organization remains dynamic and responsive, staying ahead of competitors who may be slower to adapt.
Strategic alignment also plays a crucial role in decision-making. When processes are aligned with strategic objectives, decision-makers have a clear understanding of how choices impact overall goals. This clarity reduces the likelihood of decisions that may deviate from the strategic path and ensures that resources are allocated in ways that maximize value.
CMMI's emphasis on strategic alignment helps organizations create a seamless connection between their processes and overarching business objectives. This alignment enhances organizational agility, fosters a data-driven approach to performance measurement, and ultimately contributes to gaining and sustaining a competitive edge in the marketplace. As organizations implement and mature through the CMMI framework, they are better positioned to navigate the complexities of the business landscape while achieving strategic success.
Continuous Improvement Mindset
The continuous improvement mindset is a fundamental principle embedded in the Capability Maturity Model Integration (CMMI) and serves as a guiding philosophy for organizations seeking to enhance their processes and overall performance. CMMI encourages a culture where the pursuit of excellence is ongoing, and teams are committed to refining their practices incrementally over time.
CMMI's continuous improvement mindset involves the systematic identification and implementation of enhancements. Organizations are encouraged to gather data, feedback, and lessons learned from ongoing projects. This information is then analyzed to identify patterns and trends, providing insights that inform strategic decisions for improvement. The focus is not only on fixing immediate issues but on creating a foundation for sustained and long-term advancement.
CMMI's commitment to continuous improvement extends beyond individual projects to encompass the entire organization. It advocates for the establishment of metrics and key performance indicators (KPIs) that provide quantifiable insights into process effectiveness. Regular reviews of these metrics enable organizations to track progress, measure success, and identify areas for further enhancement.
The continuous improvement mindset advocated by CMMI is a cornerstone of organizational success. It instills a culture of reflection, learning, and proactive refinement. By embracing this mindset, organizations position themselves to not only address current challenges but also to navigate future uncertainties with resilience and agility. Continuous improvement becomes a journey, ingrained in the organizational DNA, driving sustained excellence and innovation.
Resource Optimization and Cost Management
Resource optimization and cost management are integral components of implementing the Capability Maturity Model Integration (CMMI) in an organization. CMMI provides a structured framework that guides organizations in efficiently managing their resources and controlling costs, contributing to improved overall performance and sustainability.
CMMI emphasizes the importance of optimizing resources by aligning them with organizational objectives. This involves a systematic evaluation of available human, financial, and technological resources and ensuring that they are strategically allocated to projects and processes. By optimizing resource utilization, organizations can enhance productivity, reduce waste, and achieve better outcomes without unnecessary expenditures.
Cost management, within the context of CMMI, involves controlling and optimizing expenses throughout the project lifecycle. This includes not only direct project costs but also indirect costs associated with supporting processes. CMMI encourages organizations to establish clear cost management practices, such as budgeting, monitoring expenditures, and implementing cost-saving measures.
CMMI promotes a proactive approach to resource optimization by emphasizing risk management. By identifying potential risks early in the project or process, organizations can develop contingency plans to address resource-related challenges. This proactive risk management contributes to avoiding cost overruns and disruptions, enhancing the organization's ability to stay within budgetary constraints.
Resource optimization and cost management, as guided by CMMI, are essential for organizations aiming to achieve efficiency, control expenses, and enhance overall performance. The framework's emphasis on quantitative metrics, risk management, standardization of best practices, and continuous improvement contributes to a systematic and strategic approach to resource utilization and cost control. By implementing these principles, organizations can navigate resource challenges effectively, control costs, and position themselves for sustained success in a competitive business environment.
Employee Development and Engagement
Employee development and engagement, as guided by the Capability Maturity Model Integration (CMMI), encompasses various strategic initiatives aimed at fostering a skilled and motivated workforce. CMMI emphasizes the establishment of structured professional development programs, ensuring that employees continuously enhance their skills and stay abreast of industry trends. This commitment to ongoing learning contributes to the organization's adaptability and the individual growth of its employees.
CMMI also advocates for a culture of knowledge sharing and collaboration. Organizations are encouraged to create platforms for employees to share their expertise, fostering a collaborative environment where collective learning is prioritized. This collaborative culture not only enhances employee development but also strengthens the overall knowledge base within the organization.
Recognition and rewards play a pivotal role in employee engagement within CMMI. By establishing systems that acknowledge and reward employees for their contributions, organizations boost morale and reinforce a positive and engaged workforce. This recognition creates a sense of value and appreciation among employees, strengthening their commitment to the organization's success.
Employee involvement in decision-making processes is another key principle of CMMI's approach to engagement. Seeking input from employees at various levels fosters a participatory environment where individuals feel their voices are heard. This inclusion not only improves the quality of decisions but also instills a sense of ownership and commitment among employees.
Measurable Performance Metrics
Implementing measurable performance metrics is a key component of the Capability Maturity Model Integration (CMMI) framework. CMMI emphasizes the importance of quantifiable indicators to assess and improve various aspects of an organization's processes. Measurable performance metrics provide valuable insights into efficiency, effectiveness, and overall success, guiding data-driven decision-making and continuous improvement efforts.
CMMI encourages organizations to define key performance indicators (KPIs) that align with their strategic objectives. These metrics should be specific, measurable, achievable, relevant, and time-bound (SMART), ensuring clarity in measurement and facilitating accurate assessments of performance. Examples of measurable performance metrics may include project completion time, defect rates, customer satisfaction scores, and adherence to schedule and budget.
Measurable performance metrics, as advocated by CMMI, provide a structured and data-driven approach to evaluating organizational processes. By defining clear, SMART indicators, establishing baselines, incorporating both quantitative and qualitative measures, and conducting regular reviews, organizations can gain valuable insights into their performance. These metrics not only guide decision-making but also support a culture of continuous improvement, fostering organizational maturity and resilience in a competitive landscape.
Conclusion
In conclusion, the Capability Maturity Model Integration (CMMI) serves as a comprehensive and structured framework that empowers organizations to achieve higher levels of performance, maturity, and success. The principles and practices outlined by CMMI touch on various critical aspects of organizational functioning, including process improvement, risk management, quality assurance, and team collaboration.
CMMI's emphasis on measurable performance metrics underscores the importance of data-driven decision-making. By defining clear and SMART key performance indicators, organizations gain the ability to objectively assess their processes and outcomes. This not only facilitates a deeper understanding of current performance but also provides a solid foundation for continuous improvement initiatives.
In essence, CMMI provides organizations with a roadmap for achieving maturity in their processes, fostering a culture of excellence, adaptability, and continuous growth. As organizations embrace and implement the principles of CMMI, they position themselves to navigate complexities, optimize performance, and thrive in an ever-evolving business landscape.
Machine Learning Algorithms Demystified
"Machine Learning Algorithms Demystified" is an insightful journey into the intricate world of machine learning, where complex algorithms are unraveled and explained with clarity. In this enlightening exploration, readers are guided through the fundamental concepts and principles that underpin various machine learning algorithms. The book serves as a beacon for both beginners and seasoned enthusiasts, demystifying the intricate mechanisms that empower machines to learn from data and make intelligent decisions.
This comprehensive guide begins by establishing a strong foundation in the core concepts of machine learning, providing readers with a solid understanding of key terminologies and principles. It then delves into a diverse array of machine learning algorithms, ranging from the foundational supervised learning methods to advanced unsupervised and reinforcement learning techniques. The narrative is enriched with real-world examples and case studies, making abstract concepts tangible and fostering a deeper comprehension of the algorithms' applications across diverse domains.
Whether you're a curious novice seeking an introduction to machine learning or a seasoned professional aiming to deepen your understanding, this book promises to be an invaluable resource. With its accessible language, illustrative examples, and comprehensive coverage, "Machine Learning Algorithms Demystified" paves the way for a meaningful exploration of the algorithms driving the future of intelligent systems.
Table of contents
-
Foundations of Machine Learning
-
Linear Models and Regression Analysis
-
Decision Trees and Random Forests
-
Support Vector Machines (SVM)
-
Clustering Techniques
-
Neural Networks and Deep Learning Architectures
-
Gradient Boosting and XGBoost
-
Reinforcement Learning Essentials
-
Time Series Analysis and Forecasting
-
Interpretable Machine Learning
-
Conclusion
Foundations of Machine Learning
The foundations of machine learning are rooted in the fundamental principles that define this transformative field. At its core, machine learning represents a paradigm shift from traditional programming, where computers are not explicitly programmed to perform a task, but rather learn from data and experiences. This shift introduces a dynamic approach, enabling machines to improve their performance over time as they encounter more information.
One of the foundational distinctions in machine learning lies in its types: supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training models on labeled datasets, where the algorithm learns to make predictions or classifications. Unsupervised learning, on the other hand, deals with unlabeled data, seeking patterns and structures within the information. Reinforcement learning revolves around agents interacting with an environment, learning optimal actions through a system of rewards and penalties.
Overcoming challenges like overfitting and underfitting involves the application of techniques like cross-validation, which ensures a more robust estimation of model capabilities. Feature scaling and normalization contribute to model stability, enhancing convergence during the training process. Ethical considerations, including bias mitigation, transparency, and accountability, are integral components of the foundations of machine learning, emphasizing the importance of responsible AI practices in the development and deployment of models. These foundational principles provide a solid base for further exploration into the diverse and dynamic world of machine learning algorithms.
Linear Models and Regression Analysis
Linear models and regression analysis constitute a cornerstone in the realm of machine learning, offering a powerful and interpretable approach to understand and predict relationships within data. At its essence, linear regression is a foundational technique used for modeling the relationship between a dependent variable and one or more independent variables.
Linear regression finds widespread application in scenarios where understanding the linear relationship between variables is essential. For instance, it is frequently employed in economics to model the impact of independent variables on a dependent variable, such as predicting housing prices based on features like square footage and location.
While linear regression assumes a linear relationship between variables, its simplicity and interpretability make it an invaluable tool. However, it's essential to recognize its limitations, particularly when dealing with complex, nonlinear relationships. In such cases, more advanced models, including polynomial regression or other nonlinear models, may be warranted.
In summary, linear models and regression analysis provide a solid foundation for understanding and predicting relationships within datasets. From predicting stock prices to analyzing marketing trends, the versatility of linear regression makes it a fundamental tool in the machine learning toolkit, offering a clear and intuitive way to model and interpret data patterns.
Decision Trees and Random Forests
Decision trees and random forests represent powerful and versatile tools in machine learning, particularly in the domain of predictive modeling and classification tasks. These algorithms excel at capturing complex decision-making processes and are highly interpretable, making them valuable assets in various applications.
Decision Trees:At the core of decision trees is a tree-like model where each internal node represents a decision based on the value of a particular feature, each branch represents the outcome of that decision, and each leaf node represents the final prediction. The construction of a decision tree involves recursively partitioning the data based on the most informative features, resulting in a tree structure that can be easily visualized and interpreted.
Decision trees are capable of handling both categorical and numerical data, making them flexible for a wide range of tasks. They are particularly adept at capturing non-linear relationships and interactions within the data. However, decision trees are prone to overfitting, capturing noise in the training data, which can be addressed through techniques like pruning.
Random Forests:Random forests extend the power of decision trees by combining multiple trees into an ensemble model. Instead of relying on the decision of a single tree, random forests aggregate predictions from numerous decision trees, providing a more robust and accurate outcome. Each tree in the forest is trained on a random subset of the data and may consider only a random subset of features at each decision point, introducing diversity and mitigating overfitting.
In summary, decision trees and random forests offer a dynamic duo in machine learning, where decision trees provide transparency and interpretability, and random forests enhance predictive accuracy and robustness. Their versatility and effectiveness make them go-to choices for a myriad of applications, striking a balance between complexity and interpretability in the pursuit of accurate and reliable predictions.
Support Vector Machines (SVM)
Support Vector Machines (SVM) represent a powerful class of supervised learning algorithms with applications in both classification and regression tasks. Developed by Vladimir Vapnik and his colleagues in the 1990s, SVM has garnered widespread popularity due to its effectiveness in handling complex data structures and its solid theoretical foundation.
At the heart of SVM is the concept of finding an optimal hyperplane that maximally separates data points of different classes in the feature space. In a two-dimensional space, this hyperplane is a line, while in higher dimensions, it becomes a hyperplane. The uniqueness of SVM lies in its focus on the margin, the distance between the hyperplane and the nearest data points of each class. The goal is to maximize this margin, leading to a robust and generalizable model.
SVM's versatility in handling non-linear relationships is facilitated by the use of kernels. Kernels transform the original feature space into a higher-dimensional space, enabling SVM to find complex decision boundaries. Commonly used kernels include the linear kernel for linearly separable data, the polynomial kernel for capturing polynomial relationships, and the radial basis function (RBF) kernel for handling intricate, non-linear patterns.
In scenarios where perfect separation is not feasible, SVM introduces the concept of a soft margin. The soft margin allows for a controlled degree of misclassification, providing flexibility in handling real-world datasets with inherent noise or overlapping classes. The trade-off between maximizing the margin and minimizing misclassification errors is governed by a regularization parameter, denoted as C.
Read More
"Machine Learning Algorithms Demystified" is an insightful journey into the intricate world of machine learning, where complex algorithms are unraveled and explained with clarity. In this enlightening exploration, readers are guided through the fundamental concepts and principles that underpin various machine learning algorithms. The book serves as a beacon for both beginners and seasoned enthusiasts, demystifying the intricate mechanisms that empower machines to learn from data and make intelligent decisions.
This comprehensive guide begins by establishing a strong foundation in the core concepts of machine learning, providing readers with a solid understanding of key terminologies and principles. It then delves into a diverse array of machine learning algorithms, ranging from the foundational supervised learning methods to advanced unsupervised and reinforcement learning techniques. The narrative is enriched with real-world examples and case studies, making abstract concepts tangible and fostering a deeper comprehension of the algorithms' applications across diverse domains.
Whether you're a curious novice seeking an introduction to machine learning or a seasoned professional aiming to deepen your understanding, this book promises to be an invaluable resource. With its accessible language, illustrative examples, and comprehensive coverage, "Machine Learning Algorithms Demystified" paves the way for a meaningful exploration of the algorithms driving the future of intelligent systems.
Table of contents
-
Foundations of Machine Learning
-
Linear Models and Regression Analysis
-
Decision Trees and Random Forests
-
Support Vector Machines (SVM)
-
Clustering Techniques
-
Neural Networks and Deep Learning Architectures
-
Gradient Boosting and XGBoost
-
Reinforcement Learning Essentials
-
Time Series Analysis and Forecasting
-
Interpretable Machine Learning
-
Conclusion
Foundations of Machine Learning
The foundations of machine learning are rooted in the fundamental principles that define this transformative field. At its core, machine learning represents a paradigm shift from traditional programming, where computers are not explicitly programmed to perform a task, but rather learn from data and experiences. This shift introduces a dynamic approach, enabling machines to improve their performance over time as they encounter more information.
One of the foundational distinctions in machine learning lies in its types: supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training models on labeled datasets, where the algorithm learns to make predictions or classifications. Unsupervised learning, on the other hand, deals with unlabeled data, seeking patterns and structures within the information. Reinforcement learning revolves around agents interacting with an environment, learning optimal actions through a system of rewards and penalties.
Overcoming challenges like overfitting and underfitting involves the application of techniques like cross-validation, which ensures a more robust estimation of model capabilities. Feature scaling and normalization contribute to model stability, enhancing convergence during the training process. Ethical considerations, including bias mitigation, transparency, and accountability, are integral components of the foundations of machine learning, emphasizing the importance of responsible AI practices in the development and deployment of models. These foundational principles provide a solid base for further exploration into the diverse and dynamic world of machine learning algorithms.
Linear Models and Regression Analysis
Linear models and regression analysis constitute a cornerstone in the realm of machine learning, offering a powerful and interpretable approach to understand and predict relationships within data. At its essence, linear regression is a foundational technique used for modeling the relationship between a dependent variable and one or more independent variables.
Linear regression finds widespread application in scenarios where understanding the linear relationship between variables is essential. For instance, it is frequently employed in economics to model the impact of independent variables on a dependent variable, such as predicting housing prices based on features like square footage and location.
While linear regression assumes a linear relationship between variables, its simplicity and interpretability make it an invaluable tool. However, it's essential to recognize its limitations, particularly when dealing with complex, nonlinear relationships. In such cases, more advanced models, including polynomial regression or other nonlinear models, may be warranted.
In summary, linear models and regression analysis provide a solid foundation for understanding and predicting relationships within datasets. From predicting stock prices to analyzing marketing trends, the versatility of linear regression makes it a fundamental tool in the machine learning toolkit, offering a clear and intuitive way to model and interpret data patterns.
Decision Trees and Random Forests
Decision trees and random forests represent powerful and versatile tools in machine learning, particularly in the domain of predictive modeling and classification tasks. These algorithms excel at capturing complex decision-making processes and are highly interpretable, making them valuable assets in various applications.
Decision Trees:At the core of decision trees is a tree-like model where each internal node represents a decision based on the value of a particular feature, each branch represents the outcome of that decision, and each leaf node represents the final prediction. The construction of a decision tree involves recursively partitioning the data based on the most informative features, resulting in a tree structure that can be easily visualized and interpreted.
Decision trees are capable of handling both categorical and numerical data, making them flexible for a wide range of tasks. They are particularly adept at capturing non-linear relationships and interactions within the data. However, decision trees are prone to overfitting, capturing noise in the training data, which can be addressed through techniques like pruning.
Random Forests:Random forests extend the power of decision trees by combining multiple trees into an ensemble model. Instead of relying on the decision of a single tree, random forests aggregate predictions from numerous decision trees, providing a more robust and accurate outcome. Each tree in the forest is trained on a random subset of the data and may consider only a random subset of features at each decision point, introducing diversity and mitigating overfitting.
In summary, decision trees and random forests offer a dynamic duo in machine learning, where decision trees provide transparency and interpretability, and random forests enhance predictive accuracy and robustness. Their versatility and effectiveness make them go-to choices for a myriad of applications, striking a balance between complexity and interpretability in the pursuit of accurate and reliable predictions.
Support Vector Machines (SVM)
Support Vector Machines (SVM) represent a powerful class of supervised learning algorithms with applications in both classification and regression tasks. Developed by Vladimir Vapnik and his colleagues in the 1990s, SVM has garnered widespread popularity due to its effectiveness in handling complex data structures and its solid theoretical foundation.
At the heart of SVM is the concept of finding an optimal hyperplane that maximally separates data points of different classes in the feature space. In a two-dimensional space, this hyperplane is a line, while in higher dimensions, it becomes a hyperplane. The uniqueness of SVM lies in its focus on the margin, the distance between the hyperplane and the nearest data points of each class. The goal is to maximize this margin, leading to a robust and generalizable model.
SVM's versatility in handling non-linear relationships is facilitated by the use of kernels. Kernels transform the original feature space into a higher-dimensional space, enabling SVM to find complex decision boundaries. Commonly used kernels include the linear kernel for linearly separable data, the polynomial kernel for capturing polynomial relationships, and the radial basis function (RBF) kernel for handling intricate, non-linear patterns.
In scenarios where perfect separation is not feasible, SVM introduces the concept of a soft margin. The soft margin allows for a controlled degree of misclassification, providing flexibility in handling real-world datasets with inherent noise or overlapping classes. The trade-off between maximizing the margin and minimizing misclassification errors is governed by a regularization parameter, denoted as C.
Introduction to Six Sigma Yellow Belt Certification
Six Sigma Yellow Belt certification is a fundamental level of certification within the Six Sigma methodology, a data-driven approach to process improvement aimed at reducing defects and variations in a process. It is an excellent starting point for individuals who want to enhance their problem-solving skills, contribute to process improvement efforts, and play a valuable role in organizational quality management.
Six Sigma Yellow Belt Certification is an entry-level certification that can open doors to the world of process improvement and quality management. It empowers individuals to apply data-driven methods to solve problems, make processes more efficient, and ultimately contribute to the success of their organization. It serves as a foundation for those who may choose to pursue higher levels of Six Sigma certification, such as Green Belt or Black Belt.
Table of contents
-
Understanding Six Sigma
-
Role of Yellow Belts in Six Sigma
-
Why Pursue a Yellow Belt Certification
-
Certification Requirements
-
Yellow Belt Training and Curriculum
-
Industry Applications
-
Yellow Belt vs. Other Six Sigma Belts
-
Real-World Examples
-
Preparing for the Yellow Belt Exam
-
Career Advancement and Opportunities
-
Conclusion
Understanding Six Sigma
Six Sigma is a systematic and data-driven methodology for process improvement. Originally developed by Motorola in the 1980s, it has become widely adopted by organizations in various industries to enhance product and service quality, reduce defects, and streamline processes. The term "Six Sigma" refers to a statistical measure of process variation, and the goal of Six Sigma is to minimize process variation to a level where only 3.4 defects per million opportunities occur, thereby achieving near-perfect performance.
Here are the key components and concepts that help in understanding Six Sigma:
DMAIC Methodology: Six Sigma follows a structured problem-solving methodology known as DMAIC, which stands for:
Process Variation: Central to Six Sigma is the concept of process variation. Processes naturally have variations, but Six Sigma seeks to reduce and control these variations to ensure consistency and quality.
Data-Driven Approach: Six Sigma heavily relies on data analysis to make informed decisions. Statistical tools and methods are used to collect, measure, and analyze data to understand the current state of processes and identify areas for improvement.
Roles and Belts: Within a Six Sigma program, individuals are often assigned different roles based on their level of expertise. These roles include Yellow Belts, Green Belts, and Black Belts, each with increasing levels of knowledge and responsibility.
Customer Focus: Six Sigma places a strong emphasis on understanding and meeting customer requirements. It seeks to align process improvement efforts with what customers value.
Continuous Improvement: Six Sigma promotes a culture of continuous improvement. It's not a one-time project but an ongoing philosophy that strives to make incremental and sustainable changes to processes.
In summary, Six Sigma is a disciplined and data-driven approach to process improvement and problem-solving. It seeks to reduce process variation, improve quality, and ultimately enhance an organization's competitiveness and customer satisfaction. Understanding and implementing Six Sigma principles can lead to more efficient and effective processes across a wide range of industries.
Role of Yellow Belts in Six Sigma
Six Sigma Yellow Belts play a vital role in the Six Sigma methodology, supporting process improvement initiatives within an organization. While they may not have the same level of expertise and responsibility as Green Belts or Black Belts, Yellow Belts are essential team members who contribute to the success of Six Sigma projects. Here's an overview of their role:
Data Collection: Yellow Belts are responsible for gathering and organizing data related to the process under examination. They ensure that accurate and relevant data is collected to support the project's goals.
Process Mapping: They help create process maps or flowcharts to document the current process. This visual representation aids in identifying bottlenecks, redundancies, and areas for potential improvement.
Participation in Improvement Projects: Yellow Belts actively participate in process improvement projects led by Green Belts or Black Belts. They collaborate with team members to implement changes and solutions.
Problem-Solving: They assist in problem-solving activities by contributing their insights and observations. Yellow Belts may be asked to brainstorm potential causes of issues and help investigate root causes.
Basic Analysis: Yellow Belts use basic Six Sigma tools and techniques to analyze data and identify trends or patterns. They may create histograms, Pareto charts, and other simple visual aids to understand data.
In summary, Yellow Belts are entry-level Six Sigma practitioners who contribute to process improvement initiatives by collecting data, participating in projects, and supporting Green Belts and Black Belts. They are valuable team members in the pursuit of quality and efficiency improvements within an organization. While they may not lead projects, their contributions are essential for successful Six Sigma implementations.
Why Pursue a Yellow Belt Certification
Pursuing a Yellow Belt certification in Six Sigma can offer individuals and organizations several significant benefits. Here are some compelling reasons why you might consider pursuing a Yellow Belt certification:
Basic Understanding of Six Sigma: Yellow Belt training provides a foundational understanding of the Six Sigma methodology. It introduces you to the core principles, concepts, and tools used in Six Sigma process improvement projects.
Enhanced Problem-Solving Skills: Yellow Belt certification equips you with problem-solving skills that can be applied to various situations, both in your professional and personal life. You'll learn to analyze data and make informed decisions.
Career Advancement: Earning a Yellow Belt certification can enhance your resume and open doors to new career opportunities. Many employers value Six Sigma certifications and seek candidates who can contribute to process improvement efforts.
Contribution to Quality Improvement: Yellow Belts play a critical role in improving product or service quality and customer satisfaction. By identifying and addressing process issues, you contribute to your organization's success.
Organizational Impact: By addressing process issues and enhancing efficiency, Yellow Belts can positively impact their organization's performance and competitiveness in the market.
Continuous Learning: Six Sigma is a continuous improvement philosophy. Pursuing a Yellow Belt certification demonstrates your commitment to learning and evolving as a professional.
Pursuing a Yellow Belt certification in Six Sigma is a valuable investment in your professional development. It equips you with problem-solving skills, enhances your understanding of quality management, and can lead to career opportunities while simultaneously benefitting your organization through process improvement.
Certification Requirements
Certification requirements for a Six Sigma Yellow Belt may vary depending on the certifying body and the organization. However, there are common elements that are typically involved in obtaining a Yellow Belt certification. Below are the general certification requirements:
Training: Most Yellow Belt certifications require candidates to complete a specified amount of training. This training can be provided through in-person workshops, online courses, or a combination of both. Training may cover Six Sigma principles, the DMAIC methodology, and essential tools and techniques.
Coursework: Candidates are often required to complete coursework related to Six Sigma Yellow Belt concepts. This coursework may include reading materials, lectures, quizzes, and assignments.
Examination: After completing the training and coursework, candidates must pass a certification exam. The exam assesses their knowledge of Six Sigma principles, DMAIC, and problem-solving techniques. The passing score may vary depending on the certifying body but is typically set at a certain percentage.
Certification Fee: There is usually a fee associated with obtaining a Yellow Belt certification. This fee covers the cost of training, materials, examination, and certification processing.
It's important to note that different organizations and certifying bodies may have variations in their certification requirements, so it's essential to check the specific requirements of the program you are interested in. Additionally, the level of rigor and the depth of content covered in Yellow Belt programs can vary, so it's a good idea to select a program that aligns with your career goals and the depth of knowledge you wish to gain.
Yellow Belt Training and Curriculum
Yellow Belt training in Six Sigma is designed to provide individuals with a foundational understanding of the Six Sigma methodology and equip them with essential problem-solving and process improvement skills. The training typically covers a range of topics and concepts related to quality management. Below is an overview of the common elements included in Yellow Belt training and curriculum:
Introduction to Six Sigma:
Understanding the origins and evolution of Six Sigma.
The importance of quality management and its impact on organizations.
Six Sigma Principles:
Explaining the key principles and philosophies of Six Sigma.
The focus on data-driven decision-making and minimizing process variation.
Process Improvement Projects:
Understanding the various components of a Six Sigma project.
Identifying project selection criteria and defining project scope.
Project Team Dynamics:
Effective teamwork and collaboration within a Six Sigma project team.
Communication and problem-solving skills for team members.
Case Studies and Practical Examples:
Real-world examples of successful Six Sigma projects.
Analyzing how Six Sigma principles were applied to solve specific problems and achieve results.
Certification Preparation:
Guidance on preparing for the Yellow Belt certification exam, including sample questions and practice exams.
Review of key concepts covered in the training.
Practical Application (optional):
Hands-on exercises or a small-scale Six Sigma project may be included as part of the training to allow participants to apply their knowledge in a real-world context.
Yellow Belt training can be delivered through in-person workshops, online courses, or a combination of both, depending on the program and the certifying body. The curriculum is typically designed to be accessible to individuals with various levels of experience and backgrounds, making it an excellent starting point for those looking to gain proficiency in Six Sigma principles and methodologies.
Industry Applications
Six Sigma methodologies, including Yellow Belt principles, have been widely adopted across various industries due to their effectiveness in improving processes, reducing defects, and enhancing overall quality. Here are some industry-specific applications of Six Sigma:
Manufacturing:
In manufacturing, Six Sigma helps reduce defects and variations in the production process. It's used to improve product quality, increase efficiency, and minimize waste.
Applications range from automotive manufacturing to electronics, aerospace, and consumer goods production.
Healthcare:
Six Sigma has been instrumental in improving patient care and safety. Hospitals and healthcare providers use it to reduce medical errors, decrease patient waiting times, and enhance administrative processes.
Applications include optimizing emergency room operations, reducing hospital-acquired infections, and streamlining billing processes.
Education:
Educational institutions use Six Sigma to enhance administrative processes, improve curriculum delivery, and optimize resource allocation.
Applications range from streamlining student enrollment processes to reducing dropout rates.
Government and Public Services:
Government agencies apply Six Sigma to improve public services, streamline administrative processes, and reduce costs.
Applications include optimizing the issuance of permits and licenses, enhancing public transportation, and improving emergency response times.
Energy and Utilities:
Energy companies use Six Sigma to optimize power generation and distribution, reduce energy waste, and enhance safety procedures.
Applications include improving equipment maintenance, reducing energy consumption, and ensuring regulatory compliance.
These are just a few examples of the many industries where Six Sigma methodologies, including those implemented by Yellow Belts, have been effectively applied to drive process improvements, reduce costs, and enhance quality. The versatility of Six Sigma makes it a valuable tool in virtually any sector seeking to improve its operations.
Yellow Belt vs. Other Six Sigma Belts
Six Sigma certifications come in various levels, including Yellow Belt, Green Belt, Black Belt, and Master Black Belt. Each of these belts represents a different level of expertise and responsibility within the Six Sigma framework. Here's a comparison of Yellow Belt with other Six Sigma belts:
Yellow Belt:
Role: Yellow Belts are typically team members or support staff in Six Sigma projects. They play a foundational role, assisting Green Belts, Black Belts, and Master Black Belts in process improvement initiatives.
Responsibilities: They contribute to projects by assisting with data collection, process mapping, basic analysis, and problem-solving tasks. Yellow Belts often work on smaller-scale projects or specific aspects of larger projects.
Training: Yellow Belt training provides a basic understanding of Six Sigma principles, the DMAIC methodology, and core tools used in process improvement.
Certification: Earning a Yellow Belt certification requires completing training and passing an exam. It is an entry-level certification.
Green Belt:
Role: Green Belts lead process improvement projects and work under the guidance of Black Belts. They are responsible for project management and data analysis.
Responsibilities: Green Belts are more directly involved in the DMAIC process, including problem identification, root cause analysis, solution implementation, and process control.
Training: Green Belt training is more comprehensive than Yellow Belt training, covering advanced tools and statistical techniques.
Certification: Earning a Green Belt certification involves completing training, demonstrating proficiency through a project, and often passing an exam.
Black Belt:
Role: Black Belts are project leaders and are responsible for overseeing complex Six Sigma projects. They are often involved in multiple projects simultaneously.
Responsibilities: Black Belts are expected to have a deep understanding of Six Sigma tools and techniques. They identify projects, lead teams, and drive significant process improvements.
Training: Black Belt training is extensive, covering advanced statistical analysis, project management, and leadership skills.
Certification: Earning a Black Belt certification involves completing intensive training, leading successful projects, and passing a certification exam.
In summary, the primary differences between the various Six Sigma belts lie in their level of expertise, responsibilities, and the complexity of projects they handle. Yellow Belts are entry-level participants, Green Belts lead specific projects, Black Belts manage complex projects, and Master Black Belts are experts who guide and mentor others. The choice of belt level depends on one's career goals, level of expertise, and the scope of desired involvement in Six Sigma projects.
Real-World Examples
Real-world examples of Six Sigma Yellow Belt projects and their outcomes illustrate the practical applications of this methodology in improving processes and reducing defects. Here are a few examples:
Manufacturing Industry:
Project: A manufacturing company noticed high defect rates in a particular product line. A Yellow Belt team was formed to identify and address the root causes.
Outcome: Through process analysis and the implementation of changes, they reduced defect rates by 30% and increased production efficiency.
Healthcare Industry:
Project: A hospital's emergency department had long patient wait times and overcrowding issues. A Yellow Belt team was tasked with reducing waiting times and improving patient flow.
Outcome: The team implemented new triage processes, improved communication among staff, and streamlined admission procedures, resulting in a 40% reduction in wait times.
IT Services:Project: An IT support department had high call resolution times and frequent escalations. A Yellow Belt team worked on improving support processes.
Outcome: They restructured the support flow, developed a knowledge base, and provided additional training for staff. As a result, call resolution times decreased by 50%, and escalations reduced significantly.
Education:Project: A school district was facing budget constraints and wanted to optimize transportation routes for school buses. A Yellow Belt team was tasked with improving route efficiency.
Outcome: By analyzing bus schedules and optimizing routes, the district saved 15% in transportation costs while maintaining service quality.
These examples demonstrate how Six Sigma Yellow Belts can make meaningful contributions to process improvement across diverse industries. While they may not lead the projects independently, their involvement in problem-solving and data analysis plays a crucial role in achieving positive outcomes. Additionally, these successes showcase the versatility of Six Sigma in addressing a wide range of process-related challenges.
Preparing for the Yellow Belt Exam
Preparing for a Yellow Belt certification exam in Six Sigma involves systematic study, practice, and a clear understanding of the key concepts and tools associated with the methodology. Here's a step-by-step guide to help you prepare for your Yellow Belt exam:
Understand the Exam Format:Start by familiarizing yourself with the structure and format of the Yellow Belt exam. Understand the number of questions, time constraints, and any specific requirements for the exam.
Review Training Materials:Revisit your Yellow Belt training materials, including textbooks, lecture notes, and any online resources provided during your training. Ensure you have a solid grasp of the fundamental concepts, principles, and tools of Six Sigma.
Use Study Guides:Consider using study guides or reference materials designed specifically for Six Sigma Yellow Belt certification. These resources often provide concise summaries of key topics and sample questions.
Self-Assessments:Take self-assessment quizzes and tests to identify your strengths and
Time Management:Develop a study schedule that allows you to allocate sufficient time for each topic. Consistent, organized studying can help you cover all relevant content before the exam.
Mock Exams:Take full-length mock exams under timed conditions to simulate the exam experience. This helps you become comfortable with the format and identify areas that need improvement.
Remember that effective preparation is not just about memorizing facts but understanding the underlying principles and being able to apply them in real-world scenarios. By following these steps and staying committed to your study plan, you'll increase your chances of success in the Yellow Belt certification exam.
Career Advancement and Opportunities
Earning a Six Sigma Yellow Belt certification can lead to several career advancement opportunities and benefits. Here's how this certification can positively impact your career:
Enhanced Problem-Solving Skills: Yellow Belt training equips you with problem-solving skills that are valuable in many industries. This skillset can make you a more effective and efficient employee, contributing to career growth.
Cross-Functional Collaboration: Six Sigma projects often involve cross-functional teams. Collaborating with colleagues from different departments can expand your network and expose you to new career prospects.
Certification Path: Earning a Yellow Belt can serve as a stepping stone to higher-level Six Sigma certifications, such as Green Belt or Black Belt. These advanced certifications open doors to more complex and impactful roles within an organization.
Salary Increase: Many organizations offer salary increases or bonuses for employees who obtain Six Sigma certifications due to the potential cost savings and quality improvements they bring to the organization.
Consulting Opportunities: After gaining experience and expertise as a Yellow Belt, you may consider a career in Six Sigma consulting, where you can help other organizations improve their processes.
In summary, a Six Sigma Yellow Belt certification can provide numerous career advantages, including the potential for promotions, salary increases, and the opportunity to work on impactful projects. It also equips you with valuable problem-solving skills that are relevant in many industries, making you a valuable asset in the job market.
Conclusion
In conclusion, Six Sigma Yellow Belt certification is a valuable step in your professional development journey. It equips you with foundational knowledge and skills in the Six Sigma methodology, problem-solving, and process improvement. Whether you're looking to advance your career within your current organization, transition to a new field, or pursue further Six Sigma certifications, the Yellow Belt is a worthwhile investment.
By understanding the principles of Six Sigma, learning how to use data-driven approaches to solve problems, and actively participating in process improvement projects, you can contribute to your organization's success and enhance your own career prospects. The benefits of Yellow Belt certification are numerous, from increased problem-solving abilities to potential salary enhancements and new career opportunities.
Remember that Yellow Belt certification is just the beginning of your Six Sigma journey. With dedication, continued learning, and the possibility of pursuing higher-level certifications, you can make a significant impact in your organization and in your own career advancement. Whether you're in manufacturing, healthcare, finance, or any other industry, Six Sigma principles can lead to improved quality, efficiency, and competitiveness.
So, as you embark on your Yellow Belt certification journey, embrace the opportunity to learn and grow. Keep in mind that Six Sigma is not just about achieving certification; it's about applying these valuable principles and tools to create meaningful, positive change in the processes and systems that shape our professional world.
Read More
Six Sigma Yellow Belt certification is a fundamental level of certification within the Six Sigma methodology, a data-driven approach to process improvement aimed at reducing defects and variations in a process. It is an excellent starting point for individuals who want to enhance their problem-solving skills, contribute to process improvement efforts, and play a valuable role in organizational quality management.
Six Sigma Yellow Belt Certification is an entry-level certification that can open doors to the world of process improvement and quality management. It empowers individuals to apply data-driven methods to solve problems, make processes more efficient, and ultimately contribute to the success of their organization. It serves as a foundation for those who may choose to pursue higher levels of Six Sigma certification, such as Green Belt or Black Belt.
Table of contents
-
Understanding Six Sigma
-
Role of Yellow Belts in Six Sigma
-
Why Pursue a Yellow Belt Certification
-
Certification Requirements
-
Yellow Belt Training and Curriculum
-
Industry Applications
-
Yellow Belt vs. Other Six Sigma Belts
-
Real-World Examples
-
Preparing for the Yellow Belt Exam
-
Career Advancement and Opportunities
-
Conclusion
Understanding Six Sigma
Six Sigma is a systematic and data-driven methodology for process improvement. Originally developed by Motorola in the 1980s, it has become widely adopted by organizations in various industries to enhance product and service quality, reduce defects, and streamline processes. The term "Six Sigma" refers to a statistical measure of process variation, and the goal of Six Sigma is to minimize process variation to a level where only 3.4 defects per million opportunities occur, thereby achieving near-perfect performance.
Here are the key components and concepts that help in understanding Six Sigma:
DMAIC Methodology: Six Sigma follows a structured problem-solving methodology known as DMAIC, which stands for:
Process Variation: Central to Six Sigma is the concept of process variation. Processes naturally have variations, but Six Sigma seeks to reduce and control these variations to ensure consistency and quality.
Data-Driven Approach: Six Sigma heavily relies on data analysis to make informed decisions. Statistical tools and methods are used to collect, measure, and analyze data to understand the current state of processes and identify areas for improvement.
Roles and Belts: Within a Six Sigma program, individuals are often assigned different roles based on their level of expertise. These roles include Yellow Belts, Green Belts, and Black Belts, each with increasing levels of knowledge and responsibility.
Customer Focus: Six Sigma places a strong emphasis on understanding and meeting customer requirements. It seeks to align process improvement efforts with what customers value.
Continuous Improvement: Six Sigma promotes a culture of continuous improvement. It's not a one-time project but an ongoing philosophy that strives to make incremental and sustainable changes to processes.
In summary, Six Sigma is a disciplined and data-driven approach to process improvement and problem-solving. It seeks to reduce process variation, improve quality, and ultimately enhance an organization's competitiveness and customer satisfaction. Understanding and implementing Six Sigma principles can lead to more efficient and effective processes across a wide range of industries.
Role of Yellow Belts in Six Sigma
Six Sigma Yellow Belts play a vital role in the Six Sigma methodology, supporting process improvement initiatives within an organization. While they may not have the same level of expertise and responsibility as Green Belts or Black Belts, Yellow Belts are essential team members who contribute to the success of Six Sigma projects. Here's an overview of their role:
Data Collection: Yellow Belts are responsible for gathering and organizing data related to the process under examination. They ensure that accurate and relevant data is collected to support the project's goals.
Process Mapping: They help create process maps or flowcharts to document the current process. This visual representation aids in identifying bottlenecks, redundancies, and areas for potential improvement.
Participation in Improvement Projects: Yellow Belts actively participate in process improvement projects led by Green Belts or Black Belts. They collaborate with team members to implement changes and solutions.
Problem-Solving: They assist in problem-solving activities by contributing their insights and observations. Yellow Belts may be asked to brainstorm potential causes of issues and help investigate root causes.
Basic Analysis: Yellow Belts use basic Six Sigma tools and techniques to analyze data and identify trends or patterns. They may create histograms, Pareto charts, and other simple visual aids to understand data.
In summary, Yellow Belts are entry-level Six Sigma practitioners who contribute to process improvement initiatives by collecting data, participating in projects, and supporting Green Belts and Black Belts. They are valuable team members in the pursuit of quality and efficiency improvements within an organization. While they may not lead projects, their contributions are essential for successful Six Sigma implementations.
Why Pursue a Yellow Belt Certification
Pursuing a Yellow Belt certification in Six Sigma can offer individuals and organizations several significant benefits. Here are some compelling reasons why you might consider pursuing a Yellow Belt certification:
Basic Understanding of Six Sigma: Yellow Belt training provides a foundational understanding of the Six Sigma methodology. It introduces you to the core principles, concepts, and tools used in Six Sigma process improvement projects.
Enhanced Problem-Solving Skills: Yellow Belt certification equips you with problem-solving skills that can be applied to various situations, both in your professional and personal life. You'll learn to analyze data and make informed decisions.
Career Advancement: Earning a Yellow Belt certification can enhance your resume and open doors to new career opportunities. Many employers value Six Sigma certifications and seek candidates who can contribute to process improvement efforts.
Contribution to Quality Improvement: Yellow Belts play a critical role in improving product or service quality and customer satisfaction. By identifying and addressing process issues, you contribute to your organization's success.
Organizational Impact: By addressing process issues and enhancing efficiency, Yellow Belts can positively impact their organization's performance and competitiveness in the market.
Continuous Learning: Six Sigma is a continuous improvement philosophy. Pursuing a Yellow Belt certification demonstrates your commitment to learning and evolving as a professional.
Pursuing a Yellow Belt certification in Six Sigma is a valuable investment in your professional development. It equips you with problem-solving skills, enhances your understanding of quality management, and can lead to career opportunities while simultaneously benefitting your organization through process improvement.
Certification Requirements
Certification requirements for a Six Sigma Yellow Belt may vary depending on the certifying body and the organization. However, there are common elements that are typically involved in obtaining a Yellow Belt certification. Below are the general certification requirements:
Training: Most Yellow Belt certifications require candidates to complete a specified amount of training. This training can be provided through in-person workshops, online courses, or a combination of both. Training may cover Six Sigma principles, the DMAIC methodology, and essential tools and techniques.
Coursework: Candidates are often required to complete coursework related to Six Sigma Yellow Belt concepts. This coursework may include reading materials, lectures, quizzes, and assignments.
Examination: After completing the training and coursework, candidates must pass a certification exam. The exam assesses their knowledge of Six Sigma principles, DMAIC, and problem-solving techniques. The passing score may vary depending on the certifying body but is typically set at a certain percentage.
Certification Fee: There is usually a fee associated with obtaining a Yellow Belt certification. This fee covers the cost of training, materials, examination, and certification processing.
It's important to note that different organizations and certifying bodies may have variations in their certification requirements, so it's essential to check the specific requirements of the program you are interested in. Additionally, the level of rigor and the depth of content covered in Yellow Belt programs can vary, so it's a good idea to select a program that aligns with your career goals and the depth of knowledge you wish to gain.
Yellow Belt Training and Curriculum
Yellow Belt training in Six Sigma is designed to provide individuals with a foundational understanding of the Six Sigma methodology and equip them with essential problem-solving and process improvement skills. The training typically covers a range of topics and concepts related to quality management. Below is an overview of the common elements included in Yellow Belt training and curriculum:
Introduction to Six Sigma:
Understanding the origins and evolution of Six Sigma.
The importance of quality management and its impact on organizations.
Six Sigma Principles:
Explaining the key principles and philosophies of Six Sigma.
The focus on data-driven decision-making and minimizing process variation.
Process Improvement Projects:
Understanding the various components of a Six Sigma project.
Identifying project selection criteria and defining project scope.
Project Team Dynamics:
Effective teamwork and collaboration within a Six Sigma project team.
Communication and problem-solving skills for team members.
Case Studies and Practical Examples:
Real-world examples of successful Six Sigma projects.
Analyzing how Six Sigma principles were applied to solve specific problems and achieve results.
Certification Preparation:
Guidance on preparing for the Yellow Belt certification exam, including sample questions and practice exams.
Review of key concepts covered in the training.
Practical Application (optional):
Hands-on exercises or a small-scale Six Sigma project may be included as part of the training to allow participants to apply their knowledge in a real-world context.
Yellow Belt training can be delivered through in-person workshops, online courses, or a combination of both, depending on the program and the certifying body. The curriculum is typically designed to be accessible to individuals with various levels of experience and backgrounds, making it an excellent starting point for those looking to gain proficiency in Six Sigma principles and methodologies.
Industry Applications
Six Sigma methodologies, including Yellow Belt principles, have been widely adopted across various industries due to their effectiveness in improving processes, reducing defects, and enhancing overall quality. Here are some industry-specific applications of Six Sigma:
Manufacturing:
In manufacturing, Six Sigma helps reduce defects and variations in the production process. It's used to improve product quality, increase efficiency, and minimize waste.
Applications range from automotive manufacturing to electronics, aerospace, and consumer goods production.
Healthcare:
Six Sigma has been instrumental in improving patient care and safety. Hospitals and healthcare providers use it to reduce medical errors, decrease patient waiting times, and enhance administrative processes.
Applications include optimizing emergency room operations, reducing hospital-acquired infections, and streamlining billing processes.
Education:
Educational institutions use Six Sigma to enhance administrative processes, improve curriculum delivery, and optimize resource allocation.
Applications range from streamlining student enrollment processes to reducing dropout rates.
Government and Public Services:
Government agencies apply Six Sigma to improve public services, streamline administrative processes, and reduce costs.
Applications include optimizing the issuance of permits and licenses, enhancing public transportation, and improving emergency response times.
Energy and Utilities:
Energy companies use Six Sigma to optimize power generation and distribution, reduce energy waste, and enhance safety procedures.
Applications include improving equipment maintenance, reducing energy consumption, and ensuring regulatory compliance.
These are just a few examples of the many industries where Six Sigma methodologies, including those implemented by Yellow Belts, have been effectively applied to drive process improvements, reduce costs, and enhance quality. The versatility of Six Sigma makes it a valuable tool in virtually any sector seeking to improve its operations.
Yellow Belt vs. Other Six Sigma Belts
Six Sigma certifications come in various levels, including Yellow Belt, Green Belt, Black Belt, and Master Black Belt. Each of these belts represents a different level of expertise and responsibility within the Six Sigma framework. Here's a comparison of Yellow Belt with other Six Sigma belts:
Yellow Belt:
Role: Yellow Belts are typically team members or support staff in Six Sigma projects. They play a foundational role, assisting Green Belts, Black Belts, and Master Black Belts in process improvement initiatives.
Responsibilities: They contribute to projects by assisting with data collection, process mapping, basic analysis, and problem-solving tasks. Yellow Belts often work on smaller-scale projects or specific aspects of larger projects.
Training: Yellow Belt training provides a basic understanding of Six Sigma principles, the DMAIC methodology, and core tools used in process improvement.
Certification: Earning a Yellow Belt certification requires completing training and passing an exam. It is an entry-level certification.
Green Belt:
Role: Green Belts lead process improvement projects and work under the guidance of Black Belts. They are responsible for project management and data analysis.
Responsibilities: Green Belts are more directly involved in the DMAIC process, including problem identification, root cause analysis, solution implementation, and process control.
Training: Green Belt training is more comprehensive than Yellow Belt training, covering advanced tools and statistical techniques.
Certification: Earning a Green Belt certification involves completing training, demonstrating proficiency through a project, and often passing an exam.
Black Belt:
Role: Black Belts are project leaders and are responsible for overseeing complex Six Sigma projects. They are often involved in multiple projects simultaneously.
Responsibilities: Black Belts are expected to have a deep understanding of Six Sigma tools and techniques. They identify projects, lead teams, and drive significant process improvements.
Training: Black Belt training is extensive, covering advanced statistical analysis, project management, and leadership skills.
Certification: Earning a Black Belt certification involves completing intensive training, leading successful projects, and passing a certification exam.
In summary, the primary differences between the various Six Sigma belts lie in their level of expertise, responsibilities, and the complexity of projects they handle. Yellow Belts are entry-level participants, Green Belts lead specific projects, Black Belts manage complex projects, and Master Black Belts are experts who guide and mentor others. The choice of belt level depends on one's career goals, level of expertise, and the scope of desired involvement in Six Sigma projects.
Real-World Examples
Real-world examples of Six Sigma Yellow Belt projects and their outcomes illustrate the practical applications of this methodology in improving processes and reducing defects. Here are a few examples:
Manufacturing Industry:
Project: A manufacturing company noticed high defect rates in a particular product line. A Yellow Belt team was formed to identify and address the root causes.
Outcome: Through process analysis and the implementation of changes, they reduced defect rates by 30% and increased production efficiency.
Healthcare Industry:
Project: A hospital's emergency department had long patient wait times and overcrowding issues. A Yellow Belt team was tasked with reducing waiting times and improving patient flow.
Outcome: The team implemented new triage processes, improved communication among staff, and streamlined admission procedures, resulting in a 40% reduction in wait times.
IT Services:Project: An IT support department had high call resolution times and frequent escalations. A Yellow Belt team worked on improving support processes.
Outcome: They restructured the support flow, developed a knowledge base, and provided additional training for staff. As a result, call resolution times decreased by 50%, and escalations reduced significantly.
Education:Project: A school district was facing budget constraints and wanted to optimize transportation routes for school buses. A Yellow Belt team was tasked with improving route efficiency.
Outcome: By analyzing bus schedules and optimizing routes, the district saved 15% in transportation costs while maintaining service quality.
These examples demonstrate how Six Sigma Yellow Belts can make meaningful contributions to process improvement across diverse industries. While they may not lead the projects independently, their involvement in problem-solving and data analysis plays a crucial role in achieving positive outcomes. Additionally, these successes showcase the versatility of Six Sigma in addressing a wide range of process-related challenges.
Preparing for the Yellow Belt Exam
Preparing for a Yellow Belt certification exam in Six Sigma involves systematic study, practice, and a clear understanding of the key concepts and tools associated with the methodology. Here's a step-by-step guide to help you prepare for your Yellow Belt exam:
Understand the Exam Format:Start by familiarizing yourself with the structure and format of the Yellow Belt exam. Understand the number of questions, time constraints, and any specific requirements for the exam.
Review Training Materials:Revisit your Yellow Belt training materials, including textbooks, lecture notes, and any online resources provided during your training. Ensure you have a solid grasp of the fundamental concepts, principles, and tools of Six Sigma.
Use Study Guides:Consider using study guides or reference materials designed specifically for Six Sigma Yellow Belt certification. These resources often provide concise summaries of key topics and sample questions.
Self-Assessments:Take self-assessment quizzes and tests to identify your strengths and
Time Management:Develop a study schedule that allows you to allocate sufficient time for each topic. Consistent, organized studying can help you cover all relevant content before the exam.
Mock Exams:Take full-length mock exams under timed conditions to simulate the exam experience. This helps you become comfortable with the format and identify areas that need improvement.
Remember that effective preparation is not just about memorizing facts but understanding the underlying principles and being able to apply them in real-world scenarios. By following these steps and staying committed to your study plan, you'll increase your chances of success in the Yellow Belt certification exam.
Career Advancement and Opportunities
Earning a Six Sigma Yellow Belt certification can lead to several career advancement opportunities and benefits. Here's how this certification can positively impact your career:
Enhanced Problem-Solving Skills: Yellow Belt training equips you with problem-solving skills that are valuable in many industries. This skillset can make you a more effective and efficient employee, contributing to career growth.
Cross-Functional Collaboration: Six Sigma projects often involve cross-functional teams. Collaborating with colleagues from different departments can expand your network and expose you to new career prospects.
Certification Path: Earning a Yellow Belt can serve as a stepping stone to higher-level Six Sigma certifications, such as Green Belt or Black Belt. These advanced certifications open doors to more complex and impactful roles within an organization.
Salary Increase: Many organizations offer salary increases or bonuses for employees who obtain Six Sigma certifications due to the potential cost savings and quality improvements they bring to the organization.
Consulting Opportunities: After gaining experience and expertise as a Yellow Belt, you may consider a career in Six Sigma consulting, where you can help other organizations improve their processes.
In summary, a Six Sigma Yellow Belt certification can provide numerous career advantages, including the potential for promotions, salary increases, and the opportunity to work on impactful projects. It also equips you with valuable problem-solving skills that are relevant in many industries, making you a valuable asset in the job market.
Conclusion
In conclusion, Six Sigma Yellow Belt certification is a valuable step in your professional development journey. It equips you with foundational knowledge and skills in the Six Sigma methodology, problem-solving, and process improvement. Whether you're looking to advance your career within your current organization, transition to a new field, or pursue further Six Sigma certifications, the Yellow Belt is a worthwhile investment.
By understanding the principles of Six Sigma, learning how to use data-driven approaches to solve problems, and actively participating in process improvement projects, you can contribute to your organization's success and enhance your own career prospects. The benefits of Yellow Belt certification are numerous, from increased problem-solving abilities to potential salary enhancements and new career opportunities.
Remember that Yellow Belt certification is just the beginning of your Six Sigma journey. With dedication, continued learning, and the possibility of pursuing higher-level certifications, you can make a significant impact in your organization and in your own career advancement. Whether you're in manufacturing, healthcare, finance, or any other industry, Six Sigma principles can lead to improved quality, efficiency, and competitiveness.
So, as you embark on your Yellow Belt certification journey, embrace the opportunity to learn and grow. Keep in mind that Six Sigma is not just about achieving certification; it's about applying these valuable principles and tools to create meaningful, positive change in the processes and systems that shape our professional world.
Is project management a good career?
Project management is a multifaceted and dynamic field that plays a pivotal role in shaping the success of organizations across various industries. It involves planning, organizing, and overseeing the execution of projects to achieve specific objectives efficiently and effectively. As professionals in this field, project managers are responsible for guiding teams, managing resources, and ensuring that projects are completed on time and within budget. The question of whether project management is a good career choice is one that prospective professionals and individuals considering a career change often ponder.
This article explores the many facets of project management as a career choice, aiming to shed light on the factors that make it a compelling option for those seeking a fulfilling and rewarding profession. We will delve into aspects such as the job market, compensation, required skills and qualifications, specialization opportunities, challenges, work-life balance, job satisfaction, advancement possibilities, and the future outlook of project management. By the end, you will have a more informed perspective on the viability and appeal of a career in project management.
Table of contents
-
Project Management Overview
-
Job Market and Demand
-
Salary and Compensation
-
Required Skills and Qualifications
-
Career Paths and Specializations
-
Challenges and Stress Levels
-
Work-Life Balance
-
Job Satisfaction and Fulfillment
-
Advancement Opportunities
-
Future of Project Management
-
Conclusion
Project Management Overview
Project management is a discipline that involves planning, organizing, and overseeing a project's execution to achieve specific objectives. Whether it's building a new skyscraper, launching a software application, or organizing a marketing campaign, project management provides a structured approach to ensure that projects are completed successfully, on time, and within budget.
Key components of project management include:
Project Initiation: This is where the project's objectives, scope, and stakeholders are identified. Project managers work closely with stakeholders to define what the project will achieve.
Planning: Project managers develop detailed plans that outline the tasks, resources, and timelines required to complete the project. This phase includes creating a project schedule, budget, and risk management plan.
Execution: During this phase, project teams carry out the work defined in the project plan. The project manager oversees team members, allocates resources, and monitors progress to ensure the project stays on track.
Closing: When the project is complete and objectives are met, the project is closed. This involves handing over deliverables to the client or stakeholders, evaluating the project's success, and documenting lessons learned for future projects.
Project management is crucial in various industries, including construction, IT, healthcare, finance, and more. It helps organizations manage complexity, reduce risks, and improve efficiency. Skilled project managers are in high demand to ensure that projects are delivered successfully, making it a valuable and rewarding career choice.
Throughout this article, we will explore various aspects of project management as a career, from job market trends and compensation to the skills and qualifications required, challenges, job satisfaction, and the potential for career advancement. This comprehensive overview will provide you with insights to determine if project management is the right career path for you.
Job Market and Demand
The job market for project management professionals has shown consistent growth and high demand in recent years, making it a promising career choice. Several factors contribute to this trend:
Industry Versatility: Project management is applicable across a wide range of industries, including IT, construction, healthcare, finance, marketing, and more. This versatility ensures that project management roles are available in various sectors.
Globalization: With businesses expanding their operations globally, the need for project managers who can coordinate and manage projects across different regions has increased significantly.
Technology and Innovation: The integration of technology and innovation in project management has led to new job opportunities. Project managers with expertise in areas like Agile, Scrum, and data analytics are particularly sought after.
Regulatory Requirements: Some industries, such as healthcare and finance, have stringent regulatory requirements. Project managers who can navigate these regulations are in high demand to ensure compliance.
Sustainability and Green Initiatives: With a global focus on sustainability and environmental responsibility, project managers with expertise in eco-friendly projects and sustainable practices are increasingly in demand.
It's essential to note that the demand for project management professionals can vary by location, industry, and economic conditions. Some regions or industries may have a higher demand for project managers than others. Prospective project managers should consider these factors and conduct thorough research to identify the most promising opportunities within the field. Overall, project management is a career with a positive job market outlook and offers a wide range of possibilities for those interested in this profession.
Salary and Compensation
Salaries and compensation for project managers can vary widely based on factors such as location, industry, experience, and specific job roles. Here's an overview of the typical salary and compensation considerations in project management:
Experience Level: Salary levels in project management typically increase with experience. Entry-level project managers may earn less than their seasoned counterparts, but as they gain more experience, their earning potential grows.
Location: Salaries for project managers vary greatly by location. Cities with a higher cost of living, such as New York City or San Francisco, tend to offer higher salaries to match the increased expenses.
Industry: The industry in which a project manager works can significantly impact compensation. For example, project managers in IT and healthcare often earn competitive salaries due to the complexity and critical nature of projects in those fields.
Company Size: Larger organizations often offer higher salaries and more comprehensive compensation packages for project managers. They may also provide additional benefits like bonuses and profit-sharing.
Certifications: Obtaining project management certifications, such as PMP (Project Management Professional) or PRINCE2, can lead to higher salaries and better job opportunities. Many employers value certified project managers for their expertise and knowledge.
Freelance and Consulting: Freelance project managers or consultants may have more control over their compensation but should consider factors like self-employment taxes and a lack of traditional benefits.
It's important for individuals considering a career in project management to research salary data specific to their location and industry. Websites and resources like the Project Management Institute (PMI) and the Bureau of Labor Statistics (BLS) can provide valuable insights into average salaries in various regions and sectors. As project management continues to be a sought-after profession, competitive compensation and opportunities for career growth make it an attractive choice for many professionals.
Required Skills and Qualifications
To excel in a project management career, professionals need a specific set of skills and qualifications. These skills and qualifications are essential for effectively planning, executing, and managing projects. Here's a list of key requirements for success in project management:
Leadership Skills:
Communication: Project managers must be effective communicators, both verbally and in writing. They need to convey project goals, expectations, and progress to team members and stakeholders.
Motivation: Project managers should inspire and motivate their teams to achieve project objectives. Leadership skills are crucial for driving team performance.
Risk Management:Identifying potential risks and developing risk management strategies is crucial for minimizing project disruptions.
Problem-Solving:Project managers often encounter unforeseen issues. The ability to think critically and find solutions is a valuable skill.
Negotiation Skills:Negotiation skills are important for managing stakeholder expectations, resolving conflicts, and securing necessary resources for the project.
Team Building:Building cohesive and effective project teams is a key responsibility of a project manager. This involves selecting the right team members and fostering collaboration.
Financial Management:Budgeting and cost control skills are important for ensuring projects stay within budget.
Certification: Many project managers pursue professional certifications, such as the Project Management Professional (PMP) or Certified ScrumMaster (CSM) certification, to enhance their qualifications and demonstrate their expertise to employers.
Experience:Gaining experience in project management is vital for career progression. This can be through internships, entry-level positions, or assistant project management roles.
Successful project managers often possess a combination of these skills and qualifications. However, the specific requirements may vary depending on the industry and the type of projects being managed. Continuous learning and professional development are also essential in project management, as the field is constantly evolving.
Career Paths and Specializations
Project management is a versatile field with various career paths and specializations, allowing professionals to tailor their careers to their interests and expertise. Here are some common career paths and specializations within the realm of project management:
IT Project Management:
Software Development: Managing projects related to software development, including web applications, mobile apps, and system integration.
Infrastructure Projects: Overseeing IT infrastructure projects, such as network upgrades, data center migrations, and cloud implementations.
Agile and Scrum:
Agile Coach: Assisting organizations in implementing Agile methodologies across various departments.
Scrum Master: Facilitating Scrum processes and ensuring teams follow Scrum principles in software development projects.
Engineering Project Management:
Civil Engineering: Overseeing projects such as bridges, highways, and infrastructure development.
Environmental Engineering: Managing projects related to environmental protection, waste management, and sustainability initiatives.
Event Management:
Corporate Events: Planning and executing corporate events, conferences, trade shows, and exhibitions.
Wedding Planning: Managing weddings, including venue selection, vendor coordination, and logistics.
Risk Management:
Financial Risk Management: Specializing in managing financial and investment projects with a focus on risk assessment and mitigation.
Compliance and Regulatory Risk: Overseeing projects to ensure regulatory compliance and mitigate legal and compliance risks.
Nonprofit and NGO Project Management:
International Development: Managing projects related to global development, humanitarian aid, and disaster relief.
Fundraising Campaigns: Overseeing fundraising initiatives, donor management, and grant-funded projects.
Real Estate Development:
Residential Development: Managing residential property development projects, including housing communities and apartment complexes.
Commercial Real Estate: Overseeing commercial real estate development, such as office buildings and shopping centers.
Aerospace and Defense:
Aerospace Engineering: Managing projects related to aircraft and spacecraft design, development, and manufacturing.
Defense Contracts: Overseeing defense projects, including military equipment procurement and technology development.
These are just a few examples of career paths and specializations within project management. Project managers can transition between specializations or gain expertise in multiple areas throughout their careers, making project management a highly adaptable and diverse profession.
Challenges and Stress Levels
Project management is a rewarding career, but it also comes with its fair share of challenges and stressors. Here are some of the common challenges and factors that can contribute to stress in project management:
Scope Creep: Changes to the project scope, objectives, or requirements can increase complexity and lead to stress. Project managers must effectively manage scope changes to prevent project derailment.
Stakeholder Expectations: Managing the expectations of various stakeholders, including clients, team members, and sponsors, can be demanding. Effective communication and expectation management are critical.
Risk Management: Identifying and mitigating risks is a fundamental part of project management. Handling unexpected issues and risks can be stressful if not managed effectively.
Quality Control: Maintaining project quality and ensuring that deliverables meet the required standards can be a complex and demanding task.
Communication Challenges: Ineffective communication can lead to misunderstandings, delays, and project issues. Project managers must establish clear lines of communication and convey information accurately.
Project Complexity: Projects with high complexity, multiple dependencies, and intricate requirements can be especially stressful to manage.
Work-Life Balance: The demand for project managers to work long hours, including evenings and weekends, can strain work-life balance, leading to burnout.
Uncertainty: Project managers often work with incomplete information, and project outcomes may be uncertain. Managing projects with ambiguity can be mentally taxing.
Decision-Making: Project managers are frequently required to make critical decisions under pressure, which can lead to stress.
Project Failures: Facing the possibility of project failure and the associated consequences can be highly stressful.
Despite these challenges, many project managers find the field to be gratifying. They develop problem-solving skills, leadership abilities, and the satisfaction of successfully completing complex projects. Moreover, organizations may implement stress-reduction measures, such as providing adequate resources and support, to help their project managers thrive in a demanding profession.
Work-Life Balance
Maintaining a healthy work-life balance is a crucial aspect of a fulfilling and sustainable project management career. While project management can be demanding and often involves tight deadlines, effective work-life balance is essential to prevent burnout and maintain overall well-being. Here are some strategies and considerations for achieving a better work-life balance in project management:
Set Boundaries:Clearly define your work hours and communicate them to your team and stakeholders. Make an effort to separate work from personal time.
Prioritize Tasks:Identify the most critical tasks and prioritize them. This allows you to focus on what truly matters and minimize time spent on less important activities.
Delegate Responsibility:Delegate tasks to team members when possible. Effective delegation not only lightens your workload but also empowers your team and promotes their professional growth.
Time Management:Adopt time management techniques, such as the Pomodoro Technique or the Eisenhower Matrix, to maximize productivity during work hours.
Avoid Overcommitment:Be mindful of your capacity and avoid overcommitting to projects. Take on a workload that is manageable without excessive stress.
Take Breaks:Regular short breaks during work can refresh your mind and boost productivity. Plan for longer breaks and vacations to recharge and spend time with family and friends.
Negotiate Flexibility:If possible, negotiate flexible work arrangements with your employer. Options like remote work or flexible hours can greatly improve work-life balance.
Communication:Communicate your work-life balance needs with your team and supervisor. A supportive work environment is more likely to accommodate your requirements.
Self-Care:Make self-care a priority. This includes exercise, a balanced diet, adequate sleep, and stress-reduction techniques like meditation or mindfulness.
Evaluate and Adjust:Regularly assess your work-life balance and make necessary adjustments. As your career evolves, your needs and priorities may change.
Remember that achieving a work-life balance in project management is an ongoing process. It requires self-awareness, effective time management, and clear communication with your team and superiors. By taking steps to maintain a balance, you can not only excel in your career but also enjoy a fulfilling personal life. Work-life balance is essential not only for your well-being but also for your long-term success as a project manager.
Job Satisfaction and Fulfillment
Job satisfaction and fulfillment are significant aspects of a project management career. When project managers find their work rewarding and fulfilling, they are more likely to excel in their roles and achieve long-term success. Here are some factors that contribute to job satisfaction and fulfillment in project management:
Achieving Project Success:Successfully completing projects on time, within budget, and to the satisfaction of stakeholders can be highly fulfilling and boost job satisfaction.
Problem Solving:Project managers are often faced with complex challenges and problem-solving opportunities. Overcoming these obstacles can provide a sense of accomplishment.
Leadership and Impact:Leading project teams and making critical decisions can be fulfilling, as it allows project managers to see the direct impact of their leadership and expertise.
Continuous Learning:Project management is a dynamic field, and professionals have the opportunity to continuously learn and acquire new skills, which can be intellectually stimulating.
Professional Development:Organizations often support the professional development of project managers through training, certifications, and mentorship programs. This can enhance job satisfaction.
Diverse Projects:Working on diverse projects in different industries and sectors can keep the job exciting and offer new challenges.
Recognition and Rewards:Being recognized and rewarded for outstanding performance, whether through bonuses, promotions, or awards, can boost job satisfaction.
Work-Life Balance:Maintaining a healthy work-life balance is vital for overall job satisfaction and life fulfillment.
Strong Team Dynamics:Positive team dynamics, effective collaboration, and a supportive work environment contribute to job satisfaction.
Feedback and Improvement:Constructive feedback and opportunities for improvement are essential for personal and professional growth, enhancing job satisfaction.
Alignment with Personal Values:Feeling that your work aligns with your personal values and beliefs can lead to greater job satisfaction.
Recognition of Contributions:Feeling valued for the contributions you make to projects and the organization can foster job satisfaction.
Mentoring and Mentorship:Having the opportunity to mentor or be mentored by experienced professionals can be fulfilling and provide valuable insights.
Autonomy and Responsibility:A degree of autonomy and the responsibility to make critical decisions can be personally rewarding for project managers.
Overall, job satisfaction and fulfillment in project management are influenced by a combination of intrinsic factors (personal values, sense of accomplishment) and extrinsic factors (recognition, compensation, work environment). It's essential for project managers to align their roles with their career goals and values, continuously seek opportunities for growth, and maintain a positive work-life balance to maximize their job satisfaction and overall fulfillment.
Advancement Opportunities
Project management offers numerous opportunities for career advancement and growth. As professionals gain experience and expertise, they can progress in their careers and take on more significant roles. Here are some common paths for advancement in project management:
Senior Project Manager:Experienced project managers often advance to senior project manager roles. These positions involve greater responsibility, oversight of larger projects, and more complex decision-making.
Program Manager:Program managers oversee multiple related projects within an organization, ensuring they align with the company's strategic objectives. This role involves higher-level planning and coordination.
Portfolio Manager:Portfolio managers manage a collection of projects and programs within an organization. They focus on optimizing project selection and resource allocation to meet business goals.
Project Management Office (PMO) Director:PMO directors are responsible for leading and overseeing an organization's project management office. They set policies, standards, and best practices for project management.
Industry-Specific Specializations:Project managers can specialize in specific industries, such as healthcare, IT, or construction, and advance within those sectors to become industry experts.
Professional Certifications:Earning advanced project management certifications, such as the PMI Program Management Professional (PgMP) or PMI Portfolio Management Professional (PfMP), can open doors to higher-level positions.
Entrepreneurship:Launching a project management consulting or training business is an option for experienced project managers who want to be their own bosses.
International and Multinational Roles:Opportunities exist for project managers to work on international projects or assume roles within multinational organizations, which can broaden their global expertise and cultural understanding.
Advancement in project management often requires a combination of experience, education, and professional development. It's crucial to continue learning, stay up-to-date with industry trends, and seek opportunities for leadership and skill development. Networking and mentorship can also play a significant role in career advancement, as they provide valuable insights and connections within the field. Overall, the career path in project management is diverse, and professionals can choose the direction that aligns with their interests and career goals.
Future of Project Management
The future of project management is evolving in response to technological advancements, changing work environments, and the increasing complexity of projects. Here are some key trends and considerations that shape the future of project management:
Digital Transformation: Technology plays a central role in the future of project management. Project managers will need to adapt to and leverage emerging technologies, including AI, machine learning, data analytics, and automation, to enhance project planning, execution, and monitoring.
Agile and Adaptive Approaches: Agile methodologies are becoming increasingly popular, not only in software development but also in other industries. Agile and adaptive project management approaches are being adopted to respond to changing project requirements and market dynamics more effectively.
Globalization: As businesses expand globally, project managers will need to manage cross-border projects, navigate international regulations, and work with diverse cultural and linguistic groups.
Predictive Analytics: Project managers will increasingly use data-driven insights to make informed decisions, anticipate project risks, and optimize resource allocation.
Emphasis on Soft Skills: As technology handles repetitive tasks, soft skills such as leadership, communication, emotional intelligence, and conflict resolution will become even more critical for project managers.
Certifications and Professional Development: Continuous learning and the acquisition of relevant certifications, such as Agile or specialized industry certifications, will be essential to stay competitive in the field.
Hybrid Work Models: A mix of remote and in-person work will likely become more common, and project managers will need to adapt their management styles accordingly.
Resilience and Risk Management: Given the increasing frequency of disruptive events like pandemics and climate-related crises, project managers will need to focus on building resilience and robust risk management strategies.
Artificial Intelligence Assistance: AI tools may help automate routine project management tasks, allowing project managers to focus on more strategic and creative aspects of their work.
Conclusion
In conclusion, project management is a dynamic and multifaceted field that offers numerous opportunities for individuals seeking a fulfilling and rewarding career. This article has explored various aspects of project management, including its job market, salary and compensation, required skills and qualifications, career paths and specializations, challenges and stress levels, work-life balance, job satisfaction, and advancement opportunities.
Project management is not only a well-paying profession but also one that plays a pivotal role in ensuring the successful execution of projects in various industries. Project managers are in high demand due to the increasing complexity of projects and the need for effective coordination and leadership.
While project management can be challenging and demanding, professionals in this field have the opportunity to excel by continually developing their skills, managing stress, and achieving a healthy work-life balance
Whether you're considering a career in project management or are an experienced professional seeking to advance your career, a thorough understanding of the job market, necessary skills, and opportunities for growth is vital. Project management is a profession that offers both personal fulfillment and the chance to contribute significantly to the success of organizations and projects across the globe.
Read More
Project management is a multifaceted and dynamic field that plays a pivotal role in shaping the success of organizations across various industries. It involves planning, organizing, and overseeing the execution of projects to achieve specific objectives efficiently and effectively. As professionals in this field, project managers are responsible for guiding teams, managing resources, and ensuring that projects are completed on time and within budget. The question of whether project management is a good career choice is one that prospective professionals and individuals considering a career change often ponder.
This article explores the many facets of project management as a career choice, aiming to shed light on the factors that make it a compelling option for those seeking a fulfilling and rewarding profession. We will delve into aspects such as the job market, compensation, required skills and qualifications, specialization opportunities, challenges, work-life balance, job satisfaction, advancement possibilities, and the future outlook of project management. By the end, you will have a more informed perspective on the viability and appeal of a career in project management.
Table of contents
-
Project Management Overview
-
Job Market and Demand
-
Salary and Compensation
-
Required Skills and Qualifications
-
Career Paths and Specializations
-
Challenges and Stress Levels
-
Work-Life Balance
-
Job Satisfaction and Fulfillment
-
Advancement Opportunities
-
Future of Project Management
-
Conclusion
Project Management Overview
Project management is a discipline that involves planning, organizing, and overseeing a project's execution to achieve specific objectives. Whether it's building a new skyscraper, launching a software application, or organizing a marketing campaign, project management provides a structured approach to ensure that projects are completed successfully, on time, and within budget.
Key components of project management include:
Project Initiation: This is where the project's objectives, scope, and stakeholders are identified. Project managers work closely with stakeholders to define what the project will achieve.
Planning: Project managers develop detailed plans that outline the tasks, resources, and timelines required to complete the project. This phase includes creating a project schedule, budget, and risk management plan.
Execution: During this phase, project teams carry out the work defined in the project plan. The project manager oversees team members, allocates resources, and monitors progress to ensure the project stays on track.
Closing: When the project is complete and objectives are met, the project is closed. This involves handing over deliverables to the client or stakeholders, evaluating the project's success, and documenting lessons learned for future projects.
Project management is crucial in various industries, including construction, IT, healthcare, finance, and more. It helps organizations manage complexity, reduce risks, and improve efficiency. Skilled project managers are in high demand to ensure that projects are delivered successfully, making it a valuable and rewarding career choice.
Throughout this article, we will explore various aspects of project management as a career, from job market trends and compensation to the skills and qualifications required, challenges, job satisfaction, and the potential for career advancement. This comprehensive overview will provide you with insights to determine if project management is the right career path for you.
Job Market and Demand
The job market for project management professionals has shown consistent growth and high demand in recent years, making it a promising career choice. Several factors contribute to this trend:
Industry Versatility: Project management is applicable across a wide range of industries, including IT, construction, healthcare, finance, marketing, and more. This versatility ensures that project management roles are available in various sectors.
Globalization: With businesses expanding their operations globally, the need for project managers who can coordinate and manage projects across different regions has increased significantly.
Technology and Innovation: The integration of technology and innovation in project management has led to new job opportunities. Project managers with expertise in areas like Agile, Scrum, and data analytics are particularly sought after.
Regulatory Requirements: Some industries, such as healthcare and finance, have stringent regulatory requirements. Project managers who can navigate these regulations are in high demand to ensure compliance.
Sustainability and Green Initiatives: With a global focus on sustainability and environmental responsibility, project managers with expertise in eco-friendly projects and sustainable practices are increasingly in demand.
It's essential to note that the demand for project management professionals can vary by location, industry, and economic conditions. Some regions or industries may have a higher demand for project managers than others. Prospective project managers should consider these factors and conduct thorough research to identify the most promising opportunities within the field. Overall, project management is a career with a positive job market outlook and offers a wide range of possibilities for those interested in this profession.
Salary and Compensation
Salaries and compensation for project managers can vary widely based on factors such as location, industry, experience, and specific job roles. Here's an overview of the typical salary and compensation considerations in project management:
Experience Level: Salary levels in project management typically increase with experience. Entry-level project managers may earn less than their seasoned counterparts, but as they gain more experience, their earning potential grows.
Location: Salaries for project managers vary greatly by location. Cities with a higher cost of living, such as New York City or San Francisco, tend to offer higher salaries to match the increased expenses.
Industry: The industry in which a project manager works can significantly impact compensation. For example, project managers in IT and healthcare often earn competitive salaries due to the complexity and critical nature of projects in those fields.
Company Size: Larger organizations often offer higher salaries and more comprehensive compensation packages for project managers. They may also provide additional benefits like bonuses and profit-sharing.
Certifications: Obtaining project management certifications, such as PMP (Project Management Professional) or PRINCE2, can lead to higher salaries and better job opportunities. Many employers value certified project managers for their expertise and knowledge.
Freelance and Consulting: Freelance project managers or consultants may have more control over their compensation but should consider factors like self-employment taxes and a lack of traditional benefits.
It's important for individuals considering a career in project management to research salary data specific to their location and industry. Websites and resources like the Project Management Institute (PMI) and the Bureau of Labor Statistics (BLS) can provide valuable insights into average salaries in various regions and sectors. As project management continues to be a sought-after profession, competitive compensation and opportunities for career growth make it an attractive choice for many professionals.
Required Skills and Qualifications
To excel in a project management career, professionals need a specific set of skills and qualifications. These skills and qualifications are essential for effectively planning, executing, and managing projects. Here's a list of key requirements for success in project management:
Leadership Skills:
Communication: Project managers must be effective communicators, both verbally and in writing. They need to convey project goals, expectations, and progress to team members and stakeholders.
Motivation: Project managers should inspire and motivate their teams to achieve project objectives. Leadership skills are crucial for driving team performance.
Risk Management:Identifying potential risks and developing risk management strategies is crucial for minimizing project disruptions.
Problem-Solving:Project managers often encounter unforeseen issues. The ability to think critically and find solutions is a valuable skill.
Negotiation Skills:Negotiation skills are important for managing stakeholder expectations, resolving conflicts, and securing necessary resources for the project.
Team Building:Building cohesive and effective project teams is a key responsibility of a project manager. This involves selecting the right team members and fostering collaboration.
Financial Management:Budgeting and cost control skills are important for ensuring projects stay within budget.
Certification: Many project managers pursue professional certifications, such as the Project Management Professional (PMP) or Certified ScrumMaster (CSM) certification, to enhance their qualifications and demonstrate their expertise to employers.
Experience:Gaining experience in project management is vital for career progression. This can be through internships, entry-level positions, or assistant project management roles.
Successful project managers often possess a combination of these skills and qualifications. However, the specific requirements may vary depending on the industry and the type of projects being managed. Continuous learning and professional development are also essential in project management, as the field is constantly evolving.
Career Paths and Specializations
Project management is a versatile field with various career paths and specializations, allowing professionals to tailor their careers to their interests and expertise. Here are some common career paths and specializations within the realm of project management:
IT Project Management:
Software Development: Managing projects related to software development, including web applications, mobile apps, and system integration.
Infrastructure Projects: Overseeing IT infrastructure projects, such as network upgrades, data center migrations, and cloud implementations.
Agile and Scrum:
Agile Coach: Assisting organizations in implementing Agile methodologies across various departments.
Scrum Master: Facilitating Scrum processes and ensuring teams follow Scrum principles in software development projects.
Engineering Project Management:
Civil Engineering: Overseeing projects such as bridges, highways, and infrastructure development.
Environmental Engineering: Managing projects related to environmental protection, waste management, and sustainability initiatives.
Event Management:
Corporate Events: Planning and executing corporate events, conferences, trade shows, and exhibitions.
Wedding Planning: Managing weddings, including venue selection, vendor coordination, and logistics.
Risk Management:
Financial Risk Management: Specializing in managing financial and investment projects with a focus on risk assessment and mitigation.
Compliance and Regulatory Risk: Overseeing projects to ensure regulatory compliance and mitigate legal and compliance risks.
Nonprofit and NGO Project Management:
International Development: Managing projects related to global development, humanitarian aid, and disaster relief.
Fundraising Campaigns: Overseeing fundraising initiatives, donor management, and grant-funded projects.
Real Estate Development:
Residential Development: Managing residential property development projects, including housing communities and apartment complexes.
Commercial Real Estate: Overseeing commercial real estate development, such as office buildings and shopping centers.
Aerospace and Defense:
Aerospace Engineering: Managing projects related to aircraft and spacecraft design, development, and manufacturing.
Defense Contracts: Overseeing defense projects, including military equipment procurement and technology development.
These are just a few examples of career paths and specializations within project management. Project managers can transition between specializations or gain expertise in multiple areas throughout their careers, making project management a highly adaptable and diverse profession.
Challenges and Stress Levels
Project management is a rewarding career, but it also comes with its fair share of challenges and stressors. Here are some of the common challenges and factors that can contribute to stress in project management:
Scope Creep: Changes to the project scope, objectives, or requirements can increase complexity and lead to stress. Project managers must effectively manage scope changes to prevent project derailment.
Stakeholder Expectations: Managing the expectations of various stakeholders, including clients, team members, and sponsors, can be demanding. Effective communication and expectation management are critical.
Risk Management: Identifying and mitigating risks is a fundamental part of project management. Handling unexpected issues and risks can be stressful if not managed effectively.
Quality Control: Maintaining project quality and ensuring that deliverables meet the required standards can be a complex and demanding task.
Communication Challenges: Ineffective communication can lead to misunderstandings, delays, and project issues. Project managers must establish clear lines of communication and convey information accurately.
Project Complexity: Projects with high complexity, multiple dependencies, and intricate requirements can be especially stressful to manage.
Work-Life Balance: The demand for project managers to work long hours, including evenings and weekends, can strain work-life balance, leading to burnout.
Uncertainty: Project managers often work with incomplete information, and project outcomes may be uncertain. Managing projects with ambiguity can be mentally taxing.
Decision-Making: Project managers are frequently required to make critical decisions under pressure, which can lead to stress.
Project Failures: Facing the possibility of project failure and the associated consequences can be highly stressful.
Despite these challenges, many project managers find the field to be gratifying. They develop problem-solving skills, leadership abilities, and the satisfaction of successfully completing complex projects. Moreover, organizations may implement stress-reduction measures, such as providing adequate resources and support, to help their project managers thrive in a demanding profession.
Work-Life Balance
Maintaining a healthy work-life balance is a crucial aspect of a fulfilling and sustainable project management career. While project management can be demanding and often involves tight deadlines, effective work-life balance is essential to prevent burnout and maintain overall well-being. Here are some strategies and considerations for achieving a better work-life balance in project management:
Set Boundaries:Clearly define your work hours and communicate them to your team and stakeholders. Make an effort to separate work from personal time.
Prioritize Tasks:Identify the most critical tasks and prioritize them. This allows you to focus on what truly matters and minimize time spent on less important activities.
Delegate Responsibility:Delegate tasks to team members when possible. Effective delegation not only lightens your workload but also empowers your team and promotes their professional growth.
Time Management:Adopt time management techniques, such as the Pomodoro Technique or the Eisenhower Matrix, to maximize productivity during work hours.
Avoid Overcommitment:Be mindful of your capacity and avoid overcommitting to projects. Take on a workload that is manageable without excessive stress.
Take Breaks:Regular short breaks during work can refresh your mind and boost productivity. Plan for longer breaks and vacations to recharge and spend time with family and friends.
Negotiate Flexibility:If possible, negotiate flexible work arrangements with your employer. Options like remote work or flexible hours can greatly improve work-life balance.
Communication:Communicate your work-life balance needs with your team and supervisor. A supportive work environment is more likely to accommodate your requirements.
Self-Care:Make self-care a priority. This includes exercise, a balanced diet, adequate sleep, and stress-reduction techniques like meditation or mindfulness.
Evaluate and Adjust:Regularly assess your work-life balance and make necessary adjustments. As your career evolves, your needs and priorities may change.
Remember that achieving a work-life balance in project management is an ongoing process. It requires self-awareness, effective time management, and clear communication with your team and superiors. By taking steps to maintain a balance, you can not only excel in your career but also enjoy a fulfilling personal life. Work-life balance is essential not only for your well-being but also for your long-term success as a project manager.
Job Satisfaction and Fulfillment
Job satisfaction and fulfillment are significant aspects of a project management career. When project managers find their work rewarding and fulfilling, they are more likely to excel in their roles and achieve long-term success. Here are some factors that contribute to job satisfaction and fulfillment in project management:
Achieving Project Success:Successfully completing projects on time, within budget, and to the satisfaction of stakeholders can be highly fulfilling and boost job satisfaction.
Problem Solving:Project managers are often faced with complex challenges and problem-solving opportunities. Overcoming these obstacles can provide a sense of accomplishment.
Leadership and Impact:Leading project teams and making critical decisions can be fulfilling, as it allows project managers to see the direct impact of their leadership and expertise.
Continuous Learning:Project management is a dynamic field, and professionals have the opportunity to continuously learn and acquire new skills, which can be intellectually stimulating.
Professional Development:Organizations often support the professional development of project managers through training, certifications, and mentorship programs. This can enhance job satisfaction.
Diverse Projects:Working on diverse projects in different industries and sectors can keep the job exciting and offer new challenges.
Recognition and Rewards:Being recognized and rewarded for outstanding performance, whether through bonuses, promotions, or awards, can boost job satisfaction.
Work-Life Balance:Maintaining a healthy work-life balance is vital for overall job satisfaction and life fulfillment.
Strong Team Dynamics:Positive team dynamics, effective collaboration, and a supportive work environment contribute to job satisfaction.
Feedback and Improvement:Constructive feedback and opportunities for improvement are essential for personal and professional growth, enhancing job satisfaction.
Alignment with Personal Values:Feeling that your work aligns with your personal values and beliefs can lead to greater job satisfaction.
Recognition of Contributions:Feeling valued for the contributions you make to projects and the organization can foster job satisfaction.
Mentoring and Mentorship:Having the opportunity to mentor or be mentored by experienced professionals can be fulfilling and provide valuable insights.
Autonomy and Responsibility:A degree of autonomy and the responsibility to make critical decisions can be personally rewarding for project managers.
Overall, job satisfaction and fulfillment in project management are influenced by a combination of intrinsic factors (personal values, sense of accomplishment) and extrinsic factors (recognition, compensation, work environment). It's essential for project managers to align their roles with their career goals and values, continuously seek opportunities for growth, and maintain a positive work-life balance to maximize their job satisfaction and overall fulfillment.
Advancement Opportunities
Project management offers numerous opportunities for career advancement and growth. As professionals gain experience and expertise, they can progress in their careers and take on more significant roles. Here are some common paths for advancement in project management:
Senior Project Manager:Experienced project managers often advance to senior project manager roles. These positions involve greater responsibility, oversight of larger projects, and more complex decision-making.
Program Manager:Program managers oversee multiple related projects within an organization, ensuring they align with the company's strategic objectives. This role involves higher-level planning and coordination.
Portfolio Manager:Portfolio managers manage a collection of projects and programs within an organization. They focus on optimizing project selection and resource allocation to meet business goals.
Project Management Office (PMO) Director:PMO directors are responsible for leading and overseeing an organization's project management office. They set policies, standards, and best practices for project management.
Industry-Specific Specializations:Project managers can specialize in specific industries, such as healthcare, IT, or construction, and advance within those sectors to become industry experts.
Professional Certifications:Earning advanced project management certifications, such as the PMI Program Management Professional (PgMP) or PMI Portfolio Management Professional (PfMP), can open doors to higher-level positions.
Entrepreneurship:Launching a project management consulting or training business is an option for experienced project managers who want to be their own bosses.
International and Multinational Roles:Opportunities exist for project managers to work on international projects or assume roles within multinational organizations, which can broaden their global expertise and cultural understanding.
Advancement in project management often requires a combination of experience, education, and professional development. It's crucial to continue learning, stay up-to-date with industry trends, and seek opportunities for leadership and skill development. Networking and mentorship can also play a significant role in career advancement, as they provide valuable insights and connections within the field. Overall, the career path in project management is diverse, and professionals can choose the direction that aligns with their interests and career goals.
Future of Project Management
The future of project management is evolving in response to technological advancements, changing work environments, and the increasing complexity of projects. Here are some key trends and considerations that shape the future of project management:
Digital Transformation: Technology plays a central role in the future of project management. Project managers will need to adapt to and leverage emerging technologies, including AI, machine learning, data analytics, and automation, to enhance project planning, execution, and monitoring.
Agile and Adaptive Approaches: Agile methodologies are becoming increasingly popular, not only in software development but also in other industries. Agile and adaptive project management approaches are being adopted to respond to changing project requirements and market dynamics more effectively.
Globalization: As businesses expand globally, project managers will need to manage cross-border projects, navigate international regulations, and work with diverse cultural and linguistic groups.
Predictive Analytics: Project managers will increasingly use data-driven insights to make informed decisions, anticipate project risks, and optimize resource allocation.
Emphasis on Soft Skills: As technology handles repetitive tasks, soft skills such as leadership, communication, emotional intelligence, and conflict resolution will become even more critical for project managers.
Certifications and Professional Development: Continuous learning and the acquisition of relevant certifications, such as Agile or specialized industry certifications, will be essential to stay competitive in the field.
Hybrid Work Models: A mix of remote and in-person work will likely become more common, and project managers will need to adapt their management styles accordingly.
Resilience and Risk Management: Given the increasing frequency of disruptive events like pandemics and climate-related crises, project managers will need to focus on building resilience and robust risk management strategies.
Artificial Intelligence Assistance: AI tools may help automate routine project management tasks, allowing project managers to focus on more strategic and creative aspects of their work.
Conclusion
In conclusion, project management is a dynamic and multifaceted field that offers numerous opportunities for individuals seeking a fulfilling and rewarding career. This article has explored various aspects of project management, including its job market, salary and compensation, required skills and qualifications, career paths and specializations, challenges and stress levels, work-life balance, job satisfaction, and advancement opportunities.
Project management is not only a well-paying profession but also one that plays a pivotal role in ensuring the successful execution of projects in various industries. Project managers are in high demand due to the increasing complexity of projects and the need for effective coordination and leadership.
While project management can be challenging and demanding, professionals in this field have the opportunity to excel by continually developing their skills, managing stress, and achieving a healthy work-life balance
Whether you're considering a career in project management or are an experienced professional seeking to advance your career, a thorough understanding of the job market, necessary skills, and opportunities for growth is vital. Project management is a profession that offers both personal fulfillment and the chance to contribute significantly to the success of organizations and projects across the globe.
Java 3D Graphics Programming
In the dynamic landscape of software development, where the demand for visually compelling applications continues to rise, the synergy of Java and 3D graphics programming emerges as a potent force. Beyond its conventional role in application development, Java proves to be a versatile language capable of creating immersive visual experiences. This blog series, "Java 3D Graphics Programming," invites you to embark on a journey where code and creativity converge, unlocking the potential to craft captivating visualizations within the Java ecosystem.
Java's prowess extends far beyond its reputation as a reliable programming language. In the realm of 3D graphics, Java shines as a formidable contender, offering a robust set of tools to breathe life into diverse applications. Whether you're venturing into game development, exploring scientific visualizations, or seeking to elevate user engagement through dynamic interfaces, the 3D graphics capabilities of Java provide a canvas limited only by imagination.
Over the course of this series, we will delve into the core concepts, techniques, and best practices that constitute Java 3D graphics programming. Each installment will unravel a layer of complexity, starting from the basics and progressing to advanced topics. From setting up your development environment and understanding the rendering pipeline to exploring shaders and implementing interactive elements, we aim to provide a comprehensive guide for developers eager to harness the potential of 3D graphics in Java.
Table of contents
-
Introduction to Java 3D Graphics:
-
Setting Up Your Development Environment:
-
Creating Your First 3D Scene:
-
Rendering and Transformations:
-
Lights, Camera, Action: Illuminating Scenes in 3D:
-
Textures and Materials in Java 3D:
-
Handling User Input in 3D Environments:
-
Advanced Techniques: Shaders and Special Effects:
-
Optimizing Performance in Java 3D Graphics:
-
Case Studies: Real-world Applications of Java 3D Graphics:
-
Conclusion
Introduction to Java 3D Graphics:
"Java 3D Graphics Programming," a voyage into the realm where Java's versatility converges with the captivating world of three-dimensional visualizations. In the expansive landscape of software development, Java transcends its traditional roles and emerges as a powerful tool for crafting immersive and dynamic visual experiences. This series serves as a gateway for developers and enthusiasts alike, inviting them to explore the expressive canvas of 3D graphics within the Java ecosystem.
In this initial chapter, we lay the groundwork by delving into the essence of Java 3D graphics. We will trace the evolution of the Java 3D API and elucidate its importance, providing an overview of the key components that define its capabilities. As we progress, this series promises to unfold a series of engaging discussions and practical tutorials, guiding you from the basics of setting up your development environment to the intricacies of advanced techniques like shaders and special effects.
This journey is designed for a diverse audience – from seasoned Java developers eager to expand their skill set to newcomers with a passion for visual arts in programming. While a fundamental understanding of Java is advantageous, our commitment is to make the content accessible, ensuring that learners at various levels can benefit from the exploration into the world of "Java 3D Graphics Programming." Join us as we embark on this thrilling adventure, where lines of code transform into dynamic visual narratives, breathing life into applications and unlocking the boundless potential of visual creativity.
Setting Up Your Development Environment
Setting up your development environment is the crucial first stride towards unlocking the dynamic world of Java 3D graphics programming. To embark on this journey seamlessly, begin by installing the latest Java Development Kit (JDK) on your machine, ensuring compatibility with the subsequent steps. Selecting an Integrated Development Environment (IDE) tailored to your preferences, such as Eclipse or IntelliJ IDEA, follows suit, with the IDE configured to recognize the installed JDK. Central to the setup is the incorporation of the Java 3D library, an extension vital for three-dimensional visualizations. Whether manually downloading the library from the official website or leveraging dependency management tools like Maven or Gradle, this step is pivotal to integrating Java 3D into your projects effectively.
As you venture into the realm of 3D graphics, consider employing tools like Blender or Unity for creating intricate 3D models and scenes, enriching your development toolkit. Once your environment is configured, it's imperative to conduct verification tests, ensuring your setup is error-free. Start with a simple Java 3D project, perhaps displaying a basic 3D shape, to guarantee that your development environment compiles and runs seamlessly.
To fortify your knowledge base, delve into the official Java 3D documentation and explore additional resources such as tutorials and community forums. These valuable references will serve as guiding lights, aiding you as you progress in your Java 3D graphics programming journey. With a meticulously set up development environment, you're now poised to delve into the creative and dynamic realm of Java 3D, where lines of code transform into immersive visual narratives.
Creating Your First 3D Scene:
Embarking on the exciting path of Java 3D graphics programming, "Creating Your First 3D Scene" is a pivotal step that bridges theoretical understanding with hands-on application. In this phase, we transition from the preparatory steps of setting up the development environment to the practical realization of a dynamic three-dimensional space using Java code.
Begin by conceptualizing the elements that will populate your 3D environment. Whether it's geometric shapes, intricate objects, or textured surfaces, envision the scene you want to bring to life. This creative visualization forms the blueprint for your coding endeavors.
Navigate through the Java 3D API to instantiate and manipulate the objects that will compose your scene. Key components like TransformGroups and Shapes become your tools for positioning and shaping entities within the virtual space. Consider incorporating lighting effects to introduce depth and realism to your scene.
Creating your first 3D scene is more than a technical accomplishment – it's a creative expression of your vision within the realm of Java 3D graphics. Embrace the iterative nature of coding, experiment with different elements, and relish the transformation of lines of code into a visually immersive world. This initial step marks a significant milestone in your exploration of Java's visual capabilities, laying the foundation for further creativity and innovation in the realm of 3D graphics programming.
Rendering and Transformations:
In the intricate world of Java 3D graphics programming, mastering "Rendering and Transformations" stands as a crucial chapter where static entities come to life through dynamic visual representation. This segment delves into the core concepts of rendering and transformations, unveiling the mechanisms by which objects are brought to fruition within a three-dimensional space.
Rendering in Java 3D involves the translation of abstract entities into tangible visual elements on the screen. It encompasses the processes of shading, lighting, and projecting objects to create a realistic and visually appealing scene. Understanding the rendering pipeline and its various stages becomes paramount in manipulating how your 3D scene is ultimately perceived by the viewer.
As you delve into the practical application of rendering and transformations, experiment with different rendering techniques to achieve desired visual effects. Witness how transformations can breathe life into your 3D scene, allowing you to create immersive and interactive visual narratives.
Throughout this exploration, embrace the iterative nature of the creative process. Expect challenges, engage in experimentation, and refine your understanding of rendering and transformations through hands-on experience. By mastering these fundamental concepts, you pave the way for more advanced and nuanced expressions of creativity in the dynamic realm of Java 3D graphics programming.
Lights, Camera, Action: Illuminating Scenes in 3D:
In the captivating landscape of Java 3D graphics programming, "Lights, Camera, Action: Illuminating Scenes in 3D" introduces a pivotal chapter where the transformative power of lighting takes center stage. This section explores how strategic lighting configurations can breathe life into three-dimensional scenes, enhancing visual depth and realism.
Understanding the nuances of lighting in a 3D environment is essential for creating visually compelling scenes. Various types of lights, including ambient, directional, point, and spotlights, each contribute to the overall ambiance and mood of your scene. This chapter delves into the intricacies of configuring lights, adjusting their properties, and strategically placing them to achieve desired visual effects.
The camera, acting as the audience's viewpoint, is another critical element in the cinematography of 3D graphics. This segment explores the principles of configuring the camera in Java 3D, determining its position, orientation, and field of view. Crafting a well-composed visual experience involves aligning the camera's perspective with your creative vision, and this section guides you through the process.
Through hands-on exploration and experimentation, you'll not only gain proficiency in illuminating 3D scenes but also cultivate an artistic sensibility for orchestrating visually engaging compositions. "Lights, Camera, Action" sets the stage for a cinematic experience within the realm of Java 3D graphics programming, empowering you to infuse your creations with the captivating play of light and shadow.
Textures and Materials in Java 3D:
"Textures and Materials in Java 3D" brings forth a captivating chapter in the realm of three-dimensional visualizations, exploring the art of enhancing surfaces and materials to elevate the realism and aesthetic appeal of your scenes. This segment delves into the intricacies of incorporating textures and materials within Java 3D, offering a palette of tools to infuse your creations with depth, detail, and visual richness.
Textures play a pivotal role in adding realism to 3D objects by wrapping them in images or patterns. This section guides you through the process of applying textures to surfaces, whether it be mapping an image onto a geometric shape or creating intricate patterns to simulate various materials. Understanding texture coordinates, filtering, and mapping techniques will empower you to create visually stunning and lifelike surfaces.
Materials, on the other hand, dictate how surfaces react to light, influencing their appearance and reflectivity. Java 3D provides a range of material properties that allow you to craft surfaces with different levels of shininess, transparency, and color. This chapter explores the manipulation of material attributes, offering insights into creating surfaces that respond dynamically to lighting conditions.
Throughout this exploration, experiment with combining textures and materials to achieve nuanced visual effects. Whether it's simulating the roughness of a stone surface or the smoothness of polished metal, the fusion of textures and materials grants you the creative freedom to evoke specific sensations within your 3D environment.
As you delve into the intricacies of textures and materials, consider the impact of these elements on the overall narrative of your scenes. Witness how surfaces come to life with the application of textures, and observe the subtle changes in appearance as materials interact with light sources. "Textures and Materials in Java 3D" is a gateway to infusing your creations with visual richness, opening up new dimensions of creativity within the dynamic realm of Java 3D graphics programming.
Advanced Techniques: Shaders and Special Effects:
"Advanced Techniques: Shaders and Special Effects" marks a pinnacle in your journey through Java 3D graphics programming, as we delve into the realm of cutting-edge techniques that elevate your creations to new heights. This section explores the powerful world of shaders and special effects, enabling you to unleash unparalleled visual sophistication and dynamism within your 3D scenes.
Shaders, the backbone of modern graphics programming, allow for fine-grained control over the rendering pipeline. This chapter delves into the principles and implementation of shaders in Java 3D, providing insights into vertex and fragment shaders. Explore how shaders empower you to manipulate lighting, shadows, and visual effects, pushing the boundaries of realism and creativity in your 3D environments.
Experimentation becomes key as you harness the potential of shaders and special effects to breathe life into your 3D worlds. Whether you're creating a cinematic sequence, a game environment, or a simulation, these advanced techniques open up avenues for expressing your artistic vision and pushing the boundaries of what's achievable within Java 3D graphics programming.
Consider the impact of shaders and special effects on the overall narrative of your scenes. From simulating realistic water reflections to creating mesmerizing particle animations, these techniques allow you to craft visual stories that captivate and astonish. "Advanced Techniques: Shaders and Special Effects" is your gateway to the forefront of graphics programming, offering the tools to transform your 3D creations into immersive masterpieces.
Optimizing Performance in Java 3D Graphics:
"Optimizing Performance in Java 3D Graphics" stands as a critical chapter in the journey of crafting efficient and responsive three-dimensional visualizations. This section delves into strategies and techniques aimed at fine-tuning your Java 3D applications, ensuring optimal performance and a seamless user experience.
Performance optimization in Java 3D begins with a comprehensive understanding of the rendering pipeline and the underlying mechanisms that contribute to computational load. This chapter explores techniques for reducing rendering complexity, managing resources efficiently, and streamlining the overall rendering process. By implementing efficient algorithms and data structures, you can significantly enhance the speed and responsiveness of your 3D graphics.
One key consideration in performance optimization is the judicious use of memory. Learn techniques for optimizing memory usage, such as smart resource management, minimizing unnecessary object creation, and employing appropriate data structures. Effective memory management not only contributes to smoother performance but also ensures the scalability of your Java 3D applications.
Benchmarking and profiling tools become essential companions in the optimization process. Learn how to identify performance bottlenecks, measure frame rates, and analyze resource usage to pinpoint areas for improvement. Through systematic testing and refinement, you can iteratively enhance the efficiency of your Java 3D applications.
"Optimizing Performance in Java 3D Graphics" empowers you to elevate your 3D creations by ensuring they run smoothly and efficiently across a spectrum of devices. Through meticulous attention to performance considerations, you can deliver an immersive and responsive user experience, making your Java 3D applications stand out for their visual brilliance and technical prowess.
Case Studies: Real-world Applications of Java 3D Graphics
"Case Studies: Real-world Applications of Java 3D Graphics" delves into the practical applications of Java 3D graphics, showcasing how this versatile technology is harnessed in diverse industries to create impactful and visually compelling solutions. This section offers a glimpse into real-world scenarios where Java 3D graphics plays a pivotal role, demonstrating its versatility and applicability.
Scientific Visualization:Explore how Java 3D graphics is employed in scientific research and data analysis. Case studies may include visualizing complex datasets, molecular structures, or simulations for researchers and scientists.
Architectural Visualization:Dive into the realm of architectural design, where Java 3D graphics aids in creating realistic visualizations of buildings, interiors, and urban landscapes. Case studies could illustrate how architects leverage Java 3D for client presentations and project planning.
Gaming and Entertainment:Explore how Java 3D graphics contributes to the gaming and entertainment industry. Case studies could showcase the development of interactive games, virtual reality experiences, or immersive simulations using Java 3D.
Product Design and Prototyping:Showcase how Java 3D graphics is utilized in product design, allowing engineers and designers to create realistic prototypes and visualizations before physical production. Case studies may include applications in automotive design, industrial machinery, and consumer products.
Virtual Tours and Simulations:Explore the use of Java 3D graphics in creating virtual tours and simulations for industries such as tourism, real estate, and historical preservation. Case studies could illustrate how Java 3D enhances the user experience in navigating virtual environments.
Each case study offers a tangible example of Java 3D graphics making a significant impact, providing inspiration and insights into the diverse applications of this technology across various domains. By examining real-world scenarios, developers can glean valuable lessons and apply best practices to their own Java 3D graphics projects.
Conclusion
In conclusion, "Java 3D Graphics Programming" unveils a captivating journey into the dynamic world where code transforms into immersive visual experiences. Through the exploration of foundational concepts, hands-on tutorials, and a glimpse into real-world applications, this series aims to empower developers to harness the full potential of Java in crafting compelling three-dimensional worlds.
The journey progressed into the realm of user interaction, enabling dynamic engagement with 3D environments. As we advanced, the series unveiled the secrets of advanced techniques, exploring shaders and special effects that elevate the visual sophistication of our scenes. The imperative task of optimizing performance ensures that our applications not only dazzle visually but also run seamlessly across diverse hardware configurations.
As we conclude this series, the world of Java 3D graphics beckons with endless possibilities. Armed with the knowledge gained throughout this exploration, developers are equipped to venture into the creative space where lines of code become visual narratives, and where Java proves itself not just as a programming language but as a gateway to a vibrant and visually stunning world of innovation. Whether you're developing games, simulations, educational tools, or groundbreaking visualizations, Java 3D graphics programming empowers you to transcend boundaries and bring your digital creations to life in three-dimensional splendor. Happy coding, and may your Java 3D journey be as limitless as your imagination.
Read More
In the dynamic landscape of software development, where the demand for visually compelling applications continues to rise, the synergy of Java and 3D graphics programming emerges as a potent force. Beyond its conventional role in application development, Java proves to be a versatile language capable of creating immersive visual experiences. This blog series, "Java 3D Graphics Programming," invites you to embark on a journey where code and creativity converge, unlocking the potential to craft captivating visualizations within the Java ecosystem.
Java's prowess extends far beyond its reputation as a reliable programming language. In the realm of 3D graphics, Java shines as a formidable contender, offering a robust set of tools to breathe life into diverse applications. Whether you're venturing into game development, exploring scientific visualizations, or seeking to elevate user engagement through dynamic interfaces, the 3D graphics capabilities of Java provide a canvas limited only by imagination.
Over the course of this series, we will delve into the core concepts, techniques, and best practices that constitute Java 3D graphics programming. Each installment will unravel a layer of complexity, starting from the basics and progressing to advanced topics. From setting up your development environment and understanding the rendering pipeline to exploring shaders and implementing interactive elements, we aim to provide a comprehensive guide for developers eager to harness the potential of 3D graphics in Java.
Table of contents
-
Introduction to Java 3D Graphics:
-
Setting Up Your Development Environment:
-
Creating Your First 3D Scene:
-
Rendering and Transformations:
-
Lights, Camera, Action: Illuminating Scenes in 3D:
-
Textures and Materials in Java 3D:
-
Handling User Input in 3D Environments:
-
Advanced Techniques: Shaders and Special Effects:
-
Optimizing Performance in Java 3D Graphics:
-
Case Studies: Real-world Applications of Java 3D Graphics:
-
Conclusion
Introduction to Java 3D Graphics:
"Java 3D Graphics Programming," a voyage into the realm where Java's versatility converges with the captivating world of three-dimensional visualizations. In the expansive landscape of software development, Java transcends its traditional roles and emerges as a powerful tool for crafting immersive and dynamic visual experiences. This series serves as a gateway for developers and enthusiasts alike, inviting them to explore the expressive canvas of 3D graphics within the Java ecosystem.
In this initial chapter, we lay the groundwork by delving into the essence of Java 3D graphics. We will trace the evolution of the Java 3D API and elucidate its importance, providing an overview of the key components that define its capabilities. As we progress, this series promises to unfold a series of engaging discussions and practical tutorials, guiding you from the basics of setting up your development environment to the intricacies of advanced techniques like shaders and special effects.
This journey is designed for a diverse audience – from seasoned Java developers eager to expand their skill set to newcomers with a passion for visual arts in programming. While a fundamental understanding of Java is advantageous, our commitment is to make the content accessible, ensuring that learners at various levels can benefit from the exploration into the world of "Java 3D Graphics Programming." Join us as we embark on this thrilling adventure, where lines of code transform into dynamic visual narratives, breathing life into applications and unlocking the boundless potential of visual creativity.
Setting Up Your Development Environment
Setting up your development environment is the crucial first stride towards unlocking the dynamic world of Java 3D graphics programming. To embark on this journey seamlessly, begin by installing the latest Java Development Kit (JDK) on your machine, ensuring compatibility with the subsequent steps. Selecting an Integrated Development Environment (IDE) tailored to your preferences, such as Eclipse or IntelliJ IDEA, follows suit, with the IDE configured to recognize the installed JDK. Central to the setup is the incorporation of the Java 3D library, an extension vital for three-dimensional visualizations. Whether manually downloading the library from the official website or leveraging dependency management tools like Maven or Gradle, this step is pivotal to integrating Java 3D into your projects effectively.
As you venture into the realm of 3D graphics, consider employing tools like Blender or Unity for creating intricate 3D models and scenes, enriching your development toolkit. Once your environment is configured, it's imperative to conduct verification tests, ensuring your setup is error-free. Start with a simple Java 3D project, perhaps displaying a basic 3D shape, to guarantee that your development environment compiles and runs seamlessly.
To fortify your knowledge base, delve into the official Java 3D documentation and explore additional resources such as tutorials and community forums. These valuable references will serve as guiding lights, aiding you as you progress in your Java 3D graphics programming journey. With a meticulously set up development environment, you're now poised to delve into the creative and dynamic realm of Java 3D, where lines of code transform into immersive visual narratives.
Creating Your First 3D Scene:
Embarking on the exciting path of Java 3D graphics programming, "Creating Your First 3D Scene" is a pivotal step that bridges theoretical understanding with hands-on application. In this phase, we transition from the preparatory steps of setting up the development environment to the practical realization of a dynamic three-dimensional space using Java code.
Begin by conceptualizing the elements that will populate your 3D environment. Whether it's geometric shapes, intricate objects, or textured surfaces, envision the scene you want to bring to life. This creative visualization forms the blueprint for your coding endeavors.
Navigate through the Java 3D API to instantiate and manipulate the objects that will compose your scene. Key components like TransformGroups and Shapes become your tools for positioning and shaping entities within the virtual space. Consider incorporating lighting effects to introduce depth and realism to your scene.
Creating your first 3D scene is more than a technical accomplishment – it's a creative expression of your vision within the realm of Java 3D graphics. Embrace the iterative nature of coding, experiment with different elements, and relish the transformation of lines of code into a visually immersive world. This initial step marks a significant milestone in your exploration of Java's visual capabilities, laying the foundation for further creativity and innovation in the realm of 3D graphics programming.
Rendering and Transformations:
In the intricate world of Java 3D graphics programming, mastering "Rendering and Transformations" stands as a crucial chapter where static entities come to life through dynamic visual representation. This segment delves into the core concepts of rendering and transformations, unveiling the mechanisms by which objects are brought to fruition within a three-dimensional space.
Rendering in Java 3D involves the translation of abstract entities into tangible visual elements on the screen. It encompasses the processes of shading, lighting, and projecting objects to create a realistic and visually appealing scene. Understanding the rendering pipeline and its various stages becomes paramount in manipulating how your 3D scene is ultimately perceived by the viewer.
As you delve into the practical application of rendering and transformations, experiment with different rendering techniques to achieve desired visual effects. Witness how transformations can breathe life into your 3D scene, allowing you to create immersive and interactive visual narratives.
Throughout this exploration, embrace the iterative nature of the creative process. Expect challenges, engage in experimentation, and refine your understanding of rendering and transformations through hands-on experience. By mastering these fundamental concepts, you pave the way for more advanced and nuanced expressions of creativity in the dynamic realm of Java 3D graphics programming.
Lights, Camera, Action: Illuminating Scenes in 3D:
In the captivating landscape of Java 3D graphics programming, "Lights, Camera, Action: Illuminating Scenes in 3D" introduces a pivotal chapter where the transformative power of lighting takes center stage. This section explores how strategic lighting configurations can breathe life into three-dimensional scenes, enhancing visual depth and realism.
Understanding the nuances of lighting in a 3D environment is essential for creating visually compelling scenes. Various types of lights, including ambient, directional, point, and spotlights, each contribute to the overall ambiance and mood of your scene. This chapter delves into the intricacies of configuring lights, adjusting their properties, and strategically placing them to achieve desired visual effects.
The camera, acting as the audience's viewpoint, is another critical element in the cinematography of 3D graphics. This segment explores the principles of configuring the camera in Java 3D, determining its position, orientation, and field of view. Crafting a well-composed visual experience involves aligning the camera's perspective with your creative vision, and this section guides you through the process.
Through hands-on exploration and experimentation, you'll not only gain proficiency in illuminating 3D scenes but also cultivate an artistic sensibility for orchestrating visually engaging compositions. "Lights, Camera, Action" sets the stage for a cinematic experience within the realm of Java 3D graphics programming, empowering you to infuse your creations with the captivating play of light and shadow.
Textures and Materials in Java 3D:
"Textures and Materials in Java 3D" brings forth a captivating chapter in the realm of three-dimensional visualizations, exploring the art of enhancing surfaces and materials to elevate the realism and aesthetic appeal of your scenes. This segment delves into the intricacies of incorporating textures and materials within Java 3D, offering a palette of tools to infuse your creations with depth, detail, and visual richness.
Textures play a pivotal role in adding realism to 3D objects by wrapping them in images or patterns. This section guides you through the process of applying textures to surfaces, whether it be mapping an image onto a geometric shape or creating intricate patterns to simulate various materials. Understanding texture coordinates, filtering, and mapping techniques will empower you to create visually stunning and lifelike surfaces.
Materials, on the other hand, dictate how surfaces react to light, influencing their appearance and reflectivity. Java 3D provides a range of material properties that allow you to craft surfaces with different levels of shininess, transparency, and color. This chapter explores the manipulation of material attributes, offering insights into creating surfaces that respond dynamically to lighting conditions.
Throughout this exploration, experiment with combining textures and materials to achieve nuanced visual effects. Whether it's simulating the roughness of a stone surface or the smoothness of polished metal, the fusion of textures and materials grants you the creative freedom to evoke specific sensations within your 3D environment.
As you delve into the intricacies of textures and materials, consider the impact of these elements on the overall narrative of your scenes. Witness how surfaces come to life with the application of textures, and observe the subtle changes in appearance as materials interact with light sources. "Textures and Materials in Java 3D" is a gateway to infusing your creations with visual richness, opening up new dimensions of creativity within the dynamic realm of Java 3D graphics programming.
Advanced Techniques: Shaders and Special Effects:
"Advanced Techniques: Shaders and Special Effects" marks a pinnacle in your journey through Java 3D graphics programming, as we delve into the realm of cutting-edge techniques that elevate your creations to new heights. This section explores the powerful world of shaders and special effects, enabling you to unleash unparalleled visual sophistication and dynamism within your 3D scenes.
Shaders, the backbone of modern graphics programming, allow for fine-grained control over the rendering pipeline. This chapter delves into the principles and implementation of shaders in Java 3D, providing insights into vertex and fragment shaders. Explore how shaders empower you to manipulate lighting, shadows, and visual effects, pushing the boundaries of realism and creativity in your 3D environments.
Experimentation becomes key as you harness the potential of shaders and special effects to breathe life into your 3D worlds. Whether you're creating a cinematic sequence, a game environment, or a simulation, these advanced techniques open up avenues for expressing your artistic vision and pushing the boundaries of what's achievable within Java 3D graphics programming.
Consider the impact of shaders and special effects on the overall narrative of your scenes. From simulating realistic water reflections to creating mesmerizing particle animations, these techniques allow you to craft visual stories that captivate and astonish. "Advanced Techniques: Shaders and Special Effects" is your gateway to the forefront of graphics programming, offering the tools to transform your 3D creations into immersive masterpieces.
Optimizing Performance in Java 3D Graphics:
"Optimizing Performance in Java 3D Graphics" stands as a critical chapter in the journey of crafting efficient and responsive three-dimensional visualizations. This section delves into strategies and techniques aimed at fine-tuning your Java 3D applications, ensuring optimal performance and a seamless user experience.
Performance optimization in Java 3D begins with a comprehensive understanding of the rendering pipeline and the underlying mechanisms that contribute to computational load. This chapter explores techniques for reducing rendering complexity, managing resources efficiently, and streamlining the overall rendering process. By implementing efficient algorithms and data structures, you can significantly enhance the speed and responsiveness of your 3D graphics.
One key consideration in performance optimization is the judicious use of memory. Learn techniques for optimizing memory usage, such as smart resource management, minimizing unnecessary object creation, and employing appropriate data structures. Effective memory management not only contributes to smoother performance but also ensures the scalability of your Java 3D applications.
Benchmarking and profiling tools become essential companions in the optimization process. Learn how to identify performance bottlenecks, measure frame rates, and analyze resource usage to pinpoint areas for improvement. Through systematic testing and refinement, you can iteratively enhance the efficiency of your Java 3D applications.
"Optimizing Performance in Java 3D Graphics" empowers you to elevate your 3D creations by ensuring they run smoothly and efficiently across a spectrum of devices. Through meticulous attention to performance considerations, you can deliver an immersive and responsive user experience, making your Java 3D applications stand out for their visual brilliance and technical prowess.
Case Studies: Real-world Applications of Java 3D Graphics
"Case Studies: Real-world Applications of Java 3D Graphics" delves into the practical applications of Java 3D graphics, showcasing how this versatile technology is harnessed in diverse industries to create impactful and visually compelling solutions. This section offers a glimpse into real-world scenarios where Java 3D graphics plays a pivotal role, demonstrating its versatility and applicability.
Scientific Visualization:Explore how Java 3D graphics is employed in scientific research and data analysis. Case studies may include visualizing complex datasets, molecular structures, or simulations for researchers and scientists.
Architectural Visualization:Dive into the realm of architectural design, where Java 3D graphics aids in creating realistic visualizations of buildings, interiors, and urban landscapes. Case studies could illustrate how architects leverage Java 3D for client presentations and project planning.
Gaming and Entertainment:Explore how Java 3D graphics contributes to the gaming and entertainment industry. Case studies could showcase the development of interactive games, virtual reality experiences, or immersive simulations using Java 3D.
Product Design and Prototyping:Showcase how Java 3D graphics is utilized in product design, allowing engineers and designers to create realistic prototypes and visualizations before physical production. Case studies may include applications in automotive design, industrial machinery, and consumer products.
Virtual Tours and Simulations:Explore the use of Java 3D graphics in creating virtual tours and simulations for industries such as tourism, real estate, and historical preservation. Case studies could illustrate how Java 3D enhances the user experience in navigating virtual environments.
Each case study offers a tangible example of Java 3D graphics making a significant impact, providing inspiration and insights into the diverse applications of this technology across various domains. By examining real-world scenarios, developers can glean valuable lessons and apply best practices to their own Java 3D graphics projects.
Conclusion
In conclusion, "Java 3D Graphics Programming" unveils a captivating journey into the dynamic world where code transforms into immersive visual experiences. Through the exploration of foundational concepts, hands-on tutorials, and a glimpse into real-world applications, this series aims to empower developers to harness the full potential of Java in crafting compelling three-dimensional worlds.
The journey progressed into the realm of user interaction, enabling dynamic engagement with 3D environments. As we advanced, the series unveiled the secrets of advanced techniques, exploring shaders and special effects that elevate the visual sophistication of our scenes. The imperative task of optimizing performance ensures that our applications not only dazzle visually but also run seamlessly across diverse hardware configurations.
As we conclude this series, the world of Java 3D graphics beckons with endless possibilities. Armed with the knowledge gained throughout this exploration, developers are equipped to venture into the creative space where lines of code become visual narratives, and where Java proves itself not just as a programming language but as a gateway to a vibrant and visually stunning world of innovation. Whether you're developing games, simulations, educational tools, or groundbreaking visualizations, Java 3D graphics programming empowers you to transcend boundaries and bring your digital creations to life in three-dimensional splendor. Happy coding, and may your Java 3D journey be as limitless as your imagination.
Overview of Digital Marketing Certification Programs
In the rapidly evolving landscape of digital marketing, staying ahead of the curve is crucial for professionals aspiring to make a mark in the industry. Digital marketing certification programs have emerged as invaluable tools for individuals seeking to enhance their skills, validate their expertise, and gain a competitive edge in the job market. In this comprehensive overview, we'll delve into the world of digital marketing certifications, exploring the myriad options available and shedding light on the significance of these programs in today's dynamic business environment.
Digital marketing certifications encompass a diverse range of modules, each designed to cover essential aspects of online marketing, from search engine optimization (SEO) and social media marketing to analytics and content strategy. These programs not only serve as structured learning paths but also provide a standardized means of assessment, ensuring that certified professionals possess a well-rounded understanding of the multifaceted realm of digital marketing.
This overview will guide you through the considerations involved in choosing a certification program, whether you're a seasoned professional looking to upskill or a newcomer eager to establish a foothold in the industry. From exploring the content and structure of popular certification courses to understanding the broader implications of being certified, this series aims to be your go-to resource for navigating the diverse landscape of digital marketing certifications. Join us on this journey as we unravel the opportunities, challenges, and transformative potential of digital marketing certification programs.
Table of contents
-
Key Digital Marketing Certification Providers
-
Choosing the Right Certification for Your Career Goals
-
Examining the Curriculum
-
Certification Levels and Specializations
-
Industry Recognition and Credibility
-
Online vs In-Person Certification Programs
-
Practical Application and Real-World Projects
-
Cost and Time Considerations
-
Success Stories and Testimonials
-
Maintaining Certification Relevance in a Changing Landscape
-
Conclusion
Key Digital Marketing Certification Providers
In the dynamic landscape of digital marketing, several reputable certification providers offer comprehensive programs designed to equip professionals with the skills needed to thrive in the ever-evolving online space. Here are key digital marketing certification providers
Google Digital Garage:Google offers a range of free courses through its Digital Garage platform. Courses cover various aspects of digital marketing, including search engine optimization (SEO), social media, and analytics.
HubSpot Academy:HubSpot provides a comprehensive set of free certification courses on inbound marketing, content marketing, social media strategy, and more. Their certifications are well-regarded in the marketing community.
LinkedIn Learning (formerly Lynda.com):LinkedIn Learning provides a variety of courses on digital marketing, with a focus on skill development. Courses cover SEO, content marketing, email marketing, and more.
Semrush Academy:Semrush, a tool for SEO and online visibility management, provides a certification program covering the use of their platform as well as broader digital marketing topics.
Content Marketing Institute (CMI):CMI offers a content marketing certification program that covers content strategy, creation, and distribution. It's ideal for professionals looking to specialize in content marketing.
Simplilearn:Simplilearn offers a variety of digital marketing courses and certification programs. They cover topics like SEO, social media, pay-per-click (PPC), and digital strategy.
Microsoft Advertising Certification:Microsoft Advertising offers a certification program covering their advertising platform. It includes topics such as search engine marketing (SEM), display advertising, and analytics.
Choosing the Right Certification for Your Career Goals
Embarking on a journey to choose the right digital marketing certification is a crucial step in shaping a successful career in the ever-evolving landscape of online marketing. To navigate this decision effectively, it's essential to align your certification choice with your unique career goals and aspirations within the diverse field of digital marketing.
As you delve into the myriad of certification options available, carefully research the specializations offered by each program. Certifications often cater to specific aspects of digital marketing, and understanding the content focus will help you pinpoint the most relevant and impactful certification for your chosen path. Platforms like Facebook Blueprint or Hootsuite Academy may be particularly beneficial for those seeking expertise in social media marketing, while broader certifications from reputable providers like Google Digital Garage cover a spectrum of digital marketing disciplines.
Consider the industry recognition and reputation of the certification programs under consideration. Opting for certifications from well-established providers, such as Google Digital Garage, HubSpot, or Digital Marketing Institute, can enhance your credibility in the eyes of potential employers. A certification's standing within the industry is a valuable asset, opening doors to opportunities and signaling a commitment to excellence in the field.
Evaluate the structure and format of the certification programs to ensure they align with your preferred learning style and schedule. Whether you thrive in self-paced online courses or prefer the structure of live sessions, choosing a format that suits your needs is crucial for a successful learning experience. Additionally, assess whether the program incorporates practical, hands-on components, as these can significantly enhance your ability to apply learned skills in real-world scenarios.
Certification levels also play a pivotal role in the decision-making process. Some programs offer different levels, catering to individuals at various stages of their careers. Assess your current skill level and opt for a certification that matches your expertise, with the flexibility to progress to more advanced levels as you gain experience.
Budget constraints and accessibility are practical considerations that should not be overlooked. While some certifications, such as those from Google Digital Garage, offer free courses, others may involve costs. Ensure that the chosen certification aligns with your budget and is accessible in terms of time commitment and scheduling.
By thoughtfully considering these factors, you can make a well-informed decision when choosing the right digital marketing certification for your career goals. Remember that the certification you select should not only enhance your skill set but also align with your professional aspirations, setting the stage for a fulfilling and successful career in digital marketing.
Examining the Curriculum
Examining the curriculum of a digital marketing certification program is a critical step in ensuring that the educational content aligns with your learning objectives and professional aspirations. Begin by exploring the breadth and depth of the topics covered within the program. A well-rounded curriculum should encompass key aspects of digital marketing, including search engine optimization (SEO), social media marketing, email marketing, content strategy, and analytics.
Delve into the specifics of each module to understand the depth of coverage. For instance, in SEO, examine whether the curriculum addresses both on-page and off-page optimization techniques, keyword research strategies, and the latest trends in search engine algorithms. Similarly, in social media marketing, assess whether the program covers platforms comprehensively, explores paid advertising strategies, and includes insights into audience engagement and analytics.
In summary, scrutinizing the curriculum of a digital marketing certification program is a meticulous process that involves assessing the comprehensiveness, practicality, currency, flexibility, and continuous learning aspects of the educational content. By ensuring that the curriculum aligns with your specific learning objectives and industry demands, you can make an informed decision that propels you toward a successful and fulfilling career in digital marketing.
Certification Levels and Specializations
Understanding the certification levels and specializations within digital marketing is crucial for professionals seeking to tailor their learning experience to their specific career goals and expertise. Digital marketing certification programs often offer different levels of proficiency and opportunities for specialization to cater to the diverse needs of learners.
Certification levels typically range from foundational or beginner to intermediate and advanced. These levels are designed to accommodate individuals at different stages of their careers, ensuring that the content is relevant to their knowledge and experience. Beginners may start with foundational certifications, covering essential concepts and strategies, while experienced marketers may pursue advanced certifications that delve into intricate, specialized areas.
Foundational certifications often introduce learners to the fundamental principles of digital marketing. This may include an overview of key channels such as SEO, social media, email marketing, and basic analytics. These certifications provide a solid understanding of the digital marketing landscape, making them suitable for newcomers or those looking to establish a broad foundation.
Intermediate certifications build upon the foundational knowledge and delve deeper into specific areas of digital marketing. Learners may choose to specialize in disciplines like content marketing, paid advertising, or social media strategy. These certifications aim to enhance expertise in targeted domains while maintaining a comprehensive view of the broader digital marketing ecosystem.
When selecting a digital marketing certification, it's essential to consider both the certification level and any available specializations. Assess your current skill level, career aspirations, and the areas of digital marketing that align with your interests. Choosing a program that offers the right combination of certification level and specialization will ensure a tailored learning experience that adds significant value to your professional journey.
Industry Recognition and Credibility
Industry recognition and credibility are paramount considerations when selecting a digital marketing certification, as these factors play a pivotal role in how your qualifications are perceived by employers, clients, and peers within the competitive landscape of digital marketing. A certification from a recognized and respected institution enhances your professional standing and can open doors to opportunities within the industry.
One key aspect of industry recognition is the reputation of the certification provider. Certifications from well-established and reputable organizations are more likely to be acknowledged and valued by employers. Recognized providers, such as Google Digital Garage, HubSpot, and Digital Marketing Institute, have a track record of delivering high-quality content and staying abreast of industry trends.
Employers often use industry-recognized certifications as a benchmark for evaluating the skills and expertise of candidates. Having a certification from a reputable institution can serve as a tangible demonstration of your commitment to continuous learning and professional development. It provides assurance to employers that you possess a standardized set of skills and knowledge, which is particularly important in a field as dynamic as digital marketing.
Ultimately, the goal is to choose a digital marketing certification that not only imparts valuable knowledge but also holds weight in the eyes of employers and peers. Industry recognition and credibility are powerful assets that can boost your career prospects, increase your employability, and position you as a credible and competent digital marketing professional within the competitive landscape of the industry.
Online vs In-Person Certification Programs
The choice between online and in-person certification programs in digital marketing is a significant decision that depends on various factors, including personal preferences, learning styles, and logistical considerations.
Online Certification Programs:
Flexibility: One of the primary advantages of online certification programs is the flexibility they offer. Learners can access course materials at their own pace and schedule, making it suitable for individuals with varying commitments such as full-time jobs or other responsibilities.
Accessibility: Online programs provide access to a global pool of resources and instructors. Learners can engage with content from industry experts and connect with peers from around the world, fostering a diverse learning environment.
Cost-Effectiveness: Online programs often have lower tuition costs compared to in-person options. Additionally, learners can save on travel, accommodation, and other expenses associated with attending in-person classes.
Diverse Learning Formats: Online programs often incorporate a variety of multimedia elements, such as video lectures, interactive quizzes, and discussion forums, catering to different learning styles.
In-Person Certification Programs:
Real-Time Interaction: In-person programs provide the opportunity for immediate interaction with instructors and fellow learners. This can facilitate a more dynamic learning experience with real-time feedback and discussions.
Structured Learning Environment: Classroom settings offer a structured learning environment with set schedules, which can be beneficial for individuals who thrive in a more regimented and organized setting.
Networking Opportunities: In-person programs provide valuable networking opportunities. Engaging with instructors and classmates face-to-face can lead to meaningful professional connections and collaborations.
Hands-On Experience: Some in-person programs incorporate hands-on activities, workshops, and group projects that may be challenging to replicate in an online format.
Ultimately, the choice between online and in-person certification programs depends on individual preferences, lifestyle, and learning preferences. Some learners may thrive in the flexibility of online programs, while others may benefit more from the structure and personal interaction offered by in-person options. Consider your own learning style, time constraints, and budget when making this decision.
Practical Application and Real-World Projects
Integrating practical application and real-world projects into a digital marketing certification program is a cornerstone in bridging the gap between theoretical knowledge and practical skills. This hands-on approach serves as a catalyst for a more immersive and impactful learning experience, offering learners the opportunity to directly apply acquired concepts in scenarios reflective of the challenges encountered in professional digital marketing environments.
Real-world projects, such as case studies, play a pivotal role in grounding learners in the complexities of the digital marketing landscape. By dissecting and solving actual business challenges, learners gain a nuanced understanding of how theoretical concepts manifest in practical situations. This process not only reinforces theoretical knowledge but also hones problem-solving skills, preparing individuals to navigate the dynamic and ever-evolving field of digital marketing.
Hands-on exercises, ranging from creating and optimizing digital campaigns to analyzing performance metrics, offer learners tangible experiences that mirror the tasks they will encounter in real-world professional settings. These exercises not only develop technical proficiency but also instill a sense of confidence in learners as they apply their knowledge to concrete, actionable projects.
In summary, the inclusion of practical application and real-world projects in a digital marketing certification program is more than a supplement to theoretical learning; it is a cornerstone for cultivating a holistic and industry-ready skill set. These experiences not only prepare learners for the demands of the professional realm but also empower them to confidently navigate the multifaceted landscape of digital marketing upon completion of their certification.
Cost and Time Considerations
Considering the cost and time implications of a digital marketing certification program is crucial for individuals seeking to strike a balance between their educational aspirations, budget constraints, and personal commitments. Both factors play significant roles in shaping the overall feasibility and effectiveness of the certification journey.
Cost Considerations:The cost of a digital marketing certification program varies widely based on factors such as the institution, the level of the certification, and the inclusion of additional features like real-world projects or instructor-led sessions. Some certifications, like those offered by Google Digital Garage, are available for free, providing an accessible entry point for learners on a budget. On the other hand, certifications from well-known institutions or those with specialized content may come with a higher price tag.
In addition to tuition fees, learners should factor in potential additional costs such as study materials, textbooks, or software tools that may be required for the program. Travel expenses, particularly for in-person programs, should also be considered, as attending physical classes or workshops may incur additional costs.
Time Considerations:The time required to complete a digital marketing certification program can vary based on factors such as the level of the certification, the learning format (self-paced or instructor-led), and the individual learner's pace. Some certifications can be completed in a matter of weeks, while others may take several months.
Self-paced online programs offer flexibility in terms of scheduling, allowing learners to balance certification studies with other commitments such as work or family responsibilities. In contrast, in-person or live online programs with fixed schedules may require a more structured time commitment.
Balancing Cost and Time:Ultimately, finding the right balance between cost and time requires careful consideration of personal circumstances and educational goals. While a more affordable program may suit a tight budget, learners should ensure that it still meets their learning objectives and provides a reputable certification. Similarly, an intensive program that demands significant time commitments may be worthwhile for those seeking a comprehensive and immersive learning experience.
Before committing to a digital marketing certification program, individuals should thoroughly research the program's cost structure, available resources, and time requirements. This informed approach ensures that learners can make a strategic investment in their professional development, aligning their educational choices with both budgetary constraints and career aspirations.
Success Stories and Testimonials
Exploring success stories and testimonials is a valuable step in assessing the impact and effectiveness of a digital marketing certification program. Learning from the experiences of individuals who have completed the program provides insights into the tangible benefits, career advancements, and transformative outcomes that others have achieved. Success stories and testimonials offer a glimpse into the real-world impact of the certification on professional journeys.
Gaining Insight into Real-World Application: Success stories often highlight how individuals have applied the knowledge and skills acquired through the certification in their professional roles. These narratives provide concrete examples of how the certification program translated theoretical concepts into practical solutions, campaigns, or strategies within the dynamic field of digital marketing.
Understanding Career Progression: Testimonials frequently shed light on the career progression of individuals who completed the certification. They may detail how the certification acted as a catalyst for job promotions, career transitions, or enhanced job responsibilities. Such insights offer a tangible understanding of the certification's role in career development and marketability within the industry.
Identifying Diverse Perspectives: Testimonials come from a diverse range of individuals with varied backgrounds, experiences, and career goals. Examining testimonials from professionals with different profiles can provide a holistic view of the certification program's applicability across various industry sectors and roles.
Validating Program Quality: Success stories and testimonials serve as endorsements of the program's quality and effectiveness. Positive feedback from those who have successfully navigated the certification adds credibility to the program's curriculum, instructors, and overall educational approach.
Before enrolling in a digital marketing certification program, individuals should actively seek out success stories and testimonials on official program websites, forums, or professional networking platforms. Analyzing these narratives enables prospective learners to make informed decisions based on the real-world experiences of their peers and validates the potential impact of the certification on their own professional journey.
Maintaining Certification Relevance in a Changing Landscape
Maintaining the relevance of a digital marketing certification in a constantly evolving landscape is a critical consideration for both certification providers and professionals seeking to stay abreast of industry advancements. The field of digital marketing is dynamic, with technology, consumer behaviors, and platforms undergoing frequent changes. Ensuring that certification programs adapt to these changes is essential for professionals to acquire skills that align with current industry demands.
Integration of practical, hands-on experiences is another crucial element. Real-world projects, case studies, and simulations should mirror the challenges professionals face in contemporary digital marketing roles. This not only enhances the practical application of knowledge but also ensures that the skills gained are directly transferable to the current industry landscape.
Establishing partnerships with industry leaders and organizations can also contribute to certification relevance. Collaboration with companies at the forefront of digital marketing ensures that certification programs are informed by real-world practices and insights. Industry partnerships can facilitate access to cutting-edge tools, case studies, and expertise that enhance the overall quality and relevance of the certification.
In summary, maintaining certification relevance in the ever-changing digital marketing landscape requires a proactive and adaptive approach. Certification providers must commit to regular updates, modular learning structures, practical experiences, community engagement, industry partnerships, and feedback mechanisms. Simultaneously, professionals should embrace a mindset of continuous learning, leveraging these certification programs as a foundation for ongoing professional development in the dynamic world of digital marketing.
Conclusion
In conclusion, the world of digital marketing is marked by its constant evolution, with technologies, trends, and consumer behaviors continuously shaping the industry's landscape. The pursuit of a digital marketing certification is not merely a one-time achievement but a commitment to ongoing learning and adaptation. As professionals seek to navigate this dynamic environment, choosing a certification program that prioritizes relevance and adaptability is paramount.
Certification providers play a pivotal role in maintaining the currency and effectiveness of their programs. By regularly updating content, embracing modular learning structures, integrating practical experiences, fostering a culture of continuous learning, establishing industry partnerships, and actively seeking feedback from professionals, certification providers can ensure that their offerings remain at the forefront of the digital marketing field.
Read More
In the rapidly evolving landscape of digital marketing, staying ahead of the curve is crucial for professionals aspiring to make a mark in the industry. Digital marketing certification programs have emerged as invaluable tools for individuals seeking to enhance their skills, validate their expertise, and gain a competitive edge in the job market. In this comprehensive overview, we'll delve into the world of digital marketing certifications, exploring the myriad options available and shedding light on the significance of these programs in today's dynamic business environment.
Digital marketing certifications encompass a diverse range of modules, each designed to cover essential aspects of online marketing, from search engine optimization (SEO) and social media marketing to analytics and content strategy. These programs not only serve as structured learning paths but also provide a standardized means of assessment, ensuring that certified professionals possess a well-rounded understanding of the multifaceted realm of digital marketing.
This overview will guide you through the considerations involved in choosing a certification program, whether you're a seasoned professional looking to upskill or a newcomer eager to establish a foothold in the industry. From exploring the content and structure of popular certification courses to understanding the broader implications of being certified, this series aims to be your go-to resource for navigating the diverse landscape of digital marketing certifications. Join us on this journey as we unravel the opportunities, challenges, and transformative potential of digital marketing certification programs.
Table of contents
-
Key Digital Marketing Certification Providers
-
Choosing the Right Certification for Your Career Goals
-
Examining the Curriculum
-
Certification Levels and Specializations
-
Industry Recognition and Credibility
-
Online vs In-Person Certification Programs
-
Practical Application and Real-World Projects
-
Cost and Time Considerations
-
Success Stories and Testimonials
-
Maintaining Certification Relevance in a Changing Landscape
-
Conclusion
Key Digital Marketing Certification Providers
In the dynamic landscape of digital marketing, several reputable certification providers offer comprehensive programs designed to equip professionals with the skills needed to thrive in the ever-evolving online space. Here are key digital marketing certification providers
Google Digital Garage:Google offers a range of free courses through its Digital Garage platform. Courses cover various aspects of digital marketing, including search engine optimization (SEO), social media, and analytics.
HubSpot Academy:HubSpot provides a comprehensive set of free certification courses on inbound marketing, content marketing, social media strategy, and more. Their certifications are well-regarded in the marketing community.
LinkedIn Learning (formerly Lynda.com):LinkedIn Learning provides a variety of courses on digital marketing, with a focus on skill development. Courses cover SEO, content marketing, email marketing, and more.
Semrush Academy:Semrush, a tool for SEO and online visibility management, provides a certification program covering the use of their platform as well as broader digital marketing topics.
Content Marketing Institute (CMI):CMI offers a content marketing certification program that covers content strategy, creation, and distribution. It's ideal for professionals looking to specialize in content marketing.
Simplilearn:Simplilearn offers a variety of digital marketing courses and certification programs. They cover topics like SEO, social media, pay-per-click (PPC), and digital strategy.
Microsoft Advertising Certification:Microsoft Advertising offers a certification program covering their advertising platform. It includes topics such as search engine marketing (SEM), display advertising, and analytics.
Choosing the Right Certification for Your Career Goals
Embarking on a journey to choose the right digital marketing certification is a crucial step in shaping a successful career in the ever-evolving landscape of online marketing. To navigate this decision effectively, it's essential to align your certification choice with your unique career goals and aspirations within the diverse field of digital marketing.
As you delve into the myriad of certification options available, carefully research the specializations offered by each program. Certifications often cater to specific aspects of digital marketing, and understanding the content focus will help you pinpoint the most relevant and impactful certification for your chosen path. Platforms like Facebook Blueprint or Hootsuite Academy may be particularly beneficial for those seeking expertise in social media marketing, while broader certifications from reputable providers like Google Digital Garage cover a spectrum of digital marketing disciplines.
Consider the industry recognition and reputation of the certification programs under consideration. Opting for certifications from well-established providers, such as Google Digital Garage, HubSpot, or Digital Marketing Institute, can enhance your credibility in the eyes of potential employers. A certification's standing within the industry is a valuable asset, opening doors to opportunities and signaling a commitment to excellence in the field.
Evaluate the structure and format of the certification programs to ensure they align with your preferred learning style and schedule. Whether you thrive in self-paced online courses or prefer the structure of live sessions, choosing a format that suits your needs is crucial for a successful learning experience. Additionally, assess whether the program incorporates practical, hands-on components, as these can significantly enhance your ability to apply learned skills in real-world scenarios.
Certification levels also play a pivotal role in the decision-making process. Some programs offer different levels, catering to individuals at various stages of their careers. Assess your current skill level and opt for a certification that matches your expertise, with the flexibility to progress to more advanced levels as you gain experience.
Budget constraints and accessibility are practical considerations that should not be overlooked. While some certifications, such as those from Google Digital Garage, offer free courses, others may involve costs. Ensure that the chosen certification aligns with your budget and is accessible in terms of time commitment and scheduling.
By thoughtfully considering these factors, you can make a well-informed decision when choosing the right digital marketing certification for your career goals. Remember that the certification you select should not only enhance your skill set but also align with your professional aspirations, setting the stage for a fulfilling and successful career in digital marketing.
Examining the Curriculum
Examining the curriculum of a digital marketing certification program is a critical step in ensuring that the educational content aligns with your learning objectives and professional aspirations. Begin by exploring the breadth and depth of the topics covered within the program. A well-rounded curriculum should encompass key aspects of digital marketing, including search engine optimization (SEO), social media marketing, email marketing, content strategy, and analytics.
Delve into the specifics of each module to understand the depth of coverage. For instance, in SEO, examine whether the curriculum addresses both on-page and off-page optimization techniques, keyword research strategies, and the latest trends in search engine algorithms. Similarly, in social media marketing, assess whether the program covers platforms comprehensively, explores paid advertising strategies, and includes insights into audience engagement and analytics.
In summary, scrutinizing the curriculum of a digital marketing certification program is a meticulous process that involves assessing the comprehensiveness, practicality, currency, flexibility, and continuous learning aspects of the educational content. By ensuring that the curriculum aligns with your specific learning objectives and industry demands, you can make an informed decision that propels you toward a successful and fulfilling career in digital marketing.
Certification Levels and Specializations
Understanding the certification levels and specializations within digital marketing is crucial for professionals seeking to tailor their learning experience to their specific career goals and expertise. Digital marketing certification programs often offer different levels of proficiency and opportunities for specialization to cater to the diverse needs of learners.
Certification levels typically range from foundational or beginner to intermediate and advanced. These levels are designed to accommodate individuals at different stages of their careers, ensuring that the content is relevant to their knowledge and experience. Beginners may start with foundational certifications, covering essential concepts and strategies, while experienced marketers may pursue advanced certifications that delve into intricate, specialized areas.
Foundational certifications often introduce learners to the fundamental principles of digital marketing. This may include an overview of key channels such as SEO, social media, email marketing, and basic analytics. These certifications provide a solid understanding of the digital marketing landscape, making them suitable for newcomers or those looking to establish a broad foundation.
Intermediate certifications build upon the foundational knowledge and delve deeper into specific areas of digital marketing. Learners may choose to specialize in disciplines like content marketing, paid advertising, or social media strategy. These certifications aim to enhance expertise in targeted domains while maintaining a comprehensive view of the broader digital marketing ecosystem.
When selecting a digital marketing certification, it's essential to consider both the certification level and any available specializations. Assess your current skill level, career aspirations, and the areas of digital marketing that align with your interests. Choosing a program that offers the right combination of certification level and specialization will ensure a tailored learning experience that adds significant value to your professional journey.
Industry Recognition and Credibility
Industry recognition and credibility are paramount considerations when selecting a digital marketing certification, as these factors play a pivotal role in how your qualifications are perceived by employers, clients, and peers within the competitive landscape of digital marketing. A certification from a recognized and respected institution enhances your professional standing and can open doors to opportunities within the industry.
One key aspect of industry recognition is the reputation of the certification provider. Certifications from well-established and reputable organizations are more likely to be acknowledged and valued by employers. Recognized providers, such as Google Digital Garage, HubSpot, and Digital Marketing Institute, have a track record of delivering high-quality content and staying abreast of industry trends.
Employers often use industry-recognized certifications as a benchmark for evaluating the skills and expertise of candidates. Having a certification from a reputable institution can serve as a tangible demonstration of your commitment to continuous learning and professional development. It provides assurance to employers that you possess a standardized set of skills and knowledge, which is particularly important in a field as dynamic as digital marketing.
Ultimately, the goal is to choose a digital marketing certification that not only imparts valuable knowledge but also holds weight in the eyes of employers and peers. Industry recognition and credibility are powerful assets that can boost your career prospects, increase your employability, and position you as a credible and competent digital marketing professional within the competitive landscape of the industry.
Online vs In-Person Certification Programs
The choice between online and in-person certification programs in digital marketing is a significant decision that depends on various factors, including personal preferences, learning styles, and logistical considerations.
Online Certification Programs:
Flexibility: One of the primary advantages of online certification programs is the flexibility they offer. Learners can access course materials at their own pace and schedule, making it suitable for individuals with varying commitments such as full-time jobs or other responsibilities.
Accessibility: Online programs provide access to a global pool of resources and instructors. Learners can engage with content from industry experts and connect with peers from around the world, fostering a diverse learning environment.
Cost-Effectiveness: Online programs often have lower tuition costs compared to in-person options. Additionally, learners can save on travel, accommodation, and other expenses associated with attending in-person classes.
Diverse Learning Formats: Online programs often incorporate a variety of multimedia elements, such as video lectures, interactive quizzes, and discussion forums, catering to different learning styles.
In-Person Certification Programs:
Real-Time Interaction: In-person programs provide the opportunity for immediate interaction with instructors and fellow learners. This can facilitate a more dynamic learning experience with real-time feedback and discussions.
Structured Learning Environment: Classroom settings offer a structured learning environment with set schedules, which can be beneficial for individuals who thrive in a more regimented and organized setting.
Networking Opportunities: In-person programs provide valuable networking opportunities. Engaging with instructors and classmates face-to-face can lead to meaningful professional connections and collaborations.
Hands-On Experience: Some in-person programs incorporate hands-on activities, workshops, and group projects that may be challenging to replicate in an online format.
Ultimately, the choice between online and in-person certification programs depends on individual preferences, lifestyle, and learning preferences. Some learners may thrive in the flexibility of online programs, while others may benefit more from the structure and personal interaction offered by in-person options. Consider your own learning style, time constraints, and budget when making this decision.
Practical Application and Real-World Projects
Integrating practical application and real-world projects into a digital marketing certification program is a cornerstone in bridging the gap between theoretical knowledge and practical skills. This hands-on approach serves as a catalyst for a more immersive and impactful learning experience, offering learners the opportunity to directly apply acquired concepts in scenarios reflective of the challenges encountered in professional digital marketing environments.
Real-world projects, such as case studies, play a pivotal role in grounding learners in the complexities of the digital marketing landscape. By dissecting and solving actual business challenges, learners gain a nuanced understanding of how theoretical concepts manifest in practical situations. This process not only reinforces theoretical knowledge but also hones problem-solving skills, preparing individuals to navigate the dynamic and ever-evolving field of digital marketing.
Hands-on exercises, ranging from creating and optimizing digital campaigns to analyzing performance metrics, offer learners tangible experiences that mirror the tasks they will encounter in real-world professional settings. These exercises not only develop technical proficiency but also instill a sense of confidence in learners as they apply their knowledge to concrete, actionable projects.
In summary, the inclusion of practical application and real-world projects in a digital marketing certification program is more than a supplement to theoretical learning; it is a cornerstone for cultivating a holistic and industry-ready skill set. These experiences not only prepare learners for the demands of the professional realm but also empower them to confidently navigate the multifaceted landscape of digital marketing upon completion of their certification.
Cost and Time Considerations
Considering the cost and time implications of a digital marketing certification program is crucial for individuals seeking to strike a balance between their educational aspirations, budget constraints, and personal commitments. Both factors play significant roles in shaping the overall feasibility and effectiveness of the certification journey.
Cost Considerations:The cost of a digital marketing certification program varies widely based on factors such as the institution, the level of the certification, and the inclusion of additional features like real-world projects or instructor-led sessions. Some certifications, like those offered by Google Digital Garage, are available for free, providing an accessible entry point for learners on a budget. On the other hand, certifications from well-known institutions or those with specialized content may come with a higher price tag.
In addition to tuition fees, learners should factor in potential additional costs such as study materials, textbooks, or software tools that may be required for the program. Travel expenses, particularly for in-person programs, should also be considered, as attending physical classes or workshops may incur additional costs.
Time Considerations:The time required to complete a digital marketing certification program can vary based on factors such as the level of the certification, the learning format (self-paced or instructor-led), and the individual learner's pace. Some certifications can be completed in a matter of weeks, while others may take several months.
Self-paced online programs offer flexibility in terms of scheduling, allowing learners to balance certification studies with other commitments such as work or family responsibilities. In contrast, in-person or live online programs with fixed schedules may require a more structured time commitment.
Balancing Cost and Time:Ultimately, finding the right balance between cost and time requires careful consideration of personal circumstances and educational goals. While a more affordable program may suit a tight budget, learners should ensure that it still meets their learning objectives and provides a reputable certification. Similarly, an intensive program that demands significant time commitments may be worthwhile for those seeking a comprehensive and immersive learning experience.
Before committing to a digital marketing certification program, individuals should thoroughly research the program's cost structure, available resources, and time requirements. This informed approach ensures that learners can make a strategic investment in their professional development, aligning their educational choices with both budgetary constraints and career aspirations.
Success Stories and Testimonials
Exploring success stories and testimonials is a valuable step in assessing the impact and effectiveness of a digital marketing certification program. Learning from the experiences of individuals who have completed the program provides insights into the tangible benefits, career advancements, and transformative outcomes that others have achieved. Success stories and testimonials offer a glimpse into the real-world impact of the certification on professional journeys.
Gaining Insight into Real-World Application: Success stories often highlight how individuals have applied the knowledge and skills acquired through the certification in their professional roles. These narratives provide concrete examples of how the certification program translated theoretical concepts into practical solutions, campaigns, or strategies within the dynamic field of digital marketing.
Understanding Career Progression: Testimonials frequently shed light on the career progression of individuals who completed the certification. They may detail how the certification acted as a catalyst for job promotions, career transitions, or enhanced job responsibilities. Such insights offer a tangible understanding of the certification's role in career development and marketability within the industry.
Identifying Diverse Perspectives: Testimonials come from a diverse range of individuals with varied backgrounds, experiences, and career goals. Examining testimonials from professionals with different profiles can provide a holistic view of the certification program's applicability across various industry sectors and roles.
Validating Program Quality: Success stories and testimonials serve as endorsements of the program's quality and effectiveness. Positive feedback from those who have successfully navigated the certification adds credibility to the program's curriculum, instructors, and overall educational approach.
Before enrolling in a digital marketing certification program, individuals should actively seek out success stories and testimonials on official program websites, forums, or professional networking platforms. Analyzing these narratives enables prospective learners to make informed decisions based on the real-world experiences of their peers and validates the potential impact of the certification on their own professional journey.
Maintaining Certification Relevance in a Changing Landscape
Maintaining the relevance of a digital marketing certification in a constantly evolving landscape is a critical consideration for both certification providers and professionals seeking to stay abreast of industry advancements. The field of digital marketing is dynamic, with technology, consumer behaviors, and platforms undergoing frequent changes. Ensuring that certification programs adapt to these changes is essential for professionals to acquire skills that align with current industry demands.
Integration of practical, hands-on experiences is another crucial element. Real-world projects, case studies, and simulations should mirror the challenges professionals face in contemporary digital marketing roles. This not only enhances the practical application of knowledge but also ensures that the skills gained are directly transferable to the current industry landscape.
Establishing partnerships with industry leaders and organizations can also contribute to certification relevance. Collaboration with companies at the forefront of digital marketing ensures that certification programs are informed by real-world practices and insights. Industry partnerships can facilitate access to cutting-edge tools, case studies, and expertise that enhance the overall quality and relevance of the certification.
In summary, maintaining certification relevance in the ever-changing digital marketing landscape requires a proactive and adaptive approach. Certification providers must commit to regular updates, modular learning structures, practical experiences, community engagement, industry partnerships, and feedback mechanisms. Simultaneously, professionals should embrace a mindset of continuous learning, leveraging these certification programs as a foundation for ongoing professional development in the dynamic world of digital marketing.
Conclusion
In conclusion, the world of digital marketing is marked by its constant evolution, with technologies, trends, and consumer behaviors continuously shaping the industry's landscape. The pursuit of a digital marketing certification is not merely a one-time achievement but a commitment to ongoing learning and adaptation. As professionals seek to navigate this dynamic environment, choosing a certification program that prioritizes relevance and adaptability is paramount.
Certification providers play a pivotal role in maintaining the currency and effectiveness of their programs. By regularly updating content, embracing modular learning structures, integrating practical experiences, fostering a culture of continuous learning, establishing industry partnerships, and actively seeking feedback from professionals, certification providers can ensure that their offerings remain at the forefront of the digital marketing field.
Azure Resource Manager (ARM) Templates: A Deep Dive
In the dynamic landscape of cloud computing, the effective management of resources is paramount for organizations seeking optimal performance, scalability, and cost efficiency. Enter Azure Resource Manager (ARM) Templates, a powerful toolset that revolutionizes the provisioning and management of Azure resources. This deep dive into ARM Templates aims to unravel the intricacies of this technology, providing a comprehensive understanding of its capabilities and empowering both novices and seasoned professionals to harness its full potential.
At its core, Azure Resource Manager serves as the deployment and management service for Azure, orchestrating the creation, updating, and deletion of resources in a declarative manner. ARM Templates, then, represent the blueprint for defining the desired state of a resource group, encompassing virtual machines, storage accounts, networking configurations, and more. This declarative approach not only streamlines the deployment process but also facilitates version control, collaboration, and repeatability, crucial aspects in the realm of infrastructure as code.
As we navigate the intricacies of ARM Templates, a spotlight will be cast on advanced features and best practices. From conditional deployments and template functions to the use of linked and nested templates, we will uncover the arsenal of tools available for crafting sophisticated solutions. Through real-world examples and practical scenarios, readers will gain insights into solving complex challenges and optimizing resource management workflows.
In essence, this exploration of Azure Resource Manager (ARM) Templates transcends the surface, offering an in-depth understanding that empowers Azure practitioners to architect, deploy, and manage resources with precision and efficiency. Whether you are an IT professional aiming to enhance your cloud orchestration skills or a developer seeking to integrate infrastructure as code into your workflow, this deep dive serves as a valuable compass in navigating the rich landscape of Azure Resource Manager Templates.
Table of contents
-
Understanding ARM Template Basics
-
ARM Template Structure and Syntax
-
Parameterization in ARM Templates
-
Variables and Expressions
-
Resource Dependencies and Ordering
-
Advanced ARM Template Features
-
Security Considerations in ARM Templates
-
Testing and Debugging ARM Templates
-
Scaling with ARM Templates
-
Best Practices for ARM Template Development
-
Conclusion
Understanding ARM Template Basics
Understanding ARM (Azure Resource Manager) template basics is crucial for efficiently deploying and managing resources in the Microsoft Azure cloud environment. An ARM template is a JSON (JavaScript Object Notation) file that defines the resources to be deployed, their configurations, and the relationships between them. This declarative approach allows users to describe their desired state, and Azure Resource Manager takes care of deploying and managing the resources accordingly.
At the core of an ARM template are the resource definitions. These definitions specify the characteristics of each resource to be deployed, such as the resource type, name, location, and properties. For example, if you want to deploy a virtual machine, the ARM template would include a resource definition for a Virtual Machine, specifying details like its size, operating system, and networking configurations.
Parameters play a crucial role in ARM templates by allowing users to customize deployments without modifying the template itself. Parameters act as placeholders for values that can be provided at the time of deployment. This flexibility enables the reuse of templates for different scenarios, as users can input different parameter values based on their specific requirements.
Understanding ARM template basics is fundamental for efficiently managing and deploying resources in Azure. The declarative nature of ARM templates, combined with parameters, variables, expressions, dependencies, and outputs, provides a powerful framework for orchestrating complex infrastructure deployments in a consistent and reproducible manner.
ARM Template Structure and Syntax
The structure and syntax of an ARM (Azure Resource Manager) template are fundamental aspects that define how resources are provisioned and managed in the Azure cloud. An ARM template is essentially a JSON (JavaScript Object Notation) file, structured to convey the configuration details and relationships among various Azure resources. Understanding the key components of this structure is crucial for effectively deploying and orchestrating infrastructure in Azure.
The top-level structure of an ARM template includes the "schema" and "contentVersion" fields. The "schema" specifies the version of the ARM template language, ensuring compatibility with Azure Resource Manager. The "contentVersion" is a user-defined string that represents the version of the template itself, enabling version control and tracking changes over time.
The "parameters" section allows users to define values that can be input at deployment time. These parameters serve as customizable inputs, allowing users to tailor deployments without altering the underlying template. This flexibility is particularly valuable when deploying the same template with variations in configurations.
Variables in ARM templates provide a way to define reusable expressions or values. The "variables" section is used to store these expressions, making the template more readable and maintainable. Variables are helpful when certain values need to be referenced multiple times within the template, as they centralize and simplify the management of these values.
The "resources" section is the core of the ARM template, where each resource to be deployed is defined. Each resource definition includes properties such as the resource type, name, location, and specific configurations. The declarative nature of ARM templates means that users specify the desired end state of the infrastructure, and Azure Resource Manager takes care of the deployment details.
Dependencies between resources are expressed through the "dependsOn" property within a resource definition. This property ensures that resources are deployed in the correct order, addressing scenarios where one resource relies on the existence or configuration of another. Properly managing dependencies is crucial for a smooth and error-free deployment process.
The ARM template structure and syntax provide a powerful framework for describing, deploying, and managing Azure resources. From top-level fields to parameters, variables, resources, expressions, dependencies, and outputs, each component contributes to creating a flexible, reusable, and maintainable deployment process in the Azure cloud environment.
Parameterization in ARM Templates
Parameterization is a fundamental concept in ARM (Azure Resource Manager) templates that significantly enhances their flexibility and reusability. In the context of ARM templates, parameterization involves defining parameters, which serve as placeholders for values that can be provided at the time of deployment. This allows users to customize various aspects of the template without altering its core structure, providing a dynamic and adaptable approach to resource provisioning in the Azure cloud.
The flexibility afforded by parameterization is particularly advantageous in scenarios where templates need to be reused for different deployments. By incorporating parameters, users can create generic templates that serve as templates for various situations. This reusability is achieved by providing different parameter values for each deployment, enabling a single template to cater to diverse requirements without necessitating multiple template versions.
One of the key benefits of parameterization is its impact on the maintainability of ARM templates. When adjustments or updates are required, users can modify parameter values without affecting the underlying template structure. This separation between parameters and template logic simplifies the management process, making it easier to maintain, version, and evolve templates over time.
Parameterization in ARM templates is a pivotal mechanism for tailoring resource deployments in Azure. By introducing parameters, users can inject flexibility, reusability, and maintainability into their templates, creating a powerful foundation for building dynamic and adaptable infrastructure in the ever-evolving cloud environment.
Variables and Expressions
Variables and expressions in ARM (Azure Resource Manager) templates play a crucial role in enhancing the readability, maintainability, and adaptability of deployment configurations within the Azure cloud environment. Variables serve as named containers for values or expressions, allowing users to simplify template authoring and avoid redundancy. These variables are defined within the "variables" section of the ARM template, providing a centralized location for expressing complex or frequently used values.
Expressions in ARM templates enable dynamic evaluation of values during deployment. These expressions can be used to concatenate strings, perform mathematical operations, or reference other elements within the template. The use of expressions enhances the template's flexibility, allowing for the creation of more adaptive and intelligent deployments. For example, an expression can be employed to dynamically generate a unique name for a resource based on certain parameters.
An illustrative example of variables and expressions in an ARM template might involve the definition of a variable for a storage account name, incorporating an expression to concatenate a prefix with a unique identifier. This not only enhances the template's readability but also ensures that each deployment generates a storage account name that is both descriptive and distinct.
Variables and expressions are powerful features in ARM templates that contribute to the template's clarity, maintainability, and adaptability. Variables simplify the template structure by providing a centralized mechanism for managing values, while expressions introduce dynamic behavior, making templates more responsive to changing deployment conditions. By effectively utilizing variables and expressions, users can create ARM templates that are not only more readable but also more robust and versatile.
Resource Dependencies and Ordering
Resource dependencies and ordering are critical aspects of ARM (Azure Resource Manager) templates, providing a mechanism to define the relationships and sequencing of resources during deployment in the Microsoft Azure cloud environment. The "dependsOn" property within a resource definition is used to specify dependencies, ensuring that resources are created or modified in the correct order to satisfy inter-resource relationships. This property establishes a logical linkage between resources, addressing scenarios where the configuration or existence of one resource depends on the state of another.
In ARM templates, the ordering of resource deployment is significant for maintaining the integrity and functionality of the overall infrastructure. For example, if a virtual machine depends on a storage account for its data disks, the "dependsOn" property is employed to ensure that the storage account is created or updated before the virtual machine. This sequencing prevents deployment errors that might occur if the virtual machine attempts to reference a storage account that does not yet exist.
Resource dependencies and ordering in ARM templates are essential for orchestratng the deployment of complex infrastructures in Azure. The "dependsOn" property provides a straightforward means of expressing relationships between resources, ensuring that the deployment sequence aligns with the dependencies specified in the template. This capability is pivotal for maintaining a consistent and error-free deployment process, particularly in scenarios where the correct functioning of one resource relies on the state of another.
Advanced ARM Template Features
Advanced ARM (Azure Resource Manager) template features empower users with a more sophisticated and versatile toolkit for orchestrating complex deployments in the Azure cloud. These features extend beyond the foundational elements of resource definitions and parameters, offering capabilities that enhance the modularity, efficiency, and customization of infrastructure configurations.
Deployment scripts are another advanced feature that enhances the extensibility of ARM templates. These scripts, written in languages such as PowerShell or Bash, can be executed during the deployment process. This capability allows users to perform custom provisioning steps, execute configuration tasks, or integrate with external systems, providing a flexible and powerful mechanism for customizing deployment workflows.
Integration with Azure's Role-Based Access Control (RBAC) system is an advanced ARM template feature that brings security policies and access controls into the template definition. This enables users to codify permissions directly within the template, ensuring that security configurations align with resource deployments. This integration supports a more comprehensive and auditable approach to infrastructure governance.
Advanced ARM template features offer users a sophisticated set of tools to create, manage, and customize intricate infrastructure configurations in Azure. These features provide a pathway to more dynamic, modular, and secure deployments, empowering users to tailor their templates to diverse scenarios while maintaining a high level of efficiency and maintainability.
Security Considerations in ARM Templates
Security considerations in ARM (Azure Resource Manager) templates are paramount to ensuring the integrity, confidentiality, and availability of resources deployed in the Microsoft Azure cloud. When crafting ARM templates, developers and administrators must be diligent in implementing best practices to safeguard against potential vulnerabilities and adhere to security standards. Several key considerations contribute to creating secure ARM templates.
Access Control and RBAC: A fundamental security consideration involves defining appropriate access controls through Azure's Role-Based Access Control (RBAC) system. ARM templates can codify RBAC configurations, specifying the roles and permissions assigned to different entities within the Azure environment. Properly configuring RBAC ensures that only authorized users have access to resources and limits potential security risks.
Template Validation and Review: Regularly validating and reviewing ARM templates is a critical security practice. This involves employing tools like Azure Policy, Azure Security Center, or third-party solutions to assess templates for compliance with security policies and standards. Additionally, conducting code reviews helps identify and rectify potential security vulnerabilities before deployment.
Audit Logging and Monitoring: ARM templates should be configured to enable comprehensive audit logging and monitoring. Azure Monitor and Azure Security Center can be leveraged to gain insights into resource activities, detect potential security incidents, and respond to security events promptly. Logging and monitoring play a crucial role in maintaining visibility into the security posture of deployed resources.
Regular Updates and Patching: ARM templates should be designed with considerations for regular updates and patching. This involves incorporating mechanisms for deploying the latest security updates and patches to the underlying operating systems and software. Keeping software up-to-date is vital for addressing known vulnerabilities and maintaining a secure deployment environment.
Security considerations in ARM templates are integral to establishing a robust and resilient Azure deployment. By incorporating access controls, securing parameters, implementing network security measures, conducting regular reviews, enabling audit logging, employing encryption, and embracing continuous testing, users can significantly enhance the security posture of their Azure resources deployed through ARM templates.
Testing and Debugging ARM Templates
Testing and debugging ARM (Azure Resource Manager) templates is a crucial aspect of the development lifecycle, ensuring the reliability and correctness of infrastructure deployments in the Microsoft Azure cloud. The complexity of ARM templates and the variety of resources they manage necessitate thorough testing to identify and rectify issues before deployment. Several key practices contribute to effective testing and debugging of ARM templates.
Unit Testing with Azure PowerShell or Azure CLI: Unit testing involves testing individual components of the ARM template in isolation. Using Azure PowerShell or Azure CLI, developers can script and automate the deployment and validation of specific resources or configurations. This allows for targeted testing of individual modules within the template, ensuring their functionality in isolation.
Integration Testing in Staging Environments: Integration testing involves deploying the entire ARM template in a staging environment that closely mirrors the production environment. This comprehensive test validates the interactions and dependencies between different resources within the template. It helps identify issues related to resource interdependence, network configurations, and overall deployment logic.
Azure Policy for Compliance Testing: Azure Policy can be leveraged to enforce organizational standards and compliance requirements during testing. Policies can be defined to check whether ARM templates adhere to specific security, naming, or configuration standards. Running compliance tests ensures that templates align with organizational governance policies and industry best practices.
Debugging with Visual Studio Code and ARM Tools: Developers can utilize Visual Studio Code, along with extensions like the Azure Resource Manager (ARM) Tools, for debugging ARM templates. Visual Studio Code provides a rich set of features, including template parameterization, IntelliSense, and real-time validation, making it easier to identify and address issues within the template code.
Azure Resource Manager Template Test Toolkit (arm-ttk): The ARM Template Test Toolkit is a set of PowerShell scripts that enables automated testing of ARM templates. It includes a suite of tests that cover various aspects, such as template structure, naming conventions, and security controls. Integrating arm-ttk into the testing pipeline ensures a comprehensive and standardized approach to template validation.
Effective testing and debugging of ARM templates involve a combination of linting, local testing, unit testing, integration testing, compliance testing, debugging tools, and version control practices. This comprehensive approach helps identify and address issues at various stages of development, leading to more reliable and resilient infrastructure deployments in the Azure cloud.
Scaling with ARM Templates
Scaling with ARM (Azure Resource Manager) templates is a fundamental aspect of efficiently managing and adapting cloud infrastructure to changing requirements in the Microsoft Azure environment. ARM templates provide a declarative way to define and deploy resources, and they offer several features that facilitate scaling operations seamlessly.
One primary mechanism for scaling with ARM templates is leveraging the flexibility of parameterization. Parameters allow users to define configurable values, such as the number of instances or the size of resources, at the time of deployment. By parameterizing key aspects of the template, users can easily scale resources up or down based on their specific needs without modifying the underlying template structure. This adaptability is particularly useful in scenarios where dynamic scaling is required to handle varying workloads.
ARM templates also support the deployment of resource instances within a loop. This loop capability enables the repetition of resource creation based on specified conditions or parameters. For example, a template can include a loop to create multiple virtual machines or storage accounts with similar configurations. This feature is instrumental in achieving horizontal scaling, where additional instances of a resource are added to distribute workload or improve performance.
Scaling with ARM templates in Azure involves leveraging parameterization, loops, and specialized features like virtual machine scale sets. By parameterizing key aspects of the template and utilizing features that support dynamic scaling, users can create templates that adapt to changing workloads and efficiently manage resources. Properly managing dependencies and incorporating auto-scaling configurations further enhances the scalability and responsiveness of ARM template deployments in the Azure cloud.
Best Practices for ARM Template Development
Developing ARM (Azure Resource Manager) templates effectively requires adherence to best practices that enhance the reliability, maintainability, and security of infrastructure deployments in Microsoft Azure. These best practices cover a spectrum of considerations, from template design and parameterization to security measures and overall management practices.
Parameterization is a key aspect of creating flexible and customizable templates. By leveraging parameters, users can input values at deployment time, allowing for adaptability across different environments or scenarios. Thoughtful parameterization not only enhances the template's flexibility but also contributes to its reusability across diverse deployment scenarios, promoting a more agile infrastructure.
Comprehensive documentation is a cornerstone of effective template development. Maintaining documentation that outlines the purpose of each resource, intended configurations, and specific deployment steps ensures clarity for current and future users. Well-documented templates are easier to understand and manage over time.
Regular testing is an integral part of the development lifecycle. Implementing a robust testing strategy, including linting, unit testing, integration testing, and compliance testing, helps identify and address issues early in the development process, ensuring the reliability and correctness of templates.
Continuous Integration/Continuous Deployment (CI/CD) pipelines streamline the testing, validation, and deployment processes. Integrating ARM templates into CI/CD pipelines automates these processes, ensuring consistency and enabling rapid and reliable deployments, fostering a more efficient and controlled deployment pipeline.
These best practices collectively contribute to the effectiveness of ARM template development in Azure. By embracing modular design, parameterization, version control, and security measures, developers and administrators can create templates that are not only reliable and scalable but also align with organizational standards and security considerations, ensuring a robust and efficient infrastructure deployment process.
Conclusion
In conclusion, adopting best practices for ARM (Azure Resource Manager) template development is instrumental in ensuring the success, reliability, and security of infrastructure deployments in Microsoft Azure. The combination of modular design, parameterization, version control, and security measures creates a foundation for creating templates that are not only readable and maintainable but also adaptable to evolving requirements. By adhering to consistent naming conventions, implementing resource tagging, and incorporating robust error handling and logging mechanisms, developers and administrators can streamline resource management and troubleshooting processes.
Comprehensive documentation remains a cornerstone of effective template development, providing clarity for current and future users. Regular testing, including linting, unit testing, and compliance testing, helps identify and address issues early in the development lifecycle, ensuring the correctness of templates. Integrating ARM templates into CI/CD pipelines automates testing, validation, and deployment processes, contributing to consistency and reliability in the deployment pipeline.
Role-Based Access Control (RBAC) configurations enhance security by defining and managing access controls within templates, aligning with governance requirements. Minimizing hard-coding and relying on parameters and variables fosters flexibility and adaptability, making templates more dynamic and responsive to changes in the Azure environment.
In essence, these best practices collectively contribute to the creation of ARM templates that are scalable, maintainable, and aligned with security and compliance standards. By following these guidelines, organizations can build a foundation for efficient and secure infrastructure as code (IaC) practices in Azure, enabling them to respond effectively to evolving business needs while maintaining a high standard of reliability and security in their cloud deployments.
Read More
In the dynamic landscape of cloud computing, the effective management of resources is paramount for organizations seeking optimal performance, scalability, and cost efficiency. Enter Azure Resource Manager (ARM) Templates, a powerful toolset that revolutionizes the provisioning and management of Azure resources. This deep dive into ARM Templates aims to unravel the intricacies of this technology, providing a comprehensive understanding of its capabilities and empowering both novices and seasoned professionals to harness its full potential.
At its core, Azure Resource Manager serves as the deployment and management service for Azure, orchestrating the creation, updating, and deletion of resources in a declarative manner. ARM Templates, then, represent the blueprint for defining the desired state of a resource group, encompassing virtual machines, storage accounts, networking configurations, and more. This declarative approach not only streamlines the deployment process but also facilitates version control, collaboration, and repeatability, crucial aspects in the realm of infrastructure as code.
As we navigate the intricacies of ARM Templates, a spotlight will be cast on advanced features and best practices. From conditional deployments and template functions to the use of linked and nested templates, we will uncover the arsenal of tools available for crafting sophisticated solutions. Through real-world examples and practical scenarios, readers will gain insights into solving complex challenges and optimizing resource management workflows.
In essence, this exploration of Azure Resource Manager (ARM) Templates transcends the surface, offering an in-depth understanding that empowers Azure practitioners to architect, deploy, and manage resources with precision and efficiency. Whether you are an IT professional aiming to enhance your cloud orchestration skills or a developer seeking to integrate infrastructure as code into your workflow, this deep dive serves as a valuable compass in navigating the rich landscape of Azure Resource Manager Templates.
Table of contents
-
Understanding ARM Template Basics
-
ARM Template Structure and Syntax
-
Parameterization in ARM Templates
-
Variables and Expressions
-
Resource Dependencies and Ordering
-
Advanced ARM Template Features
-
Security Considerations in ARM Templates
-
Testing and Debugging ARM Templates
-
Scaling with ARM Templates
-
Best Practices for ARM Template Development
-
Conclusion
Understanding ARM Template Basics
Understanding ARM (Azure Resource Manager) template basics is crucial for efficiently deploying and managing resources in the Microsoft Azure cloud environment. An ARM template is a JSON (JavaScript Object Notation) file that defines the resources to be deployed, their configurations, and the relationships between them. This declarative approach allows users to describe their desired state, and Azure Resource Manager takes care of deploying and managing the resources accordingly.
At the core of an ARM template are the resource definitions. These definitions specify the characteristics of each resource to be deployed, such as the resource type, name, location, and properties. For example, if you want to deploy a virtual machine, the ARM template would include a resource definition for a Virtual Machine, specifying details like its size, operating system, and networking configurations.
Parameters play a crucial role in ARM templates by allowing users to customize deployments without modifying the template itself. Parameters act as placeholders for values that can be provided at the time of deployment. This flexibility enables the reuse of templates for different scenarios, as users can input different parameter values based on their specific requirements.
Understanding ARM template basics is fundamental for efficiently managing and deploying resources in Azure. The declarative nature of ARM templates, combined with parameters, variables, expressions, dependencies, and outputs, provides a powerful framework for orchestrating complex infrastructure deployments in a consistent and reproducible manner.
ARM Template Structure and Syntax
The structure and syntax of an ARM (Azure Resource Manager) template are fundamental aspects that define how resources are provisioned and managed in the Azure cloud. An ARM template is essentially a JSON (JavaScript Object Notation) file, structured to convey the configuration details and relationships among various Azure resources. Understanding the key components of this structure is crucial for effectively deploying and orchestrating infrastructure in Azure.
The top-level structure of an ARM template includes the "schema" and "contentVersion" fields. The "schema" specifies the version of the ARM template language, ensuring compatibility with Azure Resource Manager. The "contentVersion" is a user-defined string that represents the version of the template itself, enabling version control and tracking changes over time.
The "parameters" section allows users to define values that can be input at deployment time. These parameters serve as customizable inputs, allowing users to tailor deployments without altering the underlying template. This flexibility is particularly valuable when deploying the same template with variations in configurations.
Variables in ARM templates provide a way to define reusable expressions or values. The "variables" section is used to store these expressions, making the template more readable and maintainable. Variables are helpful when certain values need to be referenced multiple times within the template, as they centralize and simplify the management of these values.
The "resources" section is the core of the ARM template, where each resource to be deployed is defined. Each resource definition includes properties such as the resource type, name, location, and specific configurations. The declarative nature of ARM templates means that users specify the desired end state of the infrastructure, and Azure Resource Manager takes care of the deployment details.
Dependencies between resources are expressed through the "dependsOn" property within a resource definition. This property ensures that resources are deployed in the correct order, addressing scenarios where one resource relies on the existence or configuration of another. Properly managing dependencies is crucial for a smooth and error-free deployment process.
The ARM template structure and syntax provide a powerful framework for describing, deploying, and managing Azure resources. From top-level fields to parameters, variables, resources, expressions, dependencies, and outputs, each component contributes to creating a flexible, reusable, and maintainable deployment process in the Azure cloud environment.
Parameterization in ARM Templates
Parameterization is a fundamental concept in ARM (Azure Resource Manager) templates that significantly enhances their flexibility and reusability. In the context of ARM templates, parameterization involves defining parameters, which serve as placeholders for values that can be provided at the time of deployment. This allows users to customize various aspects of the template without altering its core structure, providing a dynamic and adaptable approach to resource provisioning in the Azure cloud.
The flexibility afforded by parameterization is particularly advantageous in scenarios where templates need to be reused for different deployments. By incorporating parameters, users can create generic templates that serve as templates for various situations. This reusability is achieved by providing different parameter values for each deployment, enabling a single template to cater to diverse requirements without necessitating multiple template versions.
One of the key benefits of parameterization is its impact on the maintainability of ARM templates. When adjustments or updates are required, users can modify parameter values without affecting the underlying template structure. This separation between parameters and template logic simplifies the management process, making it easier to maintain, version, and evolve templates over time.
Parameterization in ARM templates is a pivotal mechanism for tailoring resource deployments in Azure. By introducing parameters, users can inject flexibility, reusability, and maintainability into their templates, creating a powerful foundation for building dynamic and adaptable infrastructure in the ever-evolving cloud environment.
Variables and Expressions
Variables and expressions in ARM (Azure Resource Manager) templates play a crucial role in enhancing the readability, maintainability, and adaptability of deployment configurations within the Azure cloud environment. Variables serve as named containers for values or expressions, allowing users to simplify template authoring and avoid redundancy. These variables are defined within the "variables" section of the ARM template, providing a centralized location for expressing complex or frequently used values.
Expressions in ARM templates enable dynamic evaluation of values during deployment. These expressions can be used to concatenate strings, perform mathematical operations, or reference other elements within the template. The use of expressions enhances the template's flexibility, allowing for the creation of more adaptive and intelligent deployments. For example, an expression can be employed to dynamically generate a unique name for a resource based on certain parameters.
An illustrative example of variables and expressions in an ARM template might involve the definition of a variable for a storage account name, incorporating an expression to concatenate a prefix with a unique identifier. This not only enhances the template's readability but also ensures that each deployment generates a storage account name that is both descriptive and distinct.
Variables and expressions are powerful features in ARM templates that contribute to the template's clarity, maintainability, and adaptability. Variables simplify the template structure by providing a centralized mechanism for managing values, while expressions introduce dynamic behavior, making templates more responsive to changing deployment conditions. By effectively utilizing variables and expressions, users can create ARM templates that are not only more readable but also more robust and versatile.
Resource Dependencies and Ordering
Resource dependencies and ordering are critical aspects of ARM (Azure Resource Manager) templates, providing a mechanism to define the relationships and sequencing of resources during deployment in the Microsoft Azure cloud environment. The "dependsOn" property within a resource definition is used to specify dependencies, ensuring that resources are created or modified in the correct order to satisfy inter-resource relationships. This property establishes a logical linkage between resources, addressing scenarios where the configuration or existence of one resource depends on the state of another.
In ARM templates, the ordering of resource deployment is significant for maintaining the integrity and functionality of the overall infrastructure. For example, if a virtual machine depends on a storage account for its data disks, the "dependsOn" property is employed to ensure that the storage account is created or updated before the virtual machine. This sequencing prevents deployment errors that might occur if the virtual machine attempts to reference a storage account that does not yet exist.
Resource dependencies and ordering in ARM templates are essential for orchestratng the deployment of complex infrastructures in Azure. The "dependsOn" property provides a straightforward means of expressing relationships between resources, ensuring that the deployment sequence aligns with the dependencies specified in the template. This capability is pivotal for maintaining a consistent and error-free deployment process, particularly in scenarios where the correct functioning of one resource relies on the state of another.
Advanced ARM Template Features
Advanced ARM (Azure Resource Manager) template features empower users with a more sophisticated and versatile toolkit for orchestrating complex deployments in the Azure cloud. These features extend beyond the foundational elements of resource definitions and parameters, offering capabilities that enhance the modularity, efficiency, and customization of infrastructure configurations.
Deployment scripts are another advanced feature that enhances the extensibility of ARM templates. These scripts, written in languages such as PowerShell or Bash, can be executed during the deployment process. This capability allows users to perform custom provisioning steps, execute configuration tasks, or integrate with external systems, providing a flexible and powerful mechanism for customizing deployment workflows.
Integration with Azure's Role-Based Access Control (RBAC) system is an advanced ARM template feature that brings security policies and access controls into the template definition. This enables users to codify permissions directly within the template, ensuring that security configurations align with resource deployments. This integration supports a more comprehensive and auditable approach to infrastructure governance.
Advanced ARM template features offer users a sophisticated set of tools to create, manage, and customize intricate infrastructure configurations in Azure. These features provide a pathway to more dynamic, modular, and secure deployments, empowering users to tailor their templates to diverse scenarios while maintaining a high level of efficiency and maintainability.
Security Considerations in ARM Templates
Security considerations in ARM (Azure Resource Manager) templates are paramount to ensuring the integrity, confidentiality, and availability of resources deployed in the Microsoft Azure cloud. When crafting ARM templates, developers and administrators must be diligent in implementing best practices to safeguard against potential vulnerabilities and adhere to security standards. Several key considerations contribute to creating secure ARM templates.
Access Control and RBAC: A fundamental security consideration involves defining appropriate access controls through Azure's Role-Based Access Control (RBAC) system. ARM templates can codify RBAC configurations, specifying the roles and permissions assigned to different entities within the Azure environment. Properly configuring RBAC ensures that only authorized users have access to resources and limits potential security risks.
Template Validation and Review: Regularly validating and reviewing ARM templates is a critical security practice. This involves employing tools like Azure Policy, Azure Security Center, or third-party solutions to assess templates for compliance with security policies and standards. Additionally, conducting code reviews helps identify and rectify potential security vulnerabilities before deployment.
Audit Logging and Monitoring: ARM templates should be configured to enable comprehensive audit logging and monitoring. Azure Monitor and Azure Security Center can be leveraged to gain insights into resource activities, detect potential security incidents, and respond to security events promptly. Logging and monitoring play a crucial role in maintaining visibility into the security posture of deployed resources.
Regular Updates and Patching: ARM templates should be designed with considerations for regular updates and patching. This involves incorporating mechanisms for deploying the latest security updates and patches to the underlying operating systems and software. Keeping software up-to-date is vital for addressing known vulnerabilities and maintaining a secure deployment environment.
Security considerations in ARM templates are integral to establishing a robust and resilient Azure deployment. By incorporating access controls, securing parameters, implementing network security measures, conducting regular reviews, enabling audit logging, employing encryption, and embracing continuous testing, users can significantly enhance the security posture of their Azure resources deployed through ARM templates.
Testing and Debugging ARM Templates
Testing and debugging ARM (Azure Resource Manager) templates is a crucial aspect of the development lifecycle, ensuring the reliability and correctness of infrastructure deployments in the Microsoft Azure cloud. The complexity of ARM templates and the variety of resources they manage necessitate thorough testing to identify and rectify issues before deployment. Several key practices contribute to effective testing and debugging of ARM templates.
Unit Testing with Azure PowerShell or Azure CLI: Unit testing involves testing individual components of the ARM template in isolation. Using Azure PowerShell or Azure CLI, developers can script and automate the deployment and validation of specific resources or configurations. This allows for targeted testing of individual modules within the template, ensuring their functionality in isolation.
Integration Testing in Staging Environments: Integration testing involves deploying the entire ARM template in a staging environment that closely mirrors the production environment. This comprehensive test validates the interactions and dependencies between different resources within the template. It helps identify issues related to resource interdependence, network configurations, and overall deployment logic.
Azure Policy for Compliance Testing: Azure Policy can be leveraged to enforce organizational standards and compliance requirements during testing. Policies can be defined to check whether ARM templates adhere to specific security, naming, or configuration standards. Running compliance tests ensures that templates align with organizational governance policies and industry best practices.
Debugging with Visual Studio Code and ARM Tools: Developers can utilize Visual Studio Code, along with extensions like the Azure Resource Manager (ARM) Tools, for debugging ARM templates. Visual Studio Code provides a rich set of features, including template parameterization, IntelliSense, and real-time validation, making it easier to identify and address issues within the template code.
Azure Resource Manager Template Test Toolkit (arm-ttk): The ARM Template Test Toolkit is a set of PowerShell scripts that enables automated testing of ARM templates. It includes a suite of tests that cover various aspects, such as template structure, naming conventions, and security controls. Integrating arm-ttk into the testing pipeline ensures a comprehensive and standardized approach to template validation.
Effective testing and debugging of ARM templates involve a combination of linting, local testing, unit testing, integration testing, compliance testing, debugging tools, and version control practices. This comprehensive approach helps identify and address issues at various stages of development, leading to more reliable and resilient infrastructure deployments in the Azure cloud.
Scaling with ARM Templates
Scaling with ARM (Azure Resource Manager) templates is a fundamental aspect of efficiently managing and adapting cloud infrastructure to changing requirements in the Microsoft Azure environment. ARM templates provide a declarative way to define and deploy resources, and they offer several features that facilitate scaling operations seamlessly.
One primary mechanism for scaling with ARM templates is leveraging the flexibility of parameterization. Parameters allow users to define configurable values, such as the number of instances or the size of resources, at the time of deployment. By parameterizing key aspects of the template, users can easily scale resources up or down based on their specific needs without modifying the underlying template structure. This adaptability is particularly useful in scenarios where dynamic scaling is required to handle varying workloads.
ARM templates also support the deployment of resource instances within a loop. This loop capability enables the repetition of resource creation based on specified conditions or parameters. For example, a template can include a loop to create multiple virtual machines or storage accounts with similar configurations. This feature is instrumental in achieving horizontal scaling, where additional instances of a resource are added to distribute workload or improve performance.
Scaling with ARM templates in Azure involves leveraging parameterization, loops, and specialized features like virtual machine scale sets. By parameterizing key aspects of the template and utilizing features that support dynamic scaling, users can create templates that adapt to changing workloads and efficiently manage resources. Properly managing dependencies and incorporating auto-scaling configurations further enhances the scalability and responsiveness of ARM template deployments in the Azure cloud.
Best Practices for ARM Template Development
Developing ARM (Azure Resource Manager) templates effectively requires adherence to best practices that enhance the reliability, maintainability, and security of infrastructure deployments in Microsoft Azure. These best practices cover a spectrum of considerations, from template design and parameterization to security measures and overall management practices.
Parameterization is a key aspect of creating flexible and customizable templates. By leveraging parameters, users can input values at deployment time, allowing for adaptability across different environments or scenarios. Thoughtful parameterization not only enhances the template's flexibility but also contributes to its reusability across diverse deployment scenarios, promoting a more agile infrastructure.
Comprehensive documentation is a cornerstone of effective template development. Maintaining documentation that outlines the purpose of each resource, intended configurations, and specific deployment steps ensures clarity for current and future users. Well-documented templates are easier to understand and manage over time.
Regular testing is an integral part of the development lifecycle. Implementing a robust testing strategy, including linting, unit testing, integration testing, and compliance testing, helps identify and address issues early in the development process, ensuring the reliability and correctness of templates.
Continuous Integration/Continuous Deployment (CI/CD) pipelines streamline the testing, validation, and deployment processes. Integrating ARM templates into CI/CD pipelines automates these processes, ensuring consistency and enabling rapid and reliable deployments, fostering a more efficient and controlled deployment pipeline.
These best practices collectively contribute to the effectiveness of ARM template development in Azure. By embracing modular design, parameterization, version control, and security measures, developers and administrators can create templates that are not only reliable and scalable but also align with organizational standards and security considerations, ensuring a robust and efficient infrastructure deployment process.
Conclusion
In conclusion, adopting best practices for ARM (Azure Resource Manager) template development is instrumental in ensuring the success, reliability, and security of infrastructure deployments in Microsoft Azure. The combination of modular design, parameterization, version control, and security measures creates a foundation for creating templates that are not only readable and maintainable but also adaptable to evolving requirements. By adhering to consistent naming conventions, implementing resource tagging, and incorporating robust error handling and logging mechanisms, developers and administrators can streamline resource management and troubleshooting processes.
Comprehensive documentation remains a cornerstone of effective template development, providing clarity for current and future users. Regular testing, including linting, unit testing, and compliance testing, helps identify and address issues early in the development lifecycle, ensuring the correctness of templates. Integrating ARM templates into CI/CD pipelines automates testing, validation, and deployment processes, contributing to consistency and reliability in the deployment pipeline.
Role-Based Access Control (RBAC) configurations enhance security by defining and managing access controls within templates, aligning with governance requirements. Minimizing hard-coding and relying on parameters and variables fosters flexibility and adaptability, making templates more dynamic and responsive to changes in the Azure environment.
In essence, these best practices collectively contribute to the creation of ARM templates that are scalable, maintainable, and aligned with security and compliance standards. By following these guidelines, organizations can build a foundation for efficient and secure infrastructure as code (IaC) practices in Azure, enabling them to respond effectively to evolving business needs while maintaining a high standard of reliability and security in their cloud deployments.
Overview of CAPM Certification: A Beginner's Guide
The Certified Associate in Project Management (CAPM)® certification is a credential designed to prepare candidates for entry-level project management positions. It is administered by the Project Management Institute (PMI), a leading worldwide organisation in project management.
Certainly! The CAPM (Certified Associate in Project Management) certification is a globally recognized entry-level certification for project management professionals. It is offered by the Project Management Institute (PMI) and is designed for individuals who are interested in or just starting their careers in project management.
The CAPM certification is a valuable credential for individuals seeking to establish a foundation in project management. It provides a standardized framework and demonstrates a commitment to the profession. As individuals gain more experience, they may choose to pursue advanced certifications such as the Project Management Professional (PMP) certification.
Candidates interested in obtaining the most up-to-date information on the CAPM certification should refer to the official PMI website or contact PMI directly.
Table of contents
-
Introduction to Project Management
-
Overview of CAPM Certification
-
PMI and CAPM
-
CAPM Eligibility Criteria
-
CAPM Exam Structure
-
CAPM Exam Content
-
Preparing for the CAPM Exam
-
CAPM Exam Day
-
Maintaining CAPM Certification
-
Career Benefits of CAPM Certification
-
Conclusion
Introduction to Project Management
Project management is a multifaceted discipline integral to achieving organizational objectives. It encompasses the strategic application of knowledge, skills, tools, and techniques to navigate the complexities of project execution. At its core, project management involves planning, executing, monitoring, and closing projects to meet specific goals within predetermined success criteria. Projects, characterized by their uniqueness, have defined start and end points, specific objectives, and often require cross-functional teams collaborating towards a common purpose.
The role of a project manager is pivotal in orchestrating these efforts. Project managers lead teams through the initiation, planning, execution, monitoring and controlling, and closure phases of the project life cycle. Within this framework, various constraints such as time, cost, scope, quality, and risk must be carefully balanced to deliver a successful outcome. Identifying and managing stakeholders—individuals or groups with an interest or influence in the project—is another critical aspect of effective project management.
Project management processes, as defined by the Project Management Institute (PMI), provide a structured approach. These processes include initiating, planning, executing, monitoring and controlling, and closing. Additionally, organizations adopt different project management methodologies, such as Agile, Waterfall, or Scrum, based on the nature of the project and organizational preferences.
Individuals aspiring to lead or contribute to successful projects often pursue certifications like the Certified Associate in Project Management (CAPM) or Project Management Professional (PMP) to validate their skills and knowledge. Whether in business, IT, construction, or other industries, understanding and applying project management principles are essential for ensuring efficiency, minimizing risks, and achieving project objectives.
Overview of CAPM Certification
The Certified Associate in Project Management (CAPM) certification, offered by the Project Management Institute (PMI), serves as a foundational credential for those seeking entry into the field of project management. Its primary purpose is to validate a candidate's comprehension of essential project management concepts and terminology. To be eligible for the CAPM exam, candidates must possess a secondary degree, such as a high school diploma or associate's degree, along with either 1,500 hours of project experience or 23 hours of formal project management education.
The CAPM exam itself is a computer-based test comprising 150 multiple-choice questions, covering the five key process groups of project management: Initiating, Planning, Executing, Monitoring and Controlling, and Closing. With a duration of three hours, the exam evaluates candidates on their understanding of project management processes outlined in the Project Management Body of Knowledge (PMBOK Guide), the primary reference material provided by PMI.
Successful preparation for the CAPM exam involves a thorough study of the PMBOK Guide, practice exams to familiarize candidates with the format, and participation in study groups for collaborative learning. As individuals progress in their project management careers, they may choose to pursue advanced certifications, such as the Project Management Professional (PMP) certification. Overall, the CAPM certification serves as a valuable starting point for those aspiring to establish a solid foundation in project management and advance their professional growth in this dynamic field.
PMI and CAPM
The Project Management Institute (PMI) stands as a pivotal force in the field of project management. Established in 1969, PMI is a non-profit organization committed to advancing the practice, science, and profession of project management on a global scale. At the heart of PMI's contributions is the Project Management Body of Knowledge (PMBOK Guide), a comprehensive resource that sets industry standards and serves as a foundational guide for project management professionals.
CAPM certification brings with it a host of benefits. Recognized globally, it establishes a standardized framework for project management knowledge and acts as a stepping stone for career advancement in the field. CAPM holders contribute to a common language and understanding of fundamental project management principles within the industry.
While PMI membership is not mandatory for certification, it offers additional advantages. PMI members gain access to a wealth of resources, networking opportunities, and enjoy discounts on certification exams and educational events. In essence, PMI, through its standards and certifications, including the CAPM, plays a pivotal role in shaping the professional landscape of project management, fostering growth, and facilitating the exchange of knowledge and expertise among practitioners worldwide.
CAPM Eligibility Criteria
The eligibility criteria for the Certified Associate in Project Management (CAPM) certification, offered by the Project Management Institute (PMI), are designed to ensure that candidates have a foundational level of education and experience in project management. Here is a detailed overview of the CAPM eligibility criteria:
Educational Requirement:Candidates must possess a secondary degree, which can include a high school diploma, associate's degree, or a global equivalent.
Application Process:Candidates are required to submit an application to PMI, providing details about their educational background and project management experience. The application is typically completed online through the PMI website.
Payment of Fees:Once the application is approved, candidates need to pay the certification fee. PMI members usually receive a discounted rate for the CAPM exam.
Scheduling the Exam:After payment, candidates can schedule and take the CAPM exam at a designated Prometric testing center. The exam is computer-based and consists of 150 multiple-choice questions.
It's important for candidates to carefully review the eligibility criteria and ensure that they meet the specified requirements before applying for the CAPM certification. Meeting these criteria is essential for the successful completion of the certification process and obtaining the CAPM credential, which is globally recognized as a valuable certification for individuals starting their careers in project management.
CAPM Exam Structure
The Certified Associate in Project Management (CAPM) exam is designed to assess a candidate's knowledge and understanding of fundamental project management concepts, as outlined in the Project Management Institute's (PMI) Project Management Body of Knowledge (PMBOK) Guide. Here is an overview of the CAPM exam structure:
Number of Questions:The CAPM exam consists of a total of 150 multiple-choice questions.
Question Format:All questions in the CAPM exam are multiple-choice, meaning that each question has four answer choices, and the candidate must select the one that they believe is correct.
Time Duration:The duration of the CAPM exam is three hours. Candidates have this fixed period to complete all 150 questions.
Content Coverage:The exam content is based on the PMBOK Guide, which is a comprehensive guide to project management best practices. The questions cover the five process groups and ten knowledge areas defined in the PMBOK Guide.
Difficulty Level:The questions are designed to assess both the candidate's theoretical understanding of project management concepts and their ability to apply these concepts in practical scenarios.
Computer-Based Testing:The CAPM exam is a computer-based test (CBT), meaning that candidates take the exam on a computer at a designated Prometric testing center.
Results and Certification:Candidates receive their exam results immediately upon completion of the test. If successful, candidates are awarded the CAPM certification.
To prepare for the CAPM exam, candidates typically study the PMBOK Guide and may use additional study resources and practice exams. The exam structure aims to evaluate a candidate's knowledge and competence in foundational project management principles.
CAPM Exam Content
The Certified Associate in Project Management (CAPM) exam content is derived from the Project Management Institute's (PMI) Project Management Body of Knowledge (PMBOK) Guide, a comprehensive standard in the field of project management. The exam is structured to evaluate candidates on a range of project management principles across various knowledge areas.
The first aspect of the CAPM exam content involves understanding the broader Project Management Framework. This includes grasping the role of the project manager, the dynamics of stakeholders, and the influences that an organization can exert on project management practices.
Project Scope Management is another crucial component, evaluating candidates on their understanding of defining, validating, and controlling project scope. This ensures that the project encompasses all the work required for successful completion.
Project Schedule Management involves knowledge of activities such as defining activities, sequencing, estimating durations, developing schedules, and controlling the schedule to manage project timelines effectively.
In Project Cost Management, candidates are tested on their grasp of processes related to estimating, budgeting, and controlling costs within the project. This is vital for effective financial management of the project.
Quality is a critical consideration, and Project Quality Management assesses candidates on their understanding of planning, assurance, and control processes to ensure that project deliverables meet specified requirements.
Project Resource Management involves knowledge of processes related to acquiring, developing, and managing the project team and physical resources. Effective resource management is crucial for project success.
Lastly, Project Stakeholder Management assesses candidates on their ability to identify stakeholders, plan stakeholder engagement, and manage and control stakeholder engagement to ensure project success.
Additionally, candidates should be aware of ethical considerations and professional responsibilities in project management, reflecting the importance of ethical behavior in the profession. The CAPM exam content is designed to be comprehensive, covering a wide array of topics that are crucial for effective project management practice.
CAPM Exam Day
On the day of the Certified Associate in Project Management (CAPM) exam, it's crucial to approach the experience with a combination of preparedness and calmness. In the lead-up to the exam, it's advisable to engage in a brief review of key concepts without attempting to cram new information. Ensure you have all the required identification documents and your exam authorization from the Project Management Institute (PMI) in order to streamline the check-in process at the testing center.
Upon arriving at the exam center, plan to be there well ahead of time to ease into the environment and minimize stress. Dress comfortably, considering that you'll be seated for an extended period, and be mindful of any items allowed by the testing center. Once inside, carefully listen to the instructions provided by the exam proctor and follow the guidelines for the testing environment.
During the exam, make effective use of any provided scratch paper for calculations or notes. Manage your time wisely, as each question carries equal weight, and avoid spending excessive time on any single question. If you encounter challenging questions, stay calm and move on, with the option to revisit them during a review if time permits.
After completing the exam, submit your answers, and if taking a computer-based exam, receive immediate results. Take a moment to review any marked questions if time allows. Whether you pass or not, reflect on your performance, identifying areas of strength and those that may need improvement. If successful, consider your next steps in the project management journey. If a retake is necessary, use feedback from the score report to guide focused study efforts. Ultimately, approaching the CAPM exam day with a balanced mindset and adherence to logistical details enhances the likelihood of a successful and stress-free experience.
Maintaining CAPM Certification
Maintaining the Certified Associate in Project Management (CAPM) certification involves a commitment to ongoing professional development and engagement in the field of project management. CAPM certification is valid for five years, and to ensure its continued relevance and currency, certified professionals must fulfill the Continuing Certification Requirements (CCR) established by the Project Management Institute (PMI).
Engaging in continuous learning and staying updated on industry best practices is not only a requirement but also an opportunity for CAPM professionals to enhance their knowledge and skills. PMI provides a comprehensive online system for reporting and tracking PDUs, making it convenient for certified individuals to document their professional development activities.
Additionally, maintaining an active PMI membership is encouraged. PMI members enjoy access to a wide range of resources, networking opportunities, and exclusive events that can contribute to ongoing professional growth. Staying connected to the project management community through membership facilitates the exchange of ideas, experiences, and best practices.
In summary, maintaining the CAPM certification is not only a requirement but an opportunity for continuous professional development. By earning PDUs through various activities and staying engaged in the project management community, certified professionals can ensure that their skills remain current and relevant, contributing to their success in the dynamic field of project management.
Career Benefits of CAPM Certification
The Certified Associate in Project Management (CAPM) certification provides professionals with a host of career benefits, positioning them for success in the dynamic field of project management. One of the primary advantages is the global recognition and credibility that comes with a certification awarded by the Project Management Institute (PMI). This acknowledgment opens doors to a variety of opportunities, especially for those at the entry level, as it signifies a commitment to mastering fundamental project management principles.
CAPM serves as an ideal credential for individuals seeking entry into the project management profession. It acts as a stepping stone for career advancement, offering a structured framework for building expertise. As professionals gain practical experience, the CAPM certification provides a solid foundation that can be leveraged for pursuing more advanced certifications, such as the esteemed Project Management Professional (PMP) designation.
Employers worldwide recognize and value PMI certifications, and CAPM is often listed as a preferred qualification in job postings. The certification equips individuals with standardized knowledge of project management processes, enhancing their ability to contribute effectively to project teams. CAPM-certified professionals bring a level of confidence to their roles, backed by a common understanding of industry best practices outlined in the Project Management Body of Knowledge (PMBOK) Guide.
CAPM certification not only validates a professional's foundational knowledge in project management but also opens doors to diverse career paths. The certification's global recognition, standardized approach, and emphasis on continuous learning contribute to the career growth and success of individuals in the field of project management.
Conclusion
In conclusion, the Certified Associate in Project Management (CAPM) certification stands as a valuable asset for professionals aspiring to enter the world of project management or seeking to advance their careers in the field. As a globally recognized credential awarded by the Project Management Institute (PMI), the CAPM certification offers a standardized framework for understanding project management principles and practices.
The career benefits of CAPM are multifaceted. For those at the entry level, it provides a credible pathway into project management roles, opening doors to a range of opportunities. As professionals gain practical experience, the certification serves as a foundational step toward more advanced certifications, such as the Project Management Professional (PMP) designation.
CAPM not only signifies a commitment to excellence but also enhances professionals' confidence in their project management abilities. Employers value the certification for its global recognition and adherence to industry standards, often listing it as a preferred qualification in job postings. This recognition, coupled with the standardized approach outlined in the Project Management Body of Knowledge (PMBOK) Guide, ensures that CAPM-certified individuals contribute effectively to project teams and align with best practices.
The benefits extend beyond the technical aspects of project management. CAPM certification fosters a sense of community through PMI membership, providing networking opportunities, mentorship, and continuous learning. The certification's emphasis on maintaining relevance through ongoing professional development ensures that certified professionals stay at the forefront of industry trends.
In essence, the CAPM certification is a catalyst for career growth and success. It not only validates foundational knowledge but also empowers professionals to navigate the complexities of project management with confidence. As individuals embark on their CAPM journey, they join a global community of practitioners dedicated to advancing the profession, setting the stage for a fulfilling and prosperous career in project management.
Read More
The Certified Associate in Project Management (CAPM)® certification is a credential designed to prepare candidates for entry-level project management positions. It is administered by the Project Management Institute (PMI), a leading worldwide organisation in project management.
Certainly! The CAPM (Certified Associate in Project Management) certification is a globally recognized entry-level certification for project management professionals. It is offered by the Project Management Institute (PMI) and is designed for individuals who are interested in or just starting their careers in project management.
The CAPM certification is a valuable credential for individuals seeking to establish a foundation in project management. It provides a standardized framework and demonstrates a commitment to the profession. As individuals gain more experience, they may choose to pursue advanced certifications such as the Project Management Professional (PMP) certification.
Candidates interested in obtaining the most up-to-date information on the CAPM certification should refer to the official PMI website or contact PMI directly.
Table of contents
-
Introduction to Project Management
-
Overview of CAPM Certification
-
PMI and CAPM
-
CAPM Eligibility Criteria
-
CAPM Exam Structure
-
CAPM Exam Content
-
Preparing for the CAPM Exam
-
CAPM Exam Day
-
Maintaining CAPM Certification
-
Career Benefits of CAPM Certification
-
Conclusion
Introduction to Project Management
Project management is a multifaceted discipline integral to achieving organizational objectives. It encompasses the strategic application of knowledge, skills, tools, and techniques to navigate the complexities of project execution. At its core, project management involves planning, executing, monitoring, and closing projects to meet specific goals within predetermined success criteria. Projects, characterized by their uniqueness, have defined start and end points, specific objectives, and often require cross-functional teams collaborating towards a common purpose.
The role of a project manager is pivotal in orchestrating these efforts. Project managers lead teams through the initiation, planning, execution, monitoring and controlling, and closure phases of the project life cycle. Within this framework, various constraints such as time, cost, scope, quality, and risk must be carefully balanced to deliver a successful outcome. Identifying and managing stakeholders—individuals or groups with an interest or influence in the project—is another critical aspect of effective project management.
Project management processes, as defined by the Project Management Institute (PMI), provide a structured approach. These processes include initiating, planning, executing, monitoring and controlling, and closing. Additionally, organizations adopt different project management methodologies, such as Agile, Waterfall, or Scrum, based on the nature of the project and organizational preferences.
Individuals aspiring to lead or contribute to successful projects often pursue certifications like the Certified Associate in Project Management (CAPM) or Project Management Professional (PMP) to validate their skills and knowledge. Whether in business, IT, construction, or other industries, understanding and applying project management principles are essential for ensuring efficiency, minimizing risks, and achieving project objectives.
Overview of CAPM Certification
The Certified Associate in Project Management (CAPM) certification, offered by the Project Management Institute (PMI), serves as a foundational credential for those seeking entry into the field of project management. Its primary purpose is to validate a candidate's comprehension of essential project management concepts and terminology. To be eligible for the CAPM exam, candidates must possess a secondary degree, such as a high school diploma or associate's degree, along with either 1,500 hours of project experience or 23 hours of formal project management education.
The CAPM exam itself is a computer-based test comprising 150 multiple-choice questions, covering the five key process groups of project management: Initiating, Planning, Executing, Monitoring and Controlling, and Closing. With a duration of three hours, the exam evaluates candidates on their understanding of project management processes outlined in the Project Management Body of Knowledge (PMBOK Guide), the primary reference material provided by PMI.
Successful preparation for the CAPM exam involves a thorough study of the PMBOK Guide, practice exams to familiarize candidates with the format, and participation in study groups for collaborative learning. As individuals progress in their project management careers, they may choose to pursue advanced certifications, such as the Project Management Professional (PMP) certification. Overall, the CAPM certification serves as a valuable starting point for those aspiring to establish a solid foundation in project management and advance their professional growth in this dynamic field.
PMI and CAPM
The Project Management Institute (PMI) stands as a pivotal force in the field of project management. Established in 1969, PMI is a non-profit organization committed to advancing the practice, science, and profession of project management on a global scale. At the heart of PMI's contributions is the Project Management Body of Knowledge (PMBOK Guide), a comprehensive resource that sets industry standards and serves as a foundational guide for project management professionals.
CAPM certification brings with it a host of benefits. Recognized globally, it establishes a standardized framework for project management knowledge and acts as a stepping stone for career advancement in the field. CAPM holders contribute to a common language and understanding of fundamental project management principles within the industry.
While PMI membership is not mandatory for certification, it offers additional advantages. PMI members gain access to a wealth of resources, networking opportunities, and enjoy discounts on certification exams and educational events. In essence, PMI, through its standards and certifications, including the CAPM, plays a pivotal role in shaping the professional landscape of project management, fostering growth, and facilitating the exchange of knowledge and expertise among practitioners worldwide.
CAPM Eligibility Criteria
The eligibility criteria for the Certified Associate in Project Management (CAPM) certification, offered by the Project Management Institute (PMI), are designed to ensure that candidates have a foundational level of education and experience in project management. Here is a detailed overview of the CAPM eligibility criteria:
Educational Requirement:Candidates must possess a secondary degree, which can include a high school diploma, associate's degree, or a global equivalent.
Application Process:Candidates are required to submit an application to PMI, providing details about their educational background and project management experience. The application is typically completed online through the PMI website.
Payment of Fees:Once the application is approved, candidates need to pay the certification fee. PMI members usually receive a discounted rate for the CAPM exam.
Scheduling the Exam:After payment, candidates can schedule and take the CAPM exam at a designated Prometric testing center. The exam is computer-based and consists of 150 multiple-choice questions.
It's important for candidates to carefully review the eligibility criteria and ensure that they meet the specified requirements before applying for the CAPM certification. Meeting these criteria is essential for the successful completion of the certification process and obtaining the CAPM credential, which is globally recognized as a valuable certification for individuals starting their careers in project management.
CAPM Exam Structure
The Certified Associate in Project Management (CAPM) exam is designed to assess a candidate's knowledge and understanding of fundamental project management concepts, as outlined in the Project Management Institute's (PMI) Project Management Body of Knowledge (PMBOK) Guide. Here is an overview of the CAPM exam structure:
Number of Questions:The CAPM exam consists of a total of 150 multiple-choice questions.
Question Format:All questions in the CAPM exam are multiple-choice, meaning that each question has four answer choices, and the candidate must select the one that they believe is correct.
Time Duration:The duration of the CAPM exam is three hours. Candidates have this fixed period to complete all 150 questions.
Content Coverage:The exam content is based on the PMBOK Guide, which is a comprehensive guide to project management best practices. The questions cover the five process groups and ten knowledge areas defined in the PMBOK Guide.
Difficulty Level:The questions are designed to assess both the candidate's theoretical understanding of project management concepts and their ability to apply these concepts in practical scenarios.
Computer-Based Testing:The CAPM exam is a computer-based test (CBT), meaning that candidates take the exam on a computer at a designated Prometric testing center.
Results and Certification:Candidates receive their exam results immediately upon completion of the test. If successful, candidates are awarded the CAPM certification.
To prepare for the CAPM exam, candidates typically study the PMBOK Guide and may use additional study resources and practice exams. The exam structure aims to evaluate a candidate's knowledge and competence in foundational project management principles.
CAPM Exam Content
The Certified Associate in Project Management (CAPM) exam content is derived from the Project Management Institute's (PMI) Project Management Body of Knowledge (PMBOK) Guide, a comprehensive standard in the field of project management. The exam is structured to evaluate candidates on a range of project management principles across various knowledge areas.
The first aspect of the CAPM exam content involves understanding the broader Project Management Framework. This includes grasping the role of the project manager, the dynamics of stakeholders, and the influences that an organization can exert on project management practices.
Project Scope Management is another crucial component, evaluating candidates on their understanding of defining, validating, and controlling project scope. This ensures that the project encompasses all the work required for successful completion.
Project Schedule Management involves knowledge of activities such as defining activities, sequencing, estimating durations, developing schedules, and controlling the schedule to manage project timelines effectively.
In Project Cost Management, candidates are tested on their grasp of processes related to estimating, budgeting, and controlling costs within the project. This is vital for effective financial management of the project.
Quality is a critical consideration, and Project Quality Management assesses candidates on their understanding of planning, assurance, and control processes to ensure that project deliverables meet specified requirements.
Project Resource Management involves knowledge of processes related to acquiring, developing, and managing the project team and physical resources. Effective resource management is crucial for project success.
Lastly, Project Stakeholder Management assesses candidates on their ability to identify stakeholders, plan stakeholder engagement, and manage and control stakeholder engagement to ensure project success.
Additionally, candidates should be aware of ethical considerations and professional responsibilities in project management, reflecting the importance of ethical behavior in the profession. The CAPM exam content is designed to be comprehensive, covering a wide array of topics that are crucial for effective project management practice.
CAPM Exam Day
On the day of the Certified Associate in Project Management (CAPM) exam, it's crucial to approach the experience with a combination of preparedness and calmness. In the lead-up to the exam, it's advisable to engage in a brief review of key concepts without attempting to cram new information. Ensure you have all the required identification documents and your exam authorization from the Project Management Institute (PMI) in order to streamline the check-in process at the testing center.
Upon arriving at the exam center, plan to be there well ahead of time to ease into the environment and minimize stress. Dress comfortably, considering that you'll be seated for an extended period, and be mindful of any items allowed by the testing center. Once inside, carefully listen to the instructions provided by the exam proctor and follow the guidelines for the testing environment.
During the exam, make effective use of any provided scratch paper for calculations or notes. Manage your time wisely, as each question carries equal weight, and avoid spending excessive time on any single question. If you encounter challenging questions, stay calm and move on, with the option to revisit them during a review if time permits.
After completing the exam, submit your answers, and if taking a computer-based exam, receive immediate results. Take a moment to review any marked questions if time allows. Whether you pass or not, reflect on your performance, identifying areas of strength and those that may need improvement. If successful, consider your next steps in the project management journey. If a retake is necessary, use feedback from the score report to guide focused study efforts. Ultimately, approaching the CAPM exam day with a balanced mindset and adherence to logistical details enhances the likelihood of a successful and stress-free experience.
Maintaining CAPM Certification
Maintaining the Certified Associate in Project Management (CAPM) certification involves a commitment to ongoing professional development and engagement in the field of project management. CAPM certification is valid for five years, and to ensure its continued relevance and currency, certified professionals must fulfill the Continuing Certification Requirements (CCR) established by the Project Management Institute (PMI).
Engaging in continuous learning and staying updated on industry best practices is not only a requirement but also an opportunity for CAPM professionals to enhance their knowledge and skills. PMI provides a comprehensive online system for reporting and tracking PDUs, making it convenient for certified individuals to document their professional development activities.
Additionally, maintaining an active PMI membership is encouraged. PMI members enjoy access to a wide range of resources, networking opportunities, and exclusive events that can contribute to ongoing professional growth. Staying connected to the project management community through membership facilitates the exchange of ideas, experiences, and best practices.
In summary, maintaining the CAPM certification is not only a requirement but an opportunity for continuous professional development. By earning PDUs through various activities and staying engaged in the project management community, certified professionals can ensure that their skills remain current and relevant, contributing to their success in the dynamic field of project management.
Career Benefits of CAPM Certification
The Certified Associate in Project Management (CAPM) certification provides professionals with a host of career benefits, positioning them for success in the dynamic field of project management. One of the primary advantages is the global recognition and credibility that comes with a certification awarded by the Project Management Institute (PMI). This acknowledgment opens doors to a variety of opportunities, especially for those at the entry level, as it signifies a commitment to mastering fundamental project management principles.
CAPM serves as an ideal credential for individuals seeking entry into the project management profession. It acts as a stepping stone for career advancement, offering a structured framework for building expertise. As professionals gain practical experience, the CAPM certification provides a solid foundation that can be leveraged for pursuing more advanced certifications, such as the esteemed Project Management Professional (PMP) designation.
Employers worldwide recognize and value PMI certifications, and CAPM is often listed as a preferred qualification in job postings. The certification equips individuals with standardized knowledge of project management processes, enhancing their ability to contribute effectively to project teams. CAPM-certified professionals bring a level of confidence to their roles, backed by a common understanding of industry best practices outlined in the Project Management Body of Knowledge (PMBOK) Guide.
CAPM certification not only validates a professional's foundational knowledge in project management but also opens doors to diverse career paths. The certification's global recognition, standardized approach, and emphasis on continuous learning contribute to the career growth and success of individuals in the field of project management.
Conclusion
In conclusion, the Certified Associate in Project Management (CAPM) certification stands as a valuable asset for professionals aspiring to enter the world of project management or seeking to advance their careers in the field. As a globally recognized credential awarded by the Project Management Institute (PMI), the CAPM certification offers a standardized framework for understanding project management principles and practices.
The career benefits of CAPM are multifaceted. For those at the entry level, it provides a credible pathway into project management roles, opening doors to a range of opportunities. As professionals gain practical experience, the certification serves as a foundational step toward more advanced certifications, such as the Project Management Professional (PMP) designation.
CAPM not only signifies a commitment to excellence but also enhances professionals' confidence in their project management abilities. Employers value the certification for its global recognition and adherence to industry standards, often listing it as a preferred qualification in job postings. This recognition, coupled with the standardized approach outlined in the Project Management Body of Knowledge (PMBOK) Guide, ensures that CAPM-certified individuals contribute effectively to project teams and align with best practices.
The benefits extend beyond the technical aspects of project management. CAPM certification fosters a sense of community through PMI membership, providing networking opportunities, mentorship, and continuous learning. The certification's emphasis on maintaining relevance through ongoing professional development ensures that certified professionals stay at the forefront of industry trends.
In essence, the CAPM certification is a catalyst for career growth and success. It not only validates foundational knowledge but also empowers professionals to navigate the complexities of project management with confidence. As individuals embark on their CAPM journey, they join a global community of practitioners dedicated to advancing the profession, setting the stage for a fulfilling and prosperous career in project management.
Introduction to Lean Management: Key Principles and Concepts
In a world where efficiency, sustainability, and productivity are the cornerstones of success for businesses and organizations, mastering the art of lean management has never been more critical. Lean management is not just a buzzword; it's a proven methodology that has revolutionized industries, improved processes, and enhanced profitability. Whether you're an entrepreneur, a manager, or simply someone curious about what makes organizations work seamlessly, understanding the key principles and concepts of lean management is a journey well worth embarking upon.
Lean management, often referred to as simply "lean," is not a new concept, but its applications and impact continue to evolve. At its core, lean is about doing more with less. It's about eliminating waste, optimizing resources, and constantly improving processes to deliver more value to customers, stakeholders, and employees. While lean management initially gained fame in manufacturing settings, its principles have since transcended industries, finding a place in healthcare, service sectors, and beyond.
In this blog post, we're taking the first step in unraveling the mysteries of lean management. We'll explore the fundamental principles and concepts that serve as the foundation for lean thinking. You'll discover how lean management can lead to cost reductions, improved quality, faster delivery times, and increased customer satisfaction. By the end of this journey, you'll have a clear understanding of the fundamental lean principles and how they can be applied to any organization or process.
Table of contents
-
The Origins of Lean Thinking
-
Five Lean Principles
-
Eliminating Waste
-
Continuous Improvement (Kaizen)
-
Value Stream Mapping
-
Just-In-Time (JIT) Production
-
Pull Systems and Kanban
-
Standardized Work
-
Gemba Walks
-
Key Performance Indicators (KPIs) for Lean
-
Conclusion
The Origins of Lean Thinking
In the world of management and process optimization, few concepts have had as profound an impact as lean thinking. It's a methodology that has transcended industries, revolutionized production processes, and significantly improved efficiency. To truly grasp the power of lean thinking, it's essential to delve into its origins and understand how it all began.
The Birthplace: Toyota's Production System
The roots of lean thinking can be traced back to post-World War II Japan. The country was rebuilding, and resources were scarce. Toyota, under the leadership of visionary Taiichi Ohno and Eiji Toyoda, faced the challenge of making the most of limited resources. This necessity became the mother of invention, giving rise to what we now know as the Toyota Production System (TPS).
The Influential Figures
Two figures, in particular, played pivotal roles in the development of lean thinking:
Taiichi Ohno: Often referred to as the "father of the Toyota Production System," Ohno was instrumental in the development of key lean concepts. He focused on reducing waste, particularly overproduction, and introduced the concept of "Just-In-Time" (JIT) production, which remains a cornerstone of lean thinking.
Shigeo Shingo: Working in tandem with Ohno, Shigeo Shingo contributed to the TPS by developing practices such as Poka-Yoke (error-proofing) and Single-Minute Exchange of Die (SMED), which aimed to reduce setup times and errors.
Over time, the success of the TPS and lean thinking became evident, and it expanded beyond Toyota. Other industries and organizations worldwide started adopting these principles to improve their processes. Lean thinking's influence extended to manufacturing, healthcare, service sectors, and more, becoming a universal approach to efficiency and waste reduction.
Understanding the origins of lean thinking helps us appreciate the transformative power of these principles. It's a journey that began with necessity in a post-war Japan and continues to shape the way organizations operate today, emphasizing efficiency, quality, and the relentless pursuit of improvement. Lean thinking is not just a management approach; it's a philosophy that inspires organizations to do more with less and continuously strive for perfection.
Five Lean Principles
Lean management is built upon a set of fundamental principles that guide organizations towards improved efficiency, reduced waste, and enhanced value delivery. These principles provide a roadmap for organizations seeking to streamline processes and operations. Let's delve into the five core lean principles:
Value
At the core of lean management is the principle of "value." This principle focuses on defining value from the customer's perspective. In essence, anything that doesn't directly contribute to meeting customer needs and expectations is considered waste. To apply this principle, organizations must:
Value Stream
The "value stream" principle extends beyond individual processes to look at the entire flow of activities required to deliver a product or service. This involves mapping the steps, from raw materials to the customer's hands, to understand how value is created and how waste is generated. By analyzing the value stream, organizations can:
Flow
The "flow" principle emphasizes the importance of creating a smooth and continuous workflow. In a lean context, this means ensuring that work moves swiftly from one step to the next with minimal interruptions or delays. To achieve flow, organizations should:
Pull
The "pull" principle is about aligning production with customer demand. Rather than producing items in anticipation of demand (push), organizations should respond directly to customer orders (pull). Key elements of this principle include:
Perfection
Continuous improvement is the essence of the "perfection" principle. Lean management encourages organizations to never stop seeking better ways of working. Perfection is an ideal that may never be fully achieved, but it's the relentless pursuit of it that drives progress. To practice this principle, organizations should:
These five core lean principles serve as the foundation for lean thinking and can be applied across various industries and organizational contexts. By understanding and implementing these principles, organizations can reduce waste, enhance productivity, and improve the overall value they provide to customers.
Eliminating Waste
In the world of lean management, the relentless pursuit of efficiency revolves around one fundamental principle: eliminating waste. Lean thinking views waste as an obstacle to delivering value to customers and seeks to minimize or eradicate it from all processes and operations. Let's explore the concept of waste elimination and the different types of waste that organizations aim to conquer.
The Eight Types of Waste (Downtime)
Overproduction: Producing more than what the customer demands leads to excess inventory, storage costs, and the risk of obsolescence.
Inventory: Excessive inventory ties up capital, consumes storage space, and can lead to increased handling and damage.
Defects: Defective products or services result in rework, scrap, and additional resources required for correction.
Waiting: Unproductive downtime, whether due to equipment breakdowns or inefficient processes, adds no value.
Overprocessing: Performing unnecessary or redundant steps in a process is a waste of time and resources.
Motion: Excessive physical movement or unnecessary actions by employees can be a source of waste.
Transportation: Unneeded or excessive movement of materials or products between processes or locations increases costs and the risk of damage.
Underutilized Employee Skills: Failing to tap into the full potential of employees' skills and knowledge is a waste of talent and creativity.
The Quest to Eliminate Waste
Lean management techniques aim to identify and eliminate these eight forms of waste, creating streamlined, efficient, and value-driven processes. The process of waste elimination often involves tools like value stream mapping, which helps organizations visualize the flow of value and identify areas of waste.
Moreover, continuous improvement, often referred to as "Kaizen," is a cornerstone of lean management. It encourages employees at all levels to regularly identify and address waste in their work. By empowering employees to participate in waste reduction, organizations can continuously improve their operations.
Continuous Improvement (Kaizen)
In the realm of lean management, one principle stands out as the driving force behind ongoing progress and efficiency - Kaizen, which is the Japanese word for "change for better" or "continuous improvement." Kaizen is not just a concept; it's a philosophy that shapes the way organizations operate, strive for perfection, and embrace a culture of continuous growth and progress.
The Essence of Kaizen
At its core, Kaizen is about making small, incremental improvements in all aspects of an organization, from processes and operations to products and services. Instead of relying on infrequent, major overhauls or revolutionary changes, Kaizen encourages the consistent and relentless pursuit of excellence through a series of small, manageable, and sustainable improvements.
Key Principles of Kaizen
Kaizen is guided by several principles that help organizations create a culture of continuous improvement:
Improvement is Everyone's Responsibility: In a Kaizen-oriented organization, everyone, from leadership to frontline employees, is responsible for seeking and implementing improvements. This bottom-up approach harnesses the collective intelligence and expertise of the entire workforce.
Small Steps Lead to Big Gains: Kaizen advocates for taking small, manageable steps toward improvement rather than attempting radical changes. These small changes are less disruptive, easier to implement, and collectively lead to significant progress.
Standardization and Documentation: Documenting processes and standardizing best practices are essential in Kaizen. This ensures that improvements are sustained over time and can be built upon.
Elimination of Waste: Kaizen aligns with the lean management principle of eliminating waste. The focus is on identifying and eliminating non-value-adding activities and processes to enhance efficiency and value delivery.
Customer-Centric Approach: The ultimate goal of Kaizen is to enhance the quality of products and services, meeting or exceeding customer expectations. Customer feedback is a valuable source of insight for improvement.
The Kaizen Culture
Implementing Kaizen is not just about the individual improvements but also about fostering a culture of continuous learning, adaptability, and innovation. Organizations that embrace the Kaizen culture encourage employees to seek and implement improvements daily.
Kaizen is the lifeblood of lean management, driving organizations to achieve higher efficiency, better quality, and greater customer satisfaction through small, continuous improvements. By prioritizing Kaizen and creating a culture of continuous improvement, organizations can remain adaptable, competitive, and ever-evolving in an ever-changing business landscape.
Value Stream Mapping
In the world of lean management, one of the most powerful tools for understanding, analyzing, and optimizing processes is value stream mapping. Value stream mapping is a visual representation of how materials and information flow through an entire process, from the initial customer need to the finished product or service. It allows organizations to identify and eliminate waste, improve efficiency, and enhance the overall value delivered to customers.
What is Value Stream Mapping?
Value stream mapping is a structured, visual technique that provides a clear and holistic view of a process or series of processes. It captures not only the steps involved but also the information flow, cycle times, and decision points, enabling organizations to see the entire process at a glance.
The Components of Value Stream Mapping
A typical value stream map includes several key components:
Value-Adding Activities: These are the activities that directly contribute to creating value for the customer. They are the steps in the process that customers are willing to pay for.
Non-Value-Adding Activities (Waste): These are activities that do not add value but are necessary due to inefficiencies or other constraints. Identifying and minimizing waste is a primary goal of value stream mapping.
Information Flow: This component illustrates how information, such as customer orders, instructions, and feedback, flows within the process.
Cycle Time: Value stream maps often include data on the time it takes to complete each step in the process, helping to identify bottlenecks and areas of delay.
Inventory Levels: Visual representation of the inventory at various stages in the process, which can highlight areas of overproduction and inefficiency.
Value stream mapping is a powerful tool that enables organizations to gain insights into their processes, reduce waste, and enhance efficiency. By creating a visual representation of the entire value stream, organizations can identify areas for improvement and drive a culture of continuous enhancement, aligning processes with customer needs and delivering value more effectively.
Just-In-Time (JIT) Production
Just-In-Time (JIT) production is a lean manufacturing and inventory management strategy that has revolutionized the way organizations produce goods and manage their supply chains. JIT aims to reduce waste, minimize inventory, and optimize production, all with the goal of delivering products or services to customers exactly when they're needed.
Understanding JIT Production:
At its core, JIT is about producing only what is needed, in the quantity needed, and at the time it is needed, with minimal waste. The primary objective is to eliminate excess inventory and the associated costs while maintaining a smooth production flow.
Key Principles of JIT Production:
JIT production is guided by several key principles:
Pull System: JIT operates on a pull system, where production is initiated based on actual customer demand. This contrasts with traditional push systems, where products are produced based on forecasts or speculative demand.
Continuous Flow: JIT encourages a continuous and unbroken flow of work through the production process, minimizing interruptions, waiting times, and inventory buildup.
Kanban System: A core element of JIT is the use of Kanban, a visual signaling system that ensures just-in-time production. Kanban cards or signals trigger the replenishment of materials only when they are needed, preventing overproduction.
Takt Time: Takt time is the heartbeat of JIT. It is the rate at which products must be produced to meet customer demand. JIT aligns production to match this takt time.
Reducing Setup Times (SMED): JIT places great emphasis on reducing setup times to allow for more frequent, smaller production runs. The Single-Minute Exchange of Die (SMED) methodology is often used for this purpose.
In summary, Just-In-Time (JIT) production is a lean strategy that seeks to optimize production and minimize waste by producing goods or services exactly when they are needed. By eliminating excess inventory and aligning production with customer demand, organizations can achieve cost savings, improve efficiency, and enhance their overall competitiveness. However, JIT production requires careful planning and a reliable supply chain to be effective.
Pull Systems and Kanban
Pull systems and Kanban are integral components of lean manufacturing and production, facilitating efficient and waste-reducing processes. By employing these principles, organizations can synchronize production with customer demand, minimize inventory, and ensure a smooth workflow.
Pull Systems in Lean Manufacturing
Pull systems operate in contrast to traditional push systems, which produce goods based on forecasts or production schedules. In a pull system, work is initiated in response to actual customer demand, which "pulls" the product through the production process. The primary objective is to avoid overproduction and excess inventory, as well as to respond quickly to changes in customer requirements.
Key elements of pull systems include:
Kanban: A visual signaling system that regulates the flow of work. Kanban cards or signals are used to indicate when more materials or work can be pulled into a process.
Takt Time: The rate at which products must be produced to meet customer demand, based on the available production time. Takt time sets the pace for production in a pull system.
Continuous Flow: A pull system encourages a continuous and uninterrupted flow of work, minimizing downtime and waiting times.
Pull systems and Kanban are essential components of lean manufacturing, ensuring that work is initiated based on actual customer demand, minimizing inventory, and facilitating a smooth and efficient production process. When implemented effectively, these principles reduce waste, enhance quality, and improve overall production efficiency.
Standardized Work
Standardized work is a fundamental concept within the realm of lean management. It plays a crucial role in ensuring consistency, efficiency, and continuous improvement in processes and operations. Standardized work involves documenting and following a set of predefined procedures, methods, and best practices for completing a task or a process.
Key Components of Standardized Work
Standardized work typically includes the following key components:
Work Sequence: A detailed and specific sequence of tasks, steps, or activities that need to be completed to accomplish a particular job or process.
Takt Time: The rate at which work must be completed to meet customer demand. Takt time is often used to pace the work.
Standard Work-in-Process (WIP): The prescribed amount of work or inventory that should be in process at any given time to maintain flow and minimize waste.
Work Instructions: Clear and precise instructions for each task or operation, often including information on tools, equipment, and quality standards.
Safety Measures: Guidelines for ensuring the safety of workers during the execution of tasks.
Quality Standards: Specifications for the desired quality of work or products.
Standardized work is a foundational element of lean management, providing a structured approach to ensure consistency, efficiency, and quality in processes and operations. By documenting and adhering to standardized work, organizations can create a solid foundation for continuous improvement and operational excellence.
Gemba Walks
In the world of lean management, the Gemba walk is a powerful practice that allows leaders and managers to gain firsthand insights into their organization's processes, identify opportunities for improvement, and build a culture of continuous enhancement. The term "Gemba" is Japanese and refers to the "actual place" where work happens, whether that's a shop floor, a healthcare facility, an office, or any other work environment.
The Purpose of Gemba Walks
The primary purpose of Gemba walks is to encourage leaders and managers to engage with the work environment, interact with employees, and gain a deep understanding of how processes operate. By physically visiting the Gemba, leaders can:
Identify Waste: Gemba walks help in recognizing inefficiencies, bottlenecks, and non-value-adding activities (waste) in the work process.
Enhance Communication: Direct interactions with employees on the shop floor or in their work environment facilitate open communication and idea sharing.
Problem-Solving: Gemba walks allow leaders to see problems as they occur, understand their root causes, and work with employees to develop solutions.
Coaching and Learning: Leaders can offer guidance, mentorship, and learning opportunities to employees, fostering their development and improvement.
Observing Standard Work: Leaders can observe whether standardized work processes are being followed and make necessary adjustments.
Key Principles of Gemba Walks
To conduct effective Gemba walks, leaders should keep in mind the following principles:
Go and See for Yourself: Gemba walks involve firsthand observation, not just relying on reports or data. Leaders need to physically visit the workplace to understand the real situation.
Respect for People: The Gemba walk should be conducted with a respectful attitude, valuing the insights and expertise of the employees working in that environment.
Ask Why: Leaders should ask questions to dig deeper and understand the underlying reasons for what they observe.
Engage and Collaborate: Gemba walks are not inspections; they are opportunities to engage with employees and collaborate on improvements.
Foster a Culture of Improvement: Encourage employees to suggest improvements and be open to their ideas.
In summary, Gemba walks are an essential practice in lean management, allowing leaders to gain a deep understanding of their organization's processes, identify opportunities for improvement, and build a culture of continuous enhancement. By physically engaging with the work environment and the people who operate within it, organizations can make more informed decisions and drive operational excellence.
Key Performance Indicators (KPIs) for Lean
In lean management, the use of Key Performance Indicators (KPIs) is essential for monitoring, evaluating, and continuously improving operations. KPIs help organizations track their progress toward lean goals, identify areas for improvement, and ensure that lean principles are effectively applied. Here are some key KPIs commonly used in lean management:
Cycle Time: The time it takes to complete a specific task, process, or operation. Reducing cycle times is a fundamental objective of lean management, as it leads to greater efficiency.
Lead Time: The time it takes to fulfill a customer order, from the moment the order is placed to when the product is delivered. Reducing lead times is crucial for meeting customer demand more effectively.
Quality Defect Rate: This KPI measures the number of defects or errors in a product or service. Reducing the defect rate is vital for enhancing quality and customer satisfaction.
WIP (Work-in-Process) Inventory: Measuring the amount of work in process helps identify overproduction and areas where materials are waiting to be processed.
First Pass Yield (FPY): FPY measures the percentage of products that pass through a process or stage without the need for rework or corrections. A high FPY indicates effective quality control.
Customer Satisfaction: While not a numerical KPI, customer satisfaction is a critical measure of lean success. Satisfied customers are more likely to be repeat customers and advocates for your organization.
Waste Reduction: Quantifying and tracking reductions in the eight types of waste (as identified in lean management) can be a key performance indicator in itself. This includes waste reduction in areas such as overproduction, inventory, and defects.
Effective lean management involves selecting KPIs that align with your organization's goals and continuously monitoring and analyzing them. KPIs provide the data needed to make informed decisions, foster a culture of improvement, and measure the impact of lean practices on efficiency, quality, and customer satisfaction.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, lean management is a powerful philosophy and set of principles aimed at optimizing processes, reducing waste, and enhancing efficiency across various industries and organizational contexts. This approach focuses on delivering value to customers while continuously improving operations. Throughout this discussion, we've explored key aspects of lean management, including its principles, tools, and key performance indicators (KPIs).
Lean management emphasizes the elimination of waste, the pursuit of perfection, and a commitment to continuous improvement. Key principles such as value stream mapping, standardized work, pull systems, and Kaizen contribute to streamlining operations and driving organizational success.
Additionally, concepts like Gemba walks encourage leaders to engage with the workplace, collaborate with employees, and identify opportunities for improvement at the grassroots level. Value stream mapping, Kanban, and Just-In-Time (JIT) production play crucial roles in reducing waste and optimizing production processes.
Standardized work ensures consistency and efficiency, while KPIs help measure performance and track progress. By monitoring key metrics such as cycle time, lead time, quality defect rates, and inventory turnover, organizations can better understand their strengths and areas for growth.
Incorporating lean management into an organization's culture can lead to significant benefits, including cost savings, improved product quality, enhanced customer satisfaction, and a competitive edge in today's dynamic business environment.
As organizations continue to adapt and evolve, the principles and practices of lean management remain invaluable in guiding them toward greater efficiency, effectiveness, and overall success. Lean is not just a management philosophy; it's a journey of continuous improvement and a commitment to delivering value while eliminating waste.
Read More
In a world where efficiency, sustainability, and productivity are the cornerstones of success for businesses and organizations, mastering the art of lean management has never been more critical. Lean management is not just a buzzword; it's a proven methodology that has revolutionized industries, improved processes, and enhanced profitability. Whether you're an entrepreneur, a manager, or simply someone curious about what makes organizations work seamlessly, understanding the key principles and concepts of lean management is a journey well worth embarking upon.
Lean management, often referred to as simply "lean," is not a new concept, but its applications and impact continue to evolve. At its core, lean is about doing more with less. It's about eliminating waste, optimizing resources, and constantly improving processes to deliver more value to customers, stakeholders, and employees. While lean management initially gained fame in manufacturing settings, its principles have since transcended industries, finding a place in healthcare, service sectors, and beyond.
In this blog post, we're taking the first step in unraveling the mysteries of lean management. We'll explore the fundamental principles and concepts that serve as the foundation for lean thinking. You'll discover how lean management can lead to cost reductions, improved quality, faster delivery times, and increased customer satisfaction. By the end of this journey, you'll have a clear understanding of the fundamental lean principles and how they can be applied to any organization or process.
Table of contents
-
The Origins of Lean Thinking
-
Five Lean Principles
-
Eliminating Waste
-
Continuous Improvement (Kaizen)
-
Value Stream Mapping
-
Just-In-Time (JIT) Production
-
Pull Systems and Kanban
-
Standardized Work
-
Gemba Walks
-
Key Performance Indicators (KPIs) for Lean
-
Conclusion
The Origins of Lean Thinking
In the world of management and process optimization, few concepts have had as profound an impact as lean thinking. It's a methodology that has transcended industries, revolutionized production processes, and significantly improved efficiency. To truly grasp the power of lean thinking, it's essential to delve into its origins and understand how it all began.
The Birthplace: Toyota's Production System
The roots of lean thinking can be traced back to post-World War II Japan. The country was rebuilding, and resources were scarce. Toyota, under the leadership of visionary Taiichi Ohno and Eiji Toyoda, faced the challenge of making the most of limited resources. This necessity became the mother of invention, giving rise to what we now know as the Toyota Production System (TPS).
The Influential Figures
Two figures, in particular, played pivotal roles in the development of lean thinking:
Taiichi Ohno: Often referred to as the "father of the Toyota Production System," Ohno was instrumental in the development of key lean concepts. He focused on reducing waste, particularly overproduction, and introduced the concept of "Just-In-Time" (JIT) production, which remains a cornerstone of lean thinking.
Shigeo Shingo: Working in tandem with Ohno, Shigeo Shingo contributed to the TPS by developing practices such as Poka-Yoke (error-proofing) and Single-Minute Exchange of Die (SMED), which aimed to reduce setup times and errors.
Over time, the success of the TPS and lean thinking became evident, and it expanded beyond Toyota. Other industries and organizations worldwide started adopting these principles to improve their processes. Lean thinking's influence extended to manufacturing, healthcare, service sectors, and more, becoming a universal approach to efficiency and waste reduction.
Understanding the origins of lean thinking helps us appreciate the transformative power of these principles. It's a journey that began with necessity in a post-war Japan and continues to shape the way organizations operate today, emphasizing efficiency, quality, and the relentless pursuit of improvement. Lean thinking is not just a management approach; it's a philosophy that inspires organizations to do more with less and continuously strive for perfection.
Five Lean Principles
Lean management is built upon a set of fundamental principles that guide organizations towards improved efficiency, reduced waste, and enhanced value delivery. These principles provide a roadmap for organizations seeking to streamline processes and operations. Let's delve into the five core lean principles:
Value
At the core of lean management is the principle of "value." This principle focuses on defining value from the customer's perspective. In essence, anything that doesn't directly contribute to meeting customer needs and expectations is considered waste. To apply this principle, organizations must:
Value Stream
The "value stream" principle extends beyond individual processes to look at the entire flow of activities required to deliver a product or service. This involves mapping the steps, from raw materials to the customer's hands, to understand how value is created and how waste is generated. By analyzing the value stream, organizations can:
Flow
The "flow" principle emphasizes the importance of creating a smooth and continuous workflow. In a lean context, this means ensuring that work moves swiftly from one step to the next with minimal interruptions or delays. To achieve flow, organizations should:
Pull
The "pull" principle is about aligning production with customer demand. Rather than producing items in anticipation of demand (push), organizations should respond directly to customer orders (pull). Key elements of this principle include:
Perfection
Continuous improvement is the essence of the "perfection" principle. Lean management encourages organizations to never stop seeking better ways of working. Perfection is an ideal that may never be fully achieved, but it's the relentless pursuit of it that drives progress. To practice this principle, organizations should:
These five core lean principles serve as the foundation for lean thinking and can be applied across various industries and organizational contexts. By understanding and implementing these principles, organizations can reduce waste, enhance productivity, and improve the overall value they provide to customers.
Eliminating Waste
In the world of lean management, the relentless pursuit of efficiency revolves around one fundamental principle: eliminating waste. Lean thinking views waste as an obstacle to delivering value to customers and seeks to minimize or eradicate it from all processes and operations. Let's explore the concept of waste elimination and the different types of waste that organizations aim to conquer.
The Eight Types of Waste (Downtime)
Overproduction: Producing more than what the customer demands leads to excess inventory, storage costs, and the risk of obsolescence.
Inventory: Excessive inventory ties up capital, consumes storage space, and can lead to increased handling and damage.
Defects: Defective products or services result in rework, scrap, and additional resources required for correction.
Waiting: Unproductive downtime, whether due to equipment breakdowns or inefficient processes, adds no value.
Overprocessing: Performing unnecessary or redundant steps in a process is a waste of time and resources.
Motion: Excessive physical movement or unnecessary actions by employees can be a source of waste.
Transportation: Unneeded or excessive movement of materials or products between processes or locations increases costs and the risk of damage.
Underutilized Employee Skills: Failing to tap into the full potential of employees' skills and knowledge is a waste of talent and creativity.
The Quest to Eliminate Waste
Lean management techniques aim to identify and eliminate these eight forms of waste, creating streamlined, efficient, and value-driven processes. The process of waste elimination often involves tools like value stream mapping, which helps organizations visualize the flow of value and identify areas of waste.
Moreover, continuous improvement, often referred to as "Kaizen," is a cornerstone of lean management. It encourages employees at all levels to regularly identify and address waste in their work. By empowering employees to participate in waste reduction, organizations can continuously improve their operations.
Continuous Improvement (Kaizen)
In the realm of lean management, one principle stands out as the driving force behind ongoing progress and efficiency - Kaizen, which is the Japanese word for "change for better" or "continuous improvement." Kaizen is not just a concept; it's a philosophy that shapes the way organizations operate, strive for perfection, and embrace a culture of continuous growth and progress.
The Essence of Kaizen
At its core, Kaizen is about making small, incremental improvements in all aspects of an organization, from processes and operations to products and services. Instead of relying on infrequent, major overhauls or revolutionary changes, Kaizen encourages the consistent and relentless pursuit of excellence through a series of small, manageable, and sustainable improvements.
Key Principles of Kaizen
Kaizen is guided by several principles that help organizations create a culture of continuous improvement:
Improvement is Everyone's Responsibility: In a Kaizen-oriented organization, everyone, from leadership to frontline employees, is responsible for seeking and implementing improvements. This bottom-up approach harnesses the collective intelligence and expertise of the entire workforce.
Small Steps Lead to Big Gains: Kaizen advocates for taking small, manageable steps toward improvement rather than attempting radical changes. These small changes are less disruptive, easier to implement, and collectively lead to significant progress.
Standardization and Documentation: Documenting processes and standardizing best practices are essential in Kaizen. This ensures that improvements are sustained over time and can be built upon.
Elimination of Waste: Kaizen aligns with the lean management principle of eliminating waste. The focus is on identifying and eliminating non-value-adding activities and processes to enhance efficiency and value delivery.
Customer-Centric Approach: The ultimate goal of Kaizen is to enhance the quality of products and services, meeting or exceeding customer expectations. Customer feedback is a valuable source of insight for improvement.
The Kaizen Culture
Implementing Kaizen is not just about the individual improvements but also about fostering a culture of continuous learning, adaptability, and innovation. Organizations that embrace the Kaizen culture encourage employees to seek and implement improvements daily.
Kaizen is the lifeblood of lean management, driving organizations to achieve higher efficiency, better quality, and greater customer satisfaction through small, continuous improvements. By prioritizing Kaizen and creating a culture of continuous improvement, organizations can remain adaptable, competitive, and ever-evolving in an ever-changing business landscape.
Value Stream Mapping
In the world of lean management, one of the most powerful tools for understanding, analyzing, and optimizing processes is value stream mapping. Value stream mapping is a visual representation of how materials and information flow through an entire process, from the initial customer need to the finished product or service. It allows organizations to identify and eliminate waste, improve efficiency, and enhance the overall value delivered to customers.
What is Value Stream Mapping?
Value stream mapping is a structured, visual technique that provides a clear and holistic view of a process or series of processes. It captures not only the steps involved but also the information flow, cycle times, and decision points, enabling organizations to see the entire process at a glance.
The Components of Value Stream Mapping
A typical value stream map includes several key components:
Value-Adding Activities: These are the activities that directly contribute to creating value for the customer. They are the steps in the process that customers are willing to pay for.
Non-Value-Adding Activities (Waste): These are activities that do not add value but are necessary due to inefficiencies or other constraints. Identifying and minimizing waste is a primary goal of value stream mapping.
Information Flow: This component illustrates how information, such as customer orders, instructions, and feedback, flows within the process.
Cycle Time: Value stream maps often include data on the time it takes to complete each step in the process, helping to identify bottlenecks and areas of delay.
Inventory Levels: Visual representation of the inventory at various stages in the process, which can highlight areas of overproduction and inefficiency.
Value stream mapping is a powerful tool that enables organizations to gain insights into their processes, reduce waste, and enhance efficiency. By creating a visual representation of the entire value stream, organizations can identify areas for improvement and drive a culture of continuous enhancement, aligning processes with customer needs and delivering value more effectively.
Just-In-Time (JIT) Production
Just-In-Time (JIT) production is a lean manufacturing and inventory management strategy that has revolutionized the way organizations produce goods and manage their supply chains. JIT aims to reduce waste, minimize inventory, and optimize production, all with the goal of delivering products or services to customers exactly when they're needed.
Understanding JIT Production:
At its core, JIT is about producing only what is needed, in the quantity needed, and at the time it is needed, with minimal waste. The primary objective is to eliminate excess inventory and the associated costs while maintaining a smooth production flow.
Key Principles of JIT Production:
JIT production is guided by several key principles:
Pull System: JIT operates on a pull system, where production is initiated based on actual customer demand. This contrasts with traditional push systems, where products are produced based on forecasts or speculative demand.
Continuous Flow: JIT encourages a continuous and unbroken flow of work through the production process, minimizing interruptions, waiting times, and inventory buildup.
Kanban System: A core element of JIT is the use of Kanban, a visual signaling system that ensures just-in-time production. Kanban cards or signals trigger the replenishment of materials only when they are needed, preventing overproduction.
Takt Time: Takt time is the heartbeat of JIT. It is the rate at which products must be produced to meet customer demand. JIT aligns production to match this takt time.
Reducing Setup Times (SMED): JIT places great emphasis on reducing setup times to allow for more frequent, smaller production runs. The Single-Minute Exchange of Die (SMED) methodology is often used for this purpose.
In summary, Just-In-Time (JIT) production is a lean strategy that seeks to optimize production and minimize waste by producing goods or services exactly when they are needed. By eliminating excess inventory and aligning production with customer demand, organizations can achieve cost savings, improve efficiency, and enhance their overall competitiveness. However, JIT production requires careful planning and a reliable supply chain to be effective.
Pull Systems and Kanban
Pull systems and Kanban are integral components of lean manufacturing and production, facilitating efficient and waste-reducing processes. By employing these principles, organizations can synchronize production with customer demand, minimize inventory, and ensure a smooth workflow.
Pull Systems in Lean Manufacturing
Pull systems operate in contrast to traditional push systems, which produce goods based on forecasts or production schedules. In a pull system, work is initiated in response to actual customer demand, which "pulls" the product through the production process. The primary objective is to avoid overproduction and excess inventory, as well as to respond quickly to changes in customer requirements.
Key elements of pull systems include:
Kanban: A visual signaling system that regulates the flow of work. Kanban cards or signals are used to indicate when more materials or work can be pulled into a process.
Takt Time: The rate at which products must be produced to meet customer demand, based on the available production time. Takt time sets the pace for production in a pull system.
Continuous Flow: A pull system encourages a continuous and uninterrupted flow of work, minimizing downtime and waiting times.
Pull systems and Kanban are essential components of lean manufacturing, ensuring that work is initiated based on actual customer demand, minimizing inventory, and facilitating a smooth and efficient production process. When implemented effectively, these principles reduce waste, enhance quality, and improve overall production efficiency.
Standardized Work
Standardized work is a fundamental concept within the realm of lean management. It plays a crucial role in ensuring consistency, efficiency, and continuous improvement in processes and operations. Standardized work involves documenting and following a set of predefined procedures, methods, and best practices for completing a task or a process.
Key Components of Standardized Work
Standardized work typically includes the following key components:
Work Sequence: A detailed and specific sequence of tasks, steps, or activities that need to be completed to accomplish a particular job or process.
Takt Time: The rate at which work must be completed to meet customer demand. Takt time is often used to pace the work.
Standard Work-in-Process (WIP): The prescribed amount of work or inventory that should be in process at any given time to maintain flow and minimize waste.
Work Instructions: Clear and precise instructions for each task or operation, often including information on tools, equipment, and quality standards.
Safety Measures: Guidelines for ensuring the safety of workers during the execution of tasks.
Quality Standards: Specifications for the desired quality of work or products.
Standardized work is a foundational element of lean management, providing a structured approach to ensure consistency, efficiency, and quality in processes and operations. By documenting and adhering to standardized work, organizations can create a solid foundation for continuous improvement and operational excellence.
Gemba Walks
In the world of lean management, the Gemba walk is a powerful practice that allows leaders and managers to gain firsthand insights into their organization's processes, identify opportunities for improvement, and build a culture of continuous enhancement. The term "Gemba" is Japanese and refers to the "actual place" where work happens, whether that's a shop floor, a healthcare facility, an office, or any other work environment.
The Purpose of Gemba Walks
The primary purpose of Gemba walks is to encourage leaders and managers to engage with the work environment, interact with employees, and gain a deep understanding of how processes operate. By physically visiting the Gemba, leaders can:
Identify Waste: Gemba walks help in recognizing inefficiencies, bottlenecks, and non-value-adding activities (waste) in the work process.
Enhance Communication: Direct interactions with employees on the shop floor or in their work environment facilitate open communication and idea sharing.
Problem-Solving: Gemba walks allow leaders to see problems as they occur, understand their root causes, and work with employees to develop solutions.
Coaching and Learning: Leaders can offer guidance, mentorship, and learning opportunities to employees, fostering their development and improvement.
Observing Standard Work: Leaders can observe whether standardized work processes are being followed and make necessary adjustments.
Key Principles of Gemba Walks
To conduct effective Gemba walks, leaders should keep in mind the following principles:
Go and See for Yourself: Gemba walks involve firsthand observation, not just relying on reports or data. Leaders need to physically visit the workplace to understand the real situation.
Respect for People: The Gemba walk should be conducted with a respectful attitude, valuing the insights and expertise of the employees working in that environment.
Ask Why: Leaders should ask questions to dig deeper and understand the underlying reasons for what they observe.
Engage and Collaborate: Gemba walks are not inspections; they are opportunities to engage with employees and collaborate on improvements.
Foster a Culture of Improvement: Encourage employees to suggest improvements and be open to their ideas.
In summary, Gemba walks are an essential practice in lean management, allowing leaders to gain a deep understanding of their organization's processes, identify opportunities for improvement, and build a culture of continuous enhancement. By physically engaging with the work environment and the people who operate within it, organizations can make more informed decisions and drive operational excellence.
Key Performance Indicators (KPIs) for Lean
In lean management, the use of Key Performance Indicators (KPIs) is essential for monitoring, evaluating, and continuously improving operations. KPIs help organizations track their progress toward lean goals, identify areas for improvement, and ensure that lean principles are effectively applied. Here are some key KPIs commonly used in lean management:
Cycle Time: The time it takes to complete a specific task, process, or operation. Reducing cycle times is a fundamental objective of lean management, as it leads to greater efficiency.
Lead Time: The time it takes to fulfill a customer order, from the moment the order is placed to when the product is delivered. Reducing lead times is crucial for meeting customer demand more effectively.
Quality Defect Rate: This KPI measures the number of defects or errors in a product or service. Reducing the defect rate is vital for enhancing quality and customer satisfaction.
WIP (Work-in-Process) Inventory: Measuring the amount of work in process helps identify overproduction and areas where materials are waiting to be processed.
First Pass Yield (FPY): FPY measures the percentage of products that pass through a process or stage without the need for rework or corrections. A high FPY indicates effective quality control.
Customer Satisfaction: While not a numerical KPI, customer satisfaction is a critical measure of lean success. Satisfied customers are more likely to be repeat customers and advocates for your organization.
Waste Reduction: Quantifying and tracking reductions in the eight types of waste (as identified in lean management) can be a key performance indicator in itself. This includes waste reduction in areas such as overproduction, inventory, and defects.
Effective lean management involves selecting KPIs that align with your organization's goals and continuously monitoring and analyzing them. KPIs provide the data needed to make informed decisions, foster a culture of improvement, and measure the impact of lean practices on efficiency, quality, and customer satisfaction.
How to obtain Lean Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
Conclusion
In conclusion, lean management is a powerful philosophy and set of principles aimed at optimizing processes, reducing waste, and enhancing efficiency across various industries and organizational contexts. This approach focuses on delivering value to customers while continuously improving operations. Throughout this discussion, we've explored key aspects of lean management, including its principles, tools, and key performance indicators (KPIs).
Lean management emphasizes the elimination of waste, the pursuit of perfection, and a commitment to continuous improvement. Key principles such as value stream mapping, standardized work, pull systems, and Kaizen contribute to streamlining operations and driving organizational success.
Additionally, concepts like Gemba walks encourage leaders to engage with the workplace, collaborate with employees, and identify opportunities for improvement at the grassroots level. Value stream mapping, Kanban, and Just-In-Time (JIT) production play crucial roles in reducing waste and optimizing production processes.
Standardized work ensures consistency and efficiency, while KPIs help measure performance and track progress. By monitoring key metrics such as cycle time, lead time, quality defect rates, and inventory turnover, organizations can better understand their strengths and areas for growth.
Incorporating lean management into an organization's culture can lead to significant benefits, including cost savings, improved product quality, enhanced customer satisfaction, and a competitive edge in today's dynamic business environment.
As organizations continue to adapt and evolve, the principles and practices of lean management remain invaluable in guiding them toward greater efficiency, effectiveness, and overall success. Lean is not just a management philosophy; it's a journey of continuous improvement and a commitment to delivering value while eliminating waste.
Citrix Cloud Administration: A Comprehensive Guide
In today's rapidly evolving digital landscape, businesses and organizations are continually seeking agile, secure, and efficient solutions to manage their virtual applications and desktops. Citrix Cloud, a game-changing platform, has emerged as the answer to this growing demand. As a Citrix administrator or IT professional, mastering the art of Citrix Cloud administration is an essential skillset.
Welcome to our comprehensive guide on Citrix Cloud Administration. Whether you're a seasoned Citrix expert looking to transition to the cloud or a newcomer eager to explore the vast potential of Citrix's cloud-based offerings, this guide is your roadmap to navigating the intricacies of Citrix Cloud.
Citrix Cloud introduces a new paradigm for managing your virtual apps and desktops. It brings flexibility, scalability, and simplified infrastructure management to the forefront. From resource provisioning to user management, networking, security, and much more, Citrix Cloud is a versatile toolbox waiting to be harnessed.
Table of contents
-
Getting Started with Citrix Cloud: An Introduction to the Platform
-
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
-
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
-
User Management in Citrix Cloud: User Authentication and Access Control
-
Citrix Cloud Networking: Configuring Secure Connectivity
-
Citrix Cloud Monitoring and Analytics: Tools and Techniques
-
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
-
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
-
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
-
Citrix Cloud Security: Strategies for Data Protection and Compliance
-
Conclusion
Getting Started with Citrix Cloud: An Introduction to the Platform
Citrix Cloud is a transformative platform that brings the power of Citrix solutions to the cloud, providing a new level of flexibility and efficiency in managing virtual applications and desktops. Whether you're an IT professional seeking to streamline your organization's workspace or a Citrix administrator looking to expand your skill set, understanding the fundamentals of Citrix Cloud is the first step to harnessing its potential.
In this introductory article, we'll explore the core concepts of Citrix Cloud, its benefits, and the foundational elements that make it a compelling choice for organizations of all sizes. We'll break down the key components of the platform, its architecture, and the advantages it offers in terms of agility, scalability, and simplified infrastructure management.
By the end of this article, you'll have a solid grasp of what Citrix Cloud is, why it's a game-changer in the world of virtualization and cloud computing, and how it can empower your organization to deliver a superior digital workspace experience.
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
The Citrix Cloud Connector serves as the bridge between your on-premises infrastructure and the Citrix Cloud platform, enabling a seamless connection for managing virtual applications and desktops. In this guide, we'll walk you through the essential steps for installing and configuring the Citrix Cloud Connector, while highlighting best practices to ensure a secure and efficient connection.
Installing and configuring the Citrix Cloud Connector is a critical phase in your Citrix Cloud deployment. It enables your on-premises resources to be managed and extended into the Citrix Cloud, creating a unified, cohesive environment. Whether you're setting up your connector for the first time or looking to optimize an existing installation, this guide will provide the necessary insights.
We'll cover the prerequisites, installation process, and post-installation configuration steps in a clear and concise manner, ensuring that you have a comprehensive understanding of the tasks involved. Additionally, we'll share best practices that will help you maintain a reliable connection to the Citrix Cloud, enhance security, and streamline management.
By the end of this guide, you'll be well-equipped to confidently install and configure the Citrix Cloud Connector, facilitating a smooth and efficient link between your on-premises infrastructure and the Citrix Cloud platform. Let's dive in and get started on this important journey of connecting your environment to the cloud.
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
The Citrix Virtual Apps and Desktops Service, part of the Citrix Cloud platform, empowers organizations to deliver virtual applications and desktops to users across the globe. In this guide, we will explore the essential steps and best practices for setting up and managing resources within this service.
Citrix Virtual Apps and Desktops Service offers a powerful, cloud-based solution for creating, delivering, and managing virtualized applications and desktops. With this service, you can streamline resource provisioning, enhance user experiences, and simplify administration.
We'll take you through the process of creating and configuring virtual app and desktop resources, including machine catalogs and delivery groups. We'll also cover resource management, scaling, and optimizing your environment for peak performance. Additionally, we'll discuss user access, policies, and how to ensure a secure and productive workspace.
By the end of this guide, you'll have the knowledge and insights needed to effectively set up and manage resources within the Citrix Virtual Apps and Desktops Service, providing your users with a seamless and feature-rich virtual workspace. Let's begin the journey of optimizing your virtualization infrastructure in the cloud.
User Management in Citrix Cloud: User Authentication and Access Control
User management is a fundamental aspect of any Citrix Cloud deployment, as it directly impacts the security and accessibility of your virtual applications and desktops. In this guide, we will delve into the intricacies of user management within Citrix Cloud, focusing on user authentication and access control.
Ensuring the right individuals have access to your Citrix Cloud resources while maintaining a secure environment is paramount. In this guide, we'll explore the various methods of user authentication, from single sign-on (SSO) to multi-factor authentication (MFA), and discuss the best practices for implementing these solutions effectively.
We will also dive into access control mechanisms, such as role-based access control (RBAC) and user group management. You'll learn how to define and assign user roles and permissions to control what actions users can perform within your Citrix Cloud environment, whether it's managing resources, configuring settings, or simply accessing applications and desktops.
By the end of this guide, you'll have a comprehensive understanding of user management in Citrix Cloud, ensuring that your users are authenticated securely and that access control is finely tuned to meet your organization's specific needs. Let's explore the key elements of user authentication and access control in the world of Citrix Cloud.
Citrix Cloud Networking: Configuring Secure Connectivity
Networking forms the backbone of any successful Citrix Cloud deployment, as it directly influences the performance, reliability, and security of your virtualized resources. In this comprehensive guide, we will delve into the critical aspects of Citrix Cloud networking, focusing on configuring secure connectivity.
Citrix Cloud networking is about more than just connecting your virtual applications and desktops to the cloud—it's about creating a robust and secure infrastructure that ensures seamless access for users, no matter where they are. In this guide, we'll explore the key considerations, best practices, and steps to configure secure connectivity.
We'll cover topics such as setting up Virtual Private Networks (VPNs), leveraging Citrix Gateway for secure access, and optimizing network performance. We'll also delve into strategies for load balancing, content switching, and SSL offloading to create a seamless and secure experience for your users.
By the end of this guide, you'll be well-versed in the art of configuring secure connectivity in Citrix Cloud, ensuring that your virtualized resources are not only easily accessible but also well-protected from potential threats. Let's embark on this journey to create a robust and secure networking foundation for your Citrix Cloud environment.
Citrix Cloud Monitoring and Analytics: Tools and Techniques
In the dynamic world of Citrix Cloud administration, monitoring and analytics play a pivotal role in ensuring the optimal performance, availability, and security of your virtual applications and desktops. This guide will delve into the essential tools and techniques you need to effectively monitor and analyze your Citrix Cloud environment.
Citrix Cloud monitoring and analytics provide insights that help administrators proactively address issues, optimize resource utilization, and enhance the end-user experience. With the right tools and techniques, you can gain a deeper understanding of your environment and make data-driven decisions.
In this guide, we will explore the various monitoring and analytics solutions available within Citrix Cloud, including Citrix Director, Citrix Analytics, and third-party integrations. You'll learn how to set up and configure these tools, interpret the data they provide, and take action based on the insights gained.
We'll also cover best practices for proactive monitoring, performance tuning, and troubleshooting common issues. By the end of this guide, you'll have a clear roadmap for implementing monitoring and analytics within your Citrix Cloud environment, ensuring that it runs smoothly and efficiently. Let's dive into the world of Citrix Cloud monitoring and analytics to empower your administration efforts.
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
In the ever-evolving landscape of Citrix Cloud, staying up-to-date is essential for maintaining the security, performance, and functionality of your virtual applications and desktops. This guide is dedicated to helping you understand the best practices for managing updates and maintenance in your Citrix Cloud environment.
Citrix Cloud, like any other software platform, undergoes periodic updates and maintenance to address vulnerabilities, introduce new features, and improve overall performance. Staying current with these updates is crucial to ensure a reliable and secure environment.
In this guide, we will walk you through the essential steps of managing Citrix Cloud updates, including understanding the update release cycle, planning for updates, and testing updates in a safe environment before deploying them to your production environment.
We'll also explore maintenance practices that extend beyond software updates, such as resource optimization, backup strategies, and disaster recovery planning. You'll gain insights into strategies for minimizing downtime and potential disruptions.
By the end of this guide, you'll have a clear understanding of how to maintain your Citrix Cloud environment effectively, ensuring that it remains up-to-date, secure, and aligned with your organization's evolving needs. Let's delve into the world of Citrix Cloud updates and maintenance, and ensure your environment remains resilient and reliable.
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
The hybrid configuration, bridging the gap between Citrix Cloud and on-premises deployments, offers a powerful solution that combines the advantages of both worlds. In this guide, we'll explore the intricacies of integrating Citrix Cloud with your on-premises infrastructure to create a seamless, versatile, and efficient virtualization environment.
As organizations often have a mix of on-premises and cloud-based resources, integrating Citrix Cloud with your existing infrastructure can optimize the utilization of resources, enhance flexibility, and simplify administration. This guide will provide you with a step-by-step approach to create a harmonious coexistence.
We'll delve into key topics, including connecting your on-premises Virtual Apps and Desktops to Citrix Cloud, leveraging resource location flexibility, and ensuring a consistent user experience. You'll learn how to configure the necessary components for a successful hybrid deployment and how to manage resources and user access across both environments.
By the end of this guide, you'll have a solid understanding of how to implement a hybrid configuration that streamlines your virtualization infrastructure, enabling your organization to make the most of both on-premises and cloud resources. Let's embark on this journey of integrating Citrix Cloud with your on-premises deployments for enhanced versatility and efficiency.
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
Digital workspaces have become the cornerstone of modern business environments, offering a unified platform for accessing applications, data, and resources from anywhere, at any time. In this guide, we will delve into the creation and management of digital workspaces using Citrix Cloud, empowering organizations to deliver a flexible and productive workspace experience.
Citrix Cloud workspaces bring together applications, desktops, and data in a secure and user-friendly manner. They offer seamless access on various devices, enhancing productivity and user satisfaction. This guide will provide you with the knowledge and techniques required to create and manage Citrix Cloud workspaces effectively.
We'll explore the fundamental concepts of workspace creation, including the setup of storefronts, application provisioning, and customization options. Additionally, we'll cover user profile management, personalization, and the integration of collaboration tools to create a holistic digital workspace experience.
By the end of this guide, you'll be well-equipped to design, create, and manage Citrix Cloud workspaces that cater to the specific needs of your organization, ensuring a productive and efficient digital workspace for your users. Let's embark on the journey of crafting dynamic and user-friendly digital workspaces using Citrix Cloud.
Citrix Cloud Security: Strategies for Data Protection and Compliance
In today's digital landscape, the security of your Citrix Cloud environment is of paramount importance. Protecting sensitive data and ensuring compliance with industry regulations are crucial aspects of Citrix Cloud administration. This guide is dedicated to exploring robust security strategies that will help safeguard your data and maintain compliance within Citrix Cloud.
Citrix Cloud Security is a multi-faceted approach that involves protecting your virtual applications, desktops, and the data that flows through them. We'll delve into various strategies and best practices that address security concerns, focusing on data protection and regulatory compliance.
Throughout this guide, you'll learn about the importance of encryption, access controls, and user authentication. We'll also discuss methods for securing data in transit and at rest, as well as strategies for addressing data governance and compliance requirements specific to your industry.
By the end of this guide, you'll have a clear understanding of how to implement effective security strategies in your Citrix Cloud environment, ensuring that your data remains protected, and your organization complies with relevant regulations. Let's embark on the journey of bolstering the security of your Citrix Cloud deployment.
Conclusion
In conclusion, this comprehensive guide has taken you on a journey through the world of Citrix Cloud administration, covering a wide range of critical topics and best practices. We've explored the fundamental concepts of Citrix Cloud, from its initial setup and resource management to user authentication, secure networking, and monitoring and analytics.
We've also discussed the importance of staying current with updates and maintenance and the benefits of integrating Citrix Cloud with on-premises deployments. Additionally, we delved into the creation and management of digital workspaces, empowering organizations to provide a productive and flexible workspace experience for their users.
Lastly, we highlighted the critical aspect of Citrix Cloud security, emphasizing data protection and compliance strategies to keep your environment safe and in adherence with industry regulations.
As you continue your Citrix Cloud administration journey, remember that technology and best practices are continually evolving. Staying informed, exploring new solutions, and adapting to the changing landscape will help you navigate the complex world of Citrix Cloud effectively.
We hope this guide has provided you with valuable insights, and we encourage you to put this knowledge into practice to optimize your Citrix Cloud environment, enhance security, and provide an exceptional digital workspace experience for your users. Thank you for joining us on this journey, and we wish you every success in your Citrix Cloud administration endeavors.
Read More
In today's rapidly evolving digital landscape, businesses and organizations are continually seeking agile, secure, and efficient solutions to manage their virtual applications and desktops. Citrix Cloud, a game-changing platform, has emerged as the answer to this growing demand. As a Citrix administrator or IT professional, mastering the art of Citrix Cloud administration is an essential skillset.
Welcome to our comprehensive guide on Citrix Cloud Administration. Whether you're a seasoned Citrix expert looking to transition to the cloud or a newcomer eager to explore the vast potential of Citrix's cloud-based offerings, this guide is your roadmap to navigating the intricacies of Citrix Cloud.
Citrix Cloud introduces a new paradigm for managing your virtual apps and desktops. It brings flexibility, scalability, and simplified infrastructure management to the forefront. From resource provisioning to user management, networking, security, and much more, Citrix Cloud is a versatile toolbox waiting to be harnessed.
Table of contents
-
Getting Started with Citrix Cloud: An Introduction to the Platform
-
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
-
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
-
User Management in Citrix Cloud: User Authentication and Access Control
-
Citrix Cloud Networking: Configuring Secure Connectivity
-
Citrix Cloud Monitoring and Analytics: Tools and Techniques
-
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
-
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
-
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
-
Citrix Cloud Security: Strategies for Data Protection and Compliance
-
Conclusion
Getting Started with Citrix Cloud: An Introduction to the Platform
Citrix Cloud is a transformative platform that brings the power of Citrix solutions to the cloud, providing a new level of flexibility and efficiency in managing virtual applications and desktops. Whether you're an IT professional seeking to streamline your organization's workspace or a Citrix administrator looking to expand your skill set, understanding the fundamentals of Citrix Cloud is the first step to harnessing its potential.
In this introductory article, we'll explore the core concepts of Citrix Cloud, its benefits, and the foundational elements that make it a compelling choice for organizations of all sizes. We'll break down the key components of the platform, its architecture, and the advantages it offers in terms of agility, scalability, and simplified infrastructure management.
By the end of this article, you'll have a solid grasp of what Citrix Cloud is, why it's a game-changer in the world of virtualization and cloud computing, and how it can empower your organization to deliver a superior digital workspace experience.
Citrix Cloud Connector Installation and Configuration: Steps and Best Practices
The Citrix Cloud Connector serves as the bridge between your on-premises infrastructure and the Citrix Cloud platform, enabling a seamless connection for managing virtual applications and desktops. In this guide, we'll walk you through the essential steps for installing and configuring the Citrix Cloud Connector, while highlighting best practices to ensure a secure and efficient connection.
Installing and configuring the Citrix Cloud Connector is a critical phase in your Citrix Cloud deployment. It enables your on-premises resources to be managed and extended into the Citrix Cloud, creating a unified, cohesive environment. Whether you're setting up your connector for the first time or looking to optimize an existing installation, this guide will provide the necessary insights.
We'll cover the prerequisites, installation process, and post-installation configuration steps in a clear and concise manner, ensuring that you have a comprehensive understanding of the tasks involved. Additionally, we'll share best practices that will help you maintain a reliable connection to the Citrix Cloud, enhance security, and streamline management.
By the end of this guide, you'll be well-equipped to confidently install and configure the Citrix Cloud Connector, facilitating a smooth and efficient link between your on-premises infrastructure and the Citrix Cloud platform. Let's dive in and get started on this important journey of connecting your environment to the cloud.
Citrix Virtual Apps and Desktops Service: Setting Up and Managing Resources
The Citrix Virtual Apps and Desktops Service, part of the Citrix Cloud platform, empowers organizations to deliver virtual applications and desktops to users across the globe. In this guide, we will explore the essential steps and best practices for setting up and managing resources within this service.
Citrix Virtual Apps and Desktops Service offers a powerful, cloud-based solution for creating, delivering, and managing virtualized applications and desktops. With this service, you can streamline resource provisioning, enhance user experiences, and simplify administration.
We'll take you through the process of creating and configuring virtual app and desktop resources, including machine catalogs and delivery groups. We'll also cover resource management, scaling, and optimizing your environment for peak performance. Additionally, we'll discuss user access, policies, and how to ensure a secure and productive workspace.
By the end of this guide, you'll have the knowledge and insights needed to effectively set up and manage resources within the Citrix Virtual Apps and Desktops Service, providing your users with a seamless and feature-rich virtual workspace. Let's begin the journey of optimizing your virtualization infrastructure in the cloud.
User Management in Citrix Cloud: User Authentication and Access Control
User management is a fundamental aspect of any Citrix Cloud deployment, as it directly impacts the security and accessibility of your virtual applications and desktops. In this guide, we will delve into the intricacies of user management within Citrix Cloud, focusing on user authentication and access control.
Ensuring the right individuals have access to your Citrix Cloud resources while maintaining a secure environment is paramount. In this guide, we'll explore the various methods of user authentication, from single sign-on (SSO) to multi-factor authentication (MFA), and discuss the best practices for implementing these solutions effectively.
We will also dive into access control mechanisms, such as role-based access control (RBAC) and user group management. You'll learn how to define and assign user roles and permissions to control what actions users can perform within your Citrix Cloud environment, whether it's managing resources, configuring settings, or simply accessing applications and desktops.
By the end of this guide, you'll have a comprehensive understanding of user management in Citrix Cloud, ensuring that your users are authenticated securely and that access control is finely tuned to meet your organization's specific needs. Let's explore the key elements of user authentication and access control in the world of Citrix Cloud.
Citrix Cloud Networking: Configuring Secure Connectivity
Networking forms the backbone of any successful Citrix Cloud deployment, as it directly influences the performance, reliability, and security of your virtualized resources. In this comprehensive guide, we will delve into the critical aspects of Citrix Cloud networking, focusing on configuring secure connectivity.
Citrix Cloud networking is about more than just connecting your virtual applications and desktops to the cloud—it's about creating a robust and secure infrastructure that ensures seamless access for users, no matter where they are. In this guide, we'll explore the key considerations, best practices, and steps to configure secure connectivity.
We'll cover topics such as setting up Virtual Private Networks (VPNs), leveraging Citrix Gateway for secure access, and optimizing network performance. We'll also delve into strategies for load balancing, content switching, and SSL offloading to create a seamless and secure experience for your users.
By the end of this guide, you'll be well-versed in the art of configuring secure connectivity in Citrix Cloud, ensuring that your virtualized resources are not only easily accessible but also well-protected from potential threats. Let's embark on this journey to create a robust and secure networking foundation for your Citrix Cloud environment.
Citrix Cloud Monitoring and Analytics: Tools and Techniques
In the dynamic world of Citrix Cloud administration, monitoring and analytics play a pivotal role in ensuring the optimal performance, availability, and security of your virtual applications and desktops. This guide will delve into the essential tools and techniques you need to effectively monitor and analyze your Citrix Cloud environment.
Citrix Cloud monitoring and analytics provide insights that help administrators proactively address issues, optimize resource utilization, and enhance the end-user experience. With the right tools and techniques, you can gain a deeper understanding of your environment and make data-driven decisions.
In this guide, we will explore the various monitoring and analytics solutions available within Citrix Cloud, including Citrix Director, Citrix Analytics, and third-party integrations. You'll learn how to set up and configure these tools, interpret the data they provide, and take action based on the insights gained.
We'll also cover best practices for proactive monitoring, performance tuning, and troubleshooting common issues. By the end of this guide, you'll have a clear roadmap for implementing monitoring and analytics within your Citrix Cloud environment, ensuring that it runs smoothly and efficiently. Let's dive into the world of Citrix Cloud monitoring and analytics to empower your administration efforts.
Citrix Cloud Updates and Maintenance: Best Practices for Staying Current
In the ever-evolving landscape of Citrix Cloud, staying up-to-date is essential for maintaining the security, performance, and functionality of your virtual applications and desktops. This guide is dedicated to helping you understand the best practices for managing updates and maintenance in your Citrix Cloud environment.
Citrix Cloud, like any other software platform, undergoes periodic updates and maintenance to address vulnerabilities, introduce new features, and improve overall performance. Staying current with these updates is crucial to ensure a reliable and secure environment.
In this guide, we will walk you through the essential steps of managing Citrix Cloud updates, including understanding the update release cycle, planning for updates, and testing updates in a safe environment before deploying them to your production environment.
We'll also explore maintenance practices that extend beyond software updates, such as resource optimization, backup strategies, and disaster recovery planning. You'll gain insights into strategies for minimizing downtime and potential disruptions.
By the end of this guide, you'll have a clear understanding of how to maintain your Citrix Cloud environment effectively, ensuring that it remains up-to-date, secure, and aligned with your organization's evolving needs. Let's delve into the world of Citrix Cloud updates and maintenance, and ensure your environment remains resilient and reliable.
Integrating Citrix Cloud with On-Premises Deployments: Hybrid Configuration
The hybrid configuration, bridging the gap between Citrix Cloud and on-premises deployments, offers a powerful solution that combines the advantages of both worlds. In this guide, we'll explore the intricacies of integrating Citrix Cloud with your on-premises infrastructure to create a seamless, versatile, and efficient virtualization environment.
As organizations often have a mix of on-premises and cloud-based resources, integrating Citrix Cloud with your existing infrastructure can optimize the utilization of resources, enhance flexibility, and simplify administration. This guide will provide you with a step-by-step approach to create a harmonious coexistence.
We'll delve into key topics, including connecting your on-premises Virtual Apps and Desktops to Citrix Cloud, leveraging resource location flexibility, and ensuring a consistent user experience. You'll learn how to configure the necessary components for a successful hybrid deployment and how to manage resources and user access across both environments.
By the end of this guide, you'll have a solid understanding of how to implement a hybrid configuration that streamlines your virtualization infrastructure, enabling your organization to make the most of both on-premises and cloud resources. Let's embark on this journey of integrating Citrix Cloud with your on-premises deployments for enhanced versatility and efficiency.
Citrix Cloud Workspaces: Creating and Managing Digital Workspaces
Digital workspaces have become the cornerstone of modern business environments, offering a unified platform for accessing applications, data, and resources from anywhere, at any time. In this guide, we will delve into the creation and management of digital workspaces using Citrix Cloud, empowering organizations to deliver a flexible and productive workspace experience.
Citrix Cloud workspaces bring together applications, desktops, and data in a secure and user-friendly manner. They offer seamless access on various devices, enhancing productivity and user satisfaction. This guide will provide you with the knowledge and techniques required to create and manage Citrix Cloud workspaces effectively.
We'll explore the fundamental concepts of workspace creation, including the setup of storefronts, application provisioning, and customization options. Additionally, we'll cover user profile management, personalization, and the integration of collaboration tools to create a holistic digital workspace experience.
By the end of this guide, you'll be well-equipped to design, create, and manage Citrix Cloud workspaces that cater to the specific needs of your organization, ensuring a productive and efficient digital workspace for your users. Let's embark on the journey of crafting dynamic and user-friendly digital workspaces using Citrix Cloud.
Citrix Cloud Security: Strategies for Data Protection and Compliance
In today's digital landscape, the security of your Citrix Cloud environment is of paramount importance. Protecting sensitive data and ensuring compliance with industry regulations are crucial aspects of Citrix Cloud administration. This guide is dedicated to exploring robust security strategies that will help safeguard your data and maintain compliance within Citrix Cloud.
Citrix Cloud Security is a multi-faceted approach that involves protecting your virtual applications, desktops, and the data that flows through them. We'll delve into various strategies and best practices that address security concerns, focusing on data protection and regulatory compliance.
Throughout this guide, you'll learn about the importance of encryption, access controls, and user authentication. We'll also discuss methods for securing data in transit and at rest, as well as strategies for addressing data governance and compliance requirements specific to your industry.
By the end of this guide, you'll have a clear understanding of how to implement effective security strategies in your Citrix Cloud environment, ensuring that your data remains protected, and your organization complies with relevant regulations. Let's embark on the journey of bolstering the security of your Citrix Cloud deployment.
Conclusion
In conclusion, this comprehensive guide has taken you on a journey through the world of Citrix Cloud administration, covering a wide range of critical topics and best practices. We've explored the fundamental concepts of Citrix Cloud, from its initial setup and resource management to user authentication, secure networking, and monitoring and analytics.
We've also discussed the importance of staying current with updates and maintenance and the benefits of integrating Citrix Cloud with on-premises deployments. Additionally, we delved into the creation and management of digital workspaces, empowering organizations to provide a productive and flexible workspace experience for their users.
Lastly, we highlighted the critical aspect of Citrix Cloud security, emphasizing data protection and compliance strategies to keep your environment safe and in adherence with industry regulations.
As you continue your Citrix Cloud administration journey, remember that technology and best practices are continually evolving. Staying informed, exploring new solutions, and adapting to the changing landscape will help you navigate the complex world of Citrix Cloud effectively.
We hope this guide has provided you with valuable insights, and we encourage you to put this knowledge into practice to optimize your Citrix Cloud environment, enhance security, and provide an exceptional digital workspace experience for your users. Thank you for joining us on this journey, and we wish you every success in your Citrix Cloud administration endeavors.
what is a sprint in project management
Project management is a dynamic and multifaceted discipline that encompasses a wide array of methodologies and approaches. Among these, the Agile framework has gained significant prominence for its ability to foster flexibility, collaboration, and efficiency in managing projects. At the heart of Agile lies the concept of a "sprint," a term that is central to several Agile methodologies, particularly Scrum.
In this exploration of sprints in project management, we will unravel the fundamental principles that underpin this concept, its role in driving iterative development, and how it harmonizes with Agile methodologies. Sprints represent a powerful tool for breaking down complex projects into manageable, time-boxed segments, allowing teams to focus on delivering high-value, customer-centric work in a systematic and iterative fashion.
By the end of this exploration, you will have a comprehensive understanding of what a sprint is in project management, and how it aids in achieving project goals within the dynamic and adaptable framework of Agile methodologies. So, let's embark on this journey to uncover the significance and mechanics of sprints in project management.
Table of contents
- Definition of a Sprint
- Agile Methodology
- Scrum Framework
- Sprint Planning
- Sprint Duration
- Daily Stand-up Meetings
- Sprint Review
- Sprint Retrospective
- Definition of Done (DoD)
- Burndown Charts
- Conclusion
Definition of a Sprint
A sprint in project management, especially within the context of Agile methodologies like Scrum, is a time-bound, fixed duration iteration during which a cross-functional team works collaboratively to complete a set of pre-defined tasks or user stories. Sprints are typically short and predictable, usually lasting between 2 to 4 weeks, although this duration can vary based on the specific needs of the project.
Key features of a sprint include:
Time-Boxed: Sprints have a predetermined duration, which means that all work within the sprint must be completed within that timeframe. This time constraint creates a sense of urgency and helps the team focus on delivering a specific set of features or functionality.
User-Centric: Sprints prioritize delivering value to the end-users or customers. The work items, often referred to as user stories, are chosen based on their priority and value to the customer.
Cross-Functional Teams: A sprint team typically includes members with diverse skills, such as developers, testers, designers, and product owners. This diversity ensures that the team can complete the work independently without dependencies on external teams.
Daily Stand-up Meetings: During a sprint, the team holds daily stand-up meetings (also known as Daily Scrum) to discuss progress, challenges, and plans for the day. These short, daily meetings keep everyone informed and aligned.
Sprint Review: At the end of the sprint, a sprint review meeting is held to showcase the completed work to stakeholders and obtain feedback. This helps ensure that the product is meeting the evolving needs of the customers.
Sprints provide a structured and efficient approach to project management, allowing teams to adapt to changing requirements, gather feedback regularly, and deliver value incrementally. This iterative and customer-focused methodology is at the core of Agile project management and has become an essential tool for achieving success in complex and rapidly changing environments.
Agile Methodology
The Agile methodology is a set of principles and practices for software development and project management that prioritize flexibility, collaboration, customer feedback, and incremental progress. Agile methodologies are designed to address the challenges associated with traditional, plan-driven approaches to project management and development. They promote adaptive planning and iterative development, allowing teams to respond to changing requirements and deliver valuable products or services efficiently.
Key principles and concepts of Agile methodologies include:
Customer-Centric Approach: Agile places a strong emphasis on understanding and fulfilling customer needs. This is achieved by involving customers or end-users in the development process, continuously gathering feedback, and adapting the product or project to meet evolving requirements.
Collaboration and Communication: Agile methodologies emphasize effective collaboration among cross-functional teams, including developers, testers, designers, and product owners. Frequent communication is encouraged, often through daily stand-up meetings.
Adaptive Planning: Agile promotes adaptive planning rather than relying on a rigid, detailed plan created at the project's outset. Plans are updated and adjusted as new information becomes available or requirements change.
Working Software or Product: Agile prioritizes working software or a tangible product increment as the primary measure of progress. This ensures that value is being delivered at each step.
Agile methodologies are not limited to software development and can be applied in various contexts, including project management, product development, and even non-technical fields. Some of the most popular Agile frameworks and methodologies include Scrum, Kanban, Extreme Programming (XP), and Lean, each with its own set of practices and guidelines.
Scrum, for example, is a widely used Agile framework characterized by time-bound iterations (sprints), a specific set of roles (Scrum Master, Product Owner, Development Team), and ceremonies (sprint planning, daily stand-ups, sprint review, and sprint retrospective). Kanban, on the other hand, is focused on visualizing work, limiting work in progress, and optimizing workflow.
Agile methodologies have become essential in industries that require flexibility, adaptability, and a strong focus on delivering value to the customer. They have revolutionized project management and development practices by promoting a mindset of agility and collaboration.
Scrum Framework
The Scrum framework is a widely used Agile methodology for managing and delivering complex projects. It provides a structured approach to project management and product development, emphasizing collaboration, adaptability, and customer value. Scrum is particularly popular in software development, but its principles can be applied to a wide range of industries and projects.
Key components and concepts of the Scrum framework include:
Roles:
Scrum Master: The Scrum Master is responsible for ensuring that the Scrum framework is understood and implemented effectively. They facilitate Scrum events, remove impediments, and coach the team.
Product Owner: The Product Owner represents the customer or end-users and is responsible for defining and prioritizing the product backlog (the list of work to be done) and making decisions about what the team should work on.
Development Team: The Development Team is a cross-functional group of professionals responsible for delivering the potentially shippable product increment during each sprint.
Artifacts:
Product Backlog: This is a prioritized list of features, user stories, or tasks that represent the work to be done. The Product Owner manages and continually refines this backlog.
Sprint Backlog: At the beginning of each sprint, the team selects a set of items from the Product Backlog to work on during that sprint.
Increment: The Increment is the potentially shippable product or a piece of the product that is produced at the end of each sprint.
Events:
Sprint: A sprint is a time-boxed iteration typically lasting 2 to 4 weeks during which the Development Team works to complete a set of items from the Product Backlog.
Sprint Planning: At the start of each sprint, a sprint planning meeting is held. The team selects items from the Product Backlog to work on during the sprint and creates a plan for how to achieve the sprint goal.
Sprint Review: At the end of each sprint, a sprint review is conducted to showcase the work completed to stakeholders and gather feedback.
Sprint Retrospective: Following the sprint review, a sprint retrospective is held to reflect on the sprint's process and identify areas for improvement.
Key principles of the Scrum framework include:
Transparency: Scrum promotes transparency in all aspects of the project, including progress, issues, and the product itself. This transparency allows for effective communication and collaboration.
Inspection and Adaptation: Regular inspection of the product and the team's processes, followed by adaptation based on the inspection results, are integral to Scrum. This helps teams to continuously improve and respond to changing requirements.
Empiricism: Scrum is based on empirical process control, which means that decisions are made based on observed outcomes and feedback rather than predictions or assumptions.
Scrum is well-known for its ability to deliver value incrementally and adapt to changing requirements. It has gained widespread adoption across various industries because of its effectiveness in fostering collaboration and achieving customer satisfaction.
Sprint Planning
Sprint planning is a crucial ceremony in the Scrum framework, which is an Agile project management methodology. It's a collaborative and time-bound event that takes place at the beginning of each sprint. Sprint planning serves as a roadmap for the work the development team will undertake during the upcoming sprint, typically lasting 2 to 4 weeks. The primary goal of sprint planning is to define what will be delivered during the sprint and how it will be achieved.
Here are the key aspects of sprint planning:
Attendees:
Development Team: The cross-functional team that will be doing the work.
Scrum Master: Facilitates the sprint planning meeting.
Product Owner: Provides the team with the prioritized Product Backlog items.
Agenda:
Review of the Product Backlog: The Product Owner presents the top items in the Product Backlog, providing a brief overview of each item.
Task Breakdown: The selected items are further broken down into tasks, and the team discusses how they will complete each one.
Estimation: The team estimates the effort required for each task. Estimation is often done using story points, ideal days, or other relative sizing methods.
Capacity Planning: The team assesses its capacity for the sprint, considering team velocity (how much work they've completed in past sprints) and any known leave or holidays.
Definition of Done: The team reaffirms the Definition of Done, which outlines the criteria that must be met for work to be considered complete.
Time-Boxing: Sprint planning is time-boxed, meaning that it has a fixed duration. The time allocated for sprint planning should not exceed a certain limit, often one hour per week of the sprint.
Output:
Sprint Backlog: At the end of the sprint planning meeting, the selected items and tasks become the sprint backlog, which is a commitment by the team to complete the work during the sprint.
Sprint Goal: The sprint goal is reiterated to ensure everyone understands what the team is aiming to achieve.
Sprint planning sets clear expectations and provides a detailed plan for the team's work during the upcoming sprint. It also ensures that the team has a shared understanding of the sprint goal and the tasks required to achieve it. This collaborative approach fosters transparency and allows the team to adjust its plan if needed while maintaining a focus on delivering value to the customer.
Sprint Duration
Sprint duration, within the context of Agile and Scrum methodologies, refers to the specific length of time allocated for an iteration or sprint. Sprint durations are typically short, with the aim of achieving several objectives, including maintaining a sense of urgency, promoting regular inspection and adaptation, and delivering value incrementally. While the standard sprint duration is often two weeks, Scrum allows flexibility, and sprint durations can be adjusted based on the team's preferences and the nature of the project. Here are some key considerations regarding sprint duration:
Typical Sprint Durations: While two weeks is the most commonly used sprint duration, Scrum teams may opt for shorter sprints lasting one week or even longer sprints of three to four weeks. The choice of sprint duration depends on various factors, including the team's capacity, the project's complexity, and organizational preferences.
Advantages of Short Sprints: Shorter sprints offer benefits such as more frequent opportunities for inspection and adaptation, faster feedback from stakeholders, and greater agility in responding to changing requirements.
Stakeholder Engagement: Sprint duration affects how often stakeholders can see and provide feedback on the product. Shorter sprints enable more frequent stakeholder engagement, which can be valuable for validating product direction.
Sprint Planning Frequency: The shorter the sprint, the more often sprint planning, sprint review, and sprint retrospective meetings occur. Teams need to consider the time and effort required for these meetings when deciding on sprint duration.
Workload and Capacity: The team's capacity, velocity, and availability of team members are critical factors in determining sprint duration. Teams should select a sprint duration that allows them to consistently complete the planned work.
Consistency: Once a sprint duration is selected, it is typically kept consistent to maintain predictability. Frequent changes to sprint length can disrupt the team's rhythm and planning process.
In summary, sprint duration is a fundamental aspect of Scrum and Agile methodologies, with the flexibility to adapt to the needs of the team and the project. The choice of sprint duration should be made thoughtfully, considering factors such as project complexity, stakeholder engagement, and the team's capacity, while keeping in mind the Agile principles of delivering value regularly and promoting collaboration.
Daily Stand-up Meetings
Daily stand-up meetings, also known as Daily Scrum meetings, are a core practice within the Scrum framework, which is an Agile project management methodology. These short, daily meetings serve as a means for the development team to collaborate, share information, and maintain transparency about their work progress. Here's an overview of daily stand-up meetings:
Key Characteristics:
Frequency: Daily stand-up meetings occur every working day during a sprint. They are typically kept short, usually lasting no more than 15 minutes, to ensure that they remain focused and efficient.
Participants: The primary participants are the members of the development team. This typically includes developers, testers, designers, and anyone directly involved in the work. The Scrum Master facilitates the meeting, and the Product Owner may attend but usually doesn't speak unless there is a specific need.
Physical or Virtual: Stand-up meetings can be held in person, with participants standing to help keep the meeting brief, or they can be conducted virtually for distributed teams.
Purpose and Agenda:
The main objectives of daily stand-up meetings are as follows:
Daily Progress Update: Each team member provides a brief update on what they worked on since the last stand-up, what they plan to work on today, and any obstacles or impediments they are facing. This information helps the team understand the current state of the sprint and coordinate their efforts.
Synchronization: The meeting helps ensure that everyone on the team is aware of what their colleagues are doing. This synchronization helps avoid duplication of work and promotes a shared understanding of the sprint's progress.
Identification of Impediments: Team members use the stand-up meeting to highlight any obstacles or challenges that are impeding their progress. This is an opportunity for the team to collaboratively address these issues.
Reinforce Commitment: By speaking to their daily commitments and the sprint goal, team members reinforce their commitment to achieving the sprint's objectives.
Key Considerations:
Keep It Short: The emphasis on standing helps keep the meeting brief and focused. This is not a time for lengthy discussions or detailed technical conversations.
Consistency: Holding the stand-up at the same time and location every day helps ensure consistency and allows team members to plan their schedules accordingly.
Use of Task Boards: Many teams use visual task boards (physical or digital) to assist with the stand-up, providing a visual representation of the work and progress.
Daily stand-up meetings are an essential practice in Scrum and other Agile methodologies because they promote transparency, collaboration, and quick problem identification and resolution. They help teams stay on track with their sprint goals and ensure that everyone is aligned in their efforts to deliver value to the customer.
Sprint Review
The Sprint Review is a crucial ceremony in the Scrum framework, which is an Agile project management methodology. This event occurs at the end of each sprint, typically lasting 2 to 4 weeks, and it plays a vital role in ensuring that the Scrum team and stakeholders are aligned, and the product is developed in line with customer needs. Here's an overview of the Sprint Review:
Key Characteristics and Objectives:
Frequency: Sprint Reviews are conducted at the end of every sprint. The frequency of these meetings ensures that the product is frequently evaluated and improved.
Participants: Key participants in the Sprint Review include the Scrum Team (Development Team, Scrum Master, and Product Owner), stakeholders (customers, end-users, management, or anyone with an interest in the product), and possibly external experts or contributors.
Purpose: The primary purpose of the Sprint Review is to present the work completed during the sprint and gather feedback from stakeholders. It provides an opportunity to inspect and adapt the product based on the feedback and evolving requirements.
Agenda and Activities:
During a Sprint Review, the following activities typically take place:
Product Demonstration: The Development Team demonstrates the potentially shippable product increment that has been completed during the sprint. This demonstration showcases the new features, improvements, or functionality added in the sprint.
Feedback and Discussion: After the demonstration, stakeholders provide feedback and ask questions about the product. This feedback is valuable for ensuring that the product aligns with their needs and expectations.
Review of the Product Backlog: The Product Owner may update the Product Backlog based on feedback received during the Sprint Review. This can involve reprioritizing items or adding new ones based on stakeholder input.
Discussion of the Sprint's Achievements: The Scrum Team discusses what was completed during the sprint, what went well, and any challenges encountered. This provides transparency about the sprint's accomplishments.
Key Considerations:
Transparency: The Sprint Review emphasizes transparency, ensuring that stakeholders are informed about the state of the product and have a chance to influence its direction.
Customer-Centric: The Sprint Review reinforces the Agile principle of customer collaboration, ensuring that the product being developed aligns with customer needs.
Short and Focused: Sprint Reviews should be time-boxed, typically to around one hour or less. This maintains focus and prevents the meeting from becoming too lengthy.
In summary, the Sprint Review is a key event in Scrum that promotes collaboration, transparency, and a customer-centric approach to product development. It is an opportunity for stakeholders to inspect the product and provide feedback, ultimately leading to improvements and a better understanding of the product's alignment with customer requirements.
Sprint Retrospective
The Sprint Retrospective is an important ceremony in the Scrum framework, which is an Agile project management methodology. This meeting occurs at the end of each sprint, typically lasting 2 to 4 weeks, and it provides the Scrum Team with an opportunity to reflect on their work and processes to identify areas for improvement. Here's an overview of the Sprint Retrospective:
Key Characteristics and Objectives:
Frequency: Sprint Retrospectives are conducted at the end of every sprint. The frequent occurrence of these meetings allows for continuous improvement.
Participants: The primary participants in the Sprint Retrospective are the members of the Scrum Team, which includes the Development Team, Scrum Master, and Product Owner. These individuals collectively discuss the sprint and potential improvements.
Purpose: The primary purpose of the Sprint Retrospective is to reflect on the previous sprint's processes and outcomes. The main objectives are to identify what went well, what didn't go well, and what can be done differently in the next sprint to improve team performance and product development.
Agenda and Activities:
During a Sprint Retrospective, the following activities typically take place:
Review of the Previous Sprint: The team reviews the work accomplished during the previous sprint, including the sprint goal, the work completed, and any unfinished work or impediments.
What Went Well: The team discusses and identifies the aspects of the sprint that went well. This could include successful team collaboration, the completion of user stories, or any other positive aspects of the sprint.
What Didn't Go Well: The team also discusses and identifies the challenges or issues they encountered during the sprint. This could include impediments, communication problems, or other issues that hindered progress.
Action Items: The team commits to specific action items or changes based on the identified areas for improvement. These action items should be actionable, assignable, and measurable, and they are incorporated into the next sprint's plan.
Key Considerations:
Iterative Improvement: The Sprint Retrospective reinforces the Agile principle of continuous improvement. The goal is to incrementally enhance team performance and product development over time.
Time-Boxed: The meeting is time-boxed, typically lasting one to two hours, to maintain focus and ensure that it does not become overly lengthy.
Focus on Process: The focus of the Sprint Retrospective is on the team's processes and collaboration, rather than individual performance.
Transparency: The outcomes of the Sprint Retrospective, including action items for improvement, are made transparent to the team and relevant stakeholders.
The Sprint Retrospective is a critical element of the Scrum framework, as it provides a structured and regular means for teams to reflect on their work and make continuous improvements
Definition of Done (DoD)
The Definition of Done (DoD) is a fundamental concept in the Scrum framework and other Agile methodologies. It's a set of criteria or conditions that a product increment or work item must meet to be considered complete, potentially shippable, and ready for delivery to the customer or stakeholders. The DoD helps ensure that the team and stakeholders have a shared understanding of what it means for a task, user story, or feature to be finished. The specific criteria in the DoD are established by the Scrum Team and may vary from one project or team to another, but they typically include the following types of checks and conditions:
Functional Requirements: These criteria ensure that the work item meets its intended functionality and that all user stories or tasks are implemented as specified in the sprint backlog.
Testing: It may specify that the work item must undergo various levels of testing, such as unit testing, integration testing, and user acceptance testing, to verify that it functions correctly and doesn't introduce regressions in other parts of the product.
Documentation: The DoD may require that the work item is documented sufficiently for both team members and end-users, which can include user manuals, technical documentation, or inline code comments.
Performance: If performance is critical, the DoD may include specific performance criteria, such as response time, resource usage, or scalability requirements.
Security: Security checks and compliance with security standards may be part of the DoD to ensure that the work item doesn't introduce vulnerabilities.
No Unresolved Bugs: The DoD may specify that there are no unresolved or critical bugs associated with the work item.
Approved by the Product Owner: The Product Owner must approve the work item against the DoD criteria before it can be considered done.
The Definition of Done is important for maintaining product quality, ensuring that work is truly complete, and facilitating a shared understanding of the team's expectations. By adhering to the DoD, teams can consistently deliver high-quality, potentially shippable product increments at the end of each sprint, ultimately contributing to customer satisfaction and achieving the goals of Agile development methodologies.
Burndown Charts
A Burndown Chart is a visual tool commonly used in Agile project management, particularly in the Scrum framework. It provides a clear and easily understandable way to track the progress of work in a sprint or project. Burndown Charts help teams and stakeholders monitor how well they are staying on track to complete all the planned work within a specific time frame, typically a sprint.
Here are the key features and uses of Burndown Charts:
Time vs. Work Remaining: A Burndown Chart represents time on the horizontal axis (e.g., days or sprints) and work remaining on the vertical axis (e.g., story points, tasks, or hours). It shows how much work remains to be done over time.
Ideal Line: The chart typically includes an "ideal line" that represents the expected progress if the team completes the same amount of work every day or sprint. This line slopes downward at a constant rate from the starting point to the end of the time frame.
Tracking Progress: By comparing the actual and ideal lines, team members and stakeholders can quickly assess whether the sprint is on track, behind, or ahead of schedule. This information is valuable for making timely adjustments to meet the sprint's goals.
Transparency and Communication: Burndown Charts offer a transparent way to communicate progress to the team and stakeholders. They facilitate discussions during the Daily Stand-up meetings and Sprint Reviews, where the team can address any issues or impediments to meeting their goals.
Burndown Charts are a valuable tool for Agile teams as they offer a real-time snapshot of the project's progress. They are often used for sprint-level monitoring but can also be applied to larger project timelines. By providing visibility into work completion, Burndown Charts help teams make data-driven decisions, manage scope changes, and ultimately deliver high-quality results on time.
Conclusion
In conclusion, the concepts and practices we've explored in the realm of project management, particularly within the context of Agile and Scrum methodologies, provide a dynamic framework for managing projects and delivering value to customers.
These principles and practices collectively enable teams to deliver value incrementally, adapt to changing requirements, and maintain a strong focus on customer satisfaction. The Agile and Scrum methodologies offer a structured and collaborative approach to project management that has become a cornerstone for many industries, helping teams achieve greater agility and success in an ever-changing world.
Read More
Project management is a dynamic and multifaceted discipline that encompasses a wide array of methodologies and approaches. Among these, the Agile framework has gained significant prominence for its ability to foster flexibility, collaboration, and efficiency in managing projects. At the heart of Agile lies the concept of a "sprint," a term that is central to several Agile methodologies, particularly Scrum.
In this exploration of sprints in project management, we will unravel the fundamental principles that underpin this concept, its role in driving iterative development, and how it harmonizes with Agile methodologies. Sprints represent a powerful tool for breaking down complex projects into manageable, time-boxed segments, allowing teams to focus on delivering high-value, customer-centric work in a systematic and iterative fashion.
By the end of this exploration, you will have a comprehensive understanding of what a sprint is in project management, and how it aids in achieving project goals within the dynamic and adaptable framework of Agile methodologies. So, let's embark on this journey to uncover the significance and mechanics of sprints in project management.
Table of contents
- Definition of a Sprint
- Agile Methodology
- Scrum Framework
- Sprint Planning
- Sprint Duration
- Daily Stand-up Meetings
- Sprint Review
- Sprint Retrospective
- Definition of Done (DoD)
- Burndown Charts
- Conclusion
Definition of a Sprint
A sprint in project management, especially within the context of Agile methodologies like Scrum, is a time-bound, fixed duration iteration during which a cross-functional team works collaboratively to complete a set of pre-defined tasks or user stories. Sprints are typically short and predictable, usually lasting between 2 to 4 weeks, although this duration can vary based on the specific needs of the project.
Key features of a sprint include:
Time-Boxed: Sprints have a predetermined duration, which means that all work within the sprint must be completed within that timeframe. This time constraint creates a sense of urgency and helps the team focus on delivering a specific set of features or functionality.
User-Centric: Sprints prioritize delivering value to the end-users or customers. The work items, often referred to as user stories, are chosen based on their priority and value to the customer.
Cross-Functional Teams: A sprint team typically includes members with diverse skills, such as developers, testers, designers, and product owners. This diversity ensures that the team can complete the work independently without dependencies on external teams.
Daily Stand-up Meetings: During a sprint, the team holds daily stand-up meetings (also known as Daily Scrum) to discuss progress, challenges, and plans for the day. These short, daily meetings keep everyone informed and aligned.
Sprint Review: At the end of the sprint, a sprint review meeting is held to showcase the completed work to stakeholders and obtain feedback. This helps ensure that the product is meeting the evolving needs of the customers.
Sprints provide a structured and efficient approach to project management, allowing teams to adapt to changing requirements, gather feedback regularly, and deliver value incrementally. This iterative and customer-focused methodology is at the core of Agile project management and has become an essential tool for achieving success in complex and rapidly changing environments.
Agile Methodology
The Agile methodology is a set of principles and practices for software development and project management that prioritize flexibility, collaboration, customer feedback, and incremental progress. Agile methodologies are designed to address the challenges associated with traditional, plan-driven approaches to project management and development. They promote adaptive planning and iterative development, allowing teams to respond to changing requirements and deliver valuable products or services efficiently.
Key principles and concepts of Agile methodologies include:
Customer-Centric Approach: Agile places a strong emphasis on understanding and fulfilling customer needs. This is achieved by involving customers or end-users in the development process, continuously gathering feedback, and adapting the product or project to meet evolving requirements.
Collaboration and Communication: Agile methodologies emphasize effective collaboration among cross-functional teams, including developers, testers, designers, and product owners. Frequent communication is encouraged, often through daily stand-up meetings.
Adaptive Planning: Agile promotes adaptive planning rather than relying on a rigid, detailed plan created at the project's outset. Plans are updated and adjusted as new information becomes available or requirements change.
Working Software or Product: Agile prioritizes working software or a tangible product increment as the primary measure of progress. This ensures that value is being delivered at each step.
Agile methodologies are not limited to software development and can be applied in various contexts, including project management, product development, and even non-technical fields. Some of the most popular Agile frameworks and methodologies include Scrum, Kanban, Extreme Programming (XP), and Lean, each with its own set of practices and guidelines.
Scrum, for example, is a widely used Agile framework characterized by time-bound iterations (sprints), a specific set of roles (Scrum Master, Product Owner, Development Team), and ceremonies (sprint planning, daily stand-ups, sprint review, and sprint retrospective). Kanban, on the other hand, is focused on visualizing work, limiting work in progress, and optimizing workflow.
Agile methodologies have become essential in industries that require flexibility, adaptability, and a strong focus on delivering value to the customer. They have revolutionized project management and development practices by promoting a mindset of agility and collaboration.
Scrum Framework
The Scrum framework is a widely used Agile methodology for managing and delivering complex projects. It provides a structured approach to project management and product development, emphasizing collaboration, adaptability, and customer value. Scrum is particularly popular in software development, but its principles can be applied to a wide range of industries and projects.
Key components and concepts of the Scrum framework include:
Roles:
Scrum Master: The Scrum Master is responsible for ensuring that the Scrum framework is understood and implemented effectively. They facilitate Scrum events, remove impediments, and coach the team.
Product Owner: The Product Owner represents the customer or end-users and is responsible for defining and prioritizing the product backlog (the list of work to be done) and making decisions about what the team should work on.
Development Team: The Development Team is a cross-functional group of professionals responsible for delivering the potentially shippable product increment during each sprint.
Artifacts:
Product Backlog: This is a prioritized list of features, user stories, or tasks that represent the work to be done. The Product Owner manages and continually refines this backlog.
Sprint Backlog: At the beginning of each sprint, the team selects a set of items from the Product Backlog to work on during that sprint.
Increment: The Increment is the potentially shippable product or a piece of the product that is produced at the end of each sprint.
Events:
Sprint: A sprint is a time-boxed iteration typically lasting 2 to 4 weeks during which the Development Team works to complete a set of items from the Product Backlog.
Sprint Planning: At the start of each sprint, a sprint planning meeting is held. The team selects items from the Product Backlog to work on during the sprint and creates a plan for how to achieve the sprint goal.
Sprint Review: At the end of each sprint, a sprint review is conducted to showcase the work completed to stakeholders and gather feedback.
Sprint Retrospective: Following the sprint review, a sprint retrospective is held to reflect on the sprint's process and identify areas for improvement.
Key principles of the Scrum framework include:
Transparency: Scrum promotes transparency in all aspects of the project, including progress, issues, and the product itself. This transparency allows for effective communication and collaboration.
Inspection and Adaptation: Regular inspection of the product and the team's processes, followed by adaptation based on the inspection results, are integral to Scrum. This helps teams to continuously improve and respond to changing requirements.
Empiricism: Scrum is based on empirical process control, which means that decisions are made based on observed outcomes and feedback rather than predictions or assumptions.
Scrum is well-known for its ability to deliver value incrementally and adapt to changing requirements. It has gained widespread adoption across various industries because of its effectiveness in fostering collaboration and achieving customer satisfaction.
Sprint Planning
Sprint planning is a crucial ceremony in the Scrum framework, which is an Agile project management methodology. It's a collaborative and time-bound event that takes place at the beginning of each sprint. Sprint planning serves as a roadmap for the work the development team will undertake during the upcoming sprint, typically lasting 2 to 4 weeks. The primary goal of sprint planning is to define what will be delivered during the sprint and how it will be achieved.
Here are the key aspects of sprint planning:
Attendees:
Development Team: The cross-functional team that will be doing the work.
Scrum Master: Facilitates the sprint planning meeting.
Product Owner: Provides the team with the prioritized Product Backlog items.
Agenda:
Review of the Product Backlog: The Product Owner presents the top items in the Product Backlog, providing a brief overview of each item.
Task Breakdown: The selected items are further broken down into tasks, and the team discusses how they will complete each one.
Estimation: The team estimates the effort required for each task. Estimation is often done using story points, ideal days, or other relative sizing methods.
Capacity Planning: The team assesses its capacity for the sprint, considering team velocity (how much work they've completed in past sprints) and any known leave or holidays.
Definition of Done: The team reaffirms the Definition of Done, which outlines the criteria that must be met for work to be considered complete.
Time-Boxing: Sprint planning is time-boxed, meaning that it has a fixed duration. The time allocated for sprint planning should not exceed a certain limit, often one hour per week of the sprint.
Output:
Sprint Backlog: At the end of the sprint planning meeting, the selected items and tasks become the sprint backlog, which is a commitment by the team to complete the work during the sprint.
Sprint Goal: The sprint goal is reiterated to ensure everyone understands what the team is aiming to achieve.
Sprint planning sets clear expectations and provides a detailed plan for the team's work during the upcoming sprint. It also ensures that the team has a shared understanding of the sprint goal and the tasks required to achieve it. This collaborative approach fosters transparency and allows the team to adjust its plan if needed while maintaining a focus on delivering value to the customer.
Sprint Duration
Sprint duration, within the context of Agile and Scrum methodologies, refers to the specific length of time allocated for an iteration or sprint. Sprint durations are typically short, with the aim of achieving several objectives, including maintaining a sense of urgency, promoting regular inspection and adaptation, and delivering value incrementally. While the standard sprint duration is often two weeks, Scrum allows flexibility, and sprint durations can be adjusted based on the team's preferences and the nature of the project. Here are some key considerations regarding sprint duration:
Typical Sprint Durations: While two weeks is the most commonly used sprint duration, Scrum teams may opt for shorter sprints lasting one week or even longer sprints of three to four weeks. The choice of sprint duration depends on various factors, including the team's capacity, the project's complexity, and organizational preferences.
Advantages of Short Sprints: Shorter sprints offer benefits such as more frequent opportunities for inspection and adaptation, faster feedback from stakeholders, and greater agility in responding to changing requirements.
Stakeholder Engagement: Sprint duration affects how often stakeholders can see and provide feedback on the product. Shorter sprints enable more frequent stakeholder engagement, which can be valuable for validating product direction.
Sprint Planning Frequency: The shorter the sprint, the more often sprint planning, sprint review, and sprint retrospective meetings occur. Teams need to consider the time and effort required for these meetings when deciding on sprint duration.
Workload and Capacity: The team's capacity, velocity, and availability of team members are critical factors in determining sprint duration. Teams should select a sprint duration that allows them to consistently complete the planned work.
Consistency: Once a sprint duration is selected, it is typically kept consistent to maintain predictability. Frequent changes to sprint length can disrupt the team's rhythm and planning process.
In summary, sprint duration is a fundamental aspect of Scrum and Agile methodologies, with the flexibility to adapt to the needs of the team and the project. The choice of sprint duration should be made thoughtfully, considering factors such as project complexity, stakeholder engagement, and the team's capacity, while keeping in mind the Agile principles of delivering value regularly and promoting collaboration.
Daily Stand-up Meetings
Daily stand-up meetings, also known as Daily Scrum meetings, are a core practice within the Scrum framework, which is an Agile project management methodology. These short, daily meetings serve as a means for the development team to collaborate, share information, and maintain transparency about their work progress. Here's an overview of daily stand-up meetings:
Key Characteristics:
Frequency: Daily stand-up meetings occur every working day during a sprint. They are typically kept short, usually lasting no more than 15 minutes, to ensure that they remain focused and efficient.
Participants: The primary participants are the members of the development team. This typically includes developers, testers, designers, and anyone directly involved in the work. The Scrum Master facilitates the meeting, and the Product Owner may attend but usually doesn't speak unless there is a specific need.
Physical or Virtual: Stand-up meetings can be held in person, with participants standing to help keep the meeting brief, or they can be conducted virtually for distributed teams.
Purpose and Agenda:
The main objectives of daily stand-up meetings are as follows:
Daily Progress Update: Each team member provides a brief update on what they worked on since the last stand-up, what they plan to work on today, and any obstacles or impediments they are facing. This information helps the team understand the current state of the sprint and coordinate their efforts.
Synchronization: The meeting helps ensure that everyone on the team is aware of what their colleagues are doing. This synchronization helps avoid duplication of work and promotes a shared understanding of the sprint's progress.
Identification of Impediments: Team members use the stand-up meeting to highlight any obstacles or challenges that are impeding their progress. This is an opportunity for the team to collaboratively address these issues.
Reinforce Commitment: By speaking to their daily commitments and the sprint goal, team members reinforce their commitment to achieving the sprint's objectives.
Key Considerations:
Keep It Short: The emphasis on standing helps keep the meeting brief and focused. This is not a time for lengthy discussions or detailed technical conversations.
Consistency: Holding the stand-up at the same time and location every day helps ensure consistency and allows team members to plan their schedules accordingly.
Use of Task Boards: Many teams use visual task boards (physical or digital) to assist with the stand-up, providing a visual representation of the work and progress.
Daily stand-up meetings are an essential practice in Scrum and other Agile methodologies because they promote transparency, collaboration, and quick problem identification and resolution. They help teams stay on track with their sprint goals and ensure that everyone is aligned in their efforts to deliver value to the customer.
Sprint Review
The Sprint Review is a crucial ceremony in the Scrum framework, which is an Agile project management methodology. This event occurs at the end of each sprint, typically lasting 2 to 4 weeks, and it plays a vital role in ensuring that the Scrum team and stakeholders are aligned, and the product is developed in line with customer needs. Here's an overview of the Sprint Review:
Key Characteristics and Objectives:
Frequency: Sprint Reviews are conducted at the end of every sprint. The frequency of these meetings ensures that the product is frequently evaluated and improved.
Participants: Key participants in the Sprint Review include the Scrum Team (Development Team, Scrum Master, and Product Owner), stakeholders (customers, end-users, management, or anyone with an interest in the product), and possibly external experts or contributors.
Purpose: The primary purpose of the Sprint Review is to present the work completed during the sprint and gather feedback from stakeholders. It provides an opportunity to inspect and adapt the product based on the feedback and evolving requirements.
Agenda and Activities:
During a Sprint Review, the following activities typically take place:
Product Demonstration: The Development Team demonstrates the potentially shippable product increment that has been completed during the sprint. This demonstration showcases the new features, improvements, or functionality added in the sprint.
Feedback and Discussion: After the demonstration, stakeholders provide feedback and ask questions about the product. This feedback is valuable for ensuring that the product aligns with their needs and expectations.
Review of the Product Backlog: The Product Owner may update the Product Backlog based on feedback received during the Sprint Review. This can involve reprioritizing items or adding new ones based on stakeholder input.
Discussion of the Sprint's Achievements: The Scrum Team discusses what was completed during the sprint, what went well, and any challenges encountered. This provides transparency about the sprint's accomplishments.
Key Considerations:
Transparency: The Sprint Review emphasizes transparency, ensuring that stakeholders are informed about the state of the product and have a chance to influence its direction.
Customer-Centric: The Sprint Review reinforces the Agile principle of customer collaboration, ensuring that the product being developed aligns with customer needs.
Short and Focused: Sprint Reviews should be time-boxed, typically to around one hour or less. This maintains focus and prevents the meeting from becoming too lengthy.
In summary, the Sprint Review is a key event in Scrum that promotes collaboration, transparency, and a customer-centric approach to product development. It is an opportunity for stakeholders to inspect the product and provide feedback, ultimately leading to improvements and a better understanding of the product's alignment with customer requirements.
Sprint Retrospective
The Sprint Retrospective is an important ceremony in the Scrum framework, which is an Agile project management methodology. This meeting occurs at the end of each sprint, typically lasting 2 to 4 weeks, and it provides the Scrum Team with an opportunity to reflect on their work and processes to identify areas for improvement. Here's an overview of the Sprint Retrospective:
Key Characteristics and Objectives:
Frequency: Sprint Retrospectives are conducted at the end of every sprint. The frequent occurrence of these meetings allows for continuous improvement.
Participants: The primary participants in the Sprint Retrospective are the members of the Scrum Team, which includes the Development Team, Scrum Master, and Product Owner. These individuals collectively discuss the sprint and potential improvements.
Purpose: The primary purpose of the Sprint Retrospective is to reflect on the previous sprint's processes and outcomes. The main objectives are to identify what went well, what didn't go well, and what can be done differently in the next sprint to improve team performance and product development.
Agenda and Activities:
During a Sprint Retrospective, the following activities typically take place:
Review of the Previous Sprint: The team reviews the work accomplished during the previous sprint, including the sprint goal, the work completed, and any unfinished work or impediments.
What Went Well: The team discusses and identifies the aspects of the sprint that went well. This could include successful team collaboration, the completion of user stories, or any other positive aspects of the sprint.
What Didn't Go Well: The team also discusses and identifies the challenges or issues they encountered during the sprint. This could include impediments, communication problems, or other issues that hindered progress.
Action Items: The team commits to specific action items or changes based on the identified areas for improvement. These action items should be actionable, assignable, and measurable, and they are incorporated into the next sprint's plan.
Key Considerations:
Iterative Improvement: The Sprint Retrospective reinforces the Agile principle of continuous improvement. The goal is to incrementally enhance team performance and product development over time.
Time-Boxed: The meeting is time-boxed, typically lasting one to two hours, to maintain focus and ensure that it does not become overly lengthy.
Focus on Process: The focus of the Sprint Retrospective is on the team's processes and collaboration, rather than individual performance.
Transparency: The outcomes of the Sprint Retrospective, including action items for improvement, are made transparent to the team and relevant stakeholders.
The Sprint Retrospective is a critical element of the Scrum framework, as it provides a structured and regular means for teams to reflect on their work and make continuous improvements
Definition of Done (DoD)
The Definition of Done (DoD) is a fundamental concept in the Scrum framework and other Agile methodologies. It's a set of criteria or conditions that a product increment or work item must meet to be considered complete, potentially shippable, and ready for delivery to the customer or stakeholders. The DoD helps ensure that the team and stakeholders have a shared understanding of what it means for a task, user story, or feature to be finished. The specific criteria in the DoD are established by the Scrum Team and may vary from one project or team to another, but they typically include the following types of checks and conditions:
Functional Requirements: These criteria ensure that the work item meets its intended functionality and that all user stories or tasks are implemented as specified in the sprint backlog.
Testing: It may specify that the work item must undergo various levels of testing, such as unit testing, integration testing, and user acceptance testing, to verify that it functions correctly and doesn't introduce regressions in other parts of the product.
Documentation: The DoD may require that the work item is documented sufficiently for both team members and end-users, which can include user manuals, technical documentation, or inline code comments.
Performance: If performance is critical, the DoD may include specific performance criteria, such as response time, resource usage, or scalability requirements.
Security: Security checks and compliance with security standards may be part of the DoD to ensure that the work item doesn't introduce vulnerabilities.
No Unresolved Bugs: The DoD may specify that there are no unresolved or critical bugs associated with the work item.
Approved by the Product Owner: The Product Owner must approve the work item against the DoD criteria before it can be considered done.
The Definition of Done is important for maintaining product quality, ensuring that work is truly complete, and facilitating a shared understanding of the team's expectations. By adhering to the DoD, teams can consistently deliver high-quality, potentially shippable product increments at the end of each sprint, ultimately contributing to customer satisfaction and achieving the goals of Agile development methodologies.
Burndown Charts
A Burndown Chart is a visual tool commonly used in Agile project management, particularly in the Scrum framework. It provides a clear and easily understandable way to track the progress of work in a sprint or project. Burndown Charts help teams and stakeholders monitor how well they are staying on track to complete all the planned work within a specific time frame, typically a sprint.
Here are the key features and uses of Burndown Charts:
Time vs. Work Remaining: A Burndown Chart represents time on the horizontal axis (e.g., days or sprints) and work remaining on the vertical axis (e.g., story points, tasks, or hours). It shows how much work remains to be done over time.
Ideal Line: The chart typically includes an "ideal line" that represents the expected progress if the team completes the same amount of work every day or sprint. This line slopes downward at a constant rate from the starting point to the end of the time frame.
Tracking Progress: By comparing the actual and ideal lines, team members and stakeholders can quickly assess whether the sprint is on track, behind, or ahead of schedule. This information is valuable for making timely adjustments to meet the sprint's goals.
Transparency and Communication: Burndown Charts offer a transparent way to communicate progress to the team and stakeholders. They facilitate discussions during the Daily Stand-up meetings and Sprint Reviews, where the team can address any issues or impediments to meeting their goals.
Burndown Charts are a valuable tool for Agile teams as they offer a real-time snapshot of the project's progress. They are often used for sprint-level monitoring but can also be applied to larger project timelines. By providing visibility into work completion, Burndown Charts help teams make data-driven decisions, manage scope changes, and ultimately deliver high-quality results on time.
Conclusion
In conclusion, the concepts and practices we've explored in the realm of project management, particularly within the context of Agile and Scrum methodologies, provide a dynamic framework for managing projects and delivering value to customers.
These principles and practices collectively enable teams to deliver value incrementally, adapt to changing requirements, and maintain a strong focus on customer satisfaction. The Agile and Scrum methodologies offer a structured and collaborative approach to project management that has become a cornerstone for many industries, helping teams achieve greater agility and success in an ever-changing world.


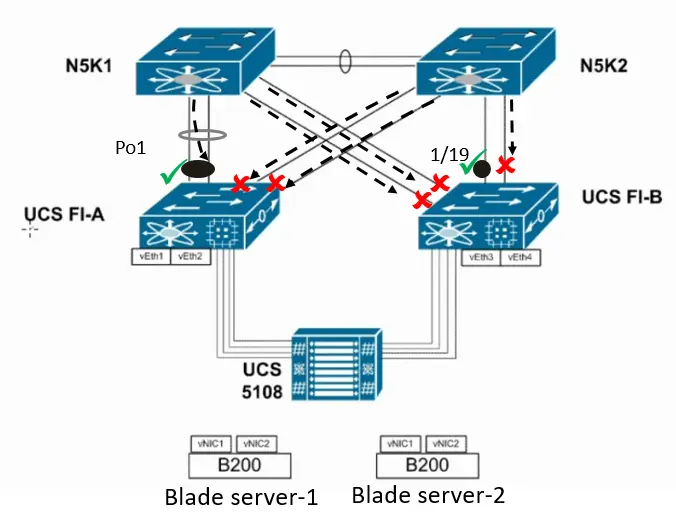


.jpg)











.png)












.jpg)
.jpg)
.png)