Quick Enquiry Form
Categories
- Agile and Scrum (218)
- BigData (34)
- Business Analysis (93)
- Cirtix Client Administration (53)
- Cisco (63)
- Cloud Technology (92)
- Cyber Security (54)
- Data Science and Business Intelligence (49)
- Developement Courses (53)
- DevOps (15)
- Digital Marketing (57)
- Emerging Technology (191)
- IT Service Management (76)
- Microsoft (54)
- Other (395)
- Project Management (494)
- Quality Management (140)
- salesforce (67)
Latest posts
5 Ways to Create a..
5 Big Trends in Content..
Data Governance Why It Matters..
Free Resources
Subscribe to Newsletter
Top Kanban Tools to Streamline Your Workflow in 2024
In today's fast-paced business world, efficient workflow management is key. It maximizes productivity and keeps teams on track. Kanban is a visual project management method. It is very popular for its simplicity and effectiveness in streamlining workflows. Visualizing tasks and progress helps teams spot bottlenecks. They can then prioritize work and improve collaboration. As we enter 2024, many Kanban tools have emerged. Each has unique features for different organizational needs. This article will discuss the best Kanban tools to improve your workflow this year.
1. Trello: The User-Friendly Classic
Trello remains one of the most popular Kanban tools for teams of all sizes. The intuitive design enables users to quickly build boards, lists, and cards. This makes it easy to organize tasks visually. Key features include:
- Drag-and-Drop Functionality: Move cards between lists to reflect progress seamlessly.
- Integration with Other Tools: Connect Trello with Slack, Google Drive, and Jira to centralize your workflow.
- Customizable Boards: Tailor boards to fit your project. It’s possible to integrate labels, establish due dates, and implement checklists.
Trello's versatility suits many uses, from to-do lists to complex project management. Its free tier is particularly attractive for small teams and individuals.
2. Asana: Advanced Project Management Capabilities
Asana takes Kanban to the next level with its comprehensive project management features. It has a Kanban board view. It also has task dependencies, timeline views, and project milestones. Key highlights include:
- Task Dependencies: Assign tasks that depend on others' completion to help teams prioritize.
- Project Templates: Utilize pre-built templates to kickstart projects quickly.
- Custom Fields: Add relevant information to tasks for better tracking and reporting.
Asana's strong reporting features help managers track progress. This keeps teams aligned and focused on their goals. The platform suits medium to large teams. They need more than a basic Kanban tool.
3. Monday.com: Customization at Its Best
Monday.com offers a customizable Kanban experience. It lets teams create workflows that suit their unique processes. Its user-friendly interface and flexibility attract organizations of all sizes. Key features include:
- Custom Workflows: Design workflows tailored to specific projects or teams, ensuring optimal efficiency.
- Automations: Set up automated notifications, reminders, and status updates to streamline communication.
- Use graphs and charts to show team performance and project progress.
Monday.com has many integrations. It can fit into any tech stack. This makes it a great tool for teams wanting to improve their workflow.
4. ClickUp: All-in-One Productivity Suite
- ClickUp is a versatile tool. It combines Kanban boards with other project management features. These include document collaboration, goal tracking, and time tracking. Its all-in-one approach makes it ideal for teams seeking a comprehensive solution. Notable features include:
- Multiple Views: Use Kanban, list, and calendar views to manage tasks in a way that suits your workflow.
- Goal Tracking: Set and track goals with tasks. This aligns the team's efforts with business objectives.
- Customizable Dashboards: Create dashboards to show key metrics and project statuses. This gives a complete view of your workflow.
ClickUp's flexibility and features suit many industries, from tech startups to creative agencies.
5. Jira: Ideal for Software Development Teams
Jira is a top project management tool. Software development teams, especially Agile ones, favor it. It is more complex than traditional Kanban tools. But, its advanced features cater to technical teams' unique needs. Key functionalities include:
- Sprint Planning: Organize tasks into sprints for effective workload management and iterative development.
- Issue Tracking: Use one platform to monitor bugs and tasks. It keeps development on schedule.
- Integrate with GitHub, Bitbucket, and other dev tools for smooth workflows.
- Jira is perfect for large software development teams. It has the tools to manage complex projects efficiently.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As organizations adapt to a changing business landscape, effective workflow tools are vital. Kanban tools like Trello, Asana, Monday.com, ClickUp, and Jira have varied features. They fit different team needs. They help improve processes and productivity. The right tool depends on your team's size, workflow, and needs.
In 2024, using these Kanban tools can improve project management. It can also enhance communication and outcomes for your organization. A Kanban solution can help any organization, big or small, visualize and manage work. Explore these tools. Evaluate their features. Then, choose the one that best fits your workflow. It will help streamline your projects.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, efficient workflow management is key. It maximizes productivity and keeps teams on track. Kanban is a visual project management method. It is very popular for its simplicity and effectiveness in streamlining workflows. Visualizing tasks and progress helps teams spot bottlenecks. They can then prioritize work and improve collaboration. As we enter 2024, many Kanban tools have emerged. Each has unique features for different organizational needs. This article will discuss the best Kanban tools to improve your workflow this year.
1. Trello: The User-Friendly Classic
Trello remains one of the most popular Kanban tools for teams of all sizes. The intuitive design enables users to quickly build boards, lists, and cards. This makes it easy to organize tasks visually. Key features include:
- Drag-and-Drop Functionality: Move cards between lists to reflect progress seamlessly.
- Integration with Other Tools: Connect Trello with Slack, Google Drive, and Jira to centralize your workflow.
- Customizable Boards: Tailor boards to fit your project. It’s possible to integrate labels, establish due dates, and implement checklists.
Trello's versatility suits many uses, from to-do lists to complex project management. Its free tier is particularly attractive for small teams and individuals.
2. Asana: Advanced Project Management Capabilities
Asana takes Kanban to the next level with its comprehensive project management features. It has a Kanban board view. It also has task dependencies, timeline views, and project milestones. Key highlights include:
- Task Dependencies: Assign tasks that depend on others' completion to help teams prioritize.
- Project Templates: Utilize pre-built templates to kickstart projects quickly.
- Custom Fields: Add relevant information to tasks for better tracking and reporting.
Asana's strong reporting features help managers track progress. This keeps teams aligned and focused on their goals. The platform suits medium to large teams. They need more than a basic Kanban tool.
3. Monday.com: Customization at Its Best
Monday.com offers a customizable Kanban experience. It lets teams create workflows that suit their unique processes. Its user-friendly interface and flexibility attract organizations of all sizes. Key features include:
- Custom Workflows: Design workflows tailored to specific projects or teams, ensuring optimal efficiency.
- Automations: Set up automated notifications, reminders, and status updates to streamline communication.
- Use graphs and charts to show team performance and project progress.
Monday.com has many integrations. It can fit into any tech stack. This makes it a great tool for teams wanting to improve their workflow.
4. ClickUp: All-in-One Productivity Suite
- ClickUp is a versatile tool. It combines Kanban boards with other project management features. These include document collaboration, goal tracking, and time tracking. Its all-in-one approach makes it ideal for teams seeking a comprehensive solution. Notable features include:
- Multiple Views: Use Kanban, list, and calendar views to manage tasks in a way that suits your workflow.
- Goal Tracking: Set and track goals with tasks. This aligns the team's efforts with business objectives.
- Customizable Dashboards: Create dashboards to show key metrics and project statuses. This gives a complete view of your workflow.
ClickUp's flexibility and features suit many industries, from tech startups to creative agencies.
5. Jira: Ideal for Software Development Teams
Jira is a top project management tool. Software development teams, especially Agile ones, favor it. It is more complex than traditional Kanban tools. But, its advanced features cater to technical teams' unique needs. Key functionalities include:
- Sprint Planning: Organize tasks into sprints for effective workload management and iterative development.
- Issue Tracking: Use one platform to monitor bugs and tasks. It keeps development on schedule.
- Integrate with GitHub, Bitbucket, and other dev tools for smooth workflows.
- Jira is perfect for large software development teams. It has the tools to manage complex projects efficiently.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As organizations adapt to a changing business landscape, effective workflow tools are vital. Kanban tools like Trello, Asana, Monday.com, ClickUp, and Jira have varied features. They fit different team needs. They help improve processes and productivity. The right tool depends on your team's size, workflow, and needs.
In 2024, using these Kanban tools can improve project management. It can also enhance communication and outcomes for your organization. A Kanban solution can help any organization, big or small, visualize and manage work. Explore these tools. Evaluate their features. Then, choose the one that best fits your workflow. It will help streamline your projects.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Essential Excel Formulas for Financial Modeling in 2024
Financial modeling is vital for analysis and forecasting. It aids decision-making in finance, investment, and corporate management. Excel is a top tool for financial modeling. It's popular for its flexibility, functionality, and accessibility. Many know basic formulas, like SUM and AVERAGE. But, advanced ones can greatly improve financial models. They can make them more accurate and efficient. In 2024, advanced Excel skills are crucial. Businesses want to improve decision-making in a data-driven world.
This article explores the best Excel formulas for financial modeling in 2024. It covers their uses, application tips, and how they improve financial analysis.
1. IFERROR and IFNA: Enhancing Data Accuracy
In financial models, data integrity is paramount. The IFERROR and IFNA functions are invaluable. They handle data that might cause errors and disrupt a model's accuracy. These functions help replace error messages (like #DIV/0!, #N/A, or #VALUE!) with different values or messages. This makes your financial models cleaner and easier to read.
- IFERROR: Allows you to return a specified value when an error is detected. In a financial model, use IFERROR to replace divide-by-zero errors with a blank cell or "N/A".
Example: =IFERROR(A1/B1, "N/A")
- IFNA: It handles only #N/A errors. It's useful for VLOOKUPs or INDEX-MATCH functions where a value might not exist in the data set.
Example: =IFNA(VLOOKUP(A1, B1:C10, 2, FALSE), "Not Found")
These functions are useful for sensitivity analysis. It uses data that may be incomplete or incorrect. Without these functions, the results could be misleading.
2. INDEX and MATCH: A More Powerful Alternative to VLOOKUP
VLOOKUP is popular but has limits. The lookup value must be in the first column of a table. It only allows left-to-right searches. The INDEX and MATCH combination overcomes these limits. It offers more flexibility for complex financial models.
MATCH: Returns the relative position of a value within a range.
Example: =MATCH("Revenue", A1:A10, 0)
- INDEX: Returns the value of a cell within a specified row and column in a table.
Example: =INDEX(A1:C10, 5, 2)
- INDEX and MATCH, when combined, let you look up values in a table. Their position in the table does not matter. This flexibility is vital for complex financial models, like DCF analysis. Their data may not be in a simple left-to-right format.
3. XLOOKUP: The Ultimate Lookup Function
XLOOKUP, introduced in newer Excel versions, is a game changer in financial modeling. It combines the best of VLOOKUP, HLOOKUP, and INDEX/MATCH into one function. It lets you look up data both horizontally and vertically. You can return exact matches or the next largest or smallest value.
- XLOOKUP: It lets you search for a value in one range. Then, it returns a matching value from another range. It has none of VLOOKUP's limitations.
Example: =XLOOKUP(A2, B1:B10, C1:C10)
- XLOOKUP fixes many problems with VLOOKUP. It is especially useful for financial projections. It can match interest rates to specific time periods. It can also retrieve costs for different business units.
4. OFFSET and INDIRECT: Dynamic Range Adjustments
The OFFSET and INDIRECT functions are perfect for financial models. They need dynamic ranges that adjust based on changing inputs. These functions allow for indirect referencing of cells or ranges. They provide more flexibility and control in a model.
- OFFSET: It returns a reference to a range. It is offset from a starting point by a specified number of rows and columns. It is useful for making models that must adapt to changing data.
Example: =OFFSET(A1, 3, 2) (This formula returns the value 3 rows down and 2 columns to the right of cell A1)
- INDIRECT: Converts a text string into a cell reference. It lets you build models that can dynamically reference different sheets, columns, or rows.
=INDIRECT("Sheet2!B"&A1) (This formula references the value in column B of Sheet2, using the row in A1.)
- These functions help create rolling forecasts and other financial models. They must handle flexible, moving ranges of data.
5. FORECAST and TREND: Predictive Analysis for Financial Projections
For forward-looking financial models, use the FORECAST and TREND functions. They predict future values based on historical data. These formulas are invaluable in financial forecasting. They help businesses make informed decisions about revenue, expenses, and market trends.
- FORECAST: Estimates a future value along a linear trend based on known values. It is often used in financial forecasting to predict future sales, costs, or cash flows.
Example: =FORECAST(B2, A2:A10, B2:B10)
- TREND: Like FORECAST, but can return many values for a range of future periods. It allows you to forecast a series of future values based on historical data.
Example: =TREND(B2:B10, A2:A10)
- These functions help create better financial models. They provide a data-driven basis for future planning and decisions.
How to obtain Microsoft Excel certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, the demands on financial models are growing. So, it's essential to master advanced Excel formulas. They are key to creating reliable, dynamic, and insightful models. The formulas discussed are powerful and flexible. They are: IFERROR, INDEX/MATCH, XLOOKUP, OFFSET/INDIRECT, and FORECAST/TREND. They help build better models that provide actionable insights.
These advanced functions can help financial analysts. They can significantly enhance the accuracy, efficiency, and predictive power of their models. These formulas help with forecasting, data analysis, and sensitivity tests. They streamline workflows and improve financial decision-making.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Financial modeling is vital for analysis and forecasting. It aids decision-making in finance, investment, and corporate management. Excel is a top tool for financial modeling. It's popular for its flexibility, functionality, and accessibility. Many know basic formulas, like SUM and AVERAGE. But, advanced ones can greatly improve financial models. They can make them more accurate and efficient. In 2024, advanced Excel skills are crucial. Businesses want to improve decision-making in a data-driven world.
This article explores the best Excel formulas for financial modeling in 2024. It covers their uses, application tips, and how they improve financial analysis.
1. IFERROR and IFNA: Enhancing Data Accuracy
In financial models, data integrity is paramount. The IFERROR and IFNA functions are invaluable. They handle data that might cause errors and disrupt a model's accuracy. These functions help replace error messages (like #DIV/0!, #N/A, or #VALUE!) with different values or messages. This makes your financial models cleaner and easier to read.
- IFERROR: Allows you to return a specified value when an error is detected. In a financial model, use IFERROR to replace divide-by-zero errors with a blank cell or "N/A".
Example: =IFERROR(A1/B1, "N/A")
- IFNA: It handles only #N/A errors. It's useful for VLOOKUPs or INDEX-MATCH functions where a value might not exist in the data set.
Example: =IFNA(VLOOKUP(A1, B1:C10, 2, FALSE), "Not Found")
These functions are useful for sensitivity analysis. It uses data that may be incomplete or incorrect. Without these functions, the results could be misleading.
2. INDEX and MATCH: A More Powerful Alternative to VLOOKUP
VLOOKUP is popular but has limits. The lookup value must be in the first column of a table. It only allows left-to-right searches. The INDEX and MATCH combination overcomes these limits. It offers more flexibility for complex financial models.
MATCH: Returns the relative position of a value within a range.
Example: =MATCH("Revenue", A1:A10, 0)
- INDEX: Returns the value of a cell within a specified row and column in a table.
Example: =INDEX(A1:C10, 5, 2)
- INDEX and MATCH, when combined, let you look up values in a table. Their position in the table does not matter. This flexibility is vital for complex financial models, like DCF analysis. Their data may not be in a simple left-to-right format.
3. XLOOKUP: The Ultimate Lookup Function
XLOOKUP, introduced in newer Excel versions, is a game changer in financial modeling. It combines the best of VLOOKUP, HLOOKUP, and INDEX/MATCH into one function. It lets you look up data both horizontally and vertically. You can return exact matches or the next largest or smallest value.
- XLOOKUP: It lets you search for a value in one range. Then, it returns a matching value from another range. It has none of VLOOKUP's limitations.
Example: =XLOOKUP(A2, B1:B10, C1:C10)
- XLOOKUP fixes many problems with VLOOKUP. It is especially useful for financial projections. It can match interest rates to specific time periods. It can also retrieve costs for different business units.
4. OFFSET and INDIRECT: Dynamic Range Adjustments
The OFFSET and INDIRECT functions are perfect for financial models. They need dynamic ranges that adjust based on changing inputs. These functions allow for indirect referencing of cells or ranges. They provide more flexibility and control in a model.
- OFFSET: It returns a reference to a range. It is offset from a starting point by a specified number of rows and columns. It is useful for making models that must adapt to changing data.
Example: =OFFSET(A1, 3, 2) (This formula returns the value 3 rows down and 2 columns to the right of cell A1)
- INDIRECT: Converts a text string into a cell reference. It lets you build models that can dynamically reference different sheets, columns, or rows.
=INDIRECT("Sheet2!B"&A1) (This formula references the value in column B of Sheet2, using the row in A1.)
- These functions help create rolling forecasts and other financial models. They must handle flexible, moving ranges of data.
5. FORECAST and TREND: Predictive Analysis for Financial Projections
For forward-looking financial models, use the FORECAST and TREND functions. They predict future values based on historical data. These formulas are invaluable in financial forecasting. They help businesses make informed decisions about revenue, expenses, and market trends.
- FORECAST: Estimates a future value along a linear trend based on known values. It is often used in financial forecasting to predict future sales, costs, or cash flows.
Example: =FORECAST(B2, A2:A10, B2:B10)
- TREND: Like FORECAST, but can return many values for a range of future periods. It allows you to forecast a series of future values based on historical data.
Example: =TREND(B2:B10, A2:A10)
- These functions help create better financial models. They provide a data-driven basis for future planning and decisions.
How to obtain Microsoft Excel certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, the demands on financial models are growing. So, it's essential to master advanced Excel formulas. They are key to creating reliable, dynamic, and insightful models. The formulas discussed are powerful and flexible. They are: IFERROR, INDEX/MATCH, XLOOKUP, OFFSET/INDIRECT, and FORECAST/TREND. They help build better models that provide actionable insights.
These advanced functions can help financial analysts. They can significantly enhance the accuracy, efficiency, and predictive power of their models. These formulas help with forecasting, data analysis, and sensitivity tests. They streamline workflows and improve financial decision-making.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Adapting PMP for AI and Automation in Project Management
Organizations must use AI and automation in project management. It's key to competing in a fast-paced digital world. As project management professionals, we must adapt traditional PMP methods. We need to leverage the benefits of AI and automation. Let's explore how to adapt PMP to new technologies and ensure project success.
Importance of Adapting PMP for AI and Automation
As AI and automation change industries, we must adapt the PMP framework to stay relevant. It stands for Project Management Professional. AI tools improve decision-making, streamline projects, and reduce errors. They make project management more efficient. Automation lets PMP-certified pros manage complex projects faster. It boosts productivity and success rates.
1. AI and automation can improve project management. They can streamline processes, cut manual work, and boost efficiency. Automation now saves time and resources on tasks. Project managers can focus on strategic decisions and problem-solving.
2. Better Decisions: AI can analyze vast data in real-time. It gives project managers insights to make quick, informed decisions. Automation tools can help spot risks and opportunities. This allows for proactive management and mitigation.
3. Adaptability to Digital Transformation: As businesses adopt digital tools, project management must evolve to align with new tech and trends. Integrating AI and automation into PMP practices will help organizations. It will keep them agile and competitive in the digital world.
4. Future-Proofing Project Management: As AI and automation advance, project managers must adapt. They need to incorporate these technologies into their workflows. By embracing innovation, project managers can future-proof their work. They should use the latest tools and techniques to ensure long-term success.
Strategies for Integrating AI and Automation in PMP
Integrating AI and automation into PMP practices can streamline workflows. It can also improve decision-making and boost efficiency. AI-driven tools for predictive analytics can help project managers. They can forecast risks and allocate resources better. Automation makes routine tasks, like scheduling and reporting, easier. It allows PMP-certified professionals to focus on strategic goals and engaging stakeholders.
1. Training and Certification: Project managers should pursue training and certifications. They should focus on AI and automation in project management. Platforms like the Project Management Institute (PMI) offer courses and certifications. They help professionals improve their skills in these areas.
2. Use of Project Management Tools: AI-powered tools can streamline processes. They improve collaboration and project efficiency. Tools like Asana, Trello, and Microsoft Project use AI and automation. They simplify project tasks and decision-making.
3. Agile and Lean project management methods are ideal for AI and automation. They stress flexibility, adaptability, and continuous improvement. By following these practices, project managers can leverage technology. They can deliver projects more efficiently.
4. Collaborate with AI experts. They can advise on using AI and automation in project management. By working together, project managers can drive innovation. They can use their expertise with AI professionals' technical knowledge.
Benefits of Combining PMP with AI and Automation
1. AI and automation can boost productivity and efficiency. They optimize workflows, automate repetitive tasks, and speed up decisions.
2. AI algorithms can analyze project data:They can find trends, patterns, and correlations that human analysts might miss. It lets project managers use insights to make data-driven decisions.
3. Improved Risk Management: AI and automation tools can spot risks early. This lets project managers fix them before they escalate. This proactive approach to risk management enhances project outcomes and minimizes disruptions.
Better risk management helps an organization spot and reduce risks. It does so before they harm key operations. Proactive strategies can help businesses. They can cut losses, ensure compliance, and keep projects on track. This approach leads to greater resilience, helping organizations adapt to uncertainty with confidence.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, we must adapt PMP for AI and automation in project management. It's essential to stay competitive in today's digital world. These technologies can boost efficiency and decision-making when used with traditional project management. It will also future-proof their processes. Project managers must embrace innovation and use the latest tools. This will help them succeed and deliver value in an AI-driven world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Organizations must use AI and automation in project management. It's key to competing in a fast-paced digital world. As project management professionals, we must adapt traditional PMP methods. We need to leverage the benefits of AI and automation. Let's explore how to adapt PMP to new technologies and ensure project success.
Importance of Adapting PMP for AI and Automation
As AI and automation change industries, we must adapt the PMP framework to stay relevant. It stands for Project Management Professional. AI tools improve decision-making, streamline projects, and reduce errors. They make project management more efficient. Automation lets PMP-certified pros manage complex projects faster. It boosts productivity and success rates.
1. AI and automation can improve project management. They can streamline processes, cut manual work, and boost efficiency. Automation now saves time and resources on tasks. Project managers can focus on strategic decisions and problem-solving.
2. Better Decisions: AI can analyze vast data in real-time. It gives project managers insights to make quick, informed decisions. Automation tools can help spot risks and opportunities. This allows for proactive management and mitigation.
3. Adaptability to Digital Transformation: As businesses adopt digital tools, project management must evolve to align with new tech and trends. Integrating AI and automation into PMP practices will help organizations. It will keep them agile and competitive in the digital world.
4. Future-Proofing Project Management: As AI and automation advance, project managers must adapt. They need to incorporate these technologies into their workflows. By embracing innovation, project managers can future-proof their work. They should use the latest tools and techniques to ensure long-term success.
Strategies for Integrating AI and Automation in PMP
Integrating AI and automation into PMP practices can streamline workflows. It can also improve decision-making and boost efficiency. AI-driven tools for predictive analytics can help project managers. They can forecast risks and allocate resources better. Automation makes routine tasks, like scheduling and reporting, easier. It allows PMP-certified professionals to focus on strategic goals and engaging stakeholders.
1. Training and Certification: Project managers should pursue training and certifications. They should focus on AI and automation in project management. Platforms like the Project Management Institute (PMI) offer courses and certifications. They help professionals improve their skills in these areas.
2. Use of Project Management Tools: AI-powered tools can streamline processes. They improve collaboration and project efficiency. Tools like Asana, Trello, and Microsoft Project use AI and automation. They simplify project tasks and decision-making.
3. Agile and Lean project management methods are ideal for AI and automation. They stress flexibility, adaptability, and continuous improvement. By following these practices, project managers can leverage technology. They can deliver projects more efficiently.
4. Collaborate with AI experts. They can advise on using AI and automation in project management. By working together, project managers can drive innovation. They can use their expertise with AI professionals' technical knowledge.
Benefits of Combining PMP with AI and Automation
1. AI and automation can boost productivity and efficiency. They optimize workflows, automate repetitive tasks, and speed up decisions.
2. AI algorithms can analyze project data:They can find trends, patterns, and correlations that human analysts might miss. It lets project managers use insights to make data-driven decisions.
3. Improved Risk Management: AI and automation tools can spot risks early. This lets project managers fix them before they escalate. This proactive approach to risk management enhances project outcomes and minimizes disruptions.
Better risk management helps an organization spot and reduce risks. It does so before they harm key operations. Proactive strategies can help businesses. They can cut losses, ensure compliance, and keep projects on track. This approach leads to greater resilience, helping organizations adapt to uncertainty with confidence.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, we must adapt PMP for AI and automation in project management. It's essential to stay competitive in today's digital world. These technologies can boost efficiency and decision-making when used with traditional project management. It will also future-proof their processes. Project managers must embrace innovation and use the latest tools. This will help them succeed and deliver value in an AI-driven world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
CCBA Role in Streamlining Complex Project Requirements!
Are you a business analyst looking to enhance your skills and advance your career in project management? If so, obtaining a CCBA certification could be the key to unlocking new opportunities in the field. This article will explore the key role of CCBA. It streamlines complex project requirements and drives successful project delivery.
What is CCBA?
The CCBA, or Certification of Capability in Business Analysis, is a global certification for business analysts with experience. The International Institute of Business Analysis (IIBA) awards it. It shows a professional's expertise in business analysis principles and techniques. A CCBA certification shows a commitment to improving and excelling at business analysis.
The Importance of Streamlining Project Requirements
In today's fast-paced business world, projects are more complex. They need careful planning and execution. Streamlining project requirements is vital. It ensures all stakeholders are aligned and that project objectives are clear from the start. By gathering, analyzing, and documenting project requirements, business analysts can help. They can align project goals with the business strategy. This will increase the chances of project success.
Streamlining project requirements is vital. It ensures clear communication and alignment among stakeholders. This reduces misunderstandings and rework. By refining and prioritizing requirements early, project teams can save time and resources. They can then focus on delivering key objectives efficiently. This approach boosts project success. It keeps the scope in check and prevents costly delays or scope creep.
How CCBA Certification Helps in Streamlining Project Requirements
The CCBA (Certification in Competency in Business Analysis) certifies skills in business analysis. It is for professionals who gather, analyze, and manage project requirements. Using methods from their certification, business analysts can better identify stakeholders' needs. This ensures all requirements are clear and complete. This approach cuts misunderstandings. It also improves projects by enhancing team communication and collaboration.
CCBA certification gives business analysts the skills to improve project requirements. Here are some ways CCBA certification can benefit professionals:
-
Improved Stakeholder Management: CCBA training stresses the need to engage and communicate with stakeholders throughout the project. By mastering stakeholder management techniques, business analysts can ensure projects meet stakeholders' needs and expectations.
-
CCBA certification provides a structured approach to requirement gathering. It ensures that all necessary information is captured and analyzed systematically. This helps in avoiding missed requirements and scope creep, leading to more efficient project delivery.
-
Improved Business Process Analysis: The CCBA curriculum teaches analysts to find ways to improve and optimize business processes. Streamlining business processes can better align project goals with the organization's. This will improve project outcomes.
-
CCBA certification gives tools for project plans and documents. By following best practices in project planning, analysts can ensure that project requirements are clear and understood. They must also manage them throughout the project.
-
CCBA certification teaches analysts to coordinate and communicate on projects. By fostering collaboration, business analysts can ensure that project requirements are met. This will help achieve project goals.
How to obtain CCBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a CCBA certification can boost a business analyst's skills. It will help them streamline complex project requirements and ensure project success. CCBA-certified professionals can tackle modern project management challenges. They excel in stakeholder management, requirements gathering, and process analysis. They are also good at project planning and communication. So, why wait? Take the next step in your career and consider pursuing CCBA certification today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Are you a business analyst looking to enhance your skills and advance your career in project management? If so, obtaining a CCBA certification could be the key to unlocking new opportunities in the field. This article will explore the key role of CCBA. It streamlines complex project requirements and drives successful project delivery.
What is CCBA?
The CCBA, or Certification of Capability in Business Analysis, is a global certification for business analysts with experience. The International Institute of Business Analysis (IIBA) awards it. It shows a professional's expertise in business analysis principles and techniques. A CCBA certification shows a commitment to improving and excelling at business analysis.
The Importance of Streamlining Project Requirements
In today's fast-paced business world, projects are more complex. They need careful planning and execution. Streamlining project requirements is vital. It ensures all stakeholders are aligned and that project objectives are clear from the start. By gathering, analyzing, and documenting project requirements, business analysts can help. They can align project goals with the business strategy. This will increase the chances of project success.
Streamlining project requirements is vital. It ensures clear communication and alignment among stakeholders. This reduces misunderstandings and rework. By refining and prioritizing requirements early, project teams can save time and resources. They can then focus on delivering key objectives efficiently. This approach boosts project success. It keeps the scope in check and prevents costly delays or scope creep.
How CCBA Certification Helps in Streamlining Project Requirements
The CCBA (Certification in Competency in Business Analysis) certifies skills in business analysis. It is for professionals who gather, analyze, and manage project requirements. Using methods from their certification, business analysts can better identify stakeholders' needs. This ensures all requirements are clear and complete. This approach cuts misunderstandings. It also improves projects by enhancing team communication and collaboration.
CCBA certification gives business analysts the skills to improve project requirements. Here are some ways CCBA certification can benefit professionals:
-
Improved Stakeholder Management: CCBA training stresses the need to engage and communicate with stakeholders throughout the project. By mastering stakeholder management techniques, business analysts can ensure projects meet stakeholders' needs and expectations.
-
CCBA certification provides a structured approach to requirement gathering. It ensures that all necessary information is captured and analyzed systematically. This helps in avoiding missed requirements and scope creep, leading to more efficient project delivery.
-
Improved Business Process Analysis: The CCBA curriculum teaches analysts to find ways to improve and optimize business processes. Streamlining business processes can better align project goals with the organization's. This will improve project outcomes.
-
CCBA certification gives tools for project plans and documents. By following best practices in project planning, analysts can ensure that project requirements are clear and understood. They must also manage them throughout the project.
-
CCBA certification teaches analysts to coordinate and communicate on projects. By fostering collaboration, business analysts can ensure that project requirements are met. This will help achieve project goals.
How to obtain CCBA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a CCBA certification can boost a business analyst's skills. It will help them streamline complex project requirements and ensure project success. CCBA-certified professionals can tackle modern project management challenges. They excel in stakeholder management, requirements gathering, and process analysis. They are also good at project planning and communication. So, why wait? Take the next step in your career and consider pursuing CCBA certification today!
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Challenges of AI Implementation in IT Service Management
In today's fast-changing tech world, using AI in ITSM brings many challenges. Organizations face many obstacles in using AI in ITSM. They must navigate integration and deployment issues to reap its benefits.
AI in ITSM Challenges
A key challenge of using AI in ITSM is integrating it with existing ITSM tools and processes. AI needs a lot of data to work well. Integrating it with ITSM systems can be tough. Another challenge organizations face is the difficulty of deploying AI in ITSM environments. Deploying an AI solution can be complex and time-consuming. It involves choosing the right AI and training ITSM teams.
Integrating AI into IT Service Management (ITSM) poses challenges. Organizations must navigate them. A big hurdle is employees' resistance to change. They may fear for their jobs and doubt AI's effectiveness. Also, there are technical obstacles. These include ensuring data quality and integrating AI tools with existing ITSM frameworks. They can complicate deployment efforts.
Obstacles of AI Implementation in ITSM
There are several key obstacles that organizations encounter when implementing AI in ITSM. One major obstacle is the lack of AI adoption in IT service management. Many organizations may be hesitant to embrace AI technology due to concerns about its impact on ITSM processes and workflows. Also, the complexities of AI adoption in ITSM can challenge organizations. Organizations must develop an AI strategy. They must also overcome risks in implementation. Only then can they integrate AI successfully.
Implementing AI in IT Service Management (ITSM) can face many hurdles. Cultural resistance is one. Employees may fear job loss and less personal service.
AI Challenges in IT Service Management
One of the key challenges of AI adoption in ITSM is the potential risks associated with implementing AI technology. AI in ITSM operations has pitfalls. AI projects can also fail. So, organizations must assess and reduce these risks. This will ensure a successful AI deployment. Furthermore, organizations may face difficulties in implementing AI in ITSM projects. AI integration in ITSM systems is complex. Organizations must overcome the challenges of AI implementation. Only then can they fully benefit from AI in ITSM.
Integrating AI into IT Service Management (ITSM) poses challenges for organizations. They must navigate them. One major hurdle is ensuring data quality and consistency. AI systems rely on accurate data to provide effective service and insights. Cultural resistance in teams can hinder AI adoption. It shows the need for change management and training to foster acceptance.
Overcoming AI Implementation Challenges
AI in ITSM has challenges. But, organizations can take steps to overcome them. Organizations can integrate AI into their ITSM workflows. To do this, they must: 1. Develop a comprehensive AI strategy. 2. Assess and reduce risks. 3. Ensure effective deployment and training. Also, organizations can use AI tools to streamline ITSM processes and boost efficiency. Investing in the right AI solutions can help organizations. It can overcome the challenges of AI in ITSM and improve business outcomes.
Implementing AI in IT Service Management (ITSM) can be challenging. There may be resistance to change and poor data quality. To overcome these obstacles, organizations must prioritize training. Staff must learn to work effectively with AI systems. Also, a culture that embraces innovation can help. Involving stakeholders in the AI integration process can boost implementation efforts.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AI in ITSM has big challenges. But, organizations can overcome them. They should develop an AI strategy, use AI tools, and manage the complexities of AI adoption in ITSM. By taking proactive steps to address these challenges, organizations can unlock the full potential of AI technology in ITSM and drive enhanced business performance.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing tech world, using AI in ITSM brings many challenges. Organizations face many obstacles in using AI in ITSM. They must navigate integration and deployment issues to reap its benefits.
AI in ITSM Challenges
A key challenge of using AI in ITSM is integrating it with existing ITSM tools and processes. AI needs a lot of data to work well. Integrating it with ITSM systems can be tough. Another challenge organizations face is the difficulty of deploying AI in ITSM environments. Deploying an AI solution can be complex and time-consuming. It involves choosing the right AI and training ITSM teams.
Integrating AI into IT Service Management (ITSM) poses challenges. Organizations must navigate them. A big hurdle is employees' resistance to change. They may fear for their jobs and doubt AI's effectiveness. Also, there are technical obstacles. These include ensuring data quality and integrating AI tools with existing ITSM frameworks. They can complicate deployment efforts.
Obstacles of AI Implementation in ITSM
There are several key obstacles that organizations encounter when implementing AI in ITSM. One major obstacle is the lack of AI adoption in IT service management. Many organizations may be hesitant to embrace AI technology due to concerns about its impact on ITSM processes and workflows. Also, the complexities of AI adoption in ITSM can challenge organizations. Organizations must develop an AI strategy. They must also overcome risks in implementation. Only then can they integrate AI successfully.
Implementing AI in IT Service Management (ITSM) can face many hurdles. Cultural resistance is one. Employees may fear job loss and less personal service.
AI Challenges in IT Service Management
One of the key challenges of AI adoption in ITSM is the potential risks associated with implementing AI technology. AI in ITSM operations has pitfalls. AI projects can also fail. So, organizations must assess and reduce these risks. This will ensure a successful AI deployment. Furthermore, organizations may face difficulties in implementing AI in ITSM projects. AI integration in ITSM systems is complex. Organizations must overcome the challenges of AI implementation. Only then can they fully benefit from AI in ITSM.
Integrating AI into IT Service Management (ITSM) poses challenges for organizations. They must navigate them. One major hurdle is ensuring data quality and consistency. AI systems rely on accurate data to provide effective service and insights. Cultural resistance in teams can hinder AI adoption. It shows the need for change management and training to foster acceptance.
Overcoming AI Implementation Challenges
AI in ITSM has challenges. But, organizations can take steps to overcome them. Organizations can integrate AI into their ITSM workflows. To do this, they must: 1. Develop a comprehensive AI strategy. 2. Assess and reduce risks. 3. Ensure effective deployment and training. Also, organizations can use AI tools to streamline ITSM processes and boost efficiency. Investing in the right AI solutions can help organizations. It can overcome the challenges of AI in ITSM and improve business outcomes.
Implementing AI in IT Service Management (ITSM) can be challenging. There may be resistance to change and poor data quality. To overcome these obstacles, organizations must prioritize training. Staff must learn to work effectively with AI systems. Also, a culture that embraces innovation can help. Involving stakeholders in the AI integration process can boost implementation efforts.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, AI in ITSM has big challenges. But, organizations can overcome them. They should develop an AI strategy, use AI tools, and manage the complexities of AI adoption in ITSM. By taking proactive steps to address these challenges, organizations can unlock the full potential of AI technology in ITSM and drive enhanced business performance.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Exploring Minitab New Methodologies for Proportion Testing
In the world of statistics and data analysis, Minitab has long been a trusted name. Its powerful analytical tools have helped professionals use data to make decisions. New methods for proportion testing have been released. Minitab has again proven its commitment to quality control and process improvement. It provides cutting-edge solutions. Let's dive into the exciting new features of Minitab for proportion testing.
What Are Proportion Testing Methodologies?
Proportion testing methodologies are statistical techniques. They analyze data where the goal is to find the proportion of a sample that meets a specific criterion. These methodologies are particularly useful in quality assurance, process optimization, and decision-making. By examining proportions, professionals can gain insights. They can assess process effectiveness and find areas for improvement. They can then make confident, data-driven decisions.
How Can Minitab’s New Methodologies Benefit You?
Minitab's new proportion testing methods help professionals in all industries. Minitab's latest features aim to improve data analysis. They include better data visualization, analytical tools, and statistical analysis. They should help users find actionable insights. Using these methods in your workflow can improve your work. You can make more accurate calculations and stronger hypotheses. You can also check your results' significance easily.
Minitab's new methods improve statistical analysis. They provide more accurate and reliable estimates. This is especially true in single population proportion testing. It can greatly enhance decision-making. These advancements let users interpret data faster. They can quickly find trends and insights. These methods can boost quality control and efficiency. So, Minitab is vital for data-driven businesses.
New Features and Analytical Tools Minitab's new methods for testing proportions are a key highlight. They offer users a wider range of statistical methods. Minitab has tools for all your analysis needs. They cover confidence intervals, hypothesis testing, decision-making, and data interpretation. If you are researching, analyzing sample sizes, or solving problems, try Minitab's new features. They can help. They provide the flexibility and functionality you need to succeed.
Minitab has added new features and tools. They aim to improve user experience and data analysis. The latest version has new visualization tools and automated reports. It also has better stats functions. They speed up analysis and improve decision-making. These tools help users tackle complex data challenges. They can now gain deeper insights from their analyses.
Practical Applications and Real-world Case Studies
Let's use a real-world example to show Minitab's new proportion testing methods. You are a quality control expert. Your task is to evaluate a new manufacturing process. Use Minitab's statistical software to analyze the data. You can compare proportions and make informed decisions about the process' performance. Minitab has a user-friendly interface and powerful tools. You can analyze ratios, test hypotheses, and create reports to support your findings.
Minitab has proven effective in many industries. It is especially good for quality control and process improvement. Its practical applications have shown this. A manufacturer was studied. It found that Minitab's SPC tools greatly reduced defects and improved product quality. Also, healthcare providers used Minitab to analyze patient data. This improved efficiency and patient outcomes.
Enhancing Your Data-driven Decisions
In today's fast-paced world, data-driven decisions are key to success. Minitab's new proportion testing methods can boost your analysis. They can help you validate hypotheses and find trends in your data. Use Minitab's software to optimize your processes. It will improve efficiency and drive continuous improvement across your organization. Minitab's user-friendly interface and advanced features can help you. They can aid you, whether you're a seasoned statistician or a novice analyst. Use Minitab to achieve your data-driven goals.
In today's data-driven world, businesses must use data to improve decisions. It's key to success. Using tools like Minitab can streamline this. They provide powerful stats and visuals to find trends and make better choices.
Using these insights, organizations can boost efficiency. They can also foster a culture of continuous improvement and innovation.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab's new methods for proportion testing offer many benefits. They will help professionals improve their statistical analysis. Minitab's tools can help you. They can streamline data analysis, validate hypotheses, and boost your decision-making. Minitab's new features can help. They can aid your research, quality testing, or process optimization. They provide the reliability and tools you need. They are vital to succeed in today's data-driven world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the world of statistics and data analysis, Minitab has long been a trusted name. Its powerful analytical tools have helped professionals use data to make decisions. New methods for proportion testing have been released. Minitab has again proven its commitment to quality control and process improvement. It provides cutting-edge solutions. Let's dive into the exciting new features of Minitab for proportion testing.
What Are Proportion Testing Methodologies?
Proportion testing methodologies are statistical techniques. They analyze data where the goal is to find the proportion of a sample that meets a specific criterion. These methodologies are particularly useful in quality assurance, process optimization, and decision-making. By examining proportions, professionals can gain insights. They can assess process effectiveness and find areas for improvement. They can then make confident, data-driven decisions.
How Can Minitab’s New Methodologies Benefit You?
Minitab's new proportion testing methods help professionals in all industries. Minitab's latest features aim to improve data analysis. They include better data visualization, analytical tools, and statistical analysis. They should help users find actionable insights. Using these methods in your workflow can improve your work. You can make more accurate calculations and stronger hypotheses. You can also check your results' significance easily.
Minitab's new methods improve statistical analysis. They provide more accurate and reliable estimates. This is especially true in single population proportion testing. It can greatly enhance decision-making. These advancements let users interpret data faster. They can quickly find trends and insights. These methods can boost quality control and efficiency. So, Minitab is vital for data-driven businesses.
New Features and Analytical Tools Minitab's new methods for testing proportions are a key highlight. They offer users a wider range of statistical methods. Minitab has tools for all your analysis needs. They cover confidence intervals, hypothesis testing, decision-making, and data interpretation. If you are researching, analyzing sample sizes, or solving problems, try Minitab's new features. They can help. They provide the flexibility and functionality you need to succeed.
Minitab has added new features and tools. They aim to improve user experience and data analysis. The latest version has new visualization tools and automated reports. It also has better stats functions. They speed up analysis and improve decision-making. These tools help users tackle complex data challenges. They can now gain deeper insights from their analyses.
Practical Applications and Real-world Case Studies
Let's use a real-world example to show Minitab's new proportion testing methods. You are a quality control expert. Your task is to evaluate a new manufacturing process. Use Minitab's statistical software to analyze the data. You can compare proportions and make informed decisions about the process' performance. Minitab has a user-friendly interface and powerful tools. You can analyze ratios, test hypotheses, and create reports to support your findings.
Minitab has proven effective in many industries. It is especially good for quality control and process improvement. Its practical applications have shown this. A manufacturer was studied. It found that Minitab's SPC tools greatly reduced defects and improved product quality. Also, healthcare providers used Minitab to analyze patient data. This improved efficiency and patient outcomes.
Enhancing Your Data-driven Decisions
In today's fast-paced world, data-driven decisions are key to success. Minitab's new proportion testing methods can boost your analysis. They can help you validate hypotheses and find trends in your data. Use Minitab's software to optimize your processes. It will improve efficiency and drive continuous improvement across your organization. Minitab's user-friendly interface and advanced features can help you. They can aid you, whether you're a seasoned statistician or a novice analyst. Use Minitab to achieve your data-driven goals.
In today's data-driven world, businesses must use data to improve decisions. It's key to success. Using tools like Minitab can streamline this. They provide powerful stats and visuals to find trends and make better choices.
Using these insights, organizations can boost efficiency. They can also foster a culture of continuous improvement and innovation.
How to obtain Minitab certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Minitab's new methods for proportion testing offer many benefits. They will help professionals improve their statistical analysis. Minitab's tools can help you. They can streamline data analysis, validate hypotheses, and boost your decision-making. Minitab's new features can help. They can aid your research, quality testing, or process optimization. They provide the reliability and tools you need. They are vital to succeed in today's data-driven world.
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Master Excel Pivot Tables: Essential Guide to Data Analysis
Excel PivotTables are among the most powerful features of Excel. They let users quickly summarize, analyze, explore, and present data. This guide helps beginners and experienced users unlock PivotTables. It will let them turn raw data into insights with ease. If you track sales, manage projects, or analyze finances, you must master PivotTables. They are essential for any data-driven professional.
Introduction
In today's data-driven world, we must analyze large datasets. It's key for making informed decisions. Excel PivotTables quickly and effectively summarize large datasets. They must no complex formulas or programming skills. PivotTables let users reorganize, filter, and display data. This helps find hidden trends and insights.
This guide will teach you the basics of Excel PivotTables. It will also explore techniques to improve your data analysis. This guide provides all the essential information you need. It goes from creating basic PivotTables to customizing your reports with advanced options. It will help you make the most of Excel's powerful features.
Table Of Contents
- Creating a Basic PivotTable
- Filtering and Sorting Data
- Grouping and Summarizing Data
- Customizing PivotTable Layout and Design
- Advanced PivotTable Features
- Conclusion
Creating a Basic PivotTable
Creating a PivotTable in Excel is easy. But, knowing the basics will help you learn advanced techniques. Here's how to create your first PivotTable:
- Step 1: Prepare Your Data Your data must be well-organized before you create a PivotTable. It should be in a table format. Each column must represent a field, and each row a record. It’s important that your dataset has headings in the first row and no empty rows or columns.
- Step 2: Insert a PivotTable. Select any cell in your dataset. Access the 'Insert' tab within the ribbon at the top of Excel. Click "PivotTable." A dialogue box will appear. It will let you choose where to place the PivotTable: in a new worksheet or the current one.
- Step 3: Build Your PivotTable The PivotTable Field List will appear on the right side of the screen. Drag and drop fields into "Rows," "Columns," "Values," and "Filters" to organize and summarize your data. For example, dragging a “Product” field to “Rows” and a “Sales” field to “Values” will summarize sales by product.
Filtering and Sorting Data
After creating your PivotTable, use Excel's filters and sorts to refine the data.
- Sorting: You can sort the data in ascending or descending order to make it easier to analyze. For example, sort products by total sales, from highest to lowest. This will show you the best-performing product.
- Filtering The filter options allow you to view specific subsets of your data. You can filter data using any of the fields added to the "Filters" area in the PivotTable. This is useful with large datasets. You may want to focus on a specific category, region, or time.
- Slicers are an advanced feature. They provide a visual way to filter data in PivotTables. Click the slicer buttons to filter your PivotTable without delay. This will make your data analysis more interactive and easier to navigate.
Grouping and Summarizing Data
PivotTables let users group data. This makes it easier to find patterns and trends over time.
- You can group numeric data into intervals. For example, summarize sales data by $1,000 increments. Right-click on a numeric field, select “Group,” and specify the interval.
- Grouping Dates Similarly, you can group date fields by days, months, quarters, or years. For example, grouping sales data by month will give a monthly sales summary. It won't need extra columns in your data source.
- PivotTables allow various summarization functions, like Sum, Average, Count, Max, and Min. These functions can analyze the "Values" data to yield deeper insights.
Customizing PivotTable Layout and Design
A strength of PivotTables is their customization. You can adjust the layout and design to fit your reporting needs.
- Changing the Report Layout Excel provides three layout options: Compact, Outline, and Tabular. The Compact layout shows data in a space-efficient way. The Tabular layout is clearer, with each field in a separate column.
- You can add subtotals for each group in your PivotTable. You can also add grand totals at the end of the rows or columns. This is helpful for understanding how individual segments contribute to overall results.
- Applying Conditional Formatting To enhance your PivotTables, you can apply conditional formatting. It will highlight important trends and make the tables more appealing. It lets you format cells automatically based on certain criteria. For example, you can highlight the top 10% of sales or use color scales to show performance trends.
Advanced PivotTable Features
Once you master the basics, use advanced PivotTable features. They can elevate your data analysis.
- PivotTables allow custom calculations using calculated fields and items. For example, you can create a new field that calculates the profit margin based on sales and cost fields.
- Using PivotCharts. They are a graphical representation of PivotTable data. They provide a visual way to analyze trends and patterns. To create a PivotChart, select your PivotTable. Then, pick a chart type from the "Insert" tab. The chart updates automatically when you change the PivotTable. This makes it a dynamic reporting tool.
- Refreshing PivotTables. If your data changes, you can refresh your PivotTable. It will then reflect the updates. This ensures your analysis uses the most current data. It avoids the need to recreate the PivotTable from scratch.
How to obtain MicroSoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Excel PivotTables are a must-have skill for anyone analyzing large datasets. PivotTables are a popular tool. They efficiently organize and summarize data. They are flexible and powerful, too. Both beginners and advanced users love them. By learning the basics of PivotTables, you can quickly analyze your data and present it well. You'll learn to create, filter, group, and customize them.
PivotTables have advanced features. They include calculated fields and PivotCharts. They allow for more complex data analysis. Mastering PivotTables will boost your Excel skills and productivity. They are vital for managing finances, tracking metrics, and analyzing market trends.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Excel PivotTables are among the most powerful features of Excel. They let users quickly summarize, analyze, explore, and present data. This guide helps beginners and experienced users unlock PivotTables. It will let them turn raw data into insights with ease. If you track sales, manage projects, or analyze finances, you must master PivotTables. They are essential for any data-driven professional.
Introduction
In today's data-driven world, we must analyze large datasets. It's key for making informed decisions. Excel PivotTables quickly and effectively summarize large datasets. They must no complex formulas or programming skills. PivotTables let users reorganize, filter, and display data. This helps find hidden trends and insights.
This guide will teach you the basics of Excel PivotTables. It will also explore techniques to improve your data analysis. This guide provides all the essential information you need. It goes from creating basic PivotTables to customizing your reports with advanced options. It will help you make the most of Excel's powerful features.
Table Of Contents
- Creating a Basic PivotTable
- Filtering and Sorting Data
- Grouping and Summarizing Data
- Customizing PivotTable Layout and Design
- Advanced PivotTable Features
- Conclusion
Creating a Basic PivotTable
Creating a PivotTable in Excel is easy. But, knowing the basics will help you learn advanced techniques. Here's how to create your first PivotTable:
- Step 1: Prepare Your Data Your data must be well-organized before you create a PivotTable. It should be in a table format. Each column must represent a field, and each row a record. It’s important that your dataset has headings in the first row and no empty rows or columns.
- Step 2: Insert a PivotTable. Select any cell in your dataset. Access the 'Insert' tab within the ribbon at the top of Excel. Click "PivotTable." A dialogue box will appear. It will let you choose where to place the PivotTable: in a new worksheet or the current one.
- Step 3: Build Your PivotTable The PivotTable Field List will appear on the right side of the screen. Drag and drop fields into "Rows," "Columns," "Values," and "Filters" to organize and summarize your data. For example, dragging a “Product” field to “Rows” and a “Sales” field to “Values” will summarize sales by product.
Filtering and Sorting Data
After creating your PivotTable, use Excel's filters and sorts to refine the data.
- Sorting: You can sort the data in ascending or descending order to make it easier to analyze. For example, sort products by total sales, from highest to lowest. This will show you the best-performing product.
- Filtering The filter options allow you to view specific subsets of your data. You can filter data using any of the fields added to the "Filters" area in the PivotTable. This is useful with large datasets. You may want to focus on a specific category, region, or time.
- Slicers are an advanced feature. They provide a visual way to filter data in PivotTables. Click the slicer buttons to filter your PivotTable without delay. This will make your data analysis more interactive and easier to navigate.
Grouping and Summarizing Data
PivotTables let users group data. This makes it easier to find patterns and trends over time.
- You can group numeric data into intervals. For example, summarize sales data by $1,000 increments. Right-click on a numeric field, select “Group,” and specify the interval.
- Grouping Dates Similarly, you can group date fields by days, months, quarters, or years. For example, grouping sales data by month will give a monthly sales summary. It won't need extra columns in your data source.
- PivotTables allow various summarization functions, like Sum, Average, Count, Max, and Min. These functions can analyze the "Values" data to yield deeper insights.
Customizing PivotTable Layout and Design
A strength of PivotTables is their customization. You can adjust the layout and design to fit your reporting needs.
- Changing the Report Layout Excel provides three layout options: Compact, Outline, and Tabular. The Compact layout shows data in a space-efficient way. The Tabular layout is clearer, with each field in a separate column.
- You can add subtotals for each group in your PivotTable. You can also add grand totals at the end of the rows or columns. This is helpful for understanding how individual segments contribute to overall results.
- Applying Conditional Formatting To enhance your PivotTables, you can apply conditional formatting. It will highlight important trends and make the tables more appealing. It lets you format cells automatically based on certain criteria. For example, you can highlight the top 10% of sales or use color scales to show performance trends.
Advanced PivotTable Features
Once you master the basics, use advanced PivotTable features. They can elevate your data analysis.
- PivotTables allow custom calculations using calculated fields and items. For example, you can create a new field that calculates the profit margin based on sales and cost fields.
- Using PivotCharts. They are a graphical representation of PivotTable data. They provide a visual way to analyze trends and patterns. To create a PivotChart, select your PivotTable. Then, pick a chart type from the "Insert" tab. The chart updates automatically when you change the PivotTable. This makes it a dynamic reporting tool.
- Refreshing PivotTables. If your data changes, you can refresh your PivotTable. It will then reflect the updates. This ensures your analysis uses the most current data. It avoids the need to recreate the PivotTable from scratch.
How to obtain MicroSoft certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Excel PivotTables are a must-have skill for anyone analyzing large datasets. PivotTables are a popular tool. They efficiently organize and summarize data. They are flexible and powerful, too. Both beginners and advanced users love them. By learning the basics of PivotTables, you can quickly analyze your data and present it well. You'll learn to create, filter, group, and customize them.
PivotTables have advanced features. They include calculated fields and PivotCharts. They allow for more complex data analysis. Mastering PivotTables will boost your Excel skills and productivity. They are vital for managing finances, tracking metrics, and analyzing market trends.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
CTFL and the Importance of Testing in DevOps Environments
In today's fast-changing software world, delivering high-quality products is a top priority. It must be done efficiently and consistently. DevOps is a top method. It boosts collaboration between development and operations teams. It aims to automate and streamline processes. This ensures continuous integration and delivery (CI/CD). Testing is key to this workflow. It helps organizations keep their apps secure, high-performing, and reliable. The ISTQB® Certified Tester Foundation Level (CTFL) is a top cert for software testers. It's especially valued in DevOps.
CTFL gives testers a solid base in testing principles and best practices. They can use these in a DevOps framework. It helps teams test quickly in DevOps, while keeping quality. This article will explore three topics. First, the importance of testing in DevOps. Second, the role of CTFL certification in improving testing skills. Third, key sub-topics that define this relationship.
Table Of Contents
- The Role of Testing in DevOps
- CTFL: A Foundation for Effective Testing in DevOps
- Continuous Testing and Automation
- Collaboration and Cross-Functional Teams
- Testing Metrics and Continuous Improvement
- Conclusion
The Role of Testing in DevOps
Testing in DevOps is vital. It ensures software quality while enabling fast deployment. DevOps encourages continuous testing (CT). It means testing early and often in the development process. Automated tests in the CI/CD pipeline let teams catch bugs and performance issues early. It also helps find security vulnerabilities. It reduces the risk of critical failures after deployment. It also promotes a culture of accountability and quality.
DevOps testing differs from traditional methods. It emphasizes automation, collaboration, and continuous feedback. Testers must work closely with developers, product owners, and operations teams. They should align testing with business goals. This team effort speeds up delivery of high-quality software by reducing bottlenecks.
CTFL: A Foundation for Effective Testing in DevOps
The ISTQB®'s Certified Tester Foundation Level (CTFL) certification is well-known. It is a basic certification for new software testers. The curriculum covers core concepts. They are testing fundamentals, test design techniques, and test management principles. All are very relevant in a DevOps environment.
In DevOps, CTFL-certified testers are vital. They ensure testing is a key part of the development process, not an afterthought. CTFL provides testers with the knowledge and skills to:
- Know the value of early testing in the DevOps lifecycle.
- Apply structured testing techniques to ensure coverage and effectiveness.
- Use automated testing tools effectively to support continuous testing.
- Work in cross-functional teams and collaborate with developers to improve testability and efficiency.
A CTFL certification shows competence and a commitment to quality. It's valuable for testers in a fast-paced DevOps environment.
Continuous Testing and Automation
Automation is a cornerstone of DevOps, and testing is no exception. Automated, continuous testing checks code changes as soon as they are made. This reduces the time between development and deployment. Test automation uses scripts, tools, and frameworks. They run tests and check results, without manual work.
CTFL-certified testers can choose and use the right tools for automation. This includes unit, integration, and performance tests. The certification also stresses test design techniques. They ensure maximum coverage and efficiency when automating tests. In a DevOps setting, automation is crucial. It maintains the speed and agility of the development cycle. CTFL testers help by designing effective automated tests. These tests catch defects early and prevent costly rework later.
Key benefits of continuous testing and automation include:
- Faster feedback loops, enabling quicker resolution of defects.
- It reduced manual work. Testers could then focus on exploratory testing.
- Improved test coverage and consistency, leading to higher-quality releases.
Collaboration and Cross-Functional Teams
DevOps thrives on collaboration and breaking down the silos between traditionally isolated teams. In this context, a separate QA department can no longer test alone. Instead, it is in every phase of the development cycle. Developers, operations, and testers work together to ensure quality.
CTFL-certified testers have a structured approach to testing. It helps streamline collaboration in cross-functional teams. Their knowledge of test management helps coordinate testing across development stages. They can also communicate well with non-testers, like developers and business analysts. This ensures quality standards are met without slowing down.
In DevOps, the role of testers expands beyond executing test cases. They often contribute to writing automated tests and defining acceptance criteria. They also work with developers to improve the code's testability. CTFL certification gives testers the skills to work well in this team environment.
Testing Metrics and Continuous Improvement
A core principle of DevOps is continuous improvement. Testing is a key area where metrics can drive better outcomes. Metrics like defect density, test coverage, and MTTR show how effective testing is.
CTFL-certified testers know how to use these metrics to optimize testing. Teams can find bottlenecks and redundant tests by analyzing testing metrics. They can also find areas for improvement. In a DevOps environment, the goal is to release high-quality software quickly. So, continuous improvement is essential. Testers are key to this. They must ensure that test strategies evolve as the product and process mature.
Using metrics for continuous improvement helps:
- Optimize testing cycles for faster releases.
- Improve test case quality and relevance.
- Ensure that testing efforts align with business objectives and user needs.
How to obtain CTFL certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In the fast-paced DevOps world, testing is critical. It ensures software is reliable, secure, and performs well in the real world. The ISTQB® Certified Tester Foundation Level (CTFL) certifies testers in DevOps. It gives them the skills to excel in a world that is collaborative, automated, and metric-driven.
CTFL-certified testers can help DevOps succeed. They know testing principles, continuous testing, automation, collaboration, and improvement. They embed quality in the software development lifecycle. This lets organizations deliver better products faster and more efficiently.
Testing is not just a step in the process. It is an ongoing activity that ensures software reliability and performance. So, it is essential to any successful DevOps strategy.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing software world, delivering high-quality products is a top priority. It must be done efficiently and consistently. DevOps is a top method. It boosts collaboration between development and operations teams. It aims to automate and streamline processes. This ensures continuous integration and delivery (CI/CD). Testing is key to this workflow. It helps organizations keep their apps secure, high-performing, and reliable. The ISTQB® Certified Tester Foundation Level (CTFL) is a top cert for software testers. It's especially valued in DevOps.
CTFL gives testers a solid base in testing principles and best practices. They can use these in a DevOps framework. It helps teams test quickly in DevOps, while keeping quality. This article will explore three topics. First, the importance of testing in DevOps. Second, the role of CTFL certification in improving testing skills. Third, key sub-topics that define this relationship.
Table Of Contents
- The Role of Testing in DevOps
- CTFL: A Foundation for Effective Testing in DevOps
- Continuous Testing and Automation
- Collaboration and Cross-Functional Teams
- Testing Metrics and Continuous Improvement
- Conclusion
The Role of Testing in DevOps
Testing in DevOps is vital. It ensures software quality while enabling fast deployment. DevOps encourages continuous testing (CT). It means testing early and often in the development process. Automated tests in the CI/CD pipeline let teams catch bugs and performance issues early. It also helps find security vulnerabilities. It reduces the risk of critical failures after deployment. It also promotes a culture of accountability and quality.
DevOps testing differs from traditional methods. It emphasizes automation, collaboration, and continuous feedback. Testers must work closely with developers, product owners, and operations teams. They should align testing with business goals. This team effort speeds up delivery of high-quality software by reducing bottlenecks.
CTFL: A Foundation for Effective Testing in DevOps
The ISTQB®'s Certified Tester Foundation Level (CTFL) certification is well-known. It is a basic certification for new software testers. The curriculum covers core concepts. They are testing fundamentals, test design techniques, and test management principles. All are very relevant in a DevOps environment.
In DevOps, CTFL-certified testers are vital. They ensure testing is a key part of the development process, not an afterthought. CTFL provides testers with the knowledge and skills to:
- Know the value of early testing in the DevOps lifecycle.
- Apply structured testing techniques to ensure coverage and effectiveness.
- Use automated testing tools effectively to support continuous testing.
- Work in cross-functional teams and collaborate with developers to improve testability and efficiency.
A CTFL certification shows competence and a commitment to quality. It's valuable for testers in a fast-paced DevOps environment.
Continuous Testing and Automation
Automation is a cornerstone of DevOps, and testing is no exception. Automated, continuous testing checks code changes as soon as they are made. This reduces the time between development and deployment. Test automation uses scripts, tools, and frameworks. They run tests and check results, without manual work.
CTFL-certified testers can choose and use the right tools for automation. This includes unit, integration, and performance tests. The certification also stresses test design techniques. They ensure maximum coverage and efficiency when automating tests. In a DevOps setting, automation is crucial. It maintains the speed and agility of the development cycle. CTFL testers help by designing effective automated tests. These tests catch defects early and prevent costly rework later.
Key benefits of continuous testing and automation include:
- Faster feedback loops, enabling quicker resolution of defects.
- It reduced manual work. Testers could then focus on exploratory testing.
- Improved test coverage and consistency, leading to higher-quality releases.
Collaboration and Cross-Functional Teams
DevOps thrives on collaboration and breaking down the silos between traditionally isolated teams. In this context, a separate QA department can no longer test alone. Instead, it is in every phase of the development cycle. Developers, operations, and testers work together to ensure quality.
CTFL-certified testers have a structured approach to testing. It helps streamline collaboration in cross-functional teams. Their knowledge of test management helps coordinate testing across development stages. They can also communicate well with non-testers, like developers and business analysts. This ensures quality standards are met without slowing down.
In DevOps, the role of testers expands beyond executing test cases. They often contribute to writing automated tests and defining acceptance criteria. They also work with developers to improve the code's testability. CTFL certification gives testers the skills to work well in this team environment.
Testing Metrics and Continuous Improvement
A core principle of DevOps is continuous improvement. Testing is a key area where metrics can drive better outcomes. Metrics like defect density, test coverage, and MTTR show how effective testing is.
CTFL-certified testers know how to use these metrics to optimize testing. Teams can find bottlenecks and redundant tests by analyzing testing metrics. They can also find areas for improvement. In a DevOps environment, the goal is to release high-quality software quickly. So, continuous improvement is essential. Testers are key to this. They must ensure that test strategies evolve as the product and process mature.
Using metrics for continuous improvement helps:
- Optimize testing cycles for faster releases.
- Improve test case quality and relevance.
- Ensure that testing efforts align with business objectives and user needs.
How to obtain CTFL certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In the fast-paced DevOps world, testing is critical. It ensures software is reliable, secure, and performs well in the real world. The ISTQB® Certified Tester Foundation Level (CTFL) certifies testers in DevOps. It gives them the skills to excel in a world that is collaborative, automated, and metric-driven.
CTFL-certified testers can help DevOps succeed. They know testing principles, continuous testing, automation, collaboration, and improvement. They embed quality in the software development lifecycle. This lets organizations deliver better products faster and more efficiently.
Testing is not just a step in the process. It is an ongoing activity that ensures software reliability and performance. So, it is essential to any successful DevOps strategy.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Creating a High Availability Environment with XenServer
High availability (HA) environments are vital for businesses. They need constant access to their apps and services. Downtime can cause big financial losses, unhappy customers, and a damaged reputation. XenServer, a Citrix virtualization platform, is powerful. It has features to create a high availability environment. This guide will discuss key concepts for a high-availability solution using XenServer. It will also cover the steps to install it. It will focus on five topics: 1. Understanding high availability. 2. Configuring XenServer for HA. 3. Storage options. 4. Monitoring and management. 5. Troubleshooting HA issues.
Table Of Contents
- Understanding High Availability
- Configuring XenServer for High Availability
- Leveraging Storage Options
- Monitoring and Management
- Troubleshooting HA Issues
- Conclusion
Understanding High Availability
High availability means designing systems to reduce downtime and ensure continuous operation. In an HA environment, we duplicate resources. We then distribute them across many servers. This redundancy lets apps keep working if some components fail.
Key Components of HA:
- Redundancy: Critical components have backups. In the event of a failure, another can effortlessly take charge to prevent any disruptions.
- Failover: This mechanism switches operations from a failed component to a standby one.
- Load Balancing: It spreads workloads across servers. This boosts performance and prevents bottlenecks.
By understanding these principles, organizations can design their systems. They can then achieve the desired availability.
Configuring XenServer for High Availability
Configuring XenServer for high availability involves several steps. This section outlines the essential tasks to set up a reliable HA environment:
- Install the XenServer software on all physical servers for the HA cluster. Ensure all servers have compatible hardware and networking configurations.
- Creating a pool: Group the XenServer hosts into a pool. A pool lets many XenServer hosts share resources, including storage and VMs. Use the XenCenter management tool to create and manage your pool.
- Enable High Availability: After creating the pool, enable the HA feature in XenServer. This process involves selecting the hosts for HA. Then, configure the HA settings to define the failover behavior.
- Resource Configuration: Configure the VMs and associated storage to ensure they are HA-aware. This config includes setting the VM parameters. This allows them to restart on another host if their primary host fails.
Leveraging Storage Options
The choice of storage can significantly impact the effectiveness of an HA environment. XenServer supports various storage types, each with unique advantages for high availability:
- Shared storage, like a SAN or NAS, lets many XenServer hosts access the same storage. This setup is vital for live migration. It ensures that VMs can quickly switch to a standby host during a failover.
- Storage Replication: Use replication to keep data consistent across storage systems. This redundancy helps protect against data loss in the event of hardware failure.
- Storage Configuration Best Practices: Regularly monitor storage performance and health. This can help you fix issues before they arise. Additionally, ensure that backup strategies are in place to safeguard against data loss.
Monitoring and Management
Effective monitoring and management are crucial to maintaining a high-availability environment. XenServer offers several tools and features for this purpose:
- XenCenter Management Tool: XenCenter is a GUI for managing XenServer pools. It monitors resource use, VM performance, and HA status. Check the status of all hosts in the pool at regular intervals. This ensures that they are functioning correctly.
- Alerts and Notifications: Set up alerts to notify admins of critical events. These include host failures, VM migrations, and resource limits. This proactive approach allows for rapid response and minimizes downtime.
- Performance Monitoring: Use built-in performance metrics to check CPU, memory, and storage usage. Analyzing these metrics helps identify potential bottlenecks and informs scaling decisions.
Troubleshooting HA Issues
- Despite the best configurations, issues can still arise in a high-availability environment. Proper troubleshooting is crucial for sustaining operational continuity.
- Common HA issues include host failures, network disruptions, and storage access problems. Understanding these potential pitfalls allows for quicker diagnostics and resolution.
- Logs and Diagnostics: Use XenServer logs to investigate issues. Logs can provide valuable insights into what went wrong and guide troubleshooting efforts.
- Testing Failover Procedures: Regularly test your failover procedures to ensure they work. Simulating a host failure can find weaknesses in your HA setup. It can also prepare your team for real-world scenarios.
How to obtain Xen Server certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Creating a high-availability environment with XenServer is a complex task. It requires careful planning, configuration, and ongoing management. Organizations can keep critical apps running despite failures. They can do this by learning about high availability and configuring XenServer. They must use the right storage and check it well. High availability boosts business resilience and builds customer trust. So, it is vital for modern IT infrastructure. These best practices will help organizations in a connected world. There, uptime is vital.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
High availability (HA) environments are vital for businesses. They need constant access to their apps and services. Downtime can cause big financial losses, unhappy customers, and a damaged reputation. XenServer, a Citrix virtualization platform, is powerful. It has features to create a high availability environment. This guide will discuss key concepts for a high-availability solution using XenServer. It will also cover the steps to install it. It will focus on five topics: 1. Understanding high availability. 2. Configuring XenServer for HA. 3. Storage options. 4. Monitoring and management. 5. Troubleshooting HA issues.
Table Of Contents
- Understanding High Availability
- Configuring XenServer for High Availability
- Leveraging Storage Options
- Monitoring and Management
- Troubleshooting HA Issues
- Conclusion
Understanding High Availability
High availability means designing systems to reduce downtime and ensure continuous operation. In an HA environment, we duplicate resources. We then distribute them across many servers. This redundancy lets apps keep working if some components fail.
Key Components of HA:
- Redundancy: Critical components have backups. In the event of a failure, another can effortlessly take charge to prevent any disruptions.
- Failover: This mechanism switches operations from a failed component to a standby one.
- Load Balancing: It spreads workloads across servers. This boosts performance and prevents bottlenecks.
By understanding these principles, organizations can design their systems. They can then achieve the desired availability.
Configuring XenServer for High Availability
Configuring XenServer for high availability involves several steps. This section outlines the essential tasks to set up a reliable HA environment:
- Install the XenServer software on all physical servers for the HA cluster. Ensure all servers have compatible hardware and networking configurations.
- Creating a pool: Group the XenServer hosts into a pool. A pool lets many XenServer hosts share resources, including storage and VMs. Use the XenCenter management tool to create and manage your pool.
- Enable High Availability: After creating the pool, enable the HA feature in XenServer. This process involves selecting the hosts for HA. Then, configure the HA settings to define the failover behavior.
- Resource Configuration: Configure the VMs and associated storage to ensure they are HA-aware. This config includes setting the VM parameters. This allows them to restart on another host if their primary host fails.
Leveraging Storage Options
The choice of storage can significantly impact the effectiveness of an HA environment. XenServer supports various storage types, each with unique advantages for high availability:
- Shared storage, like a SAN or NAS, lets many XenServer hosts access the same storage. This setup is vital for live migration. It ensures that VMs can quickly switch to a standby host during a failover.
- Storage Replication: Use replication to keep data consistent across storage systems. This redundancy helps protect against data loss in the event of hardware failure.
- Storage Configuration Best Practices: Regularly monitor storage performance and health. This can help you fix issues before they arise. Additionally, ensure that backup strategies are in place to safeguard against data loss.
Monitoring and Management
Effective monitoring and management are crucial to maintaining a high-availability environment. XenServer offers several tools and features for this purpose:
- XenCenter Management Tool: XenCenter is a GUI for managing XenServer pools. It monitors resource use, VM performance, and HA status. Check the status of all hosts in the pool at regular intervals. This ensures that they are functioning correctly.
- Alerts and Notifications: Set up alerts to notify admins of critical events. These include host failures, VM migrations, and resource limits. This proactive approach allows for rapid response and minimizes downtime.
- Performance Monitoring: Use built-in performance metrics to check CPU, memory, and storage usage. Analyzing these metrics helps identify potential bottlenecks and informs scaling decisions.
Troubleshooting HA Issues
- Despite the best configurations, issues can still arise in a high-availability environment. Proper troubleshooting is crucial for sustaining operational continuity.
- Common HA issues include host failures, network disruptions, and storage access problems. Understanding these potential pitfalls allows for quicker diagnostics and resolution.
- Logs and Diagnostics: Use XenServer logs to investigate issues. Logs can provide valuable insights into what went wrong and guide troubleshooting efforts.
- Testing Failover Procedures: Regularly test your failover procedures to ensure they work. Simulating a host failure can find weaknesses in your HA setup. It can also prepare your team for real-world scenarios.
How to obtain Xen Server certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Creating a high-availability environment with XenServer is a complex task. It requires careful planning, configuration, and ongoing management. Organizations can keep critical apps running despite failures. They can do this by learning about high availability and configuring XenServer. They must use the right storage and check it well. High availability boosts business resilience and builds customer trust. So, it is vital for modern IT infrastructure. These best practices will help organizations in a connected world. There, uptime is vital.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Categories and Instruments for Effective Data Gathering
Data gathering is a critical process in research, business, and decision-making. It involves collecting information relevant to a specific goal. The data's quality affects the results and their reliability. Thus, researchers and professionals must know the data-gathering methods and tools. This article will explore the categories of data and data collection tools. It will show their uses in various contexts. The goal is to provide insights for effective data gathering to inform decisions.
Table Of Contents
- Categories of Data
- Data Collection Instruments
- Sampling Techniques
- Ethical Considerations in Data Gathering
- Applications of Data Gathering in Various Fields
- Conclusion
Categories of Data
Data has several types. Each serves a different purpose and needs a specific collection method. The two primary categories of data are qualitative data and quantitative data.
- Qualitative Data: This type of data is descriptive and conceptual. It often includes non-numerical information, such as opinions, feelings, and experiences. Qualitative data is usually collected through interviews, focus groups, and open-ended surveys. It adds context to research. It helps researchers grasp the nuances of human behavior and perceptions.
- Quantitative Data: In contrast, quantitative data is numerical. Researchers can conduct statistical measurements and analyses of it. This data comes from structured methods, like surveys, experiments, and observations. It uses closed-ended questions. Quantitative data is vital. It helps to find patterns, predict outcomes, and establish relationships between variables.
- Both data types are vital for research. The choice of which to use depends on the research questions and goals.
Data Collection Instruments
Several instruments can collect data. Each suits specific research types and data categories. Knowing these instruments helps researchers choose the best tools for their studies.
- Surveys are a common data collection tool in quantitative research. Administrators can use various formats to administer them. These include online, paper, or phone surveys. Questionnaires are a series of questions. They gather specific information from respondents. They can have both closed and open-ended questions. This allows for a mix of quantitative and qualitative data.
- Interviews are a way to collect qualitative data. They involve direct interaction between an interviewer and a participant. You can make them set questions, semi-structured, or unstructured. Interviews let researchers explore complex topics and gather rich, detailed data from participants.
- Focus Groups: A facilitator guides a small group in discussing a topic. This method is good for exploring group opinions and attitudes. Focus groups can reveal insights that individual interviews might miss. Participants can build on each other's responses.
- Observations: Observational methods involve watching and recording behaviors in their natural setting. You can do this either as a participant observer or a nonparticipant observer.
- Observational data can be quantitative or qualitative. Quantitative data count occurrences of behaviors. Qualitative data describe behaviors and interactions.
- This method is particularly valuable in fields like anthropology, sociology, and education.
- Experiments: Experimental methods manipulate one or more variables. They then observe the effect on another variable. This method is a standard practice in scientific research for establishing cause-and-effect relationships. Researchers can conduct experiments in labs or in the field. It depends on the research goals.
Sampling Techniques
After selecting the data collection tools, researchers must choose their participants. Sampling techniques are crucial. They ensure the collected data represents the larger population.
- Random Sampling: This technique selects participants in a random manner. It gives each member of the population an equal chance to be chosen. Random sampling reduces bias. It allows us to generalize findings to the broader population.
- Stratified Sampling: This method splits the population into subgroups (strata) based on traits, like age or gender. We select participants from each stratum without a specific pattern. This ensures that the sample reflects the population's diversity.
- Convenience Sampling: This non-probability method picks participants for their availability and willingness to help. While convenient, this method can introduce bias, limiting the generalizability of the findings.
- Snowball Sampling: This technique is useful in research involving hard-to-reach populations. Existing study participants refer potential participants, creating a "snowball" effect. This method is good for exploring sensitive topics. But, it can bias samples due to its reliance on social networks.
Ethical Considerations in Data Gathering
Ethics is key in data gathering, especially with human subjects. Researchers must ensure their data collection methods are ethical and respect participants' rights. Key ethical considerations include:
- Informed Consent: Participants must know the study's nature, purpose, and data use. They should give their consent to take part without any coercion.
- Confidentiality and Anonymity: Researchers must keep participants' data confidential and anonymous. This protects their identity and privacy. This is particularly important when dealing with sensitive information.
- Avoiding Harm: Researchers must cut any harm or discomfort to participants. This includes any psychological, emotional, or physical harm from study participation.
- Integrity of Data: Researchers must be honest in data collection. They must not manipulate or falsify data. Accurate reporting of findings is essential for ethical research practices.
Applications of Data Gathering in Various Fields
Data gathering is vital in many fields. Each has unique uses.
- Healthcare: In healthcare research, data gathering helps find patient needs and treatment outcomes. It also assesses intervention effectiveness. Surveys, interviews, and clinical trials are standard methods for collecting data.
- Market Research: Businesses gather data to know consumer preferences, market trends, and competitors. Surveys, focus groups, and observational studies are instrumental in informing marketing strategies.
- Education: In educational research, data gathering helps to test teaching. It assesses methods, student performance, and learning outcomes. Observations, surveys, and interviews with educators and students provide valuable insights.
- Social Sciences: Researchers in sociology, psychology, and anthropology study humans. They focus on behavior and social interactions. They explore cultural phenomena. They use various methods to collect data.
- Environmental Studies: It is research on ecosystems, climate change, and resource management. It involves collecting data. We use studies, surveys, and experiments to gather key information for environmental conservation.
How to obtain Developement certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Data gathering is a key process. It supports research and decision-making in many fields. It's vital to know the data types and the collection tools. This is key to getting reliable and valid information. Using the right data collection methods, researchers can gain insights. These insights can inform their work and advance knowledge. Also, rank ethics to protect participants and the research's integrity. The right tools can make data gathering very beneficial. It can help research, business, and education.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Data gathering is a critical process in research, business, and decision-making. It involves collecting information relevant to a specific goal. The data's quality affects the results and their reliability. Thus, researchers and professionals must know the data-gathering methods and tools. This article will explore the categories of data and data collection tools. It will show their uses in various contexts. The goal is to provide insights for effective data gathering to inform decisions.
Table Of Contents
- Categories of Data
- Data Collection Instruments
- Sampling Techniques
- Ethical Considerations in Data Gathering
- Applications of Data Gathering in Various Fields
- Conclusion
Categories of Data
Data has several types. Each serves a different purpose and needs a specific collection method. The two primary categories of data are qualitative data and quantitative data.
- Qualitative Data: This type of data is descriptive and conceptual. It often includes non-numerical information, such as opinions, feelings, and experiences. Qualitative data is usually collected through interviews, focus groups, and open-ended surveys. It adds context to research. It helps researchers grasp the nuances of human behavior and perceptions.
- Quantitative Data: In contrast, quantitative data is numerical. Researchers can conduct statistical measurements and analyses of it. This data comes from structured methods, like surveys, experiments, and observations. It uses closed-ended questions. Quantitative data is vital. It helps to find patterns, predict outcomes, and establish relationships between variables.
- Both data types are vital for research. The choice of which to use depends on the research questions and goals.
Data Collection Instruments
Several instruments can collect data. Each suits specific research types and data categories. Knowing these instruments helps researchers choose the best tools for their studies.
- Surveys are a common data collection tool in quantitative research. Administrators can use various formats to administer them. These include online, paper, or phone surveys. Questionnaires are a series of questions. They gather specific information from respondents. They can have both closed and open-ended questions. This allows for a mix of quantitative and qualitative data.
- Interviews are a way to collect qualitative data. They involve direct interaction between an interviewer and a participant. You can make them set questions, semi-structured, or unstructured. Interviews let researchers explore complex topics and gather rich, detailed data from participants.
- Focus Groups: A facilitator guides a small group in discussing a topic. This method is good for exploring group opinions and attitudes. Focus groups can reveal insights that individual interviews might miss. Participants can build on each other's responses.
- Observations: Observational methods involve watching and recording behaviors in their natural setting. You can do this either as a participant observer or a nonparticipant observer.
- Observational data can be quantitative or qualitative. Quantitative data count occurrences of behaviors. Qualitative data describe behaviors and interactions.
- This method is particularly valuable in fields like anthropology, sociology, and education.
- Experiments: Experimental methods manipulate one or more variables. They then observe the effect on another variable. This method is a standard practice in scientific research for establishing cause-and-effect relationships. Researchers can conduct experiments in labs or in the field. It depends on the research goals.
Sampling Techniques
After selecting the data collection tools, researchers must choose their participants. Sampling techniques are crucial. They ensure the collected data represents the larger population.
- Random Sampling: This technique selects participants in a random manner. It gives each member of the population an equal chance to be chosen. Random sampling reduces bias. It allows us to generalize findings to the broader population.
- Stratified Sampling: This method splits the population into subgroups (strata) based on traits, like age or gender. We select participants from each stratum without a specific pattern. This ensures that the sample reflects the population's diversity.
- Convenience Sampling: This non-probability method picks participants for their availability and willingness to help. While convenient, this method can introduce bias, limiting the generalizability of the findings.
- Snowball Sampling: This technique is useful in research involving hard-to-reach populations. Existing study participants refer potential participants, creating a "snowball" effect. This method is good for exploring sensitive topics. But, it can bias samples due to its reliance on social networks.
Ethical Considerations in Data Gathering
Ethics is key in data gathering, especially with human subjects. Researchers must ensure their data collection methods are ethical and respect participants' rights. Key ethical considerations include:
- Informed Consent: Participants must know the study's nature, purpose, and data use. They should give their consent to take part without any coercion.
- Confidentiality and Anonymity: Researchers must keep participants' data confidential and anonymous. This protects their identity and privacy. This is particularly important when dealing with sensitive information.
- Avoiding Harm: Researchers must cut any harm or discomfort to participants. This includes any psychological, emotional, or physical harm from study participation.
- Integrity of Data: Researchers must be honest in data collection. They must not manipulate or falsify data. Accurate reporting of findings is essential for ethical research practices.
Applications of Data Gathering in Various Fields
Data gathering is vital in many fields. Each has unique uses.
- Healthcare: In healthcare research, data gathering helps find patient needs and treatment outcomes. It also assesses intervention effectiveness. Surveys, interviews, and clinical trials are standard methods for collecting data.
- Market Research: Businesses gather data to know consumer preferences, market trends, and competitors. Surveys, focus groups, and observational studies are instrumental in informing marketing strategies.
- Education: In educational research, data gathering helps to test teaching. It assesses methods, student performance, and learning outcomes. Observations, surveys, and interviews with educators and students provide valuable insights.
- Social Sciences: Researchers in sociology, psychology, and anthropology study humans. They focus on behavior and social interactions. They explore cultural phenomena. They use various methods to collect data.
- Environmental Studies: It is research on ecosystems, climate change, and resource management. It involves collecting data. We use studies, surveys, and experiments to gather key information for environmental conservation.
How to obtain Developement certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Data gathering is a key process. It supports research and decision-making in many fields. It's vital to know the data types and the collection tools. This is key to getting reliable and valid information. Using the right data collection methods, researchers can gain insights. These insights can inform their work and advance knowledge. Also, rank ethics to protect participants and the research's integrity. The right tools can make data gathering very beneficial. It can help research, business, and education.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Enhancing Application Delivery with Citrix Innovations!
Looking for ways to improve efficiency and streamline your application delivery process? Citrix has you covered. Its tech and solutions are revolutionizing app delivery to end-users. This article will explore the latest Citrix app delivery innovations. They can benefit your business.
Citrix Application Delivery Solutions
Citrix offers software and cloud solutions. They optimize app delivery and boost user experience. Citrix has everything you need for fast, secure app delivery. It covers virtualization, networking, workspaces, and deployment.
Citrix Application Delivery Solutions make app and service delivery faster. They ensure high performance and seamless access for users, no matter their location or device. These solutions use virtualization and cloud computing. They help organizations reduce complexity and improve the user experience. They also maintain strong security. Citrix empowers admins to optimize resources and quickly adapt to changes. It has centralized management and integrated analytics.
Efficient Application Delivery with Citrix
A key advantage of Citrix technology is its ability to deliver apps efficiently, no matter the end-user's device or location. Citrix's cloud and virtualization solutions help organizations. They can speed up app deployment and ensure top performance.
Citrix must deliver apps efficiently. It will boost user experience and cut costs. By using Citrix ADC and centralized management, organizations can improve their app delivery. This will make apps accessible, reliable, and secure in all environments. Also, automation features let Citrix admins simplify tasks. This boosts performance and cuts downtime.
Citrix Networking Innovations
Citrix is evolving its networking products to match the latest app delivery trends. Citrix networking solutions meet modern businesses' demands. They ensure seamless app delivery. They are optimized, reliable, scalable, and secure.
Citrix is a leader in networking innovations. Its advanced solutions, like Citrix ADC and Citrix Web App Firewall, boost app performance and security. These tools speed up app delivery in multi-cloud environments. They also have strong security features to protect against modern threats. Citrix is using automation and analytics to empower admins. They can now optimize network performance and reduce complexity. This ensures a seamless user experience.
Application Delivery Best Practices
Citrix is a pioneer in app delivery. It has best practices to optimize performance and ensure reliability. Citrix focuses on automation, orchestration, and integration. It offers a complete approach to app delivery that maximizes efficiency and minimizes downtime.
To deliver apps efficiently, organizations must build a fast, scalable, and always-on infrastructure. It must support a seamless user experience during peak loads. Using automated tools and analytics can improve monitoring. This lets admins quickly find and fix performance issues. Also, we must use security measures. These include end-to-end encryption and continuous compliance monitoring. They are essential to protect sensitive data and maintain user trust.
How to obtain Citrix Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix leads in app delivery innovation. It offers many solutions to meet modern business needs. Citrix can help you improve performance, enhance security, or streamline deployment. They have the tools and expertise to achieve your goals. With Citrix, you can take your application delivery to the next level and stay ahead of the competition.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Looking for ways to improve efficiency and streamline your application delivery process? Citrix has you covered. Its tech and solutions are revolutionizing app delivery to end-users. This article will explore the latest Citrix app delivery innovations. They can benefit your business.
Citrix Application Delivery Solutions
Citrix offers software and cloud solutions. They optimize app delivery and boost user experience. Citrix has everything you need for fast, secure app delivery. It covers virtualization, networking, workspaces, and deployment.
Citrix Application Delivery Solutions make app and service delivery faster. They ensure high performance and seamless access for users, no matter their location or device. These solutions use virtualization and cloud computing. They help organizations reduce complexity and improve the user experience. They also maintain strong security. Citrix empowers admins to optimize resources and quickly adapt to changes. It has centralized management and integrated analytics.
Efficient Application Delivery with Citrix
A key advantage of Citrix technology is its ability to deliver apps efficiently, no matter the end-user's device or location. Citrix's cloud and virtualization solutions help organizations. They can speed up app deployment and ensure top performance.
Citrix must deliver apps efficiently. It will boost user experience and cut costs. By using Citrix ADC and centralized management, organizations can improve their app delivery. This will make apps accessible, reliable, and secure in all environments. Also, automation features let Citrix admins simplify tasks. This boosts performance and cuts downtime.
Citrix Networking Innovations
Citrix is evolving its networking products to match the latest app delivery trends. Citrix networking solutions meet modern businesses' demands. They ensure seamless app delivery. They are optimized, reliable, scalable, and secure.
Citrix is a leader in networking innovations. Its advanced solutions, like Citrix ADC and Citrix Web App Firewall, boost app performance and security. These tools speed up app delivery in multi-cloud environments. They also have strong security features to protect against modern threats. Citrix is using automation and analytics to empower admins. They can now optimize network performance and reduce complexity. This ensures a seamless user experience.
Application Delivery Best Practices
Citrix is a pioneer in app delivery. It has best practices to optimize performance and ensure reliability. Citrix focuses on automation, orchestration, and integration. It offers a complete approach to app delivery that maximizes efficiency and minimizes downtime.
To deliver apps efficiently, organizations must build a fast, scalable, and always-on infrastructure. It must support a seamless user experience during peak loads. Using automated tools and analytics can improve monitoring. This lets admins quickly find and fix performance issues. Also, we must use security measures. These include end-to-end encryption and continuous compliance monitoring. They are essential to protect sensitive data and maintain user trust.
How to obtain Citrix Administrator certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Citrix leads in app delivery innovation. It offers many solutions to meet modern business needs. Citrix can help you improve performance, enhance security, or streamline deployment. They have the tools and expertise to achieve your goals. With Citrix, you can take your application delivery to the next level and stay ahead of the competition.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Enhance Security with Cisco SASE(Secure Access Service Edge)
In today's digital world, remote work and cloud apps are the norm. So, traditional network security is no longer enough for modern businesses. This is where SASE technology comes in. It offers a complete way to secure and connect networks. Cisco leads in SASE implementation. Its innovative solutions set new industry standards.
What is SASE and Why is it Important?
SASE is a concept. It combines network security with wide-area networking (WAN). It provides a unified, cloud-native solution. SASE combines networking and security into a single, cloud-based service. It simplifies management, cuts costs, and improves the user experience. With the rise of remote work and cloud apps, SASE has become vital. It helps organizations secure their digital infrastructure.
SASE (Secure Access Service Edge) is a cloud-native design. It combines networking and security services into a single framework. It gives secure access to users, devices, and apps from anywhere. It combines SD-WAN, secure web gateways, and zero trust. It's essential for businesses shifting to remote work and cloud environments. SASE boosts efficiency by merging security and networking into one platform. It simplifies tasks and protects against modern cyber threats.
SASE (Secure Access Service Edge) is a security-focused method. It combines wide area networking (WAN) with cloud-delivered security services. It streamlines network management and security. It combines firewalls, VPNs, and DLP into a single, scalable solution. SASE is crucial for organizations embracing cloud and remote work. It provides simple operations, strong security, and app access from anywhere.
Cisco's SASE Solutions: Leading the Way in Network Security
Cisco has SASE solutions for the security needs of modern businesses. They are comprehensive and designed to adapt to changing threats. Cisco's SASE architecture offers a complete solution for network security and connectivity. It includes secure access to cloud services and advanced threat detection. Cisco's SASE platform provides better security, faster performance, and easy scalability.
Cisco's SASE solutions are changing how businesses secure their networks. They combine strong security and networking features into a single, cloud-native platform. Cisco's SASE architecture combines SD-WAN, firewall-as-a-service, and zero trust access. It ensures secure, seamless connectivity for remote users and cloud apps. As firms move to hybrid and multi-cloud setups, Cisco's SASE framework is best for secure, scalable, and flexible networks.
Cisco's SASE solutions address the complexities of modern network security. They offer strong protection without sacrificing performance. With advanced threat intelligence and real-time monitoring, Cisco protects users. They can securely access critical apps from anywhere, reducing cyber risks. As businesses embrace digital transformation, Cisco's SASE offerings help. They simplify security while enhancing visibility and control over networks.
The Benefits of Implementing Cisco's SASE Solutions
Cisco's SASE (Secure Access Service Edge) solutions give firms a unified security system. It boosts performance and security across all network edges. SASE combines network security with WAN. It ensures secure, seamless access to apps, no matter the location. This simplifies management and cuts costs. It also lets businesses adopt cloud services with strong data protection.
-
Enhanced Security: Cisco's SASE solutions protect against cyber threats. They have a firewall, VPN, access control, threat detection, and endpoint security.
-
Optimized Performance: Cisco's SASE solutions combine networking and security in one platform. This boosts network performance and improves the user experience.
-
Seamless Scalability: Cisco's SASE lets organizations scale their networks to meet rising demands.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Cisco's SASE solutions are changing network security. They provide a cloud-native way to secure digital infrastructure. Cisco's SASE architecture has advanced security, fast performance, and easy scalability. It is setting new standards in the industry. To improve network security and connectivity, organizations should use Cisco's SASE solutions. They provide a secure and efficient digital environment.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In today's digital world, remote work and cloud apps are the norm. So, traditional network security is no longer enough for modern businesses. This is where SASE technology comes in. It offers a complete way to secure and connect networks. Cisco leads in SASE implementation. Its innovative solutions set new industry standards.
What is SASE and Why is it Important?
SASE is a concept. It combines network security with wide-area networking (WAN). It provides a unified, cloud-native solution. SASE combines networking and security into a single, cloud-based service. It simplifies management, cuts costs, and improves the user experience. With the rise of remote work and cloud apps, SASE has become vital. It helps organizations secure their digital infrastructure.
SASE (Secure Access Service Edge) is a cloud-native design. It combines networking and security services into a single framework. It gives secure access to users, devices, and apps from anywhere. It combines SD-WAN, secure web gateways, and zero trust. It's essential for businesses shifting to remote work and cloud environments. SASE boosts efficiency by merging security and networking into one platform. It simplifies tasks and protects against modern cyber threats.
SASE (Secure Access Service Edge) is a security-focused method. It combines wide area networking (WAN) with cloud-delivered security services. It streamlines network management and security. It combines firewalls, VPNs, and DLP into a single, scalable solution. SASE is crucial for organizations embracing cloud and remote work. It provides simple operations, strong security, and app access from anywhere.
Cisco's SASE Solutions: Leading the Way in Network Security
Cisco has SASE solutions for the security needs of modern businesses. They are comprehensive and designed to adapt to changing threats. Cisco's SASE architecture offers a complete solution for network security and connectivity. It includes secure access to cloud services and advanced threat detection. Cisco's SASE platform provides better security, faster performance, and easy scalability.
Cisco's SASE solutions are changing how businesses secure their networks. They combine strong security and networking features into a single, cloud-native platform. Cisco's SASE architecture combines SD-WAN, firewall-as-a-service, and zero trust access. It ensures secure, seamless connectivity for remote users and cloud apps. As firms move to hybrid and multi-cloud setups, Cisco's SASE framework is best for secure, scalable, and flexible networks.
Cisco's SASE solutions address the complexities of modern network security. They offer strong protection without sacrificing performance. With advanced threat intelligence and real-time monitoring, Cisco protects users. They can securely access critical apps from anywhere, reducing cyber risks. As businesses embrace digital transformation, Cisco's SASE offerings help. They simplify security while enhancing visibility and control over networks.
The Benefits of Implementing Cisco's SASE Solutions
Cisco's SASE (Secure Access Service Edge) solutions give firms a unified security system. It boosts performance and security across all network edges. SASE combines network security with WAN. It ensures secure, seamless access to apps, no matter the location. This simplifies management and cuts costs. It also lets businesses adopt cloud services with strong data protection.
-
Enhanced Security: Cisco's SASE solutions protect against cyber threats. They have a firewall, VPN, access control, threat detection, and endpoint security.
-
Optimized Performance: Cisco's SASE solutions combine networking and security in one platform. This boosts network performance and improves the user experience.
-
Seamless Scalability: Cisco's SASE lets organizations scale their networks to meet rising demands.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Cisco's SASE solutions are changing network security. They provide a cloud-native way to secure digital infrastructure. Cisco's SASE architecture has advanced security, fast performance, and easy scalability. It is setting new standards in the industry. To improve network security and connectivity, organizations should use Cisco's SASE solutions. They provide a secure and efficient digital environment.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Enable Live VM Migration in XenServer for Seamless Operation
Are you looking to enable live VM migration in XenServer without any downtime for your virtual machines? Look no further! This article will explore the seamless migration of VMs. It will use XenServer's live migration feature, which avoids service disruption.
What is Live VM Migration in XenServer?
Live VM migration in XenServer allows you to move virtual machines from one host to another without any interruption in service. It means your apps and workloads can keep running during the migration.
Live VM Migration in XenServer is moving a running VM to another host without interrupting it. This feature allows apps and services to be always available. It lets admins do maintenance or load balancing without downtime. Live Migration uses shared storage and network resources. It ensures seamless transitions while keeping active connections and workloads.
How does Live Migration Work in XenServer?
A live VM migration in XenServer transfers the VM's memory, storage, and network config in real time from the source host to the destination host. This ensures a seamless transition for your VMs without any downtime.
Live Migration in XenServer allows virtual machines (VMs) to be moved from one physical host to another without any downtime. This process copies the VM's memory state from the source host to the destination. It keeps the original VM running until the transfer is complete. Once the memory is synced, the VM's execution switches to the new host. This ensures users have uninterrupted service.
Benefits of Live Migration in XenServer
XenServer's live migration moves VMs between hosts with no downtime. It keeps the service running. This is especially useful during maintenance or upgrades. It allows seamless resource balancing across the infrastructure. Live migration boosts availability and cuts data loss risks. It does this by minimizing service interruptions and enhancing system flexibility.
-
No Downtime: Live migration in XenServer keeps your VMs accessible during migration.
-
High Availability: Live migration boosts your VMs' availability. It reduces the risk of outages.
-
Efficient Resource Use: Live migration lets you balance your hosts' load by moving VMs to optimize resources.
-
Real-Time Virtual Machine Migration: Live migration lets you move VMs in real-time. It won't affect performance or user experience.
How to Enable Live VM Migration in XenServer
XenServer's live VM migration lets you move VMs between hosts without downtime. This ensures continuous operation during maintenance or upgrades. To enable live migration, configure shared storage between hosts. Ensure network connectivity and have compatible XenServer versions on all hosts. Once set up, you can start live migrations via XenCenter or command-line tools. This will ensure smooth transitions with minimal performance impact.
To enable live VM migration in XenServer, follow these steps:
-
Configure Shared Storage: Ensure both hosts can access the shared storage with the VM files.
-
Enable Live Migration: In the XenCenter console, navigate to the VMs tab, right-click on the VM you want to migrate, and select "Migrate." Choose the destination host and follow the prompts to complete the migration.
-
Monitor the Migration: Use the XenCenter console to check the migration progress. Ensure everything is running smoothly.
-
Verify the Migration: Once the migration is complete, verify that the VM is up and running on the new host without any issues.
Best Practices for Live VM Migration in XenServer
-
Plan Ahead: Before initiating a live migration, make sure to plan out the process and consider any potential risks or challenges.
-
Test Migration: It's always a good idea to test the live migration process on a non-production VM to ensure that everything works as expected.
-
Monitor Performance: Keep an eye on the performance of your VMs during the migration to detect any anomalies or issues.
-
Backup Data: Ensure that you have recent backups of your VM data in case anything goes wrong during the migration process. By following these best practices, you can ensure a smooth, seamless live VM migration in XenServer. Your virtual machines will have no downtime.
How to obtain XenServer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, enabling live VM migration in XenServer lets you move your VMs between hosts with no service interruption. By following best practices and monitoring the process, you can ensure a seamless migration experience for your VMs. Don't let downtime affect your operations - enable live VM migration in XenServer today!
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
Are you looking to enable live VM migration in XenServer without any downtime for your virtual machines? Look no further! This article will explore the seamless migration of VMs. It will use XenServer's live migration feature, which avoids service disruption.
What is Live VM Migration in XenServer?
Live VM migration in XenServer allows you to move virtual machines from one host to another without any interruption in service. It means your apps and workloads can keep running during the migration.
Live VM Migration in XenServer is moving a running VM to another host without interrupting it. This feature allows apps and services to be always available. It lets admins do maintenance or load balancing without downtime. Live Migration uses shared storage and network resources. It ensures seamless transitions while keeping active connections and workloads.
How does Live Migration Work in XenServer?
A live VM migration in XenServer transfers the VM's memory, storage, and network config in real time from the source host to the destination host. This ensures a seamless transition for your VMs without any downtime.
Live Migration in XenServer allows virtual machines (VMs) to be moved from one physical host to another without any downtime. This process copies the VM's memory state from the source host to the destination. It keeps the original VM running until the transfer is complete. Once the memory is synced, the VM's execution switches to the new host. This ensures users have uninterrupted service.
Benefits of Live Migration in XenServer
XenServer's live migration moves VMs between hosts with no downtime. It keeps the service running. This is especially useful during maintenance or upgrades. It allows seamless resource balancing across the infrastructure. Live migration boosts availability and cuts data loss risks. It does this by minimizing service interruptions and enhancing system flexibility.
-
No Downtime: Live migration in XenServer keeps your VMs accessible during migration.
-
High Availability: Live migration boosts your VMs' availability. It reduces the risk of outages.
-
Efficient Resource Use: Live migration lets you balance your hosts' load by moving VMs to optimize resources.
-
Real-Time Virtual Machine Migration: Live migration lets you move VMs in real-time. It won't affect performance or user experience.
How to Enable Live VM Migration in XenServer
XenServer's live VM migration lets you move VMs between hosts without downtime. This ensures continuous operation during maintenance or upgrades. To enable live migration, configure shared storage between hosts. Ensure network connectivity and have compatible XenServer versions on all hosts. Once set up, you can start live migrations via XenCenter or command-line tools. This will ensure smooth transitions with minimal performance impact.
To enable live VM migration in XenServer, follow these steps:
-
Configure Shared Storage: Ensure both hosts can access the shared storage with the VM files.
-
Enable Live Migration: In the XenCenter console, navigate to the VMs tab, right-click on the VM you want to migrate, and select "Migrate." Choose the destination host and follow the prompts to complete the migration.
-
Monitor the Migration: Use the XenCenter console to check the migration progress. Ensure everything is running smoothly.
-
Verify the Migration: Once the migration is complete, verify that the VM is up and running on the new host without any issues.
Best Practices for Live VM Migration in XenServer
-
Plan Ahead: Before initiating a live migration, make sure to plan out the process and consider any potential risks or challenges.
-
Test Migration: It's always a good idea to test the live migration process on a non-production VM to ensure that everything works as expected.
-
Monitor Performance: Keep an eye on the performance of your VMs during the migration to detect any anomalies or issues.
-
Backup Data: Ensure that you have recent backups of your VM data in case anything goes wrong during the migration process. By following these best practices, you can ensure a smooth, seamless live VM migration in XenServer. Your virtual machines will have no downtime.
How to obtain XenServer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, enabling live VM migration in XenServer lets you move your VMs between hosts with no service interruption. By following best practices and monitoring the process, you can ensure a seamless migration experience for your VMs. Don't let downtime affect your operations - enable live VM migration in XenServer today!
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Real-Time Data Streaming: Kafka to WebSockets with Python
In the world of data processing and real-time analytics, Python has become a popular choice for developers and data engineers. With its versatility and ease of use, Python is often at the forefront of innovation in the field of software development. One key aspect of real-time data processing is the ability to stream data efficiently and reliably from one source to another. This is where technologies like Kafka and WebSockets come into play, providing a seamless way to transmit data in real-time.
What is Kafka and How Does it Work?
Apache Kafka is an open-source event streaming platform. It is widely used for building real-time data pipelines and streaming apps. It acts as a message broker that allows for the efficient and reliable transfer of data between systems. Kafka is designed to handle high volumes of data and can scale horizontally to support the needs of large-scale applications.? Kafka uses a publish-subscribe model. Data producers publish messages to topics. Data consumers subscribe to these topics to receive the messages. This separation of producers and consumers allows for flexible, scalable data workflows.?
Apache Kafka is a distributed event streaming platform. It handles real-time data feeds with high throughput and low latency. It uses a publish-subscribe model. Producers send messages (events) to topics. Consumers read these messages from the topics. This is done in a distributed, fault-tolerant way. Kafka efficiently manages large data volumes across systems. It's ideal for real-time apps, data pipelines, and analytics platforms.
Why Use Python for Real-Time Data Processing?
Python's simplicity and readability make it an ideal choice for real-time data processing tasks. Python has many libraries and frameworks. They let developers quickly prototype and deploy data processing pipelines. Python's async programming suits it for real-time data streams. It can scale to meet high-volume data processing demands.? Also, Python has a vast ecosystem of libraries and tools. They include Pandas, NumPy, and SciPy. They provide powerful ways to manipulate, analyze, and visualize data. Python is a versatile language. It can handle many data tasks, from ingestion to visualization.?
Python is an excellent choice for real-time data processing due to its simplicity, flexibility, and wide array of libraries. With tools like Apache Kafka, Redis, and WebSockets, Python can handle high-speed data streams. It ensures low-latency performance. Python is a powerful choice for building scalable, real-time data pipelines. Its active community and integration with big data tech are key.
How WebSockets Enhance Real-Time Data Streaming?
WebSockets are a powerful technology. They enable full-duplex communication between a client and a server over a single, long-lived connection. It allows real-time data transfer between a web browser and a server. This makes it perfect for apps that need low latency and high interactivity.? WebSockets can improve real-time data processing pipelines. They allow developers to create dynamic web apps that push data updates to clients in real-time. This allows users to communicate and collaborate seamlessly. Data can be sent instantly and displayed dynamically on the client side.?
WebSockets greatly improve real-time data streaming. They provide a persistent, full-duplex channel for clients and servers. This allows for instant data exchange. WebSockets allow continuous communication, unlike traditional HTTP requests. They require a new connection for each interaction. WebSockets reduce latency and improve responsiveness in chat apps, live notifications, and online games. This tech optimizes bandwidth and ensures a smooth user experience. It allows for a rapid, real-time flow of updates.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Python, Kafka, and WebSockets are vital for real-time data apps. Python is powerful and flexible. Developers can use it to build efficient data pipelines for real-time data. It streams, processes, and visualizes the data. Kafka is popular for data streaming due to its scalability and reliability. WebSockets improve real-time communication and interactivity in web apps. These technologies form a strong base for real-time data apps. They can meet the demands of today's data-driven world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
Read More
In the world of data processing and real-time analytics, Python has become a popular choice for developers and data engineers. With its versatility and ease of use, Python is often at the forefront of innovation in the field of software development. One key aspect of real-time data processing is the ability to stream data efficiently and reliably from one source to another. This is where technologies like Kafka and WebSockets come into play, providing a seamless way to transmit data in real-time.
What is Kafka and How Does it Work?
Apache Kafka is an open-source event streaming platform. It is widely used for building real-time data pipelines and streaming apps. It acts as a message broker that allows for the efficient and reliable transfer of data between systems. Kafka is designed to handle high volumes of data and can scale horizontally to support the needs of large-scale applications.? Kafka uses a publish-subscribe model. Data producers publish messages to topics. Data consumers subscribe to these topics to receive the messages. This separation of producers and consumers allows for flexible, scalable data workflows.?
Apache Kafka is a distributed event streaming platform. It handles real-time data feeds with high throughput and low latency. It uses a publish-subscribe model. Producers send messages (events) to topics. Consumers read these messages from the topics. This is done in a distributed, fault-tolerant way. Kafka efficiently manages large data volumes across systems. It's ideal for real-time apps, data pipelines, and analytics platforms.
Why Use Python for Real-Time Data Processing?
Python's simplicity and readability make it an ideal choice for real-time data processing tasks. Python has many libraries and frameworks. They let developers quickly prototype and deploy data processing pipelines. Python's async programming suits it for real-time data streams. It can scale to meet high-volume data processing demands.? Also, Python has a vast ecosystem of libraries and tools. They include Pandas, NumPy, and SciPy. They provide powerful ways to manipulate, analyze, and visualize data. Python is a versatile language. It can handle many data tasks, from ingestion to visualization.?
Python is an excellent choice for real-time data processing due to its simplicity, flexibility, and wide array of libraries. With tools like Apache Kafka, Redis, and WebSockets, Python can handle high-speed data streams. It ensures low-latency performance. Python is a powerful choice for building scalable, real-time data pipelines. Its active community and integration with big data tech are key.
How WebSockets Enhance Real-Time Data Streaming?
WebSockets are a powerful technology. They enable full-duplex communication between a client and a server over a single, long-lived connection. It allows real-time data transfer between a web browser and a server. This makes it perfect for apps that need low latency and high interactivity.? WebSockets can improve real-time data processing pipelines. They allow developers to create dynamic web apps that push data updates to clients in real-time. This allows users to communicate and collaborate seamlessly. Data can be sent instantly and displayed dynamically on the client side.?
WebSockets greatly improve real-time data streaming. They provide a persistent, full-duplex channel for clients and servers. This allows for instant data exchange. WebSockets allow continuous communication, unlike traditional HTTP requests. They require a new connection for each interaction. WebSockets reduce latency and improve responsiveness in chat apps, live notifications, and online games. This tech optimizes bandwidth and ensures a smooth user experience. It allows for a rapid, real-time flow of updates.
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Python, Kafka, and WebSockets are vital for real-time data apps. Python is powerful and flexible. Developers can use it to build efficient data pipelines for real-time data. It streams, processes, and visualizes the data. Kafka is popular for data streaming due to its scalability and reliability. WebSockets improve real-time communication and interactivity in web apps. These technologies form a strong base for real-time data apps. They can meet the demands of today's data-driven world.
Contact Us For More Information:
Visit :www.icertglobal.comEmail : info@icertglobal.com
The Role of CRISC in Digital Transformation Strategies!
In today's fast-changing business world, digital transformation is key. It helps organizations stay competitive and agile. As businesses embrace new technologies, they must also manage the associated risks. The Certified in Risk and Information Systems Control (CRISC) certification is key here. CRISC-certified pros specialize in managing risks in information systems. They are vital to digital transformation efforts. CRISC certification aligns IT risks with business goals. It ensures that digital innovations are secure, compliant, and support long-term aims.
This article will explore CRISC's role in digital transformation. It will also explore how the certification can help organizations with digital age challenges.
Table Of Contents
- Understanding CRISC: An Overview
- Risk Identification and Management in Digital Transformation
- Risk Assessment for Emerging Technologies
- Governance and Compliance in Digital Transformation
- Mitigating Cybersecurity Risks in a Digitally Transformed World
- Conclusion
Understanding CRISC: An Overview
ISACA offers the Certified in Risk and Information Systems Control (CRISC) certification. It is for those who manage risk and design security controls in organizations. It focuses on the four domains:
- IT risk identification
- IT risk assessment
- Risk response and mitigation
- Risk and control monitoring and reporting
How CRISC Contributes to Digital Transformation:
- CRISC-certified professionals are vital in managing risks from new technologies.
- They help identify vulnerabilities and align security measures with strategic business goals.
- CRISC ensures organizations innovate in a controlled, risk-aware way. It minimizes disruption while maximizing opportunities.
Risk Identification and Management in Digital Transformation
Digital transformation means using advanced technologies. These include cloud computing, AI, IoT, and big data analytics. But these technologies also introduce new risks. CRISC professionals equip themselves to:
- Identify potential risks associated with the implementation of these technologies.
- Know how new systems can affect existing IT frameworks. Highlight any concerns.
- Ensure that digital initiatives align with the risk appetite of the organization.
Key Points:
- Identify key vulnerabilities in new digital initiatives.
- Map risks to the organization’s existing risk management framework.
- Build controls that mitigate digital transformation risks.
Risk Assessment for Emerging Technologies
Risk assessment is a crucial part of the digital transformation journey. CRISC-certified professionals assess the risks of adopting new technologies. They test both the likelihood and impact of those risks.
- For example, a move to the cloud can raise data privacy, compliance, and operational issues. CRISC-certified experts assess these risks and provide informed solutions.
- They enable organizations to balance innovation with regulatory compliance and operational security.
Key Points:
- Use CRISC expertise to perform thorough risk assessments for each new technology.
- Rank risks based on the severity and likelihood of impact.
- Create contingency plans for high-risk areas, such as data breaches or system downtimes.
Governance and Compliance in Digital Transformation
A key challenge of digital transformation is to ensure new digital processes comply with existing rules. With data privacy laws like GDPR and CCPA, governance is vital.
CRISC-certified professionals:
- Help organizations follow global and local regulations. Do this while implementing new digital strategies.
- Create frameworks for businesses to use digital innovations while staying compliant.
- Provide tools to check and audit systems. They must meet governance standards.
Key Points:
- Build compliance frameworks that allow for the seamless integration of new technologies.
- Ensure continuous monitoring and auditing of digital systems.
- Train teams to stay updated on regulations and apply them to digital workflows.
Mitigating Cybersecurity Risks in a Digitally Transformed World
As organizations undergo digital transformation, cybersecurity risks increase. The proliferation of connected devices, cloud infrastructure, and automated systems increases potential vulnerabilities. CRISC professionals are essential for:
- Building robust cybersecurity defenses that align with digital transformation initiatives.
- Developing strategies to reduce risk. These include incident response plans, access controls, and encryption to protect digital assets.
- Collaborating with other teams to evolve security as digital strategies grow.
Key Points:
- Integrate strong cybersecurity protocols within all digital transformation initiatives.
- Check, detect, and respond to emerging cyber threats in real time.
- Educate the workforce on cybersecurity best practices to prevent insider threats.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Digital transformation is now a must for competitive businesses. But it brings challenges, especially in risk management. CRISC-certified professionals can identify, assess, and reduce risks in digital transformation strategies. They have the skills for it. The CRISC certification is vital in today's digital world. It guides organizations on cybersecurity, compliance, and risk management. It aligns these with their business goals.
By adding CRISC experts to digital transformation plans, organizations can innovate. They can do this while keeping their systems, data, and reputation safe from unknown risks.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing business world, digital transformation is key. It helps organizations stay competitive and agile. As businesses embrace new technologies, they must also manage the associated risks. The Certified in Risk and Information Systems Control (CRISC) certification is key here. CRISC-certified pros specialize in managing risks in information systems. They are vital to digital transformation efforts. CRISC certification aligns IT risks with business goals. It ensures that digital innovations are secure, compliant, and support long-term aims.
This article will explore CRISC's role in digital transformation. It will also explore how the certification can help organizations with digital age challenges.
Table Of Contents
- Understanding CRISC: An Overview
- Risk Identification and Management in Digital Transformation
- Risk Assessment for Emerging Technologies
- Governance and Compliance in Digital Transformation
- Mitigating Cybersecurity Risks in a Digitally Transformed World
- Conclusion
Understanding CRISC: An Overview
ISACA offers the Certified in Risk and Information Systems Control (CRISC) certification. It is for those who manage risk and design security controls in organizations. It focuses on the four domains:
- IT risk identification
- IT risk assessment
- Risk response and mitigation
- Risk and control monitoring and reporting
How CRISC Contributes to Digital Transformation:
- CRISC-certified professionals are vital in managing risks from new technologies.
- They help identify vulnerabilities and align security measures with strategic business goals.
- CRISC ensures organizations innovate in a controlled, risk-aware way. It minimizes disruption while maximizing opportunities.
Risk Identification and Management in Digital Transformation
Digital transformation means using advanced technologies. These include cloud computing, AI, IoT, and big data analytics. But these technologies also introduce new risks. CRISC professionals equip themselves to:
- Identify potential risks associated with the implementation of these technologies.
- Know how new systems can affect existing IT frameworks. Highlight any concerns.
- Ensure that digital initiatives align with the risk appetite of the organization.
Key Points:
- Identify key vulnerabilities in new digital initiatives.
- Map risks to the organization’s existing risk management framework.
- Build controls that mitigate digital transformation risks.
Risk Assessment for Emerging Technologies
Risk assessment is a crucial part of the digital transformation journey. CRISC-certified professionals assess the risks of adopting new technologies. They test both the likelihood and impact of those risks.
- For example, a move to the cloud can raise data privacy, compliance, and operational issues. CRISC-certified experts assess these risks and provide informed solutions.
- They enable organizations to balance innovation with regulatory compliance and operational security.
Key Points:
- Use CRISC expertise to perform thorough risk assessments for each new technology.
- Rank risks based on the severity and likelihood of impact.
- Create contingency plans for high-risk areas, such as data breaches or system downtimes.
Governance and Compliance in Digital Transformation
A key challenge of digital transformation is to ensure new digital processes comply with existing rules. With data privacy laws like GDPR and CCPA, governance is vital.
CRISC-certified professionals:
- Help organizations follow global and local regulations. Do this while implementing new digital strategies.
- Create frameworks for businesses to use digital innovations while staying compliant.
- Provide tools to check and audit systems. They must meet governance standards.
Key Points:
- Build compliance frameworks that allow for the seamless integration of new technologies.
- Ensure continuous monitoring and auditing of digital systems.
- Train teams to stay updated on regulations and apply them to digital workflows.
Mitigating Cybersecurity Risks in a Digitally Transformed World
As organizations undergo digital transformation, cybersecurity risks increase. The proliferation of connected devices, cloud infrastructure, and automated systems increases potential vulnerabilities. CRISC professionals are essential for:
- Building robust cybersecurity defenses that align with digital transformation initiatives.
- Developing strategies to reduce risk. These include incident response plans, access controls, and encryption to protect digital assets.
- Collaborating with other teams to evolve security as digital strategies grow.
Key Points:
- Integrate strong cybersecurity protocols within all digital transformation initiatives.
- Check, detect, and respond to emerging cyber threats in real time.
- Educate the workforce on cybersecurity best practices to prevent insider threats.
How to obtain CRISC certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Digital transformation is now a must for competitive businesses. But it brings challenges, especially in risk management. CRISC-certified professionals can identify, assess, and reduce risks in digital transformation strategies. They have the skills for it. The CRISC certification is vital in today's digital world. It guides organizations on cybersecurity, compliance, and risk management. It aligns these with their business goals.
By adding CRISC experts to digital transformation plans, organizations can innovate. They can do this while keeping their systems, data, and reputation safe from unknown risks.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Evolution of XenApp A Look at Its History and Future
XenApp is a top virtualization tool by Citrix. It has changed how organizations deliver apps to users. It has, over the years, adapted to changing business needs and tech advances. There is also a demand for remote access. This article will explore the history of XenApp. It will cover its key milestones, challenges, and the future of app delivery and virtualization.
Table Of Contents
- The Origins of XenApp: A Brief History
- Major Milestones in XenApp Development
- Challenges Faced by XenApp
- The Current Landscape of XenApp
- The Future of XenApp
- Conclusion
The Origins of XenApp: A Brief History
- Start and Early Years (1997-2000) Citrix was founded in 1989. It began its application virtualization journey with WinFrame. It allowed sharing Windows applications across networks. The first iteration of XenApp was launched in 1997, originally branded as MetaFrame. It let businesses run Windows apps on servers. They could then deliver them to client devices over a network.
- Transition to XenApp (2008) In 2008, Citrix rebranded MetaFrame to XenApp. This change was a big shift. It introduced features like seamless app delivery, better security, and multi-device app delivery. The focus shifted from remote desktop solutions to a broader app delivery platform.
- Early Adoption of Virtualization Technologies As organizations began using virtualization, XenApp integrated with other Citrix products, including XenDesktop. This created a better solution for both application and desktop virtualization.
Major Milestones in XenApp Development
XenApp 6.0 (2010) added support for Windows Server 2008 R2. It improved scalability and app streaming. This version laid the foundation for enhanced performance and management capabilities.
- Introduction of App Streaming (2011) XenApp introduced app streaming. It allows more efficient app delivery. Users could access apps without fully installing them. This reduced storage needs and sped up deployments.
- XenApp and XenDesktop Integration (2013) It merged XenApp and XenDesktop into one app. It gave users a seamless experience. They could access both virtual desktops and apps through a single platform. This move streamlined management and enhanced user flexibility.
Challenges Faced by XenApp
- Competition from Other Virtualization Solutions The virtualization market grew, as did the competition. VMware, Microsoft, and other players introduced their solutions, challenging XenApp's market share. Citrix had to pursue constant innovation to remain relevant.
- Security Concerns: With remote work and cloud use, security is now critical. XenApp faced scrutiny over data protection, user authentication, and compliance with regulations. Citrix improved security. It added multi-factor authentication and better data encryption.
- As organizations used XenApp more, performance and user experience became crucial. Citrix invested in better performance metrics and faster connections. They wanted apps to run well, even in low-bandwidth situations.
The Current Landscape of XenApp
- Cloud and Hybrid Solutions Today, XenApp is a cloud-ready solution. It lets organizations deploy apps in public, private, or hybrid cloud environments. This flexibility is vital for businesses. They want to optimize their IT while keeping access to critical apps.
- XenApp now supports Windows, macOS, iOS, and Android. It works on various devices. This capability allows organizations to cater to diverse workforces, enhancing mobility and productivity.
- Emphasis on User Experience Citrix has focused on user experience. Its HDX technology improves app delivery for better performance. XenApp's focus on user satisfaction has made it a top choice for many organizations.
The Future of XenApp
- AI and Machine Learning Integration. Citrix plans to add AI and machine learning to XenApp. These innovations could improve performance monitoring and automate management tasks. They could also provide insights into user behavior to enhance app delivery.
- Continued Cloud Adoption. As more organizations adopt the cloud, XenApp should evolve as a cloud-first solution. Citrix will likely boost its cloud. It will add auto-scaling, easier management, and better cost-efficiency.
- Focus on Security Enhancements. With rising threats, Citrix will focus on security in XenApp. Expect advanced security. It will use zero trust and strong compliance to protect user data and apps.
How to obtain Citrix certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, XenApp's evolution shows Citrix's commitment to innovation amid changing tech. XenApp has evolved from its early days as MetaFrame. It is now a leader in application virtualization. It meets the needs of businesses and users. In the future, AI, cloud tech, and better security will keep XenApp a top app delivery solution. This will help organizations thrive in a more digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
XenApp is a top virtualization tool by Citrix. It has changed how organizations deliver apps to users. It has, over the years, adapted to changing business needs and tech advances. There is also a demand for remote access. This article will explore the history of XenApp. It will cover its key milestones, challenges, and the future of app delivery and virtualization.
Table Of Contents
- The Origins of XenApp: A Brief History
- Major Milestones in XenApp Development
- Challenges Faced by XenApp
- The Current Landscape of XenApp
- The Future of XenApp
- Conclusion
The Origins of XenApp: A Brief History
- Start and Early Years (1997-2000) Citrix was founded in 1989. It began its application virtualization journey with WinFrame. It allowed sharing Windows applications across networks. The first iteration of XenApp was launched in 1997, originally branded as MetaFrame. It let businesses run Windows apps on servers. They could then deliver them to client devices over a network.
- Transition to XenApp (2008) In 2008, Citrix rebranded MetaFrame to XenApp. This change was a big shift. It introduced features like seamless app delivery, better security, and multi-device app delivery. The focus shifted from remote desktop solutions to a broader app delivery platform.
- Early Adoption of Virtualization Technologies As organizations began using virtualization, XenApp integrated with other Citrix products, including XenDesktop. This created a better solution for both application and desktop virtualization.
Major Milestones in XenApp Development
XenApp 6.0 (2010) added support for Windows Server 2008 R2. It improved scalability and app streaming. This version laid the foundation for enhanced performance and management capabilities.
- Introduction of App Streaming (2011) XenApp introduced app streaming. It allows more efficient app delivery. Users could access apps without fully installing them. This reduced storage needs and sped up deployments.
- XenApp and XenDesktop Integration (2013) It merged XenApp and XenDesktop into one app. It gave users a seamless experience. They could access both virtual desktops and apps through a single platform. This move streamlined management and enhanced user flexibility.
Challenges Faced by XenApp
- Competition from Other Virtualization Solutions The virtualization market grew, as did the competition. VMware, Microsoft, and other players introduced their solutions, challenging XenApp's market share. Citrix had to pursue constant innovation to remain relevant.
- Security Concerns: With remote work and cloud use, security is now critical. XenApp faced scrutiny over data protection, user authentication, and compliance with regulations. Citrix improved security. It added multi-factor authentication and better data encryption.
- As organizations used XenApp more, performance and user experience became crucial. Citrix invested in better performance metrics and faster connections. They wanted apps to run well, even in low-bandwidth situations.
The Current Landscape of XenApp
- Cloud and Hybrid Solutions Today, XenApp is a cloud-ready solution. It lets organizations deploy apps in public, private, or hybrid cloud environments. This flexibility is vital for businesses. They want to optimize their IT while keeping access to critical apps.
- XenApp now supports Windows, macOS, iOS, and Android. It works on various devices. This capability allows organizations to cater to diverse workforces, enhancing mobility and productivity.
- Emphasis on User Experience Citrix has focused on user experience. Its HDX technology improves app delivery for better performance. XenApp's focus on user satisfaction has made it a top choice for many organizations.
The Future of XenApp
- AI and Machine Learning Integration. Citrix plans to add AI and machine learning to XenApp. These innovations could improve performance monitoring and automate management tasks. They could also provide insights into user behavior to enhance app delivery.
- Continued Cloud Adoption. As more organizations adopt the cloud, XenApp should evolve as a cloud-first solution. Citrix will likely boost its cloud. It will add auto-scaling, easier management, and better cost-efficiency.
- Focus on Security Enhancements. With rising threats, Citrix will focus on security in XenApp. Expect advanced security. It will use zero trust and strong compliance to protect user data and apps.
How to obtain Citrix certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, XenApp's evolution shows Citrix's commitment to innovation amid changing tech. XenApp has evolved from its early days as MetaFrame. It is now a leader in application virtualization. It meets the needs of businesses and users. In the future, AI, cloud tech, and better security will keep XenApp a top app delivery solution. This will help organizations thrive in a more digital world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Leveraging Retrospectives to Foster Team Innovation & Growth
In project management, teams want to improve their processes and results. They seek new ways to do this in a fast-paced world. Retrospectives, linked to Agile methods, are great for reflection and learning. They set aside time for teams to analyze their work. They identify successes and failures, and brainstorm ideas for improvements. Retrospectives can help teams build a culture of improvement, collaboration, and innovation. This article looks at how retrospectives boost team innovation. It offers tips to make them more effective.
Table Of Contents
- The Importance of Retrospectives in Agile Teams
- Structuring Effective Retrospectives
- Fostering a Culture of Openness and Trust
- Turning Insights into Actionable Innovations
- Leveraging Technology to Enhance Retrospectives
- Conclusion
The Importance of Retrospectives in Agile Teams
Retrospectives are key to Agile methods. They provide a structured way to reflect and learn. The Agile Manifesto values individuals and interactions over processes and tools. So, retrospectives are vital for fostering collaboration. Here are a few key points regarding their significance:
- Retrospectives let teams regularly evaluate their performance. Teams can boost their processes and productivity. They should focus on what went well and what can be improved.
- Team Cohesion: These sessions encourage open communication and trust among team members. When people feel safe sharing their ideas, it helps the team. It fosters collaboration and innovation.
- Adaptability: Retrospectives empower teams to adapt their approaches based on real feedback. Regular work reviews allow teams to pivot quickly. They can then stay aligned with project goals and respond to challenges.
Structuring Effective Retrospectives
To drive innovation, structuring retrospectives in a purposeful manner is crucial. Here are some strategies to consider:
- Set Clear Objectives: Define the purpose of each retrospective. Is the focus on improving communication, enhancing productivity, or addressing specific challenges? Clear objectives help guide discussions and keep the team focused.
- Use Varied Formats: Mixing up formats can keep the sessions fresh and engaging. Consider using formats like Start-Stop-Continue or the 4Ls (Liked, Learned, Lacked, Longed for). They can stimulate new ideas. Fishbowl discussions can help, too.
- Time Management: Allocate time in a way that maximizes productivity during retrospectives. Allow enough time for each section. Team members should share their thoughts. But, keep a brisk pace to avoid disengagement.
Fostering a Culture of Openness and Trust
For retrospectives to drive innovation, a safe environment is essential. Team members must feel comfortable sharing their thoughts. Here are some tips for fostering this culture:
- Psychological Safety: Team members should speak openly, feeling secure from judgment. Acknowledge all contributions. Emphasize that the goal is to learn and improve together.
- Focus on Processes, Not Individuals: Discuss processes and outcomes, not blame individuals. This approach promotes a culture of learning rather than defensiveness.
- Celebrate Successes: Take the time to recognize and celebrate achievements during retrospectives. It boosts morale and reinforces good behavior in the team.
Turning Insights into Actionable Innovations
The ultimate goal of retrospectives is to translate insights into actionable innovations. Here’s how teams can make that happen:
- Identify Key Takeaways: After discussing the pros and cons, list the main points as clear, actionable items. These should be specific, measurable, and time-bound to ensure accountability.
- Create an Action Plan: Outline a plan for the team to install the improvements. Assign responsibilities and deadlines to track and follow through on actions.
- Review Progress: Incorporate a review of previous action items in later retrospectives. This practice holds the team accountable. It also lets them improve based on feedback.
Leveraging Technology to Enhance Retrospectives
As the world becomes more digital, using technology can improve retrospectives. Consider these tools and techniques:
- Virtual Collaboration Tools: Use tools like Miro, Trello, or Jira for remote retrospectives. These platforms let team members collaborate in real time, no matter where they are.
- Survey Tools: Before retrospectives, use surveys or polls to gather team input. This information can help guide discussions and ensure that everyone hears all voices.
- Recording Sessions: Consider recording retrospectives (with team consent) for future reference. It can help new members understand past discussions and decisions. This fosters a sense of continuity and shared history.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Retrospectives are not just routine check-ins. They are chances to drive innovation and boost team performance.
Teams can unlock the full potential of retrospectives by:
- Embracing continuous improvement.
- Fostering a culture of openness.
- Turning insights into actionable plans.
Leveraging technology can further enhance these sessions, making them more engaging and productive. Regular reflection and adaptation help teams build an innovative mindset. This leads to better project outcomes and a stronger team culture. Prioritizing retrospectives can empower teams to evolve and succeed in a changing world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In project management, teams want to improve their processes and results. They seek new ways to do this in a fast-paced world. Retrospectives, linked to Agile methods, are great for reflection and learning. They set aside time for teams to analyze their work. They identify successes and failures, and brainstorm ideas for improvements. Retrospectives can help teams build a culture of improvement, collaboration, and innovation. This article looks at how retrospectives boost team innovation. It offers tips to make them more effective.
Table Of Contents
- The Importance of Retrospectives in Agile Teams
- Structuring Effective Retrospectives
- Fostering a Culture of Openness and Trust
- Turning Insights into Actionable Innovations
- Leveraging Technology to Enhance Retrospectives
- Conclusion
The Importance of Retrospectives in Agile Teams
Retrospectives are key to Agile methods. They provide a structured way to reflect and learn. The Agile Manifesto values individuals and interactions over processes and tools. So, retrospectives are vital for fostering collaboration. Here are a few key points regarding their significance:
- Retrospectives let teams regularly evaluate their performance. Teams can boost their processes and productivity. They should focus on what went well and what can be improved.
- Team Cohesion: These sessions encourage open communication and trust among team members. When people feel safe sharing their ideas, it helps the team. It fosters collaboration and innovation.
- Adaptability: Retrospectives empower teams to adapt their approaches based on real feedback. Regular work reviews allow teams to pivot quickly. They can then stay aligned with project goals and respond to challenges.
Structuring Effective Retrospectives
To drive innovation, structuring retrospectives in a purposeful manner is crucial. Here are some strategies to consider:
- Set Clear Objectives: Define the purpose of each retrospective. Is the focus on improving communication, enhancing productivity, or addressing specific challenges? Clear objectives help guide discussions and keep the team focused.
- Use Varied Formats: Mixing up formats can keep the sessions fresh and engaging. Consider using formats like Start-Stop-Continue or the 4Ls (Liked, Learned, Lacked, Longed for). They can stimulate new ideas. Fishbowl discussions can help, too.
- Time Management: Allocate time in a way that maximizes productivity during retrospectives. Allow enough time for each section. Team members should share their thoughts. But, keep a brisk pace to avoid disengagement.
Fostering a Culture of Openness and Trust
For retrospectives to drive innovation, a safe environment is essential. Team members must feel comfortable sharing their thoughts. Here are some tips for fostering this culture:
- Psychological Safety: Team members should speak openly, feeling secure from judgment. Acknowledge all contributions. Emphasize that the goal is to learn and improve together.
- Focus on Processes, Not Individuals: Discuss processes and outcomes, not blame individuals. This approach promotes a culture of learning rather than defensiveness.
- Celebrate Successes: Take the time to recognize and celebrate achievements during retrospectives. It boosts morale and reinforces good behavior in the team.
Turning Insights into Actionable Innovations
The ultimate goal of retrospectives is to translate insights into actionable innovations. Here’s how teams can make that happen:
- Identify Key Takeaways: After discussing the pros and cons, list the main points as clear, actionable items. These should be specific, measurable, and time-bound to ensure accountability.
- Create an Action Plan: Outline a plan for the team to install the improvements. Assign responsibilities and deadlines to track and follow through on actions.
- Review Progress: Incorporate a review of previous action items in later retrospectives. This practice holds the team accountable. It also lets them improve based on feedback.
Leveraging Technology to Enhance Retrospectives
As the world becomes more digital, using technology can improve retrospectives. Consider these tools and techniques:
- Virtual Collaboration Tools: Use tools like Miro, Trello, or Jira for remote retrospectives. These platforms let team members collaborate in real time, no matter where they are.
- Survey Tools: Before retrospectives, use surveys or polls to gather team input. This information can help guide discussions and ensure that everyone hears all voices.
- Recording Sessions: Consider recording retrospectives (with team consent) for future reference. It can help new members understand past discussions and decisions. This fosters a sense of continuity and shared history.
How to obtain CSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Retrospectives are not just routine check-ins. They are chances to drive innovation and boost team performance.
Teams can unlock the full potential of retrospectives by:
- Embracing continuous improvement.
- Fostering a culture of openness.
- Turning insights into actionable plans.
Leveraging technology can further enhance these sessions, making them more engaging and productive. Regular reflection and adaptation help teams build an innovative mindset. This leads to better project outcomes and a stronger team culture. Prioritizing retrospectives can empower teams to evolve and succeed in a changing world.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Cybersecurity Risk Management Strategies for 2024 and Beyond
As technology evolves, so do the threats facing organizations in the digital landscape. Cybersecurity is now key to business strategy. Cyber threats risk data, privacy, and reputation, as well as business continuity. In 2024, organizations must adopt adaptive cybersecurity strategies. They must guard against a threat landscape that is in a constant state of change. This article explores ways to improve cybersecurity risk management next year. It covers effective strategies and frameworks.
Table Of Contents
- Adopting a Risk-Based Approach
- Implementing Advanced Threat Detection Technologies
- Strengthening Incident Response Plans
- Promoting a culture of cybersecurity awareness.
- Complying with regulations and standards.
- Conclusion
Adopting a Risk-Based Approach
- A risk-based approach to cybersecurity means finding and ranking risks. The organization bases it on its potential impact.
- Organizations should conduct risk assessments on a regular basis. This will identify vulnerabilities, potential threats, and the likelihood of risk events. This process involves analyzing both internal and external factors that could affect cybersecurity.
- Prioritization: After identifying risks, organizations must rank them by potential impact. This allows for effective resource use. It ensures that we fix the most critical vulnerabilities first.
- Continuous Monitoring: Cyber threats are dynamic. We must check the threat landscape and our internal systems at regular intervals. Organizations should use automated tools to track and analyze real-time data. This will allow for the quick identification of new risks.
Implementing Advanced Threat Detection Technologies
- Advanced threat detection technology can boost an organization's response to cyber incidents.
- AI and ML can analyze vast amounts of data to find threat patterns. AI-driven solutions can automate responses to common threats, thereby reducing response times.
- Behavioral Analytics: Monitoring user behavior can detect anomalies. They may indicate a security breach. Organizations should use tools that track user actions. They should alert on unusual activity.
- EDR solutions check and respond to endpoints without interruption. They help organizations detect and respond to threats across devices. This ensures that we contain any breaches without delay.
Strengthening Incident Response Plans
- A strong incident response plan (IRP) is key. It minimizes the impact of cyber incidents.
- Organizations should create a detailed IRP. It should outline roles, responsibilities, and procedures for a cyber incident. This plan should include clear communication channels and escalation procedures.
- Training and Drills: Conduct regular training and tabletop exercises. This ensures all employees understand their roles in a cybersecurity incident. These drills help find gaps in the plan. They allow organizations to make necessary adjustments.
- After a cybersecurity incident, organizations should review the response. This post-incident review should identify weaknesses in the IRP and suggest improvements. This iterative process enhances preparedness for future incidents.
Promoting a culture of cybersecurity awareness.
- A strong cybersecurity culture is vital. It helps mitigate human error, a major cause of security breaches.
- Training Programs: Organizations should run ongoing cybersecurity training for all employees. It should emphasize best practices, phishing detection, and data protection.
- Simulated Phishing Attacks: They can assess employee awareness and response. These exercises educate employees about phishing tactics. They also promote a proactive approach to cybersecurity.
- Open Communication: Encouraging discussions about cybersecurity can foster a vigilant culture. Employees should feel empowered to report suspicious activity without fear of reprisal.
Complying with regulations and standards.
Compliance with cybersecurity regulations and standards is a legal need. It's also a best practice for risk management.
- Stay Informed: Organizations must keep up with cybersecurity laws. These include the GDPR, CCPA, and PCI DSS. This ensures they know their duties and can apply the needed controls.
- Regular audits: they can help assess compliance and find areas for improvement. This approach cuts penalty risks and boosts security.
- Third-Party Risk Management: Organizations must assess their vendors' cybersecurity practices. A strong vendor risk management program. It ensures partners meet the same cybersecurity standards.
How to obtain PMI-RMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, cybersecurity risk management is vital for organizations. The digital world is now very complex.
Organizations can boost their cybersecurity by:
- Adopting a risk-based approach.
- Using advanced threat detection tech.
- Strengthening incident response plans.
- Fostering a culture of cybersecurity awareness.
- Complying with regulations and standards.
As cyber threats evolve, a proactive approach to cybersecurity is vital. It will protect sensitive data and ensure business integrity. These strategies will guard against today's threats. They will also prepare organizations for future challenges in the fast-changing world of cybersecurity.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As technology evolves, so do the threats facing organizations in the digital landscape. Cybersecurity is now key to business strategy. Cyber threats risk data, privacy, and reputation, as well as business continuity. In 2024, organizations must adopt adaptive cybersecurity strategies. They must guard against a threat landscape that is in a constant state of change. This article explores ways to improve cybersecurity risk management next year. It covers effective strategies and frameworks.
Table Of Contents
- Adopting a Risk-Based Approach
- Implementing Advanced Threat Detection Technologies
- Strengthening Incident Response Plans
- Promoting a culture of cybersecurity awareness.
- Complying with regulations and standards.
- Conclusion
Adopting a Risk-Based Approach
- A risk-based approach to cybersecurity means finding and ranking risks. The organization bases it on its potential impact.
- Organizations should conduct risk assessments on a regular basis. This will identify vulnerabilities, potential threats, and the likelihood of risk events. This process involves analyzing both internal and external factors that could affect cybersecurity.
- Prioritization: After identifying risks, organizations must rank them by potential impact. This allows for effective resource use. It ensures that we fix the most critical vulnerabilities first.
- Continuous Monitoring: Cyber threats are dynamic. We must check the threat landscape and our internal systems at regular intervals. Organizations should use automated tools to track and analyze real-time data. This will allow for the quick identification of new risks.
Implementing Advanced Threat Detection Technologies
- Advanced threat detection technology can boost an organization's response to cyber incidents.
- AI and ML can analyze vast amounts of data to find threat patterns. AI-driven solutions can automate responses to common threats, thereby reducing response times.
- Behavioral Analytics: Monitoring user behavior can detect anomalies. They may indicate a security breach. Organizations should use tools that track user actions. They should alert on unusual activity.
- EDR solutions check and respond to endpoints without interruption. They help organizations detect and respond to threats across devices. This ensures that we contain any breaches without delay.
Strengthening Incident Response Plans
- A strong incident response plan (IRP) is key. It minimizes the impact of cyber incidents.
- Organizations should create a detailed IRP. It should outline roles, responsibilities, and procedures for a cyber incident. This plan should include clear communication channels and escalation procedures.
- Training and Drills: Conduct regular training and tabletop exercises. This ensures all employees understand their roles in a cybersecurity incident. These drills help find gaps in the plan. They allow organizations to make necessary adjustments.
- After a cybersecurity incident, organizations should review the response. This post-incident review should identify weaknesses in the IRP and suggest improvements. This iterative process enhances preparedness for future incidents.
Promoting a culture of cybersecurity awareness.
- A strong cybersecurity culture is vital. It helps mitigate human error, a major cause of security breaches.
- Training Programs: Organizations should run ongoing cybersecurity training for all employees. It should emphasize best practices, phishing detection, and data protection.
- Simulated Phishing Attacks: They can assess employee awareness and response. These exercises educate employees about phishing tactics. They also promote a proactive approach to cybersecurity.
- Open Communication: Encouraging discussions about cybersecurity can foster a vigilant culture. Employees should feel empowered to report suspicious activity without fear of reprisal.
Complying with regulations and standards.
Compliance with cybersecurity regulations and standards is a legal need. It's also a best practice for risk management.
- Stay Informed: Organizations must keep up with cybersecurity laws. These include the GDPR, CCPA, and PCI DSS. This ensures they know their duties and can apply the needed controls.
- Regular audits: they can help assess compliance and find areas for improvement. This approach cuts penalty risks and boosts security.
- Third-Party Risk Management: Organizations must assess their vendors' cybersecurity practices. A strong vendor risk management program. It ensures partners meet the same cybersecurity standards.
How to obtain PMI-RMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, cybersecurity risk management is vital for organizations. The digital world is now very complex.
Organizations can boost their cybersecurity by:
- Adopting a risk-based approach.
- Using advanced threat detection tech.
- Strengthening incident response plans.
- Fostering a culture of cybersecurity awareness.
- Complying with regulations and standards.
As cyber threats evolve, a proactive approach to cybersecurity is vital. It will protect sensitive data and ensure business integrity. These strategies will guard against today's threats. They will also prepare organizations for future challenges in the fast-changing world of cybersecurity.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Blockchain & Cybersecurity: Advancing Data Protection!!
In today’s digital world, data is one of the most valuable assets. Organizations, governments, and individuals store a lot of sensitive info online. It includes personal identities, financial records, medical data, and intellectual property. This ever-increasing reliance on digital systems has made data security a pressing concern. Traditional cybersecurity measures are critical. But, they are often not enough. They struggle against sophisticated threats from hackers, ransomware, and data breaches.
Enter blockchain technology. Blockchain was made for cryptocurrencies like Bitcoin. Its decentralized, immutable, and transparent nature can revolutionize data security. Blockchain could greatly improve how we secure, store, and share data. It does this by removing the need for centralized authorities and using cryptography.
This blog will explore how blockchain can improve cybersecurity. It will focus on its benefits, real-world uses, and potential challenges. We'll explain the key principles of blockchain. Then, we'll show how they fit with today's cybersecurity needs.
1. How Blockchain Works: A Quick Overview
Before diving into how blockchain boosts cybersecurity, we must know its basics.
At its core, blockchain is a distributed ledger technology (DLT). It records transactions across multiple computers, or nodes. Each block in the chain contains a list of transactions and is cryptographically linked to the previous block, forming a chain of data. Blockchain runs on a decentralized network. No single entity controls the whole system. Instead, the network's ledger is accessible to all participants. This ensures transparency and accountability.
Here are a few key features of blockchain that contribute to its security potential:
Decentralization: Unlike traditional databases, blockchain has no central authority. It spreads data management across multiple nodes. This makes it difficult for hackers to target a single point of failure.
Immutability: Once a block of data is added to the blockchain, it cannot be altered or deleted. This immutability ensures that data is tamper-resistant.
Encryption: Blockchain uses advanced cryptography to secure data. Each transaction or block is encrypted with a hash. This makes it nearly impossible to manipulate the data.
These principles set the stage for blockchain's role in cybersecurity. It offers a powerful alternative to traditional data protection methods.
2. Decentralization: Eliminating Single Points of Failure
A major flaw in conventional cybersecurity systems is their centralized databases and servers. Cybercriminals find centralized systems, like those used by many organizations, appealing targets. Once they access the central server, they can steal or manipulate vast amounts of data. High-profile breaches of large corporations and government databases often result from exploiting these centralized vulnerabilities.
Blockchain, however, operates on a decentralized model. Since the ledger is shared across multiple nodes, there is no single point of failure. An attacker would need to compromise over 50% of the nodes to alter the data. This is both very difficult and very expensive.
This decentralized nature makes blockchain systems more resistant to attacks, like DDoS, and data breaches. They offer a more robust layer of security.
3. Immutability: Ensuring Data Integrity
Data integrity is key to cybersecurity. Blockchain's immutability offers a powerful solution. Once a transaction or piece of data is added to the blockchain, it is virtually impossible to alter or delete. To modify a block, one must alter all subsequent blocks. This is computationally infeasible in large networks. This feature makes blockchain a reliable tool for ensuring that data remains untampered and intact.
Immutability means data can be audited with confidence. The ledger has a permanent, unchangeable record of all transactions. This is vital for finance, healthcare, and legal sectors. In those fields, data integrity is critical.
For instance, in healthcare, accurate and secure patient records are essential. Blockchain can secure patient data and prevent unauthorized changes. This protects both patients and healthcare providers from data breaches and fraud.
4. Encryption and Privacy: Protecting Sensitive Information
While blockchain’s transparency is one of its strengths, it also raises concerns about privacy. Public blockchains let anyone view the data. This is a problem for sensitive information. However, blockchain uses encryption and privacy-preserving techniques to safeguard data without compromising transparency.
Every block on the blockchain is encrypted with a hash. This makes it very hard for unauthorized users to view or change the data. Also, blockchain can use zero-knowledge proofs. One party can prove they know something without revealing the actual information. It keeps sensitive data, such as personal identities and financial transactions, private in a transparent network.
Moreover, blockchain can integrate advanced cryptographic methods, like homomorphic encryption, which allows computations to be performed on encrypted data without decrypting it. This is particularly valuable for industries like finance, where encrypted transactions must be verified without exposing the actual content of the data.
By combining encryption with decentralized control, blockchain creates a secure environment that balances transparency and privacy.
5. Real-World Applications of Blockchain in Cybersecurity
Blockchain’s potential to enhance data security has led to its adoption across various industries. Here are some key areas where blockchain is making an impact:
a) Identity Management
Blockchain can revolutionize digital identity management. It can give people control over their personal information. Traditional identity systems, like those for banking and government, use centralized databases. These are vulnerable to hacks. Blockchain-based identity systems use decentralized identifiers (DIDs). They let individuals control who can access their information and under what conditions.
b) Supply Chain Security
Blockchain is being used to improve the transparency and traceability of supply chains. By recording every transaction on the blockchain, companies can verify products. They can also ensure their supply chains are untampered. It's crucial in industries like pharmaceuticals. Counterfeit drugs can be deadly.
c) Internet of Things (IoT) Security
The rise of IoT devices creates many security risks. Each connected device is now a potential entry point for attackers. Blockchain can secure IoT networks. It does this by creating a decentralized, tamper-proof record of device interactions. It can help prevent unauthorized access. It will keep data, exchanged between devices, secure.
d) Financial Services
In the financial sector, blockchain is being used to enhance security in transactions and reduce fraud. Blockchain can verify transactions. It does so automatically and immutably. This reduces the need for intermediaries and lowers fraud risk. Smart contracts are self-executing contracts. Their terms are written in code. They can streamline secure financial operations.
e) Cybersecurity for Voting Systems
Blockchain technology has been proposed as a way to secure electronic voting systems. Blockchain could securely encrypt and distribute voting records across multiple nodes. This would make it nearly impossible for bad actors to alter the results. This could improve the integrity and trustworthiness of elections, ensuring a tamper-resistant and transparent voting process.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As digital threats continue to evolve, so too must our approach to cybersecurity. Blockchain technology presents a unique and powerful solution to many of the challenges posed by traditional data protection methods. Its decentralized structure, immutability, and advanced encryption techniques make it an attractive option for enhancing data security across industries.
However, blockchain is not without its limitations. The technology is still relatively new and faces scalability challenges, particularly in public blockchains. Additionally, the adoption of blockchain in cybersecurity will require regulatory frameworks and industry standards to ensure its safe and effective use.
Despite these challenges, blockchain’s potential to reshape cybersecurity is undeniable. By eliminating single points of failure, ensuring data integrity, and offering enhanced privacy protections, blockchain can play a critical role in securing the digital world. As more industries explore the use of blockchain for cybersecurity, we can expect to see its role in data protection continue to grow.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today’s digital world, data is one of the most valuable assets. Organizations, governments, and individuals store a lot of sensitive info online. It includes personal identities, financial records, medical data, and intellectual property. This ever-increasing reliance on digital systems has made data security a pressing concern. Traditional cybersecurity measures are critical. But, they are often not enough. They struggle against sophisticated threats from hackers, ransomware, and data breaches.
Enter blockchain technology. Blockchain was made for cryptocurrencies like Bitcoin. Its decentralized, immutable, and transparent nature can revolutionize data security. Blockchain could greatly improve how we secure, store, and share data. It does this by removing the need for centralized authorities and using cryptography.
This blog will explore how blockchain can improve cybersecurity. It will focus on its benefits, real-world uses, and potential challenges. We'll explain the key principles of blockchain. Then, we'll show how they fit with today's cybersecurity needs.
1. How Blockchain Works: A Quick Overview
Before diving into how blockchain boosts cybersecurity, we must know its basics.
At its core, blockchain is a distributed ledger technology (DLT). It records transactions across multiple computers, or nodes. Each block in the chain contains a list of transactions and is cryptographically linked to the previous block, forming a chain of data. Blockchain runs on a decentralized network. No single entity controls the whole system. Instead, the network's ledger is accessible to all participants. This ensures transparency and accountability.
Here are a few key features of blockchain that contribute to its security potential:
Decentralization: Unlike traditional databases, blockchain has no central authority. It spreads data management across multiple nodes. This makes it difficult for hackers to target a single point of failure.
Immutability: Once a block of data is added to the blockchain, it cannot be altered or deleted. This immutability ensures that data is tamper-resistant.
Encryption: Blockchain uses advanced cryptography to secure data. Each transaction or block is encrypted with a hash. This makes it nearly impossible to manipulate the data.
These principles set the stage for blockchain's role in cybersecurity. It offers a powerful alternative to traditional data protection methods.
2. Decentralization: Eliminating Single Points of Failure
A major flaw in conventional cybersecurity systems is their centralized databases and servers. Cybercriminals find centralized systems, like those used by many organizations, appealing targets. Once they access the central server, they can steal or manipulate vast amounts of data. High-profile breaches of large corporations and government databases often result from exploiting these centralized vulnerabilities.
Blockchain, however, operates on a decentralized model. Since the ledger is shared across multiple nodes, there is no single point of failure. An attacker would need to compromise over 50% of the nodes to alter the data. This is both very difficult and very expensive.
This decentralized nature makes blockchain systems more resistant to attacks, like DDoS, and data breaches. They offer a more robust layer of security.
3. Immutability: Ensuring Data Integrity
Data integrity is key to cybersecurity. Blockchain's immutability offers a powerful solution. Once a transaction or piece of data is added to the blockchain, it is virtually impossible to alter or delete. To modify a block, one must alter all subsequent blocks. This is computationally infeasible in large networks. This feature makes blockchain a reliable tool for ensuring that data remains untampered and intact.
Immutability means data can be audited with confidence. The ledger has a permanent, unchangeable record of all transactions. This is vital for finance, healthcare, and legal sectors. In those fields, data integrity is critical.
For instance, in healthcare, accurate and secure patient records are essential. Blockchain can secure patient data and prevent unauthorized changes. This protects both patients and healthcare providers from data breaches and fraud.
4. Encryption and Privacy: Protecting Sensitive Information
While blockchain’s transparency is one of its strengths, it also raises concerns about privacy. Public blockchains let anyone view the data. This is a problem for sensitive information. However, blockchain uses encryption and privacy-preserving techniques to safeguard data without compromising transparency.
Every block on the blockchain is encrypted with a hash. This makes it very hard for unauthorized users to view or change the data. Also, blockchain can use zero-knowledge proofs. One party can prove they know something without revealing the actual information. It keeps sensitive data, such as personal identities and financial transactions, private in a transparent network.
Moreover, blockchain can integrate advanced cryptographic methods, like homomorphic encryption, which allows computations to be performed on encrypted data without decrypting it. This is particularly valuable for industries like finance, where encrypted transactions must be verified without exposing the actual content of the data.
By combining encryption with decentralized control, blockchain creates a secure environment that balances transparency and privacy.
5. Real-World Applications of Blockchain in Cybersecurity
Blockchain’s potential to enhance data security has led to its adoption across various industries. Here are some key areas where blockchain is making an impact:
a) Identity Management
Blockchain can revolutionize digital identity management. It can give people control over their personal information. Traditional identity systems, like those for banking and government, use centralized databases. These are vulnerable to hacks. Blockchain-based identity systems use decentralized identifiers (DIDs). They let individuals control who can access their information and under what conditions.
b) Supply Chain Security
Blockchain is being used to improve the transparency and traceability of supply chains. By recording every transaction on the blockchain, companies can verify products. They can also ensure their supply chains are untampered. It's crucial in industries like pharmaceuticals. Counterfeit drugs can be deadly.
c) Internet of Things (IoT) Security
The rise of IoT devices creates many security risks. Each connected device is now a potential entry point for attackers. Blockchain can secure IoT networks. It does this by creating a decentralized, tamper-proof record of device interactions. It can help prevent unauthorized access. It will keep data, exchanged between devices, secure.
d) Financial Services
In the financial sector, blockchain is being used to enhance security in transactions and reduce fraud. Blockchain can verify transactions. It does so automatically and immutably. This reduces the need for intermediaries and lowers fraud risk. Smart contracts are self-executing contracts. Their terms are written in code. They can streamline secure financial operations.
e) Cybersecurity for Voting Systems
Blockchain technology has been proposed as a way to secure electronic voting systems. Blockchain could securely encrypt and distribute voting records across multiple nodes. This would make it nearly impossible for bad actors to alter the results. This could improve the integrity and trustworthiness of elections, ensuring a tamper-resistant and transparent voting process.
How to obtain Blockchain certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
As digital threats continue to evolve, so too must our approach to cybersecurity. Blockchain technology presents a unique and powerful solution to many of the challenges posed by traditional data protection methods. Its decentralized structure, immutability, and advanced encryption techniques make it an attractive option for enhancing data security across industries.
However, blockchain is not without its limitations. The technology is still relatively new and faces scalability challenges, particularly in public blockchains. Additionally, the adoption of blockchain in cybersecurity will require regulatory frameworks and industry standards to ensure its safe and effective use.
Despite these challenges, blockchain’s potential to reshape cybersecurity is undeniable. By eliminating single points of failure, ensuring data integrity, and offering enhanced privacy protections, blockchain can play a critical role in securing the digital world. As more industries explore the use of blockchain for cybersecurity, we can expect to see its role in data protection continue to grow.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
AI-Driven Java IDEs: Transforming Java Development with AI
In today's fast-paced world of software development, staying ahead of the curve is essential. AI technology is now on the rise. It gives Java developers new tools that can change how they write code. AI-driven Java IDEs are transforming Java development. They add smart features that boost productivity, improve code quality, and streamline the process.
Artificial Intelligence in Java
AI has advanced significantly in recent years. Its integration into Java development tools has opened up new possibilities for developers. AI-driven Java IDEs use AI and machine learning. They can suggest code, analyze it, complete it, and debug it.
Smart Code Suggestions
One of the key features of AI-driven Java IDEs is their ability to provide developers with smart code suggestions as they write code. These suggestions come from machine learning algorithms. They analyze the context of the code being written. Then, they offer tips to improve code quality and efficiency.
Automated Code Analysis
AI-powered Java IDEs can analyze code. They help developers find bugs, errors, or performance issues. By using advanced AI algorithms, these tools can quickly scan codebases and provide instant feedback on code quality, helping developers catch issues early in the development process.
Intelligent Code Completion
Intelligent code completion is another valuable feature of AI-driven Java IDEs. These tools can analyze code in real-time. They can predict what code developers will write next. Then, they suggest ways to complete it automatically. This not only saves time but also helps reduce the likelihood of errors in the code.
Coding Assistance with AI
AI-driven Java IDEs have coding tools to help developers write better code, faster. AI tools are revolutionizing Java development. They range from predictive code generation to automated refactoring.
Predictive Code Generation
Predictive code generation is a feature. It uses machine learning to predict the next code developers will write. AI-driven Java IDEs can analyze patterns in the codebase. They can then suggest completions for code snippets. This makes coding faster and more accurate.
Automated Refactoring Tools
Code refactoring is key in software development. AI-driven Java IDEs provide tools to automate it. They can help developers optimize their codebase. These tools use AI to find code smells, inefficiencies, and redundancies. They suggest refactoring to improve code quality and readability.
AI Algorithm Optimization
AI-driven Java IDEs are also focused on optimizing the use of AI algorithms to enhance the development experience. Improving the IDE's algorithms can help developers. It will speed up code analysis and provide smarter suggestions. They will also get better debugging.
Software Development Revolution
The integration of AI into Java development tools is revolutionizing the way software is built and maintained. AI-driven Java IDEs are using machine learning and neural networks. They are also using cognitive computing. These tools are pushing the limits of software development.
Machine Learning Algorithms in Java
Machine learning algorithms are key to AI-driven Java IDEs. They provide developers with advanced code editing, new IDE features, and a better coding experience. By using machine learning, these tools can learn from developers' code. They will improve their suggestions and help over time.
Neural Networks for Coding
AI-driven Java IDEs use neural networks. They provide smart error detection, code optimization, and development tools for developers. Neural networks can mimic how the human brain processes data. They can help developers navigate complex codebases and make better coding decisions.
Advanced Code Editing Techniques
AI-driven Java IDEs have advanced code editing tools. They can help developers write cleaner, more efficient code. These tools aim to speed up coding and boost productivity. They do this with features like smart code completion and automated code restructuring.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
AI-driven Java IDEs are changing how developers code. They have smart features that boost productivity, improve code quality, and speed up development. These tools are revolutionizing Java development. They provide smart code suggestions, automated analysis, and predictive generation. They are paving the way for a new era of software development. AI can help developers. It can boost coding efficiency, improve code quality, and help them stay ahead in a competitive industry. Try AI-driven IDEs for Java development. They will revolutionize your coding!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced world of software development, staying ahead of the curve is essential. AI technology is now on the rise. It gives Java developers new tools that can change how they write code. AI-driven Java IDEs are transforming Java development. They add smart features that boost productivity, improve code quality, and streamline the process.
Artificial Intelligence in Java
AI has advanced significantly in recent years. Its integration into Java development tools has opened up new possibilities for developers. AI-driven Java IDEs use AI and machine learning. They can suggest code, analyze it, complete it, and debug it.
Smart Code Suggestions
One of the key features of AI-driven Java IDEs is their ability to provide developers with smart code suggestions as they write code. These suggestions come from machine learning algorithms. They analyze the context of the code being written. Then, they offer tips to improve code quality and efficiency.
Automated Code Analysis
AI-powered Java IDEs can analyze code. They help developers find bugs, errors, or performance issues. By using advanced AI algorithms, these tools can quickly scan codebases and provide instant feedback on code quality, helping developers catch issues early in the development process.
Intelligent Code Completion
Intelligent code completion is another valuable feature of AI-driven Java IDEs. These tools can analyze code in real-time. They can predict what code developers will write next. Then, they suggest ways to complete it automatically. This not only saves time but also helps reduce the likelihood of errors in the code.
Coding Assistance with AI
AI-driven Java IDEs have coding tools to help developers write better code, faster. AI tools are revolutionizing Java development. They range from predictive code generation to automated refactoring.
Predictive Code Generation
Predictive code generation is a feature. It uses machine learning to predict the next code developers will write. AI-driven Java IDEs can analyze patterns in the codebase. They can then suggest completions for code snippets. This makes coding faster and more accurate.
Automated Refactoring Tools
Code refactoring is key in software development. AI-driven Java IDEs provide tools to automate it. They can help developers optimize their codebase. These tools use AI to find code smells, inefficiencies, and redundancies. They suggest refactoring to improve code quality and readability.
AI Algorithm Optimization
AI-driven Java IDEs are also focused on optimizing the use of AI algorithms to enhance the development experience. Improving the IDE's algorithms can help developers. It will speed up code analysis and provide smarter suggestions. They will also get better debugging.
Software Development Revolution
The integration of AI into Java development tools is revolutionizing the way software is built and maintained. AI-driven Java IDEs are using machine learning and neural networks. They are also using cognitive computing. These tools are pushing the limits of software development.
Machine Learning Algorithms in Java
Machine learning algorithms are key to AI-driven Java IDEs. They provide developers with advanced code editing, new IDE features, and a better coding experience. By using machine learning, these tools can learn from developers' code. They will improve their suggestions and help over time.
Neural Networks for Coding
AI-driven Java IDEs use neural networks. They provide smart error detection, code optimization, and development tools for developers. Neural networks can mimic how the human brain processes data. They can help developers navigate complex codebases and make better coding decisions.
Advanced Code Editing Techniques
AI-driven Java IDEs have advanced code editing tools. They can help developers write cleaner, more efficient code. These tools aim to speed up coding and boost productivity. They do this with features like smart code completion and automated code restructuring.
How to obtain JAVA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
AI-driven Java IDEs are changing how developers code. They have smart features that boost productivity, improve code quality, and speed up development. These tools are revolutionizing Java development. They provide smart code suggestions, automated analysis, and predictive generation. They are paving the way for a new era of software development. AI can help developers. It can boost coding efficiency, improve code quality, and help them stay ahead in a competitive industry. Try AI-driven IDEs for Java development. They will revolutionize your coding!
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Real-Time Data with MongoDB Change Streams for Developers
In modern software development, the demand for real-time data processing is at an all-time high. Developers must instantly react to changes in their database. They need to trigger actions based on new information. And, their apps must be up-to-date with the latest data. This is where MongoDB Change Streams come in. They give developers a tool for real-time data sync, monitoring, and event-driven apps.
What are MongoDB Change Streams?
MongoDB Change Streams let developers get real-time updates from their database. MongoDB Change Streams capture any change to a document in the database. This includes inserts, updates, or deletes. They then push that change to a specified application in real time. This lets developers respond to changes as they happen. They can then build apps that are always in sync with the database.
MongoDB Change Streams allow developers to listen to changes in collections or databases in real-time. This enables them to build event-driven applications. Change Streams let applications react instantly to database changes. They can respond to inserts, updates, or deletions without polling. This feature is useful for real-time analytics, notifications, and syncing data across systems.
How do MongoDB Change Streams work?
MongoDB Change Streams create an update stream on a specified collection in the database. Then, this update stream can be pipelined through an aggregation pipeline. It lets developers transform the data before sending it to the application. It lets developers customize the data stream for their app. They can filter out certain data, aggregate values, or enrich it with extra info.
MongoDB Change Streams allow developers to listen for real-time changes in collections. This enables event-driven architectures and live applications. They capture changes like inserts, updates, and deletes. They provide a continuous, ordered stream of events. This feature is ideal for live data sync, notifications, or real-time analytics without polling the database.
What are the benefits of using MongoDB Change Streams?
MongoDB Change Streams give real-time updates on database changes. They let developers build responsive, event-driven apps. This feature syncs data across microservices or external systems. It improves workflows that need up-to-the-minute data. Also, Change Streams support scalability. They process data changes with low resource use. So, they are ideal for large-scale apps.
-
Real-time processing: MongoDB Change Streams let developers react to database changes instantly. This helps them build apps that are always up-to-date.
-
Scalable architecture: MongoDB Change Streams let developers easily scale their real-time data as their app grows.
-
Push notifications: Developers can use MongoDB Change Streams to trigger actions, such as sending push notifications to users, based on changes in the database.
-
Data-driven decision-making: Using MongoDB Change Streams, developers can build apps that use the latest, most accurate data.
-
MongoDB Change Streams offer an efficient way to sync data. They can sync data between different parts of an app or between services.
How can developers implement MongoDB Change Streams in their application?
To use MongoDB Change Streams, developers must first set up a change event listener on a collection in their database. This listener will receive change events as they occur, allowing developers to react to them in real time. Developers can use these change events to trigger functions, update the UI, send notifications, or take other actions based on the new data.
Developers can use MongoDB Change Streams by connecting to a MongoDB collection. They can then use the `watch()` method to track real-time changes in the database. Change Streams let apps listen for insertions, updates, and deletions. They are perfect for real-time analytics, notifications, and event-driven architectures. By integrating these streams, developers can instantly respond to data changes. They won't need to poll the database.
How to obtain Mongo DB Developer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, MongoDB Change Streams are a powerful tool. They help developers build real-time, data-driven apps. Using MongoDB Change Streams, developers can create always-up-to-date, responsive apps. They can handle many use cases. MongoDB Change Streams can help you. Use them for a dashboard, a decision tool, or a real-time analytics platform.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In modern software development, the demand for real-time data processing is at an all-time high. Developers must instantly react to changes in their database. They need to trigger actions based on new information. And, their apps must be up-to-date with the latest data. This is where MongoDB Change Streams come in. They give developers a tool for real-time data sync, monitoring, and event-driven apps.
What are MongoDB Change Streams?
MongoDB Change Streams let developers get real-time updates from their database. MongoDB Change Streams capture any change to a document in the database. This includes inserts, updates, or deletes. They then push that change to a specified application in real time. This lets developers respond to changes as they happen. They can then build apps that are always in sync with the database.
MongoDB Change Streams allow developers to listen to changes in collections or databases in real-time. This enables them to build event-driven applications. Change Streams let applications react instantly to database changes. They can respond to inserts, updates, or deletions without polling. This feature is useful for real-time analytics, notifications, and syncing data across systems.
How do MongoDB Change Streams work?
MongoDB Change Streams create an update stream on a specified collection in the database. Then, this update stream can be pipelined through an aggregation pipeline. It lets developers transform the data before sending it to the application. It lets developers customize the data stream for their app. They can filter out certain data, aggregate values, or enrich it with extra info.
MongoDB Change Streams allow developers to listen for real-time changes in collections. This enables event-driven architectures and live applications. They capture changes like inserts, updates, and deletes. They provide a continuous, ordered stream of events. This feature is ideal for live data sync, notifications, or real-time analytics without polling the database.
What are the benefits of using MongoDB Change Streams?
MongoDB Change Streams give real-time updates on database changes. They let developers build responsive, event-driven apps. This feature syncs data across microservices or external systems. It improves workflows that need up-to-the-minute data. Also, Change Streams support scalability. They process data changes with low resource use. So, they are ideal for large-scale apps.
-
Real-time processing: MongoDB Change Streams let developers react to database changes instantly. This helps them build apps that are always up-to-date.
-
Scalable architecture: MongoDB Change Streams let developers easily scale their real-time data as their app grows.
-
Push notifications: Developers can use MongoDB Change Streams to trigger actions, such as sending push notifications to users, based on changes in the database.
-
Data-driven decision-making: Using MongoDB Change Streams, developers can build apps that use the latest, most accurate data.
-
MongoDB Change Streams offer an efficient way to sync data. They can sync data between different parts of an app or between services.
How can developers implement MongoDB Change Streams in their application?
To use MongoDB Change Streams, developers must first set up a change event listener on a collection in their database. This listener will receive change events as they occur, allowing developers to react to them in real time. Developers can use these change events to trigger functions, update the UI, send notifications, or take other actions based on the new data.
Developers can use MongoDB Change Streams by connecting to a MongoDB collection. They can then use the `watch()` method to track real-time changes in the database. Change Streams let apps listen for insertions, updates, and deletions. They are perfect for real-time analytics, notifications, and event-driven architectures. By integrating these streams, developers can instantly respond to data changes. They won't need to poll the database.
How to obtain Mongo DB Developer certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, MongoDB Change Streams are a powerful tool. They help developers build real-time, data-driven apps. Using MongoDB Change Streams, developers can create always-up-to-date, responsive apps. They can handle many use cases. MongoDB Change Streams can help you. Use them for a dashboard, a decision tool, or a real-time analytics platform.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Top Tips for Salesforce Sandbox Development and Testing
Are you looking to streamline your Salesforce development and testing process? Look no further! This guide will give you expert tips. They will improve your Salesforce sandbox development and testing.
Introduction to Salesforce Sandbox Development
Salesforce sandbox is a cloud-based dev environment by Salesforce. It lets users customize, configure, deploy, and test their apps before production. It lets developers work on their projects without affecting the live site. This ensures a smooth deployment process.
Best Practices for Salesforce Sandbox Development and Testing
1. Customize and Configure with Precision
In a Salesforce sandbox, customize and configure your apps with precision. Define your objects, fields, and relationships carefully to avoid any issues during deployment.
2. Leverage Automation Tools
Use tools like Apex, Visualforce, and Lightning Web Components. They will automate repetitive tasks and streamline your development process. Automation not only saves time but also reduces the risk of errors.
Leveraging automation tools can significantly enhance productivity and streamline business processes. Automating repetitive tasks frees up time. Employees can then focus on more strategic work. Also, automation tools can improve accuracy and consistency. This leads to better decision-making and efficiency.
3. Maintain Version Control
Keep track of your metadata changes by maintaining version control. Use tools like Git to track changes, collaborate, and revert to earlier versions if needed.
Version control is crucial for managing changes in software and documents. Version control systems like Git help teams. They can track changes, collaborate, and easily revert to earlier versions if needed. It boosts transparency, accountability, and efficiency. This allows smoother workflows and reduces errors.
4. Ensure Security and Permissions
Pay close attention to security settings, roles, and profiles in your sandbox environment. Set up validation rules, workflows, and process builder flows. They will enforce data integrity and ensure security compliance.
Security and permissions in Salesforce are vital. They protect sensitive customer data and ensure compliance with regulations. Salesforce has strong security features, like role-based access controls. Organizations can use them to limit user access to data. This matches access to individual responsibilities and minimizes data exposure. Regularly reviewing and updating security settings boosts data integrity. It also fosters a culture of accountability in the organization.
5. Optimize Performance
To enhance performance, regularly monitor and optimize your code. Watch governor limits. Debug code carefully. Aim for 100% coverage in your test classes.
To optimize performance in Salesforce, regularly monitor and analyze system metrics. This will help identify areas that may need improvements. Best practices can boost app responsiveness. They include: reduce data complexity, streamline workflows, and leverage custom indexes. Also, using Salesforce's built-in optimization tools can help. They ensure your CRM runs efficiently and provides a seamless user experience.
6. Refresh Sandboxes Regularly
To keep your sandbox environments up to date, perform regular sandbox refreshes. This will ensure that your dev and test environments mirror production.
Refreshing sandboxes regularly is essential for maintaining an up-to-date and accurate testing environment. This will ensure developers and testers use the latest data and configs. It will minimize differences between production and sandbox instances. It improves development and testing. It also finds issues before they affect users.
7. Conduct Comprehensive Testing
Before deploying to production, conduct thorough testing in your sandbox environment. Test your apps. Use unit, functional, regression, and user acceptance tests.
Thorough testing is key. It ensures software works and is reliable. By evaluating all aspects of the system, organizations can find issues before deployment. They should check its performance, security, and usability. This approach boosts user satisfaction and prevents costly fixes. It leads to a more successful, robust product.
8. Embrace Continuous Integration and Deployment
Use continuous integration and deployment to automate the deployment process. This will ensure a smooth transition of changes from development to production.
9. Document and Share Knowledge
Document your development process. Share best practices with your team. Use project management and collaboration tools to collaborate effectively. Knowledge sharing is key to a successful Salesforce development team.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce sandbox development and testing are vital to the dev lifecycle.
By following these tips, you can:
-
Optimize your development process.
-
Streamline testing.
-
Ensure successful production deployments.
Use the tools in the Salesforce ecosystem. They will boost your development and drive innovation in your organization.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Are you looking to streamline your Salesforce development and testing process? Look no further! This guide will give you expert tips. They will improve your Salesforce sandbox development and testing.
Introduction to Salesforce Sandbox Development
Salesforce sandbox is a cloud-based dev environment by Salesforce. It lets users customize, configure, deploy, and test their apps before production. It lets developers work on their projects without affecting the live site. This ensures a smooth deployment process.
Best Practices for Salesforce Sandbox Development and Testing
1. Customize and Configure with Precision
In a Salesforce sandbox, customize and configure your apps with precision. Define your objects, fields, and relationships carefully to avoid any issues during deployment.
2. Leverage Automation Tools
Use tools like Apex, Visualforce, and Lightning Web Components. They will automate repetitive tasks and streamline your development process. Automation not only saves time but also reduces the risk of errors.
Leveraging automation tools can significantly enhance productivity and streamline business processes. Automating repetitive tasks frees up time. Employees can then focus on more strategic work. Also, automation tools can improve accuracy and consistency. This leads to better decision-making and efficiency.
3. Maintain Version Control
Keep track of your metadata changes by maintaining version control. Use tools like Git to track changes, collaborate, and revert to earlier versions if needed.
Version control is crucial for managing changes in software and documents. Version control systems like Git help teams. They can track changes, collaborate, and easily revert to earlier versions if needed. It boosts transparency, accountability, and efficiency. This allows smoother workflows and reduces errors.
4. Ensure Security and Permissions
Pay close attention to security settings, roles, and profiles in your sandbox environment. Set up validation rules, workflows, and process builder flows. They will enforce data integrity and ensure security compliance.
Security and permissions in Salesforce are vital. They protect sensitive customer data and ensure compliance with regulations. Salesforce has strong security features, like role-based access controls. Organizations can use them to limit user access to data. This matches access to individual responsibilities and minimizes data exposure. Regularly reviewing and updating security settings boosts data integrity. It also fosters a culture of accountability in the organization.
5. Optimize Performance
To enhance performance, regularly monitor and optimize your code. Watch governor limits. Debug code carefully. Aim for 100% coverage in your test classes.
To optimize performance in Salesforce, regularly monitor and analyze system metrics. This will help identify areas that may need improvements. Best practices can boost app responsiveness. They include: reduce data complexity, streamline workflows, and leverage custom indexes. Also, using Salesforce's built-in optimization tools can help. They ensure your CRM runs efficiently and provides a seamless user experience.
6. Refresh Sandboxes Regularly
To keep your sandbox environments up to date, perform regular sandbox refreshes. This will ensure that your dev and test environments mirror production.
Refreshing sandboxes regularly is essential for maintaining an up-to-date and accurate testing environment. This will ensure developers and testers use the latest data and configs. It will minimize differences between production and sandbox instances. It improves development and testing. It also finds issues before they affect users.
7. Conduct Comprehensive Testing
Before deploying to production, conduct thorough testing in your sandbox environment. Test your apps. Use unit, functional, regression, and user acceptance tests.
Thorough testing is key. It ensures software works and is reliable. By evaluating all aspects of the system, organizations can find issues before deployment. They should check its performance, security, and usability. This approach boosts user satisfaction and prevents costly fixes. It leads to a more successful, robust product.
8. Embrace Continuous Integration and Deployment
Use continuous integration and deployment to automate the deployment process. This will ensure a smooth transition of changes from development to production.
9. Document and Share Knowledge
Document your development process. Share best practices with your team. Use project management and collaboration tools to collaborate effectively. Knowledge sharing is key to a successful Salesforce development team.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, Salesforce sandbox development and testing are vital to the dev lifecycle.
By following these tips, you can:
-
Optimize your development process.
-
Streamline testing.
-
Ensure successful production deployments.
Use the tools in the Salesforce ecosystem. They will boost your development and drive innovation in your organization.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Hadoop vs Spark: Which Big Data Tool is Right for You ?
As big data grows, organizations are relying more on tools like Hadoop and Spark to process it. Both are open-source frameworks under the Apache Software Foundation. They are vital for managing and analyzing large datasets. However, they share similar goals. But, Hadoop and Spark differ in their architecture, speed, cost, and use cases. It depends on your needs and tech environment. Also, consider your big data projects.
This article will compare the key features of Hadoop and Spark. It will help you choose the best tool for your data processing needs.
Table Of Contents
- Overview of Hadoop
- Overview of Spark
- Speed and Performance Comparison
- Use Cases for Hadoop
- Use Cases for Spark
- Conclusion
Overview of Hadoop
What is Hadoop? : Hadoop is a framework for distributed computing. It uses simple programming models to store and process large datasets on a computer cluster. Its core components include:
- HDFS (Hadoop Distributed File System) splits data into blocks. It distributes the blocks across nodes.
- MapReduce: A programming model that processes and generates large datasets. It breaks tasks into smaller subtasks. These are processed in parallel across clusters.
- YARN (Yet Another Resource Negotiator): A resource management tool in Hadoop. It ensures efficient use of system resources.
Pros of Hadoop:
- Scalability: Hadoop can handle large datasets by scaling horizontally across clusters.
- Cost-effective: Hadoop is an open-source tool. It can run on cheap hardware, lowering costs.
- Fault tolerance: HDFS keeps multiple copies of data on different nodes. This protects against hardware failures.
Cons of Hadoop:
- Slower processing speed: Hadoop's disk storage and MapReduce's batch model make it slower than in-memory systems.
- Complexity: Hadoop's steep learning curve can be challenging for beginners.
Overview of Spark
What is Spark? : Spark is a high-performance, real-time processing framework that enhances Hadoop’s capabilities. Unlike Hadoop's disk-based approach, Spark runs in-memory. This allows for faster processing of large datasets.
Key Features of Spark:
- In-memory computing: Spark processes data in-memory. This is much faster than Hadoop's disk-based operations.
- General-purpose: Spark supports batch processing, real-time streaming, machine learning, and graph processing.
- Compatibility with Hadoop: Spark can run on HDFS. It uses Hadoop's distributed storage.
Pros of Spark:
- Speed: Spark can process data up to 100 times faster than Hadoop due to its in-memory architecture.
- Versatility: Spark is not limited to batch processing. It supports streaming, SQL queries, and machine learning.
- User-friendly APIs: Spark's APIs are in multiple languages (Java, Python, Scala, and R). This makes them more accessible for developers.
Cons of Spark:
- Memory use: Spark's in-memory processing can be costly for large datasets.
- Requires Hadoop for storage: Spark has no built-in storage. Users must implement Hadoop's HDFS or similar solutions.
Speed and Performance Comparison
One of the most significant differences between Hadoop and Spark is performance. Hadoop's MapReduce framework writes intermediate data to disk during processing. This can slow performance, especially for iterative tasks. For instance, Hadoop causes latency in machine learning algorithms that need repetitive tasks.
In contrast, Spark computes in-memory. This greatly speeds up iterative tasks. Spark's in-memory processing cuts disk I/O. It's great for real-time analytics and interactive queries. It also suits complex workflows.
However, Spark’s speed advantage comes at the cost of higher memory usage. If your system has limited RAM, use Hadoop for some batch tasks that don't need fast processing.
Use Cases for Hadoop
Hadoop is great for large-scale batch processing, especially on a budget. Its ability to run on commodity hardware makes it ideal for:
- Data archival and historical analysis: Hadoop is great for storing and analyzing large datasets. It's best when real-time processing isn't needed.
- ETL (Extract, Transform, Load) processes: Hadoop's MapReduce is great for bulk ETL jobs.
- Low-cost data warehousing: Hadoop lets organizations store massive datasets cheaply. They can then analyze them with tools like Hive and Pig.
When speed is not a priority, use Hadoop. It is best for reliable, long-term storage and batch processing.
Use Cases for Spark
Spark shines in scenarios where performance, real-time processing, and versatility are crucial. Its speed and broad functionality make it ideal for:
- Real-time data analytics: Spark Streaming lets users analyze data in real time. It's perfect for monitoring apps, fraud detection, and recommendation engines.
- Machine learning: Spark has built-in libraries like MLlib. They simplify implementing machine learning algorithms. So, Spark is popular for AI and predictive analytics.
- Interactive querying: Spark's speed is ideal for real-time data exploration and ad-hoc queries.
Spark can handle batch tasks. Its true strength is in real-time analytics and iterative machine learning. It's best for apps that need quick feedback.
How to obtain BigData certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, It depends on your big data needs. Choose between Hadoop and Spark. Hadoop is better for cost-effective, large-scale batch jobs when speed isn't critical. Its reliable, fault-tolerant, scalable storage is great for archiving data and analyzing history.
Spark, however, excels in tasks needing speed and real-time processing. Its versatility is also a plus. For real-time analytics, machine learning, or interactive querying, use Spark. Its in-memory computing and broad features will greatly outperform Hadoop.
In some cases, a mix of the two can be best. Use Hadoop for storage, and Spark for real-time processing. By evaluating your data needs, tech, and budget, you can decide. This will optimize your big data projects.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As big data grows, organizations are relying more on tools like Hadoop and Spark to process it. Both are open-source frameworks under the Apache Software Foundation. They are vital for managing and analyzing large datasets. However, they share similar goals. But, Hadoop and Spark differ in their architecture, speed, cost, and use cases. It depends on your needs and tech environment. Also, consider your big data projects.
This article will compare the key features of Hadoop and Spark. It will help you choose the best tool for your data processing needs.
Table Of Contents
- Overview of Hadoop
- Overview of Spark
- Speed and Performance Comparison
- Use Cases for Hadoop
- Use Cases for Spark
- Conclusion
Overview of Hadoop
What is Hadoop? : Hadoop is a framework for distributed computing. It uses simple programming models to store and process large datasets on a computer cluster. Its core components include:
- HDFS (Hadoop Distributed File System) splits data into blocks. It distributes the blocks across nodes.
- MapReduce: A programming model that processes and generates large datasets. It breaks tasks into smaller subtasks. These are processed in parallel across clusters.
- YARN (Yet Another Resource Negotiator): A resource management tool in Hadoop. It ensures efficient use of system resources.
Pros of Hadoop:
- Scalability: Hadoop can handle large datasets by scaling horizontally across clusters.
- Cost-effective: Hadoop is an open-source tool. It can run on cheap hardware, lowering costs.
- Fault tolerance: HDFS keeps multiple copies of data on different nodes. This protects against hardware failures.
Cons of Hadoop:
- Slower processing speed: Hadoop's disk storage and MapReduce's batch model make it slower than in-memory systems.
- Complexity: Hadoop's steep learning curve can be challenging for beginners.
Overview of Spark
What is Spark? : Spark is a high-performance, real-time processing framework that enhances Hadoop’s capabilities. Unlike Hadoop's disk-based approach, Spark runs in-memory. This allows for faster processing of large datasets.
Key Features of Spark:
- In-memory computing: Spark processes data in-memory. This is much faster than Hadoop's disk-based operations.
- General-purpose: Spark supports batch processing, real-time streaming, machine learning, and graph processing.
- Compatibility with Hadoop: Spark can run on HDFS. It uses Hadoop's distributed storage.
Pros of Spark:
- Speed: Spark can process data up to 100 times faster than Hadoop due to its in-memory architecture.
- Versatility: Spark is not limited to batch processing. It supports streaming, SQL queries, and machine learning.
- User-friendly APIs: Spark's APIs are in multiple languages (Java, Python, Scala, and R). This makes them more accessible for developers.
Cons of Spark:
- Memory use: Spark's in-memory processing can be costly for large datasets.
- Requires Hadoop for storage: Spark has no built-in storage. Users must implement Hadoop's HDFS or similar solutions.
Speed and Performance Comparison
One of the most significant differences between Hadoop and Spark is performance. Hadoop's MapReduce framework writes intermediate data to disk during processing. This can slow performance, especially for iterative tasks. For instance, Hadoop causes latency in machine learning algorithms that need repetitive tasks.
In contrast, Spark computes in-memory. This greatly speeds up iterative tasks. Spark's in-memory processing cuts disk I/O. It's great for real-time analytics and interactive queries. It also suits complex workflows.
However, Spark’s speed advantage comes at the cost of higher memory usage. If your system has limited RAM, use Hadoop for some batch tasks that don't need fast processing.
Use Cases for Hadoop
Hadoop is great for large-scale batch processing, especially on a budget. Its ability to run on commodity hardware makes it ideal for:
- Data archival and historical analysis: Hadoop is great for storing and analyzing large datasets. It's best when real-time processing isn't needed.
- ETL (Extract, Transform, Load) processes: Hadoop's MapReduce is great for bulk ETL jobs.
- Low-cost data warehousing: Hadoop lets organizations store massive datasets cheaply. They can then analyze them with tools like Hive and Pig.
When speed is not a priority, use Hadoop. It is best for reliable, long-term storage and batch processing.
Use Cases for Spark
Spark shines in scenarios where performance, real-time processing, and versatility are crucial. Its speed and broad functionality make it ideal for:
- Real-time data analytics: Spark Streaming lets users analyze data in real time. It's perfect for monitoring apps, fraud detection, and recommendation engines.
- Machine learning: Spark has built-in libraries like MLlib. They simplify implementing machine learning algorithms. So, Spark is popular for AI and predictive analytics.
- Interactive querying: Spark's speed is ideal for real-time data exploration and ad-hoc queries.
Spark can handle batch tasks. Its true strength is in real-time analytics and iterative machine learning. It's best for apps that need quick feedback.
How to obtain BigData certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, It depends on your big data needs. Choose between Hadoop and Spark. Hadoop is better for cost-effective, large-scale batch jobs when speed isn't critical. Its reliable, fault-tolerant, scalable storage is great for archiving data and analyzing history.
Spark, however, excels in tasks needing speed and real-time processing. Its versatility is also a plus. For real-time analytics, machine learning, or interactive querying, use Spark. Its in-memory computing and broad features will greatly outperform Hadoop.
In some cases, a mix of the two can be best. Use Hadoop for storage, and Spark for real-time processing. By evaluating your data needs, tech, and budget, you can decide. This will optimize your big data projects.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Networking Automation and CCNP Role in DevOps Success!!
In today's fast-paced tech world, networking automation is key to IT strategies. Organizations using DevOps to improve software development must automate systems and manage networks. The CCNP certification from Cisco is for networking pros. It teaches them to install and manage complex networks in a DevOps environment. This article explores the link between networking automation and the CCNP certification. It shows how networking pros can use these tools to innovate and boost efficiency.
Table Of Contents
- The Rise of Networking Automation
- The CCNP Certification Overview
- Networking Automation Tools and Technologies
- The Role of CCNP in a DevOps Environment
- Challenges and Future Directions in Networking Automation
- Conclusion
The Rise of Networking Automation
Networking automation is the use of software to automate network tasks. These include configuration, management, and operations. It's impossible to take out the adverb. Networking automation offers several advantages, including:
- Increased Efficiency: Automation reduces errors and speeds up network setup. It cuts deployment and management time.
- Enhanced Scalability: As organizations grow, so do their network requirements. Automation allows for seamless scaling of network resources without significant manual intervention.
- Improved Agility: Automated networks can adapt to changes with speed. This allows organizations to respond with agility to market demands and technological advances.
The CCNP Certification Overview
The CCNP certification is a professional-level credential from Cisco. It proves one's skills in planning, testing, and fixing networks. The certification covers various areas, including:
- Routing and Switching: Set up routers and switches for top performance and security.
- Wireless Networking: Install wireless solutions that integrate with the existing network.
- Security: Ensuring network security through appropriate policies and technologies.
- Automation and Programmability: A focus on network automation tools. It emphasizes the use of software to automate networking tasks.
The CCNP certification is vital for networking professionals. It helps them stay relevant in a fast-changing tech world.
Networking Automation Tools and Technologies
To use networking automation well, professionals must know various tools and technologies.
- Ansible serves as an open-source automation tool that facilitates straightforward configuration management and application deployment. You can use Ansible's playbooks to automate network device configurations and updates.
- Python: A versatile programming language. It is a common tool for scripting and automating network tasks. Many network engineers use Python to interact with devices through APIs.
- Cisco DNA Center: A platform to manage Cisco devices. It automates, assures, and analyzes them. It allows network teams to automate policy enforcement and optimize network performance.
- NetDevOps: A mix of DevOps and networking. Its goal is to enhance teamwork between development and operations departments. The goal is to deliver network services with greater efficiency.
CCNP-certified professionals must know these tools and their uses. They need to integrate automation into their networking practices.
The Role of CCNP in a DevOps Environment
DevOps teams must include CCNP-certified professionals. They are key to automating networking processes. Here are some key roles that CCNP professionals play in a DevOps environment:
- Collaboration with Development Teams: CCNP-certified pros link networking and development teams. They ensure that network configurations match app requirements.
- Infrastructure as Code (IaC): With its rise, CCNP pros now use automation tools to code networks. This allows for faster deployments and easier version control.
- CCNP-certified individuals prove expertise in using monitoring tools. They ensure that network performance meets the demands of automated apps. They also identify and fix issues before they escalate.
- Security Integration: DevOps promotes a "shift-left" approach to security. CCNP pros help by using network security measures to protect apps during development.
CCNP professionals can help their organization by knowing a DevOps environment's unique demands.
Challenges and Future Directions in Networking Automation
Despite its many benefits, networking automation also presents challenges that professionals must address.
- Skill Gaps: Many networking pros may lack the needed programming and automation skills. Continuous education and certification, such as CCNP, can help bridge these gaps.
- Integrating automation tools with existing networks can be complex. It requires careful planning and execution.
- Security Concerns: Automating network processes raises security risks. If someone does not manage them, they can exploit vulnerabilities. CCNP professionals must rank security in their automation strategies.
Looking ahead, the future of networking automation is bright. As AI and ML technologies advance, networking automation will improve. It will allow for smarter, more proactive network management.
How to obtain CCNP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Networking automation is changing IT and network management. It's vital for organizations to adopt these practices to stay competitive. The CCNP certification is vital. It gives networking pros the skills to succeed in a changing world. CCNP-certified individuals can improve network efficiency, scalability, and security. They can do this by using automation tools and collaborating in DevOps teams. As the industry evolves, networking pros must keep up with new trends and tech. This will keep them at the forefront of this exciting journey.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced tech world, networking automation is key to IT strategies. Organizations using DevOps to improve software development must automate systems and manage networks. The CCNP certification from Cisco is for networking pros. It teaches them to install and manage complex networks in a DevOps environment. This article explores the link between networking automation and the CCNP certification. It shows how networking pros can use these tools to innovate and boost efficiency.
Table Of Contents
- The Rise of Networking Automation
- The CCNP Certification Overview
- Networking Automation Tools and Technologies
- The Role of CCNP in a DevOps Environment
- Challenges and Future Directions in Networking Automation
- Conclusion
The Rise of Networking Automation
Networking automation is the use of software to automate network tasks. These include configuration, management, and operations. It's impossible to take out the adverb. Networking automation offers several advantages, including:
- Increased Efficiency: Automation reduces errors and speeds up network setup. It cuts deployment and management time.
- Enhanced Scalability: As organizations grow, so do their network requirements. Automation allows for seamless scaling of network resources without significant manual intervention.
- Improved Agility: Automated networks can adapt to changes with speed. This allows organizations to respond with agility to market demands and technological advances.
The CCNP Certification Overview
The CCNP certification is a professional-level credential from Cisco. It proves one's skills in planning, testing, and fixing networks. The certification covers various areas, including:
- Routing and Switching: Set up routers and switches for top performance and security.
- Wireless Networking: Install wireless solutions that integrate with the existing network.
- Security: Ensuring network security through appropriate policies and technologies.
- Automation and Programmability: A focus on network automation tools. It emphasizes the use of software to automate networking tasks.
The CCNP certification is vital for networking professionals. It helps them stay relevant in a fast-changing tech world.
Networking Automation Tools and Technologies
To use networking automation well, professionals must know various tools and technologies.
- Ansible serves as an open-source automation tool that facilitates straightforward configuration management and application deployment. You can use Ansible's playbooks to automate network device configurations and updates.
- Python: A versatile programming language. It is a common tool for scripting and automating network tasks. Many network engineers use Python to interact with devices through APIs.
- Cisco DNA Center: A platform to manage Cisco devices. It automates, assures, and analyzes them. It allows network teams to automate policy enforcement and optimize network performance.
- NetDevOps: A mix of DevOps and networking. Its goal is to enhance teamwork between development and operations departments. The goal is to deliver network services with greater efficiency.
CCNP-certified professionals must know these tools and their uses. They need to integrate automation into their networking practices.
The Role of CCNP in a DevOps Environment
DevOps teams must include CCNP-certified professionals. They are key to automating networking processes. Here are some key roles that CCNP professionals play in a DevOps environment:
- Collaboration with Development Teams: CCNP-certified pros link networking and development teams. They ensure that network configurations match app requirements.
- Infrastructure as Code (IaC): With its rise, CCNP pros now use automation tools to code networks. This allows for faster deployments and easier version control.
- CCNP-certified individuals prove expertise in using monitoring tools. They ensure that network performance meets the demands of automated apps. They also identify and fix issues before they escalate.
- Security Integration: DevOps promotes a "shift-left" approach to security. CCNP pros help by using network security measures to protect apps during development.
CCNP professionals can help their organization by knowing a DevOps environment's unique demands.
Challenges and Future Directions in Networking Automation
Despite its many benefits, networking automation also presents challenges that professionals must address.
- Skill Gaps: Many networking pros may lack the needed programming and automation skills. Continuous education and certification, such as CCNP, can help bridge these gaps.
- Integrating automation tools with existing networks can be complex. It requires careful planning and execution.
- Security Concerns: Automating network processes raises security risks. If someone does not manage them, they can exploit vulnerabilities. CCNP professionals must rank security in their automation strategies.
Looking ahead, the future of networking automation is bright. As AI and ML technologies advance, networking automation will improve. It will allow for smarter, more proactive network management.
How to obtain CCNP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Networking automation is changing IT and network management. It's vital for organizations to adopt these practices to stay competitive. The CCNP certification is vital. It gives networking pros the skills to succeed in a changing world. CCNP-certified individuals can improve network efficiency, scalability, and security. They can do this by using automation tools and collaborating in DevOps teams. As the industry evolves, networking pros must keep up with new trends and tech. This will keep them at the forefront of this exciting journey.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
The Role of MongoDB in AI and Machine Learning Projects
In the age of AI and ML, data management is vital for success. AI and ML rely on vast, varied, and changing data to train models, make predictions, and decide. This has created a need for databases. They must handle complex data with flexibility and scalability. MongoDB, a NoSQL database, is popular in AI and ML. It can store unstructured data, manage large datasets, and support fast analytics. This article will explore how MongoDB aids AI and ML projects. It will also explain why many developers and data scientists prefer it.
Table Of Contents
- Flexible Data Models and Unstructured Data Management
- Scalability and Performance in Handling Big Data
- Seamless Integration with AI and ML Ecosystems
- Support for Real-Time Data Processing
- Efficient Handling of Large-Scale Model Training Data
- Conclusion
Flexible Data Models and Unstructured Data Management
MongoDB's main edge in AI and ML is its ability to handle unstructured or semi-structured data. MongoDB uses a document-based model, unlike traditional relational databases. They require a strict schema. MongoDB's model allows it to store data in a flexible, JSON-like format. It is ideal for storing data, like text, images, videos, and sensor data. It's commonly used in AI and ML.
- Handling Unstructured Data: In AI and ML, datasets often come from diverse sources, like social media, IoT devices, and APIs. MongoDB's schema-less design allows easy integration of these varied data sources. It does not require conforming to rigid structures.
- Support for JSON-like Documents: MongoDB stores data as BSON (Binary JSON). It can represent rich data types. This flexibility lets MongoDB meet changing AI and ML data needs. It avoids complex migration processes.
Scalability and Performance in Handling Big Data
Scalability is crucial in AI and ML projects. They process vast amounts of data to train and evaluate models. MongoDB's sharding allows for horizontal scalability. As data grows, the database can scale.
- Horizontal Scaling: MongoDB can distribute data across multiple servers by sharding. AI models can scale seamlessly. They can handle the growing data demands of training and predictions.
- High-Performance Analytics: AI and ML often require real-time data processing. MongoDB's architecture allows low-latency reads and writes. This is vital for the constant ingestion and processing of large datasets. The database also supports in-memory storage. This boosts performance for tasks that need fast data access.
Seamless Integration with AI and ML Ecosystems
MongoDB works well with many tools and frameworks used in AI and ML projects. This makes it a great choice for developers and data scientists.
- Python and Machine Learning Libraries: MongoDB has strong integration with Python. It is a popular language in AI and ML. Popular machine learning libraries, like TensorFlow and PyTorch, can easily connect to MongoDB to fetch and store data.
- Integration with Data Pipelines: MongoDB can connect to data pipelines using tools like Apache Kafka, Spark, and Hadoop. These are often used in AI and ML workflows. This integration allows for the smooth transfer of large datasets across the pipeline.
- MongoDB Atlas: It is a fully managed database for cloud-based AI and ML projects. It has automated backups, scaling, and monitoring. This lets teams build models without worrying about database management.
Support for Real-Time Data Processing
Many AI and ML apps need real-time data processing. This is vital for fraud detection, recommendation engines, and self-driving cars. MongoDB’s ability to handle real-time data is a major benefit for these use cases.
- Real-Time Analytics: MongoDB's indexing and aggregation enable fast, real-time analytics. It's great for AI apps that need instant insights, like personalized recommendations and dynamic pricing.
- Streaming Data Support: For AI systems that rely on live data streams, like IoT data or social media feeds, MongoDB supports real-time data ingestion and processing. This ensures that AI algorithms always have access to the latest data.
Efficient Handling of Large-Scale Model Training Data
Training AI models requires access to vast amounts of historical and real-time data. MongoDB is great for storing and retrieving large datasets. They are used to train complex machine learning models.
- MongoDB's document-based structure is optimized for fast, efficient storage of large datasets. This is important for training AI models that rely on large datasets, such as deep learning and natural language processing models.
- Versioning and Auditing of Training Data: MongoDB allows easy version control of training data. It lets teams track changes over time. This is crucial for reproducibility in AI and ML experiments. It ensures that models can be retrained or improved using consistent data.
How to obtain MongoDB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As AI and machine learning projects grow, we need fast, scalable data storage. MongoDB can handle unstructured data and scale horizontally. It integrates with popular AI tools and supports real-time analytics. These features make it essential for many AI and ML projects. Using MongoDB, teams can meet AI models' growing data needs. It keeps performance and flexibility. MongoDB is key to AI and ML success. It allows real-time data processing, large model training, and easy integration with ML libraries.
AI and ML professionals should use MongoDB. It gives an edge in complex data projects. This can help build better AIs.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the age of AI and ML, data management is vital for success. AI and ML rely on vast, varied, and changing data to train models, make predictions, and decide. This has created a need for databases. They must handle complex data with flexibility and scalability. MongoDB, a NoSQL database, is popular in AI and ML. It can store unstructured data, manage large datasets, and support fast analytics. This article will explore how MongoDB aids AI and ML projects. It will also explain why many developers and data scientists prefer it.
Table Of Contents
- Flexible Data Models and Unstructured Data Management
- Scalability and Performance in Handling Big Data
- Seamless Integration with AI and ML Ecosystems
- Support for Real-Time Data Processing
- Efficient Handling of Large-Scale Model Training Data
- Conclusion
Flexible Data Models and Unstructured Data Management
MongoDB's main edge in AI and ML is its ability to handle unstructured or semi-structured data. MongoDB uses a document-based model, unlike traditional relational databases. They require a strict schema. MongoDB's model allows it to store data in a flexible, JSON-like format. It is ideal for storing data, like text, images, videos, and sensor data. It's commonly used in AI and ML.
- Handling Unstructured Data: In AI and ML, datasets often come from diverse sources, like social media, IoT devices, and APIs. MongoDB's schema-less design allows easy integration of these varied data sources. It does not require conforming to rigid structures.
- Support for JSON-like Documents: MongoDB stores data as BSON (Binary JSON). It can represent rich data types. This flexibility lets MongoDB meet changing AI and ML data needs. It avoids complex migration processes.
Scalability and Performance in Handling Big Data
Scalability is crucial in AI and ML projects. They process vast amounts of data to train and evaluate models. MongoDB's sharding allows for horizontal scalability. As data grows, the database can scale.
- Horizontal Scaling: MongoDB can distribute data across multiple servers by sharding. AI models can scale seamlessly. They can handle the growing data demands of training and predictions.
- High-Performance Analytics: AI and ML often require real-time data processing. MongoDB's architecture allows low-latency reads and writes. This is vital for the constant ingestion and processing of large datasets. The database also supports in-memory storage. This boosts performance for tasks that need fast data access.
Seamless Integration with AI and ML Ecosystems
MongoDB works well with many tools and frameworks used in AI and ML projects. This makes it a great choice for developers and data scientists.
- Python and Machine Learning Libraries: MongoDB has strong integration with Python. It is a popular language in AI and ML. Popular machine learning libraries, like TensorFlow and PyTorch, can easily connect to MongoDB to fetch and store data.
- Integration with Data Pipelines: MongoDB can connect to data pipelines using tools like Apache Kafka, Spark, and Hadoop. These are often used in AI and ML workflows. This integration allows for the smooth transfer of large datasets across the pipeline.
- MongoDB Atlas: It is a fully managed database for cloud-based AI and ML projects. It has automated backups, scaling, and monitoring. This lets teams build models without worrying about database management.
Support for Real-Time Data Processing
Many AI and ML apps need real-time data processing. This is vital for fraud detection, recommendation engines, and self-driving cars. MongoDB’s ability to handle real-time data is a major benefit for these use cases.
- Real-Time Analytics: MongoDB's indexing and aggregation enable fast, real-time analytics. It's great for AI apps that need instant insights, like personalized recommendations and dynamic pricing.
- Streaming Data Support: For AI systems that rely on live data streams, like IoT data or social media feeds, MongoDB supports real-time data ingestion and processing. This ensures that AI algorithms always have access to the latest data.
Efficient Handling of Large-Scale Model Training Data
Training AI models requires access to vast amounts of historical and real-time data. MongoDB is great for storing and retrieving large datasets. They are used to train complex machine learning models.
- MongoDB's document-based structure is optimized for fast, efficient storage of large datasets. This is important for training AI models that rely on large datasets, such as deep learning and natural language processing models.
- Versioning and Auditing of Training Data: MongoDB allows easy version control of training data. It lets teams track changes over time. This is crucial for reproducibility in AI and ML experiments. It ensures that models can be retrained or improved using consistent data.
How to obtain MongoDB certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, As AI and machine learning projects grow, we need fast, scalable data storage. MongoDB can handle unstructured data and scale horizontally. It integrates with popular AI tools and supports real-time analytics. These features make it essential for many AI and ML projects. Using MongoDB, teams can meet AI models' growing data needs. It keeps performance and flexibility. MongoDB is key to AI and ML success. It allows real-time data processing, large model training, and easy integration with ML libraries.
AI and ML professionals should use MongoDB. It gives an edge in complex data projects. This can help build better AIs.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
How to Master Data Manipulation Techniques Using SAS Base
SAS (Statistical Analysis System) is a robust and versatile software platform. It is widely used for advanced analytics, data management, and business intelligence. One of the foundational modules in SAS is SAS Base. It provides tools for data manipulation, transformation, and analysis. Mastering data manipulation techniques is vital. They enable efficient data handling and accurate results from any dataset.
This guide will show you how to master key data manipulation techniques using SAS Base. We will cover key concepts and commands. They will help you clean, transform, and analyze your data with ease. By the end of this guide, you'll know the key techniques for effective data manipulation in SAS Base.
Table Of Contents
- Understanding Data Import and Export in SAS
- Data Filtering and Subsetting Techniques
- Data Transformation Techniques
- Merging and Joining Data Sets
- Handling Missing Data
- Conclusion
Understanding Data Import and Export in SAS
The first step to manipulating data is to import it into SAS from various sources, such as Excel, CSV, or databases. Similarly, after manipulation, exporting data into different formats is equally important. This section provides a step-by-step guide to the processes involved.
- Importing Data into SAS: SAS has several ways to import data. They include PROC IMPORT, the INFILE statement, and the LIBNAME statement.
- You can also import data from relational databases using the LIBNAME statement:
- Exporting Data from SAS: After manipulating data, you often need to export it to external files. Use PROC EXPORT or DATA steps with file formats like CSV, Excel, or even custom formats.
Data Filtering and Subsetting Techniques
Once data is imported, the next critical step is filtering and subsetting it. SAS offers options to subset datasets. This extracts only the needed observations or variables.
- Filtering Rows with the WHERE Statement: Use the WHERE statement to select rows that meet a condition.
- Selecting Specific Columns: Use KEEP or DROP to specify only the needed columns.
- Conditional Data Selection with IF-THEN Statements: The IF-THEN statement provides additional flexibility in selecting subsets based on complex conditions.
- These techniques are essential for reducing the size of your dataset and focusing on the relevant information for analysis.
Data Transformation Techniques
After subsetting the data, you often need to perform transformations to create new variables or modify existing ones.
- Creating New Variables: Use DATA steps to create new variables, such as calculating age from a birthdate or generating new categories.
- Recoding Variables: Recoding variables is useful when you need to modify categorical data or change the format of existing variables.
- Using Functions for Data Transformation: SAS provides many built-in functions like SUM, MEAN, LAG, CATX, and more to perform calculations or string manipulations.
- Transformations are key in creating insights and making data analysis more meaningful.
Merging and Joining Data Sets
Combining multiple datasets is a common task when working with large data. In SAS Base, you can merge or join datasets using various techniques.
- Merging Data Sets by a Common Key: Use the MERGE statement in a DATA step to combine datasets by a common variable.
Ensure that the datasets are sorted by the key variable before merging, as this is a requirement in SAS.
- Joining Data Using SQL in SAS: You can also use SQL joins in SAS through PROC SQL to combine datasets in a more flexible way.
- Merging and joining allow you to create enriched datasets that contain information from multiple sources.
Handling Missing Data
Handling missing data is essential to ensure the integrity of your analysis. SAS provides several ways to deal with missing values.
- Identifying Missing Data: You can use the NMISS function to count the number of missing values in a dataset.
- Replacing Missing Values: You can replace missing values using various methods, such as simple imputation with the IF-THEN statement or more advanced methods using PROC MI (Multiple Imputation).
- Advanced techniques like mean or median imputation can also be used based on the nature of the data.
- Deleting Observations with Missing Data: Sometimes, it is best to delete rows with missing values.
Handling missing data properly prevents inaccuracies and biases in your final results.
How to obtain SAS Base certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, For anyone working with large datasets, mastering data manipulation with SAS Base is vital. Learn to import and export data. Filter and subset it. Transform variables. Merge datasets. Handle missing data. This will ensure your data is ready for analysis. SAS Base is a powerful data management tool. Its flexibility and robustness make it so. The techniques here will help you work with data more efficiently.
Once you master these techniques, data manipulation will become faster and more intuitive. This will let you focus on deeper analysis and finding insights in your data.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
SAS (Statistical Analysis System) is a robust and versatile software platform. It is widely used for advanced analytics, data management, and business intelligence. One of the foundational modules in SAS is SAS Base. It provides tools for data manipulation, transformation, and analysis. Mastering data manipulation techniques is vital. They enable efficient data handling and accurate results from any dataset.
This guide will show you how to master key data manipulation techniques using SAS Base. We will cover key concepts and commands. They will help you clean, transform, and analyze your data with ease. By the end of this guide, you'll know the key techniques for effective data manipulation in SAS Base.
Table Of Contents
- Understanding Data Import and Export in SAS
- Data Filtering and Subsetting Techniques
- Data Transformation Techniques
- Merging and Joining Data Sets
- Handling Missing Data
- Conclusion
Understanding Data Import and Export in SAS
The first step to manipulating data is to import it into SAS from various sources, such as Excel, CSV, or databases. Similarly, after manipulation, exporting data into different formats is equally important. This section provides a step-by-step guide to the processes involved.
- Importing Data into SAS: SAS has several ways to import data. They include PROC IMPORT, the INFILE statement, and the LIBNAME statement.
- You can also import data from relational databases using the LIBNAME statement:
- Exporting Data from SAS: After manipulating data, you often need to export it to external files. Use PROC EXPORT or DATA steps with file formats like CSV, Excel, or even custom formats.
Data Filtering and Subsetting Techniques
Once data is imported, the next critical step is filtering and subsetting it. SAS offers options to subset datasets. This extracts only the needed observations or variables.
- Filtering Rows with the WHERE Statement: Use the WHERE statement to select rows that meet a condition.
- Selecting Specific Columns: Use KEEP or DROP to specify only the needed columns.
- Conditional Data Selection with IF-THEN Statements: The IF-THEN statement provides additional flexibility in selecting subsets based on complex conditions.
- These techniques are essential for reducing the size of your dataset and focusing on the relevant information for analysis.
Data Transformation Techniques
After subsetting the data, you often need to perform transformations to create new variables or modify existing ones.
- Creating New Variables: Use DATA steps to create new variables, such as calculating age from a birthdate or generating new categories.
- Recoding Variables: Recoding variables is useful when you need to modify categorical data or change the format of existing variables.
- Using Functions for Data Transformation: SAS provides many built-in functions like SUM, MEAN, LAG, CATX, and more to perform calculations or string manipulations.
- Transformations are key in creating insights and making data analysis more meaningful.
Merging and Joining Data Sets
Combining multiple datasets is a common task when working with large data. In SAS Base, you can merge or join datasets using various techniques.
- Merging Data Sets by a Common Key: Use the MERGE statement in a DATA step to combine datasets by a common variable.
Ensure that the datasets are sorted by the key variable before merging, as this is a requirement in SAS.
- Joining Data Using SQL in SAS: You can also use SQL joins in SAS through PROC SQL to combine datasets in a more flexible way.
- Merging and joining allow you to create enriched datasets that contain information from multiple sources.
Handling Missing Data
Handling missing data is essential to ensure the integrity of your analysis. SAS provides several ways to deal with missing values.
- Identifying Missing Data: You can use the NMISS function to count the number of missing values in a dataset.
- Replacing Missing Values: You can replace missing values using various methods, such as simple imputation with the IF-THEN statement or more advanced methods using PROC MI (Multiple Imputation).
- Advanced techniques like mean or median imputation can also be used based on the nature of the data.
- Deleting Observations with Missing Data: Sometimes, it is best to delete rows with missing values.
Handling missing data properly prevents inaccuracies and biases in your final results.
How to obtain SAS Base certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, For anyone working with large datasets, mastering data manipulation with SAS Base is vital. Learn to import and export data. Filter and subset it. Transform variables. Merge datasets. Handle missing data. This will ensure your data is ready for analysis. SAS Base is a powerful data management tool. Its flexibility and robustness make it so. The techniques here will help you work with data more efficiently.
Once you master these techniques, data manipulation will become faster and more intuitive. This will let you focus on deeper analysis and finding insights in your data.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Big Data Revolutionizing Smart Home Technology for a Future
In today's digital age, the integration of big data into smart home technology has revolutionized the way we live. Big data is key to smart devices and better living spaces. It boosts analytics, AI, IoT, and machine learning. Let's explore how big data is transforming the smart home tech industry and revolutionizing the way we interact with our homes.
The Power of Data Analytics in Smart Homes
A key advantage of using big data in smart homes is the ability to analyze vast amounts of data in real-time. This data can reveal our habits and preferences. It can show our lifestyles. Smart devices can use this to learn and adapt to us. Smart home systems can use data analytics. They can then optimize energy use, streamline processes, and improve convenience for homeowners.
Data analytics is revolutionizing smart homes. It lets devices learn user habits and preferences. This creates personalized living experiences. Data-driven insights enable real-time adjustments and automation. They optimize energy use and enhance security systems. As smart home tech evolves, data analytics will be key. It will boost efficiency, convenience, and comfort for homeowners.
Artificial Intelligence and Machine Learning in Smart Home Tech
With the help of artificial intelligence (AI) and machine learning algorithms, smart home devices can continuously improve their performance and functionality. These advanced technologies enable smart devices to predict our behavior, anticipate our needs, and automate routine tasks. From smart appliances to sensor data, AI-powered systems can enhance the efficiency and effectiveness of smart home technology, making our lives easier and more convenient.
AI and ML are transforming smart home tech. They enable devices to learn from users and adjust in real-time. AI-powered homes offer better convenience and security. Smart thermostats optimize energy use. Security systems recognize familiar faces. As these technologies evolve, smart homes will become more intuitive. They will adapt to users' needs and preferences.
Benefits of Big Data in Smart Home Technology
Big data is key to improving smart home tech. It lets devices learn from users. This creates personalized, efficient home environments.
Smart homes can use real-time data to:
-
Optimize energy use.
-
Improve security.
-
Automate tasks based on user preferences.
Also, big data lets smart devices work together. This creates a more connected, responsive living experience.
-
Enhanced Connectivity: Big data connects smart devices. It creates a better smart home.
-
Big data can help smart home systems. It lets them collect and process data from many sources. This improves decision-making and efficiency.
-
Smart Appliances: Big data can optimize smart appliances. It can reduce energy use and improve their performance.
-
Predictive Analytics: Smart home systems can analyze historical data. They can then predict future trends and patterns. This allows for proactive actions.
-
Adaptive Technology: Big data lets smart devices adapt to users and their environments. This improves the user experience.
The Future of Smart Home Technology
Smart home tech will transform daily life. It will do this through more automation, better connectivity, and greater personalization. Homes will become more intuitive. Devices will learn users' habits. They will then optimize energy use, security, and convenience. As AI and IoT tech advance, smart homes will be more interoperable. This will make everyday tasks easier and more efficient.
As big data continues to evolve and permeate every aspect of our lives, the future of smart home technology looks promising. From networked devices to data-driven smart systems, the possibilities are endless. Big data will boost smart home tech. It will offer new gadgets that improve our lives.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, big data is changing how we use our homes. It is making them smarter, more efficient, and more convenient. Smart home tech will transform how we live and interact with our spaces. Advanced tech and data analytics will make it possible. Big data in smart home tech will create a more connected, efficient, and intelligent future.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital age, the integration of big data into smart home technology has revolutionized the way we live. Big data is key to smart devices and better living spaces. It boosts analytics, AI, IoT, and machine learning. Let's explore how big data is transforming the smart home tech industry and revolutionizing the way we interact with our homes.
The Power of Data Analytics in Smart Homes
A key advantage of using big data in smart homes is the ability to analyze vast amounts of data in real-time. This data can reveal our habits and preferences. It can show our lifestyles. Smart devices can use this to learn and adapt to us. Smart home systems can use data analytics. They can then optimize energy use, streamline processes, and improve convenience for homeowners.
Data analytics is revolutionizing smart homes. It lets devices learn user habits and preferences. This creates personalized living experiences. Data-driven insights enable real-time adjustments and automation. They optimize energy use and enhance security systems. As smart home tech evolves, data analytics will be key. It will boost efficiency, convenience, and comfort for homeowners.
Artificial Intelligence and Machine Learning in Smart Home Tech
With the help of artificial intelligence (AI) and machine learning algorithms, smart home devices can continuously improve their performance and functionality. These advanced technologies enable smart devices to predict our behavior, anticipate our needs, and automate routine tasks. From smart appliances to sensor data, AI-powered systems can enhance the efficiency and effectiveness of smart home technology, making our lives easier and more convenient.
AI and ML are transforming smart home tech. They enable devices to learn from users and adjust in real-time. AI-powered homes offer better convenience and security. Smart thermostats optimize energy use. Security systems recognize familiar faces. As these technologies evolve, smart homes will become more intuitive. They will adapt to users' needs and preferences.
Benefits of Big Data in Smart Home Technology
Big data is key to improving smart home tech. It lets devices learn from users. This creates personalized, efficient home environments.
Smart homes can use real-time data to:
-
Optimize energy use.
-
Improve security.
-
Automate tasks based on user preferences.
Also, big data lets smart devices work together. This creates a more connected, responsive living experience.
-
Enhanced Connectivity: Big data connects smart devices. It creates a better smart home.
-
Big data can help smart home systems. It lets them collect and process data from many sources. This improves decision-making and efficiency.
-
Smart Appliances: Big data can optimize smart appliances. It can reduce energy use and improve their performance.
-
Predictive Analytics: Smart home systems can analyze historical data. They can then predict future trends and patterns. This allows for proactive actions.
-
Adaptive Technology: Big data lets smart devices adapt to users and their environments. This improves the user experience.
The Future of Smart Home Technology
Smart home tech will transform daily life. It will do this through more automation, better connectivity, and greater personalization. Homes will become more intuitive. Devices will learn users' habits. They will then optimize energy use, security, and convenience. As AI and IoT tech advance, smart homes will be more interoperable. This will make everyday tasks easier and more efficient.
As big data continues to evolve and permeate every aspect of our lives, the future of smart home technology looks promising. From networked devices to data-driven smart systems, the possibilities are endless. Big data will boost smart home tech. It will offer new gadgets that improve our lives.
How to obtain Big Data certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, big data is changing how we use our homes. It is making them smarter, more efficient, and more convenient. Smart home tech will transform how we live and interact with our spaces. Advanced tech and data analytics will make it possible. Big data in smart home tech will create a more connected, efficient, and intelligent future.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Multilingual Digital Marketing: Key to Global Market Success
In a more connected world, the digital landscape has changed how businesses engage with consumers. Globalization has let companies reach diverse markets. But, it brings new challenges. A major challenge is the need to communicate with a multilingual audience. Multilingual digital marketing is not just an option; it is a crucial strategy for businesses aiming to thrive in global markets. This blog post will discuss multilingual digital marketing. We will cover its benefits, challenges, and best practices. We will cover five key subtopics: 1. the global marketplace, 2. localization, 3. cultural sensitivity, 4. multilingual SEO, and 5. technology's impact on multilingual marketing.
Understanding the Global Marketplace
As businesses expand beyond their home countries, they must know the global marketplace. The Internet has removed geographical barriers. It lets brands connect with consumers from diverse cultures. However, merely translating content into various languages is insufficient.
a. Diverse Consumer Preferences
Consumer preferences vary significantly across regions. For instance, the style of communication, colors, and even images that appeal to one audience may not resonate with another. Research shows that 75% of consumers prefer to buy products in their native language. This highlights the need for tailored marketing messages.
b. Market Potential
Emerging markets in Asia, Africa, and Latin America present significant growth opportunities for brands willing to adapt their marketing strategies. Understanding the local culture, customs, and consumer behavior is essential to harnessing this potential. A successful multilingual digital marketing strategy considers these factors, ensuring that messaging is relevant and engaging for each target audience.
c. Competitive Advantage
In a crowded digital marketplace, brands that embrace multilingual marketing can differentiate themselves from competitors. By catering to specific linguistic demographics, companies can establish stronger connections with potential customers, fostering brand loyalty and increasing market share.
2. The Significance of Localization
Localization is more than translation. It means adapting content to meet the target market's cultural, linguistic, and functional expectations.
a. Cultural Relevance
Localized content resonates more effectively with the audience. This includes not only language but also cultural references, idioms, and humor. For example, a marketing campaign that works in the U.S. may need big changes to succeed in Japan, where the culture and communication styles differ.
b. Legal and Regulatory Compliance
Different countries have varying laws and regulations regarding advertising and marketing. Localization ensures marketing materials comply with local laws. It avoids legal issues from using culturally insensitive or inappropriate content.
c. Enhancing User Experience
A localized website or app provides a better user experience, as it aligns with users’ expectations. For example, using local payment methods and shipping options can improve the customer journey. It will make it easier for users to engage with the brand. This attention to detail can lead to higher conversion rates and customer satisfaction.
3. The Role of Cultural Sensitivity
Cultural sensitivity is essential in creating effective multilingual marketing campaigns. Understanding and respecting cultural nuances can make or break a marketing strategy.
a. Avoiding Miscommunication
Cultural missteps can lead to disastrous consequences for a brand. For example, a marketing campaign that ignores local customs may offend the audience. Brands must invest time to understand cultural contexts. This avoids miscommunication and builds trust with their audience.
b. Building Authentic Connections
Culturally sensitive marketing fosters authentic connections with consumers. By acknowledging cultural events and holidays, brands can show their commitment to the local community. For example, local holiday campaigns can resonate with consumers. They can boost brand loyalty.
c. Adapting Tone and Messaging
The tone of voice and messaging used in marketing must align with the cultural context of the target audience. A humorous approach may work in some cultures, while a more serious tone may be preferred in others. Tailoring the tone to fit cultural expectations can significantly impact how the message is received.
4. Effective Multilingual SEO Strategies
SEO is vital for making sure multilingual content reaches its audience. Adopting effective multilingual SEO strategies can enhance visibility and drive organic traffic.
a. Keyword Research
Conducting keyword research in the target language is vital. Keywords may not translate directly. So, know local terms and search habits. Tools like Google Keyword Planner can help marketers. They find relevant keywords in different languages.
b. URL Structure
Optimizing the URL structure for multilingual sites is crucial for both user experience and SEO. Using country-specific top-level domains (ccTLDs) or subdirectories can help. They improve search engines' understanding of the target audience and rank in local search results.
c. Meta Tags and Descriptions
Translating meta tags and descriptions is equally important for SEO. Unique, localized meta descriptions can boost click-through rates and search rankings. They should resonate with the target audience.
d. Local Backlinks
Building local backlinks from reputable sites in the target market can boost a brand's authority and credibility. Partnering with local influencers or industry sites can create valuable backlinks. They can improve search visibility.
5. The Impact of Technology on Multilingual Marketing
Technology plays a pivotal role in facilitating multilingual digital marketing efforts. New tools and platforms let brands improve marketing and engage customers.
a. Translation Management Systems (TMS)
Translation Management Systems can automate and manage translation. They ensure high quality and consistency across many languages. These tools help businesses manage multilingual content. They make it easier to reach global audiences.
b. AI and Machine Learning
Artificial Intelligence (AI) and machine learning technologies are revolutionizing multilingual marketing. AI translation tools can provide quick translations. Machine learning can analyze consumer behavior. This lets brands tailor their marketing strategies.
c. Chatbots and Customer Service
Multilingual chatbots allow brands to support customers in their native languages, in real-time. It boosts customer satisfaction and engagement. Consumers can now talk with the brand.
d. Analytics and Performance Measurement
Data analytics tools can track multilingual campaigns. They provide insights into consumer behavior and preferences. Brands can use this data to refine their strategies and allocate resources more effectively.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In a globalized digital world, multilingual digital marketing is vital. It helps businesses connect with diverse audiences and improve user experiences. It also builds authentic relationships with consumers worldwide. To succeed in multilingual efforts, know the global market. Prioritize localization and be culturally sensitive. Also, effective multilingual SEO and new tech help brands to reach and engage their target markets better. As businesses expand globally, multilingual digital marketing is a must. It will be key to long-term success in the fast-changing digital world. Multilingual strategies can unlock new opportunities for brands. They can build loyalty and drive growth in the global marketplace.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In a more connected world, the digital landscape has changed how businesses engage with consumers. Globalization has let companies reach diverse markets. But, it brings new challenges. A major challenge is the need to communicate with a multilingual audience. Multilingual digital marketing is not just an option; it is a crucial strategy for businesses aiming to thrive in global markets. This blog post will discuss multilingual digital marketing. We will cover its benefits, challenges, and best practices. We will cover five key subtopics: 1. the global marketplace, 2. localization, 3. cultural sensitivity, 4. multilingual SEO, and 5. technology's impact on multilingual marketing.
Understanding the Global Marketplace
As businesses expand beyond their home countries, they must know the global marketplace. The Internet has removed geographical barriers. It lets brands connect with consumers from diverse cultures. However, merely translating content into various languages is insufficient.
a. Diverse Consumer Preferences
Consumer preferences vary significantly across regions. For instance, the style of communication, colors, and even images that appeal to one audience may not resonate with another. Research shows that 75% of consumers prefer to buy products in their native language. This highlights the need for tailored marketing messages.
b. Market Potential
Emerging markets in Asia, Africa, and Latin America present significant growth opportunities for brands willing to adapt their marketing strategies. Understanding the local culture, customs, and consumer behavior is essential to harnessing this potential. A successful multilingual digital marketing strategy considers these factors, ensuring that messaging is relevant and engaging for each target audience.
c. Competitive Advantage
In a crowded digital marketplace, brands that embrace multilingual marketing can differentiate themselves from competitors. By catering to specific linguistic demographics, companies can establish stronger connections with potential customers, fostering brand loyalty and increasing market share.
2. The Significance of Localization
Localization is more than translation. It means adapting content to meet the target market's cultural, linguistic, and functional expectations.
a. Cultural Relevance
Localized content resonates more effectively with the audience. This includes not only language but also cultural references, idioms, and humor. For example, a marketing campaign that works in the U.S. may need big changes to succeed in Japan, where the culture and communication styles differ.
b. Legal and Regulatory Compliance
Different countries have varying laws and regulations regarding advertising and marketing. Localization ensures marketing materials comply with local laws. It avoids legal issues from using culturally insensitive or inappropriate content.
c. Enhancing User Experience
A localized website or app provides a better user experience, as it aligns with users’ expectations. For example, using local payment methods and shipping options can improve the customer journey. It will make it easier for users to engage with the brand. This attention to detail can lead to higher conversion rates and customer satisfaction.
3. The Role of Cultural Sensitivity
Cultural sensitivity is essential in creating effective multilingual marketing campaigns. Understanding and respecting cultural nuances can make or break a marketing strategy.
a. Avoiding Miscommunication
Cultural missteps can lead to disastrous consequences for a brand. For example, a marketing campaign that ignores local customs may offend the audience. Brands must invest time to understand cultural contexts. This avoids miscommunication and builds trust with their audience.
b. Building Authentic Connections
Culturally sensitive marketing fosters authentic connections with consumers. By acknowledging cultural events and holidays, brands can show their commitment to the local community. For example, local holiday campaigns can resonate with consumers. They can boost brand loyalty.
c. Adapting Tone and Messaging
The tone of voice and messaging used in marketing must align with the cultural context of the target audience. A humorous approach may work in some cultures, while a more serious tone may be preferred in others. Tailoring the tone to fit cultural expectations can significantly impact how the message is received.
4. Effective Multilingual SEO Strategies
SEO is vital for making sure multilingual content reaches its audience. Adopting effective multilingual SEO strategies can enhance visibility and drive organic traffic.
a. Keyword Research
Conducting keyword research in the target language is vital. Keywords may not translate directly. So, know local terms and search habits. Tools like Google Keyword Planner can help marketers. They find relevant keywords in different languages.
b. URL Structure
Optimizing the URL structure for multilingual sites is crucial for both user experience and SEO. Using country-specific top-level domains (ccTLDs) or subdirectories can help. They improve search engines' understanding of the target audience and rank in local search results.
c. Meta Tags and Descriptions
Translating meta tags and descriptions is equally important for SEO. Unique, localized meta descriptions can boost click-through rates and search rankings. They should resonate with the target audience.
d. Local Backlinks
Building local backlinks from reputable sites in the target market can boost a brand's authority and credibility. Partnering with local influencers or industry sites can create valuable backlinks. They can improve search visibility.
5. The Impact of Technology on Multilingual Marketing
Technology plays a pivotal role in facilitating multilingual digital marketing efforts. New tools and platforms let brands improve marketing and engage customers.
a. Translation Management Systems (TMS)
Translation Management Systems can automate and manage translation. They ensure high quality and consistency across many languages. These tools help businesses manage multilingual content. They make it easier to reach global audiences.
b. AI and Machine Learning
Artificial Intelligence (AI) and machine learning technologies are revolutionizing multilingual marketing. AI translation tools can provide quick translations. Machine learning can analyze consumer behavior. This lets brands tailor their marketing strategies.
c. Chatbots and Customer Service
Multilingual chatbots allow brands to support customers in their native languages, in real-time. It boosts customer satisfaction and engagement. Consumers can now talk with the brand.
d. Analytics and Performance Measurement
Data analytics tools can track multilingual campaigns. They provide insights into consumer behavior and preferences. Brands can use this data to refine their strategies and allocate resources more effectively.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In a globalized digital world, multilingual digital marketing is vital. It helps businesses connect with diverse audiences and improve user experiences. It also builds authentic relationships with consumers worldwide. To succeed in multilingual efforts, know the global market. Prioritize localization and be culturally sensitive. Also, effective multilingual SEO and new tech help brands to reach and engage their target markets better. As businesses expand globally, multilingual digital marketing is a must. It will be key to long-term success in the fast-changing digital world. Multilingual strategies can unlock new opportunities for brands. They can build loyalty and drive growth in the global marketplace.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The Future of RPA in Hyperautomation: Trends and Insights
In today's fast-changing business world, firms are using robotic process automation (RPA). It helps them improve efficiency and drive digital transformation. However, as technology advances, hyperautomation is gaining momentum as the next evolution of RPA. But what exactly does the future hold for RPA in the era of hyperautomation?
The Evolution of RPA to Hyperautomation
Hyperautomation is the next step in Robotic Process Automation (RPA). It changes how organizations automate tasks. Hyperautomation combines RPA with advanced technologies. These include AI, machine learning, and process mining. It lets businesses automate complex workflows and decisions that were hard to solve before. This shift lets organizations be more efficient, agile, and insightful. It drives more value from their automation efforts.
-
Hyperautomation means integrating RPA with AI, machine learning, and advanced robotics. This creates a smarter, all-in-one automation solution.
-
By combining RPA with AI-driven decision-making, organizations can automate complex processes. They can also optimize workflows and boost efficiency to new levels.
Benefits of Hyperautomation
Hyperautomation can greatly help organizations. It can make processes more efficient. Hyperautomation uses RPA, AI, and machine learning. It lets businesses automate complex workflows with both structured and unstructured data. This leads to faster decisions and better accuracy. It also allows companies to quickly adapt to market changes and customer demands. This frees up human resources for more strategic tasks.
-
Hyperautomation benefits organizations in many ways. It improves workflow and cognitive automation. It also boosts process efficiency.
-
Hyperautomation uses AI and machine learning. It lets businesses automate tasks that need human-like skills in reasoning and problem-solving.
The Impact of Hyperautomation on Business Processes
Hyperautomation uses advanced tech like AI, machine learning, and RPA. It transforms business processes by automating complex workflows. This boosts efficiency. This approach boosts productivity. It also improves decision-making with data insights. This leads to greater agility and competitiveness in the market. Hyperautomation is evolving. It offers businesses a chance to redefine their operations and quickly adapt to market changes.
-
Hyperautomation lets organizations transform their processes. It automates repetitive tasks, reduces manual errors, and speeds up workflows.
-
This boosts productivity, cuts costs, and improves quality. It drives growth and a competitive edge.
The Role of Intelligent Automation in Hyperautomation
Intelligent automation is key to hyperautomation. It integrates AI and machine learning with traditional automation tools. This lets organizations streamline complex processes and improve decisions. It boosts efficiency across various business functions. As businesses adopt hyperautomation, intelligent automation is key. It unlocks more value from data and optimizes workflows. This drives digital transformation and a competitive edge.
-
Intelligent automation is key to hyperautomation. It lets machines learn from experience, adapt to new situations, and make decisions on their own.
-
AI and machine learning can boost automation, agility, and scalability. This will enable more advanced automation solutions.
Challenges and Opportunities in the Future of RPA in Hyperautomation
The future of Robotic Process Automation (RPA) within hyperautomation presents both significant challenges and opportunities for organizations. A major challenge is integrating RPA with existing systems. It requires strong change management and cross-department collaboration for success. But, it also opens opportunities for businesses. They can improve efficiency, drive innovation, and use AI to create better automation.
-
Hyperautomation can greatly benefit organizations. But, it is complex, hard to scale, and tough to integrate with existing systems.
-
However, by embracing hyperautomation, organizations can drive innovation. They can optimize their processes and stay ahead of the competition in today's fast-paced digital age.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA's future in hyperautomation is promising. It can help organizations with digital transformation, efficiency, and business success. AI, machine learning, and advanced robotics can unlock new automation and innovation. They can help organizations grow in tomorrow's fast-changing business world. To stay competitive, embrace hyperautomation. It's key to being agile and future-proof in a world that is becoming more automated.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-changing business world, firms are using robotic process automation (RPA). It helps them improve efficiency and drive digital transformation. However, as technology advances, hyperautomation is gaining momentum as the next evolution of RPA. But what exactly does the future hold for RPA in the era of hyperautomation?
The Evolution of RPA to Hyperautomation
Hyperautomation is the next step in Robotic Process Automation (RPA). It changes how organizations automate tasks. Hyperautomation combines RPA with advanced technologies. These include AI, machine learning, and process mining. It lets businesses automate complex workflows and decisions that were hard to solve before. This shift lets organizations be more efficient, agile, and insightful. It drives more value from their automation efforts.
-
Hyperautomation means integrating RPA with AI, machine learning, and advanced robotics. This creates a smarter, all-in-one automation solution.
-
By combining RPA with AI-driven decision-making, organizations can automate complex processes. They can also optimize workflows and boost efficiency to new levels.
Benefits of Hyperautomation
Hyperautomation can greatly help organizations. It can make processes more efficient. Hyperautomation uses RPA, AI, and machine learning. It lets businesses automate complex workflows with both structured and unstructured data. This leads to faster decisions and better accuracy. It also allows companies to quickly adapt to market changes and customer demands. This frees up human resources for more strategic tasks.
-
Hyperautomation benefits organizations in many ways. It improves workflow and cognitive automation. It also boosts process efficiency.
-
Hyperautomation uses AI and machine learning. It lets businesses automate tasks that need human-like skills in reasoning and problem-solving.
The Impact of Hyperautomation on Business Processes
Hyperautomation uses advanced tech like AI, machine learning, and RPA. It transforms business processes by automating complex workflows. This boosts efficiency. This approach boosts productivity. It also improves decision-making with data insights. This leads to greater agility and competitiveness in the market. Hyperautomation is evolving. It offers businesses a chance to redefine their operations and quickly adapt to market changes.
-
Hyperautomation lets organizations transform their processes. It automates repetitive tasks, reduces manual errors, and speeds up workflows.
-
This boosts productivity, cuts costs, and improves quality. It drives growth and a competitive edge.
The Role of Intelligent Automation in Hyperautomation
Intelligent automation is key to hyperautomation. It integrates AI and machine learning with traditional automation tools. This lets organizations streamline complex processes and improve decisions. It boosts efficiency across various business functions. As businesses adopt hyperautomation, intelligent automation is key. It unlocks more value from data and optimizes workflows. This drives digital transformation and a competitive edge.
-
Intelligent automation is key to hyperautomation. It lets machines learn from experience, adapt to new situations, and make decisions on their own.
-
AI and machine learning can boost automation, agility, and scalability. This will enable more advanced automation solutions.
Challenges and Opportunities in the Future of RPA in Hyperautomation
The future of Robotic Process Automation (RPA) within hyperautomation presents both significant challenges and opportunities for organizations. A major challenge is integrating RPA with existing systems. It requires strong change management and cross-department collaboration for success. But, it also opens opportunities for businesses. They can improve efficiency, drive innovation, and use AI to create better automation.
-
Hyperautomation can greatly benefit organizations. But, it is complex, hard to scale, and tough to integrate with existing systems.
-
However, by embracing hyperautomation, organizations can drive innovation. They can optimize their processes and stay ahead of the competition in today's fast-paced digital age.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, RPA's future in hyperautomation is promising. It can help organizations with digital transformation, efficiency, and business success. AI, machine learning, and advanced robotics can unlock new automation and innovation. They can help organizations grow in tomorrow's fast-changing business world. To stay competitive, embrace hyperautomation. It's key to being agile and future-proof in a world that is becoming more automated.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Predictive Maintenance Using Machine Learning for Efficiency
In today's fast-paced industrial world, businesses must be efficient and reliable to stay competitive. One key aspect of ensuring optimal performance and minimizing downtime is maintenance management. Traditional methods of maintenance scheduling can be time-consuming, costly, and inefficient. However, machine learning has sparked a new era in predictive maintenance. It has revolutionized maintenance operations.
What is Predictive Maintenance?
Predictive maintenance is a proactive strategy. It uses data analysis, machine learning, and sensors to predict equipment failures before they occur. Predictive maintenance can detect issues, predict faults, and suggest repairs. It does this by monitoring machine performance and analyzing sensor data. This approach shifts the focus from reactive to preventive maintenance. It will improve equipment reliability and cut costs.
How Does Machine Learning Enhance Predictive Maintenance?
Machine learning algorithms are vital for predictive maintenance. They analyze vast data to find patterns that may indicate equipment failures. These algorithms can detect small changes in machine behavior. They can predict failures and aid maintenance decisions. Machine learning models can learn from past data and real-time sensor info. They can adapt and improve their predictions over time. This optimizes maintenance and reduces downtime.
Machine learning greatly improves predictive maintenance. It analyzes large amounts of sensor and equipment data. It finds patterns and predicts failures before they occur. Using algorithms that learn from historical data, organizations can optimize maintenance schedules. This reduces downtime and costs while improving asset longevity.
The Benefits of Predictive Maintenance
Predictive maintenance cuts equipment downtime. It uses machine learning to analyze data. It identifies potential failures before they occur. This proactive approach saves costs from unexpected repairs and delays. It also extends machinery life by ensuring optimal performance. Also, better maintenance schedules can boost efficiency. They can help use resources better. This will increase overall productivity.
Predictive maintenance offers a wide range of benefits for businesses across various industries. Some of the key advantages include:
-
Reduced Downtime: By predicting equipment failures, businesses can schedule maintenance at the best times. This minimizes downtime and maximizes efficiency.
-
Extended Equipment Lifespan: Early detection of faults allows for timely fixes. This extends mechanical equipment's lifespan and reduces costly replacements.
-
Increased Safety: Proactive maintenance keeps equipment safe and reliable. This reduces accident risks and ensures a safe work environment.
-
Cost Savings: Preventing breakdowns and optimizing maintenance can cut costs. It improves resource use and boosts profits.
Implementing Predictive Maintenance Strategies
To use predictive maintenance, businesses must invest in advanced sensors and data analytics, as well as machine learning. By analyzing sensor data, businesses can gain insights into equipment performance. They can identify failure modes and prioritize maintenance. By using predictive analytics and risk assessment tools, businesses can create models. They can predict equipment reliability, failures, and maintenance needs.
The Future of Predictive Maintenance
The integration of machine learning technologies in predictive maintenance is transforming the way businesses manage their assets and optimize maintenance operations. As machine learning algorithms improve, predictive maintenance holds great promise. It could revolutionize maintenance, boost equipment reliability, and increase efficiency. By embracing intelligent maintenance solutions and predictive maintenance platforms, businesses can stay ahead of the curve, minimize downtime, and achieve new levels of maintenance excellence.
How to obtain Machine Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, machine learning for predictive maintenance is creating a new era of better maintenance and equipment reliability. By harnessing the power of data-driven insights, predictive algorithms, and maintenance forecasting, businesses can revolutionize their maintenance operations, enhance equipment performance, and achieve sustainable operational excellence in today's competitive industrial landscape. Predictive maintenance is a must for businesses. It is not just a trend. To thrive in the digital age, they must stay ahead of the curve.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced industrial world, businesses must be efficient and reliable to stay competitive. One key aspect of ensuring optimal performance and minimizing downtime is maintenance management. Traditional methods of maintenance scheduling can be time-consuming, costly, and inefficient. However, machine learning has sparked a new era in predictive maintenance. It has revolutionized maintenance operations.
What is Predictive Maintenance?
Predictive maintenance is a proactive strategy. It uses data analysis, machine learning, and sensors to predict equipment failures before they occur. Predictive maintenance can detect issues, predict faults, and suggest repairs. It does this by monitoring machine performance and analyzing sensor data. This approach shifts the focus from reactive to preventive maintenance. It will improve equipment reliability and cut costs.
How Does Machine Learning Enhance Predictive Maintenance?
Machine learning algorithms are vital for predictive maintenance. They analyze vast data to find patterns that may indicate equipment failures. These algorithms can detect small changes in machine behavior. They can predict failures and aid maintenance decisions. Machine learning models can learn from past data and real-time sensor info. They can adapt and improve their predictions over time. This optimizes maintenance and reduces downtime.
Machine learning greatly improves predictive maintenance. It analyzes large amounts of sensor and equipment data. It finds patterns and predicts failures before they occur. Using algorithms that learn from historical data, organizations can optimize maintenance schedules. This reduces downtime and costs while improving asset longevity.
The Benefits of Predictive Maintenance
Predictive maintenance cuts equipment downtime. It uses machine learning to analyze data. It identifies potential failures before they occur. This proactive approach saves costs from unexpected repairs and delays. It also extends machinery life by ensuring optimal performance. Also, better maintenance schedules can boost efficiency. They can help use resources better. This will increase overall productivity.
Predictive maintenance offers a wide range of benefits for businesses across various industries. Some of the key advantages include:
-
Reduced Downtime: By predicting equipment failures, businesses can schedule maintenance at the best times. This minimizes downtime and maximizes efficiency.
-
Extended Equipment Lifespan: Early detection of faults allows for timely fixes. This extends mechanical equipment's lifespan and reduces costly replacements.
-
Increased Safety: Proactive maintenance keeps equipment safe and reliable. This reduces accident risks and ensures a safe work environment.
-
Cost Savings: Preventing breakdowns and optimizing maintenance can cut costs. It improves resource use and boosts profits.
Implementing Predictive Maintenance Strategies
To use predictive maintenance, businesses must invest in advanced sensors and data analytics, as well as machine learning. By analyzing sensor data, businesses can gain insights into equipment performance. They can identify failure modes and prioritize maintenance. By using predictive analytics and risk assessment tools, businesses can create models. They can predict equipment reliability, failures, and maintenance needs.
The Future of Predictive Maintenance
The integration of machine learning technologies in predictive maintenance is transforming the way businesses manage their assets and optimize maintenance operations. As machine learning algorithms improve, predictive maintenance holds great promise. It could revolutionize maintenance, boost equipment reliability, and increase efficiency. By embracing intelligent maintenance solutions and predictive maintenance platforms, businesses can stay ahead of the curve, minimize downtime, and achieve new levels of maintenance excellence.
How to obtain Machine Learning certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, machine learning for predictive maintenance is creating a new era of better maintenance and equipment reliability. By harnessing the power of data-driven insights, predictive algorithms, and maintenance forecasting, businesses can revolutionize their maintenance operations, enhance equipment performance, and achieve sustainable operational excellence in today's competitive industrial landscape. Predictive maintenance is a must for businesses. It is not just a trend. To thrive in the digital age, they must stay ahead of the curve.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Building Scalable and Secure RESTful APIs Using Python!
In today's digital world, RESTful APIs are key. They allow smooth communication between client and server applications. Python is widely favored for its clarity and ease of use. So, it is a top choice for building RESTful APIs. This article covers the key aspects of creating RESTful APIs with Python. It explains essential concepts, tools, and best practices. The goal is to help developers design efficient, scalable APIs.
Table Of Contents
- Understanding RESTful APIs
- Choosing the Right Framework
- Creating a Simple RESTful API with Flask
- Implementing Authentication and Authorization
- Versioning Your API
- Conclusion
Understanding RESTful APIs
RESTful APIs are architectural styles that use HTTP requests to manage data. They are stateless. Each client request has all the info the server needs to fulfill it. This characteristic leads to greater scalability and performance.
Key Principles of REST:
- Statelessness: Each API call is independent; the server does not store client context.
- Resource-Based: Resources (e.g., users, products) are identified by URIs (Uniform Resource Identifiers).
- Use of HTTP Methods: Common HTTP methods include:
- GET: Retrieve data from the server.
- POST: Create a new resource.
- PUT: Update an existing resource.
- DELETE: Remove a resource.
Data Format: RESTful APIs usually use JSON for data exchange. It's lightweight and easy to read.
Choosing the Right Framework
Python offers several frameworks for building RESTful APIs, each with unique features. Here are three popular options:
Flask
- Lightweight and Flexible: Flask is a micro-framework. It enables developers to create applications rapidly.
- Extensible: It has many extensions to add features, like database and user login.
- Ideal for Prototypes: Flask is perfect for small to medium-sized applications and prototypes.
Django REST Framework (DRF)
- Full-Featured: DRF extends Django, providing a robust toolkit for building APIs.
- It has built-in features: serialization, authentication, and viewsets. They simplify managing complex apps.
- Great for Large Projects: DRF is perfect for large apps. They need scalability and maintainability.
FastAPI
- Asynchronous: FastAPI is designed for high performance and supports asynchronous programming.
- Automatic Documentation: It automatically generates interactive API documentation using Swagger and ReDoc.
- Type Hints: FastAPI leverages Python type hints for better code quality and validation.
Creating a Simple RESTful API with Flask
Step-by-Step Guide
Setting Up Flask:
- Install Flask using pip:
Creating a Basic API:
- Generate a file named app.py and include the following code:
Running the API:
- Execute the command:
- Access the API at http://127.0.0.1:5000/tasks to retrieve tasks.
Testing the API
- Use tools like Postman or cURL to test your API endpoints. For example, send a POST request to http://127.0.0.1:5000/tasks with a JSON body to add a new task.
Implementing Authentication and Authorization
Security is critical when building APIs. Implementing authentication and authorization ensures that only authorized users can access specific resources.
Common Authentication Methods
- Basic Authentication entails transmitting a username and password with every request.
- Token-Based Authentication: After a successful login, users get a token. It must be in all future requests.
- OAuth2: A more secure and scalable method often used for third-party integrations.
Example with Flask-JWT-Extended
- Install Flask-JWT-Extended:
- Add Authentication to Your API:
Versioning Your API
As your API develops, you may find it necessary to adopt modifications that do not support earlier versions. API versioning helps you manage these changes without disrupting existing clients.
Strategies for Versioning
- URI Versioning: Include the version in the URL, e.g., /api/v1/tasks.
- Header Versioning: Specify the version in the request header, allowing cleaner URLs.
- Query Parameter Versioning: Use a query parameter to say the version, e.g., /tasks?version=1.
Example of URI versioning in Flask
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Building RESTful APIs with Python is rewarding. It improves your skills in creating scalable, maintainable apps. You can develop robust APIs that meet your users' needs. To do this, know REST principles. Choose the right framework. Then, install security and versioning strategies. Python has powerful tools for building web services. Use Flask for its simplicity, Django REST Framework for its features, or FastAPI for its speed.
As you create RESTful APIs, follow best practices. Also, explore new techniques to improve your skills.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In today's digital world, RESTful APIs are key. They allow smooth communication between client and server applications. Python is widely favored for its clarity and ease of use. So, it is a top choice for building RESTful APIs. This article covers the key aspects of creating RESTful APIs with Python. It explains essential concepts, tools, and best practices. The goal is to help developers design efficient, scalable APIs.
Table Of Contents
- Understanding RESTful APIs
- Choosing the Right Framework
- Creating a Simple RESTful API with Flask
- Implementing Authentication and Authorization
- Versioning Your API
- Conclusion
Understanding RESTful APIs
RESTful APIs are architectural styles that use HTTP requests to manage data. They are stateless. Each client request has all the info the server needs to fulfill it. This characteristic leads to greater scalability and performance.
Key Principles of REST:
- Statelessness: Each API call is independent; the server does not store client context.
- Resource-Based: Resources (e.g., users, products) are identified by URIs (Uniform Resource Identifiers).
- Use of HTTP Methods: Common HTTP methods include:
- GET: Retrieve data from the server.
- POST: Create a new resource.
- PUT: Update an existing resource.
- DELETE: Remove a resource.
Data Format: RESTful APIs usually use JSON for data exchange. It's lightweight and easy to read.
Choosing the Right Framework
Python offers several frameworks for building RESTful APIs, each with unique features. Here are three popular options:
Flask
- Lightweight and Flexible: Flask is a micro-framework. It enables developers to create applications rapidly.
- Extensible: It has many extensions to add features, like database and user login.
- Ideal for Prototypes: Flask is perfect for small to medium-sized applications and prototypes.
Django REST Framework (DRF)
- Full-Featured: DRF extends Django, providing a robust toolkit for building APIs.
- It has built-in features: serialization, authentication, and viewsets. They simplify managing complex apps.
- Great for Large Projects: DRF is perfect for large apps. They need scalability and maintainability.
FastAPI
- Asynchronous: FastAPI is designed for high performance and supports asynchronous programming.
- Automatic Documentation: It automatically generates interactive API documentation using Swagger and ReDoc.
- Type Hints: FastAPI leverages Python type hints for better code quality and validation.
Creating a Simple RESTful API with Flask
Step-by-Step Guide
Setting Up Flask:
- Install Flask using pip:
Creating a Basic API:
- Generate a file named app.py and include the following code:
Running the API:
- Execute the command:
- Access the API at http://127.0.0.1:5000/tasks to retrieve tasks.
Testing the API
- Use tools like Postman or cURL to test your API endpoints. For example, send a POST request to http://127.0.0.1:5000/tasks with a JSON body to add a new task.
Implementing Authentication and Authorization
Security is critical when building APIs. Implementing authentication and authorization ensures that only authorized users can access specific resources.
Common Authentication Methods
- Basic Authentication entails transmitting a username and password with every request.
- Token-Based Authentication: After a successful login, users get a token. It must be in all future requests.
- OAuth2: A more secure and scalable method often used for third-party integrations.
Example with Flask-JWT-Extended
- Install Flask-JWT-Extended:
- Add Authentication to Your API:
Versioning Your API
As your API develops, you may find it necessary to adopt modifications that do not support earlier versions. API versioning helps you manage these changes without disrupting existing clients.
Strategies for Versioning
- URI Versioning: Include the version in the URL, e.g., /api/v1/tasks.
- Header Versioning: Specify the version in the request header, allowing cleaner URLs.
- Query Parameter Versioning: Use a query parameter to say the version, e.g., /tasks?version=1.
Example of URI versioning in Flask
How to obtain Python certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Building RESTful APIs with Python is rewarding. It improves your skills in creating scalable, maintainable apps. You can develop robust APIs that meet your users' needs. To do this, know REST principles. Choose the right framework. Then, install security and versioning strategies. Python has powerful tools for building web services. Use Flask for its simplicity, Django REST Framework for its features, or FastAPI for its speed.
As you create RESTful APIs, follow best practices. Also, explore new techniques to improve your skills.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Power BI Embedding: A Developer's Guide for Web & Apps!
Power BI stands out as a leading data visualization tool in today's market. Power BI is a favorite for business intelligence. Its interactive reports, real-time data, and dashboards make it so. Embedding Power BI in web or mobile apps lets organizations extend its features to users. It integrates analytics into workflows. This guide helps developers embed Power BI reports and dashboards in their apps. It covers both web and mobile apps. It ensures they are scalable, secure, and user-friendly.
Table Of Contents
- Understanding Power BI Embedded: Key Concepts
- Getting Started: Setting Up Power BI Embedded
- Embedding Power BI Reports Using REST API
- Customizing User Experience: API and UI Customization
- Security Considerations: Managing Permissions and Access Control
- Conclusion
Understanding Power BI Embedded: Key Concepts
Power BI Embedded is a Microsoft service. It lets developers embed Power BI reports, dashboards, and visuals into their apps. It lets users view data without leaving the current platform.
- Power BI Service vs. Power BI Embedded: The Power BI Service is for individuals and businesses to view reports on the Power BI portal. Power BI Embedded is for developers. It lets them integrate Power BI into external apps or websites.
- API and SDK: Power BI has APIs and SDKs for embedding reports. The REST API lets you programmatically interact with the Power BI service. The JavaScript APIs allow you to embed reports with rich customization options.
You must first understand these key differences and tools. They are the first step to embedding Power BI into your app.
Getting Started: Setting Up Power BI Embedded
Before embedding Power BI, developers must set up an environment. They must also obtain the necessary credentials and APIs.
- Azure Subscription: Power BI Embedded is hosted on Azure. So, you need an Azure subscription. Use the Azure portal to set up a Power BI Embedded resource. It will provide the capacity to embed reports.
- App Registration: Register your app in Azure AD to authenticate it with Power BI's API. During this process, you will obtain the client ID and secret, which are necessary for API calls.
- Power BI Workspace: Set up a dedicated workspace in Power BI. It will store your datasets, reports, and dashboards. This workspace will serve as the source for embedding reports into your app.
This infrastructure will let you integrate Power BI into any app.
Embedding Power BI Reports Using REST API
The Power BI REST API lets developers embed reports. They can also manage tasks like datasets, dashboards, and workspaces.
- Authentication: Use OAuth2 to authenticate your app with Power BI service. An authentication token will ensure that only authorized users can access the embedded reports.
- Embed Token: After authentication, generate an embed token. It grants access to specific Power BI reports or dashboards. This token is essential for securely embedding reports into your app.
- Embedding Reports: After generating the embed token, use Power BI's JavaScript library to embed the report in your app. The JavaScript code allows for customization. You can adjust the report's size and manage user interactions.
The REST API is a versatile tool. It provides full control over the embedding process. It ensures the integration is smooth and secure.
Customizing User Experience: API and UI Customization
Embedding Power BI reports goes beyond just adding visuals to your app. Customization is key. It ensures your end-users have a seamless, intuitive experience.
- Interactivity: The Power BI JavaScript API provides various methods for customizing report behavior. You can enable or disable filters, drilldowns, and page navigation based on user roles or actions in the app.
- Custom Visuals: Power BI lets you use custom visuals in reports. This is useful for embedding reports for specific industries or business processes. These visuals can be designed and incorporated using the Power BI Visuals SDK.
- Responsive Design: The embedded Power BI reports must be responsive. They should dynamically adapt to different resolutions and screen formats. This is particularly important for mobile apps where screen real estate is limited.
Using these options, developers can make Power BI reports feel native to the app they're embedded in.
Security Considerations: Managing Permissions and Access Control
Security is vital when embedding Power BI into web and mobile apps. It's vital to restrict report access to authorized users. This protects data integrity and confidentiality.
- Row-Level Security (RLS): Use RLS to restrict report data access based on the user's role. This guarantees that users have access solely to the data they are permitted to view.
- Token Expiry and Rotation: Embed tokens are time-limited. Developers should implement strategies to rotate tokens seamlessly without disrupting the user experience. This involves automatically refreshing tokens before they expire.
- Secure Data Handling: Always use secure protocols (like HTTPS) for data transmission and to embed tokens. Ensure that sensitive information is encrypted both in transit and at rest.
Follow security best practices. They will reduce risks. They will ensure your embedded Power BI reports meet data protection standards.
How to obtain Power BI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Embedding Power BI in web and mobile apps lets developers add analytics and reporting to their apps. This gives users a more interactive experience. This guide covers everything. It starts with the basics of Power BI Embedded. Then, it ends with advanced security measures. It shows how to embed Power BI into apps.
By following the steps in this guide, you can create a secure Power BI integration. It covers: setting up the environment, using REST APIs, customizing user interactions, and security. As businesses rely on data to make decisions, embedding Power BI can help. It gives users real-time insights in their existing apps.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Power BI stands out as a leading data visualization tool in today's market. Power BI is a favorite for business intelligence. Its interactive reports, real-time data, and dashboards make it so. Embedding Power BI in web or mobile apps lets organizations extend its features to users. It integrates analytics into workflows. This guide helps developers embed Power BI reports and dashboards in their apps. It covers both web and mobile apps. It ensures they are scalable, secure, and user-friendly.
Table Of Contents
- Understanding Power BI Embedded: Key Concepts
- Getting Started: Setting Up Power BI Embedded
- Embedding Power BI Reports Using REST API
- Customizing User Experience: API and UI Customization
- Security Considerations: Managing Permissions and Access Control
- Conclusion
Understanding Power BI Embedded: Key Concepts
Power BI Embedded is a Microsoft service. It lets developers embed Power BI reports, dashboards, and visuals into their apps. It lets users view data without leaving the current platform.
- Power BI Service vs. Power BI Embedded: The Power BI Service is for individuals and businesses to view reports on the Power BI portal. Power BI Embedded is for developers. It lets them integrate Power BI into external apps or websites.
- API and SDK: Power BI has APIs and SDKs for embedding reports. The REST API lets you programmatically interact with the Power BI service. The JavaScript APIs allow you to embed reports with rich customization options.
You must first understand these key differences and tools. They are the first step to embedding Power BI into your app.
Getting Started: Setting Up Power BI Embedded
Before embedding Power BI, developers must set up an environment. They must also obtain the necessary credentials and APIs.
- Azure Subscription: Power BI Embedded is hosted on Azure. So, you need an Azure subscription. Use the Azure portal to set up a Power BI Embedded resource. It will provide the capacity to embed reports.
- App Registration: Register your app in Azure AD to authenticate it with Power BI's API. During this process, you will obtain the client ID and secret, which are necessary for API calls.
- Power BI Workspace: Set up a dedicated workspace in Power BI. It will store your datasets, reports, and dashboards. This workspace will serve as the source for embedding reports into your app.
This infrastructure will let you integrate Power BI into any app.
Embedding Power BI Reports Using REST API
The Power BI REST API lets developers embed reports. They can also manage tasks like datasets, dashboards, and workspaces.
- Authentication: Use OAuth2 to authenticate your app with Power BI service. An authentication token will ensure that only authorized users can access the embedded reports.
- Embed Token: After authentication, generate an embed token. It grants access to specific Power BI reports or dashboards. This token is essential for securely embedding reports into your app.
- Embedding Reports: After generating the embed token, use Power BI's JavaScript library to embed the report in your app. The JavaScript code allows for customization. You can adjust the report's size and manage user interactions.
The REST API is a versatile tool. It provides full control over the embedding process. It ensures the integration is smooth and secure.
Customizing User Experience: API and UI Customization
Embedding Power BI reports goes beyond just adding visuals to your app. Customization is key. It ensures your end-users have a seamless, intuitive experience.
- Interactivity: The Power BI JavaScript API provides various methods for customizing report behavior. You can enable or disable filters, drilldowns, and page navigation based on user roles or actions in the app.
- Custom Visuals: Power BI lets you use custom visuals in reports. This is useful for embedding reports for specific industries or business processes. These visuals can be designed and incorporated using the Power BI Visuals SDK.
- Responsive Design: The embedded Power BI reports must be responsive. They should dynamically adapt to different resolutions and screen formats. This is particularly important for mobile apps where screen real estate is limited.
Using these options, developers can make Power BI reports feel native to the app they're embedded in.
Security Considerations: Managing Permissions and Access Control
Security is vital when embedding Power BI into web and mobile apps. It's vital to restrict report access to authorized users. This protects data integrity and confidentiality.
- Row-Level Security (RLS): Use RLS to restrict report data access based on the user's role. This guarantees that users have access solely to the data they are permitted to view.
- Token Expiry and Rotation: Embed tokens are time-limited. Developers should implement strategies to rotate tokens seamlessly without disrupting the user experience. This involves automatically refreshing tokens before they expire.
- Secure Data Handling: Always use secure protocols (like HTTPS) for data transmission and to embed tokens. Ensure that sensitive information is encrypted both in transit and at rest.
Follow security best practices. They will reduce risks. They will ensure your embedded Power BI reports meet data protection standards.
How to obtain Power BI certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Embedding Power BI in web and mobile apps lets developers add analytics and reporting to their apps. This gives users a more interactive experience. This guide covers everything. It starts with the basics of Power BI Embedded. Then, it ends with advanced security measures. It shows how to embed Power BI into apps.
By following the steps in this guide, you can create a secure Power BI integration. It covers: setting up the environment, using REST APIs, customizing user interactions, and security. As businesses rely on data to make decisions, embedding Power BI can help. It gives users real-time insights in their existing apps.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top Libraries and Tools Compatible with Angular 4 in 2024
Angular 4 is not the latest version of the Angular framework. Still, many developers use it. Those are the reasons. Its stable architecture, familiar ecosystem, and backward compatibility in legacy systems. As we enter 2024, the need to maintain and improve Angular 4 apps remains. Organizations want to support their legacy codebases. To keep apps efficient and up-to-date, developers use modern libraries and tools. They are compatible with Angular 4. This article explores the best libraries and tools for Angular 4. They help developers improve performance, enhance user experiences, and simplify development.
Table Of Contents
- RxJS: Managing Reactive Programming in Angular 4
- NgRx: State Management Simplified for Angular 4
- Angular Material: UI Component Library for Consistent Designs
- Protractor: End-to-End Testing for Angular 4 Applications
- Webpack: Optimizing Angular 4 Application Performance
- Conclusion
RxJS: Managing Reactive Programming in Angular 4
Angular is built on reactive programming. RxJS (Reactive Extensions for JavaScript) powers this approach. RxJS has evolved over time. But its version used with Angular 4 (RxJS 5.x) is still supported and works well for reactive programming in 2024.
- Asynchronous Programming: RxJS lets you handle async events, like HTTP requests, WebSockets, and user inputs. It does this seamlessly.
- Observable Streams: RxJS’s Observable lets Angular 4 apps manage complex data flows. It improves performance by handling streams efficiently.
- Backward Compatibility: With minimal updates, developers can maintain Angular 4 apps. They can use modern RxJS concepts to keep apps scalable and responsive.
Subtopics: RxJS 5.x in modern apps, using Observables in Angular 4, and ways to update RxJS 5.x while keeping legacy support.
NgRx: State Management Simplified for Angular 4
Managing application state can be complex, especially for large-scale applications. NgRx is a Redux-inspired library for Angular. Its older versions work with Angular 4.
- NgRx helps developers manage shared application states. It does so in a predictable way. This is crucial for complex user interactions, data loading, and caching.
- Store, Effects, and Actions: These core NgRx features help Angular 4 developers. They allow for maintainable code by separating concerns. They also provide a unified way to manage the state.
- Ecosystem Compatibility: Newer NgRx versions are for Angular 12+. But, NgRx v4 and v5 work well with Angular 4. They are a powerful state management tool in 2024.
Subtopics: 1. Importance of state management. 2. Using NgRx store in Angular 4. 3. Best practices for integrating NgRx with existing Angular 4 code.
Angular Material: UI Component Library for Consistent Designs
Angular Material is a top library for building modern, responsive UIs. Angular Material has had upgrades, but its older versions work with Angular 4.
- Pre-built UI Components: Developers can use many UI components, like buttons, forms, nav, and modals. This speeds up development.
- Responsive Design: Angular Material keeps apps responsive on all devices. This is key for today's multi-device users.
- Theme Customization: Angular Material makes it easy to customize themes. This ensures the app follows branding guidelines.
Subtopics: Using Angular Material with Angular 4. Customizing Material themes. Leveraging UI components to improve the user experience.
Protractor: End-to-End Testing for Angular 4 Applications
Testing is vital for developing any application. Protractor is a trusted tool for E2E testing in Angular 4 apps. Newer Angular versions have seen alternatives like Cypress. But Protractor is still very compatible with Angular 4.
- Built for Angular: Protractor works well with Angular 4. It's designed to use its internals, making test automation easier.
- Automatic Synchronization: Protractor knows when Angular 4 apps finish loading data. This ensures reliable test execution without extra setup.
- E2E Testing Frameworks: Protractor with Jasmine or Mocha lets developers write tests to simulate user actions. This ensures the app is error-free.
Subtopics: 1. Importance of E2E testing. 2. Setting up Protractor for Angular 4. 3. Writing and running tests with Protractor.
Webpack: Optimizing Angular 4 Application Performance
In 2024, Webpack is vital for Angular 4 apps. It bundles modules and optimizes performance. Angular CLI hides much of Webpack's complexity. But knowing it and configuring it can give developers more control over their app builds.
- Code Splitting and Lazy Loading: Webpack boosts Angular 4 app performance. It splits the code into smaller chunks and lazy-loads them when needed.
- Tree Shaking: This feature removes unused code. It makes the final build lighter and faster.
- Custom Webpack Configurations: Developers can configure Webpack for Angular 4 apps. They can include or exclude specific files, add polyfills, and optimize the build.
Subtopics: 1. Setting up Webpack with Angular 4. 2. Implementing lazy loading with Webpack. 3. Optimizing Angular 4 apps using tree shaking.
How to obtain Angular certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Despite newer versions, Angular 4 is a solid framework for legacy apps. In 2024, developers can use RxJS, NgRx, Angular Material, Protractor, and Webpack. These will keep their apps modern, efficient, and maintainable. These libraries are modern and backward-compatible. They keep Angular 4 apps relevant in a fast-changing tech world. We must keep optimizing and integrating the right tools. This will deliver high-performance, feature-rich applications.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Angular 4 is not the latest version of the Angular framework. Still, many developers use it. Those are the reasons. Its stable architecture, familiar ecosystem, and backward compatibility in legacy systems. As we enter 2024, the need to maintain and improve Angular 4 apps remains. Organizations want to support their legacy codebases. To keep apps efficient and up-to-date, developers use modern libraries and tools. They are compatible with Angular 4. This article explores the best libraries and tools for Angular 4. They help developers improve performance, enhance user experiences, and simplify development.
Table Of Contents
- RxJS: Managing Reactive Programming in Angular 4
- NgRx: State Management Simplified for Angular 4
- Angular Material: UI Component Library for Consistent Designs
- Protractor: End-to-End Testing for Angular 4 Applications
- Webpack: Optimizing Angular 4 Application Performance
- Conclusion
RxJS: Managing Reactive Programming in Angular 4
Angular is built on reactive programming. RxJS (Reactive Extensions for JavaScript) powers this approach. RxJS has evolved over time. But its version used with Angular 4 (RxJS 5.x) is still supported and works well for reactive programming in 2024.
- Asynchronous Programming: RxJS lets you handle async events, like HTTP requests, WebSockets, and user inputs. It does this seamlessly.
- Observable Streams: RxJS’s Observable lets Angular 4 apps manage complex data flows. It improves performance by handling streams efficiently.
- Backward Compatibility: With minimal updates, developers can maintain Angular 4 apps. They can use modern RxJS concepts to keep apps scalable and responsive.
Subtopics: RxJS 5.x in modern apps, using Observables in Angular 4, and ways to update RxJS 5.x while keeping legacy support.
NgRx: State Management Simplified for Angular 4
Managing application state can be complex, especially for large-scale applications. NgRx is a Redux-inspired library for Angular. Its older versions work with Angular 4.
- NgRx helps developers manage shared application states. It does so in a predictable way. This is crucial for complex user interactions, data loading, and caching.
- Store, Effects, and Actions: These core NgRx features help Angular 4 developers. They allow for maintainable code by separating concerns. They also provide a unified way to manage the state.
- Ecosystem Compatibility: Newer NgRx versions are for Angular 12+. But, NgRx v4 and v5 work well with Angular 4. They are a powerful state management tool in 2024.
Subtopics: 1. Importance of state management. 2. Using NgRx store in Angular 4. 3. Best practices for integrating NgRx with existing Angular 4 code.
Angular Material: UI Component Library for Consistent Designs
Angular Material is a top library for building modern, responsive UIs. Angular Material has had upgrades, but its older versions work with Angular 4.
- Pre-built UI Components: Developers can use many UI components, like buttons, forms, nav, and modals. This speeds up development.
- Responsive Design: Angular Material keeps apps responsive on all devices. This is key for today's multi-device users.
- Theme Customization: Angular Material makes it easy to customize themes. This ensures the app follows branding guidelines.
Subtopics: Using Angular Material with Angular 4. Customizing Material themes. Leveraging UI components to improve the user experience.
Protractor: End-to-End Testing for Angular 4 Applications
Testing is vital for developing any application. Protractor is a trusted tool for E2E testing in Angular 4 apps. Newer Angular versions have seen alternatives like Cypress. But Protractor is still very compatible with Angular 4.
- Built for Angular: Protractor works well with Angular 4. It's designed to use its internals, making test automation easier.
- Automatic Synchronization: Protractor knows when Angular 4 apps finish loading data. This ensures reliable test execution without extra setup.
- E2E Testing Frameworks: Protractor with Jasmine or Mocha lets developers write tests to simulate user actions. This ensures the app is error-free.
Subtopics: 1. Importance of E2E testing. 2. Setting up Protractor for Angular 4. 3. Writing and running tests with Protractor.
Webpack: Optimizing Angular 4 Application Performance
In 2024, Webpack is vital for Angular 4 apps. It bundles modules and optimizes performance. Angular CLI hides much of Webpack's complexity. But knowing it and configuring it can give developers more control over their app builds.
- Code Splitting and Lazy Loading: Webpack boosts Angular 4 app performance. It splits the code into smaller chunks and lazy-loads them when needed.
- Tree Shaking: This feature removes unused code. It makes the final build lighter and faster.
- Custom Webpack Configurations: Developers can configure Webpack for Angular 4 apps. They can include or exclude specific files, add polyfills, and optimize the build.
Subtopics: 1. Setting up Webpack with Angular 4. 2. Implementing lazy loading with Webpack. 3. Optimizing Angular 4 apps using tree shaking.
How to obtain Angular certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Despite newer versions, Angular 4 is a solid framework for legacy apps. In 2024, developers can use RxJS, NgRx, Angular Material, Protractor, and Webpack. These will keep their apps modern, efficient, and maintainable. These libraries are modern and backward-compatible. They keep Angular 4 apps relevant in a fast-changing tech world. We must keep optimizing and integrating the right tools. This will deliver high-performance, feature-rich applications.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top Video Content Trends to Watch and Dominate in 2024!
In 2024, video content rules the digital world. It shapes how brands engage audiences and influences consumer behavior. New tech, social media trends, and changing viewer tastes make video marketing vital for businesses. It helps them stay relevant. In 2024, trends in short videos and live streaming will change how marketers create content. This guide will explore the top video trends for this year. It will show how businesses can use them for maximum impact.
Table Of Contents
- Short-Form Video Content: The Power of Snappy Messaging
- Live Streaming: Authenticity and Real-Time Engagement
- Interactive Videos: Elevating Viewer Participation
- Shoppable Videos: Seamless Integration of Commerce and Content
- AI-Driven Personalization: Customizing Video Content for Every Viewer
- Conclusion
Short-Form Video Content: The Power of Snappy Messaging
In 2024, short-form videos are still popular. TikTok, Instagram Reels, and YouTube Shorts lead the way. With shorter attention spans, brands must create concise, engaging content to captivate audiences quickly.
- Why Short-Form Videos Matter: These videos (under 60 seconds) are easy to digest and share. They're perfect for viral content. They're perfect for showcasing quick product demos, teasers, or behind-the-scenes clips.
- Platforms to Leverage: TikTok is still big. But, Instagram and YouTube have added short videos. Brands can now reach different demographics across platforms.
- Best Practices: Keep the content focused, visually appealing, and ensure a clear call-to-action. Capture the viewer's attention within the opening moments. This is when they decide to keep watching or scroll past.
Live Streaming: Authenticity and Real-Time Engagement
Live streaming has changed from a novelty into a powerful tool. Brands now use it to build authenticity and engage their audience in real time. In 2024, live video is very popular. It gives businesses a chance to connect directly with consumers.
- Why Live Streaming is Effective: Live content is urgent and exclusive. It draws viewers in. It also lets brands show their human side through unedited, authentic communication.
- Popular Platforms: Facebook Live, Instagram Live, and YouTube Live are popular. But, Twitch is gaining ground for non-gaming content. LinkedIn Live is becoming a key hub for business and leadership broadcasts.
- Types of Live Streams: Popular formats include product launches, Q&As, and behind-the-scenes content. Live events are also popular. Brands can use live streaming to provide real-time updates, promote products, or engage with influencers and followers.
Interactive Videos: Elevating Viewer Participation
As engagement becomes a top priority, interactive videos are rising in popularity. These videos let users make choices that affect the content. This fosters a more tailored and engaging experience.
- Why Interaction Matters: Interactive videos engage viewers by making them participants, not just watchers. This can increase retention rates and make content more memorable.
- Key Features of Interactive Videos: They may have clickable hotspots, quizzes, or branching paths. These can change the video's course. This trend can be particularly effective in product demonstrations or educational content.
- How to Implement Interactive Videos: Use YouTube Cards, Wistia, or custom tools. Make sure the interactivity adds value. It must not hurt the viewing experience.
Shoppable Videos: Seamless Integration of Commerce and Content
E-commerce and video content are converging in 2024, with shoppable videos gaining traction. These videos let viewers shop directly from them. This provides a smooth, easy buying experience.
- Shoppable Videos Are a Game-Changer: They speed up buying after discovery. This reduces drop-offs and makes it easier for consumers to act on their impulses. Shoppable videos can drive higher conversion rates by capitalizing on immediate interest.
- Shoppable Content Platforms: Instagram and YouTube now have shoppable features. Standalone platforms like Amazon Live are also gaining ground. Even TikTok has incorporated shopping functionalities into its video format.
- How to Create Shoppable Videos: Use clickable tags or links to highlight key products. They should lead directly to your store. Ensure the video feels natural, not too promotional. It should blend entertainment with shopping.
AI-Driven Personalization: Customizing Video Content for Every Viewer
Artificial intelligence (AI) is revolutionizing video content by enabling hyper-personalized experiences for viewers. In 2024, AI video marketing will let brands customize content for users. This will make videos more relevant and engaging.
- How AI Enhances Video Content: AI can analyze viewer data. It can then suggest personalized videos. It looks at their behavior, preferences, and demographics. AI tools can automate video edits and subtitles. They can make content creation more efficient.
- Personalized Recommendations: Streaming platforms like Netflix and YouTube use AI to recommend videos. Businesses can use this tech to personalize ads and product suggestions. They can even tailor video content based on user profiles.
- Implement AI in Video Strategies: Use AI tools like Vidyard. They track viewer data to deliver tailored content. Dynamic video creation tools allow for quick edits based on user segmentation.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, video content will evolve. Businesses must stay ahead of trends to capture attention and drive engagement. Short videos are great for quickly reaching a wide audience. Live streaming and interactive videos engage viewers in real-time and boost participation. Shoppable videos speed up the customer journey, turning interest into sales. AI-driven personalization makes the content relevant and engaging for each viewer. By embracing these trends, brands can create compelling videos. They will resonate with audiences and drive results.
The future of video marketing is to adapt and innovate. As technology and consumer preferences shift, brands must be agile. Those that adapt will better connect with their audience and stand out in the crowded digital landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In 2024, video content rules the digital world. It shapes how brands engage audiences and influences consumer behavior. New tech, social media trends, and changing viewer tastes make video marketing vital for businesses. It helps them stay relevant. In 2024, trends in short videos and live streaming will change how marketers create content. This guide will explore the top video trends for this year. It will show how businesses can use them for maximum impact.
Table Of Contents
- Short-Form Video Content: The Power of Snappy Messaging
- Live Streaming: Authenticity and Real-Time Engagement
- Interactive Videos: Elevating Viewer Participation
- Shoppable Videos: Seamless Integration of Commerce and Content
- AI-Driven Personalization: Customizing Video Content for Every Viewer
- Conclusion
Short-Form Video Content: The Power of Snappy Messaging
In 2024, short-form videos are still popular. TikTok, Instagram Reels, and YouTube Shorts lead the way. With shorter attention spans, brands must create concise, engaging content to captivate audiences quickly.
- Why Short-Form Videos Matter: These videos (under 60 seconds) are easy to digest and share. They're perfect for viral content. They're perfect for showcasing quick product demos, teasers, or behind-the-scenes clips.
- Platforms to Leverage: TikTok is still big. But, Instagram and YouTube have added short videos. Brands can now reach different demographics across platforms.
- Best Practices: Keep the content focused, visually appealing, and ensure a clear call-to-action. Capture the viewer's attention within the opening moments. This is when they decide to keep watching or scroll past.
Live Streaming: Authenticity and Real-Time Engagement
Live streaming has changed from a novelty into a powerful tool. Brands now use it to build authenticity and engage their audience in real time. In 2024, live video is very popular. It gives businesses a chance to connect directly with consumers.
- Why Live Streaming is Effective: Live content is urgent and exclusive. It draws viewers in. It also lets brands show their human side through unedited, authentic communication.
- Popular Platforms: Facebook Live, Instagram Live, and YouTube Live are popular. But, Twitch is gaining ground for non-gaming content. LinkedIn Live is becoming a key hub for business and leadership broadcasts.
- Types of Live Streams: Popular formats include product launches, Q&As, and behind-the-scenes content. Live events are also popular. Brands can use live streaming to provide real-time updates, promote products, or engage with influencers and followers.
Interactive Videos: Elevating Viewer Participation
As engagement becomes a top priority, interactive videos are rising in popularity. These videos let users make choices that affect the content. This fosters a more tailored and engaging experience.
- Why Interaction Matters: Interactive videos engage viewers by making them participants, not just watchers. This can increase retention rates and make content more memorable.
- Key Features of Interactive Videos: They may have clickable hotspots, quizzes, or branching paths. These can change the video's course. This trend can be particularly effective in product demonstrations or educational content.
- How to Implement Interactive Videos: Use YouTube Cards, Wistia, or custom tools. Make sure the interactivity adds value. It must not hurt the viewing experience.
Shoppable Videos: Seamless Integration of Commerce and Content
E-commerce and video content are converging in 2024, with shoppable videos gaining traction. These videos let viewers shop directly from them. This provides a smooth, easy buying experience.
- Shoppable Videos Are a Game-Changer: They speed up buying after discovery. This reduces drop-offs and makes it easier for consumers to act on their impulses. Shoppable videos can drive higher conversion rates by capitalizing on immediate interest.
- Shoppable Content Platforms: Instagram and YouTube now have shoppable features. Standalone platforms like Amazon Live are also gaining ground. Even TikTok has incorporated shopping functionalities into its video format.
- How to Create Shoppable Videos: Use clickable tags or links to highlight key products. They should lead directly to your store. Ensure the video feels natural, not too promotional. It should blend entertainment with shopping.
AI-Driven Personalization: Customizing Video Content for Every Viewer
Artificial intelligence (AI) is revolutionizing video content by enabling hyper-personalized experiences for viewers. In 2024, AI video marketing will let brands customize content for users. This will make videos more relevant and engaging.
- How AI Enhances Video Content: AI can analyze viewer data. It can then suggest personalized videos. It looks at their behavior, preferences, and demographics. AI tools can automate video edits and subtitles. They can make content creation more efficient.
- Personalized Recommendations: Streaming platforms like Netflix and YouTube use AI to recommend videos. Businesses can use this tech to personalize ads and product suggestions. They can even tailor video content based on user profiles.
- Implement AI in Video Strategies: Use AI tools like Vidyard. They track viewer data to deliver tailored content. Dynamic video creation tools allow for quick edits based on user segmentation.
How to obtain Digital Marketing certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In 2024, video content will evolve. Businesses must stay ahead of trends to capture attention and drive engagement. Short videos are great for quickly reaching a wide audience. Live streaming and interactive videos engage viewers in real-time and boost participation. Shoppable videos speed up the customer journey, turning interest into sales. AI-driven personalization makes the content relevant and engaging for each viewer. By embracing these trends, brands can create compelling videos. They will resonate with audiences and drive results.
The future of video marketing is to adapt and innovate. As technology and consumer preferences shift, brands must be agile. Those that adapt will better connect with their audience and stand out in the crowded digital landscape.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Globalization and Quality Management Standards Worldwide
In today's globalized world, managing quality standards worldwide is more important than ever. As businesses expand and enter new markets, they must ensure quality. It's key to success. This article will explore globalization's impact on quality management. It will cover the challenges and strategies for managing global standards. It will also discuss best practices for ensuring quality in international operations.\
The Impact of Globalization on Quality Management
Globalization has brought about a dramatic shift in the way businesses operate. With global markets and linked economies, companies must now compete worldwide. So, quality management is now a global concern. It is key to success in the global marketplace.
A major challenge of globalization is ensuring quality across diverse markets. Different countries have different rules and cultures. They affect how people view products and services. To manage global quality standards, one must understand and adapt to local differences. It requires a commitment to the highest standards in every market.
Globalization has greatly affected quality management. It has increased the need for standardized processes in diverse markets. Companies must now follow international quality standards, like ISO 9001. This ensures product consistency and compliance worldwide. As supply chains grow more complex, quality management systems must evolve. They must address cross-border challenges, cultural differences, and varying regulations.
Strategies for Managing Global Standards
To manage quality standards worldwide, businesses must build strong, adaptable quality management systems. They must handle the complexities of the global marketplace. This means using standard processes and procedures. They will ensure consistency and reliability in all operations. A key strategy for managing global standards is a quality assurance program. It should cover all aspects of the business. This includes product development and customer service.
By monitoring and evaluating quality metrics, companies can find areas to improve. They can then take action to prevent quality issues. In addition, businesses must prioritize quality control throughout the supply chain. This means working closely with suppliers and partners. We must meet quality standards at every stage of production. By setting clear guidelines and auditing regularly, companies can reduce quality issues. This will help ensure consistency across all operations.
Managing global standards requires a good grasp of international rules and regional compliance. Companies must standardize processes. But, they must allow flexibility to adapt to local laws and cultures. Regular audits, cross-border communication, and training are vital. They ensure quality and consistency across all operations.
Best Practices for Ensuring Quality Worldwide
To manage global standards, businesses can adopt best practices. They ensure quality at every level. Some of these practices include:
-
Invest in training programs to ensure employees know and follow quality standards.
-
Using quality management tools to improve processes and find issues.
-
Conducting regular quality audits to monitor compliance and identify potential risks
-
Establishing key performance indicators (KPIs) to measure the effectiveness of quality management systems
-
Implementing a culture of continuous improvement to drive innovation and maintain high-quality standards
-
Work with industry partners and regulators. Stay updated on quality trends and rules. By following best practices and committing to quality, businesses can meet global standards. This will help them succeed in a competitive global market.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, globalization has changed how businesses operate. It requires a more strategic and proactive approach to quality management. Businesses can ensure excellence in operations with strong quality systems and controls. They should also follow best practices for managing global standards. This will ensure consistency and reliability. In today's global economy, managing quality worldwide is a must. It is a competitive advantage that can drive growth, innovation, and success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's globalized world, managing quality standards worldwide is more important than ever. As businesses expand and enter new markets, they must ensure quality. It's key to success. This article will explore globalization's impact on quality management. It will cover the challenges and strategies for managing global standards. It will also discuss best practices for ensuring quality in international operations.\
The Impact of Globalization on Quality Management
Globalization has brought about a dramatic shift in the way businesses operate. With global markets and linked economies, companies must now compete worldwide. So, quality management is now a global concern. It is key to success in the global marketplace.
A major challenge of globalization is ensuring quality across diverse markets. Different countries have different rules and cultures. They affect how people view products and services. To manage global quality standards, one must understand and adapt to local differences. It requires a commitment to the highest standards in every market.
Globalization has greatly affected quality management. It has increased the need for standardized processes in diverse markets. Companies must now follow international quality standards, like ISO 9001. This ensures product consistency and compliance worldwide. As supply chains grow more complex, quality management systems must evolve. They must address cross-border challenges, cultural differences, and varying regulations.
Strategies for Managing Global Standards
To manage quality standards worldwide, businesses must build strong, adaptable quality management systems. They must handle the complexities of the global marketplace. This means using standard processes and procedures. They will ensure consistency and reliability in all operations. A key strategy for managing global standards is a quality assurance program. It should cover all aspects of the business. This includes product development and customer service.
By monitoring and evaluating quality metrics, companies can find areas to improve. They can then take action to prevent quality issues. In addition, businesses must prioritize quality control throughout the supply chain. This means working closely with suppliers and partners. We must meet quality standards at every stage of production. By setting clear guidelines and auditing regularly, companies can reduce quality issues. This will help ensure consistency across all operations.
Managing global standards requires a good grasp of international rules and regional compliance. Companies must standardize processes. But, they must allow flexibility to adapt to local laws and cultures. Regular audits, cross-border communication, and training are vital. They ensure quality and consistency across all operations.
Best Practices for Ensuring Quality Worldwide
To manage global standards, businesses can adopt best practices. They ensure quality at every level. Some of these practices include:
-
Invest in training programs to ensure employees know and follow quality standards.
-
Using quality management tools to improve processes and find issues.
-
Conducting regular quality audits to monitor compliance and identify potential risks
-
Establishing key performance indicators (KPIs) to measure the effectiveness of quality management systems
-
Implementing a culture of continuous improvement to drive innovation and maintain high-quality standards
-
Work with industry partners and regulators. Stay updated on quality trends and rules. By following best practices and committing to quality, businesses can meet global standards. This will help them succeed in a competitive global market.
How to obtain Quality Management certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, globalization has changed how businesses operate. It requires a more strategic and proactive approach to quality management. Businesses can ensure excellence in operations with strong quality systems and controls. They should also follow best practices for managing global standards. This will ensure consistency and reliability. In today's global economy, managing quality worldwide is a must. It is a competitive advantage that can drive growth, innovation, and success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
How Agile Maturity Shapes the Evolving Role of a CSPO??
Agile methodology has transformed the way organizations approach project management and product development. As agile practices grow in popularity, the CSPO role is now vital to agile project success. This article will explore how agile maturity affects the CSPO's role. It will also discuss how to use this position to drive agile success.
Agile Maturity and Its Influence on the CSPO's Role:
As organizations mature in their agile journey, the CSPO's role becomes critical. They must ensure that agile principles are applied effectively. A highly mature agile team needs a skilled CSPO. They must lead product development and collaborate with the agile team. The CSPO is key to engaging stakeholders and prioritizing the backlog. They must ensure the team delivers value to the business.
The Evolution of the CSPO Role in Agile Projects:
With the increasing adoption of agile practices, the role of the CSPO has evolved to encompass a broader set of responsibilities. The CSPO now promotes a culture of continuous improvement and innovation in the agile team. In addition, they manage the product backlog and define requirements. The CSPO also acts as a liaison between the business stakeholders and the agile team, ensuring that the product meets the needs of the end-users.
The Importance of Agile Leadership Skills for CSPOs:
CSPOs must possess strong leadership skills to effectively lead agile teams and drive project success. CSPOs must excel at communication, stakeholder engagement, and decision-making. These skills are vital for navigating complex agile projects. CSPOs must deeply understand agile principles and practices. This is to guide the team in delivering high-quality products and achieving business goals.
Agile leadership skills are crucial for Certified Scrum Product Owners (CSPOs). They enable effective collaboration, build trust, and empower teams to own their work. By being transparent and adaptable, CSPOs can navigate challenges. They can align the product vision with stakeholders' needs. This will drive better outcomes. Also, strong agile leadership promotes constant learning and improvement. These are vital for thriving in today's fast-paced, ever-changing market.
The Role of the CSPO in Agile Culture Change:
As organizations adopt agile methods, the CSPO must drive cultural change and promote an agile mindset. CSPOs must champion agile values and principles. They should foster a collaborative, adaptive environment where teams can thrive. CSPOs can enable agile adoption and agility. They should be servant leaders and promote self-organization.
The Certified Scrum Product Owner (CSPO) drives agile culture change in organizations. They do this by bridging stakeholders and development teams. The CSPO ensures everyone aligns with agile principles. They do this by fostering collaboration, transparency, and a shared vision for product delivery. Also, the CSPO's focus on customer feedback boosts a culture of constant improvement. It helps them adapt to changing market needs.
Benefits of Agile Maturity for CSPOs:
Agile maturity brings a host of benefits for CSPOs, enabling them to drive agile success and deliver value to the business. Highly mature agile teams can respond to change and adapt to market demands. They can also deliver high-quality products on time. CSPOs in mature agile environments can improve their leadership skills. They can also use agile techniques and work with cross-functional teams to succeed.
Higher agile maturity helps Certified Scrum Product Owners (CSPOs). It boosts collaboration in cross-functional teams. This leads to more innovative and efficient product development. As agile maturity grows, CSPOs can better use data and feedback. This will help them adapt faster to market changes and customer needs. In the end, better agile maturity helps CSPOs. They can deliver higher-quality products that align with business goals. This fosters long-term success.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, agile maturity greatly affects the CSPO's role. It requires CSPOs to have diverse skills to drive agile success. As organizations evolve in their agile journey, CSPOs are key. They promote agile values, foster team collaboration, and deliver business value. By embracing agile principles, CSPOs can lead their teams to new heights in agile project management.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Agile methodology has transformed the way organizations approach project management and product development. As agile practices grow in popularity, the CSPO role is now vital to agile project success. This article will explore how agile maturity affects the CSPO's role. It will also discuss how to use this position to drive agile success.
Agile Maturity and Its Influence on the CSPO's Role:
As organizations mature in their agile journey, the CSPO's role becomes critical. They must ensure that agile principles are applied effectively. A highly mature agile team needs a skilled CSPO. They must lead product development and collaborate with the agile team. The CSPO is key to engaging stakeholders and prioritizing the backlog. They must ensure the team delivers value to the business.
The Evolution of the CSPO Role in Agile Projects:
With the increasing adoption of agile practices, the role of the CSPO has evolved to encompass a broader set of responsibilities. The CSPO now promotes a culture of continuous improvement and innovation in the agile team. In addition, they manage the product backlog and define requirements. The CSPO also acts as a liaison between the business stakeholders and the agile team, ensuring that the product meets the needs of the end-users.
The Importance of Agile Leadership Skills for CSPOs:
CSPOs must possess strong leadership skills to effectively lead agile teams and drive project success. CSPOs must excel at communication, stakeholder engagement, and decision-making. These skills are vital for navigating complex agile projects. CSPOs must deeply understand agile principles and practices. This is to guide the team in delivering high-quality products and achieving business goals.
Agile leadership skills are crucial for Certified Scrum Product Owners (CSPOs). They enable effective collaboration, build trust, and empower teams to own their work. By being transparent and adaptable, CSPOs can navigate challenges. They can align the product vision with stakeholders' needs. This will drive better outcomes. Also, strong agile leadership promotes constant learning and improvement. These are vital for thriving in today's fast-paced, ever-changing market.
The Role of the CSPO in Agile Culture Change:
As organizations adopt agile methods, the CSPO must drive cultural change and promote an agile mindset. CSPOs must champion agile values and principles. They should foster a collaborative, adaptive environment where teams can thrive. CSPOs can enable agile adoption and agility. They should be servant leaders and promote self-organization.
The Certified Scrum Product Owner (CSPO) drives agile culture change in organizations. They do this by bridging stakeholders and development teams. The CSPO ensures everyone aligns with agile principles. They do this by fostering collaboration, transparency, and a shared vision for product delivery. Also, the CSPO's focus on customer feedback boosts a culture of constant improvement. It helps them adapt to changing market needs.
Benefits of Agile Maturity for CSPOs:
Agile maturity brings a host of benefits for CSPOs, enabling them to drive agile success and deliver value to the business. Highly mature agile teams can respond to change and adapt to market demands. They can also deliver high-quality products on time. CSPOs in mature agile environments can improve their leadership skills. They can also use agile techniques and work with cross-functional teams to succeed.
Higher agile maturity helps Certified Scrum Product Owners (CSPOs). It boosts collaboration in cross-functional teams. This leads to more innovative and efficient product development. As agile maturity grows, CSPOs can better use data and feedback. This will help them adapt faster to market changes and customer needs. In the end, better agile maturity helps CSPOs. They can deliver higher-quality products that align with business goals. This fosters long-term success.
How to obtain CSPO certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, agile maturity greatly affects the CSPO's role. It requires CSPOs to have diverse skills to drive agile success. As organizations evolve in their agile journey, CSPOs are key. They promote agile values, foster team collaboration, and deliver business value. By embracing agile principles, CSPOs can lead their teams to new heights in agile project management.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Key Practices and Insights: Agile to DevSecOps Transition
In fast-paced software development, we must now shift from Agile to DevSecOps. Cybersecurity threats are rising. We must integrate security into the development pipeline. This is essential to mitigate risks and protect valuable data. This article will discuss key practices for organizations. It will help them transition from Agile to DevSecOps.
Agile Principles and Practices:
Agile methods have long aimed to boost collaboration in software development. They seek to increase speed and efficiency. Agile teams can deliver value to customers faster than waterfall methods. They do this by breaking projects into manageable tasks and iterating quickly. However, in today's digital landscape, cybersecurity concerns cannot be overlooked.
Stress the need to deliver value to customers. Use iterative development and constant feedback to do this. Agile methods boost teamwork and flexibility. They help teams quickly adapt to changing requirements. This keeps projects aligned with users' needs. These principles boost team dynamics. They also drive innovation and efficiency in the project lifecycle.
Security Culture:
A security culture in Agile teams is key to moving to DevSecOps. Organizations can make security a top priority in development. They should foster a mindset of security awareness and responsibility among team members.
A strong security culture is vital. It helps organizations manage risks and protect sensitive information. It creates a culture where employees prioritize cybersecurity. They know their role in protecting the organization. They also train for it. Integrating security awareness into daily work can create a vigilant, resilient workforce.
Automation and Collaboration
One of the key practices in DevSecOps is automation. Automating security testing, scanning, and threat modeling can help. It can find and fix security issues early in development. It's vital that development, operations, and security teams collaborate. This will ensure security is integrated into the development process.
In today's fast-paced business world, automation tools can boost productivity. They work best when integrated with collaboration platforms to streamline workflows. Automation of repetitive tasks lets teams focus on strategy and creativity. This synergy improves communication among team members. It speeds up project delivery and boosts efficiency.
Continuous Integration and Delivery
Continuous integration and delivery are fundamental practices in Agile and DevSecOps. Organizations can find and fix vulnerabilities by adding security tests to the CI/CD pipeline. This must be done before they reach production. This ensures that software is not only delivered quickly but also securely.
CI/CD is a modern software practice. It lets teams frequently integrate code changes and automate delivery. CI/CD helps teams find issues early in development. This leads to better software and faster releases. This approach boosts team collaboration. It also enables faster responses to customer feedback and market changes.
Secure Coding Practices
Secure coding practices are a cornerstone of DevSecOps. Developers can lower the risk of common flaws, like injection attacks and cross-site scripting. They should follow best practices for secure development. These include input validation, output encoding, and proper error handling.
They are rules and methods to prevent flaws in software. Secure coding standards can reduce the risk of attacks. These include SQL injection, cross-site scripting (XSS), and buffer overflows. These practices boost app security and build user trust. They also ensure compliance with regulations.
Risk Assessment and Security Automation
Risk assessment is another key practice in DevSecOps. Organizations can find and fix security risks. They should do regular risk assessments and use security automation tools. This proactive approach to security is essential in today's threat landscape.
In today's fast-changing digital world, we must protect sensitive data. Effective risk assessment and security automation are key to this. They help maintain our organization's integrity. Automated tools let businesses monitor their systems for vulnerabilities. They can find and fix threats in real time. This proactive approach improves security. It lets teams focus on strategy, not manual tasks.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, organizations must shift from Agile to DevSecOps. This is vital to improve their software development security. Integrating security practices into Agile can help organizations. It can boost security awareness, automate testing, and improve team work. Key practices can help organizations deliver their software quickly and securely.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In fast-paced software development, we must now shift from Agile to DevSecOps. Cybersecurity threats are rising. We must integrate security into the development pipeline. This is essential to mitigate risks and protect valuable data. This article will discuss key practices for organizations. It will help them transition from Agile to DevSecOps.
Agile Principles and Practices:
Agile methods have long aimed to boost collaboration in software development. They seek to increase speed and efficiency. Agile teams can deliver value to customers faster than waterfall methods. They do this by breaking projects into manageable tasks and iterating quickly. However, in today's digital landscape, cybersecurity concerns cannot be overlooked.
Stress the need to deliver value to customers. Use iterative development and constant feedback to do this. Agile methods boost teamwork and flexibility. They help teams quickly adapt to changing requirements. This keeps projects aligned with users' needs. These principles boost team dynamics. They also drive innovation and efficiency in the project lifecycle.
Security Culture:
A security culture in Agile teams is key to moving to DevSecOps. Organizations can make security a top priority in development. They should foster a mindset of security awareness and responsibility among team members.
A strong security culture is vital. It helps organizations manage risks and protect sensitive information. It creates a culture where employees prioritize cybersecurity. They know their role in protecting the organization. They also train for it. Integrating security awareness into daily work can create a vigilant, resilient workforce.
Automation and Collaboration
One of the key practices in DevSecOps is automation. Automating security testing, scanning, and threat modeling can help. It can find and fix security issues early in development. It's vital that development, operations, and security teams collaborate. This will ensure security is integrated into the development process.
In today's fast-paced business world, automation tools can boost productivity. They work best when integrated with collaboration platforms to streamline workflows. Automation of repetitive tasks lets teams focus on strategy and creativity. This synergy improves communication among team members. It speeds up project delivery and boosts efficiency.
Continuous Integration and Delivery
Continuous integration and delivery are fundamental practices in Agile and DevSecOps. Organizations can find and fix vulnerabilities by adding security tests to the CI/CD pipeline. This must be done before they reach production. This ensures that software is not only delivered quickly but also securely.
CI/CD is a modern software practice. It lets teams frequently integrate code changes and automate delivery. CI/CD helps teams find issues early in development. This leads to better software and faster releases. This approach boosts team collaboration. It also enables faster responses to customer feedback and market changes.
Secure Coding Practices
Secure coding practices are a cornerstone of DevSecOps. Developers can lower the risk of common flaws, like injection attacks and cross-site scripting. They should follow best practices for secure development. These include input validation, output encoding, and proper error handling.
They are rules and methods to prevent flaws in software. Secure coding standards can reduce the risk of attacks. These include SQL injection, cross-site scripting (XSS), and buffer overflows. These practices boost app security and build user trust. They also ensure compliance with regulations.
Risk Assessment and Security Automation
Risk assessment is another key practice in DevSecOps. Organizations can find and fix security risks. They should do regular risk assessments and use security automation tools. This proactive approach to security is essential in today's threat landscape.
In today's fast-changing digital world, we must protect sensitive data. Effective risk assessment and security automation are key to this. They help maintain our organization's integrity. Automated tools let businesses monitor their systems for vulnerabilities. They can find and fix threats in real time. This proactive approach improves security. It lets teams focus on strategy, not manual tasks.
How to obtain Agile and Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, organizations must shift from Agile to DevSecOps. This is vital to improve their software development security. Integrating security practices into Agile can help organizations. It can boost security awareness, automate testing, and improve team work. Key practices can help organizations deliver their software quickly and securely.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
GitOps & Infrastructure as Code for Efficient Management
Do you want to improve your software development process? Do you want to boost team collaboration and infrastructure management? If so, GitOps and Infrastructure as Code (IaC) could be the game-changer you've been searching for. This article will explore GitOps and IaC. We will cover their benefits, best practices, and implementation strategies. Our goal is to help you improve your DevOps practices.
Understanding GitOps and Infrastructure as Code
What is GitOps?
GitOps is a methodology that leverages Git as the source of truth for infrastructure automation. Storing declarative infrastructure code in Git repositories lets teams track changes. It also helps them manage their infrastructure. It also enables version control. This approach follows the principles of versioning, collaboration, and automation. It makes continuous delivery and scalability easier to achieve.
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) means using code to manage and provision infrastructure. It replaces manual processes. IaC means writing infrastructure configs in code. Tools like Terraform, Ansible, and Chef are used. This allows for automation, versioning, and repeatable deployments. This practice promotes consistency, scalability, and reliability in infrastructure management.
Infrastructure as Code (IaC) is a modern way to manage IT infrastructure. It uses code instead of manual processes. This allows for automation and version control. Using IaC, teams can consistently define and provision infrastructure. This improves reliability and speeds up deployment. It also promotes collaboration between dev and ops teams. Treating infrastructure as software enables CI/CD practices.
Benefits of GitOps and IaC
GitOps and IaC have many benefits. They improve automation and consistency in deployments. This reduces human error. It also makes infrastructure changes easy to track. Version control for apps and infrastructure lets teams roll back changes. It also keeps a clear audit trail. This improves collaboration and transparency across DevOps teams. Also, GitOps speeds up delivery. It allows continuous deployment. This helps organizations quickly meet changing market and app demands.
-
Streamlined Deployment: GitOps and IaC allow teams to automate deployments. This cuts manual errors and speeds up release cycles.
-
Improved Collaboration: A shared repository for configs helps teams work together. They can track changes easily.
-
Improved Version Control: Git has strong version control. It lets teams roll back changes, track modifications, and ensure consistency across environments.
-
IaC lets teams quickly scale infrastructure based on demand. This ensures optimal resource use.
-
Enhanced Security: By codifying security best practices into configs, teams can improve security. This will help their environments.
Best Practices for GitOps and IaC Implementation
-
Use Version Control: Store all infrastructure configs in a version control system, like GitHub. This tracks changes and manages updates.
-
Automate Deployments: Use tools like Jenkins or GitLab CI/CD to automate deployment pipelines. This will streamline the release process.
-
Adopt Infrastructure as Code Tools. Use Terraform, Ansible, or Helm. They can write infrastructure configurations and automate provisioning.
-
Implement Code Review Process: Set up a code review process. It should ensure code quality, consistency, and security.
-
Monitor Infrastructure Changes: Set up systems to track changes and detect anomalies in real-time.
Challenges of GitOps and IaC
While GitOps and IaC offer numerous benefits, they also come with their own set of challenges, including:
-
Learning Curve: Teams may need to acquire new skills and knowledge to effectively implement GitOps and IaC practices.
-
Complexity: Managing infrastructure as code can introduce complexity, especially in large-scale environments.
-
Security Risks: Improperly configured infrastructure code can introduce security vulnerabilities and risks.
-
Tooling and Integration: It's tough to integrate different tools and platforms.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GitOps and Infrastructure as Code are powerful. They can transform how organizations manage their infrastructure and improve their DevOps. By embracing automation, collaboration, and version control, teams can improve their software development. They can deploy faster, and their software will be more reliable and scalable. With the right tools, practices, and mindset, GitOps and IaC can lead to a more efficient, agile DevOps environment.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Do you want to improve your software development process? Do you want to boost team collaboration and infrastructure management? If so, GitOps and Infrastructure as Code (IaC) could be the game-changer you've been searching for. This article will explore GitOps and IaC. We will cover their benefits, best practices, and implementation strategies. Our goal is to help you improve your DevOps practices.
Understanding GitOps and Infrastructure as Code
What is GitOps?
GitOps is a methodology that leverages Git as the source of truth for infrastructure automation. Storing declarative infrastructure code in Git repositories lets teams track changes. It also helps them manage their infrastructure. It also enables version control. This approach follows the principles of versioning, collaboration, and automation. It makes continuous delivery and scalability easier to achieve.
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) means using code to manage and provision infrastructure. It replaces manual processes. IaC means writing infrastructure configs in code. Tools like Terraform, Ansible, and Chef are used. This allows for automation, versioning, and repeatable deployments. This practice promotes consistency, scalability, and reliability in infrastructure management.
Infrastructure as Code (IaC) is a modern way to manage IT infrastructure. It uses code instead of manual processes. This allows for automation and version control. Using IaC, teams can consistently define and provision infrastructure. This improves reliability and speeds up deployment. It also promotes collaboration between dev and ops teams. Treating infrastructure as software enables CI/CD practices.
Benefits of GitOps and IaC
GitOps and IaC have many benefits. They improve automation and consistency in deployments. This reduces human error. It also makes infrastructure changes easy to track. Version control for apps and infrastructure lets teams roll back changes. It also keeps a clear audit trail. This improves collaboration and transparency across DevOps teams. Also, GitOps speeds up delivery. It allows continuous deployment. This helps organizations quickly meet changing market and app demands.
-
Streamlined Deployment: GitOps and IaC allow teams to automate deployments. This cuts manual errors and speeds up release cycles.
-
Improved Collaboration: A shared repository for configs helps teams work together. They can track changes easily.
-
Improved Version Control: Git has strong version control. It lets teams roll back changes, track modifications, and ensure consistency across environments.
-
IaC lets teams quickly scale infrastructure based on demand. This ensures optimal resource use.
-
Enhanced Security: By codifying security best practices into configs, teams can improve security. This will help their environments.
Best Practices for GitOps and IaC Implementation
-
Use Version Control: Store all infrastructure configs in a version control system, like GitHub. This tracks changes and manages updates.
-
Automate Deployments: Use tools like Jenkins or GitLab CI/CD to automate deployment pipelines. This will streamline the release process.
-
Adopt Infrastructure as Code Tools. Use Terraform, Ansible, or Helm. They can write infrastructure configurations and automate provisioning.
-
Implement Code Review Process: Set up a code review process. It should ensure code quality, consistency, and security.
-
Monitor Infrastructure Changes: Set up systems to track changes and detect anomalies in real-time.
Challenges of GitOps and IaC
While GitOps and IaC offer numerous benefits, they also come with their own set of challenges, including:
-
Learning Curve: Teams may need to acquire new skills and knowledge to effectively implement GitOps and IaC practices.
-
Complexity: Managing infrastructure as code can introduce complexity, especially in large-scale environments.
-
Security Risks: Improperly configured infrastructure code can introduce security vulnerabilities and risks.
-
Tooling and Integration: It's tough to integrate different tools and platforms.
How to obtain Devops certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, GitOps and Infrastructure as Code are powerful. They can transform how organizations manage their infrastructure and improve their DevOps. By embracing automation, collaboration, and version control, teams can improve their software development. They can deploy faster, and their software will be more reliable and scalable. With the right tools, practices, and mindset, GitOps and IaC can lead to a more efficient, agile DevOps environment.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
The ScrumMaster Role in Managing Remote and Hybrid Teams
The rise of remote and hybrid work has changed team collaboration. ScrumMasters, who guide teams in agile practices, now face a challenge. They must lead distributed teams while ensuring productivity and alignment with Scrum principles. Remote and hybrid work need new strategies. They must ensure transparency, communication, and team cohesion. This article explores the changing role of the ScrumMaster in remote and hybrid work. It shows how to foster collaboration, reduce risks, and succeed in these settings.
Table Of Contents
- Ensuring Effective Communication and Collaboration
- Maintaining team engagement and morale
- Fostering Accountability and Transparency
- Supporting Continuous Improvement and Learning
- Adapting Leadership and Coaching Techniques
- Conclusion
Ensuring Effective Communication and Collaboration
In remote and hybrid teams, communication is harder than in co-located ones. The ScrumMaster must set up strong communication channels. They are key to keeping everyone informed and engaged.
- Facilitating Clear Communication: ScrumMasters must ensure seamless communication among team members. We can do this by holding regular stand-ups, sprint reviews, and retrospectives. We can use digital tools like Zoom, Slack, or Microsoft Teams.
- Using Agile Tools: Encourage using agile tools like Jira, Trello, or Asana. They help track progress and align the team.
- Overcoming Time Zone Differences: In distributed teams, time zones can cause communication gaps. The ScrumMaster can help. They should set up async channels and record key meetings for those who cannot attend live.
The ScrumMaster can ensure that remote and hybrid teams stay productive. They can do this by creating clear communication channels.
Maintaining team engagement and morale
A big challenge for remote and hybrid teams is keeping morale and engagement high. In a remote setting, team members may feel isolated and disengaged. They may also feel disconnected from their peers.
- Building Team Culture: ScrumMasters must foster a sense of community and team culture. This can be done through virtual team-building activities, informal check-ins, and social gatherings. Regular engagement helps build rapport and trust within the team.
- Recognizing and Rewarding Contributions: ScrumMasters should ensure the team values their contributions. Celebrating milestones and individual achievements boosts morale, even online.
- Encouraging Work-Life Balance: Remote work can blur the lines between personal and work life. The ScrumMaster should promote work-life balance. They should encourage regular breaks and set clear working hours to prevent burnout.
The ScrumMaster boosts engagement and morale. This creates a positive work environment. Team members feel connected, valued, and motivated.
Fostering Accountability and Transparency
Transparency is one of the key pillars of Scrum. In remote and hybrid teams, it's harder to see their progress. But, this visibility is essential for success.
- Encouraging Open Communication: ScrumMasters should foster a culture of openness. Team members should feel free to discuss challenges and blockers. Regular check-ins and sprint retrospectives can achieve this. They should encourage reflection and improvement.
- Implementing Visual Management: ScrumMasters can boost accountability. They can use tools that show task progress, like Kanban boards or burn-down charts. These tools help the team stay aligned with sprint goals. They ensure everyone knows their responsibilities.
- Tracking Deliverables: Ensuring that teams deliver quality work on time is essential. ScrumMasters must monitor user stories, manage the product backlog, and track key deliverables. They must ensure that all team members meet their commitments.
The ScrumMaster helps remote and hybrid teams stay focused on their goals. By being accountable and transparent, they build a culture of trust and responsibility.
Supporting Continuous Improvement and Learning
In any Scrum team, continuous improvement and learning are vital for long-term success. In a remote or hybrid setup, ScrumMasters must adapt. They must sustain these practices despite the challenges of distributed work.
- Facilitating Retrospectives: The ScrumMaster must organize sprint retrospectives. In them, the team reflects on what went well and what to improve. In remote settings, use video conferencing. It ensures all team members have a voice.
- Encouraging Skill Development: Remote work lets team members use their time to learn. ScrumMasters should encourage team members to get relevant certifications. They should also attend webinars or join virtual workshops.
- Promote a Growth Mindset: ScrumMasters should encourage learning from failure. It helps the team adapt quickly to change. This is vital in the fast-paced remote and hybrid work environment.
The ScrumMaster supports continuous improvement. This keeps the team adaptable and agile. They are ready to tackle new challenges, whether working remotely or in a hybrid model.
Adapting Leadership and Coaching Techniques
Leadership in a remote or hybrid environment requires a different approach. Scrum Masters must adapt their leadership and coaching. They must guide their teams despite the challenges of physical separation.
- Being a Servant Leader: In Scrum, the Scrum Master is a servant leader. They facilitate the team's success rather than directing it. This is more critical in a remote or hybrid setup. Team members may need more autonomy and empowerment.
- Providing Individual Support: ScrumMasters must better meet remote team members' needs. Regular one-on-one check-ins can help with any challenges team members face, at work or in their personal lives.
- Adapting Coaching Style: Remote coaching requires Scrum Masters to develop new skills. They must read body language and tone on video calls. They must also engage the team in meaningful ways during virtual meetings.
ScrumMasters can better coach remote and hybrid teams. They should be more empathetic and flexible. A change in leadership style is key to this.
How to obtain Agile & Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The role of the ScrumMaster in remote and hybrid teams is changing fast. Organizations are embracing flexible work models. ScrumMasters can keep remote teams productive and aligned with Scrum. They should focus on communication, engagement, and accountability. They should also promote continuous improvement and adaptive leadership. In this new work era, ScrumMasters are vital to distributed teams. They are not just facilitators; they enable success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
The rise of remote and hybrid work has changed team collaboration. ScrumMasters, who guide teams in agile practices, now face a challenge. They must lead distributed teams while ensuring productivity and alignment with Scrum principles. Remote and hybrid work need new strategies. They must ensure transparency, communication, and team cohesion. This article explores the changing role of the ScrumMaster in remote and hybrid work. It shows how to foster collaboration, reduce risks, and succeed in these settings.
Table Of Contents
- Ensuring Effective Communication and Collaboration
- Maintaining team engagement and morale
- Fostering Accountability and Transparency
- Supporting Continuous Improvement and Learning
- Adapting Leadership and Coaching Techniques
- Conclusion
Ensuring Effective Communication and Collaboration
In remote and hybrid teams, communication is harder than in co-located ones. The ScrumMaster must set up strong communication channels. They are key to keeping everyone informed and engaged.
- Facilitating Clear Communication: ScrumMasters must ensure seamless communication among team members. We can do this by holding regular stand-ups, sprint reviews, and retrospectives. We can use digital tools like Zoom, Slack, or Microsoft Teams.
- Using Agile Tools: Encourage using agile tools like Jira, Trello, or Asana. They help track progress and align the team.
- Overcoming Time Zone Differences: In distributed teams, time zones can cause communication gaps. The ScrumMaster can help. They should set up async channels and record key meetings for those who cannot attend live.
The ScrumMaster can ensure that remote and hybrid teams stay productive. They can do this by creating clear communication channels.
Maintaining team engagement and morale
A big challenge for remote and hybrid teams is keeping morale and engagement high. In a remote setting, team members may feel isolated and disengaged. They may also feel disconnected from their peers.
- Building Team Culture: ScrumMasters must foster a sense of community and team culture. This can be done through virtual team-building activities, informal check-ins, and social gatherings. Regular engagement helps build rapport and trust within the team.
- Recognizing and Rewarding Contributions: ScrumMasters should ensure the team values their contributions. Celebrating milestones and individual achievements boosts morale, even online.
- Encouraging Work-Life Balance: Remote work can blur the lines between personal and work life. The ScrumMaster should promote work-life balance. They should encourage regular breaks and set clear working hours to prevent burnout.
The ScrumMaster boosts engagement and morale. This creates a positive work environment. Team members feel connected, valued, and motivated.
Fostering Accountability and Transparency
Transparency is one of the key pillars of Scrum. In remote and hybrid teams, it's harder to see their progress. But, this visibility is essential for success.
- Encouraging Open Communication: ScrumMasters should foster a culture of openness. Team members should feel free to discuss challenges and blockers. Regular check-ins and sprint retrospectives can achieve this. They should encourage reflection and improvement.
- Implementing Visual Management: ScrumMasters can boost accountability. They can use tools that show task progress, like Kanban boards or burn-down charts. These tools help the team stay aligned with sprint goals. They ensure everyone knows their responsibilities.
- Tracking Deliverables: Ensuring that teams deliver quality work on time is essential. ScrumMasters must monitor user stories, manage the product backlog, and track key deliverables. They must ensure that all team members meet their commitments.
The ScrumMaster helps remote and hybrid teams stay focused on their goals. By being accountable and transparent, they build a culture of trust and responsibility.
Supporting Continuous Improvement and Learning
In any Scrum team, continuous improvement and learning are vital for long-term success. In a remote or hybrid setup, ScrumMasters must adapt. They must sustain these practices despite the challenges of distributed work.
- Facilitating Retrospectives: The ScrumMaster must organize sprint retrospectives. In them, the team reflects on what went well and what to improve. In remote settings, use video conferencing. It ensures all team members have a voice.
- Encouraging Skill Development: Remote work lets team members use their time to learn. ScrumMasters should encourage team members to get relevant certifications. They should also attend webinars or join virtual workshops.
- Promote a Growth Mindset: ScrumMasters should encourage learning from failure. It helps the team adapt quickly to change. This is vital in the fast-paced remote and hybrid work environment.
The ScrumMaster supports continuous improvement. This keeps the team adaptable and agile. They are ready to tackle new challenges, whether working remotely or in a hybrid model.
Adapting Leadership and Coaching Techniques
Leadership in a remote or hybrid environment requires a different approach. Scrum Masters must adapt their leadership and coaching. They must guide their teams despite the challenges of physical separation.
- Being a Servant Leader: In Scrum, the Scrum Master is a servant leader. They facilitate the team's success rather than directing it. This is more critical in a remote or hybrid setup. Team members may need more autonomy and empowerment.
- Providing Individual Support: ScrumMasters must better meet remote team members' needs. Regular one-on-one check-ins can help with any challenges team members face, at work or in their personal lives.
- Adapting Coaching Style: Remote coaching requires Scrum Masters to develop new skills. They must read body language and tone on video calls. They must also engage the team in meaningful ways during virtual meetings.
ScrumMasters can better coach remote and hybrid teams. They should be more empathetic and flexible. A change in leadership style is key to this.
How to obtain Agile & Scrum certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The role of the ScrumMaster in remote and hybrid teams is changing fast. Organizations are embracing flexible work models. ScrumMasters can keep remote teams productive and aligned with Scrum. They should focus on communication, engagement, and accountability. They should also promote continuous improvement and adaptive leadership. In this new work era, ScrumMasters are vital to distributed teams. They are not just facilitators; they enable success.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Agile Methodology's Impact on PMP Certification Success
The Project Management Professional (PMP) certification is in great demand in project management. The PMP exam, once focused on the Waterfall method, has evolved. It now reflects the rise of Agile practices in project management. The Agile method is vital to PMP certification today. Its iterative approach, flexible planning, and focus on collaboration drive this. It improves project outcomes. It also meets the fast-changing needs of businesses in software, marketing, and manufacturing. This article looks at Agile's role in PMP certification. It is important for project managers.
Table Of Contents
- Understanding Agile Methods in the PMP Framework
- Key Agile Concepts Tested in the PMP Exam
- The Agile Mindset: Key to Successful Project Management
- Agile Tools and Techniques for PMP Certification
- Challenges of Incorporating Agile in PMP Certification
- Conclusion
Understanding Agile Methods in the PMP Framework
Agile methods are now part of the PMP framework. Their flexibility and iterative development are well-known. PMP certification was once aligned with predictive (Waterfall) methods. But the PMI (Project Management Institute) has updated its PMP exam. It now includes Agile and hybrid approaches.
- Iterative Process: Agile allows for small, incremental project cycles, or "sprints." This ensures continuous feedback and the ability to adapt to changes.
- Collaboration Focus: Agile values close collaboration and constant communication between teams and stakeholders.
- Adapting to Change: Agile thrives where project requirements can change. In contrast, Waterfall has a rigid structure.
Agile methods can improve PMP. They help project managers adapt to fast-changing requirements in some industries. The updated PMP exam has 50% of its questions on Agile and hybrid methods. This reflects the growing demand for these skills.
Key Agile Concepts Tested in the PMP Exam
Several Agile principles and frameworks are emphasized within the PMP exam. PMP candidates must know these concepts. They bridge traditional project management and Agile practices.
- Scrum Framework: Scrum is a popular Agile framework. It focuses on small teams working in "sprints" to improve projects incrementally.
- Kanban: It emphasizes visualizing work, limiting work in progress, and optimizing flow. This allows teams to react quickly to project needs and constraints.
- Daily stand-ups: Agile promotes regular communication through brief meetings called stand-ups. In them, team members discuss progress, challenges, and upcoming tasks.
- User Stories: Agile captures requirements as "user stories." They describe features from the end user's perspective. This practice emphasizes the delivery of value to the customer.
PMP aspirants must understand these concepts. They must show how to use Agile tools. This will improve flexibility and customer satisfaction in a project.
The Agile Mindset: Key to Successful Project Management
The Agile mindset is centered around adaptability, collaboration, and continuous improvement. PMP candidates must adopt an Agile mindset to succeed in volatile, unpredictable environments.
- Agile focuses on delivering value to customers. It does this by quickly responding to their needs, not by following a strict project plan.
- Flexibility over Predictability: PMP project managers must be flexible. This is vital for projects with innovation or frequent scope changes.
- Continuous Improvement: Agile promotes learning and adjusting based on feedback from previous sprints. PMP-certified project managers with an Agile mindset adapt better to project changes.
Adding the Agile mindset to PMP certification will help project managers. It will prepare them to handle complex projects in fast-changing industries.
Agile Tools and Techniques for PMP Certification
Project managers must know tools and techniques to apply Agile methods effectively. These are commonly used in Agile environments. PMP certification covers many of these tools. They are vital for managing Agile projects.
- Burn-down and Burn-up Charts: These charts track progress toward project goals. They show the work completed and the work remaining over time.
- Product Backlog: A prioritized list of features or tasks for a project. It is managed by the product owner in Scrum.
- Sprint Planning and Retrospectives: Sprint planning sets the tasks for the next sprint. Retrospectives let the team reflect on what went well and what could be improved.
- Agile Metrics: KPIs like velocity, lead time, and cycle time measure efficiency. They also predict performance.
PMP-certified professionals must master these tools. They need to manage Agile projects and deliver value on time.
Challenges of Incorporating Agile in PMP Certification
Agile has many benefits. But, it can be hard to add it to traditional PMP project management. Understanding these challenges is crucial for project managers to apply Agile principles effectively.
- Cultural Resistance: Teams familiar with Waterfall may resist Agile. They may fear change or not understand Agile.
- Scaling Agile: Using Agile for large projects with many teams is tough. It's hard to coordinate sprints, backlogs, and goals across teams.
- The PMP exam emphasizes hybrid methods that blend Agile and Waterfall. Project managers must balance these methods based on project needs. This can be tough if there is a strong preference for one approach.
- Documentation: Agile values working software over heavy documentation. PMP-certified managers must balance Agile's flexibility with stakeholders' needs for documentation.
Agile is still a must-use tool for project managers. It helps them run successful, adaptive, customer-focused projects despite the challenges.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Agile is key to modern project management. It's now vital for PMP certification. As businesses use Agile methods to survive in complex, fast-changing environments, PMP-certified professionals must know Agile concepts and frameworks. Agile's iterative approach, tools, and challenges can aid PMP candidates. It will help them manage projects with greater flexibility, adaptability, and customer focus. In a world of constant change, Agile skills are a must for successful project management. They are not just an advantage.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
The Project Management Professional (PMP) certification is in great demand in project management. The PMP exam, once focused on the Waterfall method, has evolved. It now reflects the rise of Agile practices in project management. The Agile method is vital to PMP certification today. Its iterative approach, flexible planning, and focus on collaboration drive this. It improves project outcomes. It also meets the fast-changing needs of businesses in software, marketing, and manufacturing. This article looks at Agile's role in PMP certification. It is important for project managers.
Table Of Contents
- Understanding Agile Methods in the PMP Framework
- Key Agile Concepts Tested in the PMP Exam
- The Agile Mindset: Key to Successful Project Management
- Agile Tools and Techniques for PMP Certification
- Challenges of Incorporating Agile in PMP Certification
- Conclusion
Understanding Agile Methods in the PMP Framework
Agile methods are now part of the PMP framework. Their flexibility and iterative development are well-known. PMP certification was once aligned with predictive (Waterfall) methods. But the PMI (Project Management Institute) has updated its PMP exam. It now includes Agile and hybrid approaches.
- Iterative Process: Agile allows for small, incremental project cycles, or "sprints." This ensures continuous feedback and the ability to adapt to changes.
- Collaboration Focus: Agile values close collaboration and constant communication between teams and stakeholders.
- Adapting to Change: Agile thrives where project requirements can change. In contrast, Waterfall has a rigid structure.
Agile methods can improve PMP. They help project managers adapt to fast-changing requirements in some industries. The updated PMP exam has 50% of its questions on Agile and hybrid methods. This reflects the growing demand for these skills.
Key Agile Concepts Tested in the PMP Exam
Several Agile principles and frameworks are emphasized within the PMP exam. PMP candidates must know these concepts. They bridge traditional project management and Agile practices.
- Scrum Framework: Scrum is a popular Agile framework. It focuses on small teams working in "sprints" to improve projects incrementally.
- Kanban: It emphasizes visualizing work, limiting work in progress, and optimizing flow. This allows teams to react quickly to project needs and constraints.
- Daily stand-ups: Agile promotes regular communication through brief meetings called stand-ups. In them, team members discuss progress, challenges, and upcoming tasks.
- User Stories: Agile captures requirements as "user stories." They describe features from the end user's perspective. This practice emphasizes the delivery of value to the customer.
PMP aspirants must understand these concepts. They must show how to use Agile tools. This will improve flexibility and customer satisfaction in a project.
The Agile Mindset: Key to Successful Project Management
The Agile mindset is centered around adaptability, collaboration, and continuous improvement. PMP candidates must adopt an Agile mindset to succeed in volatile, unpredictable environments.
- Agile focuses on delivering value to customers. It does this by quickly responding to their needs, not by following a strict project plan.
- Flexibility over Predictability: PMP project managers must be flexible. This is vital for projects with innovation or frequent scope changes.
- Continuous Improvement: Agile promotes learning and adjusting based on feedback from previous sprints. PMP-certified project managers with an Agile mindset adapt better to project changes.
Adding the Agile mindset to PMP certification will help project managers. It will prepare them to handle complex projects in fast-changing industries.
Agile Tools and Techniques for PMP Certification
Project managers must know tools and techniques to apply Agile methods effectively. These are commonly used in Agile environments. PMP certification covers many of these tools. They are vital for managing Agile projects.
- Burn-down and Burn-up Charts: These charts track progress toward project goals. They show the work completed and the work remaining over time.
- Product Backlog: A prioritized list of features or tasks for a project. It is managed by the product owner in Scrum.
- Sprint Planning and Retrospectives: Sprint planning sets the tasks for the next sprint. Retrospectives let the team reflect on what went well and what could be improved.
- Agile Metrics: KPIs like velocity, lead time, and cycle time measure efficiency. They also predict performance.
PMP-certified professionals must master these tools. They need to manage Agile projects and deliver value on time.
Challenges of Incorporating Agile in PMP Certification
Agile has many benefits. But, it can be hard to add it to traditional PMP project management. Understanding these challenges is crucial for project managers to apply Agile principles effectively.
- Cultural Resistance: Teams familiar with Waterfall may resist Agile. They may fear change or not understand Agile.
- Scaling Agile: Using Agile for large projects with many teams is tough. It's hard to coordinate sprints, backlogs, and goals across teams.
- The PMP exam emphasizes hybrid methods that blend Agile and Waterfall. Project managers must balance these methods based on project needs. This can be tough if there is a strong preference for one approach.
- Documentation: Agile values working software over heavy documentation. PMP-certified managers must balance Agile's flexibility with stakeholders' needs for documentation.
Agile is still a must-use tool for project managers. It helps them run successful, adaptive, customer-focused projects despite the challenges.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Agile is key to modern project management. It's now vital for PMP certification. As businesses use Agile methods to survive in complex, fast-changing environments, PMP-certified professionals must know Agile concepts and frameworks. Agile's iterative approach, tools, and challenges can aid PMP candidates. It will help them manage projects with greater flexibility, adaptability, and customer focus. In a world of constant change, Agile skills are a must for successful project management. They are not just an advantage.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Salesforce Certifications for Non-Technical Professionals
In today's data-driven world, Salesforce is a top CRM platform. It has changed how businesses manage customer interactions, sales, and marketing. Many associate Salesforce with technical roles, like developers. But it has certifications for non-technical professionals too. This blog post will explore the Salesforce certifications for non-technical roles. It will show the skills they can learn. And, how the certifications can boost their careers.
Table Of Contents
- Understanding the Importance of Salesforce Certifications
- Overview of Relevant Salesforce Certifications for Non-Technical Roles
- Benefits of Obtaining Salesforce Certifications for Non-Technical Professionals
- Steps to Get Started with Salesforce Certifications
- Real-World Applications of Salesforce Certifications in Non-Technical Roles
- Conclusion
Understanding the Importance of Salesforce Certifications
Industry Demand: Organizations rely on Salesforce more than ever. So, there is a high demand for certified professionals. Sales, marketing, and customer service can enjoy knowing the platform's capabilities.
- Career Advancement: Salesforce certifications boost your knowledge. They also show your commitment to growth. They can lead to promotions, salary increases, and new job opportunities.
- Skill Development: Certifications help non-tech pros. They teach skills like data analysis, customer management, and process optimization. These are vital for navigating the complex CRM landscape.
Overview of Relevant Salesforce Certifications for Non-Technical Roles
- Salesforce Certified Administrator: This cert is for pros who manage Salesforce's configuration. It includes user management, security, and reporting. It covers fundamental concepts such as custom objects, fields, and dashboards.
- Salesforce Certified Sales Cloud Consultant: This cert is for implementing Salesforce Sales Cloud. It's perfect for sales pros. They want to improve sales, manage opportunities, and use Salesforce for leads.
- Salesforce tailored this certification for customer service professionals. It shows how to use Salesforce Service Cloud to improve support.
- Salesforce Certified Marketing Cloud Consultant: This cert is for users of Marketing Cloud. It covers email marketing, customer journeys, and campaign management. It equips professionals to boost customer engagement.
- Salesforce Certified Nonprofit Cloud Consultant: This certification is for the nonprofit sector. It focuses on using Salesforce to manage donor relationships, fundraising, and programs. It is valuable for non-technical roles in nonprofits.
Benefits of Obtaining Salesforce Certifications for Non-Technical Professionals
- Know CRM Better: Certifications teach CRM principles. They teach how to use Salesforce to boost business results. Non-technical professionals can clearly communicate with technical teams. They can also make decisions based on informed insights.
- Enhanced Income Opportunities: Certified professionals typically earn higher salaries compared to their non-certified counterparts. Industry surveys show that Salesforce-certified individuals can earn 20% more than those without.
- Networking: Joining the Salesforce-certified community lets professionals connect with other certified individuals. They can gain insights from experts and share best practices. Building these connections can open doors to collaborative ventures and foster professional advancement.
Steps to Get Started with Salesforce Certifications
- Identify Your Role and Goals: Find a certification that fits your job or career goals. Assess your strengths and interests to select the most relevant certification.
- Use Salesforce Resources: Salesforce has many resources, including free training on Trailhead. This platform offers self-paced courses and projects. They will help you prepare for your certification exam.
- Participate in Study Groups: Network with peers working toward the same certifications. Join online forums or local study groups. Collaborating with peers can enhance your learning experience and provide more motivation.
- Complete practice tests to get comfortable with the exam format and structure. This will help you gauge your readiness and identify areas where you need to focus your studies.
- Schedule Your Exam: When ready, book your certification exam on the Salesforce portal. Make sure to familiarize yourself with the exam policies and procedures in advance.
Real-World Applications of Salesforce Certifications in Non-Technical Roles
- Sales and Lead Management: Certified Sales Cloud Consultants can improve lead management. They can streamline sales processes and enhance customer relationships. This will boost sales and revenue.
- Customer Support Improvement: Service Cloud certifications help customer service professionals. They use Salesforce tools better. This results in quicker solutions and more satisfied customers.
- Marketing Campaign Optimization: Certified Marketing Cloud pros can run targeted campaigns. This boosts engagement and ROI on marketing efforts.
- Nonprofit Management: The Nonprofit Cloud Consultant certification helps nonprofit professionals. It teaches them to manage donor relationships and improve fundraising and programs.
- Cross-Functional Collaboration: Non-technical pros with Salesforce certs can connect tech and business teams. This fosters collaboration and aligns projects with organizational goals.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Salesforce certifications for non-technical roles are valuable assets in today's competitive job market. By knowing the platform's features and getting certified, professionals can advance their careers. They can learn new skills and help their organizations succeed. If you are in sales, marketing, customer service, or nonprofits, get Salesforce certifications. They can boost your career and open new doors. Start your journey today. Explore the certifications that match your goals. Use the many resources available to you.
Read More
In today's data-driven world, Salesforce is a top CRM platform. It has changed how businesses manage customer interactions, sales, and marketing. Many associate Salesforce with technical roles, like developers. But it has certifications for non-technical professionals too. This blog post will explore the Salesforce certifications for non-technical roles. It will show the skills they can learn. And, how the certifications can boost their careers.
Table Of Contents
- Understanding the Importance of Salesforce Certifications
- Overview of Relevant Salesforce Certifications for Non-Technical Roles
- Benefits of Obtaining Salesforce Certifications for Non-Technical Professionals
- Steps to Get Started with Salesforce Certifications
- Real-World Applications of Salesforce Certifications in Non-Technical Roles
- Conclusion
Understanding the Importance of Salesforce Certifications
Industry Demand: Organizations rely on Salesforce more than ever. So, there is a high demand for certified professionals. Sales, marketing, and customer service can enjoy knowing the platform's capabilities.
- Career Advancement: Salesforce certifications boost your knowledge. They also show your commitment to growth. They can lead to promotions, salary increases, and new job opportunities.
- Skill Development: Certifications help non-tech pros. They teach skills like data analysis, customer management, and process optimization. These are vital for navigating the complex CRM landscape.
Overview of Relevant Salesforce Certifications for Non-Technical Roles
- Salesforce Certified Administrator: This cert is for pros who manage Salesforce's configuration. It includes user management, security, and reporting. It covers fundamental concepts such as custom objects, fields, and dashboards.
- Salesforce Certified Sales Cloud Consultant: This cert is for implementing Salesforce Sales Cloud. It's perfect for sales pros. They want to improve sales, manage opportunities, and use Salesforce for leads.
- Salesforce tailored this certification for customer service professionals. It shows how to use Salesforce Service Cloud to improve support.
- Salesforce Certified Marketing Cloud Consultant: This cert is for users of Marketing Cloud. It covers email marketing, customer journeys, and campaign management. It equips professionals to boost customer engagement.
- Salesforce Certified Nonprofit Cloud Consultant: This certification is for the nonprofit sector. It focuses on using Salesforce to manage donor relationships, fundraising, and programs. It is valuable for non-technical roles in nonprofits.
Benefits of Obtaining Salesforce Certifications for Non-Technical Professionals
- Know CRM Better: Certifications teach CRM principles. They teach how to use Salesforce to boost business results. Non-technical professionals can clearly communicate with technical teams. They can also make decisions based on informed insights.
- Enhanced Income Opportunities: Certified professionals typically earn higher salaries compared to their non-certified counterparts. Industry surveys show that Salesforce-certified individuals can earn 20% more than those without.
- Networking: Joining the Salesforce-certified community lets professionals connect with other certified individuals. They can gain insights from experts and share best practices. Building these connections can open doors to collaborative ventures and foster professional advancement.
Steps to Get Started with Salesforce Certifications
- Identify Your Role and Goals: Find a certification that fits your job or career goals. Assess your strengths and interests to select the most relevant certification.
- Use Salesforce Resources: Salesforce has many resources, including free training on Trailhead. This platform offers self-paced courses and projects. They will help you prepare for your certification exam.
- Participate in Study Groups: Network with peers working toward the same certifications. Join online forums or local study groups. Collaborating with peers can enhance your learning experience and provide more motivation.
- Complete practice tests to get comfortable with the exam format and structure. This will help you gauge your readiness and identify areas where you need to focus your studies.
- Schedule Your Exam: When ready, book your certification exam on the Salesforce portal. Make sure to familiarize yourself with the exam policies and procedures in advance.
Real-World Applications of Salesforce Certifications in Non-Technical Roles
- Sales and Lead Management: Certified Sales Cloud Consultants can improve lead management. They can streamline sales processes and enhance customer relationships. This will boost sales and revenue.
- Customer Support Improvement: Service Cloud certifications help customer service professionals. They use Salesforce tools better. This results in quicker solutions and more satisfied customers.
- Marketing Campaign Optimization: Certified Marketing Cloud pros can run targeted campaigns. This boosts engagement and ROI on marketing efforts.
- Nonprofit Management: The Nonprofit Cloud Consultant certification helps nonprofit professionals. It teaches them to manage donor relationships and improve fundraising and programs.
- Cross-Functional Collaboration: Non-technical pros with Salesforce certs can connect tech and business teams. This fosters collaboration and aligns projects with organizational goals.
How to obtain Salesforce certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Salesforce certifications for non-technical roles are valuable assets in today's competitive job market. By knowing the platform's features and getting certified, professionals can advance their careers. They can learn new skills and help their organizations succeed. If you are in sales, marketing, customer service, or nonprofits, get Salesforce certifications. They can boost your career and open new doors. Start your journey today. Explore the certifications that match your goals. Use the many resources available to you.
Cisco DevNet Certification: Connecting Software Development
Tech's fast evolution is merging IT and software dev. It's changing how organizations work. The Cisco DevNet Certification leads this change. It equips professionals with the skills to navigate the new landscape. As businesses automate and use cloud software, networking and development skills are vital. This certification serves as a bridge. It helps IT pros use their dev skills to better their organizations.
This article will explore the significance of Cisco DevNet Certification. It will cover the certification's key concepts and benefits. It will explain its role in preparing people for a fast-paced career in IT and software development.
Table Of Contents
- Understanding the Cisco DevNet certification
- The Importance of Bridging IT and Development
- Skills Acquired through Cisco DevNet Certification
- Career Opportunities with Cisco DevNet Certification
- Preparing for the Cisco DevNet Certification
- Conclusion
Understanding the Cisco DevNet certification
The Cisco DevNet Certification program is for software developers in networking. It tests their skills. The certification covers network programming, automation, and app development for Cisco platforms. This includes REST APIs, Cisco's DNA Center, and automation tools like Ansible.
The program offers several certification levels, including:
- Cisco Certified DevNet Associate: This is a basic-level cert. It is for those starting to learn network programming and automation.
- Cisco Certified DevNet Professional: This intermediate level is for those with a deeper knowledge of software development and DevOps. It requires experience in these areas.
- Cisco Certified DevNet Specialist: These certifications focus on specific technologies. They allow professionals to specialize in areas like security, collaboration, or data centers.
Key Concepts Covered:
- Application Development and Deployment
- Infrastructure Automation
- Network Programmability
- Security and Assurance
- Understanding of Cisco platforms and tools.
The Importance of Bridging IT and Development
IT and software development must converge in today's digital world. With the rise of cloud services, IoT, and data apps, businesses need experts. They must create and manage software that integrates with network infrastructure. The Cisco DevNet Certification promotes this integration. It builds skills to develop apps that use Cisco technologies.
Key Reasons for Bridging IT and Development:
- Enhanced Collaboration: IT and software development skills help teams work better together. This improves project outcomes.
- Increased Efficiency: Automating repetitive tasks cuts errors. It frees up time for IT to focus on strategy.
- Better Problem-Solving: A dual skill set lets professionals tackle problems from different angles. This leads to innovative solutions.
- Alignment with Business Goals: IT and development-skilled professionals can better understand business needs. They can help to achieve organizational goals.
Skills Acquired through Cisco DevNet Certification
The Cisco DevNet Certification gives people the skills to succeed in today's IT world. These abilities can be grouped into several essential categories:
- Programming Fundamentals : You must know Python, JavaScript, or Go to automate tasks and develop apps. The certification covers the basics of programming. It lets professionals write scripts and integrate apps with network hardware.
- API Interaction : APIs (Application Programming Interfaces) are the backbone of modern software development. Professionals learn to use APIs to access data and services on Cisco platforms. Understanding RESTful APIs and JSON is crucial for effective integration.
- Network Automation : Automation is a vital component of network management. The certification teaches the use of tools like Ansible, Puppet, and Cisco DNA Center. They automate network configs and management tasks. This improves efficiency and reduces downtime.
- Security Practices : Security is paramount in today’s digital world. The certification covers security protocols and best practices. It ensures that applications and network interactions are secure, reducing vulnerabilities.
- Collaboration and DevOps practices : The certification promotes DevOps knowledge. It helps pros work with dev teams and improve software delivery. This includes knowledge of CI/CD pipelines, version control, and agile methodologies.
Career Opportunities with Cisco DevNet Certification
The Cisco DevNet Certification opens up many career opportunities across various sectors. With a mix of networking and software skills, certified pros can fill roles such as:
- Network Automation Engineer : These professionals design and put in place automated network solutions. They ensure that the network operations are efficient and scalable.
- Software Developer : Software developers work on network applications. They create solutions that integrate with Cisco products and services.
- DevOps Engineer : DevOps engineers are vital in bridging development and operations. They prioritize streamlining workflows and enhancing teamwork.
- Cloud Engineer : Cloud engineers design and manage cloud infrastructure. They ensure apps are cloud-optimized, secure, and high-performing.
- Technical Solutions Architect : In this role, professionals design complex network solutions for clients. They must understand both networking and development principles.
Preparing for the Cisco DevNet Certification
To pass the Cisco DevNet Certification, candidates need a good plan. Here are some effective approaches:
- Online Courses and Study Materials : Cisco offers online courses, webinars, and study materials for the DevNet certification. They tailor it. These materials offer a thorough review of the exam topics.
- Hands-on Labs : Practical experience is crucial for mastering the concepts covered in the certification. Engaging in hands-on labs allows candidates to apply theoretical knowledge in real-world scenarios.
- Community and Forums : Joining Cisco and DevNet forums can provide valuable insights. You can find tips and support from peers and experts.
- Taking practice exams provides valuable preparation for candidates. They can check their knowledge and find areas to study more. It also familiarizes them with the exam format and types of questions.
- Networking with professionals : Connecting with certified professionals can provide mentorship and insights. This can help candidates stay motivated and informed.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The Cisco DevNet Certification is key in linking IT and software development. It equips professionals with skills to thrive in a tech-driven world. As organizations adopt automation and cloud services, they will need experts to integrate them. This certification helps professionals build a successful career in IT and development. It aligns with the future of both fields. The Cisco DevNet Certification is for all IT pros. It offers a way to unlock new opportunities and improve your skills. This can lead to a bright future in tech.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Tech's fast evolution is merging IT and software dev. It's changing how organizations work. The Cisco DevNet Certification leads this change. It equips professionals with the skills to navigate the new landscape. As businesses automate and use cloud software, networking and development skills are vital. This certification serves as a bridge. It helps IT pros use their dev skills to better their organizations.
This article will explore the significance of Cisco DevNet Certification. It will cover the certification's key concepts and benefits. It will explain its role in preparing people for a fast-paced career in IT and software development.
Table Of Contents
- Understanding the Cisco DevNet certification
- The Importance of Bridging IT and Development
- Skills Acquired through Cisco DevNet Certification
- Career Opportunities with Cisco DevNet Certification
- Preparing for the Cisco DevNet Certification
- Conclusion
Understanding the Cisco DevNet certification
The Cisco DevNet Certification program is for software developers in networking. It tests their skills. The certification covers network programming, automation, and app development for Cisco platforms. This includes REST APIs, Cisco's DNA Center, and automation tools like Ansible.
The program offers several certification levels, including:
- Cisco Certified DevNet Associate: This is a basic-level cert. It is for those starting to learn network programming and automation.
- Cisco Certified DevNet Professional: This intermediate level is for those with a deeper knowledge of software development and DevOps. It requires experience in these areas.
- Cisco Certified DevNet Specialist: These certifications focus on specific technologies. They allow professionals to specialize in areas like security, collaboration, or data centers.
Key Concepts Covered:
- Application Development and Deployment
- Infrastructure Automation
- Network Programmability
- Security and Assurance
- Understanding of Cisco platforms and tools.
The Importance of Bridging IT and Development
IT and software development must converge in today's digital world. With the rise of cloud services, IoT, and data apps, businesses need experts. They must create and manage software that integrates with network infrastructure. The Cisco DevNet Certification promotes this integration. It builds skills to develop apps that use Cisco technologies.
Key Reasons for Bridging IT and Development:
- Enhanced Collaboration: IT and software development skills help teams work better together. This improves project outcomes.
- Increased Efficiency: Automating repetitive tasks cuts errors. It frees up time for IT to focus on strategy.
- Better Problem-Solving: A dual skill set lets professionals tackle problems from different angles. This leads to innovative solutions.
- Alignment with Business Goals: IT and development-skilled professionals can better understand business needs. They can help to achieve organizational goals.
Skills Acquired through Cisco DevNet Certification
The Cisco DevNet Certification gives people the skills to succeed in today's IT world. These abilities can be grouped into several essential categories:
- Programming Fundamentals : You must know Python, JavaScript, or Go to automate tasks and develop apps. The certification covers the basics of programming. It lets professionals write scripts and integrate apps with network hardware.
- API Interaction : APIs (Application Programming Interfaces) are the backbone of modern software development. Professionals learn to use APIs to access data and services on Cisco platforms. Understanding RESTful APIs and JSON is crucial for effective integration.
- Network Automation : Automation is a vital component of network management. The certification teaches the use of tools like Ansible, Puppet, and Cisco DNA Center. They automate network configs and management tasks. This improves efficiency and reduces downtime.
- Security Practices : Security is paramount in today’s digital world. The certification covers security protocols and best practices. It ensures that applications and network interactions are secure, reducing vulnerabilities.
- Collaboration and DevOps practices : The certification promotes DevOps knowledge. It helps pros work with dev teams and improve software delivery. This includes knowledge of CI/CD pipelines, version control, and agile methodologies.
Career Opportunities with Cisco DevNet Certification
The Cisco DevNet Certification opens up many career opportunities across various sectors. With a mix of networking and software skills, certified pros can fill roles such as:
- Network Automation Engineer : These professionals design and put in place automated network solutions. They ensure that the network operations are efficient and scalable.
- Software Developer : Software developers work on network applications. They create solutions that integrate with Cisco products and services.
- DevOps Engineer : DevOps engineers are vital in bridging development and operations. They prioritize streamlining workflows and enhancing teamwork.
- Cloud Engineer : Cloud engineers design and manage cloud infrastructure. They ensure apps are cloud-optimized, secure, and high-performing.
- Technical Solutions Architect : In this role, professionals design complex network solutions for clients. They must understand both networking and development principles.
Preparing for the Cisco DevNet Certification
To pass the Cisco DevNet Certification, candidates need a good plan. Here are some effective approaches:
- Online Courses and Study Materials : Cisco offers online courses, webinars, and study materials for the DevNet certification. They tailor it. These materials offer a thorough review of the exam topics.
- Hands-on Labs : Practical experience is crucial for mastering the concepts covered in the certification. Engaging in hands-on labs allows candidates to apply theoretical knowledge in real-world scenarios.
- Community and Forums : Joining Cisco and DevNet forums can provide valuable insights. You can find tips and support from peers and experts.
- Taking practice exams provides valuable preparation for candidates. They can check their knowledge and find areas to study more. It also familiarizes them with the exam format and types of questions.
- Networking with professionals : Connecting with certified professionals can provide mentorship and insights. This can help candidates stay motivated and informed.
How to obtain Cisco certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
The Cisco DevNet Certification is key in linking IT and software development. It equips professionals with skills to thrive in a tech-driven world. As organizations adopt automation and cloud services, they will need experts to integrate them. This certification helps professionals build a successful career in IT and development. It aligns with the future of both fields. The Cisco DevNet Certification is for all IT pros. It offers a way to unlock new opportunities and improve your skills. This can lead to a bright future in tech.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
PMP Certification for Success in Media & Design Industries
In today's fast world, project management is key to success in media and design. A PMP certification can create new opportunities. It can help professionals stand out in competitive job markets. Let's explore how a PMP certification can help media and design workers.
What is PMP Certification?
PMP stands for Project Management Professional. It is a globally recognized certification from the Project Management Institute (PMI). It validates a professional's expertise in project management. This certification shows that individuals can lead project teams. They can deliver results within the limits of time, budget, and resources.
How can PMP Certification Benefit Media Industry Professionals?
In the fast-paced media industry, project management skills are vital for success. They are key to executing media projects. A PMP certification can help media pros. It can streamline processes and improve project delivery. It applies to planning and executing media campaigns and managing production schedules. Also, a PMP certification can boost credibility. This can lead to more job opportunities and career growth in the media sector.
How can PMP Certification Benefit Design Industry Professionals?
Similarly, in the fast-changing design field, project management is vital. It turns creative visions into reality. Design professionals with a PMP can manage design projects. They can work with cross-functional teams. They will ensure projects finish on time and within budget. A PMP certification can boost design professionals' careers. It shows their expertise and meets the design industry's high demands.
PMP certification can greatly benefit design professionals. It gives them structured project management skills. This helps them manage complex, multi-disciplinary projects efficiently. It streamlines workflows and manages budgets, timelines, and resources. This ensures smoother project delivery. Also, PMP-certified professionals are better at leading creative teams. They can align design goals with business objectives and communicate with stakeholders.
What are the Requirements for Obtaining PMP Certification?
To be eligible for the PMP exam, candidates must meet certain requirements. These are set by the Project Management Institute. These require 4,500 hours of project management work in the past eight years (or 7,500 with a secondary degree). They also require 35 hours of project management education. Once they meet the criteria, candidates can apply for the PMP exam and start preparing for the certification.
To get PMP certification, you must meet certain education and work experience requirements. Candidates must have a four-year degree. They need 36 months of project management experience. Also, they need 35 hours of project management education. With a high school diploma or an associate's degree, you need 60 months of project management experience and 35 hours of education.
How to Prepare for the PMP Certification Exam?
Preparing for the PMP exam requires dedication, time, and effort. Many resources exist to help candidates prepare for the exam. These include PMP courses, training programs, study guides, and practice exams. Candidates can boost their chances of passing the PMP exam on their first try. They should invest in proper prep and study the exam's project management methods and tools.
Preparing for the PMP Certification Exam requires a strategic approach. First, review the PMBOK® Guide and other study materials. Then, create a detailed study plan that includes key topics, formulas, and processes. Take mock exams and PMP simulations. They will help you with the exam format and time management.
What are the Benefits of Obtaining PMP Certification?
A PMP certification has many benefits for media and design professionals. These benefits include: 1. Increased job prospects. 2. Higher earning potential. 3. Better project management skills. 4. Greater industry credibility. PMP certification holders are in a global project management community. It offers networking and professional development resources.
PMP certification has many benefits. It boosts career prospects and earning potential. It is globally recognized as a standard for project management excellence. The certification gives pros key skills in leadership, risk management, and stakeholder communication. It helps them manage projects better. Also, PMP certification builds a strong network. It gives access to valuable resources and insights from other certified project managers.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a PMP certification can greatly impact media and design professionals' careers. By proving their project management skills, individuals can advance in competitive industries. A PMP certification can boost job prospects and career growth. It helps in managing media and design projects more effectively. To boost your project management skills and stand out in media and design, get a PMP certification. It may unlock your full potential.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast world, project management is key to success in media and design. A PMP certification can create new opportunities. It can help professionals stand out in competitive job markets. Let's explore how a PMP certification can help media and design workers.
What is PMP Certification?
PMP stands for Project Management Professional. It is a globally recognized certification from the Project Management Institute (PMI). It validates a professional's expertise in project management. This certification shows that individuals can lead project teams. They can deliver results within the limits of time, budget, and resources.
How can PMP Certification Benefit Media Industry Professionals?
In the fast-paced media industry, project management skills are vital for success. They are key to executing media projects. A PMP certification can help media pros. It can streamline processes and improve project delivery. It applies to planning and executing media campaigns and managing production schedules. Also, a PMP certification can boost credibility. This can lead to more job opportunities and career growth in the media sector.
How can PMP Certification Benefit Design Industry Professionals?
Similarly, in the fast-changing design field, project management is vital. It turns creative visions into reality. Design professionals with a PMP can manage design projects. They can work with cross-functional teams. They will ensure projects finish on time and within budget. A PMP certification can boost design professionals' careers. It shows their expertise and meets the design industry's high demands.
PMP certification can greatly benefit design professionals. It gives them structured project management skills. This helps them manage complex, multi-disciplinary projects efficiently. It streamlines workflows and manages budgets, timelines, and resources. This ensures smoother project delivery. Also, PMP-certified professionals are better at leading creative teams. They can align design goals with business objectives and communicate with stakeholders.
What are the Requirements for Obtaining PMP Certification?
To be eligible for the PMP exam, candidates must meet certain requirements. These are set by the Project Management Institute. These require 4,500 hours of project management work in the past eight years (or 7,500 with a secondary degree). They also require 35 hours of project management education. Once they meet the criteria, candidates can apply for the PMP exam and start preparing for the certification.
To get PMP certification, you must meet certain education and work experience requirements. Candidates must have a four-year degree. They need 36 months of project management experience. Also, they need 35 hours of project management education. With a high school diploma or an associate's degree, you need 60 months of project management experience and 35 hours of education.
How to Prepare for the PMP Certification Exam?
Preparing for the PMP exam requires dedication, time, and effort. Many resources exist to help candidates prepare for the exam. These include PMP courses, training programs, study guides, and practice exams. Candidates can boost their chances of passing the PMP exam on their first try. They should invest in proper prep and study the exam's project management methods and tools.
Preparing for the PMP Certification Exam requires a strategic approach. First, review the PMBOK® Guide and other study materials. Then, create a detailed study plan that includes key topics, formulas, and processes. Take mock exams and PMP simulations. They will help you with the exam format and time management.
What are the Benefits of Obtaining PMP Certification?
A PMP certification has many benefits for media and design professionals. These benefits include: 1. Increased job prospects. 2. Higher earning potential. 3. Better project management skills. 4. Greater industry credibility. PMP certification holders are in a global project management community. It offers networking and professional development resources.
PMP certification has many benefits. It boosts career prospects and earning potential. It is globally recognized as a standard for project management excellence. The certification gives pros key skills in leadership, risk management, and stakeholder communication. It helps them manage projects better. Also, PMP certification builds a strong network. It gives access to valuable resources and insights from other certified project managers.
How to obtain PMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a PMP certification can greatly impact media and design professionals' careers. By proving their project management skills, individuals can advance in competitive industries. A PMP certification can boost job prospects and career growth. It helps in managing media and design projects more effectively. To boost your project management skills and stand out in media and design, get a PMP certification. It may unlock your full potential.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
PgMP Certification Challenges and Overcoming Strategies
Certifications in project management are highly valued in today's competitive job market. The PgMP (Program Management Professional) certification, offered by the Project Management Institute (PMI), is specifically designed for professionals who oversee multiple projects and programs. However, obtaining the PgMP certification is no easy feat. This article will discuss the challenges of getting PgMP certification. We will provide strategies to overcome these obstacles.
The Challenges
1. Professional Development:
A key challenge in obtaining the PgMP certification is meeting the education and experience requirements set by PMI. Applicants must have a bachelor's degree, or equivalent. They also need 4 years of project management experience. Additionally, they must have 6,000 hours of project management and 10,500 hours of program management experience. This can be a significant barrier for individuals who are relatively new to the field of project management.
Professional Development is essential for individuals seeking to enhance their skills and advance their careers. It has a mix of learning options. They include workshops, certifications, mentorships, and networking events. These help professionals stay current with industry trends and improve their skills. Continuous professional development helps you grow. It also boosts your job prospects and chances for advancement in today's competitive job market.
2. Certification Exam:
The PgMP certification exam is known for its difficulty and comprehensive nature. The exam consists of 170 multiple-choice questions that must be completed within four hours. Many candidates find the exam to be challenging due to its extensive coverage of project and program management topics.
3. Study Materials and Preparation:
Finding the right study materials and preparing for the exam can be a daunting task. Many resources exist, like books, courses, and guides. It's hard to find the best ones for exam prep.
4. Career Advancement:
Earning the PgMP certification can boost your career. But, the process is time-consuming and tough. Balancing work, study, and personal life can be difficult for many professionals seeking to enhance their credentials.
Overcoming Strategies
1. Develop a Study Plan:
A detailed study plan can help you stay organized. It should outline your study schedule, exam date, and materials. Break down the topics into manageable sections and allocate specific time for each subject.
2. Join a Study Group:
Joining a study group with like-minded individuals can help. It can provide support, motivation, and a sense of community during your preparation. Study groups can also help you gain different perspectives on challenging topics and share study tips and resources.
3. Time Management:
Effective time management is critical when preparing for the PgMP certification exam. Find your most productive study hours. Then, set a dedicated time to study. Balance this with work and personal commitments.
4. Utilize Online Resources:
Use online courses, practice tests, and study materials from trusted sources to boost your study efforts. Online resources provide flexibility and convenience, allowing you to study at your own pace.
5. Seek Professional Development Opportunities:
Engage in workshops, seminars, and conferences to boost your project management skills. Continuous learning and improvement are essential for success in the field of project management.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, getting the PgMP certification is tough but rewarding. It can greatly improve your job prospects. By understanding the challenges and using the strategies in this article, you can overcome obstacles. You can then succeed in your quest to become a Program Management Professional. Remember, to conquer the PgMP certification, you need to persevere, be dedicated, and have a strategy.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
Certifications in project management are highly valued in today's competitive job market. The PgMP (Program Management Professional) certification, offered by the Project Management Institute (PMI), is specifically designed for professionals who oversee multiple projects and programs. However, obtaining the PgMP certification is no easy feat. This article will discuss the challenges of getting PgMP certification. We will provide strategies to overcome these obstacles.
The Challenges
1. Professional Development:
A key challenge in obtaining the PgMP certification is meeting the education and experience requirements set by PMI. Applicants must have a bachelor's degree, or equivalent. They also need 4 years of project management experience. Additionally, they must have 6,000 hours of project management and 10,500 hours of program management experience. This can be a significant barrier for individuals who are relatively new to the field of project management.
Professional Development is essential for individuals seeking to enhance their skills and advance their careers. It has a mix of learning options. They include workshops, certifications, mentorships, and networking events. These help professionals stay current with industry trends and improve their skills. Continuous professional development helps you grow. It also boosts your job prospects and chances for advancement in today's competitive job market.
2. Certification Exam:
The PgMP certification exam is known for its difficulty and comprehensive nature. The exam consists of 170 multiple-choice questions that must be completed within four hours. Many candidates find the exam to be challenging due to its extensive coverage of project and program management topics.
3. Study Materials and Preparation:
Finding the right study materials and preparing for the exam can be a daunting task. Many resources exist, like books, courses, and guides. It's hard to find the best ones for exam prep.
4. Career Advancement:
Earning the PgMP certification can boost your career. But, the process is time-consuming and tough. Balancing work, study, and personal life can be difficult for many professionals seeking to enhance their credentials.
Overcoming Strategies
1. Develop a Study Plan:
A detailed study plan can help you stay organized. It should outline your study schedule, exam date, and materials. Break down the topics into manageable sections and allocate specific time for each subject.
2. Join a Study Group:
Joining a study group with like-minded individuals can help. It can provide support, motivation, and a sense of community during your preparation. Study groups can also help you gain different perspectives on challenging topics and share study tips and resources.
3. Time Management:
Effective time management is critical when preparing for the PgMP certification exam. Find your most productive study hours. Then, set a dedicated time to study. Balance this with work and personal commitments.
4. Utilize Online Resources:
Use online courses, practice tests, and study materials from trusted sources to boost your study efforts. Online resources provide flexibility and convenience, allowing you to study at your own pace.
5. Seek Professional Development Opportunities:
Engage in workshops, seminars, and conferences to boost your project management skills. Continuous learning and improvement are essential for success in the field of project management.
How to obtain PgMP certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, getting the PgMP certification is tough but rewarding. It can greatly improve your job prospects. By understanding the challenges and using the strategies in this article, you can overcome obstacles. You can then succeed in your quest to become a Program Management Professional. Remember, to conquer the PgMP certification, you need to persevere, be dedicated, and have a strategy.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
How AI is Revolutionizing Business Analysis for Insights
In today's fast-paced business world, you must use advanced tech. It is key to staying ahead of the competition. A technology that will change how businesses analyze data is AI. AI could transform business analysis. It can use machine learning, automation, predictive analytics, and big data. This article will explore how AI is changing business analysis. It is driving efficiency, innovation, and digital transformation.
The Power of AI in Business Analysis
AI can analyze huge amounts of data, faster than any human. AI can use machine learning to automate complex data analysis. It can identify patterns and generate insights in real-time. It improves decision-making. It helps businesses optimize operations and plan using data insights.
AI is revolutionizing business analysis. It changes how firms use data for strategic decisions. Machine learning and predictive analytics can help business analysts. They can find deeper insights and trends. This will improve efficiency and customer engagement. Also, AI tools enable real-time data analysis. They help businesses respond quickly to market changes and customer needs. This fosters a more agile, responsive business environment.
Transforming Operations with Intelligent Systems
AI-powered tools, like neural networks and cognitive systems, are changing business operations. These systems can adapt to market changes. They can boost productivity and efficiency. AI is helping businesses stay competitive in the fast-changing digital world. It does this by streamlining processes and automating decision-making.
Intelligent systems are changing industries. They boost efficiency and decision-making. AI, machine learning, and automation can help organizations. They can streamline workflows, cut costs, and improve services. These intelligent systems enable real-time data analysis . They also help businesses adapt to market changes and consumer demands.
Revolutionizing Data Analysis and Visualization
AI is revolutionizing the way businesses interpret and visualize data. AI algorithms can, through advanced analytics, find patterns. They can uncover hidden links and insights that human analysts may miss. AI-driven data visualization tools can help businesses. They can understand their data better and make smarter decisions.
Revolutionizing data analysis and visualization means using advanced tech. This includes AI and machine learning. They can turn raw data into insightful stories. These innovations allow organizations to create dynamic, interactive visuals. They enhance understanding and aid decision-making. They also make complex data accessible to more people. By using real-time analytics and easy-to-use visual tools, businesses can streamline operations. They can also create a data-driven culture that drives growth and innovation.
The Future of Business Analysis with AI
As we move towards Industry 4.0, the role of AI in business analysis will only continue to grow. AI will help businesses adapt to new technologies. It will enhance their competitiveness and future-proof their operations. AI-powered solutions can help businesses use their data. They can drive innovation in decision-making.
Business analysis is increasingly tied to artificial intelligence (AI). Analysts are using AI to improve data-driven decisions and to streamline processes. Machine learning algorithms can help analysts find insights in large datasets. This aids predictive analytics and trend forecasting. As AI evolves, business analysts will be key. They will integrate new technologies into organizations, driving efficiency and innovation.
Unlocking the Power of Data-Driven Insights
AI leads a new era of analytics. Businesses can now use their data to gain strategic insights. AI-driven data modeling and new tech help businesses make better, data-driven decisions. These will improve their performance and profits.
Enhancing Strategic Forecasting and Decision-Making
AI is revolutionizing the way businesses conduct strategic forecasting and make decisions. AI tools can help businesses adapt to market changes. They can analyze trends and make quick decisions using real-time insights. It boosts efficiency and helps businesses stay ahead in a fast-changing world.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the transformative power of AI in business analysis is clear. By using AI solutions, businesses can unlock new opportunities. They can also optimize resources and drive innovation in their operations. In the future, businesses using AI will be better able to handle the digital age's challenges. They will be set for long-term success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In today's fast-paced business world, you must use advanced tech. It is key to staying ahead of the competition. A technology that will change how businesses analyze data is AI. AI could transform business analysis. It can use machine learning, automation, predictive analytics, and big data. This article will explore how AI is changing business analysis. It is driving efficiency, innovation, and digital transformation.
The Power of AI in Business Analysis
AI can analyze huge amounts of data, faster than any human. AI can use machine learning to automate complex data analysis. It can identify patterns and generate insights in real-time. It improves decision-making. It helps businesses optimize operations and plan using data insights.
AI is revolutionizing business analysis. It changes how firms use data for strategic decisions. Machine learning and predictive analytics can help business analysts. They can find deeper insights and trends. This will improve efficiency and customer engagement. Also, AI tools enable real-time data analysis. They help businesses respond quickly to market changes and customer needs. This fosters a more agile, responsive business environment.
Transforming Operations with Intelligent Systems
AI-powered tools, like neural networks and cognitive systems, are changing business operations. These systems can adapt to market changes. They can boost productivity and efficiency. AI is helping businesses stay competitive in the fast-changing digital world. It does this by streamlining processes and automating decision-making.
Intelligent systems are changing industries. They boost efficiency and decision-making. AI, machine learning, and automation can help organizations. They can streamline workflows, cut costs, and improve services. These intelligent systems enable real-time data analysis . They also help businesses adapt to market changes and consumer demands.
Revolutionizing Data Analysis and Visualization
AI is revolutionizing the way businesses interpret and visualize data. AI algorithms can, through advanced analytics, find patterns. They can uncover hidden links and insights that human analysts may miss. AI-driven data visualization tools can help businesses. They can understand their data better and make smarter decisions.
Revolutionizing data analysis and visualization means using advanced tech. This includes AI and machine learning. They can turn raw data into insightful stories. These innovations allow organizations to create dynamic, interactive visuals. They enhance understanding and aid decision-making. They also make complex data accessible to more people. By using real-time analytics and easy-to-use visual tools, businesses can streamline operations. They can also create a data-driven culture that drives growth and innovation.
The Future of Business Analysis with AI
As we move towards Industry 4.0, the role of AI in business analysis will only continue to grow. AI will help businesses adapt to new technologies. It will enhance their competitiveness and future-proof their operations. AI-powered solutions can help businesses use their data. They can drive innovation in decision-making.
Business analysis is increasingly tied to artificial intelligence (AI). Analysts are using AI to improve data-driven decisions and to streamline processes. Machine learning algorithms can help analysts find insights in large datasets. This aids predictive analytics and trend forecasting. As AI evolves, business analysts will be key. They will integrate new technologies into organizations, driving efficiency and innovation.
Unlocking the Power of Data-Driven Insights
AI leads a new era of analytics. Businesses can now use their data to gain strategic insights. AI-driven data modeling and new tech help businesses make better, data-driven decisions. These will improve their performance and profits.
Enhancing Strategic Forecasting and Decision-Making
AI is revolutionizing the way businesses conduct strategic forecasting and make decisions. AI tools can help businesses adapt to market changes. They can analyze trends and make quick decisions using real-time insights. It boosts efficiency and helps businesses stay ahead in a fast-changing world.
How to obtain Business Analysis certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, the transformative power of AI in business analysis is clear. By using AI solutions, businesses can unlock new opportunities. They can also optimize resources and drive innovation in their operations. In the future, businesses using AI will be better able to handle the digital age's challenges. They will be set for long-term success.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Reviving CMDB Effectively Through IT Service Management
In IT operations, a fast-paced field, a central hub is vital. It must manage all configuration items. This is where Configuration Management Database (CMDB) comes into play. With the resurgence of CMDB, organizations see its value. A well-maintained, up-to-date database can streamline IT service management.
What is CMDB and Why is it Important?
A Configuration Management Database (CMDB) is a central store. It holds information about all configuration items in an organization's IT infrastructure. This includes hardware assets, software assets, relationships between items, and more. CMDB is vital for asset, change, and incident management. It's also key for service desk operations. A complete CMDB helps organizations understand their IT environment. It reduces risks, improves decision-making, and boosts service delivery. It also plays a key role in ITIL (IT Infrastructure Library) practices. It provides a foundation for implementing IT service management best practices.
Benefits of CMDB Implementation
-
Improved visibility and control over IT assets and configurations
-
Enhanced incident, change, and problem management processes
-
Streamlined service desk operations and increased efficiency
-
Better decision-making based on accurate and up-to-date information
-
Alignment with ITIL best practices and compliance requirements
-
Enhanced IT operations by reducing downtime and improving service quality
Best Practices for Successful CMDB Implementation
-
Define clear objectives and scope for the CMDB project
-
Align CMDB processes with IT service management goals
-
Engage stakeholders across different IT functions
-
Ensure data accuracy and quality through data reconciliation and regular updates
-
Implement automation for data collection and maintenance
-
Establish proper governance and security measures to protect sensitive information
-
Provide ongoing training for users and administrators
-
Regularly audit and monitor the CMDB for compliance and performance optimization
CMDB Integration and Architecture
It's crucial to integrate the CMDB with other IT tools. These include service, asset, and monitoring management systems. This will maximize its benefits. A well-planned CMDB architecture ensures scalability, security, and performance optimization. CMDB integration allows for smooth data exchange and relationship mapping between systems. It improves visibility and efficiency.
CMDB Integration and Architecture is vital. It ensures that all IT infrastructure components are accurately mapped and managed. A good CMDB improves visibility into asset relationships. It also helps decision-making and supports proactive IT service management. Integrating CMDBs with other IT tools can automate workflows. It also creates a single source of truth. This will boost efficiency and cut operational risks.
The Future of CMDB: Embracing Automation and Analytics
As technology evolves, the role of CMDB in IT operations is critical. Automation tools are being used to streamline data collection and updates. They also ensure data accuracy. Analytics are being added to CMDB systems. They will provide insights for better decision-making and monitoring.
The future of CMDBs is in automation and advanced analytics. They will help organizations streamline IT asset management. AI and machine learning can help businesses. They can improve data accuracy, decision-making, and responses to changes in IT. This evolution boosts efficiency. It helps organizations align IT with business goals. This fosters a more agile, responsive IT landscape.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a renewed interest in CMDBs is changing IT asset management. Organizations can unlock the CMDB's full potential. They should use best practices. They must integrate with other IT tools. They should apply automation and analytics. This will improve IT service management and efficiency.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
Read More
In IT operations, a fast-paced field, a central hub is vital. It must manage all configuration items. This is where Configuration Management Database (CMDB) comes into play. With the resurgence of CMDB, organizations see its value. A well-maintained, up-to-date database can streamline IT service management.
What is CMDB and Why is it Important?
A Configuration Management Database (CMDB) is a central store. It holds information about all configuration items in an organization's IT infrastructure. This includes hardware assets, software assets, relationships between items, and more. CMDB is vital for asset, change, and incident management. It's also key for service desk operations. A complete CMDB helps organizations understand their IT environment. It reduces risks, improves decision-making, and boosts service delivery. It also plays a key role in ITIL (IT Infrastructure Library) practices. It provides a foundation for implementing IT service management best practices.
Benefits of CMDB Implementation
-
Improved visibility and control over IT assets and configurations
-
Enhanced incident, change, and problem management processes
-
Streamlined service desk operations and increased efficiency
-
Better decision-making based on accurate and up-to-date information
-
Alignment with ITIL best practices and compliance requirements
-
Enhanced IT operations by reducing downtime and improving service quality
Best Practices for Successful CMDB Implementation
-
Define clear objectives and scope for the CMDB project
-
Align CMDB processes with IT service management goals
-
Engage stakeholders across different IT functions
-
Ensure data accuracy and quality through data reconciliation and regular updates
-
Implement automation for data collection and maintenance
-
Establish proper governance and security measures to protect sensitive information
-
Provide ongoing training for users and administrators
-
Regularly audit and monitor the CMDB for compliance and performance optimization
CMDB Integration and Architecture
It's crucial to integrate the CMDB with other IT tools. These include service, asset, and monitoring management systems. This will maximize its benefits. A well-planned CMDB architecture ensures scalability, security, and performance optimization. CMDB integration allows for smooth data exchange and relationship mapping between systems. It improves visibility and efficiency.
CMDB Integration and Architecture is vital. It ensures that all IT infrastructure components are accurately mapped and managed. A good CMDB improves visibility into asset relationships. It also helps decision-making and supports proactive IT service management. Integrating CMDBs with other IT tools can automate workflows. It also creates a single source of truth. This will boost efficiency and cut operational risks.
The Future of CMDB: Embracing Automation and Analytics
As technology evolves, the role of CMDB in IT operations is critical. Automation tools are being used to streamline data collection and updates. They also ensure data accuracy. Analytics are being added to CMDB systems. They will provide insights for better decision-making and monitoring.
The future of CMDBs is in automation and advanced analytics. They will help organizations streamline IT asset management. AI and machine learning can help businesses. They can improve data accuracy, decision-making, and responses to changes in IT. This evolution boosts efficiency. It helps organizations align IT with business goals. This fosters a more agile, responsive IT landscape.
How to obtain ITSM certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
-
Project Management: PMP, CAPM ,PMI RMP
-
Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
-
Business Analysis: CBAP, CCBA, ECBA
-
Agile Training: PMI-ACP , CSM , CSPO
-
Scrum Training: CSM
-
DevOps
-
Program Management: PgMP
-
Cloud Technology: Exin Cloud Computing
-
Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
Conclusion
In conclusion, a renewed interest in CMDBs is changing IT asset management. Organizations can unlock the CMDB's full potential. They should use best practices. They must integrate with other IT tools. They should apply automation and analytics. This will improve IT service management and efficiency.
Contact Us For More Information:
Visit : www.icertglobal.com Email : info@icertglobal.com
DevOps vs. GitOps: Key Differences & How to Choose Wisely
In the fast-evolving world of software, we need better methods. They should streamline processes and boost collaboration. Two such methodologies, DevOps and GitOps, have gained significant traction in recent years. Both aim to improve deployment speed and efficiency. But, they approach this in different ways. This article explores the key differences between DevOps and GitOps. It outlines their principles, practices, and tools. We'll also provide insights to help organizations choose the best approach for their goals.
Table Of Contents
- Understanding DevOps
- Understanding GitOps
- Key Differences Between DevOps and GitOps
- When to Choose DevOps
- When to Choose GitOps
- Conclusion
Understanding DevOps
DevOps is a movement. It promotes collaboration between development (Dev) and operations (Ops) teams. It aims to shorten the software development lifecycle. It does this by integrating software development with IT operations. It also seeks to deliver high-quality software. The primary goals of DevOps include:
- CI/CD: DevOps practices promote frequent code changes. These are automatically tested and deployed, reducing time to market.
- DevOps breaks down silos between teams. It creates a collaborative environment where developers and operations staff work closely together.
- Automation: Many DevOps processes use it to improve efficiency and reduce errors. It's especially helpful in testing and deployment.
- Monitoring and Feedback: Continuous monitoring of production applications allows for quick issue identification. This enables teams to respond rapidly to failures.
Key Tools for DevOps
- CI/CD Tools: Jenkins, GitLab CI, CircleCI
- Configuration Management: Ansible, Chef, Puppet
- Containerization: Docker, Kubernetes
- Monitoring and Logging: Prometheus, Grafana, ELK Stack
Understanding GitOps
GitOps is a newer approach that builds on DevOps. It aims to use Git as the single source of truth for apps and infrastructure. It should be declarative. It uses Git repos to manage application code and infrastructure configs. This streamlines deployment and operations. The core tenets of GitOps include:
- Declarative Configuration: It describes the states of infrastructure and apps. This allows for easier management and change tracking.
- Version Control: All changes to infrastructure and apps are in Git. It provides an audit trail and enables easy rollback to previous versions.
- Automated Deployment: Changes pushed to the Git repo trigger automated deployment processes. These are often managed by continuous deployment tools.
- Improved Security and Compliance: GitOps allows teams to enforce security and compliance standards. It does this using Git's built-in version control and change-tracking features.
Key Tools for GitOps
- Git Repositories: GitHub, GitLab, Bitbucket
- Continuous Deployment Tools: Argo CD, Flux
- Infrastructure as Code (IaC): Terraform, Pulumi
Key Differences Between DevOps and GitOps
While DevOps and GitOps share common goals, their approaches differ significantly:
Methodology and Focus
- DevOps: It focuses on the collaboration of development and operations teams. It covers the entire software development lifecycle.
- GitOps: It focuses on using Git to manage and deploy applications and infrastructure.
Infrastructure Management
- DevOps can use various tools and practices for infrastructure management. This includes both declarative and imperative methods.
- GitOps: It uses only declarative configs. This makes it easier to manage the desired state of apps and infrastructure.
Change Management
- DevOps: Changes can happen in many ways. They may must manual processes or many tools for tracking and deployment.
- GitOps: All changes are tracked in Git. This provides a clear, auditable trail of what changes were made, when, and by whom.
Automation and Rollback
- DevOps: Automation is a major focus. But rollbacks can be complex due to the tools and processes used.
- GitOps: Rollbacks are simpler. We can restore previous states from the Git history.
Team Dynamics
- DevOps: It encourages collaboration between cross-functional teams. However, it may not enforce strict version control for infrastructure.
- GitOps: It promotes a Git-centric culture. It requires collaboration between dev and ops teams. It emphasizes using Git as a core tool for all changes.
When to Choose DevOps
DevOps is ideal for groups that want to boost collaboration. It helps improve the speed and quality of software delivery. Here are some scenarios where DevOps may be more suitable:
- Large, Complex Projects: Organizations with complex software may enjoy DevOps. Its collaborative, iterative approach suits such projects.
- Mixed Environments: Companies in cloud and on-premises environments may find DevOps appealing. Its flexibility can integrate various tools and practices.
- Cultural Transformation: DevOps helps organizations that want a culture of collaboration and innovation.
When to Choose GitOps
GitOps is great for teams that want to simplify deployments. It enforces strict version control. Consider GitOps if:
- GitOps can help. It offers a clear, auditable way to manage changes. This is ideal if your organization prefers a declarative approach to infrastructure.
- Emphasis on Automation: GitOps practices will help organizations. They want to automate deployment and improve efficiency.
- Cloud-Native Environments: GitOps is often ideal for cloud-native apps. They use containers and microservices. GitOps helps teams manage these systems well.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In the battle of DevOps vs. GitOps, it depends on your needs and goals. DevOps is a broad, collaborative framework. It integrates development and operations. It is ideal for organizations that want to boost efficiency. On the other hand, GitOps is more focused. It uses Git as the sole source of truth for deployment and infrastructure management. It's perfect for teams wanting to simplify processes and boost automation.
By knowing the key differences and uses of both methods, organizations can decide wisely. This will align with their goals. It will improve software delivery, efficiency, and collaboration. Both DevOps and GitOps can help you succeed in digital transformation. In today's competitive world, you must embrace these practices.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
In the fast-evolving world of software, we need better methods. They should streamline processes and boost collaboration. Two such methodologies, DevOps and GitOps, have gained significant traction in recent years. Both aim to improve deployment speed and efficiency. But, they approach this in different ways. This article explores the key differences between DevOps and GitOps. It outlines their principles, practices, and tools. We'll also provide insights to help organizations choose the best approach for their goals.
Table Of Contents
- Understanding DevOps
- Understanding GitOps
- Key Differences Between DevOps and GitOps
- When to Choose DevOps
- When to Choose GitOps
- Conclusion
Understanding DevOps
DevOps is a movement. It promotes collaboration between development (Dev) and operations (Ops) teams. It aims to shorten the software development lifecycle. It does this by integrating software development with IT operations. It also seeks to deliver high-quality software. The primary goals of DevOps include:
- CI/CD: DevOps practices promote frequent code changes. These are automatically tested and deployed, reducing time to market.
- DevOps breaks down silos between teams. It creates a collaborative environment where developers and operations staff work closely together.
- Automation: Many DevOps processes use it to improve efficiency and reduce errors. It's especially helpful in testing and deployment.
- Monitoring and Feedback: Continuous monitoring of production applications allows for quick issue identification. This enables teams to respond rapidly to failures.
Key Tools for DevOps
- CI/CD Tools: Jenkins, GitLab CI, CircleCI
- Configuration Management: Ansible, Chef, Puppet
- Containerization: Docker, Kubernetes
- Monitoring and Logging: Prometheus, Grafana, ELK Stack
Understanding GitOps
GitOps is a newer approach that builds on DevOps. It aims to use Git as the single source of truth for apps and infrastructure. It should be declarative. It uses Git repos to manage application code and infrastructure configs. This streamlines deployment and operations. The core tenets of GitOps include:
- Declarative Configuration: It describes the states of infrastructure and apps. This allows for easier management and change tracking.
- Version Control: All changes to infrastructure and apps are in Git. It provides an audit trail and enables easy rollback to previous versions.
- Automated Deployment: Changes pushed to the Git repo trigger automated deployment processes. These are often managed by continuous deployment tools.
- Improved Security and Compliance: GitOps allows teams to enforce security and compliance standards. It does this using Git's built-in version control and change-tracking features.
Key Tools for GitOps
- Git Repositories: GitHub, GitLab, Bitbucket
- Continuous Deployment Tools: Argo CD, Flux
- Infrastructure as Code (IaC): Terraform, Pulumi
Key Differences Between DevOps and GitOps
While DevOps and GitOps share common goals, their approaches differ significantly:
Methodology and Focus
- DevOps: It focuses on the collaboration of development and operations teams. It covers the entire software development lifecycle.
- GitOps: It focuses on using Git to manage and deploy applications and infrastructure.
Infrastructure Management
- DevOps can use various tools and practices for infrastructure management. This includes both declarative and imperative methods.
- GitOps: It uses only declarative configs. This makes it easier to manage the desired state of apps and infrastructure.
Change Management
- DevOps: Changes can happen in many ways. They may must manual processes or many tools for tracking and deployment.
- GitOps: All changes are tracked in Git. This provides a clear, auditable trail of what changes were made, when, and by whom.
Automation and Rollback
- DevOps: Automation is a major focus. But rollbacks can be complex due to the tools and processes used.
- GitOps: Rollbacks are simpler. We can restore previous states from the Git history.
Team Dynamics
- DevOps: It encourages collaboration between cross-functional teams. However, it may not enforce strict version control for infrastructure.
- GitOps: It promotes a Git-centric culture. It requires collaboration between dev and ops teams. It emphasizes using Git as a core tool for all changes.
When to Choose DevOps
DevOps is ideal for groups that want to boost collaboration. It helps improve the speed and quality of software delivery. Here are some scenarios where DevOps may be more suitable:
- Large, Complex Projects: Organizations with complex software may enjoy DevOps. Its collaborative, iterative approach suits such projects.
- Mixed Environments: Companies in cloud and on-premises environments may find DevOps appealing. Its flexibility can integrate various tools and practices.
- Cultural Transformation: DevOps helps organizations that want a culture of collaboration and innovation.
When to Choose GitOps
GitOps is great for teams that want to simplify deployments. It enforces strict version control. Consider GitOps if:
- GitOps can help. It offers a clear, auditable way to manage changes. This is ideal if your organization prefers a declarative approach to infrastructure.
- Emphasis on Automation: GitOps practices will help organizations. They want to automate deployment and improve efficiency.
- Cloud-Native Environments: GitOps is often ideal for cloud-native apps. They use containers and microservices. GitOps helps teams manage these systems well.
How to obtain DevOps certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In the battle of DevOps vs. GitOps, it depends on your needs and goals. DevOps is a broad, collaborative framework. It integrates development and operations. It is ideal for organizations that want to boost efficiency. On the other hand, GitOps is more focused. It uses Git as the sole source of truth for deployment and infrastructure management. It's perfect for teams wanting to simplify processes and boost automation.
By knowing the key differences and uses of both methods, organizations can decide wisely. This will align with their goals. It will improve software delivery, efficiency, and collaboration. Both DevOps and GitOps can help you succeed in digital transformation. In today's competitive world, you must embrace these practices.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Monitoring Kafka Performance: Key Metrics and Tools Guide
Apache Kafka is key for real-time data processing. It enables data streaming between apps, systems, and services in event-driven architectures. As organizations use Kafka to manage large data, monitoring its performance is vital. It ensures reliability and efficiency. Monitoring Kafka helps you find bottlenecks and optimize resources. It also ensures the system can handle expected loads. This article covers three topics. First, the key metrics to monitor for Kafka's performance. Second, the tools for monitoring. Third, best practices for managing performance.
Table Of Contents
- Understanding Key Metrics for Kafka Performance
- Essential Tools for Monitoring Kafka
- Best Practices for Kafka Monitoring
- Troubleshooting Common Kafka Performance Issues
- Future Considerations for Kafka Performance Monitoring
- Conclusion
Understanding Key Metrics for Kafka Performance
To check Kafka performance, you must know the key metrics. They show the health and efficiency of your Kafka clusters. Here are some key metrics to keep an eye on:
- Throughput: It measures the number of messages produced and consumed in a time. It is measured in messages per second. High throughput indicates that your Kafka cluster is processing data efficiently.
- Latency: Latency refers to the time it takes for a message to be produced and then consumed. It’s crucial to measure both producer and consumer latency. High latency can signal network issues or inefficient processing.
- Consumer lag: This metric shows how many messages a consumer must process. Monitoring consumer lag helps in identifying if consumers are keeping up with producers. If the lag keeps increasing, it might mean consumers cannot process the incoming data.
- Disk Utilization: As Kafka stores messages on disk, monitoring disk usage is essential. High disk usage may cause slowdowns or data loss.
- Network I/O: This metric tracks the amount of data being sent and received over the network. High network I/O can mean your Kafka cluster is under heavy load. You may need to scale resources.
Essential Tools for Monitoring Kafka
The right tools for monitoring Kafka can greatly improve your performance tracking. Here are some popular monitoring tools for Kafka:
- Kafka’s JMX Metrics: Kafka exposes metrics through Java Management Extensions (JMX). JMX allows you to check various Kafka components, including brokers, producers, and consumers. Using JMX, you can gather a wide array of metrics that provide insights into Kafka’s performance.
- Prometheus and Grafana: Prometheus is a strong monitoring system. It collects metrics from targets at specified intervals. When paired with Grafana, a visualization tool, it provides a UI to view Kafka metrics. This combo is popular for monitoring Kafka. It's easy to use and flexible.
- Confluent Control Center: If you are using Confluent Kafka, use the Control Center. It provides a complete monitoring solution. It has a simple interface to view metrics, set alerts, and analyze data. It is particularly helpful for teams using Confluent's Kafka distribution.
- Apache Kafka Manager: This open-source tool lets users manage and check Kafka clusters. It gives insights into cluster health, topics, partitions, and consumer groups. This helps maintain and troubleshoot Kafka deployments.
Datadog and New Relic are third-party monitoring platforms. They offer Kafka integrations. Users can check performance metrics alongside other app metrics. They provide powerful visualization tools, alerting mechanisms, and anomaly detection capabilities.
Best Practices for Kafka Monitoring
To check performance effectively, follow best practices. They ensure reliable tracking.
- Set Up Alerts: Create alerts for critical metrics. Watch for consumer lag, high latency, and low throughput. Alerts can help you proactively identify and address performance issues before they escalate.
- Check Resource Utilization: Watch Kafka's CPU, memory, and disk use. Monitoring resource usage can help identify bottlenecks and inform decisions about scaling.
- Regularly Review Logs: Kafka logs provide valuable information about its operations. Regular log reviews can find errors and performance issues that metrics may miss.
- Establish Baselines: Establish baseline performance metrics to understand normal behavior. You can find issues by comparing current data to historical data.
- Capacity Planning: Regularly assess your Kafka cluster's capacity against anticipated loads. Good capacity planning avoids performance issues from resource exhaustion. It ensures your cluster can handle future growth.
Troubleshooting Common Kafka Performance Issues
Even with diligent monitoring, performance issues can arise. Here are some common performance problems and how to troubleshoot them:
- High Consumer Lag: If you notice increasing consumer lag, check the following:
- Are consumers adequately provisioned? Consider scaling consumer instances.
- Are there processing bottlenecks? Analyze consumer processing logic for inefficiencies.
- Increased Latency: High latency can stem from various sources:
- Network issues: Use network monitoring tools to check for latency.
- Broker performance: Analyze broker metrics to ensure they are not overloaded.
- Low Throughput: If throughput is lower than expected:
- Investigate how producers are performing and make sure they are configured correctly.
- Review the partitioning strategy: Poor partitioning can lead to an uneven load distribution.
Future Considerations for Kafka Performance Monitoring
As Kafka evolves, so do its performance-monitoring needs. Here are a few trends and considerations for future monitoring:
- AI and ML: Using AI and ML for anomaly detection in Kafka can predict issues. This helps teams fix problems before they impact production.
- Cloud-Native Monitoring: As more firms move Kafka to the cloud, it's vital to check its performance. Cloud-native tools can help. They can also provide insights through integrated services.
- Better Visualization Tools: Newer visualization tools can improve how we use performance data. They can lead to quicker decisions.
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Monitoring Kafka performance is vital. It ensures your data streaming system is reliable and efficient. By tracking key metrics, organizations can find performance issues. Metrics include throughput, latency, consumer lag, disk use, and network I/O. To improve Kafka's performance, use the right monitoring tools and practices. Also, be ready to fix common performance issues. As Kafka technology evolves, new trends and tools will emerge. Knowing about them will help keep your data streaming apps fast and scalable. To maximize Kafka's potential as a data integration tool, rank monitoring.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Apache Kafka is key for real-time data processing. It enables data streaming between apps, systems, and services in event-driven architectures. As organizations use Kafka to manage large data, monitoring its performance is vital. It ensures reliability and efficiency. Monitoring Kafka helps you find bottlenecks and optimize resources. It also ensures the system can handle expected loads. This article covers three topics. First, the key metrics to monitor for Kafka's performance. Second, the tools for monitoring. Third, best practices for managing performance.
Table Of Contents
- Understanding Key Metrics for Kafka Performance
- Essential Tools for Monitoring Kafka
- Best Practices for Kafka Monitoring
- Troubleshooting Common Kafka Performance Issues
- Future Considerations for Kafka Performance Monitoring
- Conclusion
Understanding Key Metrics for Kafka Performance
To check Kafka performance, you must know the key metrics. They show the health and efficiency of your Kafka clusters. Here are some key metrics to keep an eye on:
- Throughput: It measures the number of messages produced and consumed in a time. It is measured in messages per second. High throughput indicates that your Kafka cluster is processing data efficiently.
- Latency: Latency refers to the time it takes for a message to be produced and then consumed. It’s crucial to measure both producer and consumer latency. High latency can signal network issues or inefficient processing.
- Consumer lag: This metric shows how many messages a consumer must process. Monitoring consumer lag helps in identifying if consumers are keeping up with producers. If the lag keeps increasing, it might mean consumers cannot process the incoming data.
- Disk Utilization: As Kafka stores messages on disk, monitoring disk usage is essential. High disk usage may cause slowdowns or data loss.
- Network I/O: This metric tracks the amount of data being sent and received over the network. High network I/O can mean your Kafka cluster is under heavy load. You may need to scale resources.
Essential Tools for Monitoring Kafka
The right tools for monitoring Kafka can greatly improve your performance tracking. Here are some popular monitoring tools for Kafka:
- Kafka’s JMX Metrics: Kafka exposes metrics through Java Management Extensions (JMX). JMX allows you to check various Kafka components, including brokers, producers, and consumers. Using JMX, you can gather a wide array of metrics that provide insights into Kafka’s performance.
- Prometheus and Grafana: Prometheus is a strong monitoring system. It collects metrics from targets at specified intervals. When paired with Grafana, a visualization tool, it provides a UI to view Kafka metrics. This combo is popular for monitoring Kafka. It's easy to use and flexible.
- Confluent Control Center: If you are using Confluent Kafka, use the Control Center. It provides a complete monitoring solution. It has a simple interface to view metrics, set alerts, and analyze data. It is particularly helpful for teams using Confluent's Kafka distribution.
- Apache Kafka Manager: This open-source tool lets users manage and check Kafka clusters. It gives insights into cluster health, topics, partitions, and consumer groups. This helps maintain and troubleshoot Kafka deployments.
Datadog and New Relic are third-party monitoring platforms. They offer Kafka integrations. Users can check performance metrics alongside other app metrics. They provide powerful visualization tools, alerting mechanisms, and anomaly detection capabilities.
Best Practices for Kafka Monitoring
To check performance effectively, follow best practices. They ensure reliable tracking.
- Set Up Alerts: Create alerts for critical metrics. Watch for consumer lag, high latency, and low throughput. Alerts can help you proactively identify and address performance issues before they escalate.
- Check Resource Utilization: Watch Kafka's CPU, memory, and disk use. Monitoring resource usage can help identify bottlenecks and inform decisions about scaling.
- Regularly Review Logs: Kafka logs provide valuable information about its operations. Regular log reviews can find errors and performance issues that metrics may miss.
- Establish Baselines: Establish baseline performance metrics to understand normal behavior. You can find issues by comparing current data to historical data.
- Capacity Planning: Regularly assess your Kafka cluster's capacity against anticipated loads. Good capacity planning avoids performance issues from resource exhaustion. It ensures your cluster can handle future growth.
Troubleshooting Common Kafka Performance Issues
Even with diligent monitoring, performance issues can arise. Here are some common performance problems and how to troubleshoot them:
- High Consumer Lag: If you notice increasing consumer lag, check the following:
- Are consumers adequately provisioned? Consider scaling consumer instances.
- Are there processing bottlenecks? Analyze consumer processing logic for inefficiencies.
- Increased Latency: High latency can stem from various sources:
- Network issues: Use network monitoring tools to check for latency.
- Broker performance: Analyze broker metrics to ensure they are not overloaded.
- Low Throughput: If throughput is lower than expected:
- Investigate how producers are performing and make sure they are configured correctly.
- Review the partitioning strategy: Poor partitioning can lead to an uneven load distribution.
Future Considerations for Kafka Performance Monitoring
As Kafka evolves, so do its performance-monitoring needs. Here are a few trends and considerations for future monitoring:
- AI and ML: Using AI and ML for anomaly detection in Kafka can predict issues. This helps teams fix problems before they impact production.
- Cloud-Native Monitoring: As more firms move Kafka to the cloud, it's vital to check its performance. Cloud-native tools can help. They can also provide insights through integrated services.
- Better Visualization Tools: Newer visualization tools can improve how we use performance data. They can lead to quicker decisions.
How to obtain Apache Kafka certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
In Conclusion, Monitoring Kafka performance is vital. It ensures your data streaming system is reliable and efficient. By tracking key metrics, organizations can find performance issues. Metrics include throughput, latency, consumer lag, disk use, and network I/O. To improve Kafka's performance, use the right monitoring tools and practices. Also, be ready to fix common performance issues. As Kafka technology evolves, new trends and tools will emerge. Knowing about them will help keep your data streaming apps fast and scalable. To maximize Kafka's potential as a data integration tool, rank monitoring.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Top RPA Tools of 2024: In-Depth Review & Expert Insights
Robotic Process Automation (RPA) has transformed business operations. It automates repetitive tasks, streamlines workflows, and boosts productivity. As we enter 2024, the RPA landscape is evolving. New tools and upgrades are boosting efficiency in many industries. This review examines the top RPA tools of 2024. It assesses their features, usability, and impact on performance.
This guide is for you. It will help both business leaders and IT pros. Business leaders will learn about RPA solutions. IT pros will find the latest advancements. Both will gain insights to make informed decisions.
Table Of Contents
- UiPath: The Leader in RPA
- Automation Anywhere: Empowering Digital Transformation
- Blue Prism: The Enterprise-Grade Solution
- Pega: The Low-Code Automation Tool
- Microsoft Power Automate: Seamless integration with the Microsoft ecosystem
- Conclusion
UiPath: The Leader in RPA
Key Features:
- User-Friendly Interface: UiPath has a simple drag-and-drop interface. It is easy for users without a tech background.
- AI Integration: UiPath, with AI, enables the automation of complex tasks.
- The UiPath Academy has extensive training modules. They help users master the platform quickly.
Overview: UiPath, a pioneer in RPA, is a top choice for businesses. They want to automate processes at scale. Its many features, a strong community, and great support make it a top choice for enterprises.
Automation Anywhere: Empowering Digital Transformation
Key Features:
- Cloud-Native Platform: Automation Anywhere provides a fully cloud-based solution. It allows for easy deployment and scalability.
- Bot Store: A marketplace for pre-built bots. Users can use them for automation, saving time and resources.
- Cognitive Capabilities: Its AI features enable the automation of decision-making processes, enhancing efficiency.
Overview: Automation Anywhere is notable for its cloud-first, digital transformation focus. Its cognitive abilities and pre-built bots make it perfect for businesses. They want to speed up their automation efforts.
Blue Prism: The Enterprise-Grade Solution
Key Features:
- Robust Security: Blue Prism prioritizes security. It offers advanced compliance and governance features for enterprise needs.
- Scalability: The tool is designed to scale across many departments and locations seamlessly.
- Integration: Strong APIs enable integration with various apps, boosting cross-platform usability.
Overview: Blue Prism's enterprise-grade features suit large, complex organizations. Its focus on security and compliance lets businesses automate processes. This is while following regulations.
Pega: The Low-Code Automation Tool
Key Features:
- Low-Code Development: Pega lets users automate processes with low-code tools. This speeds up implementation.
- Dynamic Case Management: The platform has advanced case management tools. They boost process visibility and control.
- Customer Engagement: Pega's RPA works with its customer tools to optimize interactions.
Overview: Pega is a low-code solution. It allows businesses to automate processes with speed, without needing extensive programming skills. Its customer engagement features boost its value. They make it a great choice for groups focused on improving customer experience.
Microsoft Power Automate: Seamless integration with the Microsoft ecosystem
Key Features:
- It works perfectly with Office 365, Dynamics 365, and Azure.
- Pre-Built Templates: It offers a variety of pre-built automation templates. They make automation easier for users.
- AI Builder: The AI capabilities enable users to build intelligent workflows easily.
Overview: Microsoft Power Automate is great for organizations using the Microsoft ecosystem. Its integration and templates make it easy for all users.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As the RPA landscape evolves, businesses have many tools. They can use them to boost efficiency and drive digital transformation. In 2024, the top RPA tools are UiPath, Automation Anywhere, Blue Prism, Pega, and Microsoft Power Automate. Each has unique features for specific organizational needs.
When choosing an RPA tool, organizations must consider a few factors. These include:
- Ease of use
- Scalability
- Integration
- Fit with their digital transformation goals
The right RPA solution can boost productivity. It lets employees focus on higher-value tasks. This fosters innovation and growth in a competitive landscape.
In summary, the tools in this review enable automation. They will create a more agile and responsive business environment in 2024 and beyond. Embracing these technologies can help an organization adapt to market changes. It can also improve operations.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
Robotic Process Automation (RPA) has transformed business operations. It automates repetitive tasks, streamlines workflows, and boosts productivity. As we enter 2024, the RPA landscape is evolving. New tools and upgrades are boosting efficiency in many industries. This review examines the top RPA tools of 2024. It assesses their features, usability, and impact on performance.
This guide is for you. It will help both business leaders and IT pros. Business leaders will learn about RPA solutions. IT pros will find the latest advancements. Both will gain insights to make informed decisions.
Table Of Contents
- UiPath: The Leader in RPA
- Automation Anywhere: Empowering Digital Transformation
- Blue Prism: The Enterprise-Grade Solution
- Pega: The Low-Code Automation Tool
- Microsoft Power Automate: Seamless integration with the Microsoft ecosystem
- Conclusion
UiPath: The Leader in RPA
Key Features:
- User-Friendly Interface: UiPath has a simple drag-and-drop interface. It is easy for users without a tech background.
- AI Integration: UiPath, with AI, enables the automation of complex tasks.
- The UiPath Academy has extensive training modules. They help users master the platform quickly.
Overview: UiPath, a pioneer in RPA, is a top choice for businesses. They want to automate processes at scale. Its many features, a strong community, and great support make it a top choice for enterprises.
Automation Anywhere: Empowering Digital Transformation
Key Features:
- Cloud-Native Platform: Automation Anywhere provides a fully cloud-based solution. It allows for easy deployment and scalability.
- Bot Store: A marketplace for pre-built bots. Users can use them for automation, saving time and resources.
- Cognitive Capabilities: Its AI features enable the automation of decision-making processes, enhancing efficiency.
Overview: Automation Anywhere is notable for its cloud-first, digital transformation focus. Its cognitive abilities and pre-built bots make it perfect for businesses. They want to speed up their automation efforts.
Blue Prism: The Enterprise-Grade Solution
Key Features:
- Robust Security: Blue Prism prioritizes security. It offers advanced compliance and governance features for enterprise needs.
- Scalability: The tool is designed to scale across many departments and locations seamlessly.
- Integration: Strong APIs enable integration with various apps, boosting cross-platform usability.
Overview: Blue Prism's enterprise-grade features suit large, complex organizations. Its focus on security and compliance lets businesses automate processes. This is while following regulations.
Pega: The Low-Code Automation Tool
Key Features:
- Low-Code Development: Pega lets users automate processes with low-code tools. This speeds up implementation.
- Dynamic Case Management: The platform has advanced case management tools. They boost process visibility and control.
- Customer Engagement: Pega's RPA works with its customer tools to optimize interactions.
Overview: Pega is a low-code solution. It allows businesses to automate processes with speed, without needing extensive programming skills. Its customer engagement features boost its value. They make it a great choice for groups focused on improving customer experience.
Microsoft Power Automate: Seamless integration with the Microsoft ecosystem
Key Features:
- It works perfectly with Office 365, Dynamics 365, and Azure.
- Pre-Built Templates: It offers a variety of pre-built automation templates. They make automation easier for users.
- AI Builder: The AI capabilities enable users to build intelligent workflows easily.
Overview: Microsoft Power Automate is great for organizations using the Microsoft ecosystem. Its integration and templates make it easy for all users.
How to obtain RPA certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
As the RPA landscape evolves, businesses have many tools. They can use them to boost efficiency and drive digital transformation. In 2024, the top RPA tools are UiPath, Automation Anywhere, Blue Prism, Pega, and Microsoft Power Automate. Each has unique features for specific organizational needs.
When choosing an RPA tool, organizations must consider a few factors. These include:
- Ease of use
- Scalability
- Integration
- Fit with their digital transformation goals
The right RPA solution can boost productivity. It lets employees focus on higher-value tasks. This fosters innovation and growth in a competitive landscape.
In summary, the tools in this review enable automation. They will create a more agile and responsive business environment in 2024 and beyond. Embracing these technologies can help an organization adapt to market changes. It can also improve operations.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
XenDesktop Migration: A Comprehensive Step-by-Step Guide
As businesses shift to digital, they need efficient VDI solutions. Citrix XenDesktop is a powerful platform. It lets organizations deliver virtualized desktops and apps to users. This enhances flexibility, security, and management. Migrating to XenDesktop can seem daunting. A structured methodology, on the other hand, can promote an effortless transition. This guide will help you migrate to XenDesktop. It will optimize your VDI for better performance and user satisfaction.
Table Of Contents
- Understanding XenDesktop Architecture
- Assessing Current Infrastructure and Requirements
- Designing the XenDesktop environment
- Implementing the Migration Plan
- Training and Support for End Users
- Conclusion
Understanding XenDesktop Architecture
Before migrating, it is vital to understand XenDesktop's core architecture.
- Components: XenDesktop has several parts. They are the Delivery Controller, Virtual Delivery Agents (VDAs), StoreFront, and Citrix Director. Each plays a crucial role in managing and delivering virtual desktops and applications.
- Deployment Options: XenDesktop can be deployed in various ways. It can be on-premises, in the cloud, or in a hybrid setup. Understanding your organization's requirements will help determine the best approach for your environment.
Assessing Current Infrastructure and Requirements
A successful migration starts with a thorough assessment of your systems and users' needs.
- Inventory: Create an inventory of current hardware, software, and network configurations. Test compatibility with XenDesktop.
- User Needs: Gather feedback from end users to know their needs. This includes their app usage patterns and performance expectations.
- Capacity Planning: Analyze the number of users and the types of workloads they will run. This assessment helps in determining the necessary resources for the XenDesktop environment.
Designing the XenDesktop environment
After reviewing your setup, we must design a strong XenDesktop architecture.
- Layout Design: Decide where to place your XenDesktop components. This ensures top performance and scalability. This may include many Delivery Controllers for load balancing.
- Resource Allocation: Use the capacity data to divide enough resources among your VMs. Consider storage, CPU, and memory needs.
- Security Considerations: To protect sensitive data in the VDI, use security measures. These include network segmentation and access control.
Implementing the Migration Plan
With a design in place, it’s time to install the migration plan.
- Phased Approach: Consider migrating in phases, starting with a pilot group. This allows for testing and adjustments before a full rollout.
- Deployment of Components: Install and configure the required XenDesktop components. These include the Delivery Controller and StoreFront. Use Citrix's best practices.
- Testing: Before going live, test the environment. Check the user experience, app performance, and failover processes.
Training and Support for End Users
An often-overlooked part of migration is preparing end users to use the new system.
- User Training: Train users on how to access and use the new XenDesktop environment.
- Create clear documentation. It should outline common tasks and troubleshooting tips.
- Ongoing Support: Set up a support system for users with post-migration issues. This could include a dedicated help desk or knowledge base.
How to obtain XenDesktop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Migrating to Citrix XenDesktop is a big change. It requires careful planning, execution, and support.
Organizations can achieve a better VDI solution by:
- Understanding the architecture.
- Assessing the current infrastructure.
- Designing the environment.
- Implementing the migration plan.
- Providing user training.
Remember, a successful migration requires thorough preparation and ongoing support. This helps IT and end users maximize the benefits of XenDesktop.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com
Read More
As businesses shift to digital, they need efficient VDI solutions. Citrix XenDesktop is a powerful platform. It lets organizations deliver virtualized desktops and apps to users. This enhances flexibility, security, and management. Migrating to XenDesktop can seem daunting. A structured methodology, on the other hand, can promote an effortless transition. This guide will help you migrate to XenDesktop. It will optimize your VDI for better performance and user satisfaction.
Table Of Contents
- Understanding XenDesktop Architecture
- Assessing Current Infrastructure and Requirements
- Designing the XenDesktop environment
- Implementing the Migration Plan
- Training and Support for End Users
- Conclusion
Understanding XenDesktop Architecture
Before migrating, it is vital to understand XenDesktop's core architecture.
- Components: XenDesktop has several parts. They are the Delivery Controller, Virtual Delivery Agents (VDAs), StoreFront, and Citrix Director. Each plays a crucial role in managing and delivering virtual desktops and applications.
- Deployment Options: XenDesktop can be deployed in various ways. It can be on-premises, in the cloud, or in a hybrid setup. Understanding your organization's requirements will help determine the best approach for your environment.
Assessing Current Infrastructure and Requirements
A successful migration starts with a thorough assessment of your systems and users' needs.
- Inventory: Create an inventory of current hardware, software, and network configurations. Test compatibility with XenDesktop.
- User Needs: Gather feedback from end users to know their needs. This includes their app usage patterns and performance expectations.
- Capacity Planning: Analyze the number of users and the types of workloads they will run. This assessment helps in determining the necessary resources for the XenDesktop environment.
Designing the XenDesktop environment
After reviewing your setup, we must design a strong XenDesktop architecture.
- Layout Design: Decide where to place your XenDesktop components. This ensures top performance and scalability. This may include many Delivery Controllers for load balancing.
- Resource Allocation: Use the capacity data to divide enough resources among your VMs. Consider storage, CPU, and memory needs.
- Security Considerations: To protect sensitive data in the VDI, use security measures. These include network segmentation and access control.
Implementing the Migration Plan
With a design in place, it’s time to install the migration plan.
- Phased Approach: Consider migrating in phases, starting with a pilot group. This allows for testing and adjustments before a full rollout.
- Deployment of Components: Install and configure the required XenDesktop components. These include the Delivery Controller and StoreFront. Use Citrix's best practices.
- Testing: Before going live, test the environment. Check the user experience, app performance, and failover processes.
Training and Support for End Users
An often-overlooked part of migration is preparing end users to use the new system.
- User Training: Train users on how to access and use the new XenDesktop environment.
- Create clear documentation. It should outline common tasks and troubleshooting tips.
- Ongoing Support: Set up a support system for users with post-migration issues. This could include a dedicated help desk or knowledge base.
How to obtain XenDesktop certification?
We are an Education Technology company providing certification training courses to accelerate careers of working professionals worldwide. We impart training through instructor-led classroom workshops, instructor-led live virtual training sessions, and self-paced e-learning courses.
We have successfully conducted training sessions in 108 countries across the globe and enabled thousands of working professionals to enhance the scope of their careers.
Our enterprise training portfolio includes in-demand and globally recognized certification training courses in Project Management, Quality Management, Business Analysis, IT Service Management, Agile and Scrum, Cyber Security, Data Science, and Emerging Technologies. Download our Enterprise Training Catalog from https://www.icertglobal.com/corporate-training-for-enterprises.php and https://www.icertglobal.com/index.php
Popular Courses include:
- Project Management: PMP, CAPM ,PMI RMP
- Quality Management: Six Sigma Black Belt ,Lean Six Sigma Green Belt, Lean Management, Minitab,CMMI
- Business Analysis: CBAP, CCBA, ECBA
- Agile Training: PMI-ACP , CSM , CSPO
- Scrum Training: CSM
- DevOps
- Program Management: PgMP
- Cloud Technology: Exin Cloud Computing
- Citrix Client Adminisration: Citrix Cloud Administration
The 10 top-paying certifications to target in 2024 are:
- Certified Information Systems Security Professional® (CISSP)
- AWS Certified Solutions Architect
- Google Certified Professional Cloud Architect
- Big Data Certification
- Data Science Certification
- Certified In Risk And Information Systems Control (CRISC)
- Certified Information Security Manager(CISM)
- Project Management Professional (PMP)® Certification
- Certified Ethical Hacker (CEH)
- Certified Scrum Master (CSM)
Conclusion
Migrating to Citrix XenDesktop is a big change. It requires careful planning, execution, and support.
Organizations can achieve a better VDI solution by:
- Understanding the architecture.
- Assessing the current infrastructure.
- Designing the environment.
- Implementing the migration plan.
- Providing user training.
Remember, a successful migration requires thorough preparation and ongoing support. This helps IT and end users maximize the benefits of XenDesktop.
Contact Us :
Contact Us For More Information:
Visit :www.icertglobal.com Email : info@icertglobal.com


.webp)

.webp)
.jpg)


















.webp)

-compressed.webp)

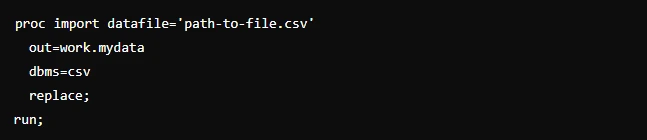
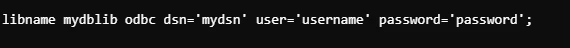


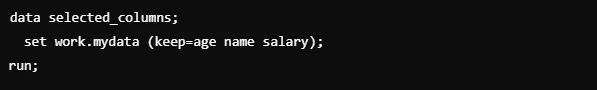

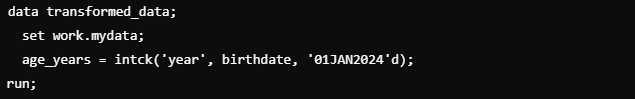
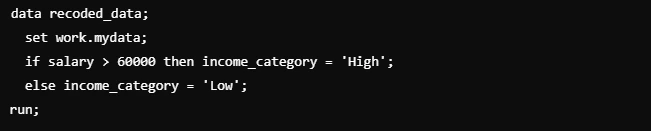
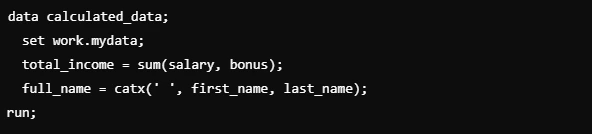

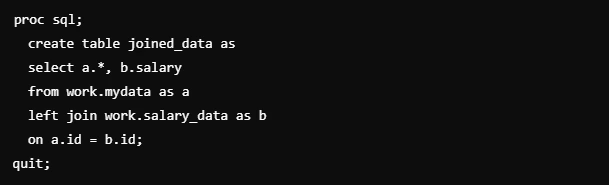

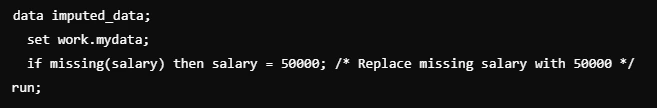







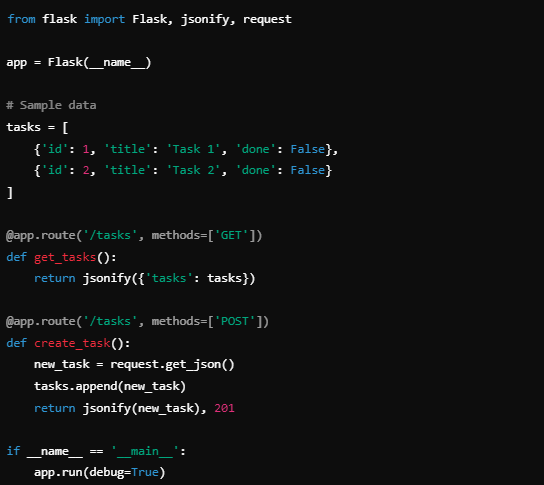


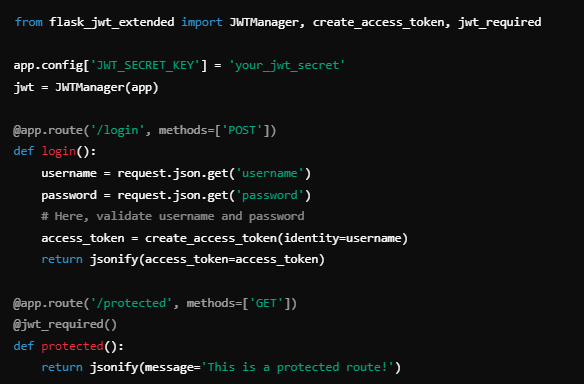
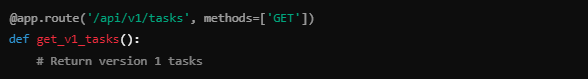







-compressed.webp)